The mixed environment will have PCs from both environments. Usually this environment uses the Linux server as an SSH, DNS or mail server.
|
|
|
- Caren Merritt
- 5 years ago
- Views:
Transcription
1 Setting Up The Lab This document is provides the steps for setting up virtual machines for use with the Principles of Computer Security CompTIA Security+ and Beyond. There are a number of virtual platforms such as VMWare, Virtual PC, Xen, Parallels, and Virtual Box. The instructions for setting up the environment do not address steps specific to any single platform. The lab technician who prepares the machines for the lab exercises will need to be familiar with the particular brand of virtualization in their environment and configure it as appropriate. The lab exercises are written for both a Windows and Linux environment. There are several lab exercises in which both environments are required so it is recommended that you set up all 4 virtual machines. The lab environment required for each lab exercise is designated by the letter w, l, m or i in the title. The letter w is for a Windows environment, l is for the Linux environment, m is for a mixed environment, and i is for the host computer or any other computer that has internet access. So for example, Lab 3w would require the Windows environment and Lab 3l would require the Linux environment. Windows Setup the w labs The Windows environment consists of 2 PCs, one with Windows XP Professional and one with Windows 2003 Server. In general, the Windows XP PC will be the client/attacking machine and the Windows 2003 Server will be the server/target machine. Linux Setup the l labs The Linux environment consists of 2 PCs, one with BackTrack4 (client/attack) and the other with Metasploitable (server/target). In general, the BackTrack will be the attacking machine and the Metasploitable will be the target machine. Mixed Setup the m labs The mixed environment will have PCs from both environments. Usually this environment uses the Linux server as an SSH, DNS or mail server. Host Setup the i labs There are several lab exercises that require an Internet connection. These can be done from the PC that is hosting the Virtual Machines or they can be done from anypc that has Internet access. 1 of 18
2 Setting Up Windows XP SP1 Steps at a Glance To setup the your computer(s) for working with the lab manual you will have to Download and gather required software Setup the host machine and ensure minimum requirements Setup the virtual machine Install Windows XP SP1 Configure the Windows XP SP1 Add other software to the tools folder Download and Gather Required Software Before beginning the install, make sure you have all the necessary software to complete the setup. The following is a list of the software needed for the setup. If you are also setting up the other virtual machines, you may want to download the software for them as well at the same time. Refer to the later section for the other lists of software to download. These files are required for configuring the virtual machine: Windows XP SP1 Check with your IT Staff about getting the software and licenses WindowsXP-KB x86-ENU (IPv6 Patch) nmap-5.21-setup wireshark-win z465 Caine-Live Secondary_harddrive with Suspect_image.e01 These file go in the the Desktop/tools folder you will create later in the setup: Spynet Camoflague Service Pack 3 Snort 2_8_6_1 WinPcap WinPT Putty WinSCP 2 of 18
3 Setup Host Machine There are a number of different ways to deploy virtual machines. The following requirements are for a single host running software such as VMware Workstation, VMware Player, or Virtual PC. Minimum Requirements CPU 1.3 GHz or faster (Pentium Core or better recommended) RAM 2 Gig (4 Gig Recommended) HD Gig of free space Setup the Virtual Machine The virtual machine for the XP installation will need the following: 1. Use at least a 10 GB partition for the C Drive. 2. Create a second hard drive at least 100MB. (The file name suspect_image will go in this drive.) 3. The RAM should be set for at least 512 MB. 4. You will need to set up the networking for host only so that no traffic from the virtual environment can make it to the actual network. 5. You may also want to disable any file sharing or copying and pasting of files to and from the virtual machine. Some of the software on the virtual machines is considered malicious code and should not leave those machines. If you are unsure of how to do this, please refer to the support provided by the vender of your virtualization product. NOTE: You need XP SP1 for this install. XP SP1 has several vulnerabilities that are used to demonstrate the need for proper patching and updating. If you use a later distribution, some labs may not work. Install Windows XP Professional SP1 Mount the Windows XP SP 1 CD and begin the install. 1) On the Welcome to Setup screen, press Enter. 2) On the End User License Agreement screen, press F8. 3) On the Partition screen, accept the defaults by pressing Enter. 3 of 18
4 4) On the next screen, select Format the Partition Using the NTFS File System and press Enter. When the computer is done formatting, it will reboot and go into the GUI portion of the installation 5) On the Regional and Language Options screen, click Next. 6) On the Personalize Your Software screen, type Security Student in the Name box. 7) In the Organization box, type Computer Security and click Next. 8) On the Your Product Key screen, type your product key and click Next. 9) View the Computer Name and Administrative Password screen: a) In the Computer Name: box, type winxppro. a) In the Password box type, password. b) In the Confirm Password box type, password. c) Click Next. 10) On the Date and Time Settings screen, set the correct date and time and select the appropriate time zone. Click Next. 11) On the Network Settings screen, select Custom Settings and click Next. 12) On the Networking Components screen, select Internet Protocol (TCP/IP) and click Properties. 13) On the Internet Protocol (TCP/IP) Properties screen, select Use the Following IP Address. 14) In the IP Address box, type ) In the Subnet Mask box, type ) In the Default Gateway box, leave blank 17) In the Preferred DNS Server box, type ) Click Ok. 19) Click Next. 20) On the Workgroup or Domain screen, click Next. 4 of 18
5 a) The installation will complete and the computer will reboot. 21) On the Welcome to Microsoft Windows screen, click Next. 22) On the How Will This Computer Connect to the Internet? Screen, click Skip. 23) On the Ready to Activate Windows? screen select No, remind me every few days, and click Next. 24) View the Who Will Use This Computer? screen a) In the Your Name: box, type Admin b) In the 2 nd User: box, type labuser c) In the 3 rd User: box, type labuser2 d) Click Next. 25) On the Thank You screen, click Finish. 26) On the Log in screen, click Admin. Set Internet Explorer s page to blank. 1) Click Start > Internet Explorer. 2) On the menu bar click Tools > Internet Options 3) On the General tab, under Home page, click the Use Blank Button. 4) Click OK. 5) Close Internet Explorer. Installing Additional Software Virtual Machine Tools Install the virtual machine tools for your particular platform. These tools add mouse functionality and improved video display, among other things. Check your documentation for this information. Installing the Advanced Networking Patch (IPv6) 1. In the Software Installation folder, double click WindowsXP-KB x86- ENU. 2. Click Next and Agree to the Terms of service and then click Next. 3. Click Finish and let the computer restart. 5 of 18
6 Nmap Zenmap 1. In the Software Installation folder, double click nmap-5.21-setup. 2. Click I Agree and click Next. (Notice it will include WinPcap which is needed for other programs as well.) 3. Continue to click Next until the end of the installation. Default settings are fine for this setup. Wireshark 1. In the Software Installation folder, double click wireshark-win Click Next and click I Agree to the Terms of service. 3. Verify that all of the boxes are ticked and click Next. 4. Uncheck the Quick Launch Icon checkbox and check the Desktop Icon checkbox, then click Next. 5. Continue to click Next until the window shows to install WinPcap. Make sure the checkbox is not checked and click Install. (This was installed with Nmap) 6. When the setup is complete, click Next and then click Finish. 7 Zip 1. In the Software Installation folder, double click 7z Click Install and after the setup copies files, click Finish. Create a Tools Folder on the desktop and put the following installer files in it: File URL Required for Lab Exercise Winpcap3.0.exe Snort 2_8_6_ Camouflage WinPT Putty WinSCP Service Pack Suspect_image file You should have created a second hard drive of at least 100 MB. Format the drive and put the file called suspect_image on the drive. Take a snap shot. 6 of 18
7 When you are done configuring the virtual machine, make sure to take a snapshot of the base image. You should do this for all of the virtual machines when they are deployed so that if a student makes a change, it will be easy to revert back to the original state which all the labs depend upon. 7 of 18
8 Setting up the Windows 2003 Server Steps at a Glance To setup the your computer(s) for working with the lab manual you will have to Download and gather required software Setup the host machine Setup the virtual machine Install Windows Server 2003 Configure the Windows Server 2003 Add other software to the tools folder Download and Gather Required Software File URL Lab location Winpcap3.0.exe Tools Snort 2_8_6_ Tools McAfee_Antispyware_Trial Tools McAfee_VirusScan_Trial Tools Camouflage Tools WinPT Tools fakedel Wwwroot, renamed as update.exe Secondary_Harddrive D drive Setup Host Machine There are a number of different ways to deploy virtual machines. The following requirements are for a single host running software such as VMware Workstation, VMware Player, or Virtual PC. Minimum Requirements CPU 1.3 GHz or faster (Pentium Core or better recommended) RAM 2 Gig (4 Gig Recommended) HD 20 Gig of free space Setting Up the Virtual Machine 1. Use at least a 10 GB partition for the C Drive. 2. The RAM should be set for at least 512 MB but 1 GB is recommended 3. You will need to set up the networking for host only so that no traffic from the virtual environment can make it to the actual network. 8 of 18
