Maintaining the NDS Database
|
|
|
- Bruno Fisher
- 5 years ago
- Views:
Transcription
1 Chapter 7 Maintaining the NDS Database Overview Concepts to Know Preserving the Database Backing Up and Restoring NDS Data Backing Up an Entry Restoring an Entry Restoring an Entry from a Backup (Existing Entry) Restoring an Entry from a Backup (Entry Not Existing) Restoring an Entry from a Move Repairing Time Stamps Sending All Updates Receiving All Updates Inspecting and Analyzing a Server s NDS Database Inspecting an Entry Reading References File Directories Related to NDS Entries Creating an Entry Directory Removing an Entry Directory Checking a User s Security Equivalence Vector Checking a Console Operator
2 Novell Directory Services Internals Overview Overview Concepts to Know This chapter discusses how NDS maintains the integrity of its database. Specifically, it will discuss the following topics: Backing up and restoring NDS data Repairing time stamps Sending and receiving all updates Inspecting and analyzing a server s NDS database Getting a remote entry ID Inspecting an entry Reading references To understand this chapter, you should be familiar with the following Novell Directory Services concepts: Entry Partition Replica Time stamp Directory Information Base (DIB) NDS reference 7-2 Version 1
3 Maintaining the NDS Database Preserving the Database Like any other database system, Novell Directory Services provides features to maintain the database in its day-to-day operations. As has been discussed already, NDS provides fault tolerance through replication and synchronization. This protects data against media or system failures. In addition, several problems could affect the database s integrity. For example, an operator might set a server s clock ahead, causing it to issue invalid time stamps. Values stamped with these values could not be overwritten or deleted. This chapter discusses the ways NDS deal with these and other problems. Backing Up and Restoring NDS Data Backing Up an Entry Novell Directory Services is a database that coexists with a file system; however, NDS does not back up its data to the file system. Instead it uses its own backup routines: Backup Entry, and Restore Entry. This operation allows a backup program to operate as a client and save a copy of an entry to be used as a backup. The backup program uses ordinary NDS access to walk the tree and locate the information to be backed up. For each entry to be backed up, the backup program, acting as a client, sends a Backup Entry request to the server holding that entry. The information is returned in one or more backup chunks, which the backup program can then write to an external medium. Each chunk returned contains the server s NDS version to allow future software versions to determine the format used when the data was backup to. Information backed up can be restored using the Restore Entry operation described in this chapter. To back up an entry: Table 7.1 Backing Up an Entry Restoring an Entry 1. Sends the server a Backup Entry request. Server 2. Checks that the requesting module has managed rights for that entry 3. Returns a Backup Entry reply containing a completion code, an iteration handle, and the backup information. To restore NDS data, the server must use the Restore Entry operation to Version 1 7-3
4 Novell Directory Services Internals Overview retrieve the backup chunks from the backup programs. The server places the backed up entries in its database and assigns them new time stamps. When a restored entry collides with an existing entry, the restored entry overrides any existing information.the server deletes the existing entry s attribute values, applies the restored values, and gives the entry a new creation time. The server then places on the new entry an obituary indicating the creation time of the overridden entry. The obituary allows servers to distinguish between the restored entry and the overridden entry. The Restore Entry operation restores a deleted entry in one of three situations: It restores an entry from a backup when the original entry still exists on the server It restores an entry from a backup when the original entry does not exist on the server When a client is moving an entry, DSARestoreEntry adds the entry to its new location Restoring an Entry from a Backup (Existing Entry) When NDS restores an entry from backup, the original entry may still exist in the Directory tree. The request indicates that the entry exists in the tree by placing [DS] at the end of the version information. In this case, the old entry must be deleted before the backup can be restored. When an NDS entry is restored, some of its attributes are filtered, meaning that they are not restored with the entry. For all object classes, the following attributes are filtered: Last Reference Time Backlink Obituary Reference Revision In addition, the following table shows the attributes that are filtered for specific object classes. Table 7.2 Filtered Attributes (By Object Class) Object Class Partition Print Server Queue Server Attributes Filtered All attributes Host Device Network Address Queue Directory Public Key Network Address 7-4 Version 1
5 Maintaining the NDS Database Table 7.2 Filtered Attributes (By Object Class) Object Class User Attributes Filtered Login Time Network Address In addition, the following conditions may apply to restoring the entry: If the original entry is present on the server, it does not receive a new time stamp. If it exists but is not present, it receives a new time stamp. If the original entry is a Queue that is not present on the server, restoring the entry removes the Queue Directory attribute from the entry s list of attributes. If the entry is a Queue whose Host Server attribute is not changing, the operation leaves this attribute in the list. If the Host Server attribute value is changing, the server sends a packet to remove the queue directory. If the entry is a Print Server whose Host Device attribute value is not changing, the operation leaves this attribute in the list. If the Host Device is changing, the server sends a packet to remove the original directory. To restore an entry from a backup when the original entry still exists in the tree: Table 7.3 Restoring an Entry from a Backup (Existing Entry) 1. Sends a Restore Entry request to the server. Server 2. Checks to see if the entry is being restored from a backup or from a move. 3. Checks that the entry exists on the server. 4. Checks that the client has Remove and Create rights to delete the old entry and add the new entry. 5. Checks to see that the entry is writable. 6. Checks to see if the entry is a partition root entry. 7. Checks to see if the entry is an alias. 8. Checks the entry s present base class. 9. Purges the naming values and any attribute values that are not valid for the new entry s object class. 10. Adds the new entry. 11. Returns a Restore Entry reply indicating success or failure. Restoring an Entry from a Backup (Entry Not Existing) The Restore Entry operation differs when the original entry does not exist in the tree. The requesting module must have Create rights to restore the entry on the server. In addition, if the original entry was a Queue, the Version 1 7-5
6 Novell Directory Services Internals Overview operation deletes the Queue Directory attribute from the entry s list of attributes. To restore an entry from a backup when the original entry does not exist in the tree: Table 7.4 Restoring an Entry from a Backup (Entry Not Existing) 1. Sends a Restore Entry request to the server. Server 2. Checks to see if the entry is being restored from a backup or from a move. 3. Checks that the entry exists on the server. 4. Checks that the client has Create rights to add the new entry. 5. Checks to see that the entry is writable. 6. Checks to see if the entry is a partition root entry. 7. Checks to see if the entry is an alias. 8. Checks the entry s present base class. 9. Purges the naming values and any attribute values that are not valid for the new entry s object class. 10. Adds the new entry. 11. Returns a Restore Entry reply indicating success or failure. Restoring an Entry from a Move The Move operation places the entry in a new partition. Consequently, the new entry does not replace an existing entry. To restore an entry that is moving: Table 7.5 Restoring a Moved Entry 1. Sends a Restore Entry request to the server. Server 2. Verifies that it holds the master replica of the entry. 3. Checks that the client has Create rights to add the entry. 4. Checks to see if the entry is being restored from a backup or a move. 5. Checks the entry s object class. 6. Checks to see if the entry is an alias and obtains the aliased entry s name. 7. Checks to see if the entry is a print server or print queue. If so, creates a file directory associated with the entry. 8. Creates the entry record. 9. Adds the subordinate entry to its parent. 10. Adds the object class and naming values. 11. Adds attribute values. 12. Returns a Restore Entry reply. The Restore Entry request is the same as the request used to restore from a 7-6 Version 1
