Content Gateway v7.x: Frequently Asked Questions
|
|
|
- Deirdre Cunningham
- 5 years ago
- Views:
Transcription
1 Content Gateway v7.x: Frequently Asked Questions Topic Content Gateway FAQs Updated: 22-October-2013 Websense Content Gateway v7.x, v7.x Websense Web Security Gateway / Anywhere v7.x, v7.x How do I configure IPTables to harden the Content Gateway host system? How do I ensure that Content Gateway is properly identified in the network? Which Web browsers provide the best user experience with Content Gateway? How do I backup and restore the SSL Incident List? Where do I download Content Gateway? How do I configure IPTables to harden the Content Gateway host system? Topic Content Gateway FAQs Updated: 22-October-2013 Websense Content Gateway 7.7.x, v7.8.x Websense Web Security Gateway Anywhere 7.7.x, v7.8.x When Content Gateway is deployed on a stand-alone server, it is strongly recommended that an IPTables firewall be configured to provide maximum security and efficiency with Content Gateway. Warning Only qualified system administrators should modify the IPTables firewall. As an aid to understanding the IPTables configuration required for Content Gateway, a sample IPTables configuration script is installed in the Content Gateway bin directory (/opt/wcg/bin, by default). The sample script is named example_iptables.sh.
2 Review the script carefully. Do not use the script directly. Create your own script that meets your specific needs. To view a text file version of the v7.6.x sample script, click here To view a text file version of the v7.7.x sample script, click here. To view a text file version of the v7.8.x sample script, click here. Configuration: The following list of rules is organized into groups that address different deployments. Be sure the /etc/sysconfig/iptables file contains all the rules that apply to your network from each section. If the proxy is configured to use multiple NICs, for each rule that applies to an interface specify the appropriate NIC with the -i option ( -i means match only if the incoming packet is on the specified interface). Typically, multiple interfaces are divided into these roles: Management interface (MGMT_NIC) - The physical interface used by the system administrator to manage the computer. Internet-facing interface (WAN_NIC) - The physical interface used to request pages from the Internet (usually the most secure interface). Client-facing interface (CLIENT_NIC) - The physical interface used by the clients to request data from the proxy. Cluster interface (CLUSTER_NIC) - The physical interface used by the proxy to communicate with members of the cluster. Note If you customized any ports that Websense software uses for communication, replace the default port shown in the following rules with the custom port you implemented. All deployments These rules are required to enable Content Gateway communications, regardless of the deployment. The following rules should be first. iptables --policy INPUT DROP iptables --policy OUTPUT iptables --policy FORWARD DROP iptables -I INPUT -m state --state RELATED,ESTABLISHED -j iptables --I OUTPUT -o lo -t raw -j NOTRACK In addition to the above rules, it is a best practice to increase the size of ip_conntrack_max to to improve performance. Typically, this can be done
3 using the following command: /sbin/sysctl net.ipv4.ip_conntrack_max= Note that this should be done after iptables is invoked. Also, this change in value will not be preserved after reboot unless you configure your system to set this value at startup. To do so, add the following line to /etc/sysctl.conf: net.ipv4.ip_conntrack_max= The next group of rules are important for general system security and should be entered immediately after the above rules: iptables -I INPUT -i lo -j iptables -i <MGMT_NIC> -I INPUT -p tcp --dport 22 -j iptables -i <MGMT_NIC> -I INPUT -p ICMP -j Include these rules in v7.7.x deployments to support proxying of HTTPS traffic and access to the SSL Manager: iptables -i $CLIENT_NIC -I INPUT -p tcp --dport j iptables -i <MGMT_NIC> -I INPUT -p tcp --dport j Include these rules to support proxying of HTTP traffic and access to the Content Gateway manager: iptables -i <CLIENT_NIC> -I INPUT -p tcp --dport j iptables -i <MGMT_NIC> -I INPUT -p tcp --dport j Local Policy Server Include these rules if the Websense Policy Server runs on the Content Gateway machine. iptables -i <MGMT_NIC> -I INPUT -p tcp --dport j iptables -i <MGMT_NIC> -I INPUT -p tcp --dport j iptables -i <MGMT_NIC> -I INPUT -p tcp --dport j iptables -i <MGMT_NIC> -I INPUT -p udp --dport j Remote Policy Server Include this rule if the Websense Policy Server does not run on the Content Gateway machine. This is required because Content Gateway has bidirectional communication over ephemeral ports. Be sure to replace <POLICY Server IP> in the command with the actual IP address of the Policy Server machine. iptables -i <MGMT_NIC> -I INPUT -p tcp -s <POLICY Server IP> --dport 1024: j Local Filtering Service
4 Include these rules if the Websense Filtering Service runs on the Content Gateway machine. iptables -i <MGMT_NIC> -I INPUT -p tcp --dport j iptables -i <MGMT_NIC> -I INPUT -p tcp --dport j Remote Filtering Service Include this rule if the Websense Filtering Service does not run on the Content Gateway machine. This is required because Content Gateway has bidirectional communication over ephemeral ports. Be sure to replace in the command with the actual IP address of the Filtering Service machine. iptables -i <MGMT_NIC> -I INPUT -s <FILTERING IP Service> -p tcp --dport 1024: j Websense Data Security Include the following rules if Content Gateway is installed as part of Websense Web Security Gateway Anywhere or deployed with Websense Data Security. iptables -i <MGMT_NIC> -I INPUT -p tcp --dport 17500: j Cluster Include the following rules if you have multiple instances of Content Gateway in a cluster. iptables -i <CLUSTER_NIC> -I INPUT -p tcp --dport j iptables -i <CLUSTER_NIC> -I INPUT -p udp --dport j iptables -i <CLUSTER_NIC> -I INPUT -p tcp --dport j iptables -i <CLUSTER_NIC> -I INPUT -p udp --dport j iptables -i <CLUSTER_NIC> -I INPUT -p udp -d <Multicast_IP_Address> -j Cache hierarchy Include the following rule if you have multiple instances of Content Gateway in a cache hierarchy. iptables -i <MGMT_NIC> -I INPUT -p udp --dport j Transparent proxy Include the following rule if your network uses proxy. Include the rule for port 2048 only if your network uses WCCP for proxy.
