CALIFORNIA SOFTWARE LABS
|
|
|
- Noreen Hampton
- 5 years ago
- Views:
Transcription
1 Real-time Implementation of NAT and Firewall in VxWorks CALIFORNIA SOFTWARE LABS R E A L I Z E Y O U R I D E A S California Software Labs 6800 Koll Center Parkway, Suite 100 Pleasanton CA 94566, USA. Phone (925) Fax (925) info@cswl.com
2 Real-time Implementation of NAT and Firewall in VxWorks A Technical Report Technical Expertise Level : Intermediate Requires knowledge of : C, TCP/IP Protocol, and VxWorks INDEX INTRODUCTION... 3 TCP/IP STACK IN VXWORKS... 3 WORKING OF THE VXWORKS' NETWORK STACK... 3 NAT AND FIREWALL IN VXWORKS... 5 NETWORK ADDRESS TRANSLATORS (NAT)... 5 HOW NAT WORKS?... 6 NETWORK ADDRESS PORT TRANSLATORS (NAPT)... 7 FIREWALL... 8 ADDING NAT AND FIREWALL TO THE TCP/IP STACK IN VXWORKS... 8 PACKET CAPTURING IN VXWORKS... 9 ETHERHOOK... 9 IPFILTERHOOK OUR SOLUTION TO NAT AND FIREWALL PACKET MANIPULATION FOR NAT AND FIREWALL CONCLUSION REFERENCES CSWL Inc, Pleasanton, California - 2 -
3 INTRODUCTION This paper details the concept of Network Address Translators (NAT) and firewalls and how they can be integrated in VxWorks. TCP/IP stack in VxWorks Wind River s real-time operating system, VxWorks comes with a full-featured, BSD 4.4-compliant TCP/IP stack. It has complete routing support and is scalable, so developers can build products ranging from IP routing devices to full TCP/IP, SNMP-managed systems. Figure below shows the layered architecture of TCP/IP stack. Figure-1 VxWorks TCP/IP stack Working of the VxWorks' network stack VxWorks allocates and initializes memory for the network stack at network initialization time. Out of this pre-allocated memory, the network stack uses the netbuflib routines to set up a memory pool. From this memory pool, the network stack gets the memory needed for data transfer. The netbuflib routines deal with data in terms of mblk structures, clblk structures and clusters. The mblk and clblk structures provide information necessary to CSWL Inc, Pleasanton, California - 3 -
4 manage the data stored in clusters. The clusters, which come in different sizes, contain the data described by the mblk and clblk structures. By default, the VxWorks network stack creates six pools for clusters ranging in size from 64 bytes to 2048 bytes. The mblk structure is the primary vehicle through which you can access data in a memory pool. Because, the mblk structure merely references the data, this lets network layers communicate data without actually having to copy the data. In addition, data can be chained using mblks. Thus, you can pass an arbitrarily large amount of data by passing the mblk at the head of an mblk chain. Figure 2 shows the presentation of 2 packets to the TCP layer. Figure-2 Presentation of two packets to the TCP layer CSWL Inc, Pleasanton, California - 4 -
5 To support chaining across multiple packets, the mblk structure contains two members that support chaining. One member points to the next mblk in the current packet. The other member points to the head mblk in the next packet if any. The clblk structure points to the cluster where the data is stored. NAT and Firewall in VxWorks The default TCP/IP stack that ships with VxWorks does not have firewalling and network address translation capabilities. However, these features can be plugged into an existing TCP/IP stack in VxWorks. Network Address Translators (NAT) One of the most compelling problems facing the IP Internet is the depletion of IP addresses. Though there had been various solutions to overcome this catastrophe, the most promising among them has been the concept of "address reuse". The address reuse solution is to place Network Address Translators (NAT) at the borders of stub domains. Each NAT box has a table consisting of pairs of local IP addresses and globally unique addresses. The IP addresses inside the stub domain are not globally unique. They are reused in other domains, thus solving the address depletion problem. The globally unique IP addresses are assigned according to current CIDR address allocation schemes. To set up a NAT, one need to define which is the "internal" and the external interface. The "internal" interface is the network adapter connected to the network with private IP addresses, which needs to be changed for communicating with the Internet. The "external" interface is configured with a valid private (globally unique) Internet address. CSWL Inc, Pleasanton, California - 5 -
6 For example, the internal interface might have an IP # of and be connected to the Ethernet, whilst the external interface might be a PPP connection with an IP number of How NAT works? NAT s basic operation is as follows: At each exit point between a stub domain and a backbone, NAT is installed. When a host from within the stub domain wishes to communicate with a machine in the Internet, the NAT translates the private IP address of the local machine to its globally unique IP address. In the scenario described in figure -3, when the local host sends a packet to a machine with the IP address , NAT replaces the source IP address in the packet ( ), with its globally unique IP address ( ) and transmits it. Since the source IP address has been modified in the packet, the response for this packet would be sent to the NAT. The NAT then replaces the destination IP address in the packet with the IP address of the local host and transmits the packet to the host in the stub domain. This address translation is totally transparent to the local host. CSWL Inc, Pleasanton, California - 6 -
7 Network Address Port Translators (NAPT) One of the drawbacks of the earlier solution is that the number of local machines that can be connected to the Internet simultaneously is limited to the availability of globally unique IP addresses in the NAT. To overcome this limitation, the NAT can be extended further to enable port translations as well, apart from address translations. This is known as masquerading or Network Address Port Translation (NAPT). In NAPT the port number of the local host in the TCP or UDP header is also translated before the packet is sent out of the stub domain to the Internet. Consider the following scenario. Machine Local Host A from the local stub domain having an IP address of sends a packet to a machine with as its IP address. Let us assume that the local machine uses port 1034 to initiate a TCP session with the machine at Hence the source port in the packet would be 1034 and the destination port number would be 80 (HTTP request). Similarly, another machine from the local stub domain, say Local Host B with the IP address initiates a TCP session to the machine at Let the port that this machine uses to initiate this session be Hence the source port in the packet would be 1500 and the destination port number would be 80. When the source address alone of both these packets is replaced with the unique IP address of the NAT ( ), an ambiguity would arise while mapping the response packets. The NAT would not be able to determine whether the response packet is destined for Local Host A or for Local Host B. CSWL Inc, Pleasanton, California - 7 -
8 To resolve this ambiguity, the source ports of the local machines are also translated before the packet is sent to the Internet. The port numbers that are used to replace the actual port numbers in the IP packet are unique for each session. In the above scenario, the port number of Local Host A could be changed from 1034 to say 5001 and that of Local Host B could be modified to When the NAT receives the response packets, it would be able to determine by checking the destination port number in the IP packet. If the destination port number is 5001, the NAT could conclude that the packet was actually destined for Local Host A. Whereas if the destination port number in the response packet was 5002, the NAT could map the packet to Local Host B by replacing the destination IP address and the destination port number to 1034(the port number used by Local Host B to initiate this session). Firewall Any device that controls network traffic for security reasons can be called a firewall. A firewall puts up a barrier that controls the flow of traffic between networks. The most basic firewalls are built on routers and work in the lower layers of the network protocol stack. Packets are first checked and then either dropped or allowed to enter based on various rules and specified criteria. Adding NAT and Firewall to the TCP/IP stack in VxWorks To add NAT and firewall to an existing TCP/IP stack in VxWorks, one should manipulate IP packets at the exit point between a local stub domain and the Internet. IP packets can be captured by hooking into the TCP/IP stack. The IP header and TCP/UDP headers can be stripped from the packet and checked against the firewall rules. Address translation needs to be performed on the packet before transmitting it to the Internet and before delivering it to the local network. CSWL Inc, Pleasanton, California - 8 -
9 Packet capturing in VxWorks VxWorks provides two hooks by which, we could capture packets in the network. These hooks are: EtherHook IpFilterHook VxWorks provides two libraries using which these hooks could be implemented. The EtherHook can be implemented using etherlib and the IpFilterHook can be implemented using ipfilterlib. EtherHook The EtherHook provides direct access to raw Ethernet packets. Incoming and outgoing packets can be examined or processed using the hooks etherinputhookadd() and etheroutputhookadd(). etherinputhookadd(): This function adds a routine to receive all Ethernet input packets. Synopsis: STATUS etherinputhookadd() ( FUNCPTR inputhook, /*Routine to receive Ethernet input packets*/ Char* pname, /*Name of device*/ Int uint /*unit of device*/ ) CSWL Inc, Pleasanton, California - 9 -
