A Bro Primer. Presenter: Adam Pumphrey, Bricata
|
|
|
- Delphia Stokes
- 5 years ago
- Views:
Transcription
1 A Bro Primer Presenter: Adam Pumphrey, Bricata
2 Intro Working in cybersecurity for about 17 years - most of which was with the civilian federal government Role and responsibilities have varied but mainly my work has been in network defense and cybersecurity First exposure to Bro was in 2009; engineers proposed it as a replacement for a network monitoring tool set that included argus, dsniff and httpry Went on to work on a variety of projects, stand up IR teams, build SOC s, design and deploy custom monitoring solutions Bro has been part of the stack ever since
3 Purpose Many network and security operations personnel don t come from a programming background The potential value is apparent, Bro s logs can be used for monitoring, threat detection, incident response and forensics Learning the programming language can be a daunting task, but is necessary in order to realize Bro s full potential Several concepts that are central to how Bro works are also very relevant to learning the language Learning how to perform common, but frequently needed, tasks can be a great way to get started
4 Bro Core PACKETS Event Engine Events Script Interpreter Logs Events Handlers Events Files
5 Things to know... You should be able to locate the local.bro policy file, typically here: $BRO_HOME/share/bro/site/local.bro You should understand the purpose and use of Bro directive Very similar to include and import commands found in other languages Specifies a script (absolute or relative paths) or a module directory If a directory name is specified Bro will attempt to load the load.bro file the directory contains You have defined the Site::local_nets and Site::local_zones variables
6 Events
7 Event Interactions PACKETS Event Engine Events Script Interpreter Logs Events Handlers Events Files Inputs
8 Event Lifecycle
9 Bro Process Events bro_init Generated once, when Bro initializes. Script operations that only need to be executed once in the lifetime of a Bro process should occur in this event handler. bro_done This Bro process is terminating. Any operations that preserve or cleanup what is in memory should go here.
10 Connection State Events new_connection A new connection has been observed. Generated for every new packet that is not part of a tracked connection. Bro s flow-based definition of connection includes TCP, UDP and ICMP flows. connection_established The SYN-ACK packet from a responder in a new connection has been seen. This does not indicate the 3-way handshake has completed. Bro tracks the state either way. connection_state_remove udp_session_done A connection is being removed from memory. By this point, all protocol analyzers have attached their data to the connection record and it is about to be written to the conn log stream. A UDP transaction has completed. Intended to make UDP handling more like TCP, supported protocols are: DNS, NTP, NetBIOS, Syslog, AYIYA, Teredo, and GTPv1
11 connection_state_remove and connection records
12 File Analysis Events file_new Generated once for each new file Bro identifies and begins to analyze. Contains information about the connection, but nothing about the file. file_sniff Generated once, for each analyzed file. Contains the inferred metadata, including mime_type, based on analysis of the first chunk of the file. file_state_remove File analysis for a file is ending. At this point the fa_file record contains all of the information gathered by the file analyzers that ran.
13 file_state_remove and fa_file record
14 Application Layer Protocol Events smtp arp ssl imap xmpp smb udp modbus sip gnutella irc dce-rpc tcp bittorrent gtpv1 rpc smnp dhcp ssh syslog krb ntlm ntp teredo dnp3 ident socks mysql rfb finger rdp dns ncp ftp http icmp netbios radius pop3
15 Find out more about events List of protocol-independent events Bro generates Review events generated by the various plugins Documentation of Files framework and the log_files event ro.html#events file_sniff and other file analysis events are generated by Bro core, see the top URL for more info
16 Log Streams and Filters
17 Bro Log Format Bro s built-in ASCII writer provides two primary output formats: Tab-delimited (Bro s proprietary log format) JSON The default is tab-delimited, but you can enable JSON with Bro Script # Enable JSON Logging redef LogAscii::use_json = T; # Specify the timestamp format, epoch is default redef LogAscii::json_timestamps = "JSON::TS_ISO8601";
18 Bro Logs Native Format #separator \x09 #set_separator, #empty_field (empty) #unset_field - #path conn #open #fields ts uid id.orig_h id.orig_p id.resp_h id.resp_p #types time string addr port addr port enum string C1CxFS3pdJ8kwbmnMl
19 Bro Logs JSON Format { "ts":" t20:04: z", "uid":"c1cxfs3pdj8kwbmnml", "id.orig_h":" ", "id.orig_p":1046, "id.resp_h":" ", "id.resp_p":80, "proto":"tcp", "service":"http", "duration": , "orig_bytes":316,
20 Enable JSON for specific streams Copy the default filter event bro_init() { # Load the default filter of the Conn log local filter = Log::get_filter(Conn::LOG,"default"); # Specify a new filter name filter$name = cat(filter$name, "-json");
21 Enable JSON for specific streams Configure JSON options # Specify a new stream path filter$path = cat(filter$path, "-json"); # Add the config options to the filter filter$config = table( ["use_json"] = "T", ["json_timestamps"] = "JSON::TS_ISO8601"); # Apply the modified default filter Log::add_filter(Conn::LOG, filter);
22 Disable a Log Stream # Disable the communication log event bro_init() { Log::disable_stream(Communication::LOG);
23 Include only certain fields in a stream # Handle the bro_init event event bro_init() { # Retrieve the default filter for the HTTP log stream local f = Log::get_filter( "default"); # Define a new value for the "include" field f$include = set("ts, "id.orig_h", "host", "uri"); # Add the modified default filter back to the HTTP log Log::add_filter( f);
24 Remove certain fields from a stream # Handle the bro_init event event bro_init() { # Remove the default filter Log::remove_default_filter(SMTP::LOG); # Add a new filter, use the exclude field Log::add_filter(SMTP::LOG, [$name = "no_smtp_recips", $exclude = set("rcptto")] );
25 Log only select events # Log only select events event bro_init() { # Remove the default filter Log::remove_default_filter(SMTP::LOG); # Provide an argument to the $pred option Log::add_filter(SMTP::LOG, [$name = "incoming_ ", $pred(rec: SMTP::Info) = { return! Site::is_local_addr(rec$id$orig_h); ]);
26 Route events based on their content Define the function # Function to return desired log file name function sort_mail(id: Log::ID, path: string, rec: SMTP::Info): string { if (Site::is_local_addr(rec$id$orig_h) && (! Site::is_local_addr(rec$id$resp_h))) return outgoing_ ; else if (! Site::is_local_addr(rec$id$orig_h) && Site::is_local_addr(rec$id$resp_h) ) return incoming_ ;
