Chapter 10 Lab 10-2, Securing VLANs INSTRUCTOR VERSION
|
|
|
- Audrey Porter
- 6 years ago
- Views:
Transcription
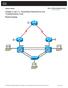
1 CCNPv7.1 SWITCH Chapter 10 Lab 10-2, Securing VLANs INSTRUCTOR VERSION Topology Objectives Background Secure the server farm using private VLANs. Secure the staff VLAN from the student VLAN. Secure the staff VLAN when temporary staff personnel are used. In this lab, you will configure the network to protect the VLANs using router ACLs, VLAN ACLs, and private VLANs. First, you will secure the new server farm (Host C) by using private VLANs. Service providers use private VLANs to separate different customers traffic while utilizing the same parent VLAN for all server traffic. The private VLANs provide traffic isolation between devices, even though they might exist on the same VLAN. You will then secure the staff VLAN from the student VLAN by using a RACL, which prevents traffic from the student VLAN from reaching the staff VLAN. This allows the student traffic to utilize the network and Internet services while keeping the students from accessing any of the staff resources Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 22
2 Lastly, you will configure a VACL that allows a host on the staff network to be set up to use the VLAN for access but keeps the host isolated from the rest of the staff machines. This machine is used by temporary staff employees. Note: This lab uses Cisco Catalyst 3560 and 2960 switches running Cisco IOS 15.0(2) IP Services and LAN Base images, respectively. The 3560 and 2960 switches are configured with the SDM templates dual-ipv4- and-ipv6 routing and lanbase-routing, respectively. Depending on the switch model and Cisco IOS Software version, the commands available and output produced might vary from what is shown in this lab. Catalyst 3650 switches (running any Cisco IOS XE release) and Catalyst 2960-Plus switches (running any supported Cisco IOS image) can be used in place of the Catalyst 3560 switches and the Catalyst 2960 switches. Required Resources 2 switches (Cisco 2960 with the Cisco IOS Release 15.0(2)SE6 C2960-LANBASEK9-M image or comparable) 2 switches (Cisco 3560 with the Cisco IOS Release 15.0(2)SE6 C3560-IPSERVICESK9-M image or comparable) 4 PCs Ethernet and console cables Prepare the switches for the lab The instructions in this lab assume that the switches are running using the final configuration from Lab 10-1 "Securing Layer 2 Switches". Part 1: Configure private VLANs. Private VLANs are an option when you have multiple devices in the same broadcast domain, but need to prevent them from communicating from each other. A good example is in a server farm where the servers do not need to receive other server's broadcast traffic. In a sense, private VLANs allow you to sub-divide the layer 2 broadcast domain. You are able to associate a primary VLAN with multiple secondary VLANs, while using the same IP address space for all of the devices. Secondary VLANs are defined as one of two types; either COMMUNITY or ISOLATED. A secondary community VLAN allows the hosts within the VLAN to communicate with one another and the primary VLAN. A secondary isolated VLAN does not allow hosts to communicate with others in the same isolated VLAN. They can only communicate with the primary VLAN. A primary VLAN can have multiple secondary community VLANs associated with it, but only one secondary isolated VLAN. Step 1: Configure VTP VTP version 2 does not support PVLANs, so any switches that must host a PVLAN port have to be in transparent mode and the PVLANs have to be manually configured. VTP version 3 does support PVLANs, so the configuration only has to be done in one place. a. Convert all switches to VTP version 3, and configure a VTP password of cisco123. Configure all four switches. An example of DLS1 configuration follows: DLS1(config)# vtp version 3 Aug 4 12:39:11.944: %SW_VLAN-6-OLD_CONFIG_FILE_READ: Old version 2 VLAN configuration file detected and read OK. Version 3 files will be written in the future. DLS1(config)# vtp password cisco Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 2 of 22
3 Setting device VTP password to cisco123 DLS1(config)# exit b. Configure DLS1 to be the primary switch for VLANs. DLS1# vtp primary vlan This system is becoming primary server for feature vlan No conflicting VTP3 devices found. Do you want to continue? [confirm] DLS1# Aug 4 12:40:44.680: %SW_VLAN-4-VTP_PRIMARY_SERVER_CHG: e f.7280 has become the primary server for the VLAN VTP feature DLS1# Step 2: Configure the Primary Private VLAN a. Based on the topology diagram, VLAN 150 will be used as the VLAN for the new server farm. On VTP server DLS1, add VLAN 150, name the VLAN server-farm and exit vlan config mode. This allows VLAN 150 to be propagated to the other switches in the network. In addition, configure DLS1 as the root bridge for VLANs 150, 151, and 152. DLS1(config)# vlan 150 DLS1(config-vlan)# name SERVER-FARM DLS1(config-vlan)# exit DLS1(config)# spanning-tree vlan root primary b. Once this is complete, verify that VLAN 150 is preset in the database on DLS2. Step 2: Configure interface VLAN 150 at DLS1 and DLS2: DLS1(config)# interface vlan 150 DLS1(config-if)# ip address DLS2(config)# interface vlan 150 DLS2(config-if)# ip add Step 3: Create the PVLANs on the VTP server a. Configure the new PVLANs on DLS1. Secondary PVLAN 151 is an isolated VLAN, while secondary PVLAN 152 is used as a community PVLAN. Configure these new PVLANs and associate them with primary VLAN 150. DLS1(config)# vlan 151 DLS1(config-vlan)# private-vlan isolated DLS1(config-vlan)# exit DLS1(config)# vlan 152 DLS1(config-vlan)# private-vlan community DLS1(config-vlan)# exit DLS1(config)# vlan 150 DLS1(config-vlan)# private-vlan primary DLS1(config-vlan)# private-vlan association 151,152 DLS1(config-vlan)# exit DLS1(config)# b. Verify the PVLANs propagate to the other switches Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 3 of 22
4 DLS2# show vlan brief include active 1 default active Fa0/1, Fa0/2, Fa0/3, Fa0/4 99 Management active 100 STAFF active 150 SERVER-FARM active 151 VLAN0151 active 152 VLAN0152 active 200 STUDENTS active 666 NATIVE_DO_NOT_USE active c. Verify the creation of the secondary PVLANs and their association with the primary VLAN using the show vlan private-vlan command. Note that no ports are currently associated with these VLANs. This is expected behavior. DLS1#show vlan private-vlan Primary Secondary Type Ports isolated community DLS2# show vlan private-vlan Primary Secondary Type Ports isolated community Step 4: Configure support for routing of PVLANs The private-vlan mapping interface configuration command permits PVLAN traffic to be switched through Layer 3. Normally you would include all the secondary VLANs to allow for HSRP to work, but for this example we will not include a mapping VLAN 151 on DLS2 so we can demonstrate the isolation of VLAN 151. Configure these commands for interface VLAN 150 on DLS1 and DLS2. DLS1(config)# interface vlan 150 DLS1(config-if)# private-vlan mapping DLS1(config-if)# end DLS2(config)# interface vlan 150 DLS2(config-if)# private-vlan mapping 152 DLS2(config-if)# end Will hosts assigned to ports on private VLAN 151 be able to communicate directly with each other? Step 5: Configure host access to PVLANs a. On DLS1, configure interface FastEthernet 0/6 so it is in private-vlan host mode and has association to VLAN 150: 2015 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 4 of 22
5 DLS1(config)# interface fastethernet 0/6 DLS1(config-if)# switchport mode private-vlan host DLS1(config-if)# switchport private-vlan host-association DLS1(config-if)# exit b. Use the show vlan private-vlan command and note that the ports configured are currently associated with these VLANs. DLS1#show vlan private-vlan Primary Secondary Type Ports isolated community Fa0/6 c. On DLS2, configure the Fast Ethernet ports that are associated with the server farm private VLANs. Fast Ethernet port 0/6 is used for the secondary isolated PVLAN 151, and ports 0/18 0/20 are used for the secondary community VLAN 152. The switchport mode private-vlan host command sets the mode on the interface and the switchport private-vlan host-association primary-vlan-id secondary-vlan-id command assigns the appropriate VLANs to the interface. The following commands configure the PVLANs on DLS2. DLS2(config)# interface fastethernet 0/6 DLS2(config-if)# switchport mode private-vlan host DLS2(config-if)# switchport private-vlan host-association DLS2(config-if)# exit DLS2(config)# interface range fa0/18-20 DLS2(config-if-range)# switchport mode private-vlan host DLS2(config-if-range)# switchport private-vlan host-association As servers are added to Fast Ethernet 0/18 20, will these servers be allowed to hear broadcasts from each other? Explain. d. Use the show vlan private-vlan command and note that the ports configured are currently associated with these VLANs. DLS2# show vlan private-vlan Primary Secondary Type Ports isolated Fa0/ community Fa0/18, Fa0/19, Fa0/20 e. Configure HOST C on DLS1 interface f0/6 with the IP address /24. Use as the default gateway address. f. Configure HOST D on DLS2 interface f0/6 with the IP address /24. Use as the default gateway address Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 5 of 22
