This document describes how to perform datapath packet tracing for Cisco IOS -XE software via the Packet Trace feature.
|
|
|
- Dwayne Wells
- 6 years ago
- Views:
Transcription
1 Contents Introduction Prerequisites Requirements Components Used Reference Topology Packet Tracing in Use Quick Start Guide Enable Platform Conditional Debugs Enable Packet Trace Egress Condition Limitation with Packet Traces Display the Packet Trace Results FIA Trace Display the Packet Trace Results Check the FIA Associated with an Interface Dump the Traced Packets Drop Trace Example Drop Trace Scenario Inject and Punt Traces Packet Trace Examples Packet Trace Example - NAT Packet Trace Example - VPN Performance Impact Related Information Introduction This document describes how to perform datapath packet tracing for Cisco IOS -XE software via the Packet Trace feature. In order to identify issues such as misconfiguration, capacity overload, or even the ordinary software bug while troubleshooting, it is necessary to understand what happens to a packet within a system. The Cisco IOS-XE Packet Trace feature addresses this need. It provides a field-safe method that is used for accounting and in order to capture per-packet processing details based on a class of user-defined conditions. Prerequisites Requirements Cisco recommends that you have knowledge of the packet trace feature that is available in Cisco IOS-XE Versions 3.10 and later, as well as in all platforms that run the Cisco IOS-XE software, such as the Cisco 1000 Series Aggregation Services Routers (ASR1K), the Cisco 1000V Series Cloud Services Router (CSR1000v), and the Cisco 4451-X Series Integrated Services Router
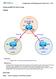
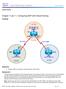
2 (ISR4451-X). Components Used The information in this document is based on these software and hardware versions: Cisco IOS-XE software Versions 3.10S (15.3(3)S) and later ASR1K The information in this document was created from devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure you understand the potential impact of any command used. Reference Topology This diagram illustrates the topology that is used for the examples that are described in this document: Packet Tracing in Use In order to illustrate the use of the packet trace feature, the example that is used throughout this section describes a trace of the Internet Control Message Protocol (ICMP) traffic from the local workstation (behind the ASR1K) to the remote host (the ingress direction for the ASR1K at the Gig0/0/1 interface). You can trace packets on the ASR1K with these two steps: 1. Enable the platform conditional debugs in order to select the packets or traffic that you want to trace on the ASR1K. 2. Enable the platform packet trace (path-trace or Feature Invocation Array (FIA) trace). Quick Start Guide Here is a quick start guide if you are already familiar with the contents of this document, and want a section for a quick look at the CLI. These are only a few examples to illustrate the use of the tool, refer the later sections that discuss the syntaxes in detail, and ensure you use the configuration that is appropriate to your requirement. 1. Configure platform conditions: debug platform condition ipv /32 both --> matches in and out packets with source or destination as /32
3 2. debug platform condition ipv4 access-list 198 egress --> (Ensure access-list 198 is defined prior to configuring this command) - matches egress packets corresponding to access-list 198 debug platform condition interface gig 0/0/0 ingress --> matches all ingress packets on interface gig 0/0/0 debug platform condition mpls 10 1 ingress --> matches MPLS packets with top ingress label 10 debug platform condition ingress --> matches all ingress packets on all interfaces (use cautiously)after a platform condition is configured, start platform conditions with this CLI command: debug platform condition start Configure packet trace: debug platform packet-trace packet > basic path-trace, and automatically stops tracing packets after 1024 packets. You can use "circular" option if needed debug platform packet-trace packet 1024 fia-trace -> enables detailed fia trace, stops tracing packets after 1024 packets debug platform packet-trace drop [code <dropcode>] -> if you want to trace/capture only packets that are dropped. Refer to Drop Trace section for more details. 3. Next, enable the platform packet trace: debug platform packet-trace enable Here are the commands to clear the buffer and reset the packet trace: no debug platform packet-trace enable --> disable the packet trace, this needs to be done before you clear the buffer clear platform packet-trace statistics --> clear the packet trace buffer debug platform packet-trace enable --> reenable the packet trace The command to clear both platform conditions and the packet trace configuration is: clear platform condition all --> clears both platform conditions and the packet trace configuration Show Commands Verify the platform condition and packet trace configuration after you apply the previous commands in order to ensure you have what you need. show platform conditions --> shows the platform conditions configured show platform packet-trace configuration --> shows the packet-trace configurations show debugging --> this will show both platform conditions and platform packet-trace configured Here are the commands to check the traced/captured packets: show platform packet-trace statistics --> statistics of packets traced show platform packet-trace summary --> summary of all the packets traced, with input and output interfaces, processing result and reason. show platform packet-trace packet 12 -> Tracing the 12th packet, with complete path trace or FIA trace details. Enable Platform Conditional Debugs The Packet Trace feature relies on the conditional debug infrastructure in order to determine the
4 packets to be traced. The conditional debug infrastructure provides the ability to filter traffic based on: Protocol IP address and mask Access Control List (ACL) Interface Traffic direction (ingress or egress) These conditions define where and when the filters are applied to a packet. For the traffic that is used in this example, enable platform conditional debugs in the ingress direction for ICMP packets from to In other words, select the traffic that you want to trace. There are various options that you can use in order to select this traffic. debug platform condition? egress Egress only debug feature For a specific feature ingress Ingress only debug interface Set interface for conditional debug ipv4 Debug IPv4 conditions ipv6 Debug IPv6 conditions start Start conditional debug stop Stop conditional debug In this example, an access-list is used in order to define the condition, as shown here: show access-list 150 Extended IP access list permit icmp host host debug platform condition interface gig 0/0/1 ipv4 access-list 150 ingress In order to begin conditional debugging, enter this command: debug platform condition start Note: In order to stop or disable the conditional debugging infrastructure, enter the debug platform condition stop command. In order to view the conditional debug filters that are configured, enter this command: show platform conditions Conditional Debug Global State: Start Conditions Direction GigabitEthernet0/0/1 & IPV4 ACL [150] ingress Feature Condition Format Value In summary, this configuration has been applied thus far: access-list 150 permit icmp host host debug platform condition interface gig 0/0/1 ipv4 access-list 150 ingress debug platform condition start Enable Packet Trace
5 Note: This section describes the packet and copy options in detail, and the other options are described later in the document. Packet traces are supported on both the physical and the logical interfaces, such as Tunnel or Virtual-access interfaces. Here is the packet trace CLI syntax: debug platform packet-trace? copy Copy packet data drop Trace drops only enable Enable packet trace inject Trace injects only packet Packet count punt Trace punts onlydebug platform packet-trace packet <pkt-size/pkt-num> [fia-trace summaryonly] [circular] [data-size <data-size>] Here are descriptions for the keywords of this command: pkt-num - The Packet Number specifies the maximum number of packets that are maintained at one time. summary-only - This specifies that only the summary data is captured. The default is to capture both summary data and feature-path data. fia-trace - This optionally performs an FIA trace in addition to the path data information. data-size - This allows you to specify the size of the path data buffer, from 2,048 to 16,384 bytes. The default is 2,048 bytes. debug platform packet-trace copy packet {in out both} [L2 L3 L4] [size <num-bytes>] Here are descriptions for the keywords of this command: in/out - This specifies the direction of the packet flow to be copied - ingress and/or egress. L2/L3/L4 - This allows you to specify the location that the copy of the packet starts. Layer 2 (L2) is the default location. size - This allows you to specify the maximum number of octets that are copied. The default is 64 octets. For this example, these are the commands used in order to enable packet trace for the traffic that is selected with the conditional debug infrastructure: debug platform packet-trace packet 16 debug platform packet-trace enable In order to review the packet trace configuration, enter this command: show platform packet-trace configuration debug platform packet-trace enable debug platform packet-trace packet 16 data-size 2048 You can also enter the show debugging command in order to view both the platform conditional