5 Include the rule for port 53 and 5353 only if you proxy DNS. FTP iptables -i <CLIENT_NIC> -I INPUT -p tcp --dport 80 -j iptables -i <CLIENT_NIC> -I INPUT -p tcp --dport 443 -j iptables -i <CLIENT_NIC> -I INPUT -p udp --dport j iptables -i <CLIENT_NIC> -I INPUT -p udp --dport 53 -j iptables -i <CLIENT_NIC> -I INPUT -p udp --dport j Include the appropriate rules, below, if you plan to proxy FTP traffic (optional). iptables -i <CLIENT_NIC> -I INPUT -p tcp --dport 21 -j iptables -i <CLIENT_NIC> -I INPUT -p tcp --dport j Optional features Include the rule for port 8082, below, to allow gathering of statistics over the overseer port. Include the rule for port 8083, below, to allow PAC file distribution from the proxy. Include the rule for port 8085, below, to allow collation of logs for multiple proxies. iptables -i <MGMT_NIC> -I INPUT -p tcp --dport j iptables -i <CLIENT_NIC> -I INPUT -p tcp --dport j iptables -i <MGMT_NIC> -I INPUT -p tcp --dport j For information on SNMP configuration, see Using SNMP with Content Gateway. Configuring IP6tables Content Gateway does not rely on IPv6, but can be configured to meet your other security requirements. Support is provided for explicit proxy deployments only. To configure IP6tables firewall, Content Gateway requires that an IPv6 port be open for each protocol that is used (HTTP, HTTPS, FTP, DNS). Port 8080 is required for Content Gateway to receive and proxy explicit HTTP and HTTPS traffic. ip6tables -i <CLIENT_NIC> -I INPUT -p tcp --dport j Include the rule below if you plan to proxy FTP traffic (optional). ip6tables -i <CLIENT_NIC> -I INPUT -p tcp --dport j
6 Include the rule for port 53 and 5353 only if you proxy DNS. ip6tables -i <CLIENT_NIC> -I INPUT -p udp --dport 53 -j ip6tables -i <CLIENT_NIC> -I INPUT -p udp --dport j How do I ensure that Content Gateway is properly identified in the network? Topic Content Gateway FAQs Updated: 22-October-2013 Websense Content Gateway v7.x Websense Web Security Gateway / Anywhere v7.x To ensure that every Content Gateway node is found and correctly identified on the network, configure the /etc/hosts file on every Content Gateway node in a cluster. If this is not done, Content Gateway may fail to connect to the Websense Web Security Policy Server or other network services. Sometimes the problem doesn t surface immediately, or surfaces after a second Content Gateway node is added. Important In a Content Gateway cluster, the cluster name, which is shared by all nodes, cannot be the same as any hostname. Configuring the /etc/hosts file: On each Content Gateway node, edit the /etc/hosts file to include--on the first line-- the IP address, fully qualified domain name, and hostname of the node. 1. Log on to the Content Gateway host system as root. 2. Edit /etc/hosts. A typical default /etc/hosts file looks like: localhost.localdomain localhost 3. Open a new first line and specify the IP address, domain name, and hostname of the system. The format is: xxx.xxx.xxx.xxx [FQDN] [hostname] where [FQDN] is the fully-qualified domain name of the machine, e.g. hostname.subdomain.top-level-domain and [hostname] is the system hostname. For example: wcg1.bighost.com wcg localhost.localdomain localhost
7 The IP address must be static and not served by DHCP. The proxy uses this IP address in features such as and hierarchical caching. Note Do not delete the second line (former first line) that begins with It specifies the loopback address and is also required. 4. Save and close /etc/hosts. Repeat the above on every Content Gateway node. Confirming the settings: To display the configured system hostname, on the Linux command line enter: # hostname To confirm the IP address that is bound to the hostname, on the Linux command line enter: # ping hostname For example: # ping wcg1.bighost.com This should return the IP address in line 1 of /etc/hosts. It should not return To test the local loopback address, on the Linux command line enter: # ping localhost This should return To test if the hostname is resolved by DNS (if it is configured), on the Linux command line enter: # nslookup hostname For example: # nslookup wcg1.bighost.com This should return the same IP address as ping. Note that in some cases it is optional to have the proxy in DNS.
8 Which Web browsers provide the best user experience with Content Gateway? Topic Content Gateway FAQs Updated: 22-October-2013 Websense Content Gateway 7.8.x Websense Web Security Gateway / Anywhere 7.8.x Not all Web browsers fully support user. The following table indicates how a browser responds to an request when Integrated Windows Authentication (IWA) is configured in version 7.8.x. For similar information for other versions, see the Release Notes for that version. Browser/ Operating System Windows Internet Explorer (v9, 10 tested) Performs Firefox Chrome Opera (v12.02 tested) Performs (v21 tested) Mac OS X Not applicable Performs (v21 tested) Red Hat Enterprise Linux, update 6 Not applicable Performs (v11 tested) Performs (v26, 27 tested) Browser issue prevents IWA from working (v23 tested) Browser issue prevents IWA from working (v27 tested) Falls back to NTLM and prompts for credentials Not tested Not tested Safari (v6.02 tested) Falls back to NTLM and prompts for credentials Performs Not applicable Note When prompted for credentials, if the user does not enter a domain name, a session timeout error can result, or the user may be re-prompted. To configure Internet Explorer for Single Sign-On, you must configure the browser to consider the proxy as a local server. Follow these steps in Internet Explorer: 1. Select Tools > Internet Options > Security > Local intranet > Sites > Advanced. 2. Enter the URL or IP address of the proxy.
9 3. Click Add. 4. Click OK until you have closed all the dialog boxes. Mozilla Firefox users browsing from the same domain as the proxy may sometimes be prompted multiple times for. The user should configure the browser as follows: 1. Open Firefox and enter about:config in the Location bar. 2. Click the I will be careful I promise button. 3. In the Filter entry field enter ntlm. 4. Double click network.automatic-ntlm-auth.trusted-uris and enter: For example: 5. Click OK and close and reopen the browser. How do I backup and restore the SSL Incident List? Topic Content Gateway FAQs Updated: 22-October-2013 Websense Content Gateway v7.x Websense Web Security Gateway / Anywhere v7.x The SSL Incident list can be backed up and restored on the Linux command line using sqlite3. Start by logging on to the Content Gateway host system and acquiring root privileges. To back up the Incident list: 1. Change to the Content Gateway SSL database directory: For v7.8.x and later: # cd /opt/wcg/config For v7.7.x and earlier: # cd /opt/wcg/sxsuitedb/db 2. Open the database with sqlite: For v7.8.x and later: # sqlite3 new_scip3.db For v7.7.x and earlier: # sqlite3 scip3.db 3. In sqlite, perform the following steps: sqlite>.tables sqlite>.output certificate_acl.bak
10 sqlite>.dump certificate_acl sqlite>.exit You now have a backup of the Incident list named certificate_acl.bak. To restore a backup: 1. Change to the Content Gateway SSL database directory and open the database with sqlite3: For 7.8.x and later: # cd /opt/wcg/config # sqlite3 new_scip3.db For 7.7.x and earlier: # cd /opt/wcg/sxsuitedb/db # sqlite3 scip3.db 2. To replace the current list with the backup list, delete the current list. Skip this step if you want to add the backup list to the current list. sqlite> drop table certificate_acl; 3. To restore the backup list: sqlite>.read certificate_acl.bak sqlite>.exit 4. In Content Gateway Manager, verify that the Incident List has been restored. Where do I download Content Gateway? Topic Content Gateway FAQs Updated: 22-October-2013 Websense Content Gateway v7.x Websense Web Security Gateway / Anywhere v7.x Log on to your MyWebsense account and go to the Downloads page. In the Product drop down select Websense Web Security Gateway or Web Security Gateway Anywhere. Locate the release number that you want and click on the + icon next to Websense Content Gateway to view download details. To begin the download, click Download. To get complete information on installing or upgrading any Websense network security components, visit the Websense Technical Library.
