Exploiting Vulnerabilities in Media Software. isec Partners
|
|
|
- Martina Hall
- 5 years ago
- Views:
Transcription
1 Exploiting Vulnerabilities in Media Software
2 Agenda Introduction Why media software? Why bugs are still out there How we're going to bang them out Fuzzing techniques Why/What/How Fuzzbox Codecs to attack Ogg Vorbis MP3 FLAC Speex Raw formats: PCM/WAV, AIFF
3 Agenda Case studies: blown up software Demo Q&A
4 Introduction Hello I'm a consultant for Focus on application security UNIX grump Audio hobbyist What's this all about? The attack surface and potential of media codecs Focus here is on audio, but that doesn't matter Video works the same way, and uses the same container formats
5 Why this matters Omnipresent, and always on Promiscuously shared, played, streamed Come from extremely untrusted, often anonymous sources Who thinks to refrain from playing untrusted sounds? Most browsers will play automatically anyhow It's political There are people out there who don't like you stealing music Like me, for example But mostly I mean the RIAA, and companies like Sony Ripe for corporate abuse It's rich Media playback software is excessively functional Does tons of parsing It's underexplored!
6 Why underexplored? Modern codecs are designed to be resistant to corruption Bit-flipping an ogg file, for example, will usually not work Example: zzuf, a popular bit-flipping fuzzer, noted VLC as being robust against fuzzing of Vorbis, Theora, FLAC As zzuf notes, this does not mean there are no bugs; we just need a targeted fuzzer Most exploits thus far have been simple Attacks on players: long playlists, URL names, etc Few attacks using media files themselves Even fewer targeting things on the codec level
7 Fuzzing techniques: what to fuzz Two main areas are important here Content metadata ID3, APEv2, Vorbis comments, album art, etc. Frame data We're mostly interested in the frame header Contains structural data describing overall file layout Sample rate, number of frames, frame size, channels Can be multiple types of frame headers in a file, especially in the case of container formats
8 Fuzzing techniques: what to fuzz with Obviously, random strings Repeating one random ASCII char to help us spot stack pointer overwrites Throw in some random unicode, encoded in funny ways Format strings Just a bunch of %ns to give us some memory corruption Random signed ints Fencepost numbers HTML! More on this later. URLs maybe we can catch some URL pingbacks
9 Fuzzing techniques: how to fuzz it Three possible approaches Reach in and just mutate Might work, might not Works a sad amount of the time Use existing parsing libraries Works well, but usually requires patching the libs Built-in error handling will obviously trip us up Metadata editing libraries don't always allow changing of data we want Let's use this for basic stuff like ID3 tags and Vorbis comments Make your own frame parser Sometimes quick and easy, sometimes painful But turns up some great bugs
10 The toolbox A few tools to make fuzzing and parsing easier: Hachoir Dissects many file types visually mutagen Help in mangling audio tags and understanding file layout vbindiff shows differences between fuzzed and non-fuzzed files bvi a hex editor with keybindings similar to a certain one true editor gdb
11 Fuzzbox A multi-codec audio stream fuzzer, written in Python Targets specific codecs, no general file fuzzing Uses third party libs like py-vorbis and mutagen for metadata fuzzing Uses built-in frame parsing for frame fuzzing NOT another fuzzing framework An example of real-world fuzzers used in pen-testing: quick, dirty and targeted
12 Ogg Frame Structure Case study: Ogg Vorbis Excellent free codec Well documented Not just for hippies Unencumbered status gets it into many things Consists of an Ogg container: Byte capture_pattern: Magic number for page start "OggS" version header_type granule_position bitstream_serial_number page_sequence_number CRC_checksum page_segments segment_table
13 Vorbis Frame Structure...with a chewy Vorbis center Contains channels, sample rate, etc Also Vorbis comments Simple name/value pairs can be any length or content, but some have special meaning Easiest to use existing libs for this in this case, py-vorbis
14 Ogg and Vorbis frame in Python Mercifully 8-bit aligned
15 Data loaded, feed to fuzzer Now we have comments and frame data Time to mangle them up Transforms are defined in randjunk.py:
16 Data fuzzed, writing back out In the case of comments, we just write them back in For our frame data, we need to pack it:
17 Fix the CRC Every ogg frame has a CRC to prevent corruption Also hides bugs :( But, easy enough to fix
18 Other supported formats MP3 Metadata with ID3 ID3v1 Length limited Stored at end of file Great for rewriting, awful for streaming ID3v2 Massively structured and complex Incompletely supported I hope it dies FLAC Lossless audio uses Vorbis comments for metadata, can use Ogg as a container
19 Even more supported formats WAV and AIFF What's to attack in raw audio? Not much, but it still works Sample width, framerate, frame number; all things that can expose integer bugs WAV and AIFF parsing libraries are included with Python Speex Optimized for speech Used in several high-profile third-party products Uses vorbis comments for metadata Can be stored in an Ogg container
20 Setting up a fuzzer run Basic usage of fuzzbox
21 Demo
22 Nifty features Autoplay mode kicks off a player of your choice under gdb Gathers backtraces, registers and resource usage itunes anti-anti-debugging itunes automation with AppleScript Kills off runaway apps
