MDS - UNIX SYSTEM ADMINISTRATOR MANUAL. INTRODUCTION... i
|
|
|
- Homer Greer
- 6 years ago
- Views:
Transcription
1 MDS - UNIX SYSTEM ADMINISTRATOR MANUAL INTRODUCTION i SUPER USER MENU SET USER PRIVILEGE MAKE USER REMOVE USER WHO'S LOGGED ON ENABLE A TTY DISABLE A TTY SYSTEM STATUS CHANGE USER PASSWORD A SET SUPERVISOR PASSWORD D KILL A PROCESS E DISPLAY DISK SPACE F DISPLAY TERMINAL TYPES H SET TERMINAL TYPES I SHOW LOGON NAMES J USER ACCOUNTING
2 K MAIL TO ALL USERS L COPY COMPANY DATA M SET PRINTER TYPE O PRINTER UTILITIES O.1 PRINTER STATUS INFORMATION O.2 ENABLE A PRINTER O.3 DISABLE A PRINTER O.4 CANCEL SPOOLED PRINT O.5 CHANGE SYSTEM DEFAULT DESTINATION PRINTER O.6 RESTART REPORTS CURRENTLY PRINTING O.7 SET DEFAULT DESTINATION FOR INDIVIDUAL O.8 NEW PRINTER SETUP SYSTEM BACKUP SYSTEM SHUTDOWN SYSTEM STARTUP UNIX SUPER USER INTRODUCTION THE SYSTEM ADMINISTRATOR HAS ACCESS TO PROGRAMS NOT NEEDED FOR THE DAILY
3 OPERATION OF THE BUSINESS BUT NECESSARY TO MAINTAIN THE INTEGRITY OF THE SYSTEM. THE PROGRAMS ARE ACCESSED THROUGH SPECIAL LOGINS AND PASSWORDS KNOWN ONLY TO THE SYSTEM ADMINISTRATOR. THE MOST IMPORTANT IS THE SUPER USER MENU. IT CONTAINS ALL PROGRAMS NEEDED TO SET UP OR DELETE A USER FROM THE SYSTEM AND CONTROL THAT USERS ACCESS TO PROGRAMS WITHIN THE SYSTEM. THE BACKUP MENU IS ANOTHER IMPORTANT MENU USED BY THE SYSTEM ADMINISTRATOR. REGULAR BACKUPS INSURE THAT IF A CATASTROPHE OCCURS VERY LITTLE IF ANY INFORMATION IS LOST OR NEEDS TO BE RE- INPUT. THE SUPER USER AND SYSTEM SHUTDOWN FUNCTIONS ARE RARELY USED. THEY EXIST TO COPE WITH SPECIFIC PROBLEMS WITH THE SYSTEM. SUPER USER MENU TO ACCESS THIS MENU TYPE IN root IN LOWERCASE LETTERS AT THE LOGIN AND PRESS ENTER. TYPE IN THE PASSWORD.(AT INITIAL SETUP THE PASSWORD IS PASSWORD IN LOWERCASE)AND PRESS ENTER. Then type super10 at the # prompt and the SUPER-USER MENU will display. TO ACCESS ANY OF THE PROGRAMS, PRESS THE NUMBER OR LETTER ON THE MENU. 1 MAKE USER THIS PROGRAM IS USED TO ADD USERS TO THE SYSTEM. ONCE A USER HAS BEEN
4 ADDED YOU SHOULD SET PRIVILEGES(OPTION 1) FOR THE USER. NEW USERS HAVE WRITE PRIVILEGE ON A MAJORITY OF PROGRAMS UNTIL EXCLUDED. THE FIRST QUESTION YOU ARE ASKED IS: WHAT IS THE USER LOGIN NAME (3 TO 8 DIGITS)? TO SET UP A NEW USER, TYPE IN THE NAME YOU WISH THE USER TO BE IDENTIFIED BY AND PRESS ENTER. USE OF ALL LOWERCASE LETTERS FOR THE USER LOGIN NAME WILL SIMPLIFY THE LOGIN PROCESS. THE NEXT QUESTION IS: SET USERS PASSWORD ALTHOUGH THE SYSTEM ALLOWS USERS TO BE SET UP WITHOUT PASSWORDS, ALWAYS ANSWER THIS QUESTION Y THEN ENTER. SETTING UP LOGINS WITHOUT PASSWORDS DAMAGES THE SECURITY INTEGRITY OF THE SYSTEM. PASSWORDS DECREASE THE CHANCES OF UNAUTHORIZED USERS ACCESSING SENSITIVE OR CONFIDENTIAL INFORMATION. IF ANY LOGINS HAVE BEEN SET UP FOR CONVENIENCE DURING THE SETUP PROCESS, THEY SHOULD BE REMOVED.(OPTION 3) ENTER NEW PASSWORD (MINIMUM OF 5 CHARACTERS) PLEASE USE A COMBINATION OF UPPER AND LOWERCASE LETTERS AND NUMBERS. NEW PASSWORD: THE PASSWORD MAY BE A COMBINATION OF UPPER AND LOWERCASE LETTERS AND NUMBERS. FOR INITIAL SETUP OF A USER, THE LOGIN NAME MAY BE USED AS A
5 PASSWORD. ONE OF THE PRIVILEGES EACH USER HAS IS THE ABILITY TO CHANGE THEIR OWN PASSWORD. WHEN YOU GIVE THE NEW USER THEIR LOGIN AND INITIAL PASSWORD, EXPLAIN THE CHANGE PASSWORD PROCEDURE AND HAVE THEM CHANGE THEIR PASSWORD TO ONE OF THEIR CHOICE. IT IS NOT NECESSARY FOR A SYSTEM ADMINISTRATOR TO KNOW THE PASSWORD OF AN INDIVIDUAL. IF A USER FORGETS THEIR PASSWORD, USE OPTION 9 "CHANGE USER PASSWORD". THIS IS THE ONLY WAY TO HANDLE FORGOTTEN PASSWORDS. BECAUSE THE SYSTEM IS DESIGNED FOR SECURITY, NO ONE CAN VIEW A PASSWORD, NOT EVEN A PROGRAMMER. TO MAINTAIN SYSTEM SECURITY, PASSWORDS SHOULD BE CHANGED ON A REGULAR BASIS. TYPE IN THE PASSWORD(THE PASSWORD DOES NOT DISPLAY AS YOU TYPE) AND PRESS ENTER. THE SCREEN DISPLAYS A NEW LINE. RE-ENTER NEW PASSWORD: TYPE IN THE PASSWORD AGAIN AND PRESS ENTER. THIS STEP IS TO CATCH ANY TYPING ERRORS. THE SYSTEM COMPARES THE TWO ENTRIES FOR A MATCH. IF THE TWO ENTRIES DO NOT MATCH THE SYSTEM RETURNS YOU TO THE FIRST STEP. IF THE TWO ENTRIES MATCH THE NEXT SCREEN DISPLAYS. TYPE IN THE NUMBER OF THE COMPANY YOU WISH THE USER TO HAVE ACCESS TO AND PRESS ENTER. IF A USER IS TO HAVE ACCESS TO MORE THAN ONE COMPANY,
6 YOU SHOULD SET UP ADDITIONAL USER NAMES AND PASSWORDS FOR EACH COMPANY. 2 SET USER PRIVILEGE THIS PROGRAM IS USED TO DEFINE THE AREAS A PARTICULAR USER IS ALLOWED ACCESS TO AND WHAT LEVEL OF ACCESS THEY HAVE. THE USER MUST FIRST BE SET UP WITH A USER LOGIN NAME(OPTION 2) BEFORE PRIVILEGES CAN BE SET. PRIVILEGES ARE SET ON TWO LEVELS; MENU OR PROGRAMS WITHIN THE MENU. READ, WRITE, OR NONE ARE THE TYPES OF USER ACCESS. THE FIRST QUESTION ASKED IS: WHAT IS THE USER LOGIN NAME (3 TO 8 DIGITS)? TYPE IN THE USER LOGIN NAME THAT YOU WISH TO DEFINE OR CHANGE PRIVILEGES(MUST BE TYPED EXACTLY AS SET UP) FOR AND PRESS ENTER. IF THE USER LOGIN NAME IS VALID THE SYSTEM ASKS: SET PRIVILEGE FOR (USER NAME) BY MENU OR PROGRAM? PRIVILEGES ARE USED TO TAILOR ACCESS TO PROGRAMS AND MENUS TO THE NEEDS OF AN INDIVIDUAL USER. MENUS AND PROGRAMS THAT A DATA ENTRY PERSON MUST HAVE WRITE ACCESS TO IN ORDER TO COMPLETE THE TASKS ASSIGNED WOULD NOT BE AREAS THAT YOU WOULD WANT MOST OTHER USERS TO HAVE WRITE ACCESS TO.
7 SOME OF THE OTHER USERS OF THE SYSTEM MIGHT NEED TO HAVE READ ACCESS TO SOME PROGRAMS FOR RESEARCH BUT SHOULD NOT HAVE WRITE ACCESS IN ORDER TO CONTROL AND STANDARDIZE INFORMATION ENTERED INTO THE SYSTEM. SET PRIVILEGE BY MENU IF A USER SHOULD HAVE READ, WRITE OR NO ACCESS TO THAT MENU. A MENU THAT ALL USERS SHOULD HAVE WRITE ACCESS TO IS THE "MAIN MENU" OTHERWISE THEY ARE UNABLE TO DO ANYTHING ON THE SYSTEM. A MENU THAT NO USER SHOULD HAVE ACCESS TO BECAUSE IT IS NOT CURRENTLY BEING USED IS THE PAYROLL MENU. SET PRIVILEGES BY PROGRAM IF A USER HAS DIFFERENT TYPES OF ACCESS TO PROGRAMS WITHIN A MENU. TYPE IN M OR P AND PRESS ENTER. IF YOU CHOOSE M, THE SYSTEM ASKS: SET PRIVILEGE TO READ WRITE OR NONE? TYPE IN R FOR READ, W FOR WRITE, OR N FOR NONE TO SET THE TYPE OF ACCESS YOU WANT THE USER TO HAVE FOR THE MENUS YOU SELECT. IF YOU ARE SETTING PRIVILEGES BY MENU, PRESS THE NUMBER OR LETTER OF THE MENUS DISPLAYED ON THE SCREEN. NO ACKNOWLEDGEMENT OF SELECTION IS MADE. THE ONLY THING THE SCREEN DOES IS BLINK. CONTINUE PRESSING MENU SELECTIONS UNTIL ALL MENUS HAVE BEEN SELECTED THAT YOU WISH TO HAVE THE TYPE OF ACCESS CHOSEN ON THE PREVIOUS SCREEN. WHEN YOU ARE FINISHED
8 SELECTING MENUS, PRESS PF2 TO EXIT THE MENU SELECTION SCREEN. IF YOU ARE SETTING PRIVILEGES BY PROGRAM, PRESS THE NUMBER OR LETTER OF THE MENU THAT THE PROGRAMS ARE IN. A NEW SCREEN DISPLAY SHOWING PROGRAMS CONTAINED IN THAT MENU THAT THE TYPE OF ACCESS CAN BE CHANGED FOR. THE SCREENS DISPLAYED VARIES FOR EACH MENU SELECTION. USE THE UP/DOWN ARROW KEYS OR ENTER KEY TO MOVE THE CURSOR TO THE PROGRAMS YOU WISH TO CHANGE ACCESS PRIVILEGES FOR. TYPE IN R FOR READ ACCESS, W FOR WRITE ACCESS, OR N FOR NONE AND PRESS ENTER. CONTINUE UNTIL ALL PROGRAMS ARE SET AS DESIRED. PRESS PF2 TO EXIT THE PROGRAMS SCREEN. CONTINUE SELECTING MENUS AND SETTING PRIVILEGES FOR PROGRAMS UNTIL ALL CHANGES ARE COMPLETE. PRESS PF2 TO EXIT. TO CHANGE THE COMPANY THE USER HAS ACCESS TO, TYPE IN THE NUMBER DISPLAYED TO THE LEFT OF THE COMPANY AND PRESS ENTER. IF YOU DO NOT WISH TO CHANGE THE COMPANY, PRESS ENTER. YOU ARE RETURNED TO THE "SUPER USER MENU". THIS SELECTION MAY BE CHOSEN AS MANY TIMES AS NEEDED TO SET UP THE VARIOUS TYPES OF ACCESS AT THE LEVEL DESIRED. A CHANGE TO A PRIVILEGE BY MENU OR BY PROGRAM OVERRIDES PREVIOUS SELECTIONS.
