CISNTWK-492e. Microsoft Exchange Server 2003 Administration. Chapter Eight Managing Routing and Internet Connectivity
|
|
|
- Magnus James
- 5 years ago
- Views:
Transcription
1 CISNTWK-492e Microsoft Exchange Server 2003 Administration Chapter Eight Managing Routing and Internet Connectivity 1
2 Objectives Understand SMTP and how it works Understand how Exchange Server 2003 makes use of SMTP Understand how message routing works within an Exchange Server 2003 infrastructure Describe the link state algorithm and how Exchange Server 2003 makes use of it Describe how external messaging is handled within Exchange Server
3 Managing Routing and Internet Connectivity Message routing: process of sending a message to an intended recipient Site: logical grouping of servers using permanent, high-bandwidth connectivity Sites define three boundaries: Single-hop routing, administrative unit, namespace 3
4 Managing Routing and Internet Connectivity Exchange Server 2003 separates boundaries Single-hop routing is defined by a routing group Administration unit is defined by the administrative group Namespace hierarchy exists in Active Directory as a domain 4
5 The Simple Mail Transfer Protocol Simple Mail Transfer Protocol (SMTP) Used to send and receive Designed to work on top of TCP/IP Primary messaging protocol used by Exchange Server 5
6 The Simple Mail Transfer Protocol Protocol: set of rules defining interaction between computers SMTP is made up of several different protocols RFC 2821 specifies interaction between two servers RFC 2822 specifies message header (envelope) elements 6
7 7
8 8
9 The Simple Mail Transfer Protocol (continued) Multipurpose Internet Mail Extension (MIME) Describes a message as consisting of many parts Each part could be formatted differently Example: Parts may be audio, video, text SMTP handles only textual (not binary) data Solved by converting binary data to text-like format Conversion process is called uuencode MIME adds six headers to RFC 2822 envelope Three mandatory and three optional headers 9
10 10
11 11
12 12
13 The Simple Mail Transfer Protocol How MIME works (continued) Concatenates all of the attachments Places message headers between attachments Defines content in attachment (plain text, HTML, etc.) Defines how content t is encoded d for transfer 13
14 The Simple Mail Transfer Protocol (continued) Content type consists of two divisions Top-level media type and corresponding subtype Other types may be specified for proprietary formats Multipart content type Defines message structure with more than one part Each part has its own headers 14
15 15
16 SMTP and Exchange Server 2003 Exchange Server 2003 and SMTP Uses SMTP service provided by Windows 2000/2003 SMTP is the native transport protocol Windows SMTP service Component of Internet Information Services (IIS) Runs as part of Inetinfo.exe 16
17 SMTP and Exchange Server 2003 (continued) Six ways Exchange Server 2003 enhances SMTP service SMTP management is removed from IIS Manager and added to Exchange System Manager Exchange added d support for link state t information Better queuing for improved message delivery, tracking Message categorizer communicates with global catalog Installable File System (IFS) store driver provides access to Exchange store Mail folder moved to \exchsrvr\mailroot\vsi \ i1\ 1\queue 17
18 SMTP and Exchange Server 2003 (continued) Active Directory stores Exchange Server modifications You can configure multiple virtual SMTP servers on each Exchange Server
19 Activity 8-1: Creating SMTP Virtual Servers Time Required: 10 to 20 minutes Objective: Create an SMTP virtual server within Exchange Server 2003 to allow the delivery of messages via SMTP to external SMTP servers Description: Create an additional SMTP virtual server on the back-end server. Reasons for creating an additional SMTP virtual server include adding additional fault tolerance to your environment and allowing your organization to host multiple default domains. 19
20 20
21 21
22 Activity 8-2: Configuring SMTP Virtual Server Options Time Required: 10 to 20 minutes Objective: Configure your SMTP virtual server to restrict access to it Description: By default, virtual servers are accessible to all IP addresses, which can present a security risk that could allow your server to be misused. To control use of a virtual server, you can grant or deny access by IP address, subnet, or domain. 22
23 23
24 Understanding Message Routing Underlying message routing subsystem functions Breaks down message processing into parts Key to understanding the big routing picture Messages delivered over the least expensive route Determine route by adding costs configured on routing connectors If the route with the lowest cost is down, the next least expensive route is used 24
25 Routing Groups and Connectors Routing group in an Exchange organization Consists of well-connected Exchange servers Full-time, full mesh connectivity guaranteed Within a routing group, special connectivity is not needed Default eautrouting gconfiguration guato for Exchange geservers Single routing group Named after administrator group Manually add additional routing groups and servers Messages may be routed to other locations External systems Other routing groups in an Exchange organization 25
26 Routing Groups and Connectors (continued) Reasons for configuring alternate routing group Limited capacity/availability of network connections Policy limits or restrictions on the size of messages Need for scheduling the flow of 26
27 Routing Groups and Connectors (continued) Exchange uses one of four connectors for alternate groups: Routing group connector SMTP connector X.400 connector Specialty connector (GroupWise or Lotus Notes) 27
28 Activity 8-3: Installing a Routing Group Connector Time Required: 10 to 20 minutes Objective: Install a routing ggroup connector to provide connectivity between two routing groups Description: Install a routing group connector between two routing groups. The routing group connector will be installed on each bridgehead d server within their respective routing group, and configured appropriately to allow connectivity. 28
29 29
30 30
31 Other Transport Methods Three methods of message flow SMTP service Internet or routing group connector Store submission Microsoft Outlook MAPI client or an OWA client MTA (Message Transfer Agent) Uses X.400 connectivity High level descriptions of SMTP message flow: Message first sent to NTFS queue Message then delivered to precategorization queue Message awaits processing by categorizer 31
32 32
33 Other Transport Methods (continued) Messages submitted via store submission or MTA Messages dropped into Exchange store driver Store driver passes message to precategorization queue Message awaits processing by categorizer Message categorizer: collection of event sinks Event sink: script run against messages Activities performed by message categorizer Distribution list expansion conducted Attributes from Active Directory retrieved Message placed in postcategorization queue 33
34 Activity 8-4: Configuring Routing Group Connector Delivery Options Time Required: 10 to 20 minutes Objective: Configure delivery options to deliver large messages during nonpeak hours Description: Configure the delivery options for the new routing group connector. Delivery options control when messages are sent through the connector. One of the key features is the ability to set connection schedules for all messages or messages of different size. 34
35 35
36 Link State Algorithm Routing engine consulted for optimal routes If routing a message internal to the organization DNS query determines address of destination server SMTP service directly delivers the message 36
37 Link State Algorithm If routing a message external to the organization Routing engine determines optimal routes Routing engine utilizes link state algorithm Link state algorithm is the basis for Open Shortest Path First protocol (OSPF) 37
38 Routing Group Master Routing group master is configured in each group Receives link state information Propagates information internally Link state algorithm operates over TCP port 691 Propagates information externally Uses bridgehead server (may be dually configured) Link state algorithm operates over TCP port 25 Maintains i link state t information 38
39 Routing Group Master Two states available for a link: up or down Bridgehead server monitors down links 39
