Defining Route Maps. Information About Route Maps CHAPTER
|
|
|
- Dwain McCormick
- 6 years ago
- Views:
Transcription
1 20 CHAPTER This chapter describes route maps and includes the following sections: Information About Route Maps, page 20-1 Licensing Requirements for Route Maps, page 20-3 Guidelines and Limitations, page 20-3 Defining a Route Map, page 20-4 Customizing a Route Map, page 20-5 Configuration Example for Route Maps, page 20-8 Feature History for Route Maps, page 20-8 Information About Route Maps Route maps are used when redistributing routes into an OSPF, RIP, or EIGRP routing process. They are also used when generating a default route into an OSPF routing process. A route map defines which of the routes from the specified routing protocol are allowed to be redistributed into the target routing process. Route maps have many features in common with widely known ACLs. These are some of the traits common to both: They are an ordered sequence of individual statements, each has a permit or deny result. Evaluation of ACL or route maps consists of a list scan, in a predetermined order, and an evaluation of the criteria of each statement that matches. A list scan is aborted once the first statement match is found and an action associated with the statement match is performed. They are generic mechanisms Criteria matches and match interpretation are dictated by the way that they are applied. The same route map applied to different tasks might be interpreted differently. These are some of the differences between route maps and ACLs: Route maps frequently use ACLs as matching criteria. The main result from the evaluation of an access list is a yes or no answer An ACL either permits or denies input data. Applied to redistribution, an ACL determines if a particular route can (route matches ACLs permit statement) or can not (matches deny statement) be redistributed. Typical route maps not only permit (some) redistributed routes but also modify information associated with the route, when it is redistributed into another protocol. Route maps are more flexible than ACLs and can verify routes based on criteria which ACLs can not verify. For example, a route map can verify if the type of route is internal. 20-1
2 Information About Route Maps Chapter 20 Each ACL ends with an implicit deny statement, by design convention; there is no similar convention for route maps. If the end of a route map is reached during matching attempts, the result depends on the specific application of the route map. Fortunately, route maps that are applied to redistribution behave the same way as ACLs: if the route does not match any clause in a route map then the route redistribution is denied, as if the route map contained deny statement at the end. The dynamic protocol redistribute command allows you to apply a route map. In ASDM, this capability for redistribution can be found when you add or edit a new route map (see the Defining a Route Map section on page 20-4). Route maps are preferred if you intend to either modify route information during redistribution or if you need more powerful matching capability than an ACL can provide. If you simply need to selectively permit some routes based on their prefix or mask, we recommends that you use a route map to map to an ACL (or equivalent prefix list) directly in the redistribute command. If you use a route map to selectively permit some routes based on their prefix or mask, you typically use more configuration commands to achieve the same goal. Note You must use a standard ACL as the match criterion for your route map. Using an extended ACL will not work, and your routes will never be redistributed. We recommend that you number clauses in intervals of 10, to reserve numbering space in case you need to insert clauses in the future. This section includes the following topics: Permit and Deny Clauses, page 20-2 Match and Set Clause Values, page 20-2 Permit and Deny Clauses Route maps can have permit and deny clauses. In the route-map ospf-to-eigrp command, there is one deny clause (with sequence number 10) and two permit clauses. The deny clause rejects route matches from redistribution. Therefore, the following rules apply: If you use an ACL in a route map using a permit clause, routes that are permitted by the ACL are redistributed. If you use an ACL in a route map deny clause, routes that are permitted by the ACL are not redistributed. If you use an ACL in a route map permit or deny clause, and the ACL denies a route, then the route map clause match is not found and the next route-map clause is evaluated. Match and Set Clause Values Each route map clause has two types of values: A match value selects routes to which this clause should be applied. A set value modifies information that will be redistributed into the target protocol. For each route that is being redistributed, the router first evaluates the match criteria of a clause in the route map. If the match criteria succeed, then the route is redistributed or rejected as dictated by the permit or deny clause, and some of its attributes might be modified by the values set from the Set Value tab in ASDM or from the set commands. If the match criteria fail, then this clause is not applicable to the route, and the software proceeds to evaluate the route against the next clause in the route map. Scanning of the route map continues until a clause is found whose match command(s), or Match Clause as set from the Match Clause tab in ASDM, match the route or until the end of the route map is reached. 20-2
3 Chapter 20 Licensing Requirements for Route Maps A match or set value in each clause can be missed or repeated several times, if one of these conditions exists: If several match commands or Match Clause values in ASDM are present in a clause, all must succeed for a given route in order for that route to match the clause (in other words, the logical AND algorithm is applied for multiple match commands). If a match command or Match Clause value in ASDM refers to several objects in one command, either of them should match (the logical OR algorithm is applied). For example, in the match ip address command, a route is permitted if access list 101 or access list 121 permits it. If a match command or Match Clause value in ASDM is not present, all routes match the clause. In the previous example, all routes that reach clause 30 match; therefore, the end of the route map is never reached. If a set command, or Set Value in ASDM, is not present in a route map permit clause, then the route is redistributed without modification of its current attributes. Note Do not configure a set command in a route map deny clause because the deny clause prohibits route redistribution there is no information to modify. A route map clause without a match or set command, or Match or Set Value as set on the Match or Set Value tab in ASDM, performs an action. An empty permit clause allows a redistribution of the remaining routes without modification. An empty deny clause does not allows a redistribution of other routes (this is the default action if a route map is completely scanned, but no explicit match is found). Licensing Requirements for Route Maps The following table shows the licensing requirements for route maps: Model All models License Requirement Base License. Guidelines and Limitations This section includes the guidelines and limitations for this feature. Context Mode Guidelines Supported in single context mode. Firewall Mode Guidelines Supported only in routed firewall mode. Transparent firewall mode is not supported. IPv6 Guidelines Does not support IPv
4 Defining a Route Map Chapter 20 Defining a Route Map You must define a route map when specifying which of the routes from the specified routing protocol are allowed to be redistributed into the target routing process. Adding or Editing a Route Map In ASDM, you can define a route map by adding, editing, or deleting a route map name, sequence number, or redistribution. To add, edit, or delete a route map, perform the following steps: In ASDM, choose Configuration > Device Setup > Routing > Route Maps. The Add Route Map or Edit Route Map dialog box appears. Enter the route map name and sequence number. The route map name is the name that you assign to a particular route. The sequence number is the order in which you add or delete the route map entries into the ASASM. Note If you are editing an existing route map, the fields for Route Map name and sequence number are already filled in. Step 4 Step 5 To reject route matches from redistribution, click Deny. If you use an ACL in a route map Deny clause, routes that are permitted by the ACL are not redistributed. To allow route matches for redistribution. click Permit. If you use an ACL in a route map Permit clause, routes that are permitted by the ACL are redistributed. In addition, if you use an ACL in a route map Permit or Deny clause, and the ACL denies a route, then the route map clause match is not found and the next route map clause is evaluated. Click the Match Clause tab to choose routes to which this clause should be applied, and set the following parameters: Check the Match first hop interface of route check box to enable or disable matching the first hop interface of a route or to match any routes with the specified next hop interface. If you specify more than one interface, then the route can match either interface. Enter the interface name in the Interface field, or click the ellipses to display the Browse Interface dialog box. Choose the interface type (inside or outside), click Selected Interface, then click OK. Check the Match IP Address check box to enable or disable the Match address of a route or match packet. Check the Match Next Hop check box to enable or disable the Match next hop address of a route. Check the Match Route Source check box to enable or disable the Match advertising source address of the route. Choose Access List ot Prefix List from the drop-down list to match the IP address. According to the previous selection, click the ellipses to display the Browse Access List or Browse Prefix List dialog box. 20-4
