irods user empowerment: A matter of Sudo microservices Chris Smeele - ITS/ResearchIT
|
|
|
- Lauren Stevens
- 6 years ago
- Views:
Transcription
1 irods user empowerment: A matter of Sudo microservices Chris Smeele - ITS/ResearchIT
2 The need for automated privileged operations Privileged operations can be needed to ensure process quality system security Implementation: manually: by designated staff automated: policy controlled process (user empowerment) Example of "manual" implementation: iadmin requires actor to be rodsadmin type user Real-time response requirements drive automation of privileged operations
3 Model of automated privileged operations control check execute return start supervised process ensure that preconditions are met execute operation with elevated privileges end supervised process
4 So how can we empower our irods users? Why not create a set of microservices that 1) wrap selected existing irods functions 2) execute them with 'rodsadmin' privileges on behalf of the user analog to the Linux "Sudo" command
5 Design principles for our Sudo microservices Security by design not enabled unless a precondition policy is defined Each privileged operation must be singular and targeted to minimize impact of any potential flaws in design, implementation or configuration A privileged operation should be able to take part in a workflow this allows for support of more complex use cases
6 Extended model of privileged operations control check execute trigger return start supervised process ensure that preconditions are met execute operation with elevated privileges optionally trigger next workflow step end supervised process
7 Implementation in Sudo microservices control check execute trigger user rule calls Sudo microservice XXX acpresudoxxx policy used to check preconditions and to authorize user (process stops here if this policy fails) execute XXX operation with elevated privileges acpostsudoxxx policy can initiate next workflow step return Sudo microservice returns control to user rule
8 Index of the set of SUDO microservices irods User management msisudouseradd msisudouserremove irods Group management msisudogroupadd msisudogroupremove msisudogroupmemberadd msisudogroupmemberremove Access control msisudoobjaclset Metadata management msisudoobjmetaadd msisudoobjmetaset msisudoobjmetaremove
9 Example use case: delegated group management irods users 'ton' and 'chris' are regular rodsusers. Via a policy they are allowed to manage the irods group 'humanities' In a rule they can call a Sudo microservice to add user 'john' to this group: msisudogroupmemberadd ('humanities', 'john', *policykv); NB: *policykv is a variable that can be used to optionally pass additional information
10 Preparation for this use case by rodsadmin Use metadata so that users "ton" and "chris" act as admins for group "humanities" imeta add u humanities Admin ton imeta add u humanities Admin chris and add the following policy to the rulebase to allow admins to add group members: acpresudogroupmemberadd( *groupname, *username, *policykv) { foreach (*admin in SELECT META_DATA_ATTR_VALUE WHERE USER_NAME = 'humanities' AND META_DATA_ATTR_NAME = 'Admin' AND META_DATA_ATTR_VALUE = '$usernameclient' ) { succeed; } fail; # disallow all other users }
11 Sudo feature to overcome chicken and egg issue Extended use case: - we also want to use Sudo services to allow 'ton' and 'chris' to add groups - (only) the actor should also act as the initial 'admin' of the newly created group Preparation: - establish policy to allow ton and chris to use msisudogroupadd() rule body that ton can use to add group 'science':... msisudogroupadd('science', 'Admin', 'ton', '', *policykv); will be added by Sudo service as initial metadata to the 'science' group object, immediately after the group is created
12 Demo ITS Research IT
13 Status of the Sudo microservices set Used by our university in our Yoda production systems (irods based) Microservices plugin set source and an RPM binary installable with irods located at Current plan: package and make available as open source by July with binaries for latest releases irods 4.1 and 4.2
14 irods User Empowerment A matter of Sudo microservices For more information: yoda@uu.nl Chris Smeele can be reached at c.j.smeele@uu.nl
15
16 SUDO microservices in detail: user management msisudouseradd ( *username, *initialattr, *initialvalue, *initialunit, *policykv ) msisudouserremove ( *username, *policykv )
17 SUDO microservices in detail: group management msisudogroupadd ( *groupname, *initialattr, *initialvalue, *initialunit, *policykv ) msisudogroupremove ( *groupname, *policykv ) msisudogroupmemberadd ( *groupname, *username, *policykv ) msisudogroupmemberremove ( *groupname, *username, *policykv )
18 SUDO microservices in detail: ACL management msisudoobjaclset ( *recursive, *accesslevel, *othername, *objpath, *policykv ) *recursive flag is of type integer 0 = no recursion, 1 = apply recursion *accesslevel can be any of "null", "read", "write", "own", "inherit", "noinherit" NB: do not specify an 'admin:' prefix, this will be applied automatically *othername is the name of an existing user or group
19 SUDO microservices in detail: metadata management msisudoobjmetaadd ( *objname, *objtype, *attribute, *value, *unit, *policykv ) msisudoobjmetaset: (parameters similar to microservice msisudoobjmetaadd) msisudoobjmetaremove ( *objname, *objtype, *wildcards, *attribute, *value, *unit, *policykv ) *wildcard flag is of type integer 0 = no wildcard, 1 = apply wildcard wildcards follow imeta command syntax
irods Security Aspects Willem Elbers CLARIN-ERIC, Netherlands
 irods Security Aspects Willem Elbers CLARIN-ERIC, Netherlands Utrecht,28-29 April 2014 Contents Client / Server connections Authentication Within Zone Across Zone Authorization EUDAT B2ACCESS Client /
irods Security Aspects Willem Elbers CLARIN-ERIC, Netherlands Utrecht,28-29 April 2014 Contents Client / Server connections Authentication Within Zone Across Zone Authorization EUDAT B2ACCESS Client /
irods for Data Management and Archiving UGM 2018 Masilamani Subramanyam
 irods for Data Management and Archiving UGM 2018 Masilamani Subramanyam Agenda Introduction Challenges Data Transfer Solution irods use in Data Transfer Solution irods Proof-of-Concept Q&A Introduction
irods for Data Management and Archiving UGM 2018 Masilamani Subramanyam Agenda Introduction Challenges Data Transfer Solution irods use in Data Transfer Solution irods Proof-of-Concept Q&A Introduction
An overview of irods clients. Ton Smeele
 An overview of irods clients Ton Smeele agenda irods client-server architecture Client libraries Out of the box clients Example customer-developed client irods used in a 2-tier model Client Server Client
An overview of irods clients Ton Smeele agenda irods client-server architecture Client libraries Out of the box clients Example customer-developed client irods used in a 2-tier model Client Server Client
irods Hands-On Elena Erastova (RZG) Based on material provided by RENCI
 irods Hands-On Elena Erastova (RZG) Based on material provided by RENCI Rome, 28 October 2013 I. irods Getting Started icommands Contents II. irods Data (grid) Administration Zone Federation Microservices
irods Hands-On Elena Erastova (RZG) Based on material provided by RENCI Rome, 28 October 2013 I. irods Getting Started icommands Contents II. irods Data (grid) Administration Zone Federation Microservices
irods Hands-On Elena Erastova (RZG) Based on material provided by RENCI
 irods Hands-On Elena Erastova (RZG) Based on material provided by RENCI Rome, 28 October 2013 I. irods Getting Started icommands Contents II. irods Data (grid) Administration Zone Federation Microservices
irods Hands-On Elena Erastova (RZG) Based on material provided by RENCI Rome, 28 October 2013 I. irods Getting Started icommands Contents II. irods Data (grid) Administration Zone Federation Microservices
irods hands-on tutorial
 irods hands-on tutorial WORKSHOP 28 TH /29 TH APRIL 2015 Christine Staiger Contents The Basics Installation Tools for administration Adding data and metadata Complex storage systems Federations between
irods hands-on tutorial WORKSHOP 28 TH /29 TH APRIL 2015 Christine Staiger Contents The Basics Installation Tools for administration Adding data and metadata Complex storage systems Federations between
TECHNICAL OVERVIEW irods Technical Overview 2016 edition RCI_iROD_Report_final2.indd 1-2 5/26/16 9:21 AM
 TECHNICAL OVERVIEW Imagine you were responsible for petabytes of genome sequencing data, which could underpin decades of medical breakthroughs? Or the digitized cultural heritage of an entire nation?
