Broker. Matthias Vallentin UC Berkeley International Computer Science Institute (ICSI) BroCon '16
|
|
|
- Clifford Gordon
- 5 years ago
- Views:
Transcription
1 Broker Matthias Vallentin UC Berkeley International Computer Science Institute (ICSI) BroCon '16
2 Communication in Bro Exploiting Independent State For Network Intrusion Detection Tap Broccoli, Independent State Internet Manager Proxy... Proxy Abstract Firewall Frontend Nodes TU München... Tap Robin Sommer Backend Nodes Bro Internal Network Network intrusion detection systems (NIDSs) critically rely on processing a great deal of state. Often much of this state resides solely in the volatile processor memory accessible to a single user-level process on Cluster a single machine. In this work we highlight the power of independent state, i.e., internal fine-grained state that can be propagated from one Vern Paxson ICSI/LBNL vern@icir.org + + in the context of a single process is a minor subset of the NIDSPython process s full state: either higher-level results (often just alerts) sent between processes to facilitate correlation or aggregation, Bindings or log files written to disk for processing in the future. The much richer (and bulkier) internal state of the Broccoli NIDS remains exactly that, internal. It cannot be accessed by other processes unless a special means is provided for doing so, and it is permanently lost upon termination of the Ruby & Perl Bindings Broccoli Broker 0.4 Broker 1.0 coming soon! /17
3 Outline Overview API Performance Outlook
4 Overview
5 Broker = Bro'ish data model + publish/subscribe communication + distributed key-value stores
6 Publish/Subscribe Communication C++ Model C++ C++ Result File Internet Organization
7 Distributed Key-Value Stores M C C C M endpoint C C M master C clone
8 Broker's Data Model Arithmetic Time Network Container Other boolean interval address vector none count timestamp port set string integer subnet table real
9 API
10 Lessons Learned Functionality: It Just Works Props to Jon Siwek! Usability: no native type support, lots of "data wrapping" Semantics: no support for nonblocking processing
11 Current API using namespace broker; init(); endpoint ep{"sender"}; ep.peer(" ", 9999); ep.outgoing_connection_status().need_pop(); auto msg = message{ "my_event", "Hello C++ Broker!", 42u }; ep.send("bro/event", msg); ep.outgoing_connection_status().need_pop(); Initialize the Broker library. (Only one broker instance per process allowed.) Create a local endpoint. Block until connection status changes. When communicating with Bro, the first argument must be a string identifying the event name. The remaining values represent the event arguments. Publish the event under topic bro/event. Block until connection status changes.
12 New API using namespace broker; context ctx; A context encapsulates global state for a set of endpoints (e.g., worker threads, scheduler, etc.) auto ep = ctx.spawn<blocking>(); ep.peer(" ", 9999); Create a local endpoint with blocking API. auto v = vector{ "my_event", "Hello C++ Broker!", Create a vector of data. New semantics: a message is a topic plus data, not a sequence of data. }; 42u ep.publish("bro/event", v); Publish the event under topic bro/event.
13 Blocking vs. Non-Blocking API context ctx; auto ep = ctx.spawn<blocking>(); ep.subscribe("foo"); ep.subscribe("bar"); // Block and wait. auto msg = ep.receive(); cout << msg.topic() << " -> " << msg.data() << endl; // Equivalent semantics; functional API. ep.receive( [&](const topic& t, const data& d) { scout << t << " -> " << d << endl; } ) context ctx; auto ep = ctx.spawn<nonblocking>(); // Called asynchronously by the runtime. ep.subscribe( "foo", [=](const topic& t, const data& d) { cout << t << " -> " << d << endl; } ); // As above, just for a different topic. ep.subscribe( "bar", [=](const topic& t, const data& d) { cout << t << " -> " << d << endl; } );
14 Data Store APIs Available backends: 1. In-memory 2. SQLite C M C 3. RocksDB // Setup endpoint topology. context ctx; auto ep0 = ctx.spawn<blocking>(); auto ep1 = ctx.spawn<blocking>(); auto ep2 = ctx.spawn<blocking>(); ep0.peer(ep1); ep0.peer(ep2); // Attach stores. auto m = ep0.attach<master, memory>("lord"); auto c0 = ep1.attach<clone>("lord"); auto c1 = ep2.attach<clone>("lord"); // Write to the master directly. m->put("foo", 42); m->put("bar", "baz"); // After propagation, query the clones. sleep(propagation_delay); auto v0 = c0->get("key"); auto v1 = c1->get("key"); assert(v0 && v1 && *v0 == *v1);
15 Data Store APIs // Blocking API. Returns expected<data>. auto v = c->get<blocking>("key"); C M C // Non-blocking API. // Runtime invokes callback. c->get<nonblocking>("key").then( [=](data& d) { cout << "got it: " << d << endl; }, [=](error& e) { cerr << "uh, this went wrong: " << e << endl; } );
16 Performance
17 Simple Benchmark Throughput analysis Two endpoints: sender & receiver Message = conn.log entry System: MacBook Pro 16 GB RAM 4 x 2.8 GHz Core i7
18 Throughput 60K 40% Throughput (msg/sec) 40K 20K 0 new Version old
19 Outlook
20 Roadmap to Finish Python bindings 2. Implement Bro endpoint 3. Pattern matching in Bro 4. Flow control from function ipaddr import lookup(key: * string) : any; from broker import * when ( local x = lookup("key") ) ctx = { Context() source local = ctx.spawn(blocking) result = ""; sink = switch( ctx.spawn(blocking) x ) source.peer(sink) { case addr: sink.subscribe("foo", if ( x /8 ) result lambda = "contained"; t, d: print("%s: %s" % (t, d))) case string: source.publish("foo.baz", result = "error: lookup() failed: " + x; [1, 3.14, "qux", IPv4Address(' ')]) } }
21 Flow Control
22 Flow Control Intermediate buffer STILL OVERFLOWING
23 Flow Control Reject at the boundary
24 CAF: Messaging Building Block CAF = C++ Actor Framework Implementation of the Actor Model Light-weight, type-safe, scalable Network transparency
25 Bro Data Flows Master Events Workers Logs write(2) Packets
26 Questions? Docs: Chat: Code:
The NIDS Cluster: Scalable, Stateful Network Intrusion Detection on Commodity Hardware
 The NIDS Cluster: Scalable, Stateful Network Intrusion Detection on Commodity Hardware Matthias Vallentin 1, Robin Sommer 2,3, Jason Lee 2, Craig Leres 2 Vern Paxson 3,2, and Brian Tierney 2 1 TU München
The NIDS Cluster: Scalable, Stateful Network Intrusion Detection on Commodity Hardware Matthias Vallentin 1, Robin Sommer 2,3, Jason Lee 2, Craig Leres 2 Vern Paxson 3,2, and Brian Tierney 2 1 TU München
Enhancing Byte-Level Network Intrusion Detection Signatures with Context
