4/5/2018. Current and future IT applications in the medical physics world From the start of computing to Information Technology as we know IT
|
|
|
- Griselda Leonard
- 5 years ago
- Views:
Transcription
1 Objectives Current and future IT applications in the medical physics world From the start of computing to Information Technology as we know IT How did we get here? Understand the history of computers and networks Where is here? Understand network terminology Review systems in use today Understand basic network concepts that affect our day to day responsibilities Where are we going? What is the cloud, exactly? What does it mean for me? Disclosure CEO ZapIT! Medical Gottfried Wilhelm Leibniz Herman Hollerith J.V. Anastoff Blaise Pascal Charles Babbage Alan Turing David Packard Bill Hewlett 1
2 John Mauchly J Presper Eckert Grace Hopper Computer w/ Mouse Floppy Disk Blaise Pascal mechanical calculator First to be patented and sold commercially J.V. Atanasoff Clifford Berry Integrated Chip 1964 UNIX 1971 Ethernet Ada Lovelace Imagination Apple Computer VisiCalc & Apple LISA Wordstar Altair Computer TRS-80 IBM PC Windows & First Apple II dot.com HTML Mosaic Browser HPCCA Al Gore It is the Combining faculty. It brings together things, facts, ideas, conceptions in new, original, endless ever varying combinations.... It is that which penetrates into the unseen worlds around us, the worlds of Science 2
3 Ada Lovelace Analytic Engine Information Technology Storing act upon other things besides number, were objects found whose mutual fundamental relations could be expressed by those of the abstract science of operations Retrieving Transmitting Manipulating Data Through networks Networked Our World PACS High Capacity Lots of information DICOM Images Plans Treatment Records Documents Reliable Responsive Cost Effective 3
4 Our World Treatment process Open Systems Interconnection Model APPLICATION PRESENTATION SESSION TRANSPORT NETWORK DATA LINK PHYSICAL Physical Structure Transmission and reception of the raw bit stream over the physical medium Cables Hubs Application Data encoding Physical medium attachment Transmission technique (broadband, baseband) Electrical impulses 4
5 Physical Layer Risks Disruption of service Power interruption Disconnection Physical damage Outright theft Data Link Frames envelopes Error free transfer of data frames from one node to another over the physical layer NIC card Switch NIC card MAC address Logical Link Control (LLC) Data Link Layer Risks MAC address spoofing VLAN circumvention ARP cache poisoning Network Packets Letter Contains IP address Controls the operations of the subnet, deciding which physical path the data takes Routing Subnet traffic control Logical physical address mapping 5
6 Network Layer Risks IP Address Spoofing Network Routes Spoofing Transport TCP Host to host flow control Ensures that messages are delivered error free, in sequence, and with no losses or duplications Message segmentation Message acknowledgement Transport Layer Risks Network infiltration Network blocking Session Sync and send to ports Allows session establishment between processes running on different stations Maintenance and termination Session support Perform security, name recognition, logging, etc. 6
7 Session Layer Risks Password spoofing Authentication spoofing Brute force Presentation Syntax Layer (Translator of the network) Formats the data to be presented to the application layer. Character code transition Data conversion Data compression Data encryption Translation Presentation Layer Risks Unicode vulnerabilities Unexpected input Application End User Layer Program that opens what was sent or prepares what is to be sent Serves as the window for users and application processes to access the network services Resource sharing Remote file access Directory services Network management 7
8 Application Layer Risks Now and the future E mail Attachments Our World PACS Our World Treatment process 8
9 Cloud computing IT Management easier Disaster management easier Software versioning easier Storage not a problem Cost reduction Green computing Data more accessible Scalability Summary 9
Copyright 2012 Pearson Education, Inc. Publishing as Prentice Hall
 1 Technology in Action Technology in Focus: The History of the PC 2 The first personal computer Sold as a kit Switches for input Lights for output Altair 8800 Bill Gates and Paul Allen created a compiler
1 Technology in Action Technology in Focus: The History of the PC 2 The first personal computer Sold as a kit Switches for input Lights for output Altair 8800 Bill Gates and Paul Allen created a compiler
Computers in Engineering COMP 208. A Brief History. Mechanical Calculators. A Historic Perspective Michael A. Hawker
 Computers in Engineering COMP 208 A Historic Perspective Michael A. Hawker Sept 4th, 2007 Computers in Engineering 1 A Brief History Abacus considered first mechanical computing device Used beads and rods
Computers in Engineering COMP 208 A Historic Perspective Michael A. Hawker Sept 4th, 2007 Computers in Engineering 1 A Brief History Abacus considered first mechanical computing device Used beads and rods
Computers in Engineering COMP 208
 Computers in Engineering COMP 208 A Historic Perspective Michael A. Hawker Sept 4th, 2007 Computers in Engineering 1 A Brief History Abacus considered first mechanical computing device Used beads and rods
Computers in Engineering COMP 208 A Historic Perspective Michael A. Hawker Sept 4th, 2007 Computers in Engineering 1 A Brief History Abacus considered first mechanical computing device Used beads and rods
OSI Layers (Open System Interconnection)
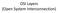 OSI Layers (Open System Interconnection) What is a Network? A network refers to two or more connected computers that can share resources such as data, a printer, an Internet connection, applications, or
OSI Layers (Open System Interconnection) What is a Network? A network refers to two or more connected computers that can share resources such as data, a printer, an Internet connection, applications, or
Computer Organization CS 206T
 Computer Organization CS 206T Topics Introduction Historical Background Structure & Function System Interconnection 2 1. Introduction Why study computer organization and architecture? Design better programs,
Computer Organization CS 206T Topics Introduction Historical Background Structure & Function System Interconnection 2 1. Introduction Why study computer organization and architecture? Design better programs,
Defining Networks with the OSI Model. Module 2
 Defining Networks with the OSI Model Module 2 Objectives Skills Concepts Objective Domain Description Objective Domain Number Understanding OSI Basics Defining the Communications Subnetwork Defining the
Defining Networks with the OSI Model Module 2 Objectives Skills Concepts Objective Domain Description Objective Domain Number Understanding OSI Basics Defining the Communications Subnetwork Defining the
Chapter 1: Introduction to Computers
 Slide 1/17 Learning Objectives In this chapter you will learn about: Computer Data processing Characteristic features of computers Computers evolution to their present form Computer generations Characteristic
Slide 1/17 Learning Objectives In this chapter you will learn about: Computer Data processing Characteristic features of computers Computers evolution to their present form Computer generations Characteristic
Learning Objectives. In this chapter you will learn about:
 Ref Page Slide 1/17 Learning Objectives In this chapter you will learn about: Computer Data processing Characteristic features of computers Computers evolution to their present form Computer generations
Ref Page Slide 1/17 Learning Objectives In this chapter you will learn about: Computer Data processing Characteristic features of computers Computers evolution to their present form Computer generations
Chapter 1: Introduction to Computers. In this chapter you will learn about:
 Ref Page Slide 1/17 Learning Objectives In this chapter you will learn about: Computer Data processing Characteristic features of computers Computers evolution to their present form Computer generations
Ref Page Slide 1/17 Learning Objectives In this chapter you will learn about: Computer Data processing Characteristic features of computers Computers evolution to their present form Computer generations
History of Computers. What Is A Computer? Egyptian Numbers. Ancient Tools for Computation. Introduction to Computers
 What Is A Computer? History of Computers Introduction to Computers Adapted from slides by Prof. Polly Huang and Prof. KM Chao (National Taiwan University) com put er Pronunciation: kâm-'pyü-ter Function:
What Is A Computer? History of Computers Introduction to Computers Adapted from slides by Prof. Polly Huang and Prof. KM Chao (National Taiwan University) com put er Pronunciation: kâm-'pyü-ter Function:
You Will Need Floppy Disks for your labs!