23 Fallout: VLC Format string issues in Vorbis comments Also CDDA, SAP/SDP broadcast exploitation!
24 Fallout: libvorbis
25 Fallout: flac-tools Stack overflow in metadata parsing
26 Demo
27
28 Collateral Damage Non-player apps, or nobody uses Vorbis! As mentioned before, some of these codecs get around Used in games custom sounds downloaded with maps... Asterisk does. (O_o);;; It also supports Speex, which is structurally very similar... In other words, any DoS or code execution in Ogg/Vorbis means the same for Asterisk Web applications Some apps aren't real careful about data parsed from media Cool for CSRF, XSS or Javascript intranet scanning Indexing services and other parsers Software like Beagle relies on media libraries to index Exploits in these libraries affect the indexer Can also be a venue for finding bugs in the indexer itself Or its web interface
29 phpmp
30 Questions? Thanks for coming! Thanks to: Chris Palmer, Jesse Burns, Tim Newsham Q&A
Exposing Vulnerabilities in Media Software
 Tools Exposing Vulnerabilities in Media Software David Thiel, isec Partners March 31st, 2008 Agenda 1 Tools 2 3 Tools 4 5 6 Tools Hello I m a consultant and researcher with isec Partners Focus on application
Tools Exposing Vulnerabilities in Media Software David Thiel, isec Partners March 31st, 2008 Agenda 1 Tools 2 3 Tools 4 5 6 Tools Hello I m a consultant and researcher with isec Partners Focus on application
Exposing Vulnerabilities in Media Software
 Exposing Vulnerabilities in Media Software David Thiel, isec Partners BlackHat USA, August 2, 2007 Abstract Deep media codec fuzzing presents a rich opportunity for turning up hard to find bugs in media
Exposing Vulnerabilities in Media Software David Thiel, isec Partners BlackHat USA, August 2, 2007 Abstract Deep media codec fuzzing presents a rich opportunity for turning up hard to find bugs in media
IDM 221. Web Design I. IDM 221: Web Authoring I 1
 IDM 221 Web Design I IDM 221: Web Authoring I 1 Week 8 IDM 221: Web Authoring I 2 Media on the Web IDM 221: Web Authoring I 3 Before we cover how to include media files in a web page, you need to be familiar
IDM 221 Web Design I IDM 221: Web Authoring I 1 Week 8 IDM 221: Web Authoring I 2 Media on the Web IDM 221: Web Authoring I 3 Before we cover how to include media files in a web page, you need to be familiar
HTML 5 and CSS 3, Illustrated Complete. Unit K: Incorporating Video and Audio
 HTML 5 and CSS 3, Illustrated Complete Unit K: Incorporating Video and Audio Objectives Understand Web video and audio Use the video element Incorporate the source element Control playback HTML 5 and CSS
HTML 5 and CSS 3, Illustrated Complete Unit K: Incorporating Video and Audio Objectives Understand Web video and audio Use the video element Incorporate the source element Control playback HTML 5 and CSS
Digital Audio Basics
 CSC 170 Introduction to Computers and Their Applications Lecture #2 Digital Audio Basics Digital Audio Basics Digital audio is music, speech, and other sounds represented in binary format for use in digital
CSC 170 Introduction to Computers and Their Applications Lecture #2 Digital Audio Basics Digital Audio Basics Digital audio is music, speech, and other sounds represented in binary format for use in digital
Top 5 Best itunes Alternatives for Playing Music on Mac Posted by Nick Orin on June 28, :34:12 PM.
 Top 5 Best itunes Alternatives for Playing Music on Mac Posted by Nick Orin on June 28, 2017 01:34:12 PM. itunes is the largest music store in the world since February 2010, you can find almost any music
Top 5 Best itunes Alternatives for Playing Music on Mac Posted by Nick Orin on June 28, 2017 01:34:12 PM. itunes is the largest music store in the world since February 2010, you can find almost any music
Black Hat Webcast Series. C/C++ AppSec in 2014
 Black Hat Webcast Series C/C++ AppSec in 2014 Who Am I Chris Rohlf Leaf SR (Security Research) - Founder / Consultant BlackHat Speaker { 2009, 2011, 2012 } BlackHat Review Board Member http://leafsr.com
Black Hat Webcast Series C/C++ AppSec in 2014 Who Am I Chris Rohlf Leaf SR (Security Research) - Founder / Consultant BlackHat Speaker { 2009, 2011, 2012 } BlackHat Review Board Member http://leafsr.com
It was a dark and stormy night. Seriously. There was a rain storm in Wisconsin, and the line noise dialing into the Unix machines was bad enough to
 1 2 It was a dark and stormy night. Seriously. There was a rain storm in Wisconsin, and the line noise dialing into the Unix machines was bad enough to keep putting garbage characters into the command
1 2 It was a dark and stormy night. Seriously. There was a rain storm in Wisconsin, and the line noise dialing into the Unix machines was bad enough to keep putting garbage characters into the command
BRIO by OraStream. Product Brief
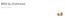 BRIO by OraStream Product Brief System Architecture BRIO Storage BRIO Server Remote Client Download Input* App Logic BRIO Control Process adaptive streaming BRIO Client Upload Output* Audio Out BRIO By
BRIO by OraStream Product Brief System Architecture BRIO Storage BRIO Server Remote Client Download Input* App Logic BRIO Control Process adaptive streaming BRIO Client Upload Output* Audio Out BRIO By
Application Layer Attacks. Application Layer Attacks. Application Layer. Application Layer. Internet Protocols. Application Layer.
 Application Layer Attacks Application Layer Attacks Week 2 Part 2 Attacks Against Programs Application Layer Application Layer Attacks come in many forms and can target each of the 5 network protocol layers
Application Layer Attacks Application Layer Attacks Week 2 Part 2 Attacks Against Programs Application Layer Application Layer Attacks come in many forms and can target each of the 5 network protocol layers
Finding media bugs in Android using file format fuzzing. Costel Maxim Intel OTC Security
 Finding media bugs in Android using file format fuzzing Costel Maxim Intel OTC Security 1 Agenda File format fuzzing Generate high-quality corpus of files Fuzzing the Stagefright Framework Logging & Triage
Finding media bugs in Android using file format fuzzing Costel Maxim Intel OTC Security 1 Agenda File format fuzzing Generate high-quality corpus of files Fuzzing the Stagefright Framework Logging & Triage
CS 161 Computer Security
 Popa & Wagner Spring 2016 CS 161 Computer Security Homework 2 Due: Monday, February 22nd, at 11:59pm Instructions. This homework is due Monday, February 22nd, at 11:59pm. It must be submitted electronically
Popa & Wagner Spring 2016 CS 161 Computer Security Homework 2 Due: Monday, February 22nd, at 11:59pm Instructions. This homework is due Monday, February 22nd, at 11:59pm. It must be submitted electronically
CITS3403 Agile Web Development Semester 1, 2016
 6 Video, Audio and Canvas CITS3403 Agile Web Development Semester 1, 2016 The audio Element Prior to HTML5, a plug- in was required to play sound while a document was being displayed Audio encoding algorithms
6 Video, Audio and Canvas CITS3403 Agile Web Development Semester 1, 2016 The audio Element Prior to HTML5, a plug- in was required to play sound while a document was being displayed Audio encoding algorithms
Biting the Hand that Feeds You
 Biting the Hand that Feeds You Storing and Serving Malicious Content from Popular Web Servers Billy K Rios (BK) and Nate McFeters Agenda Domain Names and Trust Who do you Trust? Biting the Hand - Yahoo
Biting the Hand that Feeds You Storing and Serving Malicious Content from Popular Web Servers Billy K Rios (BK) and Nate McFeters Agenda Domain Names and Trust Who do you Trust? Biting the Hand - Yahoo
Abusing Windows Opener to Bypass CSRF Protection (Never Relay On Client Side)
 Abusing Windows Opener to Bypass CSRF Protection (Never Relay On Client Side) Narendra Bhati @NarendraBhatiB http://websecgeeks.com Abusing Windows Opener To Bypass CSRF Protection Narendra Bhati Page
Abusing Windows Opener to Bypass CSRF Protection (Never Relay On Client Side) Narendra Bhati @NarendraBhatiB http://websecgeeks.com Abusing Windows Opener To Bypass CSRF Protection Narendra Bhati Page
How the Leopard hides his Spots. OS X Anti-Forensics
 How the Leopard hides his Spots OS X Anti-Forensics the.grugq@gmail.com Introduction Strategies Tactics Conclusion Overview Introduction the grugq Independent security researcher
How the Leopard hides his Spots OS X Anti-Forensics the.grugq@gmail.com Introduction Strategies Tactics Conclusion Overview Introduction the grugq Independent security researcher
I. CREATING YOUR SOUNDCLOUD ACCOUNT
 A Tutorial for creating and posting audio recordings with SoundCloud, http://soundcloud.com Table of Contents 1. Creating Your Account: Features and steps (p. 1) 2. Recording You First Audio (p. 2) 3.