TECHNICAL OVERVIEW Imagine you were responsible for petabytes of genome sequencing data, which could underpin decades of medical breakthroughs? Or the digitized cultural heritage of an entire nation?
The irods Rule Language. Hao Xu 2014/6/18
 The irods Rule Language Hao Xu xuh@email.unc.edu 2014/6/18 Outline Overview New Features Examples Overview Overview Compile Time Rule Rule core.irb Parser Type checker index File Index Runtime Rule core.irb
The irods Rule Language Hao Xu xuh@email.unc.edu 2014/6/18 Outline Overview New Features Examples Overview Overview Compile Time Rule Rule core.irb Parser Type checker index File Index Runtime Rule core.irb
DC69 C# &.NET DEC 2015
 Q.2 a. Briefly explain the advantage of framework base classes in.net. (5).NET supplies a library of base classes that we can use to implement applications quickly. We can use them by simply instantiating
Q.2 a. Briefly explain the advantage of framework base classes in.net. (5).NET supplies a library of base classes that we can use to implement applications quickly. We can use them by simply instantiating
Academic Workflow for Research Repositories Using irods and Object Storage
 1 Academic Workflow for Research Repositories Using irods and Object Storage 2016 irods User s Group Meeting 9 June 2016 Randall Splinter, Ph.D. HPC Research Computing Solutions Architect RSplinter@ 770.633.2994
1 Academic Workflow for Research Repositories Using irods and Object Storage 2016 irods User s Group Meeting 9 June 2016 Randall Splinter, Ph.D. HPC Research Computing Solutions Architect RSplinter@ 770.633.2994
irods Manual Author: Renaissance Computing Institute (RENCI) Version: Date: page 1
 Author: Renaissance Computing Institute (RENCI) Version: 4.0.3 Date: 2014-08-20 page 1 Table of Contents 1 Release Notes 6 2 License 6 3 Overview 7 4 Download 7 4.1 Binaries 7 4.2 Open Source 7 5 Installation
Author: Renaissance Computing Institute (RENCI) Version: 4.0.3 Date: 2014-08-20 page 1 Table of Contents 1 Release Notes 6 2 License 6 3 Overview 7 4 Download 7 4.1 Binaries 7 4.2 Open Source 7 5 Installation
Sudo: Switch User Do. Administrative Privileges Delegation Campus-Booster ID : **XXXXX. Copyright SUPINFO. All rights reserved
 Sudo: Switch User Do Administrative Privileges Delegation Campus-Booster ID : **XXXXX www.supinfo.com Copyright SUPINFO. All rights reserved Sudo: Switch User Do Your trainer Presenter s Name Title: **Enter
Sudo: Switch User Do Administrative Privileges Delegation Campus-Booster ID : **XXXXX www.supinfo.com Copyright SUPINFO. All rights reserved Sudo: Switch User Do Your trainer Presenter s Name Title: **Enter
Advanced Training Manual: Approvals
 Advanced Training Manual: Approvals Last Updated: March 2012 Advanced Training Manual: Approvals Page 1 of 16 Table of Contents Introduction Training Objective Approvals Settings Approval Options Configure
Advanced Training Manual: Approvals Last Updated: March 2012 Advanced Training Manual: Approvals Page 1 of 16 Table of Contents Introduction Training Objective Approvals Settings Approval Options Configure
Collecting data types from the thermodynamic data and registering those at the DCO data portal.
 Use Case: Collecting data types from the thermodynamic data and registering those at the DCO data portal. Point of Contact Name: Apurva Kumar Sinha (sinhaa2@rpi.edu) Use Case Name Give a short descriptive
Use Case: Collecting data types from the thermodynamic data and registering those at the DCO data portal. Point of Contact Name: Apurva Kumar Sinha (sinhaa2@rpi.edu) Use Case Name Give a short descriptive
Windows Server 2012 R2 Windows PowerShell Fundamentals
 Windows Server 2012 R2 Windows PowerShell Fundamentals Windows Server 2012 R2 Hands-on lab Windows PowerShell is a command-line shell and scripting language that helps IT professionals achieve greater
Windows Server 2012 R2 Windows PowerShell Fundamentals Windows Server 2012 R2 Hands-on lab Windows PowerShell is a command-line shell and scripting language that helps IT professionals achieve greater
Create and Apply Clientless SSL VPN Policies for Accessing. Connection Profile Attributes for Clientless SSL VPN
 Create and Apply Clientless SSL VPN Policies for Accessing Resources, page 1 Connection Profile Attributes for Clientless SSL VPN, page 1 Group Policy and User Attributes for Clientless SSL VPN, page 3
Create and Apply Clientless SSL VPN Policies for Accessing Resources, page 1 Connection Profile Attributes for Clientless SSL VPN, page 1 Group Policy and User Attributes for Clientless SSL VPN, page 3
Manual Prepared by GalaxyVisions Customer Care Team
 Toll Free: 1.866-GVHOST1 (484-6781) 882 3rd Ave, 8th Floor, Brooklyn, Ny 11232 Manual Prepared by GalaxyVisions Customer Care Team MySQL Main Topics How cpanel Install and Distributes MySQL How to tell
Toll Free: 1.866-GVHOST1 (484-6781) 882 3rd Ave, 8th Floor, Brooklyn, Ny 11232 Manual Prepared by GalaxyVisions Customer Care Team MySQL Main Topics How cpanel Install and Distributes MySQL How to tell
ForeScout Extended Module for IBM BigFix
 ForeScout Extended Module for IBM BigFix Version 1.0.0 Table of Contents About this Integration... 4 Use Cases... 4 Additional BigFix Documentation... 4 About this Module... 4 Concepts, Components, Considerations...
