Big and Bright - Security
|
|
|
- Dina Sherman
- 5 years ago
- Views:
Transcription
1 Big and Bright - Security
2 Big and Bright Security Embedded Tech Trends 2018 Does this mean: Everything is Big and Bright our security is 100% effective? or There are Big security concerns but Bright solutions? or Security issues are so Big and Bright - there are no solutions? We will look at this in the context of our embedded defense customers
3 Security Risks depend on the Environment Embedded Tech Trends 2018 Consumer Use Embedded Use Open and connected Closed, controlled Many Tasks Single Task Single User Multiple Users Embedded users can leverage some consumer technologies
4 Security Timeline Embedded Tech Trends User access permissions IPv6 using IPSec TPM 1.2 Bitlocker, User Account Control, Defender UEFI Secure Boot TPM 2.0 Device Guard, Credential Guard, Boot Guard TPM Trusted Platform Module
5 What is a TPM? Embedded Tech Trends 2018 A tamper-resistant integrated circuit Enables: Cryptographic key generation Safe storage of small amounts of sensitive information, such as passwords and cryptographic keys Generation of random numbers
6 TPM can help ensure image security Embedded Tech Trends 2018 The TPM can record hashes that measure the images for later validation Secure Boot only loads trusted (signed) operating system bootloaders, which in turn will only load a trusted OS BIOS Initialises HW Check loader signature Loader Locate Kernel image Check Kernel signature Kernel Start Kernel Check OS signature OS Start OS Check application measurements TPM
7 Guards utilizing TPMs Embedded Tech Trends 2018 Microsoft Credential Guard prevents against credential creep in large organizations: User credentials are isolated from the operating system kernel using virtualization and TPM measurements Intel Boot Guard is a hardware based scheme that prevents boot block takeover
8 TPM 2.0 Improvements Embedded Tech Trends 2018 Support for additional cryptographic algorithms, i.e. SHA256, SHA384, SHA512, and SM3_256 Enhancements to the availability of the TPM to applications Enhanced authorization mechanisms Simplified TPM management All new boards from Concurrent Technologies come with TPM 2.0 and it is now an option on boards announced since 2014
9 Security Timeline Embedded Tech Trends User access permissions IPv6 using IPSec TPM 1.2 Bitlocker, User Account Control, Defender UEFI Secure Boot TPM 2.0 Device Guard, Credential Guard, Boot Guard What if you can t use the latest OS?
10 Use a Hypervisor Run a legacy OS and application in a Virtual Machine Can utilize native hypervisor or OS based Has an impact on real time performance Boot method more secure but legacy OS and application concerns Virtual Machine Hypervisor
11 Use a Board based Security Solution Embedded Tech Trends 2018 Guardian Security Package Available since 2012 Processor boards are available with the option of additional hardware, firmware and software components for holistic security
12 Three Key Goals of Guardian Embedded Tech Trends 2018 Preventing unauthorized use: To prevent an unauthorized person from interfering with or operating the equipment Preventing unauthorized access: To prevent an unauthorized person from gaining access to sensitive data when they have access to the equipment To prevent a person with legitimate access to the hardware from gaining access to sensitive data Allowing sensitive data to be purged on-demand: To ensure that all sensitive data can be deleted rendering the hardware inoperable or returning it to the original factory configuration
13 Guardian protects against: Embedded Tech Trends 2018 Physical intrusion Booting from non-secure sources Accessing classified data Retrieving sensitive Intellectual Property Modifying non-volatile memory Executing non-trusted software Unauthorized modification of system configuration Bypassing low level firmware Reverse engineering
14 Testing and Deployment Embedded Tech Trends 2018 Board is configured: Enables extensive testing without lock activating Security Lock enabled: A breach of any selected measure will lock a board permanently Boards are suitable for deployment Remove from Service: Sanitization option to scrub and securely erase devices
15 Conclusions Embedded Tech Trends 2018 Improved security has now (finally) become more important to some defense customers than backwards compatibility: TPM 2.0 and Windows 10 Secure Boot Boot Guard Even tightly controlled, closed solutions need security options Be flexible - one solution doesn t fit every customer Nothing is 100% secure There are Big security concerns but Bright solutions
16 Concurrent Technologies gocct.co m Thanks for listening
Cisco Secure Boot and Trust Anchor Module Differentiation
 Solution Overview Cisco Secure Boot and Trust Anchor Module Differentiation Cisco Trust Anchor Technologies provide the foundation for Cisco Trustworthy Systems. Cisco Secure Boot helps ensure that the
Solution Overview Cisco Secure Boot and Trust Anchor Module Differentiation Cisco Trust Anchor Technologies provide the foundation for Cisco Trustworthy Systems. Cisco Secure Boot helps ensure that the
Windows 10 Security & Audit
 Windows 10 Security & Audit John Tannahill, CA, CISM, CGEIT, CRISC, CSX-P jtannahi@rogers.com Windows 10 Editions Home Pro Enterprise Education Mobile IoT Editions 1 Windows 10 Builds Windows 10 (initial
Windows 10 Security & Audit John Tannahill, CA, CISM, CGEIT, CRISC, CSX-P jtannahi@rogers.com Windows 10 Editions Home Pro Enterprise Education Mobile IoT Editions 1 Windows 10 Builds Windows 10 (initial
TPM v.s. Embedded Board. James Y
 TPM v.s. Embedded Board James Y What Is A Trusted Platform Module? (TPM 1.2) TPM 1.2 on the Enano-8523 that: How Safe is your INFORMATION? Protects secrets from attackers Performs cryptographic functions
TPM v.s. Embedded Board James Y What Is A Trusted Platform Module? (TPM 1.2) TPM 1.2 on the Enano-8523 that: How Safe is your INFORMATION? Protects secrets from attackers Performs cryptographic functions
WINDOWS 10 ENTERPRISE New Security Features
 WINDOWS 10 ENTERPRISE New Security Features J. Abernethy mindshift Technologies Josh Quinn mindshift Technologies #ILTALSS #LSS26 TODAY S AGENDA Windows 10 Security Fundamentals Managing Windows 10 Security
WINDOWS 10 ENTERPRISE New Security Features J. Abernethy mindshift Technologies Josh Quinn mindshift Technologies #ILTALSS #LSS26 TODAY S AGENDA Windows 10 Security Fundamentals Managing Windows 10 Security
Key Threats Melissa (1999), Love Letter (2000) Mainly leveraging social engineering. Key Threats Internet was just growing Mail was on the verge
 Key Threats Internet was just growing Mail was on the verge Key Threats Melissa (1999), Love Letter (2000) Mainly leveraging social engineering Key Threats Code Red and Nimda (2001), Blaster (2003), Slammer
Key Threats Internet was just growing Mail was on the verge Key Threats Melissa (1999), Love Letter (2000) Mainly leveraging social engineering Key Threats Code Red and Nimda (2001), Blaster (2003), Slammer
Better Security with Virtual Machines
 Better Security with Virtual Machines VMware Security Seminar Cambridge, 2006 Agenda VMware Evolution Virtual machine Server architecture Virtual infrastructure Looking forward VMware s security vision
Better Security with Virtual Machines VMware Security Seminar Cambridge, 2006 Agenda VMware Evolution Virtual machine Server architecture Virtual infrastructure Looking forward VMware s security vision
CSPN Security Target. HP Sure Start HW Root of Trust NPCE586HA0. December 2016 Reference: HPSSHW v1.3 Version : 1.3
 CSPN Security Target HP Sure Start HW Root of Trust NPCE586HA0 December 2016 Reference: HPSSHW v1.3 Version : 1.3 1 Table of contents 1 Introduction... 4 1.1 Document Context... 4 1.2 Product identification...