40 Link State Information Link state information held in memory, not disk Other routing ggroup masters may replicate link state Role of Active Directory Routing group information is held in naming partition Definitions of connectors and costs are also held 40
41 Link State Information Link state algorithm references connector by its GUID Conditions where link state propagation has improved Where no alternative path exists Where connections are intermittent or oscillating 41
42 How Exchange Makes Use of Link State Information Illustration with Importers of America: Routing group connects five cities Each site is represented as a distinct routing group Connectors are established among groups Costs are depicted Routing costs play a key role in optimizing message routing Connector with the lowest cost is preferred If the lowest cost connector is down, choose the next lowest 42
43 43
44 How Exchange Makes Use of Link State Information (continued) Scenario when all connections are up: Toronto server sends message to Rio de Janeiro Intermediate hop to San Francisco Lowest cost route: Toronto-San Francisco-Rio 44
45 How Exchange Makes Use of Link State Information (continued) Scenario with link failure between SF and Rio: After three attempts, SF server marks connection down SF server updates link state over TCP port 691 Routing master updates other servers in SF group SF server recalculates alternate route, notifies Toronto Toronto server uses alternate (the direct) path to Rio 45
46 Activity 8-5: Setting Routing Costs for a Connector Time Required: 10 to 20 minutes Objective: Configure routing costs for a connector Description: Configure the routing cost for a connector. Configuring multiple connectors with the same routing cost tells Exchange Server 2003 to distribute ib t the load as evenly as possible among connectors. 46
47 Activity 8-6: Configuring the Retry Intervals for SMTP Virtual Servers Time Required: 10 to 20 minutes Objective: Configure the retry interval for an SMTP virtual server Description: Configure the retry interval on your SMTP virtual server. In Exchange Server 2003, if a message cannot be delivered on the first attempt, t Exchange Server 2003 tries to send it again after a specified time. 47
48 48
49 Using Link State Information to Route Externally External routing is similar to internal routing Evaluate the connector with an address space close to the destination Evaluate costs associated with using those connectors 49
50 Using Link State Information to Route Externally Scenario with three Internet connectors (1) routes addresses based on *.br at a cost of 10 (2) routes addresses based on *.net at a cost of 20 (3) routes all other addresses at a cost of 10 Goal: route to ryan@importsofamerica.br 50
51 51
52 Using Link State Information to Route Externally (continued) Routing process is performed by Exchange Server 2003 Look for connector with similar il address space Determine that connector for *.br is a close match Route message through SMTP connector in Sao Paolo Message is then delivered using Sao Paolo connector 52
53 Using Link State Information to Route Externally (continued) Lowest cost connector is preferred Routing does not fail over to a connector with a less specific address space Example: connector serving *.br does not fail over to * 53
54 Activity 8-7: Installing an SMTP Connector Time Required: 10 to 20 minutes Objective: Provide some perspective on how Exchange Server 2003 routes external SMTP mail; install and configure an SMTP connector. Description: Install an SMTP connector for your Exchange Server 2003 organization. You must define which local bridgehead servers the connector will use as well as the connector scope, message routing technique, and address space. SMTP virtual servers act as local bridgehead servers for SMTP connectors. 54
55 55
56 Activity 8-8: Configuring Delivery Options for SMTP Time Required: 10 to 20 minutes Objective: Configure the delivery options for an SMTP connector Description: Configure the delivery options for an SMTP connector. SMTP connectors have delivery options that determine when messages are sent tthrough hthe connector as well as whether messages are queued for remote delivery. 56
57 57
58 Summary SMTP protocol suite includes RFC 2821 and 2822 RFC 2821 defines interaction between servers RFC 2822 covers the basic elements of a message MIME extends headers of basic SMTP messages SMTP messaging is implemented with virtual servers 58
59 Summary (continued) Routing group is a collection of well-connected servers Alternate routing ggroups handle limited capacity/availability Four connector types: SMTP, routing group, X.400, specialty connectors Link state routing propagates information in near real time Servers use TCP port 691 for internal communication of link state 59
60 Summary (continued) Servers use TCP port 25 for external communication of link state Link state routing improved when no alternative paths exist Link state routing also improved for intermittent connections Routing engine selects connectors with lowest cost sent externally through connector with closest address space 60
Electronic Mail
 Email Electronic Mail Electronic mail paradigm Most heavily used application on any network Electronic version of paper-based office memo Quick, low-overhead written communication Dates back to time-sharing
Email Electronic Mail Electronic mail paradigm Most heavily used application on any network Electronic version of paper-based office memo Quick, low-overhead written communication Dates back to time-sharing
Electronic Mail. Prof. Indranil Sen Gupta. Professor, Dept. of Computer Science & Engineering Indian Institute of Technology Kharagpur
 Electronic Mail Prof. Indranil Sen Gupta Professor, Dept. of Computer Science & Engineering Indian Institute of Technology Kharagpur 1 Introduction Most heavily used application on the Internet. Simple
Electronic Mail Prof. Indranil Sen Gupta Professor, Dept. of Computer Science & Engineering Indian Institute of Technology Kharagpur 1 Introduction Most heavily used application on the Internet. Simple
Designing an Exchange 2000/2003 Routing Group Connector Topology
 Pg. 1 Designing an Exchange 2000/2003 Routing Group Connector Topology By: Craig Borysowich Chief Technology Architect Imagination Edge Inc. www.imedge.net Version 3.7 BACKGROUND Large Exchange 5.5 environments
Pg. 1 Designing an Exchange 2000/2003 Routing Group Connector Topology By: Craig Borysowich Chief Technology Architect Imagination Edge Inc. www.imedge.net Version 3.7 BACKGROUND Large Exchange 5.5 environments
User Manual. Admin Report Kit for Exchange Server
 User Manual Admin Report Kit for Exchange Server Table of Contents 1 About ARKES-Admin Report Kit for Exchange Server 1 1.1 System requirements 2 1.2 How to activate the software? 3 1.3 ARKES Reports Primer
User Manual Admin Report Kit for Exchange Server Table of Contents 1 About ARKES-Admin Report Kit for Exchange Server 1 1.1 System requirements 2 1.2 How to activate the software? 3 1.3 ARKES Reports Primer
Owner of the content within this article is Written by Marc Grote
 Owner of the content within this article is www.msexchange.org Written by Marc Grote www.it-training-grote.de Exchange 2003 Mailflow Part I Written by Marc Grote - mailto:grotem@it-training-grote.de Abstract
Owner of the content within this article is www.msexchange.org Written by Marc Grote www.it-training-grote.de Exchange 2003 Mailflow Part I Written by Marc Grote - mailto:grotem@it-training-grote.de Abstract
Electronic Mail (SMTP)
 Electronic Mail (SMTP) Nowadays email is more popular than the paper letters called snail-mails. It is a form of network communication. Some of the other forms of network communication being voice-over-internet,
Electronic Mail (SMTP) Nowadays email is more popular than the paper letters called snail-mails. It is a form of network communication. Some of the other forms of network communication being voice-over-internet,
Electronic Mail Paradigm
 Electronic Mail Paradigm E-mail uses the client-server model. E-mail was designed as an electronic extension of the old paper office memo. - A quick and easy means of low-overhead written communication.
Electronic Mail Paradigm E-mail uses the client-server model. E-mail was designed as an electronic extension of the old paper office memo. - A quick and easy means of low-overhead written communication.