ForeScout Extended Module for IBM BigFix Version 1.0.0 Table of Contents About this Integration... 4 Use Cases... 4 Additional BigFix Documentation... 4 About this Module... 4 Concepts, Components, Considerations...
EMu Documentation. Multi-group Support. Document Version 1. EMu Version KE Software. All rights reserved.
 EMu Documentation Multi-group Support Document Version 1 EMu Version 4.0.0.3 www.kesoftware.com 2011 KE Software. All rights reserved. Contents SECTION 1 Overview 1 SECTION 2 Specifying a user's groups
EMu Documentation Multi-group Support Document Version 1 EMu Version 4.0.0.3 www.kesoftware.com 2011 KE Software. All rights reserved. Contents SECTION 1 Overview 1 SECTION 2 Specifying a user's groups
Network Monitoring and Management Cacti Plugin Configuration and Use (Settings and Thold)
 Network Monitoring and Management Cacti Plugin Configuration and Use (Settings and Thold) Notes: Commands preceded with "$" imply that you should execute the command as a general user - not as root. Commands
Network Monitoring and Management Cacti Plugin Configuration and Use (Settings and Thold) Notes: Commands preceded with "$" imply that you should execute the command as a general user - not as root. Commands
Overview of AdminSDHolder, protected groups and SDPROP Controlling groups that are protected by AdminSDHolder Security Descriptor propagator
 AdminSDHolder, Protected Groups and SDPROP John Policelli At a Glance: Overview of AdminSDHolder, protected groups and SDPROP Controlling groups that are protected by AdminSDHolder Security Descriptor
AdminSDHolder, Protected Groups and SDPROP John Policelli At a Glance: Overview of AdminSDHolder, protected groups and SDPROP Controlling groups that are protected by AdminSDHolder Security Descriptor
Role Configuration Mode Commands
 Role configuration mode commands allow you to define various rules for users who are assigned a role and optionally, to describe a role definition. Roles determine the privileges that a user has, the commands
Role configuration mode commands allow you to define various rules for users who are assigned a role and optionally, to describe a role definition. Roles determine the privileges that a user has, the commands
irods Manual Author: Renaissance Computing Institute (RENCI) Version: Date: page 1
 Author: Renaissance Computing Institute (RENCI) Version: 4.0.2 Date: 2014-06-17 page 1 Table of Contents 1 Release Notes 5 2 License 5 3 Overview 6 4 Download 6 4.1 Binaries 6 4.2 Open Source 6 5 Installation
Author: Renaissance Computing Institute (RENCI) Version: 4.0.2 Date: 2014-06-17 page 1 Table of Contents 1 Release Notes 5 2 License 5 3 Overview 6 4 Download 6 4.1 Binaries 6 4.2 Open Source 6 5 Installation
Red Hat Container Development Kit 3.0 Installation Guide
 Red Hat Container Development Kit 3.0 Installation Guide Guide to installing Red Hat Container Development Kit Brian Brock Robert Krátký Chris Negus Red Hat Developer Group Documentation Team Red Hat
Red Hat Container Development Kit 3.0 Installation Guide Guide to installing Red Hat Container Development Kit Brian Brock Robert Krátký Chris Negus Red Hat Developer Group Documentation Team Red Hat
Use Software Collections for PHP 5.6 support on RHEL and CentOS 6 and 7
 Use Software Collections for PHP 5.6 support on RHEL and CentOS 6 and 7 Introduction Audience Disclaimer Software Collections and PHP Installation Install MySQL Enable Software Collections Add repositories
Use Software Collections for PHP 5.6 support on RHEL and CentOS 6 and 7 Introduction Audience Disclaimer Software Collections and PHP Installation Install MySQL Enable Software Collections Add repositories
RecordPoint: Security Settings
 RecordPoint: Security Settings 1 Overview The purpose of this guide is to provide information on the Security Settings for RecordPoint. 2 RecordPoint User Personas 2.1 Record Administrator Access to all
RecordPoint: Security Settings 1 Overview The purpose of this guide is to provide information on the Security Settings for RecordPoint. 2 RecordPoint User Personas 2.1 Record Administrator Access to all
Practical Steps Implementing Red Hat Identity Management Solution David Sirrine Senior Technical Account Manager, Red Hat Jerel Gilmer SEC June 29,
 Practical Steps Implementing Red Hat Identity Management Solution David Sirrine Senior Technical Account Manager, Red Hat Jerel Gilmer SEC June 29, 2016 Agenda Brief introduction to the Red Hat Identity
Practical Steps Implementing Red Hat Identity Management Solution David Sirrine Senior Technical Account Manager, Red Hat Jerel Gilmer SEC June 29, 2016 Agenda Brief introduction to the Red Hat Identity
Bisque and irods. Kris Kvilekval. Center for Bio-Image Informatics, UCSB
 Bisque and irods Center for Bio-Image Informatics, UCSB http://bovary.iplantcollaborative.org Kris Kvilekval Bisque - Image database Ground truth Automated analysis Flexible and hierarchical annotations
Bisque and irods Center for Bio-Image Informatics, UCSB http://bovary.iplantcollaborative.org Kris Kvilekval Bisque - Image database Ground truth Automated analysis Flexible and hierarchical annotations
Building Helper Tools. #FileWave2017
 Building Helper Tools Damon O Hare - Workstation/Automation Engineer, Matthews Intl. Ben Miles - Senior Consulting Engineer, FileWave My Background Automating large deployments for 15+ years Experience
Building Helper Tools Damon O Hare - Workstation/Automation Engineer, Matthews Intl. Ben Miles - Senior Consulting Engineer, FileWave My Background Automating large deployments for 15+ years Experience
Apple TV Management. Moving education forward
 WHITE PAPER Apple TV Management Moving education forward If you think Apple TV devices are just for entertainment, think again. In a recent Jamf Nation survey, 99 percent of the 502 school respondents
WHITE PAPER Apple TV Management Moving education forward If you think Apple TV devices are just for entertainment, think again. In a recent Jamf Nation survey, 99 percent of the 502 school respondents
Globus Research Data Management: Campus Deployment and Configuration. Steve Tuecke Vas Vasiliadis
 Globus Research Data Management: Campus Deployment and Configuration Steve Tuecke Vas Vasiliadis Presentations and other useful information available at globus.org/events/xsede15/tutorial 2 Agenda Globus