9 4 WHO'S LOGGED ON THIS PROGRAM DISPLAYS A LISTING OF ALL USERS LOGGED ONTO THE SYSTEM, THE TERMINAL OR TTY THEY ARE USING, DATE AND TIME THEY LOGGED ON, THE PROCESS LAST USED, AND HOW LONG SINCE THEY TOUCHED A KEY. A PERIOD INDICATES LESS THAN A MINUTE HAS PASSED SINCE A KEY WAS TOUCHED. THIS DISPLAY CAN BE USED TO IDENTIFY THE NUMBER OF A TERMINAL A USER IS LOGGED IN ON IF THE TERMINAL NUMBER IS UNKNOWN. THIS INFORMATION IS SOMETIMES NEEDED IF A TERMINAL IS LOCKED UP AND THE SYSTEM ADMINISTRATOR HAS DETERMINED THAT THE ONLY WAY LEFT TO UNLOCK IT IS TO KILL A PROCESS.(OPTION D) USE THE ENTER KEY TO MOVE THE DISPLAY DOWN ONE LINE AND THE SHIFT BAR TO MOVE THE DISPLAY DOWN ONE PAGE. PRESS Q TO QUIT THEN ANY KEY TO EXIT. 5 ENABLE A TTY THE ENABLE FUNCTION IS NORMALLY ONLY USED AT SETUP OR WHEN ADDING ANOTHER TERMINAL TO THE SYSTEM. IT IS ALSO SOMETIMES USED UNDER THE SUPERVISION OF A PROGRAMMER TO CORRECT IDENTIFICATION PROBLEMS. A TTY IS NOT A TERMINAL IS THE OUTLET THAT THE TERMINAL IS CONNECTED TO. YOU MAY SWAP TERMINALS WITHOUT ENABLING OR DISABLING TTY'S. THE ONLY QUESTION ASKED IS:
10 ENABLE WHICH TTY (EX. 2A,2B,2C,2D,11,12) TYPE IN THE NUMBER OF THE TTY(TERMINAL POSITION) AND PRESS ENTER. IF THE NUMBER IS TYPED INCORRECTLY, AN ERROR MESSAGE DISPLAYS. IF CORRECT, THE TTY IS ENABLED AND YOU MAY ENABLE ANOTHER TTY OR PRESS PF2 TO EXIT. 6 DISABLE A TTY THE DISABLE FUNCTION IS USED WHEN REMOVING A TTY(TERMINAL POSITION) FROM THE SYSTEM. THIS IS SOMETIMES USED ALONG WITH THE ENABLE FUNCTION(OPTION 5)WHEN THE SYSTEM NO LONGER RECOGNIZES A TERMINAL AND DOES NOT ACCEPT INPUT FROM THAT TERMINAL. THE TTY IS FIRST DISABLED AND THEN ENABLED TO RECONNECT THE TERMINAL WITH THE SYSTEM. THE ONLY QUESTION ASKED IS: DISABLE WHICH TTY (EX. 2A,2B,2C,2D,11,12) TYPE IN THE NUMBER OF THE TTY(TERMINAL POSITION) AND PRESS ENTER. IF THE NUMBER IS TYPED INCORRECTLY, AN ERROR MESSAGE DISPLAYS. IF CORRECT, THE TTY IS ENABLED AND YOU MAY DISABLE ANOTHER TTY OR PRESS PF2 TO EXIT. 7 SYSTEM STATUS THE SYSTEM STATUS DISPLAYS A REPORT OF WHAT FUNCTIONS ARE BEING USED BY THE SYSTEM. THIS IS USUALLY ONLY ACCESSED AT THE REQUEST OF A SUPPORT PERSON.
11 DEFINITION OF THE FIELDS FOLLOWS: UID - WHAT SUBSYSTEM THE COMPUTER IS USING PID - PROCESS IDENTIFICATION NUMBER PPID - PREVIOUS PROCESS IDENTIFICATION NUMBER C - NUMBER OF SYSTEM CALLS THAT THE PROGRAM MAKES STIME - DATE OR TIME PROCESS STARTED TTY - TERMINAL POSITION PROCESS REQUESTED AT TIME - TIME COMPUTER TOOK TO COMPLETE LAST PROCESS COMMAND - SHORT DESCRIPTION OR NAME OF PROCESS USE THE ENTER KEY TO MOVE THE DISPLAY DOWN ONE LINE AND THE SHIFT BAR TO MOVE THE DISPLAY DOWN ONE PAGE. PRESS Q TO QUIT THEN ANY KEY TO EXIT. 9 CHANGE USER PASSWORD THE CHANGE PASSWORD PROGRAM IS USED TO CHANGE AN OPERATOR'S PASSWORD. REMEMBER, AS WITH ALL PASSWORDS THIS PASSWORD IS NOT BE DISPLAYED ON THE SCREEN AS YOU TYPE. IF YOU MAKE AN ERROR IN ENTERING THE PASSWORD, BACKSPACE AND THEN RETYPE THE PASSWORD. YOU ARE ASKED FOR THE NEW PASSWORD. TYPE IT IN AND PRESS ENTER. NEXT THE COMPUTER ASKS YOU TO RETYPE THE NEW PASSWORD. NOTICE THAT THE COMPUTER MADE YOU TYPE THE PASSWORD TWICE. THE REASON FOR THIS IS THAT THE PASSWORD IS NOT DISPLAYED ON THE SCREEN AND THE COMPUTER WANTS TO GUARD AGAINST TYPING ERRORS. IF THE TWO COPIES OF THE PASSWORD DO NOT MATCH, YOU ARE INFORMED THAT THERE IS A MISMATCH AND RETURNED TO THE SYSTEM MENU.
12 THIS OPTION IS AVAILABLE TO ALL USERS IN THE MDS SYSTEM MENU.(9.3), BUT WILL ONLY ALLOW THE CURRENT LOGIN USER TO CHANGE THEIR PASSWORD. ACCESS TO OTHER USERS PASSWORDS IS NOT ALLOWED. A SET SUPERVISOR PASSWORD THIS PROGRAM ALLOWS YOU TO CHANGE THE SYSTEM ADMINISTRATOR PASSWORD AND THE SUPERVISORY PASSWORD. THIS SHOULD BE DONE ON A REGULAR BASIS TO MAINTAIN SECURITY IN THE SYSTEM. THE SCREEN DISPLAYS: SYSTEM ADMINISTRATORS PASSWORD TYPE IN THE NEW SYSTEM ADMINISTRATORS PASSWORD AND PRESS ENTER. TYPE IN THE SYSTEM ADMINISTRATOR PASSWORD AGAIN AND PRESS ENTER. IF THE TWO ENTRIES MATCH THE SYSTEM ADMINISTRATOR PASSWORD IS CHANGED. IF THE TWO ENTRIES DO NOT MATCH YOU HAVE TO START AGAIN. IF YOU DO NOT WISH TO CHANGE THE SYSTEM ADMINISTRATOR PASSWORD, PRESS ENTER. SUPERVISORY PASSWORD TYPE IN THE NEW SUPERVISORY PASSWORD AND PRESS ENTER. TYPE IN THE SUPERVISORY PASSWORD AGAIN AND PRESS ENTER. IF THE TWO ENTRIES MATCH THE SUPERVISORY PASSWORD IS CHANGED. IF THE TWO ENTRIES DO NOT MATCH YOU WILL HAVE TO START AGAIN.
