CSNB113: System Administration - 12 th Topic: Services Networking Services
|
|
|
- Augusta West
- 5 years ago
- Views:
Transcription
1 CSNB113: System Administration - 12 th Topic: Services Networking Services
2 Services - Servers The term server has two meanings: It is the hardware ('machine') that runs as a server. It also is a service that serves the user whenever the user requests a service from the service (server). A physical machine can easily run a larger number of servcies (servers), and servers can also run on a very normal desktop. Confused? Naturally! Again: A server is either a physical or a functional unit. It depends very much on the context what is meant by the term. Server and service has the same linguistic root as servant. And in principle there is a reason for this: A server (as a function) "sits there and waits". It waits for a client to connect to it, and demand its services. A webserver is running, and listening for an incoming request. Then it will reply to that request. Very practically: A webserver sits and waits for (example) you to connect by typing the address in the address bar of your web-browser. When you press 'Enter', your request is sent to the server, who sits there and waits to return a reply: the webpage that you have requested.
3 Network Services In the last lecture, we learned how to configure interfaces, with IP-address and netmask. This is not easy, though system administrators need to know. Also, when you type this is no valid IP-address (compare with the slides of last week ). So we use some servers (services) to help us to configure networking. We use a service to 'know' which IP-address goes with a Domain Name. Last not least: when you send your request to this request needs to be routed to the webserver of Google, and of course the reply (content of the web site) needs to be send (routed) back to you. All these are done by servers: configuration: DHCP server looking up IP-address for a Domain: DNS directing and sending the packets: routers
4 DHCP This is about the most simple of the networking services: It stands for Dynamic Host Configuration Protocol When you bring in a new machine into the network, and this machine has no networking information set up (no IP-address), the client (== new machine) will 'ask around' on the local network, if there is a DHCP server, and request an IP-address from it. If there is a DHCP server, it will offer an IP-address, netmask, and a number of other information to that client. If the client is happy (it usually is), it will use this information, set its interface to the IP-address and netmask as offered, and accept the offer. Therefore DHCP has 3 basic phases: request offer accept The IP-addresses that the DHCP offers must be unique (cannot be had by any other machine), and are given out on a temporary basis. If the client needs / wants the address beyond the expiration time, it will ask for a renewal
5 DNS Type of Service This is a much more difficult protocol. There are millions of Domain Names in use world-wide, and it is rather complicated on how to retrieve the corresponding IP-address from a domain name. This task is done by so-called Domain Name Servers. How would a server in e.g. South America 'know' about the IP-address of (It actually is ) Can all DNS servers everywhere in the world know all domain names? And when you register your own domain, how can all (thousands if not millions) of DNS get to know of this new domain? This is therefore a hierarchical look-up process: And this is quite similar to what we saw in the last chapter about a postal address; only it is written on a single line here: my edu uniten metalab Therefore, 'my' is considered a top-level domain.
6 DNS - Recursion my edu uniten metalab Sticking to the example: The DNS in South-America doesn't need to 'know' about metalab. It is enough, if it 'knows' a DNS that is able to help it further. It is sufficient, in South-America, a 'know' the IPaddress that knows how to help. (That is, a server responsible for the domains within Malaysia.) This server in turn, still doesn't know about metalab, but it 'knows' about the lower domains: It might have the IP-addresses of all DNSes in Malaysian educational institutions and organisations ('edu'). And this list then contains the DNS in Uniten, where Uniten staff (ITMS) can add or delete a subdomain ('www', 'metalab', etc.)
7 Routing Routing is probably the most difficult task that services on the network need to do. There are jams on networks, sometimes one path is faster than another (depending on daytime or weekday), sometimes political occurrences interest more Internet users than usually, sometimes some routes are out of order. Therefore, on large networks, routing is done in a dynamical manner, and routes change continuously. Due to the difficulty of the topic, the details will be explained in future subjects. What remains to be noted, is that we run a number of servers (services) for all those tasks; we usually run them on servers; not on workstations or desktops. A DHCP server is usually run on a physical server, a DNS is usually run on a physical server, a machine that implements routing services is usually run on a server (and not on a desktop/workstation).
8 Services Of course, all this is done to offer services to the users of the network or the Internet. The most famous one is the World-Wide-Web (WWW). The client here is known as web browser, while the server is known as web server. But there are far more: FTP File Transfer Protocol SMTP Simple Mail Transfer Protocol SSH Secure Shell and many others This is a good moment, also under consideration of the lab exercises, to ponder about the differences between server and desktop/workstation/laptop. While the letter only make sense with a person sitting in front of the keyboard (and mouse), a server can run easily and usefully without any user directly operating it. Rather, a server is usually used (and operated) from afar. Servers also have usually a low-level, low-power graphics card; if at all.
9 Server Administration Tasks We discussed these earlier, in the beginning of this course. Now we are much better, have learned a lot more, and can understand much better, that a server is usually run unattended (at least physically unattended: there is often no administrator or operator next to it; nobody directly interfacing the physical machine; often, there is no monitor, at times no keyboard even, and seldom a mouse.) While a user of a desktop/workstation/tower/laptop can see what the machine actually does, the server has nobody to continuously see its (monitor) output. Therefore, the server logs are relevant, that note and store and save all relevant occurrences, incidents, possible attacks, usage, even free space on hard disks, logons, reboots, mail being sent and received (not the content, but recipient), success or failure of sending. It is relevant to have a record (also with respect to quality control) about all happenings on the server, generation and deletion of accounts, amount of data transferred, etc.
10 Times! With all of these logs, and services, we understand by now the relevance of the correct times and dates. While on a workstation this is not so relevant, we need to guarantee this for servers. And it is not astonishing that there are also time servers available, and we can run time services on our (physical) servers. There are some different time protocols: The early and simple Time Protocol, and the more advanced and more modern Network Time Protocol (NTP). These services offer a simple client to set the time correctly (Time Protocol); respectively to synchronise continuously with other time servers on the local network and / or the Internet (NTP). With the more simple Time Protocol, it is still possible to set the time to be correct within one second; which is mostly sufficient. With NTP it is possible to obtain a precision of the time within less than 50 microseconds off the correct time. (On Windows this is not guaranteed:
11 Times - Examples $ rdate -p Tue Feb 22 11:56:48 MYT 2011 $ rdate -p rdate: Could not connect socket: Connection refused $ ntpdate -q server , stratum 4, offset , delay Feb 11:57:35 ntpdate[3041]: step time server offset sec $ ntpdate Feb 11:59:58 ntpdate[3042]: bind() fails: Permission denied $ sudo ntpdate [sudo] password for user: 22 Feb 11:59:58 ntpdate[3054]: step time server offset sec $ ntpdate -q server , stratum 4, offset , delay Feb 12:00:08 ntpdate[3056]: adjust time server offset sec $
12 References
DESCRIPTION OF TYPICAL NETWORK SERVICES ON SERVERS
 DESCRIPTION OF TYPICAL NETWORK SERVICES ON SERVERS Before you start Objectives: Familiarize yourself with the services such as File and Print, WWW, FTP, E- mail, Faxing, Remote Access, DHCP, DNS and WINS.
