What are the differences between the Set interface and the List interface?
|
|
|
- Rodger Cole
- 6 years ago
- Views:
Transcription
1 7.1.1 Explain the effect of the following method calls. Set<String> s = new HashSet<String>(); s.add("hello"); s.add("bye"); s.addall(s); Set<String> t = new TreeSet<String>(); t.add("123"); s.addall(t); System.out.println(s.containsAll(t)); System.out.println(t.containsAll(s)); System.out.println(s.contains("ace")); s.retainall(t); t.retainall(s); System.out.println(t.contains("123")); Set<String> s = new HashSet<String>(); Creates a HashSet object to hold Strings and assignes a reference to it to the variable s. s.add("hello"); Adds the string "hello" to the set. s.add("bye"); Adds the string "bye" to the set. s.addall(s); Copies the content of s into itself. Effectively doing nothing since sets do not contain duplicate values. Set<String> t = new TreeSet<String>(); Creates a TreeSet object to hold Strings and assignes a reference to it to the variable t. t.add("123"); Adds the string "123" to t. s.addall(t); Adds the contents of t to s. s now contains {"hello", "bye", "123"} System.out.println(s.containsAll(t)); Outputs "true" since all of the elements in t are included in s. System.out.println(t.containsAll(s)); Outputs "false" since there are elements in s that are not in t. System.out.println(s.contains("ace")); Outputs "false" since "ace" is not in s. Outputs "true" since "123" is contained in s. s.retainall(t); Removes the elements from s that are not in t. Outputs "true" since "123" is still in s. t.retainall(s); Effectively nothing, since s now only contains the values in t. System.out.println(t.contains("123")); Outputs "true" since "123" is still in t What are the differences between the Set interface and the List interface?
2 Elements in a List have a position (index) and the List interface contains methods to access element using an index. Also the requirements on the equals and hashcode methods are different. The List also defines a ListIterator which allows bi-directional traversal If you were using a Map to store the following lists of items, which data field would you select as the key, and why? a. textbook title, author, ISBN (International Standard Book Number), year, publisher b. player s name, uniform number, team, position c. computer manufacturer, model number, processor, memory, disk size d. department, course title, course ID, section number, days, time, room a. ISBN Number. There may be multiple textbooks with the same year, publisher, year, or author, but the ISBN would be unique to the particular book. b. There is not good key. None of these are unique. c. Model number, because it is unique, but there could be many computer models with the same manufacturer, processor, memory, or disk size. d. Course ID, because many courses can have the same department, title, section number, days, time, or room. Explain the effect of each statement in the following fragment on the index built in Self-Check Exercise 2. lines = index.get("this"); lines = index.get("that"); lines = index.get("line"); lines.add(4); index.put("is", lines); lines = index.get("this"); lines references the list [1] lines = index.get("that"); lines is null. lines = index.get("line"); lines references the list [1, 2, 3] lines.add(4); The value of 4 is added to the list referenced by lines and indexed by "line", it is now [1, 2, 3, 4] index.put("is", lines); The list [1, 2, 3, 4] is also indexed by "is". Note "line" and "is" both are paired with the same list
3 For the hash table search algorithm shown in this section, why was it unnecessary to test whether all table entries had been examined as part of Step 5? The table is never allowed to become full, therefore, the loop will always terminate by finding the requested item or by finding a null entry The following table stores Integer keys with the int values shown. Show one sequence of insertions that would store the keys as shown. Which elements were placed in their current position because of collisions? Show the table that would be formed by chaining. Index Key [0] 24 [1] 6 [2] 20 [3] [4] 14 Inserting in the order 6, 14, 24, 20 would result in the order shown. 24 was placed in it position because of a collision with is then placed in position [2] because of collision with 24 and 6. If chaining were used the table would look as follows: [0] 20 [1] 6 [2] [3] [4] Explain what is wrong with the following strategy to reclaim space that is filled with deleted items in a hash table: When attempting to insert a new item in the table, if you encounter an item that has been deleted, replace the deleted item with the new item. Assume that we take the table given in Example 7.7 and delete "Dick", marking it with "deleted". Next we try to re-insert "Sam" The search for "Sam" will start at [4] and then advance to [0] finding the "deleted" flag. We would then insert "Sam" at that position, resulting in duplicate values in the hash table
4 One simple hash code is to use the sum of the ASCII codes for the letters in a word. Explain why this is not a good hash code. Many word contain the same letters, but in a different order. For example cat and tac. These would have the same hash code Use the hash code in Self-Check Exercise 7 to store the words "cat", "hat", "tac", "act" in a hash table of size 10. Show this table using open hashing and chaining. Letter Code Letter Code Letter Code Letter Code c 99 h 104 t 116 a 97 a 97 a 97 a 97 c 99 t 116 t 116 c 99 t 116 SUM Word Code Code % 10 cat hat tac act Position Open Hashing Chaining cat cat tac act 3 tac 4 act hat hat The following table stores Integer keys with the int values shown. Where would each key be placed in the new table resulting from rehashing the current table? Index Key
5 Index Key Explain why the nested interface Map.Entry is needed. The interface Map.Entry is needed for the return value of the entryset method. This allows one to access the contents of the map and traverse it easily. It is not strictly necessary since one could obtain the keyset and then iterate through it and obtain the corresponding value for each key, but this would be inefficient since a look-up of each key would then be required Why did we make clones of the bit string code in recursive method buildcodetable? What would happen if we didn t? If we did not clone the code parameter passed to the buildcodetable method the values leftcode and rightcode would reference the original value of code. When the append method was called it would then append the value to the original What is displayed by the execution of the following program? public static void main(string[] args) { NavigableSet<Integer> s = new TreeSet<Integer>(); s.add(5); s.add(6); s.add(3); s.add(2); s.add(9); NavigableSet<Integer> a = s.subset(1, true, 9, false); NavigableSet<Integer> b = s.subset(4, true, 9, true); System.out.println(a); System.out.println(b); System.out.println(s.higher(5)); System.out.println(s.lower(5)); System.out.println(a.first()); System.out.println(b.lower(4)); int sum = 0; for (int i : a) { System.out.println(i); sum += i; } System.out.println(sum); } [2, 3, 5, 6]
6 [5, 6, 9] null
Set<Integer> s = new TreeSet<Integer>(); s.add( 7 ); s.add( 7 ); System.out.println( s.size() );
 Advanced Java Concepts Maps and Sets and Miscellany Exercises and Programs 1. This code a) contains a compiler error. b) contains a runtime error. c) displays 1 d) displays 2 2. This code a) contains a
Advanced Java Concepts Maps and Sets and Miscellany Exercises and Programs 1. This code a) contains a compiler error. b) contains a runtime error. c) displays 1 d) displays 2 2. This code a) contains a
