Open WLANs the early results of WarDriving. Peter Shipley
|
|
|
- Dominic Richardson
- 5 years ago
- Views:
Transcription
1 Open WLANs the early results of WarDriving Peter Shipley
2 The Project The purpose of my project is to raise the awareness of the security ramifications arising from the use of wireless Lans (WLAN) in the home and office community. Presented here are the early results of a 18 month effort that started in fall of 2000.
3 Network Security and Wireless Lans The convenience and low cost of WLANs has resulted in their deployment at a feverish rate. This is very similar to the Web race a several years ago. Sadly this deployment has brought security back ten years.
4 Hardware low end Laptop with FreeBSD stable or Windows 98 External Antenna (>5db) GPS (Garmin emap) Lucent /Aironet (Wi-Fi) card
5 Software wi-scan perl script for FreeBSD Netstumbler a Windows App. dstumbler A FreeBSD App. (beta) The native drivers for cards can also be used although the operation will not be as automated.
6 Detection Methods Currently the WLANs are being detected with a feature called broadcast SSID or Null SSID. The Lucent card supports this feature that when you to set your SSID to (null) or ANY the card will detects a AP s beacon and automatically associate with it.
7 Detection Methods Currently I run a script that resets then polls the card every three to five seconds. When a new WLAN is detected the script notes the SSID, Mac address, signal strength, channel, location (via. GPS) and security configuration.
8 Detection Methods Currently we can drive at speeds of up to fifty-five miles a hour and successfully locate and identify wireless networks.
9 Long Distance? Some security officers feel that if AP is distanced from the street or on a high floor of a building they will be safe from network trespassers. Experiments show that we are able to successfully make a network connection twenty-five miles away from hilltops and high-rise buildings.
10 The view from a hilltop in Berkeley.
11 Hardware Connecting to WLANs networks from across the bay. 24db dish connecting to a network on the horizon!
12 Hardware 15 db Yaggi Laptop Portable power Amp Wyatt
13 Other Methods Other methods include sniffing frame this will all for more efferent and faster detection including more information about the Lan. Sniffing can be done with most WLAN cards and the right software.
14 Detection Methods Anyone can do this with a Windows based laptop and Wi-Fi card.
15 Detection Methods Run the Client Manager software and set your SSID to ANY or (null). Next from the Advanced menu of Client Manager and select Site Monitor a window should open listing all the local WLANs that are available from where you are standing.
16 Six networks detected from a single street corner in downtown San Francisco.
17 Detection Methods The previous slide was taken from a street corner in downtown San Francisco. Note that you have your choice of six networks open for access!
18 Statistics We are still in the process in distilling the data Currently we have located over 9000 APs. 60 % of APs are run in their default configuration. Majority are connected to a internal backbone network (not a DMZ).
19 Statistics A majority of these (85% or more) do not utilize WEP. Of those running WEP, near half utilize a default WEP/encryption key (7%).
20 Statistics Top SSIDs: 13% tsunami 11% AirWave 10% WaveLAN Network 8% WLAN 5% linksys 2% default 2% TEKLOGIX
21 Statistics Based on SSIDs and IP address it appears that over 60% of AP are running with a default configuration.
22 Risks Not just personal and corporate LANs are going wireless: Banks Hospitals Legal firms Police Stations/Jails City hall/municipal
23 Risks This places people personal information at risk.
24 Home Networks The risks to home users are greater then simple bandwidth theft. Violations of Term of Use: SPAMing Hacking Anonymous threats Violations can result in loss/disconnection of service
25 Corporate Networks Failure to protect your network can result in costly headaches SPAMing Hacking providing a starting point Unrestricted internal access. Theft of corporate information Lawsuits Failing to protect stockholders interests
26 What is Free There are are growing number of free networks in parks, coffee shops and libraries. How can you tell if a network is free?
27 Accidental Trespassing If you are at a coffee shop that offers free wireless internet access it is possible for your client to drift and associate with a corporate LAN. Making *you* unknowingly guilty of cyber trespassing.
28 Accidental Trespassing There are already documented cases where to neighboring businesses with wireless had employees unknowingly using each others networks. What is these companies were unfriendly competitors?
29 What can be done? Place APs in a DMZ Place Access Points on a dedicated subnet. Block unauthorized internal and external access. WEP Stops accidental trespassing. Some cards will not associate with out the correct key.
30 What can be done? IPSec WEP will not protect your data. Require clients to authenticate with the DMZ firewall/router. Arpwatch Discovers new MAC addresses on your network x New protocol, not well supported / tested.
31 What can be done? Locking your AP to known MAC addresses This only slows the attacker (a few seconds) Stop accidental trespassing Even with WEP the MAC address can still unencrypted. Turn off broadcast SSID This will stop you network from being discovered with simple probes. Your network will still be visible to sniffers and protocol analyzers.
32 Credit due Matt Peterson -Hardware questions Aaron Peterson (no relation) - Data processing scripts Cal -Linux support Wyatt -Misc. hardware fabrication Bay Area Wireless Users Group DoC: Dis Org Crew
33 Maps Here are some maps of the data we have collected on the open networks.
34 Downtown San Francisco
35 Downtown San Francisco
36 San Francisco & East Bay
37 Sunnyvale & Mnt. View
38 References Bay Area Wireless Users Group Dis.Org Crew info files NetStumbler.com: wireless news and references IEEE : standards Arrl: antenna design info.
39 Peter Shipley
Wireless Attacks and Countermeasures
 Wireless Attacks and Countermeasures Wireless Network Technology Wireless network refers to any type of computer network which is wireless, and is commonly associated with a network whose interconnections
Wireless Attacks and Countermeasures Wireless Network Technology Wireless network refers to any type of computer network which is wireless, and is commonly associated with a network whose interconnections
Lure10: Exploiting Windows Automatic Wireless Association Algorithm
 Lure10: Exploiting Windows Automatic Wireless Association Algorithm HITBSecConf2017, Amsterdam GEORGE CHATZISOFRONIOU (@_sophron) sophron@census-labs.com www.census-labs.com > Wi-Fi Automatic Association
Lure10: Exploiting Windows Automatic Wireless Association Algorithm HITBSecConf2017, Amsterdam GEORGE CHATZISOFRONIOU (@_sophron) sophron@census-labs.com www.census-labs.com > Wi-Fi Automatic Association
Wireless LAN, WLAN Security, and VPN
 Wireless LAN, WLAN Security, and VPN 麟瑞科技台南辦事處技術經理張晃崚 WLAN & VPN FAQ What is WLAN?802.11a?802.11b?802.11g? Which standard (product) should we use? How to deploy WLAN? How to block intruders? How to authenticate
Wireless LAN, WLAN Security, and VPN 麟瑞科技台南辦事處技術經理張晃崚 WLAN & VPN FAQ What is WLAN?802.11a?802.11b?802.11g? Which standard (product) should we use? How to deploy WLAN? How to block intruders? How to authenticate
Risks & Rewards of WiFi and WiMax
 Risks & Rewards of WiFi and WiMax BITS Wireless Security Forum Joshua Wright, Senior Security Researcher Introduction IEEE 802.11 technology and vulnerabilities Examining public WLAN attacks and the impact
Risks & Rewards of WiFi and WiMax BITS Wireless Security Forum Joshua Wright, Senior Security Researcher Introduction IEEE 802.11 technology and vulnerabilities Examining public WLAN attacks and the impact
What is a Wireless LAN? The wireless telegraph is not difficult to understand. The ordinary telegraph is like a very long cat. You pull the tail in Ne
 Introduction to Wireless Networking and Security Chino Information Technology Center Steve Siedschlag, Associate Professor What is a Wireless LAN? The wireless telegraph is not difficult to understand.