DESCRIPTION OF TYPICAL NETWORK SERVICES ON SERVERS Before you start Objectives: Familiarize yourself with the services such as File and Print, WWW, FTP, E- mail, Faxing, Remote Access, DHCP, DNS and WINS.
NETWORK CONFIGURATION AND SERVICES. route add default gw /etc/init.d/apache restart
 NETWORK CONFIGURATION AND SERVICES route add default gw 192.168.0.1 /etc/init.d/apache restart NETWORK CONFIGURATION There are two main approaches to configuring a machine for network access: Static configuration
NETWORK CONFIGURATION AND SERVICES route add default gw 192.168.0.1 /etc/init.d/apache restart NETWORK CONFIGURATION There are two main approaches to configuring a machine for network access: Static configuration
Firewall Simulation COMP620
 Firewall Simulation COMP620 Firewall Simulation The simulation allows participants to configure their own simulated firewalls using Cisco-like syntax. Participants can take benign or malicious actions
Firewall Simulation COMP620 Firewall Simulation The simulation allows participants to configure their own simulated firewalls using Cisco-like syntax. Participants can take benign or malicious actions
Web Mechanisms. Draft: 2/23/13 6:54 PM 2013 Christopher Vickery
 Web Mechanisms Draft: 2/23/13 6:54 PM 2013 Christopher Vickery Introduction While it is perfectly possible to create web sites that work without knowing any of their underlying mechanisms, web developers
Web Mechanisms Draft: 2/23/13 6:54 PM 2013 Christopher Vickery Introduction While it is perfectly possible to create web sites that work without knowing any of their underlying mechanisms, web developers
Introduction to TCP/IP
 Introduction to TCP/IP Properties and characteristics of TCP/IP IPv4 IPv6 Public vs private vs APIPA/link local Static vs dynamic Client-side DNS settings Client-side DHCP Subnet mask vs CIDR Gateway TCP/IP
Introduction to TCP/IP Properties and characteristics of TCP/IP IPv4 IPv6 Public vs private vs APIPA/link local Static vs dynamic Client-side DNS settings Client-side DHCP Subnet mask vs CIDR Gateway TCP/IP
Services: Monitoring and Logging. 9/16/2018 IST346: Info Tech Management & Administration 1
 Services: Monitoring and Logging 9/16/2018 IST346: Info Tech Management & Administration 1 Recall: Server vs. Service A server is a computer. A service is an offering provided by server(s). HTTP 9/16/2018
Services: Monitoring and Logging 9/16/2018 IST346: Info Tech Management & Administration 1 Recall: Server vs. Service A server is a computer. A service is an offering provided by server(s). HTTP 9/16/2018
INTERNET BASICS / FILE OPERATIONS Defining Information Technology
 L A B 2 INTERNET BASICS / FILE OPERATIONS Defining Information Technology This lab covers fundamental concepts of network organization, focusing on the client-server model for network resources such as
L A B 2 INTERNET BASICS / FILE OPERATIONS Defining Information Technology This lab covers fundamental concepts of network organization, focusing on the client-server model for network resources such as
LECTURE WK4 NETWORKING
 LECTURE WK4 NETWORKING Workbook and Quiz Workbook o Due in WK5 o Must hand in a hard copy to the tutor as well as an online submission Quiz o In the practical class o 30mins to complete the quiz o Short,
LECTURE WK4 NETWORKING Workbook and Quiz Workbook o Due in WK5 o Must hand in a hard copy to the tutor as well as an online submission Quiz o In the practical class o 30mins to complete the quiz o Short,
Much is done on the Server, it20:
 IT341 Introduction to System Administration Project V Implementing DNS A domain name server (DNS)... translates a human-readable address such as itvm21-1a.it.cs.umb.edu into an IP address such as 158.121.106.128
IT341 Introduction to System Administration Project V Implementing DNS A domain name server (DNS)... translates a human-readable address such as itvm21-1a.it.cs.umb.edu into an IP address such as 158.121.106.128
Introduction. An introduction to the equipment and organization of the Internet Lab.
 Introduction An introduction to the equipment and organization of the Internet Lab. Some material in this slide set is copyrighted, Pearson Education, 2004 Internet Lab Equipment 4 Linux PCs 4 Cisco Routers
Introduction An introduction to the equipment and organization of the Internet Lab. Some material in this slide set is copyrighted, Pearson Education, 2004 Internet Lab Equipment 4 Linux PCs 4 Cisco Routers
Networking Notes. Common Internet Speeds. Online Speed Test myspeed.visualware.com
 Networking Notes Common Internet Speeds Dial Up 56 kbs 1000kbs = 1 mbs (1 user capacity) DSL 1.5 mbs (1 channel 10 user capacity) T1 1.5 mbs (24 channel 500 user capacity) Scalable Ethernet (Adjustable
Networking Notes Common Internet Speeds Dial Up 56 kbs 1000kbs = 1 mbs (1 user capacity) DSL 1.5 mbs (1 channel 10 user capacity) T1 1.5 mbs (24 channel 500 user capacity) Scalable Ethernet (Adjustable
File services. Domains, DNS DHCP. Server Scripts. Intranet and Extranets. Web services. HNC COMPUTING - Network Concepts
 File services Domains, DNS 1 DHCP Server Scripts Intranet and Extranets Web services HNC COMPUTING - Network Concepts A domain is a logical grouping of networked computers that share a central directory
File services Domains, DNS 1 DHCP Server Scripts Intranet and Extranets Web services HNC COMPUTING - Network Concepts A domain is a logical grouping of networked computers that share a central directory
Semester 2, 2018: Lab 1
 Semester 2, 2018: Lab 1 S2 2018 Lab 1 This lab has two parts. Part A is intended to help you familiarise yourself with the computing environment found on the CSIT lab computers which you will be using
Semester 2, 2018: Lab 1 S2 2018 Lab 1 This lab has two parts. Part A is intended to help you familiarise yourself with the computing environment found on the CSIT lab computers which you will be using
Additional laboratory
 Additional laboratory This is addicional laboratory session where you will get familiar with the working environment. Firstly, you will learn about the different servers present in the lab and how desktops
Additional laboratory This is addicional laboratory session where you will get familiar with the working environment. Firstly, you will learn about the different servers present in the lab and how desktops
Guide to TCP/IP, Third Edition. Chapter 8: The Dynamic Host Configuration Protocol
 Guide to TCP/IP, Third Edition Chapter 8: The Dynamic Host Configuration Protocol 1 Objectives Understand the basic services DHCP offers to its clients and explain its background Understand the specifics
