The ten people she was considering as conspirators were: Anne#, Bob, Carol, Dave*, Ellen, Fred,
|
|
|
- Kathleen Black
- 5 years ago
- Views:
Transcription
1 2012 ICM Problem Modeling for Crime Busting Your organization, the Intergalactic Crime Modelers (ICM), is investigating a conspiracy to commit a criminal act. The investigators are highly confident they know several members of the conspiracy, but hope to identify the other members and the leaders before they make arrests. The conspirators and the possible suspected conspirators all work for the same company in a large office complex. The company has been growing fast and making a name for itself in developing and marketing computer software for banks and credit card companies. ICM has recently found a small set of messages from a group of 82 workers in the company that they believe will help them find the most likely candidates for the unidentified co conspirators and unknown leaders. Since the message traffic is for all the office workers in the company, it is very likely that some (maybe many) of the identified communicators in the message traffic are not involved in the conspiracy. In fact, they are certain that they know some people who are not in the conspiracy. The goal of the modeling effort will be to identify people in the office complex who are the most likely conspirators. A priority list would be ideal so ICM could investigate, place under surveillance, and/or interrogate the most likely candidates. A discriminate line separating conspirators from non conspirators would also be helpful to distinctly categorize the people in each group. It would also be helpful to the DA s office if the model nominated the conspiracy leaders. Before the data of the current case are given to your crime modeling team, your supervisor gives you the following scenario (called Investigation EZ) that she worked on a few years ago in another city. Even though she is very proud of her work on the EZ case, she says it is just a very small, simple example, but it may help you understand your task. Her data follow: The ten people she was considering as conspirators were: Anne#, Bob, Carol, Dave*, Ellen, Fred, George*, Harry, Inez, and Jaye#. (* indicates prior known conspirators, # indicate prior known nonconspirators) Chronology of the 28 messages that she had for her case with a code number for the topic of each message that she assigned based on her analysis of the message: Anne to Bob: Why were you late today? (1) Bob to Carol: That darn Anne always watches me. I wasn't late. (1) Carol to Dave: Anne and Bob are fighting again over Bob's tardiness. (1) Dave to Ellen: I need to see you this morning. When can you come by? Bring the budget files. (2) Dave to Fred: I can come by and see you anytime today. Let me know when it is a good time. Should I bring the budget files? (2) Dave to George: I will see you later lots to talk about. I hope the others are ready. It is important to get this right. (3) Harry to George: You seem stressed. What is going on? Our budget will be fine. (2) (4)
2 Inez to George: I am real tired today. How are you doing? ( 5) Jaye to Inez: Not much going on today. Wanna go to lunch today? (5) Inez to Jaye: Good thing it is quiet. I am exhausted. Can't do lunch today sorry! (5) George to Dave: Time to talk now! (3) Jaye to Anne: Can you go to lunch today? (5) Dave to George: I can't. On my way to see Fred. (3) George to Dave: Get here after that. (3) Anne to Carol: Who is supposed to watch Bob? He is goofing off all the time. (1) Carol to Anne: Leave him alone. He is working well with George and Dave. (1) George to Dave: This is important. Darn Fred. How about Ellen? (3) Ellen to George: Have you talked with Dave? (3) George to Ellen: Not yet. Did you? (3) Bob to Anne: I wasn't late. And just so you know I am working through lunch. (1) Bob to Dave: Tell them I wasn't late. You know me. (1) Ellen to Carol: Get with Anne and figure out the budget meeting schedule for next week and help me calm George. (2) Harry to Dave: Did you notice that George is stressed out again today? (4) Dave to George: Darn Harry thinks you are stressed. Don't get him worried or he will be nosing around. (4) George to Harry: Just working late and having problems at home. I will be fine. (4) Ellen to Harry: Would it be OK, if I miss the meeting today? Fred will be there and he knows the budget better than I do. (2) Harry to Fred: I think next year's budget is stressing out a few people. Maybe we should take time to reassure people today. (2) (4) Fred to Harry: I think our budget is pretty healthy. I don't see anything to stress over. (2) END of MESSAGE TRAFFIC
3 Your supervisor points outs that she assigned and coded only 5 different topics of messages: 1) Bob's tardiness, 2) the budget, 3) important unknown issue but assumed to be part of conspiracy, 4) George's stress, and 5) lunch and other social issues. As seen in the message coding, some messages had two topics assigned because of the content of the messages. The way your supervisor analyzed her situation was with a network that showed the communication links and the types of messages. The following figure is a model of the message network that resulted with the code for the types of messages annotated on the network graph. Figure 1: Network of messages from EZ Case Your supervisor points out that in addition to known conspirators George and Dave, Ellen and Carol were indicted for the conspiracy based on your supervisor's analysis and later Bob self admitted his involvement in a plea bargain for a reduced sentence, but the charges against Carol were later dropped. Your supervisor is still pretty sure Inez was involved, but the case against her was never established. Your supervisor's advice to your team is identify the guilty parties so that people like Inez don't get off, people like Carol are not falsely accused, and ICM gets the credit so people like Bob do not have the opportunity to get reduced sentences. The current case: Your supervisor has put together a network like database for the current case, which has the same structure, but is a bit larger in scope. The investigators have some indications that a conspiracy is taking place to embezzle funds from the company and use internet fraud to steal funds from credit cards of people who do business with the company. The small example she showed you for case EZ had only 10 people (nodes), 27 links (messages), 5 topics, 1 suspicious/conspiracy topic, 2 known conspirators, and 2
4 known non conspirators. So far, the new case has 83 nodes, 400 links (some involving more than 1 topic), over 21,000 words of message traffic, 15 topics (3 have been deemed to be suspicious), 7 known conspirators, and 8 known non conspirators. These data are given in the attached spreadsheet files: Names.xls, Topics.xls, and Messages.xls. Names.xls contains the key of node number to the office workers' names. Topics.xls contains the code for the 15 topic numbers to a short description of the topics. Because of security and privacy issues, your team will not have direct transcripts of all the message traffic. Messages.xls provides the links of the nodes that transmitted messages and the topic code numbers that the messages contained. Several messages contained up to three topics. To help visualize the message traffic, a network model of the people and message links is provided in Figure 2. In this case, the topics of the messages are not shown in the figure as they were in Figure 1. These topic numbers are given in the file Messages.xls and described in Topics.xls. Figure 2: Visual of the network model of the 83 people (nodes) and 400 messages between these people (links).