VMware Identity Manager Cloud Deployment. DEC 2017 VMware AirWatch 9.2 VMware Identity Manager
 VMware Identity Manager Cloud Deployment DEC 2017 VMware AirWatch 9.2 VMware Identity Manager You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/
VMware Identity Manager Cloud Deployment DEC 2017 VMware AirWatch 9.2 VMware Identity Manager You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/
VMware Identity Manager Cloud Deployment. Modified on 01 OCT 2017 VMware Identity Manager
 VMware Identity Manager Cloud Deployment Modified on 01 OCT 2017 VMware Identity Manager You can find the most up-to-date technical documentation on the VMware Web site at: https://docs.vmware.com/ The
VMware Identity Manager Cloud Deployment Modified on 01 OCT 2017 VMware Identity Manager You can find the most up-to-date technical documentation on the VMware Web site at: https://docs.vmware.com/ The
HP Management Integration Framework 1.7
 HP Management Integration Framework 1.7 Administrator Guide Abstract This document describes the use of HP Management Integration Framework interfaces and is intended for administrators involved in the
HP Management Integration Framework 1.7 Administrator Guide Abstract This document describes the use of HP Management Integration Framework interfaces and is intended for administrators involved in the
The following topics provide more information on user identity. Establishing User Identity Through Passive Authentication
 You can use identity policies to collect user identity information from connections. You can then view usage based on user identity in the dashboards, and configure access control based on user or user
You can use identity policies to collect user identity information from connections. You can then view usage based on user identity in the dashboards, and configure access control based on user or user
Load Balancing Bloxx Web Filter. Deployment Guide v Copyright Loadbalancer.org
 Load Balancing Bloxx Web Filter Deployment Guide v1.3.5 Copyright Loadbalancer.org Table of Contents 1. About this Guide...4 2. Loadbalancer.org Appliances Supported...4 3. Loadbalancer.org Software Versions
Load Balancing Bloxx Web Filter Deployment Guide v1.3.5 Copyright Loadbalancer.org Table of Contents 1. About this Guide...4 2. Loadbalancer.org Appliances Supported...4 3. Loadbalancer.org Software Versions
Load Balancing Web Proxies / Filters / Gateways. Deployment Guide v Copyright Loadbalancer.org
 Load Balancing Web Proxies / Filters / Gateways Deployment Guide v1.6.5 Copyright Loadbalancer.org Table of Contents 1. About this Guide...4 2. Loadbalancer.org Appliances Supported...4 3. Loadbalancer.org
Load Balancing Web Proxies / Filters / Gateways Deployment Guide v1.6.5 Copyright Loadbalancer.org Table of Contents 1. About this Guide...4 2. Loadbalancer.org Appliances Supported...4 3. Loadbalancer.org
Identity Policies. Identity Policy Overview. Establishing User Identity through Active Authentication
 You can use identity policies to collect user identity information from connections. You can then view usage based on user identity in the dashboards, and configure access control based on user or user
You can use identity policies to collect user identity information from connections. You can then view usage based on user identity in the dashboards, and configure access control based on user or user
Installing and Configuring vcloud Connector
 Installing and Configuring vcloud Connector vcloud Connector 2.6.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new
Installing and Configuring vcloud Connector vcloud Connector 2.6.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new
VMware Identity Manager Connector Installation and Configuration (Legacy Mode)
 VMware Identity Manager Connector Installation and Configuration (Legacy Mode) VMware Identity Manager This document supports the version of each product listed and supports all subsequent versions until
VMware Identity Manager Connector Installation and Configuration (Legacy Mode) VMware Identity Manager This document supports the version of each product listed and supports all subsequent versions until
Deploying VMware Identity Manager in the DMZ. JULY 2018 VMware Identity Manager 3.2
 Deploying VMware Identity Manager in the DMZ JULY 2018 VMware Identity Manager 3.2 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have
Deploying VMware Identity Manager in the DMZ JULY 2018 VMware Identity Manager 3.2 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have
Blue Coat Security First Steps. Solution for Integrating Authentication using IWA BCAAA
 Solution for Integrating Authentication using IWA BCAAA Third Party Copyright Notices 2014 Blue Coat Systems, Inc. All rights reserved. BLUE COAT, PROXYSG, PACKETSHAPER, CACHEFLOW, INTELLIGENCECENTER,
Solution for Integrating Authentication using IWA BCAAA Third Party Copyright Notices 2014 Blue Coat Systems, Inc. All rights reserved. BLUE COAT, PROXYSG, PACKETSHAPER, CACHEFLOW, INTELLIGENCECENTER,
VII. Corente Services SSL Client
 VII. Corente Services SSL Client Corente Release 9.1 Manual 9.1.1 Copyright 2014, Oracle and/or its affiliates. All rights reserved. Table of Contents Preface... 5 I. Introduction... 6 Chapter 1. Requirements...
VII. Corente Services SSL Client Corente Release 9.1 Manual 9.1.1 Copyright 2014, Oracle and/or its affiliates. All rights reserved. Table of Contents Preface... 5 I. Introduction... 6 Chapter 1. Requirements...
Quick Installation Guide
 Nortel IP Flow Manager Release: 2.0 Version: 02.01 Copyright 2009 Nortel Networks Nortel IP Flow Manager 2.0 Page 1 of 9 Nortel IP Flow Manager Release: 2.0 Publication: NN48015-300 Document status: Standard
Nortel IP Flow Manager Release: 2.0 Version: 02.01 Copyright 2009 Nortel Networks Nortel IP Flow Manager 2.0 Page 1 of 9 Nortel IP Flow Manager Release: 2.0 Publication: NN48015-300 Document status: Standard
Application Rules - Allows the users to add or modify or remove Custom ruleset for firewall settings.
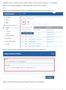 Application Rules - Allows the users to add or modify or remove Custom ruleset for firewall settings. Step [1]: Go to Endpoint Manager> CONFIGURATION TEMPLATES > Profiles Step [2]: Click Create icon and
Application Rules - Allows the users to add or modify or remove Custom ruleset for firewall settings. Step [1]: Go to Endpoint Manager> CONFIGURATION TEMPLATES > Profiles Step [2]: Click Create icon and
Deploying VMware Identity Manager in the DMZ. SEPT 2018 VMware Identity Manager 3.3
 Deploying VMware Identity Manager in the DMZ SEPT 2018 VMware Identity Manager 3.3 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have
Deploying VMware Identity Manager in the DMZ SEPT 2018 VMware Identity Manager 3.3 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have
How to Configure a Remote Management Tunnel for an F-Series Firewall
 How to Configure a Remote Management Tunnel for an F-Series Firewall If the managed NextGen Firewall F-Series cannot directly reach the NextGen Control Center, it must connect via a remote management tunnel.
How to Configure a Remote Management Tunnel for an F-Series Firewall If the managed NextGen Firewall F-Series cannot directly reach the NextGen Control Center, it must connect via a remote management tunnel.
Appliance Quick Start Guide. v7.5
 Appliance Quick Start Guide v7.5 rev. 1.0.8 Copyright 2002 2014 Loadbalancer.org, Inc. Table of Contents Loadbalancer.org Terminology... 4 What is a Virtual IP Address?... 4 What is a Floating IP Address?...
Appliance Quick Start Guide v7.5 rev. 1.0.8 Copyright 2002 2014 Loadbalancer.org, Inc. Table of Contents Loadbalancer.org Terminology... 4 What is a Virtual IP Address?... 4 What is a Floating IP Address?...
Covene Cohesion Server Installation Guide A Modular Platform for Pexip Infinity Management October 25, 2016 Version 3.3 Revision 1.
 Covene Cohesion Server Installation Guide A Modular Platform for Pexip Infinity Management October 25, 2016 Version 3.3 Revision 1.0 Table of Contents 1. Overview... 3 2. Upgrading an Existing Installation...
Covene Cohesion Server Installation Guide A Modular Platform for Pexip Infinity Management October 25, 2016 Version 3.3 Revision 1.0 Table of Contents 1. Overview... 3 2. Upgrading an Existing Installation...
Platform Compatibility... 1 Enhancements... 2 Known Issues... 3 Upgrading SonicOS Enhanced Image Procedures... 3 Related Technical Documentation...
 SonicOS Contents Platform Compatibility... 1 Enhancements... 2 Known Issues... 3 Upgrading SonicOS Enhanced Image Procedures... 3 Related Technical Documentation...7 Platform Compatibility The SonicOS
SonicOS Contents Platform Compatibility... 1 Enhancements... 2 Known Issues... 3 Upgrading SonicOS Enhanced Image Procedures... 3 Related Technical Documentation...7 Platform Compatibility The SonicOS
Installing and Configuring VMware Identity Manager Connector (Windows) OCT 2018 VMware Identity Manager VMware Identity Manager 3.
