Duo End User Education Templates
|
|
|
- Shavonne Cox
- 6 years ago
- Views:
Transcription
1 Duo End User Education Templates Table of Contents Communication Best Practices Templates #1 - Duo is coming soon, no immediate action required. #2 - Duo is coming on <DATE>, no immediate action required. #3 - Duo is coming on <DATE> + enrollment information, no immediate action required. #4 Action Required: Check Inbox for Enrollment -- Enroll Now.
2 Communication Best Practices. Below are a few best practices when ing your users about the upcoming deployment of Duo 2FA: Days to send s: Tuesdays, Wednesdays, and Thursdays are the best days to send s users will open. Who to send the from: We recommend this come from a person (IT manager, Ops director, etc) or your helpdesk. #1 - Duo is coming soon, no immediate action required. TIMELINE: 30 days prior to the enrollment send/application go-live date. SUBJECT LINE: Duo two-factor authentication is coming soon! BODY: To improve our security posture, we will be incorporating Duo Security as a two-factor authentication solution into our existing IT infrastructure. Action Required: No immediate action is necessary. This is to notify and educate you about the upcoming rollout of Duo two-factor authentication. What is Duo Security? Duo Security is a company that provides a cloud-based software service that utilizes two-factor authentication to ensure secure access to services and data. Learn more by clicking here.
3 What is two-factor authentication? Two-factor authentication provides a second layer of security to any type of login, requiring extra information or a physical device to log in, in addition to your password. By requiring two different channels of authentication, we can protect user logins from remote attacks that may exploit stolen usernames & passwords. The factors may include: Something you know: A unique username and password. Something you have: A smartphone with an app to approve authentication requests. Something you are: Biometrics - like your fingerprint or a retina scan. Why do we need two-factor authentication? Login credentials are more valuable than ever and are increasingly easy to compromise. Over 90% of breaches today involve compromised usernames & passwords. Two-factor authentication enhances the security of your account by using a secondary device to verify your identity. This prevents anyone but you from accessing your account, even if they know your password. How will Duo change my login experience? When logging in to an application that is protected by Duo, you will still enter your username and password. After inputting your login information, you will be required to complete a method of second-factor authentication. Duo does not replace or require you to change your username and password. Think of Duo as a layer of security added to your pre-existing login method. More information on the rollout of Duo coming soon.
4 #2 - Duo is coming on <DATE>, no immediate action required. TIMELINE: 15 days prior to the enrollment send/application go-live date. SUBJECT LINE: Enroll in Duo two-factor authentication on <DATE OF ENROLLMENT > BODY: To improve our security posture, we will be incorporating Duo Security as a two-factor authentication solution into our existing IT infrastructure. You will receive an enrollment from Duo on <DATE OF ENROLLMENT >. Expect to see more on this in the coming days. Action required: No immediate action is necessary. This is to notify and educate you about the upcoming rollout of Duo two-factor authentication on <DATE OF ENROLLMENT >. What is Duo Security? Duo Security is a company that provides a cloud-based software service that utilizes two-factor authentication to ensure secure access to services and data. Learn more by clicking here. What is two-factor authentication? Two-factor authentication provides a second layer of security to any type of login, requiring extra information or a physical device to log in, in addition to your password. By requiring two different channels of authentication, we can protect user logins from remote attacks that may exploit stolen usernames & passwords. The factors may include: Something you know: A unique username and password.
5 Something you have: A smartphone with an app to approve authentication requests. Something you are: Biometrics - like your fingerprint or a retina scan. Why do we need two-factor authentication? Login credentials are more valuable than ever and are increasingly easy to compromise. Over 90% of breaches today involve compromised usernames & passwords. Two-factor authentication enhances the security of your account by using a secondary device to verify your identity. This prevents anyone but you from accessing your account, even if they know your password. How will Duo change my login experience? When logging in to an application that is protected by Duo, you will still enter your username and password. After inputting your login information, you will be required to complete a method of second-factor authentication. Duo does not replace or require you to change your username and password. Think of Duo as a layer of security added to your pre-existing login method. More information on the rollout of Duo coming soon.
6 #3 - Duo is coming on <DATE> + enrollment information, no immediate action required. TIMELINE: 3 days prior to the enrollment send/application go-live date. SUBJECT LINE: Reminder: Duo two-factor authentication is coming on <DATE OF ENROLLMENT > BODY: To improve our security posture, we will be incorporating Duo Security as a two-factor authentication solution into our existing IT infrastructure. You will receive an enrollment from Duo on <DATE OF ENROLLMENT >. This will contain a personalized link allowing you to enroll with Duo. This 2 minute self-enrollment process makes it easy to register your phone and install the Duo Mobile application. If you do not have a smartphone, you can enroll a regular cell phone (SMS + calls) or landline (calls) for two-factor authentication. Action required: No immediate action required. This is to remind you of the upcoming rollout of Duo two-factor authentication on <DATE OF ENROLLMENT >. What is Duo Mobile & Duo Push? Duo Mobile is Duo Security s free app that allows you to quickly and easily approve a secondfactor authentication request with one tap using Duo Push. With Duo Mobile & Duo Push, there is no need to carry a bulky token or waste time manually entering in passcodes. Just one tap to authenticate right on your smartphone. Here is an example of Duo Push in action.
7 How will Duo change my login experience? When logging in to an application that is protected by Duo, you will still enter your username and password. After inputting your login information, you will be required to complete a method of second-factor authentication. Duo does not replace or require you to change your username and password. Think of Duo as a layer of security added to your pre-existing login method. What is Duo, what is two-factor, and why do we need it? If you ve missed our previous s, watch this video to learn more. Questions? Please reach out to the <Help Desk/Service Desk/Duo Support team> with any questions about enrolling or using Duo. <Help Desk/Service Desk/Duo Support team> Phone Number: <Help Desk/Service Desk/Duo Support team>
8 #4 Action Required: Check Inbox for Enrollment -- Enroll Now. TIMELINE: Day of enrollment send/application go-live. SUBJECT LINE: Action Required: Enroll in Duo today BODY: To improve our security posture, we will be incorporating Duo Security as a two-factor authentication solution into our existing IT infrastructure. Today you will receive an enrollment from Duo Security. This will contain a personalized link allowing you to enroll with Duo. This 2 minute self-enrollment process makes it easy to register your phone and install the Duo Mobile application. If you do not have a smartphone, you can enroll a regular cell phone (SMS + calls) or landline (calls) for two-factor authentication. You will have until <DATE OF APPLICATION + DUO GO-LIVE> to enroll. After this date, access to <APPLICATION> will require Duo two-factor. Action required: Enroll today. Check your inbox for an enrollment from Duo and complete the enrollment process. What is Duo Mobile & Duo Push? Duo Mobile is Duo Security s free app that allows you to quickly and easily approve a secondfactor authentication request with one tap using Duo Push. With Duo Mobile & Duo Push, there is no need to carry a bulky token or waste time manually entering in passcodes. Just one tap to authenticate right on your smartphone. Here is an example of Duo Push in action.