CSPN Security Target HP Sure Start HW Root of Trust NPCE586HA0 December 2016 Reference: HPSSHW v1.3 Version : 1.3 1 Table of contents 1 Introduction... 4 1.1 Document Context... 4 1.2 Product identification...
Past, Present, and Future Justin Johnson Senior Principal Firmware Engineer
 Dell Firmware Security Past, Present, and Future Justin Johnson Senior Principal Firmware Engineer justin.johnson1@dell.com Dell Security 2 What does BIOS do? Configure and Test System Memory Configure
Dell Firmware Security Past, Present, and Future Justin Johnson Senior Principal Firmware Engineer justin.johnson1@dell.com Dell Security 2 What does BIOS do? Configure and Test System Memory Configure
Windows Devices. Device Capabilities. Premium. Entry
 Windows Devices $ Premium Entry Device Capabilities Windows 10 IoT $ Premium Windows 10 IoT Enterprise Desktop Shell, Win32 apps, Universal Windows Apps and Drivers 1 GB RAM, 16 GB Storage X86 Windows
Windows Devices $ Premium Entry Device Capabilities Windows 10 IoT $ Premium Windows 10 IoT Enterprise Desktop Shell, Win32 apps, Universal Windows Apps and Drivers 1 GB RAM, 16 GB Storage X86 Windows
Bromium: Virtualization-Based Security
 Bromium: Virtualization-Based Security TAG-Cyber Briefing Presented by Simon Crosby CTO, Co-Founder of Bromium Bromium 2016 2 Bromium 2016 3 Real-time Detection & Analysis Malware manifest Bromium 2016
Bromium: Virtualization-Based Security TAG-Cyber Briefing Presented by Simon Crosby CTO, Co-Founder of Bromium Bromium 2016 2 Bromium 2016 3 Real-time Detection & Analysis Malware manifest Bromium 2016
Enterprise Ransomware Mitigations
 打造數碼安全校園 Enterprise Ransomware Mitigations Windows 10, Edge Browser, Office ATP Enterprise Mobility Suite (EMS) ATP OneDrive for Business Azure Backup 3rd party Cloud Backup THE WINDOWS CLIENT DEFENSE
打造數碼安全校園 Enterprise Ransomware Mitigations Windows 10, Edge Browser, Office ATP Enterprise Mobility Suite (EMS) ATP OneDrive for Business Azure Backup 3rd party Cloud Backup THE WINDOWS CLIENT DEFENSE
An Introduction to Platform Security
 presented by An Introduction to Platform Security Spring 2018 UEFI Seminar and Plugfest March 26-30, 2018 Presented by Brent Holtsclaw and John Loucaides (Intel) Legal Notice No computer system can be
presented by An Introduction to Platform Security Spring 2018 UEFI Seminar and Plugfest March 26-30, 2018 Presented by Brent Holtsclaw and John Loucaides (Intel) Legal Notice No computer system can be
Security: The Key to Affordable Unmanned Aircraft Systems
 AN INTEL COMPANY Security: The Key to Affordable Unmanned Aircraft Systems By Alex Wilson, Director of Business Development, Aerospace and Defense WHEN IT MATTERS, IT RUNS ON WIND RIVER EXECUTIVE SUMMARY
AN INTEL COMPANY Security: The Key to Affordable Unmanned Aircraft Systems By Alex Wilson, Director of Business Development, Aerospace and Defense WHEN IT MATTERS, IT RUNS ON WIND RIVER EXECUTIVE SUMMARY
Technical Brief Distributed Trusted Computing
 Technical Brief Distributed Trusted Computing Josh Wood Look inside to learn about Distributed Trusted Computing in Tectonic Enterprise, an industry-first set of technologies that cryptographically verify,
Technical Brief Distributed Trusted Computing Josh Wood Look inside to learn about Distributed Trusted Computing in Tectonic Enterprise, an industry-first set of technologies that cryptographically verify,
UEFI, SecureBoot, DeviceGuard, TPM a WHB (un)related technologies
 GOLD PARTNER: Hlavní partner: Hlavní odborný partner: UEFI, SecureBoot, DeviceGuard, TPM a WHB (un)related technologies Ing. Ondřej Ševeček GOPAS a.s. MCSM:Directory MVP:Security CISA CISM CEH CHFI ondrej@sevecek.com
GOLD PARTNER: Hlavní partner: Hlavní odborný partner: UEFI, SecureBoot, DeviceGuard, TPM a WHB (un)related technologies Ing. Ondřej Ševeček GOPAS a.s. MCSM:Directory MVP:Security CISA CISM CEH CHFI ondrej@sevecek.com
Deploying Secure Boot: Key Creation and Management
 presented by Deploying Secure Boot: Key Creation and Management UEFI Summer Summit July 16-20, 2012 Presented by Arie van der Hoeven (Microsoft Corporation) Updated 2011-06-01 1 Agenda Introduction Secure
presented by Deploying Secure Boot: Key Creation and Management UEFI Summer Summit July 16-20, 2012 Presented by Arie van der Hoeven (Microsoft Corporation) Updated 2011-06-01 1 Agenda Introduction Secure
SSG Platform Security Division & IOTG Jan Krueger Product Manager IoT Security Solutions
 SSG Platform Security Division & IOTG Jan Krueger Product Manager IoT Security Solutions THIS SLIDE MUST BE USED WITH ANY SLIDES REMOVED FROM THIS PRESENTATION Legal Disclaimers Intel technologies features
SSG Platform Security Division & IOTG Jan Krueger Product Manager IoT Security Solutions THIS SLIDE MUST BE USED WITH ANY SLIDES REMOVED FROM THIS PRESENTATION Legal Disclaimers Intel technologies features
HAROLD BAELE MICROSOFT CLOUD TECHNICAL CONSULTANT MICROSOFT CERTIFIED TRAINER. New protection capabilities in Windows Server 2016
 HAROLD BAELE MICROSOFT CLOUD TECHNICAL CONSULTANT MICROSOFT CERTIFIED TRAINER New protection capabilities in Windows Server 2016 HAROLD BAELE MICROSOFT CLOUD TECHNICAL CONSULTANT AND MICROSOFT CERTIFIED
HAROLD BAELE MICROSOFT CLOUD TECHNICAL CONSULTANT MICROSOFT CERTIFIED TRAINER New protection capabilities in Windows Server 2016 HAROLD BAELE MICROSOFT CLOUD TECHNICAL CONSULTANT AND MICROSOFT CERTIFIED
Windows 10 and the Enterprise. Craig A. Brown Prepared for: GMIS
 Windows 10 and the Enterprise Craig A. Brown Prepared for: GMIS 11-2-2015 Introduction Craig A. Brown Microsoft Practice Leader Global Knowledge MCT, Since 1996 MCSA / MCSE / NT / 2000 / 2003 MCDST MCITP:
Windows 10 and the Enterprise Craig A. Brown Prepared for: GMIS 11-2-2015 Introduction Craig A. Brown Microsoft Practice Leader Global Knowledge MCT, Since 1996 MCSA / MCSE / NT / 2000 / 2003 MCDST MCITP:
GSE/Belux Enterprise Systems Security Meeting
 MICROSOFT MAKES NO WARRANTIES, EXPRESS, IMPLIED OR STATUTORY, AS TO THE INFORMATION IN THIS PRESENTATION. 1 In the news Microsoft Exposes Scope of Botnet Threat By Tony Bradley, October 15, 2010 Microsoft's
