Configuring High Availability
|
|
|
- Lewis Chapman
- 6 years ago
- Views:
Transcription
1 The Cisco High Availability (HA) technology enable network-wide protection by providing quick recovery from disruptions that may occur in any part of a network. A network's hardware and software work together with Cisco High Availability technology, which besides enabling quick recovery from disruptions, ensures fault transparency to users and network applications. The following sections describe how to configure Cisco High Availability features on your router: About Cisco High Availability, page 1 Interchassis High Availability, page 1 Bidirectional Forwarding Detection, page 3 Configuring Cisco High Availability, page 3 Additional References, page 13 About Cisco High Availability The unique hardware and software architecture of your router is designed to maximize router uptime during any network event, and thereby provide maximum uptime and resilience within any network scenario. This section covers some aspects of Cisco High Availability that may be used on the Cisco 4000 series routers: Interchassis High Availability, on page 1 Bidirectional Forwarding Detection, on page 3 Interchassis High Availability The Interchassis High Availability feature is also known as the box-to-box redundancy feature. Interchassis High Availability enables the configuration of pairs of routers to act as backup for each other. This feature can be configured to determine the active router based on several failover conditions. When a failover occurs, the standby router seamlessly takes over and starts processing call signaling and performing media forwarding tasks. OL
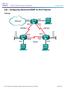
2 IPsec Failover Groups of redundant interfaces are known as redundancy groups. The following figure depicts the active-standby device scenario. It shows how the redundancy group is configured for a pair of routers that have a single outgoing interface. Figure 1: Redundancy Group Configuration The routers are joined by a configurable control link and data synchronization link. The control link is used to communicate the status of the routers. The data synchronization link is used to transfer stateful information to synchronize the stateful database for the calls and media flows. Each pair of redundant interfaces are configured with the same unique ID number, also known as the RII. For information on configuring Interchassis HA on your router, see Configuring Interchassis High Availability, on page 3. IPsec Failover The IPsec Failover feature increases the total uptime (or availability) of your IPsec network. Traditionally, the increased availability of your IPsec network is accomplished by employing a redundant (standby) router in addition to the original (active) router. When the active router becomes unavailable for a reason, the standby router takes over the processing of IKE and IPsec. IPsec failover falls into two categories: stateless failover and stateful failover. On the router, only the stateless form of IPsec failover is supported. This stateless failover uses protocols such as the Hot Standby Router Protocol (HSRP) to provide primary to secondary cutover and also allows the active and standby VPN gateways to share a common virtual IP address. 2 OL
3 Bidirectional Forwarding Detection Bidirectional Forwarding Detection Bidirectional Forwarding Detection (BFD) is a detection protocol designed to provide fast-forwarding path-failure detection times for all media types, encapsulations, topologies, and routing protocols. In addition to fast-forwarding path-failure detection, BFD provides a consistent failure detection method for network administrators. Because a network administrator can use BFD to detect forwarding path failures at a uniform rate rather than variable rates for different routing protocol hello mechanisms, network profiling and planning is easier, and reconvergence time is consistent and predictable. For more information on BFD, see the Bidirectional Forwarding Detection section in the IP Routing BFD Configuration Guide, Cisco IOS XE Release 3S. Bidirectional Forwarding Detection Offload The Bidirectional Forwarding Detection Offload feature allows the offload of BFD session management to the forwarding engine for improved failure detection times. BFD offload reduces the overall network convergence time by sending rapid failure detection packets (messages) to the routing protocols for recalculating the routing table. See Configuring BFD Offload, on page 4. Configuring Cisco High Availability Configuring Interchassis High Availability, on page 3 Configuring Bidirectional Forwarding, on page 4 Verifying Interchassis High Availability, on page 5 Verifying BFD Offload, on page 11 Configuring Interchassis High Availability Prerequisites The active device and the standby device must run on the identical version of the Cisco IOS XE software. The active device and the standby device must be connected through an L2 connection for the control path. The Embedded Service Processor (ESP) must be the same on both the active and standby devices. Route processors must also match and have a similar physical configuration. Either the Network Time Protocol (NTP) must be configured or the clock must be set identical on both devices to allow timestamps and call timers to match. Virtual router forwarding (VRF) must be defined in the same order on both active and standby routers for an accurate synchronization of data. The latency times must be minimal on all control and data links to prevent timeouts. Physically redundant links, such as Gigabit EtherChannel, must be used for the control and data paths. OL
4 Configuring Bidirectional Forwarding Restrictions The failover time for a box-to-box application is higher for a non-box-to-box application. LAN and MESH scenarios are not supported. VRFs are not supported and cannot be configured under ZBFW High Availability data and control interfaces. The maximum number of virtual MACs supported by the Front Panel Gigabit Ethernet (FPGE) interfaces depends on the platform. For information about the FPGE interfaces, see the Hardware Installation Guide for the Cisco 4000 Series Integrated Services Routers. When the configuration is replicated to the standby router, it is not committed to the startup configuration; it is in the running configuration. A user must run the write memory command to commit the changes that have been synchronized from the active router, on the standby router. How to Configure Interchassis High Availability For more information on configuring Interchassis High Availability on the router, see the IP Addressing: NAT Configuration Guide, Cisco IOS XE Release 3S. Configuring Bidirectional Forwarding For information on configuring BFD on your router, see the IP Routing BFD Configuration Guide. For BFD commands, see the Cisco IOS IP Routing: Protocol-Independent Command Reference document. Configuring BFD Offload Restrictions Only BFD version 1 is supported. When configured, only offloaded BFD sessions are supported;, BFD session on RP are not supported. Only Asynchronous mode or no echo mode of BFD is supported. 511 asynchronous BFD sessions are supported. BFD hardware offload is supported for IPv4 sessions with non-echo mode only. BFD offload is supported only on port-channel interfaces. BFD offload is supported only for the Ethernet interface. BFD offload is not supported for IPv6 BFD sessions. BFD offload is not supported for BFD with TE/FRR. How to Configure BFD Offload BFD offload functionality is enabled by default. You can configure BFD hardware offload on the route processor. For more information, see Configuring BFD and the IP Routing BFD Configuration Guide. 4 OL
5 Verifying Interchassis High Availability Verifying Interchassis High Availability Use the following show commands to verify the Interchassis High Availability. Note Prerequisites and links to additional documentation configuring Interchassis High Availability are listed in Configuring Interchassis High Availability, on page 3. show redundancy application group [group-id all] show redundancy application transport {client group [group-id]} show redundancy application control-interface group [group-id] show redundancy application faults group [group-id] show redundancy application protocol {protocol-id group [group-id]} show redundancy application if-mgr group [group-id] show redundancy application data-interface group [group-id] The following example shows the redundancy application groups configured on the router: Router# show redundancy application group Group ID Group Name State Generic-Redundancy-1 STANDBY 2 Generic-Redundancy2 ACTIVE The following example shows the details of redundancy application group 1: Router# show redundancy application group 1 Group ID:1 Group Name:Generic-Redundancy-1 Administrative State: No down Aggregate operational state : Up My Role: STANDBY Peer Role: ACTIVE Peer Presence: Yes Peer Comm: Yes Peer Progression Started: Yes RF Domain: btob-one RF state: STANDBY HOT Peer RF state: ACTIVE The following example shows the details of redundancy application group 2: Router# show redundancy application group 2 Group ID:2 Group Name:Generic-Redundancy2 Administrative State: No down Aggregate operational state : Up My Role: ACTIVE Peer Role: STANDBY Peer Presence: Yes Peer Comm: Yes Peer Progression Started: Yes RF Domain: btob-two RF state: ACTIVE Peer RF state: STANDBY HOT OL
