Windows 10 Consumer Storybook v1.0_november update_partner-ready
|
|
|
- Cathleen Barrett
- 6 years ago
- Views:
Transcription
1
2 Windows 10 Consumer Storybook v1.0_november update_partner-ready 2
3 Empower every person and every organization to achieve more
4 1 billion Windows 10 devices in 2-3 years 500 million+ Windows 7/8 devices eligible for upgrade to Windows million PCs now in use worldwide over 4 years old
5 Monthly active devices around the world running Windows 10 Hours people spent using Windows 10 in December Minutes spent in Microsoft Edge across Windows 10 devices in just the last month Faster growth trajectory than Windows 7 Hours spent playing PC games on Windows 10 Devices running Windows 10 across enterprise and education customers Questions asked of Cortana on Windows 10 Windows 10 Store visits since launch Of new Windows 10 devices becoming active since Black Friday
6 1/3 of the workforce now uses 3 or more devices of SMBs say tablets are important for their business growth of total device market between 2014 and 2019 Combined total market of smartphones, tablets plus 2-in-1s, and PCs 2-in-1 and tablet unit sales expected in 2016* of business users say tablets are their only business device increase in premium ultramobile device sales between 2014 and 2017 increase in tablet and 2-in-1 device sales between 2014 and 2017 Sources: IDC, Gartner; *Total worldwide market forecast for small tablets, large tablets and 2-in-1s across commercial and consumer segments
7 LOOKING AHEAD Windows 10 Pro MICROSOFT CONFIDENTIAL FOR NDA DISCUSSION ONLY
8 THERE ARE T WO KINDS OF BIG COMPANIES, THOSE WHO VE BEEN HACKED, AND THOSE WHO DON T KNOW THEY VE BEEN HACKED. - JA M E S C O M E Y, F B I D I R E C TO R $3Trillion $3.5Million Median number of days attackers are present on a victims network before detection Days after detection to full recovery Impact of lost productivity and growth Average cost of a data breach (15% YoY increase) MICROSOFT CONFIDENTIAL FOR NDA DISCUSSION ONLY
9 HOW DO BREACHES OCCUR? Malware and vulnerabilities are not the only thing to worry about 46% of compromised systems had no malware on them 99.9% of exploited Vulnerabilities were used more than a year after the Common Vulnerabilities Exposure (CVE) was published Fast and effective phishing attacks give you little time to react 23% of recipients opened phishing messages (11% clicked on attachments) 50% of those who open and click attachments do so within the first hour Source: Verizon 2015 Data Breach Investigation Report MICROSOFT CONFIDENTIAL FOR NDA DISCUSSION ONLY
10 The most trusted platform Protect enterprise data against leaks, theft, or accidental disclosure Enhancements to Windows Hello and Microsoft Passport Micro-virtualization to contain malware to just the Edge browser session (2017) Windows Defender provides world-class defense, detection, and response Windows Defender Advanced Threat Protection helps enterprise customers detect, investigate and respond to Advanced Attacks and data breaches
11 Windows Defender Advanced Threat Protection helps enterprise customers detect, investigate and respond to Advanced Attacks and data breaches Post breach detection for active attacks actionable, correlated, real-time and historical for known and unknown adversaries Easily investigate & explore enterprise endpoints to understand scope of breach through rich machine timeline and data pivoting Self hunting across protected assets search current and historical observables machines, files, URLs or IPs across all protected endpoints. Deep file analysis for files retrieved from endpoints or from Microsoft s global sample store Built in threat intelligence knowledge base provides actor and intent context for every threat intelligence-based detection combining 1st and 3rd party intelligence sources Built into
12 IT for the modern workplace Better upgrades to stay up to date with the latest technology Enhancements to Dynamic Provisioning to allow you to start to get out of the imaging business Continued investments in MDM and management simplicity Continued commitment to high application compatibility Data driven operational excellence to streamline upgrades and improve efficiency
13 More productive, more personal Office + Windows = The best duo for work. Inking, the quickest way to bring ideas to life Resume or complete tasks on any device Organize your personal web with Microsoft Edge and get control of browser chaos Cortana helps you unlock the power of your business data Cortana keeps you on track and in control of your busy schedule
14 Windows 10 Anniversary Update WindowsForBusiness/windows-roadmap MICROSOFT CONFIDENTIAL FOR NDA DISCUSSION ONLY Security Management Productivity Innovation Enhancements to Windows Hello Enterprise Data Protection Windows Update for Business Enhancements to set up & provisioning Windows Store for Business Windows Ink User Experience Enhancements Windows Hello Brings Biometric Security to Apps and Microsoft Edge EDP provides file-level encryption for business data and apps that helps facilitate data separation, containment, app control, and leak prevention New active hours settings schedule updates to install when you want Simplified device setup app for EDU shared cart scenarios Education specific workflows in the Windows Image and Configuration Designer (WICD) Find, acquire and deliver free and paid apps in your organization. Brings the power of Windows to the tip of your pen Use pen and touch simultaneously to use a built-in ruler to make razor-straight lines Cortana, now more helpful than ever, with over 1,000 apps and available above the lock screen. Ability to pull reminder-relevant info from s into Cortana* *July