Globus Research Data Management: Campus Deployment and Configuration Steve Tuecke Vas Vasiliadis Presentations and other useful information available at globus.org/events/xsede15/tutorial 2 Agenda Globus
P4EXP Help January 2018
 P4EXP Help 2018.1 January 2018 Copyright 1999-2018 Perforce Software. All rights reserved. Perforce Software and documentation is available from www.perforce.com. You can download and use Perforce programs,
P4EXP Help 2018.1 January 2018 Copyright 1999-2018 Perforce Software. All rights reserved. Perforce Software and documentation is available from www.perforce.com. You can download and use Perforce programs,
Joomla Pre-install Tasks
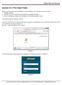 Joomla 3.0.1 Pre-install Tasks Before commencing the actual installation of Joomla CMS on your webhost you have to create: A MySQL database A MySQL user ( with password based access to the MySQL database
Joomla 3.0.1 Pre-install Tasks Before commencing the actual installation of Joomla CMS on your webhost you have to create: A MySQL database A MySQL user ( with password based access to the MySQL database
User Guide CIPA Administration Console Open e-trustex
 EUROPEAN COMMISSION DIRECTORATE-GENERAL INFORMATICS User Guide CIPA Administration Console Open e-trustex Date: 17/03/2017 Version: 1.11 Authors: Revised by: Gianluca VENTRE Anamaria BATRINU Bruno POSSEMIERS
EUROPEAN COMMISSION DIRECTORATE-GENERAL INFORMATICS User Guide CIPA Administration Console Open e-trustex Date: 17/03/2017 Version: 1.11 Authors: Revised by: Gianluca VENTRE Anamaria BATRINU Bruno POSSEMIERS
Apple TV Management. Moving higher education forward
 WHITE PAPER Apple TV Management Moving higher education forward If you think Apple TV devices are just for entertainment, think again. In a recent Jamf Nation survey, 95 percent of the 110 higher education
WHITE PAPER Apple TV Management Moving higher education forward If you think Apple TV devices are just for entertainment, think again. In a recent Jamf Nation survey, 95 percent of the 110 higher education
ForeScout CounterACT. Configuration Guide. Version 4.3
 ForeScout CounterACT Authentication Module: RADIUS Plugin Version 4.3 Table of Contents Overview... 4 Understanding the 802.1X Protocol... 4 About the CounterACT RADIUS Plugin... 6 IPv6 Support... 7 About
ForeScout CounterACT Authentication Module: RADIUS Plugin Version 4.3 Table of Contents Overview... 4 Understanding the 802.1X Protocol... 4 About the CounterACT RADIUS Plugin... 6 IPv6 Support... 7 About
CO MySQL for Database Administrators
 CO-61762 MySQL for Database Administrators Summary Duration 5 Days Audience Administrators, Database Designers, Developers Level Professional Technology Oracle MySQL 5.5 Delivery Method Instructor-led
CO-61762 MySQL for Database Administrators Summary Duration 5 Days Audience Administrators, Database Designers, Developers Level Professional Technology Oracle MySQL 5.5 Delivery Method Instructor-led
Is code in your project sane enough?
 Is code in your project sane enough? Red Hat Kamil Dudka February 6th, 2015 Abstract This demo session will show how we can easily check the sanity of code in our project. There is a tool named csmock,
Is code in your project sane enough? Red Hat Kamil Dudka February 6th, 2015 Abstract This demo session will show how we can easily check the sanity of code in our project. There is a tool named csmock,
IBM Atlas Policy Distribution Administrators Guide: IER Connector. for IBM Atlas Suite v6
 IBM Atlas Policy Distribution Administrators Guide: IER Connector for IBM Atlas Suite v6 IBM Atlas Policy Distribution: IER Connector This edition applies to version 6.0 of IBM Atlas Suite (product numbers
IBM Atlas Policy Distribution Administrators Guide: IER Connector for IBM Atlas Suite v6 IBM Atlas Policy Distribution: IER Connector This edition applies to version 6.0 of IBM Atlas Suite (product numbers
irods 4.0 and Beyond Presented at the irods & DDN User Group Meeting 2014
 irods 4.0 and Beyond Presented at the irods & DDN User Group Meeting 2014 September 8, 2014 irods 4.0 and Beyond -- irods & DDN User Group Meeting 2014 1 Motivation and Goals irods is open source middleware
irods 4.0 and Beyond Presented at the irods & DDN User Group Meeting 2014 September 8, 2014 irods 4.0 and Beyond -- irods & DDN User Group Meeting 2014 1 Motivation and Goals irods is open source middleware
Definition Center Installation for Linux
 Definition Center 10.2.0 - Installation for Linux These are instructions to install, configure, upgrade, start, stop and uninstall Definition Center 10.2.0 (DC) on a Linux system. In this installation,
Definition Center 10.2.0 - Installation for Linux These are instructions to install, configure, upgrade, start, stop and uninstall Definition Center 10.2.0 (DC) on a Linux system. In this installation,
Design Proposal for Hive Metastore Plugin
 Design Proposal for Hive Metastore Plugin 1. Use Cases and Motivations 1.1 Hive Privilege Changes as Result of SQL Object Changes SQL DROP TABLE/DATABASE command would like to have all the privileges directly
Design Proposal for Hive Metastore Plugin 1. Use Cases and Motivations 1.1 Hive Privilege Changes as Result of SQL Object Changes SQL DROP TABLE/DATABASE command would like to have all the privileges directly
DV3110 Group Setup. Setting up new user groups and assigning users and assets to the newly created group.
 DV3110 Group Setup Software Release ViewPoint v1.1.1 Scope Setting up new user groups and assigning users and assets to the newly created group. Purpose Groups are set up to associate users to Assets.
DV3110 Group Setup Software Release ViewPoint v1.1.1 Scope Setting up new user groups and assigning users and assets to the newly created group. Purpose Groups are set up to associate users to Assets.
EveBox Documentation. Release. Jason Ish
 EveBox Documentation Release Jason Ish Jan 25, 2018 Contents: 1 Installation 1 2 Server 3 2.1 Running................................................. 3 2.2 Oneshot Mode..............................................
EveBox Documentation Release Jason Ish Jan 25, 2018 Contents: 1 Installation 1 2 Server 3 2.1 Running................................................. 3 2.2 Oneshot Mode..............................................