6 debugs and the packet trace configurations: show debugging IOSXE Conditional Debug Configs: Conditional Debug Global State: Start Conditions Direction GigabitEthernet0/0/1 & IPV4 ACL [150] ingress... IOSXE Packet Tracing Configs: Feature Condition Format Value Feature Type Submode Level IOSXE Packet Tracing Configs: debug platform packet-trace enable debug platform packet-trace packet 16 data-size 2048 Note: Enter the clear platform condition all command in order to clear all of the platform debug conditions and the packet trace configurations and data. In summary, this configuration data has been used thus far in order to enable the packet trace: debug platform packet-trace packet 16 debug platform packet-trace enable Egress Condition Limitation with Packet Traces The conditions define the conditional filters and when they are applied to a packet. For example, debug platform condition interface g0/0/0 egress means that a packet is identified as a match when it reaches the output FIA on interface g0/0/0, so any packet processing that takes place from ingress until that point is missed. Note: Cisco highly recommends that you use ingress conditions for packet traces in order to get the most complete and meaningful data possible. The egress conditions can be used, but be aware of the limitations. Display the Packet Trace Results Note: This section assumes that path-trace is enabled. Three specific levels of inspection are provided by the packet trace: Accounting Per-packet summary Per-packet path data When five ICMP request packets are sent from to , these commands can be used in order to view the packet trace results:
7 show platform packet-trace statistics Packets Traced: 5 Ingress 5 Inject 0 Forward 5 Punt 0 Drop 0 Consume 0 show platform packet-trace summary Pkt Input Output State Reason 0 Gi0/0/1 Gi0/0/0 FWD 1 Gi0/0/1 Gi0/0/0 FWD 2 Gi0/0/1 Gi0/0/0 FWD 3 Gi0/0/1 Gi0/0/0 FWD 4 Gi0/0/1 Gi0/0/0 FWD show platform packet-trace packet 0 Packet: 0 CBUG ID: 4 Input : GigabitEthernet0/0/1 Output : GigabitEthernet0/0/0 State : FWD Timestamp Start : ns (05/17/ :42: UTC) Stop : ns (05/17/ :42: UTC) Source : Destination : Note: The third command provides an example that illustrates how to view the packet trace for each packet. In this example, the first packet traced is shown. From these outputs, you can see that five packets are traced and that you can view the input interface, the output interface, the state, and the path trace. State Remark FWD The packet is scheduled/queued for delivery, to be forwarded to next hop via an egress interface. PUNT The packet is punted from the Forwarding Processor (FP) to the Route Processor (RP) (control pla The packet is dropped on the FP. Run FIA trace, use global drop counters, or use datapath debug DROP order to find more details for drop reasons. The packet is consumed during a packet process, such as during the ICMP ping request or the cry CONS packets. The ingress and inject counters in the packet trace statistics output correspond to the packets that enter via an external interface and packets that are seen as injected from the control plane, respectively. FIA Trace The FIA holds the list of features that are executed sequentially by the Packet Processor Engines (PPE) in the Quantum Flow Processor (QFP) when a packet is forwarded either ingress or egress. The features are based on the configuration data that is applied on the machine. Thus, a FIA trace
8 helps to understand the flow of the packet through the system as the packet is processed. You must apply this configuration data in order to enable packet trace with FIA: debug platform packet-trace packet 16 fia-trace Display the Packet Trace Results Note: This section assumes that FIA trace is enabled. Also, when you add or modify the current packet trace commands, the buffered packet trace details are cleared, so you must send some traffic again so that you can trace it. Send five ICMP packets from to after you enter the command that is used in order to enable the FIA trace, as described in the previous section. show platform packet-trace summary Pkt Input Output State Reason 0 Gi0/0/1 Gi0/0/0 FWD 1 Gi0/0/1 Gi0/0/0 FWD 2 Gi0/0/1 Gi0/0/0 FWD 3 Gi0/0/1 Gi0/0/0 FWD 4 Gi0/0/1 Gi0/0/0 FWD show platform packet-trace packet 0 Packet: 0 CBUG ID: 9 Input : GigabitEthernet0/0/1 Output : GigabitEthernet0/0/0 State : FWD Timestamp Start : ns (05/17/ :42: UTC) Stop : ns (05/17/ :42: UTC) Source : Destination : Entry : 0x8059dbe8 - DEBUG_COND_INPUT_PKT Timestamp : Entry : 0x82011a00 - IPV4_INPUT_DST_LOOKUP_CONSUME Timestamp : Entry : 0x IPV4_INPUT_FOR_US_MARTIAN Timestamp : Entry : 0x82004b68 - IPV4_OUTPUT_LOOKUP_PROCESS Timestamp : Entry : 0x8034f210 - IPV4_INPUT_IPOPTIONS_PROCESS Timestamp : Entry : 0x IPV4_OUTPUT_GOTO_OUTPUT_FEATURE Timestamp : Entry : 0x IPV4_VFR_REFRAG Timestamp : Entry : 0x IPV6_INPUT_L2_REWRITE
9 Timestamp : Entry : 0x IPV4_OUTPUT_FRAG Timestamp : Entry : 0x8200e500 - IPV4_OUTPUT_DROP_POLICY Timestamp : Entry : 0x8059aff4 - PACTRAC_OUTPUT_STATS Timestamp : Entry : 0x MARMOT_SPA_D_TRANSMIT_PKT Timestamp : Check the FIA Associated with an Interface When you enable the platform conditional debugs, it is added to the FIA as a feature. Depending upon the location that it is added to the list, you might need to adjust your platform conditions, such as when you trace pre-encap and post-encap packets. This output shows the order of the features in the FIA for the platform conditional debugging that is enabled in the ingress direction: show platform hardware qfp active interface if-name GigabitEthernet 0/0/1 General interface information Interface Name: GigabitEthernet0/0/1 Interface state: VALID Platform interface handle: 10 QFP interface handle: 8 Rx uidb: 1021 Tx uidb: Channel: 16 Interface Relationships BGPPA/QPPB interface configuration information Ingress: BGPPA/QPPB not configured. flags: 0000 Egress : BGPPA not configured. flags: 0000 ipv4_input enabled. ipv4_output enabled. layer2_input enabled. layer2_output enabled. ess_ac_input enabled. Features Bound to Interface: 2 GIC FIA state 48 PUNT INJECT DB 39 SPA/Marmot server 40 ethernet 1 IFM 31 icmp_svr 33 ipfrag_svr 34 ipreass_svr 36 ipvfr_svr 37 ipv6vfr_svr 12 CPP IPSEC Protocol 0 - ipv4_input FIA handle - CP:0x108d99cc DP:0x8070f400 IPV4_INPUT_DST_LOOKUP_ISSUE (M)
10 IPV4_INPUT_ARL_SANITY (M) CBUG_INPUT_FIA DEBUG_COND_INPUT_PKT IPV4_INPUT_DST_LOOKUP_CONSUME (M) IPV4_INPUT_FOR_US_MARTIAN (M) IPV4_INPUT_IPSEC_CLASSIFY IPV4_INPUT_IPSEC_COPROC_PROCESS IPV4_INPUT_IPSEC_RERUN_JUMP IPV4_INPUT_LOOKUP_PROCESS (M) IPV4_INPUT_IPOPTIONS_PROCESS (M) IPV4_INPUT_GOTO_OUTPUT_FEATURE (M) Protocol 1 - ipv4_output FIA handle - CP:0x108d9a34 DP:0x8070eb00 IPV4_OUTPUT_VFR MC_OUTPUT_GEN_RECYCLE (D) IPV4_VFR_REFRAG (M) IPV4_OUTPUT_IPSEC_CLASSIFY IPV4_OUTPUT_IPSEC_COPROC_PROCESS IPV4_OUTPUT_IPSEC_RERUN_JUMP IPV4_OUTPUT_L2_REWRITE (M) IPV4_OUTPUT_FRAG (M) IPV4_OUTPUT_DROP_POLICY (M) PACTRAC_OUTPUT_STATS MARMOT_SPA_D_TRANSMIT_PKT DEF_IF_DROP_FIA (M) Protocol 8 - layer2_input FIA handle - CP:0x108d9bd4 DP:0x8070c700 LAYER2_INPUT_SIA (M) CBUG_INPUT_FIA DEBUG_COND_INPUT_PKT LAYER2_INPUT_LOOKUP_PROCESS (M) LAYER2_INPUT_GOTO_OUTPUT_FEATURE (M) Protocol 9 - layer2_output FIA handle - CP:0x108d9658 DP:0x LAYER2_OUTPUT_SERVICEWIRE (M) LAYER2_OUTPUT_DROP_POLICY (M) PACTRAC_OUTPUT_STATS MARMOT_SPA_D_TRANSMIT_PKT DEF_IF_DROP_FIA (M) Protocol 14 - ess_ac_input FIA handle - CP:0x108d9ba0 DP:0x8070cb80 PPPOE_GET_SESSION ESS_ENTER_SWITCHING PPPOE_HANDLE_UNCLASSIFIED_SESSION DEF_IF_DROP_FIA (M) QfpEth Physical Information DPS Addr: 0x11215eb8 Submap Table Addr: 0x VLAN Ethertype: 0x8100 QOS Mode: Per Link Note: The CBUG_INPUT_FIA and the DEBUG_COND_INPUT_PKT correspond to the conditional debug features that are configured on the router. Dump the Traced Packets You can copy and dump the packets as they are traced, as this section describes. This example shows how to copy a maximum of 2,048 bytes of the packets in the ingress direction (
11 to ). Here is the additional command that is needed: debug platform packet-trace copy packet input size 2048 Note: The size of the packet that is copied is in the range of 16 to 2,048 bytes. Enter this command in order to dump the copied packets: show platform packet-trace packet 0 Packet: 0 CBUG ID: 14 Input : GigabitEthernet0/0/1 Output : GigabitEthernet0/0/0 State : FWD Timestamp Start : ns (05/17/ :40: UTC) Stop : ns (05/17/ :40: UTC) Source : Destination : Entry : 0x8059dbe8 - DEBUG_COND_INPUT_PKT Timestamp : <some content excluded> Entry : 0x MARMOT_SPA_D_TRANSMIT_PKT Timestamp : Packet Copy In a4934c8e ff01 5f16ac ac fd d0 d980abcd abcdabcd abcdabcd abcdabcd abcdabcd abcdabcd abcdabcd abcdabcd abcdabcd abcdabcd abcdabcd abcdabcd abcdabcd abcdabcd abcdabcd abcdabcd abcd Drop Trace Drop trace is available in Cisco IOS-XE software Versions 3.11 and later. It enables packet trace only for dropped packets. Here are some highlights of the feature: It optionally allows you to specify the retention of packets for a specific drop code. It can be used without global or interface conditions in order to capture drop events. A drop event capture means that only the drop itself is traced, not the life of the packet. However, it still allows you to capture summary data, tuple data, and the packet in order to help refine conditions or provide clues to the next debug step. Here is the command syntax that is used in order to enable drop-type packet traces: debug platform packet-trace drop [code <code-num>] The drop code is the same as the drop ID, as reported in the show platform hardware qfp active statistics drop detail command output: show platform hardware qfp active statistics drop detail