6 Verifying Interchassis High Availability The following example shows details of the redundancy application transport client: Router# show redundancy application transport client Client Conn# Priority Interface L3 L4 ( 0)RF 0 1 CTRL IPV4 SCTP ( 1)MCP_HA 1 1 DATA IPV4 UDP_REL ( 4)AR 0 1 ASYM IPV4 UDP ( 5)CF 0 1 DATA IPV4 SCTP The following example shows configuration details for the redundancy application transport group: Router# show redundancy application transport group Transport Information for RG (1) Client = RF CTRL IPV4 SCTP Client = MCP_HA DATA IPV4 UDP_REL Client = AR NONE_IN NONE_L3 NONE_L4 Client = CF DATA IPV4 SCTP Transport Information for RG (2) Client = RF CTRL IPV4 SCTP Client = MCP_HA DATA IPV4 UDP_REL Client = AR NONE_IN NONE_L3 NONE_L4 Client = CF DATA IPV4 SCTP The following example shows the configuration details of redundancy application transport group 1: Router# show redundancy application transport group 1 Transport Information for RG (1) Client = RF CTRL IPV4 SCTP Client = MCP_HA DATA IPV4 UDP_REL Client = AR NONE_IN NONE_L3 NONE_L4 Client = CF DATA IPV4 SCTP The following example shows configuration details of redundancy application transport group 2: Router# show redundancy application transport group 2 Transport Information for RG (2) Client = RF CTRL IPV4 SCTP Client = MCP_HA DATA IPV4 UDP_REL Client = AR NONE_IN NONE_L3 NONE_L4 Client = CF 6 OL
7 Verifying Interchassis High Availability DATA IPV4 SCTP The following example shows configuration details of the redundancy application control-interface group: Router# show redundancy application control-interface group The control interface for rg[1] is GigabitEthernet0/0/0 Interface is Control interface associated with the following protocols: 2 1 BFD Enabled Interface Neighbors: Peer: Active RGs: 1 Standby RGs: 2 BFD handle: 0 The control interface for rg[2] is GigabitEthernet0/0/0 Interface is Control interface associated with the following protocols: 2 1 BFD Enabled Interface Neighbors: Peer: Active RGs: 1 Standby RGs: 2 BFD handle: 0 The following example shows configuration details of the redundancy application control-interface group 1: Router# show redundancy application control-interface group 1 The control interface for rg[1] is GigabitEthernet0/0/0 Interface is Control interface associated with the following protocols: 2 1 BFD Enabled Interface Neighbors: Peer: Active RGs: 1 Standby RGs: 2 BFD handle: 0 The following example shows configuration details of the redundancy application control-interface group 2: Router# show redundancy application control-interface group 2 The control interface for rg[2] is GigabitEthernet0/0/0 Interface is Control interface associated with the following protocols: 2 1 BFD Enabled Interface Neighbors: Peer: Active RGs: 1 Standby RGs: 2 BFD handle: 0 The following example shows configuration details of the redundancy application faults group: Router# show redundancy application faults group Faults states Group 1 info: Runtime priority: [50] RG Faults RG State: Up. Total # of switchovers due to faults: 0 Total # of down/up state changes due to faults: 2 Faults states Group 2 info: Runtime priority: [135] RG Faults RG State: Up. Total # of switchovers due to faults: 0 Total # of down/up state changes due to faults: 2 The following example shows configuration details specific to redundancy application faults group 1: Router# show redundancy application faults group 1 Faults states Group 1 info: Runtime priority: [50] RG Faults RG State: Up. Total # of switchovers due to faults: 0 Total # of down/up state changes due to faults: 2 The following example shows configuration details specific to redundancy application faults group 2: Router# show redundancy application faults group 2 Faults states Group 2 info: Runtime priority: [135] RG Faults RG State: Up. Total # of switchovers due to faults: 0 Total # of down/up state changes due to faults: 2 The following example shows configuration details for the redundancy application protocol group: Router# show redundancy application protocol group RG Protocol RG Role: Standby OL
8 Verifying Interchassis High Availability Negotiation: Enabled Priority: 50 Protocol state: Standby-hot Ctrl Intf(s) state: Up Active Peer: address , priority 150, intf Gi0/0/0 Standby Peer: Local Log counters: role change to active: 0 role change to standby: 1 disable events: rg down state 1, rg shut 0 ctrl intf events: up 2, down 1, admin_down 1 reload events: local request 0, peer request 0 RG Media Context for RG Ctx State: Standby Protocol ID: 1 Media type: Default Control Interface: GigabitEthernet0/0/0 Current Hello timer: 3000 Configured Hello timer: 3000, Hold timer: Peer Hello timer: 3000, Peer Hold timer: Stats: Pkts 117, Bytes 7254, HA Seq 0, Seq Number 117, Pkt Loss 0 Authentication not configured Authentication Failure: 0 Reload Peer: TX 0, RX 0 Resign: TX 0, RX 0 Active Peer: Present. Hold Timer: Pkts 115, Bytes 3910, HA Seq 0, Seq Number , Pkt Loss 0 RG Protocol RG Role: Active Negotiation: Enabled Priority: 135 Protocol state: Active Ctrl Intf(s) state: Up Active Peer: Local Standby Peer: address , priority 130, intf Gi0/0/0 Log counters: role change to active: 1 role change to standby: 1 disable events: rg down state 1, rg shut 0 ctrl intf events: up 2, down 1, admin_down 1 reload events: local request 0, peer request 0 RG Media Context for RG Ctx State: Active Protocol ID: 2 Media type: Default Control Interface: GigabitEthernet0/0/0 Current Hello timer: 3000 Configured Hello timer: 3000, Hold timer: Peer Hello timer: 3000, Peer Hold timer: Stats: Pkts 118, Bytes 7316, HA Seq 0, Seq Number 118, Pkt Loss 0 Authentication not configured Authentication Failure: 0 Reload Peer: TX 0, RX 0 Resign: TX 0, RX 1 Standby Peer: Present. Hold Timer: Pkts 102, Bytes 3468, HA Seq 0, Seq Number , Pkt Loss 0 The following example shows configuration details for the redundancy application protocol group 1: Router# show redundancy application protocol group 1 RG Protocol RG Role: Standby 8 OL
9 Verifying Interchassis High Availability Negotiation: Enabled Priority: 50 Protocol state: Standby-hot Ctrl Intf(s) state: Up Active Peer: address , priority 150, intf Gi0/0/0 Standby Peer: Local Log counters: role change to active: 0 role change to standby: 1 disable events: rg down state 1, rg shut 0 ctrl intf events: up 2, down 1, admin_down 1 reload events: local request 0, peer request 0 RG Media Context for RG Ctx State: Standby Protocol ID: 1 Media type: Default Control Interface: GigabitEthernet0/0/0 Current Hello timer: 3000 Configured Hello timer: 3000, Hold timer: Peer Hello timer: 3000, Peer Hold timer: Stats: Pkts 120, Bytes 7440, HA Seq 0, Seq Number 120, Pkt Loss 0 Authentication not configured Authentication Failure: 0 Reload Peer: TX 0, RX 0 Resign: TX 0, RX 0 Active Peer: Present. Hold Timer: Pkts 118, Bytes 4012, HA Seq 0, Seq Number , Pkt Loss 0 The following example shows configuration details for the redundancy application protocol group 2: Router# show redundancy application protocol group 2 RG Protocol RG Role: Active Negotiation: Enabled Priority: 135 Protocol state: Active Ctrl Intf(s) state: Up Active Peer: Local Standby Peer: address , priority 130, intf Gi0/0/0 Log counters: role change to active: 1 role change to standby: 1 disable events: rg down state 1, rg shut 0 ctrl intf events: up 2, down 1, admin_down 1 reload events: local request 0, peer request 0 RG Media Context for RG Ctx State: Active Protocol ID: 2 Media type: Default Control Interface: GigabitEthernet0/0/0 Current Hello timer: 3000 Configured Hello timer: 3000, Hold timer: Peer Hello timer: 3000, Peer Hold timer: Stats: Pkts 123, Bytes 7626, HA Seq 0, Seq Number 123, Pkt Loss 0 Authentication not configured Authentication Failure: 0 Reload Peer: TX 0, RX 0 Resign: TX 0, RX 1 Standby Peer: Present. Hold Timer: Pkts 107, Bytes 3638, HA Seq 0, Seq Number , Pkt Loss 0 The following example shows configuration details for the redundancy application protocol 1: Router# show redundancy application protocol 1 Protocol id: 1, name: rg-protocol-1 BFD: ENABLE Hello timer in msecs: 3000 OL
10 Verifying Interchassis High Availability Hold timer in msecs: OVLD-1#show redundancy application protocol 2 Protocol id: 2, name: rg-protocol-2 BFD: ENABLE Hello timer in msecs: 3000 Hold timer in msecs: The following example shows configuration details for redundancy application interface manager group: Router# show redundancy application if-mgr group RG ID: 1 ========== interface GigabitEthernet0/0/ b421.4e21 VIP shut interface GigabitEthernet0/0/ b VIP shut RG ID: 2 ========== interface GigabitEthernet0/0/ b422.14d6 VIP no shut interface GigabitEthernet0/0/ b422.0d06 VIP no shut The following examples shows configuration details for redundancy application interface manager group 1 and group 2: Router# show redundancy application if-mgr group 1 RG ID: 1 ========== interface GigabitEthernet0/0/ b421.4e21 VIP shut interface GigabitEthernet0/0/ b VIP shut Router# show redundancy application if-mgr group 2 RG ID: 2 ========== interface GigabitEthernet0/0/ OL