5 Requirements: Requirement 1: So far, it is known that Jean, Alex, Elsie, Paul, Ulf, Yao, and Harvey are conspirators. Also, it is known that Darlene, Tran, Jia, Ellin, Gard, Chris, Paige, and Este are not conspirators. The three known suspicious message topics are 7, 11, and 13. There is more detail about the topics in file Topics.xls. Build a model and algorithm to prioritize the 83 nodes by likelihood of being part of the conspiracy and explain your model and metrics. Jerome, Delores, and Gretchen are the senior managers of the company. It would be very helpful to know if any of them are involved in the conspiracy. Requirement 2: How would the priority list change if new information comes to light that Topic 1 is also connected to the conspiracy and that Chris is one of the conspirators? Requirement 3: A powerful technique to obtain and understand text information similar to this message traffic is called semantic network analysis; as a methodology in artificial intelligence and computational linguistics, it provides a structure and process for reasoning about knowledge or language. Another computational linguistics capability in natural language processing is text analysis. For our crime busting scenario, explain how semantic and text analyses of the content and context of the message traffic (if you could obtain the original messages) could empower your team to develop even better models and categorizations of the office personnel. Did you use any of these capabilities on the topic descriptions in file Topics.xls to enhance your model? Requirement 4: Your complete report will eventually go to the DA so it must be detailed and clearly state your assumptions and methodology, but cannot exceed 20 pages of write up. You may include your programs as appendices in separate files that do not count in your page restriction, but including these programs is not necessary. Your supervisor wants ICM to be the world's best in solving whitecollar, high tech conspiracy crimes and hopes your methodology will contribute to solving important cases around the world, especially those with very large databases of message traffic (thousands of people with tens of thousands of messages and possibly millions of words). She specifically asked you to include a discussion on how more thorough network, semantic, and text analyses of the message contents could help with your model and recommendations. As part of your report to her, explain the network modeling techniques you have used and why and how they can be used to identify, prioritize, and categorize similar nodes in a network database of any type, not just crime conspiracies and message data. For instance, could your method find the infected or diseased cells in a biological network where you had various kinds of image or chemical data for the nodes indicating infection probabilities and already identified some infected nodes? *Your ICM submission should consist of a 1 page Summary Sheet and your solution cannot exceed 20 pages for a maximum of 21 pages.
BBC Learning English Face up to Phrasals Bob & Jackie's Chemistry Project
 BBC Learning English Face up to Phrasals & 's Chemistry Project Episode 1: Let's Get Started : Ok, chemistry project. Let's get this up. Are you ok,? experiment set What's all this about a chemistry project?
BBC Learning English Face up to Phrasals & 's Chemistry Project Episode 1: Let's Get Started : Ok, chemistry project. Let's get this up. Are you ok,? experiment set What's all this about a chemistry project?
Text 1 Cell Phones Raise Security Concerns at School
 Text 1 Cell Phones Raise Security Concerns at School Many people think that students having cell phones in school is a great idea 1 idea. Many parents feel that they don t have to worry as much about their
Text 1 Cell Phones Raise Security Concerns at School Many people think that students having cell phones in school is a great idea 1 idea. Many parents feel that they don t have to worry as much about their
ProgressTestA Unit 5. Vocabulary. Grammar
 ProgressTestA Unit Vocabulary 1 Completethesentenceswithappropriate words.thefirstlettersofthewordshavebeen given. a Can you believe it? She s getting married to a man she has met on a s networking site!
ProgressTestA Unit Vocabulary 1 Completethesentenceswithappropriate words.thefirstlettersofthewordshavebeen given. a Can you believe it? She s getting married to a man she has met on a s networking site!
News English.com Ready-to-use ESL / EFL Lessons
 www.breaking News English.com Ready-to-use ESL / EFL Lessons 1,000 IDEAS & ACTIVITIES FOR LANGUAGE TEACHERS The Breaking News English.com Resource Book http://www.breakingnewsenglish.com/book.html Top
www.breaking News English.com Ready-to-use ESL / EFL Lessons 1,000 IDEAS & ACTIVITIES FOR LANGUAGE TEACHERS The Breaking News English.com Resource Book http://www.breakingnewsenglish.com/book.html Top
Computer Security module
 Computer Security module Revision notes Mark D. Ryan June 2010 There won't be a revision lecture for the Computer Security module. Instead, these notes are provided to help you prepare for the exam. Revision
Computer Security module Revision notes Mark D. Ryan June 2010 There won't be a revision lecture for the Computer Security module. Instead, these notes are provided to help you prepare for the exam. Revision
The security challenge in a mobile world
 The security challenge in a mobile world Contents Executive summary 2 Executive summary 3 Controlling devices and data from the cloud 4 Managing mobile devices - Overview - How it works with MDM - Scenario
The security challenge in a mobile world Contents Executive summary 2 Executive summary 3 Controlling devices and data from the cloud 4 Managing mobile devices - Overview - How it works with MDM - Scenario
LIU is fined $15 for not sending roster. They also cannot allocate because their allocation funds are frozen.
 Greek Council Minutes 9/28/2017 Meeting start at 7:00pm,2 nd : TDX Executive Board Senator: Timothy Graves, LAU Office Hours: Fridays 1-2pm Email: TG129@live.delhi.edu 009: passes rape/self-defense class
Greek Council Minutes 9/28/2017 Meeting start at 7:00pm,2 nd : TDX Executive Board Senator: Timothy Graves, LAU Office Hours: Fridays 1-2pm Email: TG129@live.delhi.edu 009: passes rape/self-defense class
Sir I will refer this along with the Hard Copy to Master Eyre.
 Sir I will refer this along with the Hard Copy to Master Eyre. Bailey Reed Team Leader Master's Support Unit Room E07 Queen's Bench High Court Strand London WC2A 2LL DX44450 Tel-0207-947-7772 From: Mike
Sir I will refer this along with the Hard Copy to Master Eyre. Bailey Reed Team Leader Master's Support Unit Room E07 Queen's Bench High Court Strand London WC2A 2LL DX44450 Tel-0207-947-7772 From: Mike
Image Credit: Photo by Lukas from Pexels
 Are you underestimating the importance of Keywords Research In SEO? If yes, then really you are making huge mistakes and missing valuable search engine traffic. Today s SEO world talks about unique content
Are you underestimating the importance of Keywords Research In SEO? If yes, then really you are making huge mistakes and missing valuable search engine traffic. Today s SEO world talks about unique content
Vendor Fraud. Goals of Presentation. Detection and Investigation
 Vendor Fraud Detection and Investigation by CPAs Dan Dreibelbis dlrg1@verizon.net Maryland Association of CPAs Goals of Presentation Alert CPAs to their ability to detect fraud Fraud detection is a responsibility