Introduction to Wireless Networking and Security Chino Information Technology Center Steve Siedschlag, Associate Professor What is a Wireless LAN? The wireless telegraph is not difficult to understand.
Wednesday, May 16, 2018
 Wednesday, May 16, 2018 8:00 AM - 5:00 PM Wi Fi/WLAN Fundamentals Training by Tessco; Day Two of a Two Day Training. (Attendees must bring laptop computers for this training. Attendees should bring available
Wednesday, May 16, 2018 8:00 AM - 5:00 PM Wi Fi/WLAN Fundamentals Training by Tessco; Day Two of a Two Day Training. (Attendees must bring laptop computers for this training. Attendees should bring available
Digital Entertainment. Networking Made Easy
 Digital Entertainment 2003 by TiVo Inc. Reproduction in whole or in part without written permission is prohibited. All rights reserved. Printed in the USA. TiVo, TiVo Central, and TiVolution are registered
Digital Entertainment 2003 by TiVo Inc. Reproduction in whole or in part without written permission is prohibited. All rights reserved. Printed in the USA. TiVo, TiVo Central, and TiVolution are registered
WPA SECURITY (Wi-Fi Protected Access) Presentation. Douglas Cheathem (csc Spring 2007)
 WPA SECURITY (Wi-Fi Protected Access) Presentation By Douglas Cheathem (csc 650.01 Spring 2007) OUTLINE Introduction Security Risk Vulnerabilities Prevention Conclusion Live Demo Q & A INTRODUCTION! WPA
WPA SECURITY (Wi-Fi Protected Access) Presentation By Douglas Cheathem (csc 650.01 Spring 2007) OUTLINE Introduction Security Risk Vulnerabilities Prevention Conclusion Live Demo Q & A INTRODUCTION! WPA
ScreenBeam Wireless display over LAN
 ScreenBeam Wireless display over LAN Deployment Guide Version: Draft v4 Table of Contents Part I Introduction... 3 1.1 Features... 3 1.2 System Requirements... 3 1.3 Related Documents... 4 Part II Setting
ScreenBeam Wireless display over LAN Deployment Guide Version: Draft v4 Table of Contents Part I Introduction... 3 1.1 Features... 3 1.2 System Requirements... 3 1.3 Related Documents... 4 Part II Setting
Wireless LAN Security (RM12/2002)
 Information Technology in Education Project Reference Materials Wireless LAN Security (RM12/2002) Infrastructure Division Education Department The Government of HKSAR www.ited.ed.gov.hk December 2002 For
Information Technology in Education Project Reference Materials Wireless LAN Security (RM12/2002) Infrastructure Division Education Department The Government of HKSAR www.ited.ed.gov.hk December 2002 For
Wi-Net Window and Rogue Access Points
 Wi-Net Window and Rogue Access Points The Wi-Net Window (WP150) has several features that make it ideal for detecting and locating rogue access points: A rogue access point is a wireless access point that
Wi-Net Window and Rogue Access Points The Wi-Net Window (WP150) has several features that make it ideal for detecting and locating rogue access points: A rogue access point is a wireless access point that
PRODUCT GUIDE Wireless Intrusion Prevention Systems
 PRODUCT GUIDE Wireless Intrusion Prevention Systems The Need for Wireless INTRUSION PREVENTION SYSTEMS A Wireless Intrusion Prevention System (WIPS) is designed to address two classes of challenges facing
PRODUCT GUIDE Wireless Intrusion Prevention Systems The Need for Wireless INTRUSION PREVENTION SYSTEMS A Wireless Intrusion Prevention System (WIPS) is designed to address two classes of challenges facing
Wireless Network Defensive Strategies
 Wireless Network Defensive Strategies Jay A. Crossler ECE 646 Analytical Project 12 Dec 2003 Topics Wireless Security Intrusion Experiment Initial Findings Attempted Attacks Results WEP Vulnerabilities
Wireless Network Defensive Strategies Jay A. Crossler ECE 646 Analytical Project 12 Dec 2003 Topics Wireless Security Intrusion Experiment Initial Findings Attempted Attacks Results WEP Vulnerabilities
Wireless Networking. Dennis Rex SCALE 3X
 Wireless Networking For Beginners Dennis Rex SCALE 3X - 2005 Agenda Wireless Choices 802.11A, B, G Devices - USB, PCI, PCMCIA, bridges Wireless chipsets - the good, the bad, the ugly Finding and installing
Wireless Networking For Beginners Dennis Rex SCALE 3X - 2005 Agenda Wireless Choices 802.11A, B, G Devices - USB, PCI, PCMCIA, bridges Wireless chipsets - the good, the bad, the ugly Finding and installing
Outline : Wireless Networks Lecture 10: Management. Management and Control Services : Infrastructure Reminder.
 Outline 18-759: Wireless Networks Lecture 10: 802.11 Management Peter Steenkiste Departments of Computer Science and Electrical and Computer Engineering Spring Semester 2016 http://www.cs.cmu.edu/~prs/wirelesss16/
Outline 18-759: Wireless Networks Lecture 10: 802.11 Management Peter Steenkiste Departments of Computer Science and Electrical and Computer Engineering Spring Semester 2016 http://www.cs.cmu.edu/~prs/wirelesss16/
Karthik Pinnamaneni COEN 150 Wireless Network Security Dr. Joan Holliday 5/21/03
 Karthik Pinnamaneni COEN 150 Wireless Network Security Dr. Joan Holliday 5/21/03 Introduction Although a variety of wireless network technologies have or will soon reach the general business market, wireless
Karthik Pinnamaneni COEN 150 Wireless Network Security Dr. Joan Holliday 5/21/03 Introduction Although a variety of wireless network technologies have or will soon reach the general business market, wireless
Chapter 11: Networks
 Chapter 11: Networks Devices in a Small Network Small Network A small network can comprise a few users, one router, one switch. A Typical Small Network Topology looks like this: Device Selection Factors
Chapter 11: Networks Devices in a Small Network Small Network A small network can comprise a few users, one router, one switch. A Typical Small Network Topology looks like this: Device Selection Factors
Complying with RBI Guidelines for Wi-Fi Vulnerabilities
 A Whitepaper by AirTight Networks, Inc. 339 N. Bernardo Avenue, Mountain View, CA 94043 www.airtightnetworks.com 2013 AirTight Networks, Inc. All rights reserved. Reserve Bank of India (RBI) guidelines
A Whitepaper by AirTight Networks, Inc. 339 N. Bernardo Avenue, Mountain View, CA 94043 www.airtightnetworks.com 2013 AirTight Networks, Inc. All rights reserved. Reserve Bank of India (RBI) guidelines
What is Eavedropping?
