Contents. Introduction. Prerequisites Components Used. Introduction. Prerequisites Components Used
|
|
|
- Zoe French
- 6 years ago
- Views:
Transcription
1 Contents Introduction Prerequisites Components Used Install Cisco Configuration Professional Router Configuration to Run Cisco CP Requirements Conventions Configure Network Diagram Interface Configuration NAT Configuration Routing Configuration Miscellaneous Configuration CLI Configuration Verify Troubleshoot How can I change the user name and password for the router? I receive an internal error when I use Internet Explorer 8 to access Cisco CP. How do I resolve this issue? I receive this error message when I try to install Cisco CP: "Unable to read the source file. File could be Corrupted. Please re-install Cisco Configuration Professional to resolve the issue." How do I resolve this issue? How do I access the Cisco CP technical logs? Router discovery takes more time than usual. How do I resolve this issue? I am unable to view the IPS configuration page on Cisco CP. How do I resolve this issue? Related Information Related Cisco Support Community Discussions Introduction This document describes how to use the Cisco Configuration Professional (Cisco CP) in order to set the basic configuration of the router. Basic configuration of the router includes configuration of the IP address, default routing, static and dynamic routing, static and dynamic NATing, host name, banner, secret password, user accounts, and other options. Cisco CP allows you to configure your router in several network environments, such as small office home office (SOHO), branch office (BO), regional office, and central site or Enterprise headquarters, with an easy-to-use web-based management interface. For more information about Cisco Configuration Professional, refer to Cisco Configuration Professional Quick Start Guide. Prerequisites Components Used
2 The information in this document is based on these software and hardware versions: Cisco 2811 Router with Cisco IOS Software Release 12.4(9) Cisco CP Version 2.5 The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command. Install Cisco Configuration Professional Perform these steps in order to install CCP: Download Cisco CP V2.5 from the Cisco Software Center (registered customers only) and install it on your local PC. The latest version of Cisco CP can be found at the CCP website. Launch Cisco CP from your local PC through Start > Programs > Cisco Configuration Professional and choose the Community which has the router you want to configure.
3
4 In order to discover the device you want to configure, highlight the router and click the Discover button.
5 Note: For information on the Cisco router models and IOS releases that are compatible to CCPv2.5, refer to the Compatible Cisco IOS releases section. Note: For information on the PC requirements that runs CCPv2.5, refer to System Requirements section Router Configuration to Run Cisco CP Perform these configuration steps in order to run Cisco CP on a Cisco router: Connect to your router using Telnet, SSH, or through the console. Enter global configuration mode using this command: Router(config)#enable Router(config)# If HTTP and HTTPS are enabled and configured to use nonstandard port numbers, you can skip this step and simply use the port number already configured.
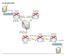
6 Enable the router HTTP or HTTPS server using these Cisco IOS Software commands: Router(config)# ip http server Router(config)# ip http secure-server Router(config)# ip http authentication local Create a user with privilege level 15: Router(config)# username <username> privilege 15 password 0 <password> Note: Replace <username> and <password> with the username and password that you want to configure. Do not use the same password for your user and enable passwords. Configure SSH and Telnet for local login and privilege level 15. Router(config)# line vty 0 4 Router(config-line)# privilege level 15 Router(config-line)# login local Router(config-line)# transport input telnet Router(config-line)# transport input telnet ssh Router(config-line)# exit (Optional) Enable local logging to support the log monitoring function: Router(config)# logging buffered warning Requirements This document assumes that the Cisco router is fully operational and configured to allow the Cisco CP to make configuration changes. For complete information on how to start using the Cisco CP, refer to Getting Started with Cisco Configuration Professional. Conventions Refer to the Cisco Technical Tips Conventions for more information on document conventions. Configure In this section, you are presented with the information to configure the basic settings for a router in a network. Note: Use the Command Lookup Tool (registered customers only) to obtain more information on the commands used in this section. Network Diagram This document uses this network setup:
7 Note: The IP addressing schemes used in this configuration are not legally routable on the Internet. They are RFC 1918 addresses which have been used in a lab environment. Interface Configuration Perform these steps in order to configure the interfaces of a Cisco router: Click Home in order to go to the Cisco CP homepage. The Cisco CP homepage provides information such as the hardware and software of the router, feature availability, and a configuration summary. Choose Configure > Interface Management > Interfaces and Connections > Create Connection in order to configure the WAN connection for the interface. As an example, for FastEthernet 0/1, choose the Ethernet option and click Create New Connection. Note: For other types of interfaces like Ethernet, choose the respective interface type and click Create New Connection to proceed.
8
9 Click Next in order to proceed once this interface appears:
10 Choose FastEthernet 0/1 (desired) from the Available Interfaces option and click Next.
11 Specify the static IP address with the corresponding subnet mask for the interface and click Next.
12 Configure the default routing with optional parameters such as the next hop IP address ( as per network diagram) supplied by the ISP and click Next.
13 This window appears and shows the configuration summary configured by the user. Click Finish. Note: The connectivity of the configuration can be checked by checking the checkbox next to Test the connectivity after configuring. This is an optional feature available.
14 This window appears and shows the command delivery status to the router. Otherwise, it displays errors if the command delivery fails due to incompatible commands or unsupported features.
15 Choose Configure > Interface Management > Interfaces and Connections > Edit Interfaces/Connections in order to add/edit/delete the various interfaces. Highlight the interface with which you want to make changes and click Edit if you want to edit or change the interface configuration. Here, you can change the existing static IP address.
16 NAT Configuration Dynamic NAT Configuration Perform these steps in order to configure the dynamic NAT in a Cisco router: Choose Configure > Router > NAT > Basic NAT and click Launch the selected task in order to configure basic NATing.
17 Click Next. Choose the interface that connects to the Internet or your ISP and choose the IP address range to which Internet access is to be shared. After choosing this information, click Next as
18 shown here: This window appears and shows the configuration summary configured by the user. Click Finish.
19 The Edit NAT Configuration window shows the configured dynamic NAT configuration with the translated IP address overloaded (PATing). If you want to configure the dynamic NATing with address pool, click Address Pool. Click Add.
20 Here, information such as the pool name and IP address range with netmask are provided. There can be times when most of the addresses in the pool have been assigned, and the IP address pool is nearly depleted. When this occurs, PAT can be used with a single IP address in order to satisfy additional requests for IP addresses. Check Port Address Translation (PAT) if you want the router to use PAT when the address pool is close to depletion. Click OK. Click Add.
21 Click Edit. Choose Address Pool in the Type field, provide the name to the Address Pool as pool, and click OK.
22 This window shows the configuration for dynamic NATing with the address pool. Click Designate NAT Interfaces. Use this window in order to designate the inside and outside interfaces that you want to use in NAT translations. NAT uses the inside and outside designations when it interprets
23 translation rules, because translations are performed from inside to outside, or from outside to inside. Once designated, these interfaces are used in all NAT translation rules. The designated interfaces appear above the Translation Rules list in the main NAT window. Static NAT Configuration Perform these steps in order to configure static NAT in a Cisco router: Choose Configure > Router > NAT > Edit NAT Configuration and click Add in order to configure static NATing.