A Tutorial for creating and posting audio recordings with SoundCloud, http://soundcloud.com Table of Contents 1. Creating Your Account: Features and steps (p. 1) 2. Recording You First Audio (p. 2) 3.
CS 161 Computer Security
 Paxson Spring 2017 CS 161 Computer Security Discussion 4 Week of February 13, 2017 Question 1 Clickjacking (5 min) Watch the following video: https://www.youtube.com/watch?v=sw8ch-m3n8m Question 2 Session
Paxson Spring 2017 CS 161 Computer Security Discussion 4 Week of February 13, 2017 Question 1 Clickjacking (5 min) Watch the following video: https://www.youtube.com/watch?v=sw8ch-m3n8m Question 2 Session
& Windows XP. ESC 12/Podcasting Workshop Handout/June 2009/Exec Svcs Tech/Rev 2
 & Windows XP Recording and Publishing a Podcast with Audacity 1.2.6 Page 1 Recording and Publishing a Podcast with Audacity Written by Jake Ludington' (With minor modifications added by Lisa McCray) http://www.jakeludington.com/podcasting/20050222_recording_a_podcast.html
& Windows XP Recording and Publishing a Podcast with Audacity 1.2.6 Page 1 Recording and Publishing a Podcast with Audacity Written by Jake Ludington' (With minor modifications added by Lisa McCray) http://www.jakeludington.com/podcasting/20050222_recording_a_podcast.html
Interactive feature: HTML5 video for
 Interactive feature: HTML5 video for email 2 HTML5 video for email Feature background Why use it? When to use it (determining usage suitability)? Which email reading environments support this? Notes for
Interactive feature: HTML5 video for email 2 HTML5 video for email Feature background Why use it? When to use it (determining usage suitability)? Which email reading environments support this? Notes for
Media player for windows 10 free download
 Media player for windows 10 free download Update to the latest version of Internet Explorer. You need to update your browser to use the site. PROS: High-quality playback, Wide range of formats, Fast and
Media player for windows 10 free download Update to the latest version of Internet Explorer. You need to update your browser to use the site. PROS: High-quality playback, Wide range of formats, Fast and
UNDERSTANDING MUSIC & VIDEO FORMATS
 ComputerFixed.co.uk Page: 1 Email: info@computerfixed.co.uk UNDERSTANDING MUSIC & VIDEO FORMATS Are you confused with all the different music and video formats available? Do you know the difference between
ComputerFixed.co.uk Page: 1 Email: info@computerfixed.co.uk UNDERSTANDING MUSIC & VIDEO FORMATS Are you confused with all the different music and video formats available? Do you know the difference between
CS 161 Computer Security
 Raluca Ada Popa Spring 2018 CS 161 Computer Security Discussion 9 Week of March 19, 2018 Question 1 Warmup: SOP (15 min) The Same Origin Policy (SOP) helps browsers maintain a sandboxed model by preventing
Raluca Ada Popa Spring 2018 CS 161 Computer Security Discussion 9 Week of March 19, 2018 Question 1 Warmup: SOP (15 min) The Same Origin Policy (SOP) helps browsers maintain a sandboxed model by preventing
Insider Tips for using Music Station & Qmusic
 Insider Tips for using Music Station & Qmusic I am a music enthusiast, and I... have a huge amount of digital music, including high resolution FLAC files. I hope there could be a huge storage to keep files
Insider Tips for using Music Station & Qmusic I am a music enthusiast, and I... have a huge amount of digital music, including high resolution FLAC files. I hope there could be a huge storage to keep files
Lecture 19 Media Formats
 Revision IMS2603 Information Management in Organisations Lecture 19 Media Formats Last week s lectures looked at MARC as a specific instance of complex metadata representation and at Content Management
Revision IMS2603 Information Management in Organisations Lecture 19 Media Formats Last week s lectures looked at MARC as a specific instance of complex metadata representation and at Content Management
HTML5 HTML & Fut ure o Web M edi dia Streami a est Work h op, ov 2010 Michael Dale Zohar Babin eve oper o Dev R l e t a i tions & C
 HTML5 &F Future of fweb bmedia Streaming Media West Workshop, Nov. 2010 Michael Dale Zohar Babin Senior Developer Head of Dev Relations & Community michael.dale@kaltura.com zohar.babin@kaltura.com @michael_dale
HTML5 &F Future of fweb bmedia Streaming Media West Workshop, Nov. 2010 Michael Dale Zohar Babin Senior Developer Head of Dev Relations & Community michael.dale@kaltura.com zohar.babin@kaltura.com @michael_dale
How To Manually Change Album Artwork On
 How To Manually Change Album Artwork On Windows Media Player Sep 14, 2014. Windows 8.1 Media Player 12.0 - Unable to Change Album Art If you've manually edited the media information for that album in your
How To Manually Change Album Artwork On Windows Media Player Sep 14, 2014. Windows 8.1 Media Player 12.0 - Unable to Change Album Art If you've manually edited the media information for that album in your
Compressed Audio Demystified by Hendrik Gideonse and Connor Smith. All Rights Reserved.
 Compressed Audio Demystified Why Music Producers Need to Care About Compressed Audio Files Download Sales Up CD Sales Down High-Definition hasn t caught on yet Consumers don t seem to care about high fidelity
Compressed Audio Demystified Why Music Producers Need to Care About Compressed Audio Files Download Sales Up CD Sales Down High-Definition hasn t caught on yet Consumers don t seem to care about high fidelity
Fuzzing. compass-security.com 1
 Fuzzing compass-security.com 1 Fuzzing Finding bugs by bombarding target with nonconform data Think: Flip a few bits in a PDF, then start Acrobat with that PDF Just more automated Steps: Create input corpus
Fuzzing compass-security.com 1 Fuzzing Finding bugs by bombarding target with nonconform data Think: Flip a few bits in a PDF, then start Acrobat with that PDF Just more automated Steps: Create input corpus
HTML5: MULTIMEDIA. Multimedia. Multimedia Formats. Common Video Formats
 LEC. 5 College of Information Technology / Department of Information Networks.... Web Page Design/ Second Class / Second Semester HTML5: MULTIMEDIA Multimedia Multimedia comes in many different formats.
