NIC: 4693 May Object: Arpa Network - Specification Outlines for Host-IMP (HI) Interface Programs.
|
|
|
- Kelly Hines
- 6 years ago
- Views:
Transcription
1 Network Working Group G. Deloche Request for Comment: 7 University of California at Los Angeles NIC: 4693 May 1969 Host-Imp Interface G. Deloche --> Prof. J. Estrin Prof. L. Kleinrock Prof. B Bussel D. Mandell S. Crocker L. Bonamy Object: Arpa Network - Specification Outlines for Host-IMP (HI) Interface Programs. Outline I. Introduction II. Scope of the software organization. II-1 Network program II-2 Handler program III. Questions [The original of RFC 7 was hand-written, and only partially illegible copies exist. RFC 7 was later typed int NLS by the Augmentation Research Center (ARC) at SRI. The following is the best reconstruction we could do. RFC Editor.] Deloche [Page 1]
2 I. Introduction This paper is concerned with the preliminary software design of the Host IMP interface. Its main purpose is on the one hand to define functions that will be implemented, and on the other hand to provide a base for discussions and...(unreadable). This study is based upon a study of the BBN Report No II. Scope of the software organization. The system is based upon two main programs: the Handler program that drives the channel hardware unit, and the Network program which carries out the user s transmission requests. As the communication is full duplex, each of these programs can be viewed as divided into two parts: one is concerned with the output data, the other with the input. (See Fig. 1) These two programs exchange data through a pool of buffers, and logical information through an interface table. In the following we only focus on the output part of each program (See Fig. 2). The input part would be very similar. II-1. Network program. II-1-1. Multiplex function. This program multiplexes the outgoing messages (and distributes the incoming messages). The multiplexing consists in stacking up all the user s (or caller, or party) requests and filling up the pool of buffers so as to keep the handler busy emitting. Multiplexing (and distribution) is based on the link identification numbers. (Link = logical connection between two users). The multiplexing problem is closely related to the interface between a user s program and the network program, that is in fact...(unreadable) operating system (See below: Questions). II-1-2. Output message processing. When a user s program wants to send out text it should indicate the following information (through a macro, or as call parameters): text location, text length in bytes, and destination. Deloche [Page 2]
3 Using these data the Network program: * prepares a 16 bit Host heading (1 bit: trace, 2 bits: spares, 8 bits: link identification no., 5 bits: destination host) * inserts a 16 bits marking between the header and the text so as to start the text at a word boundary. This marking consists of a one preceding the first bit of the text and, in turn, preceded by fifteen zeros to fill up the gap. * checks the length of the user s text - if it exceeds 1006 bytes (max host message length) - 32 (heading + marking) (byte = 8 bits) the program breaks down the text into a sequence of messages whose maximum length is 1006 bytes - Each of these messages is preceded by a heading as explained above. Remark: in that case one of the heading space bits could be used for indicating that several messages belong to the same text. * _transcodes_ the EBCDIC characters constituting the messages into ASCII characters. * _fills_ the buffers of the pool with the content of the messages. * _updates_ the content of the interface table and moves the filling pointers (see below). II-2. Handler program. This program is initiated either by the network program, or by the I/O interrupt. This program will be very short. It will be coded in master mode (privileged instructions) and should be integrated in the I/O supervisor of the operating system. Deloche [Page 3]
4 This program: * _controls_ the channel hardware unit. It initiates the emission, eventually provides data chaining between the buffers, tests the different device status upon receiving an interrupt. * _empties_ the buffers that are filled up by the network program. * _explores_ and _updates_ the interface table (see below). * can eventually insure a control transmission procedure with the IMP (See Questions). II-3 Buffers and Interface Table. II-3-1 Buffers. They should be large enough for containing the maximum host message text + heading and marking ( = 1010 bytes). Consequently the buffer size could be chosen equal to 256 words (1024 bytes). As for the buffer number it will determine the link utilization frequency - II-3-2 Interface table. It is through this table that the network program informs the handler with the location and length of the emitting data. This table could be a ring table with 2 pointers: one for filling, the other for extracting. They are respectively updated by the network and the handler program. Deloche [Page 4]
5 [Length] of the message contained in the buffer ^ Buffer addr. nb bytes <== Filling pointer V // // Buffer addr. nb bytes <== eetracting pointer Buffer addr. nb bytes V III. Questions. III-1. Why is there not a simple control procedure between the HOST and the IMP? What happens if a message, issued from the HOST, reaches the IMP with an error due to the transmission? From the BBN specifications it appears that this error will be transmitted as far [as] the receiving HOST. In that case must an HOST-HOST control procedure be provided? III-2. Where will the special channel hardware unit be connected (MIOP/SIOP)? How will this device be notified of an outgoing message end in order to start the padding? (The program will provide to the MIOP SIOP the number of bytes of the outgoing message, and will receive back an interrupt when the last byte is sent out. Is it that signal which will be also sent to the special device?) Vice versa how does the Handler know the length of the incoming message? From the contents of the previous one or should this Deloche [Page 5]
6 program always ready to receive a message of maximum length? (Then an interrupt should be triggered when the real end is detected by the hardware). III-3. When does the Gordo documentation will be available in order to design the user-network program interface. What are the mechanisms for program initiations, transferring parameters from one program to another, etc... HOST (Sigma 7) <-- / --> Outside world Users / / / Special Standard V / / V V o---- / Output --> Output --> / --> -->IMP... / / o---- (Multiplex) / _ / _ _ o---- / Input <-- Input <-- / <--<--IMP... / / o---- (Distribution) / / HARDWARE / Interface NETWORK HANDLER / Program Program / / (Fig. 1) Deloche [Page 6]
7 interface ====> Data Logical information interface table >< interrupt ^ +----< V V V V o \ \ NETWORK =>- -=> HANDLER =======> + Progr. Progr. / / o ^ +---> > ^ +- ^ -+ Commands Users Pool of buffers User s ^ Interface Hardware Interface (Fig. 2) [ This RFC was put into machine readable form for entry ] [ into the online RFC archives by Bob German & Lorrie Shiota 1/02 ] Deloche [Page 7]
Correction to BBN Report No. 1822
 7818 Network Working Group RFC # 270 NIC "7818 Categories: B.l Updates: none Obsoletes: none A. McKenzie BBN 1 January 1972 Correction to BBN In the process of generating RFC # 271 we have discovered a
7818 Network Working Group RFC # 270 NIC "7818 Categories: B.l Updates: none Obsoletes: none A. McKenzie BBN 1 January 1972 Correction to BBN In the process of generating RFC # 271 we have discovered a
Request for Comments: March 1970
 Network Working Group S. Crocker Request for Comments: 36 16 March 1970 I Overview -------- Protocol Notes The network protocol provides three facilities: 1. Connection establishment 2. Flow control 3.
Network Working Group S. Crocker Request for Comments: 36 16 March 1970 I Overview -------- Protocol Notes The network protocol provides three facilities: 1. Connection establishment 2. Flow control 3.