Vendor Fraud Detection and Investigation by CPAs Dan Dreibelbis dlrg1@verizon.net Maryland Association of CPAs Goals of Presentation Alert CPAs to their ability to detect fraud Fraud detection is a responsibility
BBC LEARNING ENGLISH 6 Minute English Wireless furniture for phones
 BBC LEARNING ENGLISH 6 Minute English Wireless furniture for phones NB: This is not a word-for-word transcript Hello and welcome to 6 Minute English. I'm and I'm. Hello. Hello,! Now,, could I borrow your
BBC LEARNING ENGLISH 6 Minute English Wireless furniture for phones NB: This is not a word-for-word transcript Hello and welcome to 6 Minute English. I'm and I'm. Hello. Hello,! Now,, could I borrow your
Lesson 52: Media (18-25 minutes)
 Main Topic VIII: Entertainment Lesson 52: Media (18-25 minutes) Today, you will practice your Reading and Listening Skills as you study texts related to MEDIA. I. READING Exercise 1: What s missing? (5-6
Main Topic VIII: Entertainment Lesson 52: Media (18-25 minutes) Today, you will practice your Reading and Listening Skills as you study texts related to MEDIA. I. READING Exercise 1: What s missing? (5-6
Design Proposal: Outline
 Design Proposal: Outline This outline should be used as a checklist to help each member of the team make sure that every section of the document meets the requirements for a design proposal. Writing Style
Design Proposal: Outline This outline should be used as a checklist to help each member of the team make sure that every section of the document meets the requirements for a design proposal. Writing Style
College Board IDOC Frequently Asked Questions
 College Board IDOC Frequently Asked Questions Produced from the College Board by West Angeles TM Education & Enrichment Program IDOC Frequently Asked Questions Q: What is the College Board and why am I
College Board IDOC Frequently Asked Questions Produced from the College Board by West Angeles TM Education & Enrichment Program IDOC Frequently Asked Questions Q: What is the College Board and why am I
# Answer Bar Response % 1 (01) Books 0 0% 2 (02) Magazines 0 0% 3 (03) Newspapers 0 0% 4 (04) Commentary 0 0% 5 (05) Drama and Literature 0 0%
 Initial Report Last Modified: 01/12/2015 1. *AWARD CATEGORY Please select the award category you are entering (select one only): 1 (01) Books 0 0% 2 (02) Magazines 0 0% 3 (03) spapers 0 0% 4 (04) Commentary
Initial Report Last Modified: 01/12/2015 1. *AWARD CATEGORY Please select the award category you are entering (select one only): 1 (01) Books 0 0% 2 (02) Magazines 0 0% 3 (03) spapers 0 0% 4 (04) Commentary
Advanced IT Risk, Security management and Cybercrime Prevention
 Advanced IT Risk, Security management and Cybercrime Prevention Course Goal and Objectives Information technology has created a new category of criminality, as cybercrime offers hackers and other tech-savvy
Advanced IT Risk, Security management and Cybercrime Prevention Course Goal and Objectives Information technology has created a new category of criminality, as cybercrime offers hackers and other tech-savvy
Student Guide. Short: Electronic Facility Clearance System (e-fcl): A Review for Industrial Security Representatives. 10 minutes
 Short: Electronic Facility Clearance System (e-fcl): A Review for Industrial Security Representatives Objective Estimated completion time Demonstrate knowledge of the e-fcl process 10 minutes Overview
Short: Electronic Facility Clearance System (e-fcl): A Review for Industrial Security Representatives Objective Estimated completion time Demonstrate knowledge of the e-fcl process 10 minutes Overview
TWINSBURG COMMUNITY SERVICE BUREAU. Senior Scam Workshop. Presented by Officer Ron Fruscella and Officer Greg Kopniske
 TWINSBURG COMMUNITY SERVICE BUREAU Senior Scam Workshop Presented by Officer Ron Fruscella and Officer Greg Kopniske CURRENT SCAMS IN TWINSBURG The I.R.S. Microsoft Driveway Roof Check I.R.S. SCAM Scammers
TWINSBURG COMMUNITY SERVICE BUREAU Senior Scam Workshop Presented by Officer Ron Fruscella and Officer Greg Kopniske CURRENT SCAMS IN TWINSBURG The I.R.S. Microsoft Driveway Roof Check I.R.S. SCAM Scammers
The Power of Unit Testing and it s impact on your business. Ashish Kumar Vice President, Engineering
 The Power of Unit Testing and it s impact on your business Ashish Kumar Vice President, Engineering Agitar Software, 2006 1 The Power of Unit Testing Why Unit Test? The Practical Reality Where do we go
The Power of Unit Testing and it s impact on your business Ashish Kumar Vice President, Engineering Agitar Software, 2006 1 The Power of Unit Testing Why Unit Test? The Practical Reality Where do we go
Blog post on updates yesterday and today:
 Beta Bug Prioritization meeting IRC Transcript 12 November 2013 Meeting was held in IRC, on the #devmo channel. Meetings are weekly, every Tuesday at 17:00 UTC (10am PST) ok, everyone, we're ready to start
Beta Bug Prioritization meeting IRC Transcript 12 November 2013 Meeting was held in IRC, on the #devmo channel. Meetings are weekly, every Tuesday at 17:00 UTC (10am PST) ok, everyone, we're ready to start
Criminals target government funded cell phone program
 #### http://www.kmov.com/news/local/criminals-target-government-funded-cell-phone-progra... Page 1 of 3 Criminals target government funded cell phone program by Chris Nagus KMOV.com Posted on November
#### http://www.kmov.com/news/local/criminals-target-government-funded-cell-phone-progra... Page 1 of 3 Criminals target government funded cell phone program by Chris Nagus KMOV.com Posted on November
MITOCW watch?v=w_-sx4vr53m
 MITOCW watch?v=w_-sx4vr53m The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high-quality educational resources for free. To
MITOCW watch?v=w_-sx4vr53m The following content is provided under a Creative Commons license. Your support will help MIT OpenCourseWare continue to offer high-quality educational resources for free. To
Employee Security Awareness Training
 Employee Security Awareness Training September 2016 Purpose Employees have access to sensitive data through the work they perform for York. Examples of sensitive data include social security numbers, medical
Employee Security Awareness Training September 2016 Purpose Employees have access to sensitive data through the work they perform for York. Examples of sensitive data include social security numbers, medical
Your security on click Jobs
 Your security on click Jobs At Click Jobs is a trading name of Raspberry Recruitment Limited, we're committed to helping you find the right job in a safe and secure environment. On these pages, you can
Your security on click Jobs At Click Jobs is a trading name of Raspberry Recruitment Limited, we're committed to helping you find the right job in a safe and secure environment. On these pages, you can
Introduction to Cryptology Dr. Sugata Gangopadhyay Department of Computer Science and Engineering Indian Institute of Technology, Roorkee
 Introduction to Cryptology Dr. Sugata Gangopadhyay Department of Computer Science and Engineering Indian Institute of Technology, Roorkee Lecture 09 Cryptanalysis and its variants, linear attack Welcome
Introduction to Cryptology Dr. Sugata Gangopadhyay Department of Computer Science and Engineering Indian Institute of Technology, Roorkee Lecture 09 Cryptanalysis and its variants, linear attack Welcome
WOODSTOCK BADMINTON CLUB BOARD MEETING MINUTES September 8, Hunter Street 7:00 p.m.