24 Choose the Direction either from inside to outside or from outside to inside, and specify the inside IP address to be translated under Translate from Interface. For the Translate to Interface area, choose the Type: Choose IP Address if you want the Translate from Address to be translated to an IP address defined in the IP Address field. Choose Interface if you want the Translate from Address to use the address of an interface on the router. The Translate from Address is translated to the IP address assigned to the interface that you specify in the Interface field. Check Redirect Port if you want to include port information for the inside device in the translation. This enables you to use the same public IP address for multiple devices, as long as the port specified for each device is different. You must create an entry for each port mapping for this Translated to address. Click TCP if this is a TCP port number and click UDP if it is a UDP port number. In the Original Port field, enter the port number on the inside device. In the Translated Port field, enter the port number that the router is to use for this translation. Refer to the Allowing the Internet to Access Internal Devices section of Configuring Network Address Translation: Getting Started.
25 This window shows the static NATing configuration with port redirection enabled:
26 Routing Configuration Static Routing Configuration Perform these steps in order to configure static routing in a Cisco router: Choose Configure > Router > Static and Dynamic Routing and click Add in order to configure static routing. Enter the Destination Network address with mask and choose either outgoing interface or next hop IP address.
27 This window shows the static route configured for the network with as the next hop IP address: Dynamic Routing Configuration Perform these steps in order to configure the dynamic routing in a Cisco router: Choose Configure > Router > Static and Dynamic Routing.
28 Select the RIP and click Edit. Check Enable RIP, choose the RIP version, and click Add.
29 Specify the Network address to be advertised.
30 Click OK. Click Deliver in order to transfer the commands to the router.
31 This window shows the dynamic RIP routing configuration:
32 Miscellaneous Configuration Perform these steps in order to configure the other basic settings in a Cisco router: Choose Configure > Router > Router Options and click Edit if you want to change the Hostname, Domain Name, Banner, and Enable Secret Password properties for a router. Choose Configure > Router Access > User Accounts/View in order to add/edit/delete the User Accounts to the router.
33
34 Choose Configure > Utilities > Save Running Config to PC in order to save the configuration to the NVRAM of the router as well as the PC and to reset the current configuration to default (factory) settings. Note: In order to use CCP to restore the configuration file stored on a computer to a router or to backup the configuration file from a router to a computer, access the Configuration Editor, and click I agree. In the Configure window, choose Import configuration from PC, and then click the replace running configuration button.
35 CLI Configuration Router Configuration
36 Router#show run Building configuration... Current configuration : 2525 bytes! version 12.4 service timestamps debug datetime msec service timestamps log datetime msec no service password-encryption! hostname Router! boot-start-marker boot-end-marker! no logging buffered enable password cisco! no aaa new-model! resource policy!!! ip cef!!!!--- RSA certificate generated after you enable the!--- ip http secureserver command. crypto pki trustpoint TP-self-signed enrollment selfsigned subject-name cn=ios- Self-Signed-Certificate revocation-check none rsakeypair TP-self-signed crypto pki certificate chain TP-self-signed certificate self-signed B1 A D0609 2A F70D F30 2D F532D 53656C66 2D E65642D D E 170D A17 0D A F302D F532D53 656C662D E 65642D D F 300D0609 2A F70D D CD35 A3A6E322 9B6005DA A0FF26C2 8A0DC5AF 27B38F3B DBF2BF58 D8F2655D EC8BC750 03FE3A25 0F79DC74 3A CB9486F1 A1F5BF43 D92BA7AF 3C72A57B D8D A5A18F7F 27955AB0 AC36B560 3BE9F648 A4F6F41F B9E9C5E6 F9570DEB 5555FDED 9593BD00 5ABB30CD D3B9BDFA F570F CE 3D A E30 0F D FF FF 301B D F E 70616D6D 692E636F 6D301F D A0A C EFDA58AB C319820D C5301D D 0E A0AC EF DA58ABC D C5300D06 092A F70D B0EC8C F 587E15D6 5485A043 E7BB258D 0C9A63F2 DA18793D CACC026E BC0B9B33 F8A27B34 5BD7DD7F FCECA34F 04662AEC 07FD7677 A90A8D1C C2562FEC 4EFFF17C 360BF88A FEDC7CAA AE308F6C A5756C4A F574F5F3 39CE14AE BAAEC655 D5920DD0 DA76E296 B246E36E 16CFBC5A BBDAD C quit!!!!!!!!!--- Create a user account named ccpccp with all privileges. username ccpccp privilege 15 password 0 cisco123 archive log config hidekeys!!!!!!!--- The LAN interface configured with a private IP address. interface FastEthernet0/0 description $ETH-LAN$ ip address !--- Designate that traffic that originates from behind!--- the interface is subject to Network Address Translation (NAT). ip nat inside ip virtual-reassembly duplex auto speed auto!!- -- This is the LAN interface configured with a routable (public) IP address. interface FastEthernet0/1 description $ETH-WAN$ ip address !--- Designate that this interface is the!--- destination for traffic that has undergone NAT. ip nat outside ip virtual-reassembly duplex auto speed auto!!!--- RIP version 2 routing is enabled. router rip version 2 network no auto-summary!--- This is where the commands to enable HTTP and HTTPS are configured. ip http server ip http authentication local ip http secure-server!!--- This configuration is for dynamic NAT.!!--- Define a pool of outside IP addresses for NAT. ip nat pool pool netmask !--- In order to enable NAT of the inside source address,!--- specify that traffic from hosts that match access list 1!--- are NATed to the address pool named pool1. ip nat inside
37 source list 1 pool pool1!!--- Access list 1 permits only network to be NATed. access-list 1 remark CCP_ACL Category=2 access-list 1 permit !!--- This configuration is for static NAT!--- In order to translate the packets between the real IP address with TCP!--- port 80 and the mapped IP address with TCP port 500.! ip nat outside source static tcp extendable!!!!!--- The default route is configured and points to ip route !!!! control-plane!!!!!!!!!! line con 0 line aux 0!--- Telnet enabled with password as cisco. line vty 0 4 password cisco transport input all line vty 5 15 password cisco transport input all!!! end Verify Choose Configure > Interface & Connections > Edit Interface Connections > Test Connection in order to test the end-to-end connectivity. You can specify the remote end IP address if you click the User-specified radio button.
38 Troubleshoot The Output Interpreter Tool (registered customers only) (OIT) supports certain show commands. Use the OIT to view an analysis of show command output. Note: Refer to Important Information on Debug Commands before you issue debug commands. You can use these options in order to troubleshoot: Choose Help > About this Router in order to view the hardware and software details of the router.
39 The Help option provides information about the various available options in the Cisco CP for the configuration of routers.
