How To Encrypt a Windows 7, 8.1 or 10 laptop or tablet
|
|
|
- Melanie Byrd
- 6 years ago
- Views:
Transcription
1 How To Encrypt a Windows 7, 8.1 or 10 laptop or tablet Introduction College sensitive information stored on a mobile computing device is at risk for unauthorized access and disclosure if appropriate security measures are not implemented to protect the device against loss or theft of information. The best way to protect College sensitive information is to not store it on a mobile computing device; however, it is recognized that storage of College sensitive information on a mobile computing device may be necessary in certain situations. In these cases, encryption provides protection against unauthorized access and disclosure. This article provides instructions for using Microsoft's Bitlocker encryption technology to encrypt and protect data stored on Windows laptops or tablets. (BitLocker is a security mechanism that provides two primary functions: verification of the overall integrity of the Windows operating system at startup, and fulldrive data encryption. Once BitLocker is enabled and configured, the file system on the protected drive(s) is unlocked, and the drive encryption does not interfere with running applications.) Encryption must be used in concert with other security measures to maximize protection of information technology resources and of College sensitive information. Lethbridge College Information Technology has provided a Mobile Computing Security website that contains further information about other security measures. Applicability This article is intended for use by any faculty, staff, or student member who would like to safeguard data stored on a Windows laptop or tablet. Note: Since Lethbridge College s most widely-deployed version of Windows is Windows 7, this article will focus on setting up Bitlocker on that operating system. Relevant links to the Windows 8.1 and Windows 10 versions of these procedures are linked where needed. Procedure Prerequisites Enabling BitLocker requires that the laptop has the correct hardware for storing a Master Volume Key (MVK) and related data. Microsoft allows this data to be stored in either a Trusted Platform Module (TPM) or on a USB drive. The College advises that BitLocker be enabled only on hardware with a functional TPM. Our experience is that USB drives are too easy to lose or damage when used in this context. Please note, if you do use a USB drive to backup your MVK contrary to this warning, and it becomes lost
2 or stolen, data recovery will not be possible. Your data will become encrypted and locked forever, and should be considered securely destroyed. To check if your laptop has the necessary TPM module, perform the following steps: 1. Windows 7: Click Start. Right-click on Computer, then left-click on Manage. You may need to allow Administrator access. 2. Windows 8.1: Swipe in from the right edge of the screen, and then tap Search. Type Device Manager in the search box, and tap or click Device Manager. You may need to allow Administrator access. In the list of installed devices, look for: Trusted Platform Module (TPM) 3. Windows 10: Click Start. Type Device Manager in the search box and tap Device Manager on the menu. You may need to allow Administrator access. In the list of installed devices, look for: Trusted Platform Module (TPM) 4. Click Security Devices. If there is no "Security Devices" option, or if there is no TPM listed, you may need to verify with the manufacturer to determine if TPM was an included option. If it was not, please contact the Help Desk at for further encryption options and assistance. If you have a domain Windows laptop, your computer should have the Microsoft Bitlocker Administration and Management client. (MDOP MBAM). The following instructions will guide you to discover if the client is installed. 1. For Windows 7: Click Start. Click Control Panel. Click Programs and Features. In the list of programs, you should see MDOP MBAM in the list of installed programs. 2. For Windows 10: Click O next to the Start menu. Type Programs. Click on Add or remove programs. You should see MDOP MBAM in the list of installed programs.
3 General instructions Note: If at any time you have difficulty or encounter problems with this process, please contact the HelpDesk at or Note: The instructions and screen captures presented here are primarily for Windows 7 computers, but the encryption process is essentially the same for Windows 8.1 and Windows 10. Some images and text may not exactly match your computer. 1. Follow the relevant steps for your device: Windows 7: Click Start, click Control Panel, and then double-click BitLocker Drive Encryption. Windows 8.1: Click Start, click Control Panel, and select System & Security BitLocker Drive Encryption. Windows 10: Open File Explorer and go to This PC. Right-click on Local Disk (C:). 2. Click Turn On BitLocker for the drive that you want to encrypt. If you see the following warning, please stop the process and call the HelpDesk at for further encryption options and assistance.
4 3. On some versions of Windows, you will be prompted to create a BitLocker password. If you already log in to your computer using a password, you will likely not see this prompt. 4. The BitLocker setup wizard will ask you to choose how to store the recovery key. You can choose from the following options: 1. Save the recovery key to a USB flash drive. (However, if you are trying to encrypt a USB drive, this option will not work.) 2. Save the recovery key to a file. (This saves the recovery key to a network drive or other location, such as a recovery partition on your hard drive, or USB removable drive. However, you cannot save the encryption recovery key to the same hard drive you re trying to encrypt.) 3. Print the recovery key. You may print to a regular printer or a PDF but if you store this document on the encrypted device, you may lose this information in the event you are locked out of the device. Use one or more of these options to preserve the recovery key. Click Save to store your recovery key. For maximum security, you should store recovery keys apart from the drives they are associated with. 5. The BitLocker setup wizard will ask if you are ready to encrypt the drive. Windows 7: Click Start Encrypting Windows 8.1 and 10: You will be prompted to reboot the computer, and will then be asked to supply your Bitlocker password. After this, click Continue.
5 The "Encrypting..." status bar will be displayed. You can monitor the ongoing status of the drive encryption by moving the mouse pointer over the BitLocker Drive Encryption icon in the notification area, at the far right of the taskbar, near the clock. 6. When encryption is complete, you may be prompted to restart your computer again to finalize the process. Backup Considerations The encryption provided by BitLocker is transparent to applications on the running operating system, and existing backup schemes should not require technical accommodations to be effective, provided the backup is server-based. Backing up a BitLocker protected system to unencrypted removable media, such as a USB drive, is strongly discouraged as it leaves the data mobile while simultaneously removing any benefit of protection provided by the encryption. Data Recovery Microsoft provides a number of data recovery methods. Their availability depends on the deployment scheme chosen. In the basic one-to-one scheme, where BitLocker is configured on each individual system, these recovery mechanisms are either a binary key or a long numeric passphrase.