USAL1J: Java Collections. S. Rosmorduc
 USAL1J: Java Collections S. Rosmorduc 1 A simple collection: ArrayList A list, implemented as an Array ArrayList l= new ArrayList() l.add(x): adds x at the end of the list l.add(i,x):
USAL1J: Java Collections S. Rosmorduc 1 A simple collection: ArrayList A list, implemented as an Array ArrayList l= new ArrayList() l.add(x): adds x at the end of the list l.add(i,x):
Collections and Maps
 Software and Programming I Collections and Maps Roman Kontchakov / Carsten Fuhs Birkbeck, University of London Outline Array Lists Enhanced for Loop ArrayList and LinkedList Collection Interface Sets and
Software and Programming I Collections and Maps Roman Kontchakov / Carsten Fuhs Birkbeck, University of London Outline Array Lists Enhanced for Loop ArrayList and LinkedList Collection Interface Sets and
Sets and Maps. Part of the Collections Framework
 Sets and Maps Part of the Collections Framework The Set interface A Set is unordered and has no duplicates Operations are exactly those for Collection int size( ); boolean isempty( ); boolean contains(object
Sets and Maps Part of the Collections Framework The Set interface A Set is unordered and has no duplicates Operations are exactly those for Collection int size( ); boolean isempty( ); boolean contains(object
Software 1 with Java. Java Collections Framework. Collection Interfaces. Online Resources. The Collection Interface
 Java Collections Framework Collection: a group of elements Based Design: Software 1 with Java Java Collections Framework s s Algorithms Recitation No. 6 (Collections) 2 Collection s Online Resources Collection
Java Collections Framework Collection: a group of elements Based Design: Software 1 with Java Java Collections Framework s s Algorithms Recitation No. 6 (Collections) 2 Collection s Online Resources Collection
Object-Oriented Programming with Java
 Object-Oriented Programming with Java Recitation No. 2 Oranit Dror The String Class Represents a character string (e.g. "Hi") Explicit constructor: String quote = "Hello World"; string literal All string
Object-Oriented Programming with Java Recitation No. 2 Oranit Dror The String Class Represents a character string (e.g. "Hi") Explicit constructor: String quote = "Hello World"; string literal All string
CONTAİNERS COLLECTİONS
 CONTAİNERS Some programs create too many objects and deal with them. In such a program, it is not feasible to declare a separate variable to hold reference to each of these objects. The proper way of keeping
CONTAİNERS Some programs create too many objects and deal with them. In such a program, it is not feasible to declare a separate variable to hold reference to each of these objects. The proper way of keeping
Lec 3. Compilers, Debugging, Hello World, and Variables
 Lec 3 Compilers, Debugging, Hello World, and Variables Announcements First book reading due tonight at midnight Complete 80% of all activities to get 100% HW1 due Saturday at midnight Lab hours posted
Lec 3 Compilers, Debugging, Hello World, and Variables Announcements First book reading due tonight at midnight Complete 80% of all activities to get 100% HW1 due Saturday at midnight Lab hours posted
Sun Certified Programmer for the Java 2 Platform. SE6.0
 Sun Certified Programmer for the Java 2 Platform. SE6.0 Version 4.0 QUESTION NO: 1 Given a pre-generics implementation of a method: 11. public static int sum(list list) { 12. int sum = 0; 13. for ( Iterator
Sun Certified Programmer for the Java 2 Platform. SE6.0 Version 4.0 QUESTION NO: 1 Given a pre-generics implementation of a method: 11. public static int sum(list list) { 12. int sum = 0; 13. for ( Iterator
CSCI 261 Computer Science II
 CSCI 261 Computer Science II Department of Mathematics and Computer Science Lecture 9 Sets and Maps Outline Sets and Baby Set Theory Why Maps? Map: Open Addressing Put Implementation Get Implementation
CSCI 261 Computer Science II Department of Mathematics and Computer Science Lecture 9 Sets and Maps Outline Sets and Baby Set Theory Why Maps? Map: Open Addressing Put Implementation Get Implementation
Oracle 1Z0-851 Java Standard Edition 6 Programmer Certified Professional Exam
 Oracle 1Z0-851 Java Standard Edition 6 Programmer Certified Professional Exam 1 QUESTION: 1 Given a pre-generics implementation of a method: 11. public static int sum(list list) { 12. int sum = 0; 13.
Oracle 1Z0-851 Java Standard Edition 6 Programmer Certified Professional Exam 1 QUESTION: 1 Given a pre-generics implementation of a method: 11. public static int sum(list list) { 12. int sum = 0; 13.
Compsci 201 Hashing. Jeff Forbes February 7, /7/18 CompSci 201, Spring 2018, Hashiing
 Compsci 201 Hashing Jeff Forbes February 7, 2018 1 G is for Garbage Collection Nice to call new and not call delete! Git Version control that's so au courant GPL First open source license Google How to
Compsci 201 Hashing Jeff Forbes February 7, 2018 1 G is for Garbage Collection Nice to call new and not call delete! Git Version control that's so au courant GPL First open source license Google How to
CS61BL Summer 2013 Midterm 2
 CS61BL Summer 2013 Midterm 2 Sample Solutions + Common Mistakes Question 0: Each of the following cost you.5 on this problem: you earned some credit on a problem and did not put your five digit on the
CS61BL Summer 2013 Midterm 2 Sample Solutions + Common Mistakes Question 0: Each of the following cost you.5 on this problem: you earned some credit on a problem and did not put your five digit on the
Java Collections. Readings and References. Collections Framework. Java 2 Collections. References. CSE 403, Winter 2003 Software Engineering
 Readings and References Java Collections References» "Collections", Java tutorial» http://java.sun.com/docs/books/tutorial/collections/index.html CSE 403, Winter 2003 Software Engineering http://www.cs.washington.edu/education/courses/403/03wi/
Readings and References Java Collections References» "Collections", Java tutorial» http://java.sun.com/docs/books/tutorial/collections/index.html CSE 403, Winter 2003 Software Engineering http://www.cs.washington.edu/education/courses/403/03wi/
Arrays. 1 Index mapping
 Arrays 1 Index mapping You are expected already to have a good understanding of arrays. We examine some array techniques in more detail, beginning with index mapping. Index mapping is a technique for compact
Arrays 1 Index mapping You are expected already to have a good understanding of arrays. We examine some array techniques in more detail, beginning with index mapping. Index mapping is a technique for compact
CS11 Java. Winter Lecture 8
 CS11 Java Winter 2010-2011 Lecture 8 Java Collections Very powerful set of classes for managing collections of objects Introduced in Java 1.2 Provides: Interfaces specifying different kinds of collections
CS11 Java Winter 2010-2011 Lecture 8 Java Collections Very powerful set of classes for managing collections of objects Introduced in Java 1.2 Provides: Interfaces specifying different kinds of collections
COURSE 4 PROGRAMMING III OOP. JAVA LANGUAGE
 COURSE 4 PROGRAMMING III OOP. JAVA LANGUAGE PREVIOUS COURSE CONTENT Inheritance Abstract classes Interfaces instanceof operator Nested classes Enumerations COUSE CONTENT Collections List Map Set Aggregate
COURSE 4 PROGRAMMING III OOP. JAVA LANGUAGE PREVIOUS COURSE CONTENT Inheritance Abstract classes Interfaces instanceof operator Nested classes Enumerations COUSE CONTENT Collections List Map Set Aggregate
Loops. CSE 114, Computer Science 1 Stony Brook University
 Loops CSE 114, Computer Science 1 Stony Brook University http://www.cs.stonybrook.edu/~cse114 1 Motivation Suppose that you need to print a string (e.g., "Welcome to Java!") a user-defined times N: N?