5 Chapter 20 Customizing a Route Map Step 6 Choose the ACL or prefix list that you want. Check the Match metric of route check box to enable or disable matching the metric of a route. In the Metric Value field, type the metric values. You can enter multiple values, separated by commas. This setting allows you to match any routes that have a specified metric. The metric value can range from 0 to Check the Match Route Type check box to enable or disable matching of the route type. Valid route types are External1, External2, Internal, Local, NSSA-External1, and NSSA-External2. When enabled, you can choose more than one route type from the list. Click the Set Clause tab to modify the following information, which will be redistributed to the target protocol: Check the Set Metric Clause check box to enable or disable the metric value for the destination routing protocol, and type the value in the Value field. Check the Set Metric Type check box to enable or disable the type of metric for the destination routing protocol, and choose the metric type from the drop-down list. Customizing a Route Map This section describes how to customize the route map and includes the following topics: Defining a Route to Match a Specific Destination Address, page 20-5 Configuring Prefix Lists, page 20-6 Configuring Prefix Rules, page 20-7 Configuring the Metric Values for a Route Action, page 20-7 Defining a Route to Match a Specific Destination Address To define a route to match a specified destination address, perform the following steps: In ASDM, choose Configuration > Device Setup > Routing > Route Maps. The Add Route Map dialog box appears. From this dialog box you can assign or choose the route map name, the sequence number, and its redistribution access (that is, permit or deny). Route map entries are read in order. You can identify the order using the sequence number, or the ASASM uses the order in which you add the entries. Click the Match Clause tab to choose routes to which this clause should be applied, and set the following parameters: Check the Match first hop interface of route check box to enable or disable matching the first hop interface of a route or to match any routes with the specified next hop interface. If you specify more than one interface, then the route can match either interface. Enter the interface name in the Interface field, or click the ellipses to display the Browse Interface dialog box. Choose the interface type (inside or outside), click Selected Interface, then click OK. 20-5
6 Customizing a Route Map Chapter 20 Check the Match IP Address check box to enable or disable the Match address of a route or match packet. Check the Match Next Hop check box to enable or disable the Match next hop address of a route. Check the Match Route Source check box to enable or disable the Match advertising source address of the route. Choose Access List ot Prefix List from the drop-down list to match the IP address. According to the previous selection, click the ellipses to display the Browse Access List or Browse Prefix List dialog box. Choose the ACL or prefix list that you want. Check the Match metric of route check box to enable or disable matching the metric of a route. In the Metric Value field, type the metric values. You can enter multiple values, separated by commas. This setting allows you to match any routes that have a specified metric. The metric value can range from 0 to Check the Match Route Type check box to enable or disable matching of the route type. Valid route types are External1, External2, Internal, Local, NSSA-External1, and NSSA-External2. When enabled, you can choose more than one route type from the list. Click OK when you are done. Configuring Prefix Lists ABR type 3 LSA filtering extends the capability of an ABR that is running OSPF to filter type 3 LSAs between different OSPF areas. Once a prefix list is configured, only the specified prefixes are sent from one OSPF area to another OSPF area. All other prefixes are restricted to their OSPF area. You can apply this type of area filtering to traffic going into or coming out of an OSPF area, or to both the incoming and outgoing traffic for that area. When multiple entries of a prefix list match a given prefix, the entry with the lowest sequence number is used. For efficiency, you may want to put the most common matches or denials near the top of the list by manually assigning them a lower sequence number. By default, sequence numbers are automatically generated in increments of 5, beginning with 5. To add prefix lists, perform the following steps: In ASDM, choose Configuration > Device Setup > Routing > Prefix Rules. From the Add drop-down list, choose Add Prefix List. The Add Prefix List dialog box appears. Enter the prefix name and description, then click OK. 20-6
7 Chapter 20 Customizing a Route Map Configuring Prefix Rules Note You must configure a prefix list before you may configure a prefix rule. To configure prefix rules, perform the following steps: Step 4 Step 5 Step 6 Step 7 Step 8 Step 9 In ASDM, choose Configuration > Device Setup > Routing > Prefix Rules. The Add Prefix Rule dialog box appears. From this dialog box, you can add a sequence number, specify a prefix for the network, its redistribution access (that is, permit or deny), the minimum and maximum prefix length. Enter an optional sequence number or accept the default value. Specify the prefix number in the format of IP address/mask length. Click the Permit or Deny radio button to indicate the redistribution access. Enter the optional minimum and maximum prefix lengths. Click OK when you are done. The new or revised prefix rule appears in the list. Check the Enable Prefix list sequence numbering check box if you want to use automatically generated sequence numbers. Click Apply to save your changes. Configuring the Metric Values for a Route Action To configure the metric value for a route action, perform the following steps: In ASDM, choose Configuration > Device Setup > Routing > Route Maps. The Add Route Map dialog box appears. From this dialog box, you can assign or select the route map name, the sequence number and its redistribution access (that is, permit or deny). Route map entries are read in order. You can identify the order using the sequence number, or the ASASM uses the order in which you add route map entries. Click the Set Clause tab to modify the following information, which will be redistributed to the target protocol: Check the Set Metric Clause check box to enable or disable the metric value for the destination routing protocol, and enter the value in the Value field. Check the Set Metric Type check box to enable or disable the type of metric for the destination routing protocol, and choose the metric type from the drop-down list. 20-7
8 Configuration Example for Route Maps Chapter 20 Configuration Example for Route Maps The following example shows how to redistribute routes with a hop count equal to 1 into OSPF. Step 4 Step 5 Step 6 Step 7 Step 8 Step 9 0 In ASDM, choose Configuration > Device Setup > Routing > Route Maps. Enter 1-to-2 in the Route Map Name field. Enter the routing sequence number in the Sequence Number field. Click the Permit radio button. By default this tab is on top. Click the Match Clause tab. Check the Match Metric of Route check box and type 1 for the metric value. Click the Set Clause tab. Check the Set Metric Value check box, and type 5 for the metric value. Check the Set Metric-Type check box, and choose Type-1. Feature History for Route Maps Table 20-1 lists each feature change and the platform release in which it was implemented. ASDM is backwards-compatible with multiple platform releases, so the specific ASDM release in which support was added is not listed. Table 20-1 Feature History for Route Maps Feature Name Platform Releases Feature Information Route maps 7.0(1) We introduced this feature. We introduced the following screen: Configuration > Device Setup > Routing > Route Maps. Enhanced support for static and dynamic route maps 8.0(2) Enhanced support for dynamic and static route maps was added. 20-8
Route Maps. About Route Maps
 This chapter describes how to configure and customize route-maps, for Cisco ASA. About, on page 1 Guidelines for, on page 3 Define a Route Map, on page 3 Customize a Route Map, on page 3 Example for, on