7 Maintaining the NDS Database backup. The DS_RESTORE_MOVING request flag is set to 0, indicating that the entry is being restored from a Move Entry operation. Repairing Time Stamps If an NDS operator set a server s clock ahead of the other servers in the network, time stamps issued by that server would be invalid because they and new time stamps would always be in the future. Thus, in a collision, the future time stamp would always override the valid time stamp. The Repair Time Stamps operation, although drastic, remedies such a situation. To repair time stamps: Table 7.6 Repairing Time Stamps Sending All Updates 1. Sends a Repair Time Stamps request to the server holding the master replica of the affected partition. Server holding master replica Server holding a nonmaster replica of the partition Server holding master replica 2. Checks all of the partition s time stamps in it local database. 3. Assigns new time stamps to any entries having time stamps that are ahead of the server s current clock time. 4. Declares a new epoch by setting a new Epoch time stamp on the partition root object. 5. Returns a Repair Time Stamps reply to the client. 6. Sends a Start Update Replica request to other servers holding replicas of the affected partition. 7. Checks its Epoch against the Epoch it receives in the Start Update Replica request. 8. Returns an Old Epoch completion code in the reply. 9. Sets the partition s operation in progress to Repairing Timestamps. This locks the partition until the operation is complete. 10. Sends Update Replica requests to all servers in the replica ring. In each request, the server sets the New Epoch request flag. It continues sending Update Replica requests until it has transferred all the partition s data. 11. Purges its replica of the partition and replaces it with the data it receives in the Update Replica requests. Server holding a nonmaster replica Server holding 12. Unlocks the partition. the master replica An error might prevent data from being propagated to all replicas of a partition. To send all information to all replicas, a client sends a Partition Function request with the function code set to Send All Updates. This causes the server to send all the partition data to all replicas. Version 1 7-7
8 Novell Directory Services Internals Overview To send all updates: Table 7.7 Sending All Updates Module Server holding affected replica Receiving All Updates Action This operation replaces a replica on a specific server if that replica s time stamps are incorrect. For example, an operation to repair the local database may not have finished correctly, leaving the replica s state unknown. To remedy such a problem, a client sends the master replica a Partition Function request with the function code set to Receive All Updates. To receive all updates: 1. Sends a Partition Function request to the server. In the request, the client sets the function code to Send All Updates. 2. Synchronizes with all other replicas, sending all partition information regardless of time stamps. Server receiving 3. Decides which information to keep, depending on time partition information stamps. Table 7.8 Receiving All Updates 1. Sends a Partition Function request to the server. In the request, the client sets the function code to Receive All Updates. Server holding 2. Tags the replica as New. affected replica 3. Synchronizes with the specified replica, sending all partition information regardless of time stamps. Server receiving partition information 4. Purges all replica information and replaces it with the data it receives from the master replica. Inspecting and Analyzing a Server s NDS Database NDS provides three operations that allow a client to analyze the database information held on a given server: Inspect Entry. This operation allows a client to obtain information about an entry and any errors that entry has experienced. Read References. This operation reports information about references a server holds. The following sections describe each of these operations. 7-8 Version 1
9 Maintaining the NDS Database Inspecting an Entry This operation is used to verify an entry s existence and list any errors associated with that entry. To inspect an entry: Table 7.9 Inspecting an Entry 1. Sends a Inspect Entry request to the server. This request specifies the entry to be inspected. Server 2. Checks that the client has Browse [Entry] rights to the entry. 3. Verifies the entry s existence and get a list of errors. 4. Returns a Inspect Entry reply to the server. Reading References A reference is a hidden attribute; clients cannot read a reference using normal Read operation. A reference uses the Distinguished Name syntax and is a per-replica attribute stored only on the replica where it originated. Unlike a back link, which keeps track of relationships between servers, references track relationships between entries on the same server. The Read References operation reports these relationships, as well as the relationships between bindery objects in bindery services. To list information about the references a server holds: Table 7.10 Reading References 1. Sends a Read Reference request to the server. Server 2. Returns a Read References reply to the server. File Directories Related to NDS Entries Each NDS entry whose object class is Queue has a Queue Directory attribute value, which identifies a file system directory where the queue s files are stored. The directory and queue to be on different systems. NDS uses two operations to maintain the correspondence between the Queue Directory attribute value and its file system directory: Create Entry Dir. The server holding the NDS entry sends this request to the server where the directory is to be created. Remove Entry Dir. A server changing or deleting the NDS entry sends this request to the server holding the directory, which deletes the directory. Version 1 7-9
10 Novell Directory Services Internals Overview The following sections describe these two operations. Creating an Entry Directory Each NDS entry of object class Queue has a Queue Directory attribute. This attribute identifies a file system directory where the queue s files are stored. To create a directory associated with a queue object, a server holding a specific entry acts as the requesting module. For example, when a server creates a Queue entry, it requests that another server create a file system directory associated with that entry. The requesting server sends a Create Entry Dir request to the server holding the volume that will hold the entry directory. To create an entry directory: Table 7.11 Creating an Entry Directory 1. Sends a Create Entry Dir request to the server holding the volume that will hold the new directory. Server 2. Creates the directory and generates a random name for the directory. It begins at x and increments by 1 until it succeeds. It appends this name to the name given in the Directory Name field. 3. Returns a Create Entry Dir reply containing the name (file path) of the directory. Removing an Entry Directory When a print queue or print server entry is deleted, its associated file system directory must also be deleted. To remove an entry directory: Table 7.12 Removing an Entry Directory 1. Sends a Remove Entry Dir request to the server. Server 2. Resolves the name of the entry. 3. Reads the root entry of the entry s partition. 4. Read the entry s base class. 5. Stores the entry s base class, partition name, entry name, client name, and directory name. 6. Schedules the background task (checks for Dir Removal Event). 7. Returns a Remove Entry Dir reply indicating success or failure Version 1
11 Maintaining the NDS Database Table 7.12 Removing an Entry Directory Module Dir Removal Event Process Action 8. Processes list saved in step Checks that the requesting module is in the partition root s replica ring. 10. If the entry is a print server, removes the directory based on the Entry ID. If the entry is a queue, removes the directory based on the Directory name. Checking a User s Security Equivalence Vector Although a User entry may hold a Security Equals attribute, its value may not accurately reflect the entry s security equivalence. Check SEV allows a client to check the entry s current security equivalence vector. To check an entry s security equivalence vector: Table 7.13 Checking an Entry s Security Equivalence Vector 1. Sends a Check SEV request to the server holding the User entry. Server 2. Resolves the entry s name. 3. Checks the entry against the entry indicated in the Possible Equivalence field to determine whether the two entries are actually equivalent. 4. Returns a Check SEV reply indicating success or failure. Checking a Console Operator A user can have operator privileges for a server. This privilege is reflected in the server entry s and the user s security equivalences. Because checking these vectors can be time consuming, the server stores a list of operators separately. If an entry with operator privileges changes, the server making the change sends a Check Console Operator request to the server whose operator list is affected. The request identifies the user, and the receiving server checks its local database to determine if it should add or delete the user from the operator list. To check a console operator: Table 7.14 Checking a Console Operator 1. Sends a Check Console Operator request to the server holding the affected Operator list. Server 2. Adds or deletes the entry to or from its Operator list. 3. Returns a Check Console Operator reply indicating success or failure. Version
12 Novell Directory Services Internals Overview 7-12 Version 1
 050-890 Passing Score: 800 Time Limit: 4 min Exam A QUESTION 1 Which time server types participate in voting for the correct time? (Choose 2) A. Master B. Primary C. Reference D. Secondary E. Single reference
050-890 Passing Score: 800 Time Limit: 4 min Exam A QUESTION 1 Which time server types participate in voting for the correct time? (Choose 2) A. Master B. Primary C. Reference D. Secondary E. Single reference
Novell edirectory Design Exam.