 Enhancing Byte-Level Network Intrusion Detection Signatures with Context Robin Sommer sommer@in.tum.de Technische Universität München Germany Vern Paxson vern@icir.org International Computer Science Institute
Enhancing Byte-Level Network Intrusion Detection Signatures with Context Robin Sommer sommer@in.tum.de Technische Universität München Germany Vern Paxson vern@icir.org International Computer Science Institute
Inside Broker How Broker Leverages the C++ Actor Framework (CAF)
 Inside Broker How Broker Leverages the C++ Actor Framework (CAF) Dominik Charousset inet RG, Department of Computer Science Hamburg University of Applied Sciences Bro4Pros, February 2017 1 What was Broker
Inside Broker How Broker Leverages the C++ Actor Framework (CAF) Dominik Charousset inet RG, Department of Computer Science Hamburg University of Applied Sciences Bro4Pros, February 2017 1 What was Broker
Operational Experiences With High-Volume Network Intrusion Detection
 Operational Experiences With High-Volume Network Intrusion Detection Holger Dreger 1 Anja Feldmann 1 Vern Paxson 2 Robin Sommer 1 1 TU München Germany 2 ICSI / LBNL Berkeley, CA, USA ACM Computer and Communications
Operational Experiences With High-Volume Network Intrusion Detection Holger Dreger 1 Anja Feldmann 1 Vern Paxson 2 Robin Sommer 1 1 TU München Germany 2 ICSI / LBNL Berkeley, CA, USA ACM Computer and Communications
VAST. AUnifiedPlatformforInteractiveNetworkForensics. Matthias Vallentin 1,2 Vern Paxson 1,2 Robin Sommer 2,3. March 17, 2016 USENIX NSDI
 VAST AUnifiedPlatformforInteractiveNetworkForensics Matthias Vallentin 1,2 Vern Paxson 1,2 Robin Sommer 2,3 1 UC Berkeley 2 International Computer Science Institute (ICSI) 3 Lawrence Berkeley National
VAST AUnifiedPlatformforInteractiveNetworkForensics Matthias Vallentin 1,2 Vern Paxson 1,2 Robin Sommer 2,3 1 UC Berkeley 2 International Computer Science Institute (ICSI) 3 Lawrence Berkeley National
The Bro Cluster The Bro Cluster
 The Bro Cluster The Bro Cluster Intrusion Detection at 10 Gig and A High-Performance beyond using the NIDS Bro Architecture IDS for the Lawrence Berkeley National Lab Robin International Computer Science
The Bro Cluster The Bro Cluster Intrusion Detection at 10 Gig and A High-Performance beyond using the NIDS Bro Architecture IDS for the Lawrence Berkeley National Lab Robin International Computer Science
The Bro Network Security Monitor. Broadmap. Bro Workshop NCSA, Urbana-Champaign, IL. Bro Workshop 2011
 The Bro Network Security Monitor Broadmap NCSA, Urbana-Champaign, IL Outline Near- to Medium-term Roadmap Current Research Projects Workshop Wrap-Up 2 Version 2.0 Final 3 Version 2.0 Final Timeline: Early
The Bro Network Security Monitor Broadmap NCSA, Urbana-Champaign, IL Outline Near- to Medium-term Roadmap Current Research Projects Workshop Wrap-Up 2 Version 2.0 Final 3 Version 2.0 Final Timeline: Early
Exploiting Multi-Core Processors For Parallelizing Network Intrusion Prevention
 Exploiting Multi-Core Processors For Parallelizing Network Intrusion Prevention Robin Sommer International Computer Science Institute, & Lawrence Berkeley National Laboratory robin@icsi.berkeley.edu http://www.icir.org
Exploiting Multi-Core Processors For Parallelizing Network Intrusion Prevention Robin Sommer International Computer Science Institute, & Lawrence Berkeley National Laboratory robin@icsi.berkeley.edu http://www.icir.org
Distributed Cooperative Security Monitoring
 Distributed Cooperative Security Monitoring Robin Sommer Lawrence Berkeley National Laboratory rsommer@lbl.gov http://www.icir.org/robin Cooperative Security Monitoring Internet sites monitor their network
Distributed Cooperative Security Monitoring Robin Sommer Lawrence Berkeley National Laboratory rsommer@lbl.gov http://www.icir.org/robin Cooperative Security Monitoring Internet sites monitor their network
Bro-Osquery. Let Bro know about the hosts it monitors. Steffen Haas Department of Computer Science IT Security and Security Management (ISS)
 Steffen Haas Department of Computer Science IT Security and Security Management (ISS) Bro-Osquery Bro Network Monitor https://www.bro.org Let Bro know about the hosts it monitors Osquery Host Monitor https://osquery.io/
Steffen Haas Department of Computer Science IT Security and Security Management (ISS) Bro-Osquery Bro Network Monitor https://www.bro.org Let Bro know about the hosts it monitors Osquery Host Monitor https://osquery.io/
The Bro Network Intrusion Detection System
 The Bro Network Intrusion Detection System Robin Sommer Lawrence Berkeley National Laboratory rsommer@lbl.gov http://www.icir.org Outline Design of the Bro NIDS Philosophy Architecture LBNL s Bro Installation
The Bro Network Intrusion Detection System Robin Sommer Lawrence Berkeley National Laboratory rsommer@lbl.gov http://www.icir.org Outline Design of the Bro NIDS Philosophy Architecture LBNL s Bro Installation
C++ Actor Framework. Transparent Scaling from IoT to Datacenter Apps. Matthias Vallentin. UC Berkeley. RISElab seminar November 21, 2016
 C++ Actor Framework Transparent Scaling from IoT to Datacenter Apps Matthias Vallentin UC Berkeley RISElab seminar November 21, 2016 Heterogeneity More cores on desktops and mobile Complex accelerators/co-processors
C++ Actor Framework Transparent Scaling from IoT to Datacenter Apps Matthias Vallentin UC Berkeley RISElab seminar November 21, 2016 Heterogeneity More cores on desktops and mobile Complex accelerators/co-processors
HILTI: An Abstract Execution Environment for Deep, Stateful Network Traffic Analysis
 HILTI: An Abstract Execution Environment for Deep, Stateful Network Traffic Analysis Robin Sommer International Computer Science Institute, & Lawrence Berkeley National Laboratory robin@icsi.berkeley.edu
HILTI: An Abstract Execution Environment for Deep, Stateful Network Traffic Analysis Robin Sommer International Computer Science Institute, & Lawrence Berkeley National Laboratory robin@icsi.berkeley.edu
ECE 7650 Scalable and Secure Internet Services and Architecture ---- A Systems Perspective
 ECE 7650 Scalable and Secure Internet Services and Architecture ---- A Systems Perspective Part II: Data Center Software Architecture: Topic 3: Programming Models Piccolo: Building Fast, Distributed Programs
ECE 7650 Scalable and Secure Internet Services and Architecture ---- A Systems Perspective Part II: Data Center Software Architecture: Topic 3: Programming Models Piccolo: Building Fast, Distributed Programs
Execution Architecture
 Execution Architecture Software Architecture VO (706.706) Roman Kern Institute for Interactive Systems and Data Science, TU Graz 2018-11-07 Roman Kern (ISDS, TU Graz) Execution Architecture 2018-11-07