12 ID Global Drop Stats Packets Octets IpTtlExceeded Ipv4Acl Example Drop Trace Scenario Apply this ACL on the Gig 0/0/0 interface of the ASR1K in order to drop traffic from to : show platform hardware qfp active statistics drop detail ID Global Drop Stats Packets Octets IpTtlExceeded Ipv4Acl With the ACL in place, which drops the traffic from the local host to the remote host, apply this drop-trace configuration: debug platform condition interface Gig 0/0/1 ingress debug platform condition start debug platform packet-trace packet 1024 fia-trace debug platform packet-trace drop debug platform packet-trace enable Send five ICMP request packets from to The drop trace captures these packets that are dropped by the ACL, as shown: show platform packet-trace statistics Packets Matched 5 Traced 5 Packets Received Ingress 5 Inject 0 Packets Processed Forward 0 Punt 0 Drop 5 Count Code Cause 5 8 Ipv4Acl Consume 0 show platform packet-trace summary Pkt Input Output State Reason 0 Gi0/0/1 Gi0/0/0 DROP 8 (Ipv4Acl) 1 Gi0/0/1 Gi0/0/0 DROP 8 (Ipv4Acl) 2 Gi0/0/1 Gi0/0/0 DROP 8 (Ipv4Acl) 3 Gi0/0/1 Gi0/0/0 DROP 8 (Ipv4Acl) 4 Gi0/0/1 Gi0/0/0 DROP 8 (Ipv4Acl) ASR1K#debug platform condition stop ASR1K#show platform packet-trace packet 0 Packet: 0 CBUG ID: 140 Input : GigabitEthernet0/0/1 Output : GigabitEthernet0/0/0 State : DROP 8 (Ipv4Acl)
13 Timestamp Start : ns (05/17/ :42: UTC) Stop : ns (05/17/ :42: UTC) Source : Destination : Entry : 0x806c7eac - DEBUG_COND_INPUT_PKT Lapsed time: 1031 ns Entry : 0x82011c00 - IPV4_INPUT_DST_LOOKUP_CONSUME Lapsed time: 657 ns Entry : 0x806a IPV4_INPUT_ACL Lapsed time: 2773 ns Entry : 0x IPV4_INPUT_FOR_US_MARTIAN Lapsed time: 1013 ns Entry : 0x IPV4_OUTPUT_LOOKUP_PROCESS Lapsed time: 2951 ns Entry : 0x c - IPV4_INPUT_IPOPTIONS_PROCESS Lapsed time: 373 ns Entry : 0x MPLS_INPUT_GOTO_OUTPUT_FEATURE Lapsed time: 2097 ns Entry : 0x803c60b8 - IPV4_MC_OUTPUT_VFR_REFRAG Lapsed time: 373 ns Entry : 0x806db148 - OUTPUT_DROP Lapsed time: 1297 ns Entry : 0x806a0c98 - IPV4_OUTPUT_ACL Lapsed time: ns Inject and Punt Traces The inject and punt packet trace feature was added in Cisco IOS-XE software Versions 3.12 and later in order to trace punt (packets that are received on the FP that are punted to the control plane) and inject (packets that are injected to the FP from the control plane) packets. Note: The punt trace can work without the global or interface conditions, just like a drop trace. However, the conditions must be defined for an inject trace to work. Here is an example of a punt and inject packet trace when you ping from the ASR1K to an adjacent router: debug platform condition ipv /32 both debug platform condition start debug platform packet-trace punt debug platform packet-trace inject debug platform packet-trace packet 16 debug platform packet-trace enable
14 ping Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to , timeout is 2 seconds:!!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 14/14/15 ms Now you can verify the punt and inject trace results: show platform packet-trace summary Pkt Input Output State Reason 0 INJ.2 Gi0/0/1 FWD 1 Gi0/0/1 internal0/0/rp:0 PUNT 11 (For-us data) 2 INJ.2 Gi0/0/1 FWD 3 Gi0/0/1 internal0/0/rp:0 PUNT 11 (For-us data) 4 INJ.2 Gi0/0/1 FWD 5 Gi0/0/1 internal0/0/rp:0 PUNT 11 (For-us data) 6 INJ.2 Gi0/0/1 FWD 7 Gi0/0/1 internal0/0/rp:0 PUNT 11 (For-us data) 8 INJ.2 Gi0/0/1 FWD 9 Gi0/0/1 internal0/0/rp:0 PUNT 11 (For-us data) show platform packet-trace packet 0 Packet: 0 CBUG ID: 120 Input : INJ.2 Output : GigabitEthernet0/0/1 State : FWD Timestamp Start : ns (05/29/ :02: UTC) Stop : ns (05/29/ :02: UTC) Source : Destination : show platform packet-trace packet 1 Packet: 1 CBUG ID: 121 Input : GigabitEthernet0/0/1 Output : internal0/0/rp:0 State : PUNT 11 (For-us data) Timestamp Start : ns (05/29/ :02: UTC) Stop : ns (05/29/ :02: UTC) Source : Destination : Packet Trace Examples This section provides some examples where the packet trace feature is useful for troubleshooting purposes. Packet Trace Example - NAT With this example, an interface source Network Address Translation (NAT) is configured on the
15 WAN interface of an ASR1K (Gig0/0/0) for the local subnet ( /24). Here is the platform condition and packet trace configuration that is used in order to trace the traffic from to , which becomes translated (NAT) on the Gig0/0/0 interface: show platform packet-trace summary Pkt Input Output State Reason 0 INJ.2 Gi0/0/1 FWD 1 Gi0/0/1 internal0/0/rp:0 PUNT 11 (For-us data) 2 INJ.2 Gi0/0/1 FWD 3 Gi0/0/1 internal0/0/rp:0 PUNT 11 (For-us data) 4 INJ.2 Gi0/0/1 FWD 5 Gi0/0/1 internal0/0/rp:0 PUNT 11 (For-us data) 6 INJ.2 Gi0/0/1 FWD 7 Gi0/0/1 internal0/0/rp:0 PUNT 11 (For-us data) 8 INJ.2 Gi0/0/1 FWD 9 Gi0/0/1 internal0/0/rp:0 PUNT 11 (For-us data) show platform packet-trace packet 0 Packet: 0 CBUG ID: 120 Input : INJ.2 Output : GigabitEthernet0/0/1 State : FWD Timestamp Start : ns (05/29/ :02: UTC) Stop : ns (05/29/ :02: UTC) Source : Destination : show platform packet-trace packet 1 Packet: 1 CBUG ID: 121 Input : GigabitEthernet0/0/1 Output : internal0/0/rp:0 State : PUNT 11 (For-us data) Timestamp Start : ns (05/29/ :02: UTC) Stop : ns (05/29/ :02: UTC) Source : Destination : When five ICMP packets are sent from to with an interface source NAT configuration, these are the packet trace results: show platform packet-trace summary Pkt Input Output State Reason 0 Gi0/0/1 Gi0/0/0 FWD 1 Gi0/0/1 Gi0/0/0 FWD 2 Gi0/0/1 Gi0/0/0 FWD 3 Gi0/0/1 Gi0/0/0 FWD 4 Gi0/0/1 Gi0/0/0 FWD show platform packet-trace statistics Packets Matched 5
16 Traced 5 Packets Received Ingress 5 Inject 0 Packets Processed Forward 5 Punt 0 Drop 0 Consume 0 show platform packet-trace packet 0 Packet: 0 CBUG ID: 146 Input : GigabitEthernet0/0/1 Output : GigabitEthernet0/0/0 State : FWD Timestamp Start : ns (05/17/ :01: UTC) Stop : ns (05/17/ :01: UTC) Source : Destination : Entry : 0x806c7eac - DEBUG_COND_INPUT_PKT Lapsed time: 1031 ns Entry : 0x82011c00 - IPV4_INPUT_DST_LOOKUP_CONSUME Lapsed time: 462 ns Entry : 0x IPV4_INPUT_FOR_US_MARTIAN Lapsed time: 355 ns Entry : 0x803c6af4 - IPV4_INPUT_VFR Lapsed time: 266 ns Entry : 0x IPV4_OUTPUT_LOOKUP_PROCESS Lapsed time: 942 ns Entry : 0x c - IPV4_INPUT_IPOPTIONS_PROCESS Lapsed time: 88 ns Entry : 0x MPLS_INPUT_GOTO_OUTPUT_FEATURE Lapsed time: 568 ns Entry : 0x803c IPV4_OUTPUT_VFR Lapsed time: 266 ns Feature: NAT Direction : IN to OUT Action : Translate Source Old Address : New Address : Entry : 0x8031c248 - IPV4_NAT_OUTPUT_FIA Lapsed time: ns Entry : 0x801424f8 - IPV4_OUTPUT_THREAT_DEFENSE Lapsed time: 693 ns Entry : 0x803c60b8 - IPV4_MC_OUTPUT_VFR_REFRAG Lapsed time: 88 ns Entry : 0x IPV6_INPUT_L2_REWRITE
17 Lapsed time: 444 ns Entry : 0x IPV4_OUTPUT_FRAG Lapsed time: 88 ns Entry : 0x8200e600 - IPV4_OUTPUT_DROP_POLICY Lapsed time: 1457 ns Entry : 0x MARMOT_SPA_D_TRANSMIT_PKT Lapsed time: 7431 ns Packet Trace Example - VPN With this example, a site-to-site VPN tunnel is used between the ASR1K and the Cisco IOS router in order to protect the traffic that flows between /24 and /24 (local and remote subnets). Here is the platform condition and packet trace configuration that is used in order to trace the VPN traffic that flows from to on the Gig 0/0/1 interface: show platform packet-trace summary Pkt Input Output State Reason 0 Gi0/0/1 Gi0/0/0 FWD 1 Gi0/0/1 Gi0/0/0 FWD 2 Gi0/0/1 Gi0/0/0 FWD 3 Gi0/0/1 Gi0/0/0 FWD 4 Gi0/0/1 Gi0/0/0 FWD show platform packet-trace statistics Packets Matched 5 Traced 5 Packets Received Ingress 5 Inject 0 Packets Processed Forward 5 Punt 0 Drop 0 Consume 0 show platform packet-trace packet 0 Packet: 0 CBUG ID: 146 Input : GigabitEthernet0/0/1 Output : GigabitEthernet0/0/0 State : FWD Timestamp Start : ns (05/17/ :01: UTC) Stop : ns (05/17/ :01: UTC) Source : Destination : Entry : 0x806c7eac - DEBUG_COND_INPUT_PKT Lapsed time: 1031 ns Entry : 0x82011c00 - IPV4_INPUT_DST_LOOKUP_CONSUME Lapsed time: 462 ns
18 Entry : 0x IPV4_INPUT_FOR_US_MARTIAN Lapsed time: 355 ns Entry : 0x803c6af4 - IPV4_INPUT_VFR Lapsed time: 266 ns Entry : 0x IPV4_OUTPUT_LOOKUP_PROCESS Lapsed time: 942 ns Entry : 0x c - IPV4_INPUT_IPOPTIONS_PROCESS Lapsed time: 88 ns Entry : 0x MPLS_INPUT_GOTO_OUTPUT_FEATURE Lapsed time: 568 ns Entry : 0x803c IPV4_OUTPUT_VFR Lapsed time: 266 ns Feature: NAT Direction : IN to OUT Action : Translate Source Old Address : New Address : Entry : 0x8031c248 - IPV4_NAT_OUTPUT_FIA Lapsed time: ns Entry : 0x801424f8 - IPV4_OUTPUT_THREAT_DEFENSE Lapsed time: 693 ns Entry : 0x803c60b8 - IPV4_MC_OUTPUT_VFR_REFRAG Lapsed time: 88 ns Entry : 0x IPV6_INPUT_L2_REWRITE Lapsed time: 444 ns Entry : 0x IPV4_OUTPUT_FRAG Lapsed time: 88 ns Entry : 0x8200e600 - IPV4_OUTPUT_DROP_POLICY Lapsed time: 1457 ns Entry : 0x MARMOT_SPA_D_TRANSMIT_PKT Lapsed time: 7431 ns When five ICMP packets are sent from to , which are encrypted by the VPN tunnel between the ASR1K and the Cisco IOS router in this example, these are the packet trace outputs: Note: The packet traces show the QFP Security Association (SA) handle in the trace that is used in order to encrypt the packet, which is useful when you troubleshoot IPSec VPN issues in order to verify that the correct SA is used for encryption. show platform packet-trace summary Pkt Input Output State Reason 0 Gi0/0/1 Gi0/0/0 FWD 1 Gi0/0/1 Gi0/0/0 FWD 2 Gi0/0/1 Gi0/0/0 FWD 3 Gi0/0/1 Gi0/0/0 FWD 4 Gi0/0/1 Gi0/0/0 FWD