 Novell 050-664 Novell edirectory Design Exam TYPE: DEMO http://www.examskey.com/050-664.html Examskey Novell 050-664 exam demo product is here for you to test the quality of the product. This Novell 050-664
Novell 050-664 Novell edirectory Design Exam TYPE: DEMO http://www.examskey.com/050-664.html Examskey Novell 050-664 exam demo product is here for you to test the quality of the product. This Novell 050-664
Novell. NetWare 6. NETWORK TIME MANAGMENT ADMINISTRATION GUIDE
 Novell NetWare 6 www.novell.com NETWORK TIME MANAGMENT ADMINISTRATION GUIDE Legal Notices Novell, Inc. makes no representations or warranties with respect to the contents or use of this documentation,
Novell NetWare 6 www.novell.com NETWORK TIME MANAGMENT ADMINISTRATION GUIDE Legal Notices Novell, Inc. makes no representations or warranties with respect to the contents or use of this documentation,
Securing NetWare Enterprise Local Area Networks H. Van Tran Cynthia D. Heagy Payoff
 87-10-10 Securing NetWare Enterprise Local Area Networks H. Van Tran Cynthia D. Heagy Payoff Data security professionals in many organizations must protect data and applications running on local area networks
87-10-10 Securing NetWare Enterprise Local Area Networks H. Van Tran Cynthia D. Heagy Payoff Data security professionals in many organizations must protect data and applications running on local area networks
NOVELL NETWARE 5.1 ADMINISTRATION CONTENTS
 CNA Certification Guide: Novell NetWare 5.1 Administration CERTIFICATION GUIDE: NOVELL NETWARE 5.1 ADMINISTRATION CONTENTS AUTHOR ACKNOWLEDGEMENTS... XIII INTRODUCTION... XV UNIT 1 NETWARE ACCESS... 1-1
CNA Certification Guide: Novell NetWare 5.1 Administration CERTIFICATION GUIDE: NOVELL NETWARE 5.1 ADMINISTRATION CONTENTS AUTHOR ACKNOWLEDGEMENTS... XIII INTRODUCTION... XV UNIT 1 NETWARE ACCESS... 1-1
Database Management. Understanding Failure Resiliency. Database Files CHAPTER
 CHAPTER 7 This chapter contains information on RDU database management and maintenance. The RDU database is the Broadband Access Center for Cable (BACC) central database. As with any database, it is essential
CHAPTER 7 This chapter contains information on RDU database management and maintenance. The RDU database is the Broadband Access Center for Cable (BACC) central database. As with any database, it is essential
Database Management. Understanding Failure Resiliency CHAPTER
 CHAPTER 10 This chapter contains information on RDU database management and maintenance. The RDU database is the Broadband Access Center (BAC) central database. The Cisco BAC RDU requires virtually no
CHAPTER 10 This chapter contains information on RDU database management and maintenance. The RDU database is the Broadband Access Center (BAC) central database. The Cisco BAC RDU requires virtually no
Consistency and Replication. Some slides are from Prof. Jalal Y. Kawash at Univ. of Calgary
 Consistency and Replication Some slides are from Prof. Jalal Y. Kawash at Univ. of Calgary Reasons for Replication Reliability/Availability : Mask failures Mask corrupted data Performance: Scalability
Consistency and Replication Some slides are from Prof. Jalal Y. Kawash at Univ. of Calgary Reasons for Replication Reliability/Availability : Mask failures Mask corrupted data Performance: Scalability
Google File System. Arun Sundaram Operating Systems
 Arun Sundaram Operating Systems 1 Assumptions GFS built with commodity hardware GFS stores a modest number of large files A few million files, each typically 100MB or larger (Multi-GB files are common)
Arun Sundaram Operating Systems 1 Assumptions GFS built with commodity hardware GFS stores a modest number of large files A few million files, each typically 100MB or larger (Multi-GB files are common)
CS 138: Google. CS 138 XVII 1 Copyright 2016 Thomas W. Doeppner. All rights reserved.
 CS 138: Google CS 138 XVII 1 Copyright 2016 Thomas W. Doeppner. All rights reserved. Google Environment Lots (tens of thousands) of computers all more-or-less equal - processor, disk, memory, network interface
CS 138: Google CS 138 XVII 1 Copyright 2016 Thomas W. Doeppner. All rights reserved. Google Environment Lots (tens of thousands) of computers all more-or-less equal - processor, disk, memory, network interface
NetIQ Advanced Authentication Framework. Deployment Guide. Version 5.1.0
 NetIQ Advanced Authentication Framework Deployment Guide Version 5.1.0 Table of Contents 1 Table of Contents 2 Introduction 3 About This Document 3 NetIQ Advanced Authentication Framework Deployment 4
NetIQ Advanced Authentication Framework Deployment Guide Version 5.1.0 Table of Contents 1 Table of Contents 2 Introduction 3 About This Document 3 NetIQ Advanced Authentication Framework Deployment 4
Import/Export Project Components. Programming Manual
 Import/Export Project Components Programming Manual Important User Information Solid state equipment has operational characteristics differing from those of electromechanical equipment. Safety Guidelines
Import/Export Project Components Programming Manual Important User Information Solid state equipment has operational characteristics differing from those of electromechanical equipment. Safety Guidelines
Configuring VTP. Understanding How VTP Version 1 and Version 2 Work CHAPTER
 10 CHAPTER This chapter describes how to configure the VLAN Trunking Protocol (VTP) on the Catalyst 6500 series switches For complete syntax and usage information for the commands that are used in this
10 CHAPTER This chapter describes how to configure the VLAN Trunking Protocol (VTP) on the Catalyst 6500 series switches For complete syntax and usage information for the commands that are used in this
Page 1 of 7 SUMMARY MORE INFORMATION. Windows 2000 DNS Event Messages 1616 Through Microsoft resource record (RR) problems.
 Page 1 of 7 Knowledge Base Windows 2000 DNS Event Messages 1616 Through 6702 PSS ID Number: 287513 Article Last Modified on 10/11/2002 The information in this article applies to: Microsoft Windows 2000
Page 1 of 7 Knowledge Base Windows 2000 DNS Event Messages 1616 Through 6702 PSS ID Number: 287513 Article Last Modified on 10/11/2002 The information in this article applies to: Microsoft Windows 2000
CS 138: Google. CS 138 XVI 1 Copyright 2017 Thomas W. Doeppner. All rights reserved.
 CS 138: Google CS 138 XVI 1 Copyright 2017 Thomas W. Doeppner. All rights reserved. Google Environment Lots (tens of thousands) of computers all more-or-less equal - processor, disk, memory, network interface
CS 138: Google CS 138 XVI 1 Copyright 2017 Thomas W. Doeppner. All rights reserved. Google Environment Lots (tens of thousands) of computers all more-or-less equal - processor, disk, memory, network interface
Error code. Description of the circumstances under which the problem occurred. Less than 200. Linux system call error.
 Error code Less than 200 Error code Error type Description of the circumstances under which the problem occurred Linux system call error. Explanation of possible causes Countermeasures 1001 CM_NO_MEMORY
Error code Less than 200 Error code Error type Description of the circumstances under which the problem occurred Linux system call error. Explanation of possible causes Countermeasures 1001 CM_NO_MEMORY
Veritas NetBackup for Lotus Notes Administrator's Guide
 Veritas NetBackup for Lotus Notes Administrator's Guide for UNIX, Windows, and Linux Release 8.0 Veritas NetBackup for Lotus Notes Administrator's Guide Document version: 8.0 Legal Notice Copyright 2016
Veritas NetBackup for Lotus Notes Administrator's Guide for UNIX, Windows, and Linux Release 8.0 Veritas NetBackup for Lotus Notes Administrator's Guide Document version: 8.0 Legal Notice Copyright 2016
The multiple spanning-tree (MST) implementation is based on the IEEE 802.1s standard.