Loops CSE 114, Computer Science 1 Stony Brook University http://www.cs.stonybrook.edu/~cse114 1 Motivation Suppose that you need to print a string (e.g., "Welcome to Java!") a user-defined times N: N?
public static<e> List<E> removeoccurrences(list<e> origlist, E remove) {
 CS 201, Fall 2008 Nov 19th Exam 2 Name: Question 1. [10 points] Complete the following generic method. It should return a list containing all of the elements in origlist, in order, except the elements
CS 201, Fall 2008 Nov 19th Exam 2 Name: Question 1. [10 points] Complete the following generic method. It should return a list containing all of the elements in origlist, in order, except the elements
1.00/1.001 Introduction to Computers and Engineering Problem Solving. Final Exam
 1.00/1.001 Introduction to Computers and Engineering Problem Solving Final Exam Name: Email Address: TA: Section: You have three hours to complete this exam. For coding questions, you do not need to include
1.00/1.001 Introduction to Computers and Engineering Problem Solving Final Exam Name: Email Address: TA: Section: You have three hours to complete this exam. For coding questions, you do not need to include
CSC 1351: Final. The code compiles, but when it runs it throws a ArrayIndexOutOfBoundsException
 VERSION A CSC 1351: Final Name: 1 Interfaces, Classes and Inheritance 2 Basic Data Types (arrays, lists, stacks, queues, trees,...) 2.1 Does the following code compile? If it does not, how can it be fixed?
VERSION A CSC 1351: Final Name: 1 Interfaces, Classes and Inheritance 2 Basic Data Types (arrays, lists, stacks, queues, trees,...) 2.1 Does the following code compile? If it does not, how can it be fixed?
A simple map: Hashtable
 Using Maps A simple map: Hashtable To create a Hashtable, use: import java.util.*; Hashtable table = new Hashtable(); To put things into a Hashtable, use: table.put(key, value); To retrieve a value from
Using Maps A simple map: Hashtable To create a Hashtable, use: import java.util.*; Hashtable table = new Hashtable(); To put things into a Hashtable, use: table.put(key, value); To retrieve a value from
CSC 321: Data Structures. Fall 2016
 CSC : Data Structures Fall 6 Hash tables HashSet & HashMap hash table, hash function collisions Ø linear probing, lazy deletion, primary clustering Ø quadratic probing, rehashing Ø chaining HashSet & HashMap
CSC : Data Structures Fall 6 Hash tables HashSet & HashMap hash table, hash function collisions Ø linear probing, lazy deletion, primary clustering Ø quadratic probing, rehashing Ø chaining HashSet & HashMap
Practice exam for CMSC131-04, Fall 2017
 Practice exam for CMSC131-04, Fall 2017 Q1 makepalindrome - Relevant topics: arrays, loops Write a method makepalidrome that takes an int array, return a new int array that contains the values from the
Practice exam for CMSC131-04, Fall 2017 Q1 makepalindrome - Relevant topics: arrays, loops Write a method makepalidrome that takes an int array, return a new int array that contains the values from the
Exam Name: Java Standard Edition 6 Programmer Certified Professional Exam
 Vendor: Oracle Exam Code: 1Z0-851 Exam Name: Java Standard Edition 6 Programmer Certified Professional Exam Version: DEMO QUESTION 1 Given a pre-generics implementation of a method: public static int sum(list
Vendor: Oracle Exam Code: 1Z0-851 Exam Name: Java Standard Edition 6 Programmer Certified Professional Exam Version: DEMO QUESTION 1 Given a pre-generics implementation of a method: public static int sum(list
11/27/12. CS202 Fall 2012 Lecture 11/15. Hashing. What: WiCS CS Courses: Inside Scoop When: Monday, Nov 19th from 5-7pm Where: SEO 1000
 What: WiCS CS Courses: Inside Scoop When: Monday, Nov 19th from -pm Where: SEO 1 Having trouble figuring out what classes to take next semester? Wish you had information on what CS course to take when?
What: WiCS CS Courses: Inside Scoop When: Monday, Nov 19th from -pm Where: SEO 1 Having trouble figuring out what classes to take next semester? Wish you had information on what CS course to take when?
Testpassport. T e s tpas s port.
 Testpassport T e s tpas s port http://www.testpassport.kr Exam : 1Z0-851 Title : Java Standard Edition 6 Programmer Certified Professional Exam Version : Demo 1 / 11 1.Given a pre-generics implementation
Testpassport T e s tpas s port http://www.testpassport.kr Exam : 1Z0-851 Title : Java Standard Edition 6 Programmer Certified Professional Exam Version : Demo 1 / 11 1.Given a pre-generics implementation
Two Dimensional Arrays
 + Two Dimensional Arrays + Two Dimensional Arrays So far we have studied how to store linear collections of data using a single dimensional array. However, the data associated with certain systems (a digital
+ Two Dimensional Arrays + Two Dimensional Arrays So far we have studied how to store linear collections of data using a single dimensional array. However, the data associated with certain systems (a digital
CPSC 211, Sections : Data Structures and Implementations, Honors Final Exam May 4, 2001
 CPSC 211, Sections 201 203: Data Structures and Implementations, Honors Final Exam May 4, 2001 Name: Section: Instructions: 1. This is a closed book exam. Do not use any notes or books. Do not confer with
CPSC 211, Sections 201 203: Data Structures and Implementations, Honors Final Exam May 4, 2001 Name: Section: Instructions: 1. This is a closed book exam. Do not use any notes or books. Do not confer with
What is the Java Collections Framework?