9 How will Duo change my login experience? When logging in to an application that is protected by Duo, you will still enter your username and password. After inputting your login information, you will be required to complete a method of second-factor authentication. Duo does not replace or require you to change your username and password. Think of Duo as a layer of security added to your pre-existing login method. What is Duo, what is two-factor, and why do we need it? If you ve missed our previous s, watch this video to learn more. Questions? Please reach out to the <Help Desk/Service Desk/Duo Support team> with any questions about enrolling or using Duo. <Help Desk/Service Desk/Duo Support team> Phone Number: <Help Desk/Service Desk/Duo Support team>
Getting Started with Duo Security Two-Factor Authentication (2FA)
 Getting Started with Duo Security Two-Factor Authentication (2FA) Table of Contents What is Two-Factor Authentication (2FA)?... 1 Why 2FA at Bates College?... 2 2FA Technologies... 3 Duo Protected Resources
Getting Started with Duo Security Two-Factor Authentication (2FA) Table of Contents What is Two-Factor Authentication (2FA)?... 1 Why 2FA at Bates College?... 2 2FA Technologies... 3 Duo Protected Resources
Using CSE Cisco Anyconnect with 2FA
 Using CSE Cisco Anyconnect with 2FA If you are using the Duo Mobile App in push mode: you open Anyconnect. 3. Enter your CSE UserName for the Username. 4. A new window will open. 5. Enter your CSE UserName
Using CSE Cisco Anyconnect with 2FA If you are using the Duo Mobile App in push mode: you open Anyconnect. 3. Enter your CSE UserName for the Username. 4. A new window will open. 5. Enter your CSE UserName
Duo Security Enrollment Guide
 Duo Security Enrollment Guide Duo's self-enrollment process makes it easy to register your phone and install the Duo Mobile application on your smartphone or tablet. Supported Browsers: Chrome, Firefox,
Duo Security Enrollment Guide Duo's self-enrollment process makes it easy to register your phone and install the Duo Mobile application on your smartphone or tablet. Supported Browsers: Chrome, Firefox,
Enroll in Two factor Authentication - iphone
 OVERVIEW Passwords are increasingly easy to compromise. They can often be stolen, guessed, or hacked you might not even know someone is accessing your account. Two factor authentication adds a second layer
OVERVIEW Passwords are increasingly easy to compromise. They can often be stolen, guessed, or hacked you might not even know someone is accessing your account. Two factor authentication adds a second layer
Duo Security Enrollment Guide
 Duo Security Enrollment Guide Duo's self-enrollment process makes it easy to register your phone and install the Duo Mobile application on your smartphone or tablet. Supported Browsers: Chrome, Firefox,
Duo Security Enrollment Guide Duo's self-enrollment process makes it easy to register your phone and install the Duo Mobile application on your smartphone or tablet. Supported Browsers: Chrome, Firefox,
User Guide: Adding a Device in Duo and Managing Settings
 User Guide: Adding a Device in Duo and Managing Settings The Duo Mobile application provides an extra layer of security when it is incorporated into the login process for applications or web sites such
User Guide: Adding a Device in Duo and Managing Settings The Duo Mobile application provides an extra layer of security when it is incorporated into the login process for applications or web sites such
Duo Self-Enrollment Guide for Android Tablets
 Duo Self-Enrollment Guide for Android Tablets The Duo Mobile application provides an extra layer of security when it is incorporated into the login process for web sites such as uab.box.com. In addition
Duo Self-Enrollment Guide for Android Tablets The Duo Mobile application provides an extra layer of security when it is incorporated into the login process for web sites such as uab.box.com. In addition
MSU Authorized User Campus Access Procedure, Campus VPN
 MSU Authorized User Campus Access Procedure, Campus VPN This document provides the requirements and procedures for access to the Campus Network for MSU Authorized Users. Access to the Campus Network is
MSU Authorized User Campus Access Procedure, Campus VPN This document provides the requirements and procedures for access to the Campus Network for MSU Authorized Users. Access to the Campus Network is
Multi-Factor Authentication FAQs
 General FAQs What is Multi-factor Authentication (MFA)? Multi-factor authentication (MFA) seeks to decrease the likelihood that others can access your data. Specifically, it enhances the security of your
General FAQs What is Multi-factor Authentication (MFA)? Multi-factor authentication (MFA) seeks to decrease the likelihood that others can access your data. Specifically, it enhances the security of your
a) Log in using your credentials. Your User Name will be your address. Enter Password and click <Log On>
 Two-Factor Authentication Installation You will need your computer, internet connection and mobile device. Open up your internet browser and go to the website: https://cloud.cetrom.net a) Log in using
Two-Factor Authentication Installation You will need your computer, internet connection and mobile device. Open up your internet browser and go to the website: https://cloud.cetrom.net a) Log in using
CHI Easy Access: Register From on the CHI Network
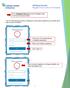 CHI Easy Access: Register From on the CHI Network Go to chieasyaccess.org and click "Register Now." You'll see the screen below. Your CHI Easy Access account is configured to use the same password you
CHI Easy Access: Register From on the CHI Network Go to chieasyaccess.org and click "Register Now." You'll see the screen below. Your CHI Easy Access account is configured to use the same password you
Duo Self-Enrollment Guide for ipads
 Duo Self-Enrollment Guide for ipads The Duo Mobile application provides an extra layer of security when it is incorporated into the login process for web sites such as uab.box.com. In addition to using
Duo Self-Enrollment Guide for ipads The Duo Mobile application provides an extra layer of security when it is incorporated into the login process for web sites such as uab.box.com. In addition to using
Reactivate the Smartphone in Your Duo Account
 Used for registered smartphone that are upgraded to a new operating system or when you get new smartphone, yet retain the same phone number. Re-Install the Duo Mobile App Complete on your Smartphone 1.
Used for registered smartphone that are upgraded to a new operating system or when you get new smartphone, yet retain the same phone number. Re-Install the Duo Mobile App Complete on your Smartphone 1.