Execution Architecture Software Architecture VO (706.706) Roman Kern Institute for Interactive Systems and Data Science, TU Graz 2018-11-07 Roman Kern (ISDS, TU Graz) Execution Architecture 2018-11-07
BEAAquaLogic. Service Bus. Interoperability With EJB Transport
 BEAAquaLogic Service Bus Interoperability With EJB Transport Version 3.0 Revised: February 2008 Contents EJB Transport Introduction...........................................................1-1 Invoking
BEAAquaLogic Service Bus Interoperability With EJB Transport Version 3.0 Revised: February 2008 Contents EJB Transport Introduction...........................................................1-1 Invoking
Click to edit Master title style
 Click to edit Master title style SCALING NETWORK MONITORING IN A LARGE ENTERPRISE BroCon 2016 Austin, TX Click to edit Master Who title am style I? I work for Amazon s Worldwide Consumer Information Security
Click to edit Master title style SCALING NETWORK MONITORING IN A LARGE ENTERPRISE BroCon 2016 Austin, TX Click to edit Master Who title am style I? I work for Amazon s Worldwide Consumer Information Security
Building a Real-time Notification System
 Building a Real-time Notification System September 2015, Geneva Author: Jorge Vicente Cantero Supervisor: Jiri Kuncar CERN openlab Summer Student Report 2015 Project Specification Configurable Notification
Building a Real-time Notification System September 2015, Geneva Author: Jorge Vicente Cantero Supervisor: Jiri Kuncar CERN openlab Summer Student Report 2015 Project Specification Configurable Notification
Deep Dive Amazon Kinesis. Ian Meyers, Principal Solution Architect - Amazon Web Services
 Deep Dive Amazon Kinesis Ian Meyers, Principal Solution Architect - Amazon Web Services Analytics Deployment & Administration App Services Analytics Compute Storage Database Networking AWS Global Infrastructure
Deep Dive Amazon Kinesis Ian Meyers, Principal Solution Architect - Amazon Web Services Analytics Deployment & Administration App Services Analytics Compute Storage Database Networking AWS Global Infrastructure
Jaguar: Enabling Efficient Communication and I/O in Java
 Jaguar: Enabling Efficient Communication and I/O in Java Matt Welsh and David Culler UC Berkeley Presented by David Hovemeyer Outline ' Motivation ' How it works ' Code mappings ' External objects ' Pre
Jaguar: Enabling Efficient Communication and I/O in Java Matt Welsh and David Culler UC Berkeley Presented by David Hovemeyer Outline ' Motivation ' How it works ' Code mappings ' External objects ' Pre
Intrusion Detection Systems. Evan Misshula
 Intrusion Detection Systems Evan Misshula emisshula@qc.cuny.edu How old is hacking? In 1972, the US Air Force was worried about computer security problems. https://www.sans.org/reading-room/whitepapers/detection/historyevolution-intrusion-detection-344
Intrusion Detection Systems Evan Misshula emisshula@qc.cuny.edu How old is hacking? In 1972, the US Air Force was worried about computer security problems. https://www.sans.org/reading-room/whitepapers/detection/historyevolution-intrusion-detection-344
MOM MESSAGE ORIENTED MIDDLEWARE OVERVIEW OF MESSAGE ORIENTED MIDDLEWARE TECHNOLOGIES AND CONCEPTS. MOM Message Oriented Middleware
 MOM MESSAGE ORIENTED MOM Message Oriented Middleware MIDDLEWARE OVERVIEW OF MESSAGE ORIENTED MIDDLEWARE TECHNOLOGIES AND CONCEPTS Peter R. Egli 1/25 Contents 1. Synchronous versus asynchronous interaction
MOM MESSAGE ORIENTED MOM Message Oriented Middleware MIDDLEWARE OVERVIEW OF MESSAGE ORIENTED MIDDLEWARE TECHNOLOGIES AND CONCEPTS Peter R. Egli 1/25 Contents 1. Synchronous versus asynchronous interaction
MSG: An Overview of a Messaging System for the Grid
 MSG: An Overview of a Messaging System for the Grid Daniel Rodrigues Presentation Summary Current Issues Messaging System Testing Test Summary Throughput Message Lag Flow Control Next Steps Current Issues
MSG: An Overview of a Messaging System for the Grid Daniel Rodrigues Presentation Summary Current Issues Messaging System Testing Test Summary Throughput Message Lag Flow Control Next Steps Current Issues
WebSphere MQ Low Latency Messaging V2.1. High Throughput and Low Latency to Maximize Business Responsiveness IBM Corporation
 WebSphere MQ Low Latency Messaging V2.1 High Throughput and Low Latency to Maximize Business Responsiveness 2008 IBM Corporation WebSphere MQ Low Latency Messaging Extends the WebSphere MQ messaging family
WebSphere MQ Low Latency Messaging V2.1 High Throughput and Low Latency to Maximize Business Responsiveness 2008 IBM Corporation WebSphere MQ Low Latency Messaging Extends the WebSphere MQ messaging family
1 Copyright 2011, Oracle and/or its affiliates. All rights reserved. Insert Information Protection Policy Classification from Slide 8
 1 Copyright 2011, Oracle and/or its affiliates. All rights reserved. Insert Information Protection Policy Classification from Slide 8 ADVANCED MYSQL REPLICATION ARCHITECTURES Luís
1 Copyright 2011, Oracle and/or its affiliates. All rights reserved. Insert Information Protection Policy Classification from Slide 8 ADVANCED MYSQL REPLICATION ARCHITECTURES Luís
JiST: Java in Simulation Time
 JiST: Java in Simulation Time Transparent Parallel and Optimistic Execution of Discrete Event Simulations (PDES) of Mobile Ad hoc Networks (MANETs) Rimon Barr barr@cs.cornell.edu Wireless Network Lab Cornell
JiST: Java in Simulation Time Transparent Parallel and Optimistic Execution of Discrete Event Simulations (PDES) of Mobile Ad hoc Networks (MANETs) Rimon Barr barr@cs.cornell.edu Wireless Network Lab Cornell
Software Architecture Patterns
 Software Architecture Patterns *based on a tutorial of Michael Stal Harald Gall University of Zurich http://seal.ifi.uzh.ch/ase www.infosys.tuwien.ac.at Overview Goal Basic architectural understanding
Software Architecture Patterns *based on a tutorial of Michael Stal Harald Gall University of Zurich http://seal.ifi.uzh.ch/ase www.infosys.tuwien.ac.at Overview Goal Basic architectural understanding
icast / TRUST Collaboration Year 2 - Kickoff Meeting
 icast / TRUST Collaboration Year 2 - Kickoff Meeting Robin Sommer International Computer Science Institute robin@icsi.berkeley.edu http://www.icir.org Projects Overview Project 1 NIDS Evasion Testing in
icast / TRUST Collaboration Year 2 - Kickoff Meeting Robin Sommer International Computer Science Institute robin@icsi.berkeley.edu http://www.icir.org Projects Overview Project 1 NIDS Evasion Testing in
What is DARMA? DARMA is a C++ abstraction layer for asynchronous many-task (AMT) runtimes.