19 show platform packet-trace packet 0 Packet: 0 CBUG ID: 211 Input : GigabitEthernet0/0/1 Output : GigabitEthernet0/0/0 State : FWD Timestamp Start : ns (05/17/ :28: UTC) Stop : ns (05/17/ :28: UTC) Source : Destination : Entry : 0x806c7eac - DEBUG_COND_INPUT_PKT Lapsed time: 622 ns Entry : 0x82011c00 - IPV4_INPUT_DST_LOOKUP_CONSUME Lapsed time: 462 ns Entry : 0x IPV4_INPUT_FOR_US_MARTIAN Lapsed time: 320 ns Entry : 0x IPV4_OUTPUT_LOOKUP_PROCESS Lapsed time: 1102 ns Entry : 0x c - IPV4_INPUT_IPOPTIONS_PROCESS Lapsed time: 88 ns Entry : 0x MPLS_INPUT_GOTO_OUTPUT_FEATURE Lapsed time: 586 ns Entry : 0x803c IPV4_OUTPUT_VFR Lapsed time: 266 ns Entry : 0x MC_OUTPUT_GEN_RECYCLE Lapsed time: 195 ns Entry : 0x803c60b8 - IPV4_MC_OUTPUT_VFR_REFRAG Lapsed time: 88 ns Feature: IPSec Result : IPSEC_RESULT_SA Action : ENCRYPT SA Handle : 6 Peer Addr : Local Addr: Entry : 0x8043caec - IPV4_OUTPUT_IPSEC_CLASSIFY Lapsed time: 9528 ns Entry : 0x c - IPV4_OUTPUT_IPSEC_DOUBLE_ACL Lapsed time: 355 ns Entry : 0x8043b45c - IPV4_IPSEC_FEATURE_RETURN Lapsed time: 657 ns Entry : 0x8043ae28 - IPV4_OUTPUT_IPSEC_RERUN_JUMP Lapsed time: 888 ns Entry : 0x80436f10 - IPV4_OUTPUT_IPSEC_POST_PROCESS Lapsed time: 2186 ns Entry : 0x8043b45c - IPV4_IPSEC_FEATURE_RETURN
20 Lapsed time: 675 ns Entry : 0x IPV6_INPUT_L2_REWRITE Lapsed time: 1902 ns Entry : 0x IPV4_OUTPUT_FRAG Lapsed time: 71 ns Entry : 0x8200e600 - IPV4_OUTPUT_DROP_POLICY Lapsed time: 1582 ns Entry : 0x MARMOT_SPA_D_TRANSMIT_PKT Lapsed time: 3964 ns Performance Impact Packet trace buffers consume QFP DRAM, so be mindful of the amount of memory that a configuration requires and the amount of memory that is available. The performance impact varies, dependent upon the packet trace options that are enabled. The packet trace only affects the forwarding performance of the packets that are traced, such as those packets that match the user-configured conditions. The more granular and detailed information that you configure the packet trace to capture, the greater it will impact resources. As with any troubleshooting, it is best to take an iterative approach and only enable the moredetailed trace options when a debug situation warrants it. The QFP DRAM usage can be estimated with this formula: memory needed = (stats overhead) + num of pkts * (summary size + path data size + copy size) Note: Where the stats overhead and summary size are fixed at 2 KB and 128 B, respectively, the path data size and copy size are user-configurable. Related Information Cisco ASR1000 Series Aggregation Series Routers Software Configuration Guide - Packet Trace Packet Drops on Cisco ASR1000 Series Service Routers Technical Support & Documentation - Cisco Systems
DHCP Server Does Not Work on a Router That Runs Cisco IOS-XE SD-WAN with DIA
 DHCP Server Does Not Work on a Router That Runs Cisco IOS-XE SD-WAN with DIA Contents Introduction Problem Solution Introduction This document describes typical problems that might be expected when centralized
DHCP Server Does Not Work on a Router That Runs Cisco IOS-XE SD-WAN with DIA Contents Introduction Problem Solution Introduction This document describes typical problems that might be expected when centralized
Contents. Introduction. Prerequisites. Background Information
 Contents Introduction Prerequisites Background Information Limitation Configure Network Diagram Initial configuration R2 R3 IPSec configuration R2 EzPM configuration Workaround Verify Troubleshooting Related
Contents Introduction Prerequisites Background Information Limitation Configure Network Diagram Initial configuration R2 R3 IPSec configuration R2 EzPM configuration Workaround Verify Troubleshooting Related
Configuring Traffic Mirroring
 This module describes the configuration of the traffic mirroring feature. Traffic mirroring is sometimes called port mirroring, or switched port analyzer (SPAN). Feature History for Traffic Mirroring Release
This module describes the configuration of the traffic mirroring feature. Traffic mirroring is sometimes called port mirroring, or switched port analyzer (SPAN). Feature History for Traffic Mirroring Release
Using the Management Ethernet Interface
 The Cisco ASR 920 Series Router has one Gigabit Ethernet Management Ethernet interface on each Route Switch Processor. The purpose of this interface is to allow users to perform management tasks on the
The Cisco ASR 920 Series Router has one Gigabit Ethernet Management Ethernet interface on each Route Switch Processor. The purpose of this interface is to allow users to perform management tasks on the
Manually Configured IPv6 over IPv4 Tunnels
 This feature provides support for manually configured IPv6 over IPv4 tunnels. A manually configured tunnel is equivalent to a permanent link between two IPv6 domains over an IPv4 backbone. Finding Feature
This feature provides support for manually configured IPv6 over IPv4 tunnels. A manually configured tunnel is equivalent to a permanent link between two IPv6 domains over an IPv4 backbone. Finding Feature
Traffic Mirroring Commands on Cisco ASR 9000 Series Router
 Traffic Mirroring Commands on Cisco ASR 9000 Series Router This module describes the commands used to configure and monitor traffic mirroring. Command Reference HR-1061 acl Traffic Mirroring Commands on
Traffic Mirroring Commands on Cisco ASR 9000 Series Router This module describes the commands used to configure and monitor traffic mirroring. Command Reference HR-1061 acl Traffic Mirroring Commands on
Lab Configuring and Verifying Standard IPv4 ACLs (Instructor Version Optional Lab)
 (Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
(Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
QoS Packet-Matching Statistics Configuration
 The QoS Packet-Matching Statistics feature comprises the following subfeatures: The QoS Packet-Matching Statistics: Per Filter feature allows users to count and display the number of packets and bytes
The QoS Packet-Matching Statistics feature comprises the following subfeatures: The QoS Packet-Matching Statistics: Per Filter feature allows users to count and display the number of packets and bytes
Chapter 8 Lab Configuring a Site-to-Site VPN Using Cisco IOS
 Chapter 8 Lab Configuring a Site-to-Site VPN Using Cisco IOS Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces. 2017 Cisco and/or its affiliates. All rights
Chapter 8 Lab Configuring a Site-to-Site VPN Using Cisco IOS Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces. 2017 Cisco and/or its affiliates. All rights
Step 2. Manual configuration of global unicast and link-local addresses
 Lab: ICMPv6 and ICMPv6 Neighbor Discovery CIS 116 IPv6 Fundamentals Enter your answers to the questions in this lab using Canvas Quiz DHCPv6 Lab. Part 1: Setup Step 1. Basics a. Log into NetLab: ccnp.bayict.cabrillo.edu
Lab: ICMPv6 and ICMPv6 Neighbor Discovery CIS 116 IPv6 Fundamentals Enter your answers to the questions in this lab using Canvas Quiz DHCPv6 Lab. Part 1: Setup Step 1. Basics a. Log into NetLab: ccnp.bayict.cabrillo.edu
Pseudowire Concepts and troubleshooting
 Pseudowire Concepts and troubleshooting Contents Introduction Prerequisites Components Used Pseudowire Concept Troubleshooting a Pseudowire Introduction Pseudowires(PW) are used to provide end-to-end services
Pseudowire Concepts and troubleshooting Contents Introduction Prerequisites Components Used Pseudowire Concept Troubleshooting a Pseudowire Introduction Pseudowires(PW) are used to provide end-to-end services
Performing Path Traces
 About Path Trace, page 1 Performing a Path Trace, page 13 Collecting QoS and Interface Statistics in a Path Trace, page 15 About Path Trace With Path Trace, the controller reviews and collects network
About Path Trace, page 1 Performing a Path Trace, page 13 Collecting QoS and Interface Statistics in a Path Trace, page 15 About Path Trace With Path Trace, the controller reviews and collects network
Using the Management Ethernet Interface
 This chapter covers the following topics: Gigabit Ethernet Management Interface Overview, page 1 Gigabit Ethernet Port Numbering, page 1 IP Address Handling in ROMmon and the Management Ethernet Port,
This chapter covers the following topics: Gigabit Ethernet Management Interface Overview, page 1 Gigabit Ethernet Port Numbering, page 1 IP Address Handling in ROMmon and the Management Ethernet Port,
Lab Configuring and Verifying Standard IPv4 ACLs Topology
 Topology 2016 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 10 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.10.1
Topology 2016 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 10 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.10.1
Packet Tracer - Connect a Router to a LAN (Instructor Version)
 (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Topology Addressing Table Device Interface IP Address Subnet Mask Default
(Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Topology Addressing Table Device Interface IP Address Subnet Mask Default
Lab - Configuring a Site-to-Site VPN Using Cisco IOS and CCP
 CCNA Security Lab - Configuring a Site-to-Site VPN Using Cisco IOS and CCP Topology Note: ISR G2 devices use GigabitEthernet interfaces instead of FastEthernet Interfaces. 2015 Cisco and/or its affiliates.