6 Step 6: Verify PVLANs are working a. From HOST C, try to ping the following addresses - they should all work: (DLS1), (DLS2), (ALS1). b. From HOST C, try to ping HOST D ( ). This should NOT work. c. From HOST D, try to ping the following addresses - they should all work: (DLS1), (ALS1). d. From HOST D, try to ping (DLS2). This should NOT work. Part 3: RACLs. You can use router access control lists (RACLs) to separate the student and staff VLANs. In this lab scenario, write an ACL that allows the staff VLAN (100) to access the student VLAN (200), and deny student VLAN access to the staff VLAN. Step 1: Write an extended IP access list Write an ACL that meets the requirement and assign the access list to the appropriate VLAN interfaces on DLS1 and DLS2 using the ip access-group acl-num {in out} command. DLS1(config)# access-list 100 permit tcp established DLS1(config)# access-list 100 permit icmp echo-reply DLS1(config)# access-list 100 deny ip DLS1(config)# access-list 100 permit ip any any DLS1(config)# interface vlan 200 DLS1(config-if)# ip access-group 100 in DLS1(config-if)# exit DLS2(config)# access-list 100 permit tcp established DLS2(config)# access-list 100 permit icmp echo-reply DLS(config)# access-list 100 deny ip DLS2(config)# access-list 100 permit ip any any DLS2(config)# interface vlan 100 DLS2(config-if)# ip access-group 100 in DLS2(config)# interface vlan 200 DLS2(config-if)# ip access-group 100 in DLS2(config-if)# exit e. Check the configuration using the show ip access-list and show ip interface vlan vlan-id commands. DLS1# show access-lists Extended IP access list permit tcp established 20 permit icmp echo-reply 30 deny ip permit ip any any DLS1# show ip interface vlan Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 6 of 22
7 Vlan100 is up, line protocol is up Internet address is /24 Broadcast address is Address determined by non-volatile memory MTU is 1500 bytes Helper address is not set Directed broadcast forwarding is disabled Multicast reserved groups joined: Outgoing access list is not set Inbound access list is 100 <output omitted> f. After the access list has been applied verify the configuration in one of the following ways. Option 1 using real hosts is preferred. Option 1: Lab 10-1 finished with ALS1 F0/6 assigned to VLAN 200. Change this assignment to VLAN 100. Host A should be connected to ALS1 F0/6 and assigned the IP address /24 with default gateway from Lab If not, set Host A up with those parameters. Host B should be connected to ALS2 F0/6 from Lab 10-1 as well, but its last configuration in that lab was to use DHCP, so assign a static IP address Connect host PC-B to ALS2 port Fa0/6 in student VLAN 200 and assign it IP address /24 with default gateway Ping the staff host from the student host. This ping should fail. Then ping the student host from the staff host. This ping should succeed. Option 2: On ALS1 set up a simulated host in VLAN 100 and one in VLAN 200 by creating a VLAN 100 and 200 interface on the switch. Give the VLAN 100 interface an IP address in VLAN 100. Give the VLAN 200 interface an IP address in VLAN 200. The following is a sample configuration on ALS1. ALS1(config)# int vlan 100 ALS1(config-if)# ip address ALS1(config)# int vlan 200 ALS1(config-if)# ip address Ping the interface of the gateway for the staff VLAN ( ) with a source of staff VLAN 100 ( ) and then ping with a source of student VLAN 200. The pings from the student VLAN should fail. ALS1# ping source vl100 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to , timeout is 2 seconds: Packet sent with a source address of !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 1/205/1007 ms ALS1# ping source vl200 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to , timeout is 2 seconds: Packet sent with a source address of U.U Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 7 of 22
8 Success rate is 0 percent (0/5) What does a U signify in the output of the ping command? Part 4: Configure VACLs. Configure the network so that the temporary staff host cannot access the rest of the staff VLAN, yet still be able to use the default gateway of the staff subnet to connect to the rest of the network and the ISP. You can accomplish this task by using a VLAN ACL (VACL). For this scenario, Host C (DLS1 Fast Ethernet 0/6) will act as a temporary staff PC, therefore the VACL must be placed on DLS1. Step 1: Configure DLS1 F0/6 and Host C a. Change the configuration of DLS1 F0/6 so that the interface is associated with VLAN 100. To keep things tidy, also remove the private vlan mapping on the interface as well: DLS1(config)#interface f0/6 DLS1(config-if)# DLS1(config-if)# DLS1(config-if)#no switchport private-vlan host-association DLS1(config-if)#exit b. Change the configuration of HOST C so that it is using the IP address /24 with the default gateway set as Step 2: Configure and apply the VACL a. Configure an access list on DLS1 called temp-host using the ip access-list extended name command. This list defines the traffic between the host and the rest of the network. Then define the traffic using the permit ip host ip-address subnet wildcard-mask command. Note that you must be explicit about what traffic to match -- this isn't a traffic filtering ACL, it is a traffic matching ACL. If you were to leave the second line of the example below out, pings would work. DLS1(config)# ip access-list extended temp-host DLS1(config-ext-nacl)# permit ip host DLS1(config-ext-nacl)# permit icmp host DLS1(config-ext-nacl)# exit b. The VACL is defined using a VLAN access map. Access maps are evaluated in a numbered sequence. To set up an access map, use the vlan access-map map-name seq# command. The following configuration defines an access map named block-temp, which uses the match statement to match the traffic defined in the access list and denies that traffic. You also need to add a line to the access map that allows all other traffic. If this line is not added, an implicit deny catches all other traffic and denies it. DLS1(config)# vlan access-map block-temp 10 DLS1(config-access-map)# match ip address temp-host DLS1(config-access-map)# action drop 2015 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 8 of 22
9 DLS1(config-access-map)# vlan access-map block-temp 20 DLS1(config-access-map)# action forward DLS1(config-access-map)# exit c. Define which VLANs the access map should be applied to using the vlan filter map-name vlan-list vlan- ID command. DLS1(config)# vlan filter block-temp vlan-list 100 d. Verify the VACL configuration using the show vlan access-map command on DLS1. DLS1# show vlan access-map Vlan access-map "block-temp" 10 Match clauses: ip address: temp-host Action: drop Vlan access-map "block-temp" 20 Match clauses: Action: forward Step 3: Test the VACL a. From HOST C, try to ping to HOST A on ALS1 ( ). The ping should fail. b. From HOST C, try to ping the default gateway ( ). The ping should fail. c. From HOST C, try to ping Host D ( ). The ping should succeed. Step 4: End of Lab Do not save your configurations. The equipment will be reset for the next lab Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 9 of 22
10 Device Configurations: Below are the final configurations for each switch. (NOTE: Be aware that some of the configuration elements presented here are left over from the final configuration in Lab 10-1) DLS1: DLS1# show run exclude! Building configuration... Current configuration : 4486 bytes version 15.0 no service pad service timestamps debug datetime msec service timestamps log datetime msec no service password-encryption hostname DLS1 boot-start-marker boot-end-marker enable secret 5 $1$nALw$wcxoHd/vGTaOMWVKSc3qH. username lastditch privilege 15 password 0 $cisco123& aaa new-model aaa authentication login REMOTE-CONTROL group radius local aaa session-id common clock timezone CST -6 0 clock summer-time CDT recurring system mtu routing 1500 ip routing no ip domain-lookup ip domain-name CCNP.NET spanning-tree mode pvst spanning-tree extend system-id spanning-tree vlan , priority spanning-tree vlan 200 priority vlan access-map block-temp 10 match ip address temp-host action drop vlan access-map block-temp 20 action forward vlan filter block-temp vlan-list 100 vlan internal allocation policy ascending interface FastEthernet0/1 interface FastEthernet0/2 interface FastEthernet0/3 interface FastEthernet0/4 interface FastEthernet0/5 interface FastEthernet0/ Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 10 of 22
11 interface FastEthernet0/7 interface FastEthernet0/8 interface FastEthernet0/9 interface FastEthernet0/10 interface FastEthernet0/11 interface FastEthernet0/12 interface FastEthernet0/13 interface FastEthernet0/14 interface FastEthernet0/15 interface FastEthernet0/16 interface FastEthernet0/17 interface FastEthernet0/18 interface FastEthernet0/19 interface FastEthernet0/20 interface FastEthernet0/ Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 11 of 22