Duo Multi-Factor Authentication Enrolling an iphone. Introduction. Enrolling an iphone
 Duo Multi-Factor Authentication Enrolling an iphone Introduction Duo is a multi-factor authentication tool chosen by Towson University to help prevent data breaches. Duo is a tool that verifies someone
Duo Multi-Factor Authentication Enrolling an iphone Introduction Duo is a multi-factor authentication tool chosen by Towson University to help prevent data breaches. Duo is a tool that verifies someone
Duo Enrollment for DA Employees
 Duo Enrollment for DA Employees Duo s Multi-Factor Authentication will be used to authenticate DA employees when using DA Portal, DA s Outlook Web Access (OWA), and DA s O365. It is RECOMMENDED to have
Duo Enrollment for DA Employees Duo s Multi-Factor Authentication will be used to authenticate DA employees when using DA Portal, DA s Outlook Web Access (OWA), and DA s O365. It is RECOMMENDED to have
Duo Multi-Factor Authentication Enrolling an ipad. Introduction
 Duo Multi-Factor Authentication Enrolling an ipad Introduction Duo is a multi-factor authentication tool chosen by Towson University to help prevent data breaches. Duo is a tool that verifies someone s
Duo Multi-Factor Authentication Enrolling an ipad Introduction Duo is a multi-factor authentication tool chosen by Towson University to help prevent data breaches. Duo is a tool that verifies someone s
Integrated Access Management Solutions. Access Televentures
 Integrated Access Management Solutions Access Televentures Table of Contents OVERCOMING THE AUTHENTICATION CHALLENGE... 2 1 EXECUTIVE SUMMARY... 2 2 Challenges to Providing Users Secure Access... 2 2.1
Integrated Access Management Solutions Access Televentures Table of Contents OVERCOMING THE AUTHENTICATION CHALLENGE... 2 1 EXECUTIVE SUMMARY... 2 2 Challenges to Providing Users Secure Access... 2 2.1
Enrolling Devices in Duo
 Enrolling Devices in Duo To use ArchPass, UGA s two-step login powered by Duo you will need to enroll a device with the Duo application. You can enroll any smartphone, mobile phone, landline phone or tablet.
Enrolling Devices in Duo To use ArchPass, UGA s two-step login powered by Duo you will need to enroll a device with the Duo application. You can enroll any smartphone, mobile phone, landline phone or tablet.
2-Step Verification. Summer 2018, Version 3. Table of Contents
 2-Step Verification Summer 2018, Version 3 Table of Contents Introduction... 2 Enrolling in 2-Step Verification... 2 Registering Your Device... 2 Mobile Phone... 3 Tablet... 6 Landline... 8 Hardware Token...
2-Step Verification Summer 2018, Version 3 Table of Contents Introduction... 2 Enrolling in 2-Step Verification... 2 Registering Your Device... 2 Mobile Phone... 3 Tablet... 6 Landline... 8 Hardware Token...
Texas Division How to Login and Register for My IT Support and ServiceNow
 Texas Division How to Login and Register for My IT Support and ServiceNow Go to texas.mychiitsuppport.org. You'll see the screen below. My IT Support/ServiceNow is a national system and utilizes national
Texas Division How to Login and Register for My IT Support and ServiceNow Go to texas.mychiitsuppport.org. You'll see the screen below. My IT Support/ServiceNow is a national system and utilizes national
DUO SECURITY SETUP INSTRUCTIONS
 DUO SECURITY SETUP INSTRUCTIONS Click on a link below to jump to a section Guide Contents INTRODUCTION TO DUO... 1 REQUESTING ACCESS... 2 EMAIL... 2 DEVICE OPTIONS... 2 ENROLLMENT GUIDE... 3 SETUP USING
DUO SECURITY SETUP INSTRUCTIONS Click on a link below to jump to a section Guide Contents INTRODUCTION TO DUO... 1 REQUESTING ACCESS... 2 EMAIL... 2 DEVICE OPTIONS... 2 ENROLLMENT GUIDE... 3 SETUP USING
Fingerprint Authentication Guide
 Fingerprint Authentication Guide What is fingerprint authentication? An electronic device is used to capture a digital image of a fingerprint pattern. This image is digitally processed to create a biometric
Fingerprint Authentication Guide What is fingerprint authentication? An electronic device is used to capture a digital image of a fingerprint pattern. This image is digitally processed to create a biometric
Timesheet Submission in Academica TRIO Upward Bound Summer Program June 25, 2018 Room 1700
 Timesheet Submission in Academica TRIO Upward Bound Summer Program June 25, 2018 Room 1700 Presentation created by Brittany Thomas *BEFORE WE BEGIN. If you have not already, you will need to call Computing
Timesheet Submission in Academica TRIO Upward Bound Summer Program June 25, 2018 Room 1700 Presentation created by Brittany Thomas *BEFORE WE BEGIN. If you have not already, you will need to call Computing
Software Token Enrollment: SafeNet MobilePASS+ for Apple ios
 Software Token Enrollment: SafeNet MobilePASS+ for Apple ios Step 1: Open the Self-Enrollment email a. Open the Self-Enrollment email on your Apple ios phone. NOTE: If using a personal phone, open the
Software Token Enrollment: SafeNet MobilePASS+ for Apple ios Step 1: Open the Self-Enrollment email a. Open the Self-Enrollment email on your Apple ios phone. NOTE: If using a personal phone, open the
a. Send Me a Push A DUO MOBILE Login request will appear on your Smartphone or Tablet. To authenticate:
 Duo Multi-Factor Authentication Authentication Methods Introduction Duo adds a second layer of security when authenticating to a system. This is done using a second device such as a phone or a landline.
Duo Multi-Factor Authentication Authentication Methods Introduction Duo adds a second layer of security when authenticating to a system. This is done using a second device such as a phone or a landline.
Cicayda Reprise Review Multi Factor Authentication (MFA) Administrative Tasks
 Cicayda Reprise Review Multi Factor Authentication (MFA) Administrative Tasks Table of Contents ADD MFA TO EXISTING REPRISE USER ACCOUNT 2 UPDATE MFA ON MY DEVICES 8 REMOVE MFA FROM REPRISE USER ACCOUNT
Cicayda Reprise Review Multi Factor Authentication (MFA) Administrative Tasks Table of Contents ADD MFA TO EXISTING REPRISE USER ACCOUNT 2 UPDATE MFA ON MY DEVICES 8 REMOVE MFA FROM REPRISE USER ACCOUNT
River Bank & Trust Online Banking Initial Log In Instructions
 River Bank & Trust Online Banking Initial Log In Instructions Step 1: Go to River Bank & Trust s website (https://riverbankandtrust.com/). Locate the Online Banking Login box in the upper right corner
River Bank & Trust Online Banking Initial Log In Instructions Step 1: Go to River Bank & Trust s website (https://riverbankandtrust.com/). Locate the Online Banking Login box in the upper right corner
Help Desk Guide. Originally released June 22, 2016 Revised July 24, 2017
 Help Desk Guide Originally released June 22, 2016 Revised July 24, 2017 Table of Contents Commonly-used terms Part 1: Overview Why do I need this guide? Part 2: Enrollment and activation What will the
Help Desk Guide Originally released June 22, 2016 Revised July 24, 2017 Table of Contents Commonly-used terms Part 1: Overview Why do I need this guide? Part 2: Enrollment and activation What will the
Securing today s identity and transaction systems:! What you need to know! about two-factor authentication!