27 Route events based on their content Apply the filter event bro_init() { # Remove the default filter Log::remove_default_filter(SMTP::LOG); # Use sort_mail for the path function Log::add_filter(SMTP::LOG, [$name = " _sorter", $path_func = sort_mail ]);
28 Add a field to a log stream Modify the Info record # Redef the Conn::Info record export { # Add the new pcr field redef record Conn::Info += { pcr: double &log &optional; ;
29 Add a field to a log stream Populate the field # Handle the appropriate event event connection_state_remove(c: connection) &priority=3 { # Verify required fields exists if (! c$conn?$orig_bytes! c$conn?$resp_bytes ) { return; # Test for specific field value conditions else if (c$conn$orig_bytes == 0 && c$conn$resp_bytes == 0 ) { c$conn$pcr = 0.0; # Calculate the new value and store in the pcr field else { local n = (c$conn$orig_bytes + 0.0) - (c$conn$resp_bytes + 0.0); local d = (c$conn$orig_bytes + 0.0) + (c$conn$resp_bytes + 0.0); local x = ( n / d ); c$conn$pcr = x;
30 Adding a new log stream Sample Use Case Separately log flow and SSL information about potential file downloads occurring over HTTPS 3 parts: 1. Set up the environment 2. Create the log stream 3. Write events to the stream
31 Add a New Log Stream
32 Set up the script environment # Load the base/utils/site # Define a module namespace module https_transfer;
33 Define export block for module declarations # Export the required objects export { # Redef the Log::ID enum to include our module's stream redef enum Log::ID += { LOG ; # Define an Info record for the log type Info: record { ts: time &log; uid: string &log; orig_h: addr &log; resp_h: addr &log; pcr: double &log; bytes_received: count &log; server_name: string &log; subject: string &log; issuer: string &log; ; global log_https_transfer: event(rec: https_transfer::info);
34 Create the log stream # Create the stream inside the bro_init event handler event bro_init() { Log::create_stream(https_transfer::LOG, [ $columns=https_transfer::info, $ev=log_https_transfer, $path="https_transfers ]);
35 Test traffic conditions with the IF statement # Handle connection_state_remove event to work with the pcr value event connection_state_remove(c: connection) &priority=0 { # Check for SSL between an internal client and external server if ( c?$ssl && (Site::is_local_addr(c$id$orig_h) &&! Site::is_local_addr(c$id$resp_h)) ) { # Check if the pcr value signifies likely file download if ( c$conn$pcr <= ) {
36 Write the Info record to the log stream # Create and populate the Info record local rec = https_transfer::info( $ts = c$start_time, $uid = c$uid, $orig_h = c$id$orig_h, $resp_h = c$id$resp_h, $pcr = c$conn$pcr, $bytes_received = c$conn$resp_bytes, $server_name = c$ssl?$server_name? c$ssl$server_name : "", $subject = c$ssl?$subject? c$ssl$subject : "", $issuer = c$ssl?$issuer? c$ssl$issuer : "" ); # Write the Info record to the log stream Log::write(https_transfer::LOG, rec);
37 Additional Resources Script Reference, supplement to the documentation pulled from source code comments: o o o o o Operators Types Attributes Declarations and Statements Directives FloCon 2014 PCR Presentation by Cater Bullard and John Gerth resentation.pdf
The Bro Network Intrusion Detection System
 The Bro Network Intrusion Detection System Robin Sommer Lawrence Berkeley National Laboratory rsommer@lbl.gov http://www.icir.org Outline Design of the Bro NIDS Philosophy Architecture LBNL s Bro Installation
The Bro Network Intrusion Detection System Robin Sommer Lawrence Berkeley National Laboratory rsommer@lbl.gov http://www.icir.org Outline Design of the Bro NIDS Philosophy Architecture LBNL s Bro Installation
The Bro Cluster The Bro Cluster
 The Bro Cluster The Bro Cluster Intrusion Detection at 10 Gig and A High-Performance beyond using the NIDS Bro Architecture IDS for the Lawrence Berkeley National Lab Robin International Computer Science
The Bro Cluster The Bro Cluster Intrusion Detection at 10 Gig and A High-Performance beyond using the NIDS Bro Architecture IDS for the Lawrence Berkeley National Lab Robin International Computer Science
An Alert has Fired. Now What?
 An Alert has Fired. Now What? Open-source Bro solves security problems traditional tools can t. May 2017 Anyone who works in a security operations center understands the drill: An alert fires from a source
An Alert has Fired. Now What? Open-source Bro solves security problems traditional tools can t. May 2017 Anyone who works in a security operations center understands the drill: An alert fires from a source
VAST. AUnifiedPlatformforInteractiveNetworkForensics. Matthias Vallentin 1,2 Vern Paxson 1,2 Robin Sommer 2,3. March 17, 2016 USENIX NSDI
 VAST AUnifiedPlatformforInteractiveNetworkForensics Matthias Vallentin 1,2 Vern Paxson 1,2 Robin Sommer 2,3 1 UC Berkeley 2 International Computer Science Institute (ICSI) 3 Lawrence Berkeley National
VAST AUnifiedPlatformforInteractiveNetworkForensics Matthias Vallentin 1,2 Vern Paxson 1,2 Robin Sommer 2,3 1 UC Berkeley 2 International Computer Science Institute (ICSI) 3 Lawrence Berkeley National
FLOCON Network Security Monitoring with IPFIX and Bro Randy Caldejon
 FLOCON 2014 Network Security Monitoring with IPFIX and Bro Randy Caldejon YAF2Bro Project YAF DPI IPFIX Mediator Bro Purpose Is it possible to create a framework for producing Ac)onable Intelligence with
FLOCON 2014 Network Security Monitoring with IPFIX and Bro Randy Caldejon YAF2Bro Project YAF DPI IPFIX Mediator Bro Purpose Is it possible to create a framework for producing Ac)onable Intelligence with
5 Reasons Corelight Gives You Better Data for Incident Response and Threat Hunting
 5 Reasons Corelight Gives You Better Data for Incident Response and Threat Hunting The Need for Better Data The network provides invaluable ground truth for incident response and threat hunting since virtually
5 Reasons Corelight Gives You Better Data for Incident Response and Threat Hunting The Need for Better Data The network provides invaluable ground truth for incident response and threat hunting since virtually
Seeking Visibility Into Network Activity for Security Analysis
 Seeking Visibility Into Network Activity for Security Analysis Robin Sommer Lawrence Berkeley National Laboratory & International Computer Science Institute robin@icsi.berkeley.org http://www.icir.org
Seeking Visibility Into Network Activity for Security Analysis Robin Sommer Lawrence Berkeley National Laboratory & International Computer Science Institute robin@icsi.berkeley.org http://www.icir.org
ch02 True/False Indicate whether the statement is true or false.