10 This routine adds a hook routine (inputhook) that will be called for every Ethernet packet that is received. The calling sequence of the input hook routine is: BOOL inputhook ( struct ifnet pif, /*interface packet was received on*/ char *buffer, /*received packet*/ int length /*length of received packet*/ ) etheroutputhookadd(): This function adds a routine to receive all Ethernet output packets. Synopsis STATUS etheroutputhookadd ( FUNCPTR outputhook /*routine to receive Ethernet output*/ ) This routine adds a hook (outputhook) and this function would be called for every Ethernet packet that is transmitted. This routine is immediately called immediately before transmission. The calling sequence of the output hook routine is: BOOL outputhook ( struct ifnet pif, /*interface packet will be sent on*/ CSWL Inc, Pleasanton, California
11 char *buffer, /* packet to transmit*/ int length /*length of packet to transmit*/ ) After the processing the Ethernet packet, both the hook routines should either return true or false. The hook should return true if it has handled the packet and no further action should be taken with it. It should return false if normal processing of the packet should take place. IpFilterHook The IpFilterHook provides direct access to IP packets. The input hook can be used to receive, examine and process raw IP packets that are part of IP (Internet Protocol) protocols. This hook can be added using the IpFilterHookAdd() function that is provided in the ipfilterlib library. ipfilterhookadd(): Synopsis STATUS ipfilterhookadd ( FUNCPTR IpFilterHook ) /*routine to receive raw ip packets*/ This routine adds a hook routine that will be called for every IP packet that is received. The filter hook function will be executed in the context of tnettask, which runs at priority 50. The calling sequence of the filter hook routine is: CSWL Inc, Pleasanton, California
12 BOOL IpFilterHook ( struct ifnet *pif, /*interface packet was received on*/ struct mbuf **pptrmbuf, /*pointer to pointer to an mbuf chain*/ struct ip **pptriphdr, /*pointer to pointer to IP header*/ int iphdrlen /* IP packet header length*/ ) The hook routine should return TRUE if it has handled the input packet and no further action should be taken with it. If returning TRUE the ipfilterhook is responsible for freeing the mbuf chain by calling m_freem(*pptrmbuf). If the IpFilterHook returns false, normal IP processing continues i.e., options processing, IP checksum computation etc. pptriphdr is a pointer to a pointer to a IP header. The pointer to the ip header is obtained by de-referencing pptriphdr. The ip header is used to examine and process the fields in the ip header. The fields ip_len, ip_id and ip_offset in the ip header are converted to the host byte order from the network byte order before a packet is handed to the filter hook. Our solution to NAT and Firewall Given the two possible solutions for NAT in VxWorks, our solution to NAT and firewall is by using the IpFilterHook. Why not EtherHook? There are a couple of disadvantages in using the ether hook. They are: Only certain VxWorks network drivers support ether hooks CSWL Inc, Pleasanton, California
13 Requires IP checksum adjustment: If ether hooks are used, the packet is manipulated below the IP layer. Hence the IP checksum has to be adjusted accordingly. This is not required if the ipfilterhook is used as the IP layer performs this IP checksum computation once the packet is returned to the IP stack from the hook routine. Packet manipulation for NAT and Firewall Once the hook routine gets the IP packet, the NAT should strip the IP header and the TCP/UDP headers from the packet. The protocol field in the IP header of the packet is used to determine whether it is a TCP or a UDP packet. Fire walling and address translation is performed based on the information obtained from the headers. The NAT uses a mapping table to perform address translations. Whenever a machine in the local network initiates a new session is initiated, the NAT dynamically adds a new entry to the mapping table. This entry is used to perform address translation A typical mapping table used for NAT would look like the following: NAT Mapping Table Real Src IP addr Real Src port Dest IP addr Dest port NAT IP addr NAT port Manipulating outgoing packets: Since the firewall rules are based on local IP numbers, outgoing packets are checked against the firewall rules before performing address translation. If the firewall rules allow the packet to be transmitted, the local IP address (private IP address) is replaced by the globally unique IP address of the NAT and the source CSWL Inc, Pleasanton, California
14 port number in the packet is replaced by a unique port number assigned by NAT for this session. The NAT first checks the mapping table to find an entry corresponding to this session. If such a mapping exists, the NAT replaces the source IP address and the source port number in the packet with the NAT IP address and the NAT port number specified in this mapping entry. If such a mapping is not available for this session, NAT creates one and uses it for address translation. Since the IP address and the source port number have been modified in the packet, the TCP/UDP checksum has to be recomputed accordingly. Manipulating incoming packets: For an incoming packet, address translation is done before checking it against the firewall rules. The NAT looks for an entry in the mapping table by comparing the destination IP, destination port, NAT IP and NAT port in the mapping table with the source IP, source port number, destination IP and destination port number in the IP packet. NAT replaces the destination IP address in the packet with the Real Src Ip addr entry and the destination port number with the Real Src port entry. Since the destination IP address and the port number have been modified, the TCP/UDP checksum is adjusted before sending the packet to the appropriate host in the local domain. CSWL Inc, Pleasanton, California
15 Conclusion Even though the Network stack in VxWorks lacks NAT and Firewall modules, we can add them using the filter hook. Our small footprint implementation of NAT and Firewall modules when tested performed well. References 1. RFC1631 The IP Network Address Translator (NAT) 2. RFC 791 Internet Protocol (IP) 3. RFC 793 Transmission Control Protocol (TCP) Copyright Notice: 2002 California Software Labs. All rights Reserved. The contents on the document are not to be reproduced or duplicated in any form or kind, either in part or full, without the written permission of California Software labs. Product and company names mentioned here in are the trademarks of their respective companies. CSWL Inc, Pleasanton, California
CALIFORNIA SOFTWARE LABS
 Using the JetSend SDK CALIFORNIA SOFTWARE LABS R E A L I Z E Y O U R I D E A S California Software Labs 6800 Koll Center Parkway, Suite 100 Pleasanton CA 94566, USA. Phone (925) 249 3000 Fax (925) 426
Using the JetSend SDK CALIFORNIA SOFTWARE LABS R E A L I Z E Y O U R I D E A S California Software Labs 6800 Koll Center Parkway, Suite 100 Pleasanton CA 94566, USA. Phone (925) 249 3000 Fax (925) 426
4. The transport layer
 4.1 The port number One of the most important information contained in the header of a segment are the destination and the source port numbers. The port numbers are necessary to identify the application
4.1 The port number One of the most important information contained in the header of a segment are the destination and the source port numbers. The port numbers are necessary to identify the application
Network Interconnection
 Network Interconnection Covers different approaches for ensuring border or perimeter security Computer Networking: A Top Down Approach 6 th edition Jim Kurose, Keith Ross Addison-Wesley March 2012 Lecture
Network Interconnection Covers different approaches for ensuring border or perimeter security Computer Networking: A Top Down Approach 6 th edition Jim Kurose, Keith Ross Addison-Wesley March 2012 Lecture
CALIFORNIA SOFTWARE LABS
 Wrapping Jini Services in ActiveX CALIFORNIA SOFTWARE LABS R E A L I Z E Y O U R I D E A S California Software Labs 6800 Koll Center Parkway, Suite 100 Pleasanton CA 94566, USA. Phone (925) 249 3000 Fax
Wrapping Jini Services in ActiveX CALIFORNIA SOFTWARE LABS R E A L I Z E Y O U R I D E A S California Software Labs 6800 Koll Center Parkway, Suite 100 Pleasanton CA 94566, USA. Phone (925) 249 3000 Fax
Teldat Router. NAT Feature
 Teldat Router NAT Feature Doc. DM520-I Rev. 8.40 October, 2000 INDEX Chapter 1 Introduction... 1 1. Introduction to NAT...2 2. Types of NAT...3 2.1. Static NAT...3 2.2. Dynamic NAT...3 2.3. NAPT (Masquerading)...4
Teldat Router NAT Feature Doc. DM520-I Rev. 8.40 October, 2000 INDEX Chapter 1 Introduction... 1 1. Introduction to NAT...2 2. Types of NAT...3 2.1. Static NAT...3 2.2. Dynamic NAT...3 2.3. NAPT (Masquerading)...4
Network Configuration Example
 Network Configuration Example Configuring Stateful NAT64 for Handling IPv4 Address Depletion Release NCE0030 Modified: 2017-01-23 Juniper Networks, Inc. 1133 Innovation Way Sunnyvale, California 94089
Network Configuration Example Configuring Stateful NAT64 for Handling IPv4 Address Depletion Release NCE0030 Modified: 2017-01-23 Juniper Networks, Inc. 1133 Innovation Way Sunnyvale, California 94089
TCP/IP Stack Introduction: Looking Under the Hood!