 Securing today s identity and transaction systems:! What you need to know! about two-factor authentication! 1 Today s Speakers! Alex Doll! CEO OneID Jim Fenton! Chief Security Officer OneID 2 Contents!
Securing today s identity and transaction systems:! What you need to know! about two-factor authentication! 1 Today s Speakers! Alex Doll! CEO OneID Jim Fenton! Chief Security Officer OneID 2 Contents!
ICE CLEAR EUROPE DMS GLOBAL ID CREATION USER GUIDE VERSION 1.0
 ICE CLEAR EUROPE DMS GLOBAL ID CREATION USER GUIDE VERSION 1.0 August 2017 Date Version Description August 2017 1.0 Initial Draft 1. Single Sign On... 2 2. To register for SSO on the Global ID webpage...
ICE CLEAR EUROPE DMS GLOBAL ID CREATION USER GUIDE VERSION 1.0 August 2017 Date Version Description August 2017 1.0 Initial Draft 1. Single Sign On... 2 2. To register for SSO on the Global ID webpage...
Attacking Your Two-Factor Authentication (PS: Use Two-Factor Authentication)
 Attacking Your Two-Factor Authentication (PS: Use Two-Factor Authentication) 08 Jun 2017 K-LUG Technical Meeting Rochester, MN Presented by: Vi Grey Independent Security Researcher https://vigrey.com Who
Attacking Your Two-Factor Authentication (PS: Use Two-Factor Authentication) 08 Jun 2017 K-LUG Technical Meeting Rochester, MN Presented by: Vi Grey Independent Security Researcher https://vigrey.com Who
DUO Two Factor Authentication (DUO 2FA) User Guide for O365 Applications Login
 DUO Two Factor Authentication (DUO 2FA) User Guide for O365 Applications Login Prepared By ITSC Version: 1 Apr 2018 Page 1 Table of Contents 1. About O365 Logon with Duo 2FA... 4 1.1. Prerequisites...
DUO Two Factor Authentication (DUO 2FA) User Guide for O365 Applications Login Prepared By ITSC Version: 1 Apr 2018 Page 1 Table of Contents 1. About O365 Logon with Duo 2FA... 4 1.1. Prerequisites...
Online Banking Initial Log In Instructions. Go to and enter your username: Ex JaneDoe
 Online Banking Initial Log In Instructions Go to www.riverbankandtrust.com and enter your username: Ex JaneDoe 1 Step 1: Enter your existing login ID: Step 2: Enter security code: username + last 4 of
Online Banking Initial Log In Instructions Go to www.riverbankandtrust.com and enter your username: Ex JaneDoe 1 Step 1: Enter your existing login ID: Step 2: Enter security code: username + last 4 of
Contents. Multi-Factor Authentication Overview. Available MFA Factors
 The purpose of this document is to provide National University student Single Sign-On users with instructions for how to configure and use Multi-Factor Authentication. Contents Multi-Factor Authentication
The purpose of this document is to provide National University student Single Sign-On users with instructions for how to configure and use Multi-Factor Authentication. Contents Multi-Factor Authentication
Two Factor Authentication
 Two Factor Authentication On December 15 th 2017 the Costpoint Cloud will require Two Factor Authentication when accessing User Manager and Citrix. Also, users will be required to access Costpoint Enterprise
Two Factor Authentication On December 15 th 2017 the Costpoint Cloud will require Two Factor Authentication when accessing User Manager and Citrix. Also, users will be required to access Costpoint Enterprise
Authentication Options
 Authentication Options The following options are available to RamsVPN users when authenticating with two-factor authentication. *** Authenticating via web browser is only necessary for enrolling/managing
Authentication Options The following options are available to RamsVPN users when authenticating with two-factor authentication. *** Authenticating via web browser is only necessary for enrolling/managing
BIDMC Multi-Factor Authentication Enrollment Guide Table of Contents
 BIDMC Multi-Factor Authentication Enrollment Guide Table of Contents Definitions... 2 Summary... 2 BIDMC Multi-Factor Authentication Enrollment... 3 Common Multi-Factor Authentication Enrollment Issues...
BIDMC Multi-Factor Authentication Enrollment Guide Table of Contents Definitions... 2 Summary... 2 BIDMC Multi-Factor Authentication Enrollment... 3 Common Multi-Factor Authentication Enrollment Issues...
Multi-Factor Authentication User Setup Guide
 Multi-Factor Authentication User Setup Guide This document is designed to provide assistance and guidance to someone setting up Multi-Factor Authentication in Office 365. Multi-factor, or 2 factor, authentication
Multi-Factor Authentication User Setup Guide This document is designed to provide assistance and guidance to someone setting up Multi-Factor Authentication in Office 365. Multi-factor, or 2 factor, authentication
First Interstate Bank s Business Online Banking
 New Clients from Bank of the Cascades First Interstate Bank s Business Online Banking CLIENT CONVERSION GUIDE Important Dates and Times Your Bank of the Cascades business online banking access will continue
New Clients from Bank of the Cascades First Interstate Bank s Business Online Banking CLIENT CONVERSION GUIDE Important Dates and Times Your Bank of the Cascades business online banking access will continue
Duo Travel Guide. duo.com
 Duo Travel Guide duo.com Overview As a member of an organization protected by Duo, you already have secure access to applications and assets. This guide is designed to help you maintain that trusted access
Duo Travel Guide duo.com Overview As a member of an organization protected by Duo, you already have secure access to applications and assets. This guide is designed to help you maintain that trusted access
Remote Access with Imprivata Two-factor Authentication
 Remote Access with Imprivata Two-factor Authentication Migrating from RSA SecureID to Imprivata ID Token Please download and install the Imprivata ID app from the Google Play Store or Apple App Store first!