 WOODSTOCK BADMINTON CLUB BOARD MEETING MINUTES September 8, 2015 310 Hunter Street 7:00 p.m. Welcome: Drew called the meeting to order and welcomed everyone at 7:08. Present: Carol Bossenberry, Wendy Clements,
WOODSTOCK BADMINTON CLUB BOARD MEETING MINUTES September 8, 2015 310 Hunter Street 7:00 p.m. Welcome: Drew called the meeting to order and welcomed everyone at 7:08. Present: Carol Bossenberry, Wendy Clements,
Chris Skorlinski Microsoft SQL Escalation Services Charlotte, NC
 Chris Skorlinski Microsoft SQL Escalation Services Charlotte, NC http://blogs.msdn.com/repltalk One of my favorite shows is CarTalk on Public Radio. Those guys always make me laugh. I enjoy listening to
Chris Skorlinski Microsoft SQL Escalation Services Charlotte, NC http://blogs.msdn.com/repltalk One of my favorite shows is CarTalk on Public Radio. Those guys always make me laugh. I enjoy listening to
Writing Cover Letters
 Writing Cover Letters Communicating with Employers What is a cover letter? A cover letter is a document submitted with a job application explaining the applicant s credentials and interest in the open
Writing Cover Letters Communicating with Employers What is a cover letter? A cover letter is a document submitted with a job application explaining the applicant s credentials and interest in the open
STAUNING Credit Application Internet Sales Process with /Voic Templates to Non-Responsive Prospects 2018 Edition
 STAUNING Credit Application Internet Sales Process with Email/Voicemail Templates to Non-Responsive Prospects 2018 Edition Contents 30-DAY CREDIT APPLICATION INTERNET SALES PROCESS... 2 DAY 1 AUTO-RESPONSE
STAUNING Credit Application Internet Sales Process with Email/Voicemail Templates to Non-Responsive Prospects 2018 Edition Contents 30-DAY CREDIT APPLICATION INTERNET SALES PROCESS... 2 DAY 1 AUTO-RESPONSE
IT & DATA SECURITY BREACH PREVENTION
 IT & DATA SECURITY BREACH PREVENTION A PRACTICAL GUIDE Part 1: Reducing Employee and Application Risks CONTENTS EMPLOYEES: IT security hygiene best practice APPLICATIONS: Make patching a priority AS CORPORATE
IT & DATA SECURITY BREACH PREVENTION A PRACTICAL GUIDE Part 1: Reducing Employee and Application Risks CONTENTS EMPLOYEES: IT security hygiene best practice APPLICATIONS: Make patching a priority AS CORPORATE
News English.com Ready-to-use ESL / EFL Lessons
 www.breaking News English.com Ready-to-use ESL / EFL Lessons The Breaking News English.com Resource Book 1,000 Ideas & Activities For Language Teachers http://www.breakingnewsenglish.com/book.html Self-destructing
www.breaking News English.com Ready-to-use ESL / EFL Lessons The Breaking News English.com Resource Book 1,000 Ideas & Activities For Language Teachers http://www.breakingnewsenglish.com/book.html Self-destructing
WEB OF DECEIT. Why are seniors targeted?
 A challenge for senior citizens who embrace the computer age is knowing how to avoid online fraud. Although people of all ages are at risk, statistics show that when it comes to online safety, seniors
A challenge for senior citizens who embrace the computer age is knowing how to avoid online fraud. Although people of all ages are at risk, statistics show that when it comes to online safety, seniors
Dan Bower Monday, December 15, :38 AM Choephel, Tenzin
 Choephel, Tenzin From: Sent: To: Cc: Subject: Monday, December 15, 2014 11:38 AM Choephel, Tenzin Kahn, Drummond [Approved Sender] RE: [Approved Sender] RE: [Approved
Choephel, Tenzin From: Sent: To: Cc: Subject: Monday, December 15, 2014 11:38 AM Choephel, Tenzin Kahn, Drummond [Approved Sender] RE: [Approved Sender] RE: [Approved
Trying To Uninstall Norton 360 Wont Let Me Connect
 Trying To Uninstall Norton 360 Wont Let Me Connect Wasn't sure if I could just delete all files to do with Norton 360/symantec from the C: when trying to open Norton or trying to remove it using add/remove
Trying To Uninstall Norton 360 Wont Let Me Connect Wasn't sure if I could just delete all files to do with Norton 360/symantec from the C: when trying to open Norton or trying to remove it using add/remove
(January 22, 2016) ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
 (January 22, 2016) In order to further improve the lines of communication and to respond to the concerns between the National VA Council and you our members, I have established a National VA Council Briefing.
(January 22, 2016) In order to further improve the lines of communication and to respond to the concerns between the National VA Council and you our members, I have established a National VA Council Briefing.
Learner. Help Guide. Page 1 of 36 Training Partner (Learner Help Guide) Revised 09/16/09
 Learner Help Guide Page 1 of 36 Table of Contents ACCESS INFORMATION Accessing Training Partner on the Web..... 3 Login to Training Partner........ 4 Add/Change Email Address....... 6 Change Password.........
Learner Help Guide Page 1 of 36 Table of Contents ACCESS INFORMATION Accessing Training Partner on the Web..... 3 Login to Training Partner........ 4 Add/Change Email Address....... 6 Change Password.........
Spotlight on Public/Private Initiatives The Atlanta Downtown Improvement District
 Spotlight on Public/Private Initiatives The Atlanta Downtown Improvement District Member: Dave Wardell, VP Operations & Public Safety, Central Atlanta Progress Inc. 1. Security Executive Council Public/Private
Spotlight on Public/Private Initiatives The Atlanta Downtown Improvement District Member: Dave Wardell, VP Operations & Public Safety, Central Atlanta Progress Inc. 1. Security Executive Council Public/Private
Outline Key Management CS 239 Computer Security February 9, 2004
 Outline Key Management CS 239 Computer Security February 9, 2004 Properties of keys Key management Key servers Certificates Page 1 Page 2 Introduction Properties of Keys It doesn t matter how strong your
Outline Key Management CS 239 Computer Security February 9, 2004 Properties of keys Key management Key servers Certificates Page 1 Page 2 Introduction Properties of Keys It doesn t matter how strong your
Problem Solving through Programming In C Prof. Anupam Basu Department of Computer Science & Engineering Indian Institute of Technology, Kharagpur
 Problem Solving through Programming In C Prof. Anupam Basu Department of Computer Science & Engineering Indian Institute of Technology, Kharagpur Lecture 17 Switch Statement (Refer Slide Time: 00:23) In
Problem Solving through Programming In C Prof. Anupam Basu Department of Computer Science & Engineering Indian Institute of Technology, Kharagpur Lecture 17 Switch Statement (Refer Slide Time: 00:23) In
It Might Be Valid, But It's Still Wrong Paul Maskens and Andy Kramek
 Seite 1 von 5 Issue Date: FoxTalk July 2000 It Might Be Valid, But It's Still Wrong Paul Maskens and Andy Kramek This month, Paul Maskens and Andy Kramek discuss the problems of validating data entry.
Seite 1 von 5 Issue Date: FoxTalk July 2000 It Might Be Valid, But It's Still Wrong Paul Maskens and Andy Kramek This month, Paul Maskens and Andy Kramek discuss the problems of validating data entry.