 CIS121 Instructor: Lynne Mayer VoiceMail: (847) 697-1000 x 2328 Lmayer@elgin.edu Office Hours: ICT 122 Mon.: 9:15-10:15 AM, 5:15-6:00 PM Wed.: 9:15-10:15 AM Fri.: 2:30-3:30 PM Website: faculty.elgin.edu/lmayer
CIS121 Instructor: Lynne Mayer VoiceMail: (847) 697-1000 x 2328 Lmayer@elgin.edu Office Hours: ICT 122 Mon.: 9:15-10:15 AM, 5:15-6:00 PM Wed.: 9:15-10:15 AM Fri.: 2:30-3:30 PM Website: faculty.elgin.edu/lmayer
The Client Server Model and Software Design
 The Client Server Model and Software Design Prof. Chuan-Ming Liu Computer Science and Information Engineering National Taipei University of Technology Taipei, TAIWAN MCSE Lab, NTUT, TAIWAN 1 Introduction
The Client Server Model and Software Design Prof. Chuan-Ming Liu Computer Science and Information Engineering National Taipei University of Technology Taipei, TAIWAN MCSE Lab, NTUT, TAIWAN 1 Introduction
COURSE OVERVIEW. Introduction to Computer Engineering 2015 Spring by Euiseong Seo
 COURSE OVERVIEW Introduction to Computer Engineering 2015 Spring by Euiseong Seo Course Objectives Introduction to computer engineering For computer engineer-wannabe For students studying other fields
COURSE OVERVIEW Introduction to Computer Engineering 2015 Spring by Euiseong Seo Course Objectives Introduction to computer engineering For computer engineer-wannabe For students studying other fields
The Generations of Computers
 The Generations of Computers The development of computers started with mechanical and electromechanical devices (17 th through 19 th century) and has progressed through four generations of computers. Mechanical
The Generations of Computers The development of computers started with mechanical and electromechanical devices (17 th through 19 th century) and has progressed through four generations of computers. Mechanical
Switching on our smartphone and sending an to a friend living 5000 km from our home is something that we take for granted, but that involves a
 Switching on our smartphone and sending an email to a friend living 5000 km from our home is something that we take for granted, but that involves a lot of very complex processes and has to take into account
Switching on our smartphone and sending an email to a friend living 5000 km from our home is something that we take for granted, but that involves a lot of very complex processes and has to take into account
Early Calculating Tools
 Early Calculating Tools Abacus At least 5,000 years old Memory aid for making calculations Cannot perform actual computations Eventually replaced by pencil and paper Early Calculating Tools Pascalene Invented
Early Calculating Tools Abacus At least 5,000 years old Memory aid for making calculations Cannot perform actual computations Eventually replaced by pencil and paper Early Calculating Tools Pascalene Invented
EVOLUTION OF COMPUTERS. In the early years, before the computer was invented, there are several inventions of counting machines.
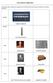 EVOLUTION OF COMPUTERS In the early years, before the computer was invented, there are several inventions of counting machines. 200 BC 500 BC CHINESE ABACUS EGYPTIAN ABACUS 1620 JOHN NAPIER NAPIER'S BONES
EVOLUTION OF COMPUTERS In the early years, before the computer was invented, there are several inventions of counting machines. 200 BC 500 BC CHINESE ABACUS EGYPTIAN ABACUS 1620 JOHN NAPIER NAPIER'S BONES
MEBS Utilities services M.Sc.(Eng) in building services Faculty of Engineering University of Hong Kong
 Open System Interconnection MEBS 6000 2010 Utilities services ISO 1984: ISO Standard 7498 Information Processing System Open System Interconnection Basic Reference Model OSI is itself not a standard, but
Open System Interconnection MEBS 6000 2010 Utilities services ISO 1984: ISO Standard 7498 Information Processing System Open System Interconnection Basic Reference Model OSI is itself not a standard, but
The trusted, student-friendly online reference tool. Name: Date:
 World Book Online: The trusted, student-friendly online reference tool. World Book Advanced Database* Name: Date: History of Computers Computers! Virtually no other form of technology has become so powerful
World Book Online: The trusted, student-friendly online reference tool. World Book Advanced Database* Name: Date: History of Computers Computers! Virtually no other form of technology has become so powerful
Computer History CSCE 101
 Computer History CSCE 101 Computer History In 40 years computers went from being giant expensive machines that only corporations could own to the personal computer we see today. Early Calculating Devices
Computer History CSCE 101 Computer History In 40 years computers went from being giant expensive machines that only corporations could own to the personal computer we see today. Early Calculating Devices
Unicasts, Multicasts and Broadcasts
 Unicasts, Multicasts and Broadcasts Part 1: Frame-Based LAN Operation V1.0: Geoff Bennett Contents LANs as a Shared Medium A "Private" Conversation Multicast Addressing Performance Issues In this tutorial
Unicasts, Multicasts and Broadcasts Part 1: Frame-Based LAN Operation V1.0: Geoff Bennett Contents LANs as a Shared Medium A "Private" Conversation Multicast Addressing Performance Issues In this tutorial
HST250 (section 740) Exam #1 Wednesday, February 10, 2010
 HST250 (section 740) Exam #1 Wednesday, February 10, 2010 NAME: PID: Instructions Make sure you enter your name & PID on the exam sheet Select the best answer from those provided You may not leave the
HST250 (section 740) Exam #1 Wednesday, February 10, 2010 NAME: PID: Instructions Make sure you enter your name & PID on the exam sheet Select the best answer from those provided You may not leave the
Chapter 1. The Big Picture
 Chapter 1 The Big Picture 1.1 Computing Systems Hardware The physical elements of a computing system (printer, circuit boards, wires, keyboard ) Software The programs that provide the instructions for