11 Verifying BFD Offload 0007.b422.14d6 VIP no shut interface GigabitEthernet0/0/ b422.0d06 VIP no shut The following example shows configuration details for redundancy application data-interface group: Router# show redundancy application data-interface group The data interface for rg[1] is GigabitEthernet0/0/1 The data interface for rg[2] is GigabitEthernet0/0/1 The following examples show configuration details specific to redundancy application data-interface group 1 and group 2: Router# show redundancy application data-interface group 1 The data interface for rg[1] is GigabitEthernet0/0/1 Router # show redundancy application data-interface group 2 The data interface for rg[2] is GigabitEthernet0/0/1 Verifying BFD Offload Use the following commands to verify and monitor BFD offload feature on your router. Note Configuration of BFD Offload is described in Configuring Bidirectional Forwarding, on page 4. show bfd neighbors [details] debug bfd [packet event] debug bfd event The show bfd neighbors command displays the BFD adjacency database: Router# show bfd neighbor IPv4 Sessions NeighAddr LD/RD RH/RS State Int /1277 Up Up Gi0/0/ /1278 Up Up Gi0/0/ /961 Up Up Gi0/0/ /946 Up Up Gi0/0/ /937 Up Up Gi0/0/ /1260 Up Up Gi0/0/ /929 Up Up Gi0/0/ /928 Up Up Gi0/0/ /1254 Up Up Gi0/0/1.10 The debug bfd neighbor detail command displays the debugging information related to BFD packets: Router# show bfd neighbor detail IPv4 Sessions NeighAddr LD/RD RH/RS State Int /1277 Up Up Gi0/0/1.2 Session state is UP and not using echo function. Session Host: Hardware OurAddr: Handle: 33 OL
12 Verifying BFD Offload Local Diag: 0, Demand mode: 0, Poll bit: 0 MinTxInt: 50000, MinRxInt: 50000, Multiplier: 3 Received MinRxInt: 50000, Received Multiplier: 3 Holddown (hits): 0(0), Hello (hits): 50(0) Rx Count: 3465, Rx Interval (ms) min/max/avg: 42/51/46 Tx Count: 3466, Tx Interval (ms) min/max/avg: 39/52/46 Elapsed time watermarks: 0 0 (last: 0) Registered protocols: CEF EIGRP Uptime: 00:02:50 Last packet: Version: 1 - Diagnostic: 0 State bit: Up - Demand bit: 0 Poll bit: 0 - Final bit: 0 C bit: 1 Multiplier: 3 - Length: 24 My Discr.: Your Discr.: 362 Min tx interval: Min rx interval: Min Echo interval: 0 The show bfd summary command displays the BFD summary: Router# show bfd summary Session Up Down Total The show bfd drops command displays the number of packets dropped in BFD: Router# show bfd drops BFD Drop Statistics IPV4 IPV6 IPV4-M IPV6-M MPLS_PW MPLS_TP_LSP Invalid TTL BFD Not Configured No BFD Adjacency Invalid Header Bits Invalid Discriminator Session AdminDown Authen invalid BFD ver Authen invalid len Authen invalid seq Authen failed The debug bfd packet command displays debugging information about BFD control packets. Router# debug bfd packet *Nov 12 23:08:27.982: BFD-DEBUG Packet: Rx IP: ld/rd:1941/0 diag:0(no Diagnostic) Down C cnt:4 ttl:254 (0) *Nov 12 23:08:27.982: BFD-DEBUG Packet: Tx IP: ld/rd:983/1941 diag:3(neighbor Signaled Session Down) Init C cnt:44 (0) *Nov 12 23:08:28.007: BFD-DEBUG Packet: Rx IP: ld/rd:1941/983 diag:0(no Diagnostic) Up PC cnt:4 ttl:254 (0) *Nov 12 23:08:28.007: BFD-DEBUG Packet: Tx IP: ld/rd:983/1941 diag:0(no Diagnostic) Up F C cnt:0 (0) *Nov 12 23:08:28.311: BFD-DEBUG Packet: Rx IP: ld/rd:1941/983 diag:0(no Diagnostic) Up FC cnt:0 ttl:254 (0) *Nov 12 23:08:28.311: BFD-DEBUG Packet: Tx IP: ld/rd:983/1941 diag:0(no Diagnostic) Up C cnt:0 (0) *Nov 12 23:08:28.311: BFD-DEBUG Packet: Rx IP: ld/rd:1907/0 diag:0(no Diagnostic) Down C cnt:3 ttl:254 (0) *Nov 12 23:08:28.311: BFD-DEBUG Packet: Tx IP: ld/rd:993/1907 diag:3(neighbor Signaled Session Down) Init C cnt:43 (0) *Nov 12 23:08:28.311: BFD-DEBUG Packet: Rx IP: ld/rd:1941/983 diag:0(no Diagnostic) Up C cnt:0 ttl:254 (0) *Nov 12 23:08:28.626: BFD-DEBUG Packet: Rx IP: ld/rd:1907/993 diag:0(no Diagnostic) Up PC cnt:3 ttl:254 (0) *Nov 12 23:08:28.626: BFD-DEBUG Packet: Tx IP: ld/rd:993/1907 diag:0(no Diagnostic) Up F C cnt:0 (0) *Nov 12 23:08:28.645: BFD-DEBUG Packet: Rx IP: ld/rd:1907/993 diag:0(no Diagnostic) Up C cnt:0 ttl:254 (0) *Nov 12 23:08:28.700: BFD-DEBUG Packet: Rx IP: ld/rd:1907/993 diag:0(no Diagnostic) Up FC cnt:0 ttl:254 (0) *Nov 12 23:08:28.700: BFD-DEBUG Packet: Tx IP: ld/rd:993/1907 diag:0(no Diagnostic) Up C cnt:0 (0) *Nov 12 23:08:28.993: BFD-DEBUG Packet: Rx IP: ld/rd:1907/993 diag:0(no Diagnostic) Up C cnt:0 ttl:254 (0) 12 OL
13 Additional References The debug bfd event displays debugging information about BFD state transitions: Router# deb bfd event *Nov 12 23:11:29.503: BFD-DEBUG Event: notify client(eigrp) IP: , ld:1401, handle:77, *Nov 12 23:11:29.503: BFD-DEBUG Event: notify client(cef) IP: , ld:1401, handle:77, *Nov 12 23:11:29.503: BFD-DEBUG Event: notify client(eigrp) IP: , ld:1400, handle:39, *Nov 12 23:11:29.503: BFD-DEBUG Event: notify client(cef) IP: , ld:1400, handle:39, *Nov 12 23:11:29.503: BFD-DEBUG Event: notify client(eigrp) IP: , ld:1399, handle:25, *Nov 12 23:11:29.503: BFD-DEBUG Event: notify client(cef) IP: , ld:1399, handle:25, *Nov 12 23:11:29.503: BFD-DEBUG Event: notify client(eigrp) IP: , ld:1403, handle:173, *Nov 12 23:11:29.503: BFD-DEBUG Event: notify client(cef) IP: , ld:1403, handle:173, *Nov 12 23:11:29.503: BFD-DEBUG Event: notify client(eigrp) IP: , ld:1402, handle:95, *Nov 12 23:11:29.503: BFD-DEBUG Event: notify client(cef) IP: , ld:1402, handle:95, *Nov 12 23:11:30.639: BFD-HW-API: Handle 1404: Timers: Tx timer Detect timer 0 *Nov 12 23:11:30.639: BFD-HW-API: Handle 1404: Flags: Poll 0 Final 0 *Nov 12 23:11:30.639: BFD-HW-API: Handle 1404: Buffer: 0x x C 0x x000F4240 0x000F4240 0x size 24 *Nov 12 23:11:30.641: BFD-HW-API: Handle 1405: Timers: Tx timer Detect timer 0 *Nov 12 23:11:30.641: BFD-HW-API: Handle 1405: Flags: Poll 0 Final 0 *Nov 12 23:11:30.641: BFD-HW-API: Handle 1405: Buffer: 0x x D 0x x000F4240 0x000F4240 0x size 24 *Nov 12 23:11:30.649: BFD-DEBUG Packet: Rx IP: ld/rd:1601/1404 diag:7(administratively Down) AdminDown C cnt:0 ttl:254 (0) *Nov 12 23:11:30.650: BFD-DEBUG Event: V1 FSM ld:1404 handle:207 event:rx ADMINDOWN state:up (0) *Nov 12 23:11:30.650: BFD-DEBUG Event: resetting timestamps ld:1404 handle:207 (0) *Nov 12 23:11:30.650: BFD-DEBUG Event: notify client(cef) IP: , ld:1404, handle:207, *Nov 12 23:11:30.650: BFD-DEBUG Packet: Tx IP: ld/rd:1404/0 diag:3(neighbor Signaled Session Down) Down C cnt:0 (0) *Nov 12 23:11:30.650: BFD-DEBUG Packet: Rx IP: ld/rd:1620/1405 diag:7(administratively Down) AdminDown C cnt:0 ttl:254 (0) *Nov 12 23:11:30.650: BFD-DEBUG Event: V1 FSM ld:1405 handle:209 event:rx ADMINDOWN state:up (0) *Nov 12 23:11:30.650: BFD-DEBUG Event: resetting timestamps ld:1405 handle:209 (0) *Nov 12 23:11:30.650: BFD-DEBUG Event: notify client(cef) IP: , ld:1405, handle:209, *Nov 12 23:11:30.650: BFD-DEBUG Packet: Tx IP: ld/rd:1405/0 diag:3(neighbor Signaled Session Down) Down C cnt:0 (0) *Nov 12 23:11:30.650: BFD-DEBUG Event: notify client(eigrp) IP: , ld:1404, handle:207, *Nov 12 23:11:30.650: BFD-DEBUG Event: notify client(cef) IP: , ld:1404, handle:207, *Nov 12 23:11:30.650: BFD-DEBUG Event: notify client(eigrp) IP: , ld:1405, handle:209, *Nov 12 23:11:30.650: BFD-DEBUG Event: notify client(cef) IP: , ld:1405, handle:209, *Nov 12 23:11:31.035: %DUAL-5-NBRCHANGE: EIGRP-IPv4 100: Neighbor Additional References The following documents provide information related to the BFD feature. OL
14 Additional References Related Topic Configuring Stateful Interchassis Configuration. IP Routing Protocol-Independent Commands. Document Title Security Configuration Guide: Zone-Based Policy Firewall, Cisco IOS XE Release 3S at: sec_data_zbf/configuration/xe-3s/ sec-data-zbf-xe-book.html. Cisco IOS IP Routing: Protocol-Independent Command Reference at: us/td/docs/ios-xml/ios/iproute_pi/command/ iri-cr-book.html. 14 OL
Configuring Stateful Interchassis Redundancy
 The Stateful Interchassis Redundancy feature enables you to configure pairs of devices to act as backups for each other. This module describes conceptual information about and tasks for configuring stateful
The Stateful Interchassis Redundancy feature enables you to configure pairs of devices to act as backups for each other. This module describes conceptual information about and tasks for configuring stateful
Zone-Based Policy Firewall High Availability
 The feature enables you to configure pairs of devices to act as backup for each other. High availability can be configured to determine the active device based on a number of failover conditions. When
The feature enables you to configure pairs of devices to act as backup for each other. High availability can be configured to determine the active device based on a number of failover conditions. When
Reducing Failure Detection Times in IS-IS Networks
 Reducing Failure Detection Times in IS-IS Networks This module describes how to customize IS-IS configuration to help you achieve fast convergence in your network. This module describes how to configure
Reducing Failure Detection Times in IS-IS Networks This module describes how to customize IS-IS configuration to help you achieve fast convergence in your network. This module describes how to configure
IP Routing: BFD Configuration Guide, Cisco IOS XE Release 3S (Cisco ASR 900 Series)
 IP Routing: BFD Configuration Guide, Cisco IOS XE Release 3S (Cisco ASR 900 Series) Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel:
IP Routing: BFD Configuration Guide, Cisco IOS XE Release 3S (Cisco ASR 900 Series) Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel:
Cisco NX-OS Interfaces Commands
 This chapter describes the Cisco NX-OS interfaces commands. IF-1 attach fex attach fex To access the command-line interface (CLI) of a connected Fabric Extender to run diagnostic commands, use the attach
This chapter describes the Cisco NX-OS interfaces commands. IF-1 attach fex attach fex To access the command-line interface (CLI) of a connected Fabric Extender to run diagnostic commands, use the attach
Interchassis Asymmetric Routing Support for Zone-Based Firewall and NAT
 Interchassis Asymmetric Routing Support for Zone-Based Firewall and NAT The Interchassis Asymmetric Routing Support for Zone-Based Firewall and NAT feature supports the forwarding of packets from a standby
Interchassis Asymmetric Routing Support for Zone-Based Firewall and NAT The Interchassis Asymmetric Routing Support for Zone-Based Firewall and NAT feature supports the forwarding of packets from a standby