 TCP/IP Stack Introduction: Looking Under the Hood! Shiv Kalyanaraman shivkuma@ecse.rpi.edu http://www.ecse.rpi.edu/homepages/shivkuma 1 Example program 1. Create UDP datagram socket; fill in server address
TCP/IP Stack Introduction: Looking Under the Hood! Shiv Kalyanaraman shivkuma@ecse.rpi.edu http://www.ecse.rpi.edu/homepages/shivkuma 1 Example program 1. Create UDP datagram socket; fill in server address
Use this section to help you quickly locate a command.
 iii iv v Use this section to help you quickly locate a command. vi Use this list to help you locate examples you d like to try or look at. vii viii This document describes the various deployment, installation,
iii iv v Use this section to help you quickly locate a command. vi Use this list to help you locate examples you d like to try or look at. vii viii This document describes the various deployment, installation,
NAT Support for Multiple Pools Using Route Maps
 NAT Support for Multiple Pools Using Route Maps Document ID: 13739 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Access List Approach Host 1 to Host
NAT Support for Multiple Pools Using Route Maps Document ID: 13739 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Access List Approach Host 1 to Host
Lecture 8. Network Layer (cont d) Network Layer 1-1
 Lecture 8 Network Layer (cont d) Network Layer 1-1 Agenda The Network Layer (cont d) What is inside a router Internet Protocol (IP) IPv4 fragmentation and addressing IP Address Classes and Subnets Network
Lecture 8 Network Layer (cont d) Network Layer 1-1 Agenda The Network Layer (cont d) What is inside a router Internet Protocol (IP) IPv4 fragmentation and addressing IP Address Classes and Subnets Network
Network Configuration Example
 Network Configuration Example Configuring Dual-Stack Lite for IPv6 Access Release NCE0025 Modified: 2016-10-12 Juniper Networks, Inc. 1133 Innovation Way Sunnyvale, California 94089 USA 408-745-2000 www.juniper.net
Network Configuration Example Configuring Dual-Stack Lite for IPv6 Access Release NCE0025 Modified: 2016-10-12 Juniper Networks, Inc. 1133 Innovation Way Sunnyvale, California 94089 USA 408-745-2000 www.juniper.net
Lecture 3. The Network Layer (cont d) Network Layer 1-1
 Lecture 3 The Network Layer (cont d) Network Layer 1-1 Agenda The Network Layer (cont d) What is inside a router? Internet Protocol (IP) IPv4 fragmentation and addressing IP Address Classes and Subnets
Lecture 3 The Network Layer (cont d) Network Layer 1-1 Agenda The Network Layer (cont d) What is inside a router? Internet Protocol (IP) IPv4 fragmentation and addressing IP Address Classes and Subnets
6.6. Wind River Network Stack for VxWorks 6. PROGRAMMER'S GUIDE Volume 3: Interfaces and Drivers
 Wind River Network Stack for VxWorks 6 Programmer's Guide, 6.6 Wind River Network Stack for VxWorks 6 PROGRAMMER'S GUIDE Volume 3: Interfaces and Drivers 6.6 Copyright 2007 Wind River Systems, Inc. All
Wind River Network Stack for VxWorks 6 Programmer's Guide, 6.6 Wind River Network Stack for VxWorks 6 PROGRAMMER'S GUIDE Volume 3: Interfaces and Drivers 6.6 Copyright 2007 Wind River Systems, Inc. All
Configuring NAT for IP Address Conservation
 This module describes how to configure Network Address Translation (NAT) for IP address conservation and how to configure inside and outside source addresses. This module also provides information about
This module describes how to configure Network Address Translation (NAT) for IP address conservation and how to configure inside and outside source addresses. This module also provides information about
AppNote-124 Adding "Flow Control" to an END or NPT type network driver
 Adding "Flow Control" to an END or NPT type network driver Adding "Flow Control" to a non-wind River supplied END or NPT network driver to prevent unrecoverable loss of network communication in a heavy
Adding "Flow Control" to an END or NPT type network driver Adding "Flow Control" to a non-wind River supplied END or NPT network driver to prevent unrecoverable loss of network communication in a heavy
Finding Feature Information
 This module describes how to configure Network Address Translation (NAT) for IP address conservation and how to configure inside and outside source addresses. This module also provides information about
This module describes how to configure Network Address Translation (NAT) for IP address conservation and how to configure inside and outside source addresses. This module also provides information about
CS 356: Computer Network Architectures. Lecture 15: DHCP, NAT, and IPv6. [PD] chapter 3.2.7, 3.2.9, 4.1.3, 4.3.3
![CS 356: Computer Network Architectures. Lecture 15: DHCP, NAT, and IPv6. [PD] chapter 3.2.7, 3.2.9, 4.1.3, 4.3.3 CS 356: Computer Network Architectures. Lecture 15: DHCP, NAT, and IPv6. [PD] chapter 3.2.7, 3.2.9, 4.1.3, 4.3.3](/thumbs/79/79922395.jpg) CS 356: Computer Network Architectures Lecture 15: DHCP, NAT, and IPv6 [PD] chapter 3.2.7, 3.2.9, 4.1.3, 4.3.3 Xiaowei Yang xwy@cs.duke.edu Dynamic Host Configuration Protocol (DHCP) Dynamic Assignment
CS 356: Computer Network Architectures Lecture 15: DHCP, NAT, and IPv6 [PD] chapter 3.2.7, 3.2.9, 4.1.3, 4.3.3 Xiaowei Yang xwy@cs.duke.edu Dynamic Host Configuration Protocol (DHCP) Dynamic Assignment
TCP/IP and the OSI Model
 TCP/IP BASICS TCP/IP and the OSI Model TCP/IP BASICS The network protocol of the Internet Composed of six main protocols IP Internet Protocol UDP User Datagram Protocol TCP Transmission Control Protocol
TCP/IP BASICS TCP/IP and the OSI Model TCP/IP BASICS The network protocol of the Internet Composed of six main protocols IP Internet Protocol UDP User Datagram Protocol TCP Transmission Control Protocol
Network Address Translation
 Claudio Cicconetti International Master on Communication Networks Engineering 2006/2007 Network Address Translation (NAT) basically provides a mapping between internal (i.e.,
Claudio Cicconetti International Master on Communication Networks Engineering 2006/2007 Network Address Translation (NAT) basically provides a mapping between internal (i.e.,
Networking Potpourri: Plug-n-Play, Next Gen
 Networking Potpourri: Plug-n-Play, Next Gen 14-740: Fundamentals of Computer Networks Bill Nace Material from Computer Networking: A Top Down Approach, 6 th edition. J.F. Kurose and K.W. Ross Administrivia
Networking Potpourri: Plug-n-Play, Next Gen 14-740: Fundamentals of Computer Networks Bill Nace Material from Computer Networking: A Top Down Approach, 6 th edition. J.F. Kurose and K.W. Ross Administrivia
Interconnecting Networks with TCP/IP. 2000, Cisco Systems, Inc. 8-1
 Interconnecting Networks with TCP/IP 2000, Cisco Systems, Inc. 8-1 Objectives Upon completion of this chapter you will be able to perform the following tasks: Identify the IP protocol stack, its protocol
Interconnecting Networks with TCP/IP 2000, Cisco Systems, Inc. 8-1 Objectives Upon completion of this chapter you will be able to perform the following tasks: Identify the IP protocol stack, its protocol
IPv4 addressing, NAT. Computer Networking: A Top Down Approach 6 th edition Jim Kurose, Keith Ross Addison-Wesley.