9 4. You may also want to disable any file sharing or copying and pasting of files to and from the virtual machine. Some of the software on the virtual machines is considered malicious code and should not leave the machines. If you are unsure of how to do this, please refer to the support provided by the vender of your virtualization product. 5. You will need to mount the SecondaryHarddrive image as the D drive. (This file is used only for lab 10.1 and 10.2) Mount the Windows Server 2003 Standard CD and begin the install. 1) On the Welcome to Setup screen, press Enter to continue 2) On the Windows Licensing Agreement, press F8 to continue 3) On the Windows Server 2003 Setup Screen, press C to create a new partition 4) On the next screen, press Enter to accept the default. 5) On the next screen, make sure Format Partition Using the NTFS file System is selected. Press Enter to continue. Windows 2003 will begin to install partition and format the drive. It will then begin to copy the files needed for the rest of the install. The next portion of the install will take a bit of time depending on your processor speed. 6) On the Regional and Language Options Screen click Next 7) On the Personalize Your Software screen a) Name Computer Security Student b) Organization Computer Security c) Click Next. 8) On the Product Key Screen, enter in your product key and click Next 9) On the Licensing Modes Screen accept the default (per server 5) and click Next. NOTE: You will have to activate the installation later. This process will vary depending on your licensing agreement. Contact your network administrator if you are unsure of this process. 10) On the Computer Name and Administrative Password Screen a) Computer Name WIN2K3SERV 9 of 18
10 b) Administrative password adminpass (This is an extremely weak password but is being used only for educational purposes and will be changed later in the labs) c) Confirm password - adminpass d) Click Next e) When prompted Are you sure you want to continue with the current password? click Yes. 11) On the Date and Time screen, enter the correct date and time as well as your time zone and click Next 12) On the Networking Settings screen select Custom Settings and click Next 13) On the Networking Components screen Select Internet Protocol and then click on Properties 14) On the Internet Protocol screen select Use the Following IP Address a) IP address b) Subnet Mask c) Default Gateway blank d) DNS e) Click OK f) Click Next. 15) On the Workgroup or Computer Domain Screen, click Next 16) The Completing the Windows 2003 Setup Wizard will show when the installation is complete 17) Click on Finish 18) The Windows 2003 Login Screen will appear. a) Press the Right Alt + Del key (not Ctrl +Alt + Del) b) Username Administrator c) Password adminpass d) Click OK 19) When the Server has completed booting up you will get Manage Your Server Screen. a) Check the box next to Don t Display This Page at Logon and close the screen. 10 of 18
11 NOTE: You may need to install the virtualization tools for your particular platform. These tools enhance the interaction with the virtual machine (improved display and mouse performance). Refer to your virtualization software documentation. Configure the Windows Server ) Click Start, Control Panel, Add or Remove Programs 2) Click Add/Remove Windows Components 3) On the Windows Components screen, select Application Server and click Details 4) Select Internet Information Services and click Details a) Check File Transfer Protocol Service b) Internet Information Service Manager c) World Wide Web Service d) Click OK 5) Click OK again 6) Click Next 7) On the Completing Windows Components Wizard screen, click Finish. 8) Rename fake_del.exe to update.exe 9) Copy update.exe to the C:\inetpub\wwwroot\ directory Configure the FTP server 1) Click Start, Administration Tools, Internet Services Manager. 2) Expand Win2K3Serv 3) Expand FTP Sites 4) Right click Default FTP Site and select Properties. 5) Select the Home Directory tab 6) Change the local path to c:\inetpub\wwwroot 7) Check the Write box 8) Click OK 9) Click OK to Override. 11 of 18
12 10) Click OK. 11) Close Internet Information Services Manager. Currently the only accounts available on this virtual machine are the administrator account and the guest account, which is disabled. Let s now create a user account. 1) Click Start, right click My Computer and click on Manage. 2) In the Tree pane of Computer Management window click on Local Users and Groups 3) Right click Users folder and select New User 4) In the New User window a) In the User Name: box type labuser b) In the Full Name: box type Lab user c) In the Description: box type User account for lab exercises d) In the Password: box type password e) In the Confirm Password: box type password f) Select User cannot change password g) Select Password never expirers h) Click Create i) Click Close 5) Close computer management 12 of 18
13 Additional Software Download and place the files in the location indicated. File URL Lab location Winpcap3.0.exe Tools Snort 2_8_6_ Tools McAfee_Antispyware_Trial Tools McAfee_VirusScan_Trial Tools Camouflage Tools WinPT Tools fakedel Wwwroot, renamed as update.exe Keylog5 Littlesister.de 10.1 D drive Nbserv exe 13 of 18
14 Linux Machine Setup Materials necessary Base computer with Virtual machine software A Bit torrent client (The official client at is fine) Metasploitable BackTrack (2)Steps at a Glance Download Metasploitable and BackTrack Install the Metasploitable base machine. Install the Backtrack machine Setup User accounts Setup DNS Setup Web Setup Mailserver Download Metasploitable and BackTrack images 1) Download the bit torrent files for metasploitable and backtrack from the following locations 2) Use both files to download the metasploitable and backtrack images. Install the Metasploitable base machine. 1) Put the Metasploitable.zip file in the directory you will be storing the virtual machines. 2) Unzip the file. 3) If you are using VMware you will can simply double click the metasploitable.vmx file and the machine will start up. If you are using a platform other than VMware you will need to refer to your virtualization documentation for the procedures to convert the image to the required format. 4) Login, The userid is msfadmin and the password is msfadmin. NOTE: Ubuntu is designed following best practices which include that a user does not directly login as root. Instead, a user logs in as a user in the group admin and then would use sudo to become root. On the metasploitable machine, the msfadmin account is a member of the group admin. To follow all the commands below you will: login as msfadmin and then run sudo su - and then enter the password of msfadmin. 14 of 18
15 5) Setup the network configuration. Edit the file: /etc/network/interfaces remove: iface eth0 inet dhcp Add: iface eth0 inet static address netmask network a) We will change the hostname to linuxserv, by changing the file /etc/hostname echo "linuxserv" > /etc/hostname b) Edit the file: /etc/resolv.conf Change the file to being just: search security.local nameserver If you are using VMware and want to access this from your base machine, you would manually setup your vmnet address (of the base machine) to The nice feature of this is that you can then ssh into the virtual machine from a terminal and will be able to copy and paste this easily. ex: on a mac running vmfusion vmnet8: flags=8863 mtu 1500 inet netmask 0xffffff00 broadcast vmnet1: flags=8863 mtu 1500 inet netmask 0xffffff00 broadcast root# ifconfig vmnet vmnet1: flags=8863 mtu 1500 inet netmask 0xffffff00 broadcast Install the Backtrack base machine. 1) Put the bt4-final-vm.zip file in the directory you will be storing the virtual machines. 2) Unzip the file. 3) If you are using VMware you will can simply double click the bt4-final-vm.vmx file and the machine will start up. If you are using a platform other than vmware you will need to refer to your virtualization documentation for the procedures to convert the image to the required format. Once the machine is up, we will setup the network interfaces and the hostname. 1. Login: user root password toor. 2. You need to copy the file hashes.txt to /pentest/passwords/jtr The file is on the cd iso. In the directory backtrack. If mount in /mnt, you would copy the file with the command cp /mnt/backtrack/hashes.txt /pentest/passwords/jtr 3. Setup the network configuration. Edit the file: /etc/network/interfaces remove: iface eth0 inet dhcp Add: iface eth0 inet static address netmask network Comment out the interface lines for (eth1 eth2 ath0 wlan0) by placing a # as the first character. 15 of 18
16 4. We will change the hostname to linuxcl, by changing the file /etc/hostname echo "linuxcl" > /etc/hostname 5. Edit the file: /etc/resolv.conf Change the file to: search security.local nameserver Create UserAaccounts The labs depend upon having the accounts labuser and labuser2. Run the following commands on both the metasploitable machine (linuxserv) and the backtrack machine. 1. useradd -m -s /bin/bash labuser 2. passwd labuser 3. Create the password of password 4. useradd -m -s /bin/bash labuser2 5. passwd labuser2 6. Create the password of password Setup DNS At this point we need to create the dns for the virtual machines. 1. The dns configuration is in the directory /etc/bind Edit the file named.conf.local Synopsis: You will comment out the global items and add the security.local lines: So you will comment out: (add // to the beginning of the line) //prime the server with knowledge of the root servers //zone "." { // type hint; // file "/etc/bind/db.root"; //}; and at the end of the file you will add zone security.local { type master; file /etc/bind/db.security.local ; }; zone in-addr.arpa { type master; file /etc/bind/db ; } 2. After this you will create the files: /etc/bind/db.security.local and /etc/bind/db The file /etc/bind/db.security.local will be the following: You can cp db.local db.security.local and then edit it to the following. ; ; BIND data file for domain security.local ; $TTL IN SOA security.local. root.securitylocal. ( 16 of 18
17 2 ; Serial ; Refresh ; Retry ; Expire ) ; Negative Cache TTL IN NS IN A IN AAAA ::1 winxppro IN A win2kserv IN A linuxcl IN A linuxserv IN A The file /etc/bind/db should be created. You can cp db.255 db and then edit the file to be as below) db ; ; BIND reverse data file for broadcast zone ; $TTL IN SOA localhost. root.localhost. ( 2 ; Serial ; Refresh ; Retry ; Expire ) ; Negative Cache TTL IN NS localhost. 101 IN PTR winxppro.security.local. 102 IN PTR win2k3serv.security.local. 201 IN PTR linuxcl.security.local. 202 IN PTR linuxserv.security.local. 4. You can now stop the dns with the commands: Setup Web Site root@metasploitable:/etc/network# /etc/init.d/bind9 stop * Stopping domain name service... bind...done. root@metasploitable:/etc/network# /etc/init.d/bind9 start * Starting domain name service... bind...done. The website does exist on the metasploitable machine right out of the box. Unzip wwh in /var/www mysqladmin -u root -p create wikihelp mysql -u root -p wikihelp < sql/wikihelp.sql That is all that is needed for the wikiwebhelp site Setup Edit /etc/postfix/main.cf set mydestination = localhost, linuxserv, linuxserv.security.local, security.local 17 of 18
18 This completes the setup. Be sure to take snapshots of the virtual machines once you have completed the install. Please send questions to Check for updates, new lab exercises, errata and other resources to support the security curriculum. 18 of 18
WA2592 Applied Data Science and Big Data Analytics. Classroom Setup Guide. Web Age Solutions Inc. Copyright Web Age Solutions Inc.