40 How can I change the user name and password for the router? You can change the router user name and password through Cisco CP. Complete these steps in order to change the user name and password: Create a new temporary user account, and then log in to the temporary user account. Change the user name and password of the main user account (that is, the user account of the router on which you want to change the user name and password) in your Cisco CP. Log out from the temporary account, and log in to the main user account. Delete the temporary user account after you change the password for the main account. I receive an internal error when I use Internet Explorer 8 to access Cisco CP. How do I resolve this issue? Problem You might receive this internal error when you use Internet Explorer 8 to configure the 2800 series router using Cisco CP: Internal error: [FaultEvent fault=[rpc Fault faultstring="send failed" faultcode="client.error.messagesend" faultdetail="channel.connect.failed error NetConnection.Call.Failed: HTTP: Status 200: url: ' messageid="a08846ff-e7c6-f578-7c38-61c6e94899c7" type="fault" bubbles=false cancelable=true eventphase=2]
41 Downgrading Java does not resolve the issue. Solution This error might be the result of a browser compatibility issue. Internet Explorer 8 changes many fundamental aspects of developing applications for IE. Cisco recommends that you downgrade Internet Explorer to version 7. You should also uninstall and reinstall Cisco CP. I receive this error message when I try to install Cisco CP: "Unable to read the source file. File could be Corrupted. Please re-install Cisco Configuration Professional to resolve the issue." How do I resolve this issue? Problem When you download the application setup file and attempt to install Cisco CP, you might receive this error: Unable to read the source file. File could be Corrupted. Please re-install Cisco Configuration Professional to resolve the issue Solution Try the following in order to resolve this. Delete all instances of Cisco CP on your PC, and perform a fresh download and install. If the previous step does not work, try to download a different version of Cisco CP. If the previous step does not work, contact Cisco TAC. Note: You must have valid Cisco user credentials in order to contact Cisco TAC. How do I access the Cisco CP technical logs? Click Start > Programs > Cisco Systems > Cisco Configuration Professional > Collect Data for Tech Support. Cisco CP automatically archives the logs in a zip file named _ccptech.zip. Perform a local file system search for this file if it is not saved to your Desktop. You can send these technical logs to Cisco TAC for further troubleshooting. Note: Close all instances of Cisco CP to get rid of any other issues in archiving the logs. Router discovery takes more time than usual. How do I resolve this issue? Problem Once Cisco CP is launched and the community is configured, discovery of the router takes more time than usual. Here are the Cisco CP logs that describe the time elapsed: July 10, :29:19 AM EDT Discovering device test-router July 10, :29:20 AM EDT Last discovery clean-up elapsed time was 47 milliseconds. July 10, :31:13 AM EDT Discovery job allocation elapsed time was milliseconds.
42 July 10, :31:13 AM EDT Authentication completed. July 10, :40:28 AM EDT Video feature disabled. Video feature discovery elapsed time= ms July 10, :51:15 AM EDT Security feature ready - elapsed time was milliseconds. July 10, :51:16 AM EDT Total device test-router discovery elapsed time was milliseconds. This issue occurs with all routers irrespective of their model and platform. In addition, there are no memory or CPU related issues on the routers. Solution Verify the authentication mode. If authentication does not occur locally, then check if there is an issue with the authenticating server. Fix any issue with the authenticating server in order to resolve this issue. I am unable to view the IPS configuration page on Cisco CP. How do I resolve this issue? Problem When a specific feature in the Configuration window does not show anything except a blank page, there might be a incompatibility issues. Solution Verify these items in order to resolve this issue: Verify if that specific feature is supported and enabled on your router model. Verify if your router version supports that feature. Router version incompatibilities could be resolved with a version upgrade. Verify if the problem is with the current licensing. Related Information Cisco Configuration Professional Quick Start Guide Cisco Product Support Page - Routers NAT Support Page Technical Support & Documentation - Cisco Systems
Basic Router Configuration using SDM
 Basic Router Configuration using SDM Document ID: 71305 Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Interface Configuration NAT Configuration Routing Configuration
Basic Router Configuration using SDM Document ID: 71305 Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Interface Configuration NAT Configuration Routing Configuration
NATIONAL_WATER_CONSERVATION#sh run Building configuration...
 NATIONAL_WATER_CONSERVATION#sh run Building configuration... Current configuration : 6390 bytes Last configuration change at 13:01:34 UTC Tue Jul 4 2017 by kembo version 15.4 service timestamps debug datetime
NATIONAL_WATER_CONSERVATION#sh run Building configuration... Current configuration : 6390 bytes Last configuration change at 13:01:34 UTC Tue Jul 4 2017 by kembo version 15.4 service timestamps debug datetime
Configuration Professional: Site to Site IPsec VPN Between Two IOS Routers Configuration Example
 Configuration Professional: Site to Site IPsec VPN Between Two IOS Routers Configuration Example Document ID: 113337 Contents Introduction Prerequisites Requirements Components Used Conventions Configuration
Configuration Professional: Site to Site IPsec VPN Between Two IOS Routers Configuration Example Document ID: 113337 Contents Introduction Prerequisites Requirements Components Used Conventions Configuration
Lab Configuring Port Address Translation (PAT) (Instructor Version)
 (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Topology Addressing Table Objectives Device Interface IP Address Subnet Mask
(Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Topology Addressing Table Objectives Device Interface IP Address Subnet Mask
Lab Configuring Dynamic and Static NAT (Instructor Version Optional Lab)
 (Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
(Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
Lab Configuring Basic RIPv2 (Solution)
 (Solution) Topology 2017 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 15 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway
(Solution) Topology 2017 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 15 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway
Lab Configuring Dynamic and Static NAT (Solution)
 (Solution) Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway Gateway G0/1 192.168.1.1 255.255.255.0 N/A S0/0/1 209.165.201.18 255.255.255.252 N/A ISP S0/0/0 (DCE)
(Solution) Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway Gateway G0/1 192.168.1.1 255.255.255.0 N/A S0/0/1 209.165.201.18 255.255.255.252 N/A ISP S0/0/0 (DCE)
IOS Router : Easy VPN (EzVPN) in Network Extension Mode (NEM) with Split tunnelling Configuration Example
 IOS Router : Easy VPN (EzVPN) in Network Extension Mode (NEM) with Split tunnelling Configuration Example Document ID: 63098 Contents Introduction Prerequisites Requirements Components Used Conventions
IOS Router : Easy VPN (EzVPN) in Network Extension Mode (NEM) with Split tunnelling Configuration Example Document ID: 63098 Contents Introduction Prerequisites Requirements Components Used Conventions
Lab Configuring and Verifying Standard IPv4 ACLs (Instructor Version Optional Lab)
 (Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
(Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
How to Configure a Cisco Router Behind a Non-Cisco Cable Modem
 How to Configure a Cisco Router Behind a Non-Cisco Cable Modem Document ID: 19268 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations Verify
How to Configure a Cisco Router Behind a Non-Cisco Cable Modem Document ID: 19268 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations Verify
Lab Troubleshooting IPv4 and IPv6 Static Routes (Instructor Version Optional Lab)
 (Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
(Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
Lab Designing and Implementing a VLSM Addressing Scheme. Topology. Objectives. Background / Scenario
 CSNB214 Packet Tracer Lab Designing and Implementing a VLSM Addressing Scheme Topology Objectives Part 1: Examine Network Requirements Part 2: Design the VLSM Address Scheme Part 3: Cable and Configure
CSNB214 Packet Tracer Lab Designing and Implementing a VLSM Addressing Scheme Topology Objectives Part 1: Examine Network Requirements Part 2: Design the VLSM Address Scheme Part 3: Cable and Configure