Request for Comments: December 1970 NIC NWG/RFC 1 7 April 1969 NIC 4687 HOST Software S. Crocker (UCLA)
 Network Working Group J. B. North Request for Comments: 84 23 December 1970 NIC 5620 LIST OF NWG/RFC s 1-80 NWG/RFC 1 7 April 1969 NIC 4687 HOST Software NWG/RFC 2 9 April 1969 NIC 4688 HOST Software B.
Network Working Group J. B. North Request for Comments: 84 23 December 1970 NIC 5620 LIST OF NWG/RFC s 1-80 NWG/RFC 1 7 April 1969 NIC 4687 HOST Software NWG/RFC 2 9 April 1969 NIC 4688 HOST Software B.
17 April ARPA Network Protocol Notes
 Network Working Group Request for Comments: 46 Edwin E. Meyer, Jr. Massachusetts Institute of Technology 17 April 1970 ARPA Network Protocol Notes The attached document contains comments and suggestions
Network Working Group Request for Comments: 46 Edwin E. Meyer, Jr. Massachusetts Institute of Technology 17 April 1970 ARPA Network Protocol Notes The attached document contains comments and suggestions
Request for Comments: 851 Obsoletes RFC: 802. The ARPANET 1822L Host Access Protocol RFC 851. Andrew G. Malis ARPANET Mail:
 Request for Comments: 851 Obsoletes RFC: 802 The ARPANET 1822L Host Access Protocol Andrew G. Malis ARPANET Mail: malis@bbn-unix Bolt Beranek and Newman Inc. 50 Moulton St. Cambridge, MA 02238 April 1983
Request for Comments: 851 Obsoletes RFC: 802 The ARPANET 1822L Host Access Protocol Andrew G. Malis ARPANET Mail: malis@bbn-unix Bolt Beranek and Newman Inc. 50 Moulton St. Cambridge, MA 02238 April 1983
Network Working Group Request for Comments: 205 NIC: August 1971
 Network Working Group R. Braden Request for Comments: 205 UCLA/CCN NIC: 7172 6 August 1971 NETCRT - A CHARACTER DISPLAY PROTOCOL At the May NWG, meeting, CCN circulated dittoed copies of a proposed character-display
Network Working Group R. Braden Request for Comments: 205 UCLA/CCN NIC: 7172 6 August 1971 NETCRT - A CHARACTER DISPLAY PROTOCOL At the May NWG, meeting, CCN circulated dittoed copies of a proposed character-display
Request for Comments: 2. 1a1 Logical link 0 will be a control link between any two HOSTs on the network
 Network Working Group Request for Comments: 2 Bill Duvall SRI [unknown title] [page 1 missing] 1 LINKS 1a Control Links 1a1 Logical link 0 will be a control link between any two HOSTs on the network 1a1a
Network Working Group Request for Comments: 2 Bill Duvall SRI [unknown title] [page 1 missing] 1 LINKS 1a Control Links 1a1 Logical link 0 will be a control link between any two HOSTs on the network 1a1a
Request for Comments: 327 NIC: 9261 April 27, 1972
 Network Working Group A. Bhushan Request for Comments: 327 MIT-MAC NIC: 9261 April 27, 1972 DATA AND FILE TRANSFER WORKSHOP NOTES On April 14 and 15, 1972, a Data and File Transfer Workshop was held at
Network Working Group A. Bhushan Request for Comments: 327 MIT-MAC NIC: 9261 April 27, 1972 DATA AND FILE TRANSFER WORKSHOP NOTES On April 14 and 15, 1972, a Data and File Transfer Workshop was held at
Bob Flegel (Utah) Lamar G. Farquar (Utah) June 1970
 Network Working Group Request for Comments: 56 Ed Belove (Harvard) Dave Black (Harvard) Bob Flegel (Utah) Lamar G. Farquar (Utah) June 1970 Third Level Protocol Logger Protocol General Description In our
Network Working Group Request for Comments: 56 Ed Belove (Harvard) Dave Black (Harvard) Bob Flegel (Utah) Lamar G. Farquar (Utah) June 1970 Third Level Protocol Logger Protocol General Description In our
Request for Comments: 171. Categories: D.4, D.5, and D.7
 Network Working Group Request for Comments: 171 NIC 6793 Categories: D.4, D.5, and D.7 Updates: 114 Obsolete: None Abhay Bhushan MIT Bob Braden UCLA Will Crowther Alex McKenzie BBN Eric Harslem John Heafner
Network Working Group Request for Comments: 171 NIC 6793 Categories: D.4, D.5, and D.7 Updates: 114 Obsolete: None Abhay Bhushan MIT Bob Braden UCLA Will Crowther Alex McKenzie BBN Eric Harslem John Heafner
NIC #22161 Mar "On a Possible Lockup Condition in the IMP Subnet Due to Message Sequencing"
 L. Kleinrock (UCLA-NMC) H. Opderbeck (UCLA-NMC) NIC #22161 Mar 1974 "On a Possible Lockup Condition in the IMP Subnet Due to Message Sequencing" Lockup or deadlock conditions are one of the most serious
L. Kleinrock (UCLA-NMC) H. Opderbeck (UCLA-NMC) NIC #22161 Mar 1974 "On a Possible Lockup Condition in the IMP Subnet Due to Message Sequencing" Lockup or deadlock conditions are one of the most serious
PCAN-Explorer 6. Tel: Professional Windows Software to Communicate with CAN and CAN FD Busses. Software >> PC Software
 PCAN-Explorer 6 Professional Windows Software to Communicate with CAN and CAN FD Busses The PCAN-Explorer 6 is a versatile, professional program for working with CAN and CAN FD networks. The user is not
PCAN-Explorer 6 Professional Windows Software to Communicate with CAN and CAN FD Busses The PCAN-Explorer 6 is a versatile, professional program for working with CAN and CAN FD networks. The user is not
4. The transport layer
 4.1 The port number One of the most important information contained in the header of a segment are the destination and the source port numbers. The port numbers are necessary to identify the application
4.1 The port number One of the most important information contained in the header of a segment are the destination and the source port numbers. The port numbers are necessary to identify the application
Request for Comments: 33. S. Carr University of Utah V. Cerf UCLA. 12 February 1973
 Network Working Group Request for Comments: 33 S. Crocker UCLA S. Carr University of Utah V. Cerf UCLA 12 February 1973 New HOST-HOST Protocol Attached is a copy of the paper to be presented at the SJCC
Network Working Group Request for Comments: 33 S. Crocker UCLA S. Carr University of Utah V. Cerf UCLA 12 February 1973 New HOST-HOST Protocol Attached is a copy of the paper to be presented at the SJCC
TSIN02 - Internetworking
 Lecture 4: Transport Layer Literature: Forouzan: ch 11-12 2004 Image Coding Group, Linköpings Universitet Lecture 4: Outline Transport layer responsibilities UDP TCP 2 Transport layer in OSI model Figure
Lecture 4: Transport Layer Literature: Forouzan: ch 11-12 2004 Image Coding Group, Linköpings Universitet Lecture 4: Outline Transport layer responsibilities UDP TCP 2 Transport layer in OSI model Figure
TCP/IP Stack Introduction: Looking Under the Hood!