Operation Manual BFD-GR H3C S3610&S5510 Series Ethernet Switches. Table of Contents
 Table of Contents Table of Contents... 1-1 1.1 Introduction to BFD... 1-1 1.1.1 How BFD Works... 1-1 1.1.2 BFD Packet Format... 1-3 1.1.3 Protocols and Standards... 1-5 1.2 BFD Configuration Task List...
Table of Contents Table of Contents... 1-1 1.1 Introduction to BFD... 1-1 1.1.1 How BFD Works... 1-1 1.1.2 BFD Packet Format... 1-3 1.1.3 Protocols and Standards... 1-5 1.2 BFD Configuration Task List...
BFD on BDI Interfaces
 The Cisco feature alleviates limitations on the maximum number of interfaces per system that switched virtual interfaces (SVI) impose. This document describes how to configure the Bidirectional Forwarding
The Cisco feature alleviates limitations on the maximum number of interfaces per system that switched virtual interfaces (SVI) impose. This document describes how to configure the Bidirectional Forwarding
Bidirectional Forwarding Detection
 Bidirectional Forwarding Detection This document describes how to enable the Bidirectional Forwarding Detection (BFD) protocol. BFD is a detection protocol designed to provide fast forwarding path failure
Bidirectional Forwarding Detection This document describes how to enable the Bidirectional Forwarding Detection (BFD) protocol. BFD is a detection protocol designed to provide fast forwarding path failure
NAT Box-to-Box High-Availability Support
 The feature enables network-wide protection by making an IP network more resilient to potential link and router failures at the Network Address Translation (NAT) border. NAT box-to-box high-availability
The feature enables network-wide protection by making an IP network more resilient to potential link and router failures at the Network Address Translation (NAT) border. NAT box-to-box high-availability
Configuring High Availability
 This section contains the following topics: Information about High Availability, on page 1 Error Messages for Amazon Web Services High Availability, on page 3 How to Configure High Availability, on page
This section contains the following topics: Information about High Availability, on page 1 Error Messages for Amazon Web Services High Availability, on page 3 How to Configure High Availability, on page
Routing Configuration Guide, Cisco IOS XE Everest a (Catalyst 9300 Switches)
 Routing Configuration Guide, Cisco IOS XE Everest 16.5.1a (Catalyst 9300 Switches) First Published: 2017-06-20 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA
Routing Configuration Guide, Cisco IOS XE Everest 16.5.1a (Catalyst 9300 Switches) First Published: 2017-06-20 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA
FlexVPN HA Dual Hub Configuration Example
 FlexVPN HA Dual Hub Configuration Example Document ID: 118888 Contributed by Piotr Kupisiewicz, Wen Zhang, and Frederic Detienne, Cisco TAC Engineers. Apr 08, 2015 Contents Introduction Prerequisites Requirements
FlexVPN HA Dual Hub Configuration Example Document ID: 118888 Contributed by Piotr Kupisiewicz, Wen Zhang, and Frederic Detienne, Cisco TAC Engineers. Apr 08, 2015 Contents Introduction Prerequisites Requirements
Configuring HSRP. Finding Feature Information. Restrictions for HSRP
 The Hot Standby Router Protocol (HSRP) is a First Hop Redundancy Protocol (FHRP) designed to allow for transparent failover of the first-hop IP device. HSRP provides high network availability by providing
The Hot Standby Router Protocol (HSRP) is a First Hop Redundancy Protocol (FHRP) designed to allow for transparent failover of the first-hop IP device. HSRP provides high network availability by providing
Link Bundling Commands
 Link Bundling Commands This module provides command line interface (CLI) commands for configuring Link Bundle interfaces on the Cisco NCS 5000 Series Router. For detailed information about Link Bundle
Link Bundling Commands This module provides command line interface (CLI) commands for configuring Link Bundle interfaces on the Cisco NCS 5000 Series Router. For detailed information about Link Bundle
Feature History for Implementing Bidirectional Forwarding Detection
 Implementing BFD This module describes the configuration of bidirectional forwarding detection (BFD) on the Cisco CRS Router. Bidirectional forwarding detection (BFD) provides low-overhead, short-duration
Implementing BFD This module describes the configuration of bidirectional forwarding detection (BFD) on the Cisco CRS Router. Bidirectional forwarding detection (BFD) provides low-overhead, short-duration
Configuring VRRP. Finding Feature Information. The Virtual Router Redundancy Protocol (VRRP) is an election protocol that dynamically assigns
 The Virtual Router Redundancy Protocol (VRRP) is an election protocol that dynamically assigns responsibility for one or more virtual routers to the VRRP routers on a LAN, allowing several routers on a
The Virtual Router Redundancy Protocol (VRRP) is an election protocol that dynamically assigns responsibility for one or more virtual routers to the VRRP routers on a LAN, allowing several routers on a
IP Routing BFD Configuration Guide, Cisco IOS Release 12.2SX
 IP Routing BFD Configuration Guide, Cisco IOS Release 12.2SX Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS
IP Routing BFD Configuration Guide, Cisco IOS Release 12.2SX Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS
Cisco Nexus 7000 Series NX-OS Interfaces Command Reference
 Cisco Nexus 7000 Series NX-OS Interfaces Command Reference July 2011 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800
Cisco Nexus 7000 Series NX-OS Interfaces Command Reference July 2011 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800
Configuring Virtual Port Channels
 This chapter contains the following sections: Information About vpcs, page 1 Guidelines and Limitations for vpcs, page 10 Configuring vpcs, page 11 Verifying the vpc Configuration, page 25 vpc Default
This chapter contains the following sections: Information About vpcs, page 1 Guidelines and Limitations for vpcs, page 10 Configuring vpcs, page 11 Verifying the vpc Configuration, page 25 vpc Default
EIGRP Nonstop Forwarding
 EIGRP nonstop forwarding (NSF) capabilities are exchanged by EIGRP peers in hello packets. NSF works with the SSO feature in Cisco software to minimize the amount of time that a network is unavailable
EIGRP nonstop forwarding (NSF) capabilities are exchanged by EIGRP peers in hello packets. NSF works with the SSO feature in Cisco software to minimize the amount of time that a network is unavailable
Configuring StackWise Virtual
 Finding Feature Information, page 1 Restrictions for Cisco StackWise Virtual, page 1 Prerequisites for Cisco StackWise Virtual, page 2 Information About Cisco Stackwise Virtual, page 2 Cisco StackWise
Finding Feature Information, page 1 Restrictions for Cisco StackWise Virtual, page 1 Prerequisites for Cisco StackWise Virtual, page 2 Information About Cisco Stackwise Virtual, page 2 Cisco StackWise
Configuring Virtual Port Channels
 Configuring Virtual Port Channels This chapter describes how to configure virtual port channels (vpcs) on Cisco Nexus 5000 Series switches. It contains the following sections: Information About vpcs, page
Configuring Virtual Port Channels This chapter describes how to configure virtual port channels (vpcs) on Cisco Nexus 5000 Series switches. It contains the following sections: Information About vpcs, page
Configuring Virtual Port Channels
 This chapter contains the following sections: Information About vpcs vpc Overview Information About vpcs, on page 1 Guidelines and Limitations for vpcs, on page 11 Verifying the vpc Configuration, on page
This chapter contains the following sections: Information About vpcs vpc Overview Information About vpcs, on page 1 Guidelines and Limitations for vpcs, on page 11 Verifying the vpc Configuration, on page
BFD on BDI Interfaces
 The Cisco feature alleviates limitations on the maximum number of interfaces per system that switched virtual interfaces (SVI) impose. This document describes how to configure the Bidirectional Forwarding
The Cisco feature alleviates limitations on the maximum number of interfaces per system that switched virtual interfaces (SVI) impose. This document describes how to configure the Bidirectional Forwarding
First Hop Redundancy Protocols Configuration Guide, Cisco IOS XE Release 3SE (Catalyst 3850 Switches)
 First Hop Redundancy Protocols Configuration Guide, Cisco IOS XE Release 3SE (Catalyst 3850 Switches) Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com
First Hop Redundancy Protocols Configuration Guide, Cisco IOS XE Release 3SE (Catalyst 3850 Switches) Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com
Configuring IEEE 802.3ad Link Bundling and Load Balancing
 Configuring IEEE 802.3ad Link Bundling and Load Balancing This document describes how the IEEE 802.3ad link bundling and load balancing leverages the EtherChannel infrastructure within Cisco software to
Configuring IEEE 802.3ad Link Bundling and Load Balancing This document describes how the IEEE 802.3ad link bundling and load balancing leverages the EtherChannel infrastructure within Cisco software to
Configuring Virtual Port Channels
 This chapter contains the following sections: Information About vpcs, page 1 Guidelines and Limitations for vpcs, page 10 Verifying the vpc Configuration, page 11 vpc Default Settings, page 16 Configuring
This chapter contains the following sections: Information About vpcs, page 1 Guidelines and Limitations for vpcs, page 10 Verifying the vpc Configuration, page 11 vpc Default Settings, page 16 Configuring
