SSAC Public Meeting Paris. 24 June 2008
|
|
|
- Domenic Horn
- 5 years ago
- Views:
Transcription
1 SSAC Public Meeting Paris 1
2 in Phishing Attacks 2
3 What is? A phishing attack The attacker impersonates a registrar The phish s are sent to The registrar's customers (bulk) A particular, targeted customer (spear) Objective: lure customer into disclosing domain management account credentials 3
4 Why are domain accounts targets? Attacker can modify registration record for malicious purposes Alter contact information to abet domain hijacking and business disruption Alter or add Type MX, A, or AAA resource records to abet malicious redirection or flux phishing attacks Attacker can obtain information that is not published (i.e., protected or proxied registrations) Attackers can use any credit or billing information associated with the account to purchase additional domains to use in attacks 4
5 One form of registrar phishing Impersonate a registrar customer portal (login site) Lure customer to the bogus site using an that Appears to be from the registrar and Is alarming or conveys a sense of urgency (plant F.U.D.) Send the phish to the contact addresses for the domain name Wait for the registrar s customers to fall prey to the deception, visit the bogus registrar customer portal and disclose login credentials Steal the customer's account credentials 5
6 What lures do phishers use? Message body is an expected correspondence from a registrar: Domain name renewal notices, transfer notices, or order confirmations Registration request confirmations Registration and DNS information change confirmations WHOIS accuracy reminders Notices of domain name expiry or cancellation Message is often personalized to enhance the deception 6
7 Example (text ASCII) THANK YOU FOR YOUR ORDER Wednesday, October 19, :18:34 AM Dear customer, Thank you for ordering from <registrar>. Here are the details of your recent transaction with us. Please save this information for future reference. CUSTOMER NUMBER: LOGIN NAME: mydomainaccount RECEIPT NUMBER: ORDER TOTAL: $19.99 CUSTOMER SERVICE: Personalized information does not have to be accurate, only convincing You must login to your account to complete this transaction. Please visit the following confirmation link at 7
8 Example (HTML, hidden tag) Dear Valued Customer, This is a confirmation that the password for your registrar.<tld> account, mydomainaccount, has been successfully changed. If you feel an unauthorized party has changed the password of your account, please contact Customer Support by submitting a request online at or contact us at +1(888) If you have any further questions about this process and wish to consult with a Customer Service Representative contact us by submitting a request online at Thank you for choosing registrar<tld>. Customer Support Hover over the hyperlink 8
9 How Registrars can reduce the risk 1. Only include information necessary to convey the desired message in customer correspondence. 2. Avoid using hyperlink references in correspondence with customers. 3. Warn customers against clicking on hyperlinks included in any correspondence. 4. Raise awareness that registrars are attractive candidates for impersonation. 5. Implement a form of non-repudiation of origin for customer correspondence, such as a digital signature. 6. Implement multi-factor authentication for high-value, high securityminded domain registrants 7. Use Extended Validation (EV) certificates for high assurance SSL connections for all sensitive transactions 8. Provide ways to report suspected phishing attacks. 9
10 Customers:avoid being phished! 1. Do not click on hyperlinks included in messages. 2. Use anti-spam and antiphishing features 3. Use an client that reveals hyperlink references 4. Be suspicious of s that claim an urgent response is required 5. Read message bodies carefully. 6. Do not trust an simply because it is personalized. 7. Verify the login form you are using is legitimate before you submit account credentials. 8. Make certain the page you visit is secured using SSL. 9. Use a unique password for your account and change it regularly. 10. Choose a registrar that requires a credit card CVV for purchases. 11. Registrants with high-value domain portfolios should consider premium services from registrars that offer additional security and monitoring measures 10
ClientNet. Portal Admin Guide
 ClientNet Portal Admin Guide Document Revision Date: June 5, 2013 ClientNet Portal Admin Guide i Contents Introduction to the Portal... 1 About the Portal... 1 Logging On and Off the Portal... 1 Language
ClientNet Portal Admin Guide Document Revision Date: June 5, 2013 ClientNet Portal Admin Guide i Contents Introduction to the Portal... 1 About the Portal... 1 Logging On and Off the Portal... 1 Language
Protecting High Value Domains
 Protecting High Value Domains SSAC Public Meeting ICANN Cairo 2008 1 What is a high value domain? Working definition: high value domain (HVD) One or a set of names which define an organization's online
Protecting High Value Domains SSAC Public Meeting ICANN Cairo 2008 1 What is a high value domain? Working definition: high value domain (HVD) One or a set of names which define an organization's online
How to recognize phishing s
 Phishing email messages, websites, and phone calls are designed to steal money, steal data and/or destroy information. Cybercriminals can do this by installing malicious software on your computer or stealing
Phishing email messages, websites, and phone calls are designed to steal money, steal data and/or destroy information. Cybercriminals can do this by installing malicious software on your computer or stealing
Phishing Attacks. Mendel Rosenblum. CS142 Lecture Notes - Phishing Attack
 Phishing Attacks Mendel Rosenblum Phishing Basic idea: Get unsuspecting users to visit an evil Web site Convince them that the evil Web site is actually a legitimate site (such as a bank or PayPal) Trick
Phishing Attacks Mendel Rosenblum Phishing Basic idea: Get unsuspecting users to visit an evil Web site Convince them that the evil Web site is actually a legitimate site (such as a bank or PayPal) Trick
Target Breach Overview
 Target Breach Overview Q: Media reports are stating that Target experienced a data breach. Can you provide more specifics? A: Yes, Target has confirmed that it experienced unauthorized access to its systems
Target Breach Overview Q: Media reports are stating that Target experienced a data breach. Can you provide more specifics? A: Yes, Target has confirmed that it experienced unauthorized access to its systems
Measures to Protect Domain Registration Services against Exploitation or Misuse. June 2009 Dave Piscitello ICANN SSAC
 Measures to Protect Domain Registration Services against Exploitation or Misuse June 2009 Dave Piscitello ICANN SSAC What instigated this work? Attacks against domain registration accounts and registrars
Measures to Protect Domain Registration Services against Exploitation or Misuse June 2009 Dave Piscitello ICANN SSAC What instigated this work? Attacks against domain registration accounts and registrars
APTLD & MYNIC JOINT SURVEY
 INTERNET SECURITY & CCTLDS SURVEY RESULTS 24 th June 2008, Tuesday ccnso meeting, Paris, France Survey Objectives Survey Summary:- For APTLD members to examine the roles and responsibilities of cctlds
INTERNET SECURITY & CCTLDS SURVEY RESULTS 24 th June 2008, Tuesday ccnso meeting, Paris, France Survey Objectives Survey Summary:- For APTLD members to examine the roles and responsibilities of cctlds
IT Security Protecting Ourselves From Phishing Attempts. Ray Copeland Chief Information Officer (CIO)
 IT Security Protecting Ourselves From Phishing Attempts Ray Copeland Chief Information Officer (CIO) Phishing Defined The fraudulent practice of sending emails claiming to be from reputable people or companies
IT Security Protecting Ourselves From Phishing Attempts Ray Copeland Chief Information Officer (CIO) Phishing Defined The fraudulent practice of sending emails claiming to be from reputable people or companies
Partner Documentation Reseller Portal Guide
 2 Partner Documentation 1.Introduction and Enrollment One of the benefits of MSP Consortium membership is access to Comodo's range of enterprise security and management tools at greatly discounted rates.
