Introducing Check Point Application Control Software Blade. Patrick Hanel Technical consultant
|
|
|
- Theodore Cannon
- 5 years ago
- Views:
Transcription
1 Introducing Check Point Application Control Software Blade Patrick Hanel Technical consultant 2010 Check Point Software Technologies Ltd. [Unrestricted] For everyone
2 Internet Applications in the Work Place Internet Applications an integral part of today s business John and Support Andy Mike Jeff Sue Julie David is (HR) sending posting team work watching Web searching updating new pictures progress the helping conferencing a to recap on his of with for corporate his personal customer Gmail Dan from last Facebook night branch candidates Twitter account on Skype office NBA status profile results IT staff lack strong visibility into this activity 2
3 The Problem with Internet Applications Malware Threats Bandwidth Hogging Productivity Loss 3
4 Introducing Check Point Application Control Software Blade Detect and control application usage AppWiki Industry s largest library with over 50,000 applications Educate users on corporate policies Available Q Available on EVERY gateway 4
5 Introducing Check Point AppWiki Unparalleled Application Control Over 4,500 applications Over 50,000 social-network widgets Grouped in over 150 categories (including Web 2.0, IM, P2P, Voice & Video, File Share) World s largest Application Classification Library 5
6 Granular Application Categorization Application Type IM Web conferencing Gaming. Advanced Properties Share files High bandwidth Use stealth techniques Security Risk Measures the potential risk 6
7 User and Machine Awareness Includes User Identification Corporate Active Directory Security Gateway User- and group-aware Machine-aware User identification with both agent-based and seamless, agentless Active Directory integration 7
8 Application Detection and Usage Controls Application Detection and Usage Controls Enable access for support team Identify, allow, block or limit usage of applications at user or group level 8
9 Reality of Standard Application Control IT defines black & white policies Policies don t match real usage IT resorts to monitor only No real control! 9
10 Check Point UserCheck Technology Ask Understand usage needs, while enforcing policy Application Usage Alert You are trying to use Skype. Corporate application use policy does not allow the use of Skype. If you require Skype access for business, please click Explain blow. Makes application control more practical Corporate Proper Use Policy Asks users to explain reasons for application usage 10
11 Check Point UserCheck Technology Ask Understand usage needs, while enforcing policy Application Usage Alert You are trying to access YouTube. Corporate application use policy limits YouTube access to business use only in order to save bandwidth. Makes application control more practical Please select and confirm your use-case: Personal, Business, or Cancel Asks users to confirm application usage in real-time 11
12 Check Point UserCheck Technology Inform Inform and educate, while allowing application usage Alerts users in real-time Educates users on risk and usage policies 12
13 Check Point UserCheck Technology Limit Use to preserve resources (bandwidth) or control acceptable use Application Usage Alert You are trying to access Facebook Games. Corporate application use policy allows access to non-business related activities such as Facebook Games only during these times: 12:30-14:00 19:30-8:30 Corporate Proper Use Policy 13
14 Practical Implementation Involve end-users using multiple policy actions Accept / Drop Traditional security policies are suitable for clear-cut cases Inform Allow but inform the user about the risks Ask Learn usage patterns to create better policies Limit Use to preserve resources (bandwidth) or control acceptable use 14
15 Fully Integrated Into Software Blade Architecture Integrated in Software Blade Architecture Available on All Security Gateways Centralized Management New Software Blade 15
16 Easy Deployment Available on All Security Gateways Application Control Identify and control usage of thousands of applications based on user and machine identity. One-click activation on any Check Point security gateway 16
17 Central Policy and Event Management Centralized Management Manage application policies, users and events from a single console 17
18 Summary Check Point Application Control Software Blade Detect and control application usage AppWiki Industry s largest library with over 50,000 applications Educate users on corporate policies Available Q Available on EVERY gateway 18
19 Thank You! 2010 Check Point Software Technologies Ltd. [Unrestricted] For everyone
Identity Awareness Software Blade Check Point Software Technologies Ltd. [Unrestricted] For everyone
![Identity Awareness Software Blade Check Point Software Technologies Ltd. [Unrestricted] For everyone Identity Awareness Software Blade Check Point Software Technologies Ltd. [Unrestricted] For everyone](/thumbs/87/96384350.jpg) Identity Awareness Software Blade 2010 Check Point Software Technologies Ltd. [Unrestricted] For everyone Agenda 1 Introduction 2 Solution Overview 3 Identity Awareness Features 4 Selling Strategy 2 Agenda
Identity Awareness Software Blade 2010 Check Point Software Technologies Ltd. [Unrestricted] For everyone Agenda 1 Introduction 2 Solution Overview 3 Identity Awareness Features 4 Selling Strategy 2 Agenda
Hardening the Education. with NGFW. Narongveth Yutithammanurak Business Development Manager 23 Feb 2012
 Hardening the Education IT Environment with NGFW Narongveth Yutithammanurak Business Development Manager 23 Feb 2012 Technology Trends Security Performance Bandwidth Efficiency Manageability Page 2 What
Hardening the Education IT Environment with NGFW Narongveth Yutithammanurak Business Development Manager 23 Feb 2012 Technology Trends Security Performance Bandwidth Efficiency Manageability Page 2 What
NewspathNow.com Quick Reference Manual November, 2017
 NewspathNow.com Quick Reference Manual November, 2017 This reference manual is designed to get you started using NewspathNow.com. If you need more information on the use of the site contact us via email
NewspathNow.com Quick Reference Manual November, 2017 This reference manual is designed to get you started using NewspathNow.com. If you need more information on the use of the site contact us via email