13 IF YOU DO NOT WISH TO CHANGE THE SUPERVISORY PASSWORD, PRESS ENTER. D KILL A PROCESS THE KILL A PROCESS PROGRAM DISPLAYS THE SAME INFORMATION AS THE SYSTEM STATUS PROGRAM(OPTION 7 )BUT GIVES YOU THE OPPORTUNITY TO KILL A PROCESS DISPLAYED. THIS IS THE LAST RESORT WHEN A TERMINAL IS LOCKED UP AND ALL OTHER OPTIONS HAVE FAILED. YOU MUST KNOW THE TTY NUMBER OF THE TERMINAL THAT IS LOCKED UP AND THE FIRST PROCESS EXECUTED AFTER LOGON IN ORDER TO SUCCESSFULLY EXECUTE THE KILL A PROCESS FUNCTION. IF YOU KILL THE WRONG PROCESS, DAMAGE TO THE SYSTEM CAN OCCUR. MAKE SURE YOU THOROUGHLY UNDERSTAND THE PROCEDURE BEFORE ATTEMPTING THIS FUNCTION. SCAN THE LIST TO FIND THE LAST LINE OF INFORMATION FOR THE TTY AND WORK BACKWARDS UP THE LIST UNTIL YOU FIND THE PPID(PREVIOUS PROCESS ID) FOR THAT TTY THAT IS 1(ONE) WITH A PID(PROCESS ID) GREATER THAN 1(ONE) NOT IN THE ROOT SYSTEM. TYPE IN THE PID NUMBER AND PRESS ENTER. IF YOU HAVE SUCCESSFULLY EXECUTED THE KILL A PROCESS FUNCTION, THE LOCKED UP TERMINAL SHOULD UNLOCK AND GO TO LOGIN. E DISPLAY DISK SPACE THIS PROGRAM SHOWS HOW MANY BLOCKS OF MEMORY ARE AVAILABLE, HOW MANY
14 HAVE BEEN USED, HOW MANY ARE FREE, AND THE PERCENTAGE OF THE TOTAL USED. THIS IS USED TO DETERMINE IF YOU ARE GETTING CLOSE TO MEMORY CAPACITY. THE EFFICIENCY OF THE SYSTEM IS DRASTICALLY REDUCED WHEN THE PERCENTAGE USED GOES BEYOND 75%. CONTACT YOUR SUPPORT PERSON WHEN THIS OCCURS AND REQUEST A REVIEW OF FILE SYSTEM. F DISPLAY TERMINAL TYPES THIS PROGRAM SHOWS ALL TERMINAL TYPES CURRENTLY SUPPORTED BY MDS. IF YOU ACCIDENTALLY GO INTO THIS PROGRAM YOU WILL HAVE TO ENTER THROUGH ALL THE PAGES TO GET OUT. H SET TERMINAL TYPES SET TERMINAL TYPES ALLOWS YOU TO SET OR CHANGE THE TYPE OF TERMINALS RECOGNIZED BY THE SYSTEM. SET AT INSTALLATION. PRESS PF2 TO EXIT. IF YOU NEED TO CONNECT A DIFFERENT TYPE OF TERMINAL TO THE SYSTEM, CONTACT YOUR SUPPORT PERSON FOR HELP. I SHOW LOGON NAMES DISPLAYS ALL USER NAMES THAT HAVE ACCESS TO THE SYSTEM. PRESS ANY KEY TO EXIT. J USER ACCOUNTING GENERATES A LISTING OF USERS THAT LOGGED INTO THE COMPUTER SYSTEM AS
15 WELL AS DATE, TIME OF LOGIN AND LOGOFF. PRESS 1 THEN ENTER TO DISPLAY THE USERS OF THE SYSTEM SINCE THE LAST TIME THE DATA WAS REMOVED. THE DISPLAY SHOWS THE USER NAME, DATE AND TIME LOGGED ON, AND DATE AND TIME LOGGED OFF. PRESS 2 THEN ENTER TO PRINT THE LISTING. THE REPORT WILL PRINT AS SOON AS IT IS FINISHED PROCESSING. PRES 3 TO PURGE THE ACCOUNTING DATA IN THE SYSTEM. THE ACCOUNTING DATA INFORMATION SHOULD BE PRINTED OUT AND REMOVED A MINIMUM OF EVERY THREE MONTHS. PRESS PF2 TO EXIT. K MAIL TO ALL USERS THIS PROGRAM IS VERY SIMILAR TO THE MAIL PROGRAM IN THE SYSTEM MENU(9.5)EXCEPT THAT IT PLACES MAIL IN THE MAILBOXES OF ALL USERS OF THE SYSTEM INSTEAD OF A SINGLE USER. PRESS 1 TO SHOW THE USER LOGIN NAMES IN THE SYSTEM. PRESS 2 TO SEND MAIL TO A USER. THE COMPUTER DISPLAYS THE VALID USER LOGIN'S ACROSS THE TOP OF THE SCREEN AND: ENTER THE MESSAGE TYPE IN THE MESSAGE YOU WISH TO SEND AND PRESS ENTER THE COMPUTER RETURNS TO THE "SUPER USER MENU".
16 L COPY COMPANY DATA THIS PROGRAM SHOULD ONLY BE ENTERED WITH THE SUPERVISION OF YOUR SUPPORT PERSON. THIS UTILITY SHELL COPIES MDS COMPANY DATA FILES FROM ONE COMPANY TO ANOTHER COMPANY. THIS PROCESS RENAMES THE DATA FILES AS NECESSARY, AS WELL AS CHANGING DIRECTORIES IF NEEDED. THE FILES BEING COPIED DISPLAY ON THE SCREEN. M SET PRINTER TYPE AT INSTALLATION THE PRINTER DEFINITION "EPS100N" IS SET UP. THIS HANDLES ANY EPSON PRINTER, THE TOSHIBA 2600, AND OTHER PRINTERS INSTALLED AT SETUP. IF YOU NEED ANY ADDITIONAL PRINTER DEFINED FOR USE WITH THE SYSTEM, CONTACT YOUR SUPPORT PERSON. THE OPTION CONTROLS COMPRESSED PRINTING TO ALLOW WIDE REPORTS TO PRINT ON NARROW(80 COLUMN) PAPER. THE TRAILING "N" IN EPS1000N INDICATES COMPRESSED PRINTING ENABLED. THIS OPTION WILL ALSO ALLOW COMPLETELY DIFFERENT PRINTERS TO BE USED BY ANY COMBINATION OF TERMINALS. O PRINTER UTILITIES THE SUPER USER PRINTER UTILITIES MENU CONTAINS ALL PROGRAMS NECESSARY FOR MASTER CONTROL OF PRINTER FUNCTIONS. PRESS PF2 TO EXIT THE MENU.
17 O.1 PRINTER STATUS INFORMATION THIS PROGRAM SHOWS A LISTING OF THE STATUS OF ALL PRINTERS IN THE SYSTEM. THIS PROGRAM IS USED BY THE SYSTEM ADMINISTRATOR WHEN PROBLEMS OCCUR WITH PRINTERS TO FIND OUT IF PRINTERS ARE ENABLED AND ACCEPTING PRINT REQUESTS. PRESS ANY KEY TO EXIT. O.2 ENABLE A PRINTER THIS PROGRAM DISPLAYS A LIST OF PRINTER NAMES AND ALLOWS YOU TO ENABLE A PRINTER BY ENTERING THE NAME OF THE PRINTER OR YOU CAN ENTER Q TO EXIT. O.3 DISABLE A PRINTER THIS PROGRAM IS USED BY THE SYSTEM ADMINISTRATOR TO DISABLE A PRINTER. THIS MAY BE NECESSARY IF A PRINTER BREAKS DOWN AND YOU DO NOT WANT REPORTS TO BE SENT TO THE PRINTER. IT ALSO IS USED WITH THE ENABLE SOMETIMES IF THERE IS PRINTER PROBLEMS. DISABLING AND THEN ENABLING A PRINTER SOMETIMES CLEARS UP PRINTER PROBLEMS. O.4 CANCEL SPOOLED PRINT THIS PROGRAM IS USED BY THE SYSTEM ADMINISTRATOR TO CANCEL A PRINT JOB THAT HAS BEEN SENT TO A PRINTER. THIS PROGRAM COMES IN HANDY WHEN
18 SOMEONE HAS ACCIDENTALLY(OR INTENTIONALLY) REQUESTED A LARGE REPORT THAT WILL TIE THE PRINTER UP FOR AN UNACCEPTABLE AMOUNT OF TIME. LARGE REPORTS SHOULD BE PRINTED AT NIGHT. A LISTING OF ALL REQUESTED JOBS APPEARS. IF THE PRINT JOB YOU WISH TO CANCEL IS THE ONE LISTED AS CURRENTLY PRINTING, ALL YOU HAVE TO DO TO CANCEL IT IS PRESS ENTER. IF THE JOB YOU WISH TO CANCEL IS NOT THE ONE CURRENTLY PRINTING, TYPE IN THE JOB NUMBER AND PRESS ENTER. IF THE JOB YOU WISH TO CANCEL IS FOR A PRINTER THAT IS NOT YOUR DEFAULT PRINTER, YOU MUST CHANGE THE DEFAULT DESTINATION PRINTER TO THAT PRINTER.(O.5) BEFORE CANCELLING THE PRINT JOB. THE CANCEL OPTION IS ALSO AVAILABLE IN THE MDS SYSTEM MENU.(9.B.4) O.5 CHANGE SYSTEM DEFAULT DESTINATION SPOOL PRINTER THIS OPTION IS SIMILAR TO THE OPTION IN THE MDS PRINTER UTILITIES MENU(9.B.5) THAT LETS YOU CHANGE THE DEFAULT DESTINATION PRINTER FOR A SINGLE TERMINAL. THE ONLY DIFFERENCE IS THAT THIS PROGRAM ALLOWS YOU TO CHANGE THE DEFAULT PRINTER FOR ALL TERMINALS NOT PREVIOUSLY DEFINED WITH A DEFAULT PRINTER. A LIST OF THE AVAILABLE PRINTERS IS SHOWN AT THE TOP LEFT. TO CHANGE THE DEFAULT PRINTER, TYPE IN A PRINTER NAME FROM THE LIST EXACTLY AS IT IS SHOWN ON THE LIST AND PRESS ENTER. YOU ARE
19 RETURNED TO THE "SUPER USER PRINTER UTILITIES MENU". CHECK THE INVERSE VIDEO DISPLAY TO THE RIGHT OF THE CHANGE SYSTEM DEFAULT DESTINATION SPOOL PRINTER OPTION TO MAKE SURE THE SYSTEM ACCEPTED THE NEW PRINTER. THE NAME OF THE PRINTER SELECTED SHOULD BE DISPLAYED AS THE DEFAULT DESTINATION PRINTER. IF THE PRINTER DISPLAYED IS NOT THE ONE YOU SELECTED, TRY THE PROCEDURE AGAIN. O.6 RESTART REPORTS CURRENTLY PRINTING THIS OPTION STOPS THE SCHEDULER AND SENDS A TOP OF FORM TO THE PRINTER. IT THEN RESTARTS THE REPORT PRINTING IF THE REPORT PRINTING WAS FOR THE DEFAULT PRINTER. IF THE REPORT PRINTING WAS NOT ON THE DEFAULT PRINTER, YOU MUST CHANGE THE DEFAULT DESTINATION PRINTER(O.5) TO THAT PRINTER IN ORDER TO RESTART THAT REPORT. O.7 SET DEFAULT DESTINATION FOR INDIVIDUAL TERMINALS THIS PROGRAM ALLOWS YOU TO CHANGE THE PRINTER THAT AN INDIVIDUAL TERMINAL SENDS ITS PRINT JOBS TO. O.8 NEW PRINTER SETUP New printers should be first setup in SCO UNIX ADMINISTRATION. After the Printer is working (type: lp d(printername) /etc/hosts) it should be Setup in MDS. First put an entry into the Printer type definition file, Which will tell MDS what control codes to send the printer. Then optionally, You can set this printer as a default destination by login name or tty.