15 The most versatile devices Innovative devices from Windows and our partners New experiences: The latest advances touch, pen, Continuum, voice, and biometrics into today s devices Better performance: Faster speeds, longer battery life
16 Windows 10 Devices
17 Why Windows 10 Now on New Devices Modern security threats, flexible management and increasing productivity require a modern OS with new features designed for the latest hardware Security Windows Hello Credential Guard/Device Guard Enterprise Data Protection (EDP)* Secure Hardware (TPM2.0, VBS) Management MDM In Place Upgrade Windows Update for Business Productivity *EDP is planned to be made broadly available in mid-2016 **Over a 5 year old system Source: Intel Microsoft Confidential Performance (Windows 10 on Skylake)** Start Menu Pen (Windows Inking) Universal Windows Apps (UWP)
18 Commercial Device Priorities for 2016 Windows 10 Hardware Differentiation Modernize the mainstream notebook Defend premium share against MacBook Air and Pro Mainstream Convertibles Mainstream Ultraslims Premium Convertibles Premium Ultraslims Windows Hello Security Sustain detachable growth & prevent ipad Pro growth Win in Cloudbook scenarios in commercial and EDU Cortana Continuum Premium Detachable Mainstream Detachable Entry Notebooks Entry Convertibles pen Docking Cloud & Storage Drive sales of Vertical-specific tablets Low Storage LTE Small Tablets/Phablets Large Tablets
19 Win in Premium - Commercial HP EliteBook Folio HP Elite X Dell Latitude Dell Latitude in1 Lenovo ThinkPad X1 Yoga Lenovo ThinkPad X1 Tablet
20 Strengthen our Core EDU Good/Better/Best Best +$449 2in Convertible with pen Intel Core i3/i5 (Core) 4/128GB, 500GB Dell Latitude 13 Education Core i3 4/128GB $579 Business-like productivity for the most demanding work Advanced STEM applications with more demanding processing needs. For teachers and administrative staff scenarios Better Approx. $329 2in Convertible with pen Intel Pentium, 4/64GB, 500GB HP ProBook 11 EE 11.6 Core i3 4/500GB $349 Built for what any school day can throw at them Shared device and mobile cart scenarios in K-12 education with full ecosystem of Windows apps Great device for STEM and collaboration scenarios. Good <$249 Clamshell, Non-touch 11.6 Intel Celeron (Entry), 2/32GB Acer TravelMate B /32GB $249 Built for the cloud, works great offline 1:1 deployments in K-12 education leveraging the Microsoft cloud Wide range of Windows Store apps and Microsoft Office apps. 20
21 *Free upgrade offer expires 29 July 2016 P A R T N E R R E V E N U E 0 $ 1x $ $
22
23 Internal Use Rights Distributor Boot Camp content Windows 10 Learning series Microsoft Learning exams Partner Marketing Center Windows Insider program * Available spring 2016
24 ModernBiz campaign Windows 10 free upgrade offer* Windows 10 devices promotional offers
25 MICROSOFT CONFIDENTIAL FOR NDA DISCUSSION ONLY Arriving Summer 2016 July 29 End of Free Upgrade* BUY NOW New Windows PCs Do More. Just Like You. *3GB+ download required; internet access fees may apply. Offer valid through July 28, Windows 10 Upgrade Offer is valid for qualified Windows 7 and Windows 8.1 devices, including devices you already own. Some *3GB+ hardware/software download required; requirements internet access apply fees and may feature apply. availability Offer valid may through vary by July region 28, and device. Windows The 10 availability Upgrade of Offer Windows is valid 10 for upgrade qualified for Windows 7 Phone and Windows 8.1 devices 8.1 may devices, vary including by OEM, devices mobile operator you already or own. carrier. Some hardware/software Features vary by device. requirements Devices must apply be and connected feature availability to the internet may and vary have by region Windows and Update device. The enabled. availability Windows of Windows 7 SP1 and 10 Windows upgrade 8.1 for Update Windows required. Phone Some 8.1 devices editions may excluded: vary by OEM, Windows mobile 7 Enterprise, operator or carrier. Windows Features vary 8/8.1 by Enterprise, device. Devices and Windows must be RT/RT connected 8.1. To to check the internet for compatibility and have and Windows other important Update enabled. installation Windows information, 7 SP1 and visit Windows your device 8.1 Update manufacturer s required. website Some and editions the Windows excluded: 10 Windows Specifications 7 Enterprise, page. Windows 10 8/8.1 is automatically Enterprise, and updated. Windows Additional RT/RT 8.1. requirements To check for may compatibility apply over and time other for updates. important See installation windows.com information, details. visit your device manufacturer s website and the Windows 10 Specifications page. Windows 10 is automatically updated. Additional requirements may apply over time for updates. See windows.com for details.