 TCP/IP Stack Introduction: Looking Under the Hood! Shiv Kalyanaraman shivkuma@ecse.rpi.edu http://www.ecse.rpi.edu/homepages/shivkuma 1 Example program 1. Create UDP datagram socket; fill in server address
TCP/IP Stack Introduction: Looking Under the Hood! Shiv Kalyanaraman shivkuma@ecse.rpi.edu http://www.ecse.rpi.edu/homepages/shivkuma 1 Example program 1. Create UDP datagram socket; fill in server address
Introduction to Networking. Operating Systems In Depth XXVII 1 Copyright 2017 Thomas W. Doeppner. All rights reserved.
 Introduction to Networking Operating Systems In Depth XXVII 1 Copyright 2017 Thomas W. Doeppner. All rights reserved. Distributed File Systems Operating Systems In Depth XXVII 2 Copyright 2017 Thomas W.
Introduction to Networking Operating Systems In Depth XXVII 1 Copyright 2017 Thomas W. Doeppner. All rights reserved. Distributed File Systems Operating Systems In Depth XXVII 2 Copyright 2017 Thomas W.
EE 610 Part 2: Encapsulation and network utilities
 EE 610 Part 2: Encapsulation and network utilities Objective: After this experiment, the students should be able to: i. Understand the format of standard frames and packet headers. Overview: The Open Systems
EE 610 Part 2: Encapsulation and network utilities Objective: After this experiment, the students should be able to: i. Understand the format of standard frames and packet headers. Overview: The Open Systems
Chapter -4 OSI Reference Model
 Chapter -4 OSI Reference Model Objectives Concept of Reference Model. OSI Reference Model Concept. Layers of OSI Reference Model. 4.1 Introduction Layered Architecture, Peer-to- Peer Processes, Interfaces
Chapter -4 OSI Reference Model Objectives Concept of Reference Model. OSI Reference Model Concept. Layers of OSI Reference Model. 4.1 Introduction Layered Architecture, Peer-to- Peer Processes, Interfaces
Chapter 8: I/O functions & socket options
 Chapter 8: I/O functions & socket options 8.1 Introduction I/O Models In general, there are normally two phases for an input operation: 1) Waiting for the data to arrive on the network. When the packet
Chapter 8: I/O functions & socket options 8.1 Introduction I/O Models In general, there are normally two phases for an input operation: 1) Waiting for the data to arrive on the network. When the packet
Request for Comments: 189 Obsoletes: RFC 88 (NIC 5668) 15 July 1971 NIC 7133 Category: D
 Network Working Group R. T. Braden Request for Comments: 189 UCLA/CCN Obsoletes: RFC 88 (NIC 5668) 15 July 1971 NIC 7133 Category: D INTERIM NETRJS SPECIFICATIONS The following document describes the operation
Network Working Group R. T. Braden Request for Comments: 189 UCLA/CCN Obsoletes: RFC 88 (NIC 5668) 15 July 1971 NIC 7133 Category: D INTERIM NETRJS SPECIFICATIONS The following document describes the operation
Transport Layer. <protocol, local-addr,local-port,foreign-addr,foreign-port> ϒ Client uses ephemeral ports /10 Joseph Cordina 2005
 Transport Layer For a connection on a host (single IP address), there exist many entry points through which there may be many-to-many connections. These are called ports. A port is a 16-bit number used
Transport Layer For a connection on a host (single IP address), there exist many entry points through which there may be many-to-many connections. These are called ports. A port is a 16-bit number used
Santa Barbara, California March In the discussions that follow, byte means 8 bits, with those eight bits numbered 0-7 from left to right.
 Network Working Group Request for Comments: 105 Category: Informational James E. White Computer Research Lab. University of California Santa Barbara, California March 1971 Network Specifications for Remote
Network Working Group Request for Comments: 105 Category: Informational James E. White Computer Research Lab. University of California Santa Barbara, California March 1971 Network Specifications for Remote
Request for Comments: 714 NIC: April A Host/Host Protocol for an ARPANET-Type Network
 Network Working Group A. McKenzie Request for Comments: 714 BBN-NCC NIC: 35144 April 1976 A Host/Host Protocol for an ARPANET-Type Network Recently we have been involved in the planning of a network, which,
Network Working Group A. McKenzie Request for Comments: 714 BBN-NCC NIC: 35144 April 1976 A Host/Host Protocol for an ARPANET-Type Network Recently we have been involved in the planning of a network, which,
Layer 2 functionality bridging and switching
 Layer 2 functionality bridging and switching BSAD 141 Dave Novak Sources: Network+ Guide to Networks, Dean 2013 Overview Layer 2 functionality Error detection Bridges Broadcast and collision domains How
Layer 2 functionality bridging and switching BSAD 141 Dave Novak Sources: Network+ Guide to Networks, Dean 2013 Overview Layer 2 functionality Error detection Bridges Broadcast and collision domains How
TSIN02 - Internetworking
 Lecture 4: Transport Layer Literature: Forouzan: ch 11-12 2004 Image Coding Group, Linköpings Universitet Lecture 4: Outline Transport layer responsibilities UDP TCP 2 Transport layer in OSI model Figure
Lecture 4: Transport Layer Literature: Forouzan: ch 11-12 2004 Image Coding Group, Linköpings Universitet Lecture 4: Outline Transport layer responsibilities UDP TCP 2 Transport layer in OSI model Figure
11/3/71 SYS BREAK (II)
 11/3/71 SYS BREAK (II) break -- set program break SYNOPSIS sys break; addr / break = 17. break sets the system s idea of the highest location used by the program to addr. Locations greater than addr and
11/3/71 SYS BREAK (II) break -- set program break SYNOPSIS sys break; addr / break = 17. break sets the system s idea of the highest location used by the program to addr. Locations greater than addr and
PROTECTION CHAPTER 4 PROTECTION
 Protection 4 CHAPTER 4 PROTECTION In protected mode, the Intel Architecture provides a protection mechanism that operates at both the segment level and the page level. This protection mechanism provides