Guide to TCP/IP, Third Edition Chapter 8: The Dynamic Host Configuration Protocol 1 Objectives Understand the basic services DHCP offers to its clients and explain its background Understand the specifics
CSC 101: Lab #1 Introduction and Setup Due Date: 5:00pm, day after your lab session
 Name: WFU Email: Lab Section: Tuesday, 9:30 Tuesday, 12:00 Tuesday, 1:30 Tuesday, 3:00 Thursday, 3:00 CSC 101: Lab #1 Introduction and Setup Due Date: 5:00pm, day after your lab session Purpose: The purpose
Name: WFU Email: Lab Section: Tuesday, 9:30 Tuesday, 12:00 Tuesday, 1:30 Tuesday, 3:00 Thursday, 3:00 CSC 101: Lab #1 Introduction and Setup Due Date: 5:00pm, day after your lab session Purpose: The purpose
Application Layer: OSI and TCP/IP Models
 Application Layer Application Layer: OSI and TCP/IP Models The communication process between two communicating nodes is actually a communication process between two applications on these devices. Service
Application Layer Application Layer: OSI and TCP/IP Models The communication process between two communicating nodes is actually a communication process between two applications on these devices. Service
Setup for LAUSDnet - Windows 95/98/ME Revised 8/1/2001
 Setup for LAUSDnet - Windows 95/98/ME Revised 8/1/2001 Dial Up Networking Setup The following assumes that the Dial-Up Networking portions of Windows 95/98/ME have already been installed. If they have
Setup for LAUSDnet - Windows 95/98/ME Revised 8/1/2001 Dial Up Networking Setup The following assumes that the Dial-Up Networking portions of Windows 95/98/ME have already been installed. If they have
Lecture 05 Application Layer - I
 Computer Networks and Internet Protocol Prof. Soumya Kanti Ghosh Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur Lecture 05 Application Layer - I Hi. So, we will
Computer Networks and Internet Protocol Prof. Soumya Kanti Ghosh Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur Lecture 05 Application Layer - I Hi. So, we will
Session 16 Windows 7 Professional DNS & Active Directory
 Session 16 Windows 7 Professional DNS & Active Directory Fall 2011 ITE153 Operating Systems 1 Session 16 Windows 7 Professional Configuring TCP/IP Addressing & Name Resolution Fall 2011 ITE153 Operating
Session 16 Windows 7 Professional DNS & Active Directory Fall 2011 ITE153 Operating Systems 1 Session 16 Windows 7 Professional Configuring TCP/IP Addressing & Name Resolution Fall 2011 ITE153 Operating
1 BACKGROUND 2 SETTING UP THE HOME AND GOOGLE DRIVES THROUGH WEBSTORAGE. Using the Home Drive to Save from U5 Cloud Updated 8.31.
 Using the Home Drive to Save from U5 Cloud Contents 1 Background... 1 2 Setting Up the Home and Google Drives through webstorage... 1 3 Saving a Document to the Home Drive... 2 4 Finding and Opening Your
Using the Home Drive to Save from U5 Cloud Contents 1 Background... 1 2 Setting Up the Home and Google Drives through webstorage... 1 3 Saving a Document to the Home Drive... 2 4 Finding and Opening Your
CS 716: Introduction to communication networks. Instructor: Sridhar Iyer Demo by: Swati Patil IIT Bombay
 CS 716: Introduction to communication networks - 16 th class; 28 th Sept 2011 Instructor: Sridhar Iyer Demo by: Swati Patil IIT Bombay What is IP address An identifier for a computer or device on a TCP/IP
CS 716: Introduction to communication networks - 16 th class; 28 th Sept 2011 Instructor: Sridhar Iyer Demo by: Swati Patil IIT Bombay What is IP address An identifier for a computer or device on a TCP/IP
Savvius Insight Initial Configuration
 The configuration utility on Savvius Insight lets you configure device, network, time settings, and reporting options. Important! Savvius Insight comes pre-configured to obtain its IP address via DHCP.
The configuration utility on Savvius Insight lets you configure device, network, time settings, and reporting options. Important! Savvius Insight comes pre-configured to obtain its IP address via DHCP.
TENVIS Technology Co., Ltd. User Manual. For H.264 Cameras. Version 1.0.0
 TENVIS Technology Co., Ltd User Manual For H.264 Cameras Version 1.0.0 Catalogue Basic Operation... 3 Hardware Installation... 3 Search Camera... 3 For Internet Explorer... 6 Playback Record Files... 9
TENVIS Technology Co., Ltd User Manual For H.264 Cameras Version 1.0.0 Catalogue Basic Operation... 3 Hardware Installation... 3 Search Camera... 3 For Internet Explorer... 6 Playback Record Files... 9
CyberP3i Course Module Series
 CyberP3i Course Module Series Spring 2017 Designer: Dr. Lixin Wang, Associate Professor Firewall Configuration Firewall Configuration Learning Objectives 1. Be familiar with firewalls and types of firewalls
CyberP3i Course Module Series Spring 2017 Designer: Dr. Lixin Wang, Associate Professor Firewall Configuration Firewall Configuration Learning Objectives 1. Be familiar with firewalls and types of firewalls
Control Centre Manual
 Control Centre Manual Manual version 1.02 March 2009 smots Control Centre USER Guide (Administrator Guide follows at end of document) smots Control Centre login Pick your user category from the drop down
Control Centre Manual Manual version 1.02 March 2009 smots Control Centre USER Guide (Administrator Guide follows at end of document) smots Control Centre login Pick your user category from the drop down
In practice that means at least 200,000,000 computers on the net! How many people use the Internet? As of November 2000:
 Core World Wide Web Technologies: Ethernet, TCP/IP, DNS&Bind, HTTP Henry S. Thompson HCRC Language Technology Group Division of Informatics University of Edinburgh First, some terminology The Web is not
Core World Wide Web Technologies: Ethernet, TCP/IP, DNS&Bind, HTTP Henry S. Thompson HCRC Language Technology Group Division of Informatics University of Edinburgh First, some terminology The Web is not
Sysinstall main menu. Move the cursor down by using the DOWN-ARROW and select Standard.
 Initial Boot from Install Disc 1 Turn on the power for your machine. Sysinstall main menu Immediately place the first CD-ROM of the FreeBSD 5.3 install set in your machine's CD-ROM drive. You'll see an
Initial Boot from Install Disc 1 Turn on the power for your machine. Sysinstall main menu Immediately place the first CD-ROM of the FreeBSD 5.3 install set in your machine's CD-ROM drive. You'll see an
TRANSMISSION CONTROL PROTOCOL. ETI 2506 TELECOMMUNICATION SYSTEMS Monday, 7 November 2016
 TRANSMISSION CONTROL PROTOCOL ETI 2506 TELECOMMUNICATION SYSTEMS Monday, 7 November 2016 ETI 2506 - TELECOMMUNICATION SYLLABUS Principles of Telecom (IP Telephony and IP TV) - Key Issues to remember 1.