 ch02 True/False Indicate whether the statement is true or false. 1. No matter what medium connects computers on a network copper wires, fiber-optic cables, or a wireless setup the same protocol must be
ch02 True/False Indicate whether the statement is true or false. 1. No matter what medium connects computers on a network copper wires, fiber-optic cables, or a wireless setup the same protocol must be
Advanced Network Troubleshooting Using Wireshark (Hands-on)
 Advanced Network Troubleshooting Using Wireshark (Hands-on) Description This course is a continuation of the "Basic Network Troubleshooting Using Wireshark" course, and comes to provide the participants
Advanced Network Troubleshooting Using Wireshark (Hands-on) Description This course is a continuation of the "Basic Network Troubleshooting Using Wireshark" course, and comes to provide the participants
Legal and notice information
 Legal and notice information Copyright 2017 Trend Micro Incorporated. All rights reserved. TippingPoint, the TippingPoint logo, and Digital Vaccine are trademarks or registered trademarks of Trend Micro
Legal and notice information Copyright 2017 Trend Micro Incorporated. All rights reserved. TippingPoint, the TippingPoint logo, and Digital Vaccine are trademarks or registered trademarks of Trend Micro
Spicy: A Unified Deep Packet Inspection Framework Dissecting All Your Data
 Spicy: A Unified Deep Packet Inspection Framework Dissecting All Your Data Robin Sommer International Computer Science Institute, & Corelight, Inc. robin@icsi.berkeley.edu robin@corelight.io http://www.icir.org/robin
Spicy: A Unified Deep Packet Inspection Framework Dissecting All Your Data Robin Sommer International Computer Science Institute, & Corelight, Inc. robin@icsi.berkeley.edu robin@corelight.io http://www.icir.org/robin
Hands-On Ethical Hacking and Network Defense
 Hands-On Ethical Hacking and Network Defense Chapter 2 TCP/IP Concepts Review Last modified 1-11-17 Objectives Describe the TCP/IP protocol stack Explain the basic concepts of IP addressing Explain the
Hands-On Ethical Hacking and Network Defense Chapter 2 TCP/IP Concepts Review Last modified 1-11-17 Objectives Describe the TCP/IP protocol stack Explain the basic concepts of IP addressing Explain the
Arming Small Security Programs
 Arming Small Security Programs Troopers17 Arming Small Security Programs Network baseline generation with Bropy Disclaimer I borrowed my employers slide template Creating.POT files is hard This is NOT
Arming Small Security Programs Troopers17 Arming Small Security Programs Network baseline generation with Bropy Disclaimer I borrowed my employers slide template Creating.POT files is hard This is NOT
HP Load Balancing Module
 HP Load Balancing Module Load Balancing Configuration Guide Part number: 5998-4218 Software version: Feature 3221 Document version: 6PW100-20130326 Legal and notice information Copyright 2013 Hewlett-Packard
HP Load Balancing Module Load Balancing Configuration Guide Part number: 5998-4218 Software version: Feature 3221 Document version: 6PW100-20130326 Legal and notice information Copyright 2013 Hewlett-Packard
Configuring Health Monitoring
 CHAPTER1 This chapter describes how to configure health monitoring on the ACE to track the state of a server by sending out probes. Also referred to as out-of-band health monitoring, the ACE verifies the
CHAPTER1 This chapter describes how to configure health monitoring on the ACE to track the state of a server by sending out probes. Also referred to as out-of-band health monitoring, the ACE verifies the
Following the Packets: A Walk Through Bro s Internal Processing Pipeline
 Following the Packets: A Walk Through Bro s Internal Processing Pipeline Robin Sommer robin@icir.org Corelight, Inc. International Computer Science Institute Lawrence Berkeley National Laboratory Outline
Following the Packets: A Walk Through Bro s Internal Processing Pipeline Robin Sommer robin@icir.org Corelight, Inc. International Computer Science Institute Lawrence Berkeley National Laboratory Outline
BIG-IP DNS: Monitors Reference. Version 12.1
 BIG-IP DNS: Monitors Reference Version 12.1 Table of Contents Table of Contents Monitors Concepts...5 Purpose of monitors...5 Benefits of monitors...5 Methods of monitoring...5 Comparison of monitoring
BIG-IP DNS: Monitors Reference Version 12.1 Table of Contents Table of Contents Monitors Concepts...5 Purpose of monitors...5 Benefits of monitors...5 Methods of monitoring...5 Comparison of monitoring
Wireshark: Are You Under Attack? Kyle Feuz School of Computing
 Wireshark: Are You Under Attack? Kyle Feuz School of Computing Introduction Download Wireshark and capture files https://www.wireshark.org/download.html http://icarus.cs.weber.edu/~kfeuz/downloads/sai
Wireshark: Are You Under Attack? Kyle Feuz School of Computing Introduction Download Wireshark and capture files https://www.wireshark.org/download.html http://icarus.cs.weber.edu/~kfeuz/downloads/sai
Fundamentals of Computer Networking AE6382
 Computer networks are an integral part of the modern computing infrastructure The local network (LAN) is usually Ethernet LAN s are inter-connected with other LAN s in a hierarchical fashion eventually
Computer networks are an integral part of the modern computing infrastructure The local network (LAN) is usually Ethernet LAN s are inter-connected with other LAN s in a hierarchical fashion eventually
IceWarp to IceWarp Migration Guide
 IceWarp Unified Communications IceWarp to IceWarp Migration Guide Version 12.0 IceWarp to IceWarp Migration Guide 2 Contents IceWarp to IceWarp Migration Guide... 4 Used Terminology... 4 Brief Introduction...
IceWarp Unified Communications IceWarp to IceWarp Migration Guide Version 12.0 IceWarp to IceWarp Migration Guide 2 Contents IceWarp to IceWarp Migration Guide... 4 Used Terminology... 4 Brief Introduction...
A Graphical User Interface Framework for Detecting Intrusions using Bro IDS
 A Graphical User Interface Framework for Detecting Intrusions using Bro IDS Shaffali Gupta M.Tech Scholar Thapar University, Patiala Rachit Goel M.tech Scholar Doon Valley, Karnal ABSTRACT Internet has
A Graphical User Interface Framework for Detecting Intrusions using Bro IDS Shaffali Gupta M.Tech Scholar Thapar University, Patiala Rachit Goel M.tech Scholar Doon Valley, Karnal ABSTRACT Internet has
Scanning. Course Learning Outcomes for Unit III. Reading Assignment. Unit Lesson UNIT III STUDY GUIDE
 UNIT III STUDY GUIDE Course Learning Outcomes for Unit III Upon completion of this unit, students should be able to: 1. Recall the terms port scanning, network scanning, and vulnerability scanning. 2.
UNIT III STUDY GUIDE Course Learning Outcomes for Unit III Upon completion of this unit, students should be able to: 1. Recall the terms port scanning, network scanning, and vulnerability scanning. 2.