2 Partner Documentation 1.Introduction and Enrollment One of the benefits of MSP Consortium membership is access to Comodo's range of enterprise security and management tools at greatly discounted rates.
Webomania Solutions Pvt. Ltd. 2017
 The other name for link manipulation is Phishing or you can say link manipulation is type of phishing attack done generally to mislead the user to a replica website or a looka-like of some well-known site.
The other name for link manipulation is Phishing or you can say link manipulation is type of phishing attack done generally to mislead the user to a replica website or a looka-like of some well-known site.
Bank of america report phishing
 Search Search pages & people Search Search Search pages & people Search Bank of america report phishing email We recently discovered a new phishing scam from a Bank of America spam email some reports that
Search Search pages & people Search Search Search pages & people Search Bank of america report phishing email We recently discovered a new phishing scam from a Bank of America spam email some reports that
Best Practices Guide to Electronic Banking
 Best Practices Guide to Electronic Banking City Bank & Trust Company offers a variety of services to our customers. As these services have evolved over time, a much higher percentage of customers have
Best Practices Guide to Electronic Banking City Bank & Trust Company offers a variety of services to our customers. As these services have evolved over time, a much higher percentage of customers have
FAQ. Usually appear to be sent from official address
 FAQ 1. What is Phishing Email? A form of fraud by which an attacker masquerades as a reputable entity in order to obtain your personal information. Usually appear to be sent from official email address
FAQ 1. What is Phishing Email? A form of fraud by which an attacker masquerades as a reputable entity in order to obtain your personal information. Usually appear to be sent from official email address
Frequently Asked Questions (FAQ)
 Your personal information and account security is important to us. This product employs a Secure Sign On process that includes layers of protection at time of product log in to mitigate risk, and thwart
Your personal information and account security is important to us. This product employs a Secure Sign On process that includes layers of protection at time of product log in to mitigate risk, and thwart
Security & Phishing
 Email Security & Phishing Best Practices In Cybersecurity Presenters Bill Shieh Guest Speaker Staff Engineer Information Security Ellie Mae Supervisory Special Agent Cyber Crime FBI 2 What Is Phishing?
Email Security & Phishing Best Practices In Cybersecurity Presenters Bill Shieh Guest Speaker Staff Engineer Information Security Ellie Mae Supervisory Special Agent Cyber Crime FBI 2 What Is Phishing?
Phishing Read Behind The Lines
 Phishing Read Behind The Lines Veljko Pejović veljko@cs.ucsb.edu What is Phishing? "Phishing attacks use both social engineering and technical subterfuge to steal consumers' personal identity data and
Phishing Read Behind The Lines Veljko Pejović veljko@cs.ucsb.edu What is Phishing? "Phishing attacks use both social engineering and technical subterfuge to steal consumers' personal identity data and
Phishing. Eugene Davis UAH Information Security Club April 11, 2013
 Phishing Eugene Davis UAH Information Security Club April 11, 2013 Overview A social engineering attack in which the attacker impersonates a trusted entity Attacker attempts to retrieve privileged information
Phishing Eugene Davis UAH Information Security Club April 11, 2013 Overview A social engineering attack in which the attacker impersonates a trusted entity Attacker attempts to retrieve privileged information
Octopus Online Service Safety Guide
 Octopus Online Service Safety Guide This Octopus Online Service Safety Guide is to provide you with security tips and reminders that you should be aware of when using online and mobile services provided
Octopus Online Service Safety Guide This Octopus Online Service Safety Guide is to provide you with security tips and reminders that you should be aware of when using online and mobile services provided
DoD Spear-Phishing Awareness Training. Joint Task Force - Global Network Operations
 //FOUO DoD Spear-Phishing Awareness Training Joint Task Force - Global Network Operations Updated: 16 NOV 2006 //FOUO Objective Inform and increase the awareness of all Department of Defense personnel
//FOUO DoD Spear-Phishing Awareness Training Joint Task Force - Global Network Operations Updated: 16 NOV 2006 //FOUO Objective Inform and increase the awareness of all Department of Defense personnel
Evolution of Spear Phishing. White Paper
 Evolution of Spear Phishing White Paper Executive Summary Phishing is a well-known security threat, but few people understand the difference between phishing and spear phishing. Spear phishing is the latest
Evolution of Spear Phishing White Paper Executive Summary Phishing is a well-known security threat, but few people understand the difference between phishing and spear phishing. Spear phishing is the latest
A Lightweight Framework for Detection and Resolution for Phishing, Pharming and Spoofing
 A Lightweight Framework for Detection and Resolution for Phishing, Pharming and Email Spoofing Pooja Modi 1, Hardik Upadhyay 2, Ketan Modi 3, Krunal Suthar 4 ME Student, Department of Computer Engineering,
A Lightweight Framework for Detection and Resolution for Phishing, Pharming and Email Spoofing Pooja Modi 1, Hardik Upadhyay 2, Ketan Modi 3, Krunal Suthar 4 ME Student, Department of Computer Engineering,
Domain Name Hijacking A Preliminary Report. Security and Stability Advisory Committee Mar del Plata April 5, 2005
 Domain Name Hijacking A Preliminary Report Security and Stability Advisory Committee Mar del Plata April 5, 2005 1 Headlines Panix.com was hijacked on 15 Jan 2005 action returned it after 48 hours Gaining
Domain Name Hijacking A Preliminary Report Security and Stability Advisory Committee Mar del Plata April 5, 2005 1 Headlines Panix.com was hijacked on 15 Jan 2005 action returned it after 48 hours Gaining
Custom Plugin A Solution to Phishing and Pharming Attacks
 Custom Plugin A Solution to Phishing and Pharming Attacks Omer Mahmood School of Information Technology Charles Darwin University Darwin, NT, Australia Abstract - This paper proposes a new method to detect,