 WA2592 Applied Data Science and Big Data Analytics Classroom Setup Guide Web Age Solutions Inc. Copyright Web Age Solutions Inc. 1 Table of Contents Part 1 - Class Setup...3 Part 2 - Minimum Software Requirements
WA2592 Applied Data Science and Big Data Analytics Classroom Setup Guide Web Age Solutions Inc. Copyright Web Age Solutions Inc. 1 Table of Contents Part 1 - Class Setup...3 Part 2 - Minimum Software Requirements
WA2342 NoSQL Systems Comparison. Lab Server VM Setup Guide. Web Age Solutions Inc. Copyright Web Age Solutions Inc. 1
 WA2342 NoSQL Systems Comparison Lab Server VM Setup Guide Web Age Solutions Inc. Copyright Web Age Solutions Inc. 1 Table of Contents Part 1 - Minimum Hardware Requirements...3 Part 2 - Minimum Software
WA2342 NoSQL Systems Comparison Lab Server VM Setup Guide Web Age Solutions Inc. Copyright Web Age Solutions Inc. 1 Table of Contents Part 1 - Minimum Hardware Requirements...3 Part 2 - Minimum Software
Sun VirtualBox Installation Tutorial
 Sun VirtualBox Installation Tutorial Installing Linux Mint 5 LTS Guest OS By Dennis Berry Welcome to the world of virtualization and Linux. This tutorial is intended to help users who are new to the world
Sun VirtualBox Installation Tutorial Installing Linux Mint 5 LTS Guest OS By Dennis Berry Welcome to the world of virtualization and Linux. This tutorial is intended to help users who are new to the world
WA2393 Data Science for Solution Architects. Classroom Setup Guide. Web Age Solutions Inc. Copyright Web Age Solutions Inc. 1
 WA2393 Data Science for Solution Architects Classroom Setup Guide Web Age Solutions Inc. Copyright Web Age Solutions Inc. 1 Table of Contents Part 1 - Class Setup...3 Part 2 - Minimum Software Requirements
WA2393 Data Science for Solution Architects Classroom Setup Guide Web Age Solutions Inc. Copyright Web Age Solutions Inc. 1 Table of Contents Part 1 - Class Setup...3 Part 2 - Minimum Software Requirements
Windows Server 2003 { Domain Controller Installation and Configuration}
 Windows Server 2003 { Domain Controller Installation and } Benedikt Riedel MCSE + Messaging www.go-unified.com www.siemens.com/open Benedikt.riedel@siemens.com Start up the prepared Windows Server 2003
Windows Server 2003 { Domain Controller Installation and } Benedikt Riedel MCSE + Messaging www.go-unified.com www.siemens.com/open Benedikt.riedel@siemens.com Start up the prepared Windows Server 2003
Jackson State University Department of Computer Science CSC 437/539 Computer Security Fall 2013 Instructor: Dr. Natarajan Meghanathan
 Jackson State University Department of Computer Science CSC 437/539 Computer Security Fall 2013 Instructor: Dr. Natarajan Meghanathan Lab Project # 3: Simulating DHCP Snooping and DNS Cache Poisoning through
Jackson State University Department of Computer Science CSC 437/539 Computer Security Fall 2013 Instructor: Dr. Natarajan Meghanathan Lab Project # 3: Simulating DHCP Snooping and DNS Cache Poisoning through
Cisco Modeling Labs OVA Installation
 Prepare for an OVA File Installation, page 1 Download the Cisco Modeling Labs OVA File, page 2 Configure Security and Network Settings, page 2 Deploy the Cisco Modeling Labs OVA, page 12 Edit the Virtual
Prepare for an OVA File Installation, page 1 Download the Cisco Modeling Labs OVA File, page 2 Configure Security and Network Settings, page 2 Deploy the Cisco Modeling Labs OVA, page 12 Edit the Virtual
ScopTEL TM IP PBX Software. DNS Server Configuration Wizard
 ScopTEL TM IP PBX Software DNS Server Configuration Wizard Network Module - ifconfig A newly installed server uses DHCP to get an IP address from a DHCP server on the network so make sure the eth0 interface
ScopTEL TM IP PBX Software DNS Server Configuration Wizard Network Module - ifconfig A newly installed server uses DHCP to get an IP address from a DHCP server on the network so make sure the eth0 interface
DNS & DHCP CONFIGURATION
 WELCOME DNS & DHCP CONFIGURATION Group Members Anmol Nazakat Ameena Fatima Shakeel ur Rehman Gulraiz Azam Irfan Ullah 1 2 3 4 5 BSIT-F14-E78 BSIT-F14-E100 BSIT-F14-E66 BSIT-F14-E69 BSIT-F14-E79 3 Today
WELCOME DNS & DHCP CONFIGURATION Group Members Anmol Nazakat Ameena Fatima Shakeel ur Rehman Gulraiz Azam Irfan Ullah 1 2 3 4 5 BSIT-F14-E78 BSIT-F14-E100 BSIT-F14-E66 BSIT-F14-E69 BSIT-F14-E79 3 Today
10ZiG Technology. Thin Desktop Quick Start Guide
 10ZiG Technology Thin Desktop Quick Start Guide 2010 05 20 Introduction This document is intended as a quick start guide for installing Thin Desktop. After reading this document, you will know how to:
10ZiG Technology Thin Desktop Quick Start Guide 2010 05 20 Introduction This document is intended as a quick start guide for installing Thin Desktop. After reading this document, you will know how to:
HP LeftHand SAN Solutions
 HP LeftHand SAN Solutions Support Document Installation Manuals VSA 8.0 Quick Start - Demo Version Legal Notices Warranty The only warranties for HP products and services are set forth in the express warranty
HP LeftHand SAN Solutions Support Document Installation Manuals VSA 8.0 Quick Start - Demo Version Legal Notices Warranty The only warranties for HP products and services are set forth in the express warranty
202 Lab Introduction Connecting to the Lab Environment
 202 Lab Introduction Connecting to the Lab Environment Objectives During this v7.1 Deployment lab, each student (from the Blue group or Green group) must verify access (and permissions) to their assigned
202 Lab Introduction Connecting to the Lab Environment Objectives During this v7.1 Deployment lab, each student (from the Blue group or Green group) must verify access (and permissions) to their assigned
Deploying Cisco UCS Central
 This chapter includes the following sections: Obtaining the Cisco UCS Central Software from Cisco, page 1 Using the Cisco UCS Central OVA File, page 2 Using the Cisco UCS Central ISO File, page 4 Logging
This chapter includes the following sections: Obtaining the Cisco UCS Central Software from Cisco, page 1 Using the Cisco UCS Central OVA File, page 2 Using the Cisco UCS Central ISO File, page 4 Logging