12 interface FastEthernet0/22 interface FastEthernet0/23 interface FastEthernet0/24 interface GigabitEthernet0/1 interface GigabitEthernet0/2 interface Vlan1 no ip address interface Vlan99 ip address standby 0 preempt standby 99 ip standby 99 priority 150 interface Vlan100 ip address standby 100 ip standby 100 priority 150 standby 100 preempt interface Vlan150 ip address private-vlan mapping interface Vlan200 ip address ip access-group 100 in ip helper-address standby 200 ip standby 200 preempt ip http server ip http secure-server ip access-list extended temp-host permit ip host permit icmp host access-list 100 permit tcp established access-list 100 permit icmp echo-reply access-list 100 deny ip access-list 100 permit ip any any radius server RADIUS address ipv auth-port 1812 acct-port 1813 key WinRadius line con 0 exec-timeout 0 0 logging synchronous line vty Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 12 of 22
13 password cisco login authentication REMOTE-CONTROL line vty 5 15 password cisco ntp master 10 end DLS1# DLS2: DLS2# show run exclude! Building configuration... Current configuration : 3954 bytes version 15.0 no service pad service timestamps debug datetime msec service timestamps log datetime msec no service password-encryption hostname DLS2 boot-start-marker boot-end-marker enable secret 5 $1$ZyiH$/CWGDDDbxTAP5qxnFdfo3/ username lastditch privilege 15 password 0 $cisco123& aaa new-model aaa authentication login REMOTE-CONTROL group radius local aaa session-id common clock timezone CST -6 0 clock summer-time CDT recurring system mtu routing 1500 ip routing no ip domain-lookup ip domain-name CCNP.NET spanning-tree mode pvst spanning-tree extend system-id spanning-tree vlan priority spanning-tree vlan 200 priority vlan internal allocation policy ascending interface FastEthernet0/1 interface FastEthernet0/2 interface FastEthernet0/3 interface FastEthernet0/4 interface FastEthernet0/5 interface FastEthernet0/6 switchport private-vlan host-association switchport mode private-vlan host interface FastEthernet0/ Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 13 of 22
14 interface FastEthernet0/8 interface FastEthernet0/9 interface FastEthernet0/10 interface FastEthernet0/11 interface FastEthernet0/12 interface FastEthernet0/13 interface FastEthernet0/14 interface FastEthernet0/15 interface FastEthernet0/16 interface FastEthernet0/17 interface FastEthernet0/18 switchport private-vlan host-association switchport mode private-vlan host interface FastEthernet0/19 switchport private-vlan host-association switchport mode private-vlan host interface FastEthernet0/20 switchport private-vlan host-association switchport mode private-vlan host interface FastEthernet0/21 interface FastEthernet0/22 interface FastEthernet0/23 interface FastEthernet0/24 interface GigabitEthernet0/ Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 14 of 22
15 interface GigabitEthernet0/2 interface Vlan1 no ip address interface Vlan99 ip address standby 0 preempt standby 99 ip interface Vlan100 ip address ip access-group 100 in standby 100 ip standby 100 preempt interface Vlan150 ip address private-vlan mapping 152 interface Vlan200 ip address ip access-group 100 in standby 200 ip standby 200 priority 150 standby 200 preempt ip http server ip http secure-server access-list 100 permit tcp established access-list 100 permit icmp echo-reply access-list 100 deny ip access-list 100 permit ip any any radius server RADIUS address ipv auth-port 1812 acct-port 1813 key WinRadius line con 0 exec-timeout 0 0 logging synchronous line vty 0 4 password cisco login authentication REMOTE-CONTROL line vty 5 15 password cisco ntp server end DLS2# ALS1: ALS1# show run exclude! Building configuration... Current configuration : 6870 bytes version 15.0 no service pad service timestamps debug datetime msec service timestamps log datetime msec 2015 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 15 of 22
16 no service password-encryption hostname ALS1 boot-start-marker boot-end-marker enable secret 5 $1$vsgl$SlBwgh5y6we8hINmVADaH. username lastditch privilege 15 password 0 $cisco123& aaa new-model aaa authentication login REMOTE-CONTROL group radius local aaa session-id common clock timezone CST -6 0 clock summer-time CDT recurring system mtu routing 1500 ip dhcp snooping vlan 100,200 ip dhcp snooping no ip domain-lookup ip domain-name CCNP.NET errdisable recovery cause psecure-violation errdisable recovery interval 30 spanning-tree mode pvst spanning-tree extend system-id vlan internal allocation policy ascending interface FastEthernet0/1 interface FastEthernet0/2 interface FastEthernet0/3 interface FastEthernet0/4 interface FastEthernet0/5 interface FastEthernet0/6 maximum 2 mac-address sticky mac-address sticky 000c.2915.ab9d storm-control broadcast level pps 1k 300 storm-control multicast level storm-control unicast level storm-control action trap interface FastEthernet0/7 interface FastEthernet0/8 interface FastEthernet0/ Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 16 of 22
17 interface FastEthernet0/10 interface FastEthernet0/11 interface FastEthernet0/12 interface FastEthernet0/13 interface FastEthernet0/14 interface FastEthernet0/15 maximum 2 mac-address sticky storm-control broadcast level pps 1k 300 storm-control multicast level storm-control unicast level storm-control action trap interface FastEthernet0/16 maximum 2 mac-address sticky storm-control broadcast level pps 1k 300 storm-control multicast level storm-control unicast level storm-control action trap interface FastEthernet0/17 maximum 2 mac-address sticky storm-control broadcast level pps 1k 300 storm-control multicast level storm-control unicast level storm-control action trap 2015 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 17 of 22
18 interface FastEthernet0/18 maximum 2 mac-address sticky storm-control broadcast level pps 1k 300 storm-control multicast level storm-control unicast level storm-control action trap interface FastEthernet0/19 maximum 2 mac-address sticky storm-control broadcast level pps 1k 300 storm-control multicast level storm-control unicast level storm-control action trap interface FastEthernet0/20 maximum 2 mac-address sticky storm-control broadcast level pps 1k 300 storm-control multicast level storm-control unicast level storm-control action trap interface FastEthernet0/21 maximum 2 mac-address sticky storm-control broadcast level pps 1k 300 storm-control multicast level storm-control unicast level storm-control action trap interface FastEthernet0/22 maximum 2 mac-address sticky storm-control broadcast level pps 1k 300 storm-control multicast level storm-control unicast level Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 18 of 22
19 storm-control action trap interface FastEthernet0/23 maximum 2 mac-address sticky storm-control broadcast level pps 1k 300 storm-control multicast level storm-control unicast level storm-control action trap interface FastEthernet0/24 maximum 2 mac-address sticky storm-control broadcast level pps 1k 300 storm-control multicast level storm-control unicast level storm-control action trap interface GigabitEthernet0/1 interface GigabitEthernet0/2 interface Vlan1 no ip address interface Vlan99 ip address ip default-gateway ip http server ip http secure-server radius server RADIUS address ipv auth-port 1812 acct-port 1813 key WinRadius line con 0 exec-timeout 0 0 logging synchronous line vty 0 4 password cisco login authentication REMOTE-CONTROL line vty 5 15 password cisco ntp server end ALS1# 2015 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 19 of 22
20 ALS2: ALS2# show run exclude! Building configuration... Current configuration : 4150 bytes version 15.0 no service pad service timestamps debug datetime msec service timestamps log datetime msec no service password-encryption hostname ALS2 boot-start-marker boot-end-marker enable secret 5 $1$n/LD$LmuGHmSGRPgfTrsqf8q7O1 username lastditch privilege 15 password 0 $cisco123& aaa new-model aaa authentication login REMOTE-CONTROL group radius local aaa session-id common clock timezone CST -6 0 clock summer-time CDT recurring system mtu routing 1500 ip dhcp snooping vlan 100,200 ip dhcp snooping no ip domain-lookup ip domain-name CCNP.NET spanning-tree mode pvst spanning-tree extend system-id vlan internal allocation policy ascending interface FastEthernet0/1 interface FastEthernet0/2 interface FastEthernet0/3 interface FastEthernet0/4 interface FastEthernet0/5 interface FastEthernet0/6 switchport access vlan 200 interface FastEthernet0/7 interface FastEthernet0/8 interface FastEthernet0/ Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 20 of 22
21 interface FastEthernet0/10 interface FastEthernet0/11 interface FastEthernet0/12 interface FastEthernet0/13 interface FastEthernet0/14 interface FastEthernet0/15 switchport access vlan 200 interface FastEthernet0/16 switchport access vlan 200 interface FastEthernet0/17 switchport access vlan 200 interface FastEthernet0/18 switchport access vlan 200 interface FastEthernet0/19 switchport access vlan 200 interface FastEthernet0/20 switchport access vlan Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 21 of 22
22 interface FastEthernet0/21 switchport access vlan 200 interface FastEthernet0/22 switchport access vlan 200 interface FastEthernet0/23 switchport access vlan 200 interface FastEthernet0/24 switchport access vlan 200 interface GigabitEthernet0/1 interface GigabitEthernet0/2 interface Vlan1 no ip address interface Vlan99 ip address ip default-gateway ip http server ip http secure-server radius server RADIUS address ipv auth-port 1812 acct-port 1813 key WinRadius line con 0 exec-timeout 0 0 logging synchronous line vty 0 4 password cisco login authentication REMOTE-CONTROL line vty 5 15 password cisco ntp server end ALS Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 22 of 22