 Installing and Configuring VMware Identity Manager Connector 2018.8.1.0 (Windows) OCT 2018 VMware Identity Manager VMware Identity Manager 3.3 You can find the most up-to-date technical documentation on
Installing and Configuring VMware Identity Manager Connector 2018.8.1.0 (Windows) OCT 2018 VMware Identity Manager VMware Identity Manager 3.3 You can find the most up-to-date technical documentation on
BIG-IP Access Policy Manager : Secure Web Gateway. Version 13.0
 BIG-IP Access Policy Manager : Secure Web Gateway Version 13.0 Table of Contents Table of Contents BIG-IP APM Secure Web Gateway Overview...9 About APM Secure Web Gateway... 9 About APM benefits for web
BIG-IP Access Policy Manager : Secure Web Gateway Version 13.0 Table of Contents Table of Contents BIG-IP APM Secure Web Gateway Overview...9 About APM Secure Web Gateway... 9 About APM benefits for web
Cisco PCP-PNR Port Usage Information
 Cisco PCP-PNR Port Usage Information Page 1 of 18 20-Sep-2013 Table of Contents 1 Introduction... 3 2 Prerequisites... 3 3 Glossary... 3 3.1 CISCO PCP Local Machine... 3 3.1.1 CISCO PCP Component... 4
Cisco PCP-PNR Port Usage Information Page 1 of 18 20-Sep-2013 Table of Contents 1 Introduction... 3 2 Prerequisites... 3 3 Glossary... 3 3.1 CISCO PCP Local Machine... 3 3.1.1 CISCO PCP Component... 4
Configure the IM and Presence Service to Integrate with the Microsoft Exchange Server
 Configure the IM and Presence Service to Integrate with the Microsoft Exchange Server Configure a Presence Gateway for Microsoft Exchange Integration, page 1 SAN and Wildcard Certificate Support, page
Configure the IM and Presence Service to Integrate with the Microsoft Exchange Server Configure a Presence Gateway for Microsoft Exchange Integration, page 1 SAN and Wildcard Certificate Support, page
Installing and Configuring vcloud Connector
 Installing and Configuring vcloud Connector vcloud Connector 2.5.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new
Installing and Configuring vcloud Connector vcloud Connector 2.5.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new
Configuring Caching Services
 CHAPTER 8 This chapter describes how to configure conventional caching services (HTTP, FTP [FTP-over-HTTP caching and native FTP caching], HTTPS, and DNS caching) for centrally managed Content Engines.
CHAPTER 8 This chapter describes how to configure conventional caching services (HTTP, FTP [FTP-over-HTTP caching and native FTP caching], HTTPS, and DNS caching) for centrally managed Content Engines.
vcenter Server Appliance Configuration Modified on 17 APR 2018 VMware vsphere 6.7 VMware ESXi 6.7 vcenter Server 6.7
 vcenter Server Appliance Configuration Modified on 17 APR 2018 VMware vsphere 6.7 VMware ESXi 6.7 vcenter Server 6.7 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/
vcenter Server Appliance Configuration Modified on 17 APR 2018 VMware vsphere 6.7 VMware ESXi 6.7 vcenter Server 6.7 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/
WatchGuard Dimension v2.1.1 Update 3 Release Notes
 WatchGuard Dimension v2.1.1 Update 3 Release Notes Build Number 567758 Release Date 8 August 2018 Release Notes Revision Date 8 August 2018 On 8 August 2018, WatchGuard released the Dimension v2.1.1 Update
WatchGuard Dimension v2.1.1 Update 3 Release Notes Build Number 567758 Release Date 8 August 2018 Release Notes Revision Date 8 August 2018 On 8 August 2018, WatchGuard released the Dimension v2.1.1 Update
vcenter Server Appliance Configuration Update 1 Modified on 04 OCT 2017 VMware vsphere 6.5 VMware ESXi 6.5 vcenter Server 6.5
 Update 1 Modified on 04 OCT 2017 VMware vsphere 6.5 VMware ESXi 6.5 vcenter Server 6.5 You can find the most up-to-date technical documentation on the VMware Web site at: https://docs.vmware.com/ The VMware
Update 1 Modified on 04 OCT 2017 VMware vsphere 6.5 VMware ESXi 6.5 vcenter Server 6.5 You can find the most up-to-date technical documentation on the VMware Web site at: https://docs.vmware.com/ The VMware
Release Notes. Release Purpose... 1 Platform Compatibility... 1 Upgrading Information... 1 Browser Support... 1 Known Issues... 2 Resolved Issues...
 SonicOS SonicOS Contents Release Purpose... 1 Platform Compatibility... 1 Upgrading Information... 1 Browser Support... 1 Known Issues... 2 Resolved Issues... 6 Release Purpose SonicOS 6.1.1.4 is a maintenance
SonicOS SonicOS Contents Release Purpose... 1 Platform Compatibility... 1 Upgrading Information... 1 Browser Support... 1 Known Issues... 2 Resolved Issues... 6 Release Purpose SonicOS 6.1.1.4 is a maintenance
Installing or Upgrading ANM Virtual Appliance
 CHAPTER 2 This chapter describes how to deploy Cisco ANM Virtual Appliance 4.3 (new installation) and how to upgrade from ANM software version 4.1 or 4.2 to software version 4.3. This chapter includes
CHAPTER 2 This chapter describes how to deploy Cisco ANM Virtual Appliance 4.3 (new installation) and how to upgrade from ANM software version 4.1 or 4.2 to software version 4.3. This chapter includes
PlateSpin Transformation Manager Appliance Guide. June 2018
 PlateSpin Transformation Manager Appliance Guide June 2018 Legal Notice For information about legal notices, trademarks, disclaimers, warranties, export and other use restrictions, U.S. Government rights,
PlateSpin Transformation Manager Appliance Guide June 2018 Legal Notice For information about legal notices, trademarks, disclaimers, warranties, export and other use restrictions, U.S. Government rights,
Configuring Cisco Unified Presence for Integration with Microsoft Exchange Server
 CHAPTER 4 Configuring Cisco Unified Presence for Integration with Microsoft Exchange Server Revised: November 30, 2012 Configuring the Presence Gateway on Cisco Unified Presence for Microsoft Exchange
CHAPTER 4 Configuring Cisco Unified Presence for Integration with Microsoft Exchange Server Revised: November 30, 2012 Configuring the Presence Gateway on Cisco Unified Presence for Microsoft Exchange
Load Balancing Censornet USS Gateway. Deployment Guide v Copyright Loadbalancer.org
 Load Balancing Censornet USS Gateway Deployment Guide v1.0.0 Copyright Loadbalancer.org Table of Contents 1. About this Guide...3 2. Loadbalancer.org Appliances Supported...3 3. Loadbalancer.org Software
Load Balancing Censornet USS Gateway Deployment Guide v1.0.0 Copyright Loadbalancer.org Table of Contents 1. About this Guide...3 2. Loadbalancer.org Appliances Supported...3 3. Loadbalancer.org Software
HySecure Quick Start Guide. HySecure 5.0
 HySecure Quick Start Guide HySecure 5.0 Last Updated: 25 May 2017 2012-2017 Propalms Technologies Private Limited. All rights reserved. The information contained in this document represents the current
HySecure Quick Start Guide HySecure 5.0 Last Updated: 25 May 2017 2012-2017 Propalms Technologies Private Limited. All rights reserved. The information contained in this document represents the current
VMware vfabric Data Director Installation Guide
 VMware vfabric Data Director Installation Guide vfabric Data Director 2.5 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by
VMware vfabric Data Director Installation Guide vfabric Data Director 2.5 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by
Connect the Appliance to a Cisco Cloud Web Security Proxy
 Connect the Appliance to a Cisco Cloud Web Security Proxy This chapter contains the following sections: How to Configure and Use Features in Cloud Connector Mode, on page 1 Deployment in Cloud Connector
Connect the Appliance to a Cisco Cloud Web Security Proxy This chapter contains the following sections: How to Configure and Use Features in Cloud Connector Mode, on page 1 Deployment in Cloud Connector
IM and Presence Service Network Setup
 Configuration changes and service restart notifications, page 1 DNS Domain Configuration, page 2 IM and Presence Service Default Domain Configuration, page 6 IM Address Configuration, page 7 Domain Management
Configuration changes and service restart notifications, page 1 DNS Domain Configuration, page 2 IM and Presence Service Default Domain Configuration, page 6 IM Address Configuration, page 7 Domain Management
Load Balancing Microsoft Remote Desktop Services. Deployment Guide v Copyright Loadbalancer.org, Inc
 Load Balancing Microsoft Remote Desktop Services Deployment Guide v2.2 Copyright 2002 2017 Loadbalancer.org, Inc Table of Contents About this Guide...4 2. Loadbalancer.org Appliances Supported...4 3. Loadbalancer.org
Load Balancing Microsoft Remote Desktop Services Deployment Guide v2.2 Copyright 2002 2017 Loadbalancer.org, Inc Table of Contents About this Guide...4 2. Loadbalancer.org Appliances Supported...4 3. Loadbalancer.org
How does it look like?
