Stunnel Guide for Trevance 19 April 2017
|
|
|
- Magdalen Miller
- 5 years ago
- Views:
Transcription
1 Stunnel Guide for Trevance 19 April 2017 This guide is for stunnel.conf version The stunnel.conf version number is near the top of the file. When communicating with the Trevance payment application from a remote server, the communications between the two servers must be secured. Auric requires Trevance be operated behind a secure proxy. Any proxy such as stunnel, Microsoft IIS, nginx, or Apache is suitable. The stunnel proxy service provides a secure wrapper for inbound Trevance HTTPS traffic. Outbound socket connections can also be run through stunnel. The stunnel proxy provides full support for TLSv1.2 and can be upgraded independently of the Trevance application. This allows you to regularly upgrade your inbound security without impacting the underlying Trevance application. From the stunnel.org web site, Stunnel is a proxy designed to add TLS encryption functionality to existing clients and servers without any changes in the programs' code. Its architecture is optimized for security, portability, and scalability (including load-balancing), making it suitable for large deployments. Auric deploys stunnel in several production environments. It is available for many operating systems including Windows, Linux, and OS X. This guide focuses on a Windows deployment. A single stunnel installation can support both Trevance and CN!Express configurations. Please refer to the CN!Express stunnel configuration guide for details. A wide array of stunnel information is available on the Internet. Auric Systems International is a Validated Level 1 PCI Service Provider
2 Data Flow Server Transaction Source Real-time transactions to Trevance Stunnel Config File Sections tr_https Trevance Payment Application tr out Payment Processor The above diagram is a high-level overview of a transaction data flow once stunnel is installed and configured. Transactions are sent via HTTPS (TLSv1.2) to the default Trevance port. Stunnel is configured to accept HTTPS transactions. This configuration is in the tr_https section of the included stunnel.conf file. Stunnel forwards the transaction via HTTP to the local Trevance application. Trevance transforms the request and sends it back to stunnel via a socket connection. Stunnel has configuration sections (tr_xyz_out) for each payment processor connection. Stunnel forwards the transaction via secure socket (TLSv1.2) to the payment processor. Auric Systems International is a Validated PCI Level 1 Service Provider Page 2 of 6
3 Install Stunnel for Windows Download the latest stunnel for Windows from: Confirm the SHA256 signature matches the signature from the download site. The download you choose will have a corresponding signature download file ending in sha256. Run the installer. When prompted to Choose Components, choose the default (Tools and shortcuts). Recommend you accept the default installation location: C:\Program Files (x86)\stunnel. The installer prompts you to create client-side certificates (.pem files). Answer the following questions: Country Name (2 letter code): State or Province Name: Locality Name (city): Organizational Name (company): Organizational Unit Name (typically left blank): Common Name: Hostname of the server running stunnel. Edit the provided stunnel.conf file if necessary (see below). Copy your edited stunnel.conf file to: C:\ Program Files (x86)\stunnel\config\stunnel.conf Restart stunnel. NOTE: The installed stunnel SSL certificate has a one-year lifetime. It will expire in a year. Auric provides a batch file to generate a certificate that is good for ten (10) years. Download the CreateNewStunnelCert.bat batch file from the Auric stunnel download area. Move the batch file into the stunnel configuration directory: C:\Program Files (x86)\stunnel\ Right click CreateNewStunnelCert.bat and select Run as Administrator. Answer the following questions: Country Name (2 letter code): State or Province Name: Locality Name (city): Organizational Name (company): Organizational Unit Name (typically left blank): Common Name: Hostname of the server running stunnel. The new ten (10) year certificate is generated and installed. Auric Systems International is a Validated PCI Level 1 Service Provider Page 3 of 6
4 Running stunnel as an Application After the initial installation, it is useful to run stunnel as an application (vs. a service). Start stunnel from: Start>All Programs>stunnel>stunnel GUI start Running stunnel as a service allows you to quickly restart it and to also view the generated log files while working on the initial Trevance configuration. Running stunnel as a Service Install the stunnel service from the Start menu. Then use normal services controls. Start>All Programs>stunnel Service Install Configure the Trevance Application Use the Trevance configuration utility to set the Web Interface Settings as follows: Server Port: Server IP: All Host Interfaces These settings allow Trevance to listen to the default stunnel configuration. Auric Systems International is a Validated PCI Level 1 Service Provider Page 4 of 6
5 The stunnel.conf Configuration File The configuration file can be edited with a standard text editor (e.g., Notepad or Notepad++). Do not use a word processor such as WordPad or Word. General Settings The logging levels are controlled by the debug line. Values can be from 0 through 7. 0 logs only catastrophic messages and 7 logs a lot of debug information. The default setting is 5. You may want to set this to 6 (or even 7) while working on initial configurations. Example: Debug = 5 tr_https The tr_https section controls where stunnel listens for incoming HTTPS requests and determines the port on which the transactions are forwarded to Trevance. The defaults are as follows: [tr_https] accept = 8004 connect = :10004 TIMEOUTclose = 70 The default settings expect incoming HTTPS transactions on port 8004 and will forward the requests via HTTP to a Trevance listening on port The TIMEOUTclose setting determine the number of seconds to wait for a response. Processor Specific Settings The stunnel.conf file contains sections for each payment processor s test and production URLs. By default all the sections are enabled. You can leave them enabled or comment out the sections you do not use. Please refer to the following processor-specific sections for details. Auric Systems International is a Validated PCI Level 1 Service Provider Page 5 of 6
6 Outbound Connectivity to Payment Processor Trevance Configuration The Chase Paymentech configuration is shown above. The configuration is similar for all Trevance supported payment processors. Configure the Trevance Socket IP settings as follows: Socket IP: Port: Socket 2 IP: Port stunnel Configuration You must edit the stunnel.conf file to enter the IP and Ports provided by your payment proecssor for your installation. Edit the stunnel.conf file and locate the tr_01_out and tr_02_out sections. Change the connect entries to the processorsupplied settings. Restart stunnel when done. Auric Systems International is a Validated PCI Level 1 Service Provider Page 6 of 6
Stunnel Guide for CN!Express 3 April 2017
 Stunnel Guide for CN!Express 3 April 2017 When communicating with the CN!Express payment application from a remote server, the communications between the two servers must be secured. Auric requires CN!Express
Stunnel Guide for CN!Express 3 April 2017 When communicating with the CN!Express payment application from a remote server, the communications between the two servers must be secured. Auric requires CN!Express
Load Balancing Nginx Web Servers with OWASP Top 10 WAF in Azure
 Load Balancing Nginx Web Servers with OWASP Top 10 WAF in Azure Quick Reference Guide v1.0.2 ABOUT THIS GUIDE This document provides a quick reference guide on how to load balance Nginx Web Servers and
Load Balancing Nginx Web Servers with OWASP Top 10 WAF in Azure Quick Reference Guide v1.0.2 ABOUT THIS GUIDE This document provides a quick reference guide on how to load balance Nginx Web Servers and
Configure the DNS server. Secure communications for both the application server and the meeting server (HTTP and RTMP).