MICROSOFT MAKES NO WARRANTIES, EXPRESS, IMPLIED OR STATUTORY, AS TO THE INFORMATION IN THIS PRESENTATION. 1 In the news Microsoft Exposes Scope of Botnet Threat By Tony Bradley, October 15, 2010 Microsoft's
Atmel Trusted Platform Module June, 2014
 Atmel Trusted Platform Module June, 2014 1 2014 Atmel Corporation What is a TPM? The TPM is a hardware-based secret key generation and storage device providing a secure vault for any embedded system Four
Atmel Trusted Platform Module June, 2014 1 2014 Atmel Corporation What is a TPM? The TPM is a hardware-based secret key generation and storage device providing a secure vault for any embedded system Four
HP Sure Start Gen3. Table of contents. Available on HP Elite products equipped with 7th generation Intel Core TM processors September 2017
 Technical white paper Gen3 7th generation Intel Core TM processors September 2017 Table of contents 1 Gen3... 2 1.1 Background... 2 1.2 Gen3 overview... 2 1.3 Runtime Intrusion Detection (RTID)... 2 1.3.1
Technical white paper Gen3 7th generation Intel Core TM processors September 2017 Table of contents 1 Gen3... 2 1.1 Background... 2 1.2 Gen3 overview... 2 1.3 Runtime Intrusion Detection (RTID)... 2 1.3.1
How to Clear TPM HW on HP Personal Systems
 How to Clear TPM HW on HP Personal Systems Version: 6 Release Date: 18 October 2017 There are several methods to clear TPM HW on HP Personal Systems, depending on the system model. This document is only
How to Clear TPM HW on HP Personal Systems Version: 6 Release Date: 18 October 2017 There are several methods to clear TPM HW on HP Personal Systems, depending on the system model. This document is only
Trusted Computing and O/S Security
 Computer Security Spring 2008 Trusted Computing and O/S Security Aggelos Kiayias University of Connecticut O/S Security Fundamental concept for O/S Security: separation. hardware kernel system user Each
Computer Security Spring 2008 Trusted Computing and O/S Security Aggelos Kiayias University of Connecticut O/S Security Fundamental concept for O/S Security: separation. hardware kernel system user Each
Consultant since many years. Mainly working with defense and public sector. MCSE on Windows Server 2000 security ;-)
 About Consultant since many years Mainly working with defense and public sector MCSE on Windows Server 2000 security ;-) CYBERCRIME: STATE OF THE UNION EVOLUTION OF ATTACKS Mischief Fraud and theft Damage
About Consultant since many years Mainly working with defense and public sector MCSE on Windows Server 2000 security ;-) CYBERCRIME: STATE OF THE UNION EVOLUTION OF ATTACKS Mischief Fraud and theft Damage
TUX : Trust Update on Linux Kernel
 TUX : Trust Update on Linux Kernel Suhho Lee Mobile OS Lab, Dankook university suhho1993@gmail.com -- Hyunik Kim, and Seehwan Yoo {eternity13, seehwan.yoo}@dankook.ac.kr Index Intro Background Threat Model
TUX : Trust Update on Linux Kernel Suhho Lee Mobile OS Lab, Dankook university suhho1993@gmail.com -- Hyunik Kim, and Seehwan Yoo {eternity13, seehwan.yoo}@dankook.ac.kr Index Intro Background Threat Model
MODERN DESKTOP SECURITY
 MODERN DESKTOP SECURITY I M GOING TO BE HONEST. WE RE IN THE FIGHT OF OUR DIGITAL LIVES, AND WE ARE NOT WINNING! M I C H A E L M C C A U L, C H A I R M A N, U S H O M E L A N D S E C U R I T Y C O M M
MODERN DESKTOP SECURITY I M GOING TO BE HONEST. WE RE IN THE FIGHT OF OUR DIGITAL LIVES, AND WE ARE NOT WINNING! M I C H A E L M C C A U L, C H A I R M A N, U S H O M E L A N D S E C U R I T Y C O M M
Building Trust in the Internet of Things
 AN INTEL COMPANY Building Trust in the Internet of Things Developing an End-to-End Security Strategy for IoT Applications WHEN IT MATTERS, IT RUNS ON WIND RIVER EXECUTIVE SUMMARY Recent security breaches
AN INTEL COMPANY Building Trust in the Internet of Things Developing an End-to-End Security Strategy for IoT Applications WHEN IT MATTERS, IT RUNS ON WIND RIVER EXECUTIVE SUMMARY Recent security breaches
Terra: A Virtual Machine-Based Platform for Trusted Computing by Garfinkel et al. (Some slides taken from Jason Franklin s 712 lecture, Fall 2006)
 Terra: A Virtual Machine-Based Platform for Trusted Computing by Garfinkel et al. (Some slides taken from Jason Franklin s 712 lecture, Fall 2006) Trusted Computing Hardware What can you do if you have
Terra: A Virtual Machine-Based Platform for Trusted Computing by Garfinkel et al. (Some slides taken from Jason Franklin s 712 lecture, Fall 2006) Trusted Computing Hardware What can you do if you have
OVAL + The Trusted Platform Module
 OVAL + The Trusted Platform Module Charles Schmidt June 14, 2010 Overview OVAL Can assess a vast diversity of system state Usually software based software attacks can compromise Trusted Platform Module
OVAL + The Trusted Platform Module Charles Schmidt June 14, 2010 Overview OVAL Can assess a vast diversity of system state Usually software based software attacks can compromise Trusted Platform Module
CIS 4360 Secure Computer Systems Secured System Boot
 CIS 4360 Secure Computer Systems Secured System Boot Professor Qiang Zeng Spring 2017 Previous Class Attacks against System Boot Bootkit Evil Maid Attack Bios-kit Attacks against RAM DMA Attack Cold Boot
CIS 4360 Secure Computer Systems Secured System Boot Professor Qiang Zeng Spring 2017 Previous Class Attacks against System Boot Bootkit Evil Maid Attack Bios-kit Attacks against RAM DMA Attack Cold Boot
Software Vulnerability Assessment & Secure Storage
 Software Vulnerability Assessment & Secure Storage 1 Software Vulnerability Assessment Vulnerability assessment is the process of identifying flaws that reside in an OS, application software or devices
Software Vulnerability Assessment & Secure Storage 1 Software Vulnerability Assessment Vulnerability assessment is the process of identifying flaws that reside in an OS, application software or devices
Improving Security in Embedded Systems Felix Baum, Product Line Manager
 Improving Security in Embedded Systems Felix Baum, Product Line Manager The Challenge with Embedded Security Business Imperatives Security Imperatives I need to keep my production expenses as low as possible.