Office Hours: Hidden gems in Excel 2007
 Page 1 of 6 Help and How-to Office Hours: Hidden gems in Excel 2007 October 1, 2007 Jean Philippe Bagel Sometimes love at first sight lasts for years. This week's columnist offers new and interesting ways
Page 1 of 6 Help and How-to Office Hours: Hidden gems in Excel 2007 October 1, 2007 Jean Philippe Bagel Sometimes love at first sight lasts for years. This week's columnist offers new and interesting ways
The Regional Cyber Crime Unit response to Cyber Crime
 British Computer Society Tuesday 9th January 2018 The Regional Cyber Crime Unit response to Cyber Crime Cyber Protect Officer Chris Phillips Overview Cybercrime threat Law enforcement response Priorities
British Computer Society Tuesday 9th January 2018 The Regional Cyber Crime Unit response to Cyber Crime Cyber Protect Officer Chris Phillips Overview Cybercrime threat Law enforcement response Priorities
In this white paper we want to look at seven basic principles that can help make your website be the best it can be.
 websites matter A good website is important now more than ever. More and more people first visit your church through your website -- not through your front doors. Visitors will likely evaluate six to 12
websites matter A good website is important now more than ever. More and more people first visit your church through your website -- not through your front doors. Visitors will likely evaluate six to 12
Adobe Security Survey
 Adobe Security Survey October 2016 Edelman + Adobe INTRODUCTION Methodology Coinciding with National Cyber Security Awareness Month (NCSAM), Edelman Intelligence, on behalf of Adobe, conducted a nationally
Adobe Security Survey October 2016 Edelman + Adobe INTRODUCTION Methodology Coinciding with National Cyber Security Awareness Month (NCSAM), Edelman Intelligence, on behalf of Adobe, conducted a nationally
Pasco Police Department Policy Manual. CRIME ANALYSIS AND INTELLIGENCE Chapter No. 40. Effective Date: 04/01/2018. Reference:
 CRIME ANALYSIS AND INTELLIGENCE Chapter No. 40 Effective Date: 04/01/2018 Reference: 40.1.1 Crime and Intelligence Analysis Procedures Crime and intelligence analysis is a law enforcement agency function
CRIME ANALYSIS AND INTELLIGENCE Chapter No. 40 Effective Date: 04/01/2018 Reference: 40.1.1 Crime and Intelligence Analysis Procedures Crime and intelligence analysis is a law enforcement agency function
Who am I? I m a python developer who has been working on OpenStack since I currently work for Aptira, who do OpenStack, SDN, and orchestration
 Who am I? I m a python developer who has been working on OpenStack since 2011. I currently work for Aptira, who do OpenStack, SDN, and orchestration consulting. I m here today to help you learn from my
Who am I? I m a python developer who has been working on OpenStack since 2011. I currently work for Aptira, who do OpenStack, SDN, and orchestration consulting. I m here today to help you learn from my
Case Management Systems, Part II Webinar. May 13, Jeff Chenoweth Martin Gauto CLINIC
 Case Management Systems, Part II Webinar May 13, 2014 Jeff Chenoweth Martin Gauto CLINIC CLINIC Presenters Jeff Chenoweth, Director Capacity Building Section Martin Gauto, Esq./Field Support Coordinator
Case Management Systems, Part II Webinar May 13, 2014 Jeff Chenoweth Martin Gauto CLINIC CLINIC Presenters Jeff Chenoweth, Director Capacity Building Section Martin Gauto, Esq./Field Support Coordinator
It s possible to get your inbox to zero and keep it there, even if you get hundreds of s a day.
 It s possible to get your email inbox to zero and keep it there, even if you get hundreds of emails a day. It s not super complicated, though it does take effort and discipline. Many people simply need
It s possible to get your email inbox to zero and keep it there, even if you get hundreds of emails a day. It s not super complicated, though it does take effort and discipline. Many people simply need
GUIDE TO ACU MEASURES How to complete surveys
 GUIDE TO ACU MEASURES How to complete surveys 1 Contents Introduction... 3 Surveys... 3 Roles... 3 Data entry... 4 Benchmarking... 4 How do I complete a survey?... 5 Survey troubleshooting... 9 2 Introduction
GUIDE TO ACU MEASURES How to complete surveys 1 Contents Introduction... 3 Surveys... 3 Roles... 3 Data entry... 4 Benchmarking... 4 How do I complete a survey?... 5 Survey troubleshooting... 9 2 Introduction
PROGRAM APPLICATION Assistance Dog Education Program and Training (ADEPT)
 Print the application, complete it, and mail it to 9877 234 TH St. E., Lakeville MN. 55044 Applications must be postmarked by February, 25 th 2019, no late applications will be accepted. You may also print
Print the application, complete it, and mail it to 9877 234 TH St. E., Lakeville MN. 55044 Applications must be postmarked by February, 25 th 2019, no late applications will be accepted. You may also print
Today s Topics. Percentile ranks and percentiles. Standardized scores. Using standardized scores to estimate percentiles
 Today s Topics Percentile ranks and percentiles Standardized scores Using standardized scores to estimate percentiles Using µ and σ x to learn about percentiles Percentiles, standardized scores, and the
Today s Topics Percentile ranks and percentiles Standardized scores Using standardized scores to estimate percentiles Using µ and σ x to learn about percentiles Percentiles, standardized scores, and the
Objective and Subjective Specifications
 2017-7-10 0 Objective and Subjective Specifications Eric C.R. Hehner Department of Computer Science, University of Toronto hehner@cs.utoronto.ca Abstract: We examine specifications for dependence on the
2017-7-10 0 Objective and Subjective Specifications Eric C.R. Hehner Department of Computer Science, University of Toronto hehner@cs.utoronto.ca Abstract: We examine specifications for dependence on the
INCOGNITO TOOLKIT: TOOLS, APPS, AND CREATIVE METHODS FOR REMAINING ANONYMOUS, PRIVATE, AND SECURE WHILE COMMUNICATING, PUBLISHING, BUYING,
 INCOGNITO TOOLKIT: TOOLS, APPS, AND CREATIVE METHODS FOR REMAINING ANONYMOUS, PRIVATE, AND SECURE WHILE COMMUNICATING, PUBLISHING, BUYING, DOWNLOAD EBOOK : INCOGNITO TOOLKIT: TOOLS, APPS, AND CREATIVE
INCOGNITO TOOLKIT: TOOLS, APPS, AND CREATIVE METHODS FOR REMAINING ANONYMOUS, PRIVATE, AND SECURE WHILE COMMUNICATING, PUBLISHING, BUYING, DOWNLOAD EBOOK : INCOGNITO TOOLKIT: TOOLS, APPS, AND CREATIVE
Calhoun County Board of Education
 Calhoun County Board of Education Application for Superintendent of Education [Use attachments or additional sheets, if necessary.] Send to: Calhoun County Superintendent Search Bishop, Colvin, Johnson
Calhoun County Board of Education Application for Superintendent of Education [Use attachments or additional sheets, if necessary.] Send to: Calhoun County Superintendent Search Bishop, Colvin, Johnson
Product Backlog Document Template and Example
 Product Backlog Document Template and Example Introduction 1. Client Information (Name(s), Business, Location, contact information) 2. Team Information Team Member Names (contact information) 3. Project
Product Backlog Document Template and Example Introduction 1. Client Information (Name(s), Business, Location, contact information) 2. Team Information Team Member Names (contact information) 3. Project
ICANN and Technical Work: Really? Yes! Steve Crocker DNS Symposium, Madrid, 13 May 2017
 ICANN and Technical Work: Really? Yes! Steve Crocker DNS Symposium, Madrid, 13 May 2017 Welcome, everyone. I appreciate the invitation to say a few words here. This is an important meeting and I think
ICANN and Technical Work: Really? Yes! Steve Crocker DNS Symposium, Madrid, 13 May 2017 Welcome, everyone. I appreciate the invitation to say a few words here. This is an important meeting and I think
An Introduction to How PGP Works
 An Introduction to How PGP Works Revision: 0.01 Author: Kenneth Robert Ballou Date 2005-07-21 Document Change History Change Description/Reason Changed By Date Revision Initial Creation of Document Kenneth
An Introduction to How PGP Works Revision: 0.01 Author: Kenneth Robert Ballou Date 2005-07-21 Document Change History Change Description/Reason Changed By Date Revision Initial Creation of Document Kenneth
HOW TO DESIGN A SMALL SWITCHING LAYOUT BY LANCE MINDHEIM DOWNLOAD EBOOK : HOW TO DESIGN A SMALL SWITCHING LAYOUT BY LANCE MINDHEIM PDF
 Read Online and Download Ebook HOW TO DESIGN A SMALL SWITCHING LAYOUT BY LANCE MINDHEIM DOWNLOAD EBOOK : HOW TO DESIGN A SMALL SWITCHING LAYOUT BY Click link bellow and free register to download ebook:
Read Online and Download Ebook HOW TO DESIGN A SMALL SWITCHING LAYOUT BY LANCE MINDHEIM DOWNLOAD EBOOK : HOW TO DESIGN A SMALL SWITCHING LAYOUT BY Click link bellow and free register to download ebook:
Amber Weyland: [to cameraman] Just hold it there so we can see Mollie.
