Five Benefits of a Visitor Management System
|
|
|
- Harriet Stewart
- 6 years ago
- Views:
Transcription
1 Five Benefits of a Visitor Management System
2 Pencil and Paper Sign-In Sheets Are No Longer Enough It is both amazing and disturbing that more than 80% of K-12 schools in the United States still rely on handwritten logs to manage campus visitors. There are many inherent security flaws in this approach, not the least of which is that visitors can write down a name other than their own (and many do). Even if they write their own name legibly, campus personnel still know nothing about their background or whether they should be allowed to enter the school. 750k 5X $ 2.8m There are more than 750,000 registered sex offenders in the United States. Raptor software alone has flagged more than 25,000 entering schools in the last 14 years. How many have slipped through the cracks at schools using pencil and paper sign-in sheets? Custody issues present schools with ongoing security concerns and information management burdens that show no sign of decreasing. The FBI reports that the number of custody-motivated abductions increased by more than five times between October 2010 and June Custody issues can have huge financial implications for schools, such as the $2.8 million judgment holding a school district in California responsible for releasing a student to a non-custodial adult who kidnapped the student. 2
3 Traditional Front Office Safety Even if you have taken steps to limit access through a single point of entry, traditional visitor signin sheets aren t enough to monitor and manage visitors on school grounds. Along with all of their other responsibilities, how can front desk staff: Quickly determine if a visitor is a student s authorized guardian? Be alerted if there are court ordered custody restrictions? Know if an individual is a registered sex offender or even if they are who they say they are? Request assistance at the front desk instantly and discreetly? In case of events like fires or other emergencies that require buildings to be evacuated or result in the destruction of physical property, traditional paper sign-sheets become virtually useless. In the commotion, they will most likely be left behind, lost or damaged, leaving no record of who was on school premises or any way to determine if all guests have been safely accounted for. In addition, sign-in sheets can t be accessed remotely by first responders before they arrive at the scene. There Is A Better Way An alternative to paper sign-in sheets is visitor management software. These automated systems allow front desk staff to confirm that visitors are who they say they are by using government-issued identification. They also instantly check names against registered sex offender lists. They can provide alerts related to issues like child custody or court orders, and, when appropriate, send instant alerts via text and to a customized list of recipients, such as School Resource Officers and Principals. When I walk into a school to perform a security assessment, I usually sign in as Mickey Mouse or Elvis. Nobody has ever said anything to me. Paul Timm P resident of RETA Security and author of School Security: How to Build and Strengthen a School s Safety Program. 3
4 4 Five Ways Automated Systems Improve Visitor Management Today only about 20,000 schools in the U.S. currently use automated systems, leaving more than 100,000 that still rely on pencil and paper visitor records. If you are among the majority without visitor management software, you may find this paper helpful. It outlines five critical factors you should consider when assessing visitor management systems. It may also help you determine if your existing system (manual or electronic) is providing your staff and students with adequate protection. 1. Automated ID Data Capture To create a safer school entrance we need to control and monitor visiting parents, volunteers, caregivers, even substitute teachers, fieldtrip chaperones, vendors and college sports recruiters. Michael Ghilani Principal, Upper St. Claire High School Recording handwritten names or even allowing visitors to manually enter their own identification information leads to unintended mistakes and opens the door to intentional falsification. Instead, schools should rely on data read from government-issued identification cards (like a driver s license) through an ID scanner. For privacy purposes, schools should use systems whose scanners Four out of five schools still rely compile only the data necessary for screening and do not keep a photocopy of the ID. on outmoded sign in sheets This automated process is not only more efficient and reliable, but the system also allows you to create an electronic record that is accessible (even off-site) by web-based systems in case of emergency or evacuation. 2. Instant and Automatic Screening The importance of being able to instantly check names against national sex offender registries and custody orders is obvious. However, it is nearly impossible to do this manually. It takes at least a full minute to check just your own state s database not to mention the time required for each of the 49 others. And there s a high likelihood of errors when manually entering a visitor s name and date of birth. The Department of Justice s nationwide database introduces more complications since it does not screen by date of birth. That can cause common names to generate hundreds of potential matches.
5 Moreover, any screening that requires more than a few mouse clicks means that busy front desk personnel who are already juggling multiple responsibilities including a line of visitors waiting for help are likely to avoid taking those extra steps. And even a high quality solution is useless if it isn t used consistently. Appropriate visitor management software addresses these complications by automating every step: 4 Screening/scanning of IDs is a simple, intuitive, single-click process, which reduces staff learning curves and encourages consistent use for each and every visitor. 4 Processing occurs quickly in the background so visitors are not inconvenienced or made to feel that they are being scrutinized. What s Wrong with Sign-In Sheets? 7 Signatures are often illegible. 7 Staff cannot easily verify a visitor s name or identity. 7 In an emergency evacuation, the sign-in sheets will most likely be left behind. 7 District staff has no access to visitor data from the administration office. 7 Reports cannot be run without retyping all of the data. 7 Sign-in sheets offer no added benefits, such as tracking custody issues. 4 The system provider should maintain registry databases that are accessed instantly and automatically with each screening and are updated frequently. 4 The system provider should also allow local schools/districts to create their own customized alerts for issues such as custodial orders or banned visitors. 3. Appropriate Data is Visible on Visitor Badges Once visitors have been screened, it is essential that the system creates on-site identification clearly indicating that they have been officially authorized to visit. Each temporary visitor badge must include: 4 Visitor Photo Prevents badges from being shared with anyone else. 4 Visitor Name Indicates that the individual has been screened and cleared. 4 Issue Date & Time Allows access only for the approved date and time. 4 Authorized Destination Indicates access only to a pre-approved location. 5
6 4. Smart Alert Notification In the event of a match with a name on either the national sex offender registry or a local custom alert, your visitor management system needs to do more than flash a warning on a screen at the front desk. Your solution should provide two key features so that effective measures can be taken: Customizable alert lists The system should allow you to tailor different notification lists to suit established district policies since recipients may be different depending on the type of alert sent out. For example, along with on-site security and the principal, school counselors might be included for custody incidents but not for sex offender alerts. Instant alerts Contacts on alert lists should receive instant notification via both text and . Discreet notification facilitates a rapid response without advance warning to someone who may be actively trying to evade security measures. Consistency Is Key Even in close-knit communities, schools today are too big for the staff to know everybody s background, according to Paul Timm, president of RETA Security and author of School Security: How to Build and Strengthen a School s Safety Program. That s why it s important to take steps to build support in the community and to enforce screening for every visitor, every time. Timm recommends sending letters to families so they know what to expect when they visit, as well as posting signs to remind parents of ongoing screening and to deter anyone considering unauthorized access to the campus. 6
