Authentication is not limited to the workstation logon but it supports also Remote Desktop, Shares, Hyper-V Sessions, etc.
|
|
|
- Hector Little
- 6 years ago
- Views:
Transcription
1 Aloaha Smartlogin Aloaha Smartlogin allows you to logon to your windows machine with a Smart Card, PKCS #11 Token, USB Memory Stick or just a plain Memory Card such as I2c or Mifare. Authentication is not limited to the workstation logon but it supports also Remote Desktop, Shares, Hyper-V Sessions, etc. Contents Features... 3 Requirements... 3 Installation... 3 Logon Types... 4 Smart Card with any certificate loaded... 5 Automatic updating of Softtoken... 7 Sharing of Softtoken via Network Share... 7 Sharing of Softtoken via Active Directory... 8 PKCS #11 Token Plain USB Memory Stick UserPass.ini Settings Hide Username Field Aloaha Credential Provider Filter Card Removal Action ForceCRLChecks Emergency Logon Registry Settings Checking of Certificate Revocation Lists Enable/Disable CRL checking CRL checking parameter Windows XP/2003 and GINA SSO for legacy applications Single Sign-On for Web Applications Other useful applications AloahaZIP PDFCrypter.NET... 16
2 16 Aloaha Crypt Disk This document is included in the setup package. An updated version is always available at: The German version can be found at: Aloaha Smartlogin Blog:
3 Features Supports full Kerberos authentication (Active Directory required) Smart Card Logon even WITHOUT Active Directory possible. No special requirements for the Logon Certificate. Besides Smart Cards, Aloaha also supports other login tokens such as USB Memory Sticks, Memory Cards and PKCS #11 1 Tokens. Logon to network shares, remote desktop sessions, Hyper-V Consoles, etc. are also supported. Network Level Authentication (NLA) and Credential Security Support Provider (CredSSP) supported. Smart Card Logon also for legacy applications (SSO) MSI based installer available. Requirements Windows XP (Logon via GINA) Any other Windows from Vista onwards and incl. Windows 8/8.1. Both 32 and 64 Bit..NET 3.5 Framework installed Active Directory supported but NOT REQUIRED Installed Middleware 2 for Smart Card(s). Installation To install Aloaha you need to download the setup package from The MSI setup is wrapped into an executable. In case you require the plain MSI for your software management you can extract it from the exe OR request it from info@aloaha.com. Please call the setup smartlogin.exe with administrator rights. Ideally you launch the setup with a right mouse click -> Run as Administrator. In case you do not own a valid license key please request an evaluation key from info@aloaha.com. You need to make sure that the driver/middleware for your smart card is installed. If you do not have any driver/middleware for your smart card OR you are using the Aloaha Card, you can use the Aloaha Cardconnector as your middleware. It currently supports more than 45 different smart cards. Aloaha Cardconnector can be installed from: 1 Please make sure you install the PKCS #11 Library of your token. 2 The Aloaha Cardconnector Middleware supports more than 45 different Smart Cards. In case you do not have a middleware for your smart card or you are using the Aloaha Card please install the Aloaha Cardconnector from
4 Logon Types The following logon tokens are supported: 1. Smart Card with any certificate loaded. This is the most common used configuration since it does NOT require the certificate issued by a Domain Certification Authority. Active Directory is supported but not required PKCS #11 Token 3. Plain USB Memory Stick 4. Kerberos
5 Smart Card with any certificate loaded If you use a smart card, you need to link the Chipcard Certificate with the credentials. To do so please call Encrypt Credentials from the Windows Start Menu OR Card Credentials from the Aloaha System Tray Menu. The following dialog will open: You need to type in your windows password, choose the smart card to be used and click Set Credentials. A Softtoken will be created and saved to <Installdir>\CredentialStore. That Token contains some settings, the public part of the card certificate and a smart card encrypted secret. ONLY the private key of the chip card is able to decrypt this secret! Now you are already able to logon with your card to your windows system. In some cases it might be required that you need to assign a smart card to a different user than suggested. In that case please start SmartLogin_SetCredentials.exe with the parameter /e from the Aloaha installation folder. The tool will allow you then to edit all fields as shown below:
6 Alternatively, you can use the tool SetCredentials.exe from the installation folder. That tool also allows you to verify the smart card assignment(s):
7 Automatic updating of Softtoken The Softtoken Files need to be updated as soon the assigned user changes the password. With the password hook that can be carried out fully automatic. The password hook needs to be activated on the machine were the password is physically stored. In a domain that is the domain controller. Local Users are stored always on the local machine. To install and activate the hook please make sure that Smartlogin is installed. You will find the tool PasswdHK.exe in <InstallDir>\PasswdHK.exe Call the tool with right click -> Run as Administrator. Choose the tab Activate Password Hook as shown below: Now please press Enable and reboot the machine to activate the hook. Whenever a user now changes the password the Softtoken will automatically updated. Sharing of Softtoken via Network Share It is possible to change the location of the Softtoken. Per default it is <Installdir>\CredentialStore. You can change that location in the registry in HKLM\SOFTWARE\<Wow6432Node>\Aloaha\CSP\ CredentialStore and point it to a network share. But please keep in mind that the logon process is running under local system credentials and thus the share needs to give local system the required permissions.
8 Sharing of Softtoken via Active Directory In case your machines are part of an Active Directory Domain it is suggested to roam the token via AD. Aloaha is using a dedicated Active Directory Application Partition to store its data. To create the partition please follow the steps below: 1. Make sure you are logged on with a user with Schema-Admin rights 2. Create the value ForceCreate in HKLM\SOFTWARE\<Wow6432Node>\Aloaha\AD and assign the value Download and run AloahaADSI from: 4. Choose the Settings tab and fill in your Schema-Admin Username and Password and click Save. The Password fields will show empty after the save. 5. Open the Schema Tab and press Create Schema. You should see the output as in the screenshot below if everything was created properly.
9 6. Quit the tool and delete HKLM\SOFTWARE\<Wow6432Node>\Aloaha\AD\ForceCreate to hide the Schema Tab. You created now the required Application Partition to share your Softtoken across the domain. Now you need to enable sharing on EVERY client machine with setting the value enabled to 1 in HKLM\SOFTWARE\<Wow6432Node>\Aloaha\AD (please create if not exist)
10 PKCS #11 Token If you opt to use a PKCS #11 Token to logon to your machine, your credentials will be saved encrypted on the token itself. It is essential that you make sure that the PKCS #11 Library of your token is installed! To save your credentials on your token please start PKCS #11 Credentials from the Windows start menu or Aloaha System tray. 1. Choose your vendors PKCS #11 Library 2. Now your token should be listed. Please choose the token to be used. 3. Enter <domain>\user and Password. 4. Press Save to save the encrypted credentials to your token. Click Validate to simulate a logon.
11 Plain USB Memory Stick It is also possible to use a plain USB Memory Stick as a logon token. Your credentials will be saved encrypted on the portable memory. Please note that USB Memory Sticks are LESS secure than real smart cards since they do not use a dedicated crypto processor! You need to supply the USB drive letter, your username, optional your domain and the windows password. It is also essential that you define a USB PIN. That USB PIN will be later on your logon PIN. The PIN will also form part of the credential encryption key.