Chapter 5 Lab 5-1 Inter-VLAN Routing INSTRUCTOR VERSION
 CCNPv7.1 SWITCH Chapter 5 Lab 5-1 Inter-VLAN Routing INSTRUCTOR VERSION Topology Objectives Implement a Layer 3 EtherChannel Implement Static Routing Implement Inter-VLAN Routing Background Cisco's switching
CCNPv7.1 SWITCH Chapter 5 Lab 5-1 Inter-VLAN Routing INSTRUCTOR VERSION Topology Objectives Implement a Layer 3 EtherChannel Implement Static Routing Implement Inter-VLAN Routing Background Cisco's switching
Chapter 5 Lab 5-2 DHCP INSTRUCTOR VERSION
 CCNPv7.1 SWITCH Chapter 5 Lab 5-2 DHCP INSTRUCTOR VERSION Topology Objectives Configure DHCP for IPv4 Configure Stateless DHCP for IPv6 Configure Stateful DHCP for IPv6 Background To practice the various
CCNPv7.1 SWITCH Chapter 5 Lab 5-2 DHCP INSTRUCTOR VERSION Topology Objectives Configure DHCP for IPv4 Configure Stateless DHCP for IPv6 Configure Stateful DHCP for IPv6 Background To practice the various
Chapter 10 Lab 10-1, Securing Layer 2 Switches INSTRUCTOR VERSION
 CCNPv7.1 SWITCH Chapter 10 Lab 10-1, Securing Layer 2 Switches INSTRUCTOR VERSION Topology Objectives Background Prepare the Network. Implement Layer 2 network security features. Prevent DHCP spoofing
CCNPv7.1 SWITCH Chapter 10 Lab 10-1, Securing Layer 2 Switches INSTRUCTOR VERSION Topology Objectives Background Prepare the Network. Implement Layer 2 network security features. Prevent DHCP spoofing
Lab Configuring and Verifying Standard IPv4 ACLs (Instructor Version Optional Lab)
 (Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
(Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
Chapter 6 Lab 6-1, First Hop Redundancy Protocols HSRP and VRRP INSTRUCTOR VERSION
 CCNPv7.1 SWITCH Chapter 6 Lab 6-1, First Hop Redundancy Protocols HSRP and VRRP INSTRUCTOR VERSION Topology Objectives Configure inter-vlan routing with HSRP and load balancing Configure HSRP authentication
CCNPv7.1 SWITCH Chapter 6 Lab 6-1, First Hop Redundancy Protocols HSRP and VRRP INSTRUCTOR VERSION Topology Objectives Configure inter-vlan routing with HSRP and load balancing Configure HSRP authentication
Chapter 4 Lab 4-2 Multiple Spanning Tree INSTRUCTOR VERSION
 CCNPv7.1 SWITCH Chapter 4 Lab 4-2 Multiple Spanning Tree INSTRUCTOR VERSION Topology Objectives Implement Multiple Spanning Tree Leverage VTP version 3 with MST Background Cisco s Per VLAN Spanning Tree
CCNPv7.1 SWITCH Chapter 4 Lab 4-2 Multiple Spanning Tree INSTRUCTOR VERSION Topology Objectives Implement Multiple Spanning Tree Leverage VTP version 3 with MST Background Cisco s Per VLAN Spanning Tree
CCNP Lab 006 Solution: HSRP and Switch Security
 ABOUT CONTACT FAQ JOIN HOME CCNA CCNP COMPTIA DESIGN You are here: Home / 101 CCNP Labs Solutions / CCNP Lab 006 Solution: HSRP and Switch Security CCNP Lab 006 Solution: HSRP and Switch Security Lab Objective:
ABOUT CONTACT FAQ JOIN HOME CCNA CCNP COMPTIA DESIGN You are here: Home / 101 CCNP Labs Solutions / CCNP Lab 006 Solution: HSRP and Switch Security CCNP Lab 006 Solution: HSRP and Switch Security Lab Objective:
Chapter 8 Lab 8-1, IP Service Level Agreements and Remote SPAN in a Campus Environment INSTRUCTOR VERSION
 CCNPv7.1 SWITCH Chapter 8 Lab 8-1, IP Service Level Agreements and Remote SPAN in a Campus Environment INSTRUCTOR VERSION Topology Objectives Background Configure trunking, VTP, and SVIs. Implement IP
CCNPv7.1 SWITCH Chapter 8 Lab 8-1, IP Service Level Agreements and Remote SPAN in a Campus Environment INSTRUCTOR VERSION Topology Objectives Background Configure trunking, VTP, and SVIs. Implement IP
Chapter 1 Lab - Preparing the Switch INSTRUCTOR VERSION
 CCNPv7.1 SWITCH Chapter 1 Lab - Preparing the Switch INSTRUCTOR VERSION Topology Objectives Clear the configuration of all the switches in your pod Configure the database template used by all the switches
CCNPv7.1 SWITCH Chapter 1 Lab - Preparing the Switch INSTRUCTOR VERSION Topology Objectives Clear the configuration of all the switches in your pod Configure the database template used by all the switches
Lab Configuring and Verifying Standard IPv4 ACLs Topology
 Topology 2016 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 10 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.10.1
Topology 2016 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 10 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.10.1
Chapter 3 Lab 3-1 Static VLANS, Trunking, and VTP
 CCNPv7.1 SWITCH Chapter 3 Lab 3-1 Static VLANS, Trunking, and VTP INSTRUCTOR VERSION Topology Objectives Setup a VTP v2 Domain. Create and maintain VLANs. Configure 802.1Q Trunking. Setup a VTP v3 Domain.
CCNPv7.1 SWITCH Chapter 3 Lab 3-1 Static VLANS, Trunking, and VTP INSTRUCTOR VERSION Topology Objectives Setup a VTP v2 Domain. Create and maintain VLANs. Configure 802.1Q Trunking. Setup a VTP v3 Domain.
Chapter 6 Lab 6-3, Gateway Load Balancing Protocol (GLBP) INSTRUCTOR VERSION
 CCNPv7.1 SWITCH Chapter 6 Lab 6-3, Gateway Load Balancing Protocol (GLBP) INSTRUCTOR VERSION Topology Objectives Configure trunking, VTP, and inter-vlan routing using router-on-a stick Configure GLBP Configure
CCNPv7.1 SWITCH Chapter 6 Lab 6-3, Gateway Load Balancing Protocol (GLBP) INSTRUCTOR VERSION Topology Objectives Configure trunking, VTP, and inter-vlan routing using router-on-a stick Configure GLBP Configure
Chapter 7 Lab 7-1, Synchronizing Campus Network Devices using Network Time Protocol (NTP) INSTRUCTOR VERSION
 CCNPv7.1 SWITCH Chapter 7 Lab 7-1, Synchronizing Campus Network Devices using Network Time Protocol (NTP) INSTRUCTOR VERSION Topology Objective Background Configure network to synchronize time using the
CCNPv7.1 SWITCH Chapter 7 Lab 7-1, Synchronizing Campus Network Devices using Network Time Protocol (NTP) INSTRUCTOR VERSION Topology Objective Background Configure network to synchronize time using the
Lab - Troubleshooting VLAN Configurations (Instructor Version Optional Lab)
 (Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
(Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
Lab Configuring and Verifying Standard ACLs Topology
 Topology 2013 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 9 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.10.1
Topology 2013 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 9 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.10.1
Lab - Troubleshooting Standard IPv4 ACL Configuration and Placement Topology
 Lab - Troubleshooting Standard IPv4 ACL Configuration and Placement Topology 2016 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives
Lab - Troubleshooting Standard IPv4 ACL Configuration and Placement Topology 2016 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives
Lab - Troubleshooting ACL Configuration and Placement Topology
 Topology 2015 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway HQ G0/1 192.168.1.1
Topology 2015 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway HQ G0/1 192.168.1.1
Lab 8.5.2: Troubleshooting Enterprise Networks 2
 Lab 8.5.2: Troubleshooting Enterprise Networks 2 Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway Fa0/0 192.168.10.1 255.255.255.0 N/A R1 Fa0/1 192.168.11.1 255.255.255.0
Lab 8.5.2: Troubleshooting Enterprise Networks 2 Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway Fa0/0 192.168.10.1 255.255.255.0 N/A R1 Fa0/1 192.168.11.1 255.255.255.0
Lab - Configuring VLANs and Trunking (Solution)
 (Solution) Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway S1 VLAN 1 192.168.1.11 255.255.255.0 N/A S2 VLAN 1 192.168.1.12 255.255.255.0 N/A PC-A NIC 192.168.10.3
(Solution) Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway S1 VLAN 1 192.168.1.11 255.255.255.0 N/A S2 VLAN 1 192.168.1.12 255.255.255.0 N/A PC-A NIC 192.168.10.3
Lab - Configuring a Switch Management Address
 Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway S1 VLAN 1 192.168.1.2 255.255.255.0 N/A PC-A NIC 192.168.1.10 255.255.255.0 N/A Part 1: Configure a Basic Network
Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway S1 VLAN 1 192.168.1.2 255.255.255.0 N/A PC-A NIC 192.168.1.10 255.255.255.0 N/A Part 1: Configure a Basic Network
Buy full file at
 14 Chapter 2 LAN Redundancy Chapter 2 LAN Redundancy 2.0.1.2 Class Activity Stormy Traffic ( ) Objective Explain the purpose of the Spanning Tree Protocol (STP) in a switched LAN environment with redundant
14 Chapter 2 LAN Redundancy Chapter 2 LAN Redundancy 2.0.1.2 Class Activity Stormy Traffic ( ) Objective Explain the purpose of the Spanning Tree Protocol (STP) in a switched LAN environment with redundant
Lab Configuring 802.1Q Trunk-Based Inter-VLAN Routing (Instructor Version Optional Lab)
 (Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
(Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
CONFIGURATION DU SWITCH
 Current configuration : 2037 bytes version 12.2 no service pad service timestamps debug uptime service timestamps log uptime no service password-encryption hostname Switch no aaa new-model ip subnet-zero
Current configuration : 2037 bytes version 12.2 no service pad service timestamps debug uptime service timestamps log uptime no service password-encryption hostname Switch no aaa new-model ip subnet-zero
Device Interface IP Address Subnet Mask Default Gateway. Ports Assignment Network
 Felix Rohrer Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway S1 VLAN 99 172.17.99.11 255.255.255.0 N/A S2 VLAN 99 172.17.99.12 255.255.255.0 N/A S3 VLAN 99 172.17.99.13