Download the latest version of the DNS2Go Client from:
 Using DNS2Go with your Linksys Cable / DSL Router Many users with Cable and xdsl broadband connections are using hardware routers such as the Linksys Cable/DSL Routers to connect their local area network
Using DNS2Go with your Linksys Cable / DSL Router Many users with Cable and xdsl broadband connections are using hardware routers such as the Linksys Cable/DSL Routers to connect their local area network
Applied Networks & Security
 Applied Networks & Security Applications http://condor.depaul.edu/~jkristof/it263/ John Kristoff jtk@depaul.edu IT 263 Winter 2006/2007 John Kristoff - DePaul University 1 HTTP/HTTPS The language of the
Applied Networks & Security Applications http://condor.depaul.edu/~jkristof/it263/ John Kristoff jtk@depaul.edu IT 263 Winter 2006/2007 John Kristoff - DePaul University 1 HTTP/HTTPS The language of the
Network-Based Application Recognition
 Network-Based Application Recognition Last updated: September 2008 Common questions and answers regarding Cisco Network-Based Application Recognition (NBAR) follow. Q. What is NBAR? A. NBAR, an important
Network-Based Application Recognition Last updated: September 2008 Common questions and answers regarding Cisco Network-Based Application Recognition (NBAR) follow. Q. What is NBAR? A. NBAR, an important
Getting Started with Network Analysis Policies
 The following topics describe how to get started with network analysis policies: Network Analysis Policy Basics, page 1 Managing Network Analysis Policies, page 2 Network Analysis Policy Basics Network
The following topics describe how to get started with network analysis policies: Network Analysis Policy Basics, page 1 Managing Network Analysis Policies, page 2 Network Analysis Policy Basics Network
Fun with Flow. Richard Friedberg rf [at] cert.org Carnegie Mellon University
![Fun with Flow. Richard Friedberg rf [at] cert.org Carnegie Mellon University Fun with Flow. Richard Friedberg rf [at] cert.org Carnegie Mellon University](/thumbs/80/81762596.jpg) Fun with Flow Richard Friedberg rf [at] cert.org Objectives Flow Primer Why do I care? Tools Capabilities and examples Almost live demo Build it! Where to go for more 2 What is flow? The simple version:
Fun with Flow Richard Friedberg rf [at] cert.org Objectives Flow Primer Why do I care? Tools Capabilities and examples Almost live demo Build it! Where to go for more 2 What is flow? The simple version:
Global Information Assurance Certification Paper
 Global Information Assurance Certification Paper Copyright SANS Institute Author Retains Full Rights This paper is taken from the GIAC directory of certified professionals. Reposting is not permited without
Global Information Assurance Certification Paper Copyright SANS Institute Author Retains Full Rights This paper is taken from the GIAC directory of certified professionals. Reposting is not permited without
Connection Logging. Introduction to Connection Logging
 The following topics describe how to configure the Firepower System to log connections made by hosts on your monitored network: Introduction to, page 1 Strategies, page 2 Logging Decryptable Connections
The following topics describe how to configure the Firepower System to log connections made by hosts on your monitored network: Introduction to, page 1 Strategies, page 2 Logging Decryptable Connections
Connection Logging. About Connection Logging
 The following topics describe how to configure the Firepower System to log connections made by hosts on your monitored network: About, page 1 Strategies, page 2 Logging Decryptable Connections with SSL
The following topics describe how to configure the Firepower System to log connections made by hosts on your monitored network: About, page 1 Strategies, page 2 Logging Decryptable Connections with SSL
TCP, UDP Ports, and ICMP Message Types1
 Appendix A APPENDIX A TCP, UDP Ports, and ICMP Message Types1 I list useful TCP, UDP ports, and ICMP message types in this appendix. A comprehensive list of registered TCP and UDP services may be found
Appendix A APPENDIX A TCP, UDP Ports, and ICMP Message Types1 I list useful TCP, UDP ports, and ICMP message types in this appendix. A comprehensive list of registered TCP and UDP services may be found
Guide to TCP/IP, Third. Chapter 6: Basic TCP/IP Services
 Guide to TCP/IP, Third Edition Chapter 6: Basic TCP/IP Services Objectives Understand how TCP/IP Application layer protocols and services work Explain the capabilities, message types, and request/reply
Guide to TCP/IP, Third Edition Chapter 6: Basic TCP/IP Services Objectives Understand how TCP/IP Application layer protocols and services work Explain the capabilities, message types, and request/reply
Wireshark Tutorial. Chris Neasbitt UGA Dept. of Computer Science
 Wireshark Tutorial Chris Neasbitt UGA Dept. of Computer Science Contents Introduction What is a network trace? What is Wireshark? Basic UI Some of the most useful parts of the UI. Packet Capture How do
Wireshark Tutorial Chris Neasbitt UGA Dept. of Computer Science Contents Introduction What is a network trace? What is Wireshark? Basic UI Some of the most useful parts of the UI. Packet Capture How do
Firepower Threat Defense Cluster for the Firepower 4100/9300
 Firepower Threat Defense Cluster for the Firepower 4100/9300 Clustering lets you group multiple Firepower Threat Defense units together as a single logical device. Clustering is only supported for the
Firepower Threat Defense Cluster for the Firepower 4100/9300 Clustering lets you group multiple Firepower Threat Defense units together as a single logical device. Clustering is only supported for the
CNIT 50: Network Security Monitoring. 6 Command Line Packet Analysis Tools
 CNIT 50: Network Security Monitoring 6 Command Line Packet Analysis Tools Topics SO Tool Categories Running Tcpdump Using Dumpcap and Tshark Running Argus and the Ra Client SO Tool Categories Three Types
CNIT 50: Network Security Monitoring 6 Command Line Packet Analysis Tools Topics SO Tool Categories Running Tcpdump Using Dumpcap and Tshark Running Argus and the Ra Client SO Tool Categories Three Types
Introduction to Networking
 Introduction to Networking Chapters 1 and 2 Outline Computer Network Fundamentals Defining a Network Networks Defined by Geography Networks Defined by Topology Networks Defined by Resource Location OSI
Introduction to Networking Chapters 1 and 2 Outline Computer Network Fundamentals Defining a Network Networks Defined by Geography Networks Defined by Topology Networks Defined by Resource Location OSI
The Need for Collaboration between ISPs and P2P
 The Need for Collaboration between ISPs and P2P 1 P2P systems from an ISP view Structured DHTs (distributed hash tables), e.g., Chord, Pastry, Tapestry, CAN, Tulip, Globally consistent protocol with efficient
The Need for Collaboration between ISPs and P2P 1 P2P systems from an ISP view Structured DHTs (distributed hash tables), e.g., Chord, Pastry, Tapestry, CAN, Tulip, Globally consistent protocol with efficient
The Need for Collaboration between ISPs and P2P
 The Need for Collaboration between ISPs and P2P 1 P2P systems from an ISP view Structured DHTs (distributed hash tables), e.g., Chord, Pastry, Tapestry, CAN, Tulip, Globally consistent protocol with efficient
The Need for Collaboration between ISPs and P2P 1 P2P systems from an ISP view Structured DHTs (distributed hash tables), e.g., Chord, Pastry, Tapestry, CAN, Tulip, Globally consistent protocol with efficient
Network Address Translation (NAT)
 The following topics explain and how to configure it. Why Use NAT?, page 1 NAT Basics, page 2 Guidelines for NAT, page 8 Configure NAT, page 12 Translating IPv6 Networks, page 40 Monitoring NAT, page 51
The following topics explain and how to configure it. Why Use NAT?, page 1 NAT Basics, page 2 Guidelines for NAT, page 8 Configure NAT, page 12 Translating IPv6 Networks, page 40 Monitoring NAT, page 51
This document is intended to give guidance on how to read log entries from a Cisco PIX / ASA. The specific model in this case was a PIX 501.