CCNA Security Lab - Configuring a Site-to-Site VPN Using Cisco IOS and CCP Topology Note: ISR G2 devices use GigabitEthernet interfaces instead of FastEthernet Interfaces. 2015 Cisco and/or its affiliates.
Lab Configuring and Verifying Standard ACLs Topology
 Topology 2013 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 9 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.10.1
Topology 2013 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 9 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.10.1
8K GM Scale Improvement
 The feature supports optimization of the Cooperative Protocol (COOP) announcement messages by increasing the number of Group Members (GM) to 8000. Finding Feature Information, page 1 Prerequisites for,
The feature supports optimization of the Cooperative Protocol (COOP) announcement messages by increasing the number of Group Members (GM) to 8000. Finding Feature Information, page 1 Prerequisites for,
Cisco IOS LISP Application Note Series: Access Control Lists
 Cisco IOS LISP Application Note Series: Access Control Lists Version 1.1 (28 April 2011) Background The LISP Application Note Series provides targeted information that focuses on the integration and configuration
Cisco IOS LISP Application Note Series: Access Control Lists Version 1.1 (28 April 2011) Background The LISP Application Note Series provides targeted information that focuses on the integration and configuration
Configuring Traffic Mirroring
 This module describes the configuration of the traffic mirroring feature. Traffic mirroring is sometimes called port mirroring, or switched port analyzer (SPAN). Feature History for Traffic Mirroring Release
This module describes the configuration of the traffic mirroring feature. Traffic mirroring is sometimes called port mirroring, or switched port analyzer (SPAN). Feature History for Traffic Mirroring Release
Configuring Traffic Mirroring
 This module describes the configuration of the traffic mirroring feature. Traffic mirroring is sometimes called port mirroring, or switched port analyzer (SPAN). Feature History for Traffic Mirroring Release
This module describes the configuration of the traffic mirroring feature. Traffic mirroring is sometimes called port mirroring, or switched port analyzer (SPAN). Feature History for Traffic Mirroring Release
Chapter 10 - Configure ASA Basic Settings and Firewall using ASDM
 Chapter 10 - Configure ASA Basic Settings and Firewall using ASDM This lab has been updated for use on NETLAB+ Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces.
Chapter 10 - Configure ASA Basic Settings and Firewall using ASDM This lab has been updated for use on NETLAB+ Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces.
GRE Tunnel with VRF Configuration Example
 GRE Tunnel with VRF Configuration Example Document ID: 46252 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations Verify Troubleshoot Caveats
GRE Tunnel with VRF Configuration Example Document ID: 46252 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations Verify Troubleshoot Caveats
Control Plane Policing
 The feature allows you to configure a quality of service (QoS) filter that manages the traffic flow of control plane packets to protect the control plane of Cisco IOS XE routers and switches against reconnaissance
The feature allows you to configure a quality of service (QoS) filter that manages the traffic flow of control plane packets to protect the control plane of Cisco IOS XE routers and switches against reconnaissance
HOME-SYD-RTR02 GETVPN Configuration
 GETVPN OVER DMVPN Topology Details HOME-SYD-RTR02 is GETVPN KS. R2 & R3 are GETVPN Members. R2 is DMVPN Hub. R3 is DMVPN Spoke. HOME-PIX01 is Firewall between R2 and R3. IP Addressing Details HOME-SYD-RTR01
GETVPN OVER DMVPN Topology Details HOME-SYD-RTR02 is GETVPN KS. R2 & R3 are GETVPN Members. R2 is DMVPN Hub. R3 is DMVPN Spoke. HOME-PIX01 is Firewall between R2 and R3. IP Addressing Details HOME-SYD-RTR01
Configuration Professional: Site to Site IPsec VPN Between Two IOS Routers Configuration Example
 Configuration Professional: Site to Site IPsec VPN Between Two IOS Routers Configuration Example Document ID: 113337 Contents Introduction Prerequisites Requirements Components Used Conventions Configuration
Configuration Professional: Site to Site IPsec VPN Between Two IOS Routers Configuration Example Document ID: 113337 Contents Introduction Prerequisites Requirements Components Used Conventions Configuration
The information in this document is based on Cisco IOS Software Release 15.4 version.
 Contents Introduction Prerequisites Requirements Components Used Background Information Configure Network Diagram Relevant Configuration Verify Test case 1 Test case 2 Test case 3 Troubleshoot Introduction
Contents Introduction Prerequisites Requirements Components Used Background Information Configure Network Diagram Relevant Configuration Verify Test case 1 Test case 2 Test case 3 Troubleshoot Introduction
Cisco ASR 9000 Series Aggregation Services Router Netflow Command Reference, Release 4.3.x
 Cisco ASR 9000 Series Aggregation Services Router Netflow Command Reference, Release 4.3.x First Published: 2012-12-01 Last Modified: 2013-05-01 Americas Headquarters Cisco Systems, Inc. 170 West Tasman
Cisco ASR 9000 Series Aggregation Services Router Netflow Command Reference, Release 4.3.x First Published: 2012-12-01 Last Modified: 2013-05-01 Americas Headquarters Cisco Systems, Inc. 170 West Tasman
L2VPN Protocol-Based CLIs
 The feature provides a set of processes and an improved infrastructure for developing and delivering Cisco IOS software on various Cisco platforms. This feature introduces new commands and modifies or
The feature provides a set of processes and an improved infrastructure for developing and delivering Cisco IOS software on various Cisco platforms. This feature introduces new commands and modifies or
Configuring Data Export for Flexible NetFlow with Flow Exporters
 Configuring Data Export for Flexible NetFlow with Flow Exporters Last Updated: November 29, 2012 This document contains information about and instructions for configuring flow exporters to export Flexible
Configuring Data Export for Flexible NetFlow with Flow Exporters Last Updated: November 29, 2012 This document contains information about and instructions for configuring flow exporters to export Flexible
Adaptive QoS over DMVPN
 Adaptive QoS over Dynamic Multipoint VPN (DMVPN) ensures effective bandwidth management using dynamic shapers based on available bandwidth. This feature enables various QoS features to adapt to non service-level
Adaptive QoS over Dynamic Multipoint VPN (DMVPN) ensures effective bandwidth management using dynamic shapers based on available bandwidth. This feature enables various QoS features to adapt to non service-level
Using Segment Routing OAM
 Segment Routing Operations, Administration, and Maintenance (OAM) helps service providers to monitor label-switched paths (LSPs) and quickly isolate forwarding problems to assist with fault detection and
Segment Routing Operations, Administration, and Maintenance (OAM) helps service providers to monitor label-switched paths (LSPs) and quickly isolate forwarding problems to assist with fault detection and
VPN Connection through Zone based Firewall Router Configuration Example
 VPN Connection through Zone based Firewall Router Configuration Example Document ID: 112051 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Configure
VPN Connection through Zone based Firewall Router Configuration Example Document ID: 112051 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Configure
OpenFlow. Finding Feature Information. Prerequisites for OpenFlow
 Finding Feature Information, page 1 Prerequisites for, page 1 Restrictions for, page 2 Information About Open Flow, page 3 Configuring, page 8 Monitoring, page 12 Configuration Examples for, page 12 Finding
Finding Feature Information, page 1 Prerequisites for, page 1 Restrictions for, page 2 Information About Open Flow, page 3 Configuring, page 8 Monitoring, page 12 Configuration Examples for, page 12 Finding
Ping, tracert and system debugging commands
 Contents Ping, tracert and system debugging commands 1 Ping and tracert commands 1 ping 1 ping ipv6 5 tracert 7 tracert ipv6 9 System debugging commands 10 debugging 10 display debugging 11 i Ping, tracert
Contents Ping, tracert and system debugging commands 1 Ping and tracert commands 1 ping 1 ping ipv6 5 tracert 7 tracert ipv6 9 System debugging commands 10 debugging 10 display debugging 11 i Ping, tracert
MPLS Ping and Traceroute for BGP and IGP Prefix-SID
 MPLS Ping and Traceroute for BGP and IGP Prefix-SID MPLS Ping and Traceroute operations for Prefix SID are supported for various BGP and IGP scenarios, for example: Within an IS-IS level or OSPF area Across
MPLS Ping and Traceroute for BGP and IGP Prefix-SID MPLS Ping and Traceroute operations for Prefix SID are supported for various BGP and IGP scenarios, for example: Within an IS-IS level or OSPF area Across
OpenFlow. Finding Feature Information. Prerequisites for OpenFlow
 Finding Feature Information, page 1 Prerequisites for, page 1 Restrictions for, page 2 Information About Open Flow, page 3 Configuring, page 8 Monitoring, page 12 Configuration Examples for, page 12 Finding
Finding Feature Information, page 1 Prerequisites for, page 1 Restrictions for, page 2 Information About Open Flow, page 3 Configuring, page 8 Monitoring, page 12 Configuration Examples for, page 12 Finding
Port ACLs (PACLs) Prerequisites for PACls CHAPTER
 71 CHAPTER Prerequisites for PACls, page 71-1 Restrictions for PACLs, page 71-2 Information About PACLs, page 71-2 How to Configure PACLs, page 71-7 Note For complete syntax and usage information for the
71 CHAPTER Prerequisites for PACls, page 71-1 Restrictions for PACLs, page 71-2 Information About PACLs, page 71-2 How to Configure PACLs, page 71-7 Note For complete syntax and usage information for the
Network as an Enforcer (NaaE) Cisco Services. Network as an Enforcer Cisco and/or its affiliates. All rights reserved.