Custom Plugin A Solution to Phishing and Pharming Attacks Omer Mahmood School of Information Technology Charles Darwin University Darwin, NT, Australia Abstract - This paper proposes a new method to detect,
On the Surface. Security Datasheet. Security Datasheet
 Email Security Datasheet Email Security Datasheet On the Surface No additional hardware or software required to achieve 99.9%+ spam and malware filtering effectiveness Initiate service by changing MX Record
Email Security Datasheet Email Security Datasheet On the Surface No additional hardware or software required to achieve 99.9%+ spam and malware filtering effectiveness Initiate service by changing MX Record
2 User Guide. Contents
 E-mail User Guide 2 E-mail User Guide Contents Logging in to your web mail... 3 Changing your password... 5 Editing your signature... 6 Adding an e-mail account to Outlook 2010/2013/2016... 7 Adding an
E-mail User Guide 2 E-mail User Guide Contents Logging in to your web mail... 3 Changing your password... 5 Editing your signature... 6 Adding an e-mail account to Outlook 2010/2013/2016... 7 Adding an
DOMAIN NAMES. Manage Domains
 DOMAIN NAMES Manage Domains The Manage Domains page displays a list of your registered domain names. All domain purchases are automatically renewed at the end of their registration period, unless you instruct
DOMAIN NAMES Manage Domains The Manage Domains page displays a list of your registered domain names. All domain purchases are automatically renewed at the end of their registration period, unless you instruct
Quick Start Guide. Microsoft Windows 7 / Vista / XP / 2000 / 2003 / 2008
 Quick Start Guide Microsoft Windows 7 / Vista / XP / 2000 / 2003 / 2008 ESET NOD32 Antivirus provides state-of-the-art protection for your computer against malicious code. Based on the ThreatSense scanning
Quick Start Guide Microsoft Windows 7 / Vista / XP / 2000 / 2003 / 2008 ESET NOD32 Antivirus provides state-of-the-art protection for your computer against malicious code. Based on the ThreatSense scanning
Guide to Personal Online Banking. Great Things Happen!
 Great Things Happen! Table of Contents General Information Security... Getting Started - Enroll & Authenticate.........4 Accounts Overview... 0 History... Online Activity... estatements... 4 Transactions
Great Things Happen! Table of Contents General Information Security... Getting Started - Enroll & Authenticate.........4 Accounts Overview... 0 History... Online Activity... estatements... 4 Transactions
Sectigo Security Solution
 Sectigo Email Security Solution 2018 Sectigo. All rights reserved. Email hacking is a commonly used malicious tactic in our increasingly connected world. Business email compromise (BEC), or email account
Sectigo Email Security Solution 2018 Sectigo. All rights reserved. Email hacking is a commonly used malicious tactic in our increasingly connected world. Business email compromise (BEC), or email account
CENTAC HELP DOCUMENT FOR OTHER STATE. CENTAC Homepage:
 CENTAC HELP DOCUMENT FOR OTHER STATE CENTAC Homepage: http://www.centaconline.in Dear Candidate, Good day and wishes from CENTAC Team for your successful placements via centac. Along this journey I will
CENTAC HELP DOCUMENT FOR OTHER STATE CENTAC Homepage: http://www.centaconline.in Dear Candidate, Good day and wishes from CENTAC Team for your successful placements via centac. Along this journey I will
Review of Phishing Detection Techniques
 Review of Phishing Detection Techniques Swati Gaikwad Computer Engineering, DACOE, Pune, India. swatigaikwad0385@gmail.com Abstract Nowadays phishing attacks are increasing with burgeoning rate which is
Review of Phishing Detection Techniques Swati Gaikwad Computer Engineering, DACOE, Pune, India. swatigaikwad0385@gmail.com Abstract Nowadays phishing attacks are increasing with burgeoning rate which is
TIPS TO AVOID PHISHING SCAMS
 TIPS TO AVOID PHISHING SCAMS WHAT IS PHISHING? Phishing is the use of fraudulent email, websites, text messages and phone calls to trick people into disclosing personal financial or identity information,
TIPS TO AVOID PHISHING SCAMS WHAT IS PHISHING? Phishing is the use of fraudulent email, websites, text messages and phone calls to trick people into disclosing personal financial or identity information,
So Many Ways to Slap a YoHo: Hacking Facebook & YoVille
 Tom Stracener Strace, Contract Engineer MITRE EvilAdamSmith, Sr. Security Consultant Sean Barnum, Cybersecurity Principal MITRE So Many Ways to Slap a YoHo: Hacking Facebook & YoVille Misclaneous Disclaimers
Tom Stracener Strace, Contract Engineer MITRE EvilAdamSmith, Sr. Security Consultant Sean Barnum, Cybersecurity Principal MITRE So Many Ways to Slap a YoHo: Hacking Facebook & YoVille Misclaneous Disclaimers
BRING SPEAR PHISHING PROTECTION TO THE MASSES
 E-Guide BRING SPEAR PHISHING PROTECTION TO THE MASSES SearchSecurity phishing. I n this expert tip, David Sherry describes how a combination of technical controls and user awareness training can help put
E-Guide BRING SPEAR PHISHING PROTECTION TO THE MASSES SearchSecurity phishing. I n this expert tip, David Sherry describes how a combination of technical controls and user awareness training can help put
Law Enforcement Recommended RAA Amendments and ICANN Due Diligence Detailed Version
 Date: 18 October 2010 Law Enforcement Recommended RAA Amendments and ICANN Due Diligence Detailed Version Introduction: Below are: 1) suggested amendments to the RAA and; 2) due diligence recommendations
Date: 18 October 2010 Law Enforcement Recommended RAA Amendments and ICANN Due Diligence Detailed Version Introduction: Below are: 1) suggested amendments to the RAA and; 2) due diligence recommendations
Fundraising Website Guide
 This Guide will help you set-up and use your team s new fundraising website! Please let us know if you need any assistance or have any questions. This document will be updated regularly as we receive your
This Guide will help you set-up and use your team s new fundraising website! Please let us know if you need any assistance or have any questions. This document will be updated regularly as we receive your
Resellers Guide Managing your Reseller Account
 Resellers Guide Managing your Reseller Account Read our Blog: http://blog.webfusion.co.uk/ View our support site: http://webfusion-support.co.uk/ Follow us on Twitter: http://twitter.com/webfusionuk Contents
Resellers Guide Managing your Reseller Account Read our Blog: http://blog.webfusion.co.uk/ View our support site: http://webfusion-support.co.uk/ Follow us on Twitter: http://twitter.com/webfusionuk Contents
Identity Theft, Fraud & You. PrePare. Protect. Prevent.