 IPv4 addressing, NAT http://xkcd.com/195/ Computer Networking: A Top Down Approach 6 th edition Jim Kurose, Keith Ross Addison-Wesley Some materials copyright 1996-2012 J.F Kurose and K.W. Ross, All Rights
IPv4 addressing, NAT http://xkcd.com/195/ Computer Networking: A Top Down Approach 6 th edition Jim Kurose, Keith Ross Addison-Wesley Some materials copyright 1996-2012 J.F Kurose and K.W. Ross, All Rights
Internetworking/Internetteknik, Examination 2G1305 Date: August 18 th 2004 at 9:00 13:00 SOLUTIONS
 Internetworking/Internetteknik, Examination 2G1305 Date: August 18 th 2004 at 9:00 13:00 SOLUTIONS 1. General (5p) a) The so-called hourglass model (sometimes referred to as a wine-glass ) has been used
Internetworking/Internetteknik, Examination 2G1305 Date: August 18 th 2004 at 9:00 13:00 SOLUTIONS 1. General (5p) a) The so-called hourglass model (sometimes referred to as a wine-glass ) has been used
Table of Contents. Cisco How NAT Works
 Table of Contents How NAT Works...1 This document contains Flash animation...1 Introduction...1 Behind the Mask...2 Dynamic NAT and Overloading Examples...5 Security and Administration...7 Multi Homing...9
Table of Contents How NAT Works...1 This document contains Flash animation...1 Introduction...1 Behind the Mask...2 Dynamic NAT and Overloading Examples...5 Security and Administration...7 Multi Homing...9
NAT Router Performance Evaluation
 University of Aizu, Graduation Thesis. Mar, 22 17173 1 NAT Performance Evaluation HAYASHI yu-ichi 17173 Supervised by Atsushi Kara Abstract This thesis describes a quantitative analysis of NAT routers
University of Aizu, Graduation Thesis. Mar, 22 17173 1 NAT Performance Evaluation HAYASHI yu-ichi 17173 Supervised by Atsushi Kara Abstract This thesis describes a quantitative analysis of NAT routers
APPENDIX F THE TCP/IP PROTOCOL ARCHITECTURE
 APPENDIX F THE TCP/IP PROTOCOL ARCHITECTURE William Stallings F.1 TCP/IP LAYERS... 2 F.2 TCP AND UDP... 4 F.3 OPERATION OF TCP/IP... 6 F.4 TCP/IP APPLICATIONS... 10 Copyright 2014 Supplement to Computer
APPENDIX F THE TCP/IP PROTOCOL ARCHITECTURE William Stallings F.1 TCP/IP LAYERS... 2 F.2 TCP AND UDP... 4 F.3 OPERATION OF TCP/IP... 6 F.4 TCP/IP APPLICATIONS... 10 Copyright 2014 Supplement to Computer
Datagram. Source IP address. Destination IP address. Options. Data
 Datagram Version H. len Service Datagram length Datagram identifier FR-FR FR-FR-FR-FR Time-to-live Transp. prot. H. Checksum Source IP address Destination IP address Options Data Each line represents a
Datagram Version H. len Service Datagram length Datagram identifier FR-FR FR-FR-FR-FR Time-to-live Transp. prot. H. Checksum Source IP address Destination IP address Options Data Each line represents a
Network Layer PREPARED BY AHMED ABDEL-RAOUF
 Network Layer PREPARED BY AHMED ABDEL-RAOUF Network layer transport segment from sending to receiving host on sending side encapsulates segments into datagrams on receiving side, delivers segments to transport
Network Layer PREPARED BY AHMED ABDEL-RAOUF Network layer transport segment from sending to receiving host on sending side encapsulates segments into datagrams on receiving side, delivers segments to transport
CALIFORNIA SOFTWARE LABS
 Blocking TCP requests on an Ethernet Network for Bandwidth Control CALIFORNIA SOFTWARE LABS R E A L I Z E Y O U R I D E A S California Software Labs 6800 Koll Center Parkway, Suite 100 Pleasanton CA 94566,
Blocking TCP requests on an Ethernet Network for Bandwidth Control CALIFORNIA SOFTWARE LABS R E A L I Z E Y O U R I D E A S California Software Labs 6800 Koll Center Parkway, Suite 100 Pleasanton CA 94566,
Lab10: NATing. addressing conflicts, routers must never route private IP addresses.
 Introduction These are reserved private Internet addresses drawn from the three blocks shown in the figure. These addresses are for private, internal network use only. Packets containing these addresses
Introduction These are reserved private Internet addresses drawn from the three blocks shown in the figure. These addresses are for private, internal network use only. Packets containing these addresses
Network Address Translation. All you want to know about
 Network Address Translation All you want to know about (C) Herbert Haas 2005/03/11 Reasons for NAT Mitigate Internet address depletion Save global addresses (and money) Conserve internal address plan TCP
Network Address Translation All you want to know about (C) Herbert Haas 2005/03/11 Reasons for NAT Mitigate Internet address depletion Save global addresses (and money) Conserve internal address plan TCP
CS 356: Computer Network Architectures. Lecture 14: Switching hardware, IP auxiliary functions, and midterm review. [PD] chapter 3.4.1, 3.2.