Improving Security in Embedded Systems Felix Baum, Product Line Manager The Challenge with Embedded Security Business Imperatives Security Imperatives I need to keep my production expenses as low as possible.
Security in NVMe Enterprise SSDs
 Security in NVMe Enterprise SSDs Radjendirane Codandaramane, Sr. Manager, Applications, Microsemi August 2017 1 Agenda SSD Lifecycle Security threats in SSD Security measures for SSD August 2017 2 SSD
Security in NVMe Enterprise SSDs Radjendirane Codandaramane, Sr. Manager, Applications, Microsemi August 2017 1 Agenda SSD Lifecycle Security threats in SSD Security measures for SSD August 2017 2 SSD
Windows 8 BIOS Boot settings
 DE114 Windows 8 BIOS Boot settings The Windows 8 BIOS boot settings allow you to configure the new items of boot options for systems running in Windows 8 operating system. UEFI BIOS Utility - Advanced
DE114 Windows 8 BIOS Boot settings The Windows 8 BIOS boot settings allow you to configure the new items of boot options for systems running in Windows 8 operating system. UEFI BIOS Utility - Advanced
Introduction to Security and User Authentication
 Introduction to Security and User Authentication Brad Karp UCL Computer Science CS GZ03 / M030 14 th November 2016 Topics We ll Cover User login authentication (local and remote) Cryptographic primitives,
Introduction to Security and User Authentication Brad Karp UCL Computer Science CS GZ03 / M030 14 th November 2016 Topics We ll Cover User login authentication (local and remote) Cryptographic primitives,
Department of Computer Science Institute for System Architecture, Operating Systems Group TRUSTED COMPUTING CARSTEN WEINHOLD
 Department of Computer Science Institute for System Architecture, Operating Systems Group TRUSTED COMPUTING CARSTEN WEINHOLD THIS LECTURE... Today: Technology Lecture discusses basics in context of TPMs
Department of Computer Science Institute for System Architecture, Operating Systems Group TRUSTED COMPUTING CARSTEN WEINHOLD THIS LECTURE... Today: Technology Lecture discusses basics in context of TPMs
The Intel SSD Pro 2500 Series Guide for Microsoft edrive* Activation
 The Intel SSD Pro 2500 Series Guide for Microsoft edrive* Activation Solutions Blueprint January 2015 Order Number: 330880-002US INFORMATION IN THIS DOCUMENT IS PROVIDED IN CONNECTION WITH INTEL PRODUCTS.
The Intel SSD Pro 2500 Series Guide for Microsoft edrive* Activation Solutions Blueprint January 2015 Order Number: 330880-002US INFORMATION IN THIS DOCUMENT IS PROVIDED IN CONNECTION WITH INTEL PRODUCTS.
Windows IoT Security. Jackie Chang Sr. Program Manager
 Windows IoT Security Jackie Chang Sr. Program Manager Rest Physical access to a device will not give access to data Data & Control Execution Data owner has full control over data processing Motion Transport
Windows IoT Security Jackie Chang Sr. Program Manager Rest Physical access to a device will not give access to data Data & Control Execution Data owner has full control over data processing Motion Transport
BIOS Update Release Notes
 PRODUCTS: DQ77KB (Standard BIOS) BIOS Update Release Notes BIOS Version 0059 - KBQ7710H.86A.0059.2017.0526.1645 Date: May 26, 2017 ME Firmware: 8.1.71.3608 Updated Intel ME firmware to version 8.1.71.3608.
PRODUCTS: DQ77KB (Standard BIOS) BIOS Update Release Notes BIOS Version 0059 - KBQ7710H.86A.0059.2017.0526.1645 Date: May 26, 2017 ME Firmware: 8.1.71.3608 Updated Intel ME firmware to version 8.1.71.3608.
SECURITY MODELS FOR APPLICATION PROTECTION AND AGAINST REVERSE ENGINEERING
 SECURITY MODELS FOR APPLICATION PROTECTION AND AGAINST REVERSE ENGINEERING SECURITY @ KONTRON PETER MÜLLER, DIRECTOR PRODUCTLINE BOARDS & MODULES TELEREX OCTOBER, 2017 AGENDA 01 02 03 04 TECHNOLOGICAL
SECURITY MODELS FOR APPLICATION PROTECTION AND AGAINST REVERSE ENGINEERING SECURITY @ KONTRON PETER MÜLLER, DIRECTOR PRODUCTLINE BOARDS & MODULES TELEREX OCTOBER, 2017 AGENDA 01 02 03 04 TECHNOLOGICAL
QuickSpecs. Overview. HPE Ethernet 10Gb 2-port 535 Adapter. HPE Ethernet 10Gb 2-port 535 Adapter. 1. Product description. 2.
 Overview 1. Product description 2. Product features 1. Product description HPE Ethernet 10Gb 2-port 535FLR-T adapter 1 HPE Ethernet 10Gb 2-port 535T adapter The HPE Ethernet 10GBase-T 2-port 535 adapters
Overview 1. Product description 2. Product features 1. Product description HPE Ethernet 10Gb 2-port 535FLR-T adapter 1 HPE Ethernet 10Gb 2-port 535T adapter The HPE Ethernet 10GBase-T 2-port 535 adapters
Provisioning secure Identity for Microcontroller based IoT Devices
 Provisioning secure Identity for Microcontroller based IoT Devices Mark Schaeffer, Sr. Product Marketing Manager, Security Solutions Synergy IoT Platform Business Division, Renesas Electronics, Inc. May
Provisioning secure Identity for Microcontroller based IoT Devices Mark Schaeffer, Sr. Product Marketing Manager, Security Solutions Synergy IoT Platform Business Division, Renesas Electronics, Inc. May
Lecture 3 MOBILE PLATFORM SECURITY
 Lecture 3 MOBILE PLATFORM SECURITY You will be learning: What techniques are used in mobile software platform security? What techniques are used in mobile hardware platform security? Is there a common
Lecture 3 MOBILE PLATFORM SECURITY You will be learning: What techniques are used in mobile software platform security? What techniques are used in mobile hardware platform security? Is there a common
Strengthening the Chain of Trust. Kevin Lane HP Jeff Bobzin Insyde Software
 presented by Strengthening the Chain of Trust Kevin Lane HP Jeff Bobzin Insyde Software August Updated 22, 2014 2011-06-01 Agenda Quick Intro to UEFI UEFI Myths Using Linux + Secure Boot Continuing the
presented by Strengthening the Chain of Trust Kevin Lane HP Jeff Bobzin Insyde Software August Updated 22, 2014 2011-06-01 Agenda Quick Intro to UEFI UEFI Myths Using Linux + Secure Boot Continuing the
The information contained in this document represents the current view of Microsoft Corp. on the issues discussed as of the date of publication.