Felix Rohrer Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway S1 VLAN 99 172.17.99.11 255.255.255.0 N/A S2 VLAN 99 172.17.99.12 255.255.255.0 N/A S3 VLAN 99 172.17.99.13
Lab 8-2 Securing Spanning Tree Protocol
 Lab 8-2 Securing Spanning Tree Protocol Learning Objectives Secure the Layer 2 spanning tree topology with BPDU guard Protect the primary and secondary root bridge with root guard Protect switchports from
Lab 8-2 Securing Spanning Tree Protocol Learning Objectives Secure the Layer 2 spanning tree topology with BPDU guard Protect the primary and secondary root bridge with root guard Protect switchports from
Lab Configuring and Verifying Extended ACLs Topology
 Topology 2015 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.10.1
Topology 2015 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.10.1
Lab Configuring Basic Switch Settings (Solution)
 (Solution) Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway S1 VLAN 99 192.168.1.2 255.255.255.0 192.168.1.1 PC-A NIC 192.168.1.10 255.255.255.0 192.168.1.1
(Solution) Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway S1 VLAN 99 192.168.1.2 255.255.255.0 192.168.1.1 PC-A NIC 192.168.1.10 255.255.255.0 192.168.1.1
Lab Configuring Dynamic and Static NAT (Solution)
 (Solution) Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway Gateway G0/1 192.168.1.1 255.255.255.0 N/A S0/0/1 209.165.201.18 255.255.255.252 N/A ISP S0/0/0 (DCE)
(Solution) Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway Gateway G0/1 192.168.1.1 255.255.255.0 N/A S0/0/1 209.165.201.18 255.255.255.252 N/A ISP S0/0/0 (DCE)
Lab Configuring Dynamic and Static NAT (Instructor Version Optional Lab)
 (Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
(Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
Basic Router Configuration
 This section includes information about some basic router configuration, and contains the following sections: Default Configuration, on page 1 Configuring Global Parameters, on page 2 Configuring Gigabit
This section includes information about some basic router configuration, and contains the following sections: Default Configuration, on page 1 Configuring Global Parameters, on page 2 Configuring Gigabit
Lab Troubleshooting IPv4 and IPv6 Static Routes (Instructor Version Optional Lab)
 (Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
(Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
Lab Configuring Per-Interface Inter-VLAN Routing (Solution)
 (Solution) Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/0 192.168.20.1 255.255.255.0 N/A G0/1 192.168.10.1 255.255.255.0 N/A S1 VLAN 10 192.168.10.11
(Solution) Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/0 192.168.20.1 255.255.255.0 N/A G0/1 192.168.10.1 255.255.255.0 N/A S1 VLAN 10 192.168.10.11
RealCiscoLAB.com. Inter-VLAN Routing with an Internal Route Processor and Monitoring CEF Functions
 RealCiscoLAB.com CCNPv6 SWITCH Inter-VLAN Routing with an Internal Route Processor and Monitoring CEF Functions Topology Objective Background Route between VLANs using a 3560 switch with an internal route
RealCiscoLAB.com CCNPv6 SWITCH Inter-VLAN Routing with an Internal Route Processor and Monitoring CEF Functions Topology Objective Background Route between VLANs using a 3560 switch with an internal route
Lab Configuring Per-Interface Inter-VLAN Routing (Instructor Version)
 (Instructor Version) Instructor Note: Red font color or Gray highlights indicate text that appears in the instructor copy only. Topology Addressing Table Objectives Device Interface IP Address Subnet Mask
(Instructor Version) Instructor Note: Red font color or Gray highlights indicate text that appears in the instructor copy only. Topology Addressing Table Objectives Device Interface IP Address Subnet Mask
Lab Configuring Port Address Translation (PAT) (Instructor Version)
 (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Topology Addressing Table Objectives Device Interface IP Address Subnet Mask
(Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Topology Addressing Table Objectives Device Interface IP Address Subnet Mask
RealCiscoLAB.com. Configure inter-vlan routing with HSRP to provide redundant, fault-tolerant routing to the internal network.
 RealCiscoLAB.com CCNPv6 SWITCH Hot Standby Router Protocol Topology Objective Background Configure inter-vlan routing with HSRP to provide redundant, fault-tolerant routing to the internal network. Hot
RealCiscoLAB.com CCNPv6 SWITCH Hot Standby Router Protocol Topology Objective Background Configure inter-vlan routing with HSRP to provide redundant, fault-tolerant routing to the internal network. Hot
Lab Catalyst 2950T and 3550 Series Basic Setup
 Lab 1.2.9.1 Catalyst 2950T and 3550 Series Basic Setup Objective Configure a Cisco Catalyst 2950T or 3550 series Ethernet switch for the first time using the command-line interface (CLI) mode. Basic first
Lab 1.2.9.1 Catalyst 2950T and 3550 Series Basic Setup Objective Configure a Cisco Catalyst 2950T or 3550 series Ethernet switch for the first time using the command-line interface (CLI) mode. Basic first
Lab Troubleshooting VTP Configuration
 Lab 4.4.3 Troubleshooting VTP Configuration Topology Diagram Addressing Table Device (Hostname) Interface IP Address Subnet Mask S1 VLAN 99 172.17.99.11 255.255.255.0 S2 VLAN 99 172.17.99.12 255.255.255.0
Lab 4.4.3 Troubleshooting VTP Configuration Topology Diagram Addressing Table Device (Hostname) Interface IP Address Subnet Mask S1 VLAN 99 172.17.99.11 255.255.255.0 S2 VLAN 99 172.17.99.12 255.255.255.0
CCNA Semester 2 labs. Labs for chapters 2 10
 CCNA Semester 2 labs Labs for chapters 2 10 2.2.2.5 Lab - Configuring IPv4 Static and Default Routes 2.3.2.4 Lab - Troubleshooting Static Routes 3.2.1.9 Lab - Configuring Basic RIPv2 5.2.2.9 Lab - Configuring
CCNA Semester 2 labs Labs for chapters 2 10 2.2.2.5 Lab - Configuring IPv4 Static and Default Routes 2.3.2.4 Lab - Troubleshooting Static Routes 3.2.1.9 Lab - Configuring Basic RIPv2 5.2.2.9 Lab - Configuring
Lab Configuring Switch Security Features Topology
 Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 172.16.99.1 255.255.255.0 N/A S1 VLAN 99 172.16.99.11 255.255.255.0 172.16.99.1 PC-A NIC 172.16.99.3
Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 172.16.99.1 255.255.255.0 N/A S1 VLAN 99 172.16.99.11 255.255.255.0 172.16.99.1 PC-A NIC 172.16.99.3
Chapter 10 - Configure ASA Basic Settings and Firewall using ASDM
 Chapter 10 - Configure ASA Basic Settings and Firewall using ASDM This lab has been updated for use on NETLAB+ Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces.
Chapter 10 - Configure ASA Basic Settings and Firewall using ASDM This lab has been updated for use on NETLAB+ Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces.
RealCiscoLAB.com. Configuring EtherChannel. Topology. Objective. Background. Required Resources. CCNPv6 Switch. Configure EtherChannel.
 RealCiscoLAB.com CCNPv6 Switch Configuring EtherChannel Topology Objective Background Configure EtherChannel. Four switches have just been installed. The distribution layer switches are Catalyst 3560 switches,
RealCiscoLAB.com CCNPv6 Switch Configuring EtherChannel Topology Objective Background Configure EtherChannel. Four switches have just been installed. The distribution layer switches are Catalyst 3560 switches,
Lab Configuring Basic RIPv2 (Solution)
 (Solution) Topology 2017 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 15 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway
(Solution) Topology 2017 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 15 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway
when interoperating with a Cisco Layer 3 Switch Situation: VLAN 1 shutdown, no IP on default VLAN on Cisco switch
 CONFIGURING VLANS ON MNS-6K AND MNS-6K-SECURE when interoperating with a Cisco Layer 3 Switch Situation: VLAN 1 shutdown, no IP on default VLAN on Cisco switch A Technical Brief from GarrettCom, Inc.,
CONFIGURING VLANS ON MNS-6K AND MNS-6K-SECURE when interoperating with a Cisco Layer 3 Switch Situation: VLAN 1 shutdown, no IP on default VLAN on Cisco switch A Technical Brief from GarrettCom, Inc.,
QUESTION/SOLUTION SET LAB 4
 QUESTION/SOLUTION SET LAB 4 CCIE lab Routing & Switching (v4.0) lab:4 Updated Testing Guidelines 1. The equipment on the rack assigned to you is physically Cabled and should not be tempered with. 2. Router
QUESTION/SOLUTION SET LAB 4 CCIE lab Routing & Switching (v4.0) lab:4 Updated Testing Guidelines 1. The equipment on the rack assigned to you is physically Cabled and should not be tempered with. 2. Router
Lab 5-1 Hot Standby Router Protocol
 Lab 5-1 Hot Standby Router Protocol Topology Diagram Objective Configure inter-vlan routing with HSRP to provide redundant, fault tolerant routing to the internal network. Scenario Step 1 HSRP provides
Lab 5-1 Hot Standby Router Protocol Topology Diagram Objective Configure inter-vlan routing with HSRP to provide redundant, fault tolerant routing to the internal network. Scenario Step 1 HSRP provides
Chapter 3 Lab 3-1, Assembling Maintenance and Troubleshooting Tools
 Chapter 3 Lab 3-1, Assembling Maintenance and Troubleshooting Tools Physical Topology All contents are Copyright 1992 2010 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information.
