Using CSC-SSM 6.2 with Trend Micro Damage Cleanup Services. Setup Guide
|
|
|
- Gabriella Hunter
- 6 years ago
- Views:
Transcription
1 Using CSC-SSM 6.2 with Trend Micro Damage Cleanup Services Setup Guide
2 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files, release notes, and the latest version of the applicable user documentation, which are available from the Trend Micro Web site at: Trend Micro, the Trend Micro logo, and Damage Cleanup Services are trademarks or registered trademarks of Trend Micro, Incorporated. All other product or company names may be trademarks or registered trademarks of their owners. Copyright Trend Micro Incorporated. All rights reserved. 2
3 Abstract This document describes how to configure CSC-SSM 6.2 Content Security to work with Trend Micro s Damage Cleanup Services. Document Modifications Revision Name Date Comments 1 Erwin Benavidez 9/06/07 CSC 6.2 with DCS 3
4 Contents Contents Required Resources... Exercise 1: Equipment Verification : Document Conventions : Network Layout..... Exercise 2: Registration and Activation of DCS..... Exercise 3: Setting Up DCS Accounts. Exercise 4: Registering CSC-SSM to DCS.... Un-registering CSC-SSM from DCS
5 Required Resources The following are required to perform/complete this exercise. Software Requirements: - Cisco Adaptive Security Appliance software version 7.1 (2) - CSC-SSM version 6.2 (Build# 1599) - Operating system and applications: o MS Windows 2003 Server Standard Edition SP1 with the latest hot fixes or MS Windows XP Professional Edition SP2 with the latest hot fixes o Windows Internet Explorer 6.0 (or higher) o Cisco ASDM launcher version 1.4 (7) o Trend Micro DCS File Requirements: - DCS32_1023_Repack3.zip Hardware Requirements: - 1 Unit Cisco Adaptive Security Appliance ASA5510 with Content Security and Control (CSC) - Security Services Module SSM10-2 Units personal computer/laptop each with: o 256 MB or RAM or higher o 1 Fast Ethernet LAN adapter o 2 Gig free disk space o At least 256 color screen and a minimum of 800x600 pixels of resolution o Keyboard and mouse - Unit layer-2 Fast Ethernet switch (4 ports at least) - 3 Sets (straight-through) Ethernet cables - 1 Set (crossover) Ethernet cable - 1 Set rollover (console patch) cable with DB9 serial connector - One of the PCs must have a serial communications port 5
6 Exercise 1: Equipment Verification 1.1 Document Conventions This document presumes that you will be installing your Cisco ASA appliance in a test network laboratory with the device settings illustrated in Figure 1, and that your Cisco ASA has working PIX and ASDM images in it. Where your IP addresses and other system configuration settings differ from this example, you will need to replace settings in the PIX and InterScan configuration commands with your system parameters. Command fields surrounded by < > braces indicate field variables that require values corresponding to your system s settings. 1.2 Network Layout The PIX firewall will be configured to allow all outgoing TCP, UDP and ICMP traffic. The ASA inside network interface will have an IP address of /24 and a single PC attached to it (through a Fast Ethernet switch) with an IP address of /24. The DCS server will be installed and configured later into the machine in the internal network using the DCS configuration guide that can be downloaded from The ASA outside network interface will have an IP address of /24 and a single PC attached to it with an IP address of /24. The SSM management port will connect to the Fast Ethernet switch in the inside network and will have an IP address of /24. The ASA console port will be connected with a rollover cable (with a DB9 connector) to the serial port (COM) of the PC attached to the inside network. Figure 1: ASA with CSC-SSM Sample Network Layout 6
7 Exercise 2: Registration and Activation of DCS DCS is available at the following link: Registration and activation information are available in the DCS product documentation. Exercise 3: Setting Up DCS Accounts Using the DCS Account Management Tool, add entries for accounts on each domain that has local administrative privileges for machines to be scanned. To add a domain or machine account, perform the following steps: Step 1. To open the Account Management Tool, choose Start>Programs>Trend Micro Damage Cleanup Services>Account Management Tool. The Login screen appears. Step 2. Type your DCS administrative password and click Log On. A list of all existing accounts appears, showing account type and the available descriptions. 7
8 Step 3. Click Add to add an account. The Add Account screen appears. 8
9 Step 4. Under Select the type of account to add: select what kind of account to add by accepting the default choice of Domain account or by choosing Machine account. Step 5. If the account is a domain account and you would like to use it as the default account, check the Make this account the default account check box. Note: If, during a scan, DCS is unable to access a remote machine using the account for that machine, DCS uses the default account to access the machine. Because only a domain account can be a default account, this option is disabled for machine accounts. Step 6. In the Machine name field, type the name of the machine account. Step 7. Type the administrator account. Step 8. Type the password for the administrator account, and then retype it to confirm the entry. Step 9. (Optional) Type a description for this account (for example, Company domain 1). Step 10. Click Verify to verify that DCS can connect to the domain with the information provided. 9
10 If DCS can connect to the domain, a Connectivity to client verified. message appears. Step 11. Click OK to close the verification message, and click OK to finish adding the new domain. The account name appears in the Name column of the Accounts table. Step 12. Click Close to close the Account Management Tool. Exercise 4: Registering CSC-SSM to DCS For CSC SSM to acknowledge DCS, the CSC SSM must register to DCS. To register CSC SSM to DCS, perform the following steps: 10