 The information contained in this document represents the current view of Microsoft Corp. on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions,
The information contained in this document represents the current view of Microsoft Corp. on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions,
Boot Mode Considerations: BIOS vs. UEFI
 Boot Mode Considerations: BIOS vs. UEFI An overview of differences between UEFI Boot Mode and traditional BIOS Boot Mode Dell Engineering October 2017 A Dell EMC Deployment and Configuration Guide Revisions
Boot Mode Considerations: BIOS vs. UEFI An overview of differences between UEFI Boot Mode and traditional BIOS Boot Mode Dell Engineering October 2017 A Dell EMC Deployment and Configuration Guide Revisions
From TPM 1.2 to 2.0 and some more. Federico Mancini AFSecurity Seminar,
 From TPM 1.2 to 2.0 and some more Federico Mancini AFSecurity Seminar, 30.11.2015 The trusted platform module - TPM The TPM (Trusted Platform Module) is both a set of specifications and its implementation.
From TPM 1.2 to 2.0 and some more Federico Mancini AFSecurity Seminar, 30.11.2015 The trusted platform module - TPM The TPM (Trusted Platform Module) is both a set of specifications and its implementation.
PYTHIA SERVICE BY VIRGIL SECURITY WHITE PAPER
 PYTHIA SERVICE WHITEPAPER BY VIRGIL SECURITY WHITE PAPER May 21, 2018 CONTENTS Introduction 2 How does Pythia solve these problems? 3 Are there any other solutions? 4 What is Pythia? 4 How does it work?
PYTHIA SERVICE WHITEPAPER BY VIRGIL SECURITY WHITE PAPER May 21, 2018 CONTENTS Introduction 2 How does Pythia solve these problems? 3 Are there any other solutions? 4 What is Pythia? 4 How does it work?
Improve productivity with modernized PCs and Windows 10. Christopher Choong, DTM Field Marketing Manager
 Improve productivity with modernized PCs and Windows 10 Christopher Choong, DTM Field Marketing Manager Impressive innovation. Inside and out. 3 4 It s an important time to refresh Design Every product
Improve productivity with modernized PCs and Windows 10 Christopher Choong, DTM Field Marketing Manager Impressive innovation. Inside and out. 3 4 It s an important time to refresh Design Every product
RISCV with Sanctum Enclaves. Victor Costan, Ilia Lebedev, Srini Devadas
 RISCV with Sanctum Enclaves Victor Costan, Ilia Lebedev, Srini Devadas Today, privilege implies trust (1/3) If computing remotely, what is the TCB? Priviledge CPU HW Hypervisor trusted computing base OS
RISCV with Sanctum Enclaves Victor Costan, Ilia Lebedev, Srini Devadas Today, privilege implies trust (1/3) If computing remotely, what is the TCB? Priviledge CPU HW Hypervisor trusted computing base OS
Configuring TPM Firmware Version
 Configuring TPM Firmware Version Step-by-Step Guide Updated September 2016 HP has been moving to utilize version 2.0 of the Trusted Platform Module (TPM) Firmware on its newer products. The previous version
Configuring TPM Firmware Version Step-by-Step Guide Updated September 2016 HP has been moving to utilize version 2.0 of the Trusted Platform Module (TPM) Firmware on its newer products. The previous version
Windows 10 edition. Find out which. is right for you. Core features. Familar, and better than ever Home Pro Enterprise Education Mobile.
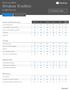 Core features Familar, and better than ever Home Pro Education Customizable Start Menu Windows Defender & Windows firewall N/A 1 N/A Fast start up with Hiberboot and InstantGo 2 N/A N/A TPM support 3 Battery
Core features Familar, and better than ever Home Pro Education Customizable Start Menu Windows Defender & Windows firewall N/A 1 N/A Fast start up with Hiberboot and InstantGo 2 N/A N/A TPM support 3 Battery
Cybersecurity in Government
 Cybersecurity in Government Executive Development Course: Digital Government Ng Lup Houh, Principal Cybersecurity Specialist Cybersecurity Group 03 April 2018 Agenda Cyber Threats & Vulnerabilities Cyber
Cybersecurity in Government Executive Development Course: Digital Government Ng Lup Houh, Principal Cybersecurity Specialist Cybersecurity Group 03 April 2018 Agenda Cyber Threats & Vulnerabilities Cyber
IPM Secure Hardening Guidelines
 IPM Secure Hardening Guidelines Introduction Due to rapidly increasing Cyber Threats and cyber warfare on Industrial Control System Devices and applications, Eaton recommends following best practices for
IPM Secure Hardening Guidelines Introduction Due to rapidly increasing Cyber Threats and cyber warfare on Industrial Control System Devices and applications, Eaton recommends following best practices for
Department of Computer Science Institute for System Architecture, Operating Systems Group TRUSTED COMPUTING CARSTEN WEINHOLD
 Department of Computer Science Institute for System Architecture, Operating Systems Group TRUSTED COMPUTING CARSTEN WEINHOLD THIS LECTURE... Today: Technology Lecture discusses basics in context of TPMs
Department of Computer Science Institute for System Architecture, Operating Systems Group TRUSTED COMPUTING CARSTEN WEINHOLD THIS LECTURE... Today: Technology Lecture discusses basics in context of TPMs
HP Manageability Integration Kit HP Client Management Solutions
 HP Manageability Integration Kit HP Client Management Solutions November 2017 925167-002 Table of contents 1 Overview... 9 2 System requirements... 10 2.1 Supported Microsoft System Center Configuration
HP Manageability Integration Kit HP Client Management Solutions November 2017 925167-002 Table of contents 1 Overview... 9 2 System requirements... 10 2.1 Supported Microsoft System Center Configuration
Windows Server Security Guide
 Windows Server Security Guide August 2017 Contents Windows Server 2016 Security Guide... 3 Why is Windows Server 2016 security important?... 3 How does Windows Server 2016 help prevent and detect compromise?...
Windows Server Security Guide August 2017 Contents Windows Server 2016 Security Guide... 3 Why is Windows Server 2016 security important?... 3 How does Windows Server 2016 help prevent and detect compromise?...