 Configure software-based SSL When you configure software-based SSL, you can secure network connections to the web application server (HTTPS protocol), the meeting server (RTMPS protocol), or both. No matter
Configure software-based SSL When you configure software-based SSL, you can secure network connections to the web application server (HTTPS protocol), the meeting server (RTMPS protocol), or both. No matter
Load Balancing Nginx Web Servers with OWASP Top 10 WAF in AWS
 Load Balancing Nginx Web Servers with OWASP Top 10 WAF in AWS Quick Reference Guide V1.0.2 ABOUT THIS GUIDE This document provides a quick reference guide on how to load balance Nginx Web Servers and configure
Load Balancing Nginx Web Servers with OWASP Top 10 WAF in AWS Quick Reference Guide V1.0.2 ABOUT THIS GUIDE This document provides a quick reference guide on how to load balance Nginx Web Servers and configure
VMware Identity Manager Connector Installation and Configuration (Legacy Mode)
 VMware Identity Manager Connector Installation and Configuration (Legacy Mode) VMware Identity Manager This document supports the version of each product listed and supports all subsequent versions until
VMware Identity Manager Connector Installation and Configuration (Legacy Mode) VMware Identity Manager This document supports the version of each product listed and supports all subsequent versions until
Purpose. Target Audience. Solution Overview NCPA. Using NCPA For Passive Checks
 Using For Passive Checks Purpose This document describes how to configure the Nagios Cross Platform Agent () to send passive check results to Nagios XI or Nagios Core using Nagios Remote Data Processor
Using For Passive Checks Purpose This document describes how to configure the Nagios Cross Platform Agent () to send passive check results to Nagios XI or Nagios Core using Nagios Remote Data Processor
Configuring SSL CHAPTER
 7 CHAPTER This chapter describes the steps required to configure your ACE appliance as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination. The topics included in this section
7 CHAPTER This chapter describes the steps required to configure your ACE appliance as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination. The topics included in this section
CN!Express R User Guide
 CN!Express R User Guide Auric Systems International Payment Processing Simplified R 7 March 2013 Version 5.0 Copyright c 1994-2012 Auric Systems International. All rights reserved. Contents 1 Welcome
CN!Express R User Guide Auric Systems International Payment Processing Simplified R 7 March 2013 Version 5.0 Copyright c 1994-2012 Auric Systems International. All rights reserved. Contents 1 Welcome
Configuring SSL. SSL Overview CHAPTER
 7 CHAPTER This topic describes the steps required to configure your ACE appliance as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination. The topics included in this section are:
7 CHAPTER This topic describes the steps required to configure your ACE appliance as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination. The topics included in this section are:
Load Balancing Web Servers with OWASP Top 10 WAF in Azure
 Load Balancing Web Servers with OWASP Top 10 WAF in Azure Quick Reference Guide v1.0.3 ABOUT THIS GUIDE This document provides a quick reference guide on how to load balance Web Servers and configure a
Load Balancing Web Servers with OWASP Top 10 WAF in Azure Quick Reference Guide v1.0.3 ABOUT THIS GUIDE This document provides a quick reference guide on how to load balance Web Servers and configure a
Purpose. Target Audience. Overview. Prerequisites. Nagios Log Server. Sending NXLogs With SSL/TLS
 Purpose This document describes how to setup encryption between and NXLog on Windows using self signed certificates. Target Audience This document is intended for use by Administrators who would like encryption
Purpose This document describes how to setup encryption between and NXLog on Windows using self signed certificates. Target Audience This document is intended for use by Administrators who would like encryption
Configuring SSL. SSL Overview CHAPTER
 CHAPTER 8 Date: 4/23/09 This topic describes the steps required to configure your ACE (both the ACE module and the ACE appliance) as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination.
CHAPTER 8 Date: 4/23/09 This topic describes the steps required to configure your ACE (both the ACE module and the ACE appliance) as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination.
VMware Horizon View Deployment
 VMware Horizon View provides end users with access to their machines and applications through a unified workspace across multiple devices, locations, and connections. The Horizon View Connection Server
VMware Horizon View provides end users with access to their machines and applications through a unified workspace across multiple devices, locations, and connections. The Horizon View Connection Server
Secure Communications Over a Network
 Secure Communications Over a Network Course: MITS:5400G Proffessor: Dr. Xiaodong Lin By: Geoff Vaughan 100309160 March 20th 2012 Abstract The purpose of this experiment is to transmit an encrypted message
Secure Communications Over a Network Course: MITS:5400G Proffessor: Dr. Xiaodong Lin By: Geoff Vaughan 100309160 March 20th 2012 Abstract The purpose of this experiment is to transmit an encrypted message
How to Make the Client IP Address Available to the Back-end Server
 How to Make the Client IP Address Available to the Back-end Server For Layer 4 - UDP and Layer 4 - TCP services, the actual client IP address is passed to the server in the TCP header. No further configuration
How to Make the Client IP Address Available to the Back-end Server For Layer 4 - UDP and Layer 4 - TCP services, the actual client IP address is passed to the server in the TCP header. No further configuration
An internal CA that is part of your IT infrastructure, like a Microsoft Windows CA
 Purpose This document will describe how to setup to use SSL/TLS to provide encrypted connections to the. This document can also be used as an initial point for troubleshooting SSL/TLS connections. Target
Purpose This document will describe how to setup to use SSL/TLS to provide encrypted connections to the. This document can also be used as an initial point for troubleshooting SSL/TLS connections. Target
Secure Web Appliance. SSL Intercept
 Secure Web Appliance SSL Intercept Table of Contents 1. Introduction... 1 1.1. About CYAN Secure Web Appliance... 1 1.2. About SSL Intercept... 1 1.3. About this Manual... 1 1.3.1. Document Conventions...
Secure Web Appliance SSL Intercept Table of Contents 1. Introduction... 1 1.1. About CYAN Secure Web Appliance... 1 1.2. About SSL Intercept... 1 1.3. About this Manual... 1 1.3.1. Document Conventions...