This chapter describes how to configure and customize route-maps, for Cisco ASA. About, on page 1 Guidelines for, on page 3 Define a Route Map, on page 3 Customize a Route Map, on page 3 Example for, on
Routing Overview for Firepower Threat Defense
 Path Determination This chapter describes underlying concepts of how routing behaves within the Cisco Firepower Threat Defense, and the routing protocols that are supported. Routing is the act of moving
Path Determination This chapter describes underlying concepts of how routing behaves within the Cisco Firepower Threat Defense, and the routing protocols that are supported. Routing is the act of moving
Configuring RIP. Information About RIP CHAPTER
 CHAPTER 23 This chapter describes how to configure the ASASM to route data, perform authentication, and redistribute routing information using the Routing Information Protocol (RIP). This chapter includes
CHAPTER 23 This chapter describes how to configure the ASASM to route data, perform authentication, and redistribute routing information using the Routing Information Protocol (RIP). This chapter includes
EIGRP Support for Route Map Filtering
 The feature enables Enhanced Interior Gateway Routing Protocol (EIGRP) to interoperate with other protocols to leverage additional routing functionality by filtering inbound and outbound traffic based
The feature enables Enhanced Interior Gateway Routing Protocol (EIGRP) to interoperate with other protocols to leverage additional routing functionality by filtering inbound and outbound traffic based
Internetwork Expert s CCNP Bootcamp. Redistribution & Layer 3 Path Control. Route Redistribution Overview
 Internetwork Expert s CCNP Bootcamp Redistribution & Layer 3 Path Control http:// Route Redistribution Overview Process of exchanging reachability information between routing domains e.g. OSPF to EIGRP
Internetwork Expert s CCNP Bootcamp Redistribution & Layer 3 Path Control http:// Route Redistribution Overview Process of exchanging reachability information between routing domains e.g. OSPF to EIGRP
Chapter 13 RIP Commands
 Chapter 13 RIP Commands NOTE: This chapter contains information about IPv4 RIP commands only. For information about IPv6 RIP commands, see IPv6 RIP Commands on page 14-1. default-metric Defines the global
Chapter 13 RIP Commands NOTE: This chapter contains information about IPv4 RIP commands only. For information about IPv6 RIP commands, see IPv6 RIP Commands on page 14-1. default-metric Defines the global
Configuring EIGRP. Overview CHAPTER
 CHAPTER 24 This chapter describes how to configure the adaptive security appliance to route data, perform authentication, and redistribute routing information, using the Enhanced Interior Gateway Routing
CHAPTER 24 This chapter describes how to configure the adaptive security appliance to route data, perform authentication, and redistribute routing information, using the Enhanced Interior Gateway Routing
Chapter 4: Manipulating Routing
 : Manipulating Routing Updates CCNP ROUTE: Implementing IP Routing ROUTE v6 1 Objectives Describe network performance issues and ways to control routing updates and traffic (3). Describe the purpose of
: Manipulating Routing Updates CCNP ROUTE: Implementing IP Routing ROUTE v6 1 Objectives Describe network performance issues and ways to control routing updates and traffic (3). Describe the purpose of
Configuring Policy-Based Routing
 CHAPTER 17 This chapter describes how to configure policy based routing. This chapter includes the following sections: Information About Policy Based Routing, page 17-1 Licensing Requirements for Policy-Based
CHAPTER 17 This chapter describes how to configure policy based routing. This chapter includes the following sections: Information About Policy Based Routing, page 17-1 Licensing Requirements for Policy-Based
Basic IP Routing. Finding Feature Information. Information About Basic IP Routing. Variable-Length Subnet Masks
 This module describes how to configure basic IP routing. The Internet Protocol (IP) is a network layer (Layer 3) protocol that contains addressing information and some control information that enables
This module describes how to configure basic IP routing. The Internet Protocol (IP) is a network layer (Layer 3) protocol that contains addressing information and some control information that enables
EIGRP. About EIGRP. CLI Book 1: Cisco ASA Series General Operations CLI Configuration Guide, 9.7 1
 This chapter describes how to configure the Cisco ASA to route data, perform authentication, and redistribute routing information using the Enhanced Interior Gateway Routing Protocol (). About, page 1
This chapter describes how to configure the Cisco ASA to route data, perform authentication, and redistribute routing information using the Enhanced Interior Gateway Routing Protocol (). About, page 1
Chapter 9 RIP Commands
 Chapter 9 RIP Commands default-metric Defines the global default-metric value that will be assigned to all external routes imported into RIP for redistribution. RIP must be active on the routing switch
Chapter 9 RIP Commands default-metric Defines the global default-metric value that will be assigned to all external routes imported into RIP for redistribution. RIP must be active on the routing switch
Basic IP Routing. Finding Feature Information. Information About Basic IP Routing. Variable-Length Subnet Masks
 This module describes how to configure basic IP routing. The Internet Protocol (IP) is a network layer (Layer 3) protocol that contains addressing information and some control information that enables
This module describes how to configure basic IP routing. The Internet Protocol (IP) is a network layer (Layer 3) protocol that contains addressing information and some control information that enables
OSPF Commands. Cisco IOS IP Command Reference, Volume 2 of 3: Routing Protocols IP2R-61
 OSPF Commands Use the commands in this chapter to configure and monitor the Open Shortest Path First (OSPF) routing protocol. For OSPF configuration information and examples, refer to the Configuring OSPF
OSPF Commands Use the commands in this chapter to configure and monitor the Open Shortest Path First (OSPF) routing protocol. For OSPF configuration information and examples, refer to the Configuring OSPF
BGP Route-Map Continue
 The feature introduces the continue clause to BGP route-map configuration. The continue clause allows for more programmable policy configuration and route filtering and introduces the capability to execute
The feature introduces the continue clause to BGP route-map configuration. The continue clause allows for more programmable policy configuration and route filtering and introduces the capability to execute
Chapter 4 Lab 4-2, Controlling Routing Updates. Topology. Objectives. CCNPv7 ROUTE
 Chapter 4 Lab 4-2, Controlling Routing Updates Topology Objectives Filter routes using a distribute list and ACL. Filter routes using a distribute list and prefix list. Filter redistributed routes using
Chapter 4 Lab 4-2, Controlling Routing Updates Topology Objectives Filter routes using a distribute list and ACL. Filter routes using a distribute list and prefix list. Filter redistributed routes using
Policy Based Routing:
 This chapter describes how to configure the Cisco ASA to support policy based routing (PBR). The following sections describe policy based routing, guidelines for PBR, and configuration for PBR. About,
This chapter describes how to configure the Cisco ASA to support policy based routing (PBR). The following sections describe policy based routing, guidelines for PBR, and configuration for PBR. About,
OSPFv2 Local RIB. Finding Feature Information
 With the feature, each OSPF protocol instance has its own local Routing Information Base (RIB). The OSPF local RIB serves as the primary state for OSPF SPF route computation. The global RIB is not updated
With the feature, each OSPF protocol instance has its own local Routing Information Base (RIB). The OSPF local RIB serves as the primary state for OSPF SPF route computation. The global RIB is not updated
IP Routing Protocol-Independent Commands
 IP Routing Protocol-Independent Commands Use the commands in this chapter to configure and monitor the features that are routing protocol-independent. For configuration information and examples on IP routing
IP Routing Protocol-Independent Commands Use the commands in this chapter to configure and monitor the features that are routing protocol-independent. For configuration information and examples on IP routing
Network Layer Week 5. Module : Computer Networks Lecturer: Lucy White Office : 324
 Network Layer Week 5 Module : Computer Networks Lecturer: Lucy White lbwhite@wit.ie Office : 324 1 Network Layer Network Layer Protocols Common Network Layer Protocols Internet Protocol version 4 (IPv4)
Network Layer Week 5 Module : Computer Networks Lecturer: Lucy White lbwhite@wit.ie Office : 324 1 Network Layer Network Layer Protocols Common Network Layer Protocols Internet Protocol version 4 (IPv4)
Routing Implementation
 L3Out Subnets, page 1 L3Out Subnets About Defining L3Out Subnets L3Outs are the Cisco Application Centric Infrastructure (ACI) objects used to provide external connectivity in external Layer 3 networks.