 DARMA Janine C. Bennett, Jonathan Lifflander, David S. Hollman, Jeremiah Wilke, Hemanth Kolla, Aram Markosyan, Nicole Slattengren, Robert L. Clay (PM) PSAAP-WEST February 22, 2017 Sandia National Laboratories
DARMA Janine C. Bennett, Jonathan Lifflander, David S. Hollman, Jeremiah Wilke, Hemanth Kolla, Aram Markosyan, Nicole Slattengren, Robert L. Clay (PM) PSAAP-WEST February 22, 2017 Sandia National Laboratories
Network Security Today: Finding Complex Attacks at 100Gb/s
 : Finding Complex Attacks at 100Gb/s Robin Sommer International Computer Science Institute, & Lawrence Berkeley National Laboratory robin@icsi.berkeley.edu http://www.icir.org/robin The Old Days Border
: Finding Complex Attacks at 100Gb/s Robin Sommer International Computer Science Institute, & Lawrence Berkeley National Laboratory robin@icsi.berkeley.edu http://www.icir.org/robin The Old Days Border
Distributed Filesystem
 Distributed Filesystem 1 How do we get data to the workers? NAS Compute Nodes SAN 2 Distributing Code! Don t move data to workers move workers to the data! - Store data on the local disks of nodes in the
Distributed Filesystem 1 How do we get data to the workers? NAS Compute Nodes SAN 2 Distributing Code! Don t move data to workers move workers to the data! - Store data on the local disks of nodes in the
6. Pointers, Structs, and Arrays. March 14 & 15, 2011
 March 14 & 15, 2011 Einführung in die Programmierung Introduction to C/C++, Tobias Weinzierl page 1 of 47 Outline Recapitulation Pointers Dynamic Memory Allocation Structs Arrays Bubble Sort Strings Einführung
March 14 & 15, 2011 Einführung in die Programmierung Introduction to C/C++, Tobias Weinzierl page 1 of 47 Outline Recapitulation Pointers Dynamic Memory Allocation Structs Arrays Bubble Sort Strings Einführung
Broker Clusters. Cluster Models
 4 CHAPTER 4 Broker Clusters Cluster Models Message Queue supports the use of broker clusters: groups of brokers working together to provide message delivery services to clients. Clusters enable a Message
4 CHAPTER 4 Broker Clusters Cluster Models Message Queue supports the use of broker clusters: groups of brokers working together to provide message delivery services to clients. Clusters enable a Message
CHAPTER - 4 REMOTE COMMUNICATION
 CHAPTER - 4 REMOTE COMMUNICATION Topics Introduction to Remote Communication Remote Procedural Call Basics RPC Implementation RPC Communication Other RPC Issues Case Study: Sun RPC Remote invocation Basics
CHAPTER - 4 REMOTE COMMUNICATION Topics Introduction to Remote Communication Remote Procedural Call Basics RPC Implementation RPC Communication Other RPC Issues Case Study: Sun RPC Remote invocation Basics
The Intelligence Framework Update
 The Intelligence Framework Update Jan Grashöfer DECENTRALIZED SYSTEMS AND NETWORK SERVICES RESEARCH GROUP (DSN) INSTITUTE OF TELEMATICS, FACULTY OF INFORMATICS KIT The Research University in the Helmholtz
The Intelligence Framework Update Jan Grashöfer DECENTRALIZED SYSTEMS AND NETWORK SERVICES RESEARCH GROUP (DSN) INSTITUTE OF TELEMATICS, FACULTY OF INFORMATICS KIT The Research University in the Helmholtz
libcppa Now: High-Level Distributed Programming Without Sacrificing Performance
 libcppa Now: High-Level Distributed Programming Without Sacrificing Performance Matthias Vallentin matthias@bro.org University of California, Berkeley C ++ Now May 14, 2013 Outline 1. Example Application:
libcppa Now: High-Level Distributed Programming Without Sacrificing Performance Matthias Vallentin matthias@bro.org University of California, Berkeley C ++ Now May 14, 2013 Outline 1. Example Application:
Introduction to Protocols for Realtime Data Sharing. Deepti Nagarkar
 Introduction to Protocols for Realtime Data Sharing Deepti Nagarkar Real Time Systems What are Real time systems? Realtime systems are those which must process data and respond immediately to avoid failure
Introduction to Protocols for Realtime Data Sharing Deepti Nagarkar Real Time Systems What are Real time systems? Realtime systems are those which must process data and respond immediately to avoid failure
CAS 703 Software Design
 Dr. Ridha Khedri Department of Computing and Software, McMaster University Canada L8S 4L7, Hamilton, Ontario Acknowledgments: Material based on Software by Tao et al. (Chapters 9 and 10) (SOA) 1 Interaction
Dr. Ridha Khedri Department of Computing and Software, McMaster University Canada L8S 4L7, Hamilton, Ontario Acknowledgments: Material based on Software by Tao et al. (Chapters 9 and 10) (SOA) 1 Interaction
Achieving Scalability and High Availability for clustered Web Services using Apache Synapse. Ruwan Linton WSO2 Inc.
 Achieving Scalability and High Availability for clustered Web Services using Apache Synapse Ruwan Linton [ruwan@apache.org] WSO2 Inc. Contents Introduction Apache Synapse Web services clustering Scalability/Availability
Achieving Scalability and High Availability for clustered Web Services using Apache Synapse Ruwan Linton [ruwan@apache.org] WSO2 Inc. Contents Introduction Apache Synapse Web services clustering Scalability/Availability
What s New in MySQL 5.7 Geir Høydalsvik, Sr. Director, MySQL Engineering. Copyright 2015, Oracle and/or its affiliates. All rights reserved.
 What s New in MySQL 5.7 Geir Høydalsvik, Sr. Director, MySQL Engineering Safe Harbor Statement The following is intended to outline our general product direction. It is intended for information purposes
What s New in MySQL 5.7 Geir Høydalsvik, Sr. Director, MySQL Engineering Safe Harbor Statement The following is intended to outline our general product direction. It is intended for information purposes
Adaptive Cluster Computing using JavaSpaces
 Adaptive Cluster Computing using JavaSpaces Jyoti Batheja and Manish Parashar The Applied Software Systems Lab. ECE Department, Rutgers University Outline Background Introduction Related Work Summary of
Adaptive Cluster Computing using JavaSpaces Jyoti Batheja and Manish Parashar The Applied Software Systems Lab. ECE Department, Rutgers University Outline Background Introduction Related Work Summary of
Performance Best Practices Paper for IBM Tivoli Directory Integrator v6.1 and v6.1.1
 Performance Best Practices Paper for IBM Tivoli Directory Integrator v6.1 and v6.1.1 version 1.0 July, 2007 Table of Contents 1. Introduction...3 2. Best practices...3 2.1 Preparing the solution environment...3
Performance Best Practices Paper for IBM Tivoli Directory Integrator v6.1 and v6.1.1 version 1.0 July, 2007 Table of Contents 1. Introduction...3 2. Best practices...3 2.1 Preparing the solution environment...3
Heckaton. SQL Server's Memory Optimized OLTP Engine
 Heckaton SQL Server's Memory Optimized OLTP Engine Agenda Introduction to Hekaton Design Consideration High Level Architecture Storage and Indexing Query Processing Transaction Management Transaction Durability
Heckaton SQL Server's Memory Optimized OLTP Engine Agenda Introduction to Hekaton Design Consideration High Level Architecture Storage and Indexing Query Processing Transaction Management Transaction Durability
6. Pointers, Structs, and Arrays. 1. Juli 2011
 1. Juli 2011 Einführung in die Programmierung Introduction to C/C++, Tobias Weinzierl page 1 of 50 Outline Recapitulation Pointers Dynamic Memory Allocation Structs Arrays Bubble Sort Strings Einführung
1. Juli 2011 Einführung in die Programmierung Introduction to C/C++, Tobias Weinzierl page 1 of 50 Outline Recapitulation Pointers Dynamic Memory Allocation Structs Arrays Bubble Sort Strings Einführung
Prerequisites: The student should have programming experience in a high-level language. ITCourseware, LLC Page 1. Object-Oriented Programming in C#
 Microsoft s.net is a revolutionary advance in programming technology that greatly simplifies application development and is a good match for the emerging paradigm of Web-based services, as opposed to proprietary
Microsoft s.net is a revolutionary advance in programming technology that greatly simplifies application development and is a good match for the emerging paradigm of Web-based services, as opposed to proprietary
Fabric Interfaces Architecture. Sean Hefty - Intel Corporation
 Fabric Interfaces Architecture Sean Hefty - Intel Corporation Changes v2 Remove interface object Add open interface as base object Add SRQ object Add EQ group object www.openfabrics.org 2 Overview Object
Fabric Interfaces Architecture Sean Hefty - Intel Corporation Changes v2 Remove interface object Add open interface as base object Add SRQ object Add EQ group object www.openfabrics.org 2 Overview Object
IEMS 5780 / IERG 4080 Building and Deploying Scalable Machine Learning Services
 IEMS 5780 / IERG 4080 Building and Deploying Scalable Machine Learning Services Lecture 11 - Asynchronous Tasks and Message Queues Albert Au Yeung 22nd November, 2018 1 / 53 Asynchronous Tasks 2 / 53 Client
IEMS 5780 / IERG 4080 Building and Deploying Scalable Machine Learning Services Lecture 11 - Asynchronous Tasks and Message Queues Albert Au Yeung 22nd November, 2018 1 / 53 Asynchronous Tasks 2 / 53 Client
Harvard School of Engineering and Applied Sciences CS 152: Programming Languages
 Harvard School of Engineering and Applied Sciences CS 152: Programming Languages Lecture 24 Thursday, April 19, 2018 1 Error-propagating semantics For the last few weeks, we have been studying type systems.
