A Simple Way to Make Passwords More Effective
|
|
|
- Mabel Booth
- 5 years ago
- Views:
Transcription
1 A Simple Way to Make Passwords More Effective J. Scott Magruder The University of Southern Mississippi /Fax Stanley X. Lewis, Jr. The University of Southern Mississippi /Fax Eddy J. Burks Athens State University /Fax ABSTRACT A simple change to the login process is shown to make passwords more effective. An illustration is presented where users login through a Web browser, but the logic also applies to any situation where a login/password combination are required. By adding to the existing password security features typically found in a network additional layers of encryption a company s network can be made more secure. For the illustration, the code is written in perl. THE NORMAL LOGIN PROCESS The normal login process is illustrated using a Web page login/password requirement. The user points their browser to an HTML page that has a textbox for a username, a textbox for their password and a submit button. Once filled in, the user clicks on the submit button which calls the cgi (Common Gateway Interface) program (written in perl in this example) which checks to see if the username and password are in the password file. If the user's login is correct, then they are allowed access to the Web page, directory, etc. If not, then the user may be allowed to try again. The failed access may be logged. The perl program reads what the user has typed in the two textboxes. In this case, the input would be of the form UserName=Name_Typed_In&password=Password_Typed_In 450
2 where UserName and password are the names given to the html text boxes. The & separates the two pieces of information. Thus, splitting the line on & gives the two pieces of information in a key=value structure. Then splitting on the = in both parts gives us the values that the user typed into the textboxes. Next, the password sent via the textbox is encrypted with the system encryption routine. The username (and the associated encrypted password) is found in the password file and the encrypted password from the file is compared with the user's encrypted password. If they are the same, then access is granted. Otherwise, the user will receive a Web page indicating that access is denied. The user may be allowed to try again. The html code for the login page would look like this: <html> <body> <form method="post" action="/cgi-bin1/processpassword.pl"> Username<input type="text" name="username"><br> Password<input type="password" name="password"><br><p> <input type="submit"> </form> </body> </html> The user types in their login name (Username) and their password and clicks on Submit. The form statement calls the program (processpassword.pl) to check the Username/password pair. NORMAL PASSWORD TESTING In a company s network a password checking routine is implemented as typically as a module in the network operating system. As such the checking routine does not cause a delay in the acceptance or rejection of a person attempting to access the network. The authors have generated a set of three modules (programs) to illustration the typical approach found in a networked environment to provide security over access to the system. Program 1 - Password Testing The perl code testing the password would look like this: @split3=split(/=/,$split1[1]); $flag=0; open(p,"/diskb1/home/demo2/pass"); print "Content-type: text/html\n\n"; print "<html><body>"; while ($line=<p>) # This is where the perl interpreter resides # Read the information passed from the html page # Split the information into the two key=value pieces #Split the first piece; the username is in $split2[1] #Split the second piece; the password is in split3[1] #Open the password file #This is the required first line in the html protocol when a #page is sent back to the user #Start the web page #Read a record from the password file 451
3 ($name,$encpass)=split(/\ /,$line); chomp($encpass); record delimiter if ($split2[1] eq $name) $salt = substr($encpass,0,2); if ($encpass eq $checkpass) #Split the password record into the username and encrypted password #Get rid of the newline (\n) which is the password #split2[1] is the username from the html document; compare it to the #username from the password file [1] #A match has been found; extract the salt which is the first two #characters of the encrypted password document and #passed to this program; Encrypt the password #Compare the encrypted password from the html document with the #encrypted password from the password file opendir(dir,"/diskb1/home/mis408/public_html"); #A match has been found; open the #directory we are protecting and send a web #page back to the #Read the directory entries into an array foreach (@dir) #Go through each directory entry if (($_ ne ".") && ($_ ne "..")) #exclude. and.. print "<a href=\" #print the directory entry in a #format so the user can click on the #entry and the contents will be #shown to the user print "<BR>"; Else print "Login incorrect"; print "</body></html>"; #print a break (html newline) between each entry #A match was not found between the (encrypted) password the user #entered and the encrypted password for that user in the password file #print an error message #print the ending components of the web page 452
4 Program 2 - Acceptance & Encryption Accept the name and password; encrypt the password and compare it with the encrypted password associated with the name in the password file. To create the password file, the following perl program could be used: #!/usr/bin/perl use Term::ReadKey; print "Enter login name: "; $Name=<>; chomp($name); ReadMode 2; print "Enter password: "; $pass=<>; chomp($pass); ReadMode 0; $salt=''; $s1=('a'..'z','a'..'z')[52*rand]; $s2=('a'..'z','a'..'z')[52*rand]; $salt=$s1.$s2; print "\n$salt\n"; open (P,">>pass"); print P "$Name $encrypted\n"; #We use this perl module so the password will not be echoed to the #screen #prompt the user #Read the user name #Get rid of the newline attached to what the user types in when they hit #enter #Go into the non-echo mode #prompt the user for the password #Read the password #Get rid of the newline #Go back to regular echo mode #predefine $salt to be empty #randomly generate the first salt character #randomly generate the second salt character #Reference (Holzner, 2001) #Combine the two randomly generated characters into one salt #Use the generated salt to encrypt the password #Open the password file (pass) in append mode #Print the user name and encrypted password (the salt is the first two #character of the encrypted password) to the password file using #as the delimiter Program 3 - Encrypted Passwords & Password File Generation Generate encrypted passwords and put the name and encrypted password in the password file. The perl code is not presented for this program. HACKING PASSWORDS Common knowledge of network systems and a public media blitz about the hacking of network systems presents network administrators an increasng challenge to restrict their company s network system (internal network, Internet, intranet and extranet) environment to users authorized by the company. 453