7 5. Cloud-based Access Systems that reside on a local computer are less effective in case of emergencies and evacuations. By contrast, software accessed online provides distinct operational advantages: In the event of emergencies that require evacuation or result in physical damage to the front office, electronic visitor logs can still be accessed from any internet connection. Cloud-based services are maintained by the service provider, who assumes responsibility for system updates and ongoing maintenance. Schools can maintain their focus on education and administration without having to also manage the technology. To monitor compliance, archived visitor logs can automatically generate reports for an entire district rather than requiring collection of data from each individual school. Why Choose Raptor Technologies As Your Visitor Management Provider The five critical factors noted above should be "table stakes" for any visitor management system that you consider. And they only touch the surface of the capabilities offered by Raptor Technologies. Since 2002, the Raptor Visitor Management System has provided effective, automated visitor management software that does more than instantly compare visitors' government-issued identification against a comprehensive national list of registered sex offenders. It also accommodates customized private alerts related to child custody, court orders, known gang member or other individuals who are not allowed on school grounds. The Raptor system protects more than 20,000 K-12 campuses across the United States and serves more K-12 districts of all sizes than any other visitor management system. For more information on how Raptor Technologies can help improve visitor management at your school call toll free RAPTOR or Raptor Technologies at info@raptortech.com. 7
8
Raptor University. Volunteer Module 101. Instructor: RAPTOR TECHNOLOGIES, LLC
 Raptor University Volunteer Module 101 Instructor: RAPTOR TECHNOLOGIES, LLC Volunteer Module This course includes the following topics to get you started using the Raptor Volunteer Module: Volunteer Sign-In
Raptor University Volunteer Module 101 Instructor: RAPTOR TECHNOLOGIES, LLC Volunteer Module This course includes the following topics to get you started using the Raptor Volunteer Module: Volunteer Sign-In
Raptor University. Visitor Module 101. Instructor: RAPTOR TECHNOLOGIES, LLC
 Raptor University Visitor Module 101 Instructor: RAPTOR TECHNOLOGIES, LLC Visitor Module This course includes the following topics to get you started using the Raptor Visitor Module: Logging into Raptor
Raptor University Visitor Module 101 Instructor: RAPTOR TECHNOLOGIES, LLC Visitor Module This course includes the following topics to get you started using the Raptor Visitor Module: Logging into Raptor
Sign In. Use the Sign In/Sign Out workspace to sign in people entering your building.
 Sign In Use the Sign In/Sign Out workspace to sign in people entering your building. The following sign-in methods are available, depending who you are signing in: Use barcode reader to scan the 1D Barcode
Sign In Use the Sign In/Sign Out workspace to sign in people entering your building. The following sign-in methods are available, depending who you are signing in: Use barcode reader to scan the 1D Barcode
Raptor University. District Admin Training. Instructor: RAPTOR TECHNOLOGIES, LLC
 Raptor University District Admin Training Instructor: RAPTOR TECHNOLOGIES, LLC This presentation includes instruction on the following topics to get you started using Raptor: Learning Objectives Navigating
Raptor University District Admin Training Instructor: RAPTOR TECHNOLOGIES, LLC This presentation includes instruction on the following topics to get you started using Raptor: Learning Objectives Navigating
Raptor University. Raptor System Entry Admin Training. Instructor: RAPTOR TECHNOLOGIES, LLC
 Raptor University Raptor System Entry Admin Training Instructor: RAPTOR TECHNOLOGIES, LLC This training will provide you with the skills necessary to perform the following functions within the Raptor System:
Raptor University Raptor System Entry Admin Training Instructor: RAPTOR TECHNOLOGIES, LLC This training will provide you with the skills necessary to perform the following functions within the Raptor System:
Raptor University. Building Admin Training. Instructor: RAPTOR TECHNOLOGIES, LLC
 Raptor University Building Admin Training Instructor: RAPTOR TECHNOLOGIES, LLC This presentation includes the following topics to get you started using Raptor: Learning Objectives Create and Manage Users
Raptor University Building Admin Training Instructor: RAPTOR TECHNOLOGIES, LLC This presentation includes the following topics to get you started using Raptor: Learning Objectives Create and Manage Users
Red Flags/Identity Theft Prevention Policy: Purpose
 Red Flags/Identity Theft Prevention Policy: 200.3 Purpose Employees and students depend on Morehouse College ( Morehouse ) to properly protect their personal non-public information, which is gathered and
Red Flags/Identity Theft Prevention Policy: 200.3 Purpose Employees and students depend on Morehouse College ( Morehouse ) to properly protect their personal non-public information, which is gathered and
Baker Intermediate School Phase II: School Safety Report
 Baker Intermediate School Phase II: School Safety Report 2017-2018 Phase II: School Safety Report Josh Mounts 1645 Martin Luther King Jr Dr Winchester, Kentucky, 40391-2812 United States of America Last
Baker Intermediate School Phase II: School Safety Report 2017-2018 Phase II: School Safety Report Josh Mounts 1645 Martin Luther King Jr Dr Winchester, Kentucky, 40391-2812 United States of America Last
Raptor University. Raptor System Training. Instructor: RAPTOR TECHNOLOGIES, LLC
 Raptor University Raptor System Training Instructor: RAPTOR TECHNOLOGIES, LLC Log In and Log Out 1. In your browser, enter https://apps.raptortech.com. 2. On the Raptor Login screen, enter your assigned
Raptor University Raptor System Training Instructor: RAPTOR TECHNOLOGIES, LLC Log In and Log Out 1. In your browser, enter https://apps.raptortech.com. 2. On the Raptor Login screen, enter your assigned
Data Centers and Mission Critical Facilities Access and Physical Security Procedures
 Planning & Facilities Data Centers and Mission Critical Facilities Access and Physical Security Procedures Attachment B (Referenced in UW Information Technology Data Centers and Mission Critical Facilities
Planning & Facilities Data Centers and Mission Critical Facilities Access and Physical Security Procedures Attachment B (Referenced in UW Information Technology Data Centers and Mission Critical Facilities
Facility Security Policy
 1. PURPOSE 1.1 The New Brunswick Institute for Research, Data and Training (NB-IRDT) is located in the University of New Brunswick. It consists of: (i) employee offices in Singer Hall and Keirstead Hall,
1. PURPOSE 1.1 The New Brunswick Institute for Research, Data and Training (NB-IRDT) is located in the University of New Brunswick. It consists of: (i) employee offices in Singer Hall and Keirstead Hall,
TCPA Features Guide. 100 Enterprise Way, Suite A-300. Scotts Valley, CA
 TCPA Features Guide West Corporation 100 Enterprise Way, Suite A-300 Scotts Valley, CA 95066 888-527-5225 www.schoolmessenger.com Table of Contents Introduction... 3 The Telephone Consumer Protection Act
TCPA Features Guide West Corporation 100 Enterprise Way, Suite A-300 Scotts Valley, CA 95066 888-527-5225 www.schoolmessenger.com Table of Contents Introduction... 3 The Telephone Consumer Protection Act
St James Primary School Mobile Phone Policy for staff, visitors, volunteers and pupils
 2017-19 Learning to live, living to learn, learning from Christ Signed by Chair Date.. This policy provides clear guidance on the use of mobile phones in school by both staff and pupils Introduction St
2017-19 Learning to live, living to learn, learning from Christ Signed by Chair Date.. This policy provides clear guidance on the use of mobile phones in school by both staff and pupils Introduction St
GUIDE FOR INDIVIDUALS WHO ARE THE SUBJECT OF DATA
 GUIDE FOR INDIVIDUALS WHO ARE THE SUBJECT OF DATA This document explains the rights of individuals (meaning natural persons) who are the subject of MnDOT data and how those individuals can obtain public
GUIDE FOR INDIVIDUALS WHO ARE THE SUBJECT OF DATA This document explains the rights of individuals (meaning natural persons) who are the subject of MnDOT data and how those individuals can obtain public
The essential guide to creating a School Bring Your Own Device Policy. (BYOD)
 The essential guide to creating a School Bring Your Own Device Policy. (BYOD) Contents Introduction.... 3 Considerations when creating a BYOD policy.... 3 General Guidelines for use (Acceptable Use Policy)....