12 UserPass.ini Settings Hide Username Field The Username field of the logon tile can be left empty. Aloaha will then try to guess the right username based on the certificate of the card. You can also disable and hide the username field. <Installdir>UserPass.ini [Generic] DisableUserName=0 EnableUserName=1 [Generic] DisableUserName=1 EnableUserName=0 Aloaha Credential Provider Filter It is possible to hide any Logon Tile via the Aloaha Credential Provider Filter: In some cases Credential Providers should be hidden from the Logon User Interface BUT still usable from within the session. For example someone might not want to see the Username/Password Tile during logon but obviously still requires it when mounting a network drive or connecting via RDP to another machine. In that case you cannot hide/disable the providers via windows group policy but a Credential Provider Filter is required. Aloaha Smartlogin comes with an integrated Credential Provider Filter to be able to hide Tiles from the Windows Logon Interface WITHOUT removing its functionality inside the session. To activate the Aloaha Credential Provider Filter you need to open the file UserPass.ini in the installation folder. In the section CredentialProviders you can configure different filter for different provider. To enable a filter please set it to 1. Set all the keys as shown below in order to disable ALL non-aloaha CredentialProviders: [CredentialProviders] 25CBB996-92ED-457e-B28C BD562=1 3dd6bec ffe-ae25-e08e39ea4063= d0-4c5e-4cfd-b3ba-d881334f0df2=1 6f45dc1e a-bc13-2cd81b0d28ed=1 8bf9a910-a8ff-457f-999f-a5ca10b4a885=1
13 94596c7e ce-893e-bbf09122f76a=1 AC3AC249-E A65B-377AC634DC09=1 e74e57b0-6c6d-44d5-9cda-fb2df5ed7435=1 F8A0B131-5F68-486c E8FC3C85BB6=1 Card Removal Action Per default Aloaha reads the Machines or Domains Card Removal policy. It can be fine-tuned and overwritten with: [AutoLock] PolicyAction=1 RemoveActionM=1 Furthermore you need to set HKLM\Software\Aloaha\CSP\RemoveAction=1 1 = Lock Screen, 2 = Lock Off, 3 = Reboot ForceCRLChecks [Generic] ForceCRLChecks=1 This if this key is set to 1 it enforces CRL Checking. If this key is set to 1 it CANNOT be deactivated with any other CRL setting. Emergency Logon [Generic] AllowUP=1 If AllowUP is activated (default) the user can logon to the machine if he knows the valid user password. He has to add up: for username/password to his username and enter the password instead of the PIN. For example instead of entering JohnDoe into the Username field you would enter up:johndoe Instead of the PIN 0815 you would enter his password LetMeIn If this emergency logon is NOT required please deactivate it! Registry Settings Checking of Certificate Revocation Lists If you have a fresh install of Aloaha Smart Login it will make only very basic checks on the certificate used. Revocation lists will NOT be used. There are several reasons why revocation checking is disabled by default: 1. When evaluating Aloaha customer usually use test certificates without any valid CA behind. Checks would fail in that case and the customer might not be able to log on by smart card.
14 2. In case a user reports his smart card as lost the admin could just delete the softtoken to block the lost smart card. The same effect would have been a change of the user s password. That would lock out immediately the lost smart card but would still allow the user to logon with his new smart card and certificate. The second point shows that revocation lists are just an extra layer of security but they are not really required. Even without revocation lists cards can be blocked. Enable/Disable CRL checking With the key HKLM\SOFTWARE\<Wow6432Node>\Aloaha\CSP\CertificateAlwaysValid the user can enable or disable the CRL checking. Default is disabled. CRL checking parameter Only certificates chaining up to the root are valid: HKLM\<Wow6432Node>\Software\Aloaha\CSP\EnforceChain HKLM\<Wow6432Node>\Software\Aloaha\CSP\ ForceCRLChecks See also in Chapter: ForceCRLChecks Define CRL Type: HKLM\<Wow6432Node>\Software\Aloaha\CSP\ForceCRL HKLM\<Wow6432Node>\Software\Aloaha\CSP\offCRL HKLM\<Wow6432Node>\Software\Aloaha\CSP\onlCRL HKLM\<Wow6432Node>\Software\Aloaha\CSP\ForceOCSP Consider unknown status as valid: HKLM\<Wow6432Node>\Software\Aloaha\CSP\UnknownCertStatusIsValid Accept expired certificates: HKLM\<Wow6432Node>\Software\Aloaha\CSP\IgnoreCertTime Windows XP/2003 and GINA On Windows XP/2003 Aloaha will install a GINA dll instead of the credential provider. In some cases it might be required to deactivate or remove the GINA. In that case you need to remove GinaDLL from HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion.
15 SSO for legacy applications Please read the following documentation: PDF: DOCX: Single Sign-On for Web Applications PDF: DOCX: Other useful applications Aloaha offers a couple of small and portable applications for Aloaha user. AloahaZIP With AloahaZIP you can certificate encrypt your ZIP documents:
16 PDFCrypter.NET With the PDFCrypter.NET you can encrypt your PDF documents with a password or certificates: Create digital certificates To create quickly exportable or non-exportable certificates please use the following tool: Aloaha Crypt Disk With Aloaha Crypt Disk you can create a certificate or smart card encrypted drive container:
Aloaha Smartlogin allows you to logon to your windows machine with a Smart Card, PKCS #11 Token or USB Memory Stick.
 Aloaha Smartlogin Aloaha Smartlogin allows you to logon to your windows machine with a Smart Card, PKCS #11 Token or USB Memory Stick. Aloaha even supports plain and simple cards such as MIFARE, I2C or
Aloaha Smartlogin Aloaha Smartlogin allows you to logon to your windows machine with a Smart Card, PKCS #11 Token or USB Memory Stick. Aloaha even supports plain and simple cards such as MIFARE, I2C or
SafeGuard LAN Crypt: Loading Profile Troubleshooting Guide
 1 Troubleshooting Guide SafeGuard LAN Crypt: Loading Profile Troubleshooting Guide Document date: 26/11/2014 Contents 1 Introduction... 4 2 SafeGuard LAN Crypt User application... 4 3 Loading the user
1 Troubleshooting Guide SafeGuard LAN Crypt: Loading Profile Troubleshooting Guide Document date: 26/11/2014 Contents 1 Introduction... 4 2 SafeGuard LAN Crypt User application... 4 3 Loading the user
Getting started with ActiveSecurity MyLogin
 1 (5) Getting started with ActiveSecurity MyLogin 1 Introduction This document contains instructions for starting to use Aventra s ActiveSecurity MyLogin software and explanations of the basic settings.
1 (5) Getting started with ActiveSecurity MyLogin 1 Introduction This document contains instructions for starting to use Aventra s ActiveSecurity MyLogin software and explanations of the basic settings.