Data Sheet: Endpoint Security Symantec Multi-tier Protection Trusted protection for endpoints and messaging environments
 Trusted protection for endpoints and messaging environments Overview creates a protected endpoint and messaging environment that is secure against today s complex data loss, malware, and spam threats controlling
Trusted protection for endpoints and messaging environments Overview creates a protected endpoint and messaging environment that is secure against today s complex data loss, malware, and spam threats controlling
Here(is(the(XML(Schema(that(describes(the(format:
 BuildingBusinessDashboardsusingXSLT,SVG,HTML5 Today seconomyhasdramaticallychangedthewaycompaniesdobusiness,havinganonlinepresenceisnolonger sufficient,andordermanagementsystemshavetobereal:timeandaccessibleonalargevarietyofdevices:
BuildingBusinessDashboardsusingXSLT,SVG,HTML5 Today seconomyhasdramaticallychangedthewaycompaniesdobusiness,havinganonlinepresenceisnolonger sufficient,andordermanagementsystemshavetobereal:timeandaccessibleonalargevarietyofdevices:
We Secure The Highways. Safety comes first.with data availability and data security 24x7 Highway Monitoring and Control
 We Secure The Highways Safety comes first.with data availability and data security 24x7 Highway Monitoring and Control 1 About Nea Odos S.A. Concession period: 30 years Ionia Motorway: PATHE Motorway:
We Secure The Highways Safety comes first.with data availability and data security 24x7 Highway Monitoring and Control 1 About Nea Odos S.A. Concession period: 30 years Ionia Motorway: PATHE Motorway:
Dealing with & Chat
 Dealing with Email & Chat Paul White Chief Executive Officer @mplsystems #crm #custserv #contactcentre The evolving customer landscape Email still only accounts for 15.4% of inbound transactions ContactBabel
Dealing with Email & Chat Paul White Chief Executive Officer @mplsystems #crm #custserv #contactcentre The evolving customer landscape Email still only accounts for 15.4% of inbound transactions ContactBabel
Cato Cloud. Software-defined and cloud-based secure enterprise network. Solution Brief
 Cato Cloud Software-defined and cloud-based secure enterprise network Solution Brief Legacy WAN and Security Appliances are Incompatible with the Modern Enterprise Cato Networks: Software-defined and Cloud-based
Cato Cloud Software-defined and cloud-based secure enterprise network Solution Brief Legacy WAN and Security Appliances are Incompatible with the Modern Enterprise Cato Networks: Software-defined and Cloud-based
BUFFERZONE Advanced Endpoint Security
 BUFFERZONE Advanced Endpoint Security Enterprise-grade Containment, Bridging and Intelligence BUFFERZONE defends endpoints against a wide range of advanced and targeted threats with patented containment,
BUFFERZONE Advanced Endpoint Security Enterprise-grade Containment, Bridging and Intelligence BUFFERZONE defends endpoints against a wide range of advanced and targeted threats with patented containment,
IBM Next Generation Intrusion Prevention System
 IBM Next Generation Intrusion Prevention System Fadly Yahaya SWAT Optimizing the World s Infrastructure Oct 2012 Moscow 2012 IBM Corporation Please note: IBM s statements regarding its plans, directions,
IBM Next Generation Intrusion Prevention System Fadly Yahaya SWAT Optimizing the World s Infrastructure Oct 2012 Moscow 2012 IBM Corporation Please note: IBM s statements regarding its plans, directions,
Sourcefire Solutions Overview Security for the Real World. SEE everything in your environment. LEARN by applying security intelligence to data
 SEE everything in your environment LEARN by applying security intelligence to data ADAPT defenses automatically ACT in real-time Sourcefire Solutions Overview Security for the Real World Change is constant.
SEE everything in your environment LEARN by applying security intelligence to data ADAPT defenses automatically ACT in real-time Sourcefire Solutions Overview Security for the Real World Change is constant.
SOCIAL NETWORKING IN TODAY S BUSINESS WORLD
 SOCIAL NETWORKING IN TODAY S BUSINESS WORLD AGENDA Review the use of social networking applications within the business environment Review current trends in threats, attacks and incidents Understand how
SOCIAL NETWORKING IN TODAY S BUSINESS WORLD AGENDA Review the use of social networking applications within the business environment Review current trends in threats, attacks and incidents Understand how
What You Don t Know About Web Conferencing and Synchronous Technologies for Education and Training
 What You Don t Know About Web Conferencing and Synchronous Technologies for Education and Training Andrew Black, PhD, MBA Executive Director of Educational Technologies Assistant Professor University of
What You Don t Know About Web Conferencing and Synchronous Technologies for Education and Training Andrew Black, PhD, MBA Executive Director of Educational Technologies Assistant Professor University of
SD-WAN Transform Your Agency
 Federal SD-WAN Transform Your Agency 1 Overview Is your agency facing network traffic challenges? Is migration to the secured cloud hogging scarce bandwidth? How about increased mobile computing that is
Federal SD-WAN Transform Your Agency 1 Overview Is your agency facing network traffic challenges? Is migration to the secured cloud hogging scarce bandwidth? How about increased mobile computing that is
1110 Cool Things Your Firewall Should Do. Extend beyond blocking network threats to protect, manage and control application traffic
 1110 Cool Things Your Firewall Should Do Extend beyond blocking network threats to protect, manage and control application traffic Table of Contents The Firewall Grows Up 1 What does SonicWALL Application
1110 Cool Things Your Firewall Should Do Extend beyond blocking network threats to protect, manage and control application traffic Table of Contents The Firewall Grows Up 1 What does SonicWALL Application
University Integrates Voice and Collaboration Tools in One Interface
 Customer Case Study University Integrates Voice and Collaboration Tools in One Interface Liberty University prepared for enrollment growth with Unified Communications Integration for Microsoft Office Communicator.
Customer Case Study University Integrates Voice and Collaboration Tools in One Interface Liberty University prepared for enrollment growth with Unified Communications Integration for Microsoft Office Communicator.