Chapter 3 Lab 3-1, Assembling Maintenance and Troubleshooting Tools Physical Topology All contents are Copyright 1992 2010 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information.
CCNA Routing & Switching Lab Workbook - Full-Scale Lab 1
 CCNA Routing & Switching Lab Workbook - Full-Scale Lab 1 Task 1.1 Tasks You must load the initial configuration files for the section, FS Lab-1 Initial, which can be found in CCNA Routing & Switching Topology
CCNA Routing & Switching Lab Workbook - Full-Scale Lab 1 Task 1.1 Tasks You must load the initial configuration files for the section, FS Lab-1 Initial, which can be found in CCNA Routing & Switching Topology
CCNA Semester 3 labs. Labs for chapters 2 10
 CCNA Semester 3 labs Labs for chapters 2 10 2.1.4.5 Lab - Configure Extended VLANs, VTP, and DTP 2.2.2.5 Lab - Troubleshooting Inter-VLAN Routing 3.1.2.12 Lab - Building a Switched Network with Redundant
CCNA Semester 3 labs Labs for chapters 2 10 2.1.4.5 Lab - Configure Extended VLANs, VTP, and DTP 2.2.2.5 Lab - Troubleshooting Inter-VLAN Routing 3.1.2.12 Lab - Building a Switched Network with Redundant
Lab - Configuring Basic DHCPv4 on a Router (Solution)
 (Solution) Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/0 192.168.0.1 255.255.255.0 N/A G0/1 192.168.1.1 255.255.255.0 N/A S0/0/0 (DCE) 192.168.2.253
(Solution) Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/0 192.168.0.1 255.255.255.0 N/A G0/1 192.168.1.1 255.255.255.0 N/A S0/0/0 (DCE) 192.168.2.253
!! Last configuration change at 16:04:19 UTC Tue Feb by zdrillin! NVRAM config last updated at 21:07:18 UTC Thu Feb ! version 12.
 Last configuration change at 16:04:19 UTC Tue Feb 15 2011 by zdrillin NVRAM config last updated at 21:07:18 UTC Thu Feb 10 2011 version 12.2 no service pad service timestamps debug datetime msec service
Last configuration change at 16:04:19 UTC Tue Feb 15 2011 by zdrillin NVRAM config last updated at 21:07:18 UTC Thu Feb 10 2011 version 12.2 no service pad service timestamps debug datetime msec service
Lab Troubleshooting Using traceroute Instructor Version 2500
 Lab 9.3.4 Troubleshooting Using traceroute Instructor Version 2500 294-833 CCNA 2: Routers and Routing Basics v 3.1 - Lab 9.3.4 Copyright 2003, Cisco Systems, Inc. Objective Use the traceroute Cisco IOS
Lab 9.3.4 Troubleshooting Using traceroute Instructor Version 2500 294-833 CCNA 2: Routers and Routing Basics v 3.1 - Lab 9.3.4 Copyright 2003, Cisco Systems, Inc. Objective Use the traceroute Cisco IOS
Lab Configuring HSRP and GLBP Topology
 Topology 2014 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 9 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.1.1
Topology 2014 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 9 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.1.1
Table of Contents. isco Configuring 802.1q Trunking Between a Catalyst 3550 and Catalyst Switches Running Integrated Cisco IOS (Nativ
 king Between a Catalyst 3550 and Catalyst Switches Running isco Configuring 802.1q Trunking Between a Catalyst 3550 and Catalyst Switches Running Integrated Cisco IOS (Nativ Table of Contents Configuring
king Between a Catalyst 3550 and Catalyst Switches Running isco Configuring 802.1q Trunking Between a Catalyst 3550 and Catalyst Switches Running Integrated Cisco IOS (Nativ Table of Contents Configuring
CCNA Semester 3 labs. Part 1 of 1 Labs for chapters 1 8
 CCNA Semester 3 labs Part 1 of 1 Labs for chapters 1 8 2.1.2.12 Lab - Building a Switched Network with Redundant Links 2.3.2.3 Lab - Configuring Rapid PVST+, PortFast and BPDU Guard 2.4.3.4 Lab - Configuring
CCNA Semester 3 labs Part 1 of 1 Labs for chapters 1 8 2.1.2.12 Lab - Building a Switched Network with Redundant Links 2.3.2.3 Lab - Configuring Rapid PVST+, PortFast and BPDU Guard 2.4.3.4 Lab - Configuring
Configuring EtherChannel
 L4 Configuring EtherChannel Global Knowledge Training LLC L4-1 Objectives In this lab you will first verify that one of the parallel connections to the core switch is blocked by STP. You will then configure
L4 Configuring EtherChannel Global Knowledge Training LLC L4-1 Objectives In this lab you will first verify that one of the parallel connections to the core switch is blocked by STP. You will then configure
Default Gateway Fa0/ N/A. Device Interface IP Address Subnet Mask
 Felix Rohrer Topology Addressing Table Device Interface IP Address Subnet Mask Default Gateway Fa0/1 10.0.0.1 255.255.255.128 N/A S0/0/0 172.16.0.1 255.255.255.252 N/A S0/0/1 172.16.0.9 255.255.255.252
Felix Rohrer Topology Addressing Table Device Interface IP Address Subnet Mask Default Gateway Fa0/1 10.0.0.1 255.255.255.128 N/A S0/0/0 172.16.0.1 255.255.255.252 N/A S0/0/1 172.16.0.9 255.255.255.252
Lab 5.5.2: Challenge Spanning Tree Protocol
 Topology Diagram Addressing Table Device (Hostname) Interface IP Address Subnet Mask Default Gateway S1 VLAN 99 172.17.99.11 255.255.255.0 N/A S2 VLAN 99 172.17.99.12 255.255.255.0 N/A S3 VLAN 99 172.17.99.13
Topology Diagram Addressing Table Device (Hostname) Interface IP Address Subnet Mask Default Gateway S1 VLAN 99 172.17.99.11 255.255.255.0 N/A S2 VLAN 99 172.17.99.12 255.255.255.0 N/A S3 VLAN 99 172.17.99.13
Lab Designing and Implementing a VLSM Addressing Scheme. Topology. Objectives. Background / Scenario
 CSNB214 Packet Tracer Lab Designing and Implementing a VLSM Addressing Scheme Topology Objectives Part 1: Examine Network Requirements Part 2: Design the VLSM Address Scheme Part 3: Cable and Configure
CSNB214 Packet Tracer Lab Designing and Implementing a VLSM Addressing Scheme Topology Objectives Part 1: Examine Network Requirements Part 2: Design the VLSM Address Scheme Part 3: Cable and Configure
Lab 5: Basic VLAN Configuration
 Topology Diagram Addressing Table Device (Hostname) Interface IP Address Subnet Mask Default Gateway S1 VLAN 99 172.17.99.11 255.255.255.0 N/A S2 VLAN 99 172.17.99.12 255.255.255.0 N/A S3 VLAN 99 172.17.99.13
Topology Diagram Addressing Table Device (Hostname) Interface IP Address Subnet Mask Default Gateway S1 VLAN 99 172.17.99.11 255.255.255.0 N/A S2 VLAN 99 172.17.99.12 255.255.255.0 N/A S3 VLAN 99 172.17.99.13
Advanced IPv6 Training Course. Lab Manual. v1.3 Page 1
 Advanced IPv6 Training Course Lab Manual v1.3 Page 1 Network Diagram AS66 AS99 10.X.0.1/30 2001:ffXX:0:01::a/127 E0/0 R 1 E1/0 172.X.255.1 2001:ffXX::1/128 172.16.0.X/24 2001:ff69::X/64 E0/1 10.X.0.5/30
Advanced IPv6 Training Course Lab Manual v1.3 Page 1 Network Diagram AS66 AS99 10.X.0.1/30 2001:ffXX:0:01::a/127 E0/0 R 1 E1/0 172.X.255.1 2001:ffXX::1/128 172.16.0.X/24 2001:ff69::X/64 E0/1 10.X.0.5/30
Laboration 2 Troubleshooting Switching and First-Hop Redundancy
 Laboration 2 Troubleshooting Switching and First-Hop Redundancy Topology All contents are Copyright 1992 2011 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 1
Laboration 2 Troubleshooting Switching and First-Hop Redundancy Topology All contents are Copyright 1992 2011 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 1
CISCO SWITCH BEST PRACTICES GUIDE
 CISCO SWITCH BEST PRACTICES GUIDE Table of Contents (After Clicking Link Hit HOME to Return to TOC) 1) Add Hostname... 2 2) Add Username and Password... 2 3) Create Secret Password... 2 4) Encrypt Password...