C. The ESP that is installed in the Cisco ASR 1006 Router does not support SSO.
 Volume: 197 Questions Question No : 1 SSO was configured on a Cisco ASR 1006 Router by using two RPs. When the main RP failed, a service disruption occurred. What are two reasons that the SSO did not work?
Volume: 197 Questions Question No : 1 SSO was configured on a Cisco ASR 1006 Router by using two RPs. When the main RP failed, a service disruption occurred. What are two reasons that the SSO did not work?
Configuring Cisco NSF with SSO Supervisor Engine Redundancy
 CHAPTER 9 Configuring Cisco NSF with SSO Supervisor Engine Redundancy This chapter describes how to configure supervisor engine redundancy using Cisco nonstop forwarding (NSF) with stateful switchover
CHAPTER 9 Configuring Cisco NSF with SSO Supervisor Engine Redundancy This chapter describes how to configure supervisor engine redundancy using Cisco nonstop forwarding (NSF) with stateful switchover
Cisco Exam Troubleshooting and Maintaining Cisco IP Networks (TSHOOT) Version: 6.0 [ Total Questions: 79 ]
![Cisco Exam Troubleshooting and Maintaining Cisco IP Networks (TSHOOT) Version: 6.0 [ Total Questions: 79 ] Cisco Exam Troubleshooting and Maintaining Cisco IP Networks (TSHOOT) Version: 6.0 [ Total Questions: 79 ]](/thumbs/96/129009026.jpg) s@lm@n Cisco Exam 300-135 Troubleshooting and Maintaining Cisco IP Networks (TSHOOT) Version: 6.0 [ Total Questions: 79 ] Topic break down Topic No. of Questions Topic 1: Mix Questions 26 Topic 2: Troubleshooting
s@lm@n Cisco Exam 300-135 Troubleshooting and Maintaining Cisco IP Networks (TSHOOT) Version: 6.0 [ Total Questions: 79 ] Topic break down Topic No. of Questions Topic 1: Mix Questions 26 Topic 2: Troubleshooting
CUBE High Availability Overview
 High Availability (HA) is a feature that ensures the availability of resources in a computer system, in case of component failures in the system. The unique hardware and software architecture of the Cisco
High Availability (HA) is a feature that ensures the availability of resources in a computer system, in case of component failures in the system. The unique hardware and software architecture of the Cisco
Identity Firewall. About the Identity Firewall
 This chapter describes how to configure the ASA for the. About the, on page 1 Guidelines for the, on page 7 Prerequisites for the, on page 9 Configure the, on page 10 Monitoring the, on page 16 History
This chapter describes how to configure the ASA for the. About the, on page 1 Guidelines for the, on page 7 Prerequisites for the, on page 9 Configure the, on page 10 Monitoring the, on page 16 History
WiNG 5.x How-To Guide
 WiNG 5.x How-To Guide Tunneling Remote Traffic using L2TPv3 Part No. TME-08-2012-01 Rev. A MOTOROLA, MOTO, MOTOROLA SOLUTIONS and the Stylized M Logo are trademarks or registered trademarks of Motorola
WiNG 5.x How-To Guide Tunneling Remote Traffic using L2TPv3 Part No. TME-08-2012-01 Rev. A MOTOROLA, MOTO, MOTOROLA SOLUTIONS and the Stylized M Logo are trademarks or registered trademarks of Motorola
Cisco ASR 1000 Series Aggregation Services Routers: ISSU Deployment Guide and Case Study
 Cisco ASR 1000 Series Aggregation Services Routers: ISSU Deployment Guide and Case Study In most networks, a significant cause of downtime is planned maintenance and software upgrades. The Cisco ASR 1000
Cisco ASR 1000 Series Aggregation Services Routers: ISSU Deployment Guide and Case Study In most networks, a significant cause of downtime is planned maintenance and software upgrades. The Cisco ASR 1000
Contents. Configuring EVI 1
 Contents Configuring EVI 1 Overview 1 Layer 2 connectivity extension issues 1 Network topologies 2 Terminology 3 Working mechanism 4 Placement of Layer 3 gateways 6 ARP flood suppression 7 Selective flood
Contents Configuring EVI 1 Overview 1 Layer 2 connectivity extension issues 1 Network topologies 2 Terminology 3 Working mechanism 4 Placement of Layer 3 gateways 6 ARP flood suppression 7 Selective flood
debug backhaul-session-manager session through debug channel packets, page 1
 debug backhaul-session-manager session through debug channel packets debug backhaul-session-manager session through debug channel packets, page 1 debug backhaul-session-manager session through debug channel
debug backhaul-session-manager session through debug channel packets debug backhaul-session-manager session through debug channel packets, page 1 debug backhaul-session-manager session through debug channel
standby arp gratuitous through track vrrp
 standby arp gratuitous, page 2 standby authentication, page 4 standby bfd, page 7 standby bfd all-interfaces, page 9 standby delay minimum reload, page 11 standby follow, page 13 standby ip, page 15 standby
standby arp gratuitous, page 2 standby authentication, page 4 standby bfd, page 7 standby bfd all-interfaces, page 9 standby delay minimum reload, page 11 standby follow, page 13 standby ip, page 15 standby
Configuring Virtual Private LAN Services
 Virtual Private LAN Services (VPLS) enables enterprises to link together their Ethernet-based LANs from multiple sites via the infrastructure provided by their service provider. This module explains VPLS
Virtual Private LAN Services (VPLS) enables enterprises to link together their Ethernet-based LANs from multiple sites via the infrastructure provided by their service provider. This module explains VPLS
Bidirectional Forwarding Detection (BFD) NANOG 39
 An Introduction to Bidirectional Forwarding Detection (BFD) NANOG 39 Aamer Akhter / aa@cisco.com ECMD, cisco Systems 1 Why BFD? Methods needed to quickly determine forwarding failure Not everything is
An Introduction to Bidirectional Forwarding Detection (BFD) NANOG 39 Aamer Akhter / aa@cisco.com ECMD, cisco Systems 1 Why BFD? Methods needed to quickly determine forwarding failure Not everything is
Configuring VRRP. Finding Feature Information. Contents
 Configuring VRRP First Published: May 2, 2005 Last Updated: July 30, 2010 The Virtual Router Redundancy Protocol (VRRP) is an election protocol that dynamically assigns responsibility for one or more virtual
Configuring VRRP First Published: May 2, 2005 Last Updated: July 30, 2010 The Virtual Router Redundancy Protocol (VRRP) is an election protocol that dynamically assigns responsibility for one or more virtual
VRRPv3 Protocol Support
 Virtual Router Redundancy Protocol (VRRP) enables a group of routers to form a single virtual router to provide redundancy. The LAN clients can then be configured with the virtual router as their default
Virtual Router Redundancy Protocol (VRRP) enables a group of routers to form a single virtual router to provide redundancy. The LAN clients can then be configured with the virtual router as their default
Redundancy Commands CHAPTER
 CHAPTER 7 CPU switch module redundancy provides protection against CPU switch module failure. Use the following commands to configure and monitor CPU switch module redundancy operations. 7-1 auto-sync
CHAPTER 7 CPU switch module redundancy provides protection against CPU switch module failure. Use the following commands to configure and monitor CPU switch module redundancy operations. 7-1 auto-sync
Configuring Redundant Routing on the VPN 3000 Concentrator
 Configuring Redundant Routing on the VPN 3000 Concentrator Document ID: 13354 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Router Configurations
Configuring Redundant Routing on the VPN 3000 Concentrator Document ID: 13354 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Router Configurations
Highly Available Wide Area Network Design
 Highly Available Wide Area Network Design David Prall, Communications Architect dprall@cisco.com CCIE #6508 (R&S/SP/Security) BRKRST-2042 Agenda Introduction Cisco IOS and IP Routing Convergence Techniques
Highly Available Wide Area Network Design David Prall, Communications Architect dprall@cisco.com CCIE #6508 (R&S/SP/Security) BRKRST-2042 Agenda Introduction Cisco IOS and IP Routing Convergence Techniques
Stack Manager and High Availability
 debug platform stack-manager, on page 2 mode sso, on page 3 main-cpu, on page 4 policy config-sync prc reload, on page 5 mode sso, on page 6 policy config-sync prc reload, on page 7 redundancy config-sync