Protection 4 CHAPTER 4 PROTECTION In protected mode, the Intel Architecture provides a protection mechanism that operates at both the segment level and the page level. This protection mechanism provides
Lecture 6: memory structure 8086 Outline: 1.introduction 2.memory reserve 3.bus operation
 Lecture 6: memory structure 8086 Outline: 1.introduction 2.memory reserve 3.bus operation 1 1.INRTODUCTION The 8086 memory is a sequence of up to 1 million 8-bit bytes, a considerable increase over the
Lecture 6: memory structure 8086 Outline: 1.introduction 2.memory reserve 3.bus operation 1 1.INRTODUCTION The 8086 memory is a sequence of up to 1 million 8-bit bytes, a considerable increase over the
CALIFORNIA SOFTWARE LABS
 Real-time Implementation of NAT and Firewall in VxWorks CALIFORNIA SOFTWARE LABS R E A L I Z E Y O U R I D E A S California Software Labs 6800 Koll Center Parkway, Suite 100 Pleasanton CA 94566, USA. Phone
Real-time Implementation of NAT and Firewall in VxWorks CALIFORNIA SOFTWARE LABS R E A L I Z E Y O U R I D E A S California Software Labs 6800 Koll Center Parkway, Suite 100 Pleasanton CA 94566, USA. Phone
Network Working Group NIC Category: Informational 12 February 1971
 Network Working Group NIC 5739 Request for Comments: 96 Richard W. Watson Category: Informational SRI-ARC 12 February 1971 An Interactive Network Experiment to Study Modes of Access the Network Information
Network Working Group NIC 5739 Request for Comments: 96 Richard W. Watson Category: Informational SRI-ARC 12 February 1971 An Interactive Network Experiment to Study Modes of Access the Network Information
Lecture 3: The Transport Layer: UDP and TCP
 Lecture 3: The Transport Layer: UDP and TCP Prof. Shervin Shirmohammadi SITE, University of Ottawa Prof. Shervin Shirmohammadi CEG 4395 3-1 The Transport Layer Provides efficient and robust end-to-end
Lecture 3: The Transport Layer: UDP and TCP Prof. Shervin Shirmohammadi SITE, University of Ottawa Prof. Shervin Shirmohammadi CEG 4395 3-1 The Transport Layer Provides efficient and robust end-to-end
58 Building an Application
 Chapter 58 Building an Application This chapter describes how you can use the Cadvanced SDL to C Compiler to generate applications and especially how to design the environment functions. These functions
Chapter 58 Building an Application This chapter describes how you can use the Cadvanced SDL to C Compiler to generate applications and especially how to design the environment functions. These functions
Michael D. Kudlick MDK (SRI-ARC)
 NWG/RFC#469 NIC 14798 Michael D. Kudlick MDK (SRI-ARC) 8-MAR-73 Network Mail Meeting Summary Introduction The purpose of this RFC is to briefly summarize, from the NIC s viewpoint, the principal conclusions
NWG/RFC#469 NIC 14798 Michael D. Kudlick MDK (SRI-ARC) 8-MAR-73 Network Mail Meeting Summary Introduction The purpose of this RFC is to briefly summarize, from the NIC s viewpoint, the principal conclusions
Request for Comments: 938 February 1985
 Network Working Group Request for Comments: 938 Trudy Miller ACC February 1985 Functional and Interface Specification STATUS OF THIS MEMO This RFC is being distributed to members of the DARPA research
Network Working Group Request for Comments: 938 Trudy Miller ACC February 1985 Functional and Interface Specification STATUS OF THIS MEMO This RFC is being distributed to members of the DARPA research
Network Working Group Request for Comments: XXXX NIC: February 1971
 Network Working Group P. Karp Request for Comments: XXXX MITRE NIC: 5761 26 February 1971 Categorization and Guide to NWG/RFCs The NWG/RFC Guide is an attempt to introduce some order into the NWG/RFC series,
Network Working Group P. Karp Request for Comments: XXXX MITRE NIC: 5761 26 February 1971 Categorization and Guide to NWG/RFCs The NWG/RFC Guide is an attempt to introduce some order into the NWG/RFC series,
Network Working Group Request for Comments: 323 NIC: 9630 March 23, 1972
 Network Working Group Vint Cerf Request for Comments: 323 UCLA-NMC NIC: 9630 March 23, 1972 Formation of Network Measurement Group (NMG) On March 17, 1972, at MIT project MAC, the following group met to
Network Working Group Vint Cerf Request for Comments: 323 UCLA-NMC NIC: 9630 March 23, 1972 Formation of Network Measurement Group (NMG) On March 17, 1972, at MIT project MAC, the following group met to
Networking Applications
 Networking Dr. Ayman A. Abdel-Hamid College of Computing and Information Technology Arab Academy for Science & Technology and Maritime Transport 1 Outline Internet Layers Internet Data Packet transmission
Networking Dr. Ayman A. Abdel-Hamid College of Computing and Information Technology Arab Academy for Science & Technology and Maritime Transport 1 Outline Internet Layers Internet Data Packet transmission
Secure Cisco Discovery Protocol
 The Cisco Discovery Protocol does not possess inherent security mechanisms and is vulnerable to attacks. The feature allows users to select the type, length, value (TLV) fields that are sent on a particular
The Cisco Discovery Protocol does not possess inherent security mechanisms and is vulnerable to attacks. The feature allows users to select the type, length, value (TLV) fields that are sent on a particular
Tracking the Virtual World
 Tracking the Virtual World Synopsys: For many years the JTAG interface has been used for ARM-based SoC debugging. With this JTAG style debugging, the developer has been granted the ability to debug software
Tracking the Virtual World Synopsys: For many years the JTAG interface has been used for ARM-based SoC debugging. With this JTAG style debugging, the developer has been granted the ability to debug software
SCUBA-2 PCI Card DSP Code Overview
 UK Astronomy Technology Centre David Atkinson Royal Observatory Edinburgh 05/10/05 SCUBA-2 Project SC2/ELE/S565/01 Version 0.1 1. Summary SCUBA-2 PCI Card DSP Code Overview This document describes the
UK Astronomy Technology Centre David Atkinson Royal Observatory Edinburgh 05/10/05 SCUBA-2 Project SC2/ELE/S565/01 Version 0.1 1. Summary SCUBA-2 PCI Card DSP Code Overview This document describes the