LEC. 5 College of Information Technology / Department of Information Networks.... Web Page Design/ Second Class / Second Semester HTML5: MULTIMEDIA Multimedia Multimedia comes in many different formats.
Windows Media Player Manual Update Vista Full Version
 Windows Media Player Manual Update Vista Full Version How to Manually Check for Updates in Windows Media Player Information Windows Media Player (WMP) is updated from time to Click image for larger version.
Windows Media Player Manual Update Vista Full Version How to Manually Check for Updates in Windows Media Player Information Windows Media Player (WMP) is updated from time to Click image for larger version.
SoundBridge Helpful Tips. For customers who want to use Roku SoundBridge with the SlimServer music server
 SoundBridge Helpful Tips For customers who want to use Roku SoundBridge with the SlimServer music server Revision 1.2 October 25, 2004 1 I. Setting Up Your SlimServer-based Network Choosing Your Software
SoundBridge Helpful Tips For customers who want to use Roku SoundBridge with the SlimServer music server Revision 1.2 October 25, 2004 1 I. Setting Up Your SlimServer-based Network Choosing Your Software
Flash, Video. How to add Flash movies into your site How to add video and audio to your site HTML5 <video> and <audio> elements
 9 Flash, Video & Audio XX XX X X How to add Flash movies into your site How to add video and audio to your site HTML5 and elements Flash is a very popular technology used to add animations,
9 Flash, Video & Audio XX XX X X How to add Flash movies into your site How to add video and audio to your site HTML5 and elements Flash is a very popular technology used to add animations,
Multi-Room Music Servers
 CT-1: 1 Stream Server CT-8: 8 Stream Server CT-2: 2 Stream Server CT-12: 12 Stream Server CT-16: 16 Stream Server CT-3: 3 Stream Server CT-20: 20 Stream Server CT-4+: 5 Stream Server CT-24: 24 Stream Server
CT-1: 1 Stream Server CT-8: 8 Stream Server CT-2: 2 Stream Server CT-12: 12 Stream Server CT-16: 16 Stream Server CT-3: 3 Stream Server CT-20: 20 Stream Server CT-4+: 5 Stream Server CT-24: 24 Stream Server
Fuzzing Clang to find ABI Bugs. David Majnemer
 Fuzzing Clang to find ABI Bugs David Majnemer What s in an ABI? The size, alignment, etc. of types Layout of records, RTTI, virtual tables, etc. The decoration of types, functions, etc. To generalize:
Fuzzing Clang to find ABI Bugs David Majnemer What s in an ABI? The size, alignment, etc. of types Layout of records, RTTI, virtual tables, etc. The decoration of types, functions, etc. To generalize:
2.1 Transcoding audio files
 2.1 Transcoding audio files 2.1.1 Introduction to Transcoding One of the basic tasks you can perform on an audio track is to convert it into another format. This process known as Transcoding, is the direct
2.1 Transcoding audio files 2.1.1 Introduction to Transcoding One of the basic tasks you can perform on an audio track is to convert it into another format. This process known as Transcoding, is the direct
Example 1: Denary = 1. Answer: Binary = (1 * 1) = 1. Example 2: Denary = 3. Answer: Binary = (1 * 1) + (2 * 1) = 3
 1.1.1 Binary systems In mathematics and digital electronics, a binary number is a number expressed in the binary numeral system, or base-2 numeral system, which represents numeric values using two different
1.1.1 Binary systems In mathematics and digital electronics, a binary number is a number expressed in the binary numeral system, or base-2 numeral system, which represents numeric values using two different
A Heap of Trouble Exploiting the Linux Kernel SLOB Allocator
 A Heap of Trouble Exploiting the Linux Kernel SLOB Allocator Dan Rosenberg 1 Who am I? Security consultant and vulnerability researcher at VSR in Boston App/net pentesting, code review, etc. Published
A Heap of Trouble Exploiting the Linux Kernel SLOB Allocator Dan Rosenberg 1 Who am I? Security consultant and vulnerability researcher at VSR in Boston App/net pentesting, code review, etc. Published
ExeFilter. An open-source framework for active content filtering. CanSecWest /03/2008
 ExeFilter An open-source framework for active content filtering CanSecWest 2008 28/03/2008 http://cansecwest.com Philippe Lagadec NATO/NC3A philippe.lagadec(à)nc3a.nato.int ExeFilter Goals To protect sensitive
ExeFilter An open-source framework for active content filtering CanSecWest 2008 28/03/2008 http://cansecwest.com Philippe Lagadec NATO/NC3A philippe.lagadec(à)nc3a.nato.int ExeFilter Goals To protect sensitive
Adon'tbe an Adobe victim
 Adon'tbe an Adobe victim An overview of how recent Adobe-related flaws affect your web application Joshua Stabiner EY Agenda Introductions Background Cross-site scripting (PDF) Overview Exploit Mitigation
Adon'tbe an Adobe victim An overview of how recent Adobe-related flaws affect your web application Joshua Stabiner EY Agenda Introductions Background Cross-site scripting (PDF) Overview Exploit Mitigation
Various text document, image and media file formats and how to select and convert between them.
 Various text document, image and media file formats and how to select and convert between them. Plain text Rich Text Format.DOC.DOCX No fancy formatting but can be read by any computer. Use Notepad or
Various text document, image and media file formats and how to select and convert between them. Plain text Rich Text Format.DOC.DOCX No fancy formatting but can be read by any computer. Use Notepad or
NET 311 INFORMATION SECURITY
 NET 311 INFORMATION SECURITY Networks and Communication Department Lec12: Software Security / Vulnerabilities lecture contents: o Vulnerabilities in programs Buffer Overflow Cross-site Scripting (XSS)
NET 311 INFORMATION SECURITY Networks and Communication Department Lec12: Software Security / Vulnerabilities lecture contents: o Vulnerabilities in programs Buffer Overflow Cross-site Scripting (XSS)
CSE 451: Operating Systems Winter Processes. Gary Kimura
 CSE 451: Operating Systems Winter 2013 Processes Gary Kimura Process management This module begins a series of topics on processes, threads, and synchronization this is the most important part of the class,
CSE 451: Operating Systems Winter 2013 Processes Gary Kimura Process management This module begins a series of topics on processes, threads, and synchronization this is the most important part of the class,
Frontend guide. Everything you need to know about HTML, CSS, JavaScript and DOM. Dejan V Čančarević
 Frontend guide Everything you need to know about HTML, CSS, JavaScript and DOM Dejan V Čančarević Today frontend is treated as a separate part of Web development and therefore frontend developer jobs are
Frontend guide Everything you need to know about HTML, CSS, JavaScript and DOM Dejan V Čančarević Today frontend is treated as a separate part of Web development and therefore frontend developer jobs are
Secure Software Development: Theory and Practice
 Secure Software Development: Theory and Practice Suman Jana MW 2:40-3:55pm 415 Schapiro [SCEP] *Some slides are borrowed from Dan Boneh and John Mitchell Software Security is a major problem! Why writing
Secure Software Development: Theory and Practice Suman Jana MW 2:40-3:55pm 415 Schapiro [SCEP] *Some slides are borrowed from Dan Boneh and John Mitchell Software Security is a major problem! Why writing
Home/Network Computing
 Home/Network Computing How to avoid becoming road kill on the Internet (Information Superhighway) Home Computing not as simple as it used to be almost all computers need to have sys-admin disk drives will
Home/Network Computing How to avoid becoming road kill on the Internet (Information Superhighway) Home Computing not as simple as it used to be almost all computers need to have sys-admin disk drives will
CTF Workshop. Crim Synopsys, Inc. 1
 CTF Workshop Crim2018 31.10.2018 2018 Synopsys, Inc. 1 CTF (Capture the Flag) Capture the Flag (CTF) is a computer security competition. CTF are usually designed test and teach computer security skills.