 WLAN Security What is Eavedropping? War Driving War Driving refers to someone driving around with a laptop and an 802.11 client card looking for an 802.11 system to exploit. War Walking Someone walks
WLAN Security What is Eavedropping? War Driving War Driving refers to someone driving around with a laptop and an 802.11 client card looking for an 802.11 system to exploit. War Walking Someone walks
Mobile Security Fall 2013
 Mobile Security 14-829 Fall 2013 Patrick Tague Class #6 More WiFi Security & Privacy Issues WiFi Security Issues A Scenario Internet Open AP SSID Network X Open OpenAP AP SSID Attacker Network X LaptopLaptop
Mobile Security 14-829 Fall 2013 Patrick Tague Class #6 More WiFi Security & Privacy Issues WiFi Security Issues A Scenario Internet Open AP SSID Network X Open OpenAP AP SSID Attacker Network X LaptopLaptop
Wireless Security Protocol Analysis and Design. Artoré & Bizollon : Wireless Security Protocol Analysis and Design
 Protocol Analysis and Design 1 Networks 1. WIRELESS NETWORKS 2 Networks 1. WIRELESS NETWORKS 1.1 WiFi 802.11 3 Networks OSI Structure 4 Networks Infrastructure Networks BSS : Basic Set Service ESS : Extended
Protocol Analysis and Design 1 Networks 1. WIRELESS NETWORKS 2 Networks 1. WIRELESS NETWORKS 1.1 WiFi 802.11 3 Networks OSI Structure 4 Networks Infrastructure Networks BSS : Basic Set Service ESS : Extended
Learn How to Configure EnGenius Wi-Fi Products for Popular Applications
 Learn How to Configure EnGenius Wi-Fi Products for Popular Applications Operation Modes Access Point (AP) / WDS AP Client Bridge (CB) Repeater WDS Bridge Client Router AP Router Access Point An access
Learn How to Configure EnGenius Wi-Fi Products for Popular Applications Operation Modes Access Point (AP) / WDS AP Client Bridge (CB) Repeater WDS Bridge Client Router AP Router Access Point An access
Chapter 16: Advanced Security
 : Advanced Security IT Essentials: PC Hardware and Software v4.0 1 Purpose of this Presentation To provide to instructors an overview of : List of chapter objectives Overview of the chapter contents, including
: Advanced Security IT Essentials: PC Hardware and Software v4.0 1 Purpose of this Presentation To provide to instructors an overview of : List of chapter objectives Overview of the chapter contents, including
Exam Questions CWSP-205
 Exam Questions CWSP-205 Certified Wireless Security Professional https://www.2passeasy.com/dumps/cwsp-205/ 1.. What is one advantage of using EAP-TTLS instead of EAP-TLS as an authentication mechanism
Exam Questions CWSP-205 Certified Wireless Security Professional https://www.2passeasy.com/dumps/cwsp-205/ 1.. What is one advantage of using EAP-TTLS instead of EAP-TLS as an authentication mechanism
Install Your Own Wireless Network
 Brigham Young University BYU ScholarsArchive All Faculty Publications 2004-11-01 Install Your Own Wireless Network William G. Heninger heninger@byu.edu Craig J. Lindstrom See next page for additional authors
Brigham Young University BYU ScholarsArchive All Faculty Publications 2004-11-01 Install Your Own Wireless Network William G. Heninger heninger@byu.edu Craig J. Lindstrom See next page for additional authors
Table of Contents 1 WLAN Service Configuration 1-1
 Table of Contents 1 WLAN Service Configuration 1-1 WLAN Service Overview 1-1 Terminology 1-1 Wireless Client Access 1-2 802.11 Overview 1-4 WLAN Topologies 1-5 Single BSS 1-5 Multi-ESS 1-5 Single ESS Multiple
Table of Contents 1 WLAN Service Configuration 1-1 WLAN Service Overview 1-1 Terminology 1-1 Wireless Client Access 1-2 802.11 Overview 1-4 WLAN Topologies 1-5 Single BSS 1-5 Multi-ESS 1-5 Single ESS Multiple
Wireless 11n Smart Repeater AP (1T1R)
 (1T1R) 2014 Table of Contents 1. Introduction...3 1.1 Package contents... 3 1.2 Product Features... 3 1.3 Front Panel Description... 4 1.4 Rear Panel Description... 5 2. Installation...6 2.1 Hardware Installation...
(1T1R) 2014 Table of Contents 1. Introduction...3 1.1 Package contents... 3 1.2 Product Features... 3 1.3 Front Panel Description... 4 1.4 Rear Panel Description... 5 2. Installation...6 2.1 Hardware Installation...
D-Link AirPlus G DWL-G700AP
 TM D-Link AirPlus G DWL-G700AP 2.4GHz Wireless Access Point Manual Building Networks for People Contents Package Contents...3 Introduction...4 Wireless Basics...6 Getting Started...8 Using the Configuration
TM D-Link AirPlus G DWL-G700AP 2.4GHz Wireless Access Point Manual Building Networks for People Contents Package Contents...3 Introduction...4 Wireless Basics...6 Getting Started...8 Using the Configuration
GCIA. GIAC Certified Intrusion Analyst.
 GIAC GCIA GIAC Certified Intrusion Analyst TYPE: DEMO http://www.examskey.com/gcia.html Examskey GIAC GCIA exam demo product is here for you to test the quality of the product. This GIAC GCIA demo also
GIAC GCIA GIAC Certified Intrusion Analyst TYPE: DEMO http://www.examskey.com/gcia.html Examskey GIAC GCIA exam demo product is here for you to test the quality of the product. This GIAC GCIA demo also
SMART CAMPUS, BUILDING AND VENUES
 SMART CAMPUS, BUILDING AND VENUES Greg Deffenbaugh, Corporate Solutions Technologist SDS & Hospitality SDN Solutions and Strategy, Avaya @gregdeff gregdeff 1 Thank you Sponsors! Global Sponsors Gold Sponsors
SMART CAMPUS, BUILDING AND VENUES Greg Deffenbaugh, Corporate Solutions Technologist SDS & Hospitality SDN Solutions and Strategy, Avaya @gregdeff gregdeff 1 Thank you Sponsors! Global Sponsors Gold Sponsors
Chapter 11: It s a Network. Introduction to Networking
 Chapter 11: It s a Network Introduction to Networking Small Network Topologies Typical Small Network Topology IT Essentials v5.0 2 Device Selection for a Small Network Factors to be considered when selecting
Chapter 11: It s a Network Introduction to Networking Small Network Topologies Typical Small Network Topology IT Essentials v5.0 2 Device Selection for a Small Network Factors to be considered when selecting
Secure Mobility Challenges. Fat APs, Decentralized Risk. Physical Access. Business Requirements
 Unified Wireless Switching Enabling a Truly Converged Network White Paper Abstract As businesses scale, traditional wireless network deployments become more complex, more costly and less secure. Users
Unified Wireless Switching Enabling a Truly Converged Network White Paper Abstract As businesses scale, traditional wireless network deployments become more complex, more costly and less secure. Users
300Mbps Long Range Wireless N Ceiling Mount AP Model : N10+
 SKT Standard UI Flipbook v0.8 CREATIVE AGENCY VINYL Model : N10+ Web site www.totolink.net Address BLDG A1&A2, Lantian Technology Park, Xinyu Rd, Xinqiao Henggang Block, Shajing St, Baoan District, Shenzhen
SKT Standard UI Flipbook v0.8 CREATIVE AGENCY VINYL Model : N10+ Web site www.totolink.net Address BLDG A1&A2, Lantian Technology Park, Xinyu Rd, Xinqiao Henggang Block, Shajing St, Baoan District, Shenzhen
How Insecure is Wireless LAN?