Securing the Virtualized Environment: Meeting a New Class of Challenges with Check Point Security Gateway Virtual Edition
 Securing the Virtualized Environment: Meeting a New Class of Challenges with Check Point Security Gateway Virtual Edition An ENTERPRISE MANAGEMENT ASSOCIATES (EMA ) White Paper Prepared for Check Point
Securing the Virtualized Environment: Meeting a New Class of Challenges with Check Point Security Gateway Virtual Edition An ENTERPRISE MANAGEMENT ASSOCIATES (EMA ) White Paper Prepared for Check Point
Getting the Most Out of Your Next-Generation Firewall
 White Paper Getting the Most Out of Your Next-Generation Firewall Comprehensive network visibility and control increases business efficiency and enables business growth while maximizing security. To address
White Paper Getting the Most Out of Your Next-Generation Firewall Comprehensive network visibility and control increases business efficiency and enables business growth while maximizing security. To address
IT & DATA SECURITY BREACH PREVENTION
 IT & DATA SECURITY BREACH PREVENTION A PRACTICAL GUIDE Part 1: Reducing Employee and Application Risks CONTENTS EMPLOYEES: IT security hygiene best practice APPLICATIONS: Make patching a priority AS CORPORATE
IT & DATA SECURITY BREACH PREVENTION A PRACTICAL GUIDE Part 1: Reducing Employee and Application Risks CONTENTS EMPLOYEES: IT security hygiene best practice APPLICATIONS: Make patching a priority AS CORPORATE
SRX als NGFW. Michel Tepper Consultant
 SRX als NGFW Michel Tepper Consultant Firewall Security Challenges Organizations are looking for ways to protect their assets amidst today s ever-increasing threat landscape. The latest generation of web-based
SRX als NGFW Michel Tepper Consultant Firewall Security Challenges Organizations are looking for ways to protect their assets amidst today s ever-increasing threat landscape. The latest generation of web-based
SearchInform DLP. Data Loss Prevention and Insider Threat Security
 SearchInform DLP Data Loss Prevention and Insider Threat Security SearchInform Today Over 2000 customers in 17 countries Over 11 years on the DLP market, 22 years in the IT industry SearchInform DLP monitors
SearchInform DLP Data Loss Prevention and Insider Threat Security SearchInform Today Over 2000 customers in 17 countries Over 11 years on the DLP market, 22 years in the IT industry SearchInform DLP monitors
Advanced Internet Features
 Advanced Internet Features The following topics will create awareness of the vast opportunities the internet has to offer and allow users to get the most out of the web experience. As highspeed internet
Advanced Internet Features The following topics will create awareness of the vast opportunities the internet has to offer and allow users to get the most out of the web experience. As highspeed internet
Mission Defense via Information-Centric Security
 Mission Defense via Information-Centric Security Overview It s About the Information Traditional CND Tools are Not Sufficient Not All Data is Created Equal "The views expressed in this presentation are
Mission Defense via Information-Centric Security Overview It s About the Information Traditional CND Tools are Not Sufficient Not All Data is Created Equal "The views expressed in this presentation are
Take Back Control: Increase Security, Empower Employees, Protect the Business
 Take Back Control: Increase Security, Empower Employees, Protect the Business Application Control White Paper Introduction: Balancing Productivity with Security As workers find new and creative ways to
Take Back Control: Increase Security, Empower Employees, Protect the Business Application Control White Paper Introduction: Balancing Productivity with Security As workers find new and creative ways to
Angelo Gentili Head of Business Development, EMEA Region, PartnerNET
 Angelo Gentili Head of Business Development, EMEA Region, PartnerNET The Innovation Solution in the Business Security Field. PartnerNet introduces Seqrite Welcome To Dynamic. Scalable. Future-Ready. Why
Angelo Gentili Head of Business Development, EMEA Region, PartnerNET The Innovation Solution in the Business Security Field. PartnerNet introduces Seqrite Welcome To Dynamic. Scalable. Future-Ready. Why
Meraki Solution Brochure
 Meraki 2016 Solution Brochure Introduction 100% Cloud Managed IT Cisco Meraki cloud managed edge, branch, and enterprise-class campus IT solutions bring simplicity to organizations of every size. With
Meraki 2016 Solution Brochure Introduction 100% Cloud Managed IT Cisco Meraki cloud managed edge, branch, and enterprise-class campus IT solutions bring simplicity to organizations of every size. With
ADDRESSING TODAY S VULNERABILITIES
 E-Guide ADDRESSING TODAY S VULNERABILITIES SearchSecurity E ven if your firm has no legal or contractual obligation to perform them, authenticated scans should be an essential part of your security program.
E-Guide ADDRESSING TODAY S VULNERABILITIES SearchSecurity E ven if your firm has no legal or contractual obligation to perform them, authenticated scans should be an essential part of your security program.
Microsoft Security Management
 Microsoft Security Management MICROSOFT SECURITY MANAGEMENT SECURITY MANAGEMENT CHALLENGES Some large financial services organizations have as many as 40 or more different security vendors inside their
Microsoft Security Management MICROSOFT SECURITY MANAGEMENT SECURITY MANAGEMENT CHALLENGES Some large financial services organizations have as many as 40 or more different security vendors inside their
Aerohive and IntelliGO End-to-End Security for devices on your network
 Aerohive and IntelliGO End-to-End Security for devices on your network Introduction Networks have long used a password to authenticate users and devices. Today, many cyber attacks can be used to capture
Aerohive and IntelliGO End-to-End Security for devices on your network Introduction Networks have long used a password to authenticate users and devices. Today, many cyber attacks can be used to capture
BUFFERZONE Advanced Endpoint Security
 BUFFERZONE Advanced Endpoint Security Enterprise-grade Containment, Bridging and Intelligence BUFFERZONE defends endpoints against a wide range of advanced and targeted threats with patented containment,
BUFFERZONE Advanced Endpoint Security Enterprise-grade Containment, Bridging and Intelligence BUFFERZONE defends endpoints against a wide range of advanced and targeted threats with patented containment,
Meraki 2018 Solution Brochure
 Meraki 2018 Solution Brochure INTRODUCTION 100% Cloud Managed IT Cisco Meraki cloud managed edge, branch, and enterprise-class campus IT solutions bring simplicity to organizations of every size. With
Meraki 2018 Solution Brochure INTRODUCTION 100% Cloud Managed IT Cisco Meraki cloud managed edge, branch, and enterprise-class campus IT solutions bring simplicity to organizations of every size. With
GFI Product Comparison. GFI WebMonitor 2015 vs. McAfee Web Gateway
 GFI Product Comparison GFI WebMonitor 2015 vs. McAfee Web Gateway Features GFI WebMonitor 2015 McAfee Web Gateway General features Platforms Windows servers and workstation OS Standalone proxy Win 7, 8,
GFI Product Comparison GFI WebMonitor 2015 vs. McAfee Web Gateway Features GFI WebMonitor 2015 McAfee Web Gateway General features Platforms Windows servers and workstation OS Standalone proxy Win 7, 8,
ACHIEVING FIFTH GENERATION CYBER SECURITY