The essential guide to creating a School Bring Your Own Device Policy. (BYOD) Contents Introduction.... 3 Considerations when creating a BYOD policy.... 3 General Guidelines for use (Acceptable Use Policy)....
Mobile Phone Policy January 2014 January 2015 January 2016 Reviewed 2017 Reviewed 2018
 Mobile Phone Policy January 2014 January 2015 January 2016 Reviewed 2017 Reviewed 2018 CONTENTS PURPOSE OF THE POLICY... 3 RATIONALE... 3 PHONE USE... 3 SECURITY... 4 RESPONSIBILITIES... 4 POLICY RELEASE
Mobile Phone Policy January 2014 January 2015 January 2016 Reviewed 2017 Reviewed 2018 CONTENTS PURPOSE OF THE POLICY... 3 RATIONALE... 3 PHONE USE... 3 SECURITY... 4 RESPONSIBILITIES... 4 POLICY RELEASE
TARGETING CITIZENS WITH LOCATION BASED NOTIFICATIONS.
 TARGETING CITIZENS WITH LOCATION BASED NOTIFICATIONS Introduction State and local government departments, agencies and groups face a wide variety of events. Each have their own unique characteristics.
TARGETING CITIZENS WITH LOCATION BASED NOTIFICATIONS Introduction State and local government departments, agencies and groups face a wide variety of events. Each have their own unique characteristics.
desktop Security Rev 3.0
 desktop Security Rev 3.0 Technology that works for you. Imagine having the ability to automate your establishment s safety and security procedures with the simple click of a button. Even better, imagine
desktop Security Rev 3.0 Technology that works for you. Imagine having the ability to automate your establishment s safety and security procedures with the simple click of a button. Even better, imagine
LobbyGuard Assist. User Guide. Version 4.4
 LobbyGuard Assist User Guide Version 4.4 What s New... 4 Getting Started... 4 The LobbyGuard Assist Hardware... 5 Installing LobbyGuard Assist... 6 The LobbyGuard Assist Software... 6 Launching the LobbyGuard
LobbyGuard Assist User Guide Version 4.4 What s New... 4 Getting Started... 4 The LobbyGuard Assist Hardware... 5 Installing LobbyGuard Assist... 6 The LobbyGuard Assist Software... 6 Launching the LobbyGuard
OffenderCHECK Settings, Configuration & Options
 OffenderCHECK Settings, Configuration & Options Visitors Checking IN or OUT a visitor with OffenderCHECK is fast and easy to do. Click the Visitor button Checking IN -- Click the CHECK IN button. Offender
OffenderCHECK Settings, Configuration & Options Visitors Checking IN or OUT a visitor with OffenderCHECK is fast and easy to do. Click the Visitor button Checking IN -- Click the CHECK IN button. Offender
Identity Theft Prevention Program. Effective beginning August 1, 2009
 Identity Theft Prevention Program Effective beginning August 1, 2009 I. PROGRAM ADOPTION Christian Brothers University developed this Identity Theft Prevention Program pursuant to the Federal Trade Commission's
Identity Theft Prevention Program Effective beginning August 1, 2009 I. PROGRAM ADOPTION Christian Brothers University developed this Identity Theft Prevention Program pursuant to the Federal Trade Commission's
Why use Remind? Get students and parents to sign up for your Remind class! How is Remind safe?
 remind.com Why use Remind? Remind helps you connect instantly with students and parents on their mobile devices. SAVE TIME Send or schedule quick Announcements to your class, sports team, school club,
remind.com Why use Remind? Remind helps you connect instantly with students and parents on their mobile devices. SAVE TIME Send or schedule quick Announcements to your class, sports team, school club,
How to set up Skylert notifications in Skyward Family Access
 How to set up Skylert notifications in Skyward Family Access Skylert is the district s automated notification system that provides emergency alerts, attendance notifications and other informational alerts
How to set up Skylert notifications in Skyward Family Access Skylert is the district s automated notification system that provides emergency alerts, attendance notifications and other informational alerts
Raptor University. Volunteer Admin Training. Instructor: RAPTOR TECHNOLOGIES, LLC
 Raptor University Volunteer Admin Training Instructor: RAPTOR TECHNOLOGIES, LLC This presentation includes the detailed instruction of the following tasks to get you started using Raptor: Navigating Volunteer
Raptor University Volunteer Admin Training Instructor: RAPTOR TECHNOLOGIES, LLC This presentation includes the detailed instruction of the following tasks to get you started using Raptor: Navigating Volunteer
Dumas ISD. Acceptable Use Policy
 Dumas ISD Acceptable Use Policy Introduction Dumas ISD is excited to offer our staff and students access to modern technologies and mobile devices in conjunction with access to the Internet. Use of the
Dumas ISD Acceptable Use Policy Introduction Dumas ISD is excited to offer our staff and students access to modern technologies and mobile devices in conjunction with access to the Internet. Use of the
HIPAA FOR BROKERS. revised 10/17
 HIPAA FOR BROKERS revised 10/17 COURSE PURPOSE The purpose of this information is to help ensure that all Optima Health Brokers are prepared to protect the privacy and security of our members health information.
HIPAA FOR BROKERS revised 10/17 COURSE PURPOSE The purpose of this information is to help ensure that all Optima Health Brokers are prepared to protect the privacy and security of our members health information.