 CHAPTER 18 This chapter describes how to configure the Cisco implementation of the IEEE 802.1s Multiple STP (MSTP) on the IE 3010 switch. Note The multiple spanning-tree (MST) implementation is based on
CHAPTER 18 This chapter describes how to configure the Cisco implementation of the IEEE 802.1s Multiple STP (MSTP) on the IE 3010 switch. Note The multiple spanning-tree (MST) implementation is based on
CS435 Introduction to Big Data FALL 2018 Colorado State University. 11/7/2018 Week 12-B Sangmi Lee Pallickara. FAQs
 11/7/2018 CS435 Introduction to Big Data - FALL 2018 W12.B.0.0 CS435 Introduction to Big Data 11/7/2018 CS435 Introduction to Big Data - FALL 2018 W12.B.1 FAQs Deadline of the Programming Assignment 3
11/7/2018 CS435 Introduction to Big Data - FALL 2018 W12.B.0.0 CS435 Introduction to Big Data 11/7/2018 CS435 Introduction to Big Data - FALL 2018 W12.B.1 FAQs Deadline of the Programming Assignment 3
NetWare Configuration with Client 32
 NetWare Configuration with Client 32 This document covers the use of BiAdmin for Novell NetWare configuration when NetWare Client 32 is installed on your PC. Overview With NetWare Client 32 installed on
NetWare Configuration with Client 32 This document covers the use of BiAdmin for Novell NetWare configuration when NetWare Client 32 is installed on your PC. Overview With NetWare Client 32 installed on
Dynamo: Key-Value Cloud Storage
 Dynamo: Key-Value Cloud Storage Brad Karp UCL Computer Science CS M038 / GZ06 22 nd February 2016 Context: P2P vs. Data Center (key, value) Storage Chord and DHash intended for wide-area peer-to-peer systems
Dynamo: Key-Value Cloud Storage Brad Karp UCL Computer Science CS M038 / GZ06 22 nd February 2016 Context: P2P vs. Data Center (key, value) Storage Chord and DHash intended for wide-area peer-to-peer systems
CS /15/16. Paul Krzyzanowski 1. Question 1. Distributed Systems 2016 Exam 2 Review. Question 3. Question 2. Question 5.
 Question 1 What makes a message unstable? How does an unstable message become stable? Distributed Systems 2016 Exam 2 Review Paul Krzyzanowski Rutgers University Fall 2016 In virtual sychrony, a message
Question 1 What makes a message unstable? How does an unstable message become stable? Distributed Systems 2016 Exam 2 Review Paul Krzyzanowski Rutgers University Fall 2016 In virtual sychrony, a message
The Google File System
 The Google File System Sanjay Ghemawat, Howard Gobioff, and Shun-Tak Leung Google* 정학수, 최주영 1 Outline Introduction Design Overview System Interactions Master Operation Fault Tolerance and Diagnosis Conclusions
The Google File System Sanjay Ghemawat, Howard Gobioff, and Shun-Tak Leung Google* 정학수, 최주영 1 Outline Introduction Design Overview System Interactions Master Operation Fault Tolerance and Diagnosis Conclusions
Administrating CaseMap User Guide
 Administrating User Guide, Version 12.1 Optimizing Case Files Replicating and Synchronizing Managing Links to Cases Managing File Viewers Managing the Case Index Managing OCR processing Managing Case Scripts
Administrating User Guide, Version 12.1 Optimizing Case Files Replicating and Synchronizing Managing Links to Cases Managing File Viewers Managing the Case Index Managing OCR processing Managing Case Scripts
The Google File System
 October 13, 2010 Based on: S. Ghemawat, H. Gobioff, and S.-T. Leung: The Google file system, in Proceedings ACM SOSP 2003, Lake George, NY, USA, October 2003. 1 Assumptions Interface Architecture Single
October 13, 2010 Based on: S. Ghemawat, H. Gobioff, and S.-T. Leung: The Google file system, in Proceedings ACM SOSP 2003, Lake George, NY, USA, October 2003. 1 Assumptions Interface Architecture Single
32 GroupWise 6.5 Administration Guide
 I System Chapter 1, GroupWise System Administration, on page 33 Chapter 2, ConsoleOne Administration Tool, on page 35 Chapter 3, GroupWise View, on page 37 Chapter 4, System Operations, on page 43 Chapter
I System Chapter 1, GroupWise System Administration, on page 33 Chapter 2, ConsoleOne Administration Tool, on page 35 Chapter 3, GroupWise View, on page 37 Chapter 4, System Operations, on page 43 Chapter
Workforce Management Administrator's Guide. MS SQL Database Replication
 Workforce Management Administrator's Guide MS SQL Database Replication 12/24/2017 Contents 1 MS SQL Database Replication 1.1 System Requirements 1.2 Setting Up the Database Replication 1.3 Maintaining
Workforce Management Administrator's Guide MS SQL Database Replication 12/24/2017 Contents 1 MS SQL Database Replication 1.1 System Requirements 1.2 Setting Up the Database Replication 1.3 Maintaining
Introduction to Autodesk Vault
 Chapter Introduction to Autodesk Vault 1 This chapter provides an overview of Autodesk Vault features and functionality. You learn how to use Autodesk Vault to manage engineering design data in a secure,
Chapter Introduction to Autodesk Vault 1 This chapter provides an overview of Autodesk Vault features and functionality. You learn how to use Autodesk Vault to manage engineering design data in a secure,
Memory may be insufficient. Memory may be insufficient.