L3Out Subnets, page 1 L3Out Subnets About Defining L3Out Subnets L3Outs are the Cisco Application Centric Infrastructure (ACI) objects used to provide external connectivity in external Layer 3 networks.
Configuring Policy-Based Routing
 25 CHAPTER This chapter describes the tasks for configuring policy-based routing (PBR) on a router and includes these major sections: Overview of Policy-Based Routing, page 25-1 Policy-Based Routing Configuration
25 CHAPTER This chapter describes the tasks for configuring policy-based routing (PBR) on a router and includes these major sections: Overview of Policy-Based Routing, page 25-1 Policy-Based Routing Configuration
Chapter 12 Configuring IPX
 Chapter 12 Configuring IPX This chapter covers how to configure the IPX protocol on the HP routing switches using the CLI and Web management interface. A summary of all CLI commands noting syntax along
Chapter 12 Configuring IPX This chapter covers how to configure the IPX protocol on the HP routing switches using the CLI and Web management interface. A summary of all CLI commands noting syntax along
Configuring Policy-Based Routing
 CHAPTER 28 This chapter describes the tasks for configuring policy-based routing (PBR) on a router and includes these major sections: Overview of Policy-Based Routing, page 28-1 Policy-Based Routing Configuration
CHAPTER 28 This chapter describes the tasks for configuring policy-based routing (PBR) on a router and includes these major sections: Overview of Policy-Based Routing, page 28-1 Policy-Based Routing Configuration
EIGRP Route Tag Enhancements
 The feature enables you to specify and display route tags in dotted-decimal format, filter routes using the route tag value with wildcard mask, and set a default route tag for all internal Enhanced Interior
The feature enables you to specify and display route tags in dotted-decimal format, filter routes using the route tag value with wildcard mask, and set a default route tag for all internal Enhanced Interior
OSPFv3 Route Filtering Using Distribute-List
 The OSPFv3 route filtering using distribute-list feature allows users to filter the incoming routes that are programmed in routing table, and the outgoing routes that are advertised. Finding Feature Information,
The OSPFv3 route filtering using distribute-list feature allows users to filter the incoming routes that are programmed in routing table, and the outgoing routes that are advertised. Finding Feature Information,
A Commands. Send comments to
 This chapter describes the Cisco NX-OS Open Shortest Path First (OSPF) commands that begin with A. UCR-555 area authentication (OSPF) area authentication (OSPF) To enable authentication for an Open Shortest
This chapter describes the Cisco NX-OS Open Shortest Path First (OSPF) commands that begin with A. UCR-555 area authentication (OSPF) area authentication (OSPF) To enable authentication for an Open Shortest
BGP can also be used for carrying routing information for IPv6 prefix over IPv6 networks.
 This chapter describes how to configure the Cisco ASA to route data, perform authentication, and redistribute routing information using the Border Gateway Protocol (). About, page 1 Guidelines for, page
This chapter describes how to configure the Cisco ASA to route data, perform authentication, and redistribute routing information using the Border Gateway Protocol (). About, page 1 Guidelines for, page
Chapter 8 Configuring OSPF
 Chapter 8 Configuring OSPF This chapter describes how to configure OSPF on HP routing switches using the CLI and Web management interface. To display OSPF configuration information and statistics, see
Chapter 8 Configuring OSPF This chapter describes how to configure OSPF on HP routing switches using the CLI and Web management interface. To display OSPF configuration information and statistics, see
BTEC Level 3 Extended Diploma
 BTEC Level 3 Extended Diploma Unit 9 Computer Network Routing and Routing Protocols BTEC Level 3 Extended Diploma Introduction to Routing Routing is the process that a router uses to forward packets toward
BTEC Level 3 Extended Diploma Unit 9 Computer Network Routing and Routing Protocols BTEC Level 3 Extended Diploma Introduction to Routing Routing is the process that a router uses to forward packets toward
RIP. Table of Contents. General Information. Summary. Specifications
 RIP Document revision 1 (Wed Mar 24 12:32:12 GMT 2004) This document applies to V2.8 Table of Contents Table of Contents General Information Summary Specifications Related Documents Additional Documents
RIP Document revision 1 (Wed Mar 24 12:32:12 GMT 2004) This document applies to V2.8 Table of Contents Table of Contents General Information Summary Specifications Related Documents Additional Documents
Access Rules. Controlling Network Access
 This chapter describes how to control network access through or to the ASA using access rules. You use access rules to control network access in both routed and transparent firewall modes. In transparent
This chapter describes how to control network access through or to the ASA using access rules. You use access rules to control network access in both routed and transparent firewall modes. In transparent
Antonio Cianfrani. Access Control List (ACL) Part I
 Antonio Cianfrani Access Control List (ACL) Part I Index ACL? How to configure Standard ACL Extended ACL Named ACL Limiting the vty access ACL (1/3) Control lists applied to traffic incoming in / outgoing
Antonio Cianfrani Access Control List (ACL) Part I Index ACL? How to configure Standard ACL Extended ACL Named ACL Limiting the vty access ACL (1/3) Control lists applied to traffic incoming in / outgoing
Information About Routing
 19 CHAPTER This chapter describes underlying concepts of how routing behaves within the adaptive security appliance, and the routing protocols that are supported. The chapter includes the following sections:,
19 CHAPTER This chapter describes underlying concepts of how routing behaves within the adaptive security appliance, and the routing protocols that are supported. The chapter includes the following sections:,
IP Access List Overview
 Access control lists (ACLs) perform packet filtering to control which packets move through a network and to where. The packet filtering provides security by helping to limit the network traffic, restrict
Access control lists (ACLs) perform packet filtering to control which packets move through a network and to where. The packet filtering provides security by helping to limit the network traffic, restrict
OSPF Not So Stubby Area (NSSA)
 OSPF Not So Stubby Area (NSSA) Document ID: 6208 Contents Introduction Prerequisites Requirements Components Used Conventions What Is a Type 7 LSA? Configuration Tasks Defining a Not So Stubby Area Defining