Deployment Guide AX Series with Oracle E-Business Suite 12
 Deployment Guide AX Series with Oracle E-Business Suite 12 DG_OEBS_032013.1 TABLE OF CONTENTS 1 Introduction... 4 2 Deployment Prerequisites... 4 3 Oracle E-Business Topology... 5 4 Accessing the AX Series
Deployment Guide AX Series with Oracle E-Business Suite 12 DG_OEBS_032013.1 TABLE OF CONTENTS 1 Introduction... 4 2 Deployment Prerequisites... 4 3 Oracle E-Business Topology... 5 4 Accessing the AX Series
AD Sync Client Install Guide. Contents
 AD Sync Client Install Guide Contents AD Sync Client Install Guide... 1 Introduction... 2 Deployment Prerequisites... 2 Configure SQL Prerequisites... 3 Switch SQL to Mixed Mode authentication... 3 Create
AD Sync Client Install Guide Contents AD Sync Client Install Guide... 1 Introduction... 2 Deployment Prerequisites... 2 Configure SQL Prerequisites... 3 Switch SQL to Mixed Mode authentication... 3 Create
Configuring SSL Security
 CHAPTER9 This chapter describes how to configure SSL on the Cisco 4700 Series Application Control Engine (ACE) appliance. This chapter contains the following sections: Overview Configuring SSL Termination
CHAPTER9 This chapter describes how to configure SSL on the Cisco 4700 Series Application Control Engine (ACE) appliance. This chapter contains the following sections: Overview Configuring SSL Termination
CYAN SECURE WEB HOWTO. SSL Intercept
 CYAN SECURE WEB HOWTO January 2009 Applies to: CYAN Secure Web 1.6 and above allows you to inspect SSL encrypted traffic. Therefore all filter mechanisms can be applied to HTTPS traffic. Without, all data
CYAN SECURE WEB HOWTO January 2009 Applies to: CYAN Secure Web 1.6 and above allows you to inspect SSL encrypted traffic. Therefore all filter mechanisms can be applied to HTTPS traffic. Without, all data
Creating an authorized SSL certificate
 Creating an authorized SSL certificate for MeetingSphere Meeting Center Server MeetingSphere Meeting Center Server requires an authorized SSL certificate by which its Meeting center is identified, and
Creating an authorized SSL certificate for MeetingSphere Meeting Center Server MeetingSphere Meeting Center Server requires an authorized SSL certificate by which its Meeting center is identified, and
Have documentation feedback? Submit a Documentation Feedback support ticket using the Support Wizard on support.air-watch.com.
 VMware AirWatch Email Notification Service Installation Guide Providing real-time email notifications to ios devices with AirWatch Inbox and VMware Boxer AirWatch v9.1 Have documentation feedback? Submit
VMware AirWatch Email Notification Service Installation Guide Providing real-time email notifications to ios devices with AirWatch Inbox and VMware Boxer AirWatch v9.1 Have documentation feedback? Submit
CP860, SIP-T28P, SIP-T26P, SIP-T22P, SIP-T21P, SIP-T20P, SIP-T19P, SIP-T46G, SIP-T42G and SIP-T41P IP phones running firmware version 71 or later.
 This guide provides the detailed instructions on how to configure and use certificates on Yealink IP phones. In addition, this guide provides step-by-step instructions on how to create custom certificates
This guide provides the detailed instructions on how to configure and use certificates on Yealink IP phones. In addition, this guide provides step-by-step instructions on how to create custom certificates
Load Balancing Web Servers with OWASP Top 10 WAF in AWS
 Load Balancing Web Servers with OWASP Top 10 WAF in AWS Quick Reference Guide V1.0.1 ABOUT THIS GUIDE This document provides a quick reference guide on how to load balance Web Servers and configure a WAF
Load Balancing Web Servers with OWASP Top 10 WAF in AWS Quick Reference Guide V1.0.1 ABOUT THIS GUIDE This document provides a quick reference guide on how to load balance Web Servers and configure a WAF
MSE System and Appliance Hardening Guidelines
 MSE System and Appliance Hardening Guidelines This appendix describes the hardening of MSE, which requires some services and processes to be exposed to function properly. This is referred to as MSE Appliance
MSE System and Appliance Hardening Guidelines This appendix describes the hardening of MSE, which requires some services and processes to be exposed to function properly. This is referred to as MSE Appliance
Managing Certificates
 Loading an Externally Generated SSL Certificate, page 1 Downloading Device Certificates, page 4 Uploading Device Certificates, page 6 Downloading CA Certificates, page 8 Uploading CA Certificates, page
Loading an Externally Generated SSL Certificate, page 1 Downloading Device Certificates, page 4 Uploading Device Certificates, page 6 Downloading CA Certificates, page 8 Uploading CA Certificates, page
Jabber OCS Gateway. Setup Guide. Product: OCS Gateway Document Version: C
 Jabber OCS Gateway Setup Guide Product: OCS Gateway 5.4.1 Document Version: C Disclaimers Trademarks Copyright 2008 Jabber, Inc. The information contained in this document is proprietary to Jabber, Inc.
Jabber OCS Gateway Setup Guide Product: OCS Gateway 5.4.1 Document Version: C Disclaimers Trademarks Copyright 2008 Jabber, Inc. The information contained in this document is proprietary to Jabber, Inc.
Have documentation feedback? Submit a Documentation Feedback support ticket using the Support Wizard on support.air-watch.com.
 VMware AirWatch Email Notification Service Installation Guide Providing real-time email notifications to ios devices with AirWatch Inbox and VMware Boxer Workspace ONE UEM v9.4 Have documentation feedback?
VMware AirWatch Email Notification Service Installation Guide Providing real-time email notifications to ios devices with AirWatch Inbox and VMware Boxer Workspace ONE UEM v9.4 Have documentation feedback?
Getting Started with the VQE Startup Configuration Utility
 CHAPTER 2 Getting Started with the VQE Startup Configuration Utility This chapter explains how to use the Cisco VQE Startup Configuration Utility to perform the initial configuration tasks needed to get
CHAPTER 2 Getting Started with the VQE Startup Configuration Utility This chapter explains how to use the Cisco VQE Startup Configuration Utility to perform the initial configuration tasks needed to get
Comprehensive Setup Guide for TLS on ESA
 Comprehensive Setup Guide for TLS on ESA Contents Introduction Prerequisites Requirements Components Used Background Information Functional Overview and Requirements Bring Your Own Certificate Update a
Comprehensive Setup Guide for TLS on ESA Contents Introduction Prerequisites Requirements Components Used Background Information Functional Overview and Requirements Bring Your Own Certificate Update a
Scan Report Executive Summary
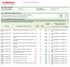 Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: WineDirect ASV Company: Comodo CA Limited 10/11/2018 Scan expiration date: 01/09/2019 Part 2. Summary
Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: WineDirect ASV Company: Comodo CA Limited 10/11/2018 Scan expiration date: 01/09/2019 Part 2. Summary
Installing and Configuring VMware Identity Manager Connector (Windows) OCT 2018 VMware Identity Manager VMware Identity Manager 3.