Honu. Version November 6, 2010
 Honu Version 5.0.2 November 6, 2010 Honu is a family of languages built on top of Racket. Honu syntax resembles Java. Like Racket, however, Honu has no fixed syntax, because Honu supports extensibility
Honu Version 5.0.2 November 6, 2010 Honu is a family of languages built on top of Racket. Honu syntax resembles Java. Like Racket, however, Honu has no fixed syntax, because Honu supports extensibility
Installation and Setup Guide
 SnapCenter Software 4.1 Installation and Setup Guide December 2018 215-13401_C0 doccomments@netapp.com Updated for 4.1.1 Table of Contents 3 Contents Deciding whether to read the SnapCenter installation
SnapCenter Software 4.1 Installation and Setup Guide December 2018 215-13401_C0 doccomments@netapp.com Updated for 4.1.1 Table of Contents 3 Contents Deciding whether to read the SnapCenter installation
penelope SET UP AN ACTION TRIGGER FOR A DOCUMENT ATHENA SOFTWARE Last updated: November 13, 2015
 penelope SET UP AN ACTION TRIGGER FOR A DOCUMENT ATHENA SOFTWARE Last updated: November 13, 2015 about action triggers THE BASICS There is set of Action Triggers specific to Documents that are available
penelope SET UP AN ACTION TRIGGER FOR A DOCUMENT ATHENA SOFTWARE Last updated: November 13, 2015 about action triggers THE BASICS There is set of Action Triggers specific to Documents that are available
Collecting data types from the thermodynamic data and registering those at the DCO data portal.
 Use Case: Collecting data types from the thermodynamic data and registering those at the DCO data portal. Point of Contact Name: Apurva Kumar Sinha (sinhaa2@rpi.edu) Use Case Name Give a short descriptive
Use Case: Collecting data types from the thermodynamic data and registering those at the DCO data portal. Point of Contact Name: Apurva Kumar Sinha (sinhaa2@rpi.edu) Use Case Name Give a short descriptive
Security Provider Integration LDAP Server
 Security Provider Integration LDAP Server 2017 Bomgar Corporation. All rights reserved worldwide. BOMGAR and the BOMGAR logo are trademarks of Bomgar Corporation; other trademarks shown are the property
Security Provider Integration LDAP Server 2017 Bomgar Corporation. All rights reserved worldwide. BOMGAR and the BOMGAR logo are trademarks of Bomgar Corporation; other trademarks shown are the property
client through crl configure Commands
 CHAPTER 7 7-1 client-access-rule Chapter 7 client-access-rule To configure rules that limit the remote access client types and versions that can connect via IPSec through the adaptive security appliance,
CHAPTER 7 7-1 client-access-rule Chapter 7 client-access-rule To configure rules that limit the remote access client types and versions that can connect via IPSec through the adaptive security appliance,
Lab Working with Linux Command Line
 Introduction In this lab, you will use the Linux command line to manage files and folders and perform some basic administrative tasks. Recommended Equipment A computer with a Linux OS, either installed
Introduction In this lab, you will use the Linux command line to manage files and folders and perform some basic administrative tasks. Recommended Equipment A computer with a Linux OS, either installed
Apache Ranger User Guide
 Apache Ranger 0.5 - User Guide USER GUIDE Version : 0.5.0 September 2015 About this document Getting started General Features Login to the system: Log out to the system: Service Manager (Access Manager)
Apache Ranger 0.5 - User Guide USER GUIDE Version : 0.5.0 September 2015 About this document Getting started General Features Login to the system: Log out to the system: Service Manager (Access Manager)
Partner Center: Secure application model
 Partner Center: Secure application model The information provided in this document is provided "as is" without warranty of any kind. Microsoft disclaims all warranties, either express or implied, including
Partner Center: Secure application model The information provided in this document is provided "as is" without warranty of any kind. Microsoft disclaims all warranties, either express or implied, including
How to: Create a Site in a SharePoint Site Collection. Updated: 12 July 2012
 How to: Create a Site in a SharePoint Site Collection Updated: 12 July 2012 Table of Contents Creating sites in the HPIT/Sites sit e collect ion... 3 Create the site... 3 Initial setup... 4 Banner Setup...
How to: Create a Site in a SharePoint Site Collection Updated: 12 July 2012 Table of Contents Creating sites in the HPIT/Sites sit e collect ion... 3 Create the site... 3 Initial setup... 4 Banner Setup...
Lesson 3 Transcript: Part 2 of 2 Tools & Scripting
 Lesson 3 Transcript: Part 2 of 2 Tools & Scripting Slide 1: Cover Welcome to lesson 3 of the DB2 on Campus Lecture Series. Today we are going to talk about tools and scripting. And this is part 2 of 2
Lesson 3 Transcript: Part 2 of 2 Tools & Scripting Slide 1: Cover Welcome to lesson 3 of the DB2 on Campus Lecture Series. Today we are going to talk about tools and scripting. And this is part 2 of 2
Using the Horizon vcenter Orchestrator Plug-In. VMware Horizon 6 6.0
 Using the Horizon vcenter Orchestrator Plug-In VMware Horizon 6 6.0 You can find the most up-to-date technical documentation on the VMware Web site at: https://docs.vmware.com/ The VMware Web site also
Using the Horizon vcenter Orchestrator Plug-In VMware Horizon 6 6.0 You can find the most up-to-date technical documentation on the VMware Web site at: https://docs.vmware.com/ The VMware Web site also
Tableau Server on Linux 2018 Update
 # T C 1 8 Tableau Server on Linux 2018 Update Robert S. Brewer Manager, Engineering Tableau Software, Inc. About Me At Tableau Why Linux? Because you wanted it! Orgs already using Linux for servers Reduce
# T C 1 8 Tableau Server on Linux 2018 Update Robert S. Brewer Manager, Engineering Tableau Software, Inc. About Me At Tableau Why Linux? Because you wanted it! Orgs already using Linux for servers Reduce
Trigger: Actor clicks on the Register button on the website s homepage.