5 A hacker would try to break into this system by cracking the passwords in the password file. The hacker would have to have a copy or access to the password file, a dictionary file and a program that would take the list of words in the dictionary file, encrypt them using the same encryption scheme as the system he is trying to break into. If one of the encrypted words is found in the password file, then that password is broken. PROGRAM 4 Password Hacked The following perl program illustrates the process of password cracking: #!/usr/bin/perl open (PASS,"passwd"); while ($precord=<pass>) ($name,$encpass)=split(/\ /,$precord); $salt = substr($encpass,0,2); open (DICT,"dictionary"); while ($word=<dict>) chomp($word); $TestPass=crypt($word,$salt); if ($encpass eq $TestPass) #open the password file #continue while we have passwords to check #The password record consists of a username and an #encrypted password separated by the delimiter #extract the salt --the first two characters of the encrypted password #from the password file #open the dictionary file #read the next word in the dictionary file #get rid of the newline that is attached to the word #encrypt the word from the dictionary file using the salt #check to see if the encrypted password from the password file matches the encrypted word from the dictionary file print "The password is $word for user $name \n"; #the two encrypted words match; thus we have broken that password else # no match found; try another dictionary word until all of these words have been encrypted and tested for a match close(dict); #go to the next password, again encrypting all dictionary words and #comparing the result with the encrypted password Using the above perl program on the password file, passwd: John KGHfKJy1j6AjQ tom Q]ieHZZ3qLSWw 454
6 lester _Gb0IxQ.QUSpI produces the following output: The password is klop for user lester A very small dictionary file was used in this demonstration. The dictionary contained the password so that we would be able to demonstrate that a password would be broken. MAKING THE PASSWORD SCHEME MORE SECURE Now that the stage has been set, more secure procedures can be presented. Hackers must have access to the password file, a dictionary file, a password cracking program and the password encryption process used by the organization. The more secure password procedures presented here change slightly the organization's password encryption process without letting the hackers know the process has changed. Encrypt the password more than one time. The first change is to encrypt the password more than once. This requires changes to the code in Program 2 and Program 3: The line - Program 2 changes: document and passed to this program; Encrypt the password becomes two lines as shown next. document and passed to this program; Encrypt the password $checkpass=crypt($checkpass,$salt); In this case, the same salt was used when the password was encrypted again. Program 3 changes: The line - $encrypted=crypt($encrypted,$salt); #Use the generated salt to encrypt the password becomes two lines as shwon next. #Use the generated salt to encrypt the password Now the same algorithm (encrypting the password twice) is being used by the (encrypted) password generator and the login name/password checker. Thus, the users will be correctly validated and the login process would continue. However, the hacker's cracking algorithm only encrypts one time and thus will not break the password. Changing the salt The second salt can also be changed in the above process. The salt could be reversed. 455
7 Program 2 code changes: The line - $ReverseSalt=reverse($salt); $checkpass=crypt($checkpass,$reversesalt); Program 3 changes: The line: $ReverseSalt=reverse($salt); $encrypted=crypt($encrypted,$reversesalt); document and passed to this program; Encrypt the password is replaced by the next three lines document and passed to this program; Encrypt the password by the next lines #Use the generated salt to encrypt the password becomes two lines as shown next #Use the generated salt to encrypt the password The salt could be the last two characters of the first encrypted result. There are many possible variations on this theme. Again, this process is not an attempt to make the encryption algorithm more secure. Rather, the overall process is changed so the hacker is wasting their time using the "old process". This makes the overall process more secure to a dictionary and brute force attack. This process can also be extended to multiple encryptions by putting the code in a loop: $I=5; #This is the number of times to perform the encryption for ($I=1;$I<=$j;$I++) The only problem is "remembering" the number of times to encrypt and allowing the salt to be changed. The first problem could be solved by saving the number of times to encrypt the password in the password file, i.e., a record in the password file would look like: LoginName encryptedpassword Number of times to loop However, if the hacker does have access to the password file, then the additional field will give them too much information. Rather, the numerical value of the last character of the login name (as an example) can be used to determine the number of loops. For example, the ASCII value of A is 65. We can subtract 64 from that and determine the loop should be done one time. Thus, each login name may have a different number of encryptions associated with the password. This makes the hackers attacks even less profitable. 456
8 The Test The password cracker John-The-Ripper (available on the Internet) was used to test the original change in the login process. Jack was chosen since it is very easy to add words to the word-list. The regular text for a password was added to Jack's list and then encrypted twice and put in the password file. The user was able to login properly, but after several hours of running time, Jack did not crack the password. CONCLUSION This paper has demonstrated how making minor changes in the login process may make sites secured by a login process more secure. These minor changes include encrypting the password z multiple times, with the same or changed salt. REFERENCES Holzner, Steven. PERL BLACK BOOK, 2 nd Edition, Coriolis, 2001,
Forms, CGI. Cristian Bogdan 2D2052 / 2D1335 F5 1
 Forms, CGI Cristian Bogdan 2D2052 / 2D1335 F5 1 Objectives The basics of HTML forms How form content is submitted GET, POST Elements that you can have in forms Responding to forms Common Gateway Interface
Forms, CGI Cristian Bogdan 2D2052 / 2D1335 F5 1 Objectives The basics of HTML forms How form content is submitted GET, POST Elements that you can have in forms Responding to forms Common Gateway Interface
Forms, CGI. Objectives
 Forms, CGI Objectives The basics of HTML forms How form content is submitted GET, POST Elements that you can have in forms Responding to forms Common Gateway Interface (CGI) Later: Servlets Generation
Forms, CGI Objectives The basics of HTML forms How form content is submitted GET, POST Elements that you can have in forms Responding to forms Common Gateway Interface (CGI) Later: Servlets Generation
ESS Security Enhancements
 ESS Security Enhancements payentry.com Employee Self Service Enhancements 1 Table of Contents INTRODUCTION 3 EXISTING EMPLOYEES 3 Existing Employee -Email Address 4 Existing Employee - Username 4 Existing
ESS Security Enhancements payentry.com Employee Self Service Enhancements 1 Table of Contents INTRODUCTION 3 EXISTING EMPLOYEES 3 Existing Employee -Email Address 4 Existing Employee - Username 4 Existing
Writing Perl Programs using Control Structures Worked Examples
 Writing Perl Programs using Control Structures Worked Examples Louise Dennis October 27, 2004 These notes describe my attempts to do some Perl programming exercises using control structures and HTML Forms.
Writing Perl Programs using Control Structures Worked Examples Louise Dennis October 27, 2004 These notes describe my attempts to do some Perl programming exercises using control structures and HTML Forms.
Forms, CGI. HTML forms. Form example. Form example...
 Objectives HTML forms The basics of HTML forms How form content is submitted GET, POST Elements that you can have in forms Responding to forms CGI the Common Gateway Interface Later: Servlets Generation
Objectives HTML forms The basics of HTML forms How form content is submitted GET, POST Elements that you can have in forms Responding to forms CGI the Common Gateway Interface Later: Servlets Generation
User authentication, passwords
 User authentication, passwords User Authentication Nowadays most internet applications are available only for registered (paying) users How do we restrict access to our website only to privileged users?
User authentication, passwords User Authentication Nowadays most internet applications are available only for registered (paying) users How do we restrict access to our website only to privileged users?