 Installing and Configuring VMware Identity Manager Connector 2018.8.1.0 (Windows) OCT 2018 VMware Identity Manager VMware Identity Manager 3.3 You can find the most up-to-date technical documentation on
Installing and Configuring VMware Identity Manager Connector 2018.8.1.0 (Windows) OCT 2018 VMware Identity Manager VMware Identity Manager 3.3 You can find the most up-to-date technical documentation on
VNS3 3.5 Container System Add-Ons
 VNS3 3.5 Container System Add-Ons Instructions for VNS3 2015 copyright 2015 1 Table of Contents Introduction 3 Docker Container Network 7 Uploading a Image or Dockerfile 9 Allocating a Container 13 Saving
VNS3 3.5 Container System Add-Ons Instructions for VNS3 2015 copyright 2015 1 Table of Contents Introduction 3 Docker Container Network 7 Uploading a Image or Dockerfile 9 Allocating a Container 13 Saving
REMOTE ACCESS IPSEC. Course /14/2014 Global Technology Associates, Inc.
 REMOTE ACCESS IPSEC Course 4002 1 Remote Access Features! Granular Network Access and Authorization based on groups and policies.! Windows, Linux, and MAC client support. Windows ShrewSoft Client MAC IPSecuritas
REMOTE ACCESS IPSEC Course 4002 1 Remote Access Features! Granular Network Access and Authorization based on groups and policies.! Windows, Linux, and MAC client support. Windows ShrewSoft Client MAC IPSecuritas
Configuration Guide. BlackBerry UEM Cloud
 Configuration Guide BlackBerry UEM Cloud Published: 2018-04-18 SWD-20180411125526296 Contents About this guide... 7 Getting started... 8 Configuring BlackBerry UEM Cloud for the first time... 8 Administrator
Configuration Guide BlackBerry UEM Cloud Published: 2018-04-18 SWD-20180411125526296 Contents About this guide... 7 Getting started... 8 Configuring BlackBerry UEM Cloud for the first time... 8 Administrator
Convio Data Sync Connector 3 Installation Guide
 Convio Data Sync Connector 3 Installation Guide Convio Connector Installation Instructions.doc 1 INSTALLATION Installation Prerequisites... 3 Technical Requirements... 3 Installing the Pervasive Data Integrator...
Convio Data Sync Connector 3 Installation Guide Convio Connector Installation Instructions.doc 1 INSTALLATION Installation Prerequisites... 3 Technical Requirements... 3 Installing the Pervasive Data Integrator...
Getting Started with the VQE Startup Configuration Utility
 CHAPTER 2 Getting Started with the VQE Startup Configuration Utility This chapter explains how to use the Cisco VQE Startup Configuration Utility to perform the initial configuration tasks needed to get
CHAPTER 2 Getting Started with the VQE Startup Configuration Utility This chapter explains how to use the Cisco VQE Startup Configuration Utility to perform the initial configuration tasks needed to get
Real-Time Dashboard Integration Bomgar Remote Support
 Real-Time Dashboard Integration Bomgar Remote Support 2017 Bomgar Corporation. All rights reserved worldwide. BOMGAR and the BOMGAR logo are trademarks of Bomgar Corporation; other trademarks shown are
Real-Time Dashboard Integration Bomgar Remote Support 2017 Bomgar Corporation. All rights reserved worldwide. BOMGAR and the BOMGAR logo are trademarks of Bomgar Corporation; other trademarks shown are
Have documentation feedback? Submit a Documentation Feedback support ticket using the Support Wizard on support.air-watch.com.
 VMware AirWatch Email Notification Service Installation Guide Providing real-time email notifications to ios devices with AirWatch Inbox and VMware Boxer Workspace ONE UEM v9.7 Have documentation feedback?
VMware AirWatch Email Notification Service Installation Guide Providing real-time email notifications to ios devices with AirWatch Inbox and VMware Boxer Workspace ONE UEM v9.7 Have documentation feedback?
Configuring Cisco Unified MeetingPlace Web Conferencing Security Features
 Configuring Cisco Unified MeetingPlace Web Conferencing Security Features Release 7.1 Revised: February 15, 2012 3:42 pm How to Configure Restricted Meeting ID Patterns, page 1 How to Configure Secure
Configuring Cisco Unified MeetingPlace Web Conferencing Security Features Release 7.1 Revised: February 15, 2012 3:42 pm How to Configure Restricted Meeting ID Patterns, page 1 How to Configure Secure
Deltek Time & Expense with Employee Self Service Version New Installation for Microsoft SQL Sever
 Deltek Time & Expense with Employee Self Service Version 9.0.1 New Installation for Microsoft SQL Sever July 31, 2013 While Deltek has attempted to verify that the information in this document is accurate
Deltek Time & Expense with Employee Self Service Version 9.0.1 New Installation for Microsoft SQL Sever July 31, 2013 While Deltek has attempted to verify that the information in this document is accurate
Setting up the Sophos Mobile Control External EAS Proxy
 Setting up the Sophos Mobile Control External EAS Proxy Setting up the External EAS Proxy This document tries to explain the concept of the Sophos Mobile Control External EAS Proxy which is available for
Setting up the Sophos Mobile Control External EAS Proxy Setting up the External EAS Proxy This document tries to explain the concept of the Sophos Mobile Control External EAS Proxy which is available for
Ubiquity Server Manual
 Ubiquity Server Manual Compatible with version 9.0 Introduction Ubiquity is the ASEM software solution for remote access and remote assistance on Industrial PCs and operator panels based on Windows operating
Ubiquity Server Manual Compatible with version 9.0 Introduction Ubiquity is the ASEM software solution for remote access and remote assistance on Industrial PCs and operator panels based on Windows operating
3. Optionally, if you want to use the new Web SSO feature, complete the steps in Adding Web Single Sign-On Functionality.