Chapter 1 The Big Picture 1.1 Computing Systems Hardware The physical elements of a computing system (printer, circuit boards, wires, keyboard ) Software The programs that provide the instructions for
CCNA Exploration Network Fundamentals. Chapter 03 Application Functionality and Protocols
 CCNA Exploration Network Fundamentals Chapter 03 Application Functionality and Protocols Updated: 27/04/2008 1 3.1 Applications: The Interface Between Human and Networks Applications provide the means
CCNA Exploration Network Fundamentals Chapter 03 Application Functionality and Protocols Updated: 27/04/2008 1 3.1 Applications: The Interface Between Human and Networks Applications provide the means
Welcome to COS151! 1.1
 Welcome to COS151! Title: Introduction to Computer Science Course website: https://cs.up.ac.za/admin/courses/cos151 Find the study guide there Announcements Assignments (download & upload) Brief overview
Welcome to COS151! Title: Introduction to Computer Science Course website: https://cs.up.ac.za/admin/courses/cos151 Find the study guide there Announcements Assignments (download & upload) Brief overview
1: Review Of Semester Provide an overview of encapsulation.
 1: Review Of Semester 1 1.1.1.1. Provide an overview of encapsulation. Networking evolves to support current and future applications. By dividing and organizing the networking tasks into separate layers/functions,
1: Review Of Semester 1 1.1.1.1. Provide an overview of encapsulation. Networking evolves to support current and future applications. By dividing and organizing the networking tasks into separate layers/functions,
NETWORK INTRUSION. Information Security in Systems & Networks Public Development Program. Sanjay Goel University at Albany, SUNY Fall 2006
 NETWORK INTRUSION Information Security in Systems & Networks Public Development Program Sanjay Goel University at Albany, SUNY Fall 2006 1 Learning Objectives Students should be able to: Recognize different
NETWORK INTRUSION Information Security in Systems & Networks Public Development Program Sanjay Goel University at Albany, SUNY Fall 2006 1 Learning Objectives Students should be able to: Recognize different
Introduction to Computer Systems
 Introduction to Computer Systems By Farhan Ahmad farhanahmad@uet.edu.pk Department of Chemical Engineering, University of Engineering & Technology Lahore Introducing Computer Systems Exploring computers
Introduction to Computer Systems By Farhan Ahmad farhanahmad@uet.edu.pk Department of Chemical Engineering, University of Engineering & Technology Lahore Introducing Computer Systems Exploring computers
Revision of Previous Lectures
 Lecture 15 Overview Last Lecture Local area networking This Lecture Wide area networking 1 Source: chapters 8.1-8.3, 17.1, 18.1, 18.2 Next Lecture Wide area networking 2 Source: Chapter 20 COSC244 Lecture
Lecture 15 Overview Last Lecture Local area networking This Lecture Wide area networking 1 Source: chapters 8.1-8.3, 17.1, 18.1, 18.2 Next Lecture Wide area networking 2 Source: Chapter 20 COSC244 Lecture
A Brief History of Computer Science
 A Brief History of Computer Science 4700 Hundred years ago Sumerians invented the abacus Sand, lines, pebbles Sexagesimal Base 60 still used today Time, distance How do you count like that? Side trip Factors
A Brief History of Computer Science 4700 Hundred years ago Sumerians invented the abacus Sand, lines, pebbles Sexagesimal Base 60 still used today Time, distance How do you count like that? Side trip Factors
Computer Network : Lecture Notes Nepal Engineering College Compiled by: Junior Professor: Daya Ram Budhathoki Nepal Engineering college, Changunarayan
 Computer Network : Lecture Notes Nepal Engineering College Compiled by: Junior Professor: Daya Ram Budhathoki Nepal Engineering college, Changunarayan Chapter3: OSI Reference Model: Network Software: Network
Computer Network : Lecture Notes Nepal Engineering College Compiled by: Junior Professor: Daya Ram Budhathoki Nepal Engineering college, Changunarayan Chapter3: OSI Reference Model: Network Software: Network
Guide to Networking Essentials, 6 th Edition. Chapter 6: Network Reference Models and Standards
 Guide to Networking Essentials, 6 th Edition Chapter 6: Network Reference Models and Standards Objectives Explain the OSI reference model layers and their relationship to hardware and software Explain
Guide to Networking Essentials, 6 th Edition Chapter 6: Network Reference Models and Standards Objectives Explain the OSI reference model layers and their relationship to hardware and software Explain
CS 105 Review Questions #3
 1 CS 105 Review Questions #3 These review questions only include topics since our second test. To study for the final, please look at the first two review documents as well. Almost all of these questions
1 CS 105 Review Questions #3 These review questions only include topics since our second test. To study for the final, please look at the first two review documents as well. Almost all of these questions
Fundamentals of Python: First Programs. Chapter 1: Introduction Modifications by Mr. Dave Clausen
 Fundamentals of Python: First Programs Chapter 1: Introduction Modifications by Mr. Dave Clausen Objectives After completing this chapter, you will be able to: Describe the basic features of an algorithm
Fundamentals of Python: First Programs Chapter 1: Introduction Modifications by Mr. Dave Clausen Objectives After completing this chapter, you will be able to: Describe the basic features of an algorithm
OSI Reference Model. Computer Networks lab ECOM Prepared By : Eng. Motaz Murtaja Eng. Ola Abd Elatief
 Islamic University of Gaza Faculty of Engineering Computer Engineering Department Computer Networks lab ECOM 4121 OSI Reference Model Prepared By : Eng. Motaz Murtaja Eng. Ola Abd Elatief May /2010 OSI
Islamic University of Gaza Faculty of Engineering Computer Engineering Department Computer Networks lab ECOM 4121 OSI Reference Model Prepared By : Eng. Motaz Murtaja Eng. Ola Abd Elatief May /2010 OSI