CTF Workshop Crim2018 31.10.2018 2018 Synopsys, Inc. 1 CTF (Capture the Flag) Capture the Flag (CTF) is a computer security competition. CTF are usually designed test and teach computer security skills.
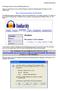 Installing Audacity Sound Editing Software Open up a web browser such as Internet Explorer and type the following Internet address in to the address field: http://audacity.sourceforge.net/download/ The
Installing Audacity Sound Editing Software Open up a web browser such as Internet Explorer and type the following Internet address in to the address field: http://audacity.sourceforge.net/download/ The
Practical Automated Web Application Attack Techniques Justin Clarke Gotham Digital Science Gotham Digital Science Ltd
 Practical Automated Web Application Attack Techniques Justin Clarke Gotham Digital Science Why this talk? The techniques are well known, but how about some way of applying ppy them? Commercial tools are
Practical Automated Web Application Attack Techniques Justin Clarke Gotham Digital Science Why this talk? The techniques are well known, but how about some way of applying ppy them? Commercial tools are
WaveSurfer at a glance
 WaveSurfer at a glance WaveSurfer has a simple but powerful interface. The basic document you work with is a sound. When WaveSurfer is first started, it contains an empty sound. You can load a sound file
WaveSurfer at a glance WaveSurfer has a simple but powerful interface. The basic document you work with is a sound. When WaveSurfer is first started, it contains an empty sound. You can load a sound file
Copyright 2015 MathEmbedded Ltd.r. Finding security vulnerabilities by fuzzing and dynamic code analysis
 Finding security vulnerabilities by fuzzing and dynamic code analysis Security Vulnerabilities Top code security vulnerabilities don t change much: Security Vulnerabilities Top code security vulnerabilities
Finding security vulnerabilities by fuzzing and dynamic code analysis Security Vulnerabilities Top code security vulnerabilities don t change much: Security Vulnerabilities Top code security vulnerabilities
HTML Forms. CITS3403 Agile Web Development. 2018, Semester 1
 HTML Forms CITS3403 Agile Web Development 2018, Semester 1 Some material Copyright 2013 Pearson Education, Inc. Publishing as Pearson Addison-Wesley. Forms A form is the usual way to get information from
HTML Forms CITS3403 Agile Web Development 2018, Semester 1 Some material Copyright 2013 Pearson Education, Inc. Publishing as Pearson Addison-Wesley. Forms A form is the usual way to get information from
FROM 4D WRITE TO 4D WRITE PRO INTRODUCTION. Presented by: Achim W. Peschke
 4 D S U M M I T 2 0 1 8 FROM 4D WRITE TO 4D WRITE PRO Presented by: Achim W. Peschke INTRODUCTION In this session we will talk to you about the new 4D Write Pro. I think in between everyone knows what
4 D S U M M I T 2 0 1 8 FROM 4D WRITE TO 4D WRITE PRO Presented by: Achim W. Peschke INTRODUCTION In this session we will talk to you about the new 4D Write Pro. I think in between everyone knows what
7.2.4 on Media content; on XSS) sws2 1
 Software and Web Security 2 Attacks on Clients (Section 7.1.3 on JavaScript; 7.2.4 on Media content; 7.2.6 on XSS) sws2 1 Last week: web server can be attacked by malicious input web browser web server
Software and Web Security 2 Attacks on Clients (Section 7.1.3 on JavaScript; 7.2.4 on Media content; 7.2.6 on XSS) sws2 1 Last week: web server can be attacked by malicious input web browser web server
Export Audio Mixdown
 26 Introduction The function in Cubase Essential allows you to mix down audio from the program to a file on your hard disk. You always mix down an output bus. For example, if you have set up a stereo mix
26 Introduction The function in Cubase Essential allows you to mix down audio from the program to a file on your hard disk. You always mix down an output bus. For example, if you have set up a stereo mix
HTML5 - INTERVIEW QUESTIONS
 HTML5 - INTERVIEW QUESTIONS http://www.tutorialspoint.com/html5/html5_interview_questions.htm Copyright tutorialspoint.com Dear readers, these HTML5 Interview Questions have been designed specially to
HTML5 - INTERVIEW QUESTIONS http://www.tutorialspoint.com/html5/html5_interview_questions.htm Copyright tutorialspoint.com Dear readers, these HTML5 Interview Questions have been designed specially to
ESOTERIC Sound Stream. User s Manual
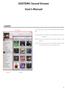 ESOTERIC Sound Stream User s Manual Layout Now Playing This is the main screen of the ESOTERIC Sound Stream app. Now Playing: Use to show the current file and control its playback. Playlist: This shows
ESOTERIC Sound Stream User s Manual Layout Now Playing This is the main screen of the ESOTERIC Sound Stream app. Now Playing: Use to show the current file and control its playback. Playlist: This shows
In-Memory Fuzzing in JAVA
 Your texte here. In-Memory Fuzzing in JAVA 2012.12.17 Xavier ROUSSEL Summary I. What is Fuzzing? Your texte here. Introduction Fuzzing process Targets Inputs vectors Data generation Target monitoring Advantages
Your texte here. In-Memory Fuzzing in JAVA 2012.12.17 Xavier ROUSSEL Summary I. What is Fuzzing? Your texte here. Introduction Fuzzing process Targets Inputs vectors Data generation Target monitoring Advantages
Elementary Computing CSC 100. M. Cheng, Computer Science
 Elementary Computing CSC 100 1 Graphics & Media Scalable Outline & Bit- mapped Fonts Binary Number Representation & Text Pixels, Colors and Resolution Sound & Digital Audio Film & Digital Video Data Compression
Elementary Computing CSC 100 1 Graphics & Media Scalable Outline & Bit- mapped Fonts Binary Number Representation & Text Pixels, Colors and Resolution Sound & Digital Audio Film & Digital Video Data Compression
BeaqleJS: HTML5 and JavaScript based Framework for the Subjective Evaluation of Audio Quality
 Professur Allgemeine Nachrichtentechnik Prof. Dr.-Ing. Udo Zölzer BeaqleJS: HTML5 and JavaScript based Framework for the Subjective Evaluation of Audio Quality Sebastian Kraft, Udo Zölzer Helmut-Schmidt-University,
Professur Allgemeine Nachrichtentechnik Prof. Dr.-Ing. Udo Zölzer BeaqleJS: HTML5 and JavaScript based Framework for the Subjective Evaluation of Audio Quality Sebastian Kraft, Udo Zölzer Helmut-Schmidt-University,
Control Flow Hijacking Attacks. Prof. Dr. Michael Backes
 Control Flow Hijacking Attacks Prof. Dr. Michael Backes Control Flow Hijacking malicious.pdf Contains bug in PDF parser Control of viewer can be hijacked Control Flow Hijacking Principles Normal Control