Harvard School of Engineering and Applied Sciences CS 152: Programming Languages Lecture 24 Thursday, April 19, 2018 1 Error-propagating semantics For the last few weeks, we have been studying type systems.
Apache Flink Streaming Done Right. Till
 Apache Flink Streaming Done Right Till Rohrmann trohrmann@apache.org @stsffap What Is Apache Flink? Apache TLP since December 2014 Parallel streaming data flow runtime Low latency & high throughput Exactly
Apache Flink Streaming Done Right Till Rohrmann trohrmann@apache.org @stsffap What Is Apache Flink? Apache TLP since December 2014 Parallel streaming data flow runtime Low latency & high throughput Exactly
Alan Bateman Java Platform Group, Oracle November Copyright 2018, Oracle and/or its affiliates. All rights reserved.!1
 Alan Bateman Java Platform Group, Oracle November 2018 Copyright 2018, Oracle and/or its affiliates. All rights reserved.!1 Project Loom Continuations Fibers Tail-calls Copyright 2018, Oracle and/or its
Alan Bateman Java Platform Group, Oracle November 2018 Copyright 2018, Oracle and/or its affiliates. All rights reserved.!1 Project Loom Continuations Fibers Tail-calls Copyright 2018, Oracle and/or its
Streaming Analytics with Apache Flink. Stephan
 Streaming Analytics with Apache Flink Stephan Ewen @stephanewen Apache Flink Stack Libraries DataStream API Stream Processing DataSet API Batch Processing Runtime Distributed Streaming Data Flow Streaming
Streaming Analytics with Apache Flink Stephan Ewen @stephanewen Apache Flink Stack Libraries DataStream API Stream Processing DataSet API Batch Processing Runtime Distributed Streaming Data Flow Streaming
Blink: 3D Display Multiplexing for Virtualized Applications
 : 3D Display Multiplexing for Virtualized Applications January 20, 2006 : 3D Display Multiplexing for Virtualized Applications Motivation Sprites and Tiles Lessons Learned GL in, GL out Communication Protocol
: 3D Display Multiplexing for Virtualized Applications January 20, 2006 : 3D Display Multiplexing for Virtualized Applications Motivation Sprites and Tiles Lessons Learned GL in, GL out Communication Protocol
What will happen if we try to compile, link and run this program? Do you have any comments to the code?
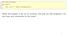 1 # include < iostream > 2 3 int main () 4 { 5 std :: cout
1 # include < iostream > 2 3 int main () 4 { 5 std :: cout
Executive Summary. It is important for a Java Programmer to understand the power and limitations of concurrent programming in Java using threads.
 Executive Summary. It is important for a Java Programmer to understand the power and limitations of concurrent programming in Java using threads. Poor co-ordination that exists in threads on JVM is bottleneck
Executive Summary. It is important for a Java Programmer to understand the power and limitations of concurrent programming in Java using threads. Poor co-ordination that exists in threads on JVM is bottleneck
ECE 7650 Scalable and Secure Internet Services and Architecture ---- A Systems Perspective
 ECE 7650 Scalable and Secure Internet Services and Architecture ---- A Systems Perspective Part II: Data Center Software Architecture: Topic 3: Programming Models CIEL: A Universal Execution Engine for
ECE 7650 Scalable and Secure Internet Services and Architecture ---- A Systems Perspective Part II: Data Center Software Architecture: Topic 3: Programming Models CIEL: A Universal Execution Engine for
Real World Web Scalability. Ask Bjørn Hansen Develooper LLC
 Real World Web Scalability Ask Bjørn Hansen Develooper LLC Hello. 28 brilliant methods to make your website keep working past $goal requests/transactions/sales per second/hour/day Requiring minimal extra
Real World Web Scalability Ask Bjørn Hansen Develooper LLC Hello. 28 brilliant methods to make your website keep working past $goal requests/transactions/sales per second/hour/day Requiring minimal extra
DCCP (Datagram Congestion Control Protocol)
 DCCP (Datagram Congestion Control Protocol) Keith Briggs Keith.Briggs@bt.com research.btexact.com/teralab/keithbriggs.html CRG meeting 2003 Nov 21 (should have been 17) 15:00 typeset 2003 November 21 10:04
DCCP (Datagram Congestion Control Protocol) Keith Briggs Keith.Briggs@bt.com research.btexact.com/teralab/keithbriggs.html CRG meeting 2003 Nov 21 (should have been 17) 15:00 typeset 2003 November 21 10:04
OPENSHMEM AND OFI: BETTER TOGETHER
 4th ANNUAL WORKSHOP 208 OPENSHMEM AND OFI: BETTER TOGETHER James Dinan, David Ozog, and Kayla Seager Intel Corporation [ April, 208 ] NOTICES AND DISCLAIMERS Intel technologies features and benefits depend
4th ANNUAL WORKSHOP 208 OPENSHMEM AND OFI: BETTER TOGETHER James Dinan, David Ozog, and Kayla Seager Intel Corporation [ April, 208 ] NOTICES AND DISCLAIMERS Intel technologies features and benefits depend
NOX, POX, and lessons learned. James Murphy McCauley
 NOX, POX, and lessons learned James Murphy McCauley Organization A Bit of History Lessons Learned Part 1: Two little lessons Part 2: Thinking big Ongoing Work Wrap-Up 2 Current NOX and POX Collaborators
NOX, POX, and lessons learned James Murphy McCauley Organization A Bit of History Lessons Learned Part 1: Two little lessons Part 2: Thinking big Ongoing Work Wrap-Up 2 Current NOX and POX Collaborators
Lecture 2: January 24
 CMPSCI 677 Operating Systems Spring 2017 Lecture 2: January 24 Lecturer: Prashant Shenoy Scribe: Phuthipong Bovornkeeratiroj 2.1 Lecture 2 Distributed systems fall into one of the architectures teaching
CMPSCI 677 Operating Systems Spring 2017 Lecture 2: January 24 Lecturer: Prashant Shenoy Scribe: Phuthipong Bovornkeeratiroj 2.1 Lecture 2 Distributed systems fall into one of the architectures teaching
CSE 307: Principles of Programming Languages