Remote Access with Imprivata Two-factor Authentication Migrating from RSA SecureID to Imprivata ID Token Please download and install the Imprivata ID app from the Google Play Store or Apple App Store first!
The security challenge in a mobile world
 The security challenge in a mobile world Contents Executive summary 2 Executive summary 3 Controlling devices and data from the cloud 4 Managing mobile devices - Overview - How it works with MDM - Scenario
The security challenge in a mobile world Contents Executive summary 2 Executive summary 3 Controlling devices and data from the cloud 4 Managing mobile devices - Overview - How it works with MDM - Scenario
Authentication Methods
 CERT-EU Security Whitepaper 16-003 Authentication Methods D.Antoniou, K.Socha ver. 1.0 20/12/2016 TLP: WHITE 1 Authentication Lately, protecting data has become increasingly difficult task. Cyber-attacks
CERT-EU Security Whitepaper 16-003 Authentication Methods D.Antoniou, K.Socha ver. 1.0 20/12/2016 TLP: WHITE 1 Authentication Lately, protecting data has become increasingly difficult task. Cyber-attacks
DPHremote.ucsf.edu for Webconnect Users
 Page 1 of 10 DPHremote.ucsf.edu for Webconnect Users The current version of DPH WebConnect heavily depends on Java and Safari preferences and these settings periodically are changed as Java, Citrix, and
Page 1 of 10 DPHremote.ucsf.edu for Webconnect Users The current version of DPH WebConnect heavily depends on Java and Safari preferences and these settings periodically are changed as Java, Citrix, and
The MSU Department of Mathematics "Account Manager" can be used for the following:
 MSU Department of Mathematics Account Manager Tutorial Overview The MSU Department of Mathematics "Account Manager" can be used for the following: Change your Math account password Reset a forgotten password
MSU Department of Mathematics Account Manager Tutorial Overview The MSU Department of Mathematics "Account Manager" can be used for the following: Change your Math account password Reset a forgotten password
Imprivata ID Enrollment Instructions iphone instructions
 Imprivata ID Enrollment Instructions iphone instructions Imprivata ID is the system EvergreenHealth uses to provide an extra layer of security in addition to username/password when logging in remotely
Imprivata ID Enrollment Instructions iphone instructions Imprivata ID is the system EvergreenHealth uses to provide an extra layer of security in addition to username/password when logging in remotely
2FA ENROLLMENT INSTRUCTIONS
 2FA ENROLLMENT INSTRUCTIONS Should you need assistance with these enrollment instructions, please contact the ITS Support Center at 703-993-8870 or support@gmu.edu Select which device: U.S. Phone Number
2FA ENROLLMENT INSTRUCTIONS Should you need assistance with these enrollment instructions, please contact the ITS Support Center at 703-993-8870 or support@gmu.edu Select which device: U.S. Phone Number
BOCHK Mobile Token FAQ
 BOCHK Mobile Token FAQ 1. What is "Mobile Token"? "Mobile Token" is a feature of BOCHK Mobile App. Upon activation of "Mobile Token" with a designated mobile device ("mobile phone"), you can use it immediately
BOCHK Mobile Token FAQ 1. What is "Mobile Token"? "Mobile Token" is a feature of BOCHK Mobile App. Upon activation of "Mobile Token" with a designated mobile device ("mobile phone"), you can use it immediately
Modern two-factor authentication: Easy. Affordable. Secure.
 Modern two-factor authentication: Easy. Affordable. Secure. www.duosecurity.com Your systems and users are under attack like never before The last few years have seen an unprecedented number of attacks
Modern two-factor authentication: Easy. Affordable. Secure. www.duosecurity.com Your systems and users are under attack like never before The last few years have seen an unprecedented number of attacks
Getting Started Accessing Okta All Employees
 Purpose Okta is a cloud platform that provides single sign-on for Magellan applications. HR systems such as Workday, Saba, VERN along with communication platforms and collaboration tools such as MagellanNOW,
Purpose Okta is a cloud platform that provides single sign-on for Magellan applications. HR systems such as Workday, Saba, VERN along with communication platforms and collaboration tools such as MagellanNOW,
UH Secure Remote Access (SecureAuth)
 (SecureAuth) User Registration Process In the near future, UH will use a new secure remote access process that features two-factor authentication to further protect our network and applications. Completing
(SecureAuth) User Registration Process In the near future, UH will use a new secure remote access process that features two-factor authentication to further protect our network and applications. Completing
Information & Technology Services. Opting in for Multi-Factor Authentication
 Information & Technology Services Opting in for Multi-Factor Authentication Login to mycampus.astate.edu When logged in, After you have logged in successfully, you should see folders on the left side of
Information & Technology Services Opting in for Multi-Factor Authentication Login to mycampus.astate.edu When logged in, After you have logged in successfully, you should see folders on the left side of
Access and Setup Guide
 ss Access and Setup Guide Creating an Account with Duo and Setting up Citrix Workspace/Receiver to Log in to the Interactive Reporting Site BCBSM PGIP INTERACTI VE REPORTING Contents Introduction... 2
ss Access and Setup Guide Creating an Account with Duo and Setting up Citrix Workspace/Receiver to Log in to the Interactive Reporting Site BCBSM PGIP INTERACTI VE REPORTING Contents Introduction... 2
HIPAA Compliance discussion
 HIPAA Compliance discussion GoToWebinar Housekeeping: attendee participation Open and hide your control panel Join audio: Choose Mic & Speakers to use VoIP Choose Telephone and dial using the information
HIPAA Compliance discussion GoToWebinar Housekeeping: attendee participation Open and hide your control panel Join audio: Choose Mic & Speakers to use VoIP Choose Telephone and dial using the information
Using MFA with the Pulse Client
 Using MFA with the Pulse Client 1. Launch the Pulse client and open your preferred connection. 2. A new pre-sign in notification will display similar to the one shown below. This page explains your options
Using MFA with the Pulse Client 1. Launch the Pulse client and open your preferred connection. 2. A new pre-sign in notification will display similar to the one shown below. This page explains your options
Creating a Parent Account and setting up Notification preferences.