 Webthority HOW TO Upgrade The steps required to upgrade depend on the version you are upgrading from: upgrading from 6.5 upgrading from 6.0. Upgrading from 6.5 To upgrade from 6.5 perform the following
Webthority HOW TO Upgrade The steps required to upgrade depend on the version you are upgrading from: upgrading from 6.5 upgrading from 6.0. Upgrading from 6.5 To upgrade from 6.5 perform the following
Sterling Secure Proxy Version 3 FTP Adapter Configuration with SSL. ProFTP SSL Certificate creation with openssl
 Sterling Secure Proxy Version 3 FTP Adapter Configuration with SSL The SSP configuration has been tested with the following components. SSP 3 on Windows 2003 ProFTP Version 1.2.10 on Red Hat ES 4 Lftp
Sterling Secure Proxy Version 3 FTP Adapter Configuration with SSL The SSP configuration has been tested with the following components. SSP 3 on Windows 2003 ProFTP Version 1.2.10 on Red Hat ES 4 Lftp
Workspace ONE UEM Notification Service. VMware Workspace ONE UEM 1811
 Workspace ONE UEM Email Notification Service VMware Workspace ONE UEM 1811 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments
Workspace ONE UEM Email Notification Service VMware Workspace ONE UEM 1811 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments
Okta Integration Guide for Web Access Management with F5 BIG-IP
 Okta Integration Guide for Web Access Management with F5 BIG-IP Contents Introduction... 3 Publishing SAMPLE Web Application VIA F5 BIG-IP... 5 Configuring Okta as SAML 2.0 Identity Provider for F5 BIG-IP...
Okta Integration Guide for Web Access Management with F5 BIG-IP Contents Introduction... 3 Publishing SAMPLE Web Application VIA F5 BIG-IP... 5 Configuring Okta as SAML 2.0 Identity Provider for F5 BIG-IP...
Updating the Client Access URL using IBM Traveler Server. OPEN MIC WEBCAST March 22, 2017 Alvin John Marron L2 Software Engineer IBM Traveler
 Updating the Client Access URL using IBM Traveler Server OPEN MIC WEBCAST March 22, 2017 Alvin John Marron L2 Software Engineer IBM Traveler AGENDA: Overview Why use HTTPS instead of HTTP? Required Components
Updating the Client Access URL using IBM Traveler Server OPEN MIC WEBCAST March 22, 2017 Alvin John Marron L2 Software Engineer IBM Traveler AGENDA: Overview Why use HTTPS instead of HTTP? Required Components
Installation on Windows Server 2008
 USER GUIDE MADCAP PULSE 4 Installation on Windows Server 2008 Copyright 2018 MadCap Software. All rights reserved. Information in this document is subject to change without notice. The software described
USER GUIDE MADCAP PULSE 4 Installation on Windows Server 2008 Copyright 2018 MadCap Software. All rights reserved. Information in this document is subject to change without notice. The software described
Managing the SSL Certificate for the ESRS HTTPS Listener Service Technical Notes P/N Rev 01 July, 2012
 Managing the SSL Certificate for the ESRS HTTPS Listener Service Technical Notes P/N 300-013-818 Rev 01 July, 2012 This document contains information on these topics: Introduction... 2 Terminology... 2
Managing the SSL Certificate for the ESRS HTTPS Listener Service Technical Notes P/N 300-013-818 Rev 01 July, 2012 This document contains information on these topics: Introduction... 2 Terminology... 2
DEPLOYMENT GUIDE DEPLOYING F5 WITH ORACLE ACCESS MANAGER
 DEPLOYMENT GUIDE DEPLOYING F5 WITH ORACLE ACCESS MANAGER Table of Contents Table of Contents Introducing the F5 and Oracle Access Manager configuration Prerequisites and configuration notes... 1 Configuration
DEPLOYMENT GUIDE DEPLOYING F5 WITH ORACLE ACCESS MANAGER Table of Contents Table of Contents Introducing the F5 and Oracle Access Manager configuration Prerequisites and configuration notes... 1 Configuration
Configure IBM Security Privileged Identity Manager Appliance with a Load Balancer
 Configure IBM Security Privileged Identity Manager Appliance with a Load Balancer Aanchal Sinha aansinha@in.ibm.com Nitesh Mehare nimehare@in.ibm.com Parag Gokhale parag.gokhale@in.ibm.com Santosh Ankushkar
Configure IBM Security Privileged Identity Manager Appliance with a Load Balancer Aanchal Sinha aansinha@in.ibm.com Nitesh Mehare nimehare@in.ibm.com Parag Gokhale parag.gokhale@in.ibm.com Santosh Ankushkar
Cisco CTL Client setup
 Cisco CTL Client setup This chapter provides information about Cisco CTL client setup. About Cisco CTL Client setup, page 2 Remove etoken Run Time Environment 3.00 for CTL Client 5.0 plug-in, page 2 Cisco
Cisco CTL Client setup This chapter provides information about Cisco CTL client setup. About Cisco CTL Client setup, page 2 Remove etoken Run Time Environment 3.00 for CTL Client 5.0 plug-in, page 2 Cisco
Load Balancing Microsoft IIS. Deployment Guide v Copyright Loadbalancer.org
 Load Balancing Microsoft IIS Deployment Guide v1.6.4 Copyright Loadbalancer.org Table of Contents 1. About this Guide...4 2. Loadbalancer.org Appliances Supported...4 3. Loadbalancer.org Software Versions
Load Balancing Microsoft IIS Deployment Guide v1.6.4 Copyright Loadbalancer.org Table of Contents 1. About this Guide...4 2. Loadbalancer.org Appliances Supported...4 3. Loadbalancer.org Software Versions
Qualified Integrators and Resellers (QIR) TM. QIR Implementation Statement, v2.0
 Qualified Integrators and Resellers (QIR) TM Implementation Statement For each Qualified Installation performed, the QIR Employee must complete this document and confirm whether the Validated Payment Application
Qualified Integrators and Resellers (QIR) TM Implementation Statement For each Qualified Installation performed, the QIR Employee must complete this document and confirm whether the Validated Payment Application
On-demand target, up and running
 On-demand target, up and running ii On-demand target, up and running Contents Chapter 1. Assumptions........ 1 Chapter 2. Overview......... 3 Chapter 3. Component purpose.... 5 Chapter 5. Starting a session
On-demand target, up and running ii On-demand target, up and running Contents Chapter 1. Assumptions........ 1 Chapter 2. Overview......... 3 Chapter 3. Component purpose.... 5 Chapter 5. Starting a session
Your Apache ssl.conf in /etc/httpd.conf.d directory has the following SSLCertificate related directives.