CISCO SWITCH BEST PRACTICES GUIDE Table of Contents (After Clicking Link Hit HOME to Return to TOC) 1) Add Hostname... 2 2) Add Username and Password... 2 3) Create Secret Password... 2 4) Encrypt Password...
CCNA Semester 1 labs. Part 1 of 2 Labs for chapters 1 7
 CCNA Semester 1 labs Part 1 of 2 Labs for chapters 1 7 2.3.3.3 Lab - Building a Simple Network 2.3.3.4 Lab - Configuring a Switch Management Address 3.4.1.2 Lab - Using Wireshark to View Network Traffic
CCNA Semester 1 labs Part 1 of 2 Labs for chapters 1 7 2.3.3.3 Lab - Building a Simple Network 2.3.3.4 Lab - Configuring a Switch Management Address 3.4.1.2 Lab - Using Wireshark to View Network Traffic
Skills Assessment Student Training
 Skills Assessment Student Training Topology Assessment Objectives Part 1: Initialize Devices (6 points, 5 minutes) Part 2: Configure Device Basic Settings (33 points, 20 minutes) Part 3: Configure Switch
Skills Assessment Student Training Topology Assessment Objectives Part 1: Initialize Devices (6 points, 5 minutes) Part 2: Configure Device Basic Settings (33 points, 20 minutes) Part 3: Configure Switch
SSG Configuration Example
 APPENDIX A Example A-1 is a sample SSG configuration for the Cisco 10000 series router based on the topology in Figure A-1. The configuration includes AAA, PPP, SSG, and RADIUS. The SSG configuration enables
APPENDIX A Example A-1 is a sample SSG configuration for the Cisco 10000 series router based on the topology in Figure A-1. The configuration includes AAA, PPP, SSG, and RADIUS. The SSG configuration enables
Lab 7 Configuring Basic Router Settings with IOS CLI
 Lab 7 Configuring Basic Router Settings with IOS CLI Objectives Part 1: Set Up the Topology and Initialize Devices Cable equipment to match the network topology. Initialize and restart the router and switch.
Lab 7 Configuring Basic Router Settings with IOS CLI Objectives Part 1: Set Up the Topology and Initialize Devices Cable equipment to match the network topology. Initialize and restart the router and switch.
Chapter 8 Lab Configuring a Site-to-Site VPN Using Cisco IOS
 Chapter 8 Lab Configuring a Site-to-Site VPN Using Cisco IOS Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces. 2017 Cisco and/or its affiliates. All rights
Chapter 8 Lab Configuring a Site-to-Site VPN Using Cisco IOS Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces. 2017 Cisco and/or its affiliates. All rights
Lab Managing Router Configuration Files with Terminal Emulation Software
 Lab Managing Router Configuration Files with Terminal Emulation Software Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.1.1 255.255.255.0 N/A
Lab Managing Router Configuration Files with Terminal Emulation Software Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.1.1 255.255.255.0 N/A
Chapter 2 Lab 2-1, Static VLANS, VLAN Trunking, and VTP Domains and Modes
 Chapter 2 Lab 2-1, Static VLANS, VLAN Trunking, and VTP Domains and Modes Topology Objectives Background Set up a VTP domain. Create and maintain VLANs. Configure ISL and 802.1Q trunking. VLANs logically
Chapter 2 Lab 2-1, Static VLANS, VLAN Trunking, and VTP Domains and Modes Topology Objectives Background Set up a VTP domain. Create and maintain VLANs. Configure ISL and 802.1Q trunking. VLANs logically
Troubleshooting VLANs and Trunks
 L2 Troubleshooting VLANs and Trunks Global Knowledge Training LLC L2-1 Objectives In this lab you will download configuration files into PxSW s running configuration to introduce VLAN and trunking issues
L2 Troubleshooting VLANs and Trunks Global Knowledge Training LLC L2-1 Objectives In this lab you will download configuration files into PxSW s running configuration to introduce VLAN and trunking issues
Network security session 9-2 Router Security. Network II
 Network security session 9-2 Router Security Network II Router security First line of defense of the network Compromise of a router can lead to many issues: Denial of network services Degrading of network
Network security session 9-2 Router Security Network II Router security First line of defense of the network Compromise of a router can lead to many issues: Denial of network services Degrading of network
Lab Configuring IPv4 Static and Default Routes (Solution)
 (Solution) Topology Addressing Table Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.0.1 255.255.255.0 N/A S0/0/1 10.1.1.1 255.255.255.252 N/A R3 G0/1 192.168.1.1 255.255.255.0
(Solution) Topology Addressing Table Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.0.1 255.255.255.0 N/A S0/0/1 10.1.1.1 255.255.255.252 N/A R3 G0/1 192.168.1.1 255.255.255.0
Lab Catalyst 2950 and 3550 Series Intra-VLAN Security
 Lab 7.2.5.1 Catalyst 2950 and 3550 Series Intra-VLAN Security Objective Scenario Configure intra-vlan security with Access Control Lists (ACLs) using the command-line interface (CLI) mode. This lab will
Lab 7.2.5.1 Catalyst 2950 and 3550 Series Intra-VLAN Security Objective Scenario Configure intra-vlan security with Access Control Lists (ACLs) using the command-line interface (CLI) mode. This lab will
Configuring HSRP. Global Knowledge Training LLC L5-1
 L5 Configuring HSRP Global Knowledge Training LLC L5-1 Objectives In this lab you will examine the hot standby router protocol (HSRP). First you will configure PxR2 similar to PxR1, so they are both possible
L5 Configuring HSRP Global Knowledge Training LLC L5-1 Objectives In this lab you will examine the hot standby router protocol (HSRP). First you will configure PxR2 similar to PxR1, so they are both possible
RealCiscoLAB.com. Securing Spanning Tree Protocol. Topology. Objectives. Background. CCNPv6 SWITCH
 RealCiscoLAB.com CCNPv6 SWITCH Securing Spanning Tree Protocol Topology Objectives Background Secure the Layer 2 spanning-tree topology with BPDU guard. Protect the primary and secondary root bridge with
RealCiscoLAB.com CCNPv6 SWITCH Securing Spanning Tree Protocol Topology Objectives Background Secure the Layer 2 spanning-tree topology with BPDU guard. Protect the primary and secondary root bridge with
Payload Types At Different OSI Layers: Layer 2 - Frame Layer 3 - Packet Layer 4 - Datagram
 Payload Types At Different OSI Layers: Layer 2 - Frame Layer 3 - Packet Layer 4 - Datagram Default Cisco Terminal Options: 9600 bits/second No hardware flow control 8-bit ASCII No parity 1 stop bit Setting
Payload Types At Different OSI Layers: Layer 2 - Frame Layer 3 - Packet Layer 4 - Datagram Default Cisco Terminal Options: 9600 bits/second No hardware flow control 8-bit ASCII No parity 1 stop bit Setting
Lab Configuring IPv6 Static and Default Routes (Solution)
 (Solution) Topology Addressing Table Device Interface IPv6 Address / Prefix Length Default Gateway R1 G0/1 2001:DB8:ACAD:A::/64 eui-64 N/A S0/0/1 FC00::1/64 N/A R3 G0/1 2001:DB8:ACAD:B::/64 eui-64 N/A
(Solution) Topology Addressing Table Device Interface IPv6 Address / Prefix Length Default Gateway R1 G0/1 2001:DB8:ACAD:A::/64 eui-64 N/A S0/0/1 FC00::1/64 N/A R3 G0/1 2001:DB8:ACAD:B::/64 eui-64 N/A
Lab b Standard ACLs Instructor Version 2500
 Lab 11.2.1b Standard ACLs Instructor Version 2500 Objective Scenario Plan, configure, and apply a standard ACL to permit or deny specific traffic and test the ACL to determine if the desired results were
Lab 11.2.1b Standard ACLs Instructor Version 2500 Objective Scenario Plan, configure, and apply a standard ACL to permit or deny specific traffic and test the ACL to determine if the desired results were
Packet Tracer - Connect a Router to a LAN (Instructor Version)
 (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Topology Addressing Table Device Interface IP Address Subnet Mask Default
(Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Topology Addressing Table Device Interface IP Address Subnet Mask Default
Lab 5.6b Configuring AAA and RADIUS
 Lab 5.6b Configuring AAA and RADIUS Learning Objectives Install CiscoSecure ACS Configure CiscoSecure ACS as a RADIUS server Enable AAA on a router using a remote RADIUS server Topology Diagram Scenario
Lab 5.6b Configuring AAA and RADIUS Learning Objectives Install CiscoSecure ACS Configure CiscoSecure ACS as a RADIUS server Enable AAA on a router using a remote RADIUS server Topology Diagram Scenario
Actual4Test. Actual4test - actual test exam dumps-pass for IT exams
 Actual4Test http://www.actual4test.com Actual4test - actual test exam dumps-pass for IT exams Exam : 200-125 Title : CCNA Cisco Certified Network Associate CCNA (v3.0) Vendor : Cisco Version : DEMO Get
Actual4Test http://www.actual4test.com Actual4test - actual test exam dumps-pass for IT exams Exam : 200-125 Title : CCNA Cisco Certified Network Associate CCNA (v3.0) Vendor : Cisco Version : DEMO Get
Configuring VLANs. Finding Feature Information. Prerequisites for VLANs
 Finding Feature Information, page 1 Prerequisites for VLANs, page 1 Restrictions for VLANs, page 2 Information About VLANs, page 2 How to Configure VLANs, page 7 Monitoring VLANs, page 19 Where to Go Next,
Finding Feature Information, page 1 Prerequisites for VLANs, page 1 Restrictions for VLANs, page 2 Information About VLANs, page 2 How to Configure VLANs, page 7 Monitoring VLANs, page 19 Where to Go Next,
Route between VLANs using a 3560 switch with an internal route processor using Cisco Express Forwarding (CEF).