 Network as an Enforcer (NaaE) Cisco Services INTRODUCTION... 6 Overview of Network as an Enforcer... 6 Key Benefits... 6 Audience... 6 Scope... 6... 8 Guidelines and Limitations... 8 Configuring SGACL
Network as an Enforcer (NaaE) Cisco Services INTRODUCTION... 6 Overview of Network as an Enforcer... 6 Key Benefits... 6 Audience... 6 Scope... 6... 8 Guidelines and Limitations... 8 Configuring SGACL
Configuration and Operation of FTD Prefilter
 Configuration and Operation of FTD Prefilter Policies Contents Introduction Prerequisites Requirements Components Used Background Information Configure Pre-filter Policy Use Case 1 Pre-filter Policy Use
Configuration and Operation of FTD Prefilter Policies Contents Introduction Prerequisites Requirements Components Used Background Information Configure Pre-filter Policy Use Case 1 Pre-filter Policy Use
L2VPN Interworking. Finding Feature Information
 Interworking is a transforming function that is required to interconnect two heterogeneous attachment circuits (ACs). Several types of interworking functions exist. The function that is used would depend
Interworking is a transforming function that is required to interconnect two heterogeneous attachment circuits (ACs). Several types of interworking functions exist. The function that is used would depend
Configuration and Management of Networks 2012
 Configuring BGP with default routing Topology Objectives Background Instructions Configure BGP to exchange routing information with two ISPs. The International Travel Agency (ITA) relies extensively on
Configuring BGP with default routing Topology Objectives Background Instructions Configure BGP to exchange routing information with two ISPs. The International Travel Agency (ITA) relies extensively on
Quick Note. Configure an IPSec VPN tunnel in Aggressive mode between a TransPort LR router and a Cisco router. Digi Technical Support 7 October 2016
 Quick Note Configure an IPSec VPN tunnel in Aggressive mode between a TransPort LR router and a Cisco router. Digi Technical Support 7 October 2016 Contents 1 Introduction... 3 1.1 Outline... 3 1.2 Assumptions...
Quick Note Configure an IPSec VPN tunnel in Aggressive mode between a TransPort LR router and a Cisco router. Digi Technical Support 7 October 2016 Contents 1 Introduction... 3 1.1 Outline... 3 1.2 Assumptions...
The Radio Aware Routing feature offers the following benefits: Provides faster network convergence through immediate recognition of changes.
 Radio-Aware Routing (RAR) is a mechanism that uses radios to interact with the routing protocol OSPFv3 to signal the appearance, disappearance, and link conditions of one-hop routing neighbors. In a large
Radio-Aware Routing (RAR) is a mechanism that uses radios to interact with the routing protocol OSPFv3 to signal the appearance, disappearance, and link conditions of one-hop routing neighbors. In a large
Punt Policing and Monitoring
 Punt policing protects the Route Processor (RP) from having to process noncritical traffic, which increases the CPU bandwidth available to critical traffic. Traffic is placed into different CPU queues
Punt policing protects the Route Processor (RP) from having to process noncritical traffic, which increases the CPU bandwidth available to critical traffic. Traffic is placed into different CPU queues
Sections Describing Standard Software Features
 27 CHAPTER This chapter describes how to configure quality of service (QoS) by using automatic-qos (auto-qos) commands or by using standard QoS commands. With QoS, you can give preferential treatment to
27 CHAPTER This chapter describes how to configure quality of service (QoS) by using automatic-qos (auto-qos) commands or by using standard QoS commands. With QoS, you can give preferential treatment to
Configuring Application Visibility and Control for Cisco Flexible Netflow
 Configuring Application Visibility and Control for Cisco Flexible Netflow First published: July 22, 2011 This guide contains information about the Cisco Application Visibility and Control feature. It also
Configuring Application Visibility and Control for Cisco Flexible Netflow First published: July 22, 2011 This guide contains information about the Cisco Application Visibility and Control feature. It also
Configuring NetFlow and NetFlow Data Export
 This module contains information about and instructions for configuring NetFlow to capture and export network traffic data. NetFlow capture and export are performed independently on each internetworking
This module contains information about and instructions for configuring NetFlow to capture and export network traffic data. NetFlow capture and export are performed independently on each internetworking
Table of Contents. isco Configuring 802.1q Trunking Between a Catalyst 3550 and Catalyst Switches Running Integrated Cisco IOS (Nativ
 king Between a Catalyst 3550 and Catalyst Switches Running isco Configuring 802.1q Trunking Between a Catalyst 3550 and Catalyst Switches Running Integrated Cisco IOS (Nativ Table of Contents Configuring
king Between a Catalyst 3550 and Catalyst Switches Running isco Configuring 802.1q Trunking Between a Catalyst 3550 and Catalyst Switches Running Integrated Cisco IOS (Nativ Table of Contents Configuring
Sections Describing Standard Software Features
 30 CHAPTER This chapter describes how to configure quality of service (QoS) by using automatic-qos (auto-qos) commands or by using standard QoS commands. With QoS, you can give preferential treatment to
30 CHAPTER This chapter describes how to configure quality of service (QoS) by using automatic-qos (auto-qos) commands or by using standard QoS commands. With QoS, you can give preferential treatment to
Building Service-Aware Networks
 Building Service-Aware Networks The Next-Generation WAN/MAN Muhammad Afaq Khan, CCIE No. 9070 Cisco Press 800 East 96th Street Indianapolis, IN 46240 Building Service-Aware Networks: The Next-Generation
Building Service-Aware Networks The Next-Generation WAN/MAN Muhammad Afaq Khan, CCIE No. 9070 Cisco Press 800 East 96th Street Indianapolis, IN 46240 Building Service-Aware Networks: The Next-Generation
Basic Router Configuration
 This section includes information about some basic router configuration, and contains the following sections: Default Configuration, on page 1 Configuring Global Parameters, on page 2 Configuring Gigabit
This section includes information about some basic router configuration, and contains the following sections: Default Configuration, on page 1 Configuring Global Parameters, on page 2 Configuring Gigabit
Chapter 7 Lab 7-1, Configuring BGP with Default Routing
 Chapter 7 Topology Objectives Configure BGP to exchange routing information with two ISPs. Background The International Travel Agency (ITA) relies extensively on the Internet for sales. For this reason,
Chapter 7 Topology Objectives Configure BGP to exchange routing information with two ISPs. Background The International Travel Agency (ITA) relies extensively on the Internet for sales. For this reason,
AVC Notes, Limitations, and Caveats
 CHAPTER 6 Revised: November 21, 2013, This section includes the following topics: Notes, page 6-1 Limitations, page 6-2 Caveats, page 6-5 Notes Hidden Fields Two hidden fields (first/last timestamp) are
CHAPTER 6 Revised: November 21, 2013, This section includes the following topics: Notes, page 6-1 Limitations, page 6-2 Caveats, page 6-5 Notes Hidden Fields Two hidden fields (first/last timestamp) are
Match-in-VRF Support for NAT
 The feature supports Network Address Translation (NAT) of packets that communicate between two hosts within the same VPN routing and forwarding (VRF) instance. In intra-vpn NAT, both the local and global
The feature supports Network Address Translation (NAT) of packets that communicate between two hosts within the same VPN routing and forwarding (VRF) instance. In intra-vpn NAT, both the local and global
ASR1000 OTV Deployment Modes (OTV Appliance on a Stick)
 ASR1000 OTV Deployment Modes (OTV Appliance on a Stick) UMA SANKAR MOHANTY, Technical Services Agenda The WW(WHAT & WHY) of OTV Role of ASR1000 in OTV Deployments OTV on STICK Health Check Packet Tracer
ASR1000 OTV Deployment Modes (OTV Appliance on a Stick) UMA SANKAR MOHANTY, Technical Services Agenda The WW(WHAT & WHY) of OTV Role of ASR1000 in OTV Deployments OTV on STICK Health Check Packet Tracer
Layer 2 Access Control Lists on EVCs
 The ability to filter packets in a modular and scalable way is important for both network security and network management. Access Control Lists (ACLs) provide the capability to filter packets at a fine
The ability to filter packets in a modular and scalable way is important for both network security and network management. Access Control Lists (ACLs) provide the capability to filter packets at a fine
QoS: Policing and Shaping Configuration Guide, Cisco IOS XE Release 3S (Cisco ASR 920 Series)
 QoS: Policing and Shaping Configuration Guide, Cisco IOS XE Release 3S (Cisco ASR 920 Series) First Published: 2014-07-29 Last Modified: 2014-11-22 Americas Headquarters Cisco Systems, Inc. 170 West Tasman
QoS: Policing and Shaping Configuration Guide, Cisco IOS XE Release 3S (Cisco ASR 920 Series) First Published: 2014-07-29 Last Modified: 2014-11-22 Americas Headquarters Cisco Systems, Inc. 170 West Tasman
Chapter 10 Lab 10-2, Securing VLANs INSTRUCTOR VERSION
 CCNPv7.1 SWITCH Chapter 10 Lab 10-2, Securing VLANs INSTRUCTOR VERSION Topology Objectives Background Secure the server farm using private VLANs. Secure the staff VLAN from the student VLAN. Secure the
CCNPv7.1 SWITCH Chapter 10 Lab 10-2, Securing VLANs INSTRUCTOR VERSION Topology Objectives Background Secure the server farm using private VLANs. Secure the staff VLAN from the student VLAN. Secure the
I Commands. iping, page 2 iping6, page 4 itraceroute, page 5 itraceroute6 vrf, page 6. itraceroute vrf encap vxlan, page 12
 iping, page 2 iping6, page 4 itraceroute, page 5 itraceroute6 vrf, page 6 itraceroute6 vrf encap vlan, page 7 itraceroute6 vrf encap vxlan dst-mac, page 8 itraceroute vrf, page 9 itraceroute vrf encap
iping, page 2 iping6, page 4 itraceroute, page 5 itraceroute6 vrf, page 6 itraceroute6 vrf encap vlan, page 7 itraceroute6 vrf encap vxlan dst-mac, page 8 itraceroute vrf, page 9 itraceroute vrf encap