 1 of 13 What is the Java Collections Framework? To begin with, what is a collection?. I have a collection of comic books. In that collection, I have Tarzan comics, Phantom comics, Superman comics and several
1 of 13 What is the Java Collections Framework? To begin with, what is a collection?. I have a collection of comic books. In that collection, I have Tarzan comics, Phantom comics, Superman comics and several
Bjarne Stroustrup. creator of C++
 We Continue GEEN163 I have always wished for my computer to be as easy to use as my telephone; my wish has come true because I can no longer figure out how to use my telephone. Bjarne Stroustrup creator
We Continue GEEN163 I have always wished for my computer to be as easy to use as my telephone; my wish has come true because I can no longer figure out how to use my telephone. Bjarne Stroustrup creator
Java Standard Edition 6 Programmer Certified Professional Exam
 Oracle 1z0-851 Java Standard Edition 6 Programmer Certified Professional Exam Version: 4.3 Topic 1, Volume A QUESTION NO: 1 Given a pre-generics implementation of a method: 11. public static int sum(list
Oracle 1z0-851 Java Standard Edition 6 Programmer Certified Professional Exam Version: 4.3 Topic 1, Volume A QUESTION NO: 1 Given a pre-generics implementation of a method: 11. public static int sum(list
Points off Total off Net Score. CS 314 Final Exam Spring 2017
 Points off 1 2 3 4 5 6 Total off Net Score CS 314 Final Exam Spring 2017 Your Name Your UTEID Instructions: 1. There are 6 questions on this test. 100 points available. Scores will be scaled to 300 points.
Points off 1 2 3 4 5 6 Total off Net Score CS 314 Final Exam Spring 2017 Your Name Your UTEID Instructions: 1. There are 6 questions on this test. 100 points available. Scores will be scaled to 300 points.
Questions. 6. Suppose we were to define a hash code on strings s by:
 Questions 1. Suppose you are given a list of n elements. A brute force method to find duplicates could use two (nested) loops. The outer loop iterates over position i the list, and the inner loop iterates
Questions 1. Suppose you are given a list of n elements. A brute force method to find duplicates could use two (nested) loops. The outer loop iterates over position i the list, and the inner loop iterates
Hash Tables. Hashing Probing Separate Chaining Hash Function
 Hash Tables Hashing Probing Separate Chaining Hash Function Introduction In Chapter 4 we saw: linear search O( n ) binary search O( log n ) Can we improve the search operation to achieve better than O(
Hash Tables Hashing Probing Separate Chaining Hash Function Introduction In Chapter 4 we saw: linear search O( n ) binary search O( log n ) Can we improve the search operation to achieve better than O(
CSE 143. Lecture 28: Hashing
 CSE 143 Lecture 28: Hashing SearchTree as a set We implemented a class SearchTree to store a BST of ints: Our BST is essentially a set of integers. Operations we support: add contains remove... -3 overallroot
CSE 143 Lecture 28: Hashing SearchTree as a set We implemented a class SearchTree to store a BST of ints: Our BST is essentially a set of integers. Operations we support: add contains remove... -3 overallroot
CSC 321: Data Structures. Fall 2017
 CSC : Data Structures Fall 7 Hash tables HashSet & HashMap hash table, hash function collisions Ø linear probing, lazy deletion, clustering, rehashing Ø chaining Java hashcode method HW6: finite state
CSC : Data Structures Fall 7 Hash tables HashSet & HashMap hash table, hash function collisions Ø linear probing, lazy deletion, clustering, rehashing Ø chaining Java hashcode method HW6: finite state
Topic #9: Collections. Readings and References. Collections. Collection Interface. Java Collections CSE142 A-1
 Topic #9: Collections CSE 413, Autumn 2004 Programming Languages http://www.cs.washington.edu/education/courses/413/04au/ If S is a subtype of T, what is S permitted to do with the methods of T? Typing
Topic #9: Collections CSE 413, Autumn 2004 Programming Languages http://www.cs.washington.edu/education/courses/413/04au/ If S is a subtype of T, what is S permitted to do with the methods of T? Typing
CONDITIONAL EXECUTION
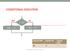 CONDITIONAL EXECUTION yes x > y? no max = x; max = y; logical AND logical OR logical NOT &&! Fundamentals of Computer Science I Outline Conditional Execution if then if then Nested if then statements Comparisons
CONDITIONAL EXECUTION yes x > y? no max = x; max = y; logical AND logical OR logical NOT &&! Fundamentals of Computer Science I Outline Conditional Execution if then if then Nested if then statements Comparisons
Trees in java.util. A set is an object that stores unique elements In Java, two implementations are available:
 Trees in java.util A set is an object that stores unique elements In Java, two implementations are available: The class HashSet implements the set with a hash table and a hash function The class TreeSet,
Trees in java.util A set is an object that stores unique elements In Java, two implementations are available: The class HashSet implements the set with a hash table and a hash function The class TreeSet,
Programming Basics. Digital Urban Visualization. People as Flows. ia
 Programming Basics Digital Urban Visualization. People as Flows. 28.09.2015 ia zuend@arch.ethz.ch treyer@arch.ethz.ch Programming? Programming is the interaction between the programmer and the computer.
Programming Basics Digital Urban Visualization. People as Flows. 28.09.2015 ia zuend@arch.ethz.ch treyer@arch.ethz.ch Programming? Programming is the interaction between the programmer and the computer.