![Amber Weyland: [to cameraman] Just hold it there so we can see Mollie. Amber Weyland: [to cameraman] Just hold it there so we can see Mollie.](/thumbs/96/128551622.jpg) Interview Transcript Interviewer: Amber Weyland Interviewee: Mollie Hummer Cameraman: Christopher Smith [friend to both] Date: March 22, 2010 Beginning time of interview: 2:30pm End time of interview:
Interview Transcript Interviewer: Amber Weyland Interviewee: Mollie Hummer Cameraman: Christopher Smith [friend to both] Date: March 22, 2010 Beginning time of interview: 2:30pm End time of interview:
CPSC 467b: Cryptography and Computer Security
 Outline ZKIP Other IP CPSC 467b: Cryptography and Computer Security Lecture 19 Michael J. Fischer Department of Computer Science Yale University March 31, 2010 Michael J. Fischer CPSC 467b, Lecture 19
Outline ZKIP Other IP CPSC 467b: Cryptography and Computer Security Lecture 19 Michael J. Fischer Department of Computer Science Yale University March 31, 2010 Michael J. Fischer CPSC 467b, Lecture 19
Smart Working Concept Seedble
 page 1 of 32 If you want to get in touch, contact me on Twitter (@KLHartog), Google+ (+KLHartog) or LinkedIn. page 2 of 32 Our lives have been fundamentally changed by new technological possibilities.
page 1 of 32 If you want to get in touch, contact me on Twitter (@KLHartog), Google+ (+KLHartog) or LinkedIn. page 2 of 32 Our lives have been fundamentally changed by new technological possibilities.
SOFTWARE ENGINEERING Prof.N.L.Sarda Computer Science & Engineering IIT Bombay. Lecture #10 Process Modelling DFD, Function Decomp (Part 2)
 SOFTWARE ENGINEERING Prof.N.L.Sarda Computer Science & Engineering IIT Bombay Lecture #10 Process Modelling DFD, Function Decomp (Part 2) Let us continue with the data modeling topic. So far we have seen
SOFTWARE ENGINEERING Prof.N.L.Sarda Computer Science & Engineering IIT Bombay Lecture #10 Process Modelling DFD, Function Decomp (Part 2) Let us continue with the data modeling topic. So far we have seen
BTEC Nationals IT - Unit2 FAQs
 BTEC Nationals IT - Unit2 FAQs Q1 Q2 I need more clarity on what is required in the design task Is it expected that the race officials are entering times as raw times and then the table is set up so it
BTEC Nationals IT - Unit2 FAQs Q1 Q2 I need more clarity on what is required in the design task Is it expected that the race officials are entering times as raw times and then the table is set up so it
Post Experiment Interview Questions
 Post Experiment Interview Questions Questions about the Maximum Problem 1. What is this problem statement asking? 2. What is meant by positive integers? 3. What does it mean by the user entering valid
Post Experiment Interview Questions Questions about the Maximum Problem 1. What is this problem statement asking? 2. What is meant by positive integers? 3. What does it mean by the user entering valid
Bellevue job Don C Burdick to: Ted A Carlson
 Bellevue job C Burdick to: Ted A Carlson 08/16/2011 09:34 PM I talked to Lorna and she didn't consider the Bellevue job a conflict of interest from the cities perspective. I will be following up with a
Bellevue job C Burdick to: Ted A Carlson 08/16/2011 09:34 PM I talked to Lorna and she didn't consider the Bellevue job a conflict of interest from the cities perspective. I will be following up with a
I have had the same experience. I wish I could get it for my offices too... Andrew M. Ayers, New York
 UPSP Informed Delivery The Post Office recently offered me Informed delivery, a free service where they send you a picture of each piece of incoming, letter-sized mail that will be delivered each day.
UPSP Informed Delivery The Post Office recently offered me Informed delivery, a free service where they send you a picture of each piece of incoming, letter-sized mail that will be delivered each day.
Handling Your Data in SPSS. Columns, and Labels, and Values... Oh My! The Structure of SPSS. You should think about SPSS as having three major parts.
 Handling Your Data in SPSS Columns, and Labels, and Values... Oh My! You might think that simple intuition will guide you to a useful organization of your data. If you follow that path, you might find
Handling Your Data in SPSS Columns, and Labels, and Values... Oh My! You might think that simple intuition will guide you to a useful organization of your data. If you follow that path, you might find
Here s the Re-Notice, that will be going out in today s USPS to the defendant.