 EasyAdmin Windows Authentication KB4031b 1 The OpenLM EasyAdmin administrative web interface incorporates a role-based security access scheme, facilitating different levels of access to different role
EasyAdmin Windows Authentication KB4031b 1 The OpenLM EasyAdmin administrative web interface incorporates a role-based security access scheme, facilitating different levels of access to different role
Stonesoft Management Center. Release Notes Revision A
 Stonesoft Management Center Release Notes 5.10.5 Revision A Table of contents 1 About this release...3 System requirements... 3 Build version...4 Compatibility... 5 2 New features...6 3 Enhancements...
Stonesoft Management Center Release Notes 5.10.5 Revision A Table of contents 1 About this release...3 System requirements... 3 Build version...4 Compatibility... 5 2 New features...6 3 Enhancements...
User guide. ApplianX DPNSS-to-Q.SIG Gateway
 User guide ApplianX DPNSS-to-Q.SIG Gateway Version 1.3 5/12/2008 Contents Contents 1 GETTING STARTED...4 1.1 How to use this guide... 4 1.2 Prerequisites... 4 1.3 L.E.Ds... 4 1.4 Logging in to the web
User guide ApplianX DPNSS-to-Q.SIG Gateway Version 1.3 5/12/2008 Contents Contents 1 GETTING STARTED...4 1.1 How to use this guide... 4 1.2 Prerequisites... 4 1.3 L.E.Ds... 4 1.4 Logging in to the web
Installing Cisco APIC-EM on a Virtual Machine
 About the Virtual Machine Installation, page 1 System Requirements Virtual Machine, page 2 Pre-Install Checklists, page 4 Cisco APIC-EM Ports Reference, page 7 Verifying the Cisco ISO Image, page 8 Installing
About the Virtual Machine Installation, page 1 System Requirements Virtual Machine, page 2 Pre-Install Checklists, page 4 Cisco APIC-EM Ports Reference, page 7 Verifying the Cisco ISO Image, page 8 Installing
BIG-IP Access Policy Manager : Portal Access. Version 12.1
 BIG-IP Access Policy Manager : Portal Access Version 12.1 Table of Contents Table of Contents Overview of Portal Access...7 Overview: What is portal access?...7 About portal access configuration elements...7
BIG-IP Access Policy Manager : Portal Access Version 12.1 Table of Contents Table of Contents Overview of Portal Access...7 Overview: What is portal access?...7 About portal access configuration elements...7
Setup for Cisco Unified Communications Manager
 Setup for Cisco Unified Communications Manager This chapter describes how you can set up Cisco Jabber for ipad using Cisco Unified Communications Manager. System and Network Requirements, page 1 Recommended
Setup for Cisco Unified Communications Manager This chapter describes how you can set up Cisco Jabber for ipad using Cisco Unified Communications Manager. System and Network Requirements, page 1 Recommended
Stonesoft Management Center. Release Notes Revision A
 Stonesoft Management Center Release Notes 5.10.2 Revision A Table of contents 1 About this release...3 System requirements... 3 Build version...4 Compatibility... 5 2 New features...6 3 Enhancements...
Stonesoft Management Center Release Notes 5.10.2 Revision A Table of contents 1 About this release...3 System requirements... 3 Build version...4 Compatibility... 5 2 New features...6 3 Enhancements...
Browser Configuration Reference
 Sitecore CMS 7.0 or later Browser Configuration Reference Rev: 2013-09-30 Sitecore CMS 7.0 or later Browser Configuration Reference Optimizing Internet Explorer and other web browsers to work with Sitecore
Sitecore CMS 7.0 or later Browser Configuration Reference Rev: 2013-09-30 Sitecore CMS 7.0 or later Browser Configuration Reference Optimizing Internet Explorer and other web browsers to work with Sitecore
Clearswift SECURE Gateway Installation & Getting Started Guide. Version 4.3 Document Revision 1.0
 Clearswift SECURE Email Gateway Installation & Getting Started Guide Version 4.3 Document Revision 1.0 Copyright Revision 1.1, March, 2016 Published by Clearswift Ltd. 1995 2016 Clearswift Ltd. All rights
Clearswift SECURE Email Gateway Installation & Getting Started Guide Version 4.3 Document Revision 1.0 Copyright Revision 1.1, March, 2016 Published by Clearswift Ltd. 1995 2016 Clearswift Ltd. All rights
CA Agile Central Administrator Guide. CA Agile Central On-Premises
 CA Agile Central Administrator Guide CA Agile Central On-Premises 2018.1 Table of Contents Overview... 3 Server Requirements...3 Browser Requirements...3 Access Help and WSAPI...4 Time Zone...5 Architectural
CA Agile Central Administrator Guide CA Agile Central On-Premises 2018.1 Table of Contents Overview... 3 Server Requirements...3 Browser Requirements...3 Access Help and WSAPI...4 Time Zone...5 Architectural
Contents. Platform Compatibility. New Features. Secure Remote Access SonicWALL SSL VPN 2.5 Early Field Trial (EFT) for SSL-VPN 200
 Secure Remote Access SonicWALL SSL VPN 2.5 Early Field Trial (EFT) for SSL-VPN 200 Contents Platform Compatibility New Features Known Issues Resolved Issues Upgrading SonicWALL SSL VPN Software Procedures
Secure Remote Access SonicWALL SSL VPN 2.5 Early Field Trial (EFT) for SSL-VPN 200 Contents Platform Compatibility New Features Known Issues Resolved Issues Upgrading SonicWALL SSL VPN Software Procedures
NMS300 Network Management System Application
 NMS300 Network Management System Application Quick Start Guide October 2013 202-11288-02 350 East Plumeria Drive San Jose, CA 95134 USA Support Thank you for purchasing this NETGEAR product. After installing
NMS300 Network Management System Application Quick Start Guide October 2013 202-11288-02 350 East Plumeria Drive San Jose, CA 95134 USA Support Thank you for purchasing this NETGEAR product. After installing
Integrating IBM Security Privileged Identity Manager with ObserveIT Enterprise Session Recording
 Integrating IBM Security Privileged Identity Manager with ObserveIT Enterprise Session Recording Contents 1 About This Document... 2 2 Overview... 2 3 Before You Begin... 2 4 Deploying ObserveIT with IBM
Integrating IBM Security Privileged Identity Manager with ObserveIT Enterprise Session Recording Contents 1 About This Document... 2 2 Overview... 2 3 Before You Begin... 2 4 Deploying ObserveIT with IBM
Realms and Identity Policies
 The following topics describe realms and identity policies: Introduction:, page 1 Creating a Realm, page 5 Creating an Identity Policy, page 11 Creating an Identity Rule, page 15 Managing Realms, page
The following topics describe realms and identity policies: Introduction:, page 1 Creating a Realm, page 5 Creating an Identity Policy, page 11 Creating an Identity Rule, page 15 Managing Realms, page
Copyright and Trademarks
 Copyright and Trademarks Specops Password Reset is a trademark owned by Specops Software. All other trademarks used and mentioned in this document belong to their respective owners. 2 Contents Key Components
Copyright and Trademarks Specops Password Reset is a trademark owned by Specops Software. All other trademarks used and mentioned in this document belong to their respective owners. 2 Contents Key Components
CounterACT 7.0. Quick Installation Guide for a Single Virtual CounterACT Appliance
 CounterACT 7.0 Quick Installation Guide for a Single Virtual CounterACT Appliance Table of Contents Welcome to CounterACT Version 7.0... 3 Overview... 4 1. Create a Deployment Plan... 5 Decide Where to
CounterACT 7.0 Quick Installation Guide for a Single Virtual CounterACT Appliance Table of Contents Welcome to CounterACT Version 7.0... 3 Overview... 4 1. Create a Deployment Plan... 5 Decide Where to
How to Configure SSL VPN Portal for Forcepoint NGFW TECHNICAL DOCUMENT
 How to Configure SSL VPN Portal for Forcepoint NGFW TECHNICAL DOCUMENT Ta Table of Contents Table of Contents TA TABLE OF CONTENTS 1 TABLE OF CONTENTS 1 BACKGROUND 2 CONFIGURATION STEPS 2 Create a SSL
How to Configure SSL VPN Portal for Forcepoint NGFW TECHNICAL DOCUMENT Ta Table of Contents Table of Contents TA TABLE OF CONTENTS 1 TABLE OF CONTENTS 1 BACKGROUND 2 CONFIGURATION STEPS 2 Create a SSL
The SSL device also supports the 64-bit Internet Explorer with new ActiveX loaders for Assessment, Abolishment, and the Access Client.