The Collections API. Lecture Objectives. The Collections API. Mark Allen Weiss
 The Collections API Mark Allen Weiss Lecture Objectives To learn how to use the Collections package in Java 1.2. To illustrate features of Java that help (and hurt) the design of the Collections API. Tuesday,
The Collections API Mark Allen Weiss Lecture Objectives To learn how to use the Collections package in Java 1.2. To illustrate features of Java that help (and hurt) the design of the Collections API. Tuesday,
Lecture 18. Collision Resolution
 Lecture 18 Collision Resolution Introduction In this lesson we will discuss several collision resolution strategies. The key thing in hashing is to find an easy to compute hash function. However, collisions
Lecture 18 Collision Resolution Introduction In this lesson we will discuss several collision resolution strategies. The key thing in hashing is to find an easy to compute hash function. However, collisions
HO #13 Fall 2015 Gary Chan. Hashing (N:12)
 HO #13 Fall 2015 Gary Chan Hashing (N:12) Outline Motivation Hashing Algorithms and Improving the Hash Functions Collisions Strategies Open addressing and linear probing Separate chaining COMP2012H (Hashing)
HO #13 Fall 2015 Gary Chan Hashing (N:12) Outline Motivation Hashing Algorithms and Improving the Hash Functions Collisions Strategies Open addressing and linear probing Separate chaining COMP2012H (Hashing)
MIDTERM EXAM THURSDAY MARCH
 Week 6 Assignments: Program 2: is being graded Program 3: available soon and due before 10pm on Thursday 3/14 Homework 5: available soon and due before 10pm on Monday 3/4 X-Team Exercise #2: due before
Week 6 Assignments: Program 2: is being graded Program 3: available soon and due before 10pm on Thursday 3/14 Homework 5: available soon and due before 10pm on Monday 3/4 X-Team Exercise #2: due before
Software 1 with Java. Recitation No. 6 (Collections)
 Software 1 with Java Recitation No. 6 (Collections) Java Collections Framework Collection: a group of elements Interface Based Design: Java Collections Framework Interfaces Implementations Algorithms 2
Software 1 with Java Recitation No. 6 (Collections) Java Collections Framework Collection: a group of elements Interface Based Design: Java Collections Framework Interfaces Implementations Algorithms 2
Final assignment: Hash map
 Final assignment: Hash map 1 Introduction In this final assignment you will implement a hash map 1. A hash map is a data structure that associates a key with a value (a chunk of data). Most hash maps are
Final assignment: Hash map 1 Introduction In this final assignment you will implement a hash map 1. A hash map is a data structure that associates a key with a value (a chunk of data). Most hash maps are
Oracle. Exam Questions 1Z Java Standard Edition 6 Programmer Certified Professional Exam. Version:Demo
 Oracle Exam Questions 1Z0-851 Java Standard Edition 6 Programmer Certified Professional Exam Version:Demo 1. Given a pre-generics implementation of a method: 11. public static int sum(list list) { 12.
Oracle Exam Questions 1Z0-851 Java Standard Edition 6 Programmer Certified Professional Exam Version:Demo 1. Given a pre-generics implementation of a method: 11. public static int sum(list list) { 12.
Instance Members and Static Members
 Instance Members and Static Members You may notice that all the members are declared w/o static. These members belong to some specific object. They are called instance members. This implies that these
Instance Members and Static Members You may notice that all the members are declared w/o static. These members belong to some specific object. They are called instance members. This implies that these
CS 101 Spring 2007 Midterm 2 Name: ID:
 You only need to write your name and e-mail ID on the first page. This exam is CLOSED text book, closed-notes, closed-calculator, closed-neighbor, etc. Questions are worth different amounts, so be sure
You only need to write your name and e-mail ID on the first page. This exam is CLOSED text book, closed-notes, closed-calculator, closed-neighbor, etc. Questions are worth different amounts, so be sure
CS 307 Final Spring 2010
 Points off 1 2 3 4 5 Total off Net Score CS 307 Final Spring 2010 Name UTEID login name Instructions: 1. Please turn off your cell phones. 2. There are 5 questions on this test. 3. You have 3 hours to
Points off 1 2 3 4 5 Total off Net Score CS 307 Final Spring 2010 Name UTEID login name Instructions: 1. Please turn off your cell phones. 2. There are 5 questions on this test. 3. You have 3 hours to
Overview of Java ArrayList, HashTable, HashMap, Hashet,LinkedList
 Overview of Java ArrayList, HashTable, HashMap, Hashet,LinkedList This article discusses the main classes of Java Collection API. The following figure demonstrates the Java Collection framework. Figure
Overview of Java ArrayList, HashTable, HashMap, Hashet,LinkedList This article discusses the main classes of Java Collection API. The following figure demonstrates the Java Collection framework. Figure
Since it is an interface, we need a concrete class during its declaration. There are many ways to initialize a Queue object, most common being-
 Laboratory 2 Data Structures-II Implementation of Daa structures using Collection frame work Obecjective Data Structures. A data structure is a particular way of storing and organizing data in a computer
Laboratory 2 Data Structures-II Implementation of Daa structures using Collection frame work Obecjective Data Structures. A data structure is a particular way of storing and organizing data in a computer
Hash Tables. Computer Science S-111 Harvard University David G. Sullivan, Ph.D. Data Dictionary Revisited
 Unit 9, Part 4 Hash Tables Computer Science S-111 Harvard University David G. Sullivan, Ph.D. Data Dictionary Revisited We've considered several data structures that allow us to store and search for data
Unit 9, Part 4 Hash Tables Computer Science S-111 Harvard University David G. Sullivan, Ph.D. Data Dictionary Revisited We've considered several data structures that allow us to store and search for data
University of Maryland College Park Dept of Computer Science
 University of Maryland College Park Dept of Computer Science CMSC132H Fall 2009 Midterm First Name (PRINT): Last Name (PRINT): University ID: I pledge on my honor that I have not given or received any
University of Maryland College Park Dept of Computer Science CMSC132H Fall 2009 Midterm First Name (PRINT): Last Name (PRINT): University ID: I pledge on my honor that I have not given or received any
Midterm Exam CS 251, Intermediate Programming March 6, 2015
 Midterm Exam CS 251, Intermediate Programming March 6, 2015 Name: NetID: Answer all questions in the space provided. Write clearly and legibly, you will not get credit for illegible or incomprehensible
Midterm Exam CS 251, Intermediate Programming March 6, 2015 Name: NetID: Answer all questions in the space provided. Write clearly and legibly, you will not get credit for illegible or incomprehensible
Building Java Programs
 Building Java Programs Generics, hashing reading: 18.1 2 3 Wednesday Notecards Difference between int[] and List? How does HashSet get sorted? 4 Hashing hash: To map a value to an integer index.
Building Java Programs Generics, hashing reading: 18.1 2 3 Wednesday Notecards Difference between int[] and List? How does HashSet get sorted? 4 Hashing hash: To map a value to an integer index.
Hash tables. hashing -- idea collision resolution. hash function Java hashcode() for HashMap and HashSet big-o time bounds applications
 hashing -- idea collision resolution Hash tables closed addressing (chaining) open addressing techniques hash function Java hashcode() for HashMap and HashSet big-o time bounds applications Hash tables
hashing -- idea collision resolution Hash tables closed addressing (chaining) open addressing techniques hash function Java hashcode() for HashMap and HashSet big-o time bounds applications Hash tables
C/C++ Programming Lecture 18 Name:
 . The following is the textbook's code for a linear search on an unsorted array. //***************************************************************** // The searchlist function performs a linear search
. The following is the textbook's code for a linear search on an unsorted array. //***************************************************************** // The searchlist function performs a linear search
CMP 326 Midterm Fall 2015
 CMP 326 Midterm Fall 2015 Name: 1) (30 points; 5 points each) Write the output of each piece of code. If the code gives an error, write any output that would happen before the error, and then write ERROR.
CMP 326 Midterm Fall 2015 Name: 1) (30 points; 5 points each) Write the output of each piece of code. If the code gives an error, write any output that would happen before the error, and then write ERROR.