BitLocker to Go: Encryption for personal USB
 BitLocker to Go: Encryption for personal USB [Windows 10] Encryption is an effective method of protecting data stored on portable USB devices such as flash drives and external hard drives. Encryption encodes
BitLocker to Go: Encryption for personal USB [Windows 10] Encryption is an effective method of protecting data stored on portable USB devices such as flash drives and external hard drives. Encryption encodes
BitLocker Encryption for non-tpm laptops
 BitLocker Encryption for non-tpm laptops Contents 1.0 Introduction... 2 2.0 What is a TPM?... 2 3.0 Users of non-tpm University laptops... 2 3.1 Existing Windows 7 laptop users... 2 3.2 Existing Windows
BitLocker Encryption for non-tpm laptops Contents 1.0 Introduction... 2 2.0 What is a TPM?... 2 3.0 Users of non-tpm University laptops... 2 3.1 Existing Windows 7 laptop users... 2 3.2 Existing Windows
Protecting your data with Windows 10 BitLocker
 Microsoft IT Showcase Protecting your data with Windows 10 BitLocker Microsoft BitLocker Drive Encryption technology uses the strongest publicly available encryption to protect your computer s data. It
Microsoft IT Showcase Protecting your data with Windows 10 BitLocker Microsoft BitLocker Drive Encryption technology uses the strongest publicly available encryption to protect your computer s data. It
Expert Reference Series of White Papers. BitLocker: Is It Really Secure? COURSES.
 Expert Reference Series of White Papers BitLocker: Is It Really Secure? 1-800-COURSES www.globalknowledge.com BitLocker: Is It Really Secure? Mark Mizrahi, Global Knowledge Instructor, MCSE, MCT, CEH Introduction:
Expert Reference Series of White Papers BitLocker: Is It Really Secure? 1-800-COURSES www.globalknowledge.com BitLocker: Is It Really Secure? Mark Mizrahi, Global Knowledge Instructor, MCSE, MCT, CEH Introduction:
Sophos Central Device Encryption. Administrator Guide
 Sophos Central Device Encryption Administrator Guide Contents About... 1 Manage BitLocker Drive Encryption... 2 Migrate to...2 Prepare Device Encryption...3 Device Encryption step by step... 3 Device Encryption
Sophos Central Device Encryption Administrator Guide Contents About... 1 Manage BitLocker Drive Encryption... 2 Migrate to...2 Prepare Device Encryption...3 Device Encryption step by step... 3 Device Encryption
Best practices for mobile device encryption and security
 Best practices for mobile device encryption and security Introduction College sensitive information stored on a mobile computing device is at risk for unauthorized access and disclosure if appropriate
Best practices for mobile device encryption and security Introduction College sensitive information stored on a mobile computing device is at risk for unauthorized access and disclosure if appropriate
WINDOWS 7 BITLOCKER DRIVE ENCRYPTION
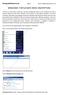 ComputerFixed.co.uk Page: 1 Email: info@computerfixed.co.uk WINDOWS 7 BITLOCKER DRIVE ENCRYPTION There are so many ways in which you can stop unauthorized access to your computer but what if someone steals
ComputerFixed.co.uk Page: 1 Email: info@computerfixed.co.uk WINDOWS 7 BITLOCKER DRIVE ENCRYPTION There are so many ways in which you can stop unauthorized access to your computer but what if someone steals
SafeGuard Enterprise. user help. Product Version: 8.1
 SafeGuard Enterprise user help Product Version: 8.1 Contents About SafeGuard Enterprise...1 Modules... 2 Full disk encryption with BitLocker...2 Full disk encryption with SafeGuard Power-on Authentication...
SafeGuard Enterprise user help Product Version: 8.1 Contents About SafeGuard Enterprise...1 Modules... 2 Full disk encryption with BitLocker...2 Full disk encryption with SafeGuard Power-on Authentication...
SafeGuard Enterprise user help. Product version: 8.0
 SafeGuard Enterprise user help Product version: 8.0 Contents 1 About SafeGuard Enterprise...4 2 SafeGuard Enterprise modules...5 3 Security recommendations...7 4 Full disk encryption...9 4.1 Encryption
SafeGuard Enterprise user help Product version: 8.0 Contents 1 About SafeGuard Enterprise...4 2 SafeGuard Enterprise modules...5 3 Security recommendations...7 4 Full disk encryption...9 4.1 Encryption
UNIVERSITY OF EXETER BITLOCKER USER GUIDE
 Exeter IT Technical Planning & Development UNIVERSITY OF EXETER BITLOCKER USER GUIDE BitLocker is an encryption system which allows the University to secure sensitive information on University owned laptops,
Exeter IT Technical Planning & Development UNIVERSITY OF EXETER BITLOCKER USER GUIDE BitLocker is an encryption system which allows the University to secure sensitive information on University owned laptops,
Once a USB drive has been inserted into an encrypted machine, the Dell Data Protection software will recognize the unencrypted device.
 Dell Data Protection USB Drive Encryption Introduction To further protect PC s that have access to sensitive data, the Dell Data Protection (DDP) client detects and encrypts USB/Flash drives when they
Dell Data Protection USB Drive Encryption Introduction To further protect PC s that have access to sensitive data, the Dell Data Protection (DDP) client detects and encrypts USB/Flash drives when they
TPM 1.2 Firmware Update Guidance. for Infineon SLB9655 and SLB9660
 TPM 1.2 Firmware Update Guidance for Infineon SLB9655 and SLB9660 Rev. 05 Toshiba Client Solutions Co., Ltd. Document Number: 3600xxxxx 1. Introduction This guidance described about in-field firmware update
TPM 1.2 Firmware Update Guidance for Infineon SLB9655 and SLB9660 Rev. 05 Toshiba Client Solutions Co., Ltd. Document Number: 3600xxxxx 1. Introduction This guidance described about in-field firmware update
Symantec Encryption (PGP) Installation Guide
 System Requirements Symantec Encryption (PGP) Installation Guide Windows 8 (32 and 64 bit versions) Windows 7 (32 and 64 bit versions)] Windows Vista (32- and 64-bit editions) Additional Requirements Boot
System Requirements Symantec Encryption (PGP) Installation Guide Windows 8 (32 and 64 bit versions) Windows 7 (32 and 64 bit versions)] Windows Vista (32- and 64-bit editions) Additional Requirements Boot
BitLocker Drive Encryption Guide
 BitLocker Drive Encryption Guide How to create a virtual hard drive and encrypt it with BitLocker... 2 How to Mount and Open your VHD after you restart your Computer... 11 Encrypting removable drives (Flash
BitLocker Drive Encryption Guide How to create a virtual hard drive and encrypt it with BitLocker... 2 How to Mount and Open your VHD after you restart your Computer... 11 Encrypting removable drives (Flash
Registering an ipad for Duo Two-Factor Authentication
 University Information Technology Services Technology Outreach Registering an ipad for Duo Two-Factor Authentication Duo is a two-factor authentication solution for campus community members. Using Duo,
University Information Technology Services Technology Outreach Registering an ipad for Duo Two-Factor Authentication Duo is a two-factor authentication solution for campus community members. Using Duo,
Registering an Android Tablet for Duo Two-Factor Authentication
 University Information Technology Services Technology Outreach Registering an Android Tablet for Duo Two-Factor Authentication Duo is a two-factor authentication solution for campus community members.