USQ/CSC2406 Web Publishing
 USQ/CSC2406 Web Publishing Lecture 4: HTML Forms, Server & CGI Scripts Tralvex (Rex) Yeap 19 December 2002 Outline Quick Review on Lecture 3 Topic 7: HTML Forms Topic 8: Server & CGI Scripts Class Activity
USQ/CSC2406 Web Publishing Lecture 4: HTML Forms, Server & CGI Scripts Tralvex (Rex) Yeap 19 December 2002 Outline Quick Review on Lecture 3 Topic 7: HTML Forms Topic 8: Server & CGI Scripts Class Activity
O/S & Access Control. Aggelos Kiayias - Justin Neumann
 O/S & Access Control Aggelos Kiayias - Justin Neumann One system Many users Objects that require protection memory I/O devices (disks, printers) programs and processes networks stored data in general Separation
O/S & Access Control Aggelos Kiayias - Justin Neumann One system Many users Objects that require protection memory I/O devices (disks, printers) programs and processes networks stored data in general Separation
Introduction to UNIX. Logging in. Basic System Architecture 10/7/10. most systems have graphical login on Linux machines
 Introduction to UNIX Logging in Basic system architecture Getting help Intro to shell (tcsh) Basic UNIX File Maintenance Intro to emacs I/O Redirection Shell scripts Logging in most systems have graphical
Introduction to UNIX Logging in Basic system architecture Getting help Intro to shell (tcsh) Basic UNIX File Maintenance Intro to emacs I/O Redirection Shell scripts Logging in most systems have graphical
SMS GATEWAY API INTEGRATION GUIDE
 SMS GATEWAY API INTEGRATION GUIDE For PHP Developers Are you a developer or bulk SMS reseller? You can interface your application, website or system with our 247 reliable messaging gateway by using our
SMS GATEWAY API INTEGRATION GUIDE For PHP Developers Are you a developer or bulk SMS reseller? You can interface your application, website or system with our 247 reliable messaging gateway by using our
WinCapWEB- New User Account Registration
 WinCapWEB- New User Account Registration As an employee of Franklin Essex Hamilton BOCES you will receive an email from WinCapWEB asking you to create an account. Below is a sample email you will receive
WinCapWEB- New User Account Registration As an employee of Franklin Essex Hamilton BOCES you will receive an email from WinCapWEB asking you to create an account. Below is a sample email you will receive
Integrating legacy software with a Web front end
 Integrating legacy software with a Web fron... 1 of 6 http://web.archive.org/web/200006090127... Integrating legacy software with a Web front end How to solve your legacy access problems with Web-based
Integrating legacy software with a Web fron... 1 of 6 http://web.archive.org/web/200006090127... Integrating legacy software with a Web front end How to solve your legacy access problems with Web-based
Introduction to Information Security Prof. V. Kamakoti Department of Computer Science and Engineering Indian Institute of Technology, Madras
 Introduction to Information Security Prof. V. Kamakoti Department of Computer Science and Engineering Indian Institute of Technology, Madras Lecture 09 Now, we discuss about the insecurity of passwords.
Introduction to Information Security Prof. V. Kamakoti Department of Computer Science and Engineering Indian Institute of Technology, Madras Lecture 09 Now, we discuss about the insecurity of passwords.
CHAPTER 9. Implementing Web Security Using auth-lib.pl
 CHAPTER 9 Implementing Web Security Using auth-lib.pl OVERVIEW A natural extension of most applications is the capability to restrict or track access through the application. To do this, we need a system
CHAPTER 9 Implementing Web Security Using auth-lib.pl OVERVIEW A natural extension of most applications is the capability to restrict or track access through the application. To do this, we need a system
ITS331 IT Laboratory I: (Laboratory #11) Session Handling
 School of Information and Computer Technology Sirindhorn International Institute of Technology Thammasat University ITS331 Information Technology Laboratory I Laboratory #11: Session Handling Creating
School of Information and Computer Technology Sirindhorn International Institute of Technology Thammasat University ITS331 Information Technology Laboratory I Laboratory #11: Session Handling Creating
CGI Programming. What is "CGI"?
 CGI Programming What is "CGI"? Common Gateway Interface A means of running an executable program via the Web. CGI is not a Perl-specific concept. Almost any language can produce CGI programs even C++ (gasp!!)
CGI Programming What is "CGI"? Common Gateway Interface A means of running an executable program via the Web. CGI is not a Perl-specific concept. Almost any language can produce CGI programs even C++ (gasp!!)
ADSelfService Plus' Password Policy Enforcer. Active Directory Group Policy Object-based password policy
 Comparison Document ADSelfService Plus' Password Policy Enforcer Vs Active Directory Group Policy Object-based password policy Vs Active Directory Fine-grained password policies Passwords are the first
Comparison Document ADSelfService Plus' Password Policy Enforcer Vs Active Directory Group Policy Object-based password policy Vs Active Directory Fine-grained password policies Passwords are the first
L5: Basic Grammar Based Probabilistic Password Cracking
 L5: Basic Grammar Based Probabilistic Password Cracking Sudhir Aggarwal and Shiva Houshmand and Matt Weir Florida State University Department of Computer Science E-Crime Investigative Technologies Lab
L5: Basic Grammar Based Probabilistic Password Cracking Sudhir Aggarwal and Shiva Houshmand and Matt Weir Florida State University Department of Computer Science E-Crime Investigative Technologies Lab
Security Course. WebGoat Lab sessions
 Security Course WebGoat Lab sessions WebGoat Lab sessions overview Initial Setup Tamper Data Web Goat Lab Session 4 Access Control, session information stealing Lab Session 2 HTTP Basics Sniffing Parameter
Security Course WebGoat Lab sessions WebGoat Lab sessions overview Initial Setup Tamper Data Web Goat Lab Session 4 Access Control, session information stealing Lab Session 2 HTTP Basics Sniffing Parameter
Using Perl to Prepare Data Collected from the Internet for SAS Input. Robert Workman Southern Connecticut State University
 Using Perl to Prepare Data Collected from the Internet for SAS Input Robert Workman Southern Connecticut State University ABSTRACT This presentation will discuss the use of the Perl programming language
Using Perl to Prepare Data Collected from the Internet for SAS Input Robert Workman Southern Connecticut State University ABSTRACT This presentation will discuss the use of the Perl programming language
Installation & Configuration Guide Version 3.1
 ARPMiner Installation & Configuration Guide Version 3.1 Document Revision 2.2 https://www.kaplansoft.com/ ARPMiner is built by Yasin KAPLAN Read Readme.txt for last minute changes and updates which can
ARPMiner Installation & Configuration Guide Version 3.1 Document Revision 2.2 https://www.kaplansoft.com/ ARPMiner is built by Yasin KAPLAN Read Readme.txt for last minute changes and updates which can
PHP 5 if...else...elseif Statements
 PHP 5 if...else...elseif Statements Conditional statements are used to perform different actions based on different conditions. PHP Conditional Statements Very often when you write code, you want to perform
PHP 5 if...else...elseif Statements Conditional statements are used to perform different actions based on different conditions. PHP Conditional Statements Very often when you write code, you want to perform
SmartVoice Portal. End User Quick Start Guide. Contact Customer Care at /26/2017 for additional assistance.