11 Step 1. DCS. Step 2. In the CSC SSM console, go to Administration>Register to Click Enable. Step 3. Enter the DCS server name or IP address in the appropriate field, and then click Add. Step 4. Enter the port number. Step 5. If a cleanup failure occurs, you can redirect the client to DCS by checking the check box near the bottom of the screen. CSC-SSM is now registered to the DCS server; it can now send cleanup requests to the DCS server. Un-registering CSC SSM from DCS You can un-register from DCS if your DCS server changes or if you no longer need DCS. To un-register the CSC SSM from DCS, perform the following steps: Step 1. DCS. In the CSC SSM console, go to Administration>Register to Step 2. In the registration table, click the Delete icon beside the registered DCS server name or IP address. 11
Using CSC SSM with Trend Micro Damage Cleanup Services
 APPENDIXD Using CSC SSM with Trend Micro Damage Cleanup Services Trend Micro InterScan for CSC SSM works with Trend Micro Damage Cleanup Services (DCS) as part of an enterprise protection strategy. The
APPENDIXD Using CSC SSM with Trend Micro Damage Cleanup Services Trend Micro InterScan for CSC SSM works with Trend Micro Damage Cleanup Services (DCS) as part of an enterprise protection strategy. The
Monitoring Content Security
 CHAPTER 7 This chapter describes monitoring content security from ASDM, and includes the following sections: Features of the Content Security Tab, page 7-1, page 7-2 Features of the Content Security Tab
CHAPTER 7 This chapter describes monitoring content security from ASDM, and includes the following sections: Features of the Content Security Tab, page 7-1, page 7-2 Features of the Content Security Tab
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the product, please review the readme files,
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the product, please review the readme files,
Installing Encompass360 SmartClient
 Installing Encompass360 SmartClient This document describes Encompass360 system requirements, configuration options, and installation steps for the SmartClient. Before installing Encompass360 SmartClient,
Installing Encompass360 SmartClient This document describes Encompass360 system requirements, configuration options, and installation steps for the SmartClient. Before installing Encompass360 SmartClient,
Document Part No. NVEM12103/41110
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
How to Configure ASA 5500-X Series Firewall to send logs to EventTracker. EventTracker
 How to Configure ASA 5500-X Series Firewall to send logs to EventTracker EventTracker Publication Date: September 14, 2018 Abstract This guide helps you in configuring ASA 5500-X Series Firewall to send
How to Configure ASA 5500-X Series Firewall to send logs to EventTracker EventTracker Publication Date: September 14, 2018 Abstract This guide helps you in configuring ASA 5500-X Series Firewall to send
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the product, please review the readme files,
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the product, please review the readme files,
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the product, please review the readme files,
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the product, please review the readme files,
RSA NetWitness Logs. Cisco Adaptive Security Appliance Last Modified: Wednesday, November 8, Event Source Log Configuration Guide
 RSA NetWitness Logs Event Source Log Configuration Guide Cisco Adaptive Security Appliance Last Modified: Wednesday, November 8, 2017 Event Source Product Information: Vendor: Cisco Event Source: Adaptive
RSA NetWitness Logs Event Source Log Configuration Guide Cisco Adaptive Security Appliance Last Modified: Wednesday, November 8, 2017 Event Source Product Information: Vendor: Cisco Event Source: Adaptive
Lab Configure Service Object Groups using ASDM
 Lab 9.2.3 Configure Service Object Groups using ASDM Objective Scenario In this lab, the students will complete the following tasks: Configure an inbound access control list (ACL) with object groups. Configure
Lab 9.2.3 Configure Service Object Groups using ASDM Objective Scenario In this lab, the students will complete the following tasks: Configure an inbound access control list (ACL) with object groups. Configure
RSA NetWitness Logs. Juniper Networks NetScreen ScreenOS Last Modified: Wednesday, November 8, Event Source Log Configuration Guide
 RSA NetWitness Logs Event Source Log Configuration Guide Juniper Networks NetScreen ScreenOS Last Modified: Wednesday, November 8, 2017 Event Source Product Information: Vendor: Juniper Networks Event
RSA NetWitness Logs Event Source Log Configuration Guide Juniper Networks NetScreen ScreenOS Last Modified: Wednesday, November 8, 2017 Event Source Product Information: Vendor: Juniper Networks Event
Introducing the CSC SSM
 CHAPTER 1 This chapter introduces the Content Security and Control (CSC) Security Services Module (SSM), and includes the following sections: Overview, page 1-1 Features and Benefits, page 1-2 Available
CHAPTER 1 This chapter introduces the Content Security and Control (CSC) Security Services Module (SSM), and includes the following sections: Overview, page 1-1 Features and Benefits, page 1-2 Available
CounterACT 7.0. Quick Installation Guide for a Single Virtual CounterACT Appliance
 CounterACT 7.0 Quick Installation Guide for a Single Virtual CounterACT Appliance Table of Contents Welcome to CounterACT Version 7.0... 3 Overview... 4 1. Create a Deployment Plan... 5 Decide Where to
CounterACT 7.0 Quick Installation Guide for a Single Virtual CounterACT Appliance Table of Contents Welcome to CounterACT Version 7.0... 3 Overview... 4 1. Create a Deployment Plan... 5 Decide Where to
 Trend Micro Incorporated reserves the right to make changes to this document and to the product described herein without notice. Before installing and using the product, review the readme files, release
Trend Micro Incorporated reserves the right to make changes to this document and to the product described herein without notice. Before installing and using the product, review the readme files, release
Cisco ASA 5500 Series IPS Edition for the Enterprise