 PrePare. Protect. Prevent. Identity Theft, Fraud & You Fraud and identity theft incidents claimed fewer victims in 2010 than in previous years. But don t get too comfortable. Average out-of-pocket consumer
PrePare. Protect. Prevent. Identity Theft, Fraud & You Fraud and identity theft incidents claimed fewer victims in 2010 than in previous years. But don t get too comfortable. Average out-of-pocket consumer
Wayward Wi-Fi. How Rogue Hotspots Can Hijack Your Data and Put Your Mobile Devices at Risk
 Wayward Wi-Fi How Rogue Hotspots Can Hijack Your Data and Put Your Mobile Devices at Risk 288 MILLION There are more than 288 million unique Wi-Fi networks worldwide. Source: Wireless Geographic Logging
Wayward Wi-Fi How Rogue Hotspots Can Hijack Your Data and Put Your Mobile Devices at Risk 288 MILLION There are more than 288 million unique Wi-Fi networks worldwide. Source: Wireless Geographic Logging
CE Advanced Network Security Phishing I
 CE 817 - Advanced Network Security Phishing I Lecture 15 Mehdi Kharrazi Department of Computer Engineering Sharif University of Technology Acknowledgments: Some of the slides are fully or partially obtained
CE 817 - Advanced Network Security Phishing I Lecture 15 Mehdi Kharrazi Department of Computer Engineering Sharif University of Technology Acknowledgments: Some of the slides are fully or partially obtained
Explanation of Data Element Data Element Potentially Legitimate purposes for Collection/Retention
 Data Element Data Element Potentially Legitimate purposes for Collection/Retention 1.1.1. First and last name or full legal name of Registrant 1.1.2. First and last name or, in the event Registrant is
Data Element Data Element Potentially Legitimate purposes for Collection/Retention 1.1.1. First and last name or full legal name of Registrant 1.1.2. First and last name or, in the event Registrant is
Web Cash Fraud Prevention Best Practices
 Web Cash Fraud Prevention Best Practices Tips on what you can do to prevent Online fraud. This document provides best practices to avoid or reduce exposure to fraud. You can use it to educate your Web
Web Cash Fraud Prevention Best Practices Tips on what you can do to prevent Online fraud. This document provides best practices to avoid or reduce exposure to fraud. You can use it to educate your Web
Cyber Security Guide for NHSmail
 Cyber Security Guide for NHSmail Version 3.0 February 2017 Copyright 2017Health and Social Care Information Centre. The Health and Social Care Information Centre is a non-departmental body created by statute,
Cyber Security Guide for NHSmail Version 3.0 February 2017 Copyright 2017Health and Social Care Information Centre. The Health and Social Care Information Centre is a non-departmental body created by statute,
Provider Portal. User Manual. Therapists and Health Practitioners
 Provider Portal User Manual Therapists and Health Practitioners Table of Contents 1. Introduction... 3 2. Registering for the Provider Portal... 4 i. Changing Your Password...6 ii. Accepting Terms and
Provider Portal User Manual Therapists and Health Practitioners Table of Contents 1. Introduction... 3 2. Registering for the Provider Portal... 4 i. Changing Your Password...6 ii. Accepting Terms and
Introduction. Logging in. WebMail User Guide
 Introduction modusmail s WebMail allows you to access and manage your email, quarantine contents and your mailbox settings through the Internet. This user guide will walk you through each of the tasks
Introduction modusmail s WebMail allows you to access and manage your email, quarantine contents and your mailbox settings through the Internet. This user guide will walk you through each of the tasks
s and Anti-spam
 E-mails and Anti-spam Standard authentication AUTH method As the spammers become increasing aggressive more and more legit emails get banned as spam. When you send e-mails from your webcrm system, we use
E-mails and Anti-spam Standard authentication AUTH method As the spammers become increasing aggressive more and more legit emails get banned as spam. When you send e-mails from your webcrm system, we use
Center for Science Outreach Public View
 Vanderbilt University Center for Science Outreach Public View Destiny One Page 1 Contents Create a Student Profile/Account... 3 Browse for a Course... 5 Register for a Course and Checkout... 7 Page 2 Create
Vanderbilt University Center for Science Outreach Public View Destiny One Page 1 Contents Create a Student Profile/Account... 3 Browse for a Course... 5 Register for a Course and Checkout... 7 Page 2 Create
WHAT IS CORPORATE ACCOUNT TAKEOVER? HOW DOES IT HAPPEN?
 WHAT IS CORPORATE ACCOUNT TAKEOVER? Corporate Account Takeover (also referred to as CATO) is a type of fraud where criminals gain access to a business financial accounts to make unauthorized transactions.
WHAT IS CORPORATE ACCOUNT TAKEOVER? Corporate Account Takeover (also referred to as CATO) is a type of fraud where criminals gain access to a business financial accounts to make unauthorized transactions.