 SmartVoice Portal End User Quick Start Guide Contact Customer Care at 877-487-8722 3/26/2017 for additional assistance. 1 LOGIN Go to https://portal.sv.tpx.com Enter the Username and Password information
SmartVoice Portal End User Quick Start Guide Contact Customer Care at 877-487-8722 3/26/2017 for additional assistance. 1 LOGIN Go to https://portal.sv.tpx.com Enter the Username and Password information
CSE 127 Computer Security
 CSE 127 Computer Security Fall 2015 Web Security I: SQL injection Stefan Savage The Web creates new problems Web sites are programs Partially implemented in browser» Javascript, Java, Flash Partially implemented
CSE 127 Computer Security Fall 2015 Web Security I: SQL injection Stefan Savage The Web creates new problems Web sites are programs Partially implemented in browser» Javascript, Java, Flash Partially implemented
Hashes, MACs & Passwords. Tom Chothia Computer Security Lecture 5
 Hashes, MACs & Passwords Tom Chothia Computer Security Lecture 5 Today s Lecture Hash functions: Generates a unique short code from a large file Uses of hashes MD5, SHA1, SHA2, SHA3 Message Authentication
Hashes, MACs & Passwords Tom Chothia Computer Security Lecture 5 Today s Lecture Hash functions: Generates a unique short code from a large file Uses of hashes MD5, SHA1, SHA2, SHA3 Message Authentication
The LinkedIn Hack: Understanding Why It Was So Easy to Crack the Passwords
 The LinkedIn Hack: Understanding Why It Was So Easy to Crack the Passwords LinkedIn was breached in 2012 with a reported 6.5 million user accounts compromised. LinkedIn sent a request to known hacked users
The LinkedIn Hack: Understanding Why It Was So Easy to Crack the Passwords LinkedIn was breached in 2012 with a reported 6.5 million user accounts compromised. LinkedIn sent a request to known hacked users
AIR FORCE ASSOCIATION S CYBERPATRIOT NATIONAL YOUTH CYBER EDUCATION PROGRAM UNIT FIVE. Microsoft Windows Security.
 AIR FORCE ASSOCIATION S CYBERPATRIOT NATIONAL YOUTH CYBER EDUCATION PROGRAM UNIT FIVE Microsoft Windows Security www.uscyberpatriot.org AIR FORCE ASSOCIATION S CYBERPATRIOT NATIONAL YOUTH CYBER EDUCATION
AIR FORCE ASSOCIATION S CYBERPATRIOT NATIONAL YOUTH CYBER EDUCATION PROGRAM UNIT FIVE Microsoft Windows Security www.uscyberpatriot.org AIR FORCE ASSOCIATION S CYBERPATRIOT NATIONAL YOUTH CYBER EDUCATION
(Refer Slide Time: 01:12)
 Internet Technology Prof. Indranil Sengupta Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur Lecture No #22 PERL Part II We continue with our discussion on the Perl
Internet Technology Prof. Indranil Sengupta Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur Lecture No #22 PERL Part II We continue with our discussion on the Perl
Computer Forensics: Investigating File and Operating Systems, Wireless Networks, and Storage, 2nd Edition. Chapter 7 Application Password Crackers
 Computer Forensics: Investigating File and Operating Systems, Wireless Networks, and Storage, 2nd Edition Chapter 7 Application Password Crackers Objectives After completing this chapter, you should be
Computer Forensics: Investigating File and Operating Systems, Wireless Networks, and Storage, 2nd Edition Chapter 7 Application Password Crackers Objectives After completing this chapter, you should be
Quick Start: Permission requests and approvals
 Quick Start: Permission requests and approvals and approvals Microsoft Volume Licensing Field Center This guide shows field users the process for requesting access to the Volume Licensing Field Center
Quick Start: Permission requests and approvals and approvals Microsoft Volume Licensing Field Center This guide shows field users the process for requesting access to the Volume Licensing Field Center
P2P Programming Assignment
 P2P Programming Assignment Overview This project is to implement a Peer-to-Peer (P2P) networking project similar to a simplified Napster. You will provide a centralized server to handle cataloging the
P2P Programming Assignment Overview This project is to implement a Peer-to-Peer (P2P) networking project similar to a simplified Napster. You will provide a centralized server to handle cataloging the
New Password Reset for Dental Connect Provider
 New Password Reset for Dental Connect Provider 1 INDEX Access Dental Connect for Providers:... 3 1. Username verification:... 4 1.1 user name not provided:... 5 1.2 Invalid user name:... 6 1.3 Invalid
New Password Reset for Dental Connect Provider 1 INDEX Access Dental Connect for Providers:... 3 1. Username verification:... 4 1.1 user name not provided:... 5 1.2 Invalid user name:... 6 1.3 Invalid
Welcome to VFW WebMail. We hope you enjoy your new mailbox. For those users who had been using the old VFW WebMail system, a couple of items:
 VFW WebMail Help Help for VFW WebMail Users Getting Started Welcome to VFW WebMail. We hope you enjoy your new mailbox. For those users who had been using the old VFW WebMail system, a couple of items:
VFW WebMail Help Help for VFW WebMail Users Getting Started Welcome to VFW WebMail. We hope you enjoy your new mailbox. For those users who had been using the old VFW WebMail system, a couple of items:
CHAPTER 23. The Fortune Cookie
 CHAPTER 23 The Fortune Cookie OVERVIEW The fortune cookie script goes through a datafile of fortunes, chooses one of them at random, and then displays it on the Web. The script can also be configured to
CHAPTER 23 The Fortune Cookie OVERVIEW The fortune cookie script goes through a datafile of fortunes, chooses one of them at random, and then displays it on the Web. The script can also be configured to
Passwords CSC 193 WAKE FOREST. U N I V E R S I T Y Department of Computer Science. Spring 2014
 Passwords CSC 193 WAKE FOREST U N I V E R S I T Y Department of Computer Science Spring 2014 Unix Passwords In Unix, users are identified by user names Authenticated by passwords Therefore to login as
Passwords CSC 193 WAKE FOREST U N I V E R S I T Y Department of Computer Science Spring 2014 Unix Passwords In Unix, users are identified by user names Authenticated by passwords Therefore to login as
Practical Session 0 Introduction to Linux
 School of Computer Science and Software Engineering Clayton Campus, Monash University CSE2303 and CSE2304 Semester I, 2001 Practical Session 0 Introduction to Linux Novell accounts. Every Monash student
School of Computer Science and Software Engineering Clayton Campus, Monash University CSE2303 and CSE2304 Semester I, 2001 Practical Session 0 Introduction to Linux Novell accounts. Every Monash student
INTRODUCTION TO CGI PROGRAMMING By Jumail Bin Taliba, GMM, FSKSM, UTM INTRODUCTION
 INTRODUCTION TO CGI PROGRAMMING By Jumail Bin Taliba, GMM, FSKSM, UTM 2003 1. INTRODUCTION What is CGI? CGI-which stands for Common Gateway Interface- is a protocol (a way of doing things), not a programming
INTRODUCTION TO CGI PROGRAMMING By Jumail Bin Taliba, GMM, FSKSM, UTM 2003 1. INTRODUCTION What is CGI? CGI-which stands for Common Gateway Interface- is a protocol (a way of doing things), not a programming
Final Exam. IT 3203 Introduction to Web Development. Rescheduling Final Exams. PHP Arrays. Arrays as Hashes. Looping over Arrays
 IT 3203 Introduction to Web Development Introduction to PHP II April 5 Notice: This session is being recorded. Copyright 2007 by Bob Brown Final Exam The Registrar has released the final exam schedule.
IT 3203 Introduction to Web Development Introduction to PHP II April 5 Notice: This session is being recorded. Copyright 2007 by Bob Brown Final Exam The Registrar has released the final exam schedule.