SecureDoc Disk Encryption Cryptographic Engine
 SecureDoc Disk Encryption Cryptographic Engine Security Policy Abstract: This document specifies Security Policy enforced by the SecureDoc Cryptographic Engine compliant with the requirements of FIPS 140-2
SecureDoc Disk Encryption Cryptographic Engine Security Policy Abstract: This document specifies Security Policy enforced by the SecureDoc Cryptographic Engine compliant with the requirements of FIPS 140-2
MANAGING LOCAL AUTHENTICATION IN WINDOWS
 MANAGING LOCAL AUTHENTICATION IN WINDOWS Credentials Manager Windows OS has a set of tools that help remedy some of the authentication challenges. For example, the Credential Manager in Windows 7 and newer
MANAGING LOCAL AUTHENTICATION IN WINDOWS Credentials Manager Windows OS has a set of tools that help remedy some of the authentication challenges. For example, the Credential Manager in Windows 7 and newer
Remote Device Mounting Service
 HOW TO USE REMOTE DEVICE MOUNTING SERVICES The Remote Data Mounting Services (RDMS) lets you acquire live evidence from active and remote network computers. You can gather many types of active information
HOW TO USE REMOTE DEVICE MOUNTING SERVICES The Remote Data Mounting Services (RDMS) lets you acquire live evidence from active and remote network computers. You can gather many types of active information
TFS WorkstationControl White Paper
 White Paper Intelligent Public Key Credential Distribution and Workstation Access Control TFS Technology www.tfstech.com Table of Contents Overview 3 Introduction 3 Important Concepts 4 Logon Modes 4 Password
White Paper Intelligent Public Key Credential Distribution and Workstation Access Control TFS Technology www.tfstech.com Table of Contents Overview 3 Introduction 3 Important Concepts 4 Logon Modes 4 Password
Parallels Remote Application Server
 Parallels Remote Application Server Parallels Client for Windows User's Guide v15.5 Parallels International GmbH Vordergasse 59 8200 Schaffhausen Switzerland Tel: + 41 52 672 20 30 www.parallels.com Copyright
Parallels Remote Application Server Parallels Client for Windows User's Guide v15.5 Parallels International GmbH Vordergasse 59 8200 Schaffhausen Switzerland Tel: + 41 52 672 20 30 www.parallels.com Copyright
McAfee Drive Encryption Interface Reference Guide. (McAfee epolicy Orchestrator)
 McAfee Drive Encryption 7.2.5 Interface Reference Guide (McAfee epolicy Orchestrator) COPYRIGHT Copyright 2018 McAfee, LLC TRADEMARK ATTRIBUTIONS McAfee and the McAfee logo, McAfee Active Protection, epolicy
McAfee Drive Encryption 7.2.5 Interface Reference Guide (McAfee epolicy Orchestrator) COPYRIGHT Copyright 2018 McAfee, LLC TRADEMARK ATTRIBUTIONS McAfee and the McAfee logo, McAfee Active Protection, epolicy
ZENworks 2017 Full Disk Encryption Pre-Boot Authentication Reference. December 2016
 ZENworks 2017 Full Disk Encryption Pre-Boot Authentication Reference December 2016 Legal Notice For information about legal notices, trademarks, disclaimers, warranties, export and other use restrictions,
ZENworks 2017 Full Disk Encryption Pre-Boot Authentication Reference December 2016 Legal Notice For information about legal notices, trademarks, disclaimers, warranties, export and other use restrictions,
2018/5. Ver BthLogon. Windows Logon Authentication using Android Device. RiBiG Inc.
 2018/5 Ver. 1.0 BthLogon Windows Logon Authentication using Android Device RiBiG Inc. http://www.ribig.co.jp/bthlogon Contents 1. Introduction... 4 1.1 Remote Desktop Support... 5 1.2 Security... 6 2.
2018/5 Ver. 1.0 BthLogon Windows Logon Authentication using Android Device RiBiG Inc. http://www.ribig.co.jp/bthlogon Contents 1. Introduction... 4 1.1 Remote Desktop Support... 5 1.2 Security... 6 2.
keyon / PKCS#11 to MS-CAPI Bridge User Guide V2.4
 / PKCS#11 to MS-CAPI Bridge V2.4 April 2017 Table of Contents Copyright 2017 by AG All rights reserved. No part of the contents of this manual may be reproduced or transmitted in any form or by any means
/ PKCS#11 to MS-CAPI Bridge V2.4 April 2017 Table of Contents Copyright 2017 by AG All rights reserved. No part of the contents of this manual may be reproduced or transmitted in any form or by any means
Steganos Safe Professional th June 2007
 Steganos Safe Professional 2007 26 th June 2007 Contents Page Introduction 4 Installation and Deployment 5 Managing and Policies 6 Recovery Using EDK 8 Setting Up Network Shares 8 Creating A Key Pair 8
Steganos Safe Professional 2007 26 th June 2007 Contents Page Introduction 4 Installation and Deployment 5 Managing and Policies 6 Recovery Using EDK 8 Setting Up Network Shares 8 Creating A Key Pair 8
BlackShield ID. Windows Logon Agent CRYPTOCard Corp. All rights reserved.
 Windows Logon Agent 2010 CRYPTOCard Corp. All rights reserved. http:// www.cryptocard.com Copyright Copyright 2010, CRYPTOCard All Rights Reserved. No part of this publication may be reproduced, transmitted,
Windows Logon Agent 2010 CRYPTOCard Corp. All rights reserved. http:// www.cryptocard.com Copyright Copyright 2010, CRYPTOCard All Rights Reserved. No part of this publication may be reproduced, transmitted,
SecuRemote for Windows 32-bit/64-bit
 SecuRemote for Windows 32-bit/64-bit E75.20 User Guide 13 September 2011 2011 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by copyright
SecuRemote for Windows 32-bit/64-bit E75.20 User Guide 13 September 2011 2011 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by copyright
Evaluation Guide Host Access Management and Security Server 12.4 SP1 ( )
 Evaluation Guide Host Access Management and Security Server 12.4 SP1 (12.4.10) Legal Notice For information about legal notices, trademarks, disclaimers, warranties, export and other use restrictions,
Evaluation Guide Host Access Management and Security Server 12.4 SP1 (12.4.10) Legal Notice For information about legal notices, trademarks, disclaimers, warranties, export and other use restrictions,
Fixed issue with Wifi connection. Login would hang for minutes or unlock screen fails.
 VERSION 5.95 BUILD 1299, 4 OCTOBER 2017 ENHANCEMENTS Manually typed keywords by are no longer resolved. VMWare View Java monitor updated to provide more feedback. Java monitor improved to be able to support
VERSION 5.95 BUILD 1299, 4 OCTOBER 2017 ENHANCEMENTS Manually typed keywords by are no longer resolved. VMWare View Java monitor updated to provide more feedback. Java monitor improved to be able to support
Parallels Remote Application Server
 Parallels Remote Application Server Parallels Client for Windows User's Guide v16.1 Parallels International GmbH Vordergasse 59 8200 Schaffhausen Switzerland Tel: + 41 52 672 20 30 www.parallels.com Copyright
Parallels Remote Application Server Parallels Client for Windows User's Guide v16.1 Parallels International GmbH Vordergasse 59 8200 Schaffhausen Switzerland Tel: + 41 52 672 20 30 www.parallels.com Copyright
Copyright 2017 Softerra, Ltd. All rights reserved
 Copyright 2017 Softerra, Ltd. All rights reserved Contents Introduction Security Considerations Installation Configuration Uninstallation Automated Bulk Enrollment Troubleshooting Introduction Adaxes Self-Service
Copyright 2017 Softerra, Ltd. All rights reserved Contents Introduction Security Considerations Installation Configuration Uninstallation Automated Bulk Enrollment Troubleshooting Introduction Adaxes Self-Service
User Profile Manager 2.0
 User Profile Manager 2.0 User Guide ForensiT Limited, 75 Riverside III, Sir Thomas Longley Road, Rochester, Kent, ME2 4BH England. Tel: US 1-877-224-1721 (Toll Free) Intl. +44 (0) 845 838 7122 Fax: +44
User Profile Manager 2.0 User Guide ForensiT Limited, 75 Riverside III, Sir Thomas Longley Road, Rochester, Kent, ME2 4BH England. Tel: US 1-877-224-1721 (Toll Free) Intl. +44 (0) 845 838 7122 Fax: +44
Ekran System v.6.0 Privileged User Accounts and Sessions (PASM)
 Ekran System v.6.0 Privileged User Accounts and Sessions (PASM) Table of Contents About... 3 Using Privileged User Accounts... 4 Password Vault Configuration... 5 Defining Domain Administrator Credentials...
Ekran System v.6.0 Privileged User Accounts and Sessions (PASM) Table of Contents About... 3 Using Privileged User Accounts... 4 Password Vault Configuration... 5 Defining Domain Administrator Credentials...