 1.0 Overview This document is intended to give guidance on how to read log entries from a Cisco PIX / ASA. The specific model in this case was a PIX 501. 2.0 PIX Config The following is the PIX config
1.0 Overview This document is intended to give guidance on how to read log entries from a Cisco PIX / ASA. The specific model in this case was a PIX 501. 2.0 PIX Config The following is the PIX config
Port Utilization in Unified CVP
 Utilization in Unified CVP Utilization Table Columns, page 1 Unified CVP Utilization, page 2 Utilization Table Columns The columns in the port utilization tables in this document describe the following:
Utilization in Unified CVP Utilization Table Columns, page 1 Unified CVP Utilization, page 2 Utilization Table Columns The columns in the port utilization tables in this document describe the following:
Appendix B Policies and Filters
 Appendix B Policies and Filters NOTE: This appendix does not describe Access Control Lists (ACLs) or IPX SAP ACLs, which are additional methods for filtering packets. See Software-Based IP Access Control
Appendix B Policies and Filters NOTE: This appendix does not describe Access Control Lists (ACLs) or IPX SAP ACLs, which are additional methods for filtering packets. See Software-Based IP Access Control
WHITE PAPER HIGH-FIDELITY THREAT INTELLIGENCE: UNDERSTANDING FALSE POSITIVES IN A MULTI-LAYER SECURITY STRATEGY
 WHITE PAPER HIGH-FIDELITY THREAT INTELLIGENCE: UNDERSTANDING FALSE POSITIVES IN A MULTI-LAYER SECURITY STRATEGY Dave Dubois, Global Security Product Management Version: 1.0, Jan 2018 A Multi-Layer Approach
WHITE PAPER HIGH-FIDELITY THREAT INTELLIGENCE: UNDERSTANDING FALSE POSITIVES IN A MULTI-LAYER SECURITY STRATEGY Dave Dubois, Global Security Product Management Version: 1.0, Jan 2018 A Multi-Layer Approach
Systrome Next Gen Firewalls
 N E T K S Systrome Next Gen Firewalls Systrome s Next Generation Firewalls provides comprehensive security protection from layer 2 to layer 7 for the mobile Internet era. The new next generation security
N E T K S Systrome Next Gen Firewalls Systrome s Next Generation Firewalls provides comprehensive security protection from layer 2 to layer 7 for the mobile Internet era. The new next generation security
HP ArcSight Port and Protocol Information
 Important Notice HP ArcSight Port and Protocol Information The information (data) contained on all sheets of this document constitutes confidential information of Hewlett- Packard Company or its affiliates
Important Notice HP ArcSight Port and Protocol Information The information (data) contained on all sheets of this document constitutes confidential information of Hewlett- Packard Company or its affiliates
PrepAwayExam. High-efficient Exam Materials are the best high pass-rate Exam Dumps
 PrepAwayExam http://www.prepawayexam.com/ High-efficient Exam Materials are the best high pass-rate Exam Dumps Exam : 642-618 Title : Deploying Cisco ASA Firewall Solutions (FIREWALL v2.0) Vendors : Cisco
PrepAwayExam http://www.prepawayexam.com/ High-efficient Exam Materials are the best high pass-rate Exam Dumps Exam : 642-618 Title : Deploying Cisco ASA Firewall Solutions (FIREWALL v2.0) Vendors : Cisco
NAT and Firewall ALG Support on Cisco ASR 1000 Series Aggregation Services Routers
 NAT and Firewall ALG Support on Cisco ASR 1000 Series Aggregation Services Routers First Published: February 06, 2009 Last Updated: October 10, 2017 The following tables summarize Network Address Translation
NAT and Firewall ALG Support on Cisco ASR 1000 Series Aggregation Services Routers First Published: February 06, 2009 Last Updated: October 10, 2017 The following tables summarize Network Address Translation
Lecture Overview. INF5290 Ethical Hacking. Lecture 4: Get in touch with services. Where are we in the process of ethical hacking?
 Lecture Overview INF5290 Ethical Hacking Lecture 4: Get in touch with services Trying out default credentials Brute-forcing techniques and mitigations What are the exploits and how to use them Using open-relay
Lecture Overview INF5290 Ethical Hacking Lecture 4: Get in touch with services Trying out default credentials Brute-forcing techniques and mitigations What are the exploits and how to use them Using open-relay
INF5290 Ethical Hacking. Lecture 4: Get in touch with services. Universitetet i Oslo Laszlo Erdödi
 INF5290 Ethical Hacking Lecture 4: Get in touch with services Universitetet i Oslo Laszlo Erdödi Lecture Overview Trying out default credentials Brute-forcing techniques and mitigations What are the exploits
INF5290 Ethical Hacking Lecture 4: Get in touch with services Universitetet i Oslo Laszlo Erdödi Lecture Overview Trying out default credentials Brute-forcing techniques and mitigations What are the exploits
Protection of Communication Infrastructures
 Protection of Communication Infrastructures Chapter 5 Internet Firewalls 1 Introduction to Network Firewalls (1) In building construction, a firewall is designed to keep a fire from spreading from one
Protection of Communication Infrastructures Chapter 5 Internet Firewalls 1 Introduction to Network Firewalls (1) In building construction, a firewall is designed to keep a fire from spreading from one
CISCO EXAM QUESTIONS & ANSWERS
 CISCO 642-618 EXAM QUESTIONS & ANSWERS Number: 642-618 Passing Score: 800 Time Limit: 120 min File Version: 39.6 http://www.gratisexam.com/ CISCO 642-618 EXAM QUESTIONS & ANSWERS Exam Name: Deploying Cisco
CISCO 642-618 EXAM QUESTIONS & ANSWERS Number: 642-618 Passing Score: 800 Time Limit: 120 min File Version: 39.6 http://www.gratisexam.com/ CISCO 642-618 EXAM QUESTIONS & ANSWERS Exam Name: Deploying Cisco
What is New in Cisco ACE 4710 Application Control Engine Software Release 3.1
 What is New in Cisco ACE 4710 Application Control Engine Software Release 3.1 PB478675 Product Overview The Cisco ACE Application Control Engine 4710 represents the next generation of application switches
What is New in Cisco ACE 4710 Application Control Engine Software Release 3.1 PB478675 Product Overview The Cisco ACE Application Control Engine 4710 represents the next generation of application switches
CCNA Exploration Network Fundamentals. Chapter 03 Application Functionality and Protocols
 CCNA Exploration Network Fundamentals Chapter 03 Application Functionality and Protocols Updated: 27/04/2008 1 3.1 Applications: The Interface Between Human and Networks Applications provide the means
CCNA Exploration Network Fundamentals Chapter 03 Application Functionality and Protocols Updated: 27/04/2008 1 3.1 Applications: The Interface Between Human and Networks Applications provide the means
Network Review TEJ4M. SBrace
 Network Review TEJ4M SBrace Example of how the OSI Layers work using an e-mail sent from the computer on the left. Email sent from John: Meet me at Carl s 1:30 John Identify sender and intended receiver;
Network Review TEJ4M SBrace Example of how the OSI Layers work using an e-mail sent from the computer on the left. Email sent from John: Meet me at Carl s 1:30 John Identify sender and intended receiver;
Nessus Scan Report. Hosts Summary (Executive) Hosts Summary (Executive) Mon, 15 May :27:44 EDT
 Nessus Scan Report Mon, 15 May 2017 15:27:44 EDT Table Of Contents Hosts Summary (Executive) 192.168.168.134 Hosts Summary (Executive) [-] Collapse All [+] Expand All 192.168.168.134 Summary Critical High
Nessus Scan Report Mon, 15 May 2017 15:27:44 EDT Table Of Contents Hosts Summary (Executive) 192.168.168.134 Hosts Summary (Executive) [-] Collapse All [+] Expand All 192.168.168.134 Summary Critical High
Ethernet / TCP-IP - Training Suite Application level protocols
 Ethernet / TCP-IP - Training Suite 05 - Application level protocols Application layer protocols 2 World Wide Web HTTP I want HTTP this resource. Hypertext Transfer Protocol (HTTP) Used by the World Wide
Ethernet / TCP-IP - Training Suite 05 - Application level protocols Application layer protocols 2 World Wide Web HTTP I want HTTP this resource. Hypertext Transfer Protocol (HTTP) Used by the World Wide
CCNA Exploration Network Fundamentals. Chapter 3 Application Layer Functionality and Protocols
 CCNA Exploration Network Fundamentals Chapter 3 Application Layer Functionality and Protocols Application Layer Functionality and Protocols Applications: The Interface Between the Networks Horny/Coufal
CCNA Exploration Network Fundamentals Chapter 3 Application Layer Functionality and Protocols Application Layer Functionality and Protocols Applications: The Interface Between the Networks Horny/Coufal
Detecting Network Reconnaissance with the Cisco Cyber Threat Defense Solution 1.0
 Detecting Network Reconnaissance with the Cisco Cyber Threat Defense Solution 1.0 April 9, 2012 Introduction One of the earliest indicators of an impending network attack is the presence of network reconnaissance.