FTP. FTP offers many facilities :
 FTP Given a reliable end-to-end trasport protocol like TCP, File Transfer might seem trivial. But, the details authorization, representation among heterogeneous machines make the protocol complex. FTP
FTP Given a reliable end-to-end trasport protocol like TCP, File Transfer might seem trivial. But, the details authorization, representation among heterogeneous machines make the protocol complex. FTP
FTP,HTTP. By Nidhi Jindal
 APPLICATION LAYER: SMTP, POP, IMAP, FTP,HTTP By Nidhi Jindal. MESSAGE TRANSFER AGENT: SMTP The actual mail transfer requires message transfer agents (MTAs). The protocol that defines the MTA client and
APPLICATION LAYER: SMTP, POP, IMAP, FTP,HTTP By Nidhi Jindal. MESSAGE TRANSFER AGENT: SMTP The actual mail transfer requires message transfer agents (MTAs). The protocol that defines the MTA client and
Envelope Journaling for Microsoft Exchange 2003 Version 1.0
 Barracuda Message Archiver Organizations using Microsoft Exchange 2003 can take advantage of its envelope journaling feature to send all messages along with all recipient information directly to the Barracuda
Barracuda Message Archiver Organizations using Microsoft Exchange 2003 can take advantage of its envelope journaling feature to send all messages along with all recipient information directly to the Barracuda
is still the most used Internet app. According to some studies around 85% of Internet users still use for communication.
 1 E-mail is still the most used Internet app. According to some studies around 85% of Internet users still use e-mail for communication. Electronic mail is a method to exchange digital messages from a
1 E-mail is still the most used Internet app. According to some studies around 85% of Internet users still use e-mail for communication. Electronic mail is a method to exchange digital messages from a
Computer Network 1 1
 Computer Network 1 1 Chapter 10: Application Layer Advanced Principal Concepts Samples and Techniques Foundation Summary Question and Answer 2 Outline Application Layer There is a need for support protocols,
Computer Network 1 1 Chapter 10: Application Layer Advanced Principal Concepts Samples and Techniques Foundation Summary Question and Answer 2 Outline Application Layer There is a need for support protocols,
APPLICATION LAYER APPLICATION LAYER : DNS, HTTP, , SMTP, Telnet, FTP, Security-PGP-SSH.
 APPLICATION LAYER : DNS, HTTP, E-mail, SMTP, Telnet, FTP, Security-PGP-SSH. To identify an entity, the Internet used the IP address, which uniquely identifies the connection of a host to the Internet.
APPLICATION LAYER : DNS, HTTP, E-mail, SMTP, Telnet, FTP, Security-PGP-SSH. To identify an entity, the Internet used the IP address, which uniquely identifies the connection of a host to the Internet.
5047 : Introduction to Installing and Managing Microsoft Exchange Server 2007
 5047 : Introduction to Installing and Managing Microsoft Exchange Server 2007 Introduction Elements of this syllabus are subject to change. At the end of this three-day course, students who are new to
5047 : Introduction to Installing and Managing Microsoft Exchange Server 2007 Introduction Elements of this syllabus are subject to change. At the end of this three-day course, students who are new to
INTERNET & WORLD WIDE WEB (UNIT-1) MECHANISM OF INTERNET
 INTERNET & WORLD WIDE WEB (UNIT-1) MECHANISM OF INTERNET 1. INTRODUCTION Hello friends are topic is Internet and World Wide Web the most popular services of our topic is social networking and online shopping
INTERNET & WORLD WIDE WEB (UNIT-1) MECHANISM OF INTERNET 1. INTRODUCTION Hello friends are topic is Internet and World Wide Web the most popular services of our topic is social networking and online shopping
Simple Network Management Protocol (SNMP)
 Announcements Project #5 extended until Dec. 10 Reading: 7.3, start 7.4 Midterm #2 last day to request re-grades Th in class HW#2 (due Tuesday Dec. 7) 1 Simple Network Management Protocol (SNMP) Managed
Announcements Project #5 extended until Dec. 10 Reading: 7.3, start 7.4 Midterm #2 last day to request re-grades Th in class HW#2 (due Tuesday Dec. 7) 1 Simple Network Management Protocol (SNMP) Managed
Objectives CINS/F1-01
 Email Security (1) Objectives Understand how e-mail systems operate over networks. Classify the threats to the security of e-mail. Study how S/MIME and PGP can be used to add security to e-mail systems.
Email Security (1) Objectives Understand how e-mail systems operate over networks. Classify the threats to the security of e-mail. Study how S/MIME and PGP can be used to add security to e-mail systems.
MailEnable System Overview
 MailEnable System Overview MailEnable Messaging Services for Microsoft Windows NT/2000/2003 MailEnable Pty. Ltd. 59 Murrumbeena Road Murrumbeena VIC 3163 Australia t: +61 3 9569 0772 f: +61 3 9530 4066
MailEnable System Overview MailEnable Messaging Services for Microsoft Windows NT/2000/2003 MailEnable Pty. Ltd. 59 Murrumbeena Road Murrumbeena VIC 3163 Australia t: +61 3 9569 0772 f: +61 3 9530 4066
System: Basic Functionality
 E-mail System: Basic Functionality E-mail systems support five basic functions: Composition: Creating messages Transfer: Moving messages from the originator to the recipient E-mail transfer is a connection-oriented
E-mail System: Basic Functionality E-mail systems support five basic functions: Composition: Creating messages Transfer: Moving messages from the originator to the recipient E-mail transfer is a connection-oriented
Chapter 7 (Week 13) The Application Layer ANDREW S. TANENBAUM COMPUTER NETWORKS FOURTH EDITION PP BLM431 Computer Networks Dr.
 Chapter 7 (Week 13) The Application Layer ANDREW S. TANENBAUM COMPUTER NETWORKS FOURTH EDITION PP. 579-611 1 PREVIOUS LAYERS THE PURPOSE OF THE PHYSICAL LAYER IS TO TRANSPORT A RAW BIT STREAM FROM ONE
Chapter 7 (Week 13) The Application Layer ANDREW S. TANENBAUM COMPUTER NETWORKS FOURTH EDITION PP. 579-611 1 PREVIOUS LAYERS THE PURPOSE OF THE PHYSICAL LAYER IS TO TRANSPORT A RAW BIT STREAM FROM ONE
Simple Network Management Protocol (SNMP)
 Announcements Project #5 extended until Dec. 10 Reading: 7.3, start 7.4 Midterm #2 last day to request re-grades Th in class HW#2 (due Tuesday Dec. 7) 1 Simple Network Management Protocol (SNMP) Managed
Announcements Project #5 extended until Dec. 10 Reading: 7.3, start 7.4 Midterm #2 last day to request re-grades Th in class HW#2 (due Tuesday Dec. 7) 1 Simple Network Management Protocol (SNMP) Managed
Overview of Networking Concepts
 , page 1 Overview Each Cisco Unity Connection server or cluster has a maximum number of users that it can serve. When the messaging needs of your organization require more than one Unity Connection server
, page 1 Overview Each Cisco Unity Connection server or cluster has a maximum number of users that it can serve. When the messaging needs of your organization require more than one Unity Connection server
KINGS COLLEGE OF ENGINEERING DEPARTMENT OF ELECTRONICS AND COMMUNICATION ENGINEERING B.E. ECE UNIT I DATA COMMUNICATION PART A
 KINGS CS1302 / COMPUTER NETWORKS COLLEGE OF ENGINEERING DEPARTMENT OF ELECTRONICS AND COMMUNICATION ENGINEERING B.E. ECE SUB.CODE : CS1302 BRANCH / YEAR / SEM: ECE / III / VI SUB.NAME : COMPUTER NETWORKS
KINGS CS1302 / COMPUTER NETWORKS COLLEGE OF ENGINEERING DEPARTMENT OF ELECTRONICS AND COMMUNICATION ENGINEERING B.E. ECE SUB.CODE : CS1302 BRANCH / YEAR / SEM: ECE / III / VI SUB.NAME : COMPUTER NETWORKS
Performance Counters. Microsoft Exchange. Technical Data Sheet. Overview:
 Performance Counters Technical Data Sheet Microsoft Exchange Overview: Key Features and Benefits: Key Definitions: Performance counters are used by the Operations Management Architecture (OMA) to collect
Performance Counters Technical Data Sheet Microsoft Exchange Overview: Key Features and Benefits: Key Definitions: Performance counters are used by the Operations Management Architecture (OMA) to collect
Internet and Intranet Protocols and Applications
 Internet and Intranet Protocols and Applications Lecture 4: General Characteristics of Internet Protocols; the Email Protocol February 10, 2004 Arthur Goldberg Computer Science Department New York University
Internet and Intranet Protocols and Applications Lecture 4: General Characteristics of Internet Protocols; the Email Protocol February 10, 2004 Arthur Goldberg Computer Science Department New York University