 Error code Less than 200 Error code Error type Description of the circumstances under which the problem occurred Linux system call error. Explanation of possible causes Countermeasures 1001 CM_NO_MEMORY
Error code Less than 200 Error code Error type Description of the circumstances under which the problem occurred Linux system call error. Explanation of possible causes Countermeasures 1001 CM_NO_MEMORY
Consistency in Distributed Systems
 Consistency in Distributed Systems Recall the fundamental DS properties DS may be large in scale and widely distributed 1. concurrent execution of components 2. independent failure modes 3. transmission
Consistency in Distributed Systems Recall the fundamental DS properties DS may be large in scale and widely distributed 1. concurrent execution of components 2. independent failure modes 3. transmission
Synchronization. Clock Synchronization
 Synchronization Clock Synchronization Logical clocks Global state Election algorithms Mutual exclusion Distributed transactions 1 Clock Synchronization Time is counted based on tick Time judged by query
Synchronization Clock Synchronization Logical clocks Global state Election algorithms Mutual exclusion Distributed transactions 1 Clock Synchronization Time is counted based on tick Time judged by query
Database Management. Understanding Failure Resiliency CHAPTER
 CHAPTER 14 This chapter contains information on RDU database management and maintenance. The RDU database is the Broadband Access Center (BAC) central database. The BAC RDU requires virtually no maintenance
CHAPTER 14 This chapter contains information on RDU database management and maintenance. The RDU database is the Broadband Access Center (BAC) central database. The BAC RDU requires virtually no maintenance
Recap. CSE 486/586 Distributed Systems Google Chubby Lock Service. Paxos Phase 2. Paxos Phase 1. Google Chubby. Paxos Phase 3 C 1
 Recap CSE 486/586 Distributed Systems Google Chubby Lock Service Steve Ko Computer Sciences and Engineering University at Buffalo Paxos is a consensus algorithm. Proposers? Acceptors? Learners? A proposer
Recap CSE 486/586 Distributed Systems Google Chubby Lock Service Steve Ko Computer Sciences and Engineering University at Buffalo Paxos is a consensus algorithm. Proposers? Acceptors? Learners? A proposer
Archiving and Purging Data from the Database
 CHAPTER 10 These topics provide basic information about data purging and archiving and system stability: Prime Network Database Schemas, page 10-1, describes the schemas supported by the Prime Network
CHAPTER 10 These topics provide basic information about data purging and archiving and system stability: Prime Network Database Schemas, page 10-1, describes the schemas supported by the Prime Network
GFS: The Google File System. Dr. Yingwu Zhu
 GFS: The Google File System Dr. Yingwu Zhu Motivating Application: Google Crawl the whole web Store it all on one big disk Process users searches on one big CPU More storage, CPU required than one PC can
GFS: The Google File System Dr. Yingwu Zhu Motivating Application: Google Crawl the whole web Store it all on one big disk Process users searches on one big CPU More storage, CPU required than one PC can
Introduction to Autodesk VaultChapter1:
 Introduction to Autodesk VaultChapter1: Chapter 1 This chapter provides an overview of Autodesk Vault features and functionality. You learn how to use Autodesk Vault to manage engineering design data in
Introduction to Autodesk VaultChapter1: Chapter 1 This chapter provides an overview of Autodesk Vault features and functionality. You learn how to use Autodesk Vault to manage engineering design data in
Database Management. Understanding Failure Resiliency CHAPTER
 CHAPTER 15 This chapter contains information on RDU database management and maintenance. The RDU database is the Cisco Broadband Access Center (Cisco BAC) central database. The Cisco BAC RDU requires virtually
CHAPTER 15 This chapter contains information on RDU database management and maintenance. The RDU database is the Cisco Broadband Access Center (Cisco BAC) central database. The Cisco BAC RDU requires virtually
Linearizability CMPT 401. Sequential Consistency. Passive Replication
 Linearizability CMPT 401 Thursday, March 31, 2005 The execution of a replicated service (potentially with multiple requests interleaved over multiple servers) is said to be linearizable if: The interleaved
Linearizability CMPT 401 Thursday, March 31, 2005 The execution of a replicated service (potentially with multiple requests interleaved over multiple servers) is said to be linearizable if: The interleaved
SOURCEFIRE 3D SYSTEM RELEASE NOTES
 SOURCEFIRE 3D SYSTEM RELEASE NOTES Version 5.3.0.2 Original Publication: April 21, 2014 Last Updated: April 25, 2016 These release notes are valid for Version 5.3.0.2 of the Sourcefire 3D System. Even
SOURCEFIRE 3D SYSTEM RELEASE NOTES Version 5.3.0.2 Original Publication: April 21, 2014 Last Updated: April 25, 2016 These release notes are valid for Version 5.3.0.2 of the Sourcefire 3D System. Even
Archiving and Purging Data
 CHAPTER 10 These topics provide basic information about data purging and archiving and system stability: Prime Network Database Schemas, page 10-1, describes the schemas supported by the Prime Network
CHAPTER 10 These topics provide basic information about data purging and archiving and system stability: Prime Network Database Schemas, page 10-1, describes the schemas supported by the Prime Network
Introduction...4. Purpose...4 Scope...4 Manitoba ehealth Incident Management...4 Icons...4
 Remedy Incident Management Version 3.2 Modified: 08/24/2017 TABLE OF CONTENTS Introduction...4 Purpose...4 Scope...4 Manitoba ehealth Incident Management...4 Icons...4 Incident Stages Overview...5 Identification
Remedy Incident Management Version 3.2 Modified: 08/24/2017 TABLE OF CONTENTS Introduction...4 Purpose...4 Scope...4 Manitoba ehealth Incident Management...4 Icons...4 Incident Stages Overview...5 Identification
Ebook : Overview of application development. All code from the application series books listed at:
 Ebook : Overview of application development. All code from the application series books listed at: http://www.vkinfotek.com with permission. Publishers: VK Publishers Established: 2001 Type of books: Develop
Ebook : Overview of application development. All code from the application series books listed at: http://www.vkinfotek.com with permission. Publishers: VK Publishers Established: 2001 Type of books: Develop
CCURE Access Control Plugin and Video Integration Guide 3.2. Click here for the most recent version of this document.
 CCURE Access Control Plugin and Video Integration Guide 3.2 Click here for the most recent version of this document. Document last updated: November 22, 2017 Copyright notice Genetec Inc., 2017 Genetec
CCURE Access Control Plugin and Video Integration Guide 3.2 Click here for the most recent version of this document. Document last updated: November 22, 2017 Copyright notice Genetec Inc., 2017 Genetec
SUDOERS_TIMESTAMP(5) File Formats Manual SUDOERS_TIMESTAMP(5)
 NAME sudoers_timestamp - Sudoers Time Stamp Format DESCRIPTION The sudoers plugin uses per-user time stamp files for credential caching. Once a user has been authenticated, they may use sudo without a
NAME sudoers_timestamp - Sudoers Time Stamp Format DESCRIPTION The sudoers plugin uses per-user time stamp files for credential caching. Once a user has been authenticated, they may use sudo without a
Backup and Restore Operations
 Backup Data Type, page 1 Backup and Restore Repositories, page 2 On-Demand and Scheduled Backups, page 3 Cisco ISE Restore Operation, page 8 Export Authentication and Authorization Policy Configuration,
Backup Data Type, page 1 Backup and Restore Repositories, page 2 On-Demand and Scheduled Backups, page 3 Cisco ISE Restore Operation, page 8 Export Authentication and Authorization Policy Configuration,
Using the VMware vrealize Orchestrator Client
 Using the VMware vrealize Orchestrator Client vrealize Orchestrator 7.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by
Using the VMware vrealize Orchestrator Client vrealize Orchestrator 7.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by
Grapevine web hosting user manual. 12 August 2005
 Grapevine web hosting user manual 12 August 2005 Grapevine web hosting user manual 2 Contents Contents... 2 Introduction... 4 System features... 4 How it looks... 5 Main navigation... 5 Reports... 6 Web
Grapevine web hosting user manual 12 August 2005 Grapevine web hosting user manual 2 Contents Contents... 2 Introduction... 4 System features... 4 How it looks... 5 Main navigation... 5 Reports... 6 Web
70-290: MCSE Guide to Managing a Microsoft Windows Server 2003 Environment, Enhanced. Chapter 7: Advanced File System Management
 70-290: MCSE Guide to Managing a Microsoft Windows Server 2003 Environment, Enhanced Chapter 7: Advanced File System Management Objectives Understand and configure file and folder attributes Understand
70-290: MCSE Guide to Managing a Microsoft Windows Server 2003 Environment, Enhanced Chapter 7: Advanced File System Management Objectives Understand and configure file and folder attributes Understand
CORAL Resources Module User Guide
 CORAL Resources Module User Guide About CORAL Resources A component of Hesburgh Libraries locally developed ERM, CORAL Resources aids in the management of the electronic resource workflow from the initial
CORAL Resources Module User Guide About CORAL Resources A component of Hesburgh Libraries locally developed ERM, CORAL Resources aids in the management of the electronic resource workflow from the initial
Active Directory Synchronisation
 Active Directory Synchronisation Table of Contents Overview... 3 Important Notes... 3 Installation & Configuration... 4 Configuration & Field Mappings... 4 Attribute Mappings... 7 Adding New Mappings...
Active Directory Synchronisation Table of Contents Overview... 3 Important Notes... 3 Installation & Configuration... 4 Configuration & Field Mappings... 4 Attribute Mappings... 7 Adding New Mappings...