Chapter 3: Network Protocols and Communications CCENT Routing and Switching Introduction to Networks v6.0 Instructor Planning Guide
 Chapter 3: Network Protocols and Communications CCENT Routing and Switching Introduction to Networks v6.0 Instructor Planning Guide CCNET v6 1 Chapter 3: Network Protocols and Communications CCENT Routing
Chapter 3: Network Protocols and Communications CCENT Routing and Switching Introduction to Networks v6.0 Instructor Planning Guide CCNET v6 1 Chapter 3: Network Protocols and Communications CCENT Routing
Data Communication and Network. Introducing Networks
 Data Communication and Network Introducing Networks Introduction to Networking Computer network, or simply network Refers to the connection of two or more computers by some type of medium You can connect
Data Communication and Network Introducing Networks Introduction to Networking Computer network, or simply network Refers to the connection of two or more computers by some type of medium You can connect
Configuring your VLAN. Presented by Gregory Laffoon
 Configuring your VLAN Presented by Gregory Laffoon 1 Overview of Networking Terms Networking Terms Overview OSI Model Defines a networking framework for implementing protocols in seven layers Control is
Configuring your VLAN Presented by Gregory Laffoon 1 Overview of Networking Terms Networking Terms Overview OSI Model Defines a networking framework for implementing protocols in seven layers Control is
Network Review TEJ4M. SBrace
 Network Review TEJ4M SBrace Example of how the OSI Layers work using an e-mail sent from the computer on the left. Email sent from John: Meet me at Carl s 1:30 John Identify sender and intended receiver;
Network Review TEJ4M SBrace Example of how the OSI Layers work using an e-mail sent from the computer on the left. Email sent from John: Meet me at Carl s 1:30 John Identify sender and intended receiver;
Computer Forensics: Investigating Network Intrusions and Cybercrime, 2nd Edition. Chapter 2 Investigating Network Traffic
 Computer Forensics: Investigating Network Intrusions and Cybercrime, 2nd Edition Chapter 2 Investigating Network Traffic Objectives After completing this chapter, you should be able to: Understand network
Computer Forensics: Investigating Network Intrusions and Cybercrime, 2nd Edition Chapter 2 Investigating Network Traffic Objectives After completing this chapter, you should be able to: Understand network
Lecture Outline. Lecture 2. OSI model and networking. The OSI model and networking. The OSI model and networking. The OSI model and networking
 Lecture 2 The OSI model Chapter 2, specifically pages 42-58 Dave Novak School of Business Administration, University of Vermont Sources: 1) Network+ Guide to Networks, Dean 2013 2) Comer, Computer Networks
Lecture 2 The OSI model Chapter 2, specifically pages 42-58 Dave Novak School of Business Administration, University of Vermont Sources: 1) Network+ Guide to Networks, Dean 2013 2) Comer, Computer Networks
HISTORY OF COMPUTERS HISTORY OF COMPUTERS. Mesleki İngilizce - Technical English. Punch Card. Digital Data. II Prof. Dr. Nizamettin AYDIN.
 Mesleki İngilizce - Technical English II Prof. Dr. Nizamettin AYDIN naydin@yildiz.edu.tr Notes: In the slides, texts enclosed by curly parenthesis, { }, are examples. texts enclosed by square parenthesis,
Mesleki İngilizce - Technical English II Prof. Dr. Nizamettin AYDIN naydin@yildiz.edu.tr Notes: In the slides, texts enclosed by curly parenthesis, { }, are examples. texts enclosed by square parenthesis,
Unit A - Connecting to the Network
 Unit A - Connecting to the Network 1 What is a network? The ability to connect people and equipment no matter where they are in the world. telephone computers television How does your body work as a network?
Unit A - Connecting to the Network 1 What is a network? The ability to connect people and equipment no matter where they are in the world. telephone computers television How does your body work as a network?
Chapter -4 OSI Reference Model
 Chapter -4 OSI Reference Model Objectives Concept of Reference Model. OSI Reference Model Concept. Layers of OSI Reference Model. 4.1 Introduction Layered Architecture, Peer-to- Peer Processes, Interfaces
Chapter -4 OSI Reference Model Objectives Concept of Reference Model. OSI Reference Model Concept. Layers of OSI Reference Model. 4.1 Introduction Layered Architecture, Peer-to- Peer Processes, Interfaces
The OSI Model. Open Systems Interconnection (OSI). Developed by the International Organization for Standardization (ISO).
 Network Models The OSI Model Open Systems Interconnection (OSI). Developed by the International Organization for Standardization (ISO). Model for understanding and developing computer-to-computer communication
Network Models The OSI Model Open Systems Interconnection (OSI). Developed by the International Organization for Standardization (ISO). Model for understanding and developing computer-to-computer communication
Chapter 2. Communicating Over The Network. CCNA1-1 Chapter 2
 Chapter 2 Communicating Over The Network CCNA1-1 Chapter 2 Communicating Over the Network The Platform for Communications CCNA1-2 Chapter 2 Elements of Communication People communicate in many different
Chapter 2 Communicating Over The Network CCNA1-1 Chapter 2 Communicating Over the Network The Platform for Communications CCNA1-2 Chapter 2 Elements of Communication People communicate in many different
Getting Started. Contents
 Contents 1 Contents Introduction................................................... 1-2 Conventions................................................... 1-2 Feature Descriptions by Model................................
Contents 1 Contents Introduction................................................... 1-2 Conventions................................................... 1-2 Feature Descriptions by Model................................