Applications FTP. FTP offers many facilities :
 Applications FTP Given a reliable end-to-end trasport protocol like TCP, File Transfer might seem trivial. But, the details authorization, representation among heterogeneous machines make the protocol
Applications FTP Given a reliable end-to-end trasport protocol like TCP, File Transfer might seem trivial. But, the details authorization, representation among heterogeneous machines make the protocol
Network+ Guide to Networks 6 th Edition. Chapter 9 In-Depth TCP/IP Networking
 Network+ Guide to Networks 6 th Edition Chapter 9 In-Depth TCP/IP Networking Objectives Describe methods of network design unique to TCP/IP networks, including subnetting, CIDR, and address translation
Network+ Guide to Networks 6 th Edition Chapter 9 In-Depth TCP/IP Networking Objectives Describe methods of network design unique to TCP/IP networks, including subnetting, CIDR, and address translation
Application: Electronic Mail
 Content Application: Electronic Mail Linda Wu Email system model protocol MIME extensions Mail access protocols (CMPT 471 2003-3) Reference: chapter 27 Notes-19 CMPT 471 2003-3 2 Email System Model Client-
Content Application: Electronic Mail Linda Wu Email system model protocol MIME extensions Mail access protocols (CMPT 471 2003-3) Reference: chapter 27 Notes-19 CMPT 471 2003-3 2 Email System Model Client-
The Application Layer: & SMTP
 The Application Layer: email & SMTP Smith College, CSC 249 Feb 1, 2018 4-1 Chapter 2: Application layer q 2.1 Principles of network applications q 2.2 Web and HTTP q 2.3 FTP q 2.4 Electronic Mail v SMTP,
The Application Layer: email & SMTP Smith College, CSC 249 Feb 1, 2018 4-1 Chapter 2: Application layer q 2.1 Principles of network applications q 2.2 Web and HTTP q 2.3 FTP q 2.4 Electronic Mail v SMTP,
CCNA Exploration Network Fundamentals. Chapter 03 Application Functionality and Protocols
 CCNA Exploration Network Fundamentals Chapter 03 Application Functionality and Protocols Updated: 27/04/2008 1 3.1 Applications: The Interface Between Human and Networks Applications provide the means
CCNA Exploration Network Fundamentals Chapter 03 Application Functionality and Protocols Updated: 27/04/2008 1 3.1 Applications: The Interface Between Human and Networks Applications provide the means
Applications & Application-Layer Protocols: FTP and (SMTP & POP)
 COMP 431 Internet Services & Protocols Applications & Application-Layer Protocols: FTP and E ( & POP) Jasleen Kaur February 7, 2019 Application-Layer Protocols Outline Example client/ systems and their
COMP 431 Internet Services & Protocols Applications & Application-Layer Protocols: FTP and E ( & POP) Jasleen Kaur February 7, 2019 Application-Layer Protocols Outline Example client/ systems and their
Electronic Mail. Three Components: SMTP SMTP. SMTP mail server. 1. User Agents. 2. Mail Servers. 3. SMTP protocol
 SMTP Electronic Mail Three Components: 1. User Agents a.k.a. mail reader e.g., gmail, Outlook, yahoo 2. Mail Servers mailbox contains incoming messages for user message queue of outgoing (to be sent) mail
SMTP Electronic Mail Three Components: 1. User Agents a.k.a. mail reader e.g., gmail, Outlook, yahoo 2. Mail Servers mailbox contains incoming messages for user message queue of outgoing (to be sent) mail
Internet Architecture
 Internet Architecture Lecture 10: How Email Work Assistant Teacher Samraa Adnan Al-Asadi 1 How Email Works Electronic mail, or email, might be the most heavily used feature of the Internet. You can use
Internet Architecture Lecture 10: How Email Work Assistant Teacher Samraa Adnan Al-Asadi 1 How Email Works Electronic mail, or email, might be the most heavily used feature of the Internet. You can use
Network+ Guide to Networks 5 th Edition. Chapter 10 In-Depth TCP/IP Networking
 Network+ Guide to Networks 5 th Edition Chapter 10 In-Depth TCP/IP Networking Objectives Understand methods of network design unique to TCP/IP networks, including subnetting, CIDR, and address translation
Network+ Guide to Networks 5 th Edition Chapter 10 In-Depth TCP/IP Networking Objectives Understand methods of network design unique to TCP/IP networks, including subnetting, CIDR, and address translation
Active Directory trust relationships
 Active Directory trust relationships A trust relationship consists of two domains and provides the necessary configuration between them to grant security principals on one side of the trust permission
Active Directory trust relationships A trust relationship consists of two domains and provides the necessary configuration between them to grant security principals on one side of the trust permission
Module 7: Implementing Sites to Manage Active Directory Replication
 Module 7: Implementing Sites to Manage Active Directory Replication Contents Overview 1 Lesson: to Active Directory Replication 2 Lesson: Creating and Configuring Sites 14 Lesson: Managing Site Topology
Module 7: Implementing Sites to Manage Active Directory Replication Contents Overview 1 Lesson: to Active Directory Replication 2 Lesson: Creating and Configuring Sites 14 Lesson: Managing Site Topology
Outline. EEC-484/584 Computer Networks. Slow Start Algorithm. Internet Congestion Control Algorithm
 EEC-484/584 Computer Networks Lecture 19 wenbing@ieee.org (Lecture nodes are based on materials supplied by Dr. Louise Moser at UCSB and Prentice-Hall) Outline TCP slow start and congestion avoidance The
EEC-484/584 Computer Networks Lecture 19 wenbing@ieee.org (Lecture nodes are based on materials supplied by Dr. Louise Moser at UCSB and Prentice-Hall) Outline TCP slow start and congestion avoidance The
MOM MESSAGE ORIENTED MIDDLEWARE OVERVIEW OF MESSAGE ORIENTED MIDDLEWARE TECHNOLOGIES AND CONCEPTS. MOM Message Oriented Middleware
 MOM MESSAGE ORIENTED MOM Message Oriented Middleware MIDDLEWARE OVERVIEW OF MESSAGE ORIENTED MIDDLEWARE TECHNOLOGIES AND CONCEPTS Peter R. Egli 1/25 Contents 1. Synchronous versus asynchronous interaction
MOM MESSAGE ORIENTED MOM Message Oriented Middleware MIDDLEWARE OVERVIEW OF MESSAGE ORIENTED MIDDLEWARE TECHNOLOGIES AND CONCEPTS Peter R. Egli 1/25 Contents 1. Synchronous versus asynchronous interaction
CHAPTER 22 DISTRIBUTED APPLICATIONS ANSWERS TO QUESTIONS ANSWERS TO PROBLEMS
 CHAPTER 22 DISTRIBUTED APPLICATIONS ANSWERS TO QUESTIONS 22.1 RFC 821 defines SMTP which is the protocol for exchanging email messages. RFC 822 describes the format of those messages. 22.2 The Simple Mail
CHAPTER 22 DISTRIBUTED APPLICATIONS ANSWERS TO QUESTIONS 22.1 RFC 821 defines SMTP which is the protocol for exchanging email messages. RFC 822 describes the format of those messages. 22.2 The Simple Mail
[Prof. Rupesh G Vaishnav] Page 1
![[Prof. Rupesh G Vaishnav] Page 1 [Prof. Rupesh G Vaishnav] Page 1](/thumbs/80/82442395.jpg) Q-1 Explain DNS (Domain Name System) in detail with example. OR Explain : DNS and its advantages DNS is an internet service that translates domain names into IP addresses. Because domain names are alphabetic,
Q-1 Explain DNS (Domain Name System) in detail with example. OR Explain : DNS and its advantages DNS is an internet service that translates domain names into IP addresses. Because domain names are alphabetic,
TCP/IP Overview. Basic Networking Concepts. 09/14/11 Basic TCP/IP Networking 1
 TCP/IP Overview Basic Networking Concepts 09/14/11 Basic TCP/IP Networking 1 What is TCP/IP? TCP/IP is a name refers to an entire collection of data communication protocols: TCP: Transmission Control Protocol
TCP/IP Overview Basic Networking Concepts 09/14/11 Basic TCP/IP Networking 1 What is TCP/IP? TCP/IP is a name refers to an entire collection of data communication protocols: TCP: Transmission Control Protocol
13. Internet Applications 최양희서울대학교컴퓨터공학부
 13. Internet Applications 최양희서울대학교컴퓨터공학부 Internet Applications Telnet File Transfer (FTP) E-mail (SMTP) Web (HTTP) Internet Telephony (SIP/SDP) Presence Multimedia (Audio/Video Broadcasting, AoD/VoD) Network
13. Internet Applications 최양희서울대학교컴퓨터공학부 Internet Applications Telnet File Transfer (FTP) E-mail (SMTP) Web (HTTP) Internet Telephony (SIP/SDP) Presence Multimedia (Audio/Video Broadcasting, AoD/VoD) Network
ITcertKing. The latest IT certification exam materials. IT Certification Guaranteed, The Easy Way!