20 SYSTEM BACKUP SYSTEM BACKUPS ARE DOWN DAILY AND KEPT FOR A WEEK. A FULL SYSTEM BACKUP SHOULD BE DONE AT LEAST ONCE A MONTH. SIERRA USES TAPES (CARTRIDGES) FOR IT'S BACKUP MEDIA. YOU SHOULD HAVE BACKUP TAPES LABELED FOR A MINIMUM OF EACH DAY PLUS A BACKUP TAPE LABELED FOR THE LAST MONTH CLOSED. EXTRA BACKUP TAPES ARE LABELLED AS REQUIRED. BACKUPS CAN BE RUN WHILE USERS ARE ON THE SYSTEM. THE SYSTEM RUNS THE BACKUP UNTIL IT ENCOUNTERS A FILE THAT A USER IS ACCESSING THAT IT NEEDS TO BACKUP. IT WAITS UNTIL THE USER RELEASES THE FILE THEN CONTINUES THE BACKUP. IF A USER TRIES TO ACCESS A FILE THAT THE SYSTEM IS CURRENTLY BACKING UP, THEY ARE DENIED ACCESS UNTIL THE SYSTEM FINISHES WITH AND RELEASES THAT FILE. TO ENTER THE BACKUP PROGRAM, TYPE IN BACKUP IN LOWERCASE LETTERS AND PRESS ENTER. THE COMPUTER DISPLAYS A MENU THAT ALLOWS YOU TO SELECT THE MEDIA YOU WANT TO USE FOR BACKUP. SELECT IF YOU WANT TO USE DISK OR CARTRIDGE(TAPE) BACKUP MEDIA. PRESS THE DESIRED SELECTION THEN ENTER TO SELECT CARTRIDGE MEDIA. IF YOU HAVE ENTERED THE BACKUP PROGRAM IN ERROR OR DO NOT WANT TO A
21 BACKUP, PRESS 3 THEN ENTER TO ABORT THE BACKUP. THE NEXT SCREEN DISPLAYED IS THE FILE SYSTEM MAINTENANCE MENU. IF YOU PRESS 1 OR 2 THEN ENTER, THE SYSTEM ASKS YOU TO INSERT THE MEDIA INTO THE DRIVE AND PRESS ENTER. THE BACKUP BEGINS IMMEDIATELY. THE DAILY BACKUP COPIES ALL TRANSACTIONS FOR THE DAY INPUT ON THE SYSTEM TO THE BACKUP MEDIA. THE FULL SYSTEM BACKUP COPIES ALL THE TRANSACTIONS PLUS ALL THE SYSTEM PROGRAMS. IF YOU PRESS 3 THEN ENTER, THE SYSTEM ASKS FOR THE FILE PATHNAME. THE PATHNAME MUST BE TYPED IN COMPLETELY. WHEN YOU PRESS ENTER, THE SYSTEM ASKS FOR ANOTHER PATHNAME. CONTINUE ENTERING PATHNAME UNTIL FINISHED. PRESS ENTER AT A BLANK PATHNAME TO START THE BACKUP. THE SYSTEM TAKES THE PATHNAMES ENTERED, FINDS THEM ON THE MEDIA, FINDS THEM ON THE SYSTEM AND REPLACES THE SYSTEM FILES WITH THE MEDIA FILES. THIS SHOULD ONLY BE DONE WITH THE SUPERVISION OF YOUR SUPPORT PERSON. IF YOU PRESS 4 THEN ENTER, THE SYSTEM ASKS YOU TO INSERT THE MEDIA AND PRESS ENTER. THE SYSTEM COPIES FILES FROM THE MEDIA AND WRITES THEM OVER THE FILES IN THE SYSTEM. THIS SHOULD ONLY BE DONE WITH THE SUPERVISION OF YOUR SUPPORT PERSON. IF YOU DO NOT WISH TO CONTINUE THE BACKUP PRESS Q TO ABORT THE BACKUP. YOU ARE RETURNED TO THE LOGIN.
22 IF YOU ARE IN THE PROCESS OF DOING A BACKUP OR RESTORE AND YOU NEED TO ABORT, THE ONLY WAY YOU CAN ABORT IS THE PRESS THE DELETE KEY. THIS IS THE ONLY WAY YOU CAN BREAK OUT OF A BACKUP ONCE IT IS IN PROGRESS. THIS IS VERY DANGEROUS IF YOU ARE DOING A RESTORE. IT IS ADVISED THAT YOU DO NOT BREAK OUT OF A RESTORE UNLESS ADVISED TO DO SO BY YOUR SUPPORT PERSON. SYSTEM SHUTDOWN IT IS NOT REQUIRED OR ADVISED THAT YOU SHUT THE SYSTEM DOWN EACH NIGHT. SYSTEM SHUTDOWNS ARE USUALLY DONE IF THERE IS A POSSIBILITY OF THE POWER GOING OFF OR BEING SHUT OFF FOR AN EXTENDED PERIOD. BATTERY BACKUPS ARE PROVIDED AT EACH LOCATION TO HANDLE TEMPORARY POWER LOSES. IF POWER IS LOST AND THE SYSTEM SWITCHES TO THE BACKUP BATTERIES A DETERMINATION MUST BE MADE BY THE SYSTEM ADMINISTRATOR AS TO THE PROBABLE LENGTH OF THE POWER LOSS. IF THE SYSTEM ADMINISTRATOR FEELS THE POWER LOSS WILL EXTEND PAST THE BATTERY BACKUP RESERVES THE SYSTEM SHOULD BE SHUT DOWN. TO SHUTDOWN THE SYSTEM, TYPE DOWN IN LOWERCASE LETTERS AT THE SYSTEM LOGIN. THE COMPUTER ASKS HOW MANY MINUTES TO SHUTDOWN. THIS MAY BE FROM 0(ZERO) TO 15(FIFTEEN). TYPE IN THE NUMBER OF MINUTES TO SHUTDOWN AND PRESS ENTER. A MESSAGE IS BROADCAST EACH MINUTE TO ANY USERS STILL ON THE SYSTEM. THE MESSAGE ADVISES THEM THAT THE SYSTEM IS SHUTTING DOWN
23 IN X MINUTES AND TO LOG OFF TO PREVENT FILE DAMAGE. WHEN THE COUNTDOWN IS COMPLETE THE COMPUTER EXECUTES INTERNAL KILL COMMANDS TO CLOSE FILES. WHEN THE PROCESS IS COMPLETE A SAFE TO POWER OFF OR PRESS ANY KEY TO REBOOT MESSAGE DISPLAYS. AT THIS POINT AND ONLY AT THIS POINT IS IT SAFE TO TURN OFF THE SYSTEM. SYSTEM STARTUP IT IS SOMETIMES NECESSARY TO TURN OFF THE SYSTEM DUE TO POWER LOSS OR SYSTEM PROBLEMS. TO RESTART THE SYSTEM, TURN THE POWER ON. THE SYSTEM AUTOMATICALLY DOES A SERIES OF INTERNAL CHECKS. ONCE THE SERIES IS COMPLETE A REBOOT MESSAGE DISPLAYS. PRESS ENTER. THE SYSTEM DISPLAYS A DATE AND TIME AND ASKS YOU TO ENTER A CORRECT DATE AND TIME. IF THE DATE AND TIME DISPLAYED IS CORRECT, PRESS ENTER. OTHERWISE ENTER THE DATE AND TIME IN THE FORMAT DISPLAYED AND PRESS ENTER. AFTER THE SYSTEM CHECKS AND ENABLES ALL PERIPHERY EQUIPMENT A MESSAGE DISPLAYS GIVING THE OPTION OF PRESSING ALT D TO CONTINUE WITH NORMAL REBOOT OR ENTERING A COMMAND TO ACCESS OTHER SYSTEM CHECKS. THE NORMAL PROCEDURE IS ALT-D UNLESS INSTRUCTED OTHERWISE BY YOUR SUPPORT PERSON.
CAD-CARE TROUBLESHOOTING GUIDE
 CAD-CARE TROUBLESHOOTING GUIDE CAD-Care is a stable and error free system. The biggest problem encountered with CAD-Care is when something stops CAD-Care during a system sort. Windows Screen Savers have
CAD-CARE TROUBLESHOOTING GUIDE CAD-Care is a stable and error free system. The biggest problem encountered with CAD-Care is when something stops CAD-Care during a system sort. Windows Screen Savers have
Storage Security Software (Version )
 For Toshiba CANVIO series Storage Security Software (Version 1.00.6904) User s Manual Version 1.00 This document explains the installation process and basic usage of the Storage Security Software designed
For Toshiba CANVIO series Storage Security Software (Version 1.00.6904) User s Manual Version 1.00 This document explains the installation process and basic usage of the Storage Security Software designed
SP LOCKER USER MANUAL. v1.0
 SP LOCKER USER MANUAL v1.0 Table of Contents 1 Introduction to the SP Locker Security Software... 2 2 Before You Get Started... 2 3 Features... 2 4 Public and Secured Partition... 3 5 How to use SP Locker...
SP LOCKER USER MANUAL v1.0 Table of Contents 1 Introduction to the SP Locker Security Software... 2 2 Before You Get Started... 2 3 Features... 2 4 Public and Secured Partition... 3 5 How to use SP Locker...
Contents. Getting Started...1. Managing Your Drives...9. Backing Up & Restoring Folders Synchronizing Folders...52
 Contents Getting Started.....................................................1 Installing the Software...........................................1 Using the Maxtor System Tray Icon................................6
Contents Getting Started.....................................................1 Installing the Software...........................................1 Using the Maxtor System Tray Icon................................6
R A D I O N I C S. READYKEY K6100 Readykey for Windows. User Guide. Logging In. Logging Out. If an ID device has been issued:
 R A D I O N I C S READYKEY K6100 Readykey for Windows User Guide Logging In If an ID device has been issued: 1. Use your ID device with the desktop administration or Central Network Controller (CNC) reader,
R A D I O N I C S READYKEY K6100 Readykey for Windows User Guide Logging In If an ID device has been issued: 1. Use your ID device with the desktop administration or Central Network Controller (CNC) reader,
Chapter 4 Using the Entry-Master Disk Utilities
 Chapter 4 Using the Entry-Master Disk Utilities Now that you have learned how to setup and maintain the Entry-Master System, you need to learn how to backup and restore your important database files. Making
Chapter 4 Using the Entry-Master Disk Utilities Now that you have learned how to setup and maintain the Entry-Master System, you need to learn how to backup and restore your important database files. Making
IRONKEY D300S SECURE USB 3.0 FLASH DRIVE
 IRONKEY D300S SECURE USB 3.0 FLASH DRIVE User Guide Document No. 48000130-001.A01 D300S Page 1 of 27 Table of Contents About This Manual... 3 System Requirements...3 Recommendations...3 Setup (Windows
IRONKEY D300S SECURE USB 3.0 FLASH DRIVE User Guide Document No. 48000130-001.A01 D300S Page 1 of 27 Table of Contents About This Manual... 3 System Requirements...3 Recommendations...3 Setup (Windows
cm3520 cm3525 Security Function
 wwwiagisticsco c3520 c3525 Security Function Contents Contents 1 Security 11 Introduction 1-2 12 Tradearks and Registered Tradearks 1-2 13 Copliance with the ISO15408 Standard 1-2 14 Operating Precautions1-2
wwwiagisticsco c3520 c3525 Security Function Contents Contents 1 Security 11 Introduction 1-2 12 Tradearks and Registered Tradearks 1-2 13 Copliance with the ISO15408 Standard 1-2 14 Operating Precautions1-2
MYOB Exo PC Clock. User Guide
 MYOB Exo PC Clock User Guide 2018.01 Table of Contents Introduction to MYOB Exo PC Clock... 1 Installation & Setup... 2 Server-based... 2 Standalone... 3 Using Exo PC Clock... 4 Clocking Times... 5 Updating
MYOB Exo PC Clock User Guide 2018.01 Table of Contents Introduction to MYOB Exo PC Clock... 1 Installation & Setup... 2 Server-based... 2 Standalone... 3 Using Exo PC Clock... 4 Clocking Times... 5 Updating
This is Lab Worksheet 13 - not an Assignment. Boot Process and GRUB
 This is Lab Worksheet 13 - not an Assignment This Lab Worksheet contains some practical examples that will prepare you to complete your Assignments. You do not have to hand in this Lab Worksheet. Make
This is Lab Worksheet 13 - not an Assignment This Lab Worksheet contains some practical examples that will prepare you to complete your Assignments. You do not have to hand in this Lab Worksheet. Make
Utilities Reference Manual
 Utilities Reference Manual FASPAC 3.5 FPD/205 Faspac Systems, Inc. 7590 Fay Avenue, Suite 301 La Jolla, CA 92037 Confidential and Proprietary Copyright 2000 Faspac Systems, Inc. All Rights Reserved This
Utilities Reference Manual FASPAC 3.5 FPD/205 Faspac Systems, Inc. 7590 Fay Avenue, Suite 301 La Jolla, CA 92037 Confidential and Proprietary Copyright 2000 Faspac Systems, Inc. All Rights Reserved This
Table of Contents. A. Introduction...2. B. General Description...2. C. Features...3. D. Before Using the Security Application Program LOCK...