OSI Model. Teran Subasinghe MBCS, Bsc.(Hons) in Computer Science - University of Greenwich, UK
 OSI Model Teran Subasinghe MBCS, Bsc.(Hons) in Computer Science - University of Greenwich, UK What is OSI Model? Open Systems Interconnection Reference Model Developed in 1984 by the International Standards
OSI Model Teran Subasinghe MBCS, Bsc.(Hons) in Computer Science - University of Greenwich, UK What is OSI Model? Open Systems Interconnection Reference Model Developed in 1984 by the International Standards
A Short History of Computers
 A Short History of Computers Geoffrey M. Rockwell x 24072 Togo Salmon 309A grockwel@mcmaster.ca URL: http://www.humanities.mcmaster.ca/~hccrs/ihchome.htm McMaster University Administration u Homework 3
A Short History of Computers Geoffrey M. Rockwell x 24072 Togo Salmon 309A grockwel@mcmaster.ca URL: http://www.humanities.mcmaster.ca/~hccrs/ihchome.htm McMaster University Administration u Homework 3
ITEC 3800 Data Communication and Network. Introducing Networks
 ITEC 3800 Data Communication and Network Introducing Networks Introduction to Networking Computer network, or simply network Refers to the connection of two or more computers by some type of medium You
ITEC 3800 Data Communication and Network Introducing Networks Introduction to Networking Computer network, or simply network Refers to the connection of two or more computers by some type of medium You
Chapter 2. Communicating Over The Network
 Chapter 2 Communicating Over The Network CCNA1-1 Chapter 2 Note for Instructors These presentations are the result of a collaboration among the instructors at St. Clair College in Windsor, Ontario. Thanks
Chapter 2 Communicating Over The Network CCNA1-1 Chapter 2 Note for Instructors These presentations are the result of a collaboration among the instructors at St. Clair College in Windsor, Ontario. Thanks
Architectures of Communication Subsystems
 Architectures of Communication Subsystems Open System Interconnection Reference Model Computer Networks Lecture 2 http://goo.gl/pze5o8 Connection-Oriented versus Connectionless Communication 2 Connection-Oriented
Architectures of Communication Subsystems Open System Interconnection Reference Model Computer Networks Lecture 2 http://goo.gl/pze5o8 Connection-Oriented versus Connectionless Communication 2 Connection-Oriented
A (BRIEF) HISTORY OF COMPUTING. By Dane Paschal
 A (BRIEF) HISTORY OF COMPUTING By Dane Paschal BIASES Amero-Euro centric Computer science centric Google centric ANCIENT ORIGINS Counting is hard The Human Brain Abacus Numerals THE 1700 S AND 1800 S Computing
A (BRIEF) HISTORY OF COMPUTING By Dane Paschal BIASES Amero-Euro centric Computer science centric Google centric ANCIENT ORIGINS Counting is hard The Human Brain Abacus Numerals THE 1700 S AND 1800 S Computing
Computer Communication & Networks / Data Communication & Computer Networks Week # 03
 Computer Communication & Networks / Data Communication & Computer Networks Week # 03 M.Nadeem Akhtar CS & IT Department The University of Lahore Email: nadeem.akhtar@cs.uol.edu.pk URL-https://sites.google.com/site/nadeemuolcsccn/home
Computer Communication & Networks / Data Communication & Computer Networks Week # 03 M.Nadeem Akhtar CS & IT Department The University of Lahore Email: nadeem.akhtar@cs.uol.edu.pk URL-https://sites.google.com/site/nadeemuolcsccn/home
20-CS Cyber Defense Overview Fall, Network Basics
 20-CS-5155 6055 Cyber Defense Overview Fall, 2017 Network Basics Who Are The Attackers? Hackers: do it for fun or to alert a sysadmin Criminals: do it for monetary gain Malicious insiders: ignores perimeter
20-CS-5155 6055 Cyber Defense Overview Fall, 2017 Network Basics Who Are The Attackers? Hackers: do it for fun or to alert a sysadmin Criminals: do it for monetary gain Malicious insiders: ignores perimeter
Describe the layers of a computer system
 Chapter 1 The Big Picture Chapter Goals Describe the layers of a computer system Describe the concept of abstraction and its relationship to computing Describe the history of computer hardware and software
Chapter 1 The Big Picture Chapter Goals Describe the layers of a computer system Describe the concept of abstraction and its relationship to computing Describe the history of computer hardware and software
Component 4: Introduction to Information and Computer Science
 Component 4: Introduction to Information and Computer Science Unit 7: Networks & Networking (Part 5 of 5) Unit Objectives Understand the history of networks and their evolution. List and describe the various
Component 4: Introduction to Information and Computer Science Unit 7: Networks & Networking (Part 5 of 5) Unit Objectives Understand the history of networks and their evolution. List and describe the various
Welcome to COSC Introduction to Computer Science
 Welcome to COSC 1302 Introduction to Computer Science (Syllabus) Chapter 1 The Big Picture 1.1 Computing Systems Hardware The physical elements of a computing system (printer, circuit boards, wires, keyboard
Welcome to COSC 1302 Introduction to Computer Science (Syllabus) Chapter 1 The Big Picture 1.1 Computing Systems Hardware The physical elements of a computing system (printer, circuit boards, wires, keyboard
Introduction to Networking
 Introduction to Networking Chapters 1 and 2 Outline Computer Network Fundamentals Defining a Network Networks Defined by Geography Networks Defined by Topology Networks Defined by Resource Location OSI
Introduction to Networking Chapters 1 and 2 Outline Computer Network Fundamentals Defining a Network Networks Defined by Geography Networks Defined by Topology Networks Defined by Resource Location OSI
1: History, Generation & Classification. Shobhanjana Kalita, Dept. of CSE, Tezpur University
 1: History, Generation & Classification Shobhanjana Kalita, Dept. of CSE, Tezpur University History Computer originally (17 th century) meant someone who computes Only in the 20 th century it was associated
1: History, Generation & Classification Shobhanjana Kalita, Dept. of CSE, Tezpur University History Computer originally (17 th century) meant someone who computes Only in the 20 th century it was associated
time step first instruction second instruction
 COMP1200 2001 Semester 1 61 Parallelism Microprocessors can use a variety of tricks to execute more instructions in a given amount of time. One of the most successful is to execute more than one instruction
COMP1200 2001 Semester 1 61 Parallelism Microprocessors can use a variety of tricks to execute more instructions in a given amount of time. One of the most successful is to execute more than one instruction
An Incomplete History of Computation