![CS 356: Computer Network Architectures. Lecture 14: Switching hardware, IP auxiliary functions, and midterm review. [PD] chapter 3.4.1, 3.2. CS 356: Computer Network Architectures. Lecture 14: Switching hardware, IP auxiliary functions, and midterm review. [PD] chapter 3.4.1, 3.2.](/thumbs/85/92708725.jpg) CS 356: Computer Network Architectures Lecture 14: Switching hardware, IP auxiliary functions, and midterm review [PD] chapter 3.4.1, 3.2.7 Xiaowei Yang xwy@cs.duke.edu Switching hardware Software switch
CS 356: Computer Network Architectures Lecture 14: Switching hardware, IP auxiliary functions, and midterm review [PD] chapter 3.4.1, 3.2.7 Xiaowei Yang xwy@cs.duke.edu Switching hardware Software switch
CS 4390 Computer Networks. Transport Services and Protocols
 CS 4390 Computer Networks UT D data Session 07 Transport Layer Overview and UDP Adapted from Computer Networking a Top-Down Approach 1996-2012 by J.F Kurose and K.W. Ross, All Rights Reserved Transport
CS 4390 Computer Networks UT D data Session 07 Transport Layer Overview and UDP Adapted from Computer Networking a Top-Down Approach 1996-2012 by J.F Kurose and K.W. Ross, All Rights Reserved Transport
ipro-04n Security Configuration Guide
 Disclaimer: The contents of these notes does not specifically relate to any release of Firmware and may change without notice Status: uncontrolled 1 Introduction...5 2 Security package...6 2.1 Basic network
Disclaimer: The contents of these notes does not specifically relate to any release of Firmware and may change without notice Status: uncontrolled 1 Introduction...5 2 Security package...6 2.1 Basic network
Computer Network Fundamentals Spring Week 4 Network Layer Andreas Terzis
 Computer Network Fundamentals Spring 2008 Week 4 Network Layer Andreas Terzis Outline Internet Protocol Service Model Addressing Original addressing scheme Subnetting CIDR Fragmentation ICMP Address Shortage
Computer Network Fundamentals Spring 2008 Week 4 Network Layer Andreas Terzis Outline Internet Protocol Service Model Addressing Original addressing scheme Subnetting CIDR Fragmentation ICMP Address Shortage
CS 348 Computer Networks. IP and Routing. Indian Institute of Technology, Bombay
 Computer Networks IP and Routing Network Interconnections Data Link Layer Delivery of frames on the same LAN Extend reach using switches/bridges and hubs Limitations Solution? Cannot address heterogeniety
Computer Networks IP and Routing Network Interconnections Data Link Layer Delivery of frames on the same LAN Extend reach using switches/bridges and hubs Limitations Solution? Cannot address heterogeniety
CS 520: Network Architecture I Winter Lecture 11: NAT and IPv6
 CS 520: Network Architecture I Winter 2007 Lecture 11: NAT and IPv6 The previous lecture discussed how subnetting and supernetting (CIDR) can be used to make better use of global IP addresses. This lecture
CS 520: Network Architecture I Winter 2007 Lecture 11: NAT and IPv6 The previous lecture discussed how subnetting and supernetting (CIDR) can be used to make better use of global IP addresses. This lecture
CSC 474/574 Information Systems Security
 CSC 474/574 Information Systems Security Topic 7.4 Firewalls CSC 474/574 Dr. Peng Ning 1 Outline What are firewalls? Types Filtering Packet filtering Session filtering Proxy Circuit Level Application Level
CSC 474/574 Information Systems Security Topic 7.4 Firewalls CSC 474/574 Dr. Peng Ning 1 Outline What are firewalls? Types Filtering Packet filtering Session filtering Proxy Circuit Level Application Level
Chapter 3. Internet Protocol Layer
 Chapter 3 Internet Protocol Layer Problem Statement The Internet protocol (IP) layer provides a host-to-host transmission service. In order to provide the host-to-host service, how to connect millions
Chapter 3 Internet Protocol Layer Problem Statement The Internet protocol (IP) layer provides a host-to-host transmission service. In order to provide the host-to-host service, how to connect millions
IP Addressing: Fragmentation and Reassembly Configuration Guide
 First Published: December 05, 2012 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387) Fax: 408 527-0883
First Published: December 05, 2012 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387) Fax: 408 527-0883
ACL Rule Configuration on the WAP371
 Article ID: 5089 ACL Rule Configuration on the WAP371 Objective A network access control list (ACL) is an optional layer of security that acts as a firewall for controlling traffic in and out of a subnet.
Article ID: 5089 ACL Rule Configuration on the WAP371 Objective A network access control list (ACL) is an optional layer of security that acts as a firewall for controlling traffic in and out of a subnet.
H3C SecPath Series High-End Firewalls
 H3C SecPath Series High-End Firewalls NAT and ALG Configuration Guide Hangzhou H3C Technologies Co., Ltd. http://www.h3c.com Software version: SECPATHF1000SAI&F1000AEI&F1000ESI-CMW520-R3721 SECPATH5000FA-CMW520-F3210
H3C SecPath Series High-End Firewalls NAT and ALG Configuration Guide Hangzhou H3C Technologies Co., Ltd. http://www.h3c.com Software version: SECPATHF1000SAI&F1000AEI&F1000ESI-CMW520-R3721 SECPATH5000FA-CMW520-F3210
1-1. Switching Networks (Fall 2010) EE 586 Communication and. October 25, Lecture 24
 EE 586 Communication and Switching Networks (Fall 2010) Lecture 24 October 25, 2010 1-1 Announcements Midterm 1: Mean = 92.2 Stdev = 8 Still grading your programs (sorry about the delay) Network Layer
EE 586 Communication and Switching Networks (Fall 2010) Lecture 24 October 25, 2010 1-1 Announcements Midterm 1: Mean = 92.2 Stdev = 8 Still grading your programs (sorry about the delay) Network Layer
Transport Layer. The transport layer is responsible for the delivery of a message from one process to another. RSManiaol
 Transport Layer Transport Layer The transport layer is responsible for the delivery of a message from one process to another Types of Data Deliveries Client/Server Paradigm An application program on the
Transport Layer Transport Layer The transport layer is responsible for the delivery of a message from one process to another Types of Data Deliveries Client/Server Paradigm An application program on the
The TCP Protocol Stack
 The TCP Protocol Stack Michael Brockway February 16, 2018 Introduction - Layered archtecture Networking software is desgined in a layered fashion The bottom layer is the services offered by the underlying
The TCP Protocol Stack Michael Brockway February 16, 2018 Introduction - Layered archtecture Networking software is desgined in a layered fashion The bottom layer is the services offered by the underlying
CSC 4900 Computer Networks: Network Layer
 CSC 4900 Computer Networks: Network Layer Professor Henry Carter Fall 2017 Chapter 4: Network Layer 4. 1 Introduction 4.2 What s inside a router 4.3 IP: Internet Protocol Datagram format 4.4 Generalized
CSC 4900 Computer Networks: Network Layer Professor Henry Carter Fall 2017 Chapter 4: Network Layer 4. 1 Introduction 4.2 What s inside a router 4.3 IP: Internet Protocol Datagram format 4.4 Generalized
Grandstream Networks, Inc. GWN Firewall Features Advanced NAT Configuration Guide
 Grandstream Networks, Inc. GWN7000 - Firewall Features Advanced NAT Configuration Guide Table of Content INTRODUCTION... 3 INPUT/OUPUT POLICIES... 4 Overview... 4 Configuration... 4 SNAT (SOURCE NAT)...
Grandstream Networks, Inc. GWN7000 - Firewall Features Advanced NAT Configuration Guide Table of Content INTRODUCTION... 3 INPUT/OUPUT POLICIES... 4 Overview... 4 Configuration... 4 SNAT (SOURCE NAT)...
Internet Security: Firewall
 Internet Security: Firewall What is a Firewall firewall = wall to protect against fire propagation More like a moat around a medieval castle restricts entry to carefully controlled points restricts exits
Internet Security: Firewall What is a Firewall firewall = wall to protect against fire propagation More like a moat around a medieval castle restricts entry to carefully controlled points restricts exits
CMPE 80N: Introduction to Networking and the Internet
 CMPE 80N: Introduction to Networking and the Internet Katia Obraczka Computer Engineering UCSC Baskin Engineering Lecture 17 CMPE 80N Spring'10 1 Announcements Next class: Presentation of fun projects
CMPE 80N: Introduction to Networking and the Internet Katia Obraczka Computer Engineering UCSC Baskin Engineering Lecture 17 CMPE 80N Spring'10 1 Announcements Next class: Presentation of fun projects
EC441 Fall 2018 Introduction to Computer Networking Chapter4: Network Layer Data Plane
 EC441 Fall 2018 Introduction to Computer Networking Chapter4: Network Layer Data Plane This presentation is adapted from slides produced by Jim Kurose and Keith Ross for their book, Computer Networking:
EC441 Fall 2018 Introduction to Computer Networking Chapter4: Network Layer Data Plane This presentation is adapted from slides produced by Jim Kurose and Keith Ross for their book, Computer Networking:
1/18/13. Network+ Guide to Networks 5 th Edition. Objectives. Chapter 10 In-Depth TCP/IP Networking
 Network+ Guide to Networks 5 th Edition Chapter 10 In-Depth TCP/IP Networking Objectives Understand methods of network design unique to TCP/IP networks, including subnetting, CIDR, and address translation
Network+ Guide to Networks 5 th Edition Chapter 10 In-Depth TCP/IP Networking Objectives Understand methods of network design unique to TCP/IP networks, including subnetting, CIDR, and address translation
Politecnico di Milano Scuola di Ingegneria Industriale e dell Informazione. 09 Intranetting. Fundamentals of Communication Networks
 Politecnico di Milano Scuola di Ingegneria Industriale e dell Informazione 09 Intranetting Fundamentals of Communication Networks 1 Private networks and Intranets EG subnet IG IG Private network IG o Private
Politecnico di Milano Scuola di Ingegneria Industriale e dell Informazione 09 Intranetting Fundamentals of Communication Networks 1 Private networks and Intranets EG subnet IG IG Private network IG o Private
Prof. Bill Buchanan Room: C.63
 Wireless LAN CO72047 Unit 7: Filtering Prof. Bill Buchanan Contact: w.buchanan@napier.ac.uk Room: C.63 Telephone: X2759 MSN Messenger: w_j_buchanan@hotmail.com WWW: http://www.dcs.napier.ac.uk/~bill http://buchananweb.co.uk
Wireless LAN CO72047 Unit 7: Filtering Prof. Bill Buchanan Contact: w.buchanan@napier.ac.uk Room: C.63 Telephone: X2759 MSN Messenger: w_j_buchanan@hotmail.com WWW: http://www.dcs.napier.ac.uk/~bill http://buchananweb.co.uk
HP A-F1000-A-EI_A-F1000-S-EI VPN Firewalls
 HP A-F1000-A-EI_A-F1000-S-EI VPN Firewalls NAT Configuration Guide Part number:5998-2649 Document version: 6PW100-20110909 Legal and notice information Copyright 2011 Hewlett-Packard Development Company,
HP A-F1000-A-EI_A-F1000-S-EI VPN Firewalls NAT Configuration Guide Part number:5998-2649 Document version: 6PW100-20110909 Legal and notice information Copyright 2011 Hewlett-Packard Development Company,
The Internet. 9.1 Introduction. The Internet is a global network that supports a variety of interpersonal and interactive multimedia applications.