 If you ever need to use HTTPS or SSL with your website, you will need to have an SSL certificate created, which your Apache web server would use to hand out to the web browsers of the site visitors. The
If you ever need to use HTTPS or SSL with your website, you will need to have an SSL certificate created, which your Apache web server would use to hand out to the web browsers of the site visitors. The
A10 Thunder ADC with Oracle E-Business Suite 12.2 DEPLOYMENT GUIDE
 A10 Thunder ADC with Oracle E-Business Suite 12.2 DEPLOYMENT GUIDE Table of Contents 1. Introduction... 2 2 Deployment Prerequisites... 2 3 Oracle E-Business Topology... 3 4 Accessing the Thunder ADC Application
A10 Thunder ADC with Oracle E-Business Suite 12.2 DEPLOYMENT GUIDE Table of Contents 1. Introduction... 2 2 Deployment Prerequisites... 2 3 Oracle E-Business Topology... 3 4 Accessing the Thunder ADC Application
HySecure Quick Start Guide. HySecure 5.0
 HySecure Quick Start Guide HySecure 5.0 Last Updated: 25 May 2017 2012-2017 Propalms Technologies Private Limited. All rights reserved. The information contained in this document represents the current
HySecure Quick Start Guide HySecure 5.0 Last Updated: 25 May 2017 2012-2017 Propalms Technologies Private Limited. All rights reserved. The information contained in this document represents the current
Container System Overview
 Container System Overview 2018 Table of Contents Introduction 3 Container Network 7 Uploading an Image or Dockerfile 9 Allocating a Container 13 Saving a Running Container 15 Access Considerations 18 2
Container System Overview 2018 Table of Contents Introduction 3 Container Network 7 Uploading an Image or Dockerfile 9 Allocating a Container 13 Saving a Running Container 15 Access Considerations 18 2
Enterprise Vault.cloud CloudLink Google Account Synchronization Guide. CloudLink to 4.0.3
 Enterprise Vault.cloud CloudLink Google Account Synchronization Guide CloudLink 4.0.1 to 4.0.3 Enterprise Vault.cloud: CloudLink Google Account Synchronization Guide Last updated: 2018-06-08. Legal Notice
Enterprise Vault.cloud CloudLink Google Account Synchronization Guide CloudLink 4.0.1 to 4.0.3 Enterprise Vault.cloud: CloudLink Google Account Synchronization Guide Last updated: 2018-06-08. Legal Notice
CLEO VLTrader Made Simple Guide
 CLEO VLTrader Made Simple Guide Table of Contents Quick Reference... 3 Miscellaneous Technical Notes... 3 CLEO VLTrader at a Glance... 3 Introduction... 5 Application Page Layout... 5 Preconfigured Hosts...
CLEO VLTrader Made Simple Guide Table of Contents Quick Reference... 3 Miscellaneous Technical Notes... 3 CLEO VLTrader at a Glance... 3 Introduction... 5 Application Page Layout... 5 Preconfigured Hosts...
VMware AirWatch Cloud Connector Guide ACC Installation and Integration
 VMware AirWatch Cloud Connector Guide ACC Installation and Integration Workspace ONE UEM v1810 Have documentation feedback? Submit a Documentation Feedback support ticket using the Support Wizard on support.air-watch.com.
VMware AirWatch Cloud Connector Guide ACC Installation and Integration Workspace ONE UEM v1810 Have documentation feedback? Submit a Documentation Feedback support ticket using the Support Wizard on support.air-watch.com.
WatchGuard XCS and Outlook Web Access 2013
 WatchGuard XCS and Outlook Web Access 2013 The Secure WebMail proxy provides a highly secure mechanism for accessing Microsoft OWA (Outlook Web Access). OWA uses a very similar interface to Outlook and
WatchGuard XCS and Outlook Web Access 2013 The Secure WebMail proxy provides a highly secure mechanism for accessing Microsoft OWA (Outlook Web Access). OWA uses a very similar interface to Outlook and
Installing Cisco APIC-EM on a Virtual Machine
 About the Virtual Machine Installation, page 1 System Requirements Virtual Machine, page 2 Pre-Install Checklists, page 4 Cisco APIC-EM Ports Reference, page 7 Verifying the Cisco ISO Image, page 8 Installing
About the Virtual Machine Installation, page 1 System Requirements Virtual Machine, page 2 Pre-Install Checklists, page 4 Cisco APIC-EM Ports Reference, page 7 Verifying the Cisco ISO Image, page 8 Installing
CSM - How to install Third-Party SSL Certificates for GUI access
 CSM - How to install Third-Party SSL Certificates for GUI access Contents Introduction Prerequisites Requirements Components Used CSR creation from the User Interface Identity Certificate Upload into CSM
CSM - How to install Third-Party SSL Certificates for GUI access Contents Introduction Prerequisites Requirements Components Used CSR creation from the User Interface Identity Certificate Upload into CSM
WebReport/i. Report Intranet Feature. Version 12. As of May Kisco Information Systems 89 Church Street Saranac Lake, New York 12983
 WebReport/i Report Intranet Feature Version 12 As of May 2012 Kisco Information Systems 89 Church Street Saranac Lake, New York 12983 Phone: (518) 897-5002 FAX: (518) 897-5003 E-mail: Sales@Kisco.com WWW:
WebReport/i Report Intranet Feature Version 12 As of May 2012 Kisco Information Systems 89 Church Street Saranac Lake, New York 12983 Phone: (518) 897-5002 FAX: (518) 897-5003 E-mail: Sales@Kisco.com WWW:
Manage Certificates. Certificates Overview
 Certificates Overview, page 1 Show Certificates, page 3 Download Certificates, page 4 Install Intermediate Certificates, page 4 Delete a Trust Certificate, page 5 Regenerate a Certificate, page 6 Upload
Certificates Overview, page 1 Show Certificates, page 3 Download Certificates, page 4 Install Intermediate Certificates, page 4 Delete a Trust Certificate, page 5 Regenerate a Certificate, page 6 Upload
AppDirector and AppXcel With Oracle Application Server 10g Release 3 ( ) - Oracle SOA Suite Enterprise Deployment
 AppDirector, AppXcel with Oracle SOA Suite 7/16/2008 TESTING & INTEGRATION GROUP AppDirector and AppXcel With Oracle Application Server 10g Release 3 (10.1.3.1.0) - Oracle SOA Suite Enterprise Deployment
AppDirector, AppXcel with Oracle SOA Suite 7/16/2008 TESTING & INTEGRATION GROUP AppDirector and AppXcel With Oracle Application Server 10g Release 3 (10.1.3.1.0) - Oracle SOA Suite Enterprise Deployment
Deltek Costpoint New Installation Guide for Microsoft SQL Server
 Deltek Costpoint 7.1.1 New Installation Guide for Microsoft SQL Server December 11, 2017 While Deltek has attempted to verify that the information in this document is accurate and complete, some typographical
Deltek Costpoint 7.1.1 New Installation Guide for Microsoft SQL Server December 11, 2017 While Deltek has attempted to verify that the information in this document is accurate and complete, some typographical