Installation Manual InfraManage.NET Installation Instructions for Ubuntu
 Installation Manual InfraManage.NET Installation Instructions for Ubuntu Copyright 1996 2017 Timothy Ste. Marie Version 7.5.72SQL InfraManage.NET Installing InfraManage.NET Page 1 of 78 Table of Contents
Installation Manual InfraManage.NET Installation Instructions for Ubuntu Copyright 1996 2017 Timothy Ste. Marie Version 7.5.72SQL InfraManage.NET Installing InfraManage.NET Page 1 of 78 Table of Contents
CIS 76 VLab Pod Setup
 CIS 76 VLab Pod Setup Last updated 9/4/2017 Status on setup instructions: 1. pfsense (2.3.1, 64 bit) pfsense-ce-2.3.4-release-amd64 - DONE for Fa17 2. Kali (2017.1, 64 bit) kali-linux-2017.1-amd64.iso
CIS 76 VLab Pod Setup Last updated 9/4/2017 Status on setup instructions: 1. pfsense (2.3.1, 64 bit) pfsense-ce-2.3.4-release-amd64 - DONE for Fa17 2. Kali (2017.1, 64 bit) kali-linux-2017.1-amd64.iso
Wowza Media Server Pro for Riverbed Steelhead. Installation Guide
 Wowza Media Server Pro for Riverbed Steelhead Installation Guide Wowza Media Server Pro for Riverbed Steelhead Installation Guide Version 2.0 Wowza Media Systems, Inc. 1153 Bergen Parkway, #181 Evergreen,
Wowza Media Server Pro for Riverbed Steelhead Installation Guide Wowza Media Server Pro for Riverbed Steelhead Installation Guide Version 2.0 Wowza Media Systems, Inc. 1153 Bergen Parkway, #181 Evergreen,
Networks Lab Pod Diagram
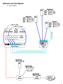 (Console cable) Networks Lab Pod Diagram (x = pod number) 190.111.50.x 190.111.x.254 PodxLinux Addr: 190.111.x.3 Mask: 255.255.255.0 GW: 190.111.x.254 DNS: 190.111.x.1 PodxServer Addr: 190.111.x.1 Mask:
(Console cable) Networks Lab Pod Diagram (x = pod number) 190.111.50.x 190.111.x.254 PodxLinux Addr: 190.111.x.3 Mask: 255.255.255.0 GW: 190.111.x.254 DNS: 190.111.x.1 PodxServer Addr: 190.111.x.1 Mask:
CCNA Discovery Server Live CD v2.0
 CCNA Discovery Overview CCNA Discovery Server Live CD v2.0 Information and Installation Instructions The Discovery Server Live CD provides all of the network services necessary to support the CCNA Discovery
CCNA Discovery Overview CCNA Discovery Server Live CD v2.0 Information and Installation Instructions The Discovery Server Live CD provides all of the network services necessary to support the CCNA Discovery
Comodo Dome Data Protection Software Version 3.8
 Comodo Dome Data Protection Software Version 3.8 Installation Guide Guide Version 3.8.102417 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1.About Dome Data Protection...
Comodo Dome Data Protection Software Version 3.8 Installation Guide Guide Version 3.8.102417 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1.About Dome Data Protection...
Installing Cisco MSE in a VMware Virtual Machine
 Installing Cisco MSE in a VMware Virtual Machine This chapter describes how to install and deploy a Cisco Mobility Services Engine (MSE) virtual appliance. Cisco MSE is a prebuilt software solution that
Installing Cisco MSE in a VMware Virtual Machine This chapter describes how to install and deploy a Cisco Mobility Services Engine (MSE) virtual appliance. Cisco MSE is a prebuilt software solution that
Installing and Upgrading Cisco Network Registrar Virtual Appliance
 CHAPTER 3 Installing and Upgrading Cisco Network Registrar Virtual Appliance The Cisco Network Registrar virtual appliance includes all the functionality available in a version of Cisco Network Registrar
CHAPTER 3 Installing and Upgrading Cisco Network Registrar Virtual Appliance The Cisco Network Registrar virtual appliance includes all the functionality available in a version of Cisco Network Registrar
LAN Setup Reflection
 LAN Setup Reflection After the LAN setup, ask yourself some questions: o Does your VM have the correct IP? o Are you able to ping some locations, internal and external? o Are you able to log into other
LAN Setup Reflection After the LAN setup, ask yourself some questions: o Does your VM have the correct IP? o Are you able to ping some locations, internal and external? o Are you able to log into other
dctrack Quick Setup Guide (Recommended) Obtain a dctrack Support Website Username and Password
 dctrack 5.0.0 Quick Setup Guide This guide walks you through installing dctrack for the first time. In other words, this is a clean install - it is not an integration of dctrack and Power IQ, and it is
dctrack 5.0.0 Quick Setup Guide This guide walks you through installing dctrack for the first time. In other words, this is a clean install - it is not an integration of dctrack and Power IQ, and it is
SANS Institute - Operations Essentials. Operating System Installation Guidelines. Windows XP Professional Installation. Creating Boot Disks
 SANS Institute - Operations Essentials Operating System Installation Guidelines The following document guides you step-by-step through the process of creating a dualboot system. Even if you do not use
SANS Institute - Operations Essentials Operating System Installation Guidelines The following document guides you step-by-step through the process of creating a dualboot system. Even if you do not use
The Ip address / Name value should be: srvvcenter-cis
 CIS133 Installation Lab #1 - DESKTOP CLIENT OpenSUSE Install. Before beginning the installation, create a virtual machine in which you will install the operating system. 1) Open the VMware vsphere Client.
CIS133 Installation Lab #1 - DESKTOP CLIENT OpenSUSE Install. Before beginning the installation, create a virtual machine in which you will install the operating system. 1) Open the VMware vsphere Client.
LAN Setup Reflection. Ask yourself some questions: o Does your VM have the correct IP? o Are you able to ping some locations, internal and external?
 LAN Setup Reflection Ask yourself some questions: o Does your VM have the correct IP? o Are you able to ping some locations, internal and external? o Are you able to log into other VMs in the classroom?
LAN Setup Reflection Ask yourself some questions: o Does your VM have the correct IP? o Are you able to ping some locations, internal and external? o Are you able to log into other VMs in the classroom?