TRANSMISSION CONTROL PROTOCOL ETI 2506 TELECOMMUNICATION SYSTEMS Monday, 7 November 2016 ETI 2506 - TELECOMMUNICATION SYLLABUS Principles of Telecom (IP Telephony and IP TV) - Key Issues to remember 1.
COMS3200/7201 Computer Networks 1 (Version 1.0)
 COMS3200/7201 Computer Networks 1 (Version 1.0) Assignment 3 Due 8pm Monday 29 th May 2017. V1 draft (hopefully final) Note that the assignment has three parts Part A, B & C, each worth 50 marks. Total
COMS3200/7201 Computer Networks 1 (Version 1.0) Assignment 3 Due 8pm Monday 29 th May 2017. V1 draft (hopefully final) Note that the assignment has three parts Part A, B & C, each worth 50 marks. Total
Local DNS Attack Lab. 1 Lab Overview. 2 Lab Environment. 2.1 Install and configure the DNS server. SEED Labs Local DNS Attack Lab 1
 SEED Labs Local DNS Attack Lab 1 Local DNS Attack Lab Copyright c 2006-2015 Wenliang Du, Syracuse University. The development of this document is partially funded by the National Science Foundation s Course,
SEED Labs Local DNS Attack Lab 1 Local DNS Attack Lab Copyright c 2006-2015 Wenliang Du, Syracuse University. The development of this document is partially funded by the National Science Foundation s Course,
CS 716: Introduction to communication networks th class; 11 th Nov Instructor: Sridhar Iyer IIT Bombay
 CS 716: Introduction to communication networks - 24 th class; 11 th Nov 2011 Instructor: Sridhar Iyer IIT Bombay Layering: physical communication data application transport network link physical application
CS 716: Introduction to communication networks - 24 th class; 11 th Nov 2011 Instructor: Sridhar Iyer IIT Bombay Layering: physical communication data application transport network link physical application
Deploy the ExtraHop Discover 3100, 6100, 8100, or 9100 Appliances
 Deploy the ExtraHop Discover 3100, 6100, 8100, or 9100 s Published: 2017-12-29 This guide explains how to install the rack-mounted EDA 3100, EDA 6100, EDA 8100, and EDA 9100 ExtraHop Discover appliances.
Deploy the ExtraHop Discover 3100, 6100, 8100, or 9100 s Published: 2017-12-29 This guide explains how to install the rack-mounted EDA 3100, EDA 6100, EDA 8100, and EDA 9100 ExtraHop Discover appliances.
The trace is here: https://kevincurran.org/com320/labs/wireshark/trace-dhcp.pcap
 Lab Exercise DHCP Objective To see how DHCP (Dynamic Host Configuration Protocol) works. The trace is here: https://kevincurran.org/com320/labs/wireshark/trace-dhcp.pcap Network Setup Recall that DHCP
Lab Exercise DHCP Objective To see how DHCP (Dynamic Host Configuration Protocol) works. The trace is here: https://kevincurran.org/com320/labs/wireshark/trace-dhcp.pcap Network Setup Recall that DHCP
Exercise Sheet 2. (Classifications of Operating Systems)
 Exercise Sheet 2 Exercise 1 (Classifications of Operating Systems) 1. At any given moment, only a single program can be executed. What is the technical term for this operation mode? 2. What are half multi-user
Exercise Sheet 2 Exercise 1 (Classifications of Operating Systems) 1. At any given moment, only a single program can be executed. What is the technical term for this operation mode? 2. What are half multi-user
3. Is it correct to say that folders/directories directly contain data? Why or why not?
 Lab 3 Internet Basics This lab covers fundamental concepts of network organization, focusing on the clientserver model for network resources such as web pages and file storage. The procedure includes uploading
Lab 3 Internet Basics This lab covers fundamental concepts of network organization, focusing on the clientserver model for network resources such as web pages and file storage. The procedure includes uploading
Applying for Jobs Online
 Applying for Jobs Online Hi, I m Sarah. I m here to show you how to apply for a job using an online application form. Most jobs now require you to fill out an application on the Internet. In this course
Applying for Jobs Online Hi, I m Sarah. I m here to show you how to apply for a job using an online application form. Most jobs now require you to fill out an application on the Internet. In this course
Overview LEARN. History of Linux Linux Architecture Linux File System Linux Access Linux Commands File Permission Editors Conclusion and Questions
 Lanka Education and Research Network Linux Architecture, Linux File System, Linux Basic Commands 28 th November 2016 Dilum Samarasinhe () Overview History of Linux Linux Architecture Linux File System
Lanka Education and Research Network Linux Architecture, Linux File System, Linux Basic Commands 28 th November 2016 Dilum Samarasinhe () Overview History of Linux Linux Architecture Linux File System
Guide to Networking Essentials, 6 th Edition. Chapter 5: Network Protocols
 Guide to Networking Essentials, 6 th Edition Chapter 5: Network Protocols Objectives Describe the purpose of a network protocol, the layers in the TCP/IP architecture, and the protocols in each TCP/IP
Guide to Networking Essentials, 6 th Edition Chapter 5: Network Protocols Objectives Describe the purpose of a network protocol, the layers in the TCP/IP architecture, and the protocols in each TCP/IP
IT341 Introduction to System Administration Project V Implementing DNS
 IT341 Introduction to System Administration Project V Implementing DNS A domain name server (DNS) translates a human- readable address such as itvm21-1.it.cs.umb.edu into an IP address such as 158.121.106.128.
IT341 Introduction to System Administration Project V Implementing DNS A domain name server (DNS) translates a human- readable address such as itvm21-1.it.cs.umb.edu into an IP address such as 158.121.106.128.
CSCI 1100L: Topics in Computing Lab Lab 1: Introduction to the Lab! Part I
 CSCI 1100L: Topics in Computing Lab Lab 1: Introduction to the Lab! Part I Welcome to your CSCI-1100 Lab! In the fine tradition of the CSCI-1100 course, we ll start off the lab with the classic bad joke
CSCI 1100L: Topics in Computing Lab Lab 1: Introduction to the Lab! Part I Welcome to your CSCI-1100 Lab! In the fine tradition of the CSCI-1100 course, we ll start off the lab with the classic bad joke
Incident Response Tools
 Incident Response Tools James Madison University Dept. of Computer Science June 13, 2013 1 Introduction Being successfully attacked is inevitable. A determined hacker WILL be able to penetrate your network.
Incident Response Tools James Madison University Dept. of Computer Science June 13, 2013 1 Introduction Being successfully attacked is inevitable. A determined hacker WILL be able to penetrate your network.