 From: Houp, otus [mailto:otus.houp@kingcounty.gov] Sent: Wednesday, August 26, 2015 8:45 AM To: Court, Carey Subject: RE: Resetting Jason Markley Hi Kelli: Here s the Re-Notice, that will be going out
From: Houp, otus [mailto:otus.houp@kingcounty.gov] Sent: Wednesday, August 26, 2015 8:45 AM To: Court, Carey Subject: RE: Resetting Jason Markley Hi Kelli: Here s the Re-Notice, that will be going out
Managing Groups Using InFellowship. A guide for Small Group Leaders
 Managing Groups Using InFellowship A guide for Small Group Leaders 2 3 Managing Groups Using InFellowship Table of Contents MyLifePoint your InFellowship account...4 InFellowship Groups - Your Dashboard...5
Managing Groups Using InFellowship A guide for Small Group Leaders 2 3 Managing Groups Using InFellowship Table of Contents MyLifePoint your InFellowship account...4 InFellowship Groups - Your Dashboard...5
OVERVIEW. 120 minutes. Technology tools / Platforms Tested (Mandatory) i) NA ii) Technology tools / Platforms Tested (Select any one) i) NA ii)
 QP CODE: QP TITLE: Q6702 Software Developer OVERVIEW Test Duration Duration - SSC/N0502 Duration - SSC/N9001 Duration SSC/N9002 Duration SSC/N9003 Duration SSC/N9004 Duration SSC/N9005 Natural Language
QP CODE: QP TITLE: Q6702 Software Developer OVERVIEW Test Duration Duration - SSC/N0502 Duration - SSC/N9001 Duration SSC/N9002 Duration SSC/N9003 Duration SSC/N9004 Duration SSC/N9005 Natural Language
MITOCW ocw f99-lec07_300k
 MITOCW ocw-18.06-f99-lec07_300k OK, here's linear algebra lecture seven. I've been talking about vector spaces and specially the null space of a matrix and the column space of a matrix. What's in those
MITOCW ocw-18.06-f99-lec07_300k OK, here's linear algebra lecture seven. I've been talking about vector spaces and specially the null space of a matrix and the column space of a matrix. What's in those
Outlier Detection With SQL And R. Kevin Feasel, Engineering Manager, ChannelAdvisor Moderated By: Satya Jayanty
 Outlier Detection With SQL And R Kevin Feasel, Engineering Manager, ChannelAdvisor Moderated By: Satya Jayanty Technical Assistance If you require assistance during the session, type your inquiry into
Outlier Detection With SQL And R Kevin Feasel, Engineering Manager, ChannelAdvisor Moderated By: Satya Jayanty Technical Assistance If you require assistance during the session, type your inquiry into
Helping the Compiler Help You. Thomas Dy
 Helping the Compiler Help You Thomas Dy Programming do { programmer.write_code(); if(lazy) { sleep(); } compile_code(); } while(compiler.has_errors()); Compiler: Me no speaky English Programmer: Compiler,
Helping the Compiler Help You Thomas Dy Programming do { programmer.write_code(); if(lazy) { sleep(); } compile_code(); } while(compiler.has_errors()); Compiler: Me no speaky English Programmer: Compiler,
Institute of Internal Auditors 2019 CONNECT WITH THE IIA CHICAGO #IIACHI
 Institute of Internal Auditors 2019 CONNECT WITH THE IIA CHICAGO CHAPTER: @IIACHI #IIACHI WWW.FACEBOOK.COM/IIACHICAGO HTTPS://WWW.LINKEDIN.COM/GROUPS/1123977 1 CAE Communications and Common Audit Committee
Institute of Internal Auditors 2019 CONNECT WITH THE IIA CHICAGO CHAPTER: @IIACHI #IIACHI WWW.FACEBOOK.COM/IIACHICAGO HTTPS://WWW.LINKEDIN.COM/GROUPS/1123977 1 CAE Communications and Common Audit Committee
5 Easy Ways To Grow Your List
 JENNA KUTCHER 5 Easy Ways To Grow Your Email List CHEAT SHEET GROW YOUR EMAIL LIST So you wanna grow your email list, right? B U T Y O U M I G H T B E W O N D E R I N G H O W? Hey you, So glad you re here
JENNA KUTCHER 5 Easy Ways To Grow Your Email List CHEAT SHEET GROW YOUR EMAIL LIST So you wanna grow your email list, right? B U T Y O U M I G H T B E W O N D E R I N G H O W? Hey you, So glad you re here
PROFESSOR: So far in this course we've been talking a lot about data abstraction. And remember the idea is that
 MITOCW Lecture 4B [MUSIC-- "JESU, JOY OF MAN'S DESIRING" BY JOHANN SEBASTIAN BACH] PROFESSOR: So far in this course we've been talking a lot about data abstraction. And remember the idea is that we build
MITOCW Lecture 4B [MUSIC-- "JESU, JOY OF MAN'S DESIRING" BY JOHANN SEBASTIAN BACH] PROFESSOR: So far in this course we've been talking a lot about data abstraction. And remember the idea is that we build
FBI Project. Cell Phone Triangulation TASKS
 LAW OF SINES/LAW OF COSINES FBI Project Cell Phone Triangulation TASKS Cell Phone Triangulation 1. Complete cell phone triangulation and sketch diagrams using the Law of Cosines and Law of Sines. Forensic
LAW OF SINES/LAW OF COSINES FBI Project Cell Phone Triangulation TASKS Cell Phone Triangulation 1. Complete cell phone triangulation and sketch diagrams using the Law of Cosines and Law of Sines. Forensic
Top 5 Tips To Take A Stand Against Telephone Scams
 Scammers often use the telephone as a method to gain personal details and con people out of their life savings. Avoid being one of them, protect yourself. Top 5 Tips To Take A Stand Against Telephone Scams
Scammers often use the telephone as a method to gain personal details and con people out of their life savings. Avoid being one of them, protect yourself. Top 5 Tips To Take A Stand Against Telephone Scams
Spam. Time: five years from now Place: England
 Spam Time: five years from now Place: England Oh no! said Joe Turner. When I go on the computer, all I get is spam email that nobody wants. It s all from people who are trying to sell you things. Email
Spam Time: five years from now Place: England Oh no! said Joe Turner. When I go on the computer, all I get is spam email that nobody wants. It s all from people who are trying to sell you things. Email
Guide to Personal Online Banking. Great Things Happen!
 Great Things Happen! Table of Contents General Information Security... Getting Started - Enroll & Authenticate.........4 Accounts Overview... 0 History... Online Activity... estatements... 4 Transactions
Great Things Happen! Table of Contents General Information Security... Getting Started - Enroll & Authenticate.........4 Accounts Overview... 0 History... Online Activity... estatements... 4 Transactions
Lesson 8 Transcript: Database Security
 Lesson 8 Transcript: Database Security Slide 1: Cover Welcome to Lesson 8 of the DB2 on Campus Series. Today we are going to talk about database security. My name is Raul Chong, and I am the DB2 on Campus
Lesson 8 Transcript: Database Security Slide 1: Cover Welcome to Lesson 8 of the DB2 on Campus Series. Today we are going to talk about database security. My name is Raul Chong, and I am the DB2 on Campus
P1_L6 Mandatory Access Control Page 1
 P1_L6 Mandatory Access Control Page 1 We discussed access control in the last lesson. But that was only one kind of access control called discretionary access control, or DAC. That allows you to decide
P1_L6 Mandatory Access Control Page 1 We discussed access control in the last lesson. But that was only one kind of access control called discretionary access control, or DAC. That allows you to decide
Launch the TotPlan application from Navigate > applications > Planning > TotPlan.