Operating System Control Structures
 Operating System Control Structures Information about the current status of each process and resource Tables are constructed for each entity the operating system manages 26 Memory Tables Allocation of
Operating System Control Structures Information about the current status of each process and resource Tables are constructed for each entity the operating system manages 26 Memory Tables Allocation of
IT 540 Operating Systems ECE519 Advanced Operating Systems
 IT 540 Operating Systems ECE519 Advanced Operating Systems Prof. Dr. Hasan Hüseyin BALIK (3 rd Week) (Advanced) Operating Systems 3. Process Description and Control 3. Outline What Is a Process? Process
IT 540 Operating Systems ECE519 Advanced Operating Systems Prof. Dr. Hasan Hüseyin BALIK (3 rd Week) (Advanced) Operating Systems 3. Process Description and Control 3. Outline What Is a Process? Process
Vorlesung Kommunikationsnetze
 Picture 15 13 Vorlesung Kommunikationsnetze Prof. Dr. H. P. Großmann mit B. Wiegel sowie A. Schmeiser und M. Rabel Sommersemester 2009 Institut für Organisation und Management von Informationssystemen
Picture 15 13 Vorlesung Kommunikationsnetze Prof. Dr. H. P. Großmann mit B. Wiegel sowie A. Schmeiser und M. Rabel Sommersemester 2009 Institut für Organisation und Management von Informationssystemen
OPERATING SYSTEM OVERVIEW
 OPERATING SYSTEM OVERVIEW Contents Basic hardware elements Interrupts Most I/O devices are much slower than the processor Active waiting cycle (polling) Interrupt request signal Interrupt mechanism An
OPERATING SYSTEM OVERVIEW Contents Basic hardware elements Interrupts Most I/O devices are much slower than the processor Active waiting cycle (polling) Interrupt request signal Interrupt mechanism An
William Stallings Computer Organization and Architecture. Chapter 11 CPU Structure and Function
 William Stallings Computer Organization and Architecture Chapter 11 CPU Structure and Function CPU Structure CPU must: Fetch instructions Interpret instructions Fetch data Process data Write data Registers
William Stallings Computer Organization and Architecture Chapter 11 CPU Structure and Function CPU Structure CPU must: Fetch instructions Interpret instructions Fetch data Process data Write data Registers
NIC: July 1971
 Network Working Group P. Deutsch Request for Comments: 190 Xerox Research Center, Palo Alto, CA NIC: 7135 13 July 1971 DEC PDP-10 -- IMLAC COMMUNICATION SYSTEM This report describes an operational system
Network Working Group P. Deutsch Request for Comments: 190 Xerox Research Center, Palo Alto, CA NIC: 7135 13 July 1971 DEC PDP-10 -- IMLAC COMMUNICATION SYSTEM This report describes an operational system
9th Slide Set Computer Networks
 Prof. Dr. Christian Baun 9th Slide Set Computer Networks Frankfurt University of Applied Sciences WS1718 1/49 9th Slide Set Computer Networks Prof. Dr. Christian Baun Frankfurt University of Applied Sciences
Prof. Dr. Christian Baun 9th Slide Set Computer Networks Frankfurt University of Applied Sciences WS1718 1/49 9th Slide Set Computer Networks Prof. Dr. Christian Baun Frankfurt University of Applied Sciences
8051 Microcontroller
 8051 Microcontroller 1 Salient Features (1). 8 bit microcontroller originally developed by Intel in 1980. (2). High-performance CMOS Technology. (3). Contains Total 40 pins. (4). Address bus is of 16 bit
8051 Microcontroller 1 Salient Features (1). 8 bit microcontroller originally developed by Intel in 1980. (2). High-performance CMOS Technology. (3). Contains Total 40 pins. (4). Address bus is of 16 bit
RFC 802: The ARPANET 1822L Host Access Protocol. Andrew G. Malis Netmail: Bolt Beranek and Newman Inc.
 : The ARPANET 1822L Host Access Protocol Netmail: malis@bbn-unix Bolt Beranek and Newman Inc. November 1981 Table of Contents 1 INTRODUCTION... 1 2 THE ARPANET 1822L HOST ACCESS PROTOCOL... 4 2.1 Addresses
: The ARPANET 1822L Host Access Protocol Netmail: malis@bbn-unix Bolt Beranek and Newman Inc. November 1981 Table of Contents 1 INTRODUCTION... 1 2 THE ARPANET 1822L HOST ACCESS PROTOCOL... 4 2.1 Addresses
September 1980 MAIL TRANSITION PLAN PREFACE. This is a draft memo and comments are requested. INTRODUCTION
 Network Working Group Request for Comments: 771 V. Cerf (ARPA) J. Postel (ISI) September 1980 MAIL TRANSITION PLAN PREFACE This is a draft memo and comments are requested. INTRODUCTION The principal aim
Network Working Group Request for Comments: 771 V. Cerf (ARPA) J. Postel (ISI) September 1980 MAIL TRANSITION PLAN PREFACE This is a draft memo and comments are requested. INTRODUCTION The principal aim
TCP/IP-2. Transmission control protocol:
 TCP/IP-2 Transmission control protocol: TCP and IP are the workhorses in the Internet. In this section we first discuss how TCP provides reliable, connectionoriented stream service over IP. To do so, TCP
TCP/IP-2 Transmission control protocol: TCP and IP are the workhorses in the Internet. In this section we first discuss how TCP provides reliable, connectionoriented stream service over IP. To do so, TCP
Chapter 2 PROTOCOL ARCHITECTURE
 Chapter 2 PROTOCOL ARCHITECTURE 2.1 INTRODUCTION IPv6 is a new version of Internet protocol which is expected to substitute IPv4. It is very difficult to predict exactly when IPv4 will eventually come
Chapter 2 PROTOCOL ARCHITECTURE 2.1 INTRODUCTION IPv6 is a new version of Internet protocol which is expected to substitute IPv4. It is very difficult to predict exactly when IPv4 will eventually come
ECE4110 Internetwork Programming. Introduction and Overview
 ECE4110 Internetwork Programming Introduction and Overview 1 EXAMPLE GENERAL NETWORK ALGORITHM Listen to wire Are signals detected Detect a preamble Yes Read Destination Address No data carrying or noise?
ECE4110 Internetwork Programming Introduction and Overview 1 EXAMPLE GENERAL NETWORK ALGORITHM Listen to wire Are signals detected Detect a preamble Yes Read Destination Address No data carrying or noise?