 Cisco ASA 5500 Series IPS Edition for the Enterprise Attacks on critical information assets and infrastructure can seriously degrade an organization s ability to do business. The most effective risk mitigation
Cisco ASA 5500 Series IPS Edition for the Enterprise Attacks on critical information assets and infrastructure can seriously degrade an organization s ability to do business. The most effective risk mitigation
 Trend Micro Incorporated reserves the right to make changes to this document and to the product described herein without notice. Before installing and using the product, review the readme files, release
Trend Micro Incorporated reserves the right to make changes to this document and to the product described herein without notice. Before installing and using the product, review the readme files, release
About This Guide. Document Objectives. Audience
 This preface introduce the, and includes the following sections: Document Objectives, page xxxv Audience, page xxxv Related Documentation, page xxxvi Document Organization, page xxxvi Document Conventions,
This preface introduce the, and includes the following sections: Document Objectives, page xxxv Audience, page xxxv Related Documentation, page xxxvi Document Organization, page xxxvi Document Conventions,
Managing Services Modules
 CHAPTER 58 This chapter describes how to manage the following module types: Security Services Cards (SSCs) Security Services Modules (SSMs) Security Services Processors (SSPs) Modules run advanced security
CHAPTER 58 This chapter describes how to manage the following module types: Security Services Cards (SSCs) Security Services Modules (SSMs) Security Services Processors (SSPs) Modules run advanced security
F5 WANJet 200. Quick Start Guide. Quick Start Overview
 F5 WANJet 200 Quick Start Guide Quick Start Overview Following is a high level overview of the steps required to successfully install and configure your F5 WANJet 200 appliance. For detailed instructions
F5 WANJet 200 Quick Start Guide Quick Start Overview Following is a high level overview of the steps required to successfully install and configure your F5 WANJet 200 appliance. For detailed instructions
Reinstalling the Operating System on the Dell PowerVault 745N
 Reinstalling the Operating System on the Dell PowerVault 745N This document details the following steps to reinstall the operating system on a PowerVault 745N system: 1. Install the Reinstallation Console
Reinstalling the Operating System on the Dell PowerVault 745N This document details the following steps to reinstall the operating system on a PowerVault 745N system: 1. Install the Reinstallation Console
Application Notes for Mirage Networks Endpoint Controller in an Avaya IP Telephony Infrastructure Issue 1.0
 Avaya Solution & Interoperability Test Lab Application Notes for Mirage Networks Endpoint Controller in an Avaya IP Telephony Infrastructure Issue 1.0 Abstract These Application Notes describe a configuration
Avaya Solution & Interoperability Test Lab Application Notes for Mirage Networks Endpoint Controller in an Avaya IP Telephony Infrastructure Issue 1.0 Abstract These Application Notes describe a configuration
Symantec Desktop and Laptop Option 8.0 SP2. Symantec Desktop Agent for Mac. Getting Started Guide
 Symantec Desktop and Laptop Option 8.0 SP2 Symantec Desktop Agent for Mac Getting Started Guide Disclaimer The information contained in this publication is subject to change without notice. Symantec Corporation
Symantec Desktop and Laptop Option 8.0 SP2 Symantec Desktop Agent for Mac Getting Started Guide Disclaimer The information contained in this publication is subject to change without notice. Symantec Corporation
User Guide. (Network Version) 2008 Certiport, Inc. certiprep 1
 User Guide (Network Version) 2008 Certiport, Inc. certiprep 1 Table of Contents I. GETTING STARTED 3 INTRODUCTION 3 IMPORTANT INFORMATION 3 SYSTEM REQUIREMENTS 4 INSTALLATION 4 Basic Installation Network
User Guide (Network Version) 2008 Certiport, Inc. certiprep 1 Table of Contents I. GETTING STARTED 3 INTRODUCTION 3 IMPORTANT INFORMATION 3 SYSTEM REQUIREMENTS 4 INSTALLATION 4 Basic Installation Network
Trend Micro Core Protection Module 10.6 SP1 System Requirements
 Trend Micro Core Protection Module 10.6 System Requirements Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing
Trend Micro Core Protection Module 10.6 System Requirements Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing
 Trend Micro Incorporated reserves the right to make changes to this document and to the product described herein without notice. Before installing and using the product, review the readme files, release
Trend Micro Incorporated reserves the right to make changes to this document and to the product described herein without notice. Before installing and using the product, review the readme files, release
User s Manual ADSL Router Modem DB Ethernet Ports
 User s Manual ADSL Router Modem DB 120 4 Ethernet Ports 1. About ADSL ADSL (Asymmetric Digital Subscriber Line) is a technology that allows high-speed data to be transmitted over existing copper telephone
User s Manual ADSL Router Modem DB 120 4 Ethernet Ports 1. About ADSL ADSL (Asymmetric Digital Subscriber Line) is a technology that allows high-speed data to be transmitted over existing copper telephone
ASA/PIX Security Appliance
 I N D E X A AAA, implementing, 27 28 access to ASA/PIX Security Appliance monitoring, 150 151 securing, 147 150 to websites, blocking, 153 155 access control, 30 access policies, creating for web and mail
I N D E X A AAA, implementing, 27 28 access to ASA/PIX Security Appliance monitoring, 150 151 securing, 147 150 to websites, blocking, 153 155 access control, 30 access policies, creating for web and mail
Alcatel-Lucent IPSec Client
 Alcatel-Lucent IPSec Client IPSec Release 10.0 RELEASE NOTES IPSec Client Release 10.0 December 2009 ISSUE 1 Legal Notice Alcatel, Lucent, Alcatel-Lucent and the Alcatel-Lucent logo are trademarks of Alcatel-Lucent.
Alcatel-Lucent IPSec Client IPSec Release 10.0 RELEASE NOTES IPSec Client Release 10.0 December 2009 ISSUE 1 Legal Notice Alcatel, Lucent, Alcatel-Lucent and the Alcatel-Lucent logo are trademarks of Alcatel-Lucent.