NPTEL Course Jan K. Gopinath Indian Institute of Science
 Storage Systems NPTEL Course Jan 2012 (Lecture 40) K. Gopinath Indian Institute of Science Google File System Non-Posix scalable distr file system for large distr dataintensive applications performance,
Storage Systems NPTEL Course Jan 2012 (Lecture 40) K. Gopinath Indian Institute of Science Google File System Non-Posix scalable distr file system for large distr dataintensive applications performance,
Unicon TM CL Series Software REFERENCE MANUAL
 Unicon TM CL Series Software REFERENCE MANUAL Trademarks The following items are trademarks or registered trademarks of Kaba Mas in the United States and/or other countries. Unicon Windows, Windows 2000,
Unicon TM CL Series Software REFERENCE MANUAL Trademarks The following items are trademarks or registered trademarks of Kaba Mas in the United States and/or other countries. Unicon Windows, Windows 2000,
Distributed Systems. Before We Begin. Advantages. What is a Distributed System? CSE 120: Principles of Operating Systems. Lecture 13.
 CSE 120: Principles of Operating Systems Lecture 13 Distributed Systems December 2, 2003 Before We Begin Read Chapters 15, 17 (on Distributed Systems topics) Prof. Joe Pasquale Department of Computer Science
CSE 120: Principles of Operating Systems Lecture 13 Distributed Systems December 2, 2003 Before We Begin Read Chapters 15, 17 (on Distributed Systems topics) Prof. Joe Pasquale Department of Computer Science
Veritas NetBackup for Microsoft Exchange Server Administrator s Guide
 Veritas NetBackup for Microsoft Exchange Server Administrator s Guide for Windows Release 8.1.1 Veritas NetBackup for Microsoft Exchange Server Administrator s Guide Last updated: 2018-02-16 Document version:netbackup
Veritas NetBackup for Microsoft Exchange Server Administrator s Guide for Windows Release 8.1.1 Veritas NetBackup for Microsoft Exchange Server Administrator s Guide Last updated: 2018-02-16 Document version:netbackup
EMC SourceOne for File Systems
 EMC SourceOne for File Systems Version 7.2 Administration Guide 302-000-958 REV 02 Copyright 2005-2015 EMC Corporation. All rights reserved. Published in the USA. Published December 9, 2015 EMC believes
EMC SourceOne for File Systems Version 7.2 Administration Guide 302-000-958 REV 02 Copyright 2005-2015 EMC Corporation. All rights reserved. Published in the USA. Published December 9, 2015 EMC believes
DISTRIBUTED SYSTEMS [COMP9243] Lecture 9a: Naming WHAT IS NAMING? Name: Entity: Slide 3. Slide 1. Address: Identifier:
![DISTRIBUTED SYSTEMS [COMP9243] Lecture 9a: Naming WHAT IS NAMING? Name: Entity: Slide 3. Slide 1. Address: Identifier: DISTRIBUTED SYSTEMS [COMP9243] Lecture 9a: Naming WHAT IS NAMING? Name: Entity: Slide 3. Slide 1. Address: Identifier:](/thumbs/89/100181269.jpg) BASIC CONCEPTS DISTRIBUTED SYSTEMS [COMP9243] Name: String of bits or characters Refers to an entity Slide 1 Lecture 9a: Naming ➀ Basic Concepts ➁ Naming Services ➂ Attribute-based Naming (aka Directory
BASIC CONCEPTS DISTRIBUTED SYSTEMS [COMP9243] Name: String of bits or characters Refers to an entity Slide 1 Lecture 9a: Naming ➀ Basic Concepts ➁ Naming Services ➂ Attribute-based Naming (aka Directory
VMware Mirage Getting Started Guide
 Mirage 5.8 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions of this document,
Mirage 5.8 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions of this document,
NetBackup TM for VMware configuration
 289771 NetBackup TM for VMware configuration This document describes how to use NetBackup 6.5 with VMware virtual machines that run on VMware ESX servers. License requirements Features available in NetBackup
289771 NetBackup TM for VMware configuration This document describes how to use NetBackup 6.5 with VMware virtual machines that run on VMware ESX servers. License requirements Features available in NetBackup
(Self-Study) Identify How to Back Up and Restore NetWare Systems
 SECTION 18 (Self-Study) Identify How to Back Up and Restore NetWare Systems The following objective will be tested: Develop a Network Backup Strategy In this section you learn how you can back up and restore
SECTION 18 (Self-Study) Identify How to Back Up and Restore NetWare Systems The following objective will be tested: Develop a Network Backup Strategy In this section you learn how you can back up and restore
Backup and Restore Operations
 Backup Data Type Backup Data Type, on page 1 Backup and Restore Repositories, on page 1 On-Demand and Scheduled Backups, on page 3 Cisco ISE Restore Operation, on page 8 Export Authentication and Authorization
Backup Data Type Backup Data Type, on page 1 Backup and Restore Repositories, on page 1 On-Demand and Scheduled Backups, on page 3 Cisco ISE Restore Operation, on page 8 Export Authentication and Authorization
Google File System 2
 Google File System 2 goals monitoring, fault tolerance, auto-recovery (thousands of low-cost machines) focus on multi-gb files handle appends efficiently (no random writes & sequential reads) co-design
Google File System 2 goals monitoring, fault tolerance, auto-recovery (thousands of low-cost machines) focus on multi-gb files handle appends efficiently (no random writes & sequential reads) co-design
vcenter Server Installation and Setup Update 1 Modified on 30 OCT 2018 VMware vsphere 6.7 vcenter Server 6.7
 vcenter Server Installation and Setup Update 1 Modified on 30 OCT 2018 VMware vsphere 6.7 vcenter Server 6.7 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/
vcenter Server Installation and Setup Update 1 Modified on 30 OCT 2018 VMware vsphere 6.7 vcenter Server 6.7 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/
Distributed File Systems. Directory Hierarchy. Transfer Model
 Distributed File Systems Ken Birman Goal: view a distributed system as a file system Storage is distributed Web tries to make world a collection of hyperlinked documents Issues not common to usual file
Distributed File Systems Ken Birman Goal: view a distributed system as a file system Storage is distributed Web tries to make world a collection of hyperlinked documents Issues not common to usual file
MSMQ-MQSeries Bridge Configuration Guide White Paper
 MSMQ-MQSeries Bridge Configuration Guide White Paper Published: November 2000 Table of Contents Table of Contents...1 Introduction...1 Definitions... 2 How the Bridge Works...5 MSMQ-MQSeries Bridge Installation...
MSMQ-MQSeries Bridge Configuration Guide White Paper Published: November 2000 Table of Contents Table of Contents...1 Introduction...1 Definitions... 2 How the Bridge Works...5 MSMQ-MQSeries Bridge Installation...
Silberschatz and Galvin Chapter 18
 Silberschatz and Galvin Chapter 18 Distributed Coordination CPSC 410--Richard Furuta 4/21/99 1 Distributed Coordination Synchronization in a distributed environment Ð Event ordering Ð Mutual exclusion
Silberschatz and Galvin Chapter 18 Distributed Coordination CPSC 410--Richard Furuta 4/21/99 1 Distributed Coordination Synchronization in a distributed environment Ð Event ordering Ð Mutual exclusion
Active Directory Replicationm
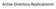 Active Directory Replicationm Site 1 Read/Write copy of Active Directory Database Ntds.dit Site 1 C D All domain controllers host a full replica of the domain information for its own domain Replication:
Active Directory Replicationm Site 1 Read/Write copy of Active Directory Database Ntds.dit Site 1 C D All domain controllers host a full replica of the domain information for its own domain Replication:
Web Browser Application Troubleshooting Guide. Table of Contents
 Web Browser Application Troubleshooting Guide The following trouble shooting guide outlines tips for common problems which may resolve incorrect or unexpected behavior of NMFTA s web based applications.