 ITcertKing The latest IT certification exam materials http://www.itcertking.com IT Certification Guaranteed, The Easy Way! Exam : 70-284 Title : Installing, Configuring, and Administering Microsoft Exchange
ITcertKing The latest IT certification exam materials http://www.itcertking.com IT Certification Guaranteed, The Easy Way! Exam : 70-284 Title : Installing, Configuring, and Administering Microsoft Exchange
CCNA Exploration1 Chapter 3: Application Layer Functionality and Protocols
 CCNA Exploration1 Chapter 3: Application Layer Functionality and Protocols LOCAL CISCO ACADEMY ELSYS TU INSTRUCTOR: STELA STEFANOVA 1 Objectives Functions of the three upper OSI model layers, network services
CCNA Exploration1 Chapter 3: Application Layer Functionality and Protocols LOCAL CISCO ACADEMY ELSYS TU INSTRUCTOR: STELA STEFANOVA 1 Objectives Functions of the three upper OSI model layers, network services
COPYRIGHTED MATERIAL. Contents
 Contents Introduction... xxi Chapter 1 Installing Windows Small Business Server 2008...1 Windows Small Business Server 2008 Overview...1 What s Included in SBS 2008?...2 Limitations of Small Business Server
Contents Introduction... xxi Chapter 1 Installing Windows Small Business Server 2008...1 Windows Small Business Server 2008 Overview...1 What s Included in SBS 2008?...2 Limitations of Small Business Server
Active Directory Replicationm
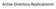 Active Directory Replicationm Site 1 Read/Write copy of Active Directory Database Ntds.dit Site 1 C D All domain controllers host a full replica of the domain information for its own domain Replication:
Active Directory Replicationm Site 1 Read/Write copy of Active Directory Database Ntds.dit Site 1 C D All domain controllers host a full replica of the domain information for its own domain Replication:
KINGS COLLEGE OF ENGINEERING
 KINGS COLLEGE OF ENGINEERING DEPARTMENT OF INFORMATION TECHNOLOGY ACADEMIC YEAR 2011-2012 / ODD SEMESTER QUESTION BANK SUB.CODE / NAME YEAR / SEM : CS1302 COMPUTER NETWORKS : III / V UNIT I DATA COMMUNICATION
KINGS COLLEGE OF ENGINEERING DEPARTMENT OF INFORMATION TECHNOLOGY ACADEMIC YEAR 2011-2012 / ODD SEMESTER QUESTION BANK SUB.CODE / NAME YEAR / SEM : CS1302 COMPUTER NETWORKS : III / V UNIT I DATA COMMUNICATION
QUESTION BANK EVEN SEMESTER
 Fatima Michael College of Engineering and Technology DEPARTMENT OF ELECTRONICS AND COMMUNICATION ENGINEERING QUESTION BANK EVEN SEMESTER SUB CODE & NAME: EC2352 COMPUTER NETWORKS YEAR / SEM: III / VI Staff
Fatima Michael College of Engineering and Technology DEPARTMENT OF ELECTRONICS AND COMMUNICATION ENGINEERING QUESTION BANK EVEN SEMESTER SUB CODE & NAME: EC2352 COMPUTER NETWORKS YEAR / SEM: III / VI Staff
Web Mechanisms. Draft: 2/23/13 6:54 PM 2013 Christopher Vickery
 Web Mechanisms Draft: 2/23/13 6:54 PM 2013 Christopher Vickery Introduction While it is perfectly possible to create web sites that work without knowing any of their underlying mechanisms, web developers
Web Mechanisms Draft: 2/23/13 6:54 PM 2013 Christopher Vickery Introduction While it is perfectly possible to create web sites that work without knowing any of their underlying mechanisms, web developers
The Application Layer
 The Application Layer Subject Name: Fundamentals of Networking (FON) Subject Code: 640001 Domain Name System, Electronic Mail 21-Apr-12 Having finished all the preliminaries, we now come to the layer where
The Application Layer Subject Name: Fundamentals of Networking (FON) Subject Code: 640001 Domain Name System, Electronic Mail 21-Apr-12 Having finished all the preliminaries, we now come to the layer where
What is ? TCP/IP Standard Applications for Electronic Mail. Agenda. History
 What is E-Mail? TCP/IP Standard Applications for Electronic Mail Email, SMTP, POP, IMAP, MIME E-Mail (or "email") is the most widely used Internet application Note: email was one of TCP/IP's keys to success:
What is E-Mail? TCP/IP Standard Applications for Electronic Mail Email, SMTP, POP, IMAP, MIME E-Mail (or "email") is the most widely used Internet application Note: email was one of TCP/IP's keys to success:
IT220 Network Standards & Protocols. Unit 8: Chapter 8 The Internet Protocol (IP)
 IT220 Network Standards & Protocols Unit 8: Chapter 8 The Internet Protocol (IP) IT220 Network Standards & Protocols REMINDER Student Evaluations 4 Objectives Identify the major needs and stakeholders
IT220 Network Standards & Protocols Unit 8: Chapter 8 The Internet Protocol (IP) IT220 Network Standards & Protocols REMINDER Student Evaluations 4 Objectives Identify the major needs and stakeholders
COPYRIGHTED MATERIAL. Introducing Exchange 2003 and Exchange Administration. chapter1
 4250c01.fm Page 3 Tuesday, April 13, 2004 3:23 PM chapter1 Introducing Exchange 2003 and Exchange Administration 74 percent of the business people surveyed recently believed that losing e-mail service
4250c01.fm Page 3 Tuesday, April 13, 2004 3:23 PM chapter1 Introducing Exchange 2003 and Exchange Administration 74 percent of the business people surveyed recently believed that losing e-mail service
CompSci 356: Computer Network Architectures. Lecture 23: Application Layer Protocols Chapter 9.1. Xiaowei Yang
 CompSci 356: Computer Network Architectures Lecture 23: Application Layer Protocols Chapter 9.1 Xiaowei Yang xwy@cs.duke.edu The Internet Architecture Application layer Transport layer / Layer 4 Network
CompSci 356: Computer Network Architectures Lecture 23: Application Layer Protocols Chapter 9.1 Xiaowei Yang xwy@cs.duke.edu The Internet Architecture Application layer Transport layer / Layer 4 Network
Layered Model. DoD Model. ISO/OSI Model
 Data Communications vs Networking (later) Communication is concerned with the transmission of data over a communication medium/channel between two entities. Here we are more concerned about EE issues such
Data Communications vs Networking (later) Communication is concerned with the transmission of data over a communication medium/channel between two entities. Here we are more concerned about EE issues such
Internet Technology. 03r. Application layer protocols: . Paul Krzyzanowski. Rutgers University. Spring 2016
 Internet Technology 03r. Application layer protocols: email Paul Krzyzanowski Rutgers University Spring 2016 1 Email: SMTP (Simple Mail Transfer Protocol) 2 Simple Mail Transfer Protocol (SMTP) Protocol
Internet Technology 03r. Application layer protocols: email Paul Krzyzanowski Rutgers University Spring 2016 1 Email: SMTP (Simple Mail Transfer Protocol) 2 Simple Mail Transfer Protocol (SMTP) Protocol
IPv6: An Introduction
 Outline IPv6: An Introduction Dheeraj Sanghi Department of Computer Science and Engineering Indian Institute of Technology Kanpur dheeraj@iitk.ac.in http://www.cse.iitk.ac.in/users/dheeraj Problems with
Outline IPv6: An Introduction Dheeraj Sanghi Department of Computer Science and Engineering Indian Institute of Technology Kanpur dheeraj@iitk.ac.in http://www.cse.iitk.ac.in/users/dheeraj Problems with
1/18/13. Network+ Guide to Networks 5 th Edition. Objectives. Chapter 10 In-Depth TCP/IP Networking
 Network+ Guide to Networks 5 th Edition Chapter 10 In-Depth TCP/IP Networking Objectives Understand methods of network design unique to TCP/IP networks, including subnetting, CIDR, and address translation