HLSE02P Dual Port Serial to Ethernet server Quick Installation guide for Windows 7 32-bit
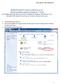 HLSE02P Dual Port Serial to Ethernet server Quick Installation guide for Windows 7 32-bit This installation guide describes how to setup the HLSE02P with Fabulatech COM Redirector. As an alternative COM
HLSE02P Dual Port Serial to Ethernet server Quick Installation guide for Windows 7 32-bit This installation guide describes how to setup the HLSE02P with Fabulatech COM Redirector. As an alternative COM
Lab IP Addresses and Network Communication
 Lab 3.5.2 IP Addresses and Network Communication Objectives Build a simple peer-to-peer network and verify physical connectivity. Assign various IP addresses to hosts and observe the effects on network
Lab 3.5.2 IP Addresses and Network Communication Objectives Build a simple peer-to-peer network and verify physical connectivity. Assign various IP addresses to hosts and observe the effects on network
Deep Security 9.5 Supported Features by Platform
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
Deep Security 9 vcenter Operations Manager Integration
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
Veritas Desktop Agent for Mac Getting Started Guide
 Veritas Desktop Agent for Mac Getting Started Guide The software described in this document is furnished under a license agreement and may be used only in accordance with the terms of the agreement. Documentation
Veritas Desktop Agent for Mac Getting Started Guide The software described in this document is furnished under a license agreement and may be used only in accordance with the terms of the agreement. Documentation
TOPS Installation Instructions Issue 1
 TOPS Installation Instructions Issue 1 Author: Technical Publications Issue: 1 Date: 18/02/2009 Part Number: TG201036 Copyright: 2009 Honeywell Technologies Sàrl, ECC Division. All rights reserved. This
TOPS Installation Instructions Issue 1 Author: Technical Publications Issue: 1 Date: 18/02/2009 Part Number: TG201036 Copyright: 2009 Honeywell Technologies Sàrl, ECC Division. All rights reserved. This
iscsi Storage Appliance Getting Started Guide
 iscsi Storage Appliance Getting Started Guide 2 Copyright 2007 Adaptec, Inc. All rights reserved. No part of this publication may be reproduced, stored in a retrieval system, or transmitted in any form
iscsi Storage Appliance Getting Started Guide 2 Copyright 2007 Adaptec, Inc. All rights reserved. No part of this publication may be reproduced, stored in a retrieval system, or transmitted in any form
OPERATION MANUAL. MV-410HS Web Browser. Version Rev.2
 OPERATION MANUAL MV-410HS Web Browser Version 1.0 - Rev.2 Table of Contents 1. Setup... 1 1-1. Overview... 1 1-2. System Requirements... 1 1-3. Installing Java(TM)... 2 1-4. Connections... 3 1-5. Communication
OPERATION MANUAL MV-410HS Web Browser Version 1.0 - Rev.2 Table of Contents 1. Setup... 1 1-1. Overview... 1 1-2. System Requirements... 1 1-3. Installing Java(TM)... 2 1-4. Connections... 3 1-5. Communication
Copyright 2012 Trend Micro Incorporated. All rights reserved.
 Trend Micro reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files, release notes,
Trend Micro reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files, release notes,
Virtual Recovery Assistant user s guide
 Virtual Recovery Assistant user s guide Part number: T2558-96323 Second edition: March 2009 Copyright 2009 Hewlett-Packard Development Company, L.P. Hewlett-Packard Company makes no warranty of any kind
Virtual Recovery Assistant user s guide Part number: T2558-96323 Second edition: March 2009 Copyright 2009 Hewlett-Packard Development Company, L.P. Hewlett-Packard Company makes no warranty of any kind
Dell SupportAssist Agent User s Guide
 Dell SupportAssist Agent User s Guide Notes, Cautions, and Warnings NOTE: A NOTE indicates important information that helps you make better use of your computer. CAUTION: A CAUTION indicates either potential
Dell SupportAssist Agent User s Guide Notes, Cautions, and Warnings NOTE: A NOTE indicates important information that helps you make better use of your computer. CAUTION: A CAUTION indicates either potential
Laboratory Exercise 1
 I. Objectives - Using RouterSim. - Building a simple LAN. Laboratory Exercise 1 II. Using RouterSim 1. Network Visualizer Screen CCNA Network Visualizer 6.0 Net Visualizer Screen 2. Adding a Device to
I. Objectives - Using RouterSim. - Building a simple LAN. Laboratory Exercise 1 II. Using RouterSim 1. Network Visualizer Screen CCNA Network Visualizer 6.0 Net Visualizer Screen 2. Adding a Device to
Cisco VPN 3000 Concentrator QuickConfig Guide
 Cisco VPN 3000 Concentrator QuickConfig Guide For ASAS 2.4 and Above 1 Overview........................................................................ 1 1.1 Requirements........................................................................
Cisco VPN 3000 Concentrator QuickConfig Guide For ASAS 2.4 and Above 1 Overview........................................................................ 1 1.1 Requirements........................................................................