Control Flow Hijacking Attacks Prof. Dr. Michael Backes Control Flow Hijacking malicious.pdf Contains bug in PDF parser Control of viewer can be hijacked Control Flow Hijacking Principles Normal Control
#596*Free Download: 'Audio Editor - 3 PC / Liftetime free update' by GilISoft Internatioinal LLC. Coupon Code
 #596*Free Download: 'Audio Editor - 3 PC / Liftetime free update' by GilISoft Internatioinal LLC. Coupon Code Howdy, and you are welcome to this useful online site. On this information site you'll discover
#596*Free Download: 'Audio Editor - 3 PC / Liftetime free update' by GilISoft Internatioinal LLC. Coupon Code Howdy, and you are welcome to this useful online site. On this information site you'll discover
TotalRecorder On-line Help (Version 8.2)
 TotalRecorder On-line Help (Version 8.2) You can freely copy or print this manual I TotalRecorder On-line Help Table of Contents Part I Overview 1 Part II General Information 2 1 Total Recorder... Editions
TotalRecorder On-line Help (Version 8.2) You can freely copy or print this manual I TotalRecorder On-line Help Table of Contents Part I Overview 1 Part II General Information 2 1 Total Recorder... Editions
CS 161 Computer Security
 Wagner Spring 2014 CS 161 Computer Security Midterm 1 Print your name:, (last) (first) I am aware of the Berkeley Campus Code of Student Conduct and acknowledge that academic misconduct will be reported
Wagner Spring 2014 CS 161 Computer Security Midterm 1 Print your name:, (last) (first) I am aware of the Berkeley Campus Code of Student Conduct and acknowledge that academic misconduct will be reported
Real Player 11 Manual Windows 7 Latest Version Cnet
 Real Player 11 Manual Windows 7 Latest Version Cnet 7,576 results for "realplayer youtube downloader" Windows 7 (927) Android 2.3.3 - Android 2.3.7 (116) Windows Version 4.1.400. Added: 11/30/14. Plug-in
Real Player 11 Manual Windows 7 Latest Version Cnet 7,576 results for "realplayer youtube downloader" Windows 7 (927) Android 2.3.3 - Android 2.3.7 (116) Windows Version 4.1.400. Added: 11/30/14. Plug-in
Instant access to endless music. Liberate the music on your computer and enjoy it in every room
 In this article we are going to: Talk about what Sonos is Discuss how Sonos is controlled Explore how Sonos provides internet access to endless music Outline Internet music service providers Show what
In this article we are going to: Talk about what Sonos is Discuss how Sonos is controlled Explore how Sonos provides internet access to endless music Outline Internet music service providers Show what
convert MP4 m3u8 convert MP4 MP4 Convert MP4 MP4 MP4 M3U8 convert M3U8 MP4 mp4 MP4
 M3u8 mp4 convert May 14, 2016. The m3u8 file extension is commonly used for m3u playlists in UTF-8. M3U8 Converter app can download m3u8 to mp4 in easy step just past. Jun 7, 2017. If you're looking to
M3u8 mp4 convert May 14, 2016. The m3u8 file extension is commonly used for m3u playlists in UTF-8. M3U8 Converter app can download m3u8 to mp4 in easy step just past. Jun 7, 2017. If you're looking to
PS Audio Primer on Network Audio. February 2, 2011
 PS Audio Primer on Network Audio February 2, 2011 In 1982, Sony and Philips jointly introduced the world to digital audio through the Compact Disc, or CD. For the nearly 30 years following the introduction
PS Audio Primer on Network Audio February 2, 2011 In 1982, Sony and Philips jointly introduced the world to digital audio through the Compact Disc, or CD. For the nearly 30 years following the introduction
TotalRecorder On-line Help (Version 8.5)
 TotalRecorder On-line Help (Version 8.5) You can freely copy or print this manual I TotalRecorder On-line Help Table of Contents Part I Overview 1 Part II General Information 2 1 Total Recorder... Editions
TotalRecorder On-line Help (Version 8.5) You can freely copy or print this manual I TotalRecorder On-line Help Table of Contents Part I Overview 1 Part II General Information 2 1 Total Recorder... Editions
Fix the Missing Tags in your MP3 Files
 Fix the Missing Tags in your MP3 Files Use the Free Software FixTunes to Automagically Find, and Correct the Tags missing from your MP3 Collection in itunes, Windows Media Player, etc. Table of Contents
Fix the Missing Tags in your MP3 Files Use the Free Software FixTunes to Automagically Find, and Correct the Tags missing from your MP3 Collection in itunes, Windows Media Player, etc. Table of Contents
CSE 374 Programming Concepts & Tools
 CSE 374 Programming Concepts & Tools Hal Perkins Fall 2017 Lecture 11 gdb and Debugging 1 Administrivia HW4 out now, due next Thursday, Oct. 26, 11 pm: C code and libraries. Some tools: gdb (debugger)
CSE 374 Programming Concepts & Tools Hal Perkins Fall 2017 Lecture 11 gdb and Debugging 1 Administrivia HW4 out now, due next Thursday, Oct. 26, 11 pm: C code and libraries. Some tools: gdb (debugger)
GCSE Computing. Revision Pack TWO. Data Representation Questions. Name: /113. Attempt One % Attempt Two % Attempt Three %
 GCSE Computing Revision Pack TWO Data Representation Questions Name: /113 Attempt One % Attempt Two % Attempt Three % Areas of Strength Areas for Development 1. Explain how ASCII is used to represent text
GCSE Computing Revision Pack TWO Data Representation Questions Name: /113 Attempt One % Attempt Two % Attempt Three % Areas of Strength Areas for Development 1. Explain how ASCII is used to represent text
Creating An MP3 Player With HTML5 By Mark Lassoff READ ONLINE
 Creating An MP3 Player With HTML5 By Mark Lassoff READ ONLINE Create a Customized HTML5 Audio Player Creating the HTML5 Audio Player: The OGG format for Firefox and MP3 for other browsers. I then create
Creating An MP3 Player With HTML5 By Mark Lassoff READ ONLINE Create a Customized HTML5 Audio Player Creating the HTML5 Audio Player: The OGG format for Firefox and MP3 for other browsers. I then create
Apology of 0days. Nicolás Waisman
 Apology of 0days Nicolás Waisman Who Am I? Senior Security Researcher and Regional Manager at Immunity, Inc. Research and Development of reliable Heap Overflow exploitation for CANVAS attack framework
Apology of 0days Nicolás Waisman Who Am I? Senior Security Researcher and Regional Manager at Immunity, Inc. Research and Development of reliable Heap Overflow exploitation for CANVAS attack framework
ITunes. itunes works with Windows 2000, XP, Windows Server 2003, Mac OS X and it also works on a few cellular phones.