NIC # RFC # August 1972 Categories: F, G.3 Updates: RFC #370 Obsoletes: None
 Network Working Group Ellen Westheimer NIC # 11118 BBN RFC # 376 8 August 1972 Categories: F, G.3 Updates: RFC #370 Obsoletes: None NETWORK HOST STATUS This RFC reports on the status of most Network Hosts
Network Working Group Ellen Westheimer NIC # 11118 BBN RFC # 376 8 August 1972 Categories: F, G.3 Updates: RFC #370 Obsoletes: None NETWORK HOST STATUS This RFC reports on the status of most Network Hosts
TSIN02 - Internetworking
 Lecture 4: Outline Literature: Lecture 4: Transport Layer Forouzan: ch 11-12 RFC? Transport layer introduction UDP TCP 2004 Image Coding Group, Linköpings Universitet 2 The Transport Layer Transport layer
Lecture 4: Outline Literature: Lecture 4: Transport Layer Forouzan: ch 11-12 RFC? Transport layer introduction UDP TCP 2004 Image Coding Group, Linköpings Universitet 2 The Transport Layer Transport layer
Linux based 3G Specification. Multimedia Mobile Phone API. Circuit Switched Communication Service CELF_MPP_CS_D_2.2.3_
 Linux based 3G Specification Multimedia Mobile Phone API Circuit Switched Communication Service Document: CELF_MPP_CS_D_2.2.3_20051228 WARNING: This is a working draft for review only, it is NOT a published
Linux based 3G Specification Multimedia Mobile Phone API Circuit Switched Communication Service Document: CELF_MPP_CS_D_2.2.3_20051228 WARNING: This is a working draft for review only, it is NOT a published
Lecture Outline. Lecture 2. OSI model and networking. The OSI model and networking. The OSI model and networking. The OSI model and networking
 Lecture 2 The OSI model Chapter 2, specifically pages 42-58 Dave Novak School of Business Administration, University of Vermont Sources: 1) Network+ Guide to Networks, Dean 2013 2) Comer, Computer Networks
Lecture 2 The OSI model Chapter 2, specifically pages 42-58 Dave Novak School of Business Administration, University of Vermont Sources: 1) Network+ Guide to Networks, Dean 2013 2) Comer, Computer Networks
INPUT/OUTPUT ORGANIZATION
 INPUT/OUTPUT ORGANIZATION Accessing I/O Devices I/O interface Input/output mechanism Memory-mapped I/O Programmed I/O Interrupts Direct Memory Access Buses Synchronous Bus Asynchronous Bus I/O in CO and
INPUT/OUTPUT ORGANIZATION Accessing I/O Devices I/O interface Input/output mechanism Memory-mapped I/O Programmed I/O Interrupts Direct Memory Access Buses Synchronous Bus Asynchronous Bus I/O in CO and
RFC 803. Dacom 450/500 Facsimile Data Transcoding A. Agarwal, M. J. O Connor and D. L. Mills 2 November Introduction
 RFC 803 Dacom 450/500 Facsimile Data Transcoding A. Agarwal, M. J. O Connor and D. L. Mills 2 November 1981 1. Introduction As part of our effort in support of the DARPA Internet Program, software modules
RFC 803 Dacom 450/500 Facsimile Data Transcoding A. Agarwal, M. J. O Connor and D. L. Mills 2 November 1981 1. Introduction As part of our effort in support of the DARPA Internet Program, software modules
Transport Layer. Gursharan Singh Tatla. Upendra Sharma. 1
 Transport Layer Gursharan Singh Tatla mailme@gursharansingh.in Upendra Sharma 1 Introduction The transport layer is the fourth layer from the bottom in the OSI reference model. It is responsible for message
Transport Layer Gursharan Singh Tatla mailme@gursharansingh.in Upendra Sharma 1 Introduction The transport layer is the fourth layer from the bottom in the OSI reference model. It is responsible for message
Configuring attack detection and prevention 1
 Contents Configuring attack detection and prevention 1 Overview 1 Attacks that the device can prevent 1 Single-packet attacks 1 Scanning attacks 2 Flood attacks 3 TCP fragment attack 4 Login DoS attack
Contents Configuring attack detection and prevention 1 Overview 1 Attacks that the device can prevent 1 Single-packet attacks 1 Scanning attacks 2 Flood attacks 3 TCP fragment attack 4 Login DoS attack
ET4254 Communications and Networking 1
 Topic 9 Internet Protocols Aims:- basic protocol functions internetworking principles connectionless internetworking IP IPv6 IPSec 1 Protocol Functions have a small set of functions that form basis of
Topic 9 Internet Protocols Aims:- basic protocol functions internetworking principles connectionless internetworking IP IPv6 IPSec 1 Protocol Functions have a small set of functions that form basis of
6.9. Communicating to the Outside World: Cluster Networking
 6.9 Communicating to the Outside World: Cluster Networking This online section describes the networking hardware and software used to connect the nodes of cluster together. As there are whole books and
6.9 Communicating to the Outside World: Cluster Networking This online section describes the networking hardware and software used to connect the nodes of cluster together. As there are whole books and
Simulation of TCP Layer
 39 Simulation of TCP Layer Preeti Grover, M.Tech, Computer Science, Uttrakhand Technical University, Dehradun ABSTRACT The Transmission Control Protocol (TCP) represents the most deployed transport protocol
39 Simulation of TCP Layer Preeti Grover, M.Tech, Computer Science, Uttrakhand Technical University, Dehradun ABSTRACT The Transmission Control Protocol (TCP) represents the most deployed transport protocol
REQUEST FOR COMMENTS #283 NIC #8165 DECEMBER 20, 1971 CATEGORIES: D OBSOLETES: NONE UPDATES: RFC #189
 NETWORK WORKING GROUP R. T. BRADEN REQUEST FOR COMMENTS #283 UCLA/CCN NIC #8165 DECEMBER 20, 1971 CATEGORIES: D OBSOLETES: NONE UPDATES: RFC #189 A. INTRODUCTION ------------ NETRJT -- Remote Job Service
NETWORK WORKING GROUP R. T. BRADEN REQUEST FOR COMMENTS #283 UCLA/CCN NIC #8165 DECEMBER 20, 1971 CATEGORIES: D OBSOLETES: NONE UPDATES: RFC #189 A. INTRODUCTION ------------ NETRJT -- Remote Job Service
Chapter 4 NETWORK HARDWARE
 Chapter 4 NETWORK HARDWARE 1 Network Devices As Organizations grow, so do their networks Growth in number of users Geographical Growth Network Devices : Are products used to expand or connect networks.
Chapter 4 NETWORK HARDWARE 1 Network Devices As Organizations grow, so do their networks Growth in number of users Geographical Growth Network Devices : Are products used to expand or connect networks.
Maxim > Design Support > Technical Documents > Application Notes > Microcontrollers > APP 4465
 Maxim > Design Support > Technical Documents > Application Notes > Microcontrollers > APP 4465 Keywords: MAXQ, MAXQ610, UART, USART, serial, serial port APPLICATION NOTE 4465 Using the Serial Port on the
Maxim > Design Support > Technical Documents > Application Notes > Microcontrollers > APP 4465 Keywords: MAXQ, MAXQ610, UART, USART, serial, serial port APPLICATION NOTE 4465 Using the Serial Port on the
Stream Control Transmission Protocol
 Chapter 13 Stream Control Transmission Protocol Objectives Upon completion you will be able to: Be able to name and understand the services offered by SCTP Understand SCTP s flow and error control and
Chapter 13 Stream Control Transmission Protocol Objectives Upon completion you will be able to: Be able to name and understand the services offered by SCTP Understand SCTP s flow and error control and
Lecture 2: Links and Signaling
 Lecture 2: Links and Signaling CSE 123: Computer Networks Alex C. Snoeren DISCUSSION @7pm Tomorrow Our Problem Communications is complicated Modulation and encoding bits Splitting sequences of bits into
Lecture 2: Links and Signaling CSE 123: Computer Networks Alex C. Snoeren DISCUSSION @7pm Tomorrow Our Problem Communications is complicated Modulation and encoding bits Splitting sequences of bits into
Request for Comments: 508 Computer Systems Laboratory / UCSB 7 May 1973
 Network Working Group Request for Comments: 508 NIC: 16159 L. Pfeifer J. McAfee Computer Systems Laboratory / UCSB 7 May 1973 REAL-TIME DATA TRANSMISSION ON THE ARPANET I. INTRODUCTION The ARPA Network
Network Working Group Request for Comments: 508 NIC: 16159 L. Pfeifer J. McAfee Computer Systems Laboratory / UCSB 7 May 1973 REAL-TIME DATA TRANSMISSION ON THE ARPANET I. INTRODUCTION The ARPA Network
Overview of Network Software. CS158a Chris Pollett Jan 31, 2007.