Installing AX Server with PostgreSQL (multi-server)
 Installing AX Server with PostgreSQL (multi-server) Version: 13 Published: Wednesday, November 29, 2017 ACL Services Ltd. 2017 Table of contents Table of contents Table of contents 3 Introduction 7 Intended
Installing AX Server with PostgreSQL (multi-server) Version: 13 Published: Wednesday, November 29, 2017 ACL Services Ltd. 2017 Table of contents Table of contents Table of contents 3 Introduction 7 Intended
Cisco CTL Client Setup
 This chapter provides information about Cisco CTL client setup. About, page 2 Addition of Second SAST Role in the CTL File for Recovery, page 2 Cluster Encryption Configuration Through CLI, page 3 Remove
This chapter provides information about Cisco CTL client setup. About, page 2 Addition of Second SAST Role in the CTL File for Recovery, page 2 Cluster Encryption Configuration Through CLI, page 3 Remove
Upgrade Instructions. NetBrain Integrated Edition 7.1. Two-Server Deployment
 NetBrain Integrated Edition 7.1 Upgrade Instructions Two-Server Deployment Version 7.1a Last Updated 2018-09-04 Copyright 2004-2018 NetBrain Technologies, Inc. All rights reserved. Contents 1. Upgrading
NetBrain Integrated Edition 7.1 Upgrade Instructions Two-Server Deployment Version 7.1a Last Updated 2018-09-04 Copyright 2004-2018 NetBrain Technologies, Inc. All rights reserved. Contents 1. Upgrading
App Orchestration 2.0
 App Orchestration 2.0 Getting Started with Citrix App Orchestration 2.0 Prepared by: Jenny Berger Commissioning Editor: Erin Smith Version: 1.0 Last Updated: April 4, 2014 Page 1 Contents Welcome to App
App Orchestration 2.0 Getting Started with Citrix App Orchestration 2.0 Prepared by: Jenny Berger Commissioning Editor: Erin Smith Version: 1.0 Last Updated: April 4, 2014 Page 1 Contents Welcome to App
VMware Enterprise Systems Connector Guide for SaaS Customers ACC Installation and Integration for SaaS
 Connector Guide for SaaS Customers ACC Installation and Integration for SaaS Workspace ONE UEM v9.5 Have documentation feedback? Submit a Documentation Feedback support ticket using the Support Wizard
Connector Guide for SaaS Customers ACC Installation and Integration for SaaS Workspace ONE UEM v9.5 Have documentation feedback? Submit a Documentation Feedback support ticket using the Support Wizard
Cisco Configuration Engine 2.0
 Cisco Configuration Engine 2.0 The Cisco Configuration Engine provides a unified, secure solution for automating the deployment of Cisco customer premises equipment (CPE). This scalable product distributes
Cisco Configuration Engine 2.0 The Cisco Configuration Engine provides a unified, secure solution for automating the deployment of Cisco customer premises equipment (CPE). This scalable product distributes
Example - Reverse Proxy for Exchange Services
 The reverse proxy redirects incoming requests from Microsoft Exchange Server services to clients without providing the origin details. This example configuration shows how to configure a reverse proxy
The reverse proxy redirects incoming requests from Microsoft Exchange Server services to clients without providing the origin details. This example configuration shows how to configure a reverse proxy
Advantech AE Technical Share Document
 Advantech AE Technical Share Document Date 2019/1/4 SR# 1-3643162399 Category FAQ SOP Related OS N/A Abstract Keyword Related Product How to use MQTT TLS with irtu device MQTT, SSL, TLS, CA, certification,
Advantech AE Technical Share Document Date 2019/1/4 SR# 1-3643162399 Category FAQ SOP Related OS N/A Abstract Keyword Related Product How to use MQTT TLS with irtu device MQTT, SSL, TLS, CA, certification,
Installation Guide for Pulse on Windows Server 2012
 USER GUIDE MADCAP PULSE 4 Installation Guide for Pulse on Windows Server 2012 Copyright 2018 MadCap Software. All rights reserved. Information in this document is subject to change without notice. The
USER GUIDE MADCAP PULSE 4 Installation Guide for Pulse on Windows Server 2012 Copyright 2018 MadCap Software. All rights reserved. Information in this document is subject to change without notice. The
Implementing Single Signon in IBM Sterling B2B Integrator
 Implementing Single Signon in IBM Sterling B2B Integrator Written by : Swaroopa Regulavalasa Reviewer 1: Martin Warnes (2016) Reviewer 2: Barry Barton ( 2018) Contents Implementing Single Signon in IBM
Implementing Single Signon in IBM Sterling B2B Integrator Written by : Swaroopa Regulavalasa Reviewer 1: Martin Warnes (2016) Reviewer 2: Barry Barton ( 2018) Contents Implementing Single Signon in IBM
SCCM Plug-in (for the Jamf Software Server) User Guide. Version 3.51
 SCCM Plug-in (for the Jamf Software Server) User Guide Version 3.51 copyright 2002-2017 Jamf. All rights reserved. Jamf has made all efforts to ensure that this guide is accurate. Jamf 100 Washington Ave
SCCM Plug-in (for the Jamf Software Server) User Guide Version 3.51 copyright 2002-2017 Jamf. All rights reserved. Jamf has made all efforts to ensure that this guide is accurate. Jamf 100 Washington Ave
Upgrade EZ-Pay V6 Guide
 Upgrade EZ-Pay V6 Guide Who should use this patch Users who are using versions 3.0.4 of EZ-Pay can upgrade to version 3.1.0 Where to get this patch Download it from http://www.hr21.com.hk/ -> Products->
Upgrade EZ-Pay V6 Guide Who should use this patch Users who are using versions 3.0.4 of EZ-Pay can upgrade to version 3.1.0 Where to get this patch Download it from http://www.hr21.com.hk/ -> Products->
INSTALLATION GUIDE FOR ACPL FM220 RD WINDOWS APPLICATION INDEX
 INSTALLATION GUIDE FOR ACPL FM220 RD WINDOWS APPLICATION INDEX CONTENT PAGE No. Setup FM220 RD Service 2 Setup FM220 RD Service Support Tool 5 Instructions to enable HTTPS in RD Service 8 RD Service troubleshooting
INSTALLATION GUIDE FOR ACPL FM220 RD WINDOWS APPLICATION INDEX CONTENT PAGE No. Setup FM220 RD Service 2 Setup FM220 RD Service Support Tool 5 Instructions to enable HTTPS in RD Service 8 RD Service troubleshooting
Quick Start Access Manager 3.1 SP5 January 2013
 www.novell.com/documentation Quick Start Access Manager 3.1 SP5 January 2013 Legal Notices Novell, Inc., makes no representations or warranties with respect to the contents or use of this documentation,
www.novell.com/documentation Quick Start Access Manager 3.1 SP5 January 2013 Legal Notices Novell, Inc., makes no representations or warranties with respect to the contents or use of this documentation,