26 Thank You
Pieter Wigleven Windows Technical Specialist
 Pieter Wigleven Windows Technical Specialist HOW DO BREACHES OCCUR? Malware and vulnerabilities are not the only thing to worry about 46% of compromised systems had no malware on them 99.9% of exploited
Pieter Wigleven Windows Technical Specialist HOW DO BREACHES OCCUR? Malware and vulnerabilities are not the only thing to worry about 46% of compromised systems had no malware on them 99.9% of exploited
Windows 10 edition. Find out which. is right for you. Core features. Familar, and better than ever Home Pro Enterprise Education Mobile.
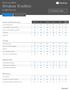 Core features Familar, and better than ever Home Pro Education Customizable Start Menu Windows Defender & Windows firewall N/A 1 N/A Fast start up with Hiberboot and InstantGo 2 N/A N/A TPM support 3 Battery
Core features Familar, and better than ever Home Pro Education Customizable Start Menu Windows Defender & Windows firewall N/A 1 N/A Fast start up with Hiberboot and InstantGo 2 N/A N/A TPM support 3 Battery
1
 Best platform for modern business Affordable and innovative devices Highly mobile and built for agility Broadest range and selection Presented by Dmitri Milov Simple to setup and manage Setup out of the
Best platform for modern business Affordable and innovative devices Highly mobile and built for agility Broadest range and selection Presented by Dmitri Milov Simple to setup and manage Setup out of the
Professional Development
 Professional Development HOW TO LEVERAGE MICROSOFT TECHNOLOGIES TO SAVE MONEY AND BE MORE PRODUCTIVE Geoffrey Whidden & Dustin Miller Brockman Coats Gedelian & Co. (800) 686-2727 www.ohiocpa.com How to
Professional Development HOW TO LEVERAGE MICROSOFT TECHNOLOGIES TO SAVE MONEY AND BE MORE PRODUCTIVE Geoffrey Whidden & Dustin Miller Brockman Coats Gedelian & Co. (800) 686-2727 www.ohiocpa.com How to
MODERN DESKTOP SECURITY
 MODERN DESKTOP SECURITY I M GOING TO BE HONEST. WE RE IN THE FIGHT OF OUR DIGITAL LIVES, AND WE ARE NOT WINNING! M I C H A E L M C C A U L, C H A I R M A N, U S H O M E L A N D S E C U R I T Y C O M M
MODERN DESKTOP SECURITY I M GOING TO BE HONEST. WE RE IN THE FIGHT OF OUR DIGITAL LIVES, AND WE ARE NOT WINNING! M I C H A E L M C C A U L, C H A I R M A N, U S H O M E L A N D S E C U R I T Y C O M M
Windows 10 Pro device opportunity
 Windows 10 Pro device opportunity I m too limited in what I can do and what I can achieve on Chromebook. Corey Weathers, CEO Homegrown Trailers Work more securely Modern PCs can protect against botnets
Windows 10 Pro device opportunity I m too limited in what I can do and what I can achieve on Chromebook. Corey Weathers, CEO Homegrown Trailers Work more securely Modern PCs can protect against botnets
Windows 10 Pro for Your Modern Workforce. Jared Bernatt Microsoft Windows
 Windows 10 Pro for Your Modern Workforce Jared Bernatt Microsoft Windows Agenda Windows 10 Pro means business The most comprehensive security for your business Best-in-class management that grows with
Windows 10 Pro for Your Modern Workforce Jared Bernatt Microsoft Windows Agenda Windows 10 Pro means business The most comprehensive security for your business Best-in-class management that grows with
Improve productivity with modernized PCs and Windows 10. Christopher Choong, DTM Field Marketing Manager
 Improve productivity with modernized PCs and Windows 10 Christopher Choong, DTM Field Marketing Manager Impressive innovation. Inside and out. 3 4 It s an important time to refresh Design Every product
Improve productivity with modernized PCs and Windows 10 Christopher Choong, DTM Field Marketing Manager Impressive innovation. Inside and out. 3 4 It s an important time to refresh Design Every product
Evolution of Cyber Security. Nasser Kettani Chief Technology Officer Microsoft, Middle East and Africa
 Evolution of Cyber Security Nasser Kettani Chief Technology Officer Microsoft, Middle East and Africa Nasser.Kettani@microsoft.com @nkettani MODERN SECURITY THREATS THERE ARE TWO KINDS OF BIG COMPANIES:
Evolution of Cyber Security Nasser Kettani Chief Technology Officer Microsoft, Middle East and Africa Nasser.Kettani@microsoft.com @nkettani MODERN SECURITY THREATS THERE ARE TWO KINDS OF BIG COMPANIES:
Windows 10 IoT Overview. Microsoft Corporation
 Windows 10 IoT Overview Microsoft Corporation 25 $7.2 BILLION TRILLION Connected things will by 2020 be in use by 2020 worldwide market for IoT solutions IDC: Worldwide and Regional Internet of Things
Windows 10 IoT Overview Microsoft Corporation 25 $7.2 BILLION TRILLION Connected things will by 2020 be in use by 2020 worldwide market for IoT solutions IDC: Worldwide and Regional Internet of Things
More Personal Computing Windows 10 and Surface in the Enterprise. Guenter Weimer GM Windows & Devices Group Microsoft APAC
 More Personal Computing Windows 10 and Surface in the Enterprise Guenter Weimer GM Windows & Devices Group Microsoft APAC +110 MILLION +12 MILLION "IT COULD BE THANKS TO HOW LIGHTWEIGHT WINDOWS 10 CAN
More Personal Computing Windows 10 and Surface in the Enterprise Guenter Weimer GM Windows & Devices Group Microsoft APAC +110 MILLION +12 MILLION "IT COULD BE THANKS TO HOW LIGHTWEIGHT WINDOWS 10 CAN
Made for the way you work: Big ideas and innovation from Windows 10 and Lenovo
 Made for the way you work: Big ideas and innovation from Windows 10 and Lenovo When it comes to technology, leadership matters. Together, Windows 10 and Lenovo are giving organizations dependable solutions
Made for the way you work: Big ideas and innovation from Windows 10 and Lenovo When it comes to technology, leadership matters. Together, Windows 10 and Lenovo are giving organizations dependable solutions
Windows 10 Momentum For Windows 10, Microsoft went all-out to turn around perceptions among corporate customers Windows 10 supports learning, business
 Windows 10 Momentum For Windows 10, Microsoft went all-out to turn around perceptions among corporate customers Windows 10 supports learning, business development, and efficiencies across our school. It
Windows 10 Momentum For Windows 10, Microsoft went all-out to turn around perceptions among corporate customers Windows 10 supports learning, business development, and efficiencies across our school. It
Windows 10 listening tour. What is REALLY on the minds of our customers?
 Windows 10 listening tour What is REALLY on the minds of our customers? What we are (really) hearing We need to adopt new technologies as fast as our customers No more big deployments Security is a top
Windows 10 listening tour What is REALLY on the minds of our customers? What we are (really) hearing We need to adopt new technologies as fast as our customers No more big deployments Security is a top
Enterprise Ransomware Mitigations
 打造數碼安全校園 Enterprise Ransomware Mitigations Windows 10, Edge Browser, Office ATP Enterprise Mobility Suite (EMS) ATP OneDrive for Business Azure Backup 3rd party Cloud Backup THE WINDOWS CLIENT DEFENSE
打造數碼安全校園 Enterprise Ransomware Mitigations Windows 10, Edge Browser, Office ATP Enterprise Mobility Suite (EMS) ATP OneDrive for Business Azure Backup 3rd party Cloud Backup THE WINDOWS CLIENT DEFENSE
INDIA The Changing Face of the Workplace: Going Light and Mobile
 An IDC InfoBrief May 2016 Commissioned by Executive Summary In today s hypercompetitive business environment, organizations are pushing for greater efficiencies to drive business growth. The growing diversity
An IDC InfoBrief May 2016 Commissioned by Executive Summary In today s hypercompetitive business environment, organizations are pushing for greater efficiencies to drive business growth. The growing diversity
Power of the Threat Detection Trinity
 White Paper Security Power of the Threat Detection Trinity How to Best Combine Real-time Correlation, Insider Threat Analysis and Hunting to protect against cyber threats. Combine real-time correlation,
White Paper Security Power of the Threat Detection Trinity How to Best Combine Real-time Correlation, Insider Threat Analysis and Hunting to protect against cyber threats. Combine real-time correlation,
Bromium: Virtualization-Based Security