TM-800/1000 and TS-700/900 Administrator Manual
 TM-800/1000 and TS-700/900 Administrator Manual Version 4.0 The RHUB web conferencing and remote support appliance RHUB Communications, Inc. 4340 Stevens Creek Blvd. Suite 282 San Jose, CA 95129 support@rhubcom.com
TM-800/1000 and TS-700/900 Administrator Manual Version 4.0 The RHUB web conferencing and remote support appliance RHUB Communications, Inc. 4340 Stevens Creek Blvd. Suite 282 San Jose, CA 95129 support@rhubcom.com
Assignment 3, Due October 4
 Assignment 3, Due October 4 1 Summary This assignment gives you practice with writing shell scripts. Shell scripting is also known as bash programming. Your shell is bash, and when you write a shell script
Assignment 3, Due October 4 1 Summary This assignment gives you practice with writing shell scripts. Shell scripting is also known as bash programming. Your shell is bash, and when you write a shell script
Outline. Lecture 8: CGI (Common Gateway Interface ) Common Gateway Interface (CGI) CGI Overview
 Outline Lecture 8: CGI (Common Gateway Interface ) CGI Overview Between Client and Handler Between Web Server and Handler Wendy Liu CSC309F Fall 2007 1 2 Common Gateway Interface (CGI) CGI Overview http://www.oreilly.com/openbook/cgi/
Outline Lecture 8: CGI (Common Gateway Interface ) CGI Overview Between Client and Handler Between Web Server and Handler Wendy Liu CSC309F Fall 2007 1 2 Common Gateway Interface (CGI) CGI Overview http://www.oreilly.com/openbook/cgi/
MANAGING LOCAL AUTHENTICATION IN WINDOWS
 MANAGING LOCAL AUTHENTICATION IN WINDOWS Credentials Manager Windows OS has a set of tools that help remedy some of the authentication challenges. For example, the Credential Manager in Windows 7 and newer
MANAGING LOCAL AUTHENTICATION IN WINDOWS Credentials Manager Windows OS has a set of tools that help remedy some of the authentication challenges. For example, the Credential Manager in Windows 7 and newer
By the end of this section of the practical, the students should be able to:
 By the end of this section of the practical, the students should be able to: Connecting to a MySQL database in PHP with the mysql_connect() and mysql_select_db() functions Trapping and displaying database
By the end of this section of the practical, the students should be able to: Connecting to a MySQL database in PHP with the mysql_connect() and mysql_select_db() functions Trapping and displaying database
Brute Force Attack. Ahmad Karawash 12/17/2015 1
 Brute Force Attack Ahmad Karawash 12/17/2015 1 Definition A Brute Force attack is a method or an algorithm to determine a password or user name using an automatic process. 12/17/2015 2 Way of work A Brute
Brute Force Attack Ahmad Karawash 12/17/2015 1 Definition A Brute Force attack is a method or an algorithm to determine a password or user name using an automatic process. 12/17/2015 2 Way of work A Brute
Outline of Lecture 5. Course Content. Objectives of Lecture 6 CGI and HTML Forms
 Web-Based Information Systems Fall 2004 CMPUT 410: CGI and HTML Forms Dr. Osmar R. Zaïane University of Alberta Outline of Lecture 5 Introduction Poor Man s Animation Animation with Java Animation with
Web-Based Information Systems Fall 2004 CMPUT 410: CGI and HTML Forms Dr. Osmar R. Zaïane University of Alberta Outline of Lecture 5 Introduction Poor Man s Animation Animation with Java Animation with
ORAC Match. User Manual for Support Workers. V1.0 Updated 13/11/2017
 ORAC Match User Manual for Support Workers V1.0 Updated 13/11/2017 1 Contents: The Login Screen: ORAC can be accessed through any web browser, smartphone or tablet via the following link; https://app.orac.support
ORAC Match User Manual for Support Workers V1.0 Updated 13/11/2017 1 Contents: The Login Screen: ORAC can be accessed through any web browser, smartphone or tablet via the following link; https://app.orac.support
Examples of Cisco APE Scenarios
 CHAPTER 5 This chapter describes three example scenarios with which to use Cisco APE: Access to Asynchronous Lines, page 5-1 Cisco IOS Shell, page 5-3 Command Authorization, page 5-5 Note For intructions
CHAPTER 5 This chapter describes three example scenarios with which to use Cisco APE: Access to Asynchronous Lines, page 5-1 Cisco IOS Shell, page 5-3 Command Authorization, page 5-5 Note For intructions
Area Access Manager User Guide
 Area Access Manager User Guide Area Access Manager User Guide Table of Contents Chapter 1: Introduction...9 Conventions Used in this Documentation... 9 Getting Started... 10 Licensing Requirements...
Area Access Manager User Guide Area Access Manager User Guide Table of Contents Chapter 1: Introduction...9 Conventions Used in this Documentation... 9 Getting Started... 10 Licensing Requirements...
Indian Institute of Technology Kharagpur. PERL Part II. Prof. Indranil Sen Gupta Dept. of Computer Science & Engg. I.I.T.
 Indian Institute of Technology Kharagpur PERL Part II Prof. Indranil Sen Gupta Dept. of Computer Science & Engg. I.I.T. Kharagpur, INDIA Lecture 22: PERL Part II On completion, the student will be able
Indian Institute of Technology Kharagpur PERL Part II Prof. Indranil Sen Gupta Dept. of Computer Science & Engg. I.I.T. Kharagpur, INDIA Lecture 22: PERL Part II On completion, the student will be able
Lesson 3. Form By Raymond Tsang. Certificate Programme in Cyber Security
 Lesson 3 Form By Raymond Tsang Certificate Programme in Cyber Security What is a form How to create a form Getting input from users Generate a result It s a section of a document containing normal content,
Lesson 3 Form By Raymond Tsang Certificate Programme in Cyber Security What is a form How to create a form Getting input from users Generate a result It s a section of a document containing normal content,
User Authentication and Passwords
 User Authentication and : Security and Cryptography Sirindhorn International Institute of Technology Thammasat University Prepared by Steven Gordon on 31 October 2012 Y12S2L11, Steve/Courses/2012/s2/css322/lectures/passwords.tex,
User Authentication and : Security and Cryptography Sirindhorn International Institute of Technology Thammasat University Prepared by Steven Gordon on 31 October 2012 Y12S2L11, Steve/Courses/2012/s2/css322/lectures/passwords.tex,
Main Documentation. Contents
 TM Main Documentation This document provides an overview of the FormRouter service including: how to configure your HTML forms for use with FormRouter, and how to use the FormRouter Desktop Retrieval tool.
TM Main Documentation This document provides an overview of the FormRouter service including: how to configure your HTML forms for use with FormRouter, and how to use the FormRouter Desktop Retrieval tool.