 An Incomplete History of Computation Charles Babbage 1791-1871 Lucasian Professor of Mathematics, Cambridge University, 1827-1839 First computer designer Ada Lovelace 1815-1852 First computer programmer
An Incomplete History of Computation Charles Babbage 1791-1871 Lucasian Professor of Mathematics, Cambridge University, 1827-1839 First computer designer Ada Lovelace 1815-1852 First computer programmer
Test 2 Ch. 1,2 consists of 40 questions selected from the following:
 1. refers to the programs that give commands to the computer. 2. can keep track of the purchases customers make along with their geographic data, past buying history, and lists of items they examine but
1. refers to the programs that give commands to the computer. 2. can keep track of the purchases customers make along with their geographic data, past buying history, and lists of items they examine but
ALGORITHMS AND PROGRAMMING
 ALGORITHMS AND PROGRAMMING -2- CSC 2201 Dokuz Eylul University, Faculty of Science, Department of Mathematics 2 History of Computers 2600 (BC) Abacus Simple addition and subtraction 1621 Slide Rule 3 The
ALGORITHMS AND PROGRAMMING -2- CSC 2201 Dokuz Eylul University, Faculty of Science, Department of Mathematics 2 History of Computers 2600 (BC) Abacus Simple addition and subtraction 1621 Slide Rule 3 The
CIT 380: Securing Computer Systems. Network Security Concepts
 CIT 380: Securing Computer Systems Network Security Concepts Topics 1. Protocols and Layers 2. Layer 2 Network Concepts 3. MAC Spoofing 4. ARP 5. ARP Spoofing 6. Network Sniffing Protocols A protocol defines
CIT 380: Securing Computer Systems Network Security Concepts Topics 1. Protocols and Layers 2. Layer 2 Network Concepts 3. MAC Spoofing 4. ARP 5. ARP Spoofing 6. Network Sniffing Protocols A protocol defines
History of Computing. Slides from NYU and Georgia Tech
 History of Computing Slides from NYU and Georgia Tech Early Computational Devices (Chinese) Abacus 2700 2300 BC Used for performing arithmetic operations Early Computational Devices Napier s Bones, 1617
History of Computing Slides from NYU and Georgia Tech Early Computational Devices (Chinese) Abacus 2700 2300 BC Used for performing arithmetic operations Early Computational Devices Napier s Bones, 1617
CS 1 Notes 1 - Early Computing and 2 - Electronic Computing
 CS 1 Notes 1 - Early Computing and 2 - Electronic Computing Computer Science: The discipline that seeks to build a scientific foundation for such topics as: computer design computer programming information
CS 1 Notes 1 - Early Computing and 2 - Electronic Computing Computer Science: The discipline that seeks to build a scientific foundation for such topics as: computer design computer programming information
History of Modern Computing Lesson 1
 History of Modern Computing Lesson 1 www.soe.ucsc.edu/classes/cmpe080h/fall05 David Pease Computer Engineering Department Jack Baskin School of Engineering Lesson Outline Definition of a computer Types
History of Modern Computing Lesson 1 www.soe.ucsc.edu/classes/cmpe080h/fall05 David Pease Computer Engineering Department Jack Baskin School of Engineering Lesson Outline Definition of a computer Types
Network Architecture. TOC Architecture
 Network Architecture Introduction Layering Example Internet Layers First Look Layering Step by Step Downside of Layering Interconnecting Networks The Internet TOC Architecture Introduction Issues: Inter-operability
Network Architecture Introduction Layering Example Internet Layers First Look Layering Step by Step Downside of Layering Interconnecting Networks The Internet TOC Architecture Introduction Issues: Inter-operability
Prehistory, History, Present, Future. Lenuţa Alboaie
 Prehistory, History, Present, Future Lenuţa Alboaie adria@info.uaic.ro 2018 2019 Computer Networks http://www.info.uaic.ro/~computernetworks 1 Prehistory Origins of the Internet The desire to communicate
Prehistory, History, Present, Future Lenuţa Alboaie adria@info.uaic.ro 2018 2019 Computer Networks http://www.info.uaic.ro/~computernetworks 1 Prehistory Origins of the Internet The desire to communicate
Algorithm: Program: Programming: Software: Hardware:
 0-1 0-2 Terminology Algorithm: A set of steps that defines how a task is performed Program: A representation of an algorithm Programming: The process of developing a program Software: Programs and algorithms
0-1 0-2 Terminology Algorithm: A set of steps that defines how a task is performed Program: A representation of an algorithm Programming: The process of developing a program Software: Programs and algorithms
Engineering Problem Solving with C++, Etter/Ingber
 Engineering Problem Solving with C++, Etter/Ingber Chapter 1 1 Introduction to Computing and Engineering Problem Solving Historical Perspective Recent Engineering Achievements Computing Systems Data Representation
Engineering Problem Solving with C++, Etter/Ingber Chapter 1 1 Introduction to Computing and Engineering Problem Solving Historical Perspective Recent Engineering Achievements Computing Systems Data Representation
CSC101 Furman University Professor Batchelor
 CSC101 Furman University Professor Batchelor The First Mechanical Calculator Blaise Pascal The Difference Engine Charles Babbage While Tomas of Colmar was developing the first successful commercial
CSC101 Furman University Professor Batchelor The First Mechanical Calculator Blaise Pascal The Difference Engine Charles Babbage While Tomas of Colmar was developing the first successful commercial
Overview of a computer
 Overview of a computer One marks 1. What is von Neumann concept also called as? Stored memory or stored program concept. 2. Who is the father of computer Charles Babbage 3. What is a computer? It is an
Overview of a computer One marks 1. What is von Neumann concept also called as? Stored memory or stored program concept. 2. Who is the father of computer Charles Babbage 3. What is a computer? It is an
Communication Fundamentals in Computer Networks
 Lecture 11 Communication Fundamentals in Computer Networks M. Adnan Quaium Assistant Professor Department of Electrical and Electronic Engineering Ahsanullah University of Science and Technology Room 4A07
Lecture 11 Communication Fundamentals in Computer Networks M. Adnan Quaium Assistant Professor Department of Electrical and Electronic Engineering Ahsanullah University of Science and Technology Room 4A07
CCNA Exam File with Answers. Note: Underlines options are correct answers.
 CCNA Exam File with Answers. Note: Underlines options are correct answers. 1. Which of the following are ways to provide login access to a router? (choose all that apply) A. HTTP B. Aux Port /TELNET C.