debug platform stack-manager, on page 2 mode sso, on page 3 main-cpu, on page 4 policy config-sync prc reload, on page 5 mode sso, on page 6 policy config-sync prc reload, on page 7 redundancy config-sync
Using the Management Ethernet Interface
 This chapter covers the following topics: Gigabit Ethernet Management Interface Overview, page 1 Gigabit Ethernet Port Numbering, page 1 IP Address Handling in ROMmon and the Management Ethernet Port,
This chapter covers the following topics: Gigabit Ethernet Management Interface Overview, page 1 Gigabit Ethernet Port Numbering, page 1 IP Address Handling in ROMmon and the Management Ethernet Port,
Network-Level High Availability
 This chapter describes Cisco NX-OS network high availability and includes the following sections: Information About, page 1 Licensing Requirements, page 2 Spanning Tree Protocol, page 2 Virtual Port Channels,
This chapter describes Cisco NX-OS network high availability and includes the following sections: Information About, page 1 Licensing Requirements, page 2 Spanning Tree Protocol, page 2 Virtual Port Channels,
VRRP Aware PIM with PIM NonDR Join Feature Configuration Example
 VRRP Aware PIM with PIM NonDR Join Feature Configuration Example Document ID: 118859 Contributed by Mohammed Muddasir Khan, Cisco TAC Engineer. Mar 26, 2015 Contents Introduction Prerequisites Requirements
VRRP Aware PIM with PIM NonDR Join Feature Configuration Example Document ID: 118859 Contributed by Mohammed Muddasir Khan, Cisco TAC Engineer. Mar 26, 2015 Contents Introduction Prerequisites Requirements
Segment Routing On Demand for L2VPN/VPWS
 On-Demand Next Hop (ODN) for Layer 2 Virtual Private Network (L2VPN) creates a segment routing (SR) traffic-engineering (TE) auto-tunnel and uses the auto-tunnel for pseudowire dataplane. Restrictions
On-Demand Next Hop (ODN) for Layer 2 Virtual Private Network (L2VPN) creates a segment routing (SR) traffic-engineering (TE) auto-tunnel and uses the auto-tunnel for pseudowire dataplane. Restrictions
NSF SSO ISSU Support for VPLS
 Virtual Private LAN Services (VPLS), with nonstop forwarding (NSF), stateful switchover (SSO), and in service software upgrade (ISSU) support, improves the availability of service provider networks that
Virtual Private LAN Services (VPLS), with nonstop forwarding (NSF), stateful switchover (SSO), and in service software upgrade (ISSU) support, improves the availability of service provider networks that
Static NAT Mapping with HSRP
 This module contains procedures for configuring Network Address Translation (NAT) to support the increasing need for highly resilient IP networks. This network resiliency is required where application
This module contains procedures for configuring Network Address Translation (NAT) to support the increasing need for highly resilient IP networks. This network resiliency is required where application
EIGRP on SVTI, DVTI, and IKEv2 FlexVPN with the "IP[v6] Unnumbered" Command Configuration Example
![EIGRP on SVTI, DVTI, and IKEv2 FlexVPN with the IP[v6] Unnumbered Command Configuration Example EIGRP on SVTI, DVTI, and IKEv2 FlexVPN with the IP[v6] Unnumbered Command Configuration Example](/thumbs/92/108645128.jpg) EIGRP on SVTI, DVTI, and IKEv2 FlexVPN with the "IP[v6] Unnumbered" Command Configuration Example Document ID: 116346 Contributed by Michal Garcarz and Olivier Pelerin, Cisco TAC Engineers. Sep 18, 2013
EIGRP on SVTI, DVTI, and IKEv2 FlexVPN with the "IP[v6] Unnumbered" Command Configuration Example Document ID: 116346 Contributed by Michal Garcarz and Olivier Pelerin, Cisco TAC Engineers. Sep 18, 2013
Chapter 6 Lab 6-3, Gateway Load Balancing Protocol (GLBP) INSTRUCTOR VERSION
 CCNPv7.1 SWITCH Chapter 6 Lab 6-3, Gateway Load Balancing Protocol (GLBP) INSTRUCTOR VERSION Topology Objectives Configure trunking, VTP, and inter-vlan routing using router-on-a stick Configure GLBP Configure
CCNPv7.1 SWITCH Chapter 6 Lab 6-3, Gateway Load Balancing Protocol (GLBP) INSTRUCTOR VERSION Topology Objectives Configure trunking, VTP, and inter-vlan routing using router-on-a stick Configure GLBP Configure
Resilient Ethernet Protocol (REP)
 The is a Cisco proprietary protocol that provides an alternative to the Spanning Tree Protocol (STP). REP provides a way to control network loops, handle link failures, and improve convergence time. It
The is a Cisco proprietary protocol that provides an alternative to the Spanning Tree Protocol (STP). REP provides a way to control network loops, handle link failures, and improve convergence time. It
Performance Routing (PfR) Master Controller Redundancy Configuration
 Performance Routing (PfR) Master Controller Redundancy Configuration This application note provides an overview on how to configure a Performance Routing (PfR) master controller in a redundant configuration.
Performance Routing (PfR) Master Controller Redundancy Configuration This application note provides an overview on how to configure a Performance Routing (PfR) master controller in a redundant configuration.
Configuring Bridge Domain Interfaces
 The Cisco ASR 1000 Series Aggregation Services Routers support the bridge domain interface (BDI) feature for packaging Layer 2 Ethernet segments into Layer 3 IP. Restrictions for Bridge Domain Interfaces,
The Cisco ASR 1000 Series Aggregation Services Routers support the bridge domain interface (BDI) feature for packaging Layer 2 Ethernet segments into Layer 3 IP. Restrictions for Bridge Domain Interfaces,
Configuring Pseudowire Group Switchover
 Note Pseudowire Group Switchover configuration is not supported on the Cisco ASR 900 RSP3 module. Pseudowire Group Switchover Configuration, page 1 Pseudowire Group Switchover, page 2 Configuring Predictive
Note Pseudowire Group Switchover configuration is not supported on the Cisco ASR 900 RSP3 module. Pseudowire Group Switchover Configuration, page 1 Pseudowire Group Switchover, page 2 Configuring Predictive
HP Load Balancing Module
 HP Load Balancing Module High Availability Configuration Guide Part number: 5998-2687 Document version: 6PW101-20120217 Legal and notice information Copyright 2012 Hewlett-Packard Development Company,
HP Load Balancing Module High Availability Configuration Guide Part number: 5998-2687 Document version: 6PW101-20120217 Legal and notice information Copyright 2012 Hewlett-Packard Development Company,
Configuring static routing
 Contents Configuring static routing 1 Introduction 1 Static route 1 Default route 1 Static route configuration items 1 Configuring a static route 2 Configuration prerequisites 2 Configuration procedure
Contents Configuring static routing 1 Introduction 1 Static route 1 Default route 1 Static route configuration items 1 Configuring a static route 2 Configuration prerequisites 2 Configuration procedure
HP Routing Switch Series
 HP 12500 Routing Switch Series EVI Configuration Guide Part number: 5998-3419 Software version: 12500-CMW710-R7128 Document version: 6W710-20121130 Legal and notice information Copyright 2012 Hewlett-Packard
HP 12500 Routing Switch Series EVI Configuration Guide Part number: 5998-3419 Software version: 12500-CMW710-R7128 Document version: 6W710-20121130 Legal and notice information Copyright 2012 Hewlett-Packard
Basic Router Configuration
 This section includes information about some basic router configuration, and contains the following sections: Default Configuration, on page 1 Configuring Global Parameters, on page 2 Configuring Gigabit
This section includes information about some basic router configuration, and contains the following sections: Default Configuration, on page 1 Configuring Global Parameters, on page 2 Configuring Gigabit
Highly Available Wide Area Network Design
 Highly Available Wide Area Network Design David Prall, Communications Architect dprall@cisco.com Agenda Introduction Cisco IOS and IP Routing Convergence Techniques Design and Deployment Final Wrap Up
Highly Available Wide Area Network Design David Prall, Communications Architect dprall@cisco.com Agenda Introduction Cisco IOS and IP Routing Convergence Techniques Design and Deployment Final Wrap Up
Configuration Note. AudioCodes Mediant Multi-Service Business Routers (MSBR) Mediant MSBR. IP Networking Configuration. Version 7.