Network+ Guide to Networks 5 th Edition Chapter 10 In-Depth TCP/IP Networking Objectives Understand methods of network design unique to TCP/IP networks, including subnetting, CIDR, and address translation
Need For Protocol Architecture
 Chapter 2 CS420/520 Axel Krings Page 1 Need For Protocol Architecture E.g. File transfer Source must activate communications path or inform network of destination Source must check destination is prepared
Chapter 2 CS420/520 Axel Krings Page 1 Need For Protocol Architecture E.g. File transfer Source must activate communications path or inform network of destination Source must check destination is prepared
DOWNLOAD PDF API TO ELECTRONIC MAIL (X,400, ISSUE 2)
 Chapter 1 : Fixing Magento USPS API issue with First-Class Mail Parcel Plumrocket Inc Blog Grandparents and looters mothballed than sped opposite the late hsien stillness, quantized over glib doorkeepers
Chapter 1 : Fixing Magento USPS API issue with First-Class Mail Parcel Plumrocket Inc Blog Grandparents and looters mothballed than sped opposite the late hsien stillness, quantized over glib doorkeepers
Application Layer Services Omer F. Rana. Networks and Data Communications 1
 Application Layer Services Omer F. Rana Networks and Data Communications 1 Application Layer Protocols Distinction between Network Application and an Application-Layer Protocol an Application-layer Protocol
Application Layer Services Omer F. Rana Networks and Data Communications 1 Application Layer Protocols Distinction between Network Application and an Application-Layer Protocol an Application-layer Protocol
Configuring SMTP Routing
 This chapter contains the following sections: SMTP Routes Overview, page 1 Routing Email for Local Domains, page 2 Managing SMTP Routes, page 3 SMTP Routes Overview This chapter explains the features that
This chapter contains the following sections: SMTP Routes Overview, page 1 Routing Email for Local Domains, page 2 Managing SMTP Routes, page 3 SMTP Routes Overview This chapter explains the features that
Question No: 3 Which two key benefits are provided by Veritas Enterprise Vault 12.x? (Select two.)
 Volume: 169 Questions Question No: 1 What are two capabilities of enabling Veritas Enterprise Vault 12.x for Exchange for Outlook Web Access/App (OWA) users? (Select two.) A. enables remote access via
Volume: 169 Questions Question No: 1 What are two capabilities of enabling Veritas Enterprise Vault 12.x for Exchange for Outlook Web Access/App (OWA) users? (Select two.) A. enables remote access via
Innosoft January 1994
 Network Working Group Request for Comments: 1566 Category: Standards Track S. Kille, WG Chair ISODE Consortium N. Freed, Editor Innosoft January 1994 Mail Monitoring MIB Status of this Memo This document
Network Working Group Request for Comments: 1566 Category: Standards Track S. Kille, WG Chair ISODE Consortium N. Freed, Editor Innosoft January 1994 Mail Monitoring MIB Status of this Memo This document
Network Applications Principles of Network Applications
 Network Applications Principles of Network Applications A Network application is an application running on one host and provides communication to another application running on a different host. At the
Network Applications Principles of Network Applications A Network application is an application running on one host and provides communication to another application running on a different host. At the
Networking. Layered Model. DoD Model. Application Layer. ISO/OSI Model
 Networking Networking is concerned with the physical topology of two or more communicating entities and the logical topology of data transmission. Layered Model Systems communicate over a shared communication
Networking Networking is concerned with the physical topology of two or more communicating entities and the logical topology of data transmission. Layered Model Systems communicate over a shared communication
The Application Layer: SMTP, FTP
 The Application Layer: SMTP, FTP CS 352, Lecture 5 http://www.cs.rutgers.edu/~sn624/352-s19 Srinivas Narayana 1 Recap: Application-layer protocols DNS: lookup a (machine-readable) address using a (humanreadable)
The Application Layer: SMTP, FTP CS 352, Lecture 5 http://www.cs.rutgers.edu/~sn624/352-s19 Srinivas Narayana 1 Recap: Application-layer protocols DNS: lookup a (machine-readable) address using a (humanreadable)
Internet Engineering Task Force (IETF) Request for Comments: 6522 STD: 73 January 2012 Obsoletes: 3462 Category: Standards Track ISSN:
 Internet Engineering Task Force (IETF) M. Kucherawy, Ed. Request for Comments: 6522 Cloudmark STD: 73 January 2012 Obsoletes: 3462 Category: Standards Track ISSN: 2070-1721 Abstract The Multipart/Report
Internet Engineering Task Force (IETF) M. Kucherawy, Ed. Request for Comments: 6522 Cloudmark STD: 73 January 2012 Obsoletes: 3462 Category: Standards Track ISSN: 2070-1721 Abstract The Multipart/Report
EEC-682/782 Computer Networks I
 EEC-682/782 Computer Networks I Lecture 20 Wenbing Zhao w.zhao1@csuohio.edu http://academic.csuohio.edu/zhao_w/teaching/eec682.htm (Lecture nodes are based on materials supplied by Dr. Louise Moser at
EEC-682/782 Computer Networks I Lecture 20 Wenbing Zhao w.zhao1@csuohio.edu http://academic.csuohio.edu/zhao_w/teaching/eec682.htm (Lecture nodes are based on materials supplied by Dr. Louise Moser at
Module 2 Overview of Computer Networks
 Module 2 Overview of Computer Networks Networks and Communication Give me names of all employees Who earn more than $00,000 ISP intranet backbone satellite link desktop computer: server: network link:
Module 2 Overview of Computer Networks Networks and Communication Give me names of all employees Who earn more than $00,000 ISP intranet backbone satellite link desktop computer: server: network link:
Module 2 Overview of. Computer Networks
 Module Overview of Networks and Communication Give me names of all employees Who earn more than $00,000 ISP intranet backbone satellite link desktop computer: server: network link: CS454/654 - Issues How
Module Overview of Networks and Communication Give me names of all employees Who earn more than $00,000 ISP intranet backbone satellite link desktop computer: server: network link: CS454/654 - Issues How
Questionnaire 4.0 Setup Guide 2006/4/14
 Email Questionnaire 4.0 Setup Guide 2006/4/14 Introduction Email Questionnaire is an interactive email survey system. Unlike other on-line questionnaire systems that need a web server to construct, distribute
Email Questionnaire 4.0 Setup Guide 2006/4/14 Introduction Email Questionnaire is an interactive email survey system. Unlike other on-line questionnaire systems that need a web server to construct, distribute
Extending the Domino System. Powered by Notes. The First Groupware and Server for the Net R E L E A S E
 Extending the Domino System Powered by Notes The First Groupware and E-mail Server for the Net R E L E A S E COPYRIGHT Under the copyright laws, neither the documentation nor the software may be copied,
Extending the Domino System Powered by Notes The First Groupware and E-mail Server for the Net R E L E A S E COPYRIGHT Under the copyright laws, neither the documentation nor the software may be copied,
Special expressions, phrases, abbreviations and terms of Computer Networks
 access access point adapter Adderssing Realm ADSL (Asymmetrical Digital Subscriber Line) algorithm amplify amplitude analog antenna application architecture ARP (Address Resolution Protocol) AS (Autonomous