 Creating a Parent Account and setting up Notification preferences. This document will walk you through the steps to: 1. Create a Parent Account so that you can have access to the courses your child is
Creating a Parent Account and setting up Notification preferences. This document will walk you through the steps to: 1. Create a Parent Account so that you can have access to the courses your child is
WHITE PAPER AUTHENTICATION YOUR WAY SECURING ACCESS IN A CHANGING WORLD
 WHITE PAPER AUTHENTICATION YOUR WAY SECURING ACCESS IN A CHANGING WORLD Imagine that you re a CISO in charge of identity and access management for a major global technology and manufacturing company. You
WHITE PAPER AUTHENTICATION YOUR WAY SECURING ACCESS IN A CHANGING WORLD Imagine that you re a CISO in charge of identity and access management for a major global technology and manufacturing company. You
Electronically Prescribing Controlled Substances
 Audience: All E-Prescribing Physicians To e-prescribe controlled substances in Epic, you must first install the SecureAuth Authenticate app on your smartphone. This app is required as a secondary form
Audience: All E-Prescribing Physicians To e-prescribe controlled substances in Epic, you must first install the SecureAuth Authenticate app on your smartphone. This app is required as a secondary form
SAFETY TRAINING APP INSTRUCTION GUIDE Powered by. For Apple (ios) Mobile Devices
 For Apple (ios) Mobile Devices 1 For Apple (ios) Products 1. Download App page 3 2. Create Account page 4-5 3. Login to App page 6-7 4. Create Attendees page 8-9 5. Create Training Event page 10-13 6.
For Apple (ios) Mobile Devices 1 For Apple (ios) Products 1. Download App page 3 2. Create Account page 4-5 3. Login to App page 6-7 4. Create Attendees page 8-9 5. Create Training Event page 10-13 6.
Deprecating the Password: A Progress Report. Dr. Michael B. Jones Identity Standards Architect, Microsoft May 17, 2018
 Deprecating the Password: A Progress Report Dr. Michael B. Jones Identity Standards Architect, Microsoft May 17, 2018 The password problem Alpha-numeric passwords are hard for humans to remember and easy
Deprecating the Password: A Progress Report Dr. Michael B. Jones Identity Standards Architect, Microsoft May 17, 2018 The password problem Alpha-numeric passwords are hard for humans to remember and easy
Protect Yourself Against VPN-Based Attacks: Five Do s and Don ts
 White Paper Protect Yourself Against VPN-Based Attacks: Five Do s and Don ts Don t let stolen VPN credentials jeopardize your security March 2015 A TECHTARGET WHITE PAPER Most IT professionals take for
White Paper Protect Yourself Against VPN-Based Attacks: Five Do s and Don ts Don t let stolen VPN credentials jeopardize your security March 2015 A TECHTARGET WHITE PAPER Most IT professionals take for
Welcome! Ready To Secure Access to Your Microsoft Applications?
 Welcome! Ready To Secure Access to Your Microsoft Applications? During the Webinar Audio In presentation mode until end Control Panel View webinar in full screen mode Feel Free to submit written questions
Welcome! Ready To Secure Access to Your Microsoft Applications? During the Webinar Audio In presentation mode until end Control Panel View webinar in full screen mode Feel Free to submit written questions
SAFETY TRAINING APP INSTRUCTION GUIDE Powered by. For Android Devices
 For Android Devices 1 For Android Devices 1. Download App page 3 2. Create Account page 4-5 3. Login to App page 6-7 4. Create Attendees page 8-9 5. Create Training Event page 10-13 6. Document Training
For Android Devices 1 For Android Devices 1. Download App page 3 2. Create Account page 4-5 3. Login to App page 6-7 4. Create Attendees page 8-9 5. Create Training Event page 10-13 6. Document Training
Welcome to the. Patient Portal!
 Welcome to the Patient Portal! You re about to find out just how easy it can be to communicate with your healthcare provider and take control of your medical information. Using this quick reference guide,
Welcome to the Patient Portal! You re about to find out just how easy it can be to communicate with your healthcare provider and take control of your medical information. Using this quick reference guide,
Using Biometric Authentication to Elevate Enterprise Security
 Using Biometric Authentication to Elevate Enterprise Security Biometric authentication in the enterprise? It s just a matter of time Mobile biometric authentication is officially here to stay. Most of
Using Biometric Authentication to Elevate Enterprise Security Biometric authentication in the enterprise? It s just a matter of time Mobile biometric authentication is officially here to stay. Most of
AppSpider Enterprise. Getting Started Guide
 AppSpider Enterprise Getting Started Guide Contents Contents 2 About AppSpider Enterprise 4 Getting Started (System Administrator) 5 Login 5 Client 6 Add Client 7 Cloud Engines 8 Scanner Groups 8 Account
AppSpider Enterprise Getting Started Guide Contents Contents 2 About AppSpider Enterprise 4 Getting Started (System Administrator) 5 Login 5 Client 6 Add Client 7 Cloud Engines 8 Scanner Groups 8 Account
Securing Your Salesforce Org: The Human Factor. February 2016 User Group Meeting
 Securing Your Salesforce Org: The Human Factor February 2016 User Group Meeting Safe Harbor Safe harbor statement under the Private Securities Litigation Reform Act of 1995: This presentation may contain
Securing Your Salesforce Org: The Human Factor February 2016 User Group Meeting Safe Harbor Safe harbor statement under the Private Securities Litigation Reform Act of 1995: This presentation may contain
Manual: Create a Staff Posting Initiator
 Manual: Create a Staff Posting Initiator Revised: 11-27-17 Introduction The University of Georgia has implemented a new version of its applicant tracking system, ipaws. The objective of ipaws is to streamline
Manual: Create a Staff Posting Initiator Revised: 11-27-17 Introduction The University of Georgia has implemented a new version of its applicant tracking system, ipaws. The objective of ipaws is to streamline
Jordan Levesque - Keeping your Business Secure
 Jordan Levesque - Keeping your Business Secure Review of PCI Benefits of hosting with RCS File Integrity Monitoring Two Factor Log Aggregation Vulnerability Scanning Configuration Management and Continuous
Jordan Levesque - Keeping your Business Secure Review of PCI Benefits of hosting with RCS File Integrity Monitoring Two Factor Log Aggregation Vulnerability Scanning Configuration Management and Continuous
Multi-Factor Authentication
 Introduction (MFA) provides an additional layer of security to your NHSmail account when signing in to NHSmail via a web browser. As a Local Administrator (LA) you will have MFA automatically enabled on
Introduction (MFA) provides an additional layer of security to your NHSmail account when signing in to NHSmail via a web browser. As a Local Administrator (LA) you will have MFA automatically enabled on
Multi-Factor Authentication (MFA)
 10.10.18 1 Multi-Factor Authentication (MFA) What is it? Why should I use it? CYBERSECURITY Tech Fair 2018 10.10.18 2 Recent Password Hacks PlayStation Network (2011) 77 Million accounts hacked Adobe (2013)
10.10.18 1 Multi-Factor Authentication (MFA) What is it? Why should I use it? CYBERSECURITY Tech Fair 2018 10.10.18 2 Recent Password Hacks PlayStation Network (2011) 77 Million accounts hacked Adobe (2013)
Two-Factor Authentication over Mobile: Simplifying Security and Authentication
 SAP Thought Leadership Paper SAP Digital Interconnect Two-Factor Authentication over Mobile: Simplifying Security and Authentication Controlling Fraud and Validating End Users Easily and Cost-Effectively
SAP Thought Leadership Paper SAP Digital Interconnect Two-Factor Authentication over Mobile: Simplifying Security and Authentication Controlling Fraud and Validating End Users Easily and Cost-Effectively
Multi-Factor Authentication (MFA)
 What is it? Multi-Factor Authentication, or MFA, is a process that requires more than one type of authentication to gain access to a program. You have probably seen this with your bank or other secure
What is it? Multi-Factor Authentication, or MFA, is a process that requires more than one type of authentication to gain access to a program. You have probably seen this with your bank or other secure
What is Authentication? All requests for resources have to be monitored. Every request must be authenticated and authorized to use the resource.