OSPF Not So Stubby Area (NSSA) Document ID: 6208 Contents Introduction Prerequisites Requirements Components Used Conventions What Is a Type 7 LSA? Configuration Tasks Defining a Not So Stubby Area Defining
ASA 9.x EIGRP Configuration Example
 ASA 9.x EIGRP Configuration Example Contents Introduction Prerequisites Requirements Components Used Background Information Guidelines and Limitations EIGRP and Failover Configure Network Diagram ASDM
ASA 9.x EIGRP Configuration Example Contents Introduction Prerequisites Requirements Components Used Background Information Guidelines and Limitations EIGRP and Failover Configure Network Diagram ASDM
Routing Design. Transit Routing. About Transit Routing
 Transit Routing, page 1 L3Out Ingress Policy Enforcement, page 16 L3Out MTU Considerations, page 20 Shared L3Outs, page 22 L3Out Router IDs, page 27 Multiple External Connectivity, page 30 Transit Routing
Transit Routing, page 1 L3Out Ingress Policy Enforcement, page 16 L3Out MTU Considerations, page 20 Shared L3Outs, page 22 L3Out Router IDs, page 27 Multiple External Connectivity, page 30 Transit Routing
FiberstoreOS IP Routing Configuration Guide
 FiberstoreOS IP Routing Configuration Guide Contents 1 Configuring IP Unicast-Routing... 6 1.1 Overview...6 1.2 Topology... 6 1.3 Configuration... 6 1.4 Validation... 8 2 Configuring RIP... 10 2.1 Overview...10
FiberstoreOS IP Routing Configuration Guide Contents 1 Configuring IP Unicast-Routing... 6 1.1 Overview...6 1.2 Topology... 6 1.3 Configuration... 6 1.4 Validation... 8 2 Configuring RIP... 10 2.1 Overview...10
Chapter 16 OSPF Version 3 Commands
 Chapter 16 OSPF Version 3 Commands NOTE: The OSPF version 3 configuration level is present only on HP devices that support IPv6. area Assigns OSPF version 3 areas. You can assign an IPv4 address or a number
Chapter 16 OSPF Version 3 Commands NOTE: The OSPF version 3 configuration level is present only on HP devices that support IPv6. area Assigns OSPF version 3 areas. You can assign an IPv4 address or a number
What metric value is assigned by default when OSPF route is redistributed into EIGRP?
 What metric value is assigned by default when OSPF route is redistributed into EIGRP? A. 90 B. 110 C. 20 D. 15 E. Infinity Answer: E metric-value - (Optional) A parameter that specifies the EIGRP seed
What metric value is assigned by default when OSPF route is redistributed into EIGRP? A. 90 B. 110 C. 20 D. 15 E. Infinity Answer: E metric-value - (Optional) A parameter that specifies the EIGRP seed
Chapter 4 Lab 4-2, Redistribution Between EIGRP and OSPF
 Chapter 4 Lab 4-2, Redistribution Between EIGRP and OSPF Topology Objectives Review EIGRP and OSPF configuration. Redistribute into EIGRP. Redistribute into OSPF. Summarize routes in EIGRP. Filter routes
Chapter 4 Lab 4-2, Redistribution Between EIGRP and OSPF Topology Objectives Review EIGRP and OSPF configuration. Redistribute into EIGRP. Redistribute into OSPF. Summarize routes in EIGRP. Filter routes
Operation Manual IPv4 Routing H3C S3610&S5510 Series Ethernet Switches. Table of Contents
 Table of Contents Table of Contents Chapter 1 Static Routing Configuration... 1-1 1.1 Introduction... 1-1 1.1.1 Static Route... 1-1 1.1.2 Default Route... 1-1 1.1.3 Application Environment of Static Routing...
Table of Contents Table of Contents Chapter 1 Static Routing Configuration... 1-1 1.1 Introduction... 1-1 1.1.1 Static Route... 1-1 1.1.2 Default Route... 1-1 1.1.3 Application Environment of Static Routing...
Introduction to OSPF
 Introduction to OSPF ISP/IXP Workshops ISP/IXP Workshops 1999, Cisco Systems, Inc. 1 OSPF Dynamic Routing Protocol Link State technology Runs over IP, protocol 89 Designed by IETF for TCP/IP Supports VLSM
Introduction to OSPF ISP/IXP Workshops ISP/IXP Workshops 1999, Cisco Systems, Inc. 1 OSPF Dynamic Routing Protocol Link State technology Runs over IP, protocol 89 Designed by IETF for TCP/IP Supports VLSM
Implementing Access Lists and Prefix Lists
 An access control list (ACL) consists of one or more access control entries (ACE) that collectively define the network traffic profile. This profile can then be referenced by Cisco IOS XR softwarefeatures
An access control list (ACL) consists of one or more access control entries (ACE) that collectively define the network traffic profile. This profile can then be referenced by Cisco IOS XR softwarefeatures
ACI Transit Routing, Route Peering, and EIGRP Support
 ACI Transit Routing, Route Peering, and EIGRP Support ACI Transit Routing This chapter contains the following sections: ACI Transit Routing, on page 1 Transit Routing Use Cases, on page 1 ACI Fabric Route
ACI Transit Routing, Route Peering, and EIGRP Support ACI Transit Routing This chapter contains the following sections: ACI Transit Routing, on page 1 Transit Routing Use Cases, on page 1 ACI Fabric Route
Configuring Logging for Access Lists
 CHAPTER 17 This chapter describes how to configure access list logging for extended access lists and Webytpe access lists, and it describes how to manage deny flows. This section includes the following
CHAPTER 17 This chapter describes how to configure access list logging for extended access lists and Webytpe access lists, and it describes how to manage deny flows. This section includes the following
Configuring Policy-Based Routing
 This chapter contains the following sections: Finding Feature Information, page 1 Information About Policy Based Routing, page 1 Licensing Requirements for Policy-Based Routing, page 5 Prerequisites for
This chapter contains the following sections: Finding Feature Information, page 1 Information About Policy Based Routing, page 1 Licensing Requirements for Policy-Based Routing, page 5 Prerequisites for
BGP Commands. Network Protocols Command Reference, Part 1 P1R-355
 BGP Commands Use the commands in this chapter to configure and monitor Border Gateway Protocol (BGP). For BGP configuration information and examples, refer to the Configuring BGP chapter of the Network
BGP Commands Use the commands in this chapter to configure and monitor Border Gateway Protocol (BGP). For BGP configuration information and examples, refer to the Configuring BGP chapter of the Network
ASA Access Control. Section 3
 [ 39 ] CCNP Security Firewall 642-617 Quick Reference Section 3 ASA Access Control Now that you have connectivity to the ASA and have configured basic networking settings on the ASA, you can start to look
[ 39 ] CCNP Security Firewall 642-617 Quick Reference Section 3 ASA Access Control Now that you have connectivity to the ASA and have configured basic networking settings on the ASA, you can start to look
FiberstoreOS IP Routing Configuration Guide
 FiberstoreOS IP Routing Configuration Guide Contents 1 Configuring IP Unicast-Routing... 1 1.1 Overview... 1 1.2 Topology...1 1.3 Configuration... 2 1.4 Validation... 3 2 Configuring RIP...5 2.1 Overview...