 1 / 26 CSE 307: Principles of Programming Languages Names, Scopes, and Bindings R. Sekar 2 / 26 Topics Bindings 1. Bindings Bindings: Names and Attributes Names are a fundamental abstraction in languages
1 / 26 CSE 307: Principles of Programming Languages Names, Scopes, and Bindings R. Sekar 2 / 26 Topics Bindings 1. Bindings Bindings: Names and Attributes Names are a fundamental abstraction in languages
Bigtable. A Distributed Storage System for Structured Data. Presenter: Yunming Zhang Conglong Li. Saturday, September 21, 13
 Bigtable A Distributed Storage System for Structured Data Presenter: Yunming Zhang Conglong Li References SOCC 2010 Key Note Slides Jeff Dean Google Introduction to Distributed Computing, Winter 2008 University
Bigtable A Distributed Storage System for Structured Data Presenter: Yunming Zhang Conglong Li References SOCC 2010 Key Note Slides Jeff Dean Google Introduction to Distributed Computing, Winter 2008 University
A First Look at Modern Enterprise Traffic
 A First Look at Modern Enterprise Traffic Ruoming Pang, Princeton University Mark Allman (ICSI), Mike Bennett (LBNL), Jason Lee (LBNL), Vern Paxson (ICSI/LBNL), and Brian Tierney (LBNL) The Question What
A First Look at Modern Enterprise Traffic Ruoming Pang, Princeton University Mark Allman (ICSI), Mike Bennett (LBNL), Jason Lee (LBNL), Vern Paxson (ICSI/LBNL), and Brian Tierney (LBNL) The Question What
Seeking Visibility Into Network Activity for Security Analysis
 Seeking Visibility Into Network Activity for Security Analysis Robin Sommer Lawrence Berkeley National Laboratory & International Computer Science Institute robin@icsi.berkeley.org http://www.icir.org
Seeking Visibility Into Network Activity for Security Analysis Robin Sommer Lawrence Berkeley National Laboratory & International Computer Science Institute robin@icsi.berkeley.org http://www.icir.org
10266 Programming in C Sharp with Microsoft Visual Studio 2010
 10266 Programming in C Sharp with Microsoft Visual Studio 2010 Course Number: 10266A Category: Visual Studio 2010 Duration: 5 days Course Description The course focuses on C# program structure, language
10266 Programming in C Sharp with Microsoft Visual Studio 2010 Course Number: 10266A Category: Visual Studio 2010 Duration: 5 days Course Description The course focuses on C# program structure, language
Using the SDACK Architecture to Build a Big Data Product. Yu-hsin Yeh (Evans Ye) Apache Big Data NA 2016 Vancouver
 Using the SDACK Architecture to Build a Big Data Product Yu-hsin Yeh (Evans Ye) Apache Big Data NA 2016 Vancouver Outline A Threat Analytic Big Data product The SDACK Architecture Akka Streams and data
Using the SDACK Architecture to Build a Big Data Product Yu-hsin Yeh (Evans Ye) Apache Big Data NA 2016 Vancouver Outline A Threat Analytic Big Data product The SDACK Architecture Akka Streams and data
GFS: The Google File System
 GFS: The Google File System Brad Karp UCL Computer Science CS GZ03 / M030 24 th October 2014 Motivating Application: Google Crawl the whole web Store it all on one big disk Process users searches on one
GFS: The Google File System Brad Karp UCL Computer Science CS GZ03 / M030 24 th October 2014 Motivating Application: Google Crawl the whole web Store it all on one big disk Process users searches on one
"Charting the Course... MOC Programming in C# with Microsoft Visual Studio Course Summary
 Course Summary NOTE - The course delivery has been updated to Visual Studio 2013 and.net Framework 4.5! Description The course focuses on C# program structure, language syntax, and implementation details
Course Summary NOTE - The course delivery has been updated to Visual Studio 2013 and.net Framework 4.5! Description The course focuses on C# program structure, language syntax, and implementation details
Atrium Webinar- What's new in ADDM Version 10
 Atrium Webinar- What's new in ADDM Version 10 This document provides question and answers discussed during following webinar session: Atrium Webinar- What's new in ADDM Version 10 on May 8th, 2014 Q: Hi,
Atrium Webinar- What's new in ADDM Version 10 This document provides question and answers discussed during following webinar session: Atrium Webinar- What's new in ADDM Version 10 on May 8th, 2014 Q: Hi,
A BIG DATA STREAMING RECIPE WHAT TO CONSIDER WHEN BUILDING A REAL TIME BIG DATA APPLICATION
 A BIG DATA STREAMING RECIPE WHAT TO CONSIDER WHEN BUILDING A REAL TIME BIG DATA APPLICATION Konstantin Gregor / konstantin.gregor@tngtech.com ABOUT ME So ware developer for TNG in Munich Client in telecommunication
A BIG DATA STREAMING RECIPE WHAT TO CONSIDER WHEN BUILDING A REAL TIME BIG DATA APPLICATION Konstantin Gregor / konstantin.gregor@tngtech.com ABOUT ME So ware developer for TNG in Munich Client in telecommunication
MATRIX:DJLSYS EXPLORING RESOURCE ALLOCATION TECHNIQUES FOR DISTRIBUTED JOB LAUNCH UNDER HIGH SYSTEM UTILIZATION
 MATRIX:DJLSYS EXPLORING RESOURCE ALLOCATION TECHNIQUES FOR DISTRIBUTED JOB LAUNCH UNDER HIGH SYSTEM UTILIZATION XIAOBING ZHOU(xzhou40@hawk.iit.edu) HAO CHEN (hchen71@hawk.iit.edu) Contents Introduction
MATRIX:DJLSYS EXPLORING RESOURCE ALLOCATION TECHNIQUES FOR DISTRIBUTED JOB LAUNCH UNDER HIGH SYSTEM UTILIZATION XIAOBING ZHOU(xzhou40@hawk.iit.edu) HAO CHEN (hchen71@hawk.iit.edu) Contents Introduction
Understanding StoRM: from introduction to internals
 Understanding StoRM: from introduction to internals 13 November 2007 Outline Storage Resource Manager The StoRM service StoRM components and internals Deployment configuration Authorization and ACLs Conclusions.
Understanding StoRM: from introduction to internals 13 November 2007 Outline Storage Resource Manager The StoRM service StoRM components and internals Deployment configuration Authorization and ACLs Conclusions.