 The Internet 9.1 Introduction The Internet is a global network that supports a variety of interpersonal and interactive multimedia applications. Associated with each access network - ISP network, intranet,
The Internet 9.1 Introduction The Internet is a global network that supports a variety of interpersonal and interactive multimedia applications. Associated with each access network - ISP network, intranet,
Networking interview questions
 Networking interview questions What is LAN? LAN is a computer network that spans a relatively small area. Most LANs are confined to a single building or group of buildings. However, one LAN can be connected
Networking interview questions What is LAN? LAN is a computer network that spans a relatively small area. Most LANs are confined to a single building or group of buildings. However, one LAN can be connected
BIG-IP Local Traffic Management: Basics. Version 12.1
 BIG-IP Local Traffic Management: Basics Version 12.1 Table of Contents Table of Contents Introduction to Local Traffic Management...7 About local traffic management...7 About the network map...7 Viewing
BIG-IP Local Traffic Management: Basics Version 12.1 Table of Contents Table of Contents Introduction to Local Traffic Management...7 About local traffic management...7 About the network map...7 Viewing
Networks. Other Matters: draft Assignment 2 up (Labs 7 & 8 v. important!!) Ref: [Coulouris&al Ch 3, 4] network performance and principles
![Networks. Other Matters: draft Assignment 2 up (Labs 7 & 8 v. important!!) Ref: [Coulouris&al Ch 3, 4] network performance and principles Networks. Other Matters: draft Assignment 2 up (Labs 7 & 8 v. important!!) Ref: [Coulouris&al Ch 3, 4] network performance and principles](/thumbs/86/94947115.jpg) Networks Other Matters: draft Assignment 2 up (Labs 7 & 8 v. important!!) Ref: [Coulouris&al Ch 3, 4] network performance and principles OSI protocol; routing TCP/IP layers and packet organization IP addresses
Networks Other Matters: draft Assignment 2 up (Labs 7 & 8 v. important!!) Ref: [Coulouris&al Ch 3, 4] network performance and principles OSI protocol; routing TCP/IP layers and packet organization IP addresses
Network layer: Overview. Network layer functions IP Routing and forwarding NAT ARP IPv6 Routing
 Network layer: Overview Network layer functions IP Routing and forwarding NAT ARP IPv6 Routing 1 Network Layer Functions Transport packet from sending to receiving hosts Network layer protocols in every
Network layer: Overview Network layer functions IP Routing and forwarding NAT ARP IPv6 Routing 1 Network Layer Functions Transport packet from sending to receiving hosts Network layer protocols in every
! encor e networks TM
 ! encor e networks TM Revision A, May 2004 Document Part Number 15737.0001 Copyright 2004 Encore Networks, Inc. All rights reserved. VSR-30 Installation Guide for ELIOS Software Version 0500 T his guide
! encor e networks TM Revision A, May 2004 Document Part Number 15737.0001 Copyright 2004 Encore Networks, Inc. All rights reserved. VSR-30 Installation Guide for ELIOS Software Version 0500 T his guide
440GX Application Note
 Overview of TCP/IP Acceleration Hardware January 22, 2008 Introduction Modern interconnect technology offers Gigabit/second (Gb/s) speed that has shifted the bottleneck in communication from the physical
Overview of TCP/IP Acceleration Hardware January 22, 2008 Introduction Modern interconnect technology offers Gigabit/second (Gb/s) speed that has shifted the bottleneck in communication from the physical
Create New Virtual Hub window.
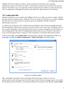 SoftEther VPN Server makes it possible to create a plurality of Virtual Hubs, and to separate administration objects and VPN session layer 2 communication between each Virtual Hub. This manual explains
SoftEther VPN Server makes it possible to create a plurality of Virtual Hubs, and to separate administration objects and VPN session layer 2 communication between each Virtual Hub. This manual explains
Network layer: Overview. Network Layer Functions
 Network layer: Overview Network layer functions IP Routing and forwarding NAT ARP IPv6 Routing 1 Network Layer Functions Transport packet from sending to receiving hosts Network layer protocols in every
Network layer: Overview Network layer functions IP Routing and forwarding NAT ARP IPv6 Routing 1 Network Layer Functions Transport packet from sending to receiving hosts Network layer protocols in every
W is a Firewall. Internet Security: Firewall. W a Firewall can Do. firewall = wall to protect against fire propagation
 W is a Firewall firewall = wall to protect against fire propagation Internet Security: Firewall More like a moat around a medieval castle restricts entry to carefully controlled points restricts exits
W is a Firewall firewall = wall to protect against fire propagation Internet Security: Firewall More like a moat around a medieval castle restricts entry to carefully controlled points restricts exits
Mike Anderson. TCP/IP in Embedded Systems. CTO/Chief Scientist The PTR Group, Inc.