 v1.00 Table of Contents A. Introduction...2 B. General Description...2 C. Features...3 D. Before Using the Security Application Program LOCK...4 E. Introduction to the Security Application Program LOCK...5
v1.00 Table of Contents A. Introduction...2 B. General Description...2 C. Features...3 D. Before Using the Security Application Program LOCK...4 E. Introduction to the Security Application Program LOCK...5
Table of Contents. Overview of the TEA Login Application Features Roles in Obtaining Application Access Approval Process...
 TEAL Help Table of Contents Overview of the TEA Login Application... 7 Features... 7 Roles in Obtaining Application Access... 7 Approval Process... 8 Processing an Application Request... 9 The Process
TEAL Help Table of Contents Overview of the TEA Login Application... 7 Features... 7 Roles in Obtaining Application Access... 7 Approval Process... 8 Processing an Application Request... 9 The Process
IDEA. User s Guide. Part No IDE02 Issue 1-0, April 1995 Printed in U.S.A. (183)
 IDEA User s Guide Part No. 17500IDE02 Issue 1-0, April 1995 Printed in U.S.A. (183) 4 FOREST PARKWAY, SHELTON, CONNECTICUT 06484 TEL: 203-926-5400 FAX: 203-929-0535 This manual has been developed by Nitsuko
IDEA User s Guide Part No. 17500IDE02 Issue 1-0, April 1995 Printed in U.S.A. (183) 4 FOREST PARKWAY, SHELTON, CONNECTICUT 06484 TEL: 203-926-5400 FAX: 203-929-0535 This manual has been developed by Nitsuko
Part 1: Understanding Windows XP Basics
 542362 Ch01.qxd 9/18/03 9:54 PM Page 1 Part 1: Understanding Windows XP Basics 1: Starting Up and Logging In 2: Logging Off and Shutting Down 3: Activating Windows 4: Enabling Fast Switching between Users
542362 Ch01.qxd 9/18/03 9:54 PM Page 1 Part 1: Understanding Windows XP Basics 1: Starting Up and Logging In 2: Logging Off and Shutting Down 3: Activating Windows 4: Enabling Fast Switching between Users
Configuring Passwords and Privileges
 Configuring Passwords and Privileges Using passwords and assigning privilege levels is a simple way of providing terminal access control in your network. This chapter describes the following topics and
Configuring Passwords and Privileges Using passwords and assigning privilege levels is a simple way of providing terminal access control in your network. This chapter describes the following topics and
MILLENNIUM RELEASE 2011 UPGRADE VIA SECURE FTP
 SECURE FTP UPGRADE INSTRUCTIONS Nov 2011 MILLENNIUM RELEASE 2011 UPGRADE VIA SECURE FTP 5850 Shellmound Way Emeryville, CA 94608 510/655-6200 www.iii.com This publication is supplied for the exclusive
SECURE FTP UPGRADE INSTRUCTIONS Nov 2011 MILLENNIUM RELEASE 2011 UPGRADE VIA SECURE FTP 5850 Shellmound Way Emeryville, CA 94608 510/655-6200 www.iii.com This publication is supplied for the exclusive
Super USB. User Manual. 2007, March
 Super USB User Manual 2007, March Windows98 Driver Install/Uninstall Driver Install: 1. Execute Win 98 UFD driver, then restart PC. 2. Plug Super USB into an available USB port. A new Removable Disk drive
Super USB User Manual 2007, March Windows98 Driver Install/Uninstall Driver Install: 1. Execute Win 98 UFD driver, then restart PC. 2. Plug Super USB into an available USB port. A new Removable Disk drive
Customer Service Hours... 2 Glossary... 3 Starting Up The System... 4 Software Tips... 5 Point Of Sale: Problems And Solutions...
 Customer Service Hours... 2 Glossary... 3 Starting Up The System... 4 Software Tips... 5 Point Of Sale: Problems And Solutions... 6 Purchasing: Problems And Solutions... 9 Inventory File: Problems And
Customer Service Hours... 2 Glossary... 3 Starting Up The System... 4 Software Tips... 5 Point Of Sale: Problems And Solutions... 6 Purchasing: Problems And Solutions... 9 Inventory File: Problems And
RK-LINK TM Version 2.x Instructions
 Quick Start Steps Requirements - Windows 95 or Windows NT 4.0 or later, 16MB RAM, 20-30MB Hard Disk, 486 or better processor, Serial COM Port capable of 19.2K Baud. RKAT Module must be installed at the
Quick Start Steps Requirements - Windows 95 or Windows NT 4.0 or later, 16MB RAM, 20-30MB Hard Disk, 486 or better processor, Serial COM Port capable of 19.2K Baud. RKAT Module must be installed at the
Accessing Your Payroll Stubs via
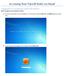 Accessing Your Payroll Stubs via Email Logging On to a Computer within the District: (does not apply to your computer at home) 1) Turn on the computer, if it is not already on. At this screen, press the
Accessing Your Payroll Stubs via Email Logging On to a Computer within the District: (does not apply to your computer at home) 1) Turn on the computer, if it is not already on. At this screen, press the
bbc Adobe Central Output Server Getting Started for Microsoft Windows Version 5.7
 bbc Adobe Central Output Server Version 5.7 Getting Started for Microsoft Windows Getting Started for Microsoft Windows Edition 4.0, March 2009 2009 Adobe Systems Incorporated All rights reserved. As of
bbc Adobe Central Output Server Version 5.7 Getting Started for Microsoft Windows Getting Started for Microsoft Windows Edition 4.0, March 2009 2009 Adobe Systems Incorporated All rights reserved. As of
Windows 2000 / XP / Vista User Guide
 Windows 2000 / XP / Vista User Guide Version 5.5.1.0 September 2008 Backup Island v5.5 Copyright Notice The use and copying of this product is subject to a license agreement. Any other use is prohibited.
Windows 2000 / XP / Vista User Guide Version 5.5.1.0 September 2008 Backup Island v5.5 Copyright Notice The use and copying of this product is subject to a license agreement. Any other use is prohibited.
User Guide V6.1g / 48730B
 READYKEY User Guide Readykey for Windows Software 17231 V6.1g / 48730B UL Listings Trademarks UL 294 - Access Control System Units Microsoft, Windows, Windows NT are either registered trademarks or trademarks
READYKEY User Guide Readykey for Windows Software 17231 V6.1g / 48730B UL Listings Trademarks UL 294 - Access Control System Units Microsoft, Windows, Windows NT are either registered trademarks or trademarks
Level 23 Eagle Software Conversion Guide. Please see page 5 for changes made to Special Security
 Level 23 Eagle Software Conversion Guide Please see page 5 for changes made to Special Security Publication No. EL1035 Publication Date: January 2002 This manual contains reference information about CCITRIAD
Level 23 Eagle Software Conversion Guide Please see page 5 for changes made to Special Security Publication No. EL1035 Publication Date: January 2002 This manual contains reference information about CCITRIAD
ADVANCED USER S GUIDE
 ADVANCED USER S GUIDE MFC-7360 MFC-7360N MFC-7460DN MFC-7470D MFC-7860DW Not all models are available in all countries. Version A SAF/GLF User's Guides and where do I find it? Which manual? What's in it?
ADVANCED USER S GUIDE MFC-7360 MFC-7360N MFC-7460DN MFC-7470D MFC-7860DW Not all models are available in all countries. Version A SAF/GLF User's Guides and where do I find it? Which manual? What's in it?