University Information Technology Services Technology Outreach Registering an Android Tablet for Duo Two-Factor Authentication Duo is a two-factor authentication solution for campus community members.
MU2b Authentication, Authorization and Accounting Questions Set 2
 MU2b Authentication, Authorization and Accounting Questions Set 2 1. You enable the audit of successful and failed policy changes. Where can you view entries related to policy change attempts? Lesson 2
MU2b Authentication, Authorization and Accounting Questions Set 2 1. You enable the audit of successful and failed policy changes. Where can you view entries related to policy change attempts? Lesson 2
Information protection BitLocker Overview of BitLocker Device Encryption in Windows 10 BitLocker frequently asked questions (FAQ) Prepare your
 Table of Contents Information protection BitLocker Overview of BitLocker Device Encryption in Windows 10 BitLocker frequently asked questions (FAQ) Prepare your organization for BitLocker: Planning and
Table of Contents Information protection BitLocker Overview of BitLocker Device Encryption in Windows 10 BitLocker frequently asked questions (FAQ) Prepare your organization for BitLocker: Planning and
Fix Three Common Accounting Firm Data Vulnerabilities
 Fix Three Common Accounting Firm Data Vulnerabilities Fix Three Common Accounting Firm Data Vulnerabilities Use these step-by-step guides to protect your business from data thieves Brought to you by: Encyro
Fix Three Common Accounting Firm Data Vulnerabilities Fix Three Common Accounting Firm Data Vulnerabilities Use these step-by-step guides to protect your business from data thieves Brought to you by: Encyro
BitLocker Group Policy Settings
 BitLocker Group Policy Settings Updated: September 13, 2013 Applies To: Windows 8, Windows 8.1, Windows Server 2012, Windows Server 2012 R2 This reference topic for the IT professional describes the function,
BitLocker Group Policy Settings Updated: September 13, 2013 Applies To: Windows 8, Windows 8.1, Windows Server 2012, Windows Server 2012 R2 This reference topic for the IT professional describes the function,
Veeam Endpoint Backup
 Veeam Endpoint Backup Version 1.5 User Guide March, 2016 2016 Veeam Software. All rights reserved. All trademarks are the property of their respective owners. No part of this publication may be reproduced,
Veeam Endpoint Backup Version 1.5 User Guide March, 2016 2016 Veeam Software. All rights reserved. All trademarks are the property of their respective owners. No part of this publication may be reproduced,
Why Implement Endpoint Encryption?
 Why Implement Endpoint Encryption? James Christiansen October 21,2013 Table of Contents Part I Why Implement Endpoint Encryption?... 2 Introduction... 2 Series Key Points... 2 Why Implement Endpoint Encryption?...
Why Implement Endpoint Encryption? James Christiansen October 21,2013 Table of Contents Part I Why Implement Endpoint Encryption?... 2 Introduction... 2 Series Key Points... 2 Why Implement Endpoint Encryption?...
The Future of Windows
 The Future of Windows What s New: Taskbar The quick launch area is gone Application icons can be docked You can drag-and-drop application icons to this area but running apps will appear here as well. Functions
The Future of Windows What s New: Taskbar The quick launch area is gone Application icons can be docked You can drag-and-drop application icons to this area but running apps will appear here as well. Functions
Table of Contents. Table of Figures. 2 Wave Systems Corp. Client User Guide
 2 Wave Systems Corp. Client User Guide Table of Contents Overview... 3 What is the Trusted Drive Manager?... 3 Key Features of Trusted Drive Manager... 3 Getting Started... 4 Required Components... 4 Configure
2 Wave Systems Corp. Client User Guide Table of Contents Overview... 3 What is the Trusted Drive Manager?... 3 Key Features of Trusted Drive Manager... 3 Getting Started... 4 Required Components... 4 Configure
Connecting to the eduroam Wireless Network. 1. If you are using a PC, move the. 2. Next Click or Tap the Settings. Help Sheet Windows 8.
 Connecting to the eduroam Wireless Network Help Sheet Windows 8 October 2013 This Help Sheet assists Windows 8 users to access the eduroam Wireless Network. 1. If you are using a PC, move the mouse to
Connecting to the eduroam Wireless Network Help Sheet Windows 8 October 2013 This Help Sheet assists Windows 8 users to access the eduroam Wireless Network. 1. If you are using a PC, move the mouse to
2-Step Verification. Summer 2018, Version 3. Table of Contents
 2-Step Verification Summer 2018, Version 3 Table of Contents Introduction... 2 Enrolling in 2-Step Verification... 2 Registering Your Device... 2 Mobile Phone... 3 Tablet... 6 Landline... 8 Hardware Token...
2-Step Verification Summer 2018, Version 3 Table of Contents Introduction... 2 Enrolling in 2-Step Verification... 2 Registering Your Device... 2 Mobile Phone... 3 Tablet... 6 Landline... 8 Hardware Token...