Cybersecurity in Data Centers. Murat Cudi Erentürk ISACA CISA, ISO Lead Auditor Gandalf Consulting and Software Ltd.
 Cybersecurity in Data Centers Murat Cudi Erentürk ISACA CISA, ISO 27001 Lead Auditor Gandalf Consulting and Software Ltd. What is Cybersecurity? Information Security IT Systems Security Physical Security
Cybersecurity in Data Centers Murat Cudi Erentürk ISACA CISA, ISO 27001 Lead Auditor Gandalf Consulting and Software Ltd. What is Cybersecurity? Information Security IT Systems Security Physical Security
Trusted Computing and O/S Security. Aggelos Kiayias Justin Neumann
 Trusted Computing and O/S Security Aggelos Kiayias Justin Neumann O/S Security Fundamental concept for O/S Security: separation. hardware kernel system user Each layer may try to verify the outer layer
Trusted Computing and O/S Security Aggelos Kiayias Justin Neumann O/S Security Fundamental concept for O/S Security: separation. hardware kernel system user Each layer may try to verify the outer layer
Titan silicon root of trust for Google Cloud
 Scott Johnson Dominic Rizzo Secure Enclaves Workshop 8/29/2018 Titan silicon root of trust for Google Cloud 1 Cloud Perspective: We need a silicon root of trust Software infrastructure Datacenter equipment
Scott Johnson Dominic Rizzo Secure Enclaves Workshop 8/29/2018 Titan silicon root of trust for Google Cloud 1 Cloud Perspective: We need a silicon root of trust Software infrastructure Datacenter equipment
Lifecycle Controller Platform Update in Dell PowerEdge 1 2 th Generation Servers
 Lifecycle Controller Platform Update in Dell PowerEdge 1 2 th Generation Servers This Dell Technical White Paper provides detailed information about the capabilities of Lifecycle Controller to perform
Lifecycle Controller Platform Update in Dell PowerEdge 1 2 th Generation Servers This Dell Technical White Paper provides detailed information about the capabilities of Lifecycle Controller to perform
How Shielded VMs Protect Your Data
 How Shielded VMs Protect Your Data Jan Marek MVP MCC MCT MCSE MCSD Head of CDM & marek@kpcs.cz Architect @ KPCS CZ www.atom.ms www.kpcs.cz www.janmarek.eu Traditional Security Services (AD, MSSQL, ShP)
How Shielded VMs Protect Your Data Jan Marek MVP MCC MCT MCSE MCSD Head of CDM & marek@kpcs.cz Architect @ KPCS CZ www.atom.ms www.kpcs.cz www.janmarek.eu Traditional Security Services (AD, MSSQL, ShP)
Feature Comparison Summary
 Feature Comparison Summary,, and The cloud-ready operating system is the cloud-ready operating system that delivers new layers of security and Azure-inspired innovation for the applications and infrastructure
Feature Comparison Summary,, and The cloud-ready operating system is the cloud-ready operating system that delivers new layers of security and Azure-inspired innovation for the applications and infrastructure
INTERNET OF THINGS KONTRON
 INTERNET OF THINGS SECURITY @ KONTRON EMBEDDED COMPUTING CONFERENCE 2017 ECC WINTERTHUR SEPTEMBER 5 TH, 2017 AGENDA 01 INTRODUCTION 02 SECURITY LAYERS 03 KONTRON & S&T // 2 WHAT IS IN IT FOR YOU THROUGH
INTERNET OF THINGS SECURITY @ KONTRON EMBEDDED COMPUTING CONFERENCE 2017 ECC WINTERTHUR SEPTEMBER 5 TH, 2017 AGENDA 01 INTRODUCTION 02 SECURITY LAYERS 03 KONTRON & S&T // 2 WHAT IS IN IT FOR YOU THROUGH
Enhance your Cloud Security with AMD EPYC Hardware Memory Encryption
 Enhance your Cloud Security with AMD EPYC Hardware Memory Encryption White Paper October, 2018 Introduction Consumers and enterprises are becoming increasingly concerned about the security of their digital
Enhance your Cloud Security with AMD EPYC Hardware Memory Encryption White Paper October, 2018 Introduction Consumers and enterprises are becoming increasingly concerned about the security of their digital
Operating system hardening
 Operating system Comp Sci 3600 Security Outline 1 2 3 4 5 6 What is OS? Hardening process that includes planning, ation, uration, update, and maintenance of the operating system and the key applications
Operating system Comp Sci 3600 Security Outline 1 2 3 4 5 6 What is OS? Hardening process that includes planning, ation, uration, update, and maintenance of the operating system and the key applications
Virtualisation on Mobile Devices {Hugo Marques, Nuno Conceição, Luis Pereira}
 Virtualisation on Mobile Devices {Hugo Marques, Nuno Conceição, Luis Pereira} Security Approaches for the Mobile Platform In a nutshell (Mobi)Trust is the...expectation that a device will behave in a particular
Virtualisation on Mobile Devices {Hugo Marques, Nuno Conceição, Luis Pereira} Security Approaches for the Mobile Platform In a nutshell (Mobi)Trust is the...expectation that a device will behave in a particular
One Ring to Rule them All
 One Ring to Rule them All A primer on virtualization enhanced security @SimonCrosby Co-founder & CTO Introduction We use micro-virtualization to secure endpoints We serve enterprises and government agencies
One Ring to Rule them All A primer on virtualization enhanced security @SimonCrosby Co-founder & CTO Introduction We use micro-virtualization to secure endpoints We serve enterprises and government agencies
HP Manageability Integration Kit HP Client Management Solutions
 Technical white paper HP Manageability Integration Kit HP Client Management Solutions Table of contents Overview... 4 System requirements... 4 Supported Microsoft System Center Configuration Manager versions...
Technical white paper HP Manageability Integration Kit HP Client Management Solutions Table of contents Overview... 4 System requirements... 4 Supported Microsoft System Center Configuration Manager versions...