Web Browser Application Troubleshooting Guide The following trouble shooting guide outlines tips for common problems which may resolve incorrect or unexpected behavior of NMFTA s web based applications.
Chapter 3. NetWare Configuration
 Chapter 3 NetWare Configuration 3 re tpa Ch Overview... 3-2 Configuring NetWare 3.1x and 4.1x... 3-3 Primary File Server... 3-3 Configuring the NIC in NetWare Directory Services... 3-5 Configuring NetWare
Chapter 3 NetWare Configuration 3 re tpa Ch Overview... 3-2 Configuring NetWare 3.1x and 4.1x... 3-3 Primary File Server... 3-3 Configuring the NIC in NetWare Directory Services... 3-5 Configuring NetWare
Distributed systems. Lecture 6: distributed transactions, elections, consensus and replication. Malte Schwarzkopf
 Distributed systems Lecture 6: distributed transactions, elections, consensus and replication Malte Schwarzkopf Last time Saw how we can build ordered multicast Messages between processes in a group Need
Distributed systems Lecture 6: distributed transactions, elections, consensus and replication Malte Schwarzkopf Last time Saw how we can build ordered multicast Messages between processes in a group Need
Recap. CSE 486/586 Distributed Systems Google Chubby Lock Service. Recap: First Requirement. Recap: Second Requirement. Recap: Strengthening P2
 Recap CSE 486/586 Distributed Systems Google Chubby Lock Service Steve Ko Computer Sciences and Engineering University at Buffalo Paxos is a consensus algorithm. Proposers? Acceptors? Learners? A proposer
Recap CSE 486/586 Distributed Systems Google Chubby Lock Service Steve Ko Computer Sciences and Engineering University at Buffalo Paxos is a consensus algorithm. Proposers? Acceptors? Learners? A proposer
NetIQ Advanced Authentication Framework. Deployment Guide. Version 5.1.0
 NetIQ Advanced Authentication Framework Deployment Guide Version 5.1.0 Table of Contents 1 Table of Contents 2 Introduction 3 About This Document 3 NetIQ Advanced Authentication Framework Deployment 4
NetIQ Advanced Authentication Framework Deployment Guide Version 5.1.0 Table of Contents 1 Table of Contents 2 Introduction 3 About This Document 3 NetIQ Advanced Authentication Framework Deployment 4
Replication is the process of creating an
 Chapter 13 Local tion tion is the process of creating an exact copy of data. Creating one or more replicas of the production data is one of the ways to provide Business Continuity (BC). These replicas
Chapter 13 Local tion tion is the process of creating an exact copy of data. Creating one or more replicas of the production data is one of the ways to provide Business Continuity (BC). These replicas
Using the VMware vcenter Orchestrator Client. vrealize Orchestrator 5.5.1
 Using the VMware vcenter Orchestrator Client vrealize Orchestrator 5.5.1 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments
Using the VMware vcenter Orchestrator Client vrealize Orchestrator 5.5.1 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments
Storage Manager. Summary. Panel access. Modified by on 10-Jan-2014
 Storage Manager Old Content - visit altium.com/documentation Modified by on 10-Jan-2014 Related panel: Differences Panel Related documents: Version Control and Altium Designer Version Control Terminology
Storage Manager Old Content - visit altium.com/documentation Modified by on 10-Jan-2014 Related panel: Differences Panel Related documents: Version Control and Altium Designer Version Control Terminology
QVS Distributed Data Services/Controller Services for Windows. Programming Guide. Version 3
 QVS Distributed Data Services/Controller Services for Windows Programming Guide Version 3 First Edition (March 2001) This edition applies to Version 3 of the QVS Distributed Data Services/Controller Services
QVS Distributed Data Services/Controller Services for Windows Programming Guide Version 3 First Edition (March 2001) This edition applies to Version 3 of the QVS Distributed Data Services/Controller Services
EECS 498 Introduction to Distributed Systems
 EECS 498 Introduction to Distributed Systems Fall 2017 Harsha V. Madhyastha Dynamo Recap Consistent hashing 1-hop DHT enabled by gossip Execution of reads and writes Coordinated by first available successor
EECS 498 Introduction to Distributed Systems Fall 2017 Harsha V. Madhyastha Dynamo Recap Consistent hashing 1-hop DHT enabled by gossip Execution of reads and writes Coordinated by first available successor
Mobile and Heterogeneous databases Distributed Database System Transaction Management. A.R. Hurson Computer Science Missouri Science & Technology
 Mobile and Heterogeneous databases Distributed Database System Transaction Management A.R. Hurson Computer Science Missouri Science & Technology 1 Distributed Database System Note, this unit will be covered
Mobile and Heterogeneous databases Distributed Database System Transaction Management A.R. Hurson Computer Science Missouri Science & Technology 1 Distributed Database System Note, this unit will be covered
Agents Implementation for C++ MASS Library
 Agents Implementation for C++ MASS Library CSS 497 Spring 2014 Term Report Chris Rouse Contents Work Summary... 2 Initial Goals... 2 Current Work Progress... 3 Detailed Specification... 3 Agent Diagram...
Agents Implementation for C++ MASS Library CSS 497 Spring 2014 Term Report Chris Rouse Contents Work Summary... 2 Initial Goals... 2 Current Work Progress... 3 Detailed Specification... 3 Agent Diagram...
BlueCielo Meridian Enterprise Server Quick start for application administrators
 BlueCielo Meridian Enterprise Server 2013 Quick start for application administrators BlueCielo Meridian Enterprise Server 2013 Introduction BlueCielo Publisher and Meridian Explorer have been integrated
BlueCielo Meridian Enterprise Server 2013 Quick start for application administrators BlueCielo Meridian Enterprise Server 2013 Introduction BlueCielo Publisher and Meridian Explorer have been integrated
Novell imanager 2.5 Administration Guide. novdocx (ENU) 01 February Novell imanager ADMINISTRATION GUIDE.
 Novell imanager 2.5 Administration Guide Novell imanager 2.5 March 15, 2006 ADMINISTRATION GUIDE www.novell.com Legal Notices Novell, Inc. makes no representations or warranties with respect to the contents
Novell imanager 2.5 Administration Guide Novell imanager 2.5 March 15, 2006 ADMINISTRATION GUIDE www.novell.com Legal Notices Novell, Inc. makes no representations or warranties with respect to the contents
MarkLogic Server. Flexible Replication Guide. MarkLogic 9 May, Copyright 2018 MarkLogic Corporation. All rights reserved.