Abstract data types (again) Announcements. Example ADT an integer bag (next) The Java Collections Framework
 Announcements Abstract data types (again) PS 5 ready Tutoring schedule updated with more hours Today s topic: The Java Collections Framework Reading: Section 7.5 An ADT is a model of a collection of data
Announcements Abstract data types (again) PS 5 ready Tutoring schedule updated with more hours Today s topic: The Java Collections Framework Reading: Section 7.5 An ADT is a model of a collection of data
More on methods and variables. Fundamentals of Computer Science Keith Vertanen
 More on methods and variables Fundamentals of Computer Science Keith Vertanen Terminology of a method Goal: helper method than can draw a random integer between start and end (inclusive) access modifier
More on methods and variables Fundamentals of Computer Science Keith Vertanen Terminology of a method Goal: helper method than can draw a random integer between start and end (inclusive) access modifier
HASH TABLES cs2420 Introduction to Algorithms and Data Structures Spring 2015
 HASH TABLES cs2420 Introduction to Algorithms and Data Structures Spring 2015 1 administrivia 2 -assignment 9 is due on Monday -assignment 10 will go out on Thursday -midterm on Thursday 3 last time 4
HASH TABLES cs2420 Introduction to Algorithms and Data Structures Spring 2015 1 administrivia 2 -assignment 9 is due on Monday -assignment 10 will go out on Thursday -midterm on Thursday 3 last time 4
HASH TABLES. Hash Tables Page 1
 HASH TABLES TABLE OF CONTENTS 1. Introduction to Hashing 2. Java Implementation of Linear Probing 3. Maurer s Quadratic Probing 4. Double Hashing 5. Separate Chaining 6. Hash Functions 7. Alphanumeric
HASH TABLES TABLE OF CONTENTS 1. Introduction to Hashing 2. Java Implementation of Linear Probing 3. Maurer s Quadratic Probing 4. Double Hashing 5. Separate Chaining 6. Hash Functions 7. Alphanumeric
Basic computer skills such as using Windows, Internet Explorer, and Microsoft Word. Chapter 1 Introduction to Computers, Programs, and Java
 Basic computer skills such as using Windows, Internet Explorer, and Microsoft Word Chapter 1 Introduction to Computers, Programs, and Java Chapter 2 Primitive Data Types and Operations Chapter 3 Selection
Basic computer skills such as using Windows, Internet Explorer, and Microsoft Word Chapter 1 Introduction to Computers, Programs, and Java Chapter 2 Primitive Data Types and Operations Chapter 3 Selection
27/04/2012. Objectives. Collection. Collections Framework. "Collection" Interface. Collection algorithm. Legacy collection
 Objectives Collection Collections Framework Concrete collections Collection algorithm By Võ Văn Hải Faculty of Information Technologies Summer 2012 Legacy collection 1 2 2/27 Collections Framework "Collection"
Objectives Collection Collections Framework Concrete collections Collection algorithm By Võ Văn Hải Faculty of Information Technologies Summer 2012 Legacy collection 1 2 2/27 Collections Framework "Collection"
Cuckoo Hashing for Undergraduates
 Cuckoo Hashing for Undergraduates Rasmus Pagh IT University of Copenhagen March 27, 2006 Abstract This lecture note presents and analyses two simple hashing algorithms: Hashing with Chaining, and Cuckoo
Cuckoo Hashing for Undergraduates Rasmus Pagh IT University of Copenhagen March 27, 2006 Abstract This lecture note presents and analyses two simple hashing algorithms: Hashing with Chaining, and Cuckoo
CMPS 12A - Winter 2002 Midterm 2 March 5, Name: ID:
 CMPS 12A - Winter 2002 Midterm 2 March 5, 2002 Name: ID: This is a closed note, closed book exam. Any place where you are asked to write code, you must declare all variables that you use. However, I just
CMPS 12A - Winter 2002 Midterm 2 March 5, 2002 Name: ID: This is a closed note, closed book exam. Any place where you are asked to write code, you must declare all variables that you use. However, I just
CIS 1068 Program Design and Abstraction Spring2016 Midterm Exam 1. Name SOLUTION
 CIS 1068 Program Design and Abstraction Spring2016 Midterm Exam 1 Name SOLUTION Page Points Score 2 15 3 8 4 18 5 10 6 7 7 7 8 14 9 11 10 10 Total 100 1 P age 1. Program Traces (41 points, 50 minutes)
CIS 1068 Program Design and Abstraction Spring2016 Midterm Exam 1 Name SOLUTION Page Points Score 2 15 3 8 4 18 5 10 6 7 7 7 8 14 9 11 10 10 Total 100 1 P age 1. Program Traces (41 points, 50 minutes)
NAME: c. (true or false) The median is always stored at the root of a binary search tree.
 EE 322C Spring 2009 (Chase) Exam 2: READ THIS FIRST. Please use the back side of each page for scratch paper. For some of the questions you may need to think quite a bit before you write down an answer.
EE 322C Spring 2009 (Chase) Exam 2: READ THIS FIRST. Please use the back side of each page for scratch paper. For some of the questions you may need to think quite a bit before you write down an answer.
Hashing. Reading: L&C 17.1, 17.3 Eck Programming Course CL I
 Hashing Reading: L&C 17.1, 17.3 Eck 10.3 Defne hashing Objectives Discuss the problem of collisions in hash tables Examine Java's HashMap implementation of hashing Look at HashMap example Save serializable
Hashing Reading: L&C 17.1, 17.3 Eck 10.3 Defne hashing Objectives Discuss the problem of collisions in hash tables Examine Java's HashMap implementation of hashing Look at HashMap example Save serializable
CSIS 10B Assignment 15 Maps and Hashing Due: next Wed
 CSIS 10B Assignment 15 Maps and Hashing Due: next Wed In class Demos (0 points) We develop a SimpleHashMap class: 1) built from an Array of Associations 2) experiment with different hash methods 3) put,
CSIS 10B Assignment 15 Maps and Hashing Due: next Wed In class Demos (0 points) We develop a SimpleHashMap class: 1) built from an Array of Associations 2) experiment with different hash methods 3) put,
CS 231 Data Structures and Algorithms Fall Binary Search Trees Lecture 23 October 29, Prof. Zadia Codabux
 CS 231 Data Structures and Algorithms Fall 2018 Binary Search Trees Lecture 23 October 29, 2018 Prof. Zadia Codabux 1 Agenda Ternary Operator Binary Search Tree Node based implementation Complexity 2 Administrative
CS 231 Data Structures and Algorithms Fall 2018 Binary Search Trees Lecture 23 October 29, 2018 Prof. Zadia Codabux 1 Agenda Ternary Operator Binary Search Tree Node based implementation Complexity 2 Administrative
COS 126 General Computer Science Spring Written Exam 1
 COS 126 General Computer Science Spring 2017 Written Exam 1 This exam has 9 questions (including question 0) worth a total of 70 points. You have 50 minutes. Write all answers inside the designated spaces.