UEFI Secure Boot and DRI. Kalyan Kumar N
 UEFI Secure Boot and DRI Kalyan Kumar N Agenda Introduction RDK Boot Loader DRI (Disaster Recovery Image) RootFS Validation Build Environment Introduction Standardization of the RDK set-top box firmware
UEFI Secure Boot and DRI Kalyan Kumar N Agenda Introduction RDK Boot Loader DRI (Disaster Recovery Image) RootFS Validation Build Environment Introduction Standardization of the RDK set-top box firmware
BIOS Setup. User s Guide. (For Skylake-W Platform) Rev.1.1
 BIOS Setup (For Skylake-W Platform) User s Guide Rev.1.1 Copyright 2017 GIGA-BYTE TECHNOLOGY CO., LTD. All rights reserved. The trademarks mentioned in this manual are legally registered to their respective
BIOS Setup (For Skylake-W Platform) User s Guide Rev.1.1 Copyright 2017 GIGA-BYTE TECHNOLOGY CO., LTD. All rights reserved. The trademarks mentioned in this manual are legally registered to their respective
Building Secure Systems: Problems and Principles. Dennis Kafura
 Building Secure Systems: Problems and Principles Dennis Kafura 1 Barriers to Secure Systems Secure systems depend on more than the discovery of more advanced technologies Security also depends on the widespread
Building Secure Systems: Problems and Principles Dennis Kafura 1 Barriers to Secure Systems Secure systems depend on more than the discovery of more advanced technologies Security also depends on the widespread
Embedded System Security Mobile Hardware Platform Security
 1 Embedded System Security Mobile Hardware Platform Security Prof. Dr.-Ing. Ahmad-Reza Sadeghi System Security Lab Technische Universität Darmstadt Germany Summer Term 2017 Acknowledgement This slide set
1 Embedded System Security Mobile Hardware Platform Security Prof. Dr.-Ing. Ahmad-Reza Sadeghi System Security Lab Technische Universität Darmstadt Germany Summer Term 2017 Acknowledgement This slide set
Embedded System Security Mobile Hardware Platform Security
 1 Embedded System Security Prof. Dr.-Ing. Ahmad-Reza Sadeghi System Security Lab Technische Universität Darmstadt Germany Summer Term 2016 Acknowledgement This slide set is based on slides provided by
1 Embedded System Security Prof. Dr.-Ing. Ahmad-Reza Sadeghi System Security Lab Technische Universität Darmstadt Germany Summer Term 2016 Acknowledgement This slide set is based on slides provided by
How Secure is your Server?
 How Secure is your Server? Key Things To Consider For Building A Safe, Robust IT Infrastructure Mukund Khatri Sr. Distinguished Engineer / VP Server & Infrastructure Solutions Rick Hall Sr. Product Planning
How Secure is your Server? Key Things To Consider For Building A Safe, Robust IT Infrastructure Mukund Khatri Sr. Distinguished Engineer / VP Server & Infrastructure Solutions Rick Hall Sr. Product Planning
Securing VMware NSX MAY 2014
 Securing VMware NSX MAY 2014 Securing VMware NSX Table of Contents Executive Summary... 2 NSX Traffic [Control, Management, and Data]... 3 NSX Manager:... 5 NSX Controllers:... 8 NSX Edge Gateway:... 9
Securing VMware NSX MAY 2014 Securing VMware NSX Table of Contents Executive Summary... 2 NSX Traffic [Control, Management, and Data]... 3 NSX Manager:... 5 NSX Controllers:... 8 NSX Edge Gateway:... 9
Connecting Securely to the Cloud
 Connecting Securely to the Cloud Security Primer Presented by Enrico Gregoratto Andrew Marsh Agenda 2 Presentation Speaker Trusting The Connection Transport Layer Security Connecting to the Cloud Enrico
Connecting Securely to the Cloud Security Primer Presented by Enrico Gregoratto Andrew Marsh Agenda 2 Presentation Speaker Trusting The Connection Transport Layer Security Connecting to the Cloud Enrico
BIOS. Chapter The McGraw-Hill Companies, Inc. All rights reserved. Mike Meyers CompTIA A+ Guide to Managing and Troubleshooting PCs
 BIOS Chapter 8 Overview In this chapter, you will learn how to Explain the function of BIOS Distinguish among various CMOS setup utility options Describe option ROM and device drivers Troubleshoot the
BIOS Chapter 8 Overview In this chapter, you will learn how to Explain the function of BIOS Distinguish among various CMOS setup utility options Describe option ROM and device drivers Troubleshoot the
The Early System Start-Up Process. Group Presentation by: Tianyuan Liu, Caiwei He, Krishna Parasuram Srinivasan, Wenbin Xu
 The Early System Start-Up Process Group Presentation by: Tianyuan Liu, Caiwei He, Krishna Parasuram Srinivasan, Wenbin Xu 1 Boot Process Booting is the initialization of a computerized system In Linux,
The Early System Start-Up Process Group Presentation by: Tianyuan Liu, Caiwei He, Krishna Parasuram Srinivasan, Wenbin Xu 1 Boot Process Booting is the initialization of a computerized system In Linux,
Protecting your system from the scum of the universe
 Protecting your system from the scum of the universe Gilad Ben-Yossef gilad@benyossef.com Twitter: @giladby About me My name is Gilad Ben-Yossef. I work on applied cryptography and security of the upstream
Protecting your system from the scum of the universe Gilad Ben-Yossef gilad@benyossef.com Twitter: @giladby About me My name is Gilad Ben-Yossef. I work on applied cryptography and security of the upstream
Six Myths of Windows RT Revealed!
 Si Myths of Windows RT Revealed! Si Myths of Windows RT Revealed! There has been a lot of (mis)information being circulated about capabilities of Windows RT, the new Microsoft tablet operating system for
Si Myths of Windows RT Revealed! Si Myths of Windows RT Revealed! There has been a lot of (mis)information being circulated about capabilities of Windows RT, the new Microsoft tablet operating system for
Total Video Solution Cybersecurity Protection. ConteraWS Platform Cybersecurity Overview
 Total Video Solution Cybersecurity Protection ConteraWS Platform Cybersecurity Overview +1.818.937.0700 www.arecontvision.com avsales@arecontvision.com Table of Contents Introduction... 3 Data & Network
Total Video Solution Cybersecurity Protection ConteraWS Platform Cybersecurity Overview +1.818.937.0700 www.arecontvision.com avsales@arecontvision.com Table of Contents Introduction... 3 Data & Network
Dawn Song
 1 Virtual Machines & Security Dawn Song dawnsong@cs.berkeley.edu Virtual Machines VM: Execution environment that gives the illusion of a real machine VMM/Hypervisor: host software which provides this capability
1 Virtual Machines & Security Dawn Song dawnsong@cs.berkeley.edu Virtual Machines VM: Execution environment that gives the illusion of a real machine VMM/Hypervisor: host software which provides this capability
SECURING DEVICES IN THE INTERNET OF THINGS
 SECURING DEVICES IN THE INTERNET OF THINGS WHEN IT MATTERS, IT RUNS ON WIND RIVER EXECUTIVE SUMMARY Security breaches at the device level in the Internet of Things (IoT) can have severe consequences, including
SECURING DEVICES IN THE INTERNET OF THINGS WHEN IT MATTERS, IT RUNS ON WIND RIVER EXECUTIVE SUMMARY Security breaches at the device level in the Internet of Things (IoT) can have severe consequences, including
Authentication Technology for a Smart eid Infrastructure.