FIT 100: Fluency with Information Technology
 FIT 100: Fluency with Information Technology Lab 2: Creating Directories and Navigating Directory Structures (or, Where am I, where are my files, and how do I put my files somewhere else?) Local vs. Remote
FIT 100: Fluency with Information Technology Lab 2: Creating Directories and Navigating Directory Structures (or, Where am I, where are my files, and how do I put my files somewhere else?) Local vs. Remote
IT 341 Introduction to System Administration Project I Installing Ubuntu Server on a Virtual Machine
 IT 341 Introduction to System Administration Project I Installing Ubuntu Server on a Virtual Machine Here we create a new virtual machine and install Ubuntu 16.04 LTS Server on it. In this instance, we
IT 341 Introduction to System Administration Project I Installing Ubuntu Server on a Virtual Machine Here we create a new virtual machine and install Ubuntu 16.04 LTS Server on it. In this instance, we
NET INTEGRATION TECHNOLOGIES INC. NET INTEGRATOR MICRO. Quick Start Guide
 NET INTEGRATOR MICRO Quick Start Guide 602-0002-02 Meet Your Net Integrator Micro Front View USB Port Ethernet LED Hard Drive LED Power LED Power button 2 Quick Start Guide Back View DC 12V input connector
NET INTEGRATOR MICRO Quick Start Guide 602-0002-02 Meet Your Net Integrator Micro Front View USB Port Ethernet LED Hard Drive LED Power LED Power button 2 Quick Start Guide Back View DC 12V input connector
UIP1869V User Interface Guide
 UIP1869V User Interface Guide (Firmware version 0.1.8 and later) Table of Contents Opening the UIP1869V's Configuration Utility... 3 Connecting to Your Broadband Modem... 5 Setting up with DHCP... 5 Updating
UIP1869V User Interface Guide (Firmware version 0.1.8 and later) Table of Contents Opening the UIP1869V's Configuration Utility... 3 Connecting to Your Broadband Modem... 5 Setting up with DHCP... 5 Updating
EP2 EP8 User Manual. Copyright 2007,ATAL
 EP2 EP8 User Manual Copyright 2007,ATAL 1) Introduction 1. What is EP? 2. What s the difference between the EP2 and the EP8? 3. How to use this manual 4. EP2 5. EP8 2) Installation 1. Assigning an IP address
EP2 EP8 User Manual Copyright 2007,ATAL 1) Introduction 1. What is EP? 2. What s the difference between the EP2 and the EP8? 3. How to use this manual 4. EP2 5. EP8 2) Installation 1. Assigning an IP address
Solar-Log WEB "Classic 2nd Edition" Manual Installation
 Solar-Log WEB "Classic 2nd Edition" Manual Installation Solar-Log 300 1200 2000 or Firmware 3.x 1 1 Setting up "Classic 2nd Edition" This Quick Start Guide describes the necessary settings to manually
Solar-Log WEB "Classic 2nd Edition" Manual Installation Solar-Log 300 1200 2000 or Firmware 3.x 1 1 Setting up "Classic 2nd Edition" This Quick Start Guide describes the necessary settings to manually
APPLICATION LAYER APPLICATION LAYER : DNS, HTTP, , SMTP, Telnet, FTP, Security-PGP-SSH.
 APPLICATION LAYER : DNS, HTTP, E-mail, SMTP, Telnet, FTP, Security-PGP-SSH. To identify an entity, the Internet used the IP address, which uniquely identifies the connection of a host to the Internet.
APPLICATION LAYER : DNS, HTTP, E-mail, SMTP, Telnet, FTP, Security-PGP-SSH. To identify an entity, the Internet used the IP address, which uniquely identifies the connection of a host to the Internet.
Hands-On Activity. Firewall Simulation. Simulated Network. Firewall Simulation 3/19/2010. On Friday, February 26, we will be meeting in
 Hands-On Activity Firewall Simulation COMP620 On Friday, February 26, we will be meeting in the Graham 212 lab to participate in a firewall configuration simulation. This simulator was written by Dr. Williams
Hands-On Activity Firewall Simulation COMP620 On Friday, February 26, we will be meeting in the Graham 212 lab to participate in a firewall configuration simulation. This simulator was written by Dr. Williams
WorldSecure/Mail Getting Started Guide
 WorldSecure/Mail Getting Started Guide Release 4.3 012-0068-43 The software described in this document is furnished under license and may be used or copied only according to the terms of such license.
WorldSecure/Mail Getting Started Guide Release 4.3 012-0068-43 The software described in this document is furnished under license and may be used or copied only according to the terms of such license.
WA2342 NoSQL Systems Comparison. Lab Server VM Setup Guide. Web Age Solutions Inc. Copyright Web Age Solutions Inc. 1
 WA2342 NoSQL Systems Comparison Lab Server VM Setup Guide Web Age Solutions Inc. Copyright Web Age Solutions Inc. 1 Table of Contents Part 1 - Minimum Hardware Requirements...3 Part 2 - Minimum Software
WA2342 NoSQL Systems Comparison Lab Server VM Setup Guide Web Age Solutions Inc. Copyright Web Age Solutions Inc. 1 Table of Contents Part 1 - Minimum Hardware Requirements...3 Part 2 - Minimum Software
and the Forensic Science CC Spring 2007 Prof. Nehru
 and the Introduction The Internet, (Information superhighway), has opened a medium for people to communicate and to access millions of pieces of information from computers located anywhere on the globe.
and the Introduction The Internet, (Information superhighway), has opened a medium for people to communicate and to access millions of pieces of information from computers located anywhere on the globe.
TCP/IP Client Server Model
 TCP/IP Model Agenda - model & Access - model defined Accessing a server on the Internet Accessing a server on a local network Static vs. Dynamic IP addresses 2013 Microchip Technology Incorporated. All
TCP/IP Model Agenda - model & Access - model defined Accessing a server on the Internet Accessing a server on a local network Static vs. Dynamic IP addresses 2013 Microchip Technology Incorporated. All
CSCI 466 Midterm Networks Fall 2013
 CSCI 466 Midterm Networks Fall 2013 Name: This exam consists of 6 problems on the following 7 pages. You may use your single-sided hand-written 8 ½ x 11 note sheet and a calculator during the exam. No
CSCI 466 Midterm Networks Fall 2013 Name: This exam consists of 6 problems on the following 7 pages. You may use your single-sided hand-written 8 ½ x 11 note sheet and a calculator during the exam. No
Today. An Animated Introduction to Programming. Prerequisites. Computer programming
 Today 1 2 3 4 Computer programming What is this course about? We re making several assumptions about you as a student. In particular, we assume that you have: Never taken a programming course before. Have
Today 1 2 3 4 Computer programming What is this course about? We re making several assumptions about you as a student. In particular, we assume that you have: Never taken a programming course before. Have
TELE 301 Lecture 8: Post
 Last Lecture System installation This Lecture Post installation Next Lecture Wireless networking Overview TELE 301 Lecture 8: Post 1 Post-configuration Create user accounts and environments Sort out the
Last Lecture System installation This Lecture Post installation Next Lecture Wireless networking Overview TELE 301 Lecture 8: Post 1 Post-configuration Create user accounts and environments Sort out the
Network+ Guide to Networks, Seventh Edition Chapter 2, Solutions
 Network+ Guide to Networks, Seventh Edition Chapter 2, Solutions Review Questions 1. Which part of a MAC address is unique to each manufacturer? A. The network identifier B. The OUI C. The device identifier
Network+ Guide to Networks, Seventh Edition Chapter 2, Solutions Review Questions 1. Which part of a MAC address is unique to each manufacturer? A. The network identifier B. The OUI C. The device identifier
G-router GSM/GPRS to RS-232 and Ethernet Gateway Release Notes
 G-router GSM/GPRS to RS-232 and Ethernet Gateway Release Notes Author RFI Support Team Revision A0 Version RN_G-router_1.2.2 Date 23-05-2011 Covering Product code G-router, RE.40.QGSM Contents 1 Introduction...