User Guide. K V1 7/05 Rev A
 NAVIGATOR REPORTER User Guide K10321-1V1 7/05 Rev A Table of Contents Conventions Used in This Manual... iii SECTION 1: General Description... 1-1 About Navigator Reporter...1-1 About User Manager...1-1
NAVIGATOR REPORTER User Guide K10321-1V1 7/05 Rev A Table of Contents Conventions Used in This Manual... iii SECTION 1: General Description... 1-1 About Navigator Reporter...1-1 About User Manager...1-1
Activant Acclaim AIX: Basic System Administration
 Activant Acclaim AIX: Basic System Administration AIX suite: course 1 of 3 Overview AIX backup Maintain AIX file systems Make new AIX users Troubleshoot Port Lockups System Shutdown AIX backup Must be
Activant Acclaim AIX: Basic System Administration AIX suite: course 1 of 3 Overview AIX backup Maintain AIX file systems Make new AIX users Troubleshoot Port Lockups System Shutdown AIX backup Must be
ARUP Connect Login User Manual November 2017
 User Manual November 2017 Table of Contents ARUP Connect Login... 1 First-Time Login... 3 Enter Password... 3 Set Up Security Questions... 3 Incorrect User Name or Password... 4 Forgotten Password... 5
User Manual November 2017 Table of Contents ARUP Connect Login... 1 First-Time Login... 3 Enter Password... 3 Set Up Security Questions... 3 Incorrect User Name or Password... 4 Forgotten Password... 5
User s Guide [Security Operations]
![User s Guide [Security Operations] User s Guide [Security Operations]](/thumbs/74/70955793.jpg) User s Guide [Security Operations] 006.1 Ver. 1.0 Contents Contents 1 Security 1.1 Introduction... 1- Compliance with the ISO15408 Standard... 1- Operating Precautions... 1- INSTALLATION CHECKLIST... 1-3
User s Guide [Security Operations] 006.1 Ver. 1.0 Contents Contents 1 Security 1.1 Introduction... 1- Compliance with the ISO15408 Standard... 1- Operating Precautions... 1- INSTALLATION CHECKLIST... 1-3
Fujitsu LifeBook U Series
 Fujitsu LifeBook U Series BIOS Guide LifeBook U Series Model: UH900 Document Date: 01/07/2010 Document Part Number: FPC58-2547-01 FUJITSU AMERICA, INC. 1 LifeBook U Series BIOS U Series BIOS BIOS SETUP
Fujitsu LifeBook U Series BIOS Guide LifeBook U Series Model: UH900 Document Date: 01/07/2010 Document Part Number: FPC58-2547-01 FUJITSU AMERICA, INC. 1 LifeBook U Series BIOS U Series BIOS BIOS SETUP
NETW 110 Lab 3 Post-Installation Configuration Page 1
 NETW 110 Lab 3 Post-Installation Configuration Page 1 Objective At the conclusion of this lab, the student will learn some very basic functions of vi, use vi to perform some post-installation configuration
NETW 110 Lab 3 Post-Installation Configuration Page 1 Objective At the conclusion of this lab, the student will learn some very basic functions of vi, use vi to perform some post-installation configuration
PowerLink Host Data Manager User Guide
 PowerLink Host Data Manager User Guide Last Updated: July 2009 Version: 2.06014 Contents Contents... 2 Introduction... 4 Quick Start... 5 Enable File Monitoring... 7 Enabling Attaché 7 File Monitoring
PowerLink Host Data Manager User Guide Last Updated: July 2009 Version: 2.06014 Contents Contents... 2 Introduction... 4 Quick Start... 5 Enable File Monitoring... 7 Enabling Attaché 7 File Monitoring
GETTING STARTED. Installing the System 2000 Hardware. Configuring Your System 2000 Hardware. Troubleshooting. Configuring Your System 2000 Network
 SYSTEM 2000 GETTING STARTED Installing the System 2000 Hardware Whether you are upgrade an existing System 2, or this is a brand new installation, there will be some hardware installation involved. We
SYSTEM 2000 GETTING STARTED Installing the System 2000 Hardware Whether you are upgrade an existing System 2, or this is a brand new installation, there will be some hardware installation involved. We
Fujitsu LifeBook A Series
 Fujitsu LifeBook A Series BIOS Guide LifeBook A Series Model: AH530 Document Date: 06/09/2010 Document Part Number: FPC58-2714-01 FUJITSU AMERICA, INC. 1 LifeBook PH520 BIOS A Series BIOS BIOS SETUP UTILITY
Fujitsu LifeBook A Series BIOS Guide LifeBook A Series Model: AH530 Document Date: 06/09/2010 Document Part Number: FPC58-2714-01 FUJITSU AMERICA, INC. 1 LifeBook PH520 BIOS A Series BIOS BIOS SETUP UTILITY
Contents. Why You Should Read This Manual...ix. 1. Introduction... 1
 Contents Why You Should Read This Manual...ix 1. Introduction... 1 Understanding Security... 2 Group and User Accounts... 2 Application Features... 3 Security Areas... 3 Using Windows Security... 7 Synchronizing
Contents Why You Should Read This Manual...ix 1. Introduction... 1 Understanding Security... 2 Group and User Accounts... 2 Application Features... 3 Security Areas... 3 Using Windows Security... 7 Synchronizing
Lockngo Professional
 Lockngo Professional User Manual Rev. 26-04.15 Updated for Version 7 Page 1 Table of contents 1. System Requirements...3 2. Using Lockngo...3 2.1. The Lockngo user interface...3 2.2. Locking your portable
Lockngo Professional User Manual Rev. 26-04.15 Updated for Version 7 Page 1 Table of contents 1. System Requirements...3 2. Using Lockngo...3 2.1. The Lockngo user interface...3 2.2. Locking your portable
Operator s Manual Version 5.4 MEMO FINANCIAL SERVICES, INC. BILL PAYMENTS TERMINAL VERSION OPERATOR S MANUAL
 Operator s Manual Version 5.4 MEMO FINANCIAL SERVICES, INC. BILL PAYMENTS TERMINAL VERSION 5.1-5.4 OPERATOR S MANUAL MEMO Technical Support 800-864-5246 MEMO Financial Services Bill Payments Terminal Page
Operator s Manual Version 5.4 MEMO FINANCIAL SERVICES, INC. BILL PAYMENTS TERMINAL VERSION 5.1-5.4 OPERATOR S MANUAL MEMO Technical Support 800-864-5246 MEMO Financial Services Bill Payments Terminal Page
Aretics T7 Installation Manual
 Aretics T7 Installation Manual 1(24) Aretics T7 Installation Manual This document describes how to manage Aretics T7 in your IT environment. Here you will find information about installing the system,
Aretics T7 Installation Manual 1(24) Aretics T7 Installation Manual This document describes how to manage Aretics T7 in your IT environment. Here you will find information about installing the system,
Lesson 3: Identifying Key Characteristics of Workgroups and Domains
 1-16 Chapter 1 Introduction to Windows XP Professional Lesson 3: Identifying Key Characteristics of Workgroups and Domains Windows XP Professional supports two types of network environments in which users
1-16 Chapter 1 Introduction to Windows XP Professional Lesson 3: Identifying Key Characteristics of Workgroups and Domains Windows XP Professional supports two types of network environments in which users
Table of Contents. D-Link SharePort Plus... 4 Introduction...4 System Requirements...4 Features...5. Installation... 6
 Table of Contents D-Link SharePort Plus... 4 Introduction...4 System Requirements...4 Features...5 Installation... 6 SharePort Plus Utility... 11 Utility Overview... 11 Device Server View... 12 Utility
Table of Contents D-Link SharePort Plus... 4 Introduction...4 System Requirements...4 Features...5 Installation... 6 SharePort Plus Utility... 11 Utility Overview... 11 Device Server View... 12 Utility
Frequently Asked Questions and other helpful information
 Frequently Asked Questions and other helpful information FAQ How do I chart? To create a chart, left click on the Chart toolbar button in the upper left corner of your CQG screen. A chart appears. In the
Frequently Asked Questions and other helpful information FAQ How do I chart? To create a chart, left click on the Chart toolbar button in the upper left corner of your CQG screen. A chart appears. In the
Configuring Cisco TelePresence Manager
 CHAPTER 3 Revised: November 27, 2006, First Published: November 27, 2006 Contents Introduction, page 3-1 System Configuration Tasks, page 3-2 Security Settings, page 3-3 Database, page 3-4 Room Phone UI,
CHAPTER 3 Revised: November 27, 2006, First Published: November 27, 2006 Contents Introduction, page 3-1 System Configuration Tasks, page 3-2 Security Settings, page 3-3 Database, page 3-4 Room Phone UI,
Client Installation and User's Guide
 IBM Tivoli Storage Manager FastBack for Workstations Version 7.1.1 Client Installation and User's Guide SC27-2809-04 IBM Tivoli Storage Manager FastBack for Workstations Version 7.1.1 Client Installation
IBM Tivoli Storage Manager FastBack for Workstations Version 7.1.1 Client Installation and User's Guide SC27-2809-04 IBM Tivoli Storage Manager FastBack for Workstations Version 7.1.1 Client Installation
Using BlueStep Backup
 Using BlueStep Backup BlueStep Backup Your data is an invaluable resource. To protect and store critical digital documents and files, BlueStep Technologies offers the ideal technological solution - BlueStep
Using BlueStep Backup BlueStep Backup Your data is an invaluable resource. To protect and store critical digital documents and files, BlueStep Technologies offers the ideal technological solution - BlueStep
Print Audit 6. Print Audit 6 Documentation Apr :07. Version: Date:
 Print Audit 6 Version: Date: 37 21-Apr-2015 23:07 Table of Contents Browse Documents:..................................................... 3 Database Documentation.................................................
Print Audit 6 Version: Date: 37 21-Apr-2015 23:07 Table of Contents Browse Documents:..................................................... 3 Database Documentation.................................................
2012 Lenovo Server Client Performs All Steps from ISP Machine 1. Check the ISP CD/DVD drive and remove any disks that are currently loaded.
 2012 Lenovo Server Client Performs All Steps from ISP Machine 1. Check the ISP CD/DVD drive and remove any disks that are currently loaded. 2. Log onto the Windows side of the ISP and go to the QsrSoft
2012 Lenovo Server Client Performs All Steps from ISP Machine 1. Check the ISP CD/DVD drive and remove any disks that are currently loaded. 2. Log onto the Windows side of the ISP and go to the QsrSoft
File System Administration
 File System Administration As System Administrator, one of your most important tasks is to ensure that your files are properly sized and error-free. Therefore, you should check the file system: Quarterly
File System Administration As System Administrator, one of your most important tasks is to ensure that your files are properly sized and error-free. Therefore, you should check the file system: Quarterly
Purchase and Setup instructions for SWVPS (Sept 15, 2014)
 Purchase and Setup instructions for SWVPS (Sept 15, 2014) Our team recommends a Virtual Private Server (VPS) that works well for only $18.00 a month. Because trading in the market requires a platform that
Purchase and Setup instructions for SWVPS (Sept 15, 2014) Our team recommends a Virtual Private Server (VPS) that works well for only $18.00 a month. Because trading in the market requires a platform that
Quick Reference Guide
 Quick Reference Guide 1 Customer Service Hours... 3 Glossary... 4 Picture Glossary... 5 Starting Up The System... 6 Software Tips... 7 Point Of Sale: Problems And Solutions... 8 Purchasing: Problems And
Quick Reference Guide 1 Customer Service Hours... 3 Glossary... 4 Picture Glossary... 5 Starting Up The System... 6 Software Tips... 7 Point Of Sale: Problems And Solutions... 8 Purchasing: Problems And
RMI ADVANTAGE Desktop User Guide. February 2010
 RMI ADVANTAGE Desktop User Guide February 2010 Table of Contents Contents Logging into the SaaS environment... 3 Logging off the Hosted Desktop... 9 Directories... 10 Wizmo AdminSet... 11 Shadowing a User...
RMI ADVANTAGE Desktop User Guide February 2010 Table of Contents Contents Logging into the SaaS environment... 3 Logging off the Hosted Desktop... 9 Directories... 10 Wizmo AdminSet... 11 Shadowing a User...