Part # Quick-Start Guide. SpeedStream 4200 Modem PPPoE Modem Router
 Part # 007-0-00 Quick-Start Guide SpeedStream 00 Modem PPPoE Modem Router Before you begin, Verify that the following items came with your DSL kit: Step > Install Line Filters 7 SpeedStream Device Documentation
Part # 007-0-00 Quick-Start Guide SpeedStream 00 Modem PPPoE Modem Router Before you begin, Verify that the following items came with your DSL kit: Step > Install Line Filters 7 SpeedStream Device Documentation
Configuring RADIUS Clients
 CHAPTER 8 This chapter describes the following: Overview Adding RADIUS Clients Editing RADIUS Clients Deleting RADIUS Clients Overview Remote Authentication Dial In User Service (RADIUS) is an AAA (authentication,
CHAPTER 8 This chapter describes the following: Overview Adding RADIUS Clients Editing RADIUS Clients Deleting RADIUS Clients Overview Remote Authentication Dial In User Service (RADIUS) is an AAA (authentication,
SATA-IP Device Demo Instruction on AC701 Rev Apr-14
 SATA-IP Device Demo Instruction on AC701 Rev1.0 11-Apr-14 This document describes SATA-IP Device evaluation procedure on AC701 using SATA-IP Device reference design bit-file. 1 Environment For real board
SATA-IP Device Demo Instruction on AC701 Rev1.0 11-Apr-14 This document describes SATA-IP Device evaluation procedure on AC701 using SATA-IP Device reference design bit-file. 1 Environment For real board
NETWORK LAB 2 Configuring Switch Desktop
 Configuring Switch 1. Select the switch tab and then add a switch from the list of switches we have to the workspace, we will choose (2950-24) switch. 2. Add a number of PCs next to the switch in order
Configuring Switch 1. Select the switch tab and then add a switch from the list of switches we have to the workspace, we will choose (2950-24) switch. 2. Add a number of PCs next to the switch in order
1. What type of network cable is used between a terminal and a console port? cross-over straight-through rollover patch cable 2.
 1. What type of network cable is used between a terminal and a console port? cross-over straight-through rollover patch cable 2. Refer to the exhibit. A network administrator has decided to use packet
1. What type of network cable is used between a terminal and a console port? cross-over straight-through rollover patch cable 2. Refer to the exhibit. A network administrator has decided to use packet
INSTALLATION GUIDE. RAPID TAG PC-Based Software Installation Guide. Version 5.0
 INSTALLATION GUIDE RAPID TAG PC-Based Software Installation Guide Version 5.0 122 West State Street Traverse City, MI 49684 www.salamanderlive.com 877.430.5171 TABLE OF CONTENTS 1 ABOUT THIS GUIDE... 2
INSTALLATION GUIDE RAPID TAG PC-Based Software Installation Guide Version 5.0 122 West State Street Traverse City, MI 49684 www.salamanderlive.com 877.430.5171 TABLE OF CONTENTS 1 ABOUT THIS GUIDE... 2
VMware vfabric Data Director Installation Guide
 VMware vfabric Data Director Installation Guide vfabric Data Director 1.0.1 This document supports the version of each product listed and supports all subsequent versions until the document is replaced
VMware vfabric Data Director Installation Guide vfabric Data Director 1.0.1 This document supports the version of each product listed and supports all subsequent versions until the document is replaced
SP PRO Communications LAN Connectivity
 SP PRO Communications LAN Connectivity Introduction This application note provides information to enable the connection of an SP PRO to a Local Area Network (LAN). Information provided is targeted at persons
SP PRO Communications LAN Connectivity Introduction This application note provides information to enable the connection of an SP PRO to a Local Area Network (LAN). Information provided is targeted at persons
ForeScout CounterACT. Single CounterACT Appliance. Quick Installation Guide. Version 8.0
 ForeScout CounterACT Single CounterACT Appliance Version 8.0 Table of Contents Welcome to CounterACT Version 8.0... 4 CounterACT Package Contents... 4 Overview... 5 1. Create a Deployment Plan... 6 Decide
ForeScout CounterACT Single CounterACT Appliance Version 8.0 Table of Contents Welcome to CounterACT Version 8.0... 4 CounterACT Package Contents... 4 Overview... 5 1. Create a Deployment Plan... 6 Decide
NET INTEGRATION TECHNOLOGIES INC. NET INTEGRATOR MICRO. Quick Start Guide
 NET INTEGRATOR MICRO Quick Start Guide 602-0002-02 Meet Your Net Integrator Micro Front View USB Port Ethernet LED Hard Drive LED Power LED Power button 2 Quick Start Guide Back View DC 12V input connector
NET INTEGRATOR MICRO Quick Start Guide 602-0002-02 Meet Your Net Integrator Micro Front View USB Port Ethernet LED Hard Drive LED Power LED Power button 2 Quick Start Guide Back View DC 12V input connector
Copyright 2013 Trend Micro Incorporated. All rights reserved.
 Trend Micro reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files, release notes,
Trend Micro reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files, release notes,
Logging In to the Sensor
 CHAPTER 12 This chapter explains how to log in to the sensor. It contains the following sections: Overview, page 12-1 Supported User Roles, page 12-1 Logging In to the Appliance, page 12-2 Connecting an
CHAPTER 12 This chapter explains how to log in to the sensor. It contains the following sections: Overview, page 12-1 Supported User Roles, page 12-1 Logging In to the Appliance, page 12-2 Connecting an
ASA 8.X and later: Add or Modify an Access List through the ASDM GUI Configuration Example
 ASA 8.X and later: Add or Modify an Access List through the ASDM GUI Configuration Example Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Configure
ASA 8.X and later: Add or Modify an Access List through the ASDM GUI Configuration Example Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Configure
RSA NetWitness Logs. Airtight Management Console. Event Source Log Configuration Guide. Last Modified: Thursday, May 04, 2017
 RSA NetWitness Logs Event Source Log Configuration Guide Airtight Management Console Last Modified: Thursday, May 04, 2017 Event Source Product Information: Vendor: AirTight Event Source: Airtight Management
RSA NetWitness Logs Event Source Log Configuration Guide Airtight Management Console Last Modified: Thursday, May 04, 2017 Event Source Product Information: Vendor: AirTight Event Source: Airtight Management
Intelligent Security & Fire Ltd
 GX Series HD Video Recording Server GX604 / GX609 / GX6016 Quick Start Guide Contents 1. Introduction... 1 1.1. Package Contents... 1 1.2. Hardware Features... 3 1.3. Functional Features... 4 1.4. Hard
GX Series HD Video Recording Server GX604 / GX609 / GX6016 Quick Start Guide Contents 1. Introduction... 1 1.1. Package Contents... 1 1.2. Hardware Features... 3 1.3. Functional Features... 4 1.4. Hard
This Technical Note document contains information on these topics:
 TECHNICAL NOTES EMC IPMI Tool 1.0 P/N 300-015-394 REV 02 May, 2016 This Technical Note document contains information on these topics: EMC IPMI Tool Overview... 2 IPMI tool description... 3 IPMI tool installation...