 WatchGuard SSL v3.2 Update 2 Release Notes Supported Devices SSL 100 and 560 WatchGuard SSL OS Build 452330 Revision Date 11 November 2014 Introduction WatchGuard is pleased to announce the release of
WatchGuard SSL v3.2 Update 2 Release Notes Supported Devices SSL 100 and 560 WatchGuard SSL OS Build 452330 Revision Date 11 November 2014 Introduction WatchGuard is pleased to announce the release of
NetApp Element Plug-in for vcenter Server User Guide
 NetApp Element Plug-in for vcenter Server User Guide Version 4.2 November 2018 215-13259_A0 doccomments@netapp.com Table of Contents 3 Contents About this guide... 8 vcenter Plug-in overview... 9 Network
NetApp Element Plug-in for vcenter Server User Guide Version 4.2 November 2018 215-13259_A0 doccomments@netapp.com Table of Contents 3 Contents About this guide... 8 vcenter Plug-in overview... 9 Network
Stonesoft Management Center. Release Notes Revision A
 Stonesoft Management Center Release Notes 6.1.3 Revision A Contents About this release on page 2 System requirements on page 2 Build version on page 3 Compatibility on page 4 New features on page 5 Enhancements
Stonesoft Management Center Release Notes 6.1.3 Revision A Contents About this release on page 2 System requirements on page 2 Build version on page 3 Compatibility on page 4 New features on page 5 Enhancements
Overview of the Cisco NCS Command-Line Interface
 CHAPTER 1 Overview of the Cisco NCS -Line Interface This chapter provides an overview of how to access the Cisco Prime Network Control System (NCS) command-line interface (CLI), the different command modes,
CHAPTER 1 Overview of the Cisco NCS -Line Interface This chapter provides an overview of how to access the Cisco Prime Network Control System (NCS) command-line interface (CLI), the different command modes,
Remote Access VPN. Remote Access VPN Overview. Licensing Requirements for Remote Access VPN
 Remote Access virtual private network (VPN) allows individual users to connect to your network from a remote location using a laptop or desktop computer connected to the Internet. This allows mobile workers
Remote Access virtual private network (VPN) allows individual users to connect to your network from a remote location using a laptop or desktop computer connected to the Internet. This allows mobile workers
Storage Manager 2018 R1. Installation Guide
 Storage Manager 2018 R1 Installation Guide Notes, Cautions, and Warnings NOTE: A NOTE indicates important information that helps you make better use of your product. CAUTION: A CAUTION indicates either
Storage Manager 2018 R1 Installation Guide Notes, Cautions, and Warnings NOTE: A NOTE indicates important information that helps you make better use of your product. CAUTION: A CAUTION indicates either
SonicWALL Security Appliances. SonicWALL SSL-VPN 200 Getting Started Guide
 SonicWALL Security Appliances SonicWALL SSL-VPN 200 Getting Started Guide SonicWALL SSL-VPN 200 Appliance Getting Started Guide This Getting Started Guide contains installation procedures and configuration
SonicWALL Security Appliances SonicWALL SSL-VPN 200 Getting Started Guide SonicWALL SSL-VPN 200 Appliance Getting Started Guide This Getting Started Guide contains installation procedures and configuration
BIG-IP Local Traffic Management: Basics. Version 12.1
 BIG-IP Local Traffic Management: Basics Version 12.1 Table of Contents Table of Contents Introduction to Local Traffic Management...7 About local traffic management...7 About the network map...7 Viewing
BIG-IP Local Traffic Management: Basics Version 12.1 Table of Contents Table of Contents Introduction to Local Traffic Management...7 About local traffic management...7 About the network map...7 Viewing
BIG-IP Access Policy Manager : Portal Access. Version 13.0
 BIG-IP Access Policy Manager : Portal Access Version 13.0 Table of Contents Table of Contents Overview of Portal Access...7 Overview: What is portal access?...7 About portal access configuration elements...
BIG-IP Access Policy Manager : Portal Access Version 13.0 Table of Contents Table of Contents Overview of Portal Access...7 Overview: What is portal access?...7 About portal access configuration elements...
Identity Firewall. About the Identity Firewall
 This chapter describes how to configure the ASA for the. About the, on page 1 Guidelines for the, on page 7 Prerequisites for the, on page 9 Configure the, on page 10 Monitoring the, on page 16 History
This chapter describes how to configure the ASA for the. About the, on page 1 Guidelines for the, on page 7 Prerequisites for the, on page 9 Configure the, on page 10 Monitoring the, on page 16 History
CounterACT 7.0 Single CounterACT Appliance
 CounterACT 7.0 Single CounterACT Appliance Quick Installation Guide Table of Contents Welcome to CounterACT Version 7.0....3 Included in your CounterACT Package....3 Overview...4 1. Create a Deployment
CounterACT 7.0 Single CounterACT Appliance Quick Installation Guide Table of Contents Welcome to CounterACT Version 7.0....3 Included in your CounterACT Package....3 Overview...4 1. Create a Deployment
Read the following information carefully, before you begin an upgrade.
 Read the following information carefully, before you begin an upgrade. Review Supported Upgrade Paths, page 1 Review Time Taken for Upgrade, page 1 Review Available Cisco APIC-EM Ports, page 2 Securing
Read the following information carefully, before you begin an upgrade. Review Supported Upgrade Paths, page 1 Review Time Taken for Upgrade, page 1 Review Available Cisco APIC-EM Ports, page 2 Securing
BIG-IP Access Policy Manager : Application Access. Version 13.0
 BIG-IP Access Policy Manager : Application Access Version 13.0 Table of Contents Table of Contents Configuring App Tunnel Access... 5 What are app tunnels?...5 About ACLs to control access from app tunnels...