 Overview of Network Software CS158a Chris Pollett Jan 31, 2007. Outline Design Issues for Protocol Hierarchies Reference Models Example Networks Protocol Hierarchies-Review To reduce design complexity
Overview of Network Software CS158a Chris Pollett Jan 31, 2007. Outline Design Issues for Protocol Hierarchies Reference Models Example Networks Protocol Hierarchies-Review To reduce design complexity
Transport layer Internet layer
 Lecture 2-bis. 2 Transport Protocols As seen by the application developer point of view The primary (in principle unique) role of transport protocols!" # $ % "!"& Transport httpd 25 80 3211... My app 131.175.15.1
Lecture 2-bis. 2 Transport Protocols As seen by the application developer point of view The primary (in principle unique) role of transport protocols!" # $ % "!"& Transport httpd 25 80 3211... My app 131.175.15.1
19: Networking. Networking Hardware. Mark Handley
 19: Networking Mark Handley Networking Hardware Lots of different hardware: Modem byte at a time, FDDI, SONET packet at a time ATM (including some DSL) 53-byte cell at a time Reality is that most networking
19: Networking Mark Handley Networking Hardware Lots of different hardware: Modem byte at a time, FDDI, SONET packet at a time ATM (including some DSL) 53-byte cell at a time Reality is that most networking
Riverbed AirPcap software AirPcapReplay
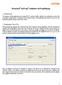 Riverbed AirPcap software AirPcapReplay 1. Introduction The purpose of this application is to replay 802.11 network traffic, whether it is contained in a trace file or simply a single packet. In addition
Riverbed AirPcap software AirPcapReplay 1. Introduction The purpose of this application is to replay 802.11 network traffic, whether it is contained in a trace file or simply a single packet. In addition
Define a situation that checks for a missing process on Windows:
 Creating a policy with SNMP activity Version 2 November 11, 2009 This document shows how to create a policy that waits on a situation and then sends an SNMP event to another server when the situation fires.
Creating a policy with SNMP activity Version 2 November 11, 2009 This document shows how to create a policy that waits on a situation and then sends an SNMP event to another server when the situation fires.
ECE 650 Systems Programming & Engineering. Spring 2018
 ECE 650 Systems Programming & Engineering Spring 2018 Networking Transport Layer Tyler Bletsch Duke University Slides are adapted from Brian Rogers (Duke) TCP/IP Model 2 Transport Layer Problem solved:
ECE 650 Systems Programming & Engineering Spring 2018 Networking Transport Layer Tyler Bletsch Duke University Slides are adapted from Brian Rogers (Duke) TCP/IP Model 2 Transport Layer Problem solved:
When an instruction is initially read from memory it goes to the Instruction register.
 CS 320 Ch. 12 Instruction Sets Computer instructions are written in mnemonics. Mnemonics typically have a 1 to 1 correspondence between a mnemonic and the machine code. Mnemonics are the assembly language
CS 320 Ch. 12 Instruction Sets Computer instructions are written in mnemonics. Mnemonics typically have a 1 to 1 correspondence between a mnemonic and the machine code. Mnemonics are the assembly language
Flow Routing to Power NGN IP Services. Dr. Lawrence G. Roberts CEO, Anagran
 Flow Routing to Power NGN IP Services Dr. Lawrence G. Roberts CEO, Anagran lroberts@anagran.com The Beginning of the Internet - ARPANET 1965 MIT Two Computer Experiment Proved Circuit Switching too slow,
Flow Routing to Power NGN IP Services Dr. Lawrence G. Roberts CEO, Anagran lroberts@anagran.com The Beginning of the Internet - ARPANET 1965 MIT Two Computer Experiment Proved Circuit Switching too slow,
External Data Representation (XDR)
 External Data Representation (XDR) Prof. Chuan-Ming Liu Computer Science and Information Engineering National Taipei University of Technology Taipei, TAIWAN NTUT, TAIWAN 1 Introduction This chapter examines
External Data Representation (XDR) Prof. Chuan-Ming Liu Computer Science and Information Engineering National Taipei University of Technology Taipei, TAIWAN NTUT, TAIWAN 1 Introduction This chapter examines
Network Working Group. NIC: June 1973
 Network Working Group J. Day Request for Comments: 520 Center for Advanced Computation NIC: 16819 25 June 1973 A Proposed File Access Protocol Specification Attached is a proposal for the File Access Protocol.
Network Working Group J. Day Request for Comments: 520 Center for Advanced Computation NIC: 16819 25 June 1973 A Proposed File Access Protocol Specification Attached is a proposal for the File Access Protocol.
Technical Notes. QoS Features on the Business Ethernet Switch 50 (BES50)
 Technical Notes QoS Features on the Business Ethernet Switch 50 (BES50) Version: NN70000-004 issue 1.00 Date: February 3 rd, 2009 Status: Released Copyright 2009 Nortel Networks. All rights reserved. The
Technical Notes QoS Features on the Business Ethernet Switch 50 (BES50) Version: NN70000-004 issue 1.00 Date: February 3 rd, 2009 Status: Released Copyright 2009 Nortel Networks. All rights reserved. The
CMPE 80N: Introduction to Networking and the Internet
 CMPE 80N: Introduction to Networking and the Internet Katia Obraczka Computer Engineering UCSC Baskin Engineering Lecture 11 CMPE 80N Fall'10 1 Announcements Forum #2 due on 11.05. CMPE 80N Fall'10 2 Last
CMPE 80N: Introduction to Networking and the Internet Katia Obraczka Computer Engineering UCSC Baskin Engineering Lecture 11 CMPE 80N Fall'10 1 Announcements Forum #2 due on 11.05. CMPE 80N Fall'10 2 Last
Computer Networks. Transmission Control Protocol. Jianping Pan Spring /3/17 CSC361 1
 Computer Networks Transmission Control Protocol Jianping Pan Spring 2017 2/3/17 CSC361 1 https://connex.csc.uvic.ca/portal NSERC USRA awards available at UVic CSc for 2017/18 2/3/17 CSC361 2 TCP Transmission
Computer Networks Transmission Control Protocol Jianping Pan Spring 2017 2/3/17 CSC361 1 https://connex.csc.uvic.ca/portal NSERC USRA awards available at UVic CSc for 2017/18 2/3/17 CSC361 2 TCP Transmission
Che-Wei Chang Department of Computer Science and Information Engineering, Chang Gung University
 Che-Wei Chang chewei@mail.cgu.edu.tw Department of Computer Science and Information Engineering, Chang Gung University l Chapter 10: File System l Chapter 11: Implementing File-Systems l Chapter 12: Mass-Storage
Che-Wei Chang chewei@mail.cgu.edu.tw Department of Computer Science and Information Engineering, Chang Gung University l Chapter 10: File System l Chapter 11: Implementing File-Systems l Chapter 12: Mass-Storage
Table of Contents 1 GRE Configuration Point to Multi-Point GRE Tunnel Configuration 2-1
 Table of Contents 1 GRE Configuration 1-1 GRE Overview 1-1 Introduction to GRE 1-1 GRE Security Options 1-3 GRE Applications 1-3 Protocols and Standards 1-4 Configuring a GRE over IPv4 Tunnel 1-4 Configuration