TECHNICAL NOTES EMC IPMI Tool 1.0 P/N 300-015-394 REV 02 May, 2016 This Technical Note document contains information on these topics: EMC IPMI Tool Overview... 2 IPMI tool description... 3 IPMI tool installation...
RSA NetWitness Logs. F5 Big-IP Application Security Manager. Event Source Log Configuration Guide. Last Modified: Friday, May 12, 2017
 RSA NetWitness Logs Event Source Log Configuration Guide F5 Big-IP Application Security Manager Last Modified: Friday, May 12, 2017 Event Source Product Information: Vendor: F5 Event Source: F5 Big-IP
RSA NetWitness Logs Event Source Log Configuration Guide F5 Big-IP Application Security Manager Last Modified: Friday, May 12, 2017 Event Source Product Information: Vendor: F5 Event Source: F5 Big-IP
Deep Security 9.5 Supported Features by Platform
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
SP PRO Communications Internet Connectivity
 SP PRO Communications Internet Connectivity Introduction Being able to remotely communicate with a SP PRO installation can provide many advantages. These include the ability to monitor system performance,
SP PRO Communications Internet Connectivity Introduction Being able to remotely communicate with a SP PRO installation can provide many advantages. These include the ability to monitor system performance,
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice.
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
System Requirements. Package Contents
 System Requirements System Requirements Computer with Windows Vista or XP SP2 PC with 1.3GHz or above; at least 128MB RAM Internet Explorer 6.0 or Netscape Navigator 7.0 and above Existing 10/100 Ethernet-based
System Requirements System Requirements Computer with Windows Vista or XP SP2 PC with 1.3GHz or above; at least 128MB RAM Internet Explorer 6.0 or Netscape Navigator 7.0 and above Existing 10/100 Ethernet-based
ASI BAS Appliance. Installation Manual. By ASI Controls
 ASI BAS Appliance Installation Manual By ASI Controls DOC-1716(2012-08-21) ASI BAS Appliance User Manual Copyright 2000-2012 ASI Controls, All Rights Reserved August 2012 Liability for products provided
ASI BAS Appliance Installation Manual By ASI Controls DOC-1716(2012-08-21) ASI BAS Appliance User Manual Copyright 2000-2012 ASI Controls, All Rights Reserved August 2012 Liability for products provided
Secomea Remote Device Management
 Secomea Remote Device Management Fast-Track BASIC Guide This guide is intended for first time users of the Secomea Remote Device Management solution, who need a practical introduction to the Secomea RDM
Secomea Remote Device Management Fast-Track BASIC Guide This guide is intended for first time users of the Secomea Remote Device Management solution, who need a practical introduction to the Secomea RDM
Veritas Desktop and Laptop Option Mac Getting Started Guide
 Veritas Desktop and Laptop Option 9.3.1 Mac Getting Started Guide 20-Nov-18 The software described in this document is furnished under a license agreement and may be used only in accordance with the terms
Veritas Desktop and Laptop Option 9.3.1 Mac Getting Started Guide 20-Nov-18 The software described in this document is furnished under a license agreement and may be used only in accordance with the terms
Quick Start Guide. Remote Console Manager
 LES1202A LES1203A-11G LES1203A-M LES1204A-R2 Remote Console Manager Quick Start Guide This Quick Start Guide helps you through installation, configuration, and local operation. For more details, refer
LES1202A LES1203A-11G LES1203A-M LES1204A-R2 Remote Console Manager Quick Start Guide This Quick Start Guide helps you through installation, configuration, and local operation. For more details, refer
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice.
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
 Trend Micro Incorporated reserves the right to make changes to this document and to the product described herein without notice. Before installing and using the product, please review the readme files,
Trend Micro Incorporated reserves the right to make changes to this document and to the product described herein without notice. Before installing and using the product, please review the readme files,
 Trend Micro Incorporated reserves the right to make changes to this document and to the product described herein without notice. Before installing and using the product, review the readme files, release
Trend Micro Incorporated reserves the right to make changes to this document and to the product described herein without notice. Before installing and using the product, review the readme files, release
Computer/Laptop Registration
 Computer/Laptop Registration Before you begin: You will need a valid KSU username and password. A computer or laptop with operating system of Windows (XP or higher) or Mac OSX. Confirm that your PC/laptop
Computer/Laptop Registration Before you begin: You will need a valid KSU username and password. A computer or laptop with operating system of Windows (XP or higher) or Mac OSX. Confirm that your PC/laptop
NCOM SERIAL DEVICE SERVER 1XX SERIES USER S MANUAL
 NCOM SERIAL DEVICE SERVER 1XX SERIES USER S MANUAL 2017-07-07 Edition Titan Electronics Inc. Web: www.titan.tw Contents 1. INTRODUCTION... 4 1.1 Key Features... 5 1.2 Specifications... 6 2. PANEL LAYOUT
NCOM SERIAL DEVICE SERVER 1XX SERIES USER S MANUAL 2017-07-07 Edition Titan Electronics Inc. Web: www.titan.tw Contents 1. INTRODUCTION... 4 1.1 Key Features... 5 1.2 Specifications... 6 2. PANEL LAYOUT
CS356 Lab NIL (Lam) In this lab you will learn: Cisco 2600 Router Configuration Static Routing PartB 20 min Access Control Lists PartC 30 min Explore!