Using SimplySecure to Deploy, Enforce & Manage BitLocker
 Whitepaper Using SimplySecure to Deploy, Enforce & Manage BitLocker Organizational management plus access control managed through the cloud Rob Weber February 2019 What is BitLocker? Microsoft s BitLocker
Whitepaper Using SimplySecure to Deploy, Enforce & Manage BitLocker Organizational management plus access control managed through the cloud Rob Weber February 2019 What is BitLocker? Microsoft s BitLocker
File Encryption. Steven M. Bellovin https://www.cs.columbia.edu/~smb
 File Encryption Steven M. Bellovin https://www.cs.columbia.edu/~smb Why Encrypt Files? Theft of files Theft of media Theft of computer Cloud storage? I.e. Someone else s computer 1 Issues with File Encryption
File Encryption Steven M. Bellovin https://www.cs.columbia.edu/~smb Why Encrypt Files? Theft of files Theft of media Theft of computer Cloud storage? I.e. Someone else s computer 1 Issues with File Encryption
Full Disk Encryption. Larry Carson, Associate Director, Information Security Management
 Full Disk Encryption Larry Carson, Associate Director, Information Security Management What Security Really Looks Like at UBC News-worthy Security Incidents VGH Loss of 450 medical records via Resident
Full Disk Encryption Larry Carson, Associate Director, Information Security Management What Security Really Looks Like at UBC News-worthy Security Incidents VGH Loss of 450 medical records via Resident
Windows 10 USB Driver Installation Procedure
 Windows 10 USB Driver Signing and certification requirements for device drivers being installed on the computer require selecting a mode that will bypass the signing requirement. The USB driver used by
Windows 10 USB Driver Signing and certification requirements for device drivers being installed on the computer require selecting a mode that will bypass the signing requirement. The USB driver used by
Dell EM+S Intune. Android Enrollment Guide. Version 1.5
 Dell EM+S Intune Android Enrollment Guide Version 1.5 Copyright 2017 Dell Inc. All rights reserved. This publication contains information that is confidential and proprietary to Dell and is subject to
Dell EM+S Intune Android Enrollment Guide Version 1.5 Copyright 2017 Dell Inc. All rights reserved. This publication contains information that is confidential and proprietary to Dell and is subject to
Microsoft Windows Updates for the Surface tablet should be checked on a regular basis. As a best practice the Surface tablet: Should be connected to
 1 Microsoft Windows Updates for the Surface tablet should be checked on a regular basis. As a best practice the Surface tablet: Should be connected to a power outlet. (The tablet may install updates via
1 Microsoft Windows Updates for the Surface tablet should be checked on a regular basis. As a best practice the Surface tablet: Should be connected to a power outlet. (The tablet may install updates via
CESecure Quick Start Guide
 CESecure Quick Start Guide Using CESecure Software CESecure software is pre-installed on CMS Products Flash or Hard Drives and does not require installation. The CESecure software moves with the encryption
CESecure Quick Start Guide Using CESecure Software CESecure software is pre-installed on CMS Products Flash or Hard Drives and does not require installation. The CESecure software moves with the encryption
Registering an iphone for Duo Two-Factor Authentication
 University Information Technology Services Technology Outreach Registering an iphone for Duo Two-Factor Authentication Duo is a two-factor authentication solution for campus community members. Using Duo,
University Information Technology Services Technology Outreach Registering an iphone for Duo Two-Factor Authentication Duo is a two-factor authentication solution for campus community members. Using Duo,
Unit III: Working with Windows and Applications. Chapters 5, 7, & 8
 Unit III: Working with Windows and Applications Chapters 5, 7, & 8 Learning Objectives In this unit, you will: Launch programs and navigate the Windows task bar. Perform common windows functions. Customize
Unit III: Working with Windows and Applications Chapters 5, 7, & 8 Learning Objectives In this unit, you will: Launch programs and navigate the Windows task bar. Perform common windows functions. Customize
Casper Remote User Guide
 Casper Remote User Guide 2 REV 1.2 Table of Contents: Introduction..3 Quick Start Guide...4 Google Authenticator.9 Remote Access Settings.13 Troubleshooting 19 3 REV 1.2 Introduction: Casper Remote Control
Casper Remote User Guide 2 REV 1.2 Table of Contents: Introduction..3 Quick Start Guide...4 Google Authenticator.9 Remote Access Settings.13 Troubleshooting 19 3 REV 1.2 Introduction: Casper Remote Control
ModeChanger
 35020808-02 2015.11 ModeChanger ModeChanger is a software utility that can switch the drive between normal mode and encrypted mode. Operating in encrypted mode will help protect your data. While the drive
35020808-02 2015.11 ModeChanger ModeChanger is a software utility that can switch the drive between normal mode and encrypted mode. Operating in encrypted mode will help protect your data. While the drive
CloudLink SecureVM 3.1 for Microsoft Azure Deployment Guide
 CloudLink SecureVM 3.1 for Microsoft Azure Deployment Guide October 2014 THIS DOCUMENT CONTAINS CONFIDENTIAL AND TRADE SECRET INFORMATION OF CLOUDLINK TECHNOLOGIES AND RECEIPT OR POSSESSION DOES NOT CONVEY
CloudLink SecureVM 3.1 for Microsoft Azure Deployment Guide October 2014 THIS DOCUMENT CONTAINS CONFIDENTIAL AND TRADE SECRET INFORMATION OF CLOUDLINK TECHNOLOGIES AND RECEIPT OR POSSESSION DOES NOT CONVEY
Maxwell RSC Tablet PC Configuration Manual for use with Windows 8 Operating System
 Maxwell RSC Tablet PC Configuration Manual for use with Windows 8 Operating System TM537 1/18 Table of Contents 1 Maxwell RSC Instrument and Tablet PC...1 2 Glossary...3 3 Adjusting Volume Settings...5
Maxwell RSC Tablet PC Configuration Manual for use with Windows 8 Operating System TM537 1/18 Table of Contents 1 Maxwell RSC Instrument and Tablet PC...1 2 Glossary...3 3 Adjusting Volume Settings...5
Windows 10 and the Enterprise. Craig A. Brown Prepared for: GMIS
 Windows 10 and the Enterprise Craig A. Brown Prepared for: GMIS 11-2-2015 Introduction Craig A. Brown Microsoft Practice Leader Global Knowledge MCT, Since 1996 MCSA / MCSE / NT / 2000 / 2003 MCDST MCITP:
Windows 10 and the Enterprise Craig A. Brown Prepared for: GMIS 11-2-2015 Introduction Craig A. Brown Microsoft Practice Leader Global Knowledge MCT, Since 1996 MCSA / MCSE / NT / 2000 / 2003 MCDST MCITP:
NORTH AMERICAN SECURITIES ADMINISTRATORS ASSOCIATION Cybersecurity Checklist for Investment Advisers
 Identify Protect Detect Respond Recover Identify: Risk Assessments & Management 1. Risk assessments are conducted frequently (e.g. annually, quarterly). 2. Cybersecurity is included in the risk assessment.
Identify Protect Detect Respond Recover Identify: Risk Assessments & Management 1. Risk assessments are conducted frequently (e.g. annually, quarterly). 2. Cybersecurity is included in the risk assessment.