RealPresence Access Director System Administrator s Guide
 [Type the document title] Polycom RealPresence Access Director System Administrator s Guide 2.1.0 March 2013 3725-78703-001A Polycom Document Title 1 Trademark Information POLYCOM and the names and marks
[Type the document title] Polycom RealPresence Access Director System Administrator s Guide 2.1.0 March 2013 3725-78703-001A Polycom Document Title 1 Trademark Information POLYCOM and the names and marks
APBnet Server Deployment
 APBnet Server Deployment February 9, 2017 APBnet software and documents related to installing version 170209 can be found at www.apbnet.net/2017download 1. As an IT person, to deploy APBnet on a server
APBnet Server Deployment February 9, 2017 APBnet software and documents related to installing version 170209 can be found at www.apbnet.net/2017download 1. As an IT person, to deploy APBnet on a server
Scenarios for Setting Up SSL Certificates for View. Modified for Horizon VMware Horizon 7 7.3
 Scenarios for Setting Up SSL Certificates for View Modified for Horizon 7 7.3.2 VMware Horizon 7 7.3 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/
Scenarios for Setting Up SSL Certificates for View Modified for Horizon 7 7.3.2 VMware Horizon 7 7.3 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/
SCCM Plug-in User Guide. Version 3.0
 SCCM Plug-in User Guide Version 3.0 JAMF Software, LLC 2012 JAMF Software, LLC. All rights reserved. JAMF Software has made all efforts to ensure that this guide is accurate. JAMF Software 301 4th Ave
SCCM Plug-in User Guide Version 3.0 JAMF Software, LLC 2012 JAMF Software, LLC. All rights reserved. JAMF Software has made all efforts to ensure that this guide is accurate. JAMF Software 301 4th Ave
Installing and Configuring vcloud Connector
 Installing and Configuring vcloud Connector vcloud Connector 2.6.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new
Installing and Configuring vcloud Connector vcloud Connector 2.6.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new
Configuring the Relay Server with Microsoft IIS using SSL 2 nd Edition
 Configuring the Relay Server with Microsoft IIS using SSL 2 nd Edition A whitepaper from Sybase ianywhere Author: Joshua Savill, Product Manager Date: April 3 rd, 2009 This whitepaper was written in the
Configuring the Relay Server with Microsoft IIS using SSL 2 nd Edition A whitepaper from Sybase ianywhere Author: Joshua Savill, Product Manager Date: April 3 rd, 2009 This whitepaper was written in the
LICENSE4J AUTO LICENSE GENERATION AND ACTIVATION SERVER USER GUIDE
 LICENSE4J AUTO LICENSE GENERATION AND ACTIVATION SERVER USER GUIDE VERSION 1.7.1 LICENSE4J www.license4j.com Table of Contents Getting Started... 2 Server Roles... 4 Installation... 9 Server WAR Deployment...
LICENSE4J AUTO LICENSE GENERATION AND ACTIVATION SERVER USER GUIDE VERSION 1.7.1 LICENSE4J www.license4j.com Table of Contents Getting Started... 2 Server Roles... 4 Installation... 9 Server WAR Deployment...
SONOTON storage server
 The SONOTON storage server offers different protocols which all use SSL secured communications. All protocols will work with the login details given to you by SONOTON. Overview: Protocols supported: HTTPS
The SONOTON storage server offers different protocols which all use SSL secured communications. All protocols will work with the login details given to you by SONOTON. Overview: Protocols supported: HTTPS
The CN!Express application is sunset. Please see inside for options. CN!Express. User Guide. Auric Systems International
 The CN!Express application is sunset. Please see inside for options. CN!Express User Guide Auric Systems International Copyright 2016 Auric Systems International. All rights reserved. www.auricsystems.com
The CN!Express application is sunset. Please see inside for options. CN!Express User Guide Auric Systems International Copyright 2016 Auric Systems International. All rights reserved. www.auricsystems.com
VMware Workspace ONE UEM VMware AirWatch Cloud Connector
 VMware AirWatch Cloud Connector VMware Workspace ONE UEM 1811 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments about this
VMware AirWatch Cloud Connector VMware Workspace ONE UEM 1811 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments about this
eroaming platform Secure Connection Guide
 eroaming platform Secure Connection Guide Contents 1. Revisions overview... 3 2. Abbrevations... 4 3. Preconditions... 5 3.1. OpenSSL... 5 3.2. Requirements for your PKCS10 CSR... 5 3.3. Java Keytool...
eroaming platform Secure Connection Guide Contents 1. Revisions overview... 3 2. Abbrevations... 4 3. Preconditions... 5 3.1. OpenSSL... 5 3.2. Requirements for your PKCS10 CSR... 5 3.3. Java Keytool...
Elastic Load Balance. User Guide. Issue 14 Date
 Issue 14 Date 2018-02-28 Contents Contents 1 Overview... 1 1.1 Basic Concepts... 1 1.1.1 Elastic Load Balance... 1 1.1.2 Public Network Load Balancer...1 1.1.3 Private Network Load Balancer... 2 1.1.4
Issue 14 Date 2018-02-28 Contents Contents 1 Overview... 1 1.1 Basic Concepts... 1 1.1.1 Elastic Load Balance... 1 1.1.2 Public Network Load Balancer...1 1.1.3 Private Network Load Balancer... 2 1.1.4
PCI DSS Compliance. White Paper Parallels Remote Application Server
 PCI DSS Compliance White Paper Parallels Remote Application Server Table of Contents Introduction... 3 What Is PCI DSS?... 3 Why Businesses Need to Be PCI DSS Compliant... 3 What Is Parallels RAS?... 3
PCI DSS Compliance White Paper Parallels Remote Application Server Table of Contents Introduction... 3 What Is PCI DSS?... 3 Why Businesses Need to Be PCI DSS Compliant... 3 What Is Parallels RAS?... 3
Setup for Cisco Unified Communications Manager
 Setup for Cisco Unified Communications Manager This chapter describes how you can set up Cisco Jabber for ipad using Cisco Unified Communications Manager. System and Network Requirements, page 1 Recommended
Setup for Cisco Unified Communications Manager This chapter describes how you can set up Cisco Jabber for ipad using Cisco Unified Communications Manager. System and Network Requirements, page 1 Recommended
McAfee Network Security Platform 9.1
 9.1.7.49-9.1.3.6 Manager-M-series, Mxx30-series, XC Cluster Release Notes McAfee Network Security Platform 9.1 Revision C Contents About the release New features Enhancements Resolved issues Installation
9.1.7.49-9.1.3.6 Manager-M-series, Mxx30-series, XC Cluster Release Notes McAfee Network Security Platform 9.1 Revision C Contents About the release New features Enhancements Resolved issues Installation