SDN Workshop. Contact: WSDN01_v0.1
 SDN Workshop Contact: training@apnic.net WSDN01_v0.1 Issue Date: [Date] Revision: [xx] Segment Routing - Lab SDN Workshop WSDN01_v0.1 Issue Date: [Date] Revision: [xx] Segment Routing Configuration 3 Configuration
SDN Workshop Contact: training@apnic.net WSDN01_v0.1 Issue Date: [Date] Revision: [xx] Segment Routing - Lab SDN Workshop WSDN01_v0.1 Issue Date: [Date] Revision: [xx] Segment Routing Configuration 3 Configuration
Segment Routing MPLS OAM Support
 Segment Routing Operations, Administration, and Maintenance (OAM) helps service providers to monitor label-switched paths (LSPs) and quickly isolate forwarding problems to assist with fault detection and
Segment Routing Operations, Administration, and Maintenance (OAM) helps service providers to monitor label-switched paths (LSPs) and quickly isolate forwarding problems to assist with fault detection and
Easy Virtual Network Configuration Example
 Easy Virtual Network Configuration Example Document ID: 117974 Contributed by Fabrice Ducomble, Cisco TAC Engineer. Aug 04, 2014 Contents Introduction Prerequisites Requirements Components Used Background
Easy Virtual Network Configuration Example Document ID: 117974 Contributed by Fabrice Ducomble, Cisco TAC Engineer. Aug 04, 2014 Contents Introduction Prerequisites Requirements Components Used Background
Cisco IOS LISP Application Note Series: Lab Testing Guide
 Cisco IOS LISP Application Note Series: Lab Testing Guide Version 3.0 (28 April 2011) Background The LISP Application Note Series provides targeted information that focuses on the integration configuration
Cisco IOS LISP Application Note Series: Lab Testing Guide Version 3.0 (28 April 2011) Background The LISP Application Note Series provides targeted information that focuses on the integration configuration
Implementing Access Lists and Prefix Lists
 An access control list (ACL) consists of one or more access control entries (ACE) that collectively define the network traffic profile. This profile can then be referenced by Cisco IOS XR softwarefeatures
An access control list (ACL) consists of one or more access control entries (ACE) that collectively define the network traffic profile. This profile can then be referenced by Cisco IOS XR softwarefeatures
Mediant MSBR. Version 6.8. Security Setup. Configuration Guide. Version 6.8. AudioCodes Family of Multi-Service Business Routers (MSBR)
 Configuration Guide AudioCodes Family of Multi-Service Business Routers (MSBR) Mediant MSBR Security Setup Version 6.8 Version 6.8 May 2014 Document # LTRT-31640 Configuration Guide Contents Table of
Configuration Guide AudioCodes Family of Multi-Service Business Routers (MSBR) Mediant MSBR Security Setup Version 6.8 Version 6.8 May 2014 Document # LTRT-31640 Configuration Guide Contents Table of
DMVPN to Group Encrypted Transport VPN Migration
 DMVPN to Group Encrypted Transport VPN Migration This document provides the steps for Dynamic Multipoint VPN (DMVPN) to Group Encrypted Transport VPN migration. DMVPN to Group Encrypted Transport VPN Migration
DMVPN to Group Encrypted Transport VPN Migration This document provides the steps for Dynamic Multipoint VPN (DMVPN) to Group Encrypted Transport VPN migration. DMVPN to Group Encrypted Transport VPN Migration
Configuring WCCPv2. Information About WCCPv2. Send document comments to CHAPTER
 CHAPTER 5 This chapter describes how to configure the Web Cache Communication Protocol version 2 (WCCPv2) on Cisco NX-OS devices. This chapter includes the following sections: Information About WCCPv2,
CHAPTER 5 This chapter describes how to configure the Web Cache Communication Protocol version 2 (WCCPv2) on Cisco NX-OS devices. This chapter includes the following sections: Information About WCCPv2,
IP SLAs QFP Time Stamping
 This module describes how to configure the IP SLA QFP Time Stamping feature for IP Service Level Agreements (SLAs) UDP jitter operations. This new probe and responder structure enables more accurate network
This module describes how to configure the IP SLA QFP Time Stamping feature for IP Service Level Agreements (SLAs) UDP jitter operations. This new probe and responder structure enables more accurate network
Configuring ARP CHAPTER 5
 CHAPTER 5 This chapter describes how the Address Resolution Protocol (ARP) on the Cisco 4700 Series Application Control Engine (ACE) appliance can manage and learn the mapping of IP to Media Access Control
CHAPTER 5 This chapter describes how the Address Resolution Protocol (ARP) on the Cisco 4700 Series Application Control Engine (ACE) appliance can manage and learn the mapping of IP to Media Access Control
Traffic Mirroring Commands on the Cisco IOS XR Software
 Traffic Mirroring Commands on the Cisco IOS XR Software This module describes the commands used to configure and monitor traffic mirroring. acl, page 2 clear monitor-session counters, page 4 destination
Traffic Mirroring Commands on the Cisco IOS XR Software This module describes the commands used to configure and monitor traffic mirroring. acl, page 2 clear monitor-session counters, page 4 destination
Segment Routing MPLS OAM Support
 Segment Routing Operations, Administration, and Maintenance (OAM) helps service providers to monitor label-switched paths (LSPs) and quickly isolate forwarding problems to assist with fault detection and
Segment Routing Operations, Administration, and Maintenance (OAM) helps service providers to monitor label-switched paths (LSPs) and quickly isolate forwarding problems to assist with fault detection and
IPv6 Tunnel through an IPv4 Network
 IPv6 Tunnel through an IPv4 Network Document ID: 25156 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations (Manual IPv6 Mode) Configurations
IPv6 Tunnel through an IPv4 Network Document ID: 25156 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations (Manual IPv6 Mode) Configurations
Cisco Configuring Hub and Spoke Frame Relay
 Table of Contents Configuring Hub and Spoke Frame Relay...1 Introduction...1 Before You Begin...1 Conventions...1 Prerequisites...1 Components Used...1 Configure...1 Network Diagram...2 Configurations...2
Table of Contents Configuring Hub and Spoke Frame Relay...1 Introduction...1 Before You Begin...1 Conventions...1 Prerequisites...1 Components Used...1 Configure...1 Network Diagram...2 Configurations...2
How to Verify Cisco Express Forwarding Switching
 How to Verify Cisco Express Forwarding Switching Document ID: 47205 Contents Introduction Prerequisites Requirements Components Used Conventions What Is Cisco IOS Switching? Verification Steps Understand
How to Verify Cisco Express Forwarding Switching Document ID: 47205 Contents Introduction Prerequisites Requirements Components Used Conventions What Is Cisco IOS Switching? Verification Steps Understand
Implementing Management Plane Protection
 The Management Plane Protection (MPP) feature in Cisco IOS XR software provides the capability to restrict the interfaces on which network management packets are allowed to enter a device. The MPP feature
The Management Plane Protection (MPP) feature in Cisco IOS XR software provides the capability to restrict the interfaces on which network management packets are allowed to enter a device. The MPP feature
EIGRP on SVTI, DVTI, and IKEv2 FlexVPN with the "IP[v6] Unnumbered" Command Configuration Example
![EIGRP on SVTI, DVTI, and IKEv2 FlexVPN with the IP[v6] Unnumbered Command Configuration Example EIGRP on SVTI, DVTI, and IKEv2 FlexVPN with the IP[v6] Unnumbered Command Configuration Example](/thumbs/92/108645128.jpg) EIGRP on SVTI, DVTI, and IKEv2 FlexVPN with the "IP[v6] Unnumbered" Command Configuration Example Document ID: 116346 Contributed by Michal Garcarz and Olivier Pelerin, Cisco TAC Engineers. Sep 18, 2013
EIGRP on SVTI, DVTI, and IKEv2 FlexVPN with the "IP[v6] Unnumbered" Command Configuration Example Document ID: 116346 Contributed by Michal Garcarz and Olivier Pelerin, Cisco TAC Engineers. Sep 18, 2013
Configuring Cisco Performance Monitor
 This document contains information about and instructions for configuring Cisco Performance Monitor. Finding Feature Information, page 1 Information About Cisco Performance Monitor, page 1 Restrictions
This document contains information about and instructions for configuring Cisco Performance Monitor. Finding Feature Information, page 1 Information About Cisco Performance Monitor, page 1 Restrictions
Lab Troubleshooting Using traceroute Instructor Version 2500
 Lab 9.3.4 Troubleshooting Using traceroute Instructor Version 2500 294-833 CCNA 2: Routers and Routing Basics v 3.1 - Lab 9.3.4 Copyright 2003, Cisco Systems, Inc. Objective Use the traceroute Cisco IOS
Lab 9.3.4 Troubleshooting Using traceroute Instructor Version 2500 294-833 CCNA 2: Routers and Routing Basics v 3.1 - Lab 9.3.4 Copyright 2003, Cisco Systems, Inc. Objective Use the traceroute Cisco IOS
Configuring IS IS over IPv6
 Configuring IS IS over IPv6 Document ID: 40262 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations Verify Troubleshoot Troubleshooting
Configuring IS IS over IPv6 Document ID: 40262 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations Verify Troubleshoot Troubleshooting
AVC Configuration. Unified Policy CLI CHAPTER
 CHAPTER 3 Revised: February 7, 2013, This chapter addresses AVC configuration and includes the following topics: Unified Policy CLI, page 3-1 Metric Producer Parameters, page 3-2 Reacts, page 3-2 NetFlow/IPFIX
CHAPTER 3 Revised: February 7, 2013, This chapter addresses AVC configuration and includes the following topics: Unified Policy CLI, page 3-1 Metric Producer Parameters, page 3-2 Reacts, page 3-2 NetFlow/IPFIX
Chapter 5 Lab 5-1 Inter-VLAN Routing INSTRUCTOR VERSION
 CCNPv7.1 SWITCH Chapter 5 Lab 5-1 Inter-VLAN Routing INSTRUCTOR VERSION Topology Objectives Implement a Layer 3 EtherChannel Implement Static Routing Implement Inter-VLAN Routing Background Cisco's switching
CCNPv7.1 SWITCH Chapter 5 Lab 5-1 Inter-VLAN Routing INSTRUCTOR VERSION Topology Objectives Implement a Layer 3 EtherChannel Implement Static Routing Implement Inter-VLAN Routing Background Cisco's switching
RealCiscoLAB.com. Chapter 6 Lab 6-1, Configuring BGP with Default Routing. Configure BGP to exchange routing information with two ISPs.