BIG-IP Access Policy Manager : Application Access Version 13.0 Table of Contents Table of Contents Configuring App Tunnel Access... 5 What are app tunnels?...5 About ACLs to control access from app tunnels...
Novell Access Manager
 SSL VPN Server Guide AUTHORIZED DOCUMENTATION Novell Access Manager 3.1 SP3 February 02, 2011 www.novell.com Novell Access Manager 3.1 SP3 SSL VPN Server Guide Legal Notices Novell, Inc., makes no representations
SSL VPN Server Guide AUTHORIZED DOCUMENTATION Novell Access Manager 3.1 SP3 February 02, 2011 www.novell.com Novell Access Manager 3.1 SP3 SSL VPN Server Guide Legal Notices Novell, Inc., makes no representations
Appliance Administration Manual. v7.2
 Appliance Administration Manual v7.2 This document covers all required administration information for Loadbalancer.org appliances Copyright 2002-2012 Loadbalancer.org, Inc. 1 Table of Contents Section
Appliance Administration Manual v7.2 This document covers all required administration information for Loadbalancer.org appliances Copyright 2002-2012 Loadbalancer.org, Inc. 1 Table of Contents Section
System Configuration. The following topics explain how to configure system configuration settings on Firepower Management Centers and managed devices:
 The following topics explain how to configure system configuration settings on Firepower Management Centers and managed devices: Introduction to, page 2 Appliance Information, page 5 Custom HTTPS Certificates,
The following topics explain how to configure system configuration settings on Firepower Management Centers and managed devices: Introduction to, page 2 Appliance Information, page 5 Custom HTTPS Certificates,
Link Gateway Initial Configuration Manual
 Link Gateway Initial Configuration Manual Copyright 2016 NetLinkz. All Rights Reserved. No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval system, or translated
Link Gateway Initial Configuration Manual Copyright 2016 NetLinkz. All Rights Reserved. No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval system, or translated
NetScaler Gateway 10.5
 NetScaler Gateway 10.5 Jun 26, 2014 About This Release Key Features What's New Known Issues Compatibility with Citrix Products System Requirements NetScaler Gateway Plug-in System Requirements Endpoint
NetScaler Gateway 10.5 Jun 26, 2014 About This Release Key Features What's New Known Issues Compatibility with Citrix Products System Requirements NetScaler Gateway Plug-in System Requirements Endpoint
Deployment in a Microsoft Windows Server 2003, 2008, and 2012 Environment
 Deployment in a Microsoft Windows Server 2003, 2008, and 2012 Environment Prepare Microsoft Windows Server 2003, 2008, and 2012 for DSR To make servers that are running Microsoft Windows Server 2003, 2008,
Deployment in a Microsoft Windows Server 2003, 2008, and 2012 Environment Prepare Microsoft Windows Server 2003, 2008, and 2012 for DSR To make servers that are running Microsoft Windows Server 2003, 2008,
USER GUIDE. CTERA Agent for Windows. June 2016 Version 5.5
 USER GUIDE CTERA Agent for Windows June 2016 Version 5.5 Copyright 2009-2016 CTERA Networks Ltd. All rights reserved. No part of this document may be reproduced in any form or by any means without written
USER GUIDE CTERA Agent for Windows June 2016 Version 5.5 Copyright 2009-2016 CTERA Networks Ltd. All rights reserved. No part of this document may be reproduced in any form or by any means without written
Office and Express Print Release High Availability Setup Guide
 Office and Express Print Release High Availability Setup Guide Version 1.0 2017 EQ-HA-DCE-20170512 Print Release High Availability Setup Guide Document Revision History Revision Date May 12, 2017 September
Office and Express Print Release High Availability Setup Guide Version 1.0 2017 EQ-HA-DCE-20170512 Print Release High Availability Setup Guide Document Revision History Revision Date May 12, 2017 September
CONFIGURATION MANUAL. English version
 CONFIGURATION MANUAL English version Frama F-Link Configuration Manual (EN) All rights reserved. Frama Group. The right to make changes in this Installation Guide is reserved. Frama Ltd also reserves the
CONFIGURATION MANUAL English version Frama F-Link Configuration Manual (EN) All rights reserved. Frama Group. The right to make changes in this Installation Guide is reserved. Frama Ltd also reserves the
Proxy Auto-Config File
 Overview, page 1 Operation, page 1 Deployment, page 2 Examples, page 2 Configuring, page 3 Hosting on a Network Share, page 4 Overview Proxy Auto-Configuration (PAC) is a method used by web browsers to
Overview, page 1 Operation, page 1 Deployment, page 2 Examples, page 2 Configuring, page 3 Hosting on a Network Share, page 4 Overview Proxy Auto-Configuration (PAC) is a method used by web browsers to
Transport Gateway Installation / Registration / Configuration
 CHAPTER 4 Transport Gateway Installation / Registration / Configuration This chapter covers the following areas: Transport Gateway requirements. Security Considerations When Using a Transport Gateway.
CHAPTER 4 Transport Gateway Installation / Registration / Configuration This chapter covers the following areas: Transport Gateway requirements. Security Considerations When Using a Transport Gateway.
Appliance Administration Manual. v7.1
 Appliance Administration Manual v7.1 This document covers all required administration information for Loadbalancer.org appliances Copyright 2002-2011 Loadbalancer.org, Inc. 1 Table of Contents Section
Appliance Administration Manual v7.1 This document covers all required administration information for Loadbalancer.org appliances Copyright 2002-2011 Loadbalancer.org, Inc. 1 Table of Contents Section
Installation Guide for Pulse on Windows Server 2012
 USER GUIDE MADCAP PULSE 4 Installation Guide for Pulse on Windows Server 2012 Copyright 2018 MadCap Software. All rights reserved. Information in this document is subject to change without notice. The
USER GUIDE MADCAP PULSE 4 Installation Guide for Pulse on Windows Server 2012 Copyright 2018 MadCap Software. All rights reserved. Information in this document is subject to change without notice. The
SSL VPN Server Guide. Access Manager Appliance 3.2 SP2. June 2013
 SSL VPN Server Guide Access Manager Appliance 3.2 SP2 June 2013 Legal Notice THIS DOCUMENT AND THE SOFTWARE DESCRIBED IN THIS DOCUMENT ARE FURNISHED UNDER AND ARE SUBJECT TO THE TERMS OF A LICENSE AGREEMENT
SSL VPN Server Guide Access Manager Appliance 3.2 SP2 June 2013 Legal Notice THIS DOCUMENT AND THE SOFTWARE DESCRIBED IN THIS DOCUMENT ARE FURNISHED UNDER AND ARE SUBJECT TO THE TERMS OF A LICENSE AGREEMENT
Web Browser Application Troubleshooting Guide. Table of Contents
 Web Browser Application Troubleshooting Guide The following trouble shooting guide outlines tips for common problems which may resolve incorrect or unexpected behavior of NMFTA s web based applications.
Web Browser Application Troubleshooting Guide The following trouble shooting guide outlines tips for common problems which may resolve incorrect or unexpected behavior of NMFTA s web based applications.