Fiery proserver User Guide
 Fiery proserver User Guide Congratulations on your purchase of the EFI Fiery proserver, a powerful production solution for your printer. Before you begin Make sure that you have: About this document Installed
Fiery proserver User Guide Congratulations on your purchase of the EFI Fiery proserver, a powerful production solution for your printer. Before you begin Make sure that you have: About this document Installed
Fujitsu STYLISTIC Q Series
 Fujitsu STYLISTIC Q Series BIOS Guide STYLISTIC Q Series Model: Q552 Document Date: 5252012 Document Part Number: FPC58-3061-01 FUJITSU AMERICA, INC. 1 STYLISTIC Q552 BIOS Q Series BIOS BIOS SETUP UTILITY
Fujitsu STYLISTIC Q Series BIOS Guide STYLISTIC Q Series Model: Q552 Document Date: 5252012 Document Part Number: FPC58-3061-01 FUJITSU AMERICA, INC. 1 STYLISTIC Q552 BIOS Q Series BIOS BIOS SETUP UTILITY
SIMATIC. Industrial PC Microsoft Windows Embedded Standard 7. Safety instructions 1. Initial startup: Commissioning the operating.
 Safety instructions 1 Initial startup: Commissioning the operating 2 system SIMATIC Industrial PC Microsoft Windows Embedded Standard 7 Restoring the factory settings of the operating system and 3 partitions
Safety instructions 1 Initial startup: Commissioning the operating 2 system SIMATIC Industrial PC Microsoft Windows Embedded Standard 7 Restoring the factory settings of the operating system and 3 partitions
Symantec Encryption Desktop
 RSA Ready Implementation Guide for RSA SecurID Last Modified: December 12, 2014 Partner Information Product Information Partner Name Web Site Product Name Version & Platform Product Description Symantec
RSA Ready Implementation Guide for RSA SecurID Last Modified: December 12, 2014 Partner Information Product Information Partner Name Web Site Product Name Version & Platform Product Description Symantec
ThinkVantage Fingerprint Software
 ThinkVantage Fingerprint Software 12 2 1First Edition (February 2006) Copyright Lenovo 2006. Portions Copyright International Business Machines Corporation 2006. All rights reserved. U.S. GOVERNMENT
ThinkVantage Fingerprint Software 12 2 1First Edition (February 2006) Copyright Lenovo 2006. Portions Copyright International Business Machines Corporation 2006. All rights reserved. U.S. GOVERNMENT
BitLocker White Paper Windows 10
 BitLocker White Paper Windows 10 This white paper gives detailed instructions how to enable BitLocker on a measurement device. BitLocker White Paper Windows 10 7.2018 1178.8859.02-01 Table of Contents
BitLocker White Paper Windows 10 This white paper gives detailed instructions how to enable BitLocker on a measurement device. BitLocker White Paper Windows 10 7.2018 1178.8859.02-01 Table of Contents
Fiery proserver User Guide
 Fiery proserver User Guide Congratulations on your purchase of the Fiery proserver, a powerful production solution for your printer. Before you begin Make sure that you have: About this document Installed
Fiery proserver User Guide Congratulations on your purchase of the Fiery proserver, a powerful production solution for your printer. Before you begin Make sure that you have: About this document Installed
Tactics, Techniques and Procedures (TTP): BitLocker End-User Guide
 Tactics, Techniques and Procedures (TTP): BitLocker End-User Guide VERSION 1.0.6 April 2015 FOR US Army Reserve Command (USARC) DISTRIBUTION IS LIMITED TO U.S. GOVERNMENT AGENCIES AND THEIR CONTRACTORS.
Tactics, Techniques and Procedures (TTP): BitLocker End-User Guide VERSION 1.0.6 April 2015 FOR US Army Reserve Command (USARC) DISTRIBUTION IS LIMITED TO U.S. GOVERNMENT AGENCIES AND THEIR CONTRACTORS.
Veeam Endpoint Backup
 Veeam Endpoint Backup Version 1.1 User Guide December, 2015 2015 Veeam Software. All rights reserved. All trademarks are the property of their respective owners. No part of this publication may be reproduced,
Veeam Endpoint Backup Version 1.1 User Guide December, 2015 2015 Veeam Software. All rights reserved. All trademarks are the property of their respective owners. No part of this publication may be reproduced,
Firmware Update Guide
 Firmware Update Guide April 2018 www.lexmark.com Contents 2 Contents Change history... 3 Overview... 4 Updating the firmware... 5 Updating the firmware using Virtual Solution Center... 5 Updating the firmware
Firmware Update Guide April 2018 www.lexmark.com Contents 2 Contents Change history... 3 Overview... 4 Updating the firmware... 5 Updating the firmware using Virtual Solution Center... 5 Updating the firmware
CloudLink SecureVM 3.1 for Microsoft Azure Deployment Guide
 CloudLink SecureVM 3.1 for Microsoft Azure Deployment Guide November 2014 THIS DOCUMENT CONTAINS CONFIDENTIAL AND TRADE SECRET INFORMATION OF CLOUDLINK TECHNOLOGIES AND RECEIPT OR POSSESSION DOES NOT CONVEY
CloudLink SecureVM 3.1 for Microsoft Azure Deployment Guide November 2014 THIS DOCUMENT CONTAINS CONFIDENTIAL AND TRADE SECRET INFORMATION OF CLOUDLINK TECHNOLOGIES AND RECEIPT OR POSSESSION DOES NOT CONVEY
Wireless for Windows 7
 Wireless for Windows 7 The new CWSL wireless network consists of three different wireless networks CWSL Faculty-Staff - This network is for faculty and staff only. (uses WPA2-Enterprise encryption) CWSL
Wireless for Windows 7 The new CWSL wireless network consists of three different wireless networks CWSL Faculty-Staff - This network is for faculty and staff only. (uses WPA2-Enterprise encryption) CWSL
CASPER SECURE SERVER EDITION 3.0 USER GUIDE
 TM CASPER SECURE TM SERVER EDITION 3.0 USER GUIDE Copyright and Trademark Information Information in this document is subject to change without notice. Federal law prohibits unauthorized use, duplication,
TM CASPER SECURE TM SERVER EDITION 3.0 USER GUIDE Copyright and Trademark Information Information in this document is subject to change without notice. Federal law prohibits unauthorized use, duplication,
Encrypting external USB drive on Linux
 Encrypting external USB drive on Linux To prevent your important or personal information from falling into the wrong hands, you can easily encrypt the files on your USB-drive with a password. Windows,
Encrypting external USB drive on Linux To prevent your important or personal information from falling into the wrong hands, you can easily encrypt the files on your USB-drive with a password. Windows,
Backup, File Backup copies of individual files made in order to replace the original file(s) in case it is damaged or lost.