FiberstoreOS IP Routing Configuration Guide Contents 1 Configuring IP Unicast-Routing... 1 1.1 Overview... 1 1.2 Topology...1 1.3 Configuration... 2 1.4 Validation... 3 2 Configuring RIP...5 2.1 Overview...
GRE Tunnel with VRF Configuration Example
 GRE Tunnel with VRF Configuration Example Document ID: 46252 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations Verify Troubleshoot Caveats
GRE Tunnel with VRF Configuration Example Document ID: 46252 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations Verify Troubleshoot Caveats
OSPF. About OSPF. CLI Book 1: Cisco ASA Series General Operations CLI Configuration Guide, 9.4 1
 This chapter describes how to configure the Cisco ASA to route data, perform authentication, and redistribute routing information using the Open Shortest Path First () routing protocol. About, page 1 Guidelines
This chapter describes how to configure the Cisco ASA to route data, perform authentication, and redistribute routing information using the Open Shortest Path First () routing protocol. About, page 1 Guidelines
FSOS IP Routing Configuration Guide
 FSOS IP Routing Configuration Guide Contents 1 Configuring IP Unicast-Routing... 6 1.1 Overview... 6 1.2 Topology...6 1.3 Configuration... 7 1.4 Validation... 8 2 Configuring RIP...10 2.1 Overview... 10
FSOS IP Routing Configuration Guide Contents 1 Configuring IP Unicast-Routing... 6 1.1 Overview... 6 1.2 Topology...6 1.3 Configuration... 7 1.4 Validation... 8 2 Configuring RIP...10 2.1 Overview... 10
Introduction to OSPF
 Introduction to OSPF 1 OSPF Open Shortest Path First Link state or SPF technology Developed by OSPF working group of IETF (RFC 1247) OSPFv2 standard described in RFC2328 Designed for: TCP/IP environment
Introduction to OSPF 1 OSPF Open Shortest Path First Link state or SPF technology Developed by OSPF working group of IETF (RFC 1247) OSPFv2 standard described in RFC2328 Designed for: TCP/IP environment
Contents. Introduction. Prerequisites. Requirements. Components Used
 Contents Introduction Prerequisites Requirements Components Used Configure Network Diagram Configurations OSPF EIGRP RIP Troubleshoot Introduction This document describes how to redistribute Internal Border
Contents Introduction Prerequisites Requirements Components Used Configure Network Diagram Configurations OSPF EIGRP RIP Troubleshoot Introduction This document describes how to redistribute Internal Border
Configuring Policy-Based Routing
 35 CHAPTER This chapter describes the tasks for configuring policy-based routing (PBR) on a router and includes these major sections: Overview of Policy-Based Routing, page 35-1 Policy-Based Routing Configuration
35 CHAPTER This chapter describes the tasks for configuring policy-based routing (PBR) on a router and includes these major sections: Overview of Policy-Based Routing, page 35-1 Policy-Based Routing Configuration
Multiprotocol BGP Extensions for IP Multicast Commands
 Multiprotocol BGP Extensions for IP Multicast Commands Use the commands in this chapter to configure and monitor multiprotocol BGP. Multiprotocol BGP is based on RFC 2283, Multiprotocol Extensions for
Multiprotocol BGP Extensions for IP Multicast Commands Use the commands in this chapter to configure and monitor multiprotocol BGP. Multiprotocol BGP is based on RFC 2283, Multiprotocol Extensions for
Routing Overview. Information About Routing CHAPTER
 21 CHAPTER This chapter describes underlying concepts of how routing behaves within the ASA, and the routing protocols that are supported. This chapter includes the following sections: Information About
21 CHAPTER This chapter describes underlying concepts of how routing behaves within the ASA, and the routing protocols that are supported. This chapter includes the following sections: Information About
Configuring Logging for Access Lists
 CHAPTER 20 This chapter describes how to configure access list logging for extended access lists and Webytpe access lists, and it describes how to manage deny flows. This chapter includes the following
CHAPTER 20 This chapter describes how to configure access list logging for extended access lists and Webytpe access lists, and it describes how to manage deny flows. This chapter includes the following
Introduction to OSPF OSPF. Link State Routing. Link State. Fast Convergence. Low Bandwidth Utilisation
 Introduction to OSPF ISP/IP Workshops OSPF Open Shortest Path First Link state or SPF technology Developed by OSPF working group of IETF (RFC 47) Designed for TCP/IP Internet environment Fast convergence
Introduction to OSPF ISP/IP Workshops OSPF Open Shortest Path First Link state or SPF technology Developed by OSPF working group of IETF (RFC 47) Designed for TCP/IP Internet environment Fast convergence
Firewall Mode Overview
 CHAPTER 16 This chapter describes how to set the firewall mode, as well as how the firewall works in each firewall mode. You can set the firewall mode independently for each context in multiple context
CHAPTER 16 This chapter describes how to set the firewall mode, as well as how the firewall works in each firewall mode. You can set the firewall mode independently for each context in multiple context
LAB11: EIGRP IPv4. EIGRP: Stub. Disclaimer
 Page1 AB11: EIGRP IPv4 isclaimer This onfiguration Guide is designed to assist members to enhance their skills in respective technology area. While every effort has been made to ensure that all material
Page1 AB11: EIGRP IPv4 isclaimer This onfiguration Guide is designed to assist members to enhance their skills in respective technology area. While every effort has been made to ensure that all material
debug ip ospf database external default-metric subnet area 0 stub distribute-list in Serial0/1
 Which statement about stateless autoconfiguration is true? A host can autoconfigure itself by appending its MAC address to the local link prefix (64 bits). 2 Autoconfiguration allows devices to connect
Which statement about stateless autoconfiguration is true? A host can autoconfigure itself by appending its MAC address to the local link prefix (64 bits). 2 Autoconfiguration allows devices to connect
Chapter 4 Software-Based IP Access Control Lists (ACLs)
 Chapter 4 Software-Based IP Access Control Lists (ACLs) This chapter describes software-based ACLs, which are ACLs that processed traffic in software or CPU. (This type of ACL was also referred to as flow-based
Chapter 4 Software-Based IP Access Control Lists (ACLs) This chapter describes software-based ACLs, which are ACLs that processed traffic in software or CPU. (This type of ACL was also referred to as flow-based
BGP Commands: M through N
 match additional-paths advertise-set, on page 3 match as-path, on page 6 match community, on page 8 match extcommunity, on page 10 match local-preference, on page 12 match policy-list, on page 14 match
match additional-paths advertise-set, on page 3 match as-path, on page 6 match community, on page 8 match extcommunity, on page 10 match local-preference, on page 12 match policy-list, on page 14 match
shortcut Tap into learning NOW! Visit for a complete list of Short Cuts. Your Short Cut to Knowledge
 shortcut Your Short Cut to Knowledge The following is an excerpt from a Short Cut published by one of the Pearson Education imprints. Short Cuts are short, concise, PDF documents designed specifically
shortcut Your Short Cut to Knowledge The following is an excerpt from a Short Cut published by one of the Pearson Education imprints. Short Cuts are short, concise, PDF documents designed specifically
Chapter 4 Lab 4-1, Redistribution Between RIP and OSPF