 CS356 Lab NIL (Lam) In this lab you will learn: PartA Time: 2 hrs 40 min Cisco 2600 Router Configuration Static Routing PartB 20 min Access Control Lists PartC 30 min Explore! Components used: 2 computers
CS356 Lab NIL (Lam) In this lab you will learn: PartA Time: 2 hrs 40 min Cisco 2600 Router Configuration Static Routing PartB 20 min Access Control Lists PartC 30 min Explore! Components used: 2 computers
Lab - Remote Desktop in Windows 8
 Lab - Remote Desktop in Windows 8 Introduction In this lab, you will remotely connect to another Windows 8 computer. Recommended Equipment The following equipment is required for this exercise: Two Windows
Lab - Remote Desktop in Windows 8 Introduction In this lab, you will remotely connect to another Windows 8 computer. Recommended Equipment The following equipment is required for this exercise: Two Windows
Setup Guide. Operating Instructions. 1 Before Setting Up 2 Installation 3 Start-up/Shutdown
 Operating Instructions Setup Guide 1 Before Setting Up 2 Installation 3 Start-up/Shutdown Read this manual carefully before you use this product and keep it handy for future reference. Introduction Important
Operating Instructions Setup Guide 1 Before Setting Up 2 Installation 3 Start-up/Shutdown Read this manual carefully before you use this product and keep it handy for future reference. Introduction Important
Hardware Installation Guide Installation (x3350)
 Title page Nortel Application Gateway 2000 Nortel Application Gateway Release 6.3 Hardware Installation Guide Installation (x3350) Document Number: NN42400-300 Document Release: Standard 04.03 Date: January
Title page Nortel Application Gateway 2000 Nortel Application Gateway Release 6.3 Hardware Installation Guide Installation (x3350) Document Number: NN42400-300 Document Release: Standard 04.03 Date: January
ASA 7.x/PIX 6.x and Above: Open/Block the Ports Configuration Example
 ASA 7.x/PIX 6.x and Above: Open/Block the Ports Configuration Example Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Configure Network Diagram Blocking the
ASA 7.x/PIX 6.x and Above: Open/Block the Ports Configuration Example Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Configure Network Diagram Blocking the
Avigilon Control Center Virtual Matrix User Guide
 Avigilon Control Center Virtual Matrix User Guide Version 5.2 PDF-ACCVM-B-Rev1 2013-2014 Avigilon Corporation. All rights reserved. Unless expressly granted in writing, no license is granted with respect
Avigilon Control Center Virtual Matrix User Guide Version 5.2 PDF-ACCVM-B-Rev1 2013-2014 Avigilon Corporation. All rights reserved. Unless expressly granted in writing, no license is granted with respect
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice.
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
Copyright 2012 Trend Micro Incorporated. All rights reserved. Protected by U.S. Patent No. 7,516,130 and U.S. Patent No. 7,747,642.
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
 Trend Micro Incorporated reserves the right to make changes to this document and to the product described herein without notice. Before installing and using the product, review the readme files, release
Trend Micro Incorporated reserves the right to make changes to this document and to the product described herein without notice. Before installing and using the product, review the readme files, release
QUICK GUIDE FOR. Installing Nokia Connectivity Cable Drivers
 QUICK GUIDE FOR Installing Nokia Connectivity Cable Drivers Contents 1. Introduction...1 2. Must haves...1 3. Installing Nokia Connectivity Cable Drivers...2 3.1 Before installation...2 3.2 Installing
QUICK GUIDE FOR Installing Nokia Connectivity Cable Drivers Contents 1. Introduction...1 2. Must haves...1 3. Installing Nokia Connectivity Cable Drivers...2 3.1 Before installation...2 3.2 Installing
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice.
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
for Small and Medium Business Quick Start Guide
 for Small and Medium Business Quick Start Guide Trend Micro Incorporated reserves the right to make changes to this document and to the products/services described herein without notice. Before using
for Small and Medium Business Quick Start Guide Trend Micro Incorporated reserves the right to make changes to this document and to the products/services described herein without notice. Before using
High Availability Deployment
 April 18, 2005 Overview Introduction This addendum provides connectivity and configuration task overviews for connecting two M appliances as a high availability (HA) cluster pair. For detailed configuration
April 18, 2005 Overview Introduction This addendum provides connectivity and configuration task overviews for connecting two M appliances as a high availability (HA) cluster pair. For detailed configuration
This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document for non-commercial distribution and
 This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document for non-commercial distribution and exclusive use by instructors in the CCNA Exploration:
This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document for non-commercial distribution and exclusive use by instructors in the CCNA Exploration:
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice.