 Configuration Note AudioCodes Mediant Multi-Service Business Routers (MSBR) Mediant MSBR IP Networking Configuration Version 7.2 Configuration Note Contents Table of Contents 1 Introduction... 11 2 IPv4...
Configuration Note AudioCodes Mediant Multi-Service Business Routers (MSBR) Mediant MSBR IP Networking Configuration Version 7.2 Configuration Note Contents Table of Contents 1 Introduction... 11 2 IPv4...
Lab Configuring Advanced EIGRP for IPv4 Features Topology
 Topology 2017 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 9 Addressing Table Device Interface IP Address Subnet Mask Default Gateway G0/0 192.168.1.1 255.255.255.0
Topology 2017 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 9 Addressing Table Device Interface IP Address Subnet Mask Default Gateway G0/0 192.168.1.1 255.255.255.0
Stateful Switchover Between Redundancy Paired Intra- or Inter-box Devices
 Stateful Switchover Between Redundancy Paired Intra- or Inter-box Devices Stateful switchover provides protection for network edge devices with dual Route Processors (RPs) that represent a single point
Stateful Switchover Between Redundancy Paired Intra- or Inter-box Devices Stateful switchover provides protection for network edge devices with dual Route Processors (RPs) that represent a single point
Configuring Resilient Ethernet Protocol
 This chapter describes Resilient Ethernet Protocol (REP), REP configuration guidelines, VLAN load balancing, REP timers, and REP over EVC. This chapter also describes procedures to configure REP. Understanding
This chapter describes Resilient Ethernet Protocol (REP), REP configuration guidelines, VLAN load balancing, REP timers, and REP over EVC. This chapter also describes procedures to configure REP. Understanding
Highly Available Wide Area Network Design
 Highly Available Wide Area Network Design David Prall, CCIE #6508, Principal Systems Engineer Cisco Spark How Questions? Use Cisco Spark to communicate with David after the session 1. Find this session
Highly Available Wide Area Network Design David Prall, CCIE #6508, Principal Systems Engineer Cisco Spark How Questions? Use Cisco Spark to communicate with David after the session 1. Find this session
Deploying a Stateful and Fault Tolerant Virtual Gateway using Open vswitch in SD-WAN
 Deploying a Stateful and Fault Tolerant Virtual Gateway using Open vswitch in SD-WAN Sabyasachi Sengupta Nuage Networks (Nokia) (sabyasachi.sengupta@nokia.com) Open vswitch Fall Conference 2016 Linux Foundation
Deploying a Stateful and Fault Tolerant Virtual Gateway using Open vswitch in SD-WAN Sabyasachi Sengupta Nuage Networks (Nokia) (sabyasachi.sengupta@nokia.com) Open vswitch Fall Conference 2016 Linux Foundation
The Radio Aware Routing feature offers the following benefits: Provides faster network convergence through immediate recognition of changes.
 Radio-Aware Routing (RAR) is a mechanism that uses radios to interact with the routing protocol OSPFv3 to signal the appearance, disappearance, and link conditions of one-hop routing neighbors. In a large
Radio-Aware Routing (RAR) is a mechanism that uses radios to interact with the routing protocol OSPFv3 to signal the appearance, disappearance, and link conditions of one-hop routing neighbors. In a large
Configuring Resilient Ethernet Protocol
 CHAPTER 19 This chapter describes how to use Resilient Ethernet Protocol (REP) on the Catalyst 4500 series switch. REP is a Cisco proprietary protocol that provides an alternative to Spanning Tree Protocol
CHAPTER 19 This chapter describes how to use Resilient Ethernet Protocol (REP) on the Catalyst 4500 series switch. REP is a Cisco proprietary protocol that provides an alternative to Spanning Tree Protocol
PIX Security Appliance Contexts, Failover, and Management
 CHAPTER 8 PIX Security Appliance Contexts, Failover, and Management Upon completion of this chapter, you should be able to answer the following questions: How do I configure a Pix Security Appliance to
CHAPTER 8 PIX Security Appliance Contexts, Failover, and Management Upon completion of this chapter, you should be able to answer the following questions: How do I configure a Pix Security Appliance to
BGP NSF Awareness. Finding Feature Information
 Nonstop Forwarding (NSF) awareness allows a device to assist NSF-capable neighbors to continue forwarding packets during a Stateful Switchover (SSO) operation. The feature allows an NSF-aware device that
Nonstop Forwarding (NSF) awareness allows a device to assist NSF-capable neighbors to continue forwarding packets during a Stateful Switchover (SSO) operation. The feature allows an NSF-aware device that
ECMP Load Balancing. MPLS: Layer 3 VPNs Configuration Guide, Cisco IOS XE Release 3S (Cisco ASR 900 Series) 1
 Equal-cost multi-path routing (ECMP) is a routing strategy where next-hop packet forwarding to a single destination can occur over multiple "best paths" which tie for top place in routing metric calculations.
Equal-cost multi-path routing (ECMP) is a routing strategy where next-hop packet forwarding to a single destination can occur over multiple "best paths" which tie for top place in routing metric calculations.
HUAWEI NetEngine5000E Core Router V800R002C01. Configuration Guide - Network Reliability. Issue 01 Date HUAWEI TECHNOLOGIES CO., LTD.
 V800R002C01 Configuration Guide - Network Reliability Issue 01 Date 2011-10-15 HUAWEI TECHNOLOGIES CO., LTD. 2011. All rights reserved. No part of this document may be reproduced or transmitted in any
V800R002C01 Configuration Guide - Network Reliability Issue 01 Date 2011-10-15 HUAWEI TECHNOLOGIES CO., LTD. 2011. All rights reserved. No part of this document may be reproduced or transmitted in any
Configuring IEEE 802.3ad LACP EtherChannels on the Cisco MWR 2941
 29 CHAPTER Configuring IEEE 802.3ad LACP EtherChannels on the Cisco MWR 2941 Cisco MWR 2941 Release 3.5.1 and later supports IEEE 802.3ad Link Aggregation Control Protocol (LACP) EtherChannels. Note The
29 CHAPTER Configuring IEEE 802.3ad LACP EtherChannels on the Cisco MWR 2941 Cisco MWR 2941 Release 3.5.1 and later supports IEEE 802.3ad Link Aggregation Control Protocol (LACP) EtherChannels. Note The
Chapter 8 Lab 8-2, Using Manual IPv6 Tunnels with EIGRP for IPv6
 Chapter 8 Lab 8-2, Using Manual IPv6 Tunnels with EIGRP for IPv6 Topology Objectives Configure EIGRP for IPv4. Create a manual IPv6 tunnel. Configure EIGRP for IPv6 across the tunnel. Background In this
Chapter 8 Lab 8-2, Using Manual IPv6 Tunnels with EIGRP for IPv6 Topology Objectives Configure EIGRP for IPv4. Create a manual IPv6 tunnel. Configure EIGRP for IPv6 across the tunnel. Background In this
Configuring PIM. Information About PIM. Send document comments to CHAPTER
 CHAPTER 3 This chapter describes how to configure the Protocol Independent Multicast (PIM) features on Cisco NX-OS switches in your IPv4 networks. This chapter includes the following sections: Information
CHAPTER 3 This chapter describes how to configure the Protocol Independent Multicast (PIM) features on Cisco NX-OS switches in your IPv4 networks. This chapter includes the following sections: Information
HP VPN Firewall Appliances
 HP VPN Firewall Appliances High Availability Configuration Guide Part number: 5998-4169 Software version: F1000-A-EI/F1000-S-EI (Feature 3726) F1000-E (Release 3177) F5000 (Feature 3211) F5000-S/F5000-C
HP VPN Firewall Appliances High Availability Configuration Guide Part number: 5998-4169 Software version: F1000-A-EI/F1000-S-EI (Feature 3726) F1000-E (Release 3177) F5000 (Feature 3211) F5000-S/F5000-C
Lab Configuring HSRP and GLBP Topology
 Topology 2014 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 9 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.1.1
Topology 2014 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 9 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.1.1
Configuring ARP. Prerequisites for Configuring ARP. Restrictions for Configuring ARP
 Address resolution is the process of mapping network addresses to Media Access Control (MAC) addresses. This process is accomplished using the Address Resolution Protocol (ARP). This module describes how
Address resolution is the process of mapping network addresses to Media Access Control (MAC) addresses. This process is accomplished using the Address Resolution Protocol (ARP). This module describes how
BGP Commands on Cisco ASR 9000 Series Router
 This module describes the commands used to configure and monitor Border Gateway Protocol (BGP) on Cisco ASR 9000 Series Aggregation Services Routers using Cisco IOS XR software. The commands in this module