 ACHIEVING FIFTH GENERATION CYBER SECURITY A Survey Research Report of IT and Security Professionals MARCH 2018 INTRODUCTION The pursuit of the highest level of cyber security is a top priority for IT and
ACHIEVING FIFTH GENERATION CYBER SECURITY A Survey Research Report of IT and Security Professionals MARCH 2018 INTRODUCTION The pursuit of the highest level of cyber security is a top priority for IT and
Effective Information Management and Governance: Building the Business Case for Taxonomy
 Effective Information Management and Governance: Building the Business Case for Taxonomy May 16, 2017 A WAND, Inc. White Paper By Mark Leher, COO, WAND, Inc. Executive Summary Companies are often reluctant
Effective Information Management and Governance: Building the Business Case for Taxonomy May 16, 2017 A WAND, Inc. White Paper By Mark Leher, COO, WAND, Inc. Executive Summary Companies are often reluctant
Snort: The World s Most Widely Deployed IPS Technology
 Technology Brief Snort: The World s Most Widely Deployed IPS Technology Overview Martin Roesch, the founder of Sourcefire and chief security architect at Cisco, created Snort in 1998. Snort is an open-source,
Technology Brief Snort: The World s Most Widely Deployed IPS Technology Overview Martin Roesch, the founder of Sourcefire and chief security architect at Cisco, created Snort in 1998. Snort is an open-source,
Microsoft 365 Business FAQs
 Microsoft 365 Business FAQs Last updated April 27 th, 2018 Table of Contents General... 3 What is Microsoft 365 Business?... 3 Who should consider adopting Microsoft 365 Business?... 3 How can I get Microsoft
Microsoft 365 Business FAQs Last updated April 27 th, 2018 Table of Contents General... 3 What is Microsoft 365 Business?... 3 Who should consider adopting Microsoft 365 Business?... 3 How can I get Microsoft
Integrating Okta and Preempt Detecting and Preventing Threats With Greater Visibility and Proactive Enforcement
 Integrating Okta and Preempt Detecting and Preventing Threats With Greater Visibility and Proactive Enforcement The Challenge: Smarter Attackers and Dissolving Perimeters Modern enterprises are simultaneously
Integrating Okta and Preempt Detecting and Preventing Threats With Greater Visibility and Proactive Enforcement The Challenge: Smarter Attackers and Dissolving Perimeters Modern enterprises are simultaneously
McAfee Family Protection The Easiest, Most Complete Way to Keep Your Children Safe Online
 The Easiest, Most Complete Way to Keep Your Children Safe Online 1 Quick Start Easy Installation STEP 1: First, ensure that your computer meets or exceeds the minimum systems requirements listed below.
The Easiest, Most Complete Way to Keep Your Children Safe Online 1 Quick Start Easy Installation STEP 1: First, ensure that your computer meets or exceeds the minimum systems requirements listed below.
Defence, Intelligence and Secure Communications Solutions
 Defence, Intelligence and Secure Communications Solutions Ensuring mission critical application performance Allot XXXXXXXXX Date Copyright 2013 Allot Communications Ltd. All rights reserved. Allot Communications,
Defence, Intelligence and Secure Communications Solutions Ensuring mission critical application performance Allot XXXXXXXXX Date Copyright 2013 Allot Communications Ltd. All rights reserved. Allot Communications,
JURUMANI MERAKI CLOUD MANAGED SECURITY & SD-WAN
 JURUMANI CLOUD MANAGED SECURITY & SD-WAN SECURITY BY DESIGN OVERVIEW Cisco Meraki MX Security Appliances are ideal for organizations considering a Unified Threat Managment (UTM) solution, for distributed
JURUMANI CLOUD MANAGED SECURITY & SD-WAN SECURITY BY DESIGN OVERVIEW Cisco Meraki MX Security Appliances are ideal for organizations considering a Unified Threat Managment (UTM) solution, for distributed
Mobility Optimized Access Layer
 solution brief Mobility Optimized Access Layer Completing the Hive with Aerohive Switches Designing for Mobile First Legacy enterprise networks were never designed to accommodate the complexity of a mobile-first
solution brief Mobility Optimized Access Layer Completing the Hive with Aerohive Switches Designing for Mobile First Legacy enterprise networks were never designed to accommodate the complexity of a mobile-first
Retail Stores & Restaurant Chains
 Use Cases Retail Stores & Restaurant Chains Enterprise INTRODUCTION This document provides a selection of customer use cases applicable for the retail stores sector. Each use case describes an individual
Use Cases Retail Stores & Restaurant Chains Enterprise INTRODUCTION This document provides a selection of customer use cases applicable for the retail stores sector. Each use case describes an individual
Office 365 Business The Microsoft Office you know, powered by the cloud.
 Office 365 Business The Microsoft Office you know, powered by the cloud. Power your business with the best-in-class productivity tools from Microsoft the applications you know, always up-to-date and accessible
Office 365 Business The Microsoft Office you know, powered by the cloud. Power your business with the best-in-class productivity tools from Microsoft the applications you know, always up-to-date and accessible
Fencing the Cloud. Roger Casals. Senior Director Product Management. Shared vision for the Identity: Fencing the Cloud 1
 Fencing the Cloud with Identity Roger Casals Senior Director Product Management Shared vision for the Identity: Fencing the Cloud 1 Disclaimer Copyright 2014 Symantec Corporation. All rights reserved.
Fencing the Cloud with Identity Roger Casals Senior Director Product Management Shared vision for the Identity: Fencing the Cloud 1 Disclaimer Copyright 2014 Symantec Corporation. All rights reserved.
IBM Internet Security Systems Proventia Management SiteProtector
 Supporting compliance and mitigating risk through centralized management of enterprise security devices IBM Internet Security Systems Proventia Management SiteProtector Highlights Reduces the costs and
Supporting compliance and mitigating risk through centralized management of enterprise security devices IBM Internet Security Systems Proventia Management SiteProtector Highlights Reduces the costs and
Cisco ASA Next-Generation Firewall Services
 Q&A Cisco ASA Next-Generation Firewall Services Q. What are Cisco ASA Next-Generation Firewall Services? A. Cisco ASA Next-Generation Firewall Services are a modular security service that extends the Cisco
Q&A Cisco ASA Next-Generation Firewall Services Q. What are Cisco ASA Next-Generation Firewall Services? A. Cisco ASA Next-Generation Firewall Services are a modular security service that extends the Cisco
A Quick Start Guide On How To Promote Your Site Using WebCEO
 Move your site to the top! A Quick Start Guide On How To Promote Your Site Using WebCEO Welcome to WebCEO, a set of 15 cloud-based tools for SEO, Social Media Analytics and Competitive Analysis. This platform
Move your site to the top! A Quick Start Guide On How To Promote Your Site Using WebCEO Welcome to WebCEO, a set of 15 cloud-based tools for SEO, Social Media Analytics and Competitive Analysis. This platform
KNect Directory (Desktop Version) (Step-by-step)
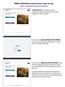 KNect Directory (Desktop Version) (Step-by-step) https://community.evertrue.com/knox - Login Screen to the desktop version. -You have the option to login with your LinkedIn Credentials or with your email.