 Project The Gender Knot Project ID: Team 1 Executive Sponsor: Mary Rose, Director of the TU Press Project Manager: Joey Garrido, Kenny Ng, and Abhay Kshirsagar Business Analyst: Loi Tran, Anthony Minford,
Project The Gender Knot Project ID: Team 1 Executive Sponsor: Mary Rose, Director of the TU Press Project Manager: Joey Garrido, Kenny Ng, and Abhay Kshirsagar Business Analyst: Loi Tran, Anthony Minford,
CounterACT Macintosh/Linux Property Scanner Plugin
 CounterACT Macintosh/Linux Property Scanner Plugin Version 7.0.1 and Above Table of Contents About the Macintosh/Linux Property Scanner Plugin... 4 Requirements... 4 Supported Operating Systems... 4 Accessing
CounterACT Macintosh/Linux Property Scanner Plugin Version 7.0.1 and Above Table of Contents About the Macintosh/Linux Property Scanner Plugin... 4 Requirements... 4 Supported Operating Systems... 4 Accessing
ForeScout Extended Module for IBM BigFix
 Version 1.1 Table of Contents About BigFix Integration... 4 Use Cases... 4 Additional BigFix Documentation... 4 About this Module... 4 About Support for Dual Stack Environments... 5 Concepts, Components,
Version 1.1 Table of Contents About BigFix Integration... 4 Use Cases... 4 Additional BigFix Documentation... 4 About this Module... 4 About Support for Dual Stack Environments... 5 Concepts, Components,
Inception Cloud User s Guide
 Inception Cloud User s Guide 1 Overview Creating an inception cloud consists of preparing your workstation, preparing the VM environment by adding a temporary boot-up machine, and then executing the orchestrator
Inception Cloud User s Guide 1 Overview Creating an inception cloud consists of preparing your workstation, preparing the VM environment by adding a temporary boot-up machine, and then executing the orchestrator
CIAM: Need for Identity Governance & Assurance. Yash Prakash VP of Products
 CIAM: Need for Identity Governance & Assurance Yash Prakash VP of Products Key Tenets of CIAM Solution Empower consumers, CSRs & administrators Scale to millions of entities, cloud based service Security
CIAM: Need for Identity Governance & Assurance Yash Prakash VP of Products Key Tenets of CIAM Solution Empower consumers, CSRs & administrators Scale to millions of entities, cloud based service Security
Operating systems. Lecture 7
 Operating systems. Lecture 7 Michał Goliński 2018-11-13 Introduction Recall Plan for today History of C/C++ Compiler on the command line Automating builds with make CPU protection rings system calls pointers
Operating systems. Lecture 7 Michał Goliński 2018-11-13 Introduction Recall Plan for today History of C/C++ Compiler on the command line Automating builds with make CPU protection rings system calls pointers
QUICK START GUIDE: CORRELEAD POWERED BY FORCIVITY
 Release Notes v2.1 Released February 19, 2018 - Bug fixes and stability fixes - Added functionality to use Salesforce Duplicate and Matching rules to associate leads to accounts v2.0 Released January 30,
Release Notes v2.1 Released February 19, 2018 - Bug fixes and stability fixes - Added functionality to use Salesforce Duplicate and Matching rules to associate leads to accounts v2.0 Released January 30,
A national approach for storage scale-out scenarios based on irods
 A national approach for storage scale-out scenarios based on irods Christine Staiger Ton Smeele SURFsara Utrecht University Science Park 140, ITS/RDM Amsterdam, The Heidelberglaan 8, Netherlands Utrecht,
A national approach for storage scale-out scenarios based on irods Christine Staiger Ton Smeele SURFsara Utrecht University Science Park 140, ITS/RDM Amsterdam, The Heidelberglaan 8, Netherlands Utrecht,
OT-C2D User Guide Alcatel-Lucent 8AL USAB Ed.01 All Rights Reserved Alcatel-Lucent 2012
 OT-C2D User Guide Alcatel-Lucent All Rights Reserved Alcatel-Lucent 2012 I. User Guide Description OT-C2D has 2 different modes of management. The first one is Customer Mode which shows only the sheets
OT-C2D User Guide Alcatel-Lucent All Rights Reserved Alcatel-Lucent 2012 I. User Guide Description OT-C2D has 2 different modes of management. The first one is Customer Mode which shows only the sheets
Using the Migration Utility to Migrate Data from ACS 4.x to ACS 5.5
 6 CHAPTER Using the Migration Utility to Migrate Data from ACS 4.x to ACS 5.5 This chapter describes how to migrate data from ACS 4.x to ACS 5.5 and contains: Introduction, page 6-1 Running the Migration
6 CHAPTER Using the Migration Utility to Migrate Data from ACS 4.x to ACS 5.5 This chapter describes how to migrate data from ACS 4.x to ACS 5.5 and contains: Introduction, page 6-1 Running the Migration
Use Cases for Unix & Linux
 WHITE PAPER 15 Server Privilege Management PowerBroker for Unix & Linux, PowerBroker Identity Services, and PowerBroker for Sudo Table of Contents Executive Summary... 3 15 Common Use Cases... 4 1. Removing
WHITE PAPER 15 Server Privilege Management PowerBroker for Unix & Linux, PowerBroker Identity Services, and PowerBroker for Sudo Table of Contents Executive Summary... 3 15 Common Use Cases... 4 1. Removing
Using the Horizon vrealize Orchestrator Plug-In
 Using the Horizon vrealize Orchestrator Plug-In VMware Horizon 6 version 6.2.3, VMware Horizon 7 versions 7.0.3 and later Modified on 4 JAN 2018 VMware Horizon 7 7.4 You can find the most up-to-date technical
Using the Horizon vrealize Orchestrator Plug-In VMware Horizon 6 version 6.2.3, VMware Horizon 7 versions 7.0.3 and later Modified on 4 JAN 2018 VMware Horizon 7 7.4 You can find the most up-to-date technical
Adobe Sign for Microsoft Dynamics
 Adobe Sign for Microsoft Dynamics Installation & Configuration Guide (v5) Last Updated: March 16, 2017 2017 Adobe Systems Incorporated. All rights reserved Table of Contents Overview... 3 Prerequisites...
Adobe Sign for Microsoft Dynamics Installation & Configuration Guide (v5) Last Updated: March 16, 2017 2017 Adobe Systems Incorporated. All rights reserved Table of Contents Overview... 3 Prerequisites...
Anchore Container Image Scanner Plugin
 Anchore Container Image Scanner Plugin Plugin Information View Anchore Container Image Scanner on the plugin site for more information. Older versions of this plugin may not be safe to use. Please review
Anchore Container Image Scanner Plugin Plugin Information View Anchore Container Image Scanner on the plugin site for more information. Older versions of this plugin may not be safe to use. Please review
Forescout. Configuration Guide. Version 4.4
 Forescout Version 4.4 Contact Information Forescout Technologies, Inc. 190 West Tasman Drive San Jose, CA 95134 USA https://www.forescout.com/support/ Toll-Free (US): 1.866.377.8771 Tel (Intl): 1.408.213.3191
Forescout Version 4.4 Contact Information Forescout Technologies, Inc. 190 West Tasman Drive San Jose, CA 95134 USA https://www.forescout.com/support/ Toll-Free (US): 1.866.377.8771 Tel (Intl): 1.408.213.3191
Quiz 0 Answer Key. Answers other than the below may be possible. Multiple Choice. 0. a 1. a 2. b 3. c 4. b 5. d. True or False.
 Quiz 0 Answer Key Answers other than the below may be possible. Multiple Choice. 0. a 1. a 2. b 3. c 4. b 5. d True or False. 6. T or F 7. T 8. F 9. T 10. T or F Itching for Week 0? 11. 00011001 + 00011001
Quiz 0 Answer Key Answers other than the below may be possible. Multiple Choice. 0. a 1. a 2. b 3. c 4. b 5. d True or False. 6. T or F 7. T 8. F 9. T 10. T or F Itching for Week 0? 11. 00011001 + 00011001
ForeScout Extended Module for ServiceNow
 ForeScout Extended Module for ServiceNow Version 1.1.0 Table of Contents About this Integration... 4 Use Cases... 4 Asset Identification... 4 Asset Inventory True-up... 5 Additional ServiceNow Documentation...