Network Online Services How to Register Guide
 Network Online Services How to Register Guide June 2016 How to Register... 2 Subscription... 5 Update My Profile... 7 Update Registration Details... 7 Contact Details / Postal Address... 15 How To Register
Network Online Services How to Register Guide June 2016 How to Register... 2 Subscription... 5 Update My Profile... 7 Update Registration Details... 7 Contact Details / Postal Address... 15 How To Register
User Directories. Overview, Pros and Cons
 User Directories Overview, Pros and Cons Overview Secure ISMS can operate with one or more of the following user directories. Secure ISMS Users (ISMS) Internal users local to the Secure ISMS application
User Directories Overview, Pros and Cons Overview Secure ISMS can operate with one or more of the following user directories. Secure ISMS Users (ISMS) Internal users local to the Secure ISMS application
CHAPTER 2. Troubleshooting CGI Scripts
 CHAPTER 2 Troubleshooting CGI Scripts OVERVIEW Web servers and their CGI environment can be set up in a variety of ways. Chapter 1 covered the basics of the installation and configuration of scripts. However,
CHAPTER 2 Troubleshooting CGI Scripts OVERVIEW Web servers and their CGI environment can be set up in a variety of ways. Chapter 1 covered the basics of the installation and configuration of scripts. However,
How to Set Up a Custom Challenge Page for Authentication
 How to Set Up a Custom Challenge Page for Authentication Setting up a custom challenge page is a three step process: 1. Create a custom challenge page. Deploy the created custom challenge page on your
How to Set Up a Custom Challenge Page for Authentication Setting up a custom challenge page is a three step process: 1. Create a custom challenge page. Deploy the created custom challenge page on your
Course Outline Repository Guide
 Contents... 1 How do I access the Course Outline Repository?... 1 How do I use the Course Outline Repository?... 2 How do I search the Course Repository?... 2 Where do I download the course outline?...
Contents... 1 How do I access the Course Outline Repository?... 1 How do I use the Course Outline Repository?... 2 How do I search the Course Repository?... 2 Where do I download the course outline?...
ETHICAL HACKING LAB SERIES. Lab 15: Abusing SYSTEMS
 ETHICAL HACKING LAB SERIES Lab 15: Abusing SYSTEMS Certified Ethical Hacking Domain: Denial of Service Document Version: 2015-08-14 otherwise noted, is licensed under the Creative Commons Attribution 3.0
ETHICAL HACKING LAB SERIES Lab 15: Abusing SYSTEMS Certified Ethical Hacking Domain: Denial of Service Document Version: 2015-08-14 otherwise noted, is licensed under the Creative Commons Attribution 3.0
The first step you should take in order to be able to use the system is accessing our web page. Follow these steps to gain access to the system:
 User s Manual A. Requirements ASI on-line has been develop to be use with Microsoft Internet Explorer 5 or latter. You can download the latest version of the browser by logging into http://www.microsoft.com/downloads/search.asp
User s Manual A. Requirements ASI on-line has been develop to be use with Microsoft Internet Explorer 5 or latter. You can download the latest version of the browser by logging into http://www.microsoft.com/downloads/search.asp
Table of Contents Step One: Create a new account... 2 Step Two: Log-in to Inspira... 5 Step Three: Sign up for mandatory courses...
 You can now access Inspira mandatory courses through elearning.un.org!!!! In this quick guide you will learn how to register and find mandatory courses on Inspira. If you are new to learning, please start
You can now access Inspira mandatory courses through elearning.un.org!!!! In this quick guide you will learn how to register and find mandatory courses on Inspira. If you are new to learning, please start
Regular expressions and case insensitivity
 Regular expressions and case insensitivity As previously mentioned, you can make matching case insensitive with the i flag: /\b[uu][nn][ii][xx]\b/; # explicitly giving case folding /\bunix\b/i; # using
Regular expressions and case insensitivity As previously mentioned, you can make matching case insensitive with the i flag: /\b[uu][nn][ii][xx]\b/; # explicitly giving case folding /\bunix\b/i; # using
Princess Nourah bint Abdulrahman University. Computer Sciences Department
 Princess Nourah bint Abdulrahman University Computer Sciences Department 1 And use http://www.w3schools.com/ PHP Part 3 Objectives Creating a new MySQL Database using Create & Check connection with Database
Princess Nourah bint Abdulrahman University Computer Sciences Department 1 And use http://www.w3schools.com/ PHP Part 3 Objectives Creating a new MySQL Database using Create & Check connection with Database
BTEC Level 3. Unit 32 Network System Security Password Authentication and Protection. Level 3 Unit 32 Network System Security
 BTEC Level 3 Unit 32 Network System Security Password Authentication and Protection Passwords Why are they important? Passwords are cheap to deploy, but also act as the first line of defense in a security
BTEC Level 3 Unit 32 Network System Security Password Authentication and Protection Passwords Why are they important? Passwords are cheap to deploy, but also act as the first line of defense in a security
Web Engineering (CC 552)
 Web Engineering (CC 552) Introduction Dr. Mohamed Magdy mohamedmagdy@gmail.com Room 405 (CCIT) Course Goals n A general understanding of the fundamentals of the Internet programming n Knowledge and experience
Web Engineering (CC 552) Introduction Dr. Mohamed Magdy mohamedmagdy@gmail.com Room 405 (CCIT) Course Goals n A general understanding of the fundamentals of the Internet programming n Knowledge and experience
Joomla Pre-install Tasks
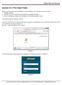 Joomla 3.0.1 Pre-install Tasks Before commencing the actual installation of Joomla CMS on your webhost you have to create: A MySQL database A MySQL user ( with password based access to the MySQL database
Joomla 3.0.1 Pre-install Tasks Before commencing the actual installation of Joomla CMS on your webhost you have to create: A MySQL database A MySQL user ( with password based access to the MySQL database
Copyright
 This video will look at configuring the default password policy in Active Directory. These setting determines setting like how long a user password will be, if the password needs to complex, and how many
This video will look at configuring the default password policy in Active Directory. These setting determines setting like how long a user password will be, if the password needs to complex, and how many
Lieberman Software. White Paper
 White Paper: Solving the Common Administrator Account Configuration Problem with the User Manager Pro Random Password Generator Module Rev 1 October 16, 2002 Written by Philip Lieberman (phil@lanicu.com)
White Paper: Solving the Common Administrator Account Configuration Problem with the User Manager Pro Random Password Generator Module Rev 1 October 16, 2002 Written by Philip Lieberman (phil@lanicu.com)
Programming Project #6: Password File Cracker
 CSE231 Spring 2017 Programming Project #6: Password File Cracker (Edits: changed itertools permutations to product either works for these passwords, but product is the correct one. Removed lists and tuples
CSE231 Spring 2017 Programming Project #6: Password File Cracker (Edits: changed itertools permutations to product either works for these passwords, but product is the correct one. Removed lists and tuples
Module Certification and Testing
 Module 20 Certification and Testing Certification and Testing Certification requirements The certification exam Online Timed Instant scoring Score required for certification Taking the exam Receiving your
Module 20 Certification and Testing Certification and Testing Certification requirements The certification exam Online Timed Instant scoring Score required for certification Taking the exam Receiving your
Getting Started. Logging In and Out. Adapted from Practical Unix and Programming Hunter College
 Getting Started Logging In and Out Adapted from Practical Unix and Programming Hunter College Copyright 2006 Stewart Weiss Getting started: logging in and out Every user in UNIX has a username (also called
Getting Started Logging In and Out Adapted from Practical Unix and Programming Hunter College Copyright 2006 Stewart Weiss Getting started: logging in and out Every user in UNIX has a username (also called
Oracle Database Security and Audit. Authentication and authorization
 Copyright 2014, Oracle Database Security and Audit Beyond Checklists Authentication and authorization Copyright 2014, Learning objectives Understand authentication Understand authorization Understand the
Copyright 2014, Oracle Database Security and Audit Beyond Checklists Authentication and authorization Copyright 2014, Learning objectives Understand authentication Understand authorization Understand the
OPEN BOOK. OPEN NOTES. OPEN MIND.