 Glossary A Active Directory a directory service that inventories, secures and manages the users, computers, rules and other components of a Microsoft Windows network. This service is typically deployed
Glossary A Active Directory a directory service that inventories, secures and manages the users, computers, rules and other components of a Microsoft Windows network. This service is typically deployed
Magic Card Professional
 Magic Card Professional User Manual Table of Contents System Requirements... 2 1. Installation... 3 2. Magic Card Settings... 5 2.1 Set Protection... 6 2.2 Set Parameters... 8 2.3 Password... 10 2.4 CMOS
Magic Card Professional User Manual Table of Contents System Requirements... 2 1. Installation... 3 2. Magic Card Settings... 5 2.1 Set Protection... 6 2.2 Set Parameters... 8 2.3 Password... 10 2.4 CMOS
Basic Computer Operations
 Basic Computer Operations Goals By learning terms associated with computers and some basic operations, you'll be ready to make best use of a computer. Contents Computer terms Starting up and shutting down
Basic Computer Operations Goals By learning terms associated with computers and some basic operations, you'll be ready to make best use of a computer. Contents Computer terms Starting up and shutting down
Using the System Utilities
 1418837261_ch03_Final.qxd 28/3/07 17:13 Page 89 3 chapter Using the System Utilities After reading this chapter and completing the exercises, you will be able to: Understand and use the Control Panel applets
1418837261_ch03_Final.qxd 28/3/07 17:13 Page 89 3 chapter Using the System Utilities After reading this chapter and completing the exercises, you will be able to: Understand and use the Control Panel applets
PGP WDE Installation Guide
 PGP WDE Installation Guide EMAIL Enrollment Version 1 June 2012 2012 Xerox Corporation. All rights reserved. XEROX and XEROX and Design are trademarks of the Xerox Corporation in the United States and/or
PGP WDE Installation Guide EMAIL Enrollment Version 1 June 2012 2012 Xerox Corporation. All rights reserved. XEROX and XEROX and Design are trademarks of the Xerox Corporation in the United States and/or
Have a Backup. Trainer Resource. This document is a reference and preparation sheet for the trainer, and a companion to the lesson plan.
 This document is a reference and preparation sheet for the trainer, and a companion to the lesson plan. The Learning Objectives summarize the knowledge that learners should have gained by the time they
This document is a reference and preparation sheet for the trainer, and a companion to the lesson plan. The Learning Objectives summarize the knowledge that learners should have gained by the time they
Configuring File Server Resource Manager (FSRM)
 Configuring File Server Resource Manager (FSRM) LESSON 5 70-411 EXAM OBJECTIVE Objective 2.2 Configure File Server Resource Manager (FSRM). This objective may include but is not limited to: install the
Configuring File Server Resource Manager (FSRM) LESSON 5 70-411 EXAM OBJECTIVE Objective 2.2 Configure File Server Resource Manager (FSRM). This objective may include but is not limited to: install the
How can I Clear a TPM module or Recover from Authorisation Lockout?
 How can I Clear a TPM module or Recover from Authorisation Lockout? Scenario TPM Modules can become locked when too many incorrect PIN attempts are made to access the information stored on the module.
How can I Clear a TPM module or Recover from Authorisation Lockout? Scenario TPM Modules can become locked when too many incorrect PIN attempts are made to access the information stored on the module.
PASS4TEST 専門 IT 認証試験問題集提供者
 PASS4TEST 専門 IT 認証試験問題集提供者 http://www.pass4test.jp 1 年で無料進級することに提供する Exam : 70-697 Title : Configuring Windows Devices Vendor : Microsoft Version : DEMO Get Latest & Valid 70-697 Exam's Question and Answers
PASS4TEST 専門 IT 認証試験問題集提供者 http://www.pass4test.jp 1 年で無料進級することに提供する Exam : 70-697 Title : Configuring Windows Devices Vendor : Microsoft Version : DEMO Get Latest & Valid 70-697 Exam's Question and Answers
APP-J: WHAT IS APPLICATION JUKEBOX?
 APP-J: WHAT IS APPLICATION JUKEBOX? Use Application Jukebox (App-J) to run University software on any Windows PC or laptop. Launch apps from the Application Jukebox web page Install the Application Jukebox
APP-J: WHAT IS APPLICATION JUKEBOX? Use Application Jukebox (App-J) to run University software on any Windows PC or laptop. Launch apps from the Application Jukebox web page Install the Application Jukebox
Welcome Guide for MP-1 Token for Microsoft Windows
 Welcome Guide for MP-1 Token for Microsoft Windows Protecting Your On-line Identity Authentication Service Delivery Made EASY Copyright 2013 SafeNet, Inc. All rights reserved. All attempts have been made
Welcome Guide for MP-1 Token for Microsoft Windows Protecting Your On-line Identity Authentication Service Delivery Made EASY Copyright 2013 SafeNet, Inc. All rights reserved. All attempts have been made
NEOMED OPERATIONAL POLICY
 (A) PURPOSE Mobile computers allow NEOUCOM faculty and staff to have computing resources at hand in meetings/classes, enable those who travel on University business to be maximally functional and productive
(A) PURPOSE Mobile computers allow NEOUCOM faculty and staff to have computing resources at hand in meetings/classes, enable those who travel on University business to be maximally functional and productive
Introduction: Broadcom BCM943142HM Wireless Communication Device User's Guide
 Introduction: Broadcom BCM943142HM Wireless Communication Device User's Guide Before you begin Things you should know BCM943142HM network Before you begin Obtain the following information from your network
Introduction: Broadcom BCM943142HM Wireless Communication Device User's Guide Before you begin Things you should know BCM943142HM network Before you begin Obtain the following information from your network
Contents. Getting Started...1. Managing Your Drives...9. Backing Up & Restoring Folders Synchronizing Folders...52
 Contents Getting Started.....................................................1 Installing the Software...........................................1 Using the Maxtor System Tray Icon................................6