ForeScout Extended Module for ServiceNow Version 1.1.0 Table of Contents About this Integration... 4 Use Cases... 4 Asset Identification... 4 Asset Inventory True-up... 5 Additional ServiceNow Documentation...
CSE 390a Lecture 3. Multi-user systems; remote login; editors; users/groups; permissions
 CSE 390a Lecture 3 Multi-user systems; remote login; editors; users/groups; permissions slides created by Marty Stepp, modified by Jessica Miller and Ruth Anderson http://www.cs.washington.edu/390a/ 1
CSE 390a Lecture 3 Multi-user systems; remote login; editors; users/groups; permissions slides created by Marty Stepp, modified by Jessica Miller and Ruth Anderson http://www.cs.washington.edu/390a/ 1
MYRO My Record Oriented privilege system
 MYRO My Record Oriented privilege system Giorgio Calderone IFC - INAF Palermo, Italy Luciano Nicastro IASF - INAF Bologna, Italy April 29, 2015 Ver. 0.3.2-alpha3 http://ross.iasfbo.inaf.it/myro This page
MYRO My Record Oriented privilege system Giorgio Calderone IFC - INAF Palermo, Italy Luciano Nicastro IASF - INAF Bologna, Italy April 29, 2015 Ver. 0.3.2-alpha3 http://ross.iasfbo.inaf.it/myro This page
Brainspace: Quick Reference
 Brainspace is a dynamic and flexible data analysis tool. The purpose of this document is to provide a quick reference guide to navigation, use, and workflow within Brainspace. This guide is divided into
Brainspace is a dynamic and flexible data analysis tool. The purpose of this document is to provide a quick reference guide to navigation, use, and workflow within Brainspace. This guide is divided into
Release Notes. Version Copyright All Rights Reserved.
 Release Notes Version 3.8.9 Copyright 2016. All Rights Reserved. Table of Contents 1 About this Release... 3 1.1 Scope... 3 1.2 Audience... 3 1.3 Definitions, Acronyms and Abbreviations... 3 2 System Requirements...
Release Notes Version 3.8.9 Copyright 2016. All Rights Reserved. Table of Contents 1 About this Release... 3 1.1 Scope... 3 1.2 Audience... 3 1.3 Definitions, Acronyms and Abbreviations... 3 2 System Requirements...
View Security and Access Privileges
 View Security and Access Privileges Individual access privileges to graphical objects in a View application can be implemented by adding users to the View target and assigning each user an appropriate
View Security and Access Privileges Individual access privileges to graphical objects in a View application can be implemented by adding users to the View target and assigning each user an appropriate
Access Control CSC WAKE FOREST. U N I V E R S I T Y Department of Computer Science. Fall 2014
 Access Control CSC 348 648 WAKE FOREST U N I V E R S I T Y Department of Computer Science Fall 2014 Attempted Topics Describe language/models for talking about security systems ACM, Capabilities and ACLs
Access Control CSC 348 648 WAKE FOREST U N I V E R S I T Y Department of Computer Science Fall 2014 Attempted Topics Describe language/models for talking about security systems ACM, Capabilities and ACLs
Protection Kevin Webb Swarthmore College April 19, 2018
 Protection Kevin Webb Swarthmore College April 19, 2018 xkcd #1200 Before you say anything, no, I know not to leave my computer sitting out logged in to all my accounts. I have it set up so after a few
Protection Kevin Webb Swarthmore College April 19, 2018 xkcd #1200 Before you say anything, no, I know not to leave my computer sitting out logged in to all my accounts. I have it set up so after a few
Named ACL Support for Noncontiguous Ports on an Access Control Entry
 Named ACL Support for Noncontiguous Ports on an Access Control Entry The Named ACL Support for Noncontiguous Ports on an Access Control Entry feature allows you to specify noncontiguous ports in a single
Named ACL Support for Noncontiguous Ports on an Access Control Entry The Named ACL Support for Noncontiguous Ports on an Access Control Entry feature allows you to specify noncontiguous ports in a single
Community Edition Getting Started Guide. July 25, 2018
 Community Edition Getting Started Guide July 25, 2018 Copyright 2018 by Qualys, Inc. All Rights Reserved. Qualys and the Qualys logo are registered trademarks of Qualys, Inc. All other trademarks are the
Community Edition Getting Started Guide July 25, 2018 Copyright 2018 by Qualys, Inc. All Rights Reserved. Qualys and the Qualys logo are registered trademarks of Qualys, Inc. All other trademarks are the
irods 4.0.0rc1 - Manual Author: Renaissance Computing Institute (RENCI) Version: 4.0.0rc1 Date: page 1
 Author: Renaissance Computing Institute (RENCI) Version: 4.0.0rc1 Date: 2014-03-08 page 1 Table of Contents 1 Release Notes 5 2 License 5 3 Overview 6 4 Download 6 4.1 Binaries 6 4.2 Open Source 6 5 Installation
Author: Renaissance Computing Institute (RENCI) Version: 4.0.0rc1 Date: 2014-03-08 page 1 Table of Contents 1 Release Notes 5 2 License 5 3 Overview 6 4 Download 6 4.1 Binaries 6 4.2 Open Source 6 5 Installation
Developer Cockpit. Introduction 1. Prerequisites 2. Application Lifecycle in MindSphere 3. User interfaces "Developer Cockpit" 4
 Introduction 1 Prerequisites 2 Application Lifecycle in MindSphere 3 System Manual User interfaces "Developer Cockpit" 4 User rights in "Developer Cockpit" 5 Workflow of Developer Cockpit 6 Develop applications
Introduction 1 Prerequisites 2 Application Lifecycle in MindSphere 3 System Manual User interfaces "Developer Cockpit" 4 User rights in "Developer Cockpit" 5 Workflow of Developer Cockpit 6 Develop applications
Cisco CCNA ACL Part II
 Cisco CCNA ACL Part II Cisco CCNA Access List Applications This slide illustrates common uses for IP access lists. While this chapter focuses on IP access lists, the concept of access lists as mechanisms
Cisco CCNA ACL Part II Cisco CCNA Access List Applications This slide illustrates common uses for IP access lists. While this chapter focuses on IP access lists, the concept of access lists as mechanisms
Mastering phpmyadmiri 3.4 for
 Mastering phpmyadmiri 3.4 for Effective MySQL Management A complete guide to getting started with phpmyadmin 3.4 and mastering its features Marc Delisle [ t]open so 1 I community experience c PUBLISHING
Mastering phpmyadmiri 3.4 for Effective MySQL Management A complete guide to getting started with phpmyadmin 3.4 and mastering its features Marc Delisle [ t]open so 1 I community experience c PUBLISHING
Installing Joomla
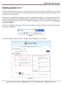 Installing Joomla 3.0.11 To start installing Joomla 3.X you have to copy the zipped file Joomla_3.0.1-Stable-Full_Package.zip to the folder in which you want to install Joomla 3.X. On a web host this is
Installing Joomla 3.0.11 To start installing Joomla 3.X you have to copy the zipped file Joomla_3.0.1-Stable-Full_Package.zip to the folder in which you want to install Joomla 3.X. On a web host this is
Contents Getting Started... 3 About Scribe Online and Connectors... 3 Scribe Online Services... 3 CDK Components... 3 Audience... 4 Prerequisites...