 RealCiscoLAB.com CCNPv6 ROUTE Chapter 6 Lab 6-1, Configuring BGP with Default Routing Topology Objectives Background Configure BGP to exchange routing information with two ISPs. The International Travel
RealCiscoLAB.com CCNPv6 ROUTE Chapter 6 Lab 6-1, Configuring BGP with Default Routing Topology Objectives Background Configure BGP to exchange routing information with two ISPs. The International Travel
GETVPN+LISP Lab Guide
 GETVPN+LISP Lab Guide Developers and Lab Proctors This lab was created by: Gregg Schudel, TME LISP Development Team Version 1.0: Created by Gregg Schudel Lab proctor: Gregg Schudel (gschudel@cisco.com)
GETVPN+LISP Lab Guide Developers and Lab Proctors This lab was created by: Gregg Schudel, TME LISP Development Team Version 1.0: Created by Gregg Schudel Lab proctor: Gregg Schudel (gschudel@cisco.com)
Punt Policing and Monitoring
 Punt policing protects the Route Processor (RP) from having to process noncritical traffic, which increases the CPU bandwidth available to critical traffic. Traffic is placed into different CPU queues
Punt policing protects the Route Processor (RP) from having to process noncritical traffic, which increases the CPU bandwidth available to critical traffic. Traffic is placed into different CPU queues
Interchassis Asymmetric Routing Support for Zone-Based Firewall and NAT
 Interchassis Asymmetric Routing Support for Zone-Based Firewall and NAT The Interchassis Asymmetric Routing Support for Zone-Based Firewall and NAT feature supports the forwarding of packets from a standby
Interchassis Asymmetric Routing Support for Zone-Based Firewall and NAT The Interchassis Asymmetric Routing Support for Zone-Based Firewall and NAT feature supports the forwarding of packets from a standby
Network Address Translation Bindings
 In Network Address Translation (NAT), the term binding describes the address binding between a local address and the global address to which the local address is translated. A binding is also called a
In Network Address Translation (NAT), the term binding describes the address binding between a local address and the global address to which the local address is translated. A binding is also called a
Implement Static Routes for IPv6 Configuration Example
 Implement Static Routes for IPv6 Configuration Example Document ID: 113361 Contents Introduction Prerequisites Components Used Conventions Configure Network Diagram Configurations Verify Related Information
Implement Static Routes for IPv6 Configuration Example Document ID: 113361 Contents Introduction Prerequisites Components Used Conventions Configure Network Diagram Configurations Verify Related Information
Configuring Data Export for Flexible NetFlow with Flow Exporters
 Configuring Data Export for Flexible NetFlow with Flow Exporters Last Updated: September 4, 2012 This document contains information about and instructions for configuring flow exporters to export Flexible
Configuring Data Export for Flexible NetFlow with Flow Exporters Last Updated: September 4, 2012 This document contains information about and instructions for configuring flow exporters to export Flexible
Configuring ARP CHAPTER4
 CHAPTER4 This chapter describes how the Address Resolution Protocol (ARP) on the ACE can manage and learn the mapping of IP to Media Access Control (MAC) information to forward and transmit packets. The
CHAPTER4 This chapter describes how the Address Resolution Protocol (ARP) on the ACE can manage and learn the mapping of IP to Media Access Control (MAC) information to forward and transmit packets. The
Throughput Issues on ASR1000 Series Router
 Throughput Issues on ASR1000 Series Router Contents Introduction Prerequisites Requirements Components Used Conventions Problem Solution Scenario 1. High Bandwidth Ingress Interface(s) and Low Bandwidth
Throughput Issues on ASR1000 Series Router Contents Introduction Prerequisites Requirements Components Used Conventions Problem Solution Scenario 1. High Bandwidth Ingress Interface(s) and Low Bandwidth
Configuring Routes on the ACE
 CHAPTER2 This chapter describes how the ACE is considered a router hop in the network when it is in routed mode. In the Admin or user contexts, the ACE supports static routes only. The ACE supports up
CHAPTER2 This chapter describes how the ACE is considered a router hop in the network when it is in routed mode. In the Admin or user contexts, the ACE supports static routes only. The ACE supports up
Configuration Example of ASA VPN with Overlapping Scenarios Contents
 Configuration Example of ASA VPN with Overlapping Scenarios Contents Introduction Prerequisites Requirements Components Used Background Information Translation on both VPN Endpoints ASA 1 Create the necessary
Configuration Example of ASA VPN with Overlapping Scenarios Contents Introduction Prerequisites Requirements Components Used Background Information Translation on both VPN Endpoints ASA 1 Create the necessary
Lab Configuring Port Address Translation (PAT) (Instructor Version)
 (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Topology Addressing Table Objectives Device Interface IP Address Subnet Mask
(Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Topology Addressing Table Objectives Device Interface IP Address Subnet Mask
Dynamic Multipoint VPN (DMVPN) Troubleshooting Scenarios
 Dynamic Multipoint VPN (DMVPN) Troubleshooting Scenarios Luke Bibby, CCIE #45527 Introduction This small workbook is meant to provide additional practice with troubleshooting Dynamic Multipoint VPN (DMVPN)
Dynamic Multipoint VPN (DMVPN) Troubleshooting Scenarios Luke Bibby, CCIE #45527 Introduction This small workbook is meant to provide additional practice with troubleshooting Dynamic Multipoint VPN (DMVPN)
RFC 430x IPsec Support
 The includes features Phase 1 and RFC430x IPsec Support Phase 2 that implement Internet Key Exchange (IKE) and IPsec behavior as specified in RFC 4301. Finding Feature Information, page 1 Information About,
The includes features Phase 1 and RFC430x IPsec Support Phase 2 that implement Internet Key Exchange (IKE) and IPsec behavior as specified in RFC 4301. Finding Feature Information, page 1 Information About,
Cisco ASR 1000 Series Aggregation Services Routers: QoS Architecture and Solutions
 Cisco ASR 1000 Series Aggregation Services Routers: QoS Architecture and Solutions Introduction Much more bandwidth is available now than during the times of 300-bps modems, but the same business principles
Cisco ASR 1000 Series Aggregation Services Routers: QoS Architecture and Solutions Introduction Much more bandwidth is available now than during the times of 300-bps modems, but the same business principles
Introduction to Routers and LAN Switches
 Introduction to Routers and LAN Switches Session 3048_05_2001_c1 2001, Cisco Systems, Inc. All rights reserved. 3 Prerequisites OSI Model Networking Fundamentals 3048_05_2001_c1 2001, Cisco Systems, Inc.
Introduction to Routers and LAN Switches Session 3048_05_2001_c1 2001, Cisco Systems, Inc. All rights reserved. 3 Prerequisites OSI Model Networking Fundamentals 3048_05_2001_c1 2001, Cisco Systems, Inc.
LAN Switching Configuration Guide
 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387) Fax: 408 527-0883 THE SPECIFICATIONS AND INFORMATION
Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387) Fax: 408 527-0883 THE SPECIFICATIONS AND INFORMATION
IEEE 802.1Q Tunneling (QinQ) and L2PT on L2 Ports
 IEEE 802.1Q Tunneling (QinQ) and L2PT on L2 Ports Revised: July 27, 2012 OL-20468-02 First Published: November 11, 2011 Last Updated: July 27, 2012 This feature provides Layer 2 Tunneling support for QinQ
IEEE 802.1Q Tunneling (QinQ) and L2PT on L2 Ports Revised: July 27, 2012 OL-20468-02 First Published: November 11, 2011 Last Updated: July 27, 2012 This feature provides Layer 2 Tunneling support for QinQ