G-router GSM/GPRS to RS-232 and Ethernet Gateway Release Notes Author RFI Support Team Revision A0 Version RN_G-router_1.2.2 Date 23-05-2011 Covering Product code G-router, RE.40.QGSM Contents 1 Introduction...
SOFTWARE UNIT 1 PART B C O M P U T E R T E C H N O L O G Y ( S 1 O B J A N D O B J 3-2)
 SOFTWARE UNIT 1 PART B C O M P U T E R T E C H N O L O G Y ( S 1 O B J 2 2-3 A N D O B J 3-2) DIGITAL LITERACY STANDARD 1 OBJECTIVE 3 Explore and demonstrate understanding of managing operating systems
SOFTWARE UNIT 1 PART B C O M P U T E R T E C H N O L O G Y ( S 1 O B J 2 2-3 A N D O B J 3-2) DIGITAL LITERACY STANDARD 1 OBJECTIVE 3 Explore and demonstrate understanding of managing operating systems
Outlook Hints and Tips
 Outlook Hints and Tips Customizing the Outlook View... 2 The Reading Pane...2 AutoPreview...2 Arranging the Inbox...2 Mail Folders...3 Customizing the Tool Bar...4 The Folder List...5 New Mail Options...
Outlook Hints and Tips Customizing the Outlook View... 2 The Reading Pane...2 AutoPreview...2 Arranging the Inbox...2 Mail Folders...3 Customizing the Tool Bar...4 The Folder List...5 New Mail Options...
Computer Network 1 1
 Computer Network 1 1 Chapter 10: Application Layer Advanced Principal Concepts Samples and Techniques Foundation Summary Question and Answer 2 Outline Application Layer There is a need for support protocols,
Computer Network 1 1 Chapter 10: Application Layer Advanced Principal Concepts Samples and Techniques Foundation Summary Question and Answer 2 Outline Application Layer There is a need for support protocols,
ICS 351: Networking Protocols
 ICS 351: Networking Protocols IP packet forwarding application layer: DNS, HTTP transport layer: TCP and UDP network layer: IP, ICMP, ARP data-link layer: Ethernet, WiFi 1 Networking concepts each protocol
ICS 351: Networking Protocols IP packet forwarding application layer: DNS, HTTP transport layer: TCP and UDP network layer: IP, ICMP, ARP data-link layer: Ethernet, WiFi 1 Networking concepts each protocol
Setting Up the Sensor
 CHAPTER 4 This chapter provides information for setting up the sensor. This chapter contains the following sections: Understanding Initialization, page 4-1 Configuring Network Settings, page 4-1 Configuring
CHAPTER 4 This chapter provides information for setting up the sensor. This chapter contains the following sections: Understanding Initialization, page 4-1 Configuring Network Settings, page 4-1 Configuring
LAN Setup Reflection
 LAN Setup Reflection After the LAN setup, ask yourself some questions: o Does your VM have the correct IP? o Are you able to ping some locations, internal and external? o Are you able to log into other
LAN Setup Reflection After the LAN setup, ask yourself some questions: o Does your VM have the correct IP? o Are you able to ping some locations, internal and external? o Are you able to log into other
Connectionless and Connection-Oriented Protocols OSI Layer 4 Common feature: Multiplexing Using. The Transmission Control Protocol (TCP)
 Lecture (07) OSI layer 4 protocols TCP/UDP protocols By: Dr. Ahmed ElShafee ١ Dr. Ahmed ElShafee, ACU Fall2014, Computer Networks II Introduction Most data-link protocols notice errors then discard frames
Lecture (07) OSI layer 4 protocols TCP/UDP protocols By: Dr. Ahmed ElShafee ١ Dr. Ahmed ElShafee, ACU Fall2014, Computer Networks II Introduction Most data-link protocols notice errors then discard frames
Lab 3a Using the vi editor
 Lab 3a Using the vi editor Objectives: Become familiar with the vi Editor Review the three vi Modes Review keystrokes to move between vi modes Create a new file with vi Editor Invoke vi with show mode
Lab 3a Using the vi editor Objectives: Become familiar with the vi Editor Review the three vi Modes Review keystrokes to move between vi modes Create a new file with vi Editor Invoke vi with show mode
CSE 333 Lecture server sockets
 CSE 333 Lecture 18 -- server sockets Hal Perkins Department of Computer Science & Engineering University of Washington Administrivia HW4 posted now, due last Thursday of the quarter Exercise covering client-side
CSE 333 Lecture 18 -- server sockets Hal Perkins Department of Computer Science & Engineering University of Washington Administrivia HW4 posted now, due last Thursday of the quarter Exercise covering client-side
Fig (1) sending and receiving s
 Electronic Mail Protocols (SMTP, POP, IMAP) It is important to (1) distinguish the user interface (i.e., your mail reader) from the underlying message transfer protocols (such as SMTP, POP or IMAP), and
Electronic Mail Protocols (SMTP, POP, IMAP) It is important to (1) distinguish the user interface (i.e., your mail reader) from the underlying message transfer protocols (such as SMTP, POP or IMAP), and
Control Panel software usage guide (v beta)
 Control Panel software usage guide (v 1.012 beta) (note: the pictures throughout the guide may not directly correspond with your server installation, however all features are covered) 1. Connecting to
Control Panel software usage guide (v 1.012 beta) (note: the pictures throughout the guide may not directly correspond with your server installation, however all features are covered) 1. Connecting to
FreeBSD Installation ISOC/AfNOG
 FreeBSD Installation ISOC/AfNOG Michuki Mwangi (Original materials by Hervey Allen NSRC) 1 READ THE INSTRUCTIONS These slides contain explicit instruc2ons to allow you to successfully install FreeBSD and
FreeBSD Installation ISOC/AfNOG Michuki Mwangi (Original materials by Hervey Allen NSRC) 1 READ THE INSTRUCTIONS These slides contain explicit instruc2ons to allow you to successfully install FreeBSD and
Infoblox Authenticated DHCP
 Infoblox Authenticated DHCP Unified Visitor Management amigopod Technical Note Revision 1.1 5 July 2010 United States of America +1 (888) 590-0882 Europe, Middle East & Asia +34 91 766 57 22 Australia