 TCP/IP in Embedded Systems Mike Anderson CTO/Chief Scientist The PTR Group, Inc. RTC/GB-1 What We ll Talk About Networking 101 Stacks Protocols Routing Drivers Embedded Stacks Porting RTC/GB-2 Connected
TCP/IP in Embedded Systems Mike Anderson CTO/Chief Scientist The PTR Group, Inc. RTC/GB-1 What We ll Talk About Networking 101 Stacks Protocols Routing Drivers Embedded Stacks Porting RTC/GB-2 Connected
Introduction p. 1 The Need for Security p. 2 Public Network Threats p. 2 Private Network Threats p. 4 The Role of Routers p. 5 Other Security Devices
 Preface p. xv Acknowledgments p. xvii Introduction p. 1 The Need for Security p. 2 Public Network Threats p. 2 Private Network Threats p. 4 The Role of Routers p. 5 Other Security Devices p. 6 Firewall
Preface p. xv Acknowledgments p. xvii Introduction p. 1 The Need for Security p. 2 Public Network Threats p. 2 Private Network Threats p. 4 The Role of Routers p. 5 Other Security Devices p. 6 Firewall
internet technologies and standards
 Institute of Telecommunications Warsaw University of Technology 2017 internet technologies and standards Piotr Gajowniczek Andrzej Bąk Michał Jarociński Network Layer The majority of slides presented in
Institute of Telecommunications Warsaw University of Technology 2017 internet technologies and standards Piotr Gajowniczek Andrzej Bąk Michał Jarociński Network Layer The majority of slides presented in
Network Layer: Internet Protocol
 Network Layer: Internet Protocol Motivation Heterogeneity Scale Intering IP is the glue that connects heterogeneous s giving the illusion of a homogenous one. Salient Features Each host is identified by
Network Layer: Internet Protocol Motivation Heterogeneity Scale Intering IP is the glue that connects heterogeneous s giving the illusion of a homogenous one. Salient Features Each host is identified by
CS-435 spring semester Network Technology & Programming Laboratory. Stefanos Papadakis & Manolis Spanakis
 CS-435 spring semester 2016 Network Technology & Programming Laboratory University of Crete Computer Science Department Stefanos Papadakis & Manolis Spanakis CS-435 Lecture #4 preview ICMP ARP DHCP NAT
CS-435 spring semester 2016 Network Technology & Programming Laboratory University of Crete Computer Science Department Stefanos Papadakis & Manolis Spanakis CS-435 Lecture #4 preview ICMP ARP DHCP NAT
Firewalls. October 13, 2017
 Firewalls October 13, 2017 Administrative submittal instructions answer the lab assignment s questions in written report form, as a text, pdf, or Word document file (no obscure formats please) email to
Firewalls October 13, 2017 Administrative submittal instructions answer the lab assignment s questions in written report form, as a text, pdf, or Word document file (no obscure formats please) email to
How to Make the Client IP Address Available to the Back-end Server
 How to Make the Client IP Address Available to the Back-end Server For Layer 4 - UDP and Layer 4 - TCP services, the actual client IP address is passed to the server in the TCP header. No further configuration
How to Make the Client IP Address Available to the Back-end Server For Layer 4 - UDP and Layer 4 - TCP services, the actual client IP address is passed to the server in the TCP header. No further configuration
Appendix B Policies and Filters
 Appendix B Policies and Filters NOTE: This appendix does not describe Access Control Lists (ACLs) or IPX SAP ACLs, which are additional methods for filtering packets. See Software-Based IP Access Control
Appendix B Policies and Filters NOTE: This appendix does not describe Access Control Lists (ACLs) or IPX SAP ACLs, which are additional methods for filtering packets. See Software-Based IP Access Control
User Datagram Protocol(UDP)
 User Datagram Protocol(UDP) UDP is a connectionless protocol. There is no mechanism for ensuring that data sent is received by the destination. Hence, it is an unreliable protocol. A unit of data sent
User Datagram Protocol(UDP) UDP is a connectionless protocol. There is no mechanism for ensuring that data sent is received by the destination. Hence, it is an unreliable protocol. A unit of data sent
IP Addressing: Fragmentation and Reassembly Configuration Guide, Cisco IOS XE Release 3S (Cisco ASR 1000)
 IP Addressing: Fragmentation and Reassembly Configuration Guide, Cisco IOS XE Release 3S (Cisco ASR 1000) Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com
IP Addressing: Fragmentation and Reassembly Configuration Guide, Cisco IOS XE Release 3S (Cisco ASR 1000) Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com
Introduction to TCP/IP networking
 Introduction to TCP/IP networking TCP/IP protocol family IP : Internet Protocol UDP : User Datagram Protocol RTP, traceroute TCP : Transmission Control Protocol HTTP, FTP, ssh What is an internet? A set
Introduction to TCP/IP networking TCP/IP protocol family IP : Internet Protocol UDP : User Datagram Protocol RTP, traceroute TCP : Transmission Control Protocol HTTP, FTP, ssh What is an internet? A set
CSC 401 Data and Computer Communications Networks
 CSC 401 Data and Computer Communications Networks Link Layer, Switches, VLANS, MPLS, Data Centers Sec 6.4 to 6.7 Prof. Lina Battestilli Fall 2017 Chapter 6 Outline Link layer and LANs: 6.1 introduction,
CSC 401 Data and Computer Communications Networks Link Layer, Switches, VLANS, MPLS, Data Centers Sec 6.4 to 6.7 Prof. Lina Battestilli Fall 2017 Chapter 6 Outline Link layer and LANs: 6.1 introduction,
Configuring Network Address Translation
 Finding Feature Information, on page 1 Network Address Translation (NAT), on page 2 Benefits of Configuring NAT, on page 2 How NAT Works, on page 2 Uses of NAT, on page 3 NAT Inside and Outside Addresses,
Finding Feature Information, on page 1 Network Address Translation (NAT), on page 2 Benefits of Configuring NAT, on page 2 How NAT Works, on page 2 Uses of NAT, on page 3 NAT Inside and Outside Addresses,
ETSF05/ETSF10 Internet Protocols. Routing on the Internet
 ETSF05/ETSF10 Internet Protocols Routing on the Internet Circuit switched routing ETSF05/ETSF10 - Internet Protocols 2 Routing in Packet Switching Networks Key design issue for (packet) switched networks
ETSF05/ETSF10 Internet Protocols Routing on the Internet Circuit switched routing ETSF05/ETSF10 - Internet Protocols 2 Routing in Packet Switching Networks Key design issue for (packet) switched networks
VxWorks Device Driver Developer's Guide, 6.6. VxWorks. DEVICE DRIVER DEVELOPER'S GUIDE Volume 3: Legacy Drivers and Migration 6.6
 VxWorks Device Driver Developer's Guide, 6.6 VxWorks DEVICE DRIVER DEVELOPER'S GUIDE Volume 3: Legacy Drivers and Migration 6.6 Copyright 2007 Wind River Systems, Inc. All rights reserved. No part of this
VxWorks Device Driver Developer's Guide, 6.6 VxWorks DEVICE DRIVER DEVELOPER'S GUIDE Volume 3: Legacy Drivers and Migration 6.6 Copyright 2007 Wind River Systems, Inc. All rights reserved. No part of this
On Distributed Communications, Rand Report RM-3420-PR, Paul Baran, August 1964
 The requirements for a future all-digital-data distributed network which provides common user service for a wide range of users having different requirements is considered. The use of a standard format
The requirements for a future all-digital-data distributed network which provides common user service for a wide range of users having different requirements is considered. The use of a standard format
CALIFORNIA SOFTWARE LABS
 JetSend Viewer for Windows CE CALIFORNIA SOFTWARE LABS R E A L I Z E Y O U R I D E A S California Software Labs 6800 Koll Center Parkway, Suite 100 Pleasanton CA 94566, USA. Phone (925) 249 3000 Fax (925)
JetSend Viewer for Windows CE CALIFORNIA SOFTWARE LABS R E A L I Z E Y O U R I D E A S California Software Labs 6800 Koll Center Parkway, Suite 100 Pleasanton CA 94566, USA. Phone (925) 249 3000 Fax (925)
Lecture 11: Middleboxes and NAT (Duct tape for IPv4)
 CSCI-351 Data communication and Networks Lecture 11: Middleboxes and NAT (Duct tape for IPv4) The slide is built with the help of Prof. Alan Mislove, Christo Wilson, and David Choffnes's class Middleboxes
CSCI-351 Data communication and Networks Lecture 11: Middleboxes and NAT (Duct tape for IPv4) The slide is built with the help of Prof. Alan Mislove, Christo Wilson, and David Choffnes's class Middleboxes
Why IPv6? Roque Gagliano LACNIC
 Why IPv6? Roque Gagliano LACNIC Agenda Initial Concepts. IPv6 History. What is IPv6? Planning IPv6. Agenda Initial Concepts. IPv6 History. What is IPv6? Planning IPv6. Some initial concepts. IPv6 is the
Why IPv6? Roque Gagliano LACNIC Agenda Initial Concepts. IPv6 History. What is IPv6? Planning IPv6. Agenda Initial Concepts. IPv6 History. What is IPv6? Planning IPv6. Some initial concepts. IPv6 is the
Agenda L2 versus L3 Switching IP Protocol, IP Addressing IP Forwarding ARP and ICMP IP Routing First Hop Redundancy
 Primer IP Technology L2 Ethernet Switching versus L3 routing IP Protocol, IP Addressing, IP Forwarding ARP and ICMP IP Routing, OSPF Basics First Hop Redundancy (HSRP) Agenda L2 versus L3 Switching IP
Primer IP Technology L2 Ethernet Switching versus L3 routing IP Protocol, IP Addressing, IP Forwarding ARP and ICMP IP Routing, OSPF Basics First Hop Redundancy (HSRP) Agenda L2 versus L3 Switching IP
E : Internet Routing
 E6998-02: Internet Routing Lecture 18 Overlay Networks John Ioannidis AT&T Labs Research ji+ir@cs.columbia.edu Copyright 2002 by John Ioannidis. All Rights Reserved. Announcements Lectures 1-18 are available.