Software Conversion Guide
 Eagle SSE Software Conversion Guide Release 17 (Server Level 29) EL2157 This manual contains reference information about software products from Activant Solutions Inc. The software described in this manual
Eagle SSE Software Conversion Guide Release 17 (Server Level 29) EL2157 This manual contains reference information about software products from Activant Solutions Inc. The software described in this manual
Fujitsu STYLISTIC Q Series
 Fujitsu STYLISTIC Q Series BIOS Guide STYLISTIC Q Series Model: Q552 Document Date: 5252012 Document Part Number: FPC58-3061-01 FUJITSU AMERICA, INC. 1 STYLISTIC Q552 BIOS Q Series BIOS BIOS SETUP UTILITY
Fujitsu STYLISTIC Q Series BIOS Guide STYLISTIC Q Series Model: Q552 Document Date: 5252012 Document Part Number: FPC58-3061-01 FUJITSU AMERICA, INC. 1 STYLISTIC Q552 BIOS Q Series BIOS BIOS SETUP UTILITY
Client Installation and User's Guide
 IBM Tivoli Storage Manager FastBack for Workstations Version 7.1 Client Installation and User's Guide SC27-2809-03 IBM Tivoli Storage Manager FastBack for Workstations Version 7.1 Client Installation
IBM Tivoli Storage Manager FastBack for Workstations Version 7.1 Client Installation and User's Guide SC27-2809-03 IBM Tivoli Storage Manager FastBack for Workstations Version 7.1 Client Installation
JUN / 04 VERSION 7.1 FOUNDATION PVI EWLUTME
 JUN / 04 VERSION 7.1 FOUNDATION PVI EWLUTME www.smar.com Specifications and information are subject to change without notice. Up-to-date address information is available on our website. web: www.smar.com/contactus.asp
JUN / 04 VERSION 7.1 FOUNDATION PVI EWLUTME www.smar.com Specifications and information are subject to change without notice. Up-to-date address information is available on our website. web: www.smar.com/contactus.asp
Desktop & Laptop Edition
 Desktop & Laptop Edition USER MANUAL For Mac OS X Copyright Notice & Proprietary Information Redstor Limited, 2016. All rights reserved. Trademarks - Mac, Leopard, Snow Leopard, Lion and Mountain Lion
Desktop & Laptop Edition USER MANUAL For Mac OS X Copyright Notice & Proprietary Information Redstor Limited, 2016. All rights reserved. Trademarks - Mac, Leopard, Snow Leopard, Lion and Mountain Lion
MANAGING THE NONUNIFORM BEHAVIOUR OF TERMINALS AND KEYBOARDS. : WHEN THINGS GO WRONG
 MANAGING THE NONUNIFORM BEHAVIOUR OF TERMINALS AND KEYBOARDS. : WHEN THINGS GO WRONG Terminals and keyboards have no uniform behavioral pattern. Terminal settings directly impact the keyboard operation.
MANAGING THE NONUNIFORM BEHAVIOUR OF TERMINALS AND KEYBOARDS. : WHEN THINGS GO WRONG Terminals and keyboards have no uniform behavioral pattern. Terminal settings directly impact the keyboard operation.
CST8207: GNU/Linux Operating Systems I Lab Ten Boot Process and GRUB. Boot Process and GRUB
 Student Name: Lab Section: Boot Process and GRUB 1 Due Date - Upload to Blackboard by 8:30am Monday April 16, 2012 Submit the completed lab to Blackboard following the Rules for submitting Online Labs
Student Name: Lab Section: Boot Process and GRUB 1 Due Date - Upload to Blackboard by 8:30am Monday April 16, 2012 Submit the completed lab to Blackboard following the Rules for submitting Online Labs
Magic Card User Manual
 Table of Contents Magic Card User Manual Magic Card Introduction 2 What is Magic card? 2 Magic Card Features 2 Working Modes 3 Magic card editions 3 Installation 4 System Requirements 4 Pre-installation
Table of Contents Magic Card User Manual Magic Card Introduction 2 What is Magic card? 2 Magic Card Features 2 Working Modes 3 Magic card editions 3 Installation 4 System Requirements 4 Pre-installation
Switched-On Schoolhouse 2014 User Guide Reports & Application Functions
 Switched-On Schoolhouse 2014 User Guide Reports & Application Functions MMVI Alpha Omega Publications, Inc. Switched-On Schoolhouse 2014, Switched-On Schoolhouse. Switched-On, and their logos are registered
Switched-On Schoolhouse 2014 User Guide Reports & Application Functions MMVI Alpha Omega Publications, Inc. Switched-On Schoolhouse 2014, Switched-On Schoolhouse. Switched-On, and their logos are registered
R A D I O N I C S READYKEY K6100 READYKEY FOR WINDOWS. User Instructions. Logging In. Logging Out. If an ID device has been issued:
 R A D I O N I C S READYKEY K6100 READYKEY FOR WINDOWS User Instructions Logging In If an ID device has been issued: 1. Use your ID device with the desktop administration or Central Network Controller (CNC)
R A D I O N I C S READYKEY K6100 READYKEY FOR WINDOWS User Instructions Logging In If an ID device has been issued: 1. Use your ID device with the desktop administration or Central Network Controller (CNC)
Visual Streamline FAQ
 How do I add a right to a user ID in Streamline? This document will guide you through maintaining User rights for both User IDs and User Groups. This document will also guide you through the setup process
How do I add a right to a user ID in Streamline? This document will guide you through maintaining User rights for both User IDs and User Groups. This document will also guide you through the setup process
Aegis Padlock DT. User s Manual
 Aegis Padlock DT User s Manual Table of Contents About the Aegis Padlock Desktop Drive 4 Package contents 4 Aegis Padlock DT button panel 5 Aegis Padlock DT - Getting Started 6 Before you begin 6 Connecting
Aegis Padlock DT User s Manual Table of Contents About the Aegis Padlock Desktop Drive 4 Package contents 4 Aegis Padlock DT button panel 5 Aegis Padlock DT - Getting Started 6 Before you begin 6 Connecting
IT Essentials v6.0 Windows 10 Software Labs
 IT Essentials v6.0 Windows 10 Software Labs 5.2.1.7 Install Windows 10... 1 5.2.1.10 Check for Updates in Windows 10... 10 5.2.4.7 Create a Partition in Windows 10... 16 6.1.1.5 Task Manager in Windows
IT Essentials v6.0 Windows 10 Software Labs 5.2.1.7 Install Windows 10... 1 5.2.1.10 Check for Updates in Windows 10... 10 5.2.4.7 Create a Partition in Windows 10... 16 6.1.1.5 Task Manager in Windows
Impossible Solutions, Inc. JDF Ticket Creator & DP2 to Indigo scripts Reference Manual Rev
 Impossible Solutions, Inc. JDF Ticket Creator & DP2 to Indigo scripts Reference Manual Rev. 06.29.09 Overview: This reference manual will cover two separate applications that work together to produce a
Impossible Solutions, Inc. JDF Ticket Creator & DP2 to Indigo scripts Reference Manual Rev. 06.29.09 Overview: This reference manual will cover two separate applications that work together to produce a
Lockout PRO Online User Guide
 Lockout PRO Online User Guide February 2009 Copyright Wizmo Inc. 2006-2009 Page 1 Contents Setting up the hosted environment... 3 Logging into the Hosted Desktop... 8 Directories... 14 Logging off the
Lockout PRO Online User Guide February 2009 Copyright Wizmo Inc. 2006-2009 Page 1 Contents Setting up the hosted environment... 3 Logging into the Hosted Desktop... 8 Directories... 14 Logging off the
SERVICE2000 QUICK START
 SERVICE2000 QUICK START Installation Guide for Release 8 Table of Contents Introduction 2 System Requirements 2 Preparation - All Editions 2 Installation - Single User Edition 3 Installation - Network
SERVICE2000 QUICK START Installation Guide for Release 8 Table of Contents Introduction 2 System Requirements 2 Preparation - All Editions 2 Installation - Single User Edition 3 Installation - Network
Fiery proserver User Guide
 Fiery proserver User Guide Congratulations on your purchase of the Fiery proserver, a powerful production solution for your printer. Before you begin Make sure that you have: About this document Installed
Fiery proserver User Guide Congratulations on your purchase of the Fiery proserver, a powerful production solution for your printer. Before you begin Make sure that you have: About this document Installed
Fiery proserver User Guide
 Fiery proserver User Guide Congratulations on your purchase of the EFI Fiery proserver, a powerful production solution for your printer. Before you begin Make sure that you have: About this document Installed
Fiery proserver User Guide Congratulations on your purchase of the EFI Fiery proserver, a powerful production solution for your printer. Before you begin Make sure that you have: About this document Installed
MLP (Multi-Link Programming) SOFTWARE
 FOR REVISIONS 1.10 AND ABOVE Doc-6001005 Rev - 3380 USER'S GUIDE TO MLP (Multi-Link Programming) SOFTWARE CHATSWORTH, CALIFORNIA Multi-Link Programming software makes programming a chain of Sentex Infinity
FOR REVISIONS 1.10 AND ABOVE Doc-6001005 Rev - 3380 USER'S GUIDE TO MLP (Multi-Link Programming) SOFTWARE CHATSWORTH, CALIFORNIA Multi-Link Programming software makes programming a chain of Sentex Infinity
System Management (X2.89A/2)
 01/09/2017 System Management (X2.89A/2) Click on the chapter titles below to view them: 1: General System Management - applicable to all systems 2: Functionality specific to Systems Without Enhanced Security
01/09/2017 System Management (X2.89A/2) Click on the chapter titles below to view them: 1: General System Management - applicable to all systems 2: Functionality specific to Systems Without Enhanced Security
Chapter A1: Setting up BankLink Practice, BankLink Notes and BankLink Notes Online
 Chapter A1: Setting up BankLink Practice, BankLink Notes and BankLink Notes Online This chapter is aimed at BankLink Administrators This chapter covers setting up BankLink Practice and BankLink Notes Online
Chapter A1: Setting up BankLink Practice, BankLink Notes and BankLink Notes Online This chapter is aimed at BankLink Administrators This chapter covers setting up BankLink Practice and BankLink Notes Online
Effort Free IT User Guidelines
 Effort Free IT User Guidelines These are some guidelines to follow to help PC Miracles manage your workstation and make sure you IT needs are met in a timely manner Please leave your pc on at night. You
Effort Free IT User Guidelines These are some guidelines to follow to help PC Miracles manage your workstation and make sure you IT needs are met in a timely manner Please leave your pc on at night. You
About MassMutual Electronic Bill Presentment & Payment
 Group Billing and Collections Frequently Asked Questions (FAQs) for ebill and epay About MassMutual Electronic Bill Presentment & Payment E-Bill Questions and Problems Payment Process Questions Payment
Group Billing and Collections Frequently Asked Questions (FAQs) for ebill and epay About MassMutual Electronic Bill Presentment & Payment E-Bill Questions and Problems Payment Process Questions Payment
Lf1w1'eLC bliotfitl ~NS C.. /00/CAL VSTEMS. Maintenance Utility
 Lf1w1'eLC bliotfitl Maintenance Utility /00/CAL VSTEMS ~NS C.. ç. TABLE OF CONTENTS LBMAINT - File Maintenance Utility... 1 Start up procedure... 2 Using LBMAINT... 3 The LBMAINT Scan menu... 5 Viewoption...
Lf1w1'eLC bliotfitl Maintenance Utility /00/CAL VSTEMS ~NS C.. ç. TABLE OF CONTENTS LBMAINT - File Maintenance Utility... 1 Start up procedure... 2 Using LBMAINT... 3 The LBMAINT Scan menu... 5 Viewoption...
Frequently Asked Questions about PowerSchool
 Frequently Asked Questions about PowerSchool Q. How does one get a PowerSchool Parent Portal username and password? A. Contact the school office. Q. Do I need a separate login for each of my children?
Frequently Asked Questions about PowerSchool Q. How does one get a PowerSchool Parent Portal username and password? A. Contact the school office. Q. Do I need a separate login for each of my children?