 Page 1 of 7 How Insecure is Wireless LAN? Abstract Wireless LAN has gained popularity in the last few years due to its enormous benefits such as scalability, mobile access of the network, and reduced cost
Page 1 of 7 How Insecure is Wireless LAN? Abstract Wireless LAN has gained popularity in the last few years due to its enormous benefits such as scalability, mobile access of the network, and reduced cost
Multi-Layered Security Framework for Metro-Scale Wi-Fi Networks
 Multi-Layered Security Framework for Metro-Scale Wi-Fi Networks A Security Whitepaper January, 2004 Photo courtesy of NASA Image exchange. Image use in no way implies endorsement by NASA of any of the
Multi-Layered Security Framework for Metro-Scale Wi-Fi Networks A Security Whitepaper January, 2004 Photo courtesy of NASA Image exchange. Image use in no way implies endorsement by NASA of any of the
Cyber Security Guidelines for Public Wi-Fi Networks
 Cyber Security Guidelines for Public Wi-Fi Networks Version: 1.0 Author: Cyber Security Policy and Standards Document Classification: PUBLIC Published Date: April 2018 Document History: Version Description
Cyber Security Guidelines for Public Wi-Fi Networks Version: 1.0 Author: Cyber Security Policy and Standards Document Classification: PUBLIC Published Date: April 2018 Document History: Version Description
WLAN Security. Dr. Siwaruk Siwamogsatham. ThaiCERT, NECTEC
 WLAN Security Dr. Siwaruk Siwamogsatham ThaiCERT, NECTEC Agenda Wireless Technology Overview IEEE 802.11 WLAN Technology WLAN Security Issues How to secure WLAN? WLAN Security Technologies Wireless Technologies
WLAN Security Dr. Siwaruk Siwamogsatham ThaiCERT, NECTEC Agenda Wireless Technology Overview IEEE 802.11 WLAN Technology WLAN Security Issues How to secure WLAN? WLAN Security Technologies Wireless Technologies
Using GIS in Designing and Deploying Wireless Network in City Plans
 Using GIS in Designing and Deploying Wireless Network in City Plans Iyad Aldasouqi Royal Scientific Society The Middle East Scientific Institute for Security Jordan Walid A. Salameh Princess Sumaya University
Using GIS in Designing and Deploying Wireless Network in City Plans Iyad Aldasouqi Royal Scientific Society The Middle East Scientific Institute for Security Jordan Walid A. Salameh Princess Sumaya University
On completing this chapter, you will be able to Explain the different WLAN configurations Explain how WLANs work Describe the risks of open wireless
 On completing this chapter, you will be able to Explain the different WLAN configurations Explain how WLANs work Describe the risks of open wireless ports Describe SAFE WLAN design techniques C H A P T
On completing this chapter, you will be able to Explain the different WLAN configurations Explain how WLANs work Describe the risks of open wireless ports Describe SAFE WLAN design techniques C H A P T
Fix Home Network. Thousands of satisfied users! Easy steps to setup Wireless router with Cable or DSL internet service provider.
 Fix Home Network Thousands of satisfied users! Easy steps to setup Wireless router with Cable or DSL internet service provider. Copyright, Legal Notice and Disclaimer: This publication is protected under
Fix Home Network Thousands of satisfied users! Easy steps to setup Wireless router with Cable or DSL internet service provider. Copyright, Legal Notice and Disclaimer: This publication is protected under
SECURITY ON PUBLIC WI-FI New Zealand. A guide to help you stay safe online while using public Wi-Fi
 SECURITY ON PUBLIC WI-FI New Zealand A guide to help you stay safe online while using public Wi-Fi WHAT S YOUR WI-FI PASSWORD? Enter password for the COFFEE_TIME Wi-Fi network An all too common question
SECURITY ON PUBLIC WI-FI New Zealand A guide to help you stay safe online while using public Wi-Fi WHAT S YOUR WI-FI PASSWORD? Enter password for the COFFEE_TIME Wi-Fi network An all too common question
Expected Outcomes Able to design the network security for the entire network Able to develop and suggest the security plan and policy
 CHAPTER 9 DEVELOPING NETWORK SECURITY STRATEGIES Expected Outcomes Able to design the network security for the entire network Able to develop and suggest the security plan and policy Network Security Design
CHAPTER 9 DEVELOPING NETWORK SECURITY STRATEGIES Expected Outcomes Able to design the network security for the entire network Able to develop and suggest the security plan and policy Network Security Design
WhatsUp Gold Wireless v16.4
 WhatsUp Gold Wireless v16.4 Contents Welcome to WhatsUp Gold Wireless Wireless Overview... 1 Wireless accessibility... 3 Using WhatsUp Gold Wireless Discovering wireless devices... 4 Modifying wireless
WhatsUp Gold Wireless v16.4 Contents Welcome to WhatsUp Gold Wireless Wireless Overview... 1 Wireless accessibility... 3 Using WhatsUp Gold Wireless Discovering wireless devices... 4 Modifying wireless
Wireless Network Security
 Wireless Network Security Why wireless? Wifi, which is short for wireless fi something, allows your computer to connect to the Internet using magic. -Motel 6 commercial 2 but it comes at a price Wireless
Wireless Network Security Why wireless? Wifi, which is short for wireless fi something, allows your computer to connect to the Internet using magic. -Motel 6 commercial 2 but it comes at a price Wireless
Department of Public Health O F S A N F R A N C I S C O
 PAGE 1 of 7 Category: Information Technology Security and HIPAA DPH Unit of Origin: Department of Public Health Policy Owner: Phillip McDown, CISSP Phone: 255-3577 CISSPCISSP/C Distribution: DPH-wide Other:
PAGE 1 of 7 Category: Information Technology Security and HIPAA DPH Unit of Origin: Department of Public Health Policy Owner: Phillip McDown, CISSP Phone: 255-3577 CISSPCISSP/C Distribution: DPH-wide Other:
Attacking Networks. Joshua Wright LightReading LIVE! October 1, 2003
 Attacking 802.11 Networks Joshua Wright Joshua.Wright@jwu.edu LightReading LIVE! October 1, 2003 Attention The material presented here reflects the personal experience and opinions of the author, and not
Attacking 802.11 Networks Joshua Wright Joshua.Wright@jwu.edu LightReading LIVE! October 1, 2003 Attention The material presented here reflects the personal experience and opinions of the author, and not
Implementing a network operations centre management console: Netmates
 Section 1 Network Systems Engineering Implementing a network operations centre management console: Netmates R.Bali and P.S.Dowland Network Research Group, University of Plymouth, Plymouth, United Kingdom
Section 1 Network Systems Engineering Implementing a network operations centre management console: Netmates R.Bali and P.S.Dowland Network Research Group, University of Plymouth, Plymouth, United Kingdom
DMK 11A & 11A GPS Owners Manual
 DMK 11A & 11A GPS Owners Manual Table of Contents Section I Description of DMK 11A & 11A-GPS 1.1 Introduction 1.2 Background 1.3 Infrastructure Connection 1.4 Components 1.5 Input Protocols 1.6 Configuration
DMK 11A & 11A GPS Owners Manual Table of Contents Section I Description of DMK 11A & 11A-GPS 1.1 Introduction 1.2 Background 1.3 Infrastructure Connection 1.4 Components 1.5 Input Protocols 1.6 Configuration
CYBER ATTACKS EXPLAINED: WIRELESS ATTACKS
 CYBER ATTACKS EXPLAINED: WIRELESS ATTACKS Wireless networks are everywhere, from the home to corporate data centres. They make our lives easier by avoiding bulky cables and related problems. But with these
CYBER ATTACKS EXPLAINED: WIRELESS ATTACKS Wireless networks are everywhere, from the home to corporate data centres. They make our lives easier by avoiding bulky cables and related problems. But with these
WhatsUp Gold v16.0 Wireless User Guide
 WhatsUp Gold v16.0 Wireless User Guide Contents Welcome to WhatsUp Gold Wireless Wireless Overview... 1 Wireless licensing and accessibility... 3 Using WhatsUp Gold Wireless Discovering wireless devices...
WhatsUp Gold v16.0 Wireless User Guide Contents Welcome to WhatsUp Gold Wireless Wireless Overview... 1 Wireless licensing and accessibility... 3 Using WhatsUp Gold Wireless Discovering wireless devices...
WNRT-627. Data Sheet. Europe/ ETSI: 2.412~2.472GHz (13 Channels) Japan/ TELEC: 2.412~2.484GHz (14 Channels) RF Power.
 300Mbps 802.11n Wireless Broadband Router Ultra High Speed 802.11n Wireless The WNRT-627 features latest IEEE 802.11n radio with 2T2R MIMO antenna technology to provide improved wireless speed and coverage
300Mbps 802.11n Wireless Broadband Router Ultra High Speed 802.11n Wireless The WNRT-627 features latest IEEE 802.11n radio with 2T2R MIMO antenna technology to provide improved wireless speed and coverage
WRE6505 v2. User s Guide. Quick Start Guide. Wireless AC750 Range Extender. Default Login Details. Version 1.00 Edition 1, 10/2016
 WRE6505 v2 Wireless AC750 Range Extender Version 1.00 Edition 1, 10/2016 Quick Start Guide User s Guide Default Login Details Web Address http://zyxelsetup http://dhcp-assigned IP www.zyxel.comhttp://192.168.1.2
WRE6505 v2 Wireless AC750 Range Extender Version 1.00 Edition 1, 10/2016 Quick Start Guide User s Guide Default Login Details Web Address http://zyxelsetup http://dhcp-assigned IP www.zyxel.comhttp://192.168.1.2
FAQ on Cisco Aironet Wireless Security
 FAQ on Cisco Aironet Wireless Security Document ID: 68583 Contents Introduction General FAQ Troubleshooting and Design FAQ Related Information Introduction This document provides information on the most
FAQ on Cisco Aironet Wireless Security Document ID: 68583 Contents Introduction General FAQ Troubleshooting and Design FAQ Related Information Introduction This document provides information on the most
PASS4TEST. IT Certification Guaranteed, The Easy Way! We offer free update service for one year
 PASS4TEST IT Certification Guaranteed, The Easy Way! \ http://www.pass4test.com We offer free update service for one year Exam : PW0-070 Title : Certified Wireless Technology Specialist Vendors : CWNP
PASS4TEST IT Certification Guaranteed, The Easy Way! \ http://www.pass4test.com We offer free update service for one year Exam : PW0-070 Title : Certified Wireless Technology Specialist Vendors : CWNP
BeeKeeper Manual Version 1.5
 BeeKeeper Manual Version 1.5 1 Contents Page Yellowjacket Hardware Users Pollenator: Instructions for Operation....... 3 Instructions for Pollenator Hardware Installation..... 4 Instructions for Pollenator
BeeKeeper Manual Version 1.5 1 Contents Page Yellowjacket Hardware Users Pollenator: Instructions for Operation....... 3 Instructions for Pollenator Hardware Installation..... 4 Instructions for Pollenator
NWD2705. User s Guide. Quick Start Guide. Dual-Band Wireless N450 USB Adapter. Version 1.00 Edition 1, 09/2012
 NWD2705 Dual-Band Wireless N450 USB Adapter Version 1.00 Edition 1, 09/2012 Quick Start Guide User s Guide www.zyxel.com Copyright 2012 ZyXEL Communications Corporation IMPORTANT! READ CAREFULLY BEFORE
NWD2705 Dual-Band Wireless N450 USB Adapter Version 1.00 Edition 1, 09/2012 Quick Start Guide User s Guide www.zyxel.com Copyright 2012 ZyXEL Communications Corporation IMPORTANT! READ CAREFULLY BEFORE
D. The bank s web server is using an X.509 certificate that is not signed by a root CA, causing the user ID and password to be sent unencrypted.
 Volume: 119 Questions Question No: 1 John Smith uses a coffee shop's Internet hot-spot (no authentication or encryption) to transfer funds between his checking and savings accounts at his bank's website.
Volume: 119 Questions Question No: 1 John Smith uses a coffee shop's Internet hot-spot (no authentication or encryption) to transfer funds between his checking and savings accounts at his bank's website.