NAME: STUDENT ID: MIDTERM 235 POINTS. Closed book, closed notes 70 minutes
 NAME: STUDENT ID: MIDTERM 235 POINTS Closed book, closed notes 70 minutes 1. Name three types of failures in a distributed system. (15 points) 5 points for each correctly names failure type Valid answers
NAME: STUDENT ID: MIDTERM 235 POINTS Closed book, closed notes 70 minutes 1. Name three types of failures in a distributed system. (15 points) 5 points for each correctly names failure type Valid answers
Instant Integration into the AMQP Cloud with Apache Qpid Messenger. Rafael Schloming Principle Software Red Hat
 Instant Integration into the AMQP Cloud with Apache Qpid Messenger Rafael Schloming Principle Software Engineer @ Red Hat rhs@apache.org Overview Introduction Messaging AMQP Proton Demo Summary Introduction
Instant Integration into the AMQP Cloud with Apache Qpid Messenger Rafael Schloming Principle Software Engineer @ Red Hat rhs@apache.org Overview Introduction Messaging AMQP Proton Demo Summary Introduction
LAPI on HPS Evaluating Federation
 LAPI on HPS Evaluating Federation Adrian Jackson August 23, 2004 Abstract LAPI is an IBM-specific communication library that performs single-sided operation. This library was well profiled on Phase 1 of
LAPI on HPS Evaluating Federation Adrian Jackson August 23, 2004 Abstract LAPI is an IBM-specific communication library that performs single-sided operation. This library was well profiled on Phase 1 of
Tag a Tiny Aggregation Service for Ad-Hoc Sensor Networks. Samuel Madden, Michael Franklin, Joseph Hellerstein,Wei Hong UC Berkeley Usinex OSDI 02
 Tag a Tiny Aggregation Service for Ad-Hoc Sensor Networks Samuel Madden, Michael Franklin, Joseph Hellerstein,Wei Hong UC Berkeley Usinex OSDI 02 Outline Introduction The Tiny AGgregation Approach Aggregate
Tag a Tiny Aggregation Service for Ad-Hoc Sensor Networks Samuel Madden, Michael Franklin, Joseph Hellerstein,Wei Hong UC Berkeley Usinex OSDI 02 Outline Introduction The Tiny AGgregation Approach Aggregate
Communication. Distributed Systems Santa Clara University 2016
 Communication Distributed Systems Santa Clara University 2016 Protocol Stack Each layer has its own protocol Can make changes at one layer without changing layers above or below Use well defined interfaces
Communication Distributed Systems Santa Clara University 2016 Protocol Stack Each layer has its own protocol Can make changes at one layer without changing layers above or below Use well defined interfaces
GUI in C++ PV264 Advanced Programming in C++ Nikola Beneš Jan Mrázek Vladimír Štill. Faculty of Informatics, Masaryk University.
 GUI in C++ PV264 Advanced Programming in C++ Nikola Beneš Jan Mrázek Vladimír Štill Faculty of Informatics, Masaryk University Spring 2017 PV264: GUI in C++ Spring 2017 1 / 23 Organisation Lectures this
GUI in C++ PV264 Advanced Programming in C++ Nikola Beneš Jan Mrázek Vladimír Štill Faculty of Informatics, Masaryk University Spring 2017 PV264: GUI in C++ Spring 2017 1 / 23 Organisation Lectures this
Ingo Brenckmann Jochen Kirsten Storage Technology Strategists SAS EMEA Copyright 2003, SAS Institute Inc. All rights reserved.
 Intelligent Storage Results from real life testing Ingo Brenckmann Jochen Kirsten Storage Technology Strategists SAS EMEA SAS Intelligent Storage components! OLAP Server! Scalable Performance Data Server!
Intelligent Storage Results from real life testing Ingo Brenckmann Jochen Kirsten Storage Technology Strategists SAS EMEA SAS Intelligent Storage components! OLAP Server! Scalable Performance Data Server!
OPENSTACK: THE OPEN CLOUD
 OPENSTACK: THE OPEN CLOUD Anuj Sehgal (s.anuj@jacobs-university.de) AIMS 2012 Labs 04 June 2012 1 Outline What is the cloud? Background Architecture OpenStack Nova OpenStack Glance 2 What is the Cloud?
OPENSTACK: THE OPEN CLOUD Anuj Sehgal (s.anuj@jacobs-university.de) AIMS 2012 Labs 04 June 2012 1 Outline What is the cloud? Background Architecture OpenStack Nova OpenStack Glance 2 What is the Cloud?
Authors: Rostislav Pinski, Dmitry Kaganov, Eli Shtein, Alexander Gorohovski. Version 1.1. Preventing Data Leakage via
 Ben Gurion University Deutsche Telekom Labs Authors: Rostislav Pinski, Dmitry Kaganov, Eli Shtein, Alexander Gorohovski Version 1.1 1 1. Introduction...4-16 1.1 Vision...4 1.2 The Problem Domain...5-6
Ben Gurion University Deutsche Telekom Labs Authors: Rostislav Pinski, Dmitry Kaganov, Eli Shtein, Alexander Gorohovski Version 1.1 1 1. Introduction...4-16 1.1 Vision...4 1.2 The Problem Domain...5-6
Distributed Systems Exam 1 Review Paul Krzyzanowski. Rutgers University. Fall 2016
 Distributed Systems 2015 Exam 1 Review Paul Krzyzanowski Rutgers University Fall 2016 1 Question 1 Why did the use of reference counting for remote objects prove to be impractical? Explain. It s not fault
Distributed Systems 2015 Exam 1 Review Paul Krzyzanowski Rutgers University Fall 2016 1 Question 1 Why did the use of reference counting for remote objects prove to be impractical? Explain. It s not fault
Hibernate Search Googling your persistence domain model. Emmanuel Bernard Doer JBoss, a division of Red Hat
 Hibernate Search Googling your persistence domain model Emmanuel Bernard Doer JBoss, a division of Red Hat Search: left over of today s applications Add search dimension to the domain model Frankly, search
Hibernate Search Googling your persistence domain model Emmanuel Bernard Doer JBoss, a division of Red Hat Search: left over of today s applications Add search dimension to the domain model Frankly, search
W b b 2.0. = = Data Ex E pl p o l s o io i n
 Hypertable Doug Judd Zvents, Inc. Background Web 2.0 = Data Explosion Web 2.0 Mt. Web 2.0 Traditional Tools Don t Scale Well Designed for a single machine Typical scaling solutions ad-hoc manual/static
Hypertable Doug Judd Zvents, Inc. Background Web 2.0 = Data Explosion Web 2.0 Mt. Web 2.0 Traditional Tools Don t Scale Well Designed for a single machine Typical scaling solutions ad-hoc manual/static
Outline. Java Models for variables Types and type checking, type safety Interpretation vs. compilation. Reasoning about code. CSCI 2600 Spring
 Java Outline Java Models for variables Types and type checking, type safety Interpretation vs. compilation Reasoning about code CSCI 2600 Spring 2017 2 Java Java is a successor to a number of languages,
Java Outline Java Models for variables Types and type checking, type safety Interpretation vs. compilation Reasoning about code CSCI 2600 Spring 2017 2 Java Java is a successor to a number of languages,
MapReduce. U of Toronto, 2014
 MapReduce U of Toronto, 2014 http://www.google.org/flutrends/ca/ (2012) Average Searches Per Day: 5,134,000,000 2 Motivation Process lots of data Google processed about 24 petabytes of data per day in
MapReduce U of Toronto, 2014 http://www.google.org/flutrends/ca/ (2012) Average Searches Per Day: 5,134,000,000 2 Motivation Process lots of data Google processed about 24 petabytes of data per day in
Lightweight RPC. Robert Grimm New York University
 Lightweight RPC Robert Grimm New York University The Three Questions What is the problem? What is new or different? What are the contributions and limitations? The Structure of Systems Monolithic kernels
Lightweight RPC Robert Grimm New York University The Three Questions What is the problem? What is new or different? What are the contributions and limitations? The Structure of Systems Monolithic kernels
Resilient Distributed Datasets
 Resilient Distributed Datasets A Fault- Tolerant Abstraction for In- Memory Cluster Computing Matei Zaharia, Mosharaf Chowdhury, Tathagata Das, Ankur Dave, Justin Ma, Murphy McCauley, Michael Franklin,
Resilient Distributed Datasets A Fault- Tolerant Abstraction for In- Memory Cluster Computing Matei Zaharia, Mosharaf Chowdhury, Tathagata Das, Ankur Dave, Justin Ma, Murphy McCauley, Michael Franklin,
Principles of Programming Languages
 Principles of Programming Languages h"p://www.di.unipi.it/~andrea/dida2ca/plp-16/ Prof. Andrea Corradini Department of Computer Science, Pisa Control Flow Iterators Recursion Con>nua>ons Lesson 25! 1 Iterators
Principles of Programming Languages h"p://www.di.unipi.it/~andrea/dida2ca/plp-16/ Prof. Andrea Corradini Department of Computer Science, Pisa Control Flow Iterators Recursion Con>nua>ons Lesson 25! 1 Iterators
Streaming data Model is opposite Queries are usually fixed and data are flows through the system.