Network Scanner Tool V3.3. User s Guide Version
 Network Scanner Tool V3.3 User s Guide Version 3.3.09 Copyright 2000-2012 by SHARP CORPORATION. All rights reserved. Reproduction, adaptation or translation without prior written permission is prohibited,
Network Scanner Tool V3.3 User s Guide Version 3.3.09 Copyright 2000-2012 by SHARP CORPORATION. All rights reserved. Reproduction, adaptation or translation without prior written permission is prohibited,
Optional Lab. Identifying the Requirements. Configuring Windows 7 with virtualization. Installing Windows Server 2008 on a virtual machine
 Optional Lab Appendix D As you go through Microsoft Windows Networking Essentials for the 98-366 exam, you may want to get your hands on Windows Server 2008 and dig a little deeper. That makes sense. While
Optional Lab Appendix D As you go through Microsoft Windows Networking Essentials for the 98-366 exam, you may want to get your hands on Windows Server 2008 and dig a little deeper. That makes sense. While
Redhat OpenStack 5.0 and PLUMgrid OpenStack Networking Suite 2.0 Installation Hands-on lab guide
 Redhat OpenStack 5.0 and PLUMgrid OpenStack Networking Suite 2.0 Installation Hands-on lab guide Oded Nahum Principal Systems Engineer PLUMgrid EMEA November 2014 Page 1 Page 2 Table of Contents Table
Redhat OpenStack 5.0 and PLUMgrid OpenStack Networking Suite 2.0 Installation Hands-on lab guide Oded Nahum Principal Systems Engineer PLUMgrid EMEA November 2014 Page 1 Page 2 Table of Contents Table
Deployment Guide: Routing Mode with No DMZ
 Deployment Guide: Routing Mode with No DMZ March 15, 2007 Deployment and Task Overview Description Follow the tasks in this guide to deploy the appliance as a router-firewall device on your network with
Deployment Guide: Routing Mode with No DMZ March 15, 2007 Deployment and Task Overview Description Follow the tasks in this guide to deploy the appliance as a router-firewall device on your network with
Creating a 2 node virtual SQL Server 2008 Cluster Configuration Using Windows 2003 MSCS
 Creating a 2 node virtual SQL Server 2008 Cluster Configuration Using Windows 2003 MSCS Reference No: Date: 10/08/2010 File Name: Creating a 2 node SQL Server 2008 Cluster Configuration using Windows 2003
Creating a 2 node virtual SQL Server 2008 Cluster Configuration Using Windows 2003 MSCS Reference No: Date: 10/08/2010 File Name: Creating a 2 node SQL Server 2008 Cluster Configuration using Windows 2003
TABLE OF CONTENTS. PRELIMINARY SETUP REQUIREMENTS... 1 Minimum Hardware/Software Requirements...1
 Worldspan RemoteLink Setup and Configuration Procedures for Worldspan Go! SM Static IP Address TABLE OF CONTENTS PRELIMINARY SETUP REQUIREMENTS... 1 Minimum Hardware/Software Requirements...1 REQUIRED
Worldspan RemoteLink Setup and Configuration Procedures for Worldspan Go! SM Static IP Address TABLE OF CONTENTS PRELIMINARY SETUP REQUIREMENTS... 1 Minimum Hardware/Software Requirements...1 REQUIRED
How to Deploy a Barracuda NG Vx using Barracuda NG Install on a VMware Hypervisor
 How to Deploy a Barracuda NG Vx using Barracuda NG Install on a VMware Hypervisor The OVA package uses a default configuration that may not be suitable for your deployment. If you want to use multiple
How to Deploy a Barracuda NG Vx using Barracuda NG Install on a VMware Hypervisor The OVA package uses a default configuration that may not be suitable for your deployment. If you want to use multiple
Lesson 1: Preparing for Installation
 2-2 Chapter 2 Installing Windows XP Professional Lesson 1: Preparing for Installation When you install Windows XP Professional, the Windows XP Professional Setup program allows you to specify how to install
2-2 Chapter 2 Installing Windows XP Professional Lesson 1: Preparing for Installation When you install Windows XP Professional, the Windows XP Professional Setup program allows you to specify how to install
For my installation, I created a VMware virtual machine with 128 MB of ram and a.1 GB hard drive (102 MB).
 HOWTO: ZeroShell WPA Enterprise by Paul Taylor ZeroShell can be obtained from: http://www.zeroshell.net/eng/ For my installation, I created a VMware virtual machine with 128 MB of ram and a.1 GB hard drive
HOWTO: ZeroShell WPA Enterprise by Paul Taylor ZeroShell can be obtained from: http://www.zeroshell.net/eng/ For my installation, I created a VMware virtual machine with 128 MB of ram and a.1 GB hard drive
CIS 231 Windows XP (SP3) Install Lab #3 Virtual Machines
 CIS 231 Windows XP (SP3) Install Lab #3 Virtual Machines Before beginning the installation, create a virtual machine in which you will install the operating system. 1) Open the VMware vsphere Client. Be
CIS 231 Windows XP (SP3) Install Lab #3 Virtual Machines Before beginning the installation, create a virtual machine in which you will install the operating system. 1) Open the VMware vsphere Client. Be
Lab: Advanced Installation of Windows XP. Introduction
 12.2.2 Lab: Advanced Installation of Windows XP Introduction Print and complete this lab. In this lab, you will install a Windows XP operating system by using an answer file for automation. You will customize
12.2.2 Lab: Advanced Installation of Windows XP Introduction Print and complete this lab. In this lab, you will install a Windows XP operating system by using an answer file for automation. You will customize
WA2503 Hadoop Programming on the. Hortonworks Data Platform. Lab Setup Guide. Web Age Solutions Inc. Copyright Web Age Solutions Inc.
 WA2503 Hadoop Programming on the Hortonworks Data Platform Lab Setup Guide Web Age Solutions Inc. Copyright Web Age Solutions Inc. 1 Table of Contents Part 1 - Minimum Hardware Requirements...3 Part 2
WA2503 Hadoop Programming on the Hortonworks Data Platform Lab Setup Guide Web Age Solutions Inc. Copyright Web Age Solutions Inc. 1 Table of Contents Part 1 - Minimum Hardware Requirements...3 Part 2
Local DNS Attack Lab. 1 Lab Overview. 2 Lab Environment. 2.1 Install and configure the DNS server. SEED Labs Local DNS Attack Lab 1
 SEED Labs Local DNS Attack Lab 1 Local DNS Attack Lab Copyright c 2006-2015 Wenliang Du, Syracuse University. The development of this document is partially funded by the National Science Foundation s Course,
SEED Labs Local DNS Attack Lab 1 Local DNS Attack Lab Copyright c 2006-2015 Wenliang Du, Syracuse University. The development of this document is partially funded by the National Science Foundation s Course,
Installing or Upgrading ANM Virtual Appliance
 CHAPTER 2 This chapter describes how to deploy Cisco ANM Virtual Appliance 4.3 (new installation) and how to upgrade from ANM software version 4.1 or 4.2 to software version 4.3. This chapter includes
CHAPTER 2 This chapter describes how to deploy Cisco ANM Virtual Appliance 4.3 (new installation) and how to upgrade from ANM software version 4.1 or 4.2 to software version 4.3. This chapter includes
Product Version 1.1 Document Version 1.0-A
 VidyoDashboard Installation Guide Product Version 1.1 Document Version 1.0-A Table of Contents 1. Overview... 3 About This Guide... 3 Prerequisites... 3... 5 Installing the OVA for VMware ESXi... 5 Configuring
VidyoDashboard Installation Guide Product Version 1.1 Document Version 1.0-A Table of Contents 1. Overview... 3 About This Guide... 3 Prerequisites... 3... 5 Installing the OVA for VMware ESXi... 5 Configuring
UDP Director Virtual Edition Installation and Configuration Guide (for Stealthwatch System v6.9.0)
 UDP Director Virtual Edition Installation and Configuration Guide (for Stealthwatch System v6.9.0) Installation and Configuration Guide: UDP Director VE v6.9.0 2016 Cisco Systems, Inc. All rights reserved.
UDP Director Virtual Edition Installation and Configuration Guide (for Stealthwatch System v6.9.0) Installation and Configuration Guide: UDP Director VE v6.9.0 2016 Cisco Systems, Inc. All rights reserved.
29 March 2017 SECURITY SERVER INSTALLATION GUIDE
 29 March 2017 SECURITY SERVER INSTALLATION GUIDE Contents 1. Introduction... 2 1.1 Assumptions... 2 1.2 Prerequisites... 2 2. Required setups prior the Security Server Installation... 3 1.1 Create domain
29 March 2017 SECURITY SERVER INSTALLATION GUIDE Contents 1. Introduction... 2 1.1 Assumptions... 2 1.2 Prerequisites... 2 2. Required setups prior the Security Server Installation... 3 1.1 Create domain
Unit- 5. Linux Systems
 Unit- 5 Linux System- Basic Concepts; System Administration-Requirements for Linux System Administrator, Setting up a LINUX Multifunction Server, Domain Name System, Setting Up Local Network Services;
Unit- 5 Linux System- Basic Concepts; System Administration-Requirements for Linux System Administrator, Setting up a LINUX Multifunction Server, Domain Name System, Setting Up Local Network Services;
Network Planning and Implementation
 Network Planning and Implementation SYLLABUS 3.1 Designing network 3.1.1 Accessing network needs- applications, users, network services, security and safety, growth and capacity planning 3.1.2 Meeting
Network Planning and Implementation SYLLABUS 3.1 Designing network 3.1.1 Accessing network needs- applications, users, network services, security and safety, growth and capacity planning 3.1.2 Meeting
Software Installations for Components
 Install Microsoft Windows Server, page 1 Install VMware Tools, page 3 Configure Network Adapters for Unified CCE Call Server and Unified CCE Data Server, page 4 Set Persistent Static Routes, page 5 Run
Install Microsoft Windows Server, page 1 Install VMware Tools, page 3 Configure Network Adapters for Unified CCE Call Server and Unified CCE Data Server, page 4 Set Persistent Static Routes, page 5 Run
XD10004: How to Install VMware ESX Server 3.5 on VMware Workstation 6.5 as a VM
 white paper XD10004: How to Install VMware ESX Server 3.5 on VMware Workstation 6.5 as a VM VI in a Box - the portable virtual infrastructure Title: How to Install VMware ESX Server 3.5 on VMware Workstation
white paper XD10004: How to Install VMware ESX Server 3.5 on VMware Workstation 6.5 as a VM VI in a Box - the portable virtual infrastructure Title: How to Install VMware ESX Server 3.5 on VMware Workstation
Local Area Networks (LAN s)
 Local Area Networks (LAN s) Local area networks are computers connected together in a single location. They vary in size from two computers connected together to share a printer, to hundreds of computers
Local Area Networks (LAN s) Local area networks are computers connected together in a single location. They vary in size from two computers connected together to share a printer, to hundreds of computers
IT Essentials v6.0 Windows 10 Software Labs
 IT Essentials v6.0 Windows 10 Software Labs 5.2.1.7 Install Windows 10... 1 5.2.1.10 Check for Updates in Windows 10... 10 5.2.4.7 Create a Partition in Windows 10... 16 6.1.1.5 Task Manager in Windows
IT Essentials v6.0 Windows 10 Software Labs 5.2.1.7 Install Windows 10... 1 5.2.1.10 Check for Updates in Windows 10... 10 5.2.4.7 Create a Partition in Windows 10... 16 6.1.1.5 Task Manager in Windows