 P1L4 Authentication What is Authentication? All requests for resources have to be monitored. Every request must be authenticated and authorized to use the resource. Authentication: Who are you? Prove it.
P1L4 Authentication What is Authentication? All requests for resources have to be monitored. Every request must be authenticated and authorized to use the resource. Authentication: Who are you? Prove it.
EXPERIENCE SIMPLER, STRONGER AUTHENTICATION
 1 EXPERIENCE SIMPLER, STRONGER AUTHENTICATION 2 Data Breaches are out of control 3 IN 2014... 708 data breaches 82 million personal records stolen $3.5 million average cost per breach 4 We have a PASSWORD
1 EXPERIENCE SIMPLER, STRONGER AUTHENTICATION 2 Data Breaches are out of control 3 IN 2014... 708 data breaches 82 million personal records stolen $3.5 million average cost per breach 4 We have a PASSWORD
TWO-STEP VERIFICATION USER GUIDE
 TWO-STEP VERIFICATION USER GUIDE TWO-STEP PROTECTS YOUR DATA EVEN IF YOUR PENNKEY PASSWORD IS COMPROMISED PROTECT YOUR PENN & PERSONAL DATA! Table of Contents Two-Step Verification User Guide... 2 1. Introduction...
TWO-STEP VERIFICATION USER GUIDE TWO-STEP PROTECTS YOUR DATA EVEN IF YOUR PENNKEY PASSWORD IS COMPROMISED PROTECT YOUR PENN & PERSONAL DATA! Table of Contents Two-Step Verification User Guide... 2 1. Introduction...
Registering an ipad for Duo Two-Factor Authentication
 University Information Technology Services Technology Outreach Registering an ipad for Duo Two-Factor Authentication Duo is a two-factor authentication solution for campus community members. Using Duo,
University Information Technology Services Technology Outreach Registering an ipad for Duo Two-Factor Authentication Duo is a two-factor authentication solution for campus community members. Using Duo,
Registering an Android Tablet for Duo Two-Factor Authentication
 University Information Technology Services Technology Outreach Registering an Android Tablet for Duo Two-Factor Authentication Duo is a two-factor authentication solution for campus community members.
University Information Technology Services Technology Outreach Registering an Android Tablet for Duo Two-Factor Authentication Duo is a two-factor authentication solution for campus community members.
The Lord of the Keys How two-part seed records solve all safety concerns regarding two-factor authentication
 White Paper The Lord of the Keys How two-part seed records solve all safety concerns regarding two-factor authentication Table of contents Introduction... 2 Password protection alone is no longer enough...
White Paper The Lord of the Keys How two-part seed records solve all safety concerns regarding two-factor authentication Table of contents Introduction... 2 Password protection alone is no longer enough...
Registering an iphone for Duo Two-Factor Authentication
 University Information Technology Services Technology Outreach Registering an iphone for Duo Two-Factor Authentication Duo is a two-factor authentication solution for campus community members. Using Duo,
University Information Technology Services Technology Outreach Registering an iphone for Duo Two-Factor Authentication Duo is a two-factor authentication solution for campus community members. Using Duo,
EBOOK 4 TIPS FOR STRENGTHENING THE SECURITY OF YOUR VPN ACCESS
 EBOOK 4 TIPS FOR STRENGTHENING THE SECURITY OF YOUR VPN ACCESS HOW SECURE IS YOUR VPN ACCESS? Remote access gateways such as VPNs and firewalls provide critical anywhere-anytime connections to the networks
EBOOK 4 TIPS FOR STRENGTHENING THE SECURITY OF YOUR VPN ACCESS HOW SECURE IS YOUR VPN ACCESS? Remote access gateways such as VPNs and firewalls provide critical anywhere-anytime connections to the networks
Do not store PHI/HIPAA data on your UTH-Share account unless you have enabled your account for PHI data access.
 Do not store PHI/HIPAA data on your UTH-Share account unless you have enabled your account for PHI data access. Information About UTH Share UTH Share is UTHealth s implementation of Google Apps for Education,
Do not store PHI/HIPAA data on your UTH-Share account unless you have enabled your account for PHI data access. Information About UTH Share UTH Share is UTHealth s implementation of Google Apps for Education,
Multi-Factor Authentication (MFA)
 What is it? Multi-Factor Authentication, or MFA, is a process that requires more than one type of authentication to gain access to a program. You have probably seen this with your bank or other secure
What is it? Multi-Factor Authentication, or MFA, is a process that requires more than one type of authentication to gain access to a program. You have probably seen this with your bank or other secure
Welcome to the. Patient Portal!
 Welcome to the Patient Portal! You re about to find out just how easy it can be to communicate with your healthcare provider, schedule and request appointments, take control of your medical information,
Welcome to the Patient Portal! You re about to find out just how easy it can be to communicate with your healthcare provider, schedule and request appointments, take control of your medical information,
Maximize your move to Microsoft in the cloud
 Citrix and Microsoft 365: Maximize your move to Microsoft in the cloud 3 reasons to manage Office 365 with Citrix Workspace Pg. 2 Pg. 4 Citrix.com e-book Maximize your Citrix Workspace 1 Content Introduction...3
Citrix and Microsoft 365: Maximize your move to Microsoft in the cloud 3 reasons to manage Office 365 with Citrix Workspace Pg. 2 Pg. 4 Citrix.com e-book Maximize your Citrix Workspace 1 Content Introduction...3
Moving to Multi Factor Authentication (MFA)
 Moving to Multi Factor Authentication (MFA) Starting on June 29, 2018 MFA will be enforced on all of our public facing services, including: Webmail, KGH Today and Kronos (Self-Serve). If you are not enrolled
Moving to Multi Factor Authentication (MFA) Starting on June 29, 2018 MFA will be enforced on all of our public facing services, including: Webmail, KGH Today and Kronos (Self-Serve). If you are not enrolled
Unlocking Office 365 without a password. How to Secure Access to Your Business Information in the Cloud without needing to remember another password.