41% Opens. 73% Clicks. 35% Submits Sent
 Phishing Awareness Attackers engage with you through your email inbox, and unless you pay close attention, you can become a victim to their masquerade. What tactic are these attackers using? It is called
Phishing Awareness Attackers engage with you through your email inbox, and unless you pay close attention, you can become a victim to their masquerade. What tactic are these attackers using? It is called
IMEI Database. Manufacturer / Brand Owner User Guide. Version September Copyright Notice. Copyright 2015 GSM Association
 IMEI Database Manufacturer / Brand Owner User Guide Version 4.0 01 September 2015 Copyright Notice Copyright 2015 GSM Association GSM and the GSM logo are registered and owned by the GSM Association. Antitrust
IMEI Database Manufacturer / Brand Owner User Guide Version 4.0 01 September 2015 Copyright Notice Copyright 2015 GSM Association GSM and the GSM logo are registered and owned by the GSM Association. Antitrust
Robust Defenses for Cross-Site Request Forgery Review
 Robust Defenses for Cross-Site Request Forgery Review Network Security Instructor:Dr. Shishir Nagaraja Submitted By: Jyoti Leeka October 16, 2011 1 Introduction to the topic and the reason for the topic
Robust Defenses for Cross-Site Request Forgery Review Network Security Instructor:Dr. Shishir Nagaraja Submitted By: Jyoti Leeka October 16, 2011 1 Introduction to the topic and the reason for the topic
RAK ICC PORTAL 09 &10 JANUARY 2017 FREQUENTLY ASKED QUESTIONS
 RAK ICC PORTAL 09 &10 JANUARY 2017 FREQUENTLY ASKED QUESTIONS 1. When would the username and password be available? Can multiple company accounts have same password? Does the portal ask for change of password
RAK ICC PORTAL 09 &10 JANUARY 2017 FREQUENTLY ASKED QUESTIONS 1. When would the username and password be available? Can multiple company accounts have same password? Does the portal ask for change of password
Why was an extra step of choosing a Security Image added to the sign-in process?
 General Information Why was an extra step of choosing a Security Image added to the sign-in process? Criminals can create websites that look very similar to legitimate business websites. We want to take
General Information Why was an extra step of choosing a Security Image added to the sign-in process? Criminals can create websites that look very similar to legitimate business websites. We want to take
Assure Self-Service Portal
 Assure Self-Service Portal Assure Self-Service Portal is a web-based portal, where Customers are able to: Record Cases to Assure Support 24/7 View existing and past Cases Find solutions to known issues
Assure Self-Service Portal Assure Self-Service Portal is a web-based portal, where Customers are able to: Record Cases to Assure Support 24/7 View existing and past Cases Find solutions to known issues
Symantec Intelligence Quarterly: Best Practices and Methodologies October - December, 2009
 Symantec Intelligence Quarterly: Best Practices and Methodologies White Paper: Symantec Intelligence Quarterly Symantec Intelligence Quarterly: Best Practices and Methodologies Contents Symantec best
Symantec Intelligence Quarterly: Best Practices and Methodologies White Paper: Symantec Intelligence Quarterly Symantec Intelligence Quarterly: Best Practices and Methodologies Contents Symantec best
Security and Privacy. Xin Liu Computer Science University of California, Davis. Introduction 1-1
 Security and Privacy Xin Liu Computer Science University of California, Davis Introduction 1-1 What is network security? Confidentiality: only sender, intended receiver should understand message contents
Security and Privacy Xin Liu Computer Science University of California, Davis Introduction 1-1 What is network security? Confidentiality: only sender, intended receiver should understand message contents
Provider Portal. User Manual. Vision Care
 Provider Portal User Manual Vision Care Table of Contents 1. Introduction... 3 2. Registering for the Provider Portal... 4 i. Changing Your Password...6 ii. Accepting Terms and Conditions...7 iii. Setting
Provider Portal User Manual Vision Care Table of Contents 1. Introduction... 3 2. Registering for the Provider Portal... 4 i. Changing Your Password...6 ii. Accepting Terms and Conditions...7 iii. Setting
Kroger Supplier Information Management System (SIM) Training Documentation
 Kroger Supplier Information Management System (SIM) Training Documentation Introduction All Kroger suppliers are required to register in Kroger s new Supplier Information Management (SIM) system. The SIM
Kroger Supplier Information Management System (SIM) Training Documentation Introduction All Kroger suppliers are required to register in Kroger s new Supplier Information Management (SIM) system. The SIM
Introduction. Logging in. WebQuarantine User Guide
 Introduction modusgate s WebQuarantine is a web application that allows you to access and manage your email quarantine. This user guide walks you through the tasks of managing your emails using the WebQuarantine
Introduction modusgate s WebQuarantine is a web application that allows you to access and manage your email quarantine. This user guide walks you through the tasks of managing your emails using the WebQuarantine
NORTH AMERICAN SECURITIES ADMINISTRATORS ASSOCIATION Cybersecurity Checklist for Investment Advisers
 Identify Protect Detect Respond Recover Identify: Risk Assessments & Management 1. Risk assessments are conducted frequently (e.g. annually, quarterly). 2. Cybersecurity is included in the risk assessment.
Identify Protect Detect Respond Recover Identify: Risk Assessments & Management 1. Risk assessments are conducted frequently (e.g. annually, quarterly). 2. Cybersecurity is included in the risk assessment.
Quick recap on ing Security Recap on where to find things on Belvidere website & a look at the Belvidere Facebook page
 Workshop #7 Email Security Previous workshops 1. Introduction 2. Smart phones & Tablets 3. All about WatsApp 4. More on WatsApp 5. Surfing the Internet 6. Emailing Quick recap on Emailing Email Security
Workshop #7 Email Security Previous workshops 1. Introduction 2. Smart phones & Tablets 3. All about WatsApp 4. More on WatsApp 5. Surfing the Internet 6. Emailing Quick recap on Emailing Email Security
ebanking User Guide ebanking echeck edelivery Mobile Banking & Deposit We Make Banking About You
 ebanking User Guide ebanking echeck edelivery Mobile Banking & Deposit Member FDIC We Make Banking About You 1-800-288-2229 www.abbybank.com 1 Account Access To log into your ebanking account, go to www.abbybank.com.
ebanking User Guide ebanking echeck edelivery Mobile Banking & Deposit Member FDIC We Make Banking About You 1-800-288-2229 www.abbybank.com 1 Account Access To log into your ebanking account, go to www.abbybank.com.