CONFIGURATION DU SWITCH
 Current configuration : 2037 bytes version 12.2 no service pad service timestamps debug uptime service timestamps log uptime no service password-encryption hostname Switch no aaa new-model ip subnet-zero
Current configuration : 2037 bytes version 12.2 no service pad service timestamps debug uptime service timestamps log uptime no service password-encryption hostname Switch no aaa new-model ip subnet-zero
Policy Based Routing with the Multiple Tracking Options Feature Configuration Example
 Policy Based Routing with the Multiple Tracking Options Feature Configuration Example Document ID: 48003 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram
Policy Based Routing with the Multiple Tracking Options Feature Configuration Example Document ID: 48003 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram
VPN Connection through Zone based Firewall Router Configuration Example
 VPN Connection through Zone based Firewall Router Configuration Example Document ID: 112051 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Configure
VPN Connection through Zone based Firewall Router Configuration Example Document ID: 112051 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Configure
Advanced IPv6 Training Course. Lab Manual. v1.3 Page 1
 Advanced IPv6 Training Course Lab Manual v1.3 Page 1 Network Diagram AS66 AS99 10.X.0.1/30 2001:ffXX:0:01::a/127 E0/0 R 1 E1/0 172.X.255.1 2001:ffXX::1/128 172.16.0.X/24 2001:ff69::X/64 E0/1 10.X.0.5/30
Advanced IPv6 Training Course Lab Manual v1.3 Page 1 Network Diagram AS66 AS99 10.X.0.1/30 2001:ffXX:0:01::a/127 E0/0 R 1 E1/0 172.X.255.1 2001:ffXX::1/128 172.16.0.X/24 2001:ff69::X/64 E0/1 10.X.0.5/30
BẮT 10 GIAO THỨC (SNMP, HTTP, HTTPS, NETMEETING, NTP, TELNET, SSH, H323, SIP, DOMAIN )
 SƠ ĐỒ MẠNG VISIO SƠ ĐỒ GNS3 BẮT 10 GIAO THỨC (SNMP, HTTP, HTTPS, NETMEETING, NTP, TELNET, SSH, H323, SIP, DOMAIN ) PING TẠO RA LƯU LƯỢNG SAU KHI CẤM PING FILE CẤU HÌNH CÁC ROUTER ROUTER SAIGON Last configuration
SƠ ĐỒ MẠNG VISIO SƠ ĐỒ GNS3 BẮT 10 GIAO THỨC (SNMP, HTTP, HTTPS, NETMEETING, NTP, TELNET, SSH, H323, SIP, DOMAIN ) PING TẠO RA LƯU LƯỢNG SAU KHI CẤM PING FILE CẤU HÌNH CÁC ROUTER ROUTER SAIGON Last configuration
No Service Password-Recovery
 No Service Password-Recovery Last Updated: January 18, 2012 The No Service Password-Recovery feature is a security enhancement that prevents anyone with console access from accessing the router configuration
No Service Password-Recovery Last Updated: January 18, 2012 The No Service Password-Recovery feature is a security enhancement that prevents anyone with console access from accessing the router configuration
Lab Configuring an ISR with SDM Express
 Lab 5.2.3 Configuring an ISR with SDM Express Objectives Configure basic router global settings router name, users, and login passwords using Cisco SDM Express. Configure LAN and Internet connections on
Lab 5.2.3 Configuring an ISR with SDM Express Objectives Configure basic router global settings router name, users, and login passwords using Cisco SDM Express. Configure LAN and Internet connections on
Configuring IDS TCP Reset Using VMS IDS MC
 Configuring IDS TCP Reset Using VMS IDS MC Document ID: 47560 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations Initial Sensor Configuration
Configuring IDS TCP Reset Using VMS IDS MC Document ID: 47560 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations Initial Sensor Configuration
Troubleshooting Network analysis Software communication tests and development Education. Protocols used for communication (10 seconds capture)
 Lab 1 Wireshark Wireshark is an open source and free packet analyser used for many purposes, such as: Troubleshooting Network analysis Software communication tests and development Education This reports
Lab 1 Wireshark Wireshark is an open source and free packet analyser used for many purposes, such as: Troubleshooting Network analysis Software communication tests and development Education This reports
Router Allows VPN Clients to Connect IPsec and Internet Using Split Tunneling Configuration Example
 Router Allows VPN Clients to Connect IPsec and Internet Using Split Tunneling Configuration Example Document ID: 91193 Contents Introduction Prerequisites Requirements Components Used Conventions Background
Router Allows VPN Clients to Connect IPsec and Internet Using Split Tunneling Configuration Example Document ID: 91193 Contents Introduction Prerequisites Requirements Components Used Conventions Background
Lab Configuring and Verifying Extended ACLs Topology
 Topology 2015 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.10.1
Topology 2015 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.10.1
CCNA Semester 2 labs. Labs for chapters 2 10
 CCNA Semester 2 labs Labs for chapters 2 10 2.2.2.5 Lab - Configuring IPv4 Static and Default Routes 2.3.2.4 Lab - Troubleshooting Static Routes 3.2.1.9 Lab - Configuring Basic RIPv2 5.2.2.9 Lab - Configuring
CCNA Semester 2 labs Labs for chapters 2 10 2.2.2.5 Lab - Configuring IPv4 Static and Default Routes 2.3.2.4 Lab - Troubleshooting Static Routes 3.2.1.9 Lab - Configuring Basic RIPv2 5.2.2.9 Lab - Configuring
Lab 8.5.2: Troubleshooting Enterprise Networks 2
 Lab 8.5.2: Troubleshooting Enterprise Networks 2 Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway Fa0/0 192.168.10.1 255.255.255.0 N/A R1 Fa0/1 192.168.11.1 255.255.255.0
Lab 8.5.2: Troubleshooting Enterprise Networks 2 Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway Fa0/0 192.168.10.1 255.255.255.0 N/A R1 Fa0/1 192.168.11.1 255.255.255.0
Lab 7 Configuring Basic Router Settings with IOS CLI
 Lab 7 Configuring Basic Router Settings with IOS CLI Objectives Part 1: Set Up the Topology and Initialize Devices Cable equipment to match the network topology. Initialize and restart the router and switch.
Lab 7 Configuring Basic Router Settings with IOS CLI Objectives Part 1: Set Up the Topology and Initialize Devices Cable equipment to match the network topology. Initialize and restart the router and switch.
Lab Using the CLI to Gather Network Device Information Topology
 Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.1.1 255.255.255.0 N/A Lo0 209.165.200.225 255.255.255.224 N/A S1 VLAN 1 192.168.1.11 255.255.255.0
Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.1.1 255.255.255.0 N/A Lo0 209.165.200.225 255.255.255.224 N/A S1 VLAN 1 192.168.1.11 255.255.255.0
Table of Contents. Cisco IPSec Tunnel through a PIX Firewall (Version 7.0) with NAT Configuration Example
 Table of Contents IPSec Tunnel through a PIX Firewall (Version 7.0) with NAT Configuration Example...1 Document ID: 63881...1 Introduction...1 Prerequisites...2 Requirements...2 Components Used...2 Conventions...2
Table of Contents IPSec Tunnel through a PIX Firewall (Version 7.0) with NAT Configuration Example...1 Document ID: 63881...1 Introduction...1 Prerequisites...2 Requirements...2 Components Used...2 Conventions...2
LAN to LAN IPsec Tunnel Between a Cisco VPN 3000 Concentrator and Router with AES Configuration Example
 LAN to LAN IPsec Tunnel Between a Cisco VPN 3000 Concentrator and Router with AES Configuration Example Document ID: 26402 Contents Introduction Prerequisites Requirements Components Used Conventions Configure
LAN to LAN IPsec Tunnel Between a Cisco VPN 3000 Concentrator and Router with AES Configuration Example Document ID: 26402 Contents Introduction Prerequisites Requirements Components Used Conventions Configure
Lab Configuring IPv4 Static and Default Routes (Solution)
 (Solution) Topology Addressing Table Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.0.1 255.255.255.0 N/A S0/0/1 10.1.1.1 255.255.255.252 N/A R3 G0/1 192.168.1.1 255.255.255.0
(Solution) Topology Addressing Table Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.0.1 255.255.255.0 N/A S0/0/1 10.1.1.1 255.255.255.252 N/A R3 G0/1 192.168.1.1 255.255.255.0
Lab Configuring Switch Security Features (Solution) Topology
 (Solution) Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 172.16.99.1 255.255.255.0 N/A S1 VLAN 99 172.16.99.11 255.255.255.0 172.16.99.1 PC-A NIC
(Solution) Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 172.16.99.1 255.255.255.0 N/A S1 VLAN 99 172.16.99.11 255.255.255.0 172.16.99.1 PC-A NIC
Lab - Configuring a Switch Management Address
 Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway S1 VLAN 1 192.168.1.2 255.255.255.0 N/A PC-A NIC 192.168.1.10 255.255.255.0 N/A Part 1: Configure a Basic Network
Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway S1 VLAN 1 192.168.1.2 255.255.255.0 N/A PC-A NIC 192.168.1.10 255.255.255.0 N/A Part 1: Configure a Basic Network
co Configuring PIX to Router Dynamic to Static IPSec with
 co Configuring PIX to Router Dynamic to Static IPSec with Table of Contents Configuring PIX to Router Dynamic to Static IPSec with NAT...1 Introduction...1 Configure...1 Components Used...1 Network Diagram...1