 Flexible Replication Guide 1 MarkLogic 9 May, 2017 Last Revised: 9.0-1, May, 2017 Copyright 2018 MarkLogic Corporation. All rights reserved. Table of Contents Table of Contents Flexible Replication Guide
Flexible Replication Guide 1 MarkLogic 9 May, 2017 Last Revised: 9.0-1, May, 2017 Copyright 2018 MarkLogic Corporation. All rights reserved. Table of Contents Table of Contents Flexible Replication Guide
Lecture 6 Consistency and Replication
 Lecture 6 Consistency and Replication Prof. Wilson Rivera University of Puerto Rico at Mayaguez Electrical and Computer Engineering Department Outline Data-centric consistency Client-centric consistency
Lecture 6 Consistency and Replication Prof. Wilson Rivera University of Puerto Rico at Mayaguez Electrical and Computer Engineering Department Outline Data-centric consistency Client-centric consistency
Comparison of edirectory Versions
 APPENDIX Comparison of edirectory Versions There have been many different versions of edirectory over the past several years. From its early existence, edirectory has progressed from NDS 5.x, NDS 6.x,
APPENDIX Comparison of edirectory Versions There have been many different versions of edirectory over the past several years. From its early existence, edirectory has progressed from NDS 5.x, NDS 6.x,
Operating System Control Structures
 Operating System Control Structures Information about the current status of each process and resource Tables are constructed for each entity the operating system manages 26 Memory Tables Allocation of
Operating System Control Structures Information about the current status of each process and resource Tables are constructed for each entity the operating system manages 26 Memory Tables Allocation of
Commit-On-Sharing High Level Design
 Commit-On-Sharing High Level Design Mike Pershin, Alexander Zam Zarochentsev 8 August 2008 1 Introduction 1.1 Definitions VBR version-based recovery transaction an atomic operation which reads and possibly
Commit-On-Sharing High Level Design Mike Pershin, Alexander Zam Zarochentsev 8 August 2008 1 Introduction 1.1 Definitions VBR version-based recovery transaction an atomic operation which reads and possibly
BCI.com Sitecore Publishing Guide. November 2017
 BCI.com Sitecore Publishing Guide November 2017 Table of contents 3 Introduction 63 Search 4 Sitecore terms 66 Change your personal settings 5 Publishing basics 5 Log in to Sitecore Editing 69 BCI.com
BCI.com Sitecore Publishing Guide November 2017 Table of contents 3 Introduction 63 Search 4 Sitecore terms 66 Change your personal settings 5 Publishing basics 5 Log in to Sitecore Editing 69 BCI.com
Glossary. The target of keyboard input in a
 Glossary absolute search A search that begins at the root directory of the file system hierarchy and always descends the hierarchy. See also relative search. access modes A set of file permissions that
Glossary absolute search A search that begins at the root directory of the file system hierarchy and always descends the hierarchy. See also relative search. access modes A set of file permissions that
Distributed Systems COMP 212. Revision 2 Othon Michail
 Distributed Systems COMP 212 Revision 2 Othon Michail Synchronisation 2/55 How would Lamport s algorithm synchronise the clocks in the following scenario? 3/55 How would Lamport s algorithm synchronise
Distributed Systems COMP 212 Revision 2 Othon Michail Synchronisation 2/55 How would Lamport s algorithm synchronise the clocks in the following scenario? 3/55 How would Lamport s algorithm synchronise
Table 12.2 Information Elements of a File Directory
 Table 12.2 Information Elements of a File Directory Basic Information File Name File Type File Organization Name as chosen by creator (user or program). Must be unique within a specific directory. For
Table 12.2 Information Elements of a File Directory Basic Information File Name File Type File Organization Name as chosen by creator (user or program). Must be unique within a specific directory. For
GUIDELINES FOR USING DEVICE LEVEL RING (DLR) WITH ETHERNET/IP. PUB00316R ODVA, Inc. Page 1 of 18
 GUIDELINES FOR USING DEVICE LEVEL RING (DLR) WITH ETHERNET/IP PUB00316R2 2017-2018 ODVA, Inc. Page 1 of 18 Guidelines for Using Device Level Ring (DLR) with EtherNet/IP Contents 1. Introduction... 3 2.
GUIDELINES FOR USING DEVICE LEVEL RING (DLR) WITH ETHERNET/IP PUB00316R2 2017-2018 ODVA, Inc. Page 1 of 18 Guidelines for Using Device Level Ring (DLR) with EtherNet/IP Contents 1. Introduction... 3 2.
This guide describes how to use the Dfs Share Creation wizard.
 Step-by-Step Guide to Distributed File System (Dfs) Because shared files are widely distributed across networks, administrators face growing problems as they try to keep users connected to the data they
Step-by-Step Guide to Distributed File System (Dfs) Because shared files are widely distributed across networks, administrators face growing problems as they try to keep users connected to the data they
Configuring the Oracle Network Environment. Copyright 2009, Oracle. All rights reserved.
 Configuring the Oracle Network Environment Objectives After completing this lesson, you should be able to: Use Enterprise Manager to: Create additional listeners Create Oracle Net Service aliases Configure
Configuring the Oracle Network Environment Objectives After completing this lesson, you should be able to: Use Enterprise Manager to: Create additional listeners Create Oracle Net Service aliases Configure
Replica Placement. Replica Placement
 Replica Placement Model: We consider objects (and don t worry whether they contain just data or code, or both) Distinguish different processes: A process is capable of hosting a replica of an object or
Replica Placement Model: We consider objects (and don t worry whether they contain just data or code, or both) Distinguish different processes: A process is capable of hosting a replica of an object or
BusinessObjects Enterprise XI
 Overview Contents This document contains information on LDAP authentication and how to configure with this type of authentication. INTRODUCTION... 2 What Is LDAP?...2 LDAP platforms supported by...3 LDAP
Overview Contents This document contains information on LDAP authentication and how to configure with this type of authentication. INTRODUCTION... 2 What Is LDAP?...2 LDAP platforms supported by...3 LDAP
EECS 498 Introduction to Distributed Systems
 EECS 498 Introduction to Distributed Systems Fall 2017 Harsha V. Madhyastha Implementing RSMs Logical clock based ordering of requests Cannot serve requests if any one replica is down Primary-backup replication
EECS 498 Introduction to Distributed Systems Fall 2017 Harsha V. Madhyastha Implementing RSMs Logical clock based ordering of requests Cannot serve requests if any one replica is down Primary-backup replication
Arcserve Backup for Windows
 Arcserve Backup for Windows Agent for Sybase Guide r17.0 This Documentation, which includes embedded help systems and electronically distributed materials, (hereinafter referred to as the Documentation
Arcserve Backup for Windows Agent for Sybase Guide r17.0 This Documentation, which includes embedded help systems and electronically distributed materials, (hereinafter referred to as the Documentation
AccuBridge for IntelliJ IDEA. User s Guide. Version March 2011
 AccuBridge for IntelliJ IDEA User s Guide Version 2011.1 March 2011 Revised 25-March-2011 Copyright AccuRev, Inc. 1995 2011 ALL RIGHTS RESERVED This product incorporates technology that may be covered
AccuBridge for IntelliJ IDEA User s Guide Version 2011.1 March 2011 Revised 25-March-2011 Copyright AccuRev, Inc. 1995 2011 ALL RIGHTS RESERVED This product incorporates technology that may be covered
Distributed Computing Environment (DCE)
 Distributed Computing Environment (DCE) Distributed Computing means computing that involves the cooperation of two or more machines communicating over a network as depicted in Fig-1. The machines participating
Distributed Computing Environment (DCE) Distributed Computing means computing that involves the cooperation of two or more machines communicating over a network as depicted in Fig-1. The machines participating
The Google File System (GFS)
 1 The Google File System (GFS) CS60002: Distributed Systems Antonio Bruto da Costa Ph.D. Student, Formal Methods Lab, Dept. of Computer Sc. & Engg., Indian Institute of Technology Kharagpur 2 Design constraints
1 The Google File System (GFS) CS60002: Distributed Systems Antonio Bruto da Costa Ph.D. Student, Formal Methods Lab, Dept. of Computer Sc. & Engg., Indian Institute of Technology Kharagpur 2 Design constraints
Content Author's Reference and Cookbook
 Sitecore CMS 7.2 Content Author's Reference and Cookbook Rev. 140225 Sitecore CMS 7.2 Content Author's Reference and Cookbook A Conceptual Overview and Practical Guide to Using Sitecore Table of Contents
Sitecore CMS 7.2 Content Author's Reference and Cookbook Rev. 140225 Sitecore CMS 7.2 Content Author's Reference and Cookbook A Conceptual Overview and Practical Guide to Using Sitecore Table of Contents