How to Claim Your GIAC Digital Badge
 How to Claim Your GIAC Digital Badge 2019 2. CONTENTS Page # Information 3-8 9-13 Utilizing Your Email Invitation To Claim Your GIAC Digital Badge Claiming Your Digital Badge From Your SANS Account 14-16
How to Claim Your GIAC Digital Badge 2019 2. CONTENTS Page # Information 3-8 9-13 Utilizing Your Email Invitation To Claim Your GIAC Digital Badge Claiming Your Digital Badge From Your SANS Account 14-16
Oracle Eloqua Legacy Authenticated Microsites and Contact Users. Configuration Guide
 Oracle Eloqua Legacy Authenticated Microsites and Contact Users Configuration Guide 2019 Oracle Corporation. All rights reserved 04-Jan-2019 Contents 1 Authenticated microsites 3 2 Creating authenticated
Oracle Eloqua Legacy Authenticated Microsites and Contact Users Configuration Guide 2019 Oracle Corporation. All rights reserved 04-Jan-2019 Contents 1 Authenticated microsites 3 2 Creating authenticated
TSSA PORTAL TRAINING GUIDE
 TSSA PORTAL TRAINING GUIDE Owner Processes Page 0 Table of Contents Contents 1.1 Redeem Invitation... 2 1.2 Reset Password... 5 1.3 Manage Profile... 7 2.1 View Your Record(s) of Inspection... 8 2.2 Validate
TSSA PORTAL TRAINING GUIDE Owner Processes Page 0 Table of Contents Contents 1.1 Redeem Invitation... 2 1.2 Reset Password... 5 1.3 Manage Profile... 7 2.1 View Your Record(s) of Inspection... 8 2.2 Validate
Nuclear Fuel Complex Recruitment Application User Manual
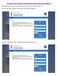 Nuclear Fuel Complex Recruitment Application User Manual The application is best viewed in Google Chrome Version 66.0.3359.139 Browse the NFC website, following screen will be displayed. For New Applicant,
Nuclear Fuel Complex Recruitment Application User Manual The application is best viewed in Google Chrome Version 66.0.3359.139 Browse the NFC website, following screen will be displayed. For New Applicant,
System Setup. Accessing the Administration Interface CHAPTER
 CHAPTER 3 The system can be configured through the web interface to provide the networking configuration for the appliance and other system settings that are important such as time and SSL certificate.
CHAPTER 3 The system can be configured through the web interface to provide the networking configuration for the appliance and other system settings that are important such as time and SSL certificate.
Auto calculate VAT in opportunities, quotes, orders and invoices in Microsoft Dynamics 365 DYNAMIC VAT IMPORT GUIDE. Version 1.0.
 DYNAMIC VAT Auto calculate VAT in opportunities, quotes, orders and invoices in Microsoft Dynamics 365 IMPORT GUIDE Version 1.0 Developed By Table of Contents Solution Import... 1 Registration... 6 Configuration...
DYNAMIC VAT Auto calculate VAT in opportunities, quotes, orders and invoices in Microsoft Dynamics 365 IMPORT GUIDE Version 1.0 Developed By Table of Contents Solution Import... 1 Registration... 6 Configuration...
IMPORTANT SECURITY CHANGES LOGGING ON. We are replacing the existing enhanced authentication.
 IMPORTANT SECURITY CHANGES We are replacing the existing enhanced authentication. All users will be required to reenroll in enhanced authentication. When you are prompted to reenroll, you will be asked
IMPORTANT SECURITY CHANGES We are replacing the existing enhanced authentication. All users will be required to reenroll in enhanced authentication. When you are prompted to reenroll, you will be asked
MYCIBSE USER GUIDE. Contents
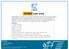 MYCIBSE USER GUIDE CIBSE upgraded its IT systems on 26th July 2016 to improve core customer functions and increase efficiency and effectiveness. As part of this upgrade members and customers that were
MYCIBSE USER GUIDE CIBSE upgraded its IT systems on 26th July 2016 to improve core customer functions and increase efficiency and effectiveness. As part of this upgrade members and customers that were
Comptia RC CompTIA Security+ Recertification Exam. For More Information Visit link below: Version = Product
 CERTSGRADE High Grade and Valuable Preparation Stuff Comptia RC0-501 CompTIA Security+ Recertification Exam For More Information Visit link below: http://www.certsgrade.com/ Version = Product Question:
CERTSGRADE High Grade and Valuable Preparation Stuff Comptia RC0-501 CompTIA Security+ Recertification Exam For More Information Visit link below: http://www.certsgrade.com/ Version = Product Question:
3.5 SECURITY. How can you reduce the risk of getting a virus?
 3.5 SECURITY 3.5.4 MALWARE WHAT IS MALWARE? Malware, short for malicious software, is any software used to disrupt the computer s operation, gather sensitive information without your knowledge, or gain
3.5 SECURITY 3.5.4 MALWARE WHAT IS MALWARE? Malware, short for malicious software, is any software used to disrupt the computer s operation, gather sensitive information without your knowledge, or gain
Maria Hishikawa MSIX Technical Lead Sarah Storms MSIX Contractor Security
 Migrant Student Information Exchange (MSIX) Security, Privacy and Account Management Webinar Deloitte Consulting LLP. February 22, 2018 Maria Hishikawa MSIX Technical Lead Sarah Storms MSIX Contractor
Migrant Student Information Exchange (MSIX) Security, Privacy and Account Management Webinar Deloitte Consulting LLP. February 22, 2018 Maria Hishikawa MSIX Technical Lead Sarah Storms MSIX Contractor
CompTIA Security+ Malware. Threats and Vulnerabilities Vulnerability Management
 CompTIA Security+ Lecture Six Threats and Vulnerabilities Vulnerability Management Copyright 2011 - VTC Malware Malicious code refers to software threats to network and systems, including viruses, Trojan
CompTIA Security+ Lecture Six Threats and Vulnerabilities Vulnerability Management Copyright 2011 - VTC Malware Malicious code refers to software threats to network and systems, including viruses, Trojan
TABLE OF CONTENTS. Select the appropriate link below for the action you wish to perform. Log In. Forgot Password. Registering for Additional Services
 TABLE OF CONTENTS Select the appropriate link below for the action you wish to perform. Log In Forgot Password Registering for Additional Services Change Password Make a One-Time Payment Home Page Show
TABLE OF CONTENTS Select the appropriate link below for the action you wish to perform. Log In Forgot Password Registering for Additional Services Change Password Make a One-Time Payment Home Page Show
Computer Forensics: Investigating Network Intrusions and Cyber Crime, 2nd Edition. Chapter 3 Investigating Web Attacks
 Computer Forensics: Investigating Network Intrusions and Cyber Crime, 2nd Edition Chapter 3 Investigating Web Attacks Objectives After completing this chapter, you should be able to: Recognize the indications
Computer Forensics: Investigating Network Intrusions and Cyber Crime, 2nd Edition Chapter 3 Investigating Web Attacks Objectives After completing this chapter, you should be able to: Recognize the indications
lyndaclassroom Getting Started Guide
 lyndaclassroom Getting Started Guide This document explains Why lyndaclassroom might be right for you and your students How to register as an approved educator with lynda.com How to set up and submit your
lyndaclassroom Getting Started Guide This document explains Why lyndaclassroom might be right for you and your students How to register as an approved educator with lynda.com How to set up and submit your
10/11/2016 WHYWE RE HERE AGENDA. What It Means For Your Future. Threat Landscape. Social Engineering. - Phishing. - Pretexting.