E6998-02: Internet Routing Lecture 18 Overlay Networks John Ioannidis AT&T Labs Research ji+ir@cs.columbia.edu Copyright 2002 by John Ioannidis. All Rights Reserved. Announcements Lectures 1-18 are available.
CCNA Exploration Network Fundamentals. Chapter 06 Addressing the Network IPv4
 CCNA Exploration Network Fundamentals Chapter 06 Addressing the Network IPv4 Updated: 20/05/2008 1 6.0.1 Introduction Addressing is a key function of Network layer protocols that enables data communication
CCNA Exploration Network Fundamentals Chapter 06 Addressing the Network IPv4 Updated: 20/05/2008 1 6.0.1 Introduction Addressing is a key function of Network layer protocols that enables data communication
UDP and TCP. Introduction. So far we have studied some data link layer protocols such as PPP which are responsible for getting data
 ELEX 4550 : Wide Area Networks 2015 Winter Session UDP and TCP is lecture describes the two most common transport-layer protocols used by IP networks: the User Datagram Protocol (UDP) and the Transmission
ELEX 4550 : Wide Area Networks 2015 Winter Session UDP and TCP is lecture describes the two most common transport-layer protocols used by IP networks: the User Datagram Protocol (UDP) and the Transmission
Configuring TCP Header Compression
 Configuring TCP Header Compression First Published: January 30, 2006 Last Updated: May 5, 2010 Header compression is a mechanism that compresses the IP header in a packet before the packet is transmitted.
Configuring TCP Header Compression First Published: January 30, 2006 Last Updated: May 5, 2010 Header compression is a mechanism that compresses the IP header in a packet before the packet is transmitted.
Networking for Data Acquisition Systems. Fabrice Le Goff - 14/02/ ISOTDAQ
 Networking for Data Acquisition Systems Fabrice Le Goff - 14/02/2018 - ISOTDAQ Outline Generalities The OSI Model Ethernet and Local Area Networks IP and Routing TCP, UDP and Transport Efficiency Networking
Networking for Data Acquisition Systems Fabrice Le Goff - 14/02/2018 - ISOTDAQ Outline Generalities The OSI Model Ethernet and Local Area Networks IP and Routing TCP, UDP and Transport Efficiency Networking
Firewalls. Firewall types. Packet filter. Proxy server. linux, iptables-based Windows XP s built-in router device built-ins single TCP conversation
 Firewalls Firewall types Packet filter linux, iptables-based Windows XP s built-in router device built-ins single TCP conversation Proxy server specialized server program on internal machine client talks
Firewalls Firewall types Packet filter linux, iptables-based Windows XP s built-in router device built-ins single TCP conversation Proxy server specialized server program on internal machine client talks
Why Firewalls? Firewall Characteristics
 Why Firewalls? Firewalls are effective to: Protect local systems. Protect network-based security threats. Provide secured and controlled access to Internet. Provide restricted and controlled access from
Why Firewalls? Firewalls are effective to: Protect local systems. Protect network-based security threats. Provide secured and controlled access to Internet. Provide restricted and controlled access from
Lecture 11: Networks & Networking
 Lecture 11: Networks & Networking Contents Distributed systems Network types Network standards ISO and TCP/IP network models Internet architecture IP addressing IP datagrams AE4B33OSS Lecture 11 / Page
Lecture 11: Networks & Networking Contents Distributed systems Network types Network standards ISO and TCP/IP network models Internet architecture IP addressing IP datagrams AE4B33OSS Lecture 11 / Page
Lab - Using Wireshark to Examine a UDP DNS Capture
 Topology Objectives Part 1: Record a PC s IP Configuration Information Part 2: Use Wireshark to Capture DNS Queries and Responses Part 3: Analyze Captured DNS or UDP Packets Background / Scenario If you
Topology Objectives Part 1: Record a PC s IP Configuration Information Part 2: Use Wireshark to Capture DNS Queries and Responses Part 3: Analyze Captured DNS or UDP Packets Background / Scenario If you
Concept Questions Demonstrate your knowledge of these concepts by answering the following questions in the space that is provided.
 223 Chapter 19 Inter mediate TCP The Transmission Control Protocol/Internet Protocol (TCP/IP) suite of protocols was developed as part of the research that the Defense Advanced Research Projects Agency
223 Chapter 19 Inter mediate TCP The Transmission Control Protocol/Internet Protocol (TCP/IP) suite of protocols was developed as part of the research that the Defense Advanced Research Projects Agency
ETSF05/ETSF10 Internet Protocols Network Layer Protocols
 ETSF05/ETSF10 Internet Protocols Network Layer Protocols 2016 Jens Andersson Agenda Internetworking IPv4/IPv6 Framentation/Reassembly ICMPv4/ICMPv6 IPv4 to IPv6 transition VPN/Ipsec NAT (Network Address
ETSF05/ETSF10 Internet Protocols Network Layer Protocols 2016 Jens Andersson Agenda Internetworking IPv4/IPv6 Framentation/Reassembly ICMPv4/ICMPv6 IPv4 to IPv6 transition VPN/Ipsec NAT (Network Address
Firewall Stateful Inspection of ICMP
 Firewall Stateful Inspection of ICMP Last Updated: March 26, 2012 The Firewall Stateful Inspection of ICMP feature addresses the limitation of qualifying Internet Control Management Protocol (ICMP) messages
Firewall Stateful Inspection of ICMP Last Updated: March 26, 2012 The Firewall Stateful Inspection of ICMP feature addresses the limitation of qualifying Internet Control Management Protocol (ICMP) messages
Lab - Using Wireshark to Examine a UDP DNS Capture
 Topology Objectives Part 1: Record a PC s IP Configuration Information Part 2: Use Wireshark to Capture DNS Queries and Responses Part 3: Analyze Captured DNS or UDP Packets Background / Scenario If you
Topology Objectives Part 1: Record a PC s IP Configuration Information Part 2: Use Wireshark to Capture DNS Queries and Responses Part 3: Analyze Captured DNS or UDP Packets Background / Scenario If you
Transport Layer. Gursharan Singh Tatla. Upendra Sharma. 1
 Transport Layer Gursharan Singh Tatla mailme@gursharansingh.in Upendra Sharma 1 Introduction The transport layer is the fourth layer from the bottom in the OSI reference model. It is responsible for message
Transport Layer Gursharan Singh Tatla mailme@gursharansingh.in Upendra Sharma 1 Introduction The transport layer is the fourth layer from the bottom in the OSI reference model. It is responsible for message
Measuring MPLS overhead
 Measuring MPLS overhead A. Pescapè +*, S. P. Romano +, M. Esposito +*, S. Avallone +, G. Ventre +* * ITEM - Laboratorio Nazionale CINI per l Informatica e la Telematica Multimediali Via Diocleziano, 328
Measuring MPLS overhead A. Pescapè +*, S. P. Romano +, M. Esposito +*, S. Avallone +, G. Ventre +* * ITEM - Laboratorio Nazionale CINI per l Informatica e la Telematica Multimediali Via Diocleziano, 328
Network Address Translation (NAT) Contents. Firewalls. NATs and Firewalls. NATs. What is NAT. Port Ranges. NAT Example
 Contents Network Address Translation (NAT) 13.10.2008 Prof. Sasu Tarkoma Overview Background Basic Network Address Translation Solutions STUN TURN ICE Summary What is NAT Expand IP address space by deploying
Contents Network Address Translation (NAT) 13.10.2008 Prof. Sasu Tarkoma Overview Background Basic Network Address Translation Solutions STUN TURN ICE Summary What is NAT Expand IP address space by deploying