[Utility Name] Identity Theft Prevention Program
![[Utility Name] Identity Theft Prevention Program [Utility Name] Identity Theft Prevention Program](/thumbs/77/75712648.jpg) [Utility Name] Identity Theft Prevention Program Effective beginning, 2008 Minnesota Municipal Utilities Association Sample Red Flag policy I. PROGRAM ADOPTION The [Utility Name] ("Utility") developed
[Utility Name] Identity Theft Prevention Program Effective beginning, 2008 Minnesota Municipal Utilities Association Sample Red Flag policy I. PROGRAM ADOPTION The [Utility Name] ("Utility") developed
YOUR PRIVACY RIGHTS Privacy Policy General Col ection and Use voluntarily
 YOUR PRIVACY RIGHTS Privacy Policy The Travel Society (DBA The Travel Society, LLC ) (AKA: Company ) in addition to the Members (AKA: Affiliates ) of The Travel Society values your privacy. This Privacy
YOUR PRIVACY RIGHTS Privacy Policy The Travel Society (DBA The Travel Society, LLC ) (AKA: Company ) in addition to the Members (AKA: Affiliates ) of The Travel Society values your privacy. This Privacy
Community Web Portal. A Guide for Parents and Students
 Community Web Portal A Guide for Parents and Students Since 2002, Sapphire Software has provided exceptional software application solutions for school districts needs. To prepare students for success in
Community Web Portal A Guide for Parents and Students Since 2002, Sapphire Software has provided exceptional software application solutions for school districts needs. To prepare students for success in
Skyward: Bells & Whistles
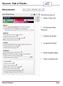 Have it your way!! From this screen you can: Choose a Theme color Set Report processing Preferences Customize the Interface Set options for Browses Enable Navigation options Utilize Accessibility tools
Have it your way!! From this screen you can: Choose a Theme color Set Report processing Preferences Customize the Interface Set options for Browses Enable Navigation options Utilize Accessibility tools
Parent. Portal. User. Manual
 EDUCATIONAL SERVICES Parent Portal User Manual Version 3.0 GENESIS STUDENT INFORMATION SYSTEM PARENT PORTAL Introduction 3 Logging In & Logging Out 4 Student Summary Dashboard The Dashboard Selecting a
EDUCATIONAL SERVICES Parent Portal User Manual Version 3.0 GENESIS STUDENT INFORMATION SYSTEM PARENT PORTAL Introduction 3 Logging In & Logging Out 4 Student Summary Dashboard The Dashboard Selecting a
Information Privacy Statement
 Information Privacy Statement Commitment to Privacy The University of Florida values individuals' privacy and actively seeks to preserve the privacy rights of those who share information with us. Your
Information Privacy Statement Commitment to Privacy The University of Florida values individuals' privacy and actively seeks to preserve the privacy rights of those who share information with us. Your
Parent. Access. Manual
 EDUCATIONAL SERVICES Parent Access Manual GENESIS STUDENT INFORMATION SYSTEM PARENT ACCESS I. Introduction II. Logging In III. Student Summary Dashboard Screen A. Viewing the Dashboard B. Choosing a Student
EDUCATIONAL SERVICES Parent Access Manual GENESIS STUDENT INFORMATION SYSTEM PARENT ACCESS I. Introduction II. Logging In III. Student Summary Dashboard Screen A. Viewing the Dashboard B. Choosing a Student
WOIS Cell Phone Policy
 Dear Secondary Parents and Students, I hope that you are finding the time to enjoy the final days of summer. The WOIS School Based Planning Team has worked diligently throughout the summer to revise and
Dear Secondary Parents and Students, I hope that you are finding the time to enjoy the final days of summer. The WOIS School Based Planning Team has worked diligently throughout the summer to revise and
How to complete academic registration
 How to complete academic registration There are two main parts to completing your registration; academic and financial. This guide will focus on academic registration. 1. Log in to your Student Center.
How to complete academic registration There are two main parts to completing your registration; academic and financial. This guide will focus on academic registration. 1. Log in to your Student Center.
UF CEMP Support Group Annex: Public Safety
 UF CEMP Support Group Annex: Public Safety Lead Representatives University of Supporting Departments External Partners Enrollment Management Shands Hospital Safety & Security Alachua County Emergency Management
UF CEMP Support Group Annex: Public Safety Lead Representatives University of Supporting Departments External Partners Enrollment Management Shands Hospital Safety & Security Alachua County Emergency Management
St Bernard s Primary School Data Protection Policy
 St Bernard s Primary School Data Protection Policy St Bernard s RC Primary School, A Voluntary Academy Approved by Governors: 11.11.2015 Review date: Autumn 2016 St Bernard s Data Protection Policy General
St Bernard s Primary School Data Protection Policy St Bernard s RC Primary School, A Voluntary Academy Approved by Governors: 11.11.2015 Review date: Autumn 2016 St Bernard s Data Protection Policy General
Data Protection Impact Assessment (DPIA) Last Updated: 21 June, 2018
 Data Protection Impact Assessment (DPIA) Last Updated: 21 June, 2018 About CareMonkey CareMonkey is an online and mobile platform for Forms, Medical Records and Field Trip Management. CareMonkey is designed
Data Protection Impact Assessment (DPIA) Last Updated: 21 June, 2018 About CareMonkey CareMonkey is an online and mobile platform for Forms, Medical Records and Field Trip Management. CareMonkey is designed
2017 Arkansas 4-H Shooting Sports State Range-Events Registration Materials For Participants, Coaches, Staff
 07 Arkansas -H Shooting Sports State Range-Events Registration Materials For Participants, Coaches, Staff.77 Air Rifle. Smallbore Rifle 5 Spot Archery Shotgun Trap.77 Air Pistol. Smallbore Pistol Muzzle
07 Arkansas -H Shooting Sports State Range-Events Registration Materials For Participants, Coaches, Staff.77 Air Rifle. Smallbore Rifle 5 Spot Archery Shotgun Trap.77 Air Pistol. Smallbore Pistol Muzzle
PRIVACY NOTICE ADMISSIONS TO HEALTH-RELATED GRADUATE PROGRAMS
 PRIVACY NOTICE ADMISSIONS TO HEALTH-RELATED GRADUATE PROGRAMS The University of Southern California ( USC or the University ) is committed to safeguarding the privacy of individuals who apply for admission.
PRIVACY NOTICE ADMISSIONS TO HEALTH-RELATED GRADUATE PROGRAMS The University of Southern California ( USC or the University ) is committed to safeguarding the privacy of individuals who apply for admission.