 2 What It Means For Your Future Managed IT & Cybersecurity. DoneBetter. AGENDA Threat Landscape Social Engineering - Phishing - Pretexting Targeting Process Attackers Take The Easiest Route Brilliance
2 What It Means For Your Future Managed IT & Cybersecurity. DoneBetter. AGENDA Threat Landscape Social Engineering - Phishing - Pretexting Targeting Process Attackers Take The Easiest Route Brilliance
Electrolux Small Appliance Reseller FAQs
 Electrolux Small Appliance Reseller FAQs Why is Electrolux instituting a Reseller Authorization Program? Electrolux takes our brand and market position very seriously and desires to protect and promote
Electrolux Small Appliance Reseller FAQs Why is Electrolux instituting a Reseller Authorization Program? Electrolux takes our brand and market position very seriously and desires to protect and promote
CSCDomainManager Frequently Asked Questions
 CSCDomainManager Frequently Asked Questions What are the benefits of migrating to CSCDomainManager? CSCDomainManager SM provides you with the ability to: Manage all your digital assets through one portal,
CSCDomainManager Frequently Asked Questions What are the benefits of migrating to CSCDomainManager? CSCDomainManager SM provides you with the ability to: Manage all your digital assets through one portal,
Phishing Activity Trends
 Phishing Activity Trends Report for the Month of September, 2007 Summarization of September Report Findings The total number of unique phishing reports submitted to APWG in September 2007 was 38,514, an
Phishing Activity Trends Report for the Month of September, 2007 Summarization of September Report Findings The total number of unique phishing reports submitted to APWG in September 2007 was 38,514, an
Privacy Policy. Effective as of October 5, 2017
 Effective as of October 5, 2017 Privacy Policy ClassApps LLC ( ClassApps, we, us, or the Company ) is committed to protecting the privacy of individuals who visit the Company s Web sites ( Visitors ),
Effective as of October 5, 2017 Privacy Policy ClassApps LLC ( ClassApps, we, us, or the Company ) is committed to protecting the privacy of individuals who visit the Company s Web sites ( Visitors ),
Understanding RDAP and the Role it can Play in RDDS Policy. ICANN October 2018
 1 Understanding RDAP and the Role it can Play in RDDS Policy ICANN 63 22 October 2018 2 Agenda Introduction RDAP Implementation Status in gtlds RDAP: Mechanism and Policy Authentication and RDAP Registrar
1 Understanding RDAP and the Role it can Play in RDDS Policy ICANN 63 22 October 2018 2 Agenda Introduction RDAP Implementation Status in gtlds RDAP: Mechanism and Policy Authentication and RDAP Registrar
Access to RTE s Information System by software certificates under Microsoft Windows 7
 by software certificates under Microsoft Windows 7 PKI User guide Version 4, 01/01/2017 Programmes & SI (PSI) TOUR MARCHAND 41 RUE BERTHELOT - 92411 COURBEVOIE CEDEX TEL : 01.78.66.50.00 - FAX : 01.78.66.50.64
by software certificates under Microsoft Windows 7 PKI User guide Version 4, 01/01/2017 Programmes & SI (PSI) TOUR MARCHAND 41 RUE BERTHELOT - 92411 COURBEVOIE CEDEX TEL : 01.78.66.50.00 - FAX : 01.78.66.50.64
Phishing: When is the Enemy
 Phishing: When E-mail is the Enemy Phishing, once only a consumer worry, is creating headaches for e-mail administrators as businesses become the next target. CONTENTS Understanding the Enemy 2 Three Things
Phishing: When E-mail is the Enemy Phishing, once only a consumer worry, is creating headaches for e-mail administrators as businesses become the next target. CONTENTS Understanding the Enemy 2 Three Things
The Shortcut Guide To. Protecting Against Web Application Threats Using SSL. Dan Sullivan
 tm The Shortcut Guide To Protecting Against Web Application Threats Using SSL Chapter 3: Planning, Deploying, and Maintaining SSL Certificates to Protect Against Inf ormation Loss and Build Customer Trust...
tm The Shortcut Guide To Protecting Against Web Application Threats Using SSL Chapter 3: Planning, Deploying, and Maintaining SSL Certificates to Protect Against Inf ormation Loss and Build Customer Trust...
TABLE OF CONTENTS. Select the appropriate link below for the action you wish to perform. Log In. Forgot Password. Registering for Additional Services
 TABLE OF CONTENTS Select the appropriate link below for the action you wish to perform. Log In Forgot Password Registering for Additional Services Change Password Make a One-Time Payment Home Page Show
TABLE OF CONTENTS Select the appropriate link below for the action you wish to perform. Log In Forgot Password Registering for Additional Services Change Password Make a One-Time Payment Home Page Show
Help file for IRDAI Corporate Agents Registration Portal
 Help file for IRDAI Corporate Agents Registration Portal Submitted By Trade Globe - Ground Floor, J.B. Nagar Andheri-Kurla Road, Andheri (E) Mumbai 400 059 www.nseit.com 10th Feb, 2016 Contents Tips...