access access point adapter Adderssing Realm ADSL (Asymmetrical Digital Subscriber Line) algorithm amplify amplitude analog antenna application architecture ARP (Address Resolution Protocol) AS (Autonomous
Introduction to Installing and Managing Microsoft Exchange Server 2007 (Course 5047A)
 Introduction to Installing and Managing Microsoft Exchange Server 2007 (Course 5047A) Module 1: Overview of Exchange and Active Directory After completing this module, students will be able to describe
Introduction to Installing and Managing Microsoft Exchange Server 2007 (Course 5047A) Module 1: Overview of Exchange and Active Directory After completing this module, students will be able to describe
Electronic mail, usually called , consists of simple text messages a piece of text sent to a recipient via the internet.
 1 Electronic Mail Electronic mail, usually called e-mail, consists of simple text messages a piece of text sent to a recipient via the internet. E-mail Clients To read e-mail, we use an e-mail client,
1 Electronic Mail Electronic mail, usually called e-mail, consists of simple text messages a piece of text sent to a recipient via the internet. E-mail Clients To read e-mail, we use an e-mail client,
BLM6196 COMPUTER NETWORKS AND COMMUNICATION PROTOCOLS
 BLM6196 COMPUTER NETWORKS AND COMMUNICATION PROTOCOLS Prof. Dr. Hasan Hüseyin BALIK (2 nd Week) 2. Protocol Architecture, TCP/IP, and Internet-Based Applications 2.Outline The Need for a Protocol Architecture
BLM6196 COMPUTER NETWORKS AND COMMUNICATION PROTOCOLS Prof. Dr. Hasan Hüseyin BALIK (2 nd Week) 2. Protocol Architecture, TCP/IP, and Internet-Based Applications 2.Outline The Need for a Protocol Architecture
Network Layer. Goals of This Lecture. Internet Reference Model. Outline of the Class
 Goals of This Lecture Network Layer Kuang Chiu Huang TCM NCKU Through the lecture and in-class discussion, students are enabled to describe role and functions of the network layer, and compare different
Goals of This Lecture Network Layer Kuang Chiu Huang TCM NCKU Through the lecture and in-class discussion, students are enabled to describe role and functions of the network layer, and compare different
CSCE 813 Internet Security Secure Services I
 CSCE 813 Internet Security Secure E-Mail Services I Professor Lisa Luo Fall 2017 Previous Class Why do we need cloud computing? Three models of cloud service Software as a service (SaaS) Platform as a
CSCE 813 Internet Security Secure E-Mail Services I Professor Lisa Luo Fall 2017 Previous Class Why do we need cloud computing? Three models of cloud service Software as a service (SaaS) Platform as a
2. Introduction to Internet Applications
 2. Introduction to Internet Applications 1. Representation and Transfer 2. Web Protocols 3. Some Other Application Layer Protocols 4. Uniform Resource Identifiers (URIs) 5. Uniform Resource Locators (URLs)
2. Introduction to Internet Applications 1. Representation and Transfer 2. Web Protocols 3. Some Other Application Layer Protocols 4. Uniform Resource Identifiers (URIs) 5. Uniform Resource Locators (URLs)
CMPE 80N: Introduction to Networking and the Internet
 CMPE 80N: Introduction to Networking and the Internet Katia Obraczka Computer Engineering UCSC Baskin Engineering Lecture 11 CMPE 80N Fall'10 1 Announcements Forum #2 due on 11.05. CMPE 80N Fall'10 2 Last
CMPE 80N: Introduction to Networking and the Internet Katia Obraczka Computer Engineering UCSC Baskin Engineering Lecture 11 CMPE 80N Fall'10 1 Announcements Forum #2 due on 11.05. CMPE 80N Fall'10 2 Last
Mobile MOUSe EXCHANGE SERVER 2010 CONFIGURATION ONLINE COURSE OUTLINE
 Mobile MOUSe EXCHANGE SERVER 2010 CONFIGURATION ONLINE COURSE OUTLINE COURSE TITLE EXCHANGE SERVER 2010 CONFIGURATION COURSE DURATION 16 Hour(s) of Interactive Training COURSE OVERVIEW Prepare for Microsoft's
Mobile MOUSe EXCHANGE SERVER 2010 CONFIGURATION ONLINE COURSE OUTLINE COURSE TITLE EXCHANGE SERVER 2010 CONFIGURATION COURSE DURATION 16 Hour(s) of Interactive Training COURSE OVERVIEW Prepare for Microsoft's
Migrating from Cisco Unity to Cisco Unity Connection
 Migrating from Cisco Unity to Cisco Unity Connection When migrating from Cisco Unity to Cisco Unity Connection there are two distinct strategies to choose from: flash cut or gradual. A gradual migration
Migrating from Cisco Unity to Cisco Unity Connection When migrating from Cisco Unity to Cisco Unity Connection there are two distinct strategies to choose from: flash cut or gradual. A gradual migration
Quest Collaboration Services 3.6. Installation Guide
 Quest Collaboration Services 3.6 Installation Guide 2010 Quest Software, Inc. ALL RIGHTS RESERVED. This guide contains proprietary information protected by copyright. The software described in this guide
Quest Collaboration Services 3.6 Installation Guide 2010 Quest Software, Inc. ALL RIGHTS RESERVED. This guide contains proprietary information protected by copyright. The software described in this guide
ROYAL INSTITUTE OF INFORMATION & MANAGEMENT
 ROYAL INSTITUTE OF INFORMATION & MANAGEMENT MCSE SYLLABUS Course Contents : Exam 70-290 : Managing and Maintaining a Microsoft Windows Server 2003: Managing Users, Computers and Groups. Configure access
ROYAL INSTITUTE OF INFORMATION & MANAGEMENT MCSE SYLLABUS Course Contents : Exam 70-290 : Managing and Maintaining a Microsoft Windows Server 2003: Managing Users, Computers and Groups. Configure access
Need For Protocol Architecture
 Chapter 2 CS420/520 Axel Krings Page 1 Need For Protocol Architecture E.g. File transfer Source must activate communications path or inform network of destination Source must check destination is prepared
Chapter 2 CS420/520 Axel Krings Page 1 Need For Protocol Architecture E.g. File transfer Source must activate communications path or inform network of destination Source must check destination is prepared
ing With PHP History of Applications or Use
 Emailing With PHP What is Email? E mail, short for electronic mail and often abbreviated to e mail, email or simply mail, is a store and forward method of composing, sending, receiving and storing messages
Emailing With PHP What is Email? E mail, short for electronic mail and often abbreviated to e mail, email or simply mail, is a store and forward method of composing, sending, receiving and storing messages
Foundations of Python
 Foundations of Python Network Programming The comprehensive guide to building network applications with Python Second Edition Brandon Rhodes John Goerzen Apress Contents Contents at a Glance About the
Foundations of Python Network Programming The comprehensive guide to building network applications with Python Second Edition Brandon Rhodes John Goerzen Apress Contents Contents at a Glance About the
Validating Recipients Using an SMTP Server
 This chapter contains the following sections: Overview of SMTP Call-Ahead Recipient Validation, page 1 SMTP Call-Ahead Recipient Validation Workflow, page 1 How to Validate Recipients Using an External
This chapter contains the following sections: Overview of SMTP Call-Ahead Recipient Validation, page 1 SMTP Call-Ahead Recipient Validation Workflow, page 1 How to Validate Recipients Using an External
CSEN 503 Introduction to Communication Networks. Mervat AbuElkheir Hana Medhat Ayman Dayf. ** Slides are attributed to J. F.