Infoblox Authenticated DHCP Unified Visitor Management amigopod Technical Note Revision 1.1 5 July 2010 United States of America +1 (888) 590-0882 Europe, Middle East & Asia +34 91 766 57 22 Australia
Chapter 19. Domain Name System (DNS)
 Chapter 19 Domain Name System (DNS) TCP/IP Protocol Suite 1 Copyright The McGraw-Hill Companies, Inc. Permission required for reproduction or display. OBJECTIVES: To describe the purpose of DNS. To define
Chapter 19 Domain Name System (DNS) TCP/IP Protocol Suite 1 Copyright The McGraw-Hill Companies, Inc. Permission required for reproduction or display. OBJECTIVES: To describe the purpose of DNS. To define
COS 116 The Computational Universe Laboratory 9: Internet Structure and Congestion Control
 COS 116 The Computational Universe Laboratory 9: Internet Structure and Congestion Control You saw in lecture that the Internet is a loose, decentralized network of computers that communicate with each
COS 116 The Computational Universe Laboratory 9: Internet Structure and Congestion Control You saw in lecture that the Internet is a loose, decentralized network of computers that communicate with each
sensorprobe2 / sensorprobe8 User Manual
 www.akcp.com sensorprobe2 / sensorprobe8 User Manual Help Version updated till firmware 382L Copyright 2007, AKCP Co., Ltd.. 1) Introduction 1. What is sensorprobe? 2. What s the difference between sp2
www.akcp.com sensorprobe2 / sensorprobe8 User Manual Help Version updated till firmware 382L Copyright 2007, AKCP Co., Ltd.. 1) Introduction 1. What is sensorprobe? 2. What s the difference between sp2
FreeBSD Installation
 1 FreeBSD Installation AFNOG Chix 2011 Blantyre, Malawi 31 st Oct - 4 th Nov 2011 Dorcas Muthoni and Evelyn Namara 2 READ THE INSTRUCTIONS These slides contain explicit instructions to allow you to successfully
1 FreeBSD Installation AFNOG Chix 2011 Blantyre, Malawi 31 st Oct - 4 th Nov 2011 Dorcas Muthoni and Evelyn Namara 2 READ THE INSTRUCTIONS These slides contain explicit instructions to allow you to successfully
Networks Lab Pod Diagram
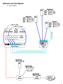 (Console cable) Networks Lab Pod Diagram (x = pod number) 190.111.50.x 190.111.x.254 PodxLinux Addr: 190.111.x.3 Mask: 255.255.255.0 GW: 190.111.x.254 DNS: 190.111.x.1 PodxServer Addr: 190.111.x.1 Mask:
(Console cable) Networks Lab Pod Diagram (x = pod number) 190.111.50.x 190.111.x.254 PodxLinux Addr: 190.111.x.3 Mask: 255.255.255.0 GW: 190.111.x.254 DNS: 190.111.x.1 PodxServer Addr: 190.111.x.1 Mask:
Using the Zoo Workstations
 Using the Zoo Workstations Version 1.86: January 16, 2014 If you ve used Linux before, you can probably skip many of these instructions, but skim just in case. Please direct corrections and suggestions
Using the Zoo Workstations Version 1.86: January 16, 2014 If you ve used Linux before, you can probably skip many of these instructions, but skim just in case. Please direct corrections and suggestions
LAN Setup Reflection. Ask yourself some questions: o Does your VM have the correct IP? o Are you able to ping some locations, internal and external?
 LAN Setup Reflection Ask yourself some questions: o Does your VM have the correct IP? o Are you able to ping some locations, internal and external? o Are you able to log into other VMs in the classroom?
LAN Setup Reflection Ask yourself some questions: o Does your VM have the correct IP? o Are you able to ping some locations, internal and external? o Are you able to log into other VMs in the classroom?
The Internet. Tim Capes. November 7, 2011
 The Internet Tim Capes November 7, 2011 What is the Internet? The internet is a global system consisting of millions if interconnected networks. These individual networks are anything from local (a Home
The Internet Tim Capes November 7, 2011 What is the Internet? The internet is a global system consisting of millions if interconnected networks. These individual networks are anything from local (a Home
Client Server Concepts, DNS, Telnet, FTP
 Indian Institute of Technology Kharagpur Client Server Concepts, DNS, Telnet, FTP Prof. Indranil Sen Gupta Dept. of Computer Science & Engg. I.I.T. Kharagpur, INDIA Lecture 9: Client server concepts, DNS,
Indian Institute of Technology Kharagpur Client Server Concepts, DNS, Telnet, FTP Prof. Indranil Sen Gupta Dept. of Computer Science & Engg. I.I.T. Kharagpur, INDIA Lecture 9: Client server concepts, DNS,
Domain Name System (DNS) Services
 12 Domain Name System (DNS) Services Contents Overview..................................................... 12-3 Host and Domain Names.................................... 12-3 Host Tables...............................................
12 Domain Name System (DNS) Services Contents Overview..................................................... 12-3 Host and Domain Names.................................... 12-3 Host Tables...............................................
System Administration
 System Administration MTAT.08.021 6 ECTS Markko Merzin markko.merzin@ut.ee http://courses.cs.ut.ee/2012/syshald/ 1/55 Markko Merzin Lecturer worked as a System administrator: 15 years (and counting) Researcher:
System Administration MTAT.08.021 6 ECTS Markko Merzin markko.merzin@ut.ee http://courses.cs.ut.ee/2012/syshald/ 1/55 Markko Merzin Lecturer worked as a System administrator: 15 years (and counting) Researcher:
7.1. Browsing CHAPTER. The Internet. Web Browser software
 CHAPTER The Internet The Internet consists of a huge number of computers connected together all over the world. While a small group of connected computers constitutes a network, the Internet is an International
CHAPTER The Internet The Internet consists of a huge number of computers connected together all over the world. While a small group of connected computers constitutes a network, the Internet is an International
Once the VM is started, the VirtualBox OS Manager window can be closed. But our Ubuntu VM is still running.