 1 Log into Workspace Launch the TotPlan application from Navigate > applications > Planning > TotPlan. Click on the Quota Planning form in the Revenue folder. As we re planning the next fiscal year, we
1 Log into Workspace Launch the TotPlan application from Navigate > applications > Planning > TotPlan. Click on the Quota Planning form in the Revenue folder. As we re planning the next fiscal year, we
Henry looks at Edith and smiles, with some embarrassment. It s alright, I m not going to criticise. You are using a Private Use Area characters in
 Henry is in the common room: on the coffee table in front of him are some large sheets of paper with handwriting on them - Henry s handwriting - and a cup of peppermint tea. Henry is engrossed and looking
Henry is in the common room: on the coffee table in front of him are some large sheets of paper with handwriting on them - Henry s handwriting - and a cup of peppermint tea. Henry is engrossed and looking
The Money Is in the Square Cash Lets Users Funds to Friends
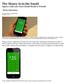 The Money Is in the Email Square Cash Lets Users Email Funds to Friends By: WALTER S. MOSSBERG October 15, 2013 Square now has a service that makes transferring money to a friend as easy as sending them
The Money Is in the Email Square Cash Lets Users Email Funds to Friends By: WALTER S. MOSSBERG October 15, 2013 Square now has a service that makes transferring money to a friend as easy as sending them
Module 2.3a IP 0:00 - 1:00 -
 Module 2.3a IP 0:00 - In this video we're going to continue looking at our simplified view of how the internet layers work and in particular we're going to look at the middle layer which is good known
Module 2.3a IP 0:00 - In this video we're going to continue looking at our simplified view of how the internet layers work and in particular we're going to look at the middle layer which is good known
Keywords. The Foundation of your Internet Business.. By Eric Graudins: TheInternetBloke.com Worldwide Rights Reserved.
 PRESENTS Keywords The Foundation of your Internet Business.. By Eric Graudins: TheInternetBloke.com 2010. Worldwide Rights Reserved. Hi, I m Eric Graudins. You ll find that I explain Internet related stuff
PRESENTS Keywords The Foundation of your Internet Business.. By Eric Graudins: TheInternetBloke.com 2010. Worldwide Rights Reserved. Hi, I m Eric Graudins. You ll find that I explain Internet related stuff
We ve been playing The Game of Life for several weeks now. You have had lots of practice making budgets, and managing income and expenses and savings.
 We ve been playing The Game of Life for several weeks now. You have had lots of practice making budgets, and managing income and expenses and savings. It is sometimes a challenge to manage a lot of data
We ve been playing The Game of Life for several weeks now. You have had lots of practice making budgets, and managing income and expenses and savings. It is sometimes a challenge to manage a lot of data
Written Communication
 Module 2: Written Communication 1 Your Passport to Professionalism: Module 2 Written Communication Step 1 Learn Introduction Sooner or later, you will need to communicate in writing. You will write down
Module 2: Written Communication 1 Your Passport to Professionalism: Module 2 Written Communication Step 1 Learn Introduction Sooner or later, you will need to communicate in writing. You will write down
CS144 Final Review. Dec 4th, 2009 Tom Wiltzius
 CS144 Final Review Dec 4th, 2009 Tom Wiltzius Topics Topics In narrative format! Let's follow Packy as he traverses the Internet! Packy comes into being to help Compy the Computer load a web page Compy
CS144 Final Review Dec 4th, 2009 Tom Wiltzius Topics Topics In narrative format! Let's follow Packy as he traverses the Internet! Packy comes into being to help Compy the Computer load a web page Compy
Site Visit Protocol for Program Directors September As Program Directors prepare for the site visit, they should keep the following in mind.
 Site Visit Protocol for Program Directors September 2016 As Program Directors prepare for the site visit, they should keep the following in mind. Before the Visit Arrange convenient, comfortable accommodations
Site Visit Protocol for Program Directors September 2016 As Program Directors prepare for the site visit, they should keep the following in mind. Before the Visit Arrange convenient, comfortable accommodations
Samples of Features and Feature Stories CSc 190
 Samples of Features and Feature Stories CSc 190 The following un-prioritized Product Backlog contains the user stories for the thirteen Features that were written to describe the initial functionality
Samples of Features and Feature Stories CSc 190 The following un-prioritized Product Backlog contains the user stories for the thirteen Features that were written to describe the initial functionality
To scope this project, we selected three top-tier biomedical journals that publish systematic reviews, hoping that they had a higher standard of
 1 Here we aim to answer the question: Does searching more databases add value to the systematic review. Especially when considering the time it takes for the ENTIRE process, the resources available like
1 Here we aim to answer the question: Does searching more databases add value to the systematic review. Especially when considering the time it takes for the ENTIRE process, the resources available like
(Refer Slide Time: 01:25)
 Computer Architecture Prof. Anshul Kumar Department of Computer Science and Engineering Indian Institute of Technology, Delhi Lecture - 32 Memory Hierarchy: Virtual Memory (contd.) We have discussed virtual
Computer Architecture Prof. Anshul Kumar Department of Computer Science and Engineering Indian Institute of Technology, Delhi Lecture - 32 Memory Hierarchy: Virtual Memory (contd.) We have discussed virtual
Media-Ready Network Transcript
 Media-Ready Network Transcript Hello and welcome to this Cisco on Cisco Seminar. I m Bob Scarbrough, Cisco IT manager on the Cisco on Cisco team. With me today are Sheila Jordan, Vice President of the
Media-Ready Network Transcript Hello and welcome to this Cisco on Cisco Seminar. I m Bob Scarbrough, Cisco IT manager on the Cisco on Cisco team. With me today are Sheila Jordan, Vice President of the
From video conversation 2. This is a gap fill exercise and can be used as either a quiz/test of
 Teacher s guide to the quizzes/tests available for Unit 4 Quiz 1 Quiz 2 Quiz 3 Quiz 4 From video conversation 1. This is a gap fill exercise and can be used as either a quiz/test of target language acquisition,
Teacher s guide to the quizzes/tests available for Unit 4 Quiz 1 Quiz 2 Quiz 3 Quiz 4 From video conversation 1. This is a gap fill exercise and can be used as either a quiz/test of target language acquisition,
SEO for small business. A beginner s guide. fundingcircle.com
 SEO for small business A beginner s guide fundingcircle.com support@fundingcircle.com 855.385.5356 A beginner s guide to SEO for small business With tight budgets and limited resources, it can be tough
SEO for small business A beginner s guide fundingcircle.com support@fundingcircle.com 855.385.5356 A beginner s guide to SEO for small business With tight budgets and limited resources, it can be tough
Trulia Reviews. Emily Mollen reviewed Amy McCafferty 10/02/2014 Helped me buy a home
 Trulia Reviews Emily Mollen reviewed Amy McCafferty 10/02/2014 Amy just helped me purchase a home in Almaden Valley, and the transaction couldn't have gone smoother! She is very personable, professional,
Trulia Reviews Emily Mollen reviewed Amy McCafferty 10/02/2014 Amy just helped me purchase a home in Almaden Valley, and the transaction couldn't have gone smoother! She is very personable, professional,
Chat Reference Assignment
 REFERENCE & INFORMATION RESOURCES & SERVICES ILS 504-70 Fall Dr. Clara Ogbaa Chat Reference Assignment Lucinda D. Mazza CHAT REFERENCE ASSIGNMENT 2 Chat Reference Assignment When first starting this assignment,
REFERENCE & INFORMATION RESOURCES & SERVICES ILS 504-70 Fall Dr. Clara Ogbaa Chat Reference Assignment Lucinda D. Mazza CHAT REFERENCE ASSIGNMENT 2 Chat Reference Assignment When first starting this assignment,