CCNA Exam File with Answers. Note: Underlines options are correct answers. 1. Which of the following are ways to provide login access to a router? (choose all that apply) A. HTTP B. Aux Port /TELNET C.
Lecture (02) The TCP/IP Networking Model
 Agenda ١ Lecture (02) The TCP/IP Networking Model Dr. Ahmed M. ElShafee Introduction to networking architecture Historical background The TCP/IP Protocol Architecture The TCP/IP Application Layer The TCP/IP
Agenda ١ Lecture (02) The TCP/IP Networking Model Dr. Ahmed M. ElShafee Introduction to networking architecture Historical background The TCP/IP Protocol Architecture The TCP/IP Application Layer The TCP/IP
ZENworks for Desktops Preboot Services
 3.2 Novell ZENworks for Desktops Preboot Services DEPLOYMENT www.novell.com Legal Notices Novell, Inc. makes no representations or warranties with respect to the contents or use of this documentation,
3.2 Novell ZENworks for Desktops Preboot Services DEPLOYMENT www.novell.com Legal Notices Novell, Inc. makes no representations or warranties with respect to the contents or use of this documentation,
Network Fundamentals Chapter 2 Modified by Tony Chen 05/20/2008
 Communicating Over the Network Network Fundamentals Chapter 2 Modified by Tony Chen 05/20/2008 ITE I Chapter 6 2006 Cisco Systems, Inc. All rights reserved. Cisco Public 1 Objectives Drippy Sweet Pancakes
Communicating Over the Network Network Fundamentals Chapter 2 Modified by Tony Chen 05/20/2008 ITE I Chapter 6 2006 Cisco Systems, Inc. All rights reserved. Cisco Public 1 Objectives Drippy Sweet Pancakes
Princess Nora Bint Abdulrahman University College of computer and information sciences Networks department Networks Security (NET 536)
 Princess Nora Bint Abdulrahman University College of computer and information sciences Networks department Networks Security (NET 536) Prepared by Dr. Samia Chelloug E-mail: samia_chelloug@yahoo.fr Content
Princess Nora Bint Abdulrahman University College of computer and information sciences Networks department Networks Security (NET 536) Prepared by Dr. Samia Chelloug E-mail: samia_chelloug@yahoo.fr Content
MTA_98-366_Vindicator930
 MTA_98-366_Vindicator930 Number: 98-366 Passing Score: 700 Time Limit: 45 min File Version: 1.0 http://www.gratisexam.com/ Microsoft Technology Associate Networking Fundamentals MTA 98-366 Exam A QUESTION
MTA_98-366_Vindicator930 Number: 98-366 Passing Score: 700 Time Limit: 45 min File Version: 1.0 http://www.gratisexam.com/ Microsoft Technology Associate Networking Fundamentals MTA 98-366 Exam A QUESTION
The OSI Model. Level 3 Unit 9 Computer Networks
 The OSI Model OSI Model Consider the network models we have already covered Whenever data is transferred from PC to PC or PC to Server it will travel through the Layers of the OSI Model OSI Model OSI Model
The OSI Model OSI Model Consider the network models we have already covered Whenever data is transferred from PC to PC or PC to Server it will travel through the Layers of the OSI Model OSI Model OSI Model
Chapter 1: An Introduction to Computer Science. Invitation to Computer Science, C++ Version, 6-th Edition
 Chapter 1: An Introduction to Computer Science Invitation to Computer Science, C++ Version, 6-th Edition Objectives In this chapter, you will learn about The definition of computer science Algorithms A
Chapter 1: An Introduction to Computer Science Invitation to Computer Science, C++ Version, 6-th Edition Objectives In this chapter, you will learn about The definition of computer science Algorithms A
products. OSI is an ISO Standard: OSI was officially adopted as an international standard by the International Organisation of Standards (ISO).
 CBCN4103 Open Systems Interconnection (OSI) is a standard d description or "reference model" for how messages should be transmitted between any two points in a telecommunication network. Its purpose is
CBCN4103 Open Systems Interconnection (OSI) is a standard d description or "reference model" for how messages should be transmitted between any two points in a telecommunication network. Its purpose is
Network Architecture
 Unit 7 Network Architecture Acknowledgments: These slides were originally developed by Prof. Jean Walrand for EE122. The past and current EE122 instructors including Kevin Fall, Abhay Parekh, Shyam Parekh,
Unit 7 Network Architecture Acknowledgments: These slides were originally developed by Prof. Jean Walrand for EE122. The past and current EE122 instructors including Kevin Fall, Abhay Parekh, Shyam Parekh,
Chapter 9. Ethernet. Part II
 Chapter 9 Ethernet Part II CCNA1-1 Chapter 9-2 Note for Instructors These presentations are the result of a collaboration among the instructors at St. Clair College in Windsor, Ontario. Thanks must go
Chapter 9 Ethernet Part II CCNA1-1 Chapter 9-2 Note for Instructors These presentations are the result of a collaboration among the instructors at St. Clair College in Windsor, Ontario. Thanks must go
Introduction to the ICA OS/2 Client
 C H A P T E R 2 Introduction to the ICA OS/2 Client Overview The ICA OS/2 Client lets you access a Citrix WinFrame or MetaFrame server from a client running IBM OS/2 Warp. When connected to a Citrix server,
C H A P T E R 2 Introduction to the ICA OS/2 Client Overview The ICA OS/2 Client lets you access a Citrix WinFrame or MetaFrame server from a client running IBM OS/2 Warp. When connected to a Citrix server,
E&CE 358: Tutorial 1. Instructor: Sherman (Xuemin) Shen TA: Miao Wang
 E&CE 358: Tutorial 1 Instructor: Sherman (Xuemin) Shen TA: Miao Wang Email: m59wang@uwaterloo.ca 1 About Tutorials TA: Miao Wang Office: EIT 3133; Tutorials: Th 4:30 5:20 pm Topics Supplementary knowledge
E&CE 358: Tutorial 1 Instructor: Sherman (Xuemin) Shen TA: Miao Wang Email: m59wang@uwaterloo.ca 1 About Tutorials TA: Miao Wang Office: EIT 3133; Tutorials: Th 4:30 5:20 pm Topics Supplementary knowledge
Lecture (02, 03) Networking Model (TCP/IP) Networking Standard (OSI)
 Lecture (02, 03) Networking Model (TCP/IP) Networking Standard (OSI) By: Dr. Ahmed ElShafee ١ Dr. Ahmed ElShafee, ACU : Fall 2014, Computer Networks II Agenda Introduction to networking architecture Historical
Lecture (02, 03) Networking Model (TCP/IP) Networking Standard (OSI) By: Dr. Ahmed ElShafee ١ Dr. Ahmed ElShafee, ACU : Fall 2014, Computer Networks II Agenda Introduction to networking architecture Historical
IT 341: Introduction to System Administration. Notes for Project #8: Backing Up Files with rsync
 IT 341: Introduction to System Administration Notes for Project #8: Backing Up Files with rsync These notes explain some of the concepts you will encounter in Project #08: Backing Up Files with rsync Topics
IT 341: Introduction to System Administration Notes for Project #8: Backing Up Files with rsync These notes explain some of the concepts you will encounter in Project #08: Backing Up Files with rsync Topics
This course prepares candidates for the CompTIA Network+ examination (2018 Objectives) N
 CompTIA Network+ (Exam N10-007) Course Description: CompTIA Network+ is the first certification IT professionals specializing in network administration and support should earn. Network+ is aimed at IT
CompTIA Network+ (Exam N10-007) Course Description: CompTIA Network+ is the first certification IT professionals specializing in network administration and support should earn. Network+ is aimed at IT
Chapter 0: Introduction. Copyright 2015 Pearson Education, Inc.