 Unlocking Office 365 without a password How to Secure Access to Your Business Information in the Cloud without needing to remember another password. Introduction It is highly likely that if you have downloaded
Unlocking Office 365 without a password How to Secure Access to Your Business Information in the Cloud without needing to remember another password. Introduction It is highly likely that if you have downloaded
Challenges and. Opportunities. MSPs are Facing in Security
 Challenges and Opportunities MSPs are Facing in 2017 Security MSPs work in an environment that is constantly changing for both the needs of customers and the technology in which they provide. Fanning the
Challenges and Opportunities MSPs are Facing in 2017 Security MSPs work in an environment that is constantly changing for both the needs of customers and the technology in which they provide. Fanning the
User Guide for Client Remote Access. Version 1.2
 User Guide for Client Remote Access Version 1.2 Table of Contents PAGE Introduction... 2 Microsoft Multi-Factor Authentication Introduction... 3-4 User Enrollment... 5-8 Accessing Remote Resources Windows
User Guide for Client Remote Access Version 1.2 Table of Contents PAGE Introduction... 2 Microsoft Multi-Factor Authentication Introduction... 3-4 User Enrollment... 5-8 Accessing Remote Resources Windows
Crash course in Azure Active Directory
 Crash course in Azure Active Directory Crash course in Azure Active Directory Competing today requires a focus on digital transformation and empowering everyone to be creative and work together securely.
Crash course in Azure Active Directory Crash course in Azure Active Directory Competing today requires a focus on digital transformation and empowering everyone to be creative and work together securely.
TFS Self-Service Password Reset Portal Getting Started Guide
 TFS Self-Service Password Reset Portal Getting Started Guide Texas A&M Forest Service (TFS) Information Resources Department (IR) A quick guide to getting started and using the TFS self-service password
TFS Self-Service Password Reset Portal Getting Started Guide Texas A&M Forest Service (TFS) Information Resources Department (IR) A quick guide to getting started and using the TFS self-service password
Multi-Factor Authentication Enrolment Guide
 Multi-Factor Authentication Enrolment Guide How to set up the service and authenticate successfully What is MFA and how does it impact the way I sign into my account or applications? Multi-Factor Authentication
Multi-Factor Authentication Enrolment Guide How to set up the service and authenticate successfully What is MFA and how does it impact the way I sign into my account or applications? Multi-Factor Authentication
AirWatch Container. VMware Workspace ONE UEM
 VMware Workspace ONE UEM You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments about this documentation, submit your feedback
VMware Workspace ONE UEM You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments about this documentation, submit your feedback
Getting Started Accessing Okta All Employees
 Purpose Okta is a cloud platform that provides single sign-on for Magellan applications. HR systems such as Workday, Saba, VERN along with communication platforms and collaboration tools such as MagellanNOW,
Purpose Okta is a cloud platform that provides single sign-on for Magellan applications. HR systems such as Workday, Saba, VERN along with communication platforms and collaboration tools such as MagellanNOW,
isupplier Portal: Multi-Factor Authentication and One-Time- Passcodes Last Updated: 4-Jun-18 Level 4 - Public INFRASTRUCTURE MINING & METALS
 INFRASTRUCTURE MINING & METALS NUCLEAR, SECURITY & ENVIRONMENTAL OIL, GAS & CHEMICALS isupplier Portal: Multi-Factor Authentication and One-Time- Passcodes Last Updated: 4-Jun-18 Level 4 - Public Table
INFRASTRUCTURE MINING & METALS NUCLEAR, SECURITY & ENVIRONMENTAL OIL, GAS & CHEMICALS isupplier Portal: Multi-Factor Authentication and One-Time- Passcodes Last Updated: 4-Jun-18 Level 4 - Public Table
Two-Factor Authentication for Q-Port
 Two-Factor Authentication for Q-Port Installation Guide Date: 2017-06-21 Document Version: 1.1 LEGAL DISCLAIMER Neither Nasdaq Inc. or any of its affiliates or subsidiaries (collectively Nasdaq ) assumes
Two-Factor Authentication for Q-Port Installation Guide Date: 2017-06-21 Document Version: 1.1 LEGAL DISCLAIMER Neither Nasdaq Inc. or any of its affiliates or subsidiaries (collectively Nasdaq ) assumes
Content: Installing and Setting Up Ever Accountable. Steps Involved To Install On Windows
 Installing and Setting Up Ever Accountable Content: Steps Involved To Install On Windows 1. Signing up for an Ever Accountable account 2. Installing Ever Accountable on your device 3. Adjusting the settings
Installing and Setting Up Ever Accountable Content: Steps Involved To Install On Windows 1. Signing up for an Ever Accountable account 2. Installing Ever Accountable on your device 3. Adjusting the settings
LinQ2FA. Helping You. Network. Direct Communication. Stay Fraud Free!
 LinQ2FA Stay Fraud Free! Helping You Direct Communication Secure to your Your customers Network LINQ2FA Stay Fraud Free! Enhance your security against cyber fraud with Two Factor Authentication Suitable
LinQ2FA Stay Fraud Free! Helping You Direct Communication Secure to your Your customers Network LINQ2FA Stay Fraud Free! Enhance your security against cyber fraud with Two Factor Authentication Suitable
Paystar Remittance Suite Tokenless Two-Factor Authentication
 Paystar Remittance Suite Tokenless Two-Factor Authentication Introduction Authentication is the process by which a computer system positively identifies a user It is commonly considered to be one of the
Paystar Remittance Suite Tokenless Two-Factor Authentication Introduction Authentication is the process by which a computer system positively identifies a user It is commonly considered to be one of the
Zimbra Collaboration Two-Factor Authentication
 Protecting Your Zimbra Collaboration Environment Zimbra Collaboration Two-Factor Authentication A Zimbra Collaboration Whitepaper Table of Contents Improves Your Company s Security 3 How Does It Work?
Protecting Your Zimbra Collaboration Environment Zimbra Collaboration Two-Factor Authentication A Zimbra Collaboration Whitepaper Table of Contents Improves Your Company s Security 3 How Does It Work?