 CS 795/895:.Net Security Summer 2014 Examination I July 16, 2014 515pm-9pm Points 100 Answer ALL questions In answering the following questions, assume Visual Studio.Net and C#. Do not cut and paste information
CS 795/895:.Net Security Summer 2014 Examination I July 16, 2014 515pm-9pm Points 100 Answer ALL questions In answering the following questions, assume Visual Studio.Net and C#. Do not cut and paste information
BraindumpsIT. BraindumpsIT - IT Certification Company provides Braindumps pdf!
 BraindumpsIT http://www.braindumpsit.com BraindumpsIT - IT Certification Company provides Braindumps pdf! Exam : GPEN Title : GIAC Certified Penetration Tester Vendor : GIAC Version : DEMO Get Latest &
BraindumpsIT http://www.braindumpsit.com BraindumpsIT - IT Certification Company provides Braindumps pdf! Exam : GPEN Title : GIAC Certified Penetration Tester Vendor : GIAC Version : DEMO Get Latest &
PERL. Pattern Extraction and Reporting Language. Example: $x = 10 $value = $x + 1 $word = "hello"
 PERL Pattern Extraction and Reporting Language Example: Web page serving through CGI: Perl is used extensively in serving up content when run in concert with a web-server. Talking to web sites and reporting
PERL Pattern Extraction and Reporting Language Example: Web page serving through CGI: Perl is used extensively in serving up content when run in concert with a web-server. Talking to web sites and reporting
Persistent systems. Traditional software: Data stored outside of program. Program
 Persistent systems Traditional software: Data stored outside of program Program Persistent systems: Data part of program Execution never stops Transaction systems Program 1 Development of persistent languages
Persistent systems Traditional software: Data stored outside of program Program Persistent systems: Data part of program Execution never stops Transaction systems Program 1 Development of persistent languages
Enroll in MyCardStatement.com Client User Guide
 Enroll in MyCardStatement.com Client User Guide GETTING STARTED Visit MyCardStatement.com. Click on Enroll Now! ACCOUNT ENROLLMENT Input your full credit card number on the face of the card (do not use
Enroll in MyCardStatement.com Client User Guide GETTING STARTED Visit MyCardStatement.com. Click on Enroll Now! ACCOUNT ENROLLMENT Input your full credit card number on the face of the card (do not use
This user guide covers how existing CSUFEDU Qualtrics account users can migrate their account from the CSUFEDU brand to the Fullerton brand.
 Quick Reference Guide Converting Your Qualtrics Account from CSUFEDU This user guide covers how existing CSUFEDU Qualtrics account users can migrate their account from the CSUFEDU brand to the Fullerton
Quick Reference Guide Converting Your Qualtrics Account from CSUFEDU This user guide covers how existing CSUFEDU Qualtrics account users can migrate their account from the CSUFEDU brand to the Fullerton
Mt. Lebanon School District 7 Horsman Drive Pittsburgh, Pennsylvania
 Accessing your Individual Multimedia Area Each faculty and staff member with an individual user account will have their own space to store multimedia files. The multimedia can be easily linked to a website,
Accessing your Individual Multimedia Area Each faculty and staff member with an individual user account will have their own space to store multimedia files. The multimedia can be easily linked to a website,
Joomla 3.X Global Settings Part III Server Settings
 Joomla 3.X Global Settings Part III Server Settings Diagram 1 Path to Temp Folder: This is a text box adjacent to this prompt which holds the path to Joomla s temp folder on the web server. This is the
Joomla 3.X Global Settings Part III Server Settings Diagram 1 Path to Temp Folder: This is a text box adjacent to this prompt which holds the path to Joomla s temp folder on the web server. This is the
Lecture 5 Security and User Input. INLS 760 Web Databases Spring 2013 Rob Capra
 Lecture 5 Security and User Input INLS 760 Web Databases Spring 2013 Rob Capra Security What data should be stored on a web server? HTTP logs? Users account information? Passwords? Possible harms Exposure
Lecture 5 Security and User Input INLS 760 Web Databases Spring 2013 Rob Capra Security What data should be stored on a web server? HTTP logs? Users account information? Passwords? Possible harms Exposure
Password cracking. IN Ethical Hacking. Bruvoll & Sørby. Department of Informatics 1 / 46
 Password cracking IN5290 - Ethical Hacking Bruvoll & Sørby Department of Informatics 2018 1 / 46 Agenda About passwords Cracking passwords 2 / 46 About passwords 3 / 46 Passwords as authentication Providing
Password cracking IN5290 - Ethical Hacking Bruvoll & Sørby Department of Informatics 2018 1 / 46 Agenda About passwords Cracking passwords 2 / 46 About passwords 3 / 46 Passwords as authentication Providing
Controlling Website Account Information. A recent survey done by Privacy Rights Clearinghouse shows that in the past five years
 Colson 1 Alex Colson Dr. Lunsford Information Security Management 10 July 2007 Controlling Website Account Information A recent survey done by Privacy Rights Clearinghouse shows that in the past five years
Colson 1 Alex Colson Dr. Lunsford Information Security Management 10 July 2007 Controlling Website Account Information A recent survey done by Privacy Rights Clearinghouse shows that in the past five years
CNIT 124: Advanced Ethical Hacking. Ch 9: Password Attacks
 CNIT 124: Advanced Ethical Hacking Ch 9: Password Attacks Topics Password Management Online Password Attacks Offline Password Attacks Dumping Passwords from RAM Password Management Password Alternatives
CNIT 124: Advanced Ethical Hacking Ch 9: Password Attacks Topics Password Management Online Password Attacks Offline Password Attacks Dumping Passwords from RAM Password Management Password Alternatives
I started off with a quick nmap scan, which showed both port 80 and 443 open.
 Mr-Robot: 1 Walkthrough Author: mrb3n Download location: https://download.vulnhub.com/mrrobot/mrrobot.ova Goal: Find 3 keys hidden in different locations -----------------------------------------------------------------------------------------------------------------
Mr-Robot: 1 Walkthrough Author: mrb3n Download location: https://download.vulnhub.com/mrrobot/mrrobot.ova Goal: Find 3 keys hidden in different locations -----------------------------------------------------------------------------------------------------------------
Web technologies. Web. basic components. embellishments in browser. DOM (document object model)
 Web technologies DOM (document object model) what's on the page and how it can be manipulated forms / CGI (common gateway interface) extract info from a form, create a page, send it back server side code
Web technologies DOM (document object model) what's on the page and how it can be manipulated forms / CGI (common gateway interface) extract info from a form, create a page, send it back server side code
A control expression must evaluate to a value that can be interpreted as true or false.