AIRPLAY AND AIRPRINT ON CAMPUS NETWORKS AN ARUBA AIRGROUP SOLUTION GUIDE
 AIRPLAY AND AIRPRINT ON CAMPUS NETWORKS AN ARUBA AIRGROUP SOLUTION GUIDE Table of Contents Warning and Disclaimer... 3 Introduction... 4 What is Zero Configuration Networking (zeroconf)?... 5 WLANs and
AIRPLAY AND AIRPRINT ON CAMPUS NETWORKS AN ARUBA AIRGROUP SOLUTION GUIDE Table of Contents Warning and Disclaimer... 3 Introduction... 4 What is Zero Configuration Networking (zeroconf)?... 5 WLANs and
Securing Wireless Networks by By Joe Klemencic Mon. Apr
 http://www.cymru.com/ Securing Wireless Networks by By Joe Klemencic (faz@home.com) Mon. Apr 30 2001 Many companies make attempts to embrace new technologies, but unfortunately, many of these new technologies
http://www.cymru.com/ Securing Wireless Networks by By Joe Klemencic (faz@home.com) Mon. Apr 30 2001 Many companies make attempts to embrace new technologies, but unfortunately, many of these new technologies
Mohammad Hossein Manshaei 1393
 Mohammad Hossein Manshaei manshaei@gmail.com 1393 Wireless Links, WiFi, Cellular Internet Access, and Mobility Slides derived from those available on the Web site of the book Computer Networking, by Kurose
Mohammad Hossein Manshaei manshaei@gmail.com 1393 Wireless Links, WiFi, Cellular Internet Access, and Mobility Slides derived from those available on the Web site of the book Computer Networking, by Kurose
How to connect to a Wi-Fi or Wireless Network
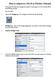 How to connect to a Wi-Fi or Wireless Network This guide will walk you through the steps of connecting to a Wi-Fi network that is broadcasting its name. Start the ipad. 1. Tap on the Settings app. The
How to connect to a Wi-Fi or Wireless Network This guide will walk you through the steps of connecting to a Wi-Fi network that is broadcasting its name. Start the ipad. 1. Tap on the Settings app. The
WRE2206. User s Guide. Quick Start Guide. Wireless N300 Range Extender. Default Details. Version 1.00 Edition 1, 01/2015
 WRE2206 Wireless N300 Range Extender Version 1.00 Edition 1, 01/2015 Quick Start Guide User s Guide Default Details Web Address http://zyxelsetup OR http://192.168.1.2 www.zyxel.com User Name admin Password
WRE2206 Wireless N300 Range Extender Version 1.00 Edition 1, 01/2015 Quick Start Guide User s Guide Default Details Web Address http://zyxelsetup OR http://192.168.1.2 www.zyxel.com User Name admin Password
MESH TECHNOLOGY PRIMER
 MESH TECHNOLOGY PRIMER The Evolution of Wi-Fi: From Hot Spots to Hot Zones to Municipal Networks Wi-Fi technology has experienced unprecedented growth for both consumer and enterprise use in a very short
MESH TECHNOLOGY PRIMER The Evolution of Wi-Fi: From Hot Spots to Hot Zones to Municipal Networks Wi-Fi technology has experienced unprecedented growth for both consumer and enterprise use in a very short
802.11ac Wireless Access Point Model WAC104
 Point Model WAC104 User Manual October 2016 202-11698-01 350 E. Plumeria Drive San Jose, CA 95134 USA Support Thank you for purchasing this NETGEAR product. You can visit www.netgear.com/support to register
Point Model WAC104 User Manual October 2016 202-11698-01 350 E. Plumeria Drive San Jose, CA 95134 USA Support Thank you for purchasing this NETGEAR product. You can visit www.netgear.com/support to register
PCI Compliance. What is it? Who uses it? Why is it important?
 PCI Compliance What is it? Who uses it? Why is it important? Definitions: PCI- Payment Card Industry DSS-Data Security Standard Merchants Anyone who takes a credit card payment 3 rd party processors companies
PCI Compliance What is it? Who uses it? Why is it important? Definitions: PCI- Payment Card Industry DSS-Data Security Standard Merchants Anyone who takes a credit card payment 3 rd party processors companies
A Division of Cisco Systems, Inc. GHz 2, g. Wireless-G. User Guide. Access Point WIRELESS WAP54G (EU/LA/UK) Model No.
 A Division of Cisco Systems, Inc. GHz 2,4 802.11g WIRELESS Wireless-G Access Point User Guide Model No. WAP54G (EU/LA/UK) Copyright and Trademarks Specifications are subject to change without notice. Linksys
A Division of Cisco Systems, Inc. GHz 2,4 802.11g WIRELESS Wireless-G Access Point User Guide Model No. WAP54G (EU/LA/UK) Copyright and Trademarks Specifications are subject to change without notice. Linksys
Networking Basics. Crystal Printer Network Installation Guidelines
 Networking Basics & Crystal Printer Network Installation Guidelines 1. Overview This guide is intended to provide the necessary basic knowledge of wireless networking needed to enable the Crystal printer
Networking Basics & Crystal Printer Network Installation Guidelines 1. Overview This guide is intended to provide the necessary basic knowledge of wireless networking needed to enable the Crystal printer
1. Press "Speed Test" to find out your actual uplink and downlink speed.
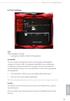 ASRock G10 Gaming Router 6.4 QoS Settings QoS Add Gaming Boost web page. Gaming Boost: Enable or disable the Gaming Boost. Bandwidth The router supports Gaming Boost natively, which identifies and intelligently
ASRock G10 Gaming Router 6.4 QoS Settings QoS Add Gaming Boost web page. Gaming Boost: Enable or disable the Gaming Boost. Bandwidth The router supports Gaming Boost natively, which identifies and intelligently
WLAN Troubleshooting Using AirCheck Wi-Fi Tester
 WLAN Troubleshooting Using AirCheck Wi-Fi Tester AirCheck Troubleshooting Capabilities AirCheck Wi-Fi Tester is a powerful troubleshooting tool that can help you identify and resolve many Wi-Fi related
WLAN Troubleshooting Using AirCheck Wi-Fi Tester AirCheck Troubleshooting Capabilities AirCheck Wi-Fi Tester is a powerful troubleshooting tool that can help you identify and resolve many Wi-Fi related
TestsDumps. Latest Test Dumps for IT Exam Certification
 TestsDumps http://www.testsdumps.com Latest Test Dumps for IT Exam Certification Exam : PW0-200 Title : Certified wireless security professional(cwsp) Vendors : CWNP Version : DEMO Get Latest & Valid PW0-200
TestsDumps http://www.testsdumps.com Latest Test Dumps for IT Exam Certification Exam : PW0-200 Title : Certified wireless security professional(cwsp) Vendors : CWNP Version : DEMO Get Latest & Valid PW0-200
PMS 138 C Moto Black spine width spine width 100% 100%
 Series MOTOROLA and the Stylized M Logo are registered in the US Patent & Trademark Office. All other product or service names are the property of their respective owners. 2009 Motorola, Inc. Table of
Series MOTOROLA and the Stylized M Logo are registered in the US Patent & Trademark Office. All other product or service names are the property of their respective owners. 2009 Motorola, Inc. Table of
How Secure is Wireless?
 How Secure is Wireless? South Carolina Chapter of HIMSS Annual Conference April 24-25, 2003 Richard Gadsden Director of Computer and Network Security Medical University of South Carolina gadsden@musc.edu
How Secure is Wireless? South Carolina Chapter of HIMSS Annual Conference April 24-25, 2003 Richard Gadsden Director of Computer and Network Security Medical University of South Carolina gadsden@musc.edu
Content. Chapter 1 Product Introduction Package Contents Product Features Product Usage... 2
 Content Chapter 1 Product Introduction... 2 1.1 Package Contents... 2 1.2 Product Features... 2 1.3 Product Usage... 2 1.4 Before Installation... 2 1.5 Disable other manufacturers wireless network adapters...