COS 126 General Computer Science Spring 2017 Written Exam 1 This exam has 9 questions (including question 0) worth a total of 70 points. You have 50 minutes. Write all answers inside the designated spaces.
תוכנה 1 מבני נתונים גנריים
 תוכנה 1 מבני נתונים גנריים תרגול 8 Java Collections Framework Collection: a group of elements Interface Based Design: Java Collections Framework Interfaces Implementations Algorithms 2 Online Resources
תוכנה 1 מבני נתונים גנריים תרגול 8 Java Collections Framework Collection: a group of elements Interface Based Design: Java Collections Framework Interfaces Implementations Algorithms 2 Online Resources
Introducing Hashing. Chapter 21. Copyright 2012 by Pearson Education, Inc. All rights reserved
 Introducing Hashing Chapter 21 Contents What Is Hashing? Hash Functions Computing Hash Codes Compressing a Hash Code into an Index for the Hash Table A demo of hashing (after) ARRAY insert hash index =
Introducing Hashing Chapter 21 Contents What Is Hashing? Hash Functions Computing Hash Codes Compressing a Hash Code into an Index for the Hash Table A demo of hashing (after) ARRAY insert hash index =
ECE 242 Data Structures and Algorithms. Hash Tables II. Lecture 25. Prof.
 ECE 242 Data Structures and Algorithms http://www.ecs.umass.edu/~polizzi/teaching/ece242/ Hash Tables II Lecture 25 Prof. Eric Polizzi Summary previous lecture Hash Tables Motivation: optimal insertion
ECE 242 Data Structures and Algorithms http://www.ecs.umass.edu/~polizzi/teaching/ece242/ Hash Tables II Lecture 25 Prof. Eric Polizzi Summary previous lecture Hash Tables Motivation: optimal insertion
Review. Primitive Data Types & Variables. String Mathematical operators: + - * / % Comparison: < > <= >= == int, long float, double boolean char
 Review Primitive Data Types & Variables int, long float, double boolean char String Mathematical operators: + - * / % Comparison: < > = == 1 1.3 Conditionals and Loops Introduction to Programming in
Review Primitive Data Types & Variables int, long float, double boolean char String Mathematical operators: + - * / % Comparison: < > = == 1 1.3 Conditionals and Loops Introduction to Programming in
Repetition, Looping. While Loop
 Repetition, Looping Last time we looked at how to use if-then statements to control the flow of a program. In this section we will look at different ways to repeat blocks of statements. Such repetitions
Repetition, Looping Last time we looked at how to use if-then statements to control the flow of a program. In this section we will look at different ways to repeat blocks of statements. Such repetitions
CSL 201 Data Structures Mid-Semester Exam minutes
 CL 201 Data tructures Mid-emester Exam - 120 minutes Name: Roll Number: Please read the following instructions carefully This is a closed book, closed notes exam. Calculators are allowed. However laptops
CL 201 Data tructures Mid-emester Exam - 120 minutes Name: Roll Number: Please read the following instructions carefully This is a closed book, closed notes exam. Calculators are allowed. However laptops
Java Classes. Produced by. Introduction to the Java Programming Language. Eamonn de Leastar
 Java Classes Introduction to the Java Programming Language Produced by Eamonn de Leastar edeleastar@wit.ie Department of Computing, Maths & Physics Waterford Institute of Technology http://www.wit.ie http://elearning.wit.ie
Java Classes Introduction to the Java Programming Language Produced by Eamonn de Leastar edeleastar@wit.ie Department of Computing, Maths & Physics Waterford Institute of Technology http://www.wit.ie http://elearning.wit.ie
Instructions. Definitions. Name: CMSC 341 Fall Question Points I. /12 II. /30 III. /10 IV. /12 V. /12 VI. /12 VII.
 CMSC 341 Fall 2013 Data Structures Final Exam B Name: Question Points I. /12 II. /30 III. /10 IV. /12 V. /12 VI. /12 VII. /12 TOTAL: /100 Instructions 1. This is a closed-book, closed-notes exam. 2. You
CMSC 341 Fall 2013 Data Structures Final Exam B Name: Question Points I. /12 II. /30 III. /10 IV. /12 V. /12 VI. /12 VII. /12 TOTAL: /100 Instructions 1. This is a closed-book, closed-notes exam. 2. You
Java Simple Data Types
 Intro to Java Unit 1 Multiple Choice Java Simple Data Types DO NOT WRITE ON THIS TEST This test includes program segments, which are not complete programs. Answer such questions with the assumption that
Intro to Java Unit 1 Multiple Choice Java Simple Data Types DO NOT WRITE ON THIS TEST This test includes program segments, which are not complete programs. Answer such questions with the assumption that
CMSC 202H. Containers and Iterators
 CMSC 202H Containers and Iterators Container Definition A container is a data structure whose purpose is to hold objects. Most languages support several ways to hold objects Arrays are compiler-supported
CMSC 202H Containers and Iterators Container Definition A container is a data structure whose purpose is to hold objects. Most languages support several ways to hold objects Arrays are compiler-supported
Review. CSE 143 Java. A Magical Strategy. Hash Function Example. Want to implement Sets of objects Want fast contains( ), add( )
 Review CSE 143 Java Hashing Want to implement Sets of objects Want fast contains( ), add( ) One strategy: a sorted list OK contains( ): use binary search Slow add( ): have to maintain list in sorted order
Review CSE 143 Java Hashing Want to implement Sets of objects Want fast contains( ), add( ) One strategy: a sorted list OK contains( ): use binary search Slow add( ): have to maintain list in sorted order
Announcements. PS 3 is due Thursday, 10/6. Midterm Exam 1: 10/14 (Fri), 9:00am-10:53am
 Announcements PS 3 is due Thursday, 10/6 Midterm Exam 1: 10/14 (Fri), 9:00am-10:53am Room TBD Scope: Lecture 1 to Lecture 9 (Chapters 1 to 6 of text) You may bring a sheet of paper (A4, both sides) Tutoring
Announcements PS 3 is due Thursday, 10/6 Midterm Exam 1: 10/14 (Fri), 9:00am-10:53am Room TBD Scope: Lecture 1 to Lecture 9 (Chapters 1 to 6 of text) You may bring a sheet of paper (A4, both sides) Tutoring
CIS 265 Exam 2 First Name Last Name
 CIS 265 Exam 2 First Name Last Name MULTIPLE CHOICE. Choose the one alternative that best completes the statement or answers the question. 1) Which of the data types below does not allow duplicates? 1)
CIS 265 Exam 2 First Name Last Name MULTIPLE CHOICE. Choose the one alternative that best completes the statement or answers the question. 1) Which of the data types below does not allow duplicates? 1)
DM550 Introduction to Programming part 2. Jan Baumbach.