co Configuring PIX to Router Dynamic to Static IPSec with Table of Contents Configuring PIX to Router Dynamic to Static IPSec with NAT...1 Introduction...1 Configure...1 Components Used...1 Network Diagram...1
L2TP IPsec Support for NAT and PAT Windows Clients
 L2TP IPsec Support for NAT and PAT Windows Clients The L2TP IPsec Support for NAT and PAT Windows Clients feature allows mulitple Windows client to connect to an IPsec-enabled Cisco IOS Layer 2 Tunneling
L2TP IPsec Support for NAT and PAT Windows Clients The L2TP IPsec Support for NAT and PAT Windows Clients feature allows mulitple Windows client to connect to an IPsec-enabled Cisco IOS Layer 2 Tunneling
Lab Configuring IPv6 Static and Default Routes (Solution)
 (Solution) Topology Addressing Table Device Interface IPv6 Address / Prefix Length Default Gateway R1 G0/1 2001:DB8:ACAD:A::/64 eui-64 N/A S0/0/1 FC00::1/64 N/A R3 G0/1 2001:DB8:ACAD:B::/64 eui-64 N/A
(Solution) Topology Addressing Table Device Interface IPv6 Address / Prefix Length Default Gateway R1 G0/1 2001:DB8:ACAD:A::/64 eui-64 N/A S0/0/1 FC00::1/64 N/A R3 G0/1 2001:DB8:ACAD:B::/64 eui-64 N/A
CISCO EXAM QUESTIONS & ANSWERS
 CISCO 100-101 EXAM QUESTIONS & ANSWERS Number: 100-101 Passing Score: 800 Time Limit: 120 min File Version: 35.5 http://www.gratisexam.com/ CISCO 100-101 EXAM QUESTIONS & ANSWERS Exam Name: CCNA Interconnecting
CISCO 100-101 EXAM QUESTIONS & ANSWERS Number: 100-101 Passing Score: 800 Time Limit: 120 min File Version: 35.5 http://www.gratisexam.com/ CISCO 100-101 EXAM QUESTIONS & ANSWERS Exam Name: CCNA Interconnecting
Three interface Router without NAT Cisco IOS Firewall Configuration
 Three interface Router without NAT Cisco IOS Firewall Configuration Document ID: 13893 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations
Three interface Router without NAT Cisco IOS Firewall Configuration Document ID: 13893 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations
Chapter 10 - Configure ASA Basic Settings and Firewall using ASDM
 Chapter 10 - Configure ASA Basic Settings and Firewall using ASDM This lab has been updated for use on NETLAB+ Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces.
Chapter 10 - Configure ASA Basic Settings and Firewall using ASDM This lab has been updated for use on NETLAB+ Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces.
Secure ACS Database Replication Configuration Example
 Secure ACS Database Replication Configuration Example Document ID: 71320 Introduction Prerequisites Requirements Components Used Related Products Conventions Background Information Scenario I Scenario
Secure ACS Database Replication Configuration Example Document ID: 71320 Introduction Prerequisites Requirements Components Used Related Products Conventions Background Information Scenario I Scenario
Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM
 Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM This lab has been updated for use on NETLAB+ Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet Interfaces.
Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM This lab has been updated for use on NETLAB+ Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet Interfaces.
Chapter 10 Configure AnyConnect Remote Access SSL VPN Using ASDM
 Chapter 10 Configure AnyConnect Remote Access SSL VPN Using ASDM Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces. 2015 Cisco and/or its affiliates. All rights
Chapter 10 Configure AnyConnect Remote Access SSL VPN Using ASDM Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces. 2015 Cisco and/or its affiliates. All rights
exam. Number: Passing Score: 800 Time Limit: 120 min CISCO Interconnecting Cisco Networking Devices Part 1 (ICND)
 100-105.exam Number: 100-105 Passing Score: 800 Time Limit: 120 min CISCO 100-105 Interconnecting Cisco Networking Devices Part 1 (ICND) Exam A QUESTION 1 Which route source code represents the routing
100-105.exam Number: 100-105 Passing Score: 800 Time Limit: 120 min CISCO 100-105 Interconnecting Cisco Networking Devices Part 1 (ICND) Exam A QUESTION 1 Which route source code represents the routing
Lab Managing Router Configuration Files with Terminal Emulation Software
 Lab Managing Router Configuration Files with Terminal Emulation Software Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.1.1 255.255.255.0 N/A
Lab Managing Router Configuration Files with Terminal Emulation Software Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.1.1 255.255.255.0 N/A
PIX/ASA 7.x and Later : Easy VPN with Split Tunneling ASA 5500 as the Server and Cisco 871 as the Easy VPN Remote Configuration Example
 PIX/ASA 7.x and Later : Easy VPN with Split Tunneling ASA 5500 as the Server and Cisco 871 as the Easy VPN Remote Configuration Example Document ID: 68815 Contents Introduction Prerequisites Requirements
PIX/ASA 7.x and Later : Easy VPN with Split Tunneling ASA 5500 as the Server and Cisco 871 as the Easy VPN Remote Configuration Example Document ID: 68815 Contents Introduction Prerequisites Requirements
How to configure MB5000 Serial Port Bridge mode
 How to configure MB5000 Serial Port Bridge mode MB5000 has a configurable serial port. With this serial port, MB5000 can be used as DCE device to be connected with Cisco router s console port so that MB5000
How to configure MB5000 Serial Port Bridge mode MB5000 has a configurable serial port. With this serial port, MB5000 can be used as DCE device to be connected with Cisco router s console port so that MB5000
Security Hardening Checklist for Cisco Routers/Switches in 10 Steps
 Security Hardening Checklist for Cisco Routers/Switches in 10 Steps Network infrastructure devices (routers, switches, load balancers, firewalls etc) are among the assets of an enterprise that play an
Security Hardening Checklist for Cisco Routers/Switches in 10 Steps Network infrastructure devices (routers, switches, load balancers, firewalls etc) are among the assets of an enterprise that play an
Configuring Dynamic Multipoint VPN Using GRE Over IPsec With OSPF, NAT, and Cisco IOS Firewall
 Configuring Dynamic Multipoint VPN Using GRE Over IPsec With OSPF, NAT, and Cisco IOS Firewall Document ID: 43068 Contents Introduction Prerequisites Requirements Components Used Conventions Configure
Configuring Dynamic Multipoint VPN Using GRE Over IPsec With OSPF, NAT, and Cisco IOS Firewall Document ID: 43068 Contents Introduction Prerequisites Requirements Components Used Conventions Configure
Lab - Configuring Basic DHCPv4 on a Router (Solution)
 (Solution) Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/0 192.168.0.1 255.255.255.0 N/A G0/1 192.168.1.1 255.255.255.0 N/A S0/0/0 (DCE) 192.168.2.253
(Solution) Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/0 192.168.0.1 255.255.255.0 N/A G0/1 192.168.1.1 255.255.255.0 N/A S0/0/0 (DCE) 192.168.2.253
Interconnecting Cisco Networking Devices Part 1 ICND1
 Interconnecting Cisco Networking Devices Part 1 ICND1 Course Length: 5 days Course Delivery: Traditional Classroom Online Live Course Overview Interconnecting Cisco Networking Devices, Part 1 (ICND1) v3.0
Interconnecting Cisco Networking Devices Part 1 ICND1 Course Length: 5 days Course Delivery: Traditional Classroom Online Live Course Overview Interconnecting Cisco Networking Devices, Part 1 (ICND1) v3.0
NAT Support for Multiple Pools Using Route Maps
 NAT Support for Multiple Pools Using Route Maps Document ID: 13739 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Access List Approach Host 1 to Host
NAT Support for Multiple Pools Using Route Maps Document ID: 13739 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Access List Approach Host 1 to Host
AutoSecure. Finding Feature Information. Last Updated: January 18, 2012
 AutoSecure Last Updated: January 18, 2012 The AutoSecure feature secures a router by using a single CLI command to disable common IP services that can be exploited for network attacks, enable IP services
AutoSecure Last Updated: January 18, 2012 The AutoSecure feature secures a router by using a single CLI command to disable common IP services that can be exploited for network attacks, enable IP services
Lab Configuring Per-Interface Inter-VLAN Routing (Instructor Version)
 (Instructor Version) Instructor Note: Red font color or Gray highlights indicate text that appears in the instructor copy only. Topology Addressing Table Objectives Device Interface IP Address Subnet Mask
(Instructor Version) Instructor Note: Red font color or Gray highlights indicate text that appears in the instructor copy only. Topology Addressing Table Objectives Device Interface IP Address Subnet Mask
Lab Configuring 802.1Q Trunk-Based Inter-VLAN Routing (Instructor Version Optional Lab)
 (Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
(Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
Note that you can also use the password command but the secret command gives you a better encryption algorithm.