Detecting Network Reconnaissance with the Cisco Cyber Threat Defense Solution 1.0 April 9, 2012 Introduction One of the earliest indicators of an impending network attack is the presence of network reconnaissance.
Foundations of Python
 Foundations of Python Network Programming The comprehensive guide to building network applications with Python Second Edition Brandon Rhodes John Goerzen Apress Contents Contents at a Glance About the
Foundations of Python Network Programming The comprehensive guide to building network applications with Python Second Edition Brandon Rhodes John Goerzen Apress Contents Contents at a Glance About the
HP High-End Firewalls
 HP High-End Firewalls Attack Protection Configuration Guide Part number: 5998-2650 Software version: F1000-A-EI&F1000-S-EI: R3721 F5000: F3210 F1000-E: F3171 Firewall module: F3171 Document version: 6PW101-20120719
HP High-End Firewalls Attack Protection Configuration Guide Part number: 5998-2650 Software version: F1000-A-EI&F1000-S-EI: R3721 F5000: F3210 F1000-E: F3171 Firewall module: F3171 Document version: 6PW101-20120719
Chapter 2. Switch Concepts and Configuration. Part II
 Chapter 2 Switch Concepts and Configuration Part II CCNA3-1 Chapter 2-2 Switch Concepts and Configuration Configuring Switch Security MAC Address Flooding Passwords Spoofing Attacks Console Security Tools
Chapter 2 Switch Concepts and Configuration Part II CCNA3-1 Chapter 2-2 Switch Concepts and Configuration Configuring Switch Security MAC Address Flooding Passwords Spoofing Attacks Console Security Tools
IX Series Protocol APPLICATION NOTE. Wiring
 IX-DA ABC JKL TUV MNO PRIVACY TRANSFER LIST SETTING IX Series Protocol APPLICATION NOTE The IX Series has a variety of IP video door stations, IP audio only door stations, and 2-wire adaptors for legacy
IX-DA ABC JKL TUV MNO PRIVACY TRANSFER LIST SETTING IX Series Protocol APPLICATION NOTE The IX Series has a variety of IP video door stations, IP audio only door stations, and 2-wire adaptors for legacy
BIG-IP Access Policy Manager : Application Access. Version 13.0
 BIG-IP Access Policy Manager : Application Access Version 13.0 Table of Contents Table of Contents Configuring App Tunnel Access... 5 What are app tunnels?...5 About ACLs to control access from app tunnels...
BIG-IP Access Policy Manager : Application Access Version 13.0 Table of Contents Table of Contents Configuring App Tunnel Access... 5 What are app tunnels?...5 About ACLs to control access from app tunnels...
Learn to Brogram. # This line is a comment. # The next line prints exactly what you expect to stdout. print "Hello, world.";
 Learn to Brogram At its most basic mode of operation, Bro only provides an impartial view/understanding of network protocols that it parses. But if you want to understand and detect higherlevel patterns/behaviors/anomalies
Learn to Brogram At its most basic mode of operation, Bro only provides an impartial view/understanding of network protocols that it parses. But if you want to understand and detect higherlevel patterns/behaviors/anomalies
Bro scripts to 595 in 45 mins
 Bro scripts - 101 to 595 in 45 mins Aashish Sharma UNIVERSITY OF CALIFORNIA Zeek scripts - 101 to 595 in 45 mins Aashish Sharma UNIVERSITY OF CALIFORNIA "Bringing Science Solutions to the World" Hundreds
Bro scripts - 101 to 595 in 45 mins Aashish Sharma UNIVERSITY OF CALIFORNIA Zeek scripts - 101 to 595 in 45 mins Aashish Sharma UNIVERSITY OF CALIFORNIA "Bringing Science Solutions to the World" Hundreds
OER uses the following default value if this command is not configured or if the no form of this command is entered: timer: 300
 holddown holddown To configure the Optimized Edge Routing (OER) prefix route dampening timer to set the minimum period of time that a new exit must be used before an alternate exit can be selected, use
holddown holddown To configure the Optimized Edge Routing (OER) prefix route dampening timer to set the minimum period of time that a new exit must be used before an alternate exit can be selected, use
Lab 4: Network Packet Capture and Analysis using Wireshark
 Lab 4: Network Packet Capture and Analysis using Wireshark 4.1 Details Aim: To provide a foundation in network packet capture and analysis. You may be faced with network traffic analysis, from traffic
Lab 4: Network Packet Capture and Analysis using Wireshark 4.1 Details Aim: To provide a foundation in network packet capture and analysis. You may be faced with network traffic analysis, from traffic
Bro: Actively defending so that you can do other stuff
 Bro: Actively defending so that you can do other stuff Aashish Sharma & LBNL Cyber Security Team Lawrence Berkeley National Lab UNIVERSITY OF CALIFORNIA The goal of this talk is to provide you with detailed
Bro: Actively defending so that you can do other stuff Aashish Sharma & LBNL Cyber Security Team Lawrence Berkeley National Lab UNIVERSITY OF CALIFORNIA The goal of this talk is to provide you with detailed
Load Balancing Technology White Paper
 Load Balancing Technology White Paper Keywords: Server, gateway, link, load balancing, SLB, LLB Abstract: This document describes the background, implementation, and operating mechanism of the load balancing
Load Balancing Technology White Paper Keywords: Server, gateway, link, load balancing, SLB, LLB Abstract: This document describes the background, implementation, and operating mechanism of the load balancing
Spirent Avalanche. Applications and Security Testing Solutions. Application. Features & Benefits. Data Sheet. Network Performance Testing
 Data Sheet Spirent Avalanche Spirent s Avalanche Layer 4-7 testing solution provides capacity, security and performance testing for network infrastructures, cloud and virtual environments, Web application
Data Sheet Spirent Avalanche Spirent s Avalanche Layer 4-7 testing solution provides capacity, security and performance testing for network infrastructures, cloud and virtual environments, Web application
Background Traffic to Quarantined Network Blocks administered by APNIC
 Background Traffic to Quarantined Network Blocks administered by APNIC March 2011 Geoff Huston George Michaelson APNIC R&D research@apnic.net APNIC is now regularly examining the unused state of IPv4 address
Background Traffic to Quarantined Network Blocks administered by APNIC March 2011 Geoff Huston George Michaelson APNIC R&D research@apnic.net APNIC is now regularly examining the unused state of IPv4 address
Packet Tracer Simulation - TCP and UDP Communications
 Topology Objectives Part 1: Generate Network Traffic in Simulation Mode Part 2: Examine the Functionality of the TCP and UDP Protocols Background This simulation activity is intended to provide a foundation
Topology Objectives Part 1: Generate Network Traffic in Simulation Mode Part 2: Examine the Functionality of the TCP and UDP Protocols Background This simulation activity is intended to provide a foundation
3.2 COMMUNICATION AND INTERNET TECHNOLOGIES
 3.2 COMMUNICATION AND INTERNET TECHNOLOGIES 3.2.1 PROTOCOLS PROTOCOL Protocol a set of rules governing the way that devices communicate with each other. With networks and the Internet, we need to allow
3.2 COMMUNICATION AND INTERNET TECHNOLOGIES 3.2.1 PROTOCOLS PROTOCOL Protocol a set of rules governing the way that devices communicate with each other. With networks and the Internet, we need to allow
Unit 28 Website Production ASSIGNMENT 1
 Unit 28 Website Production ASSIGNMENT 1 Last week Learning outcomes History HTML skeleton Annotated diagram of a WAN Servers, routers, client PC, browser, Server OS Switch, packet Architecture ISP Web
Unit 28 Website Production ASSIGNMENT 1 Last week Learning outcomes History HTML skeleton Annotated diagram of a WAN Servers, routers, client PC, browser, Server OS Switch, packet Architecture ISP Web
TSIN02 - Internetworking
 Lecture 4: Transport Layer Literature: Forouzan: ch 11-12 2004 Image Coding Group, Linköpings Universitet Lecture 4: Outline Transport layer responsibilities UDP TCP 2 Transport layer in OSI model Figure
Lecture 4: Transport Layer Literature: Forouzan: ch 11-12 2004 Image Coding Group, Linköpings Universitet Lecture 4: Outline Transport layer responsibilities UDP TCP 2 Transport layer in OSI model Figure
APPLICATION LAYER APPLICATION LAYER : DNS, HTTP, , SMTP, Telnet, FTP, Security-PGP-SSH.