 DM550 Introduction to Programming part 2 Jan Baumbach jan.baumbach@imada.sdu.dk http://www.baumbachlab.net MULTIVARIATE TREES 2 Multivariate Trees general class of trees nodes can have any number of children
DM550 Introduction to Programming part 2 Jan Baumbach jan.baumbach@imada.sdu.dk http://www.baumbachlab.net MULTIVARIATE TREES 2 Multivariate Trees general class of trees nodes can have any number of children
CSCI 135 Exam #0 Fundamentals of Computer Science I Fall 2013
 CSCI 135 Exam #0 Fundamentals of Computer Science I Fall 2013 Name: This exam consists of 7 problems on the following 6 pages. You may use your single- side hand- written 8 ½ x 11 note sheet during the
CSCI 135 Exam #0 Fundamentals of Computer Science I Fall 2013 Name: This exam consists of 7 problems on the following 6 pages. You may use your single- side hand- written 8 ½ x 11 note sheet during the
King Saud University College of Computer and Information Sciences Computer Science Department
 King Saud University College of Computer and Information Sciences Computer Science Department Course Code: CSC 111 Course Title: Introduction to Programming Semester: Fall 2017-2018 Exercises Cover Sheet:
King Saud University College of Computer and Information Sciences Computer Science Department Course Code: CSC 111 Course Title: Introduction to Programming Semester: Fall 2017-2018 Exercises Cover Sheet:
CSE 143 Lecture 14 AnagramSolver and Hashing
 CSE 143 Lecture 14 AnagramSolver and Hashing slides created by Ethan Apter http://www.cs.washington.edu/143/ Ada Lovelace (1815-1852) Ada Lovelace is considered the first computer programmer for her work
CSE 143 Lecture 14 AnagramSolver and Hashing slides created by Ethan Apter http://www.cs.washington.edu/143/ Ada Lovelace (1815-1852) Ada Lovelace is considered the first computer programmer for her work
Topic 10: The Java Collections Framework (and Iterators)
 Topic 10: The Java Collections Framework (and Iterators) A set of interfaces and classes to help manage collections of data. Why study the Collections Framework? very useful in many different kinds of
Topic 10: The Java Collections Framework (and Iterators) A set of interfaces and classes to help manage collections of data. Why study the Collections Framework? very useful in many different kinds of
Java Simple Data Types
 Intro to Java Unit 1 Multiple Choice Test Key Java Simple Data Types This Test Is a KEY DO NOT WRITE ON THIS TEST This test includes program segments, which are not complete programs. Answer such questions
Intro to Java Unit 1 Multiple Choice Test Key Java Simple Data Types This Test Is a KEY DO NOT WRITE ON THIS TEST This test includes program segments, which are not complete programs. Answer such questions
Recitation 9. Prelim Review
 Recitation 9 Prelim Review 1 Heaps 2 Review: Binary heap min heap 1 2 99 4 3 PriorityQueue Maintains max or min of collection (no duplicates) Follows heap order invariant at every level Always balanced!
Recitation 9 Prelim Review 1 Heaps 2 Review: Binary heap min heap 1 2 99 4 3 PriorityQueue Maintains max or min of collection (no duplicates) Follows heap order invariant at every level Always balanced!
CSE115 / CSE503 Introduction to Computer Science I Dr. Carl Alphonce 343 Davis Hall Office hours:
 CSE115 / CSE503 Introduction to Computer Science I Dr. Carl Alphonce 343 Davis Hall alphonce@buffalo.edu Office hours: Tuesday 10:00 AM 12:00 PM * Wednesday 4:00 PM 5:00 PM Friday 11:00 AM 12:00 PM OR
CSE115 / CSE503 Introduction to Computer Science I Dr. Carl Alphonce 343 Davis Hall alphonce@buffalo.edu Office hours: Tuesday 10:00 AM 12:00 PM * Wednesday 4:00 PM 5:00 PM Friday 11:00 AM 12:00 PM OR
COMP-202 Unit 4: Programming With Iterations. CONTENTS: The while and for statements
 COMP-202 Unit 4: Programming With Iterations CONTENTS: The while and for statements Introduction (1) Suppose we want to write a program to be used in cash registers in stores to compute the amount of money
COMP-202 Unit 4: Programming With Iterations CONTENTS: The while and for statements Introduction (1) Suppose we want to write a program to be used in cash registers in stores to compute the amount of money
CSC 1214: Object-Oriented Programming
 CSC 1214: Object-Oriented Programming J. Kizito Makerere University e-mail: jkizito@cis.mak.ac.ug www: http://serval.ug/~jona materials: http://serval.ug/~jona/materials/csc1214 e-learning environment:
CSC 1214: Object-Oriented Programming J. Kizito Makerere University e-mail: jkizito@cis.mak.ac.ug www: http://serval.ug/~jona materials: http://serval.ug/~jona/materials/csc1214 e-learning environment:
First Name Last Name ID#
 CIS 265 Sect 01 - V. Matos Exam-2 Spring-2015 First Name Last Name ID# (15 pts) MULTIPLE CHOICE. Choose the one alternative that best completes the statement or answers the question. 1) In the following
CIS 265 Sect 01 - V. Matos Exam-2 Spring-2015 First Name Last Name ID# (15 pts) MULTIPLE CHOICE. Choose the one alternative that best completes the statement or answers the question. 1) In the following
Selenium Class 9 - Java Operators
 Selenium Class 9 - Java Operators Operators are used to perform Arithmetic, Comparison, and Logical Operations, Operators are used to perform operations on variables and values. public class JavaOperators
Selenium Class 9 - Java Operators Operators are used to perform Arithmetic, Comparison, and Logical Operations, Operators are used to perform operations on variables and values. public class JavaOperators
CSEN202: Introduction to Computer Science Spring Semester 2017 Midterm Exam
 Page 0 German University in Cairo April 6, 2017 Media Engineering and Technology Faculty Prof. Dr. Slim Abdennadher CSEN202: Introduction to Computer Science Spring Semester 2017 Midterm Exam Bar Code
Page 0 German University in Cairo April 6, 2017 Media Engineering and Technology Faculty Prof. Dr. Slim Abdennadher CSEN202: Introduction to Computer Science Spring Semester 2017 Midterm Exam Bar Code