 Router Device Security Lab Configuring Secure Passwords 1. Configure the enable secret and password enable password TRUSTME enable secret letmein Look at the configuration: show config terminal Note the
Router Device Security Lab Configuring Secure Passwords 1. Configure the enable secret and password enable password TRUSTME enable secret letmein Look at the configuration: show config terminal Note the
cable modem dhcp proxy nat on Cisco Cable Modems
 cable modem dhcp proxy nat on Cisco Cable Modems Document ID: 12176 Contents Introduction Prerequisites Requirements Components Used Conventions Dynamic NAT Versus Static NAT Configuration Using cable
cable modem dhcp proxy nat on Cisco Cable Modems Document ID: 12176 Contents Introduction Prerequisites Requirements Components Used Conventions Dynamic NAT Versus Static NAT Configuration Using cable
Basic Router Configuration
 This section includes information about some basic router configuration, and contains the following sections: Default Configuration, on page 1 Configuring Global Parameters, on page 2 Configuring Gigabit
This section includes information about some basic router configuration, and contains the following sections: Default Configuration, on page 1 Configuring Global Parameters, on page 2 Configuring Gigabit
Device Interface IP Address Subnet Mask Default Gateway
 Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway BRANCH HQ ISP Fa0/0 172.20.1.129 255.255.255.128 N/A S0/0/0 172.20.1.1 255.255.255.128 N/A Fa0/0 172.20.0.129 255.255.255.128
Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway BRANCH HQ ISP Fa0/0 172.20.1.129 255.255.255.128 N/A S0/0/0 172.20.1.1 255.255.255.128 N/A Fa0/0 172.20.0.129 255.255.255.128
Lab Guide 1 - Basic Configuration and Interface Configuration
 IXP Workshop Lab Lab Guide 1 - Basic Configuration and Interface Configuration Objective: All the workshop lab routers are set to the default configuration and cabling requirements are prebuild according
IXP Workshop Lab Lab Guide 1 - Basic Configuration and Interface Configuration Objective: All the workshop lab routers are set to the default configuration and cabling requirements are prebuild according
IPsec Anti-Replay Window Expanding and Disabling
 IPsec Anti-Replay Window Expanding and Disabling Cisco IP security (IPsec) authentication provides anti-replay protection against an attacker duplicating encrypted packets by assigning a unique sequence
IPsec Anti-Replay Window Expanding and Disabling Cisco IP security (IPsec) authentication provides anti-replay protection against an attacker duplicating encrypted packets by assigning a unique sequence
Lab Configuring Per-Interface Inter-VLAN Routing (Solution)
 (Solution) Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/0 192.168.20.1 255.255.255.0 N/A G0/1 192.168.10.1 255.255.255.0 N/A S1 VLAN 10 192.168.10.11
(Solution) Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/0 192.168.20.1 255.255.255.0 N/A G0/1 192.168.10.1 255.255.255.0 N/A S1 VLAN 10 192.168.10.11
Configure the ASA for Dual Internal Networks
 Configure the ASA for Dual Internal Networks Document ID: 119195 Contributed by Dinkar Sharma, Bratin Saha, and Prashant Joshi, Cisco TAC Engineers. Aug 05, 2015 Contents Introduction Prerequisites Requirements
Configure the ASA for Dual Internal Networks Document ID: 119195 Contributed by Dinkar Sharma, Bratin Saha, and Prashant Joshi, Cisco TAC Engineers. Aug 05, 2015 Contents Introduction Prerequisites Requirements
Cisco DSL Router Configuration and Troubleshooting Guide Cisco DSL Router Acting as a PPPoE Client with a Dynamic IP Address
 Cisco DSL Router Configuration and Troubleshooting Guide Cisco DSL Router Acting as a PPPoE Client with a Dynamic IP Address Document ID: 71118 Contents Introduction Prerequisites Requirements Components
Cisco DSL Router Configuration and Troubleshooting Guide Cisco DSL Router Acting as a PPPoE Client with a Dynamic IP Address Document ID: 71118 Contents Introduction Prerequisites Requirements Components
Lab Configuring Basic Switch Settings (Solution)
 (Solution) Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway S1 VLAN 99 192.168.1.2 255.255.255.0 192.168.1.1 PC-A NIC 192.168.1.10 255.255.255.0 192.168.1.1
(Solution) Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway S1 VLAN 99 192.168.1.2 255.255.255.0 192.168.1.1 PC-A NIC 192.168.1.10 255.255.255.0 192.168.1.1
Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM
 Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet Interfaces. 2016 Cisco and/or its affiliates. All
Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet Interfaces. 2016 Cisco and/or its affiliates. All
Cisco ASA 5500 LAB Guide
 INGRAM MICRO Cisco ASA 5500 LAB Guide Ingram Micro 4/1/2009 The following LAB Guide will provide you with the basic steps involved in performing some fundamental configurations on a Cisco ASA 5500 series
INGRAM MICRO Cisco ASA 5500 LAB Guide Ingram Micro 4/1/2009 The following LAB Guide will provide you with the basic steps involved in performing some fundamental configurations on a Cisco ASA 5500 series
Cisco Branch Routers Series Network Analysis Module (NME-NAM-120S) Installation and Configuration Note, 4.2
 Cisco Branch Routers Series Network Analysis Module (NME-NAM-120S) Installation and Configuration Note, 4.2 The Cisco Network Analysis Module (NAM) is an integrated module that enables network managers
Cisco Branch Routers Series Network Analysis Module (NME-NAM-120S) Installation and Configuration Note, 4.2 The Cisco Network Analysis Module (NAM) is an integrated module that enables network managers
RSA SecurID Authentication for AnyConnect Clients on a Cisco IOS Headend Configuration Example
 RSA SecurID Authentication for AnyConnect Clients on a Cisco IOS Headend Configuration Example Document ID: 118778 Contributed by Atri Basu, Cisco TAC Engineer, and Vasavi Yellampalli, Cisco Engineering.