Content Chapter 1 Product Introduction... 2 1.1 Package Contents... 2 1.2 Product Features... 2 1.3 Product Usage... 2 1.4 Before Installation... 2 1.5 Disable other manufacturers wireless network adapters...
Alarms and Events. Using the Alarm Summary CHAPTER
 CHAPTER 16 This chapter describes the type of events and alarms reported, how to view alarms and events by product or entity and severity, and how to view IDS signature attacks. It contains these sections:
CHAPTER 16 This chapter describes the type of events and alarms reported, how to view alarms and events by product or entity and severity, and how to view IDS signature attacks. It contains these sections:
IMW-C910W. User Manuel
 IMW-C910W User Manuel Table of list Chapter 1. Attention... 4 Chapter 2. Introduction & Requirements... 4 Introduction of goods... 4 What is the IMW-C910W?... 4 System Requirements.... 4 Specification...
IMW-C910W User Manuel Table of list Chapter 1. Attention... 4 Chapter 2. Introduction & Requirements... 4 Introduction of goods... 4 What is the IMW-C910W?... 4 System Requirements.... 4 Specification...
Wireless# Guide to Wireless Communications. Objectives
 Wireless# Guide to Wireless Communications Chapter 8 High-Speed WLANs and WLAN Security Objectives Describe how IEEE 802.11a networks function and how they differ from 802.11 networks Outline how 802.11g
Wireless# Guide to Wireless Communications Chapter 8 High-Speed WLANs and WLAN Security Objectives Describe how IEEE 802.11a networks function and how they differ from 802.11 networks Outline how 802.11g
CCNA 3 (v v6.0) Chapter 4 Exam Answers % Full
 CCNA 3 (v5.0.3 + v6.0) Chapter 4 Exam Answers 2017 100% Full ccnav6.com /ccna-3-v5-0-3-v6-0-chapter-4-exam-answers-2017-100-full.html CCNA Exam Answers 2017 CCNA 3 (v5.0.3 + v6.0) Chapter 4 Exam Answers
CCNA 3 (v5.0.3 + v6.0) Chapter 4 Exam Answers 2017 100% Full ccnav6.com /ccna-3-v5-0-3-v6-0-chapter-4-exam-answers-2017-100-full.html CCNA Exam Answers 2017 CCNA 3 (v5.0.3 + v6.0) Chapter 4 Exam Answers
CSMC 417. Computer Networks Prof. Ashok K Agrawala Ashok Agrawala. Fall 2018 CMSC417 Set 1 1
 CSMC 417 Computer Networks Prof. Ashok K Agrawala 2018 Ashok Agrawala Fall 2018 CMSC417 Set 1 1 The Medium Access Control Sublayer November 18 Nov 6, 2018 2 Wireless Networking Technologies November 18
CSMC 417 Computer Networks Prof. Ashok K Agrawala 2018 Ashok Agrawala Fall 2018 CMSC417 Set 1 1 The Medium Access Control Sublayer November 18 Nov 6, 2018 2 Wireless Networking Technologies November 18
Brian S. Dennis Director Cyber Security Center for Small Business Kansas Small Business Development Center
 Brian S. Dennis Director Cyber Security Center for Small Business Kansas Small Business Development Center What to expect from today: The ugly truth about planning Why you need a plan that works Where
Brian S. Dennis Director Cyber Security Center for Small Business Kansas Small Business Development Center What to expect from today: The ugly truth about planning Why you need a plan that works Where
NT1210 Introduction to Networking. Unit 6: Chapter 6, Wireless LANs
 NT1210 Introduction to Networking Unit 6: Chapter 6, Wireless LANs Objectives Identify the major needs and stakeholders for computer networks and network applications. Identify the classifications of networks
NT1210 Introduction to Networking Unit 6: Chapter 6, Wireless LANs Objectives Identify the major needs and stakeholders for computer networks and network applications. Identify the classifications of networks
High Power Wireless N. 600mW Smart Repeater LP 9698SR
 High Power Wireless N 600mW Smart Repeater LP 9698SR INTRODUCTION...4 GETTING STARTED...5 Package Contents...5 LED Indicators...6 Back Panel Description...7 SETUP GUIDE...8 Find a Setup Location...8 Connect
High Power Wireless N 600mW Smart Repeater LP 9698SR INTRODUCTION...4 GETTING STARTED...5 Package Contents...5 LED Indicators...6 Back Panel Description...7 SETUP GUIDE...8 Find a Setup Location...8 Connect
Wireless network security: A how-to guide for SMBs
 Wireless network security: A how-to guide for SMBs Wireless network security: A how-to guide for SMBs WiFi networks are a requirement for doing business today. Employees rely on them to have constant access
Wireless network security: A how-to guide for SMBs Wireless network security: A how-to guide for SMBs WiFi networks are a requirement for doing business today. Employees rely on them to have constant access
300Mbps Wireless N Gigabit Ceilling Mount Access Point
 Datasheet 300Mbps Wireless N Gigabit Ceilling Mount Access Point 120 Highlights Wireless N speed up to 300Mbps The Controller Software enables administrators to manage hundreds of s easily from any PC
Datasheet 300Mbps Wireless N Gigabit Ceilling Mount Access Point 120 Highlights Wireless N speed up to 300Mbps The Controller Software enables administrators to manage hundreds of s easily from any PC
Motorola AirDefense Retail Solutions Wireless Security Solutions For Retail
 Motorola AirDefense Retail Solutions Wireless Security Solutions For Retail Wireless Risks in Retail The PCI Security Standards Council is an open global forum, founded by American Express, Discover Financial
Motorola AirDefense Retail Solutions Wireless Security Solutions For Retail Wireless Risks in Retail The PCI Security Standards Council is an open global forum, founded by American Express, Discover Financial
GETTING THE MOST OUT OF EVIL TWIN
 GETTING THE MOST OUT OF EVIL TWIN B-SIDES ATHENS 2016 GEORGE CHATZISOFRONIOU (@_sophron) sophron@census-labs.com www.census-labs.com > WHOAMI Security Engineer at CENSUS S.A. Cryptography, Wi-Fi hacking,
GETTING THE MOST OUT OF EVIL TWIN B-SIDES ATHENS 2016 GEORGE CHATZISOFRONIOU (@_sophron) sophron@census-labs.com www.census-labs.com > WHOAMI Security Engineer at CENSUS S.A. Cryptography, Wi-Fi hacking,
IT220 Network Standards & Protocols. Unit 6: Chapter 6 Wireless LANs
 IT220 Network Standards & Protocols Unit 6: Chapter 6 Wireless LANs 2 Objectives Identify the major needs and stakeholders for computer networks and network applications. Identify the classifications of
IT220 Network Standards & Protocols Unit 6: Chapter 6 Wireless LANs 2 Objectives Identify the major needs and stakeholders for computer networks and network applications. Identify the classifications of
Table of Contents. Your ZTE PEEL. i How to Use This Guide
 USER GUIDE by ZTE Table of Contents Your ZTE PEEL i How to Use This Guide ii Section 1: Your Device s Browser Interface 1 The Browser Interface 1 Opening the Browser Interface 1 The Administration Home
USER GUIDE by ZTE Table of Contents Your ZTE PEEL i How to Use This Guide ii Section 1: Your Device s Browser Interface 1 The Browser Interface 1 Opening the Browser Interface 1 The Administration Home
Welcome to Cogeco UltraFibre Internet. UltraFibre Internet User Guide
 Welcome to Cogeco UltraFibre Internet UltraFibre Internet User Guide Hi there. Thanks for joining us. Welcome to your new UltraFibre Internet service from Cogeco. This User Guide is a reference tool for
Welcome to Cogeco UltraFibre Internet UltraFibre Internet User Guide Hi there. Thanks for joining us. Welcome to your new UltraFibre Internet service from Cogeco. This User Guide is a reference tool for
تاثیرفناوری اطالعات برسازمان ومدیریت جلسه هشتم و نهم
 بنام خدا تاثیرفناوری اطالعات برسازمان ومدیریت جلسه هشتم و نهم امنیت بخشی به سیستمهای فناوری اطالعات Securing Information Systems 1 Learning Objectives Describe the business value of security and control.