Contents Getting Started.....................................................1 Installing the Software...........................................1 Using the Maxtor System Tray Icon................................6
RU-VPN2 - GlobalProtect Installation for Windows
 RU-VPN2 - GlobalProtect Installation for Windows Use RU-VPN2 for a secure connection to Ryerson's Administrative system via the Internet. To use RU-VPN2, you will need to install and use client software
RU-VPN2 - GlobalProtect Installation for Windows Use RU-VPN2 for a secure connection to Ryerson's Administrative system via the Internet. To use RU-VPN2, you will need to install and use client software
Infinova SS200T3R Embedded VMS Box
 Infinova SS200T3R Embedded VMS Box WARNING Embedded VMS advanced maintenance is special activity and it is highly recommended that only trained engineers operate the maintenance procedures. Incorrect configuration
Infinova SS200T3R Embedded VMS Box WARNING Embedded VMS advanced maintenance is special activity and it is highly recommended that only trained engineers operate the maintenance procedures. Incorrect configuration
Finding information on your computer
 Important Be sure to create recovery discs immediately after your computer is ready for use because there are no recovery discs provided with the computer. For instructions on how to create the recovery
Important Be sure to create recovery discs immediately after your computer is ready for use because there are no recovery discs provided with the computer. For instructions on how to create the recovery
CASPER SECURE DRIVE BACKUP
 TM CASPER SECURE DRIVE BACKUP FOR PGP WHOLE DISK ENCRYPTION USER GUIDE V3.0 TM Copyright and Trademark Information Information in this document is subject to change without notice. Federal law prohibits
TM CASPER SECURE DRIVE BACKUP FOR PGP WHOLE DISK ENCRYPTION USER GUIDE V3.0 TM Copyright and Trademark Information Information in this document is subject to change without notice. Federal law prohibits
Symantec Endpoint Encryption Full Disk for Mac OS X
 Symantec Endpoint Encryption Full Disk for Mac OS X User's Guide 8.2.1 The software described in this book is furnished under a license agreement and may be used only in accordance with the terms of the
Symantec Endpoint Encryption Full Disk for Mac OS X User's Guide 8.2.1 The software described in this book is furnished under a license agreement and may be used only in accordance with the terms of the
Encrypting Removable Media
 For security reasons all removable media must be encrypted with BitLocker to Go on Windows 7 workstations. The following will show you how to use a flash drive with BitLocker to Go. Please note that data
For security reasons all removable media must be encrypted with BitLocker to Go on Windows 7 workstations. The following will show you how to use a flash drive with BitLocker to Go. Please note that data
WINDOWS 8.1 RESTORE PROCEDURE
 Support website: MyDigitalTech Support email: hello@mydigitaltech.com Support phone number: 0845 450 6323 WINDOWS 8.1 RESTORE PROCEDURE This document describes how Windows system recovery works, in the
Support website: MyDigitalTech Support email: hello@mydigitaltech.com Support phone number: 0845 450 6323 WINDOWS 8.1 RESTORE PROCEDURE This document describes how Windows system recovery works, in the
Windows 10 Tips and Tricks
 Windows 10 Tips and Tricks You've made the move to Windows 10. The Start Menu has returned and its cloud integration is obvious, but most everything else is unfamiliar. This session will help you setup
Windows 10 Tips and Tricks You've made the move to Windows 10. The Start Menu has returned and its cloud integration is obvious, but most everything else is unfamiliar. This session will help you setup
IRONKEY WORKSPACE PROVISIONING TOOL 1.3. User Guide
 IRONKEY WORKSPACE PROVISIONING TOOL 1.3 User Guide Copyright 2014 Imation Corp. Imation and Imation logo, IronKey and IronKey logo are trademarks of Imation Corp. All other trademarks are the property
IRONKEY WORKSPACE PROVISIONING TOOL 1.3 User Guide Copyright 2014 Imation Corp. Imation and Imation logo, IronKey and IronKey logo are trademarks of Imation Corp. All other trademarks are the property
Lesson 10 Data and Hardware Protection
 Data and Hardware Protection Computer Literacy BASICS: A Comprehensive Guide to IC 3, 5 th Edition 1 Objectives Understand types of backups. Select a backup method. Determine a schedule for backing up
Data and Hardware Protection Computer Literacy BASICS: A Comprehensive Guide to IC 3, 5 th Edition 1 Objectives Understand types of backups. Select a backup method. Determine a schedule for backing up
VMware Horizon Client Install for non-uh Devices (VDI)
 Be the Difference. VMware Horizon Client Install for non-uh Devices (VDI) This document assumes that all VMware Horizon (VDI) installations on non-uh devices are occurring outside the UH firewall. Utilizing
Be the Difference. VMware Horizon Client Install for non-uh Devices (VDI) This document assumes that all VMware Horizon (VDI) installations on non-uh devices are occurring outside the UH firewall. Utilizing
VMware Horizon Client Installation Guide (Windows)
 VMware Horizon Client Installation Guide (Windows) (Please note: The steps in this document must be followed exactly as shown in order to ensure a proper installation.) Requirements: You must have an existing
VMware Horizon Client Installation Guide (Windows) (Please note: The steps in this document must be followed exactly as shown in order to ensure a proper installation.) Requirements: You must have an existing
SEC-GDL-009-W7 Encrypting Personal Computers (Windows 7)
 Technology & Information Services SEC-GDL-009-W7 Encrypting Personal Computers (Windows 7) Author: Paul Ferrier Date: 14/10/2016 Document Security Level: PUBLIC Document Version: 1.0 Document Ref: SEC-GDL-009-W7
Technology & Information Services SEC-GDL-009-W7 Encrypting Personal Computers (Windows 7) Author: Paul Ferrier Date: 14/10/2016 Document Security Level: PUBLIC Document Version: 1.0 Document Ref: SEC-GDL-009-W7
Table of Contents. A. Introduction...2. B. General Description...2. C. Features...3. D. Before Using the Security Application Program LOCK...