TEAM5 Operation Manual
 Contents System Overview Version Feature Comparison Chart Install Recommendations User Edit Importing a User List Add a User Delete User(s) Edit Multiple Users ( Global Controls ) Sort / Filter User List
Contents System Overview Version Feature Comparison Chart Install Recommendations User Edit Importing a User List Add a User Delete User(s) Edit Multiple Users ( Global Controls ) Sort / Filter User List
CONTENTS. SysReturn_Manaual Updata 06/4/24. Chapter1 Introducing SysReturn Introduction to SysReturn Features and Functions...
 CONTENTS Chapter1 Introducing SysReturn... 3 Introduction to SysReturn... 3 Features and Functions... 3 Chapter2 Glossary... 5 Chapter3 System Requirement... 6 Hardware Requirement... 6 Software Requirement...
CONTENTS Chapter1 Introducing SysReturn... 3 Introduction to SysReturn... 3 Features and Functions... 3 Chapter2 Glossary... 5 Chapter3 System Requirement... 6 Hardware Requirement... 6 Software Requirement...
Installing and Upgrading TSM 6.8
 Installing and Upgrading TSM 6.8 This guide will take you through the installation of TSM 6.8, the workstation install, and applying incremental updates. Installing TSM 1) Obtain a copy of the TSM installation
Installing and Upgrading TSM 6.8 This guide will take you through the installation of TSM 6.8, the workstation install, and applying incremental updates. Installing TSM 1) Obtain a copy of the TSM installation
MX-FR41U. Data Security Kit Operation Guide. Contents
 MX-FR41U Data Security Kit Operation Guide Contents Introduction...2 When the data security kit is installed...4 Security settings of the data security kit...4 Document control function...4 Document Filing...4
MX-FR41U Data Security Kit Operation Guide Contents Introduction...2 When the data security kit is installed...4 Security settings of the data security kit...4 Document control function...4 Document Filing...4
Copyright 2004, Mighty Computer Services
 EZ-GRAPH DATABASE PROGRAM MANUAL Copyright 2004, Mighty Computer Services The Table of Contents is located at the end of this document. I. Purpose EZ-Graph Database makes it easy to draw and maintain basic
EZ-GRAPH DATABASE PROGRAM MANUAL Copyright 2004, Mighty Computer Services The Table of Contents is located at the end of this document. I. Purpose EZ-Graph Database makes it easy to draw and maintain basic
Performer to DP2 Hot Folder Reference Manual Rev There is only one file involved with installing the Performer to DP2 Hot Folder.
 Performer to DP2 Hot Folder Reference Manual Rev. 07.11.05 Install Files: There is only one file involved with installing the Performer to DP2 Hot Folder. The installer file is named PP2DP2_1.x.x.EXE.
Performer to DP2 Hot Folder Reference Manual Rev. 07.11.05 Install Files: There is only one file involved with installing the Performer to DP2 Hot Folder. The installer file is named PP2DP2_1.x.x.EXE.
LevelOne FNS bay/1usb Soho NAS. User s Manual
 LevelOne FNS-1000 1- bay/1usb Soho NAS User s Manual Table of Contents Introduction... 2 The FNS-1000 NAS Server... 2 FNS-1000 Features... 2 Package Contents... 2 System Requirements... 2 Disclaimer...
LevelOne FNS-1000 1- bay/1usb Soho NAS User s Manual Table of Contents Introduction... 2 The FNS-1000 NAS Server... 2 FNS-1000 Features... 2 Package Contents... 2 System Requirements... 2 Disclaimer...
LiveVault. Agent Guide
 LiveVault Software Version: 7.82 Agent Guide Note The guide primarily provides instruction on how to install the LiveVault agent on Windows and Linux servers. Additionally it provides information about
LiveVault Software Version: 7.82 Agent Guide Note The guide primarily provides instruction on how to install the LiveVault agent on Windows and Linux servers. Additionally it provides information about
Networks: Access Management Windows NT Server Class Notes # 10 Administration October 24, 2003
 Networks: Access Management Windows NT Server Class Notes # 10 Administration October 24, 2003 In Windows NT server, the user manager for domains is the primary administrative tool for managing user accounts,
Networks: Access Management Windows NT Server Class Notes # 10 Administration October 24, 2003 In Windows NT server, the user manager for domains is the primary administrative tool for managing user accounts,
BounceBack 18. User Manual
 BounceBack 18 User Manual 2016 CMS Products, all rights reserved. All trademarks are the property of their respective owners. Features and specifications are subject to change without notice. The information
BounceBack 18 User Manual 2016 CMS Products, all rights reserved. All trademarks are the property of their respective owners. Features and specifications are subject to change without notice. The information
5 MANAGING USER ACCOUNTS AND GROUPS
 MANAGING USER ACCOUNTS AND GROUPS.1 Introduction to user accounts Objectives.2 Types of User Accounts.2.1 Local User Account.2.2 Built-in User Account.2.3 Domain User Account.3 User Profile.3.1 Content
MANAGING USER ACCOUNTS AND GROUPS.1 Introduction to user accounts Objectives.2 Types of User Accounts.2.1 Local User Account.2.2 Built-in User Account.2.3 Domain User Account.3 User Profile.3.1 Content
etime Version 8.0 Hourly Non-Exempt Employee Instruction Manual
 etime Version 8.0 Hourly Non-Exempt Employee Instruction Manual July 2017 1 Table of Contents: Getting Started Opening etime v.8 3 First Time Login Set Password 3 Set Security Questions 4 Sign Out 4 Using
etime Version 8.0 Hourly Non-Exempt Employee Instruction Manual July 2017 1 Table of Contents: Getting Started Opening etime v.8 3 First Time Login Set Password 3 Set Security Questions 4 Sign Out 4 Using
Advanced Accounting Software & Secure Internet Solutions. Advanced Security Administrator Reference Manual
 Advanced Accounting Software & Secure Internet Solutions Advanced Security Administrator Reference Manual Version 7.3 Information in this document is subject to change without notice and does not represent
Advanced Accounting Software & Secure Internet Solutions Advanced Security Administrator Reference Manual Version 7.3 Information in this document is subject to change without notice and does not represent
The following documents are included with your Sony VAIO computer.
 Documentation The following documents are included with your Sony VAIO computer. Printed Documentation Quick Start Guide Describes the process from unpacking to starting up your VAIO. Troubleshooting and
Documentation The following documents are included with your Sony VAIO computer. Printed Documentation Quick Start Guide Describes the process from unpacking to starting up your VAIO. Troubleshooting and
SCI APPLICATIONS SERVER. Transaction Log (D:) Raid 5
 SCI APPLICATIONS Sci Applications Server The directory structure below shows the recommended setup of the server for each individual hospital. Each application/store server should be part of a domain to
SCI APPLICATIONS Sci Applications Server The directory structure below shows the recommended setup of the server for each individual hospital. Each application/store server should be part of a domain to
IronSync File Synchronization Server. IronSync FILE SYNC SERVER. User Manual. Version 2.6. May Flexense Ltd.
 IronSync FILE SYNC SERVER User Manual Version 2.6 May 2014 www.ironsync.com info@flexense.com 1 1 Product Overview...3 2 Product Installation Procedure...4 3 Using IronSync Client GUI Application...5 3.1
IronSync FILE SYNC SERVER User Manual Version 2.6 May 2014 www.ironsync.com info@flexense.com 1 1 Product Overview...3 2 Product Installation Procedure...4 3 Using IronSync Client GUI Application...5 3.1
Pace Clock. For the System 6 Sports Timer Software User Guide. F873 rev
 Pace Clock For the System 6 Sports Timer Software User Guide F873 rev 20171114 Customer Service Department www.coloradotime.com Email: customerservice@coloradotime.com Phone: +1 970-667-1000 Toll Free
Pace Clock For the System 6 Sports Timer Software User Guide F873 rev 20171114 Customer Service Department www.coloradotime.com Email: customerservice@coloradotime.com Phone: +1 970-667-1000 Toll Free
Chapter 3. Using the System CHANGING CHANNELS USING THE MENUS OPENING THE MENUS CLOSING THE MENUS MENU OPTIONS
 CHANGING CHANNELS There are three basic ways to change channels while watching a program: Press the remote control UP or DOWN ARROW button to get to the desired channel. Use the remote control number pad
CHANGING CHANNELS There are three basic ways to change channels while watching a program: Press the remote control UP or DOWN ARROW button to get to the desired channel. Use the remote control number pad
Advanced User s Guide
 Advanced User s Guide MFC-9140CDN MFC-9330CDW MFC-9340CDW Not all models are available in all countries. Version 0 ARL/ASA/NZ User s Guides and where do I find them? Which Guide? What s in it? Where is
Advanced User s Guide MFC-9140CDN MFC-9330CDW MFC-9340CDW Not all models are available in all countries. Version 0 ARL/ASA/NZ User s Guides and where do I find them? Which Guide? What s in it? Where is
User s Guide [Security Operations]
![User s Guide [Security Operations] User s Guide [Security Operations]](/thumbs/74/70955876.jpg) User s Guide [Security Operations] 007. 3 Ver. 1.04 Contents Contents 1 Security 1.1 Introduction... 1- Compliance with the ISO15408 Standard... 1- Operating Precautions... 1- INSTALLATION CHECKLIST...
User s Guide [Security Operations] 007. 3 Ver. 1.04 Contents Contents 1 Security 1.1 Introduction... 1- Compliance with the ISO15408 Standard... 1- Operating Precautions... 1- INSTALLATION CHECKLIST...
Full User Manual and Quick Start Guide
 Full User Manual and Quick Start Guide 2 W hile every precaution has been taken in the preparation of this manual, we assume no responsibility for errors or omissions. Neither, is any liability assumed
Full User Manual and Quick Start Guide 2 W hile every precaution has been taken in the preparation of this manual, we assume no responsibility for errors or omissions. Neither, is any liability assumed
User Guide. Version 2.1
 Kaseya Backup and Disaster Recovery User Guide Version 2.1 August 11, 2008 About Kaseya Kaseya is a global provider of IT automation software for IT Solution Providers and Public and Private Sector IT
Kaseya Backup and Disaster Recovery User Guide Version 2.1 August 11, 2008 About Kaseya Kaseya is a global provider of IT automation software for IT Solution Providers and Public and Private Sector IT
h/w m/c Kernel shell Application s/w user
 Structure of Unix h/w m/c Kernel shell Application s/w. user While working with unix, several layers of interaction occur b/w the computer h/w & the user. 1. Kernel : It is the first layer which runs on
Structure of Unix h/w m/c Kernel shell Application s/w. user While working with unix, several layers of interaction occur b/w the computer h/w & the user. 1. Kernel : It is the first layer which runs on
Once a USB drive has been inserted into an encrypted machine, the Dell Data Protection software will recognize the unencrypted device.
 Dell Data Protection USB Drive Encryption Introduction To further protect PC s that have access to sensitive data, the Dell Data Protection (DDP) client detects and encrypts USB/Flash drives when they
Dell Data Protection USB Drive Encryption Introduction To further protect PC s that have access to sensitive data, the Dell Data Protection (DDP) client detects and encrypts USB/Flash drives when they