Table of Contents 1 GRE Configuration 1-1 GRE Overview 1-1 Introduction to GRE 1-1 GRE Security Options 1-3 GRE Applications 1-3 Protocols and Standards 1-4 Configuring a GRE over IPv4 Tunnel 1-4 Configuration
Volume II, Section 5 Table of Contents
 Volume II, Section 5 Table of Contents 5...5-1 5.1 Scope...5-1 5.2 Basis of...5-1 5.3 Initial Review of Documentation...5-2 5.4 Source Code Review...5-2 5.4.1 Control Constructs...5-3 5.4.1.1 Replacement
Volume II, Section 5 Table of Contents 5...5-1 5.1 Scope...5-1 5.2 Basis of...5-1 5.3 Initial Review of Documentation...5-2 5.4 Source Code Review...5-2 5.4.1 Control Constructs...5-3 5.4.1.1 Replacement
Transport Layer. The transport layer is responsible for the delivery of a message from one process to another. RSManiaol
 Transport Layer Transport Layer The transport layer is responsible for the delivery of a message from one process to another Types of Data Deliveries Client/Server Paradigm An application program on the
Transport Layer Transport Layer The transport layer is responsible for the delivery of a message from one process to another Types of Data Deliveries Client/Server Paradigm An application program on the
IP - The Internet Protocol. Based on the slides of Dr. Jorg Liebeherr, University of Virginia
 IP - The Internet Protocol Based on the slides of Dr. Jorg Liebeherr, University of Virginia Orientation IP (Internet Protocol) is a Network Layer Protocol. IP: The waist of the hourglass IP is the waist
IP - The Internet Protocol Based on the slides of Dr. Jorg Liebeherr, University of Virginia Orientation IP (Internet Protocol) is a Network Layer Protocol. IP: The waist of the hourglass IP is the waist
University of California at Berkeley April 1984
 Network Working Group Request for Comments: 893 Samuel J. Leffler Michael J. Karels University of California at Berkeley April 1984 Trailer Encapsulations Status of this Memo This RFC discusses the motivation
Network Working Group Request for Comments: 893 Samuel J. Leffler Michael J. Karels University of California at Berkeley April 1984 Trailer Encapsulations Status of this Memo This RFC discusses the motivation
Network Architecture Models
 School of Business Eastern Illinois University Network Architecture Models (September 8, 2009) Abdou Illia, Fall 2009 Learning Objectives 2 Discuss the OSI reference Model Discuss the Internet Model Compare
School of Business Eastern Illinois University Network Architecture Models (September 8, 2009) Abdou Illia, Fall 2009 Learning Objectives 2 Discuss the OSI reference Model Discuss the Internet Model Compare
4. INFOPATH Packet Switching Service 4.1 General
 Page 1 INFOPATH Packet Switching Service is furnished on existing installations only. Additions, rearrangements and moves of service are not permitted. Rates and charges for services explained herein are
Page 1 INFOPATH Packet Switching Service is furnished on existing installations only. Additions, rearrangements and moves of service are not permitted. Rates and charges for services explained herein are
Ref: A. Leon Garcia and I. Widjaja, Communication Networks, 2 nd Ed. McGraw Hill, 2006 Latest update of this lecture was on
 IP Version 4 (IPv4) Header (Continued) Identification (16 bits): One of the parameters of any network is the maximum transmission unit (MTU) parameter. This parameter specifies the maximum size of the
IP Version 4 (IPv4) Header (Continued) Identification (16 bits): One of the parameters of any network is the maximum transmission unit (MTU) parameter. This parameter specifies the maximum size of the
Outline. Heap meta-data. Non-control data overwrite
 Outline CSci 5271 Introduction to Computer Security Day 5: Low-level defenses and counterattacks Stephen McCamant University of Minnesota, Computer Science & Engineering Non-control data overwrite Heap
Outline CSci 5271 Introduction to Computer Security Day 5: Low-level defenses and counterattacks Stephen McCamant University of Minnesota, Computer Science & Engineering Non-control data overwrite Heap
CPU Structure and Function
 Computer Architecture Computer Architecture Prof. Dr. Nizamettin AYDIN naydin@yildiz.edu.tr nizamettinaydin@gmail.com http://www.yildiz.edu.tr/~naydin CPU Structure and Function 1 2 CPU Structure Registers
Computer Architecture Computer Architecture Prof. Dr. Nizamettin AYDIN naydin@yildiz.edu.tr nizamettinaydin@gmail.com http://www.yildiz.edu.tr/~naydin CPU Structure and Function 1 2 CPU Structure Registers
CSE506: Operating Systems CSE 506: Operating Systems
 CSE 506: Operating Systems What Software Expects of the OS What Software Expects of the OS Memory System Calls System Services Launching Program Executables Shell Memory Abstraction CSE506: Operating Systems
CSE 506: Operating Systems What Software Expects of the OS What Software Expects of the OS Memory System Calls System Services Launching Program Executables Shell Memory Abstraction CSE506: Operating Systems
Application Note. Introduction AN2471/D 3/2003. PC Master Software Communication Protocol Specification
 Application Note 3/2003 PC Master Software Communication Protocol Specification By Pavel Kania and Michal Hanak S 3 L Applications Engineerings MCSL Roznov pod Radhostem Introduction The purpose of this
Application Note 3/2003 PC Master Software Communication Protocol Specification By Pavel Kania and Michal Hanak S 3 L Applications Engineerings MCSL Roznov pod Radhostem Introduction The purpose of this
CS3600 SYSTEMS AND NETWORKS
 CS3600 SYSTEMS AND NETWORKS NORTHEASTERN UNIVERSITY Lecture 17: Internet architecture Prof. Alan Mislove (amislove@ccs.neu.edu) Slides used with permissions from Edward W. Knightly, T. S. Eugene Ng, Ion
CS3600 SYSTEMS AND NETWORKS NORTHEASTERN UNIVERSITY Lecture 17: Internet architecture Prof. Alan Mislove (amislove@ccs.neu.edu) Slides used with permissions from Edward W. Knightly, T. S. Eugene Ng, Ion
Introduction to Internetworking
 Introduction to Internetworking Introductory terms Communications Network Facility that provides data transfer services An internet Collection of communications networks interconnected by bridges and/or
Introduction to Internetworking Introductory terms Communications Network Facility that provides data transfer services An internet Collection of communications networks interconnected by bridges and/or
I 2 C and SPI Protocol Triggering and Decode for Infiniium 9000 Series Oscilloscopes
 I 2 C and SPI Protocol Triggering and Decode for Infiniium 9000 Series Oscilloscopes Data sheet This application is available in the following license variations. Order N5391B for a user-installed license
I 2 C and SPI Protocol Triggering and Decode for Infiniium 9000 Series Oscilloscopes Data sheet This application is available in the following license variations. Order N5391B for a user-installed license