 Chapter 0: Introduction Copyright 2015 Pearson Education, Inc. Essentials for the class Homepage http://mbm.konkuk.ac.kr/classes/ Textbook Computer Science An Overview 12 th Ed. By J. Glenn Brookshear
Chapter 0: Introduction Copyright 2015 Pearson Education, Inc. Essentials for the class Homepage http://mbm.konkuk.ac.kr/classes/ Textbook Computer Science An Overview 12 th Ed. By J. Glenn Brookshear
AN INTRODUCTION TO ARP SPOOFING
 AN INTRODUCTION TO ARP SPOOFING April, 2001 Sean Whalen Sophie Engle Dominic Romeo GENERAL INFORMATION Introduction to ARP Spoofing (April 2001) Current Revision: 1.8 Available: http://chocobospore.org
AN INTRODUCTION TO ARP SPOOFING April, 2001 Sean Whalen Sophie Engle Dominic Romeo GENERAL INFORMATION Introduction to ARP Spoofing (April 2001) Current Revision: 1.8 Available: http://chocobospore.org
Lecture (02) The TCP/IP Networking Model
 Lecture (02) The TCP/IP Networking Model Dr. Ahmed M. ElShafee ١ Agenda Introduction to networking architecture Historical background The TCP/IP Protocol Architecture The TCP/IP Application Layer The TCP/IP
Lecture (02) The TCP/IP Networking Model Dr. Ahmed M. ElShafee ١ Agenda Introduction to networking architecture Historical background The TCP/IP Protocol Architecture The TCP/IP Application Layer The TCP/IP
Introduction to Computer Science. What is Computer Science?
 Introduction to Computer Science CS A101 What is Computer Science? First, some misconceptions. Misconception 1: I can put together my own PC, am good with Windows, and can surf the net with ease, so I
Introduction to Computer Science CS A101 What is Computer Science? First, some misconceptions. Misconception 1: I can put together my own PC, am good with Windows, and can surf the net with ease, so I
Homework 4 assignment for ECE374 Posted: 04/06/15 Due: 04/13/15
 ECE374: Homework 4 1 Homework 4 assignment for ECE374 Posted: 04/06/15 Due: 04/13/15 Note: In all written assignments, please show as much of your work as you can. Even if you get a wrong answer, you can
ECE374: Homework 4 1 Homework 4 assignment for ECE374 Posted: 04/06/15 Due: 04/13/15 Note: In all written assignments, please show as much of your work as you can. Even if you get a wrong answer, you can
Computer Networks รศ.ดร.อน นต ผลเพ ม. Assoc. Prof. Anan Phonphoem, Ph.D. Kasetsart University, Bangkok, Thailand
 Jan May 2018 Computer Networks รศ.ดร.อน นต ผลเพ ม Assoc. Prof. Anan Phonphoem, Ph.D. anan.p@ku.ac.th http://www.cpe.ku.ac.th/~anan Computer Engineering Department Kasetsart University, Bangkok, Thailand
Jan May 2018 Computer Networks รศ.ดร.อน นต ผลเพ ม Assoc. Prof. Anan Phonphoem, Ph.D. anan.p@ku.ac.th http://www.cpe.ku.ac.th/~anan Computer Engineering Department Kasetsart University, Bangkok, Thailand
Outline : Wireless Networks Lecture 10: Management. Management and Control Services : Infrastructure Reminder.
 Outline 18-759: Wireless Networks Lecture 10: 802.11 Management Peter Steenkiste Departments of Computer Science and Electrical and Computer Engineering Spring Semester 2016 http://www.cs.cmu.edu/~prs/wirelesss16/
Outline 18-759: Wireless Networks Lecture 10: 802.11 Management Peter Steenkiste Departments of Computer Science and Electrical and Computer Engineering Spring Semester 2016 http://www.cs.cmu.edu/~prs/wirelesss16/
OSI ISO, OSI Reference Model
 Introduction OSI (Open Systems Interconnection) based on a proposal developed by International Standards Organisation (ISO) in 1984. Known as ISO, OSI Reference Model as it deals with connecting open systems.
Introduction OSI (Open Systems Interconnection) based on a proposal developed by International Standards Organisation (ISO) in 1984. Known as ISO, OSI Reference Model as it deals with connecting open systems.
Vendor: HP. Exam Code: HP2-Z32. Exam Name: Implementing HP MSM Wireless Networks. Version: Demo
 Vendor: HP Exam Code: HP2-Z32 Exam Name: Implementing HP MSM Wireless Networks Version: Demo QUESTION 1 A network administrator deploys several HP MSM APs and an HP MSM Controller. The APs discover the
Vendor: HP Exam Code: HP2-Z32 Exam Name: Implementing HP MSM Wireless Networks Version: Demo QUESTION 1 A network administrator deploys several HP MSM APs and an HP MSM Controller. The APs discover the