بنام خدا تاثیرفناوری اطالعات برسازمان ومدیریت جلسه هشتم و نهم امنیت بخشی به سیستمهای فناوری اطالعات Securing Information Systems 1 Learning Objectives Describe the business value of security and control.
Procedure: You can find the problem sheet on the Desktop of the lab PCs.
 University of Jordan Faculty of Engineering & Technology Computer Engineering Department Computer Advance Networks Laboratory 907529 Lab.3 WLAN Security Objectives 1. Configure administrator accounts.
University of Jordan Faculty of Engineering & Technology Computer Engineering Department Computer Advance Networks Laboratory 907529 Lab.3 WLAN Security Objectives 1. Configure administrator accounts.
WL-5420AP. User s Guide
 WL-5420AP User s Guide Table of contents INTRODUCTION... 1 About the Operation Modes...2 LED Indicators...5 Solid...5 Ports on the Rear Panel...7 GETTING CONNECTED... 8 WPA AP -CONFIGURATION VIA WEB...
WL-5420AP User s Guide Table of contents INTRODUCTION... 1 About the Operation Modes...2 LED Indicators...5 Solid...5 Ports on the Rear Panel...7 GETTING CONNECTED... 8 WPA AP -CONFIGURATION VIA WEB...
QUICK START GUIDE. Pepwave Express. Quick Start Guide. Pepwave Express. Nov Pepwave
 Quick Start Guide Nov-12 http://www.pepwave.com 1 Copyright @ 2012 Pepwave First Time Setup 1. Default Configuration IP: 192.168.0.1 Subnet Mask: 255.255.255.0 2. Network Configuration acts as a CPE bridge
Quick Start Guide Nov-12 http://www.pepwave.com 1 Copyright @ 2012 Pepwave First Time Setup 1. Default Configuration IP: 192.168.0.1 Subnet Mask: 255.255.255.0 2. Network Configuration acts as a CPE bridge
Children s Health System. Remote User Policy
 Children s Health System Remote User Policy July 28, 2008 Reason for this Policy This policy defines standards for connecting to the Children s Health System (CHS) network from any remote host. These standards
Children s Health System Remote User Policy July 28, 2008 Reason for this Policy This policy defines standards for connecting to the Children s Health System (CHS) network from any remote host. These standards
AirCheck Wi-Fi Tester Evaluation Guide
 AirCheck Wi-Fi Tester Evaluation Guide Outline 1. Getting Started 2. Finding Networks and Access Points 3. Drill in on an AP 4. Locate an AP 5. Discover Clients Associated to an AP 6. Locate a Client 7.
AirCheck Wi-Fi Tester Evaluation Guide Outline 1. Getting Started 2. Finding Networks and Access Points 3. Drill in on an AP 4. Locate an AP 5. Discover Clients Associated to an AP 6. Locate a Client 7.
AiM User Manual. Wi-Fi Configuration. Release 1.01
 AiM User Manual Wi-Fi Configuration Release 1.01 1 Wi-Fi configuration Your AiM device Wi-Fi connectivity is disabled by default and must be enabled via a USB connection or on the device menu. Your AiM
AiM User Manual Wi-Fi Configuration Release 1.01 1 Wi-Fi configuration Your AiM device Wi-Fi connectivity is disabled by default and must be enabled via a USB connection or on the device menu. Your AiM
Exam : PW Title : Certified wireless security professional(cwsp) Version : DEMO
 Exam : PW0-200 Title : Certified wireless security professional(cwsp) Version : DEMO 1. Given: John Smith often telecommutes from a coffee shop near his home. The coffee shop has an 802.11g access point
Exam : PW0-200 Title : Certified wireless security professional(cwsp) Version : DEMO 1. Given: John Smith often telecommutes from a coffee shop near his home. The coffee shop has an 802.11g access point
Guide to Networking Essentials, 6 th Edition. Chapter 7: Network Hardware in Depth
 Guide to Networking Essentials, 6 th Edition Chapter 7: Network Hardware in Depth Objectives Describe the advanced features and operation of network switches Describe routing table properties and discuss
Guide to Networking Essentials, 6 th Edition Chapter 7: Network Hardware in Depth Objectives Describe the advanced features and operation of network switches Describe routing table properties and discuss
Securing Your Airspace with WatchGuard s Wireless Intrusion Prevention (WIPS)
 Securing Your Airspace with WatchGuard s Wireless Intrusion Prevention (WIPS) Introduction The proliferation of Wi-Fi across the globe has created an attractive opportunity for cyber attackers to snoop,
Securing Your Airspace with WatchGuard s Wireless Intrusion Prevention (WIPS) Introduction The proliferation of Wi-Fi across the globe has created an attractive opportunity for cyber attackers to snoop,
Aruba Instant in AirWave 7.7
 Aruba Instant in AirWave 7.7 Deployment Guide About this Document This document describes the Aruba Instant access point and Virtual Controller system as well as the procedure to integrate this system
Aruba Instant in AirWave 7.7 Deployment Guide About this Document This document describes the Aruba Instant access point and Virtual Controller system as well as the procedure to integrate this system
AC1350 Wireless Dual Band Router
 AC1350 Wireless Dual Band Router Upgrade for Faster AC Wi-Fi to Every Device 450Mbps + 867Mbps Dual Band Wi-Fi MU-MIMO Technology for 2 Faster Performance Beamforming Technology for Better Coverage Highlights
AC1350 Wireless Dual Band Router Upgrade for Faster AC Wi-Fi to Every Device 450Mbps + 867Mbps Dual Band Wi-Fi MU-MIMO Technology for 2 Faster Performance Beamforming Technology for Better Coverage Highlights