 APPLICATION LAYER : DNS, HTTP, E-mail, SMTP, Telnet, FTP, Security-PGP-SSH. To identify an entity, the Internet used the IP address, which uniquely identifies the connection of a host to the Internet.
APPLICATION LAYER : DNS, HTTP, E-mail, SMTP, Telnet, FTP, Security-PGP-SSH. To identify an entity, the Internet used the IP address, which uniquely identifies the connection of a host to the Internet.
NAT Command Reference
 Command Reference Command Hierarchies ISA Configuration Commands on page 639 NAT Service Configuration Commands on page 640 VPRN Commands on page 643 NAT Subscriber Management Commands on page 645 NAT
Command Reference Command Hierarchies ISA Configuration Commands on page 639 NAT Service Configuration Commands on page 640 VPRN Commands on page 643 NAT Subscriber Management Commands on page 645 NAT
CCNA Exploration1 Chapter 3: Application Layer Functionality and Protocols
 CCNA Exploration1 Chapter 3: Application Layer Functionality and Protocols LOCAL CISCO ACADEMY ELSYS TU INSTRUCTOR: STELA STEFANOVA 1 Objectives Functions of the three upper OSI model layers, network services
CCNA Exploration1 Chapter 3: Application Layer Functionality and Protocols LOCAL CISCO ACADEMY ELSYS TU INSTRUCTOR: STELA STEFANOVA 1 Objectives Functions of the three upper OSI model layers, network services
Computer Forensics: Investigating Network Intrusions and Cybercrime, 2nd Edition. Chapter 2 Investigating Network Traffic
 Computer Forensics: Investigating Network Intrusions and Cybercrime, 2nd Edition Chapter 2 Investigating Network Traffic Objectives After completing this chapter, you should be able to: Understand network
Computer Forensics: Investigating Network Intrusions and Cybercrime, 2nd Edition Chapter 2 Investigating Network Traffic Objectives After completing this chapter, you should be able to: Understand network
OmniPeek Report: 21/01/ :17:00. Start: 21/01/ :16:06, Duration: 00:00:33. Total Bytes: , Total Packets: 5274
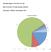 OmniPeek Report: 21/01/2015 14:17:00 Start: 21/01/2015 14:16:06, Duration: 00:00:33 Total Bytes: 1307284, Total Packets: 5274 Summary Statistics: Reported 21/01/2015 14:17:00 Name Bytes Packets Pct of
OmniPeek Report: 21/01/2015 14:17:00 Start: 21/01/2015 14:16:06, Duration: 00:00:33 Total Bytes: 1307284, Total Packets: 5274 Summary Statistics: Reported 21/01/2015 14:17:00 Name Bytes Packets Pct of
Chapter 7. Network Intrusion Detection and Analysis. SeoulTech UCS Lab (Daming Wu)
 SeoulTech UCS Lab Chapter 7 Network Intrusion Detection and Analysis 2015. 11. 3 (Daming Wu) Email: wdm1517@gmail.com Copyright c 2015 by USC Lab All Rights Reserved. Table of Contents 7.1 Why Investigate
SeoulTech UCS Lab Chapter 7 Network Intrusion Detection and Analysis 2015. 11. 3 (Daming Wu) Email: wdm1517@gmail.com Copyright c 2015 by USC Lab All Rights Reserved. Table of Contents 7.1 Why Investigate
Cisco IOS Flexible NetFlow Command Reference
 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387) Fax: 408 527-0883 THE SPECIFICATIONS AND INFORMATION
Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387) Fax: 408 527-0883 THE SPECIFICATIONS AND INFORMATION
TRANSMISSION CONTROL PROTOCOL. ETI 2506 TELECOMMUNICATION SYSTEMS Monday, 7 November 2016
 TRANSMISSION CONTROL PROTOCOL ETI 2506 TELECOMMUNICATION SYSTEMS Monday, 7 November 2016 ETI 2506 - TELECOMMUNICATION SYLLABUS Principles of Telecom (IP Telephony and IP TV) - Key Issues to remember 1.
TRANSMISSION CONTROL PROTOCOL ETI 2506 TELECOMMUNICATION SYSTEMS Monday, 7 November 2016 ETI 2506 - TELECOMMUNICATION SYLLABUS Principles of Telecom (IP Telephony and IP TV) - Key Issues to remember 1.