KNect Directory (Desktop Version) (Step-by-step) https://community.evertrue.com/knox - Login Screen to the desktop version. -You have the option to login with your LinkedIn Credentials or with your email.
Hybrid WAN Operations: Extend Network Monitoring Across SD-WAN and Legacy WAN Infrastructure
 Hybrid WAN Operations: Extend Network Monitoring Across SD-WAN and Legacy WAN Infrastructure An ENTERPRISE MANAGEMENT ASSOCIATES (EMA ) White Paper Prepared for SevOne May 2017 IT & DATA MANAGEMENT RESEARCH,
Hybrid WAN Operations: Extend Network Monitoring Across SD-WAN and Legacy WAN Infrastructure An ENTERPRISE MANAGEMENT ASSOCIATES (EMA ) White Paper Prepared for SevOne May 2017 IT & DATA MANAGEMENT RESEARCH,
Voice, Video and Data Convergence:
 : A best-practice approach for transitioning your network infrastructure White Paper The business benefits of network convergence are clear: fast, dependable, real-time communication, unprecedented information
: A best-practice approach for transitioning your network infrastructure White Paper The business benefits of network convergence are clear: fast, dependable, real-time communication, unprecedented information
Transform your network and your customer experience. Introducing SD-WAN Concierge
 Transform your network and your customer experience Introducing SD-WAN Concierge Optimize your application performance, lower your total cost of ownership and simplify your network management. 2X Bandwith
Transform your network and your customer experience Introducing SD-WAN Concierge Optimize your application performance, lower your total cost of ownership and simplify your network management. 2X Bandwith
Security from the Inside
 Security from the Inside Detect, Record, and Eliminate Malicious User Behavior 24/7 live screen recording & playback Automatically allow or block any activity Real-time user activity tracking Rule-based
Security from the Inside Detect, Record, and Eliminate Malicious User Behavior 24/7 live screen recording & playback Automatically allow or block any activity Real-time user activity tracking Rule-based
The SD-WAN security guide
 The SD-WAN security guide How a flexible, software-defined WAN can help protect your network, people and data SD-WAN security: Separating fact from fiction For many companies, the benefits of SD-WAN are
The SD-WAN security guide How a flexible, software-defined WAN can help protect your network, people and data SD-WAN security: Separating fact from fiction For many companies, the benefits of SD-WAN are
Cisco s Appliance-based Content Security: IronPort and Web Security
 Cisco s Appliance-based Content Security: IronPort E-mail and Web Security Hrvoje Dogan Consulting Systems Engineer, Security, Emerging Markets East 2010 Cisco and/or its affiliates. All rights reserved.
Cisco s Appliance-based Content Security: IronPort E-mail and Web Security Hrvoje Dogan Consulting Systems Engineer, Security, Emerging Markets East 2010 Cisco and/or its affiliates. All rights reserved.
Privileged Account Security: A Balanced Approach to Securing Unix Environments
 Privileged Account Security: A Balanced Approach to Securing Unix Environments Table of Contents Introduction 3 Every User is a Privileged User 3 Privileged Account Security: A Balanced Approach 3 Privileged
Privileged Account Security: A Balanced Approach to Securing Unix Environments Table of Contents Introduction 3 Every User is a Privileged User 3 Privileged Account Security: A Balanced Approach 3 Privileged
Use Cases. E-Commerce. Enterprise
 Use Cases E-Commerce Enterprise INTRODUCTION This document provides a selection of customer use cases applicable for the e-commerce sector. Each use case describes an individual challenge faced by e-commerce
Use Cases E-Commerce Enterprise INTRODUCTION This document provides a selection of customer use cases applicable for the e-commerce sector. Each use case describes an individual challenge faced by e-commerce
Securing Your SWIFT Environment Using Micro-Segmentation
 Securing Your SWIFT Environment Using Micro-Segmentation WP201801 Overview By January 1, 2018, all SWIFT customers must self-attest to their compliance with the new SWIFT Customer Security Program (CSP).
Securing Your SWIFT Environment Using Micro-Segmentation WP201801 Overview By January 1, 2018, all SWIFT customers must self-attest to their compliance with the new SWIFT Customer Security Program (CSP).
What to Look for When Evaluating Next-Generation Firewalls
 What to Look for When Evaluating Next-Generation Firewalls Using independent tests to compare performance, cost and functionality Table of Contents Why Use Independent Tests in Evaluations?... 3 What to
What to Look for When Evaluating Next-Generation Firewalls Using independent tests to compare performance, cost and functionality Table of Contents Why Use Independent Tests in Evaluations?... 3 What to
ACTIONABLE SECURITY INTELLIGENCE
 ACTIONABLE SECURITY INTELLIGENCE Palo Alto Networks ACC, Logging and Reporting Data is widely available. What is scarce is the ability to extract actionable intelligence from it. Palo Alto Networks next-generation
ACTIONABLE SECURITY INTELLIGENCE Palo Alto Networks ACC, Logging and Reporting Data is widely available. What is scarce is the ability to extract actionable intelligence from it. Palo Alto Networks next-generation
Collaboration & Education: Do Google & Blackboard & SMART End the Discussion?
 Collaboration & Education: Do Google & Blackboard & SMART End the Discussion? July 15 2014 Alan D. Greenberg Sr. Analyst & Partner @AlanGatWR @Wainhouse360 #WRSummit What I ll Cover What s Different about
Collaboration & Education: Do Google & Blackboard & SMART End the Discussion? July 15 2014 Alan D. Greenberg Sr. Analyst & Partner @AlanGatWR @Wainhouse360 #WRSummit What I ll Cover What s Different about
Deploying Skype for Business
 Deploying Skype for Business 24 November 2015 ulster.ac.uk A True Story Donna O Kane Unified Communications Manager Ulster University d.okane@ulster.ac.uk Dave Mailer Principal Consultant 4C Strategies
Deploying Skype for Business 24 November 2015 ulster.ac.uk A True Story Donna O Kane Unified Communications Manager Ulster University d.okane@ulster.ac.uk Dave Mailer Principal Consultant 4C Strategies
Office 365: Fact Sheet
 Office 365: Fact Sheet Microsoft Office 365 from 3C Technology Ltd brings together cloud versions of our most trusted communication and collaboration products with the latest version of our desktop suite.