Check Point GO R75. User Guide. 14 November Classification: [Public]
![Check Point GO R75. User Guide. 14 November Classification: [Public] Check Point GO R75. User Guide. 14 November Classification: [Public]](/thumbs/74/70104753.jpg) Check Point GO R75 User Guide 14 November 2011 Classification: [Public] 2011 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by copyright
Check Point GO R75 User Guide 14 November 2011 Classification: [Public] 2011 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by copyright
Parallels Remote Application Server
 Parallels Remote Application Server Parallels Client for Mac User's Guide v16 Parallels International GmbH Vordergasse 59 8200 Schaffhausen Switzerland Tel: + 41 52 672 20 30 www.parallels.com Copyright
Parallels Remote Application Server Parallels Client for Mac User's Guide v16 Parallels International GmbH Vordergasse 59 8200 Schaffhausen Switzerland Tel: + 41 52 672 20 30 www.parallels.com Copyright
citrix MetaFrame Password Manager2.0:Adminsitration
 citrix MetaFrame Password Manager2.0:Adminsitration Number: 1Y0-972 Passing Score: 800 Time Limit: 120 min File Version: 62.24 http://www.gratisexam.com/ CITRIX 1Y0-972 EXAM QUESTIONS & ANSWERS Exam Name:
citrix MetaFrame Password Manager2.0:Adminsitration Number: 1Y0-972 Passing Score: 800 Time Limit: 120 min File Version: 62.24 http://www.gratisexam.com/ CITRIX 1Y0-972 EXAM QUESTIONS & ANSWERS Exam Name:
29 March 2017 SECURITY SERVER INSTALLATION GUIDE
 29 March 2017 SECURITY SERVER INSTALLATION GUIDE Contents 1. Introduction... 2 1.1 Assumptions... 2 1.2 Prerequisites... 2 2. Required setups prior the Security Server Installation... 3 1.1 Create domain
29 March 2017 SECURITY SERVER INSTALLATION GUIDE Contents 1. Introduction... 2 1.1 Assumptions... 2 1.2 Prerequisites... 2 2. Required setups prior the Security Server Installation... 3 1.1 Create domain
SINGLE SIGN ON. The following document describes the configuration of Single Sign On (SSO) using a Windows 2008 R2 or Windows SBS server.
 SINGLE SIGN ON The following document describes the configuration of Single Sign On (SSO) using a Windows 2008 R2 or Windows SBS server. Content 1 Preconditions... 2 1.1 Required Software... 2 1.2 Required
SINGLE SIGN ON The following document describes the configuration of Single Sign On (SSO) using a Windows 2008 R2 or Windows SBS server. Content 1 Preconditions... 2 1.1 Required Software... 2 1.2 Required
8 MANAGING SHARED FOLDERS & DATA
 MANAGING SHARED FOLDERS & DATA STORAGE.1 Introduction to Windows XP File Structure.1.1 File.1.2 Folder.1.3 Drives.2 Windows XP files and folders Sharing.2.1 Simple File Sharing.2.2 Levels of access to
MANAGING SHARED FOLDERS & DATA STORAGE.1 Introduction to Windows XP File Structure.1.1 File.1.2 Folder.1.3 Drives.2 Windows XP files and folders Sharing.2.1 Simple File Sharing.2.2 Levels of access to
Activant Eagle PA-DSS Implementation Guide
 ACTIVANT EAGLE PA-DSS IMPLEMENTATION GUIDE PA-DSS IMPLEMENTATION GUIDE Activant Eagle PA-DSS Implementation Guide EL2211 This manual contains reference information about software products from Activant
ACTIVANT EAGLE PA-DSS IMPLEMENTATION GUIDE PA-DSS IMPLEMENTATION GUIDE Activant Eagle PA-DSS Implementation Guide EL2211 This manual contains reference information about software products from Activant
PKI Credentialing Handbook
 PKI Credentialing Handbook Contents Introduction...3 Dissecting PKI...4 Components of PKI...6 Digital certificates... 6 Public and private keys... 7 Smart cards... 8 Certificate Authority (CA)... 10 Key
PKI Credentialing Handbook Contents Introduction...3 Dissecting PKI...4 Components of PKI...6 Digital certificates... 6 Public and private keys... 7 Smart cards... 8 Certificate Authority (CA)... 10 Key
New in this Release...3 New in Pointsec Media Encryption New in this Release of Pointsec Media Encryption - MI Client...4
 Release Notes Pointsec Media Encryption - MI Client 2.6 Version B Copyright Pointsec Mobile Technologies AB, 2007, a Check Point Software Techonologies Ltd. company. For full documentation, please see
Release Notes Pointsec Media Encryption - MI Client 2.6 Version B Copyright Pointsec Mobile Technologies AB, 2007, a Check Point Software Techonologies Ltd. company. For full documentation, please see
Odette CA Help File and User Manual
 How to Order and Install Odette Certificates For a German version of this file please follow this link. Odette CA Help File and User Manual 1 Release date 31.05.2016 Contents Preparation for Ordering an
How to Order and Install Odette Certificates For a German version of this file please follow this link. Odette CA Help File and User Manual 1 Release date 31.05.2016 Contents Preparation for Ordering an
Balabit s Privileged Session Management and Remote Desktop Protocol Scenarios
 Balabit s Privileged Session Management and Remote Desktop Protocol Scenarios May 02, 2018 Abstract Common RDP scenarios for Balabit s Privileged Session Management (PSM) Copyright 1996-2018 Balabit, a
Balabit s Privileged Session Management and Remote Desktop Protocol Scenarios May 02, 2018 Abstract Common RDP scenarios for Balabit s Privileged Session Management (PSM) Copyright 1996-2018 Balabit, a
DigitalPersona Pro Enterprise
 DigitalPersona Pro Enterprise Quick Start Guide Version 5 DATA PROTECTION REMOTE ACCESS SECURE COMMUNICATION STRONG AUTHENTICATION ACCESS RECOVERY SINGLE SIGN-ON DigitalPersona Pro Enterprise DigitalPersona
DigitalPersona Pro Enterprise Quick Start Guide Version 5 DATA PROTECTION REMOTE ACCESS SECURE COMMUNICATION STRONG AUTHENTICATION ACCESS RECOVERY SINGLE SIGN-ON DigitalPersona Pro Enterprise DigitalPersona
Copyright Tools4ever B.V. All rights reserved.
 Copyright Tools4ever B.V. All rights reserved. No part of the contents of this user guide may be reproduced or transmitted in any form or by any means without the written permission of Tools4ever. DISCLAIMER
Copyright Tools4ever B.V. All rights reserved. No part of the contents of this user guide may be reproduced or transmitted in any form or by any means without the written permission of Tools4ever. DISCLAIMER
Microsoft Windows GINA login
 Microsoft Windows GINA login Contents 1 Introduction 2 Prerequisites 3 Baseline 4 Architecture 5 Swivel Configuration 5.1 Configure a Swivel Agent 5.2 Create a Third Party Authentication 6 Terminal Services
Microsoft Windows GINA login Contents 1 Introduction 2 Prerequisites 3 Baseline 4 Architecture 5 Swivel Configuration 5.1 Configure a Swivel Agent 5.2 Create a Third Party Authentication 6 Terminal Services
SECUDRIVE USB Office
 SECUDRIVE USB Office User Guide Doc Ver. 3.0.1.383 2013-02-10 Brainzsquare, Inc. Table of Contents 1. Overview... 3 1.1 Features... 3 1.2 Product... 4 1.3 Glossary... 4 2. How to use SECUDRIVE USB Office...
SECUDRIVE USB Office User Guide Doc Ver. 3.0.1.383 2013-02-10 Brainzsquare, Inc. Table of Contents 1. Overview... 3 1.1 Features... 3 1.2 Product... 4 1.3 Glossary... 4 2. How to use SECUDRIVE USB Office...