3. Click on the Download ZIP button under Raspbian Jessie, and select a folder to save it to.
 1. INITIAL CONFIGURATION RASPBERRY COMPONENTS INSTALL RASPBIAN IN YOUR RASPBERRY 1. Visit the official Raspberry Pi Downloads page 2. Click on Downloads Raspbian. 3. Click on the Download ZIP button under
1. INITIAL CONFIGURATION RASPBERRY COMPONENTS INSTALL RASPBIAN IN YOUR RASPBERRY 1. Visit the official Raspberry Pi Downloads page 2. Click on Downloads Raspbian. 3. Click on the Download ZIP button under
SOA Software API Gateway Appliance 6.3 Administration Guide
 SOA Software API Gateway Appliance 6.3 Administration Guide Trademarks SOA Software and the SOA Software logo are either trademarks or registered trademarks of SOA Software, Inc. Other product names, logos,
SOA Software API Gateway Appliance 6.3 Administration Guide Trademarks SOA Software and the SOA Software logo are either trademarks or registered trademarks of SOA Software, Inc. Other product names, logos,
Automating the Windows 2000 Installation
 Chapter 2 Automating the Windows 2000 Installation MICROSOFT EXAM OBJECTIVES COVERED IN THIS CHAPTER Perform an unattended installation of Windows 2000 Professional. Install Windows 2000 Professional by
Chapter 2 Automating the Windows 2000 Installation MICROSOFT EXAM OBJECTIVES COVERED IN THIS CHAPTER Perform an unattended installation of Windows 2000 Professional. Install Windows 2000 Professional by
Configuring Linux as an NIS Client
 Configuring Linux as an NIS Client Estimated Time: 30 minutes Objective Equipment Scenario Procedures To configure a Linux Red Hat system as an NIS server and client. A computer with Linux Red Hat 7.X
Configuring Linux as an NIS Client Estimated Time: 30 minutes Objective Equipment Scenario Procedures To configure a Linux Red Hat system as an NIS server and client. A computer with Linux Red Hat 7.X
CIS 231 Windows 7 Install Lab #2
 CIS 231 Windows 7 Install Lab #2 1) To avoid certain problems later in the lab, use Chrome as your browser: open this url: https://vweb.bristolcc.edu 2) Here again, to avoid certain problems later in the
CIS 231 Windows 7 Install Lab #2 1) To avoid certain problems later in the lab, use Chrome as your browser: open this url: https://vweb.bristolcc.edu 2) Here again, to avoid certain problems later in the
Cymmetria MazeRunner INSTALLATION GUIDE
 Cymmetria MazeRunner INSTALLATION GUIDE September 12, 2016 Supported environments (all must have nested virtualization enabled follow the links below to learn more) VMware Player (7 or higher) VMware Workstation
Cymmetria MazeRunner INSTALLATION GUIDE September 12, 2016 Supported environments (all must have nested virtualization enabled follow the links below to learn more) VMware Player (7 or higher) VMware Workstation
Novell BorderManager 3.7
 Novell Novell BorderManager 3.7 3.7 QUICK START www.novell.com Installing Novell BorderManager This section provides instructions for installing the Novell BorderManager 3.7 (NBM 3.7) software. SYSTEM
Novell Novell BorderManager 3.7 3.7 QUICK START www.novell.com Installing Novell BorderManager This section provides instructions for installing the Novell BorderManager 3.7 (NBM 3.7) software. SYSTEM
DNS Configuration Guide. Open Telekom Cloud
 DNS Configuration Guide Open Telekom Cloud www.telekom.de/opentelekomcloud For this guide we assume that two subnets are already configured. In our example the subnets are called subnet_dns01 (in AZ eu-de-01)
DNS Configuration Guide Open Telekom Cloud www.telekom.de/opentelekomcloud For this guide we assume that two subnets are already configured. In our example the subnets are called subnet_dns01 (in AZ eu-de-01)
Yong Peng High School System Documentation PC Section
 Yong Peng High School System Documentation PC Section Kent Ong Date: 26 May 2008 System Engineer Revision 1 Liew Toh Seng System Consultant Table of Contents Preface...1 Network Configuration (Manual Configuration)...1
Yong Peng High School System Documentation PC Section Kent Ong Date: 26 May 2008 System Engineer Revision 1 Liew Toh Seng System Consultant Table of Contents Preface...1 Network Configuration (Manual Configuration)...1
The Ip address / Name value should be: srvvcenter-cis
 CIS133 Installation Lab #1 - DESKTOP CLIENT OpenSUSE Install. Before beginning the installation, create a virtual machine in which you will install the operating system. 1) Open the VMware vsphere Client.
CIS133 Installation Lab #1 - DESKTOP CLIENT OpenSUSE Install. Before beginning the installation, create a virtual machine in which you will install the operating system. 1) Open the VMware vsphere Client.
CTEC1863/2018F Bonus Lab Page 1 of 5
 CTEC1863/2018F Bonus Lab Page 1 of 5 Bonus Lab: OpenSUSE Linux Rescue In this lab, we will install an OpenSUSE virtual machine. However, both the non-root user and the root passwords are unknown. To fix
CTEC1863/2018F Bonus Lab Page 1 of 5 Bonus Lab: OpenSUSE Linux Rescue In this lab, we will install an OpenSUSE virtual machine. However, both the non-root user and the root passwords are unknown. To fix
SAP GUI 7.30 for Windows Computer
 SAP GUI 7.30 for Windows Computer Student and Faculty Installation Instructions Table of Contents Caution:... 2 System Requirements:... 2 System Memory (RAM) requirements:... 2 Disk Space requirements:...
SAP GUI 7.30 for Windows Computer Student and Faculty Installation Instructions Table of Contents Caution:... 2 System Requirements:... 2 System Memory (RAM) requirements:... 2 Disk Space requirements:...
Create a pfsense router for your private lab network template
 Create a pfsense router for your private lab network template Some labs will require a private network where you can deploy services like DHCP. Here are instructions for setting up an uplink router for
Create a pfsense router for your private lab network template Some labs will require a private network where you can deploy services like DHCP. Here are instructions for setting up an uplink router for
Installing and Configuring Devstack Newton for Infoblox Integration
 DEPLOYMENT GUIDE Installing and Configuring Devstack Newton for Infoblox Integration 2017 Infoblox Inc. All rights reserved. Installing and Configuring Devstack Newton for Infoblox Integration Page 1 of
DEPLOYMENT GUIDE Installing and Configuring Devstack Newton for Infoblox Integration 2017 Infoblox Inc. All rights reserved. Installing and Configuring Devstack Newton for Infoblox Integration Page 1 of
LOMBA KETERAMPILAN SISWA
 LOMBA KETERAMPILAN SISWA SEKOLAH MENENGAH KEJURUAN TINGKAT NASIONAL XXV 2017 MODUL A LINUX ISLAND IT NETWORK SYSTEMS ADMINISTRATION LKS2017_ITNSA_MODUL_A 2 ISLAND A LINUX ISLAND CONTENTS This Test Project
LOMBA KETERAMPILAN SISWA SEKOLAH MENENGAH KEJURUAN TINGKAT NASIONAL XXV 2017 MODUL A LINUX ISLAND IT NETWORK SYSTEMS ADMINISTRATION LKS2017_ITNSA_MODUL_A 2 ISLAND A LINUX ISLAND CONTENTS This Test Project
IBM NetBAY Virtual Console Software. Installer and User Guide
 IBM NetBAY Virtual Console Software Installer and User Guide INSTRUCTIONS This symbol is intended to alert the user to the presence of important operating and maintenance (servicing) instructions in the
IBM NetBAY Virtual Console Software Installer and User Guide INSTRUCTIONS This symbol is intended to alert the user to the presence of important operating and maintenance (servicing) instructions in the
Chapter 6: Connecting Windows Workstations
 Chapter 6: Connecting Windows Workstations 153 Chapter 6 Connecting Windows Workstations Because this is a book about using Linux on a Microsoft Windows-based network, this chapter shows you how to connect
Chapter 6: Connecting Windows Workstations 153 Chapter 6 Connecting Windows Workstations Because this is a book about using Linux on a Microsoft Windows-based network, this chapter shows you how to connect
Configure Windows Server 2003 Release 2 Server Network File Share (NFS) as an authenticated storage repository for XenServer
 Summary This document outlines the process to perform the following tasks. 1. Configure Windows Server 2003 Release 2 Server Network File Share (NFS) as an authenticated storage repository for XenServer.