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
 Trend Micro Incorporated reserves the right to make changes to this document and to the product described herein without notice. Before installing and using the product, please review the readme files,
Trend Micro Incorporated reserves the right to make changes to this document and to the product described herein without notice. Before installing and using the product, please review the readme files,
Lab - Remote Desktop in Windows 7 and Vista
 Lab - Remote Desktop in Windows 7 and Vista Introduction In this lab, you will remotely connect to another Windows 7 or Vista computer. Recommended Equipment The following equipment is required for this
Lab - Remote Desktop in Windows 7 and Vista Introduction In this lab, you will remotely connect to another Windows 7 or Vista computer. Recommended Equipment The following equipment is required for this
CounterACT 7.0 Single CounterACT Appliance
 CounterACT 7.0 Single CounterACT Appliance Quick Installation Guide Table of Contents Welcome to CounterACT Version 7.0....3 Included in your CounterACT Package....3 Overview...4 1. Create a Deployment
CounterACT 7.0 Single CounterACT Appliance Quick Installation Guide Table of Contents Welcome to CounterACT Version 7.0....3 Included in your CounterACT Package....3 Overview...4 1. Create a Deployment
RSA NetWitness Logs. Trend Micro InterScan Messaging Security Suite. Event Source Log Configuration Guide. Last Modified: Tuesday, April 25, 2017
 RSA NetWitness Logs Event Source Log Configuration Guide Trend Micro InterScan Messaging Security Suite Last Modified: Tuesday, April 25, 2017 Event Source Product Information: Vendor: Trend Micro Event
RSA NetWitness Logs Event Source Log Configuration Guide Trend Micro InterScan Messaging Security Suite Last Modified: Tuesday, April 25, 2017 Event Source Product Information: Vendor: Trend Micro Event
Quick Start Guide. Remote Console Manager Quick Start Guide
 LES1202A-R2 LES1203A-M-R2 LES1204A-R2 Remote Console Manager Quick Start Guide Quick Start Guide This quick start guide helps you through installation, configuration, and local operation. For more details,
LES1202A-R2 LES1203A-M-R2 LES1204A-R2 Remote Console Manager Quick Start Guide Quick Start Guide This quick start guide helps you through installation, configuration, and local operation. For more details,
Installation and Configuration Guide
 Installation and Configuration Guide h-series 800-782-3762 www.edgewave.com 2001 2011 EdgeWave Inc. (formerly St. Bernard Software). All rights reserved. The EdgeWave logo, iprism and iguard are trademarks
Installation and Configuration Guide h-series 800-782-3762 www.edgewave.com 2001 2011 EdgeWave Inc. (formerly St. Bernard Software). All rights reserved. The EdgeWave logo, iprism and iguard are trademarks
Dell SupportAssist for PCs and Tablets User s Guide
 Dell SupportAssist for PCs and Tablets User s Guide Notes, cautions, and warnings NOTE: A NOTE indicates important information that helps you make better use of your computer. CAUTION: A CAUTION indicates
Dell SupportAssist for PCs and Tablets User s Guide Notes, cautions, and warnings NOTE: A NOTE indicates important information that helps you make better use of your computer. CAUTION: A CAUTION indicates
Quick Start Guide. 8-Port Value-Line Console Server QS Guide LES1508A
 LES1508A 8-Port Value-Line Console Server QS Guide Quick Start Guide This Quick Start Guide helps you through installation, configuration, and local operation. For more details, refer to the user manual
LES1508A 8-Port Value-Line Console Server QS Guide Quick Start Guide This Quick Start Guide helps you through installation, configuration, and local operation. For more details, refer to the user manual
Application Notes for Configuring Computer Instruments e-ivr, as a H.323 endpoint, with Avaya IP Office 500 V2 Issue 1.0
 Avaya Solution & Interoperability Test Lab Application Notes for Configuring Computer Instruments e-ivr, as a H.323 endpoint, with Avaya IP Office 500 V2 Issue 1.0 Abstract These Application Notes describe
Avaya Solution & Interoperability Test Lab Application Notes for Configuring Computer Instruments e-ivr, as a H.323 endpoint, with Avaya IP Office 500 V2 Issue 1.0 Abstract These Application Notes describe
User Guide. Avigilon Control Center Gateway. Version 5.0. UG-ACCGateway5-A-Rev1
 User Guide Avigilon Control Center Gateway Version 5.0 UG-ACCGateway5-A-Rev1 Copyright 2013 Avigilon. All rights reserved. No copying, distribution, publication, modification, or incorporation of this
User Guide Avigilon Control Center Gateway Version 5.0 UG-ACCGateway5-A-Rev1 Copyright 2013 Avigilon. All rights reserved. No copying, distribution, publication, modification, or incorporation of this
NCOM SERIAL DEVICE SERVER 4XX SERIES USER S MANUAL
 NCOM SERIAL DEVICE SERVER 4XX SERIES USER S MANUAL 2017-07-07 Edition Titan Electronics Inc. Web: www.titan.tw Contents 1. INTRODUCTION... 4 1.1 Key Features... 5 1.2 Specifications... 6 2. PANEL LAYOUT
NCOM SERIAL DEVICE SERVER 4XX SERIES USER S MANUAL 2017-07-07 Edition Titan Electronics Inc. Web: www.titan.tw Contents 1. INTRODUCTION... 4 1.1 Key Features... 5 1.2 Specifications... 6 2. PANEL LAYOUT
Intelligent Security & Fire Ltd
 This document describes the standard software installation process for Doors.NET software. There are three steps to software installation: install the software, activate the license, enable the communication
This document describes the standard software installation process for Doors.NET software. There are three steps to software installation: install the software, activate the license, enable the communication
ForeScout CounterACT. Cisco PIX/ASA Firewall Integration Module. Configuration Guide. Version 2.1
 ForeScout CounterACT Cisco PIX/ASA Firewall Integration Module Version 2.1 Table of Contents About the Cisco PIX/ASA Firewall Integration Module... 3 Requirements... 3 Configuring the Firewall... 3 Install
ForeScout CounterACT Cisco PIX/ASA Firewall Integration Module Version 2.1 Table of Contents About the Cisco PIX/ASA Firewall Integration Module... 3 Requirements... 3 Configuring the Firewall... 3 Install