OHIO STATE UNIVERSITY EXTENSION
 OHIO STATE UNIVERSITY EXTENSION 4HONLINE IS... The OFFICIAL Ohio 4-H Youth Development Program database for enrolled 4-H members and volunteers. This system works as a partnership between the 4-H family
OHIO STATE UNIVERSITY EXTENSION 4HONLINE IS... The OFFICIAL Ohio 4-H Youth Development Program database for enrolled 4-H members and volunteers. This system works as a partnership between the 4-H family
NATE Exam Administration Script
 NATE Exam Administration Script This script should be completely read for all of NATE s Paper Exams, which includes both NATE and ICE certification exams. Reading this script gives all candidates an equal
NATE Exam Administration Script This script should be completely read for all of NATE s Paper Exams, which includes both NATE and ICE certification exams. Reading this script gives all candidates an equal
2016 SC REGIONAL HOUSING AUTHORITY NO. 3 S EIV SECURITY POLICY
 2016 SC REGIONAL HOUSING AUTHORITY NO. 3 S EIV SECURITY POLICY Purpose: The purpose of this policy is to provide instruction and information to staff, auditors, consultants, contractors and tenants on
2016 SC REGIONAL HOUSING AUTHORITY NO. 3 S EIV SECURITY POLICY Purpose: The purpose of this policy is to provide instruction and information to staff, auditors, consultants, contractors and tenants on
Census/Registration Manual
 Census/Registration Manual Version 2011M.1038 This manual created by Custom Computer Specialists, Inc. 70 Suffolk Court Hauppauge, NY 11788 www.customonline.com Copyright 2006 Custom Computer Specialists,
Census/Registration Manual Version 2011M.1038 This manual created by Custom Computer Specialists, Inc. 70 Suffolk Court Hauppauge, NY 11788 www.customonline.com Copyright 2006 Custom Computer Specialists,
What is epals SchoolMail? Student Accounts. Passwords. Safety. Flag Attachment
 What is epals SchoolMail? http://www.epals.com/ epals Schoolmail is a complete, Internet-based email solution and collaborative toolset designed for the education environment. Student Accounts Students
What is epals SchoolMail? http://www.epals.com/ epals Schoolmail is a complete, Internet-based email solution and collaborative toolset designed for the education environment. Student Accounts Students
Seattle University Identity Theft Prevention Program. Purpose. Definitions
 Seattle University Identity Theft Prevention Program Purpose The purpose of the program is to establish an Identity Theft Prevention Program designed to detect, prevent and mitigate identity theft in connection
Seattle University Identity Theft Prevention Program Purpose The purpose of the program is to establish an Identity Theft Prevention Program designed to detect, prevent and mitigate identity theft in connection
OHIO STATE UNIVERSITY EXTENSION
 OHIO STATE UNIVERSITY EXTENSION 4HONLINE IS... The OFFICIAL Ohio 4-H Youth Development Program database for enrolled 4-H members and volunteers. This system works as a partnership between the 4-H family
OHIO STATE UNIVERSITY EXTENSION 4HONLINE IS... The OFFICIAL Ohio 4-H Youth Development Program database for enrolled 4-H members and volunteers. This system works as a partnership between the 4-H family
Training Guide. Discipline. May 2012
 Training Guide Discipline May 2012 Copyright 2012 by Texas Computer Cooperative All rights reserved Education Service Center, Region 20 1314 Hines Avenue San Antonio, TX 78208-1899 This manual was prepared
Training Guide Discipline May 2012 Copyright 2012 by Texas Computer Cooperative All rights reserved Education Service Center, Region 20 1314 Hines Avenue San Antonio, TX 78208-1899 This manual was prepared
Broadcast Notification solutions
 Broadcast Notification solutions Fast, accurate group communication to enhance your security response security.gallagher.com Broadcast Notification solutions Mobile Network Provider Staff in building 2
Broadcast Notification solutions Fast, accurate group communication to enhance your security response security.gallagher.com Broadcast Notification solutions Mobile Network Provider Staff in building 2
I-765 Form Completion Guide: 24-Month STEM OPT Extension
 I-765 Form Completion Guide: 24-Month STEM OPT Extension 2121 Euclid Ave MC 412 Important Advice: 1. Type your I-765 Use the fillable PDF I-765 on the USCIS website to type in your answers. Typing helps
I-765 Form Completion Guide: 24-Month STEM OPT Extension 2121 Euclid Ave MC 412 Important Advice: 1. Type your I-765 Use the fillable PDF I-765 on the USCIS website to type in your answers. Typing helps
2016 National Leadership Conference Registration Instructions
 2016 National Leadership Conference Registration Instructions Contents Overview of the 2016 NLC Registration Process... 2 How to Access the Registration System/Portal... 3 Register Chapter Advisers...
2016 National Leadership Conference Registration Instructions Contents Overview of the 2016 NLC Registration Process... 2 How to Access the Registration System/Portal... 3 Register Chapter Advisers...
Identity Theft Prevention Policy
 Identity Theft Prevention Policy Purpose of the Policy To establish an Identity Theft Prevention Program (Program) designed to detect, prevent and mitigate identity theft in connection with the opening
Identity Theft Prevention Policy Purpose of the Policy To establish an Identity Theft Prevention Program (Program) designed to detect, prevent and mitigate identity theft in connection with the opening
Parchment Guide to Ordering Official Transcripts
 Parchment Guide to Ordering Official Transcripts www. 2 Contents OVERVIEW 4 How it works 4 CREATE AN ACCOUNT AND ADD YOUR SCHOOL 5 ORDER YOUR TRANSCRIPT 7 TRACK YOUR TRANSCRIPT 12 TRANSCRIPT STATUSES 13
Parchment Guide to Ordering Official Transcripts www. 2 Contents OVERVIEW 4 How it works 4 CREATE AN ACCOUNT AND ADD YOUR SCHOOL 5 ORDER YOUR TRANSCRIPT 7 TRACK YOUR TRANSCRIPT 12 TRANSCRIPT STATUSES 13
PHS BYOD Frequently Asked. Question
 PHS BYOD Frequently Asked Questions We are fully implementing BYOD again at Pickens High School this year. This program will allow students to use their mobile devices at school as an educational tool.
PHS BYOD Frequently Asked Questions We are fully implementing BYOD again at Pickens High School this year. This program will allow students to use their mobile devices at school as an educational tool.