 Contents Getting Started... 3 About Scribe Online and Connectors... 3 Scribe Online Services... 3 CDK Components... 3 Audience... 4 Prerequisites... 4 Requirements... 4 CDK Workflow... 5 Scribe Online
Contents Getting Started... 3 About Scribe Online and Connectors... 3 Scribe Online Services... 3 CDK Components... 3 Audience... 4 Prerequisites... 4 Requirements... 4 CDK Workflow... 5 Scribe Online
IBM C IBM FileNet Content Manager V5.2, Specialist.
 IBM C2070-981 IBM FileNet Content Manager V5.2, Specialist http://killexams.com/exam-detail/c2070-981 QUESTION: 114 What P8 domain level entity allows specific meta data attributes to be identified that
IBM C2070-981 IBM FileNet Content Manager V5.2, Specialist http://killexams.com/exam-detail/c2070-981 QUESTION: 114 What P8 domain level entity allows specific meta data attributes to be identified that
Helix4Git Administrator Guide March 2018
 Helix4Git Administrator Guide 2018.1 March 2018 Copyright 2015-2018 Perforce Software All rights reserved. Perforce Software and documentation is available from www.perforce.com. You can download and use
Helix4Git Administrator Guide 2018.1 March 2018 Copyright 2015-2018 Perforce Software All rights reserved. Perforce Software and documentation is available from www.perforce.com. You can download and use
CounterACT 802.1X Plugin
 CounterACT 802.1X Plugin Version 4.2.0 Table of Contents Overview... 4 Understanding the 802.1X Protocol... 4 About the CounterACT 802.1X Plugin... 6 About This Document... 7 802.1X Plugin Components...
CounterACT 802.1X Plugin Version 4.2.0 Table of Contents Overview... 4 Understanding the 802.1X Protocol... 4 About the CounterACT 802.1X Plugin... 6 About This Document... 7 802.1X Plugin Components...
ADDING STAFF AS CONTACTS. DOCUMENT Here is a guide to Webdadi. WEBDADI Updated June 2015
 DOCUMENT Here is a guide to Webdadi WEBDADI Updated June 2015 ADDING STAFF AS CONTACTS How to add Internal staff and assign them their Webdadi User Rights ADDING INTERNAL STAFF IN WEBDADI: Adding staff
DOCUMENT Here is a guide to Webdadi WEBDADI Updated June 2015 ADDING STAFF AS CONTACTS How to add Internal staff and assign them their Webdadi User Rights ADDING INTERNAL STAFF IN WEBDADI: Adding staff
gateway address (ccn subsystem sip) gateway port (ccn subsystem sip) groupname
 G gateway address (ccn subsystem sip) gateway port (ccn subsystem sip) groupname 57 gateway address (ccn subsystem sip) G gateway address (ccn subsystem sip) To configure the IP address of the SIP proxy
G gateway address (ccn subsystem sip) gateway port (ccn subsystem sip) groupname 57 gateway address (ccn subsystem sip) G gateway address (ccn subsystem sip) To configure the IP address of the SIP proxy
PostgreSQL 7.3 Documentation Prev Chapter 2. Data Definition Next
 PostgreSQL 7.3 Documentation Prev Chapter 2. Data Definition Next 2.4. Constraints Data types are a way to limit the kind of data that can be stored in a table. For many applications, however, the constraint
PostgreSQL 7.3 Documentation Prev Chapter 2. Data Definition Next 2.4. Constraints Data types are a way to limit the kind of data that can be stored in a table. For many applications, however, the constraint
Computers Gone Rogue. Abusing Computer Accounts to Gain Control in an Active Directory Environment. Marina Simakov & Itai Grady
 Computers Gone Rogue Abusing Computer Accounts to Gain Control in an Active Directory Environment Marina Simakov & Itai Grady Motivation Credentials are a high value target for attackers No need for 0-day
Computers Gone Rogue Abusing Computer Accounts to Gain Control in an Active Directory Environment Marina Simakov & Itai Grady Motivation Credentials are a high value target for attackers No need for 0-day
Helix4Git Administrator Guide October 2017
 Helix4Git Administrator Guide 2017.2 October 2017 Copyright 2015-2018 Perforce Software All rights reserved. Perforce Software and documentation is available from www.perforce.com. You can download and
Helix4Git Administrator Guide 2017.2 October 2017 Copyright 2015-2018 Perforce Software All rights reserved. Perforce Software and documentation is available from www.perforce.com. You can download and
Design Document. Version 2.0 May 1, Texas Christian University, Computer Science Department
 Design Document Version 2.0 May 1, 2017 2016-2017 Texas Christian University, Computer Science Department i. Revision Signatures The following asserts that all team members have read the document and assert
Design Document Version 2.0 May 1, 2017 2016-2017 Texas Christian University, Computer Science Department i. Revision Signatures The following asserts that all team members have read the document and assert
Linux. Sirindhorn International Institute of Technology Thammasat University. Linux. Firewalls with iptables. Concepts. Examples
 Linux Sirindhorn International Institute of Technology Thammasat University Prepared by Steven Gordon on 14 October 2013 Common/Reports/-introduction.tex, r715 1/14 Contents 2/14 Linux, netfilter and netfilter:
Linux Sirindhorn International Institute of Technology Thammasat University Prepared by Steven Gordon on 14 October 2013 Common/Reports/-introduction.tex, r715 1/14 Contents 2/14 Linux, netfilter and netfilter:
upgrade-mp through xlate-bypass Commands
 CHAPTER 33 upgrade-mp To upgrade the maintenance partition software, use the upgrade-mp command. upgrade-mp {http[s]://[user:password@]server[:port]/pathname tftp[://server/pathname]} tftp http[s] server
CHAPTER 33 upgrade-mp To upgrade the maintenance partition software, use the upgrade-mp command. upgrade-mp {http[s]://[user:password@]server[:port]/pathname tftp[://server/pathname]} tftp http[s] server