Help file for IRDAI Corporate Agents Registration Portal Submitted By Trade Globe - Ground Floor, J.B. Nagar Andheri-Kurla Road, Andheri (E) Mumbai 400 059 www.nseit.com 10th Feb, 2016 Contents Tips...
Security and Privacy
 E-mail Security and Privacy Department of Computer Science Montclair State University Course : CMPT 320 Internet/Intranet Security Semester : Fall 2008 Student Instructor : Alex Chen : Dr. Stefan Robila
E-mail Security and Privacy Department of Computer Science Montclair State University Course : CMPT 320 Internet/Intranet Security Semester : Fall 2008 Student Instructor : Alex Chen : Dr. Stefan Robila
Registrar Data Form Instructions. Please complete using word processing software; then submit completed, typed form.
 Registrar Data Form Instructions Please complete using word processing software; then submit completed, typed form. Registrar Information Phone/Fax Numbers: Please make sure that phone and fax numbers
Registrar Data Form Instructions Please complete using word processing software; then submit completed, typed form. Registrar Information Phone/Fax Numbers: Please make sure that phone and fax numbers
Office Hours: Monday thru Friday 8:00 am 5:00 pm General Inquiries: ext. 10
 TABLE OF CONTENTS Select the appropriate link below for the action you wish to perform. 1. LOG IN 2. FORGOT PASSWORD 3. MANAGE YOUR ACCOUNT 4. CHANGE PASSWORD 5. MAKE A ONE-TIME PAYMENT 6. HOME PAGE 7.
TABLE OF CONTENTS Select the appropriate link below for the action you wish to perform. 1. LOG IN 2. FORGOT PASSWORD 3. MANAGE YOUR ACCOUNT 4. CHANGE PASSWORD 5. MAKE A ONE-TIME PAYMENT 6. HOME PAGE 7.
Online Security: Breaking Down the Anatomy of a Phishing
 Online Security: Breaking Down the Anatomy of a Phishing Email In today s world where everyone s information is online, phishing is one of the most popular and devastating online attacks, because you can
Online Security: Breaking Down the Anatomy of a Phishing Email In today s world where everyone s information is online, phishing is one of the most popular and devastating online attacks, because you can
STEPS FOR CANDIDATE FOR SCHEDULING ITB EXAM
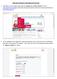 STEPS FOR CANDIDATE FOR SCHEDULING ITB EXAM 1. Candidates can start registering through the Register for an ITB Certification link on www.pearsonvue.com/itb or directly by clicking on Enrollment link of
STEPS FOR CANDIDATE FOR SCHEDULING ITB EXAM 1. Candidates can start registering through the Register for an ITB Certification link on www.pearsonvue.com/itb or directly by clicking on Enrollment link of
Yes. [No Response] General Questions
![Yes. [No Response] General Questions Yes. [No Response] General Questions](/thumbs/88/116458977.jpg) General Questions Q1. Do you agree that the proposals to refine the WHOIS opt-out eligibility and to provide a framework for registrar privacy services meets the policy objectives set out in the consultation
General Questions Q1. Do you agree that the proposals to refine the WHOIS opt-out eligibility and to provide a framework for registrar privacy services meets the policy objectives set out in the consultation
Domain Name Hijacking. Security and Stability Advisory Committee Luxembourg 12 July 2005
 Domain Name Hijacking Security and Stability Advisory Committee Luxembourg 12 July 2005 1 Speakers Steve Crocker, Chair Bruce Tonkin, CTO MelbourneIT Rodney Joffe, Chairman & CTO, UltraDNS Ram Mohan, CTO
Domain Name Hijacking Security and Stability Advisory Committee Luxembourg 12 July 2005 1 Speakers Steve Crocker, Chair Bruce Tonkin, CTO MelbourneIT Rodney Joffe, Chairman & CTO, UltraDNS Ram Mohan, CTO
Individuals Authorized Access to CMS Computer Services (IACS) Request Access to a CMS Application Quick Reference Guide
 Individuals Authorized Access to CMS Computer Services (IACS) Request Access to a CMS Application Quick Reference Guide This Quick Reference Guide provides step-by-step instructions to access the IACS
Individuals Authorized Access to CMS Computer Services (IACS) Request Access to a CMS Application Quick Reference Guide This Quick Reference Guide provides step-by-step instructions to access the IACS
ArcGIS Enterprise Security: Advanced. Gregory Ponto & Jeff Smith
 Enterprise Security: Advanced Gregory Ponto & Jeff Smith Agenda Focus: Security best practices for Enterprise Server Portal for 10.5.x Features Strongly Recommend: Knowledge of Server and Portal for Security
Enterprise Security: Advanced Gregory Ponto & Jeff Smith Agenda Focus: Security best practices for Enterprise Server Portal for 10.5.x Features Strongly Recommend: Knowledge of Server and Portal for Security
Locking down a Hitachi ID Suite server
 Locking down a Hitachi ID Suite server 2016 Hitachi ID Systems, Inc. All rights reserved. Organizations deploying Hitachi ID Identity and Access Management Suite need to understand how to secure its runtime
Locking down a Hitachi ID Suite server 2016 Hitachi ID Systems, Inc. All rights reserved. Organizations deploying Hitachi ID Identity and Access Management Suite need to understand how to secure its runtime
Techniques for detecting zero day phishing websites
 Graduate Theses and Dissertations Graduate College 2009 Techniques for detecting zero day phishing websites Michael Blasi Iowa State University Follow this and additional works at: http://lib.dr.iastate.edu/etd
Graduate Theses and Dissertations Graduate College 2009 Techniques for detecting zero day phishing websites Michael Blasi Iowa State University Follow this and additional works at: http://lib.dr.iastate.edu/etd
COACH.COM - PRIVACY POLICY
 Coach, Inc. (the "Company") and our brands value your trust. We collect certain information when you visit our U.S. site www.coach.com (the Site ), in order to improve your shopping experience and allow
Coach, Inc. (the "Company") and our brands value your trust. We collect certain information when you visit our U.S. site www.coach.com (the Site ), in order to improve your shopping experience and allow