 Control Statements Control Expressions A control expression must evaluate to a value that can be interpreted as true or false. How a control statement behaves depends on the value of its control expression.
Control Statements Control Expressions A control expression must evaluate to a value that can be interpreted as true or false. How a control statement behaves depends on the value of its control expression.
Regular expressions and case insensitivity
 Regular expressions and case insensitivity As previously mentioned, you can make matching case insensitive with the i flag: /\b[uu][nn][ii][xx]\b/; /\bunix\b/i; # explicitly giving case folding # using
Regular expressions and case insensitivity As previously mentioned, you can make matching case insensitive with the i flag: /\b[uu][nn][ii][xx]\b/; /\bunix\b/i; # explicitly giving case folding # using
SPECIAL ARBITRATION ARBITRATOR CERTIFICATION USER GUIDE
 SPECIAL ARBITRATION ARBITRATOR CERTIFICATION USER GUIDE A. CERTIFICATION SITE LOGIN 1. Enter http://training.arbfile.org into your Web browser. This link will take you to the Certification site homepage
SPECIAL ARBITRATION ARBITRATOR CERTIFICATION USER GUIDE A. CERTIFICATION SITE LOGIN 1. Enter http://training.arbfile.org into your Web browser. This link will take you to the Certification site homepage
GNU ccscript Scripting Guide IV
 GNU ccscript Scripting Guide IV David Sugar GNU Telephony 2008-08-20 (The text was slightly edited in 2017.) Contents 1 Introduction 1 2 Script file layout 2 3 Statements and syntax 4 4 Loops and conditionals
GNU ccscript Scripting Guide IV David Sugar GNU Telephony 2008-08-20 (The text was slightly edited in 2017.) Contents 1 Introduction 1 2 Script file layout 2 3 Statements and syntax 4 4 Loops and conditionals
5/15/2009. Introduction
 Part 1: Cyber-Graffiti You know, I don t know what I hate more, wearing your face, or wearing your body. Look, why don t we just give them back to each other and call it even, okay? Castor Troy (Nicolas
Part 1: Cyber-Graffiti You know, I don t know what I hate more, wearing your face, or wearing your body. Look, why don t we just give them back to each other and call it even, okay? Castor Troy (Nicolas
Attacks Against Websites. Tom Chothia Computer Security, Lecture 11
 Attacks Against Websites Tom Chothia Computer Security, Lecture 11 A typical web set up TLS Server HTTP GET cookie Client HTML HTTP file HTML PHP process Display PHP SQL Typical Web Setup HTTP website:
Attacks Against Websites Tom Chothia Computer Security, Lecture 11 A typical web set up TLS Server HTTP GET cookie Client HTML HTTP file HTML PHP process Display PHP SQL Typical Web Setup HTTP website:
ORAC Match. User Manual for Support Workers. V1.0 Updated 13/11/2017
 ORAC Match User Manual for Support Workers V1.0 Updated 13/11/2017 1 Contents: The Login Screen: ORAC can be accessed through any web browser, smartphone or tablet via the following link; https://app.orac.support
ORAC Match User Manual for Support Workers V1.0 Updated 13/11/2017 1 Contents: The Login Screen: ORAC can be accessed through any web browser, smartphone or tablet via the following link; https://app.orac.support
Examples of Using the ARGV Array. Loop Control Operators. Next Operator. Last Operator. Perl has three loop control operators.
 Examples of Using the ARGV Array # mimics the Unix echo utility foreach (@ARGV) { print $_ ; print \n ; # count the number of command line arguments $i = 0; foreach (@ARGV) { $i++; print The number of
Examples of Using the ARGV Array # mimics the Unix echo utility foreach (@ARGV) { print $_ ; print \n ; # count the number of command line arguments $i = 0; foreach (@ARGV) { $i++; print The number of
Should you encounter any issues or have questions as you go through this registration process, please send an to:
 User Registration In order to use EFIS 2.0, a one-time registration process is required. This document outlines the steps required to register your user account and access EFIS 2.0: This registration process
User Registration In order to use EFIS 2.0, a one-time registration process is required. This document outlines the steps required to register your user account and access EFIS 2.0: This registration process
Pastel Evolution BIC Web Reporting User Guide
 Pastel Evolution BIC Web Reporting User Guide Prerequisites: Pastel Evolution Business Intelligence Centre.NET Framework 3.5 Internet Information Services (version 6 and upwards) Microsoft Excel 2003 /
Pastel Evolution BIC Web Reporting User Guide Prerequisites: Pastel Evolution Business Intelligence Centre.NET Framework 3.5 Internet Information Services (version 6 and upwards) Microsoft Excel 2003 /
Requesting Accommodations
 PURPOSE: To provide instructions on the process for Testers. IMPORTANT: It is important that Testers use Chrome, Safari, Firefox, IE11 or higher. Also, you can use mobile browsers for all of the above
PURPOSE: To provide instructions on the process for Testers. IMPORTANT: It is important that Testers use Chrome, Safari, Firefox, IE11 or higher. Also, you can use mobile browsers for all of the above
Network Camera Security Guide
 Network Camera Security Guide January 2018 About This Document This Guide includes instructions for using and managing the product safely. User Manual COPYRIGHT 2018 Hangzhou Hikvision Digital Technology
Network Camera Security Guide January 2018 About This Document This Guide includes instructions for using and managing the product safely. User Manual COPYRIGHT 2018 Hangzhou Hikvision Digital Technology
Overview. Your Postini Username and Password. Recovering Your Postini Password
 Postini User Guide Overview... 2 Your Postini Username and Password... 2 Recovering Your Postini Password... 2 Logging Into Postini... 6 Viewing Quarantine... 9 Delivering Messages... 9 Accessing Your
Postini User Guide Overview... 2 Your Postini Username and Password... 2 Recovering Your Postini Password... 2 Logging Into Postini... 6 Viewing Quarantine... 9 Delivering Messages... 9 Accessing Your
Identity, Authentication, and Access Control
 Identity, Authentication, and Access Control License This work by Z. Cliffe Schreuders at Leeds Metropolitan University is licensed under a Creative Commons Attribution-ShareAlike 3.0 Unported License.
Identity, Authentication, and Access Control License This work by Z. Cliffe Schreuders at Leeds Metropolitan University is licensed under a Creative Commons Attribution-ShareAlike 3.0 Unported License.
Survey Creation Workflow These are the high level steps that are followed to successfully create and deploy a new survey:
 Overview of Survey Administration The first thing you see when you open up your browser to the Ultimate Survey Software is the Login Page. You will find that you see three icons at the top of the page,
Overview of Survey Administration The first thing you see when you open up your browser to the Ultimate Survey Software is the Login Page. You will find that you see three icons at the top of the page,