 Authentication Technology for a Smart eid Infrastructure. www.aducid.com One app to access all public and private sector online services. One registration allows users to access all their online accounts
Authentication Technology for a Smart eid Infrastructure. www.aducid.com One app to access all public and private sector online services. One registration allows users to access all their online accounts
ARM Security Solutions and Numonyx Authenticated Flash
 ARM Security Solutions and Numonyx Authenticated Flash How to integrate Numonyx Authenticated Flash with ARM TrustZone* for maximum system protection Introduction Through a combination of integrated hardware
ARM Security Solutions and Numonyx Authenticated Flash How to integrate Numonyx Authenticated Flash with ARM TrustZone* for maximum system protection Introduction Through a combination of integrated hardware
Expert Reference Series of White Papers. BitLocker: Is It Really Secure? COURSES.
 Expert Reference Series of White Papers BitLocker: Is It Really Secure? 1-800-COURSES www.globalknowledge.com BitLocker: Is It Really Secure? Mark Mizrahi, Global Knowledge Instructor, MCSE, MCT, CEH Introduction:
Expert Reference Series of White Papers BitLocker: Is It Really Secure? 1-800-COURSES www.globalknowledge.com BitLocker: Is It Really Secure? Mark Mizrahi, Global Knowledge Instructor, MCSE, MCT, CEH Introduction:
CIS 4360 Secure Computer Systems. Trusted Platform Module
 CIS 4360 Secure Computer Systems Trusted Platform Module Professor Qiang Zeng Spring 2017 Some slides were stolen from Stanford s Security Course, Bruce Maggs, and Bryan Parno Signed Integer Representation
CIS 4360 Secure Computer Systems Trusted Platform Module Professor Qiang Zeng Spring 2017 Some slides were stolen from Stanford s Security Course, Bruce Maggs, and Bryan Parno Signed Integer Representation
SECURE OFFICE OF THE FUTURE
 ** SECURE OFFICE OF THE FUTURE HP Today Powering 430 of the Global Fortune 500 Companies Working with 250,000+ Channel Partners 18,000+ patents 2 PCs & 1 Printer ship every second HP Business Personal
** SECURE OFFICE OF THE FUTURE HP Today Powering 430 of the Global Fortune 500 Companies Working with 250,000+ Channel Partners 18,000+ patents 2 PCs & 1 Printer ship every second HP Business Personal
Trusted Computing. William A. Arbaugh Department of Computer Science University of Maryland cs.umd.edu
 Trusted Computing William A. Arbaugh Department of Computer Science University of Maryland waa @ cs.umd.edu http://www.cs.umd.edu/~waa Getting Started Would you like to know what software is running on
Trusted Computing William A. Arbaugh Department of Computer Science University of Maryland waa @ cs.umd.edu http://www.cs.umd.edu/~waa Getting Started Would you like to know what software is running on
Unicorn: Two- Factor Attestation for Data Security
 ACM CCS - Oct. 18, 2011 Unicorn: Two- Factor Attestation for Data Security M. Mannan Concordia University, Canada B. Kim, A. Ganjali & D. Lie University of Toronto, Canada 1 Unicorn target systems q High
ACM CCS - Oct. 18, 2011 Unicorn: Two- Factor Attestation for Data Security M. Mannan Concordia University, Canada B. Kim, A. Ganjali & D. Lie University of Toronto, Canada 1 Unicorn target systems q High
Feature Comparison Summary
 Feature Comparison Summary, and The cloud-ready operating system Thanks to cloud technology, the rate of change is faster than ever before, putting more pressure on IT. Organizations demand increased security,
Feature Comparison Summary, and The cloud-ready operating system Thanks to cloud technology, the rate of change is faster than ever before, putting more pressure on IT. Organizations demand increased security,
Lecture Embedded System Security Trusted Platform Module
 1 Lecture Embedded System Security Prof. Dr.-Ing. Ahmad-Reza Sadeghi System Security Lab Technische Universität Darmstadt (CASED) Germany Summer Term 2015 Roadmap: TPM Introduction to TPM TPM architecture
1 Lecture Embedded System Security Prof. Dr.-Ing. Ahmad-Reza Sadeghi System Security Lab Technische Universität Darmstadt (CASED) Germany Summer Term 2015 Roadmap: TPM Introduction to TPM TPM architecture
Lenovo Imaging Checklist
 *Note: If this is a re-image, it s recommended getting into setup and clearing the Security Chip. PRE-INSTALLATION BIOS (When powering up, hit F1 at the Lenovo Logo screen) For all Lenovo Laptop models:
*Note: If this is a re-image, it s recommended getting into setup and clearing the Security Chip. PRE-INSTALLATION BIOS (When powering up, hit F1 at the Lenovo Logo screen) For all Lenovo Laptop models:
Project Cerberus Hardware Security
 Project Cerberus Hardware Security Bryan Kelly / Principal Firmware Eng Manager Microsoft Azure Cloud Hardware Infrastructure Yigal Edery / Principal Program Manager Microsoft Azure Security Talk Outline
Project Cerberus Hardware Security Bryan Kelly / Principal Firmware Eng Manager Microsoft Azure Cloud Hardware Infrastructure Yigal Edery / Principal Program Manager Microsoft Azure Security Talk Outline
OP-TEE Using TrustZone to Protect Our Own Secrets
 OP-TEE Using TrustZone to Protect Our Own Secrets ROM-Code Bootloader Kernel Root File System ELC Europe 2017, 23.10.2016 Marc Kleine-Budde Slide 1 - http://www.pengutronix.de - 2017-10-23
OP-TEE Using TrustZone to Protect Our Own Secrets ROM-Code Bootloader Kernel Root File System ELC Europe 2017, 23.10.2016 Marc Kleine-Budde Slide 1 - http://www.pengutronix.de - 2017-10-23
Backup, File Backup copies of individual files made in order to replace the original file(s) in case it is damaged or lost.
 Glossary A Active Directory a directory service that inventories, secures and manages the users, computers, rules and other components of a Microsoft Windows network. This service is typically deployed
Glossary A Active Directory a directory service that inventories, secures and manages the users, computers, rules and other components of a Microsoft Windows network. This service is typically deployed
Defense-in-Depth Against Malicious Software. Speaker name Title Group Microsoft Corporation
 Defense-in-Depth Against Malicious Software Speaker name Title Group Microsoft Corporation Agenda Understanding the Characteristics of Malicious Software Malware Defense-in-Depth Malware Defense for Client
Defense-in-Depth Against Malicious Software Speaker name Title Group Microsoft Corporation Agenda Understanding the Characteristics of Malicious Software Malware Defense-in-Depth Malware Defense for Client
Systems View -- Current. Trustworthy Computing. TC Advantages. Systems View -- Target. Bootstrapping a typical PC. Boot Guarantees
 Trustworthy Computing s View -- Current Trent Jaeger February 18, 2004 Process 1 Web server Process 2 Mail server Process 3 Java VM Operating Hardware (CPU, MMU, I/O devices) s View -- Target TC Advantages
Trustworthy Computing s View -- Current Trent Jaeger February 18, 2004 Process 1 Web server Process 2 Mail server Process 3 Java VM Operating Hardware (CPU, MMU, I/O devices) s View -- Target TC Advantages