 hapter 4 Lab 4-1, Redistribution Between RIP and OSPF Topology Objectives Review configuration and verification of RIP and OSPF. onfigure passive interfaces in both RIP and OSPF. Filter routing updates
hapter 4 Lab 4-1, Redistribution Between RIP and OSPF Topology Objectives Review configuration and verification of RIP and OSPF. onfigure passive interfaces in both RIP and OSPF. Filter routing updates
LAB5: OSPF IPv4. OSPF: Stub. Disclaimer
 Page1 LAB5: SPF IPv4 Disclaimer This onfiguration Guide is designed to assist members to enhance their skills in respective technology area. While every effort has been made to ensure that all material
Page1 LAB5: SPF IPv4 Disclaimer This onfiguration Guide is designed to assist members to enhance their skills in respective technology area. While every effort has been made to ensure that all material
FiberstoreOS IP Routing Command Line Reference
 FiberstoreOS IP Routing Command Line Reference Contents 1 IP Unicast-Routing Commands...6 1.1 ip address...6 1.2 ip icmp error-interval...7 1.3 ip redirects... 8 1.4 ip unreachables...9 1.5 ip verify unicast
FiberstoreOS IP Routing Command Line Reference Contents 1 IP Unicast-Routing Commands...6 1.1 ip address...6 1.2 ip icmp error-interval...7 1.3 ip redirects... 8 1.4 ip unreachables...9 1.5 ip verify unicast
Chapter 15 OSPF Commands
 Chapter 15 OSPF Commands NOTE: This chapter contains information about OSPF version 2 commands only. For information about OSPF version 3 commands, see OSPF Version 3 Commands on page 16-1. area Assigns
Chapter 15 OSPF Commands NOTE: This chapter contains information about OSPF version 2 commands only. For information about OSPF version 3 commands, see OSPF Version 3 Commands on page 16-1. area Assigns
Lab- Configuring Basic Single-Area OSPFv2
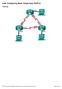 Lab- onfiguring Basic Single-Area OSPFv2 Topology G0/0 G0/0 2013 isco and/or its affiliates. All rights reserved. This document is isco Public. Page 1 of 29 Addressing Table Objectives Device Interface
Lab- onfiguring Basic Single-Area OSPFv2 Topology G0/0 G0/0 2013 isco and/or its affiliates. All rights reserved. This document is isco Public. Page 1 of 29 Addressing Table Objectives Device Interface
FSOS IP Routing Command Line Reference
 FSOS IP Routing Command Line Reference Contents 1 IP Unicast-Routing Commands... 7 1.1 ip address...7 1.2 ip icmp error-interval... 9 1.3 ip redirects...10 1.4 ip unreachables...11 1.5 ip verify unicast
FSOS IP Routing Command Line Reference Contents 1 IP Unicast-Routing Commands... 7 1.1 ip address...7 1.2 ip icmp error-interval... 9 1.3 ip redirects...10 1.4 ip unreachables...11 1.5 ip verify unicast
Configuration and Management of Networks
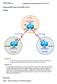 Configuring BGP using the AS_PATH attribute Topology Objectives Background Use BGP commands to prevent private AS numbers from being advertised to the outside world. Use the AS_PATH attribute to filter
Configuring BGP using the AS_PATH attribute Topology Objectives Background Use BGP commands to prevent private AS numbers from being advertised to the outside world. Use the AS_PATH attribute to filter
Table of Contents. 2 Static Route Configuration Commands 2-1 Static Route Configuration Commands 2-1 delete static-routes all 2-1 ip route-static 2-1
 Table of Contents 1 IP Routing Table Commands 1-1 IP Routing Table Commands 1-1 display ip routing-table 1-1 display ip routing-table acl 1-3 display ip routing-table ip-address 1-5 display ip routing-table
Table of Contents 1 IP Routing Table Commands 1-1 IP Routing Table Commands 1-1 display ip routing-table 1-1 display ip routing-table acl 1-3 display ip routing-table ip-address 1-5 display ip routing-table
IPv6 Neighbor Discovery
 About, page 1 Prerequisites for, page 2 Guidelines for, page 2 Defaults for, page 4 Configure, page 5 View and Clear Dynamically Discovered Neighbors, page 10 History for, page 11 About The IPv6 neighbor
About, page 1 Prerequisites for, page 2 Guidelines for, page 2 Defaults for, page 4 Configure, page 5 View and Clear Dynamically Discovered Neighbors, page 10 History for, page 11 About The IPv6 neighbor
IP Access List Overview
 Access control lists (ACLs) perform packet filtering to control which packets move through the network and where. Such control provides security by helping to limit network traffic, restrict the access
Access control lists (ACLs) perform packet filtering to control which packets move through the network and where. Such control provides security by helping to limit network traffic, restrict the access
BGP Cost Community. Prerequisites for the BGP Cost Community Feature
 The feature introduces the cost extended community attribute. The cost community is a non-transitive extended community attribute that is passed to internal BGP (ibgp) and confederation peers but not to
The feature introduces the cost extended community attribute. The cost community is a non-transitive extended community attribute that is passed to internal BGP (ibgp) and confederation peers but not to
vcloud Director Tenant Portal Guide vcloud Director 8.20
 vcloud Director Tenant Portal Guide vcloud Director 8.20 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments about this documentation,
vcloud Director Tenant Portal Guide vcloud Director 8.20 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments about this documentation,
Implementing Layer 2 Access Lists
 Implementing Layer 2 Access Lists An Ethernet services access control list (ACL) consists of one me access control entries (ACE) that collectively define the Layer 2 netwk traffic profile. This profile
Implementing Layer 2 Access Lists An Ethernet services access control list (ACL) consists of one me access control entries (ACE) that collectively define the Layer 2 netwk traffic profile. This profile
BGP Support for IP Prefix Export from a VRF Table into the Global Table
 BGP Support for IP Prefix Export from a VRF Table into the Global Table This feature allows a network administrator to export IP prefixes from a VRF table into the global routing table. Finding Feature
BGP Support for IP Prefix Export from a VRF Table into the Global Table This feature allows a network administrator to export IP prefixes from a VRF table into the global routing table. Finding Feature
OSPF NSSA Operations Test Report Revision 1.7. InterOperability Lab 121 Technology Drive, Suite 2 Durham NH,
 IPv4 CONSORTIUM OSPF NSSA Operations Test Report Revision 1.7 InterOperability Lab 121 Technology Drive, Suite 2 Durham NH, 03824 +1-603-862-3941 Consortium Managers: Erica Williamsen Timothy Winters ericaw@iol.unh.edu
IPv4 CONSORTIUM OSPF NSSA Operations Test Report Revision 1.7 InterOperability Lab 121 Technology Drive, Suite 2 Durham NH, 03824 +1-603-862-3941 Consortium Managers: Erica Williamsen Timothy Winters ericaw@iol.unh.edu
IP Named Access Control Lists
 Access control lists (ACLs) perform packet filtering to control the movement of packets through a network. Packet filtering provides security by limiting the access of traffic into a network, restricting
Access control lists (ACLs) perform packet filtering to control the movement of packets through a network. Packet filtering provides security by limiting the access of traffic into a network, restricting
Top-Down Network Design, Ch. 7: Selecting Switching and Routing Protocols. Top-Down Network Design. Selecting Switching and Routing Protocols
 Top-Down Network Design Chapter Seven Selecting Switching and Routing Protocols Copyright 2010 Cisco Press & Priscilla Oppenheimer 1 Switching 2 Page 1 Objectives MAC address table Describe the features