Salesforce1 Mobile Security White Paper. Revised: April 2014
 Salesforce1 Mobile Security White Paper Revised: April 2014 Table of Contents Introduction Salesforce1 Architecture Overview Authorization and Permissions Communication Security Authentication OAuth Pairing
Salesforce1 Mobile Security White Paper Revised: April 2014 Table of Contents Introduction Salesforce1 Architecture Overview Authorization and Permissions Communication Security Authentication OAuth Pairing
Configuring the Client Adapter through the Windows XP Operating System
 APPENDIX E through the Windows XP Operating System This appendix explains how to configure and use the client adapter with Windows XP. The following topics are covered in this appendix: Overview, page
APPENDIX E through the Windows XP Operating System This appendix explains how to configure and use the client adapter with Windows XP. The following topics are covered in this appendix: Overview, page
Advanced Security Measures for Clients and Servers
 Advanced Security Measures for Clients and Servers Wayne Harris MCSE Senior Consultant Certified Security Solutions Importance of Active Directory Security Active Directory creates a more secure network
Advanced Security Measures for Clients and Servers Wayne Harris MCSE Senior Consultant Certified Security Solutions Importance of Active Directory Security Active Directory creates a more secure network
How to Configure the Barracuda VPN Client for Windows
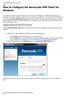 How to Configure the Barracuda VPN Client for Windows Barracuda VPN Control is the user interface of the VPN Client for Windows for configuring VPN profiles and Barracuda VPN adapter settings as well as
How to Configure the Barracuda VPN Client for Windows Barracuda VPN Control is the user interface of the VPN Client for Windows for configuring VPN profiles and Barracuda VPN adapter settings as well as
Sophos Central Device Encryption. Administrator Guide
 Sophos Central Device Encryption Administrator Guide Contents About... 1 Manage BitLocker Drive Encryption... 2 Migrate to...2 Prepare Device Encryption...3 Device Encryption step by step... 3 Device Encryption
Sophos Central Device Encryption Administrator Guide Contents About... 1 Manage BitLocker Drive Encryption... 2 Migrate to...2 Prepare Device Encryption...3 Device Encryption step by step... 3 Device Encryption
System Requirements: -Desktop or laptop computers with USB 1.1 or USB 2.0 port
 Introduction: Thank you for purchasing Axiom's Ultra High Speed E.S.P. Drive (Encryption Software Protection) with 448-Bit Blowfish Encryption Technology making it the best solution for data security on
Introduction: Thank you for purchasing Axiom's Ultra High Speed E.S.P. Drive (Encryption Software Protection) with 448-Bit Blowfish Encryption Technology making it the best solution for data security on
SafeSign Identity Client Standard
 This document contains information of a proprietary nature. No part of this manual may be reproduced or transmitted in any form or by any means electronic, mechanical or otherwise, including photocopying
This document contains information of a proprietary nature. No part of this manual may be reproduced or transmitted in any form or by any means electronic, mechanical or otherwise, including photocopying
Full file at Chapter 2: Securing and Troubleshooting Windows Vista
 Chapter 2: Securing and Troubleshooting Windows Vista TRUE/FALSE 1. An elevated command prompt can only be attained by an administrator after he or she has responded to a UAC box. T PTS: 1 REF: 70 2. There
Chapter 2: Securing and Troubleshooting Windows Vista TRUE/FALSE 1. An elevated command prompt can only be attained by an administrator after he or she has responded to a UAC box. T PTS: 1 REF: 70 2. There
Aventail Connect Client with Smart Tunneling
 Aventail Connect Client with Smart Tunneling User s Guide Windows v8.9.0 1996-2007 Aventail Corporation. All rights reserved. Aventail, Aventail Cache Control, Aventail Connect, Aventail Connect Mobile,
Aventail Connect Client with Smart Tunneling User s Guide Windows v8.9.0 1996-2007 Aventail Corporation. All rights reserved. Aventail, Aventail Cache Control, Aventail Connect, Aventail Connect Mobile,
PGP NetShare Quick Start Guide version 9.6
 PGP NetShare Quick Start Guide version 9. What is PGP NetShare? The PGP NetShare product is a software tool that provides multiple ways to protect and share your data. You can use PGP NetShare to: Let
PGP NetShare Quick Start Guide version 9. What is PGP NetShare? The PGP NetShare product is a software tool that provides multiple ways to protect and share your data. You can use PGP NetShare to: Let
SecurEnvoy Windows Logon Agent Installation and Admin Guide v9.3 Including support for SecurPassword
 SecurEnvoy Windows Logon Agent Installation and Admin Guide v9.3 Including support for SecurPassword SecurEnvoy Windows Logon Agent Guide Contents 1.1 OVERVIEW OF INSTALLATION FILES... 3 SECURENVOY WINDOWS
SecurEnvoy Windows Logon Agent Installation and Admin Guide v9.3 Including support for SecurPassword SecurEnvoy Windows Logon Agent Guide Contents 1.1 OVERVIEW OF INSTALLATION FILES... 3 SECURENVOY WINDOWS
AutoCrypt provides protection of applications without any programming efforts.
 Purpose of Application: Automatic Protection of applications without programming efforts Version: Smarx OS PPK 8.0 and higher Last Update: 31 October 2016 Target Operating Systems: Windows 10/8/7/Vista
Purpose of Application: Automatic Protection of applications without programming efforts Version: Smarx OS PPK 8.0 and higher Last Update: 31 October 2016 Target Operating Systems: Windows 10/8/7/Vista
Endpoint Protection with DigitalPersona Pro
 DigitalPersona Product Brief Endpoint Protection with DigitalPersona Pro An introductory technical overview to DigitalPersona s suite for Access Management, Data Protection and Secure Communication. April
DigitalPersona Product Brief Endpoint Protection with DigitalPersona Pro An introductory technical overview to DigitalPersona s suite for Access Management, Data Protection and Secure Communication. April
SafeGuard Enterprise Installation manual
 Professional IT-Security for your Corporation SafeGuard Enterprise Installation manual Version 5.40 Document date: July 2009 Contents CHAPTER 1 SafeGuard Enterprise Overview... 1 CHAPTER 2 SafeGuard Enterprise
Professional IT-Security for your Corporation SafeGuard Enterprise Installation manual Version 5.40 Document date: July 2009 Contents CHAPTER 1 SafeGuard Enterprise Overview... 1 CHAPTER 2 SafeGuard Enterprise
This PDF Document was generated for free by the Aloaha PDF Suite If you want to learn how to make your own PDF Documents visit:
 INSTALLING AND CONFIGURING A WINDOWS SERVER 2003 ENTERPRISE CERTIFICATION AUTHORITY Certification Authorities can issue certificates to users and computers for a variety of purposes. In the context of
INSTALLING AND CONFIGURING A WINDOWS SERVER 2003 ENTERPRISE CERTIFICATION AUTHORITY Certification Authorities can issue certificates to users and computers for a variety of purposes. In the context of
User Manual v
 DUSK-USB Encryption User Manual v. 16.9.5.0 Introduction... 3 What s New... 3 Operating Systems (OS)... 3 OS Change... 3 DeltaCrypt Upgrades... 3 Upward Compatibility... 3 Installation & Registration (if
DUSK-USB Encryption User Manual v. 16.9.5.0 Introduction... 3 What s New... 3 Operating Systems (OS)... 3 OS Change... 3 DeltaCrypt Upgrades... 3 Upward Compatibility... 3 Installation & Registration (if
IMPLEMENTING SINGLE SIGN-ON (SSO) TO KERBEROS CONSTRAINED DELEGATION AND HEADER-BASED APPS. VMware Identity Manager.