Office 365: Fact Sheet Microsoft Office 365 from 3C Technology Ltd brings together cloud versions of our most trusted communication and collaboration products with the latest version of our desktop suite.
Course 20337B: Enterprise Voice and Online Services with Microsoft Lync Server 2013 Exam Code: Duration:40 Hrs
 Course 20337B: Enterprise Voice and Online Services with Microsoft Lync Server 2013 Exam Code: 70-337 Duration:40 Hrs Course Outline Module 1: Voice Architecture This module introduce Enterprise Voice
Course 20337B: Enterprise Voice and Online Services with Microsoft Lync Server 2013 Exam Code: 70-337 Duration:40 Hrs Course Outline Module 1: Voice Architecture This module introduce Enterprise Voice
Office 365: Modern Workplace
 Office 365: Modern Workplace November 8, 2018 Bruce Ward, VP of Business Strategy Helping you grow your business with scalable IT services & solutions for today s challenges & tomorrow s vision. 2018 Peters
Office 365: Modern Workplace November 8, 2018 Bruce Ward, VP of Business Strategy Helping you grow your business with scalable IT services & solutions for today s challenges & tomorrow s vision. 2018 Peters
Ritz Camera Leverages Whitelisting for Picture Perfect Security
 Ritz Camera Leverages Whitelisting for Picture Perfect Security About Ritz Camera Nation s Largest Retail Camera and Photo Chain +3,000 Stores with Kiosks, POS and Servers PCI Data Security Standard -
Ritz Camera Leverages Whitelisting for Picture Perfect Security About Ritz Camera Nation s Largest Retail Camera and Photo Chain +3,000 Stores with Kiosks, POS and Servers PCI Data Security Standard -
De-dupe: It s not a question of if, rather where and when! What to Look for and What to Avoid
 De-dupe: It s not a question of if, rather where and when! What to Look for and What to Avoid By Greg Schulz Founder and Senior Analyst, the StorageIO Group Author The Green and Virtual Data Center (CRC)
De-dupe: It s not a question of if, rather where and when! What to Look for and What to Avoid By Greg Schulz Founder and Senior Analyst, the StorageIO Group Author The Green and Virtual Data Center (CRC)
Managed Endpoint Defense
 DATA SHEET Managed Endpoint Defense Powered by CB Defense Next-gen endpoint threat detection and response DEPLOY AND HARDEN. Rapidly deploy and optimize endpoint prevention with dedicated security experts
DATA SHEET Managed Endpoint Defense Powered by CB Defense Next-gen endpoint threat detection and response DEPLOY AND HARDEN. Rapidly deploy and optimize endpoint prevention with dedicated security experts
SEE MORE. CONTROL MORE. SAVE MORE.
 SEE MORE. CONTROL MORE. SAVE MORE. INTRODUCING INTEGRA TODAY S CHALLENGE Trying to manage your satellite communications traffic is becoming increasingly difficult, particularly in today s BYOD (bring-your-owndevice)
SEE MORE. CONTROL MORE. SAVE MORE. INTRODUCING INTEGRA TODAY S CHALLENGE Trying to manage your satellite communications traffic is becoming increasingly difficult, particularly in today s BYOD (bring-your-owndevice)
Log into your Account on Website then back to Home page.
 Log into your Account on Website then back to Home page. To get to the team roster first go to > Team Directory. After you find the team you re looking for click on Team Home. This will take you to that
Log into your Account on Website then back to Home page. To get to the team roster first go to > Team Directory. After you find the team you re looking for click on Team Home. This will take you to that
CarCareCONNECT. Boost Performance, Grow Your Shop! Your guide to improving your online brand
 CarCareCONNECT Boost Performance, Grow Your Shop! Your guide to improving your online brand ABOUT US YOUR MARKETING PLAN TABLE OF CONTENTS WHAT TO EXPECT PERSONALIZE YOUR WEBSITE LAUNCH YOUR WEBSITE MARKETING
CarCareCONNECT Boost Performance, Grow Your Shop! Your guide to improving your online brand ABOUT US YOUR MARKETING PLAN TABLE OF CONTENTS WHAT TO EXPECT PERSONALIZE YOUR WEBSITE LAUNCH YOUR WEBSITE MARKETING
Connected Experiences
 Connected Experiences 2017 Bio 7 years at Cisco Meraki Security / SD-WAN / Analytics / SP Launched MX in 2011 500M firewalls and counting Before, PM @ Dell (Wyse) Landscape Connected Experiences Applications
Connected Experiences 2017 Bio 7 years at Cisco Meraki Security / SD-WAN / Analytics / SP Launched MX in 2011 500M firewalls and counting Before, PM @ Dell (Wyse) Landscape Connected Experiences Applications
Is Your Web Application Really Secure? Ken Graf, Watchfire
 Is Your Web Application Really Secure? Ken Graf, Watchfire What we will discuss today Pressures on the application lifecycle Why application security defects matter How to create hacker resistant business
Is Your Web Application Really Secure? Ken Graf, Watchfire What we will discuss today Pressures on the application lifecycle Why application security defects matter How to create hacker resistant business
Mobile County Public School System Builds a More Secure Future with AMP for Endpoints
 Mobile County Public School System Builds a More Secure Future with AMP for Endpoints Cisco AMP for Endpoints met our needs from all security standpoints. We re seeing more and AMP is catching things that
Mobile County Public School System Builds a More Secure Future with AMP for Endpoints Cisco AMP for Endpoints met our needs from all security standpoints. We re seeing more and AMP is catching things that
Defense-in-Depth Against Malicious Software. Speaker name Title Group Microsoft Corporation
 Defense-in-Depth Against Malicious Software Speaker name Title Group Microsoft Corporation Agenda Understanding the Characteristics of Malicious Software Malware Defense-in-Depth Malware Defense for Client
Defense-in-Depth Against Malicious Software Speaker name Title Group Microsoft Corporation Agenda Understanding the Characteristics of Malicious Software Malware Defense-in-Depth Malware Defense for Client
Executive Summary...1
 Table of Contents Executive Summary...1...2 Key Findings in the Cloud...2 Growth Opportunities Overview...3 Hosted Infrastructure...4 Web Presence...6 Hosted Communication and Collaboration...9 Hosted
Table of Contents Executive Summary...1...2 Key Findings in the Cloud...2 Growth Opportunities Overview...3 Hosted Infrastructure...4 Web Presence...6 Hosted Communication and Collaboration...9 Hosted