Summary This document outlines the process to perform the following tasks. 1. Configure Windows Server 2003 Release 2 Server Network File Share (NFS) as an authenticated storage repository for XenServer.
Integrated Information Technology Services (IITS)
 Integrated Information Technology Services (IITS) User Guide for Laptops with Windows 7 Network Configuration & Software Installation Version 1.4 Updated as at 15-Aug-11 Table of Contents How to verify
Integrated Information Technology Services (IITS) User Guide for Laptops with Windows 7 Network Configuration & Software Installation Version 1.4 Updated as at 15-Aug-11 Table of Contents How to verify
= Session-(1.4) Preparing the Workstation for the Lab / OS Installation = Session-(1.4) Preparing the Workstation for the Lab / OS Installation
 = Session-(1.4) Preparing the Workstation for the Lab / OS Installation = Session-(1.4) Preparing the Workstation for the Lab / OS Installation (1.4.1) Hardware Recommendation. (1.4.2) Operating System
= Session-(1.4) Preparing the Workstation for the Lab / OS Installation = Session-(1.4) Preparing the Workstation for the Lab / OS Installation (1.4.1) Hardware Recommendation. (1.4.2) Operating System
SECURITY+ LAB SERIES. Lab 3: Protocols and Default Network Ports Connecting to a Remote System
 SECURITY+ LAB SERIES Lab 3: Protocols and Default Network Ports Connecting to a Remote System Document Version: 2015-09-24 otherwise noted, is licensed under the Creative Commons Attribution 3.0 Unported
SECURITY+ LAB SERIES Lab 3: Protocols and Default Network Ports Connecting to a Remote System Document Version: 2015-09-24 otherwise noted, is licensed under the Creative Commons Attribution 3.0 Unported
Endian Proxy / Firewall
 Endian Proxy / Firewall Created October 27, 2006 by Bruce A. Westbrook Revisions: Introduction This document describes the step by step process of installing and configuring the Endian Firewall, Community
Endian Proxy / Firewall Created October 27, 2006 by Bruce A. Westbrook Revisions: Introduction This document describes the step by step process of installing and configuring the Endian Firewall, Community
IQSweb Installation Instructions Version 5.0
 IQSweb Installation Instructions Version 5.0 Contents Additional References... 3 IQSweb ROSS Connection... 3 IQSweb V5.0 Install/Upgrade Scenarios... 4 IQSweb Configuration Options... 5 A. Single Computer/Server
IQSweb Installation Instructions Version 5.0 Contents Additional References... 3 IQSweb ROSS Connection... 3 IQSweb V5.0 Install/Upgrade Scenarios... 4 IQSweb Configuration Options... 5 A. Single Computer/Server
Installing VMware vsphere 5.1 Components
 Installing VMware vsphere 5.1 Components Module 14 You Are Here Course Introduction Introduction to Virtualization Creating Virtual Machines VMware vcenter Server Configuring and Managing Virtual Networks
Installing VMware vsphere 5.1 Components Module 14 You Are Here Course Introduction Introduction to Virtualization Creating Virtual Machines VMware vcenter Server Configuring and Managing Virtual Networks
UDP Director Virtual Edition
 UDP Director Virtual Edition (also known as FlowReplicator VE) Installation and Configuration Guide (for StealthWatch System v6.7.0) Installation and Configuration Guide: UDP Director VE v6.7.0 2015 Lancope,
UDP Director Virtual Edition (also known as FlowReplicator VE) Installation and Configuration Guide (for StealthWatch System v6.7.0) Installation and Configuration Guide: UDP Director VE v6.7.0 2015 Lancope,
VMware vsphere 5.5: Install, Configure, Manage Lab Addendum. Lab 3: Configuring VMware ESXi
 VMware vsphere 5.5: Install, Configure, Manage Lab Addendum Lab 3: Configuring VMware ESXi Document Version: 2014-07-08 Copyright Network Development Group, Inc. www.netdevgroup.com NETLAB Academy Edition,
VMware vsphere 5.5: Install, Configure, Manage Lab Addendum Lab 3: Configuring VMware ESXi Document Version: 2014-07-08 Copyright Network Development Group, Inc. www.netdevgroup.com NETLAB Academy Edition,
2 Bay 3.5 HDD SATA NAS Media Server Setting...20 Bonjour...21 TorrentFlux Maintenance...25 Disk Utility...25 RAID Setting...
 Table of contents 1. Overview of the 2 Bay NAS...3 1.1 Introduction...3 1.2 System Requirement...3 1.3 Hardware Installation...3 1.4 Setup the client PC and 2 Bay NAS...3 1.4.1 Setup network configuration
Table of contents 1. Overview of the 2 Bay NAS...3 1.1 Introduction...3 1.2 System Requirement...3 1.3 Hardware Installation...3 1.4 Setup the client PC and 2 Bay NAS...3 1.4.1 Setup network configuration
PEAP under Unified Wireless Networks with ACS 5.1 and Windows 2003 Server
 PEAP under Unified Wireless Networks with ACS 5.1 and Windows 2003 Server Document ID: 112175 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Windows
PEAP under Unified Wireless Networks with ACS 5.1 and Windows 2003 Server Document ID: 112175 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Windows
Send the Ctrl-Alt-Delete key sequence to the Guest OS one of two ways: Key sequence: Ctlr-Alt-Ins Menu Sequence: VM / Guest / Send Ctrl-Alt-Delete
 CIS 231 Windows 2008 Server Install Lab #1 (Virtual Machines) Keys to Remember when using the vsphere client. Send the Ctrl-Alt-Delete key sequence to the Guest OS one of two ways: Key sequence: Ctlr-Alt-Ins
CIS 231 Windows 2008 Server Install Lab #1 (Virtual Machines) Keys to Remember when using the vsphere client. Send the Ctrl-Alt-Delete key sequence to the Guest OS one of two ways: Key sequence: Ctlr-Alt-Ins
CTECS Connect 2.2 Release Notes December 10, 2009
 (Formerly VTECS) CTECS Connect 2.2 Release Notes December 10, 2009 This document contains information that supplements the CTECS Connect 2.2 documentation. Please visit the CTECS Connect Support area of
(Formerly VTECS) CTECS Connect 2.2 Release Notes December 10, 2009 This document contains information that supplements the CTECS Connect 2.2 documentation. Please visit the CTECS Connect Support area of
NBC-IG Installation Guide. Version 7.2
 Installation Guide Version 7.2 2017 Nuance Business Connect 7.2 Installation Guide Document Revision History Revision Date August 8, 2017 Revision List Updated supported SQL Server versions June 14, 2017
Installation Guide Version 7.2 2017 Nuance Business Connect 7.2 Installation Guide Document Revision History Revision Date August 8, 2017 Revision List Updated supported SQL Server versions June 14, 2017
Storage Manager 2018 R1. Installation Guide
 Storage Manager 2018 R1 Installation Guide Notes, Cautions, and Warnings NOTE: A NOTE indicates important information that helps you make better use of your product. CAUTION: A CAUTION indicates either
Storage Manager 2018 R1 Installation Guide Notes, Cautions, and Warnings NOTE: A NOTE indicates important information that helps you make better use of your product. CAUTION: A CAUTION indicates either
VMware ESX ESXi and vsphere. Installation Guide
 VMware ESX ESXi and vsphere Installation Guide UPDATED: 28 March 2018 Copyright Notices Copyright 2002-2018 KEMP Technologies, Inc. All rights reserved. KEMP Technologies and the KEMP Technologies logo
VMware ESX ESXi and vsphere Installation Guide UPDATED: 28 March 2018 Copyright Notices Copyright 2002-2018 KEMP Technologies, Inc. All rights reserved. KEMP Technologies and the KEMP Technologies logo
Building a 64-bit CentOS 7 Workstation using Oracle Virtual Box
 Building a 64-bit CentOS 7 Workstation using Oracle Virtual Box jthomas Enterprises, 2016 Building a CentOS 7 Workstation using Oracle VirtualBox 1 Section 1 Before You Begin This section details the environment
Building a 64-bit CentOS 7 Workstation using Oracle Virtual Box jthomas Enterprises, 2016 Building a CentOS 7 Workstation using Oracle VirtualBox 1 Section 1 Before You Begin This section details the environment
Getting Started Guide. Installation and Setup Instructions. For version Copyright 2009 Code 42 Software, Inc. All rights reserved