White Paper: Next generation disaster data infrastructure CODATA LODGD Task Group 2017
 White Paper: Next generation disaster data infrastructure CODATA LODGD Task Group 2017 Call for Authors This call for authors seeks contributions from academics and scientists who are in the fields of
White Paper: Next generation disaster data infrastructure CODATA LODGD Task Group 2017 Call for Authors This call for authors seeks contributions from academics and scientists who are in the fields of
E-Flash Series. Electronic Door Locks
 E-Flash Series Electronic Door Locks Kaba Australia has been supplying security solutions to the Australian commercial market since 2001. Kaba Australia s locks, high security key systems and electronic
E-Flash Series Electronic Door Locks Kaba Australia has been supplying security solutions to the Australian commercial market since 2001. Kaba Australia s locks, high security key systems and electronic
University Facilities Management (UFM) Access Control Procedure (non-residence areas)
 University Facilities Management (UFM) Access Control Procedure (non-residence areas) Date of Issue: October 1, 2015 A. PURPOSE University Facilities Management s (UFM) Lock Shop Access Control Procedure
University Facilities Management (UFM) Access Control Procedure (non-residence areas) Date of Issue: October 1, 2015 A. PURPOSE University Facilities Management s (UFM) Lock Shop Access Control Procedure
Prevention of Identity Theft in Student Financial Transactions AP 5800
 Reference: Fair and Accurate Credit Transactions Act (Pub. L. 108-159) The Board recognizes that some activities of the Shasta-Tehama-Trinity Joint Community College District, "District," are subject to
Reference: Fair and Accurate Credit Transactions Act (Pub. L. 108-159) The Board recognizes that some activities of the Shasta-Tehama-Trinity Joint Community College District, "District," are subject to
Standard for Security of Information Technology Resources
 MARSHALL UNIVERSITY INFORMATION TECHNOLOGY COUNCIL Standard ITP-44 Standard for Security of Information Technology Resources 1 General Information: Marshall University expects all individuals using information
MARSHALL UNIVERSITY INFORMATION TECHNOLOGY COUNCIL Standard ITP-44 Standard for Security of Information Technology Resources 1 General Information: Marshall University expects all individuals using information
Student Guide G. Technical Support
 What is Starfish? Student Guide G Starfish is an early warning and student tracking module that collects information and manages concerns so that you as a student can engage more deeply with your instructors
What is Starfish? Student Guide G Starfish is an early warning and student tracking module that collects information and manages concerns so that you as a student can engage more deeply with your instructors
( Utility Name ) Identity Theft Prevention Program
 ***DRAFT*** ( Utility Name ) Identity Theft Prevention Program Implemented as of, 2008 *** This document is intended to give guidance to municipal utilities in their understanding of the FTC Red Flag Rule.
***DRAFT*** ( Utility Name ) Identity Theft Prevention Program Implemented as of, 2008 *** This document is intended to give guidance to municipal utilities in their understanding of the FTC Red Flag Rule.
Campus PORTAL INSTRUCTIONAL PACKET for FCE Leads. August 23, 2016
 Campus PORTAL INSTRUCTIONAL PACKET for FCE Leads August 23, 2016 Table of Contents Contents TABLE OF CONTENTS... 2 SECTION 1 ACCESSING INFINITE CAMPUS... 3 PARENT PORTAL LETTER... 3 ACCOUNT ACTIVATION...
Campus PORTAL INSTRUCTIONAL PACKET for FCE Leads August 23, 2016 Table of Contents Contents TABLE OF CONTENTS... 2 SECTION 1 ACCESSING INFINITE CAMPUS... 3 PARENT PORTAL LETTER... 3 ACCOUNT ACTIVATION...
UNIVERSITY OF MASSACHUSETTS AMHERST INFORMATION SECURITY POLICY October 25, 2017
 UNIVERSITY OF MASSACHUSETTS AMHERST INFORMATION SECURITY POLICY October 25, 2017 I. Introduction Institutional information, research data, and information technology (IT) resources are critical assets
UNIVERSITY OF MASSACHUSETTS AMHERST INFORMATION SECURITY POLICY October 25, 2017 I. Introduction Institutional information, research data, and information technology (IT) resources are critical assets
OHIO STATE UNIVERSITY EXTENSION
 OHIO STATE UNIVERSITY EXTENSION 4HONLINE IS... The OFFICIAL Ohio 4-H Youth Development Program database for enrolled 4-H members and volunteers. This system works as a partnership between the 4-H family
OHIO STATE UNIVERSITY EXTENSION 4HONLINE IS... The OFFICIAL Ohio 4-H Youth Development Program database for enrolled 4-H members and volunteers. This system works as a partnership between the 4-H family
Bonzi Team 101 (Youth Sports): What does Bonzi Team do?
 Bonzi Team 101 (Youth Sports): What does Bonzi Team do? AA-00427 Bonzi Team is an extension of your Club or League software that imports all team information directly from your software to Bonzi Team,
Bonzi Team 101 (Youth Sports): What does Bonzi Team do? AA-00427 Bonzi Team is an extension of your Club or League software that imports all team information directly from your software to Bonzi Team,
This Policy applies to all staff and other authorised users in St Therese School.
 St. Therese School Computer and Internet Policy STAFF Policy Statement All staff and other authorised users of St Therese information and communications technology are to use the technology only in a way
St. Therese School Computer and Internet Policy STAFF Policy Statement All staff and other authorised users of St Therese information and communications technology are to use the technology only in a way
POLICIES AND PROCEDURES
 Integrated Information Technology Services POLICIES AND PROCEDURES Utica College Email POLICY: Email is Utica College s sole accepted mechanism for official electronic communication in the normal conduct
Integrated Information Technology Services POLICIES AND PROCEDURES Utica College Email POLICY: Email is Utica College s sole accepted mechanism for official electronic communication in the normal conduct
Archive and Records Management Policy
 Archive and Records Management Policy Rationale This Policy is to enable Thomas Carr College to create and maintain accurate and complete records that support and provide evidence of the College s business
Archive and Records Management Policy Rationale This Policy is to enable Thomas Carr College to create and maintain accurate and complete records that support and provide evidence of the College s business
Smart Education Requires a Smart Wireless Platform
 Smart Education Requires a Smart Wireless Platform Smart Education Requires a Smart Wireless Platform Using Mist to Deliver Amazing Wireless Experiences to Students, Teachers, Administrators and IT Personnel
Smart Education Requires a Smart Wireless Platform Smart Education Requires a Smart Wireless Platform Using Mist to Deliver Amazing Wireless Experiences to Students, Teachers, Administrators and IT Personnel
Volunteer Guide. Contents
 Volunteer Guide Contents Registering for the Volunteer Tracker... 2 Translating the form... 2 Completing the Volunteer Service Application Form... 3 Checking the status of your application... 6 Logging
Volunteer Guide Contents Registering for the Volunteer Tracker... 2 Translating the form... 2 Completing the Volunteer Service Application Form... 3 Checking the status of your application... 6 Logging
JSC THE JUSTICE & SAFETY CENTER. Snapshot 2014
 JSC THE JUSTICE & SAFETY CENTER Snapshot 2014 The Justice & Safety Center (JSC) is comprised of a team of faculty and staff professionals at Eastern Kentucky University (EKU) dedicated to strengthening
JSC THE JUSTICE & SAFETY CENTER Snapshot 2014 The Justice & Safety Center (JSC) is comprised of a team of faculty and staff professionals at Eastern Kentucky University (EKU) dedicated to strengthening
Lawrenceburg Community Schools Technology Laptop USE AGREEMENT
 Lawrenceburg Community Schools Technology Laptop USE AGREEMENT Please read this entire section carefully. This agreement is made effective upon receipt of a laptop, between The Lawrenceburg Community School
Lawrenceburg Community Schools Technology Laptop USE AGREEMENT Please read this entire section carefully. This agreement is made effective upon receipt of a laptop, between The Lawrenceburg Community School
Parent/Student. Web Access. User. Manual
 EDUCATIONAL SERVICES Parent/Student Web Access User Manual GENESIS STUDENT INFORMATION SYSTEM WEB ACCESS I Introduction p. 3 II Logging In & Logging Out p. 4 III Student Summary Dashboard (Summary) Screen
EDUCATIONAL SERVICES Parent/Student Web Access User Manual GENESIS STUDENT INFORMATION SYSTEM WEB ACCESS I Introduction p. 3 II Logging In & Logging Out p. 4 III Student Summary Dashboard (Summary) Screen
Electronic Device Policy (EDP)
 Powerstown Educate Together National School Roll No: 20384J Powerstown Road, Tyrrelstown, Dublin 15 Telephone: 01 8272018 Email: info@powerstownet.com www.powerstownet.com Powerstown Educate Together National
Powerstown Educate Together National School Roll No: 20384J Powerstown Road, Tyrrelstown, Dublin 15 Telephone: 01 8272018 Email: info@powerstownet.com www.powerstownet.com Powerstown Educate Together National
NCUSD 203 Campus Portal Login FAQ
 This document will provide you answers to all of your questions regarding setting up and troubleshooting issues with your Campus Portal Login Account. Please see the list of frequently questions below.