 IMPLEMENTING SINGLE SIGN-ON (SSO) TO KERBEROS CONSTRAINED DELEGATION AND HEADER-BASED APPS VMware Identity Manager February 2017 V1 1 2 Table of Contents Overview... 5 Benefits of BIG-IP APM and Identity
IMPLEMENTING SINGLE SIGN-ON (SSO) TO KERBEROS CONSTRAINED DELEGATION AND HEADER-BASED APPS VMware Identity Manager February 2017 V1 1 2 Table of Contents Overview... 5 Benefits of BIG-IP APM and Identity
COMPUTER BASICS LESSON 4 COMPUTER OPERATION SYSTEMS. Edited by C. 1Rhodes 9/11
 COMPUTER BASICS LESSON 4 COMPUTER OPERATION SYSTEMS Edited by C. 1Rhodes 9/11 ESSENTIAL STANDARD Computer Basics ESSENTIAL QUESTIONS What are the parts and features of a computer? What are the functions
COMPUTER BASICS LESSON 4 COMPUTER OPERATION SYSTEMS Edited by C. 1Rhodes 9/11 ESSENTIAL STANDARD Computer Basics ESSENTIAL QUESTIONS What are the parts and features of a computer? What are the functions
Exchange Protection Whitepaper
 Whitepaper Contents 1. 2. 3. 4. 5. 6. 7. 8. 9. 10. Introduction... 2 Documentation... 2 Licensing... 2 Exchange Server Protection overview... 3 Supported platforms... 3 Requirements by platform... 3 Remote
Whitepaper Contents 1. 2. 3. 4. 5. 6. 7. 8. 9. 10. Introduction... 2 Documentation... 2 Licensing... 2 Exchange Server Protection overview... 3 Supported platforms... 3 Requirements by platform... 3 Remote
Sphinx Feature List. Summary. Windows Logon Features. Card-secured logon to Windows. End-user managed Windows logon data
 Sphinx List Summary Version Order # Included software components Sphinx Enterprise S-30 Install Sphinx Logon Manager software and desktop card readers on end-user computers. Pre-configured Sphinx CardMaker
Sphinx List Summary Version Order # Included software components Sphinx Enterprise S-30 Install Sphinx Logon Manager software and desktop card readers on end-user computers. Pre-configured Sphinx CardMaker
visionapp Remote Desktop (vrd)
 visionapp Remote Desktop () Version Overview Product Information www..com visionapp Remote Desktop at a Glance visionapp Remote Desktop is a powerful tool for managing and accessing multiple servers and
visionapp Remote Desktop () Version Overview Product Information www..com visionapp Remote Desktop at a Glance visionapp Remote Desktop is a powerful tool for managing and accessing multiple servers and
MAGNUM-SDVN Security Administration Manual
 MAGNUM-SDVN Security Administration Manual Revision 19: November 21, 2017 Contents Overview... 3 Administrative Access... 4 Logging Into Terminal Locally... 4 Logging Out Of Local Terminal... 4 Logging
MAGNUM-SDVN Security Administration Manual Revision 19: November 21, 2017 Contents Overview... 3 Administrative Access... 4 Logging Into Terminal Locally... 4 Logging Out Of Local Terminal... 4 Logging
Release Notes. Accops HyWorks SSO Client Release. HyWorks SSO Client v
 Release Notes Accops HyWorks SSO Client Release HyWorks SSO Client v3.1.1.160 Last Updated: 31 May 2018 Copyright 2018, Accops Systems Private Limited. All Rights Reserved. The information contained in
Release Notes Accops HyWorks SSO Client Release HyWorks SSO Client v3.1.1.160 Last Updated: 31 May 2018 Copyright 2018, Accops Systems Private Limited. All Rights Reserved. The information contained in
STRS OHIO F5 Access Client Setup for ChromeBook Systems User Guide
 STRS OHIO F5 Access Client Setup for ChromeBook Systems User Guide For assistance, please contact the ITS Service Desk at x4357 or 227-8633. Table of Contents First Time Use of Remote Access... 1 F5 Access
STRS OHIO F5 Access Client Setup for ChromeBook Systems User Guide For assistance, please contact the ITS Service Desk at x4357 or 227-8633. Table of Contents First Time Use of Remote Access... 1 F5 Access
CS530 Authentication
 CS530 Authentication Bill Cheng http://merlot.usc.edu/cs530-s10 1 Identification vs. Authentication Identification associating an identity (or a claimed identity) with an individual, process, or request
CS530 Authentication Bill Cheng http://merlot.usc.edu/cs530-s10 1 Identification vs. Authentication Identification associating an identity (or a claimed identity) with an individual, process, or request
Public Key Enabling Oracle Weblogic Server
 DoD Public Key Enablement (PKE) Reference Guide Public Key Enabling Oracle Weblogic Server Contact: dodpke@mail.mil URL: http://iase.disa.mil/pki-pke URL: http://iase.disa.smil.mil/pki-pke Public Key Enabling
DoD Public Key Enablement (PKE) Reference Guide Public Key Enabling Oracle Weblogic Server Contact: dodpke@mail.mil URL: http://iase.disa.mil/pki-pke URL: http://iase.disa.smil.mil/pki-pke Public Key Enabling
Aloaha FindMail.
 Aloaha FindMail.eMail Aloaha FindMail.eMail is an email archiving solution that can archive inbound-, internal and outbound emails directly and transparently into a central mailstore. Additionally emails
Aloaha FindMail.eMail Aloaha FindMail.eMail is an email archiving solution that can archive inbound-, internal and outbound emails directly and transparently into a central mailstore. Additionally emails
User Guide. Version R92. English
 AuthAnvil User Guide Version R92 English October 9, 2015 Agreement The purchase and use of all Software and Services is subject to the Agreement as defined in Kaseya s Click-Accept EULATOS as updated from
AuthAnvil User Guide Version R92 English October 9, 2015 Agreement The purchase and use of all Software and Services is subject to the Agreement as defined in Kaseya s Click-Accept EULATOS as updated from
G/On. G/On is available for Windows, MacOS and Linux (selected distributions).
 G/On Soliton G/On is a remote access solution which establishes connections between a remote device and application servers inside an organisations network. A secure gateway is used to separate the remote
G/On Soliton G/On is a remote access solution which establishes connections between a remote device and application servers inside an organisations network. A secure gateway is used to separate the remote
DoD Common Access Card Authentication. Feature Description
 DoD Common Access Card Authentication Feature Description UPDATED: 20 June 2018 Copyright Notices Copyright 2002-2018 KEMP Technologies, Inc. All rights reserved. KEMP Technologies and the KEMP Technologies
DoD Common Access Card Authentication Feature Description UPDATED: 20 June 2018 Copyright Notices Copyright 2002-2018 KEMP Technologies, Inc. All rights reserved. KEMP Technologies and the KEMP Technologies
SPNEGO SINGLE SIGN-ON USING SECURE LOGIN SERVER X.509 CLIENT CERTIFICATES
 SPNEGO SINGLE SIGN-ON USING SECURE LOGIN SERVER X.509 CLIENT CERTIFICATES TABLE OF CONTENTS SCENARIO... 2 IMPLEMENTATION STEPS... 2 PREREQUISITES... 3 1. CONFIGURE ADMINISTRATOR FOR THE SECURE LOGIN ADMINISTRATION
SPNEGO SINGLE SIGN-ON USING SECURE LOGIN SERVER X.509 CLIENT CERTIFICATES TABLE OF CONTENTS SCENARIO... 2 IMPLEMENTATION STEPS... 2 PREREQUISITES... 3 1. CONFIGURE ADMINISTRATOR FOR THE SECURE LOGIN ADMINISTRATION
Login Defender. Quick Guide. Copyright by Cryptware di Ugo Chirico
 Login Defender Quick Guide Copyright 2006-2012 by Cryptware di Ugo Chirico Cryptware - http://www.cryptware.it 5/12/2012 Index 1 Introduction... 3 1.1 Main features... 3 2 Installation... 3 3 Control Panel...
Login Defender Quick Guide Copyright 2006-2012 by Cryptware di Ugo Chirico Cryptware - http://www.cryptware.it 5/12/2012 Index 1 Introduction... 3 1.1 Main features... 3 2 Installation... 3 3 Control Panel...