Meraki MX Family. Overview
 DATASHEET Meraki MX Family Overview The Meraki MX is a complete next generation firewall and branch gateway solution, designed to make distributed networks fast, secure, and easy to manage. The world s
DATASHEET Meraki MX Family Overview The Meraki MX is a complete next generation firewall and branch gateway solution, designed to make distributed networks fast, secure, and easy to manage. The world s
WHITEPAPER. Top Reasons Why Enterprises Must Automat DNS, DHCP and IP Address Management
 WHITEPAPER Top Reasons Why Enterprises Must Automat DNS, DHCP and IP Address Management Top Reasons Why Enterprises Must Automate DNS, DHCP and IP Address Management Regardless of size, businesses face
WHITEPAPER Top Reasons Why Enterprises Must Automat DNS, DHCP and IP Address Management Top Reasons Why Enterprises Must Automate DNS, DHCP and IP Address Management Regardless of size, businesses face
MICROSOFT APPLICATIONS
 MICROSOFT APPLICATIONS MICROSOFT SOFTWARE SOLUTIONS THE EFFECTIVE WAY TO DELIVER MICROSOFT APPLICATIONS The Microsoft Office suite of applications are a business essential; one that is used each and every
MICROSOFT APPLICATIONS MICROSOFT SOFTWARE SOLUTIONS THE EFFECTIVE WAY TO DELIVER MICROSOFT APPLICATIONS The Microsoft Office suite of applications are a business essential; one that is used each and every
Campaign Goals, Objectives and Timeline SEO & Pay Per Click Process SEO Case Studies SEO, SEM, Social Media Strategy On Page SEO Off Page SEO
 Campaign Goals, Objectives and Timeline SEO & Pay Per Click Process SEO Case Studies SEO, SEM, Social Media Strategy On Page SEO Off Page SEO Reporting Pricing Plans Why Us & Contact Generate organic search
Campaign Goals, Objectives and Timeline SEO & Pay Per Click Process SEO Case Studies SEO, SEM, Social Media Strategy On Page SEO Off Page SEO Reporting Pricing Plans Why Us & Contact Generate organic search
Using Mobile Phones for Teaching and Learning Purposes in Higher Learning Institutions: the Case of Sokoine University of Agriculture in Tanzania
 Using Mobile Phones for Teaching and Learning Purposes in Higher Learning Institutions: the Case of Sokoine University of Agriculture in Tanzania 1 Authors Wulystan P. Mtega (wmtega@gmail.com) Ronald Bernard
Using Mobile Phones for Teaching and Learning Purposes in Higher Learning Institutions: the Case of Sokoine University of Agriculture in Tanzania 1 Authors Wulystan P. Mtega (wmtega@gmail.com) Ronald Bernard
Incident Response Agility: Leverage the Past and Present into the Future
 SESSION ID: SPO1-W03 Incident Response Agility: Leverage the Past and Present into the Future Torry Campbell CTO, Endpoint and Management Technologies Intel Security The Reality we Face Reconnaissance
SESSION ID: SPO1-W03 Incident Response Agility: Leverage the Past and Present into the Future Torry Campbell CTO, Endpoint and Management Technologies Intel Security The Reality we Face Reconnaissance
Adding a Blog Page in Weebly!
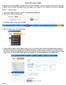 Adding a Blog Page in Weebly A blog allows you to post updates, reminders, links, and other information. There are a couple of ways you can use a blog in Weebly. You may include a blog page as one of the
Adding a Blog Page in Weebly A blog allows you to post updates, reminders, links, and other information. There are a couple of ways you can use a blog in Weebly. You may include a blog page as one of the
Exam Check Point Security Administrator R80.1 (CCSA)
 Check Point Certified Secuirty Administrator (CCSA) Exam 156-215.80 Check Point Security Administrator R80.1 (CCSA) Multiple Choice Questions (156-215.80) Check Point Certified Security Administrator (CCSA)
Check Point Certified Secuirty Administrator (CCSA) Exam 156-215.80 Check Point Security Administrator R80.1 (CCSA) Multiple Choice Questions (156-215.80) Check Point Certified Security Administrator (CCSA)
Data Protection. Rethinking. Michael Andrews, Director, Enterprise Data Protection, APJ HP Autonomy IM
 Rethinking Data Protection Michael Andrews, Director, Enterprise Data Protection, APJ HP Autonomy IM Today s Reality: The Rules of the Game Have Changed for Data Protection EXPLOSION OF DATA DATA EVERYWHERE
Rethinking Data Protection Michael Andrews, Director, Enterprise Data Protection, APJ HP Autonomy IM Today s Reality: The Rules of the Game Have Changed for Data Protection EXPLOSION OF DATA DATA EVERYWHERE
BULLETPROOF365 SECURING YOUR IT. Bulletproof365.com
 BULLETPROOF365 SECURING YOUR IT Bulletproof365.com INTRODUCING BULLETPROOF365 The world s leading productivity platform wrapped with industry-leading security, unmatched employee education and 24x7 IT
BULLETPROOF365 SECURING YOUR IT Bulletproof365.com INTRODUCING BULLETPROOF365 The world s leading productivity platform wrapped with industry-leading security, unmatched employee education and 24x7 IT
Bringing cyber to the Board of Directors & C-level and keeping it there. Dirk Lybaert, Proximus September 9 th 2016
 Bringing cyber to the Board of Directors & C-level and keeping it there Dirk Lybaert, Proximus September 9 th 2016 Dirk Lybaert Chief Group Corporate Affairs We constantly keep people connected to the
Bringing cyber to the Board of Directors & C-level and keeping it there Dirk Lybaert, Proximus September 9 th 2016 Dirk Lybaert Chief Group Corporate Affairs We constantly keep people connected to the
Effective Threat Modeling using TAM
 Effective Threat Modeling using TAM In my blog entry regarding Threat Analysis and Modeling (TAM) tool developed by (Application Consulting and Engineering) ACE, I have watched many more Threat Models
Effective Threat Modeling using TAM In my blog entry regarding Threat Analysis and Modeling (TAM) tool developed by (Application Consulting and Engineering) ACE, I have watched many more Threat Models
FireMon Security manager
 FireMon Security manager Regain control of firewalls with comprehensive firewall management The enterprise network is a complex machine. New network segments, new hosts and zero-day vulnerabilities are
FireMon Security manager Regain control of firewalls with comprehensive firewall management The enterprise network is a complex machine. New network segments, new hosts and zero-day vulnerabilities are
security FRAUD PREVENTION Business Checklist Safeguard your money, your credit and your good name.