This document will provide you answers to all of your questions regarding setting up and troubleshooting issues with your Campus Portal Login Account. Please see the list of frequently questions below.
2017_Privacy and Information Security_English_Content
 2017_Privacy and Information Security_English_Content 2.3 Staff includes all permanent or temporary, full-time, part-time, casual or contract employees, trainees and volunteers, including but not limited
2017_Privacy and Information Security_English_Content 2.3 Staff includes all permanent or temporary, full-time, part-time, casual or contract employees, trainees and volunteers, including but not limited
UNIVERSITY OF MASSACHUSETTS AMHERST INFORMATION SECURITY POLICY September 20, 2017
 UNIVERSITY OF MASSACHUSETTS AMHERST INFORMATION SECURITY POLICY September 20, 2017 I. Introduction Institutional information, research data, and information technology (IT) resources are critical assets
UNIVERSITY OF MASSACHUSETTS AMHERST INFORMATION SECURITY POLICY September 20, 2017 I. Introduction Institutional information, research data, and information technology (IT) resources are critical assets
Mobile Web Pages User Guide. PowerSchool 7.x Student Information System
 PowerSchool 7.x Student Information System Released December 2011 Document Owner: Documentation Services This edition applies to Release 7.1 of the PowerSchool software and to all subsequent releases and
PowerSchool 7.x Student Information System Released December 2011 Document Owner: Documentation Services This edition applies to Release 7.1 of the PowerSchool software and to all subsequent releases and
The information in this manual is designed to answer the following questions:
 Genesis Security Overview This document is concerned with user access security. Genesis User Access Security is designed to be comprehensive and easy to administer. The goal of User Access Security is
Genesis Security Overview This document is concerned with user access security. Genesis User Access Security is designed to be comprehensive and easy to administer. The goal of User Access Security is
Center For Emergency Response and Public Safety
 5 Steps to Redeeming your Course Code Welcome to CERPS (the Center for Emergency Response ), your online learning portal for the Ontario Fire Service. These instructions will help you to establish your
5 Steps to Redeeming your Course Code Welcome to CERPS (the Center for Emergency Response ), your online learning portal for the Ontario Fire Service. These instructions will help you to establish your
Guide to My DCC WHAT IS MY DCC? LOGGING IN YOUR PERSONAL HOMEPAGE
 Guide to My DCC WHAT IS MY DCC? Welcome to My DCC! My DCC is the online community of Door Creek Church. It provides an easy and effective way to communicate and connect with groups, staff and others who
Guide to My DCC WHAT IS MY DCC? Welcome to My DCC! My DCC is the online community of Door Creek Church. It provides an easy and effective way to communicate and connect with groups, staff and others who
NCAA Compliance Forms Database Frequently Asked Questions. Are institutions required to use the NCAA Compliance Forms Database?
 General Are institutions required to use the NCAA Compliance Forms Database? No. Institutions are not required to use the NCAA Compliance Forms Database. If our institution would like to administer the
General Are institutions required to use the NCAA Compliance Forms Database? No. Institutions are not required to use the NCAA Compliance Forms Database. If our institution would like to administer the
Tenaya Laptop Program Application *A tech and project-based GATE program*
 2018-2019 Tenaya Laptop Program Application *A tech and project-based GATE program* Please include the following when returning the Tenaya Laptop Program Application: General Laptop Program Information
2018-2019 Tenaya Laptop Program Application *A tech and project-based GATE program* Please include the following when returning the Tenaya Laptop Program Application: General Laptop Program Information
The GDPR toolkit. How to guide for Executive Committees. Version March 2018
 The GDPR toolkit How to guide for Executive Committees Version 1.0 - March 2018 Contents Document Purpose... 3 What s included... 3 Step 1 - How to assess your data... 5 a) What is GDPR?... 5 b) Video
The GDPR toolkit How to guide for Executive Committees Version 1.0 - March 2018 Contents Document Purpose... 3 What s included... 3 Step 1 - How to assess your data... 5 a) What is GDPR?... 5 b) Video
EDENRED COMMUTER BENEFITS SOLUTIONS, LLC PRIVACY POLICY. Updated: April 2017
 This Privacy Policy (this Privacy Policy ) applies to Edenred Commuter Benefits Solutions, LLC, (the Company ) online interface (i.e., website or mobile application) and any Edenred Commuter Benefit Solutions,
This Privacy Policy (this Privacy Policy ) applies to Edenred Commuter Benefits Solutions, LLC, (the Company ) online interface (i.e., website or mobile application) and any Edenred Commuter Benefit Solutions,
Nebraska State College System Cellular Services Procedures Effective Date June 15, 2012 Updated August 13, 2015
 Nebraska State College System Cellular Services Procedures Effective Date June 15, 2012 Updated August 13, 2015 Definitions Cellular Telephone Service For the purposes of this policy, cellular telephone
Nebraska State College System Cellular Services Procedures Effective Date June 15, 2012 Updated August 13, 2015 Definitions Cellular Telephone Service For the purposes of this policy, cellular telephone
eschoolplus 3.1 New Features
 South Central RIC 435 Glenwood Road Binghamton, NY 13905 607-766-3750 eschoolplus 3.1 New Features 1990-2014 SunGard Public Sector Inc. All rights reserved. No part of this publication may be reproduced
South Central RIC 435 Glenwood Road Binghamton, NY 13905 607-766-3750 eschoolplus 3.1 New Features 1990-2014 SunGard Public Sector Inc. All rights reserved. No part of this publication may be reproduced
TxEIS txconnect Training Guide August, 2012
 August, 2012 Education Service Center 3001 North Freeway Fort Worth, Texas 76106 Contents Introduction...3 How to Display a Page in another Language..4 How to Display Help 5 How to Contact the Teacher..6
August, 2012 Education Service Center 3001 North Freeway Fort Worth, Texas 76106 Contents Introduction...3 How to Display a Page in another Language..4 How to Display Help 5 How to Contact the Teacher..6
St Edmund Arrowsmith Catholic Centre for Learning
 St Edmund Arrowsmith Catholic Centre for Learning Mobile Device Policy (Students) September 2016 This Policy was adopted and ratified by the Full Governing Body of SEA. C.F.L. at the meeting held on Signed...