 1 2 3 Main difference is: Static Data Model (For related database or Hadoop) Data is stored, and we just send some query. Streaming data Model is opposite Queries are usually fixed and data are flows through
1 2 3 Main difference is: Static Data Model (For related database or Hadoop) Data is stored, and we just send some query. Streaming data Model is opposite Queries are usually fixed and data are flows through
Microsoft Visual C# Step by Step. John Sharp
 Microsoft Visual C# 2013 Step by Step John Sharp Introduction xix PART I INTRODUCING MICROSOFT VISUAL C# AND MICROSOFT VISUAL STUDIO 2013 Chapter 1 Welcome to C# 3 Beginning programming with the Visual
Microsoft Visual C# 2013 Step by Step John Sharp Introduction xix PART I INTRODUCING MICROSOFT VISUAL C# AND MICROSOFT VISUAL STUDIO 2013 Chapter 1 Welcome to C# 3 Beginning programming with the Visual
Programming in C# with Microsoft Visual Studio 2010
 Programming in C# with Microsoft Visual Studio 2010 Course 10266; 5 Days, Instructor-led Course Description: The course focuses on C# program structure, language syntax, and implementation details with.net
Programming in C# with Microsoft Visual Studio 2010 Course 10266; 5 Days, Instructor-led Course Description: The course focuses on C# program structure, language syntax, and implementation details with.net
Artix Version Session Manager Guide: C++
 Artix Version 5.6.4 Session Manager Guide: C++ Micro Focus The Lawn 22-30 Old Bath Road Newbury, Berkshire RG14 1QN UK http://www.microfocus.com Copyright Micro Focus 2017. All rights reserved. MICRO FOCUS,
Artix Version 5.6.4 Session Manager Guide: C++ Micro Focus The Lawn 22-30 Old Bath Road Newbury, Berkshire RG14 1QN UK http://www.microfocus.com Copyright Micro Focus 2017. All rights reserved. MICRO FOCUS,
Transformation-free Data Pipelines by combining the Power of Apache Kafka and the Flexibility of the ESB's
 Building Agile and Resilient Schema Transformations using Apache Kafka and ESB's Transformation-free Data Pipelines by combining the Power of Apache Kafka and the Flexibility of the ESB's Ricardo Ferreira
Building Agile and Resilient Schema Transformations using Apache Kafka and ESB's Transformation-free Data Pipelines by combining the Power of Apache Kafka and the Flexibility of the ESB's Ricardo Ferreira
Achieving Horizontal Scalability. Alain Houf Sales Engineer
 Achieving Horizontal Scalability Alain Houf Sales Engineer Scale Matters InterSystems IRIS Database Platform lets you: Scale up and scale out Scale users and scale data Mix and match a variety of approaches
Achieving Horizontal Scalability Alain Houf Sales Engineer Scale Matters InterSystems IRIS Database Platform lets you: Scale up and scale out Scale users and scale data Mix and match a variety of approaches
Data-Centric Locality in Chapel
 Data-Centric Locality in Chapel Ben Harshbarger Cray Inc. CHIUW 2015 1 Safe Harbor Statement This presentation may contain forward-looking statements that are based on our current expectations. Forward
Data-Centric Locality in Chapel Ben Harshbarger Cray Inc. CHIUW 2015 1 Safe Harbor Statement This presentation may contain forward-looking statements that are based on our current expectations. Forward
CSI33 Data Structures
 Outline Department of Mathematics and Computer Science Bronx Community College October 24, 2018 Outline Outline 1 Chapter 8: A C++ Introduction For Python Programmers Expressions and Operator Precedence
Outline Department of Mathematics and Computer Science Bronx Community College October 24, 2018 Outline Outline 1 Chapter 8: A C++ Introduction For Python Programmers Expressions and Operator Precedence
Sphinx full-text search engine
 November 15, 2008 OpenSQL Camp Piotr Biel, Percona Inc Andrew Aksyonoff, Sphinx Technologies Peter Zaitsev, Percona Inc Full Text Search Full Text Search technique for searching words in indexed documents
November 15, 2008 OpenSQL Camp Piotr Biel, Percona Inc Andrew Aksyonoff, Sphinx Technologies Peter Zaitsev, Percona Inc Full Text Search Full Text Search technique for searching words in indexed documents
Chapter 22 Network Layer: Delivery, Forwarding, and Routing 22.1
 Chapter 22 Network Layer: Delivery, Forwarding, and Routing 22.1 Copyright The McGraw-Hill Companies, Inc. Permission required for reproduction or display. 22-3 UNICAST ROUTING PROTOCOLS 22.2 A routing
Chapter 22 Network Layer: Delivery, Forwarding, and Routing 22.1 Copyright The McGraw-Hill Companies, Inc. Permission required for reproduction or display. 22-3 UNICAST ROUTING PROTOCOLS 22.2 A routing
HA solution with PXC-5.7 with ProxySQL. Ramesh Sivaraman Krunal Bauskar
 HA solution with PXC-5.7 with ProxySQL Ramesh Sivaraman Krunal Bauskar Agenda What is Good HA eco-system? Understanding PXC-5.7 Understanding ProxySQL PXC + ProxySQL = Complete HA solution Monitoring using
HA solution with PXC-5.7 with ProxySQL Ramesh Sivaraman Krunal Bauskar Agenda What is Good HA eco-system? Understanding PXC-5.7 Understanding ProxySQL PXC + ProxySQL = Complete HA solution Monitoring using