 How to use iptables on Ubuntu Revised: 16-August-2016 by David Walling This "How To" document describes using the iptables program to define firewall rules for our Ubuntu server. We will also explore using
How to use iptables on Ubuntu Revised: 16-August-2016 by David Walling This "How To" document describes using the iptables program to define firewall rules for our Ubuntu server. We will also explore using
ALLWORX NETWORKING TUTORIAL APRIL 2003
 ALLWORX NETWORKING TUTORIAL APRIL 2003 Author: Jeffrey R. Szczepanski, Chief Technical Officer, InSciTek Microsystems, Inc. Allworx Division of InSciTek Microsystems, Inc. 635 Crosskeys Office Park Fairport,
ALLWORX NETWORKING TUTORIAL APRIL 2003 Author: Jeffrey R. Szczepanski, Chief Technical Officer, InSciTek Microsystems, Inc. Allworx Division of InSciTek Microsystems, Inc. 635 Crosskeys Office Park Fairport,
Operating Systems Linux 1-2 Measurements Background material
 Operating Systems Linux 1-2 Measurements Background material Introduction The Linux measurements were designed to allow you to have an impression about the administration of Linux severs along with providing
Operating Systems Linux 1-2 Measurements Background material Introduction The Linux measurements were designed to allow you to have an impression about the administration of Linux severs along with providing
Last Class: RPCs and RMI. Today: Communication Issues
 Last Class: RPCs and RMI Case Study: Sun RPC Lightweight RPCs Remote Method Invocation (RMI) Design issues Lecture 9, page 1 Today: Communication Issues Message-oriented communication Persistence and synchronicity
Last Class: RPCs and RMI Case Study: Sun RPC Lightweight RPCs Remote Method Invocation (RMI) Design issues Lecture 9, page 1 Today: Communication Issues Message-oriented communication Persistence and synchronicity
Deploy the ExtraHop Discover Appliance 1100
 Deploy the ExtraHop Discover Appliance 1100 Published: 2018-07-17 The following procedures explain how to deploy an ExtraHop Discover appliance 1100. System requirements Your environment must meet the
Deploy the ExtraHop Discover Appliance 1100 Published: 2018-07-17 The following procedures explain how to deploy an ExtraHop Discover appliance 1100. System requirements Your environment must meet the
(Refer Slide Time: 1:26)
 Information Security-3 Prof. V Kamakoti Department of Computer science and Engineering Indian Institute of Technology Madras Basics of Unix and Network Administration Operating Systems Introduction Mod01,
Information Security-3 Prof. V Kamakoti Department of Computer science and Engineering Indian Institute of Technology Madras Basics of Unix and Network Administration Operating Systems Introduction Mod01,
Jackson State University Department of Computer Science CSC 437/539 Computer Security Fall 2013 Instructor: Dr. Natarajan Meghanathan
 Jackson State University Department of Computer Science CSC 437/539 Computer Security Fall 2013 Instructor: Dr. Natarajan Meghanathan Lab Project # 3: Simulating DHCP Snooping and DNS Cache Poisoning through
Jackson State University Department of Computer Science CSC 437/539 Computer Security Fall 2013 Instructor: Dr. Natarajan Meghanathan Lab Project # 3: Simulating DHCP Snooping and DNS Cache Poisoning through
WEBppliance for Windows User Administrator's Help
 WEBppliance for Windows User Administrator's Help September 23, 2003 Contents About This Document...3 How to use this Help system...4 Getting started...6 What to do first... 6 Viewing your account settings...
WEBppliance for Windows User Administrator's Help September 23, 2003 Contents About This Document...3 How to use this Help system...4 Getting started...6 What to do first... 6 Viewing your account settings...
SANOG VI IP Services Workshop: FreeBSD Install
 SANOG VI IP Services Workshop: FreeBSD Install FreeBSD is designed to be a server operating system. This becomes apparent during the installation process. The FreeBSD installer is a console-based (not
SANOG VI IP Services Workshop: FreeBSD Install FreeBSD is designed to be a server operating system. This becomes apparent during the installation process. The FreeBSD installer is a console-based (not
Ethernet / TCP-IP - Training Suite Application level protocols
 Ethernet / TCP-IP - Training Suite 05 - Application level protocols Application layer protocols 2 World Wide Web HTTP I want HTTP this resource. Hypertext Transfer Protocol (HTTP) Used by the World Wide
Ethernet / TCP-IP - Training Suite 05 - Application level protocols Application layer protocols 2 World Wide Web HTTP I want HTTP this resource. Hypertext Transfer Protocol (HTTP) Used by the World Wide
I m InTouch Installation Guide for the DSL/Cable environment with a Linksys router Models: BEFSRU31, BEFSR41 V.2, BEFSR11
 I m InTouch router configuration p. 1 I m InTouch Installation Guide for the DSL/Cable environment with a Linksys router Models: BEFSRU31, BEFSR41 V.2, BEFSR11 Note: Different models may vary slightly
I m InTouch router configuration p. 1 I m InTouch Installation Guide for the DSL/Cable environment with a Linksys router Models: BEFSRU31, BEFSR41 V.2, BEFSR11 Note: Different models may vary slightly
Applied Networks & Security
 Applied Networks & Security TCP/IP Networks with Critical Analysis http://condor.depaul.edu/~jkristof/it263/ John Kristoff jtk@depaul.edu IT 263 Spring 2006/2007 John Kristoff - DePaul University 1 Critical
Applied Networks & Security TCP/IP Networks with Critical Analysis http://condor.depaul.edu/~jkristof/it263/ John Kristoff jtk@depaul.edu IT 263 Spring 2006/2007 John Kristoff - DePaul University 1 Critical
UKNova s Getting Connectable Guide
 UKNova s Getting Connectable Guide Version 1.2 2010/03/22 1. WHAT IS "BEING CONNECTABLE" AND WHY DO I NEED IT? Being connectable means being able to give back to others it is the fundamental principle
UKNova s Getting Connectable Guide Version 1.2 2010/03/22 1. WHAT IS "BEING CONNECTABLE" AND WHY DO I NEED IT? Being connectable means being able to give back to others it is the fundamental principle
Network Security. Introduction to networks. Radboud University, The Netherlands. Autumn 2015
 Network Security Introduction to networks Radboud University, The Netherlands Autumn 2015 What is a (computer) network Definition A computer network is two or more computers that are connected, so that
Network Security Introduction to networks Radboud University, The Netherlands Autumn 2015 What is a (computer) network Definition A computer network is two or more computers that are connected, so that
WSC SEMIFINALS AT FINNSKILLS 2005
 SEMIFINAL TASK 1 (7) WSC SEMIFINALS 19.-20.1.2005 AT FINNSKILLS 2005 Introduction General Please read the whole part before starting work. Good luck to all competitors. If you have any questions about
SEMIFINAL TASK 1 (7) WSC SEMIFINALS 19.-20.1.2005 AT FINNSKILLS 2005 Introduction General Please read the whole part before starting work. Good luck to all competitors. If you have any questions about
Building a virtual network Maher Saad, Chestnut Residence, University of Toronto
 Building a virtual network Maher Saad, Chestnut Residence, University of Toronto Disclaimer The author of this document shall not carry responsibility for any damage to the network, computer(s) software
Building a virtual network Maher Saad, Chestnut Residence, University of Toronto Disclaimer The author of this document shall not carry responsibility for any damage to the network, computer(s) software