Xcalar Installation Guide
 Xcalar Installation Guide Publication date: 2018-03-16 www.xcalar.com Copyright 2018 Xcalar, Inc. All rights reserved. Table of Contents Xcalar installation overview 5 Audience 5 Overview of the Xcalar
Xcalar Installation Guide Publication date: 2018-03-16 www.xcalar.com Copyright 2018 Xcalar, Inc. All rights reserved. Table of Contents Xcalar installation overview 5 Audience 5 Overview of the Xcalar
Deployment Guide: Routing Mode with No DMZ
 Deployment Guide: Routing Mode with No DMZ March 15, 2007 Deployment and Task Overview Description Follow the tasks in this guide to deploy the appliance as a router-firewall device on your network with
Deployment Guide: Routing Mode with No DMZ March 15, 2007 Deployment and Task Overview Description Follow the tasks in this guide to deploy the appliance as a router-firewall device on your network with
Clearswift SECURE Gateway Installation & Getting Started Guide. Version Document Revision 1.0
 Clearswift SECURE Email Gateway Installation & Getting Started Guide Version 4.6.0 Document Revision 1.0 Copyright Revision 1.0, April, 2017 Published by Clearswift Ltd. 1995 2017 Clearswift Ltd. All rights
Clearswift SECURE Email Gateway Installation & Getting Started Guide Version 4.6.0 Document Revision 1.0 Copyright Revision 1.0, April, 2017 Published by Clearswift Ltd. 1995 2017 Clearswift Ltd. All rights
NBC-IG Installation Guide. Version 7.2
 Installation Guide Version 7.2 2017 Nuance Business Connect 7.2 Installation Guide Document Revision History Revision Date August 8, 2017 Revision List Updated supported SQL Server versions June 14, 2017
Installation Guide Version 7.2 2017 Nuance Business Connect 7.2 Installation Guide Document Revision History Revision Date August 8, 2017 Revision List Updated supported SQL Server versions June 14, 2017
Stonesoft Management Center. Release Notes Revision B
 Stonesoft Management Center Release Notes 6.1.1 Revision B Table of contents 1 About this release...3 System requirements... 3 Build version...4 Compatibility... 5 2 New features...6 3 Enhancements...
Stonesoft Management Center Release Notes 6.1.1 Revision B Table of contents 1 About this release...3 System requirements... 3 Build version...4 Compatibility... 5 2 New features...6 3 Enhancements...
BROWSER-BASED SUPPORT CONSOLE USER S GUIDE. 31 January 2017
 BROWSER-BASED SUPPORT CONSOLE USER S GUIDE 31 January 2017 Contents 1 Introduction... 2 2 Netop Host Configuration... 2 2.1 Connecting through HTTPS using Certificates... 3 2.1.1 Self-signed certificate...
BROWSER-BASED SUPPORT CONSOLE USER S GUIDE 31 January 2017 Contents 1 Introduction... 2 2 Netop Host Configuration... 2 2.1 Connecting through HTTPS using Certificates... 3 2.1.1 Self-signed certificate...
Configuring F5 for SSL Intercept
 Configuring F5 for Welcome to the F5 deployment guide for configuring the BIG-IP system for SSL intercept (formerly called with Air Gap Egress Inspection). This document contains guidance on configuring
Configuring F5 for Welcome to the F5 deployment guide for configuring the BIG-IP system for SSL intercept (formerly called with Air Gap Egress Inspection). This document contains guidance on configuring
Acronis Backup Advanced for vcloud Update 7
 Acronis Backup Advanced for vcloud Update 7 QUICK START GUIDE Copyright Statement Copyright Acronis International GmbH, 2002-2018. All rights reserved. Acronis and Acronis Secure Zone are registered trademarks
Acronis Backup Advanced for vcloud Update 7 QUICK START GUIDE Copyright Statement Copyright Acronis International GmbH, 2002-2018. All rights reserved. Acronis and Acronis Secure Zone are registered trademarks
FieldView. Management Suite
 FieldView The FieldView Management Suite (FMS) system allows administrators to view the status of remote FieldView System endpoints, create and apply system configurations, and manage and apply remote
FieldView The FieldView Management Suite (FMS) system allows administrators to view the status of remote FieldView System endpoints, create and apply system configurations, and manage and apply remote
Visualization Performance & Fault Manager
 Visualization Performance & Fault Manager Software Release 2.3 Release Notes 1. Release Summary Release Date: 29-June-2011 Purpose: Software maintenance release for Avaya branding and Avaya device support.
Visualization Performance & Fault Manager Software Release 2.3 Release Notes 1. Release Summary Release Date: 29-June-2011 Purpose: Software maintenance release for Avaya branding and Avaya device support.
ForeScout CounterACT. Single CounterACT Appliance. Quick Installation Guide. Version 8.0
 ForeScout CounterACT Single CounterACT Appliance Version 8.0 Table of Contents Welcome to CounterACT Version 8.0... 4 CounterACT Package Contents... 4 Overview... 5 1. Create a Deployment Plan... 6 Decide
ForeScout CounterACT Single CounterACT Appliance Version 8.0 Table of Contents Welcome to CounterACT Version 8.0... 4 CounterACT Package Contents... 4 Overview... 5 1. Create a Deployment Plan... 6 Decide
RealPresence Access Director System Administrator s Guide
 [Type the document title] Polycom RealPresence Access Director System Administrator s Guide 2.1.0 March 2013 3725-78703-001A Polycom Document Title 1 Trademark Information POLYCOM and the names and marks
[Type the document title] Polycom RealPresence Access Director System Administrator s Guide 2.1.0 March 2013 3725-78703-001A Polycom Document Title 1 Trademark Information POLYCOM and the names and marks
MRD-310 MRD G Cellular Modem / Router Web configuration reference guide. Web configuration reference guide
 Web configuration reference guide 6623-3201 MRD-310 MRD-330 Westermo Teleindustri AB 2008 3G Cellular Modem / Router Web configuration reference guide www.westermo.com Table of Contents 1 Basic Configuration...
Web configuration reference guide 6623-3201 MRD-310 MRD-330 Westermo Teleindustri AB 2008 3G Cellular Modem / Router Web configuration reference guide www.westermo.com Table of Contents 1 Basic Configuration...
WatchGuard Dimension v2.0 Update 2 Release Notes. Introducing New Dimension Command. Build Number Revision Date 13 August 2015
 WatchGuard Dimension v2.0 Update 2 Release Notes Build Number 483146 Revision Date 13 August 2015 On 13 August 2015, WatchGuard released Dimension v2.0 Update 2. This update resolves an issue that caused
WatchGuard Dimension v2.0 Update 2 Release Notes Build Number 483146 Revision Date 13 August 2015 On 13 August 2015, WatchGuard released Dimension v2.0 Update 2. This update resolves an issue that caused
Clearswift Gateway Installation & Getting Started Guide. Version 4.1 Document Revision 1.4
 Clearswift Gateway Installation & Getting Started Guide Version 4.1 Document Revision 1.4 Copyright Revision 1.4, March, 2015 Published by Clearswift Ltd. 1995 2015 Clearswift Ltd. All rights reserved.
Clearswift Gateway Installation & Getting Started Guide Version 4.1 Document Revision 1.4 Copyright Revision 1.4, March, 2015 Published by Clearswift Ltd. 1995 2015 Clearswift Ltd. All rights reserved.
System Administration
 Most of SocialMiner system administration is performed using the panel. This section describes the parts of the panel as well as other administrative procedures including backup and restore, managing certificates,
Most of SocialMiner system administration is performed using the panel. This section describes the parts of the panel as well as other administrative procedures including backup and restore, managing certificates,
Linux VPN Configuration
 Linux VPN Configuration Note. This information is based on Red Hat 9.0, it should be used as a guide only as other distributions may have similar installation methods. VPN Software Installation - PPP (Point-to-Point
Linux VPN Configuration Note. This information is based on Red Hat 9.0, it should be used as a guide only as other distributions may have similar installation methods. VPN Software Installation - PPP (Point-to-Point