 v1.00 Table of Contents A. Introduction...2 B. General Description...2 C. Features...3 D. Before Using the Security Application Program LOCK...4 E. Introduction to the Security Application Program LOCK...5
v1.00 Table of Contents A. Introduction...2 B. General Description...2 C. Features...3 D. Before Using the Security Application Program LOCK...4 E. Introduction to the Security Application Program LOCK...5
Introduction to Windows 10. Windsor Senior Computer Users Group October 12, 2015
 Introduction to Windows 10 Windsor Senior Computer Users Group October 12, 2015 Should you upgrade? Availability Windows 10 will be available as a free upgrade (until July 2016) for anyone with a valid
Introduction to Windows 10 Windsor Senior Computer Users Group October 12, 2015 Should you upgrade? Availability Windows 10 will be available as a free upgrade (until July 2016) for anyone with a valid
Table of Contents. Installation and Software 1
 Table of Contents Table of Contents Installation and Software Bitlocker not does not give the PIN Protection Facility Do I need the System Reserved Partition when I install Windows? I am Running NetIntelligence
Table of Contents Table of Contents Installation and Software Bitlocker not does not give the PIN Protection Facility Do I need the System Reserved Partition when I install Windows? I am Running NetIntelligence
Instrument Software Update Instructions. X-Series Multi-touch instruments
 Purpose Instrument Software Update Instructions X-Series Multi-touch instruments The purpose of this document is to outline the instrument software update procedure for the touchscreen or B model instrument
Purpose Instrument Software Update Instructions X-Series Multi-touch instruments The purpose of this document is to outline the instrument software update procedure for the touchscreen or B model instrument
SIMATIC. Industrial PC Microsoft Windows 7. Safety instructions 1. Initial startup: Commissioning the operating. system
 Safety instructions 1 Initial startup: Commissioning the operating 2 system SIMATIC Industrial PC Operating Instructions Restoring the factory settings of the operating system and 3 partitions (Restore)
Safety instructions 1 Initial startup: Commissioning the operating 2 system SIMATIC Industrial PC Operating Instructions Restoring the factory settings of the operating system and 3 partitions (Restore)
Chapter 14: Advanced Troubleshooting
 Chapter 14: Advanced Troubleshooting IT Essentials v6.0 ITE v6.0 1 Chapter 14 - Sections & Objectives 14.0 Introduction Review Troubleshooting Steps 14.1 Computer Components and Peripherals Troubleshoot
Chapter 14: Advanced Troubleshooting IT Essentials v6.0 ITE v6.0 1 Chapter 14 - Sections & Objectives 14.0 Introduction Review Troubleshooting Steps 14.1 Computer Components and Peripherals Troubleshoot
MDM Android Client x - User Guide 7P Mobile Device Management. Doc.Rel: 1.0/
 MDM Android Client 5.26.0x - User Guide 7P Mobile Device Management Doc.Rel: 1.0/ 2017-07-16 Table of Contents 1 Objectives and Target Groups... 9 1.1 Important information... 9 1.2 Third-Party Materials...
MDM Android Client 5.26.0x - User Guide 7P Mobile Device Management Doc.Rel: 1.0/ 2017-07-16 Table of Contents 1 Objectives and Target Groups... 9 1.1 Important information... 9 1.2 Third-Party Materials...
MyDataZone User s Manual
 MyDataZone User s Manual MyDataZone is a DataTraveler Secure tool that enables you to create and access a user defined password-protected area called a Privacy Zone, on your DataTraveler Secure drive.
MyDataZone User s Manual MyDataZone is a DataTraveler Secure tool that enables you to create and access a user defined password-protected area called a Privacy Zone, on your DataTraveler Secure drive.
SP LOCKER USER MANUAL. v1.0
 SP LOCKER USER MANUAL v1.0 Table of Contents 1 Introduction to the SP Locker Security Software... 2 2 Before You Get Started... 2 3 Features... 2 4 Public and Secured Partition... 3 5 How to use SP Locker...
SP LOCKER USER MANUAL v1.0 Table of Contents 1 Introduction to the SP Locker Security Software... 2 2 Before You Get Started... 2 3 Features... 2 4 Public and Secured Partition... 3 5 How to use SP Locker...
SecuRemote for Windows 32-bit/64-bit
 SecuRemote for Windows 32-bit/64-bit E75.20 User Guide 13 September 2011 2011 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by copyright
SecuRemote for Windows 32-bit/64-bit E75.20 User Guide 13 September 2011 2011 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by copyright
2 - Diving into the desktop. 2.1 Logging in
 2 - Diving into the desktop It s time for a quick tour of the Windows 10 desktop. The desktop has changed a little, but it should still be at least somewhat familiar to those of you who have used Windows
2 - Diving into the desktop It s time for a quick tour of the Windows 10 desktop. The desktop has changed a little, but it should still be at least somewhat familiar to those of you who have used Windows
Lenovo Imaging Checklist
 *Note: If this is a re-image, it s recommended getting into setup and clearing the Security Chip. PRE-INSTALLATION BIOS (When powering up, hit F1 at the Lenovo Logo screen) For all Lenovo Laptop models:
*Note: If this is a re-image, it s recommended getting into setup and clearing the Security Chip. PRE-INSTALLATION BIOS (When powering up, hit F1 at the Lenovo Logo screen) For all Lenovo Laptop models:
College of Pharmacy Windows 10
 College of Pharmacy Windows 10 Windows 10 is the version of Microsoft s flagship operating system that follows Windows 8; the OS was released in July 2015. Windows 10 is designed to address common criticisms
College of Pharmacy Windows 10 Windows 10 is the version of Microsoft s flagship operating system that follows Windows 8; the OS was released in July 2015. Windows 10 is designed to address common criticisms
BEAT 2.0 USER MANUAL
 BEAT 2.0 USER MANUAL FCC ID: 2ADLJBEAT20 The device complies with part 15 of the FCC Rules. Operation is subject to the following two conditions: (1) This device may not cause harmful interference, and
BEAT 2.0 USER MANUAL FCC ID: 2ADLJBEAT20 The device complies with part 15 of the FCC Rules. Operation is subject to the following two conditions: (1) This device may not cause harmful interference, and
Lesson 3: Identifying Key Characteristics of Workgroups and Domains
 1-16 Chapter 1 Introduction to Windows XP Professional Lesson 3: Identifying Key Characteristics of Workgroups and Domains Windows XP Professional supports two types of network environments in which users
1-16 Chapter 1 Introduction to Windows XP Professional Lesson 3: Identifying Key Characteristics of Workgroups and Domains Windows XP Professional supports two types of network environments in which users
SafeGuard Easy Demo guide. Product version: 6.1
 SafeGuard Easy Demo guide Product version: 6.1 Document date: February 2014 Contents 1 About this guide...3 2 Requirements...4 3 The demo configuration package...5 4 Install the demo software...6 5 What
SafeGuard Easy Demo guide Product version: 6.1 Document date: February 2014 Contents 1 About this guide...3 2 Requirements...4 3 The demo configuration package...5 4 Install the demo software...6 5 What
Installing and Configuring Windows 10
 Course 20698A: Installing and Configuring Windows 10 Course details Course Outline Module 1: Installing Windows 10 This module describes the features of Windows 10 and the process for installing and deploying
Course 20698A: Installing and Configuring Windows 10 Course details Course Outline Module 1: Installing Windows 10 This module describes the features of Windows 10 and the process for installing and deploying
Software Vulnerability Assessment & Secure Storage
 Software Vulnerability Assessment & Secure Storage 1 Software Vulnerability Assessment Vulnerability assessment is the process of identifying flaws that reside in an OS, application software or devices
Software Vulnerability Assessment & Secure Storage 1 Software Vulnerability Assessment Vulnerability assessment is the process of identifying flaws that reside in an OS, application software or devices