 Lab 3- Part I Inter-VLAN routing with a Multilayer Switch Configuration and Management of Networks - 2014 Topology Objective Route between VLANs using a 3560 switch with an internal route processor using
Lab 3- Part I Inter-VLAN routing with a Multilayer Switch Configuration and Management of Networks - 2014 Topology Objective Route between VLANs using a 3560 switch with an internal route processor using
Configuring DHCP Features and IP Source Guard
 CHAPTER 21 This chapter describes how to configure DHCP snooping and option-82 data insertion, and the DHCP server port-based address allocation features on the switch. It also describes how to configure
CHAPTER 21 This chapter describes how to configure DHCP snooping and option-82 data insertion, and the DHCP server port-based address allocation features on the switch. It also describes how to configure
Netw 3000 VLAN 1 LAB Darlene Redmond Ryan Gamblin January 19 th 2012
 Netw 3000 VLAN 1 LAB Darlene Redmond Ryan Gamblin January 19 th 2012 3. Attach a workstation to the Management VLAN and demonstrate a successful login to the switch at the privileged exec mode, with a
Netw 3000 VLAN 1 LAB Darlene Redmond Ryan Gamblin January 19 th 2012 3. Attach a workstation to the Management VLAN and demonstrate a successful login to the switch at the privileged exec mode, with a
Using the Management Ethernet Interface
 This chapter covers the following topics: Gigabit Ethernet Management Interface Overview, page 1 Gigabit Ethernet Port Numbering, page 1 IP Address Handling in ROMmon and the Management Ethernet Port,
This chapter covers the following topics: Gigabit Ethernet Management Interface Overview, page 1 Gigabit Ethernet Port Numbering, page 1 IP Address Handling in ROMmon and the Management Ethernet Port,
Catalyst 4500 Series IOS Commands
 CHAPTER Catalyst 4500 Series IOS Commands New Commands dot1x guest-vlan supplicant ip dhcp snooping information option allow-untrusted port-security mac-address port-security mac-address sticky port-security
CHAPTER Catalyst 4500 Series IOS Commands New Commands dot1x guest-vlan supplicant ip dhcp snooping information option allow-untrusted port-security mac-address port-security mac-address sticky port-security
3. What could you use if you wanted to reduce unnecessary broadcast, multicast, and flooded unicast packets?
 Nguyen The Nhat - Take Exam Exam questions Time remaining: 00: 00: 51 1. Which command will give the user TECH privileged-mode access after authentication with the server? username name privilege level
Nguyen The Nhat - Take Exam Exam questions Time remaining: 00: 00: 51 1. Which command will give the user TECH privileged-mode access after authentication with the server? username name privilege level
Lab - Configuring VLANs and Trunking
 Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway S1 VLAN 1 192.168.1.11 255.255.255.0 N/A S2 VLAN 1 192.168.1.12 255.255.255.0 N/A PC-A NIC 192.168.10.3 255.255.255.0
Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway S1 VLAN 1 192.168.1.11 255.255.255.0 N/A S2 VLAN 1 192.168.1.12 255.255.255.0 N/A PC-A NIC 192.168.10.3 255.255.255.0
Policy Based Routing with the Multiple Tracking Options Feature Configuration Example
 Policy Based Routing with the Multiple Tracking Options Feature Configuration Example Document ID: 48003 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram
Policy Based Routing with the Multiple Tracking Options Feature Configuration Example Document ID: 48003 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram
Catalyst Switches for Microsoft Network Load Balancing Configuration Example
 Catalyst Switches for Microsoft Network Load Balancing Configuration Example Document ID: 107995 Contributed by Shashank Singh, Cisco TAC Engineer. Dec 19, 2013 Contents Introduction Prerequisites Requirements
Catalyst Switches for Microsoft Network Load Balancing Configuration Example Document ID: 107995 Contributed by Shashank Singh, Cisco TAC Engineer. Dec 19, 2013 Contents Introduction Prerequisites Requirements
itexamdump 최고이자최신인 IT 인증시험덤프 일년무료업데이트서비스제공
 itexamdump 최고이자최신인 IT 인증시험덤프 http://www.itexamdump.com 일년무료업데이트서비스제공 Exam : 642-813 Title : Implementing Cisco IP Switched Networks Vendor : Cisco Version : DEMO Get Latest & Valid 642-813 Exam's Question
itexamdump 최고이자최신인 IT 인증시험덤프 http://www.itexamdump.com 일년무료업데이트서비스제공 Exam : 642-813 Title : Implementing Cisco IP Switched Networks Vendor : Cisco Version : DEMO Get Latest & Valid 642-813 Exam's Question
CCNA Security 1.0 Student Packet Tracer Manual
 1.0 Student Packet Tracer Manual This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document for non-commercial distribution and exclusive use by instructors
1.0 Student Packet Tracer Manual This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document for non-commercial distribution and exclusive use by instructors
BraindumpsIT. BraindumpsIT - IT Certification Company provides Braindumps pdf!
 BraindumpsIT http://www.braindumpsit.com BraindumpsIT - IT Certification Company provides Braindumps pdf! Exam : 300-115 Title : Implementing Cisco IP Switched Networks Vendor : Cisco Version : DEMO Get
BraindumpsIT http://www.braindumpsit.com BraindumpsIT - IT Certification Company provides Braindumps pdf! Exam : 300-115 Title : Implementing Cisco IP Switched Networks Vendor : Cisco Version : DEMO Get
Configuring DHCP Features and IP Source Guard
 CHAPTER 21 This chapter describes how to configure DHCP snooping and the option-82 data insertion features on the switch. It also describes how to configure the IP source guard feature.unless otherwise
CHAPTER 21 This chapter describes how to configure DHCP snooping and the option-82 data insertion features on the switch. It also describes how to configure the IP source guard feature.unless otherwise
The objective of this lab is to become familiar with Cisco switches as well as the Spanning Tree Protocol.
 CIS 83 LAB 4 - Spanning Tree Protocol Rich Simms October 3, 2006 Objective The objective of this lab is to become familiar with Cisco switches as well as the Spanning Tree Protocol. Scenario This lab was
CIS 83 LAB 4 - Spanning Tree Protocol Rich Simms October 3, 2006 Objective The objective of this lab is to become familiar with Cisco switches as well as the Spanning Tree Protocol. Scenario This lab was
Switches running the LAN Base feature set support only static routing on SVIs.
 Finding Feature Information, on page 1 Prerequisites for VLANs, on page 1 Restrictions for VLANs, on page 2 Information About VLANs, on page 2 How to Configure VLANs, on page 6 Monitoring VLANs, on page
Finding Feature Information, on page 1 Prerequisites for VLANs, on page 1 Restrictions for VLANs, on page 2 Information About VLANs, on page 2 How to Configure VLANs, on page 6 Monitoring VLANs, on page
Chapter 4 Lab 4-1, Inter-VLAN Routing with an External Router
 Chapter 4 Lab 4-1, Inter-VLAN Routing with an External Router Topology Objective Background Configure inter-vlan routing using an external router, also known as a router on a stick. Inter-VLAN routing
Chapter 4 Lab 4-1, Inter-VLAN Routing with an External Router Topology Objective Background Configure inter-vlan routing using an external router, also known as a router on a stick. Inter-VLAN routing
Lab - Troubleshooting Connectivity Issues
 Lab - Troubleshooting Connectivity Issues Topology Addressing Table R1 ISP Objectives Device Interface IP Address Subnet Mask Default Gateway G0/1 192.168.1.1 255.255.255.0 N/A S0/0/0 10.1.1.1 255.255.255.252
Lab - Troubleshooting Connectivity Issues Topology Addressing Table R1 ISP Objectives Device Interface IP Address Subnet Mask Default Gateway G0/1 192.168.1.1 255.255.255.0 N/A S0/0/0 10.1.1.1 255.255.255.252