Configuring Virtual Servers
 3 CHAPTER This section provides an overview of server load balancing and procedures for configuring virtual servers for load balancing on an ACE appliance. Note When you use the ACE CLI to configure named
3 CHAPTER This section provides an overview of server load balancing and procedures for configuring virtual servers for load balancing on an ACE appliance. Note When you use the ACE CLI to configure named
Deploying Cisco ASA Firewall Solutions (FIREWALL v1.0)
 Cisco 642-617 Deploying Cisco ASA Firewall Solutions (FIREWALL v1.0) Version: 4.8 QUESTION NO: 1 Which Cisco ASA feature enables the ASA to do these two things? 1) Act as a proxy for the server and generate
Cisco 642-617 Deploying Cisco ASA Firewall Solutions (FIREWALL v1.0) Version: 4.8 QUESTION NO: 1 Which Cisco ASA feature enables the ASA to do these two things? 1) Act as a proxy for the server and generate
User Identity Sources
 The following topics describe Firepower System user identity sources, which are sources for user awareness. These users can be controlled with identity and access control policies: About, on page 1 The
The following topics describe Firepower System user identity sources, which are sources for user awareness. These users can be controlled with identity and access control policies: About, on page 1 The
Comparison of Maxwell Family of Network Emulators. Kings Village Center #66190 Scotts Valley, CA iwl.com
 Comparison of Maxwell Family of Network Emulators Kings Village Center #66190 Scotts Valley, CA 95067 +1.831.460.7010 info@ 1 Point-and-Click Scenarios Cross-Atlantic T1 ATM Link X X Low earth orbit satellite
Comparison of Maxwell Family of Network Emulators Kings Village Center #66190 Scotts Valley, CA 95067 +1.831.460.7010 info@ 1 Point-and-Click Scenarios Cross-Atlantic T1 ATM Link X X Low earth orbit satellite
Lecture-4. TCP/IP-Overview:
 Lecture-4 TCP/IP-Overview: The history goes back to ARPANET a research network sponsored by DoD US Govt. It eventually connected hundreds of universities and govt installations, using leased telephone
Lecture-4 TCP/IP-Overview: The history goes back to ARPANET a research network sponsored by DoD US Govt. It eventually connected hundreds of universities and govt installations, using leased telephone
Computer Network Programming. The Transport Layer. Dr. Sam Hsu Computer Science & Engineering Florida Atlantic University
 Computer Network Programming The Transport Layer Dr. Sam Hsu Computer Science & Engineering Florida Atlantic University The Transport Layer The Big Picture Overview of TCP/IP protocols TCP Packet Exchanges
Computer Network Programming The Transport Layer Dr. Sam Hsu Computer Science & Engineering Florida Atlantic University The Transport Layer The Big Picture Overview of TCP/IP protocols TCP Packet Exchanges
BIG-IP Local Traffic Manager : Monitors Reference 13.0
 BIG-IP Local Traffic Manager : Monitors Reference 13.0 Table of Contents Table of Contents Monitors Concepts... 5 Purpose of monitors...5 Benefits of monitors... 5 About icheck functionality for monitors...
BIG-IP Local Traffic Manager : Monitors Reference 13.0 Table of Contents Table of Contents Monitors Concepts... 5 Purpose of monitors...5 Benefits of monitors... 5 About icheck functionality for monitors...
This article explains how to configure NSRP-Lite for a NS50 firewall to a single WAN.
 This article explains how to configure NSRP-Lite for a NS50 firewall to a single WAN. Requirements: When configuring NSRP-Lite for the NS-50, confirm the following necessary requirements: The NS-25 or
This article explains how to configure NSRP-Lite for a NS50 firewall to a single WAN. Requirements: When configuring NSRP-Lite for the NS-50, confirm the following necessary requirements: The NS-25 or
Agility2018-TCPdump Documentation
 Agility2018-TCPdump Documentation Release.01 David Larsen Aug 10, 2018 Switches 1 F5 tcpdump and Wireshark 3 1.1 tcpdump Switches............................................ 3 1.2 tcpdump Filters..............................................
Agility2018-TCPdump Documentation Release.01 David Larsen Aug 10, 2018 Switches 1 F5 tcpdump and Wireshark 3 1.1 tcpdump Switches............................................ 3 1.2 tcpdump Filters..............................................
Operating Systems. 16. Networking. Paul Krzyzanowski. Rutgers University. Spring /6/ Paul Krzyzanowski
 Operating Systems 16. Networking Paul Krzyzanowski Rutgers University Spring 2015 1 Local Area Network (LAN) LAN = communications network Small area (building, set of buildings) Same, sometimes shared,
Operating Systems 16. Networking Paul Krzyzanowski Rutgers University Spring 2015 1 Local Area Network (LAN) LAN = communications network Small area (building, set of buildings) Same, sometimes shared,
HP Instant Support Enterprise Edition (ISEE) Security overview
 HP Instant Support Enterprise Edition (ISEE) Security overview Advanced Configuration A.03.50 Mike Brandon Interex 03 / 30, 2004 2003 Hewlett-Packard Development Company, L.P. The information contained
HP Instant Support Enterprise Edition (ISEE) Security overview Advanced Configuration A.03.50 Mike Brandon Interex 03 / 30, 2004 2003 Hewlett-Packard Development Company, L.P. The information contained
Network+ Guide to Networks, Seventh Edition Chapter 2, Solutions
 Network+ Guide to Networks, Seventh Edition Chapter 2, Solutions Review Questions 1. Which part of a MAC address is unique to each manufacturer? A. The network identifier B. The OUI C. The device identifier
Network+ Guide to Networks, Seventh Edition Chapter 2, Solutions Review Questions 1. Which part of a MAC address is unique to each manufacturer? A. The network identifier B. The OUI C. The device identifier
Granular Protocol Inspection
 The feature adds flexibility to the Cisco IOS Firewall by allowing it to perform a higher degree of inspection of TCP and User Data Protocol (UDP) traffic for most RFC 1700 application types. Finding Feature
The feature adds flexibility to the Cisco IOS Firewall by allowing it to perform a higher degree of inspection of TCP and User Data Protocol (UDP) traffic for most RFC 1700 application types. Finding Feature
Monitoring SharePoint 2007/ 2010/ 2013 Server using EventTracker
 Monitoring SharePoint 2007/ 2010/ 2013 Server using EventTracker Publication Date: June 12, 2012 Abstract EventTracker allows you to effectively manage your systems and provides operational efficiencies
Monitoring SharePoint 2007/ 2010/ 2013 Server using EventTracker Publication Date: June 12, 2012 Abstract EventTracker allows you to effectively manage your systems and provides operational efficiencies
Port Mirroring in CounterACT. CounterACT Technical Note
 Table of Contents About Port Mirroring and the Packet Engine... 3 Information Based on Specific Protocols... 4 ARP... 4 DHCP... 5 HTTP... 6 NetBIOS... 7 TCP/UDP... 7 Endpoint Lifecycle... 8 Active Endpoint
Table of Contents About Port Mirroring and the Packet Engine... 3 Information Based on Specific Protocols... 4 ARP... 4 DHCP... 5 HTTP... 6 NetBIOS... 7 TCP/UDP... 7 Endpoint Lifecycle... 8 Active Endpoint
Virtual PBX Product Guide MODEL: SP-250 SP-500 SP-1000 SP-1500 SP-3000
 Virtual PBX Product Guide MODEL: SP-250 SP-500 SP-1000 SP-1500 SP-3000 Welcome to SimplifiCloud EXPAND, IMPROVE & REDUCE COSTS OF YOUR TELEPHONE SYSTEM SimplifiCloud presents unified communication systems
Virtual PBX Product Guide MODEL: SP-250 SP-500 SP-1000 SP-1500 SP-3000 Welcome to SimplifiCloud EXPAND, IMPROVE & REDUCE COSTS OF YOUR TELEPHONE SYSTEM SimplifiCloud presents unified communication systems
CSCI 466 Midterm Networks Fall 2013
 CSCI 466 Midterm Networks Fall 2013 Name: This exam consists of 6 problems on the following 7 pages. You may use your single-sided hand-written 8 ½ x 11 note sheet and a calculator during the exam. No
CSCI 466 Midterm Networks Fall 2013 Name: This exam consists of 6 problems on the following 7 pages. You may use your single-sided hand-written 8 ½ x 11 note sheet and a calculator during the exam. No