RSA SecurID Authentication for AnyConnect Clients on a Cisco IOS Headend Configuration Example Document ID: 118778 Contributed by Atri Basu, Cisco TAC Engineer, and Vasavi Yellampalli, Cisco Engineering.
Lab 5.6.2: Challenge RIP Configuration
 Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway BRANCH HQ ISP PC1 PC2 PC3 Fa0/0 S0/0/0 Fa0/0 S0/0/0 S0/0/1 Fa0/0 S0/0/1 NIC NIC NIC Learning Objectives Upon completion
Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway BRANCH HQ ISP PC1 PC2 PC3 Fa0/0 S0/0/0 Fa0/0 S0/0/0 S0/0/1 Fa0/0 S0/0/1 NIC NIC NIC Learning Objectives Upon completion
This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document for non-commercial distribution and
 This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document for non-commercial distribution and exclusive use by instructors in the CCNA Exploration:
This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document for non-commercial distribution and exclusive use by instructors in the CCNA Exploration:
Configuring NAT for IP Address Conservation
 This module describes how to configure Network Address Translation (NAT) for IP address conservation and how to configure the inside and outside source addresses. This module also provides information
This module describes how to configure Network Address Translation (NAT) for IP address conservation and how to configure the inside and outside source addresses. This module also provides information
IPsec Anti-Replay Window: Expanding and Disabling
 IPsec Anti-Replay Window: Expanding and Disabling First Published: February 28, 2005 Last Updated: March 24, 2011 Cisco IP security (IPsec) authentication provides anti-replay protection against an attacker
IPsec Anti-Replay Window: Expanding and Disabling First Published: February 28, 2005 Last Updated: March 24, 2011 Cisco IP security (IPsec) authentication provides anti-replay protection against an attacker
Lab - Examining Telnet and SSH in Wireshark
 Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.1.1 255.255.255.0 N/A PC-A NIC 192.168.1.3 255.255.255.0 192.168.1.1 Part 1: Configure the Devices
Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.1.1 255.255.255.0 N/A PC-A NIC 192.168.1.3 255.255.255.0 192.168.1.1 Part 1: Configure the Devices
1. Which OSI layers offers reliable, connection-oriented data communication services?
 CCNA 1 Practice Final Exam Answers v4.0 100% 1. Which OSI layers offers reliable, connection-oriented data communication services? application presentation session transport network 2. Refer to the exhibit.
CCNA 1 Practice Final Exam Answers v4.0 100% 1. Which OSI layers offers reliable, connection-oriented data communication services? application presentation session transport network 2. Refer to the exhibit.
Configuring Cisco Prime NAM
 Cisco SRE NAM has an internal Gigabit Ethernet interface and an external interface. You can use either interface for Prime NAM management traffic such as the NAM web GUI, telnet or ssh, but not both. You
Cisco SRE NAM has an internal Gigabit Ethernet interface and an external interface. You can use either interface for Prime NAM management traffic such as the NAM web GUI, telnet or ssh, but not both. You
Configuring a Terminal/Comm Server
 Configuring a Terminal/Comm Server Document ID: 5466 Introduction Prerequisites Requirements Components Used Conventions Cabling Design Strategy Configure Network Diagram Configurations Command Summary
Configuring a Terminal/Comm Server Document ID: 5466 Introduction Prerequisites Requirements Components Used Conventions Cabling Design Strategy Configure Network Diagram Configurations Command Summary
Configuring Secure Shell
 Configuring Secure Shell Last Updated: October 24, 2011 The Secure Shell (SSH) feature is an application and a protocol that provides a secure replacement to the Berkeley r-tools. The protocol secures
Configuring Secure Shell Last Updated: October 24, 2011 The Secure Shell (SSH) feature is an application and a protocol that provides a secure replacement to the Berkeley r-tools. The protocol secures
Sample Business Ready Branch Configuration Listings
 APPENDIX A Sample Business Ready Branch Configuration Listings The following is a sample configuration of a Business Ready Branch. There are many permutations of feature combinations when setting up the
APPENDIX A Sample Business Ready Branch Configuration Listings The following is a sample configuration of a Business Ready Branch. There are many permutations of feature combinations when setting up the
Multicast Music-on-Hold Support on Cisco UBE
 First Published: July 22, 2011 Last Updated: July 22, 2011 The Multicast Music-on-Hold (MMOH) feature enables you to subscribe to a music streaming service when you are using a Cisco Unified Border Element.
First Published: July 22, 2011 Last Updated: July 22, 2011 The Multicast Music-on-Hold (MMOH) feature enables you to subscribe to a music streaming service when you are using a Cisco Unified Border Element.
Loading Internet Protocol Security (IPSec) (CDR-882/780/790/990 Cellular Router)
 Loading Internet Protocol Security (IPSec) (CDR-882/780/790/990 Cellular Router) Call Direct Document version 1.4 Last updated 17 December, 2010 support@call-direct.com.au Loading IPSec To support IPSec
Loading Internet Protocol Security (IPSec) (CDR-882/780/790/990 Cellular Router) Call Direct Document version 1.4 Last updated 17 December, 2010 support@call-direct.com.au Loading IPSec To support IPSec
Lab Establishing and Verifying a Telnet Connection Instructor Version 2500
 Lab 4.2.2 Establishing and Verifying a Telnet Connection Instructor Version 2500 Objective Establish a Telnet connection to a remote router. Verify that the application layer between source and destination
Lab 4.2.2 Establishing and Verifying a Telnet Connection Instructor Version 2500 Objective Establish a Telnet connection to a remote router. Verify that the application layer between source and destination
MWA Deployment Guide. VPN Termination from Smartphone to Cisco ISR G2 Router
 MWA Deployment Guide Mobile Workforce Architecture: VPN Deployment Guide for Microsoft Windows Mobile and Android Devices with Cisco Integrated Services Router Generation 2 This deployment guide explains
MWA Deployment Guide Mobile Workforce Architecture: VPN Deployment Guide for Microsoft Windows Mobile and Android Devices with Cisco Integrated Services Router Generation 2 This deployment guide explains
Cisco Virtual Office: Easy VPN Deployment Guide
 Cisco Virtual Office: Easy VPN Deployment Guide This guide provides detailed design and implementation information for deployment of Easy VPN in client mode with the Cisco Virtual Office. Please refer
Cisco Virtual Office: Easy VPN Deployment Guide This guide provides detailed design and implementation information for deployment of Easy VPN in client mode with the Cisco Virtual Office. Please refer
Using Cloud VPN Service
 To begin, log in to the VMS Service Interface using your consumer credentials. In case of association with several tenants, choose a customer name from the drop-down on the left pane of the Welcome page.
To begin, log in to the VMS Service Interface using your consumer credentials. In case of association with several tenants, choose a customer name from the drop-down on the left pane of the Welcome page.