This module describes the commands used to configure and monitor Border Gateway Protocol (BGP) on Cisco ASR 9000 Series Aggregation Services Routers using Cisco IOS XR software. The commands in this module
Object Tracking: IPv6 Route Tracking
 The feature expands the Enhanced Object Tracking (EOT) functionality to allow the tracking of IPv6 routes. Finding Feature Information, page 1 Restrictions for, page 1 Information About, page 2 How to
The feature expands the Enhanced Object Tracking (EOT) functionality to allow the tracking of IPv6 routes. Finding Feature Information, page 1 Restrictions for, page 1 Information About, page 2 How to
Chapter 6 Lab 6-1, First Hop Redundancy Protocols HSRP and VRRP INSTRUCTOR VERSION
 CCNPv7.1 SWITCH Chapter 6 Lab 6-1, First Hop Redundancy Protocols HSRP and VRRP INSTRUCTOR VERSION Topology Objectives Configure inter-vlan routing with HSRP and load balancing Configure HSRP authentication
CCNPv7.1 SWITCH Chapter 6 Lab 6-1, First Hop Redundancy Protocols HSRP and VRRP INSTRUCTOR VERSION Topology Objectives Configure inter-vlan routing with HSRP and load balancing Configure HSRP authentication
Implementing DHCP for IPv6
 This module describes how to configure Dynamic Host Configuration Protocol (DHCP) for IPv6. DHCPv6 Prefix Delegation, page 1 How to Implement DHCP for IPv6, page 6 DHCPv6 Prefix Delegation The IPv6 Access
This module describes how to configure Dynamic Host Configuration Protocol (DHCP) for IPv6. DHCPv6 Prefix Delegation, page 1 How to Implement DHCP for IPv6, page 6 DHCPv6 Prefix Delegation The IPv6 Access
GoCertify Advanced Cisco CCIE Lab Scenario # 1
 GoCertify Advanced Cisco CCIE Lab Scenario # 1 (http://www.gocertify.com) IPexpert, Inc. is a leading provider in on-line Cisco CCNA, CCNP and CCIE training material. For more information please visit
GoCertify Advanced Cisco CCIE Lab Scenario # 1 (http://www.gocertify.com) IPexpert, Inc. is a leading provider in on-line Cisco CCNA, CCNP and CCIE training material. For more information please visit
Configuring Spanning Tree Protocol
 Finding Feature Information, page 1 Restrictions for STP, page 1 Information About Spanning Tree Protocol, page 2 How to Configure Spanning-Tree Features, page 14 Monitoring Spanning-Tree Status, page
Finding Feature Information, page 1 Restrictions for STP, page 1 Information About Spanning Tree Protocol, page 2 How to Configure Spanning-Tree Features, page 14 Monitoring Spanning-Tree Status, page
OSPF, MTU and LSA Packing Tech Note
 OSPF, MTU and LSA Packing Tech Note Document ID: 116119 Contributed by Luc De Ghein, Cisco TAC Engineer. Jul 29, 2013 Contents Introduction OSPF Packet Size MTU in DBD Packet OSPF Behavior and Packing
OSPF, MTU and LSA Packing Tech Note Document ID: 116119 Contributed by Luc De Ghein, Cisco TAC Engineer. Jul 29, 2013 Contents Introduction OSPF Packet Size MTU in DBD Packet OSPF Behavior and Packing
Segment Routing Commands
 Segment Routing Commands address ipv4 (PCE), page 4 adjacency-sid, page 5 apply-weight ecmp-only bandwidth, page 7 attribute-set, page 8 autoroute announce, page 10 autoroute destination, page 12 clear
Segment Routing Commands address ipv4 (PCE), page 4 adjacency-sid, page 5 apply-weight ecmp-only bandwidth, page 7 attribute-set, page 8 autoroute announce, page 10 autoroute destination, page 12 clear
Configuring HSRP. Understanding HSRP CHAPTER
 CHAPTER 40 This chapter describes how to use Hot Standby Router Protocol (HSRP) on the Cisco ME 3400E Ethernet Access switch to provide routing redundancy for routing IP traffic without being dependent
CHAPTER 40 This chapter describes how to use Hot Standby Router Protocol (HSRP) on the Cisco ME 3400E Ethernet Access switch to provide routing redundancy for routing IP traffic without being dependent
ASA 9.x EIGRP Configuration Example
 ASA 9.x EIGRP Configuration Example Contents Introduction Prerequisites Requirements Components Used Background Information Guidelines and Limitations EIGRP and Failover Configure Network Diagram ASDM
ASA 9.x EIGRP Configuration Example Contents Introduction Prerequisites Requirements Components Used Background Information Guidelines and Limitations EIGRP and Failover Configure Network Diagram ASDM
Configuring Bidirectional Forwarding Detection on Cisco IOS XR
 Configuring Bidirectional Fwarding Detection on Cisco IOS XR Bidirectional fwarding detection (BFD) provides low-overhead, sht-duration detection of failures in the path between adjacent fwarding engines.
Configuring Bidirectional Fwarding Detection on Cisco IOS XR Bidirectional fwarding detection (BFD) provides low-overhead, sht-duration detection of failures in the path between adjacent fwarding engines.
UniDirectional Link Detection (UDLD) Protocol
 The UniDirectional Link Detection protocol is a Layer 2 protocol that detects and disables one-way connections before they create undesired situation such as Spanning Tree loops. Information About the
The UniDirectional Link Detection protocol is a Layer 2 protocol that detects and disables one-way connections before they create undesired situation such as Spanning Tree loops. Information About the
OpenFlow. Finding Feature Information. Prerequisites for OpenFlow
 Finding Feature Information, page 1 Prerequisites for, page 1 Restrictions for, page 2 Information About Open Flow, page 3 Configuring, page 8 Monitoring, page 12 Configuration Examples for, page 12 Finding
Finding Feature Information, page 1 Prerequisites for, page 1 Restrictions for, page 2 Information About Open Flow, page 3 Configuring, page 8 Monitoring, page 12 Configuration Examples for, page 12 Finding
Configuring Cisco StackWise Virtual
 Finding Feature Information, page 1 Restrictions for Cisco StackWise Virtual, page 1 Prerequisites for Cisco StackWise Virtual, page 3 Information About Cisco Stackwise Virtual, page 3 Cisco StackWise
Finding Feature Information, page 1 Restrictions for Cisco StackWise Virtual, page 1 Prerequisites for Cisco StackWise Virtual, page 3 Information About Cisco Stackwise Virtual, page 3 Cisco StackWise
Chapter 10 Lab 10-2, Securing VLANs INSTRUCTOR VERSION
 CCNPv7.1 SWITCH Chapter 10 Lab 10-2, Securing VLANs INSTRUCTOR VERSION Topology Objectives Background Secure the server farm using private VLANs. Secure the staff VLAN from the student VLAN. Secure the
CCNPv7.1 SWITCH Chapter 10 Lab 10-2, Securing VLANs INSTRUCTOR VERSION Topology Objectives Background Secure the server farm using private VLANs. Secure the staff VLAN from the student VLAN. Secure the
CCNA Semester 3 labs. Part 1 of 1 Labs for chapters 1 8
 CCNA Semester 3 labs Part 1 of 1 Labs for chapters 1 8 2.1.2.12 Lab - Building a Switched Network with Redundant Links 2.3.2.3 Lab - Configuring Rapid PVST+, PortFast and BPDU Guard 2.4.3.4 Lab - Configuring
CCNA Semester 3 labs Part 1 of 1 Labs for chapters 1 8 2.1.2.12 Lab - Building a Switched Network with Redundant Links 2.3.2.3 Lab - Configuring Rapid PVST+, PortFast and BPDU Guard 2.4.3.4 Lab - Configuring
Veryx ATTEST TM. Sample Test Plan. Conformance Test Suite. Bidirectional Forwarding Detection (BFD) Part Number: T / TPS BFD-IPv /1.
 Veryx ATTEST TM Conformance Test Suite Bidirectional Forwarding Detection (BFD) Part Number: T / TPS BFD-IPv4 1.1-1210/1.0 Copyright 2005-2010 Veryx Technologies Pvt. Ltd. All rights reserved. Veryx ATTEST
Veryx ATTEST TM Conformance Test Suite Bidirectional Forwarding Detection (BFD) Part Number: T / TPS BFD-IPv4 1.1-1210/1.0 Copyright 2005-2010 Veryx Technologies Pvt. Ltd. All rights reserved. Veryx ATTEST
Cisco IOS IPv6. Cisco IOS IPv6 IPv6 IPv6 service provider IPv6. IPv6. data link IPv6 Cisco IOS IPv6. IPv6
 IP6FD v6 Fundamentals, Design, and Deployment v3.0 Cisco IOS IPv6 Cisco IOS IPv6 IPv6 IPv6 service provider IPv6 IP IPv6 IPv6 data link IPv6 Cisco IOS IPv6 IPv6 IPv6 DHCP DNS DHCP DNS IPv6 IPv4 IPv6 multicast
IP6FD v6 Fundamentals, Design, and Deployment v3.0 Cisco IOS IPv6 Cisco IOS IPv6 IPv6 IPv6 service provider IPv6 IP IPv6 IPv6 data link IPv6 Cisco IOS IPv6 IPv6 IPv6 DHCP DNS DHCP DNS IPv6 IPv4 IPv6 multicast
Virtual Switching System
 Virtual Switching System Q. What is a virtual switching system (VSS)? A. A VSS is network system virtualization technology that pools multiple Cisco Catalyst 6500 Series Switches into one virtual switch,
Virtual Switching System Q. What is a virtual switching system (VSS)? A. A VSS is network system virtualization technology that pools multiple Cisco Catalyst 6500 Series Switches into one virtual switch,