Top-Down Network Design Chapter Seven Selecting Switching and Routing Protocols Copyright 2010 Cisco Press & Priscilla Oppenheimer 1 Switching 2 Page 1 Objectives MAC address table Describe the features
Configuring an IP ACL
 9 CHAPTER This chapter describes how to configure IP access control lists (ACLs). This chapter includes the following sections: Information About ACLs, page 9-1 Prerequisites for IP ACLs, page 9-5 Guidelines
9 CHAPTER This chapter describes how to configure IP access control lists (ACLs). This chapter includes the following sections: Information About ACLs, page 9-1 Prerequisites for IP ACLs, page 9-5 Guidelines
Configuring Redundant Routing on the VPN 3000 Concentrator
 Configuring Redundant Routing on the VPN 3000 Concentrator Document ID: 13354 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Router Configurations
Configuring Redundant Routing on the VPN 3000 Concentrator Document ID: 13354 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Router Configurations
ITBraindumps. Latest IT Braindumps study guide
 ITBraindumps http://www.itbraindumps.com Latest IT Braindumps study guide Exam : 300-101 Title : Implementing Cisco IP Routing Vendor : Cisco Version : DEMO Get Latest & Valid 300-101 Exam's Question and
ITBraindumps http://www.itbraindumps.com Latest IT Braindumps study guide Exam : 300-101 Title : Implementing Cisco IP Routing Vendor : Cisco Version : DEMO Get Latest & Valid 300-101 Exam's Question and
CCNA Exploration: Routing Protocols and Concepts Chapter 11 Case Study
 bjectives: Consolidate SPF knowledge. Describe the operation of SPF multi-area. Introduce the concept of route summarization with SPF. Introduce the concept of SPF optimization. Intro: Trevni Inc. needed
bjectives: Consolidate SPF knowledge. Describe the operation of SPF multi-area. Introduce the concept of route summarization with SPF. Introduce the concept of SPF optimization. Intro: Trevni Inc. needed
BGP Commands. Network Protocols Command Reference, Part 1 P1R-355
 BGP Commands Use the commands in this chapter to configure and monitor Border Gateway Protocol (BGP). For BGP configuration information and examples, refer to the Configuring BGP chapter of the Network
BGP Commands Use the commands in this chapter to configure and monitor Border Gateway Protocol (BGP). For BGP configuration information and examples, refer to the Configuring BGP chapter of the Network
material. For more information on how to get additional questions, please see a.
 Review Questions The following questions are designed to test your understanding of this chapter s material. For more information on how to get additional questions, please see www.lammle.com/ccn a. You
Review Questions The following questions are designed to test your understanding of this chapter s material. For more information on how to get additional questions, please see www.lammle.com/ccn a. You
Implementing Static Routes for IPv6
 Implementing Static Routes for IPv6 Last Updated: July 31, 2012 This module describes how to configure static routes for IPv6. Routing defines the paths over which packets travel in the network. Manually
Implementing Static Routes for IPv6 Last Updated: July 31, 2012 This module describes how to configure static routes for IPv6. Routing defines the paths over which packets travel in the network. Manually
Question: 3 Which LSA type describes the router ID of ASBR routers located in remote areas?
 Volume: 65 Questions Question: 1 Which two statements describe aggregate routes? (Choose two.) A. Invalid routing prefixes are not advertised to external peers. B. Internal routing instabilities can be
Volume: 65 Questions Question: 1 Which two statements describe aggregate routes? (Choose two.) A. Invalid routing prefixes are not advertised to external peers. B. Internal routing instabilities can be
Attribute-Based Access Control
 Attributes are customized network objects for use in your configuration. You can define and use them in Cisco ASA configurations to filter traffic associated with one or more virtual machines in an VMware
Attributes are customized network objects for use in your configuration. You can define and use them in Cisco ASA configurations to filter traffic associated with one or more virtual machines in an VMware
Chapter 17 Configuring IPX (9300 Series Only)
 Chapter 17 Configuring IPX (9300 Series Only) This chapter describes how to configure the IPX protocol on the ProCurve Routing Switches using the CLI and Web management interface. For information about
Chapter 17 Configuring IPX (9300 Series Only) This chapter describes how to configure the IPX protocol on the ProCurve Routing Switches using the CLI and Web management interface. For information about
Implementing Static Routes
 This module describes how to implement static routes. Static routes are user-defined routes that cause packets moving between a source and a destination to take a specified path. Static routes can be important
This module describes how to implement static routes. Static routes are user-defined routes that cause packets moving between a source and a destination to take a specified path. Static routes can be important
H3C S7500E-X OSPF Configuration Examples
 H3C S7500E-X OSPF Configuration Examples Copyright 2015 Hangzhou H3C Technologies Co., Ltd. All rights reserved. No part of this manual may be reproduced or transmitted in any form or by any means without
H3C S7500E-X OSPF Configuration Examples Copyright 2015 Hangzhou H3C Technologies Co., Ltd. All rights reserved. No part of this manual may be reproduced or transmitted in any form or by any means without
IPv6 Routing: OSPFv3
 Open Shortest Path First version 3 (OSPFv3) is an IPv4 and IPv6 link-state routing protocol that supports IPv6 and IPv4 unicast address families (AFs). Finding Feature Information, page 1 Prerequisites
Open Shortest Path First version 3 (OSPFv3) is an IPv4 and IPv6 link-state routing protocol that supports IPv6 and IPv4 unicast address families (AFs). Finding Feature Information, page 1 Prerequisites
OSPFv3 Commands. address-family (OSPFv3), page 4. authentication (OSPFv3), page 7
 This module describes the commands used to configure and monitor the IP Version 6 (IPv6) Open Shortest Path First Version 3 (OSPFv3) routing protocol. For detailed information about OSPFv3 concepts, configuration
This module describes the commands used to configure and monitor the IP Version 6 (IPv6) Open Shortest Path First Version 3 (OSPFv3) routing protocol. For detailed information about OSPFv3 concepts, configuration
IBGP internals. BGP Advanced Topics. Agenda. BGP Continuity 1. L49 - BGP Advanced Topics. L49 - BGP Advanced Topics
 IBGP internals BGP Advanced Topics main IBGP aspects inside an AS continuity all packets entering the AS that were not blocked by some policies should reach the proper exit BGP router all transit routers
IBGP internals BGP Advanced Topics main IBGP aspects inside an AS continuity all packets entering the AS that were not blocked by some policies should reach the proper exit BGP router all transit routers
Why we need to divide network?
 Content Introduction Layer 3 IP Protocol IP-Header: www.ietf.org and RFC-760 Addressing Schemes Subnetting Routing Layer 3 Solution in Trains Communication Matrix (Information Based Communication) 53 Why
Content Introduction Layer 3 IP Protocol IP-Header: www.ietf.org and RFC-760 Addressing Schemes Subnetting Routing Layer 3 Solution in Trains Communication Matrix (Information Based Communication) 53 Why