WCCPv2 and WCCP Enhancements
 WCCPv2 and WCCP Enhancements Release 12.0(11)S June 20, 2000 This feature module describes the Web Cache Communication Protocol (WCCP) Enhancements feature and includes information on the benefits of the
WCCPv2 and WCCP Enhancements Release 12.0(11)S June 20, 2000 This feature module describes the Web Cache Communication Protocol (WCCP) Enhancements feature and includes information on the benefits of the
Chapter 8: Lab B: Configuring a Remote Access VPN Server and Client
 Chapter 8: Lab B: Configuring a Remote Access VPN Server and Client Topology IP Addressing Table Device Interface IP Address Subnet Mask Default Gateway Switch Port R1 FA0/1 192.168.1.1 255.255.255.0 N/A
Chapter 8: Lab B: Configuring a Remote Access VPN Server and Client Topology IP Addressing Table Device Interface IP Address Subnet Mask Default Gateway Switch Port R1 FA0/1 192.168.1.1 255.255.255.0 N/A
Interconnecting Cisco Networking Devices Part 1 (ICND1) Course Overview
 Interconnecting Cisco Networking Devices Part 1 (ICND1) Course Overview This course will teach students about building a simple network, establishing internet connectivity, managing network device security,
Interconnecting Cisco Networking Devices Part 1 (ICND1) Course Overview This course will teach students about building a simple network, establishing internet connectivity, managing network device security,
Lab Correcting RIPv2 Routing Problems
 Lab 9.4.2 Correcting RIPv2 Routing Problems e Interface IP Address Subnet Mask Default Gateway Device Host Name Interface IP Address Subnet Mask Default Gateway R1 BRANCH1 Fast Ethernet 0/0 172.16.0.1
Lab 9.4.2 Correcting RIPv2 Routing Problems e Interface IP Address Subnet Mask Default Gateway Device Host Name Interface IP Address Subnet Mask Default Gateway R1 BRANCH1 Fast Ethernet 0/0 172.16.0.1
RR> RR> RR>en RR# RR# RR# RR# *Oct 2 04:57:03.684: %AMDP2_FE-6-EXCESSCOLL: Ethernet0/2 TDR=0, TRC=0 RR#
 RR> RR> RR>en *Oct 2 04:57:03.684: %AMDP2_FE-6-EXCESSCOLL: Ethernet0/2 TDR=0, TRC=0 term len 0 show run Building configuration... Current configuration : 2568 bytes version 15.4 service timestamps debug
RR> RR> RR>en *Oct 2 04:57:03.684: %AMDP2_FE-6-EXCESSCOLL: Ethernet0/2 TDR=0, TRC=0 term len 0 show run Building configuration... Current configuration : 2568 bytes version 15.4 service timestamps debug
Design and Implementation Plan for Network Based on the ALOHA Point of Sale System. Proposed by Jedadiah Casey. Introduction
 Design and Implementation Plan for Network Based on the ALOHA Point of Sale System Proposed by Jedadiah Casey Introduction The goal of this design document is to provide a framework of suggested implementation
Design and Implementation Plan for Network Based on the ALOHA Point of Sale System Proposed by Jedadiah Casey Introduction The goal of this design document is to provide a framework of suggested implementation
Support for policy-based routing applies to the Barracuda Web Security Gateway running version 6.x only.
 Support for policy-based routing applies to the Barracuda Web Security Gateway running version 6.x only. Transparently Routing Web Traffic to the Barracuda Web Security Gateway This article demonstrates
Support for policy-based routing applies to the Barracuda Web Security Gateway running version 6.x only. Transparently Routing Web Traffic to the Barracuda Web Security Gateway This article demonstrates
CCNP TSHOOT. Quick Reference Sheet Exam
 CCNP TSHOOT Quick Reference Sheet Exam 300-135 Chapter 1. Network Principles Troubleshooting Steps Problem Identification Collection of Information Examination and Action Plan Verification Basic Troubleshooting
CCNP TSHOOT Quick Reference Sheet Exam 300-135 Chapter 1. Network Principles Troubleshooting Steps Problem Identification Collection of Information Examination and Action Plan Verification Basic Troubleshooting
Configuring Redundant Routing on the VPN 3000 Concentrator
 Configuring Redundant Routing on the VPN 3000 Concentrator Document ID: 13354 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Router Configurations
Configuring Redundant Routing on the VPN 3000 Concentrator Document ID: 13354 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Router Configurations
ICND1 v2.0 Interconnecting Cisco Networking Devices Part 1 CCENT & Part of CCNA Rout/Switch
 ICND1 v2.0 Interconnecting Cisco Networking Devices Part 1 CCENT & Part of CCNA Rout/Switch Course Length: 5 days Course Delivery: Traditional Classroom Online Live Course Overview Interconnecting Cisco
ICND1 v2.0 Interconnecting Cisco Networking Devices Part 1 CCENT & Part of CCNA Rout/Switch Course Length: 5 days Course Delivery: Traditional Classroom Online Live Course Overview Interconnecting Cisco
Configuring the Cisco NAM 2220 Appliance
 CHAPTER 5 This section describes how to configure the Cisco NAM 2220 appliance to establish network connectivity, configure IP parameters, and how to perform other required administrative tasks using the
CHAPTER 5 This section describes how to configure the Cisco NAM 2220 appliance to establish network connectivity, configure IP parameters, and how to perform other required administrative tasks using the
Lab - Troubleshooting Standard IPv4 ACL Configuration and Placement Topology
 Lab - Troubleshooting Standard IPv4 ACL Configuration and Placement Topology 2016 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives
Lab - Troubleshooting Standard IPv4 ACL Configuration and Placement Topology 2016 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives
Lab Student Lab Orientation
 Lab 1.1.1 Student Lab Orientation Objective In this lab, the students will complete the following tasks: Review the lab bundle equipment Understand the security pod topology Understand the pod naming and
Lab 1.1.1 Student Lab Orientation Objective In this lab, the students will complete the following tasks: Review the lab bundle equipment Understand the security pod topology Understand the pod naming and
F5 WANJet 200. Quick Start Guide. Quick Start Overview
 F5 WANJet 200 Quick Start Guide Quick Start Overview Following is a high level overview of the steps required to successfully install and configure your F5 WANJet 200 appliance. For detailed instructions
F5 WANJet 200 Quick Start Guide Quick Start Overview Following is a high level overview of the steps required to successfully install and configure your F5 WANJet 200 appliance. For detailed instructions
Cisco IOS Firewall Authentication Proxy
 Cisco IOS Firewall Authentication Proxy This feature module describes the Cisco IOS Firewall Authentication Proxy feature. It includes information on the benefits of the feature, supported platforms, configuration
Cisco IOS Firewall Authentication Proxy This feature module describes the Cisco IOS Firewall Authentication Proxy feature. It includes information on the benefits of the feature, supported platforms, configuration
Quick Note. Configure an IPSec VPN tunnel in Aggressive mode between a TransPort LR router and a Cisco router. Digi Technical Support 7 October 2016
 Quick Note Configure an IPSec VPN tunnel in Aggressive mode between a TransPort LR router and a Cisco router. Digi Technical Support 7 October 2016 Contents 1 Introduction... 3 1.1 Outline... 3 1.2 Assumptions...
Quick Note Configure an IPSec VPN tunnel in Aggressive mode between a TransPort LR router and a Cisco router. Digi Technical Support 7 October 2016 Contents 1 Introduction... 3 1.1 Outline... 3 1.2 Assumptions...
Configuring IOS to IOS IPSec Using AES Encryption
 Configuring IOS to IOS IPSec Using AES Encryption Document ID: 43069 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Configurations Verify Troubleshoot Troubleshooting
Configuring IOS to IOS IPSec Using AES Encryption Document ID: 43069 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Configurations Verify Troubleshoot Troubleshooting