Table of Contents. Table of Figures. 2 Wave Systems Corp. Client User Guide
 2 Wave Systems Corp. Client User Guide Table of Contents Overview... 3 What is the Trusted Drive Manager?... 3 Key Features of Trusted Drive Manager... 3 Getting Started... 4 Required Components... 4 Configure
2 Wave Systems Corp. Client User Guide Table of Contents Overview... 3 What is the Trusted Drive Manager?... 3 Key Features of Trusted Drive Manager... 3 Getting Started... 4 Required Components... 4 Configure
Product Documentation
 Product Documentation Configuring VMware View Virtual Desktops Imprivata OneSign 5.5 SP1 Imprivata Confirm ID 5.5 SP1 2018 Imprivata, Inc. All Rights Reserved. This document includes information about
Product Documentation Configuring VMware View Virtual Desktops Imprivata OneSign 5.5 SP1 Imprivata Confirm ID 5.5 SP1 2018 Imprivata, Inc. All Rights Reserved. This document includes information about
Instructions for connecting to the FDIBA Wireless Network. (Windows XP)
 Instructions for connecting to the FDIBA Wireless Network (Windows XP) In order to connect, you need your username and password, as well as the FDIBA Root Certificate which you need to install on your
Instructions for connecting to the FDIBA Wireless Network (Windows XP) In order to connect, you need your username and password, as well as the FDIBA Root Certificate which you need to install on your
Installation and configuration guide
 Winfrasoft HAS Installation and Configuration Guide Installation and configuration guide Winfrasoft HAS for Microsoft Forefront UAG 2010 Published: October 2011 Applies to: Winfrasoft HAS (Build 2.0.2300.4)
Winfrasoft HAS Installation and Configuration Guide Installation and configuration guide Winfrasoft HAS for Microsoft Forefront UAG 2010 Published: October 2011 Applies to: Winfrasoft HAS (Build 2.0.2300.4)
NetMan Desktop Manager Quick-Start Guide
 NetMan Desktop Manager Quick-Start Guide This document describes the procedure for installing NetMan Desktop Manager. The example given here presents a standard installation scenario. For details on all
NetMan Desktop Manager Quick-Start Guide This document describes the procedure for installing NetMan Desktop Manager. The example given here presents a standard installation scenario. For details on all
Setup Smart Login for Windows V2
 Setup Smart Login for Windows V2 Smart Login allows workstations to login to a Smart-Net server without having to join a domain. Smart Login is suitable for both laptops and desktop PC s. Features Users
Setup Smart Login for Windows V2 Smart Login allows workstations to login to a Smart-Net server without having to join a domain. Smart Login is suitable for both laptops and desktop PC s. Features Users
One Bay SATA/IDE Turbo NAS User Manual
 One Bay SATA/IDE Turbo NAS User Manual Revision: v0117 Date: 2009/07/23 For firmware version v1.17 Table of Contents 1. Introduction... 3 1.1. Key Features... 3 1.2. Network Environment... 3 2. Hardware
One Bay SATA/IDE Turbo NAS User Manual Revision: v0117 Date: 2009/07/23 For firmware version v1.17 Table of Contents 1. Introduction... 3 1.1. Key Features... 3 1.2. Network Environment... 3 2. Hardware
TeamViewer Manual Manager
 TeamViewer Manual Manager Rev 12/2014 TeamViewer GmbH Jahnstraße 30 D-73037 Göppingen teamviewer.com Overview Table of Contents 1 Overview... 4 1.1 About TeamViewer Manager... 4 1.2 About this manual...
TeamViewer Manual Manager Rev 12/2014 TeamViewer GmbH Jahnstraße 30 D-73037 Göppingen teamviewer.com Overview Table of Contents 1 Overview... 4 1.1 About TeamViewer Manager... 4 1.2 About this manual...
MU2b Authentication, Authorization and Accounting Questions Set 2
 MU2b Authentication, Authorization and Accounting Questions Set 2 1. You enable the audit of successful and failed policy changes. Where can you view entries related to policy change attempts? Lesson 2
MU2b Authentication, Authorization and Accounting Questions Set 2 1. You enable the audit of successful and failed policy changes. Where can you view entries related to policy change attempts? Lesson 2
YubiKey Smart Card Deployment Guide
 YubiKey Smart Card Deployment Guide Best Practices and Basic Setup YubiKey 4, YubiKey 4 Nano, YubiKey 4C, YubiKey 4C Nano, YubiKey NEO, YubiKey NEO-n Copyright 2017 Yubico Inc. All rights reserved. Trademarks
YubiKey Smart Card Deployment Guide Best Practices and Basic Setup YubiKey 4, YubiKey 4 Nano, YubiKey 4C, YubiKey 4C Nano, YubiKey NEO, YubiKey NEO-n Copyright 2017 Yubico Inc. All rights reserved. Trademarks
ATX Document Manager. User Guide
 ATX Document Manager User Guide ATX DOCUMENT MANAGER User Guide 2008 CCH Small Firm Services. All rights reserved. 6 Mathis Drive NW Rome, GA 30165 No part of this manuscript may be copied, photocopied,
ATX Document Manager User Guide ATX DOCUMENT MANAGER User Guide 2008 CCH Small Firm Services. All rights reserved. 6 Mathis Drive NW Rome, GA 30165 No part of this manuscript may be copied, photocopied,
Evaluation Guide Host Access Management and Security Server 12.4
 Evaluation Guide Host Access Management and Security Server 12.4 Copyrights and Notices Copyright 2017 Attachmate Corporation, a Micro Focus company. All rights reserved. No part of the documentation materials
Evaluation Guide Host Access Management and Security Server 12.4 Copyrights and Notices Copyright 2017 Attachmate Corporation, a Micro Focus company. All rights reserved. No part of the documentation materials
Virtual CD TS 1 Introduction... 3
 Table of Contents Table of Contents Virtual CD TS 1 Introduction... 3 Document Conventions...... 4 What Virtual CD TS Can Do for You...... 5 New Features in Version 10...... 6 Virtual CD TS Licensing......
Table of Contents Table of Contents Virtual CD TS 1 Introduction... 3 Document Conventions...... 4 What Virtual CD TS Can Do for You...... 5 New Features in Version 10...... 6 Virtual CD TS Licensing......
ZENworks 2017 Update1 Full Disk Encryption Emergency Recovery Reference. July 2017
 ZENworks 2017 Update1 Full Disk Encryption Emergency Recovery Reference July 2017 Legal Notice For information about legal notices, trademarks, disclaimers, warranties, export and other use restrictions,
ZENworks 2017 Update1 Full Disk Encryption Emergency Recovery Reference July 2017 Legal Notice For information about legal notices, trademarks, disclaimers, warranties, export and other use restrictions,
USER MANUAL FOR SECURE E MAIL MICROSOFT OUTLOOK (2003)
 YATANARPON TELEPORT COMPANY LTD., YATANARPON CERTIFICATION AUTHORITY USER MANUAL FOR SECURE E MAIL MICROSOFT OUTLOOK (2003) Yatanarpon Teleport Company Ltd., Hlaing Universities Campus, Hlaing Township,
YATANARPON TELEPORT COMPANY LTD., YATANARPON CERTIFICATION AUTHORITY USER MANUAL FOR SECURE E MAIL MICROSOFT OUTLOOK (2003) Yatanarpon Teleport Company Ltd., Hlaing Universities Campus, Hlaing Township,
Forensics Challenges. Windows Encrypted Content John Howie CISA CISM CISSP Director, Security Community, Microsoft Corporation
 Forensics Challenges Windows Encrypted Content John Howie CISA CISM CISSP Director, Security Community, Microsoft Corporation Introduction Encrypted content is a challenge for investigators Makes it difficult
Forensics Challenges Windows Encrypted Content John Howie CISA CISM CISSP Director, Security Community, Microsoft Corporation Introduction Encrypted content is a challenge for investigators Makes it difficult
ModeChanger
 35020808-02 2015.11 ModeChanger ModeChanger is a software utility that can switch the drive between normal mode and encrypted mode. Operating in encrypted mode will help protect your data. While the drive
35020808-02 2015.11 ModeChanger ModeChanger is a software utility that can switch the drive between normal mode and encrypted mode. Operating in encrypted mode will help protect your data. While the drive
Requirements. Cisco VPN Client setup file. Cisco VPN Client software installation
 Cisco VPN Client installation 1. Requirements 2. Cisco VPN Client setup file 3. Cisco VPN Client software installation 4. New connection setup 5. Authorization 6. Troubleshooting 7. Contacts Requirements
Cisco VPN Client installation 1. Requirements 2. Cisco VPN Client setup file 3. Cisco VPN Client software installation 4. New connection setup 5. Authorization 6. Troubleshooting 7. Contacts Requirements
ActiveSecurity MyClient
 ActiveSecurity MyClient Setup Guide Contents 1 Introduction... 2 2 Installation of ActiveSecurity MyClient... 2 2.1 Desktop installation... 2 3 Configuration... 6 3.1 Language... 6 3.2 Smart card management...