 ITunes itunes is an online digital media player application that is used for playing and organizing music and video files. itunes was launched by the Apple Computer company in 2001 and it's been going
ITunes itunes is an online digital media player application that is used for playing and organizing music and video files. itunes was launched by the Apple Computer company in 2001 and it's been going
Is Browsing Safe? Web Browser Security. Subverting the Browser. Browser Security Model. XSS / Script Injection. 1. XSS / Script Injection
 Is Browsing Safe? Web Browser Security Charlie Reis Guest Lecture - CSE 490K - 5/24/2007 Send Spam Search Results Change Address? Install Malware Web Mail Movie Rentals 2 Browser Security Model Pages are
Is Browsing Safe? Web Browser Security Charlie Reis Guest Lecture - CSE 490K - 5/24/2007 Send Spam Search Results Change Address? Install Malware Web Mail Movie Rentals 2 Browser Security Model Pages are
A program execution is memory safe so long as memory access errors never occur:
 A program execution is memory safe so long as memory access errors never occur: Buffer overflows, null pointer dereference, use after free, use of uninitialized memory, illegal free Memory safety categories
A program execution is memory safe so long as memory access errors never occur: Buffer overflows, null pointer dereference, use after free, use of uninitialized memory, illegal free Memory safety categories
Unable to import a video file into Lightworks Posted by Slashbuddy24-03 Mar :50
 Unable to import a video file into Lightworks Posted by Slashbuddy24-03 Mar 2016 23:50 Hello, This is my first time posting on the Lightworks forums and I did not think I would ever have to get to this
Unable to import a video file into Lightworks Posted by Slashbuddy24-03 Mar 2016 23:50 Hello, This is my first time posting on the Lightworks forums and I did not think I would ever have to get to this
Pwn ing you(r) cyber offenders
 Pwn ing you(r) cyber offenders Presented by: Piotr Duszynski @drk1wi ;WHOAMI;#? Senior Security Consultant @Trustwave OSCP, OSCE, CEH In security field for the past 6 years, hacking since 9 Enjoys security
Pwn ing you(r) cyber offenders Presented by: Piotr Duszynski @drk1wi ;WHOAMI;#? Senior Security Consultant @Trustwave OSCP, OSCE, CEH In security field for the past 6 years, hacking since 9 Enjoys security
Application Note MUSIC NEST UDP streaming example OP-AN-021. Description. Brief introduction
 Application Note MUSIC NEST UDP streaming example OP-AN-021 Device: openpicus FLYPORT and Music Nest IDE version: 2.2 External Libs: VLSICodec OpenPicus Free IDE Connections: stereo 3.5mm standard jack
Application Note MUSIC NEST UDP streaming example OP-AN-021 Device: openpicus FLYPORT and Music Nest IDE version: 2.2 External Libs: VLSICodec OpenPicus Free IDE Connections: stereo 3.5mm standard jack
Bypassing Mitigations by Attacking JIT Server in Microsoft Edge
 Bypassing Mitigations by Attacking JIT Server in Microsoft Edge Ivan Fratric Infiltrate 2018 About me Security researcher at Google Project Zero Previously: Google Security Team, Academia (UNIZG) Doing
Bypassing Mitigations by Attacking JIT Server in Microsoft Edge Ivan Fratric Infiltrate 2018 About me Security researcher at Google Project Zero Previously: Google Security Team, Academia (UNIZG) Doing
Ethical Hacking and Countermeasures: Web Applications, Second Edition. Chapter 3 Web Application Vulnerabilities
 Ethical Hacking and Countermeasures: Web Chapter 3 Web Application Vulnerabilities Objectives After completing this chapter, you should be able to: Understand the architecture of Web applications Understand
Ethical Hacking and Countermeasures: Web Chapter 3 Web Application Vulnerabilities Objectives After completing this chapter, you should be able to: Understand the architecture of Web applications Understand
Amazing Audacity: Session 1
 Online 2012 Amazing Audacity: Session 1 Katie Wardrobe Midnight Music The Audacity Screen...3 Import audio (a song or SFX)...3 Before we start... 3 File formats... 3 What s the different between WAV and
Online 2012 Amazing Audacity: Session 1 Katie Wardrobe Midnight Music The Audacity Screen...3 Import audio (a song or SFX)...3 Before we start... 3 File formats... 3 What s the different between WAV and
FilmoScope-Lab Media Control System Integration Guide for Crestron Control Systems Version 2.5
 FilmoScope-Lab Media Control System Integration Guide for Crestron Control Systems Version 2.5-1 - Table of Contents Overview... 3 Setting up MCS for Crestron Control.... 4 Requirements.... 4 Preparation....
FilmoScope-Lab Media Control System Integration Guide for Crestron Control Systems Version 2.5-1 - Table of Contents Overview... 3 Setting up MCS for Crestron Control.... 4 Requirements.... 4 Preparation....
Fundamental of Digital Media Design. Introduction to Audio
 Fundamental of Digital Media Design Introduction to Audio by Noraniza Samat Faculty of Computer Systems & Software Engineering noraniza@ump.edu.my OER Fundamental of Digital Media Design by Noraniza Samat
Fundamental of Digital Media Design Introduction to Audio by Noraniza Samat Faculty of Computer Systems & Software Engineering noraniza@ump.edu.my OER Fundamental of Digital Media Design by Noraniza Samat
G-Box System. Introduction: Signage Features. Display Images. Display Video
 G-Box Features. V 1.1 Modified Oct 07 2011 G-Box System. Introduction: G-Box is a Network Digital Signage Player and Server that can display Images, Video, Sides or any web URLs as a part of a Play list.