St Edmund Arrowsmith Catholic Centre for Learning Mobile Device Policy (Students) September 2016 This Policy was adopted and ratified by the Full Governing Body of SEA. C.F.L. at the meeting held on Signed...
Privacy Policy. How we handle your information you provide to us. Updated: 14 March 2016
 Privacy Policy How we handle your information you provide to us Updated: 14 March 2016 Overview Enteronline (Pty) Ltd and its affiliated companies and subsidiaries (collectively, Entrytime Enteronline,
Privacy Policy How we handle your information you provide to us Updated: 14 March 2016 Overview Enteronline (Pty) Ltd and its affiliated companies and subsidiaries (collectively, Entrytime Enteronline,
10 Hidden IT Risks That Might Threaten Your Business
 (Plus 1 Fast Way to Find Them) Your business depends on intelligence. But can you count on your technology? You may not be in the intelligence technology business, but it s probably impossible to imagine
(Plus 1 Fast Way to Find Them) Your business depends on intelligence. But can you count on your technology? You may not be in the intelligence technology business, but it s probably impossible to imagine
Welcome to the Student Success Network
 Welcome to the Student Success Network The Student Success Network provides you with a central location to connect to the people and services that can help you finish what you start all accessible right
Welcome to the Student Success Network The Student Success Network provides you with a central location to connect to the people and services that can help you finish what you start all accessible right
Lobby Track Getting Started Guide. An Introduction to Lobby Track
 Lobby Track Getting Started Guide An Introduction to Lobby Track Contents Introducing Lobby Track... 3 Overview... 3 A Quick Start... 6 Quick Start Option 1... 6 Getting to Configuration... 7 Changing
Lobby Track Getting Started Guide An Introduction to Lobby Track Contents Introducing Lobby Track... 3 Overview... 3 A Quick Start... 6 Quick Start Option 1... 6 Getting to Configuration... 7 Changing
LEGAL ADVICE ON THE USE OF MOBILE PHONES, PROTABLE COMPUTER GAMES, TAPE RECORDERS AND CAMERAS IN SCHOOL
 LEGAL ADVICE ON THE USE OF MOBILE PHONES, PROTABLE COMPUTER GAMES, TAPE RECORDERS AND CAMERAS IN SCHOOL DIOCESE OF WAGGA WAGGA Policy Number 02/10 Policy Name Legal advice on the use of Mobile Phones,
LEGAL ADVICE ON THE USE OF MOBILE PHONES, PROTABLE COMPUTER GAMES, TAPE RECORDERS AND CAMERAS IN SCHOOL DIOCESE OF WAGGA WAGGA Policy Number 02/10 Policy Name Legal advice on the use of Mobile Phones,
Integration of Agilent OpenLAB CDS EZChrom Edition with OpenLAB ECM Compliance with 21 CFR Part 11
 OpenLAB CDS Integration of Agilent OpenLAB CDS EZChrom Edition with OpenLAB ECM Compliance with 21 CFR Part 11 Technical Note Introduction Part 11 in Title 21 of the Code of Federal Regulations includes
OpenLAB CDS Integration of Agilent OpenLAB CDS EZChrom Edition with OpenLAB ECM Compliance with 21 CFR Part 11 Technical Note Introduction Part 11 in Title 21 of the Code of Federal Regulations includes
Faculty and Staff Instructions to Update MY DATA in Infinite Campus
 Faculty and Staff Instructions to Update MY DATA in Infinite Campus This can be completed anywhere you have an Internet connection :at school or at home. Allow three business days for processing!! Background:
Faculty and Staff Instructions to Update MY DATA in Infinite Campus This can be completed anywhere you have an Internet connection :at school or at home. Allow three business days for processing!! Background:
Campus Safety: Five Advances in Physical Security for Schools
 Brochure Campus Safety: Five Advances in Physical Security for Schools Physical Safety in a More Complex World Recent headlines underscore the need for better ways to protect students and staff from threats
Brochure Campus Safety: Five Advances in Physical Security for Schools Physical Safety in a More Complex World Recent headlines underscore the need for better ways to protect students and staff from threats
MORTON COLLEGE. Emergency Notification System
 MORTON COLLEGE Emergency Notification System About This Guide This guide will provide some frequently asked questions about the emergency notification service. This guide also covers how to login and how
MORTON COLLEGE Emergency Notification System About This Guide This guide will provide some frequently asked questions about the emergency notification service. This guide also covers how to login and how
OHIO STATE UNIVERSITY EXTENSION
 OHIO STATE UNIVERSITY EXTENSION 4HONLINE IS... The OFFICIAL Ohio 4-H Youth Development Program database for enrolled 4-H members and volunteers. This system works as a partnership between the 4-H family
OHIO STATE UNIVERSITY EXTENSION 4HONLINE IS... The OFFICIAL Ohio 4-H Youth Development Program database for enrolled 4-H members and volunteers. This system works as a partnership between the 4-H family
Canadian Anti-Spam Legislation (CASL)
 Canadian Anti-Spam Legislation (CASL) FREQUENTLY ASKED QUESTIONS The purpose of this document is to assist and guide U of R employees regarding their obligations under the Canadian Anti-Spam Legislation
Canadian Anti-Spam Legislation (CASL) FREQUENTLY ASKED QUESTIONS The purpose of this document is to assist and guide U of R employees regarding their obligations under the Canadian Anti-Spam Legislation