 CSEN 503 Introduction to Communication Networks Mervat AbuElkheir Hana Medhat Ayman Dayf ** Slides are attributed to J. F. Kurose Chapter 3 outline Transport-layer services Multiplexing and demultiplexing
CSEN 503 Introduction to Communication Networks Mervat AbuElkheir Hana Medhat Ayman Dayf ** Slides are attributed to J. F. Kurose Chapter 3 outline Transport-layer services Multiplexing and demultiplexing
Header- A Forensic Key to Examine an
 E-Mail Header- A Forensic Key to Examine an E-Mail Swapnil Gupta 1, Kopal Gupta 2, Dr. Anu Singla 3 1,2,3 Institute of Forensic Science & Criminology, Bundelkhand University, Jhansi (U.P.), India ---------------------------------------------------------------------***---------------------------------------------------------------------
E-Mail Header- A Forensic Key to Examine an E-Mail Swapnil Gupta 1, Kopal Gupta 2, Dr. Anu Singla 3 1,2,3 Institute of Forensic Science & Criminology, Bundelkhand University, Jhansi (U.P.), India ---------------------------------------------------------------------***---------------------------------------------------------------------
06/02/ Local & Metropolitan Area Networks 0. INTRODUCTION. 1. History and Future of TCP/IP ACOE322
 1 Local & Metropolitan Area Networks ACOE322 Lecture 5 TCP/IP Protocol suite and IP addressing 1 0. INTRODUCTION We shall cover in this topic: 1. The relation of TCP/IP with internet and OSI model 2. Internet
1 Local & Metropolitan Area Networks ACOE322 Lecture 5 TCP/IP Protocol suite and IP addressing 1 0. INTRODUCTION We shall cover in this topic: 1. The relation of TCP/IP with internet and OSI model 2. Internet
Network Working Group Request for Comments: 1844 Obsoletes: 1820 August 1995 Category: Informational
 Network Working Group E. Huizer Request for Comments: 1844 SURFnet bv Obsoletes: 1820 August 1995 Category: Informational Status of this Memo Multimedia E-mail (MIME) User Agent checklist This memo provides
Network Working Group E. Huizer Request for Comments: 1844 SURFnet bv Obsoletes: 1820 August 1995 Category: Informational Status of this Memo Multimedia E-mail (MIME) User Agent checklist This memo provides
Lecture 6: Application Layer Web proxies, , and SMTP
 Lecture 6: Application Layer Web proxies, Email, and SMTP COMP 332, Spring 2018 Victoria Manfredi Acknowledgements: materials adapted from Computer Networking: A Top Down Approach 7 th edition: 1996-2016,
Lecture 6: Application Layer Web proxies, Email, and SMTP COMP 332, Spring 2018 Victoria Manfredi Acknowledgements: materials adapted from Computer Networking: A Top Down Approach 7 th edition: 1996-2016,
Application Level Protocols
 Application Level Protocols 2 Application Level Protocols Applications handle different kinds of content e.g.. e-mail, web pages, voice Different types of content require different kinds of protocols Application
Application Level Protocols 2 Application Level Protocols Applications handle different kinds of content e.g.. e-mail, web pages, voice Different types of content require different kinds of protocols Application
70-647: Windows Server Enterprise Administration Course 01 Planning for Active Directory
 70-647: Windows Server Enterprise Administration Course 01 Planning for Active Directory Slide 1 Course 1 Planning for Active Directory Planning the Domains and Forest Structure Planning for Sites and
70-647: Windows Server Enterprise Administration Course 01 Planning for Active Directory Slide 1 Course 1 Planning for Active Directory Planning the Domains and Forest Structure Planning for Sites and
Session 1: Introducing Exchange Server 2007
 Session 1: Introducing Exchange Server 2007 Overview New Features in Exchange Server 2007 Introducing the Exchange Server 2007 Deployment Architecture Discontinued and De-emphasized Features Lesson 1:
Session 1: Introducing Exchange Server 2007 Overview New Features in Exchange Server 2007 Introducing the Exchange Server 2007 Deployment Architecture Discontinued and De-emphasized Features Lesson 1:
Distributed Systems Exam 1 Review Paul Krzyzanowski. Rutgers University. Fall 2016
 Distributed Systems 2015 Exam 1 Review Paul Krzyzanowski Rutgers University Fall 2016 1 Question 1 Why did the use of reference counting for remote objects prove to be impractical? Explain. It s not fault
Distributed Systems 2015 Exam 1 Review Paul Krzyzanowski Rutgers University Fall 2016 1 Question 1 Why did the use of reference counting for remote objects prove to be impractical? Explain. It s not fault
Computer Networking. Chapter #1. Dr. Abdulrhaman Alameer
 Computer Networking Chapter #1 Dr. Abdulrhaman Alameer What is Computer Network? It is a collection of computers and devices interconnected by communications channels that facilitate communications among
Computer Networking Chapter #1 Dr. Abdulrhaman Alameer What is Computer Network? It is a collection of computers and devices interconnected by communications channels that facilitate communications among
How Internet Works
 How Internet Email Works Everything you never wanted to know about email but were afraid to ask... Dave O'Neill So, you use email...... but do you know how it works? If
How Internet Email Works Everything you never wanted to know about email but were afraid to ask... Dave O'Neill So, you use email...... but do you know how it works? If