G-Box Features. V 1.1 Modified Oct 07 2011 G-Box System. Introduction: G-Box is a Network Digital Signage Player and Server that can display Images, Video, Sides or any web URLs as a part of a Play list.
Unusual Web Bugs. A Web App Hacker s Bag O Tricks. Alex kuza55 K.
 Unusual Web Bugs A Web App Hacker s Bag O Tricks Alex kuza55 K. kuza55@gmail.com http://kuza55.blogspot.com/ I'm Alex Starting Uni next year Working for SIFT http://www.sift.com.au/ This talk is Not an
Unusual Web Bugs A Web App Hacker s Bag O Tricks Alex kuza55 K. kuza55@gmail.com http://kuza55.blogspot.com/ I'm Alex Starting Uni next year Working for SIFT http://www.sift.com.au/ This talk is Not an
HTML CS 4640 Programming Languages for Web Applications
 HTML CS 4640 Programming Languages for Web Applications 1 Anatomy of (Basic) Website Your content + HTML + CSS = Your website structure presentation A website is a way to present your content to the world,
HTML CS 4640 Programming Languages for Web Applications 1 Anatomy of (Basic) Website Your content + HTML + CSS = Your website structure presentation A website is a way to present your content to the world,
Source Coding Techniques
 Source Coding Techniques Source coding is based on changing the content of the original signal. Also called semantic-based coding. Compression rates may be higher but at a price of loss of information.
Source Coding Techniques Source coding is based on changing the content of the original signal. Also called semantic-based coding. Compression rates may be higher but at a price of loss of information.
Skill Area 214: Use a Multimedia Software. Software Application (SWA)
 Skill Area 214: Use a Multimedia Application (SWA) Skill Area 214: Use a Multimedia 214.4 Produce Audio Files What is digital audio? Audio is another meaning for sound. Digital audio refers to a digital
Skill Area 214: Use a Multimedia Application (SWA) Skill Area 214: Use a Multimedia 214.4 Produce Audio Files What is digital audio? Audio is another meaning for sound. Digital audio refers to a digital
Framework for Application Security Testing. September 11th, 2018
 Framework for Application Security Testing September 11th, 2018 Create thousands of security tests from existing functional tests automatically Wallarm FAST enables secure CI / CD Wallarm FAST has many
Framework for Application Security Testing September 11th, 2018 Create thousands of security tests from existing functional tests automatically Wallarm FAST enables secure CI / CD Wallarm FAST has many
Buffer Overflow Defenses
 Buffer Overflow Defenses Some examples, pros, and cons of various defenses against buffer overflows. Caveats: 1. Not intended to be a complete list of products that defend against buffer overflows. 2.
Buffer Overflow Defenses Some examples, pros, and cons of various defenses against buffer overflows. Caveats: 1. Not intended to be a complete list of products that defend against buffer overflows. 2.
Reserve Engineering & Buffer Overflow Attacks. Tom Chothia Computer Security, Lecture 17
 Reserve Engineering & Buffer Overflow Attacks Tom Chothia Computer Security, Lecture 17 Introduction A simplified, high-level view of buffer overflow attacks. x86 architecture overflows on the stack Some
Reserve Engineering & Buffer Overflow Attacks Tom Chothia Computer Security, Lecture 17 Introduction A simplified, high-level view of buffer overflow attacks. x86 architecture overflows on the stack Some
Reference8 Pro music player Fast Operation Guide
 Reference8 Pro music player Fast Operation Guide Introduction 1/2 Front 1. Display 2. Power Switch 3. USB2.0 for Memory 4. Down Button 5. Menu Button 6. Up Button 7. IR Window 2/2 Rear 8. Power Socket
Reference8 Pro music player Fast Operation Guide Introduction 1/2 Front 1. Display 2. Power Switch 3. USB2.0 for Memory 4. Down Button 5. Menu Button 6. Up Button 7. IR Window 2/2 Rear 8. Power Socket
8/19/2018. Web Development & Design Foundations with HTML5. Learning Objectives (1 of 2) Learning Objectives (2 of 2) Helper Applications & Plug-Ins
 Web Development & Design Foundations with HTML5 Ninth Edition Chapter 11 Web Multimedia and Interactivity Slides in this presentation contain hyperlinks. JAWS users should be able to get a list of links
Web Development & Design Foundations with HTML5 Ninth Edition Chapter 11 Web Multimedia and Interactivity Slides in this presentation contain hyperlinks. JAWS users should be able to get a list of links
Playing God With Format String Attacks. Bsides Jax 2016 Travis Phillips 10/22/2016
 Playing God With Format String Attacks Bsides Jax 2016 Travis Phillips 10/22/2016 So Why This Talk? Been experimenting with them over the last year Found them simple in theory; difficult in practice. Found
Playing God With Format String Attacks Bsides Jax 2016 Travis Phillips 10/22/2016 So Why This Talk? Been experimenting with them over the last year Found them simple in theory; difficult in practice. Found
Memory Corruption 101 From Primitives to Exploit
 Memory Corruption 101 From Primitives to Exploit Created by Nick Walker @ MWR Infosecurity / @tel0seh What is it? A result of Undefined Behaviour Undefined Behaviour A result of executing computer code
Memory Corruption 101 From Primitives to Exploit Created by Nick Walker @ MWR Infosecurity / @tel0seh What is it? A result of Undefined Behaviour Undefined Behaviour A result of executing computer code
Windows Media Player Manual Update 12 For Vista Full Version
 Windows Media Player Manual Update 12 For Vista Full Version You can also extract music from CDs, while with its online connection, Windows Media Player has library updates providing you with new information.
Windows Media Player Manual Update 12 For Vista Full Version You can also extract music from CDs, while with its online connection, Windows Media Player has library updates providing you with new information.
EZCast Pro User s Manual
 EZCast Pro User s Manual Rev. 1.02 General EZCast Pro is a new product based on successful wireless app EZCast, and adds some new features for commercial/educational application. It supports Multi-users
EZCast Pro User s Manual Rev. 1.02 General EZCast Pro is a new product based on successful wireless app EZCast, and adds some new features for commercial/educational application. It supports Multi-users
Economies of Scale in Hacking Dave Aitel Immunity
 Economies of Scale in Hacking Dave Aitel Immunity Ekoparty, 2008 (Argentina) 10/01/08 1 Demand Side/Supply Side Economies of Scale Networked increase in value High barrier of entry Cheaper as you get bigger
Economies of Scale in Hacking Dave Aitel Immunity Ekoparty, 2008 (Argentina) 10/01/08 1 Demand Side/Supply Side Economies of Scale Networked increase in value High barrier of entry Cheaper as you get bigger