 Installation and Setup Instructions For version 06.11.2009 Copyright 2009 Code 42 Software, Inc. All rights reserved About This Guide This guide shows you how to install, activate and back up with CrashPlan
Installation and Setup Instructions For version 06.11.2009 Copyright 2009 Code 42 Software, Inc. All rights reserved About This Guide This guide shows you how to install, activate and back up with CrashPlan
IT 341 Introduction to System Administration Project I Installing Ubuntu Server on a Virtual Machine
 IT 341 Introduction to System Administration Project I Installing Ubuntu Server on a Virtual Machine Here we create a new virtual machine and install Ubuntu 16.04 LTS Server on it. In this instance, we
IT 341 Introduction to System Administration Project I Installing Ubuntu Server on a Virtual Machine Here we create a new virtual machine and install Ubuntu 16.04 LTS Server on it. In this instance, we
Lab 2: Creating Secure Architectures
 Lab 2: Creating Secure Architectures A Challenge Our challenge is to setup MyBank Incorp, where each of you will be allocated a network and hosts to configure and get on-line (Figure 1). For this you will
Lab 2: Creating Secure Architectures A Challenge Our challenge is to setup MyBank Incorp, where each of you will be allocated a network and hosts to configure and get on-line (Figure 1). For this you will
Understanding UCS Server Configuration Utility User Interface
 CHAPTER 3 Understanding UCS Server Configuration Utility User Interface The UCS-SCU GUI is a web-based management interface that allows you to perform tasks such as operating system installation, RAID
CHAPTER 3 Understanding UCS Server Configuration Utility User Interface The UCS-SCU GUI is a web-based management interface that allows you to perform tasks such as operating system installation, RAID
Configuring the SMA 500v Virtual Appliance
 Using the SMA 500v Virtual Appliance Configuring the SMA 500v Virtual Appliance Registering Your Appliance Using the 30-day Trial Version Upgrading Your Appliance Configuring the SMA 500v Virtual Appliance
Using the SMA 500v Virtual Appliance Configuring the SMA 500v Virtual Appliance Registering Your Appliance Using the 30-day Trial Version Upgrading Your Appliance Configuring the SMA 500v Virtual Appliance
DS2 Support. DS2 / inet System Installation Scenario 2. Scenario 1: - Windows 2003 Server - Utilizing an External SQL Server
 DS2 Support DS2 / inet System Installation Scenario 2 Scenario 1: - Windows 2003 Server - Utilizing an External SQL Server Author: Jason May Revision 8.0 Revision Date 03/2009 Overview The purpose of this
DS2 Support DS2 / inet System Installation Scenario 2 Scenario 1: - Windows 2003 Server - Utilizing an External SQL Server Author: Jason May Revision 8.0 Revision Date 03/2009 Overview The purpose of this
CompTIA Network+ Lab Series Network Concepts. Lab 3: TCP/IP Utilities
 CompTIA Network+ Lab Series Network Concepts Lab 3: TCP/IP Utilities Objective 1.5: Identify common TCP and UDP default ports Objective 1.6: Explain the function of common networking protocols Objective
CompTIA Network+ Lab Series Network Concepts Lab 3: TCP/IP Utilities Objective 1.5: Identify common TCP and UDP default ports Objective 1.6: Explain the function of common networking protocols Objective
Lab - Configure Wireless Router in Windows
 Introduction In this lab, you will configure and test the wireless settings on a wireless router. Recommended Equipment A computer with Windows installed A Wireless NIC installed An Ethernet NIC installed
Introduction In this lab, you will configure and test the wireless settings on a wireless router. Recommended Equipment A computer with Windows installed A Wireless NIC installed An Ethernet NIC installed
Procedure for SAP IDES 4.7 Install on Win 2003 Server /Windows XP
 1 Procedure for SAP IDES 4.7 Install on Win 2003 Server /Windows XP System Requirements. P-III System or Higher 1024 MB or Higher C:\ - 10GB - Windows 2000 Server/ Win XP - NTFS D:\ - 60GB - Oracle & SAP
1 Procedure for SAP IDES 4.7 Install on Win 2003 Server /Windows XP System Requirements. P-III System or Higher 1024 MB or Higher C:\ - 10GB - Windows 2000 Server/ Win XP - NTFS D:\ - 60GB - Oracle & SAP
Lab Determining Data Storage Capacity
 Lab 1.3.2 Determining Data Storage Capacity Objectives Determine the amount of RAM (in MB) installed in a PC. Determine the size of the hard disk drive (in GB) installed in a PC. Determine the used and
Lab 1.3.2 Determining Data Storage Capacity Objectives Determine the amount of RAM (in MB) installed in a PC. Determine the size of the hard disk drive (in GB) installed in a PC. Determine the used and
SWP-0036 AFHCAN Telehealth Cart Imaging and Software Configuration. Revision: 1. Effective Date: 1/4/2011
 Software Procedure SWP-0036 AFHCAN Telehealth Cart Imaging and Software Configuration Revision: 1 Effective Date: 1/4/2011 Alaska Native Tribal Health Consortium Division of Health Information & Technology
Software Procedure SWP-0036 AFHCAN Telehealth Cart Imaging and Software Configuration Revision: 1 Effective Date: 1/4/2011 Alaska Native Tribal Health Consortium Division of Health Information & Technology
SUSE Cloud Admin Appliance Walk Through. You may download the SUSE Cloud Admin Appliance the following ways.
 SUSE Cloud Admin Appliance Walk Through First before you proceed with deploying the Admin Appliance you must go through and answer the questionnaire to ensure you have an idea of the scope of the project
SUSE Cloud Admin Appliance Walk Through First before you proceed with deploying the Admin Appliance you must go through and answer the questionnaire to ensure you have an idea of the scope of the project
CIS 76 VLab Pod Setup
 CIS 76 VLab Pod Setup Last updated 11/30/2016 Status on setup instructions: 1. pfsense (2.3, 64 bit) - OK 2. Kali (2016, 64 bit) - OK 3. Windows XP (SP2, 32 bit) - OK 4. Port Forwarding - OK 5. OWASP_Broken_Web_Apps_VM_1.2
CIS 76 VLab Pod Setup Last updated 11/30/2016 Status on setup instructions: 1. pfsense (2.3, 64 bit) - OK 2. Kali (2016, 64 bit) - OK 3. Windows XP (SP2, 32 bit) - OK 4. Port Forwarding - OK 5. OWASP_Broken_Web_Apps_VM_1.2
PROBE INSTALLATION AND CONFIGURATION GUIDE RELEASE 5.1
 PROBE INSTALLATION AND CONFIGURATION GUIDE RELEASE 5.1 DOCUMENT DATE: NOVEMBER 20, 2015 Introduction Notice The information contained in this document is believed to be accurate in all respects but is
PROBE INSTALLATION AND CONFIGURATION GUIDE RELEASE 5.1 DOCUMENT DATE: NOVEMBER 20, 2015 Introduction Notice The information contained in this document is believed to be accurate in all respects but is
CommandCenter Secure Gateway
 CommandCenter Secure Gateway Quick Setup Guide for CC-SG Virtual Appliance and lmadmin License Server Management This Quick Setup Guide explains how to install and configure the CommandCenter Secure Gateway.
CommandCenter Secure Gateway Quick Setup Guide for CC-SG Virtual Appliance and lmadmin License Server Management This Quick Setup Guide explains how to install and configure the CommandCenter Secure Gateway.
Bridge Cable User s Guide
 Bridge Cable User s Guide Table of Contents Overview -------------------------------------------------------------------- 2 Driver Installation --------------------------------------------------------
Bridge Cable User s Guide Table of Contents Overview -------------------------------------------------------------------- 2 Driver Installation --------------------------------------------------------
How to securely isolate Damn Vulnerable Linux with VirtualBox
 How to securely isolate Damn Vulnerable Linux with VirtualBox Motivation I have this vision of going through and testing software inside of a closed lab that allows me to understand exploits and vulnerabilities
How to securely isolate Damn Vulnerable Linux with VirtualBox Motivation I have this vision of going through and testing software inside of a closed lab that allows me to understand exploits and vulnerabilities