ActiveSecurity MyClient Setup Guide Contents 1 Introduction... 2 2 Installation of ActiveSecurity MyClient... 2 2.1 Desktop installation... 2 3 Configuration... 6 3.1 Language... 6 3.2 Smart card management...
SecurEnvoy Windows Login Agent
 SecurEnvoy Windows Login Agent Including support for SecurPassword Version 8.1.200 SecurEnvoy Global HQ Merlin House, Brunel Road, Theale, Reading. RG7 4AB Tel: 0845 2600010 Fax: 0845 260014 www.securenvoy.com
SecurEnvoy Windows Login Agent Including support for SecurPassword Version 8.1.200 SecurEnvoy Global HQ Merlin House, Brunel Road, Theale, Reading. RG7 4AB Tel: 0845 2600010 Fax: 0845 260014 www.securenvoy.com
PROXY Pro Deployment Tool v10.0. User Guide October 2017
 PROXY Pro Deployment Tool v10.0 User Guide October 2017 Table of contents 1. System Requirements...3 2. Target Computer Requirements...4 3. Deployment Tool Operation...5 3.1 Loading a Host Install File...6
PROXY Pro Deployment Tool v10.0 User Guide October 2017 Table of contents 1. System Requirements...3 2. Target Computer Requirements...4 3. Deployment Tool Operation...5 3.1 Loading a Host Install File...6
SafeGuard Enterprise user help. Product version: 8.0
 SafeGuard Enterprise user help Product version: 8.0 Contents 1 About SafeGuard Enterprise...4 2 SafeGuard Enterprise modules...5 3 Security recommendations...7 4 Full disk encryption...9 4.1 Encryption
SafeGuard Enterprise user help Product version: 8.0 Contents 1 About SafeGuard Enterprise...4 2 SafeGuard Enterprise modules...5 3 Security recommendations...7 4 Full disk encryption...9 4.1 Encryption
Click Studios. Passwordstate. Remote Session Launcher. Installation Instructions
 Passwordstate Remote Session Launcher Installation Instructions This document and the information controlled therein is the property of Click Studios. It must not be reproduced in whole/part, or otherwise
Passwordstate Remote Session Launcher Installation Instructions This document and the information controlled therein is the property of Click Studios. It must not be reproduced in whole/part, or otherwise
YubiKey Smart Card Deployment Guide
 YubiKey Smart Card Deployment Guide Best Practices and Basic Setup YubiKey 4 Series (YubiKey 4, YubiKey 4 Nano, YubiKey 4C, YubiKey 4C Nano) YubiKey NEO Series (YubiKey NEO, YubiKey NEO-n) Last Updated:
YubiKey Smart Card Deployment Guide Best Practices and Basic Setup YubiKey 4 Series (YubiKey 4, YubiKey 4 Nano, YubiKey 4C, YubiKey 4C Nano) YubiKey NEO Series (YubiKey NEO, YubiKey NEO-n) Last Updated:
Installation User Guide SMART ACCESS 2.0
 Installation User Guide SMART ACCESS 2.0 Date: 05 March 2013 Version: 2.0 Table of Contents 1. OVERVIEW... 3 2. INSTALLATION PROCEDURE... 4 2.1. IIS INSTALLATION:... 5 2.2. REPORTSERVER 2008 SP1 INSTALLATION:...
Installation User Guide SMART ACCESS 2.0 Date: 05 March 2013 Version: 2.0 Table of Contents 1. OVERVIEW... 3 2. INSTALLATION PROCEDURE... 4 2.1. IIS INSTALLATION:... 5 2.2. REPORTSERVER 2008 SP1 INSTALLATION:...
ZENworks 11 Support Pack 4 User Source and Authentication Reference. October 2016
 ZENworks 11 Support Pack 4 User Source and Authentication Reference October 2016 Legal Notices For information about legal notices, trademarks, disclaimers, warranties, export and other use restrictions,
ZENworks 11 Support Pack 4 User Source and Authentication Reference October 2016 Legal Notices For information about legal notices, trademarks, disclaimers, warranties, export and other use restrictions,
Yubico with Centrify for Mac - Deployment Guide
 CENTRIFY DEPLOYMENT GUIDE Yubico with Centrify for Mac - Deployment Guide Abstract Centrify provides mobile device management and single sign-on services that you can trust and count on as a critical component
CENTRIFY DEPLOYMENT GUIDE Yubico with Centrify for Mac - Deployment Guide Abstract Centrify provides mobile device management and single sign-on services that you can trust and count on as a critical component
SafeNet Authentication Manager
 SafeNet Authentication Manager Version 8.0 Rev A User s Guide Copyright 2010 SafeNet, Inc. All rights reserved. All attempts have been made to make the information in this document complete and accurate.
SafeNet Authentication Manager Version 8.0 Rev A User s Guide Copyright 2010 SafeNet, Inc. All rights reserved. All attempts have been made to make the information in this document complete and accurate.
Hitachi ID Systems Inc Identity Manager 8.2.6
 Systems Inc RSA SecurID Ready Implementation Guide Partner Information Last Modified: December 5, 2014 Product Information Partner Name Hitachi ID Systems Inc Web Site www.hitachi-id.com Product Name Identity
Systems Inc RSA SecurID Ready Implementation Guide Partner Information Last Modified: December 5, 2014 Product Information Partner Name Hitachi ID Systems Inc Web Site www.hitachi-id.com Product Name Identity
Install Certificate on the Cisco Secure ACS Appliance for PEAP Clients
 Install Certificate on the Cisco Secure ACS Appliance for PEAP Clients Document ID: 64067 Contents Introduction Prerequisites Requirements Components Used Conventions Microsoft Certificate Service Installation
Install Certificate on the Cisco Secure ACS Appliance for PEAP Clients Document ID: 64067 Contents Introduction Prerequisites Requirements Components Used Conventions Microsoft Certificate Service Installation
VMware Horizon Client for Windows 10 UWP Installation and Setup Guide. Modified on 21 SEP 2017 VMware Horizon Client for Windows 10 UWP 4.
 VMware Horizon Client for Windows 10 UWP Installation and Setup Guide Modified on 21 SEP 2017 VMware Horizon Client for Windows 10 UWP 4.6 You can find the most up-to-date technical documentation on the
VMware Horizon Client for Windows 10 UWP Installation and Setup Guide Modified on 21 SEP 2017 VMware Horizon Client for Windows 10 UWP 4.6 You can find the most up-to-date technical documentation on the
Installing AX Server with PostgreSQL (multi-server)
 Installing AX Server with PostgreSQL (multi-server) Version: 13 Published: Wednesday, November 29, 2017 ACL Services Ltd. 2017 Table of contents Table of contents Table of contents 3 Introduction 7 Intended
Installing AX Server with PostgreSQL (multi-server) Version: 13 Published: Wednesday, November 29, 2017 ACL Services Ltd. 2017 Table of contents Table of contents Table of contents 3 Introduction 7 Intended