 security FRAUD PREVENTION Business Checklist Safeguard your money, your credit and your good name. Security for Your Business Mitigating risk is a daily reality for business owners, but you don t have
security FRAUD PREVENTION Business Checklist Safeguard your money, your credit and your good name. Security for Your Business Mitigating risk is a daily reality for business owners, but you don t have
Guide to patching. Published 14 May 2017
 Published 14 May 2017 Copyright 2017 Health and Social Care Information Centre. The Health and Social Care Information Centre is a non-departmental body created by statute, also known as NHS Digital. How
Published 14 May 2017 Copyright 2017 Health and Social Care Information Centre. The Health and Social Care Information Centre is a non-departmental body created by statute, also known as NHS Digital. How
Securing Your Journey to the Cloud. CEO Eva Chen
 Securing Your Journey to the Cloud CEO Eva Chen Classification 8/10/2011 Copyright 2011 Trend Micro Inc. 1 Building Cloud Security Strategy Around IT 4 Pillars Virtualization & Network Mobile & Endpoint
Securing Your Journey to the Cloud CEO Eva Chen Classification 8/10/2011 Copyright 2011 Trend Micro Inc. 1 Building Cloud Security Strategy Around IT 4 Pillars Virtualization & Network Mobile & Endpoint
Microsoft Cloud & Datacenter Monitoring with System Center Operations Manager
 1800 ULEARN (853 276) www.ddls.com.au Microsoft 10964 - Cloud & Datacenter Monitoring with System Center Operations Manager Length 5 days Price $4290.00 (inc GST) Version C Overview This course equips
1800 ULEARN (853 276) www.ddls.com.au Microsoft 10964 - Cloud & Datacenter Monitoring with System Center Operations Manager Length 5 days Price $4290.00 (inc GST) Version C Overview This course equips
Five Essential Capabilities for Airtight Cloud Security
 Five Essential Capabilities for Airtight Cloud Security SECURITY IN THE CLOUD REQUIRES NEW CAPABILITIES It is no secret; security and compliance are at the top of the list of concerns tied to cloud adoption.
Five Essential Capabilities for Airtight Cloud Security SECURITY IN THE CLOUD REQUIRES NEW CAPABILITIES It is no secret; security and compliance are at the top of the list of concerns tied to cloud adoption.
Simplifying the Branch Network
 Simplifying the Branch Network By: Lee Doyle, Principal Analyst at Doyle Research Sponsored by Aruba, a Hewlett Packard Enterprise company Executive Summary A majority of IT organizations are experiencing
Simplifying the Branch Network By: Lee Doyle, Principal Analyst at Doyle Research Sponsored by Aruba, a Hewlett Packard Enterprise company Executive Summary A majority of IT organizations are experiencing
Converting CVT Account to Microsoft Account
 Email: Converting CVT Email Account to Microsoft Email Account If you need any assistance with this process, please contact us: Copper Valley Telecom Solutions Team 329 Fairbanks Drive, Valdez, AK 99686
Email: Converting CVT Email Account to Microsoft Email Account If you need any assistance with this process, please contact us: Copper Valley Telecom Solutions Team 329 Fairbanks Drive, Valdez, AK 99686
ForeScout CounterACT. Continuous Monitoring and Mitigation. Real-time Visibility. Network Access Control. Endpoint Compliance.
 Real-time Visibility Network Access Control Endpoint Compliance Mobile Security ForeScout CounterACT Continuous Monitoring and Mitigation Rapid Threat Response Benefits Rethink IT Security Security Do
Real-time Visibility Network Access Control Endpoint Compliance Mobile Security ForeScout CounterACT Continuous Monitoring and Mitigation Rapid Threat Response Benefits Rethink IT Security Security Do
Security for the real World NG IPS Jean-Paul Kerouanton Sourcefire, Inc.
 Security for the real World NG IPS Jean-Paul Kerouanton Sourcefire, Inc. Prepared for: Agenda Your Security Challenges About Sourcefire A New Approach How It Works Products & Services Questions & Next
Security for the real World NG IPS Jean-Paul Kerouanton Sourcefire, Inc. Prepared for: Agenda Your Security Challenges About Sourcefire A New Approach How It Works Products & Services Questions & Next
Overview... 3 Provisioning Sites for Security Awareness Training... 3 Understanding Phishing Simulations... 6 Understanding Types...
 Overview... 3 Provisioning Sites for Security Awareness Training... 3 Understanding Phishing Simulations... 6 Understanding Email Types... 6 Understanding Programs and Campaign Scheduling... 6 Welcome
Overview... 3 Provisioning Sites for Security Awareness Training... 3 Understanding Phishing Simulations... 6 Understanding Email Types... 6 Understanding Programs and Campaign Scheduling... 6 Welcome
Checklists for Advertising
 Checklists for Advertising Email Signature Link to your completed and most recent TREC IABS form, named properly according to size, above your name Link to document, one click away Link to your TREC Consumer
Checklists for Advertising Email Signature Link to your completed and most recent TREC IABS form, named properly according to size, above your name Link to document, one click away Link to your TREC Consumer
Insider Threat Detection Including review of 2017 SolarWinds Federal Cybersecurity Survey
 Insider Threat Detection Including review of 2017 SolarWinds Federal Cybersecurity Survey CyberMaryland Conference 2017 Bob Andersen, Sr. Manager Federal Sales Engineering robert.andersen@solarwinds.com
Insider Threat Detection Including review of 2017 SolarWinds Federal Cybersecurity Survey CyberMaryland Conference 2017 Bob Andersen, Sr. Manager Federal Sales Engineering robert.andersen@solarwinds.com