 Bromium: Virtualization-Based Security TAG-Cyber Briefing Presented by Simon Crosby CTO, Co-Founder of Bromium Bromium 2016 2 Bromium 2016 3 Real-time Detection & Analysis Malware manifest Bromium 2016
Bromium: Virtualization-Based Security TAG-Cyber Briefing Presented by Simon Crosby CTO, Co-Founder of Bromium Bromium 2016 2 Bromium 2016 3 Real-time Detection & Analysis Malware manifest Bromium 2016
BULLETPROOF365 SECURING YOUR IT. Bulletproof365.com
 BULLETPROOF365 SECURING YOUR IT Bulletproof365.com INTRODUCING BULLETPROOF365 The world s leading productivity platform wrapped with industry-leading security, unmatched employee education and 24x7 IT
BULLETPROOF365 SECURING YOUR IT Bulletproof365.com INTRODUCING BULLETPROOF365 The world s leading productivity platform wrapped with industry-leading security, unmatched employee education and 24x7 IT
BULLETPROOF365 SECURING YOUR IT. Bulletproof365.com
 BULLETPROOF365 SECURING YOUR IT Bulletproof365.com INTRODUCING BULLETPROOF365 The world s leading productivity platform wrapped with industry-leading security, unmatched employee education and 24x7 IT
BULLETPROOF365 SECURING YOUR IT Bulletproof365.com INTRODUCING BULLETPROOF365 The world s leading productivity platform wrapped with industry-leading security, unmatched employee education and 24x7 IT
Why is Office 365 the right choice?
 Why is Office 365 the right choice? People today want to be productive wherever they go. They want to work faster and smarter across their favorite devices, while staying current and connected. Simply
Why is Office 365 the right choice? People today want to be productive wherever they go. They want to work faster and smarter across their favorite devices, while staying current and connected. Simply
Microsoft 365 Business FAQs
 Microsoft 365 Business FAQs Last updated April 27 th, 2018 Table of Contents General... 3 What is Microsoft 365 Business?... 3 Who should consider adopting Microsoft 365 Business?... 3 How can I get Microsoft
Microsoft 365 Business FAQs Last updated April 27 th, 2018 Table of Contents General... 3 What is Microsoft 365 Business?... 3 Who should consider adopting Microsoft 365 Business?... 3 How can I get Microsoft
SECURE OFFICE OF THE FUTURE
 ** SECURE OFFICE OF THE FUTURE HP Today Powering 430 of the Global Fortune 500 Companies Working with 250,000+ Channel Partners 18,000+ patents 2 PCs & 1 Printer ship every second HP Business Personal
** SECURE OFFICE OF THE FUTURE HP Today Powering 430 of the Global Fortune 500 Companies Working with 250,000+ Channel Partners 18,000+ patents 2 PCs & 1 Printer ship every second HP Business Personal
Mobile Field Worker Security Advocate Series: Customer Conversation Guide. Research by IDC, 2015
 Mobile Field Worker Security Advocate Series: Customer Conversation Guide Research by IDC, 2015 Agenda 1. Security Requirements for Mobile Field Workers 2. Key Mobile Security Challenges Companies Face
Mobile Field Worker Security Advocate Series: Customer Conversation Guide Research by IDC, 2015 Agenda 1. Security Requirements for Mobile Field Workers 2. Key Mobile Security Challenges Companies Face
Consultant since many years. Mainly working with defense and public sector. MCSE on Windows Server 2000 security ;-)
 About Consultant since many years Mainly working with defense and public sector MCSE on Windows Server 2000 security ;-) CYBERCRIME: STATE OF THE UNION EVOLUTION OF ATTACKS Mischief Fraud and theft Damage
About Consultant since many years Mainly working with defense and public sector MCSE on Windows Server 2000 security ;-) CYBERCRIME: STATE OF THE UNION EVOLUTION OF ATTACKS Mischief Fraud and theft Damage
WHITE PAPER. Operationalizing Threat Intelligence Data: The Problems of Relevance and Scale
 WHITE PAPER Operationalizing Threat Intelligence Data: The Problems of Relevance and Scale Operationalizing Threat Intelligence Data: The Problems of Relevance and Scale One key number that is generally
WHITE PAPER Operationalizing Threat Intelligence Data: The Problems of Relevance and Scale Operationalizing Threat Intelligence Data: The Problems of Relevance and Scale One key number that is generally
WINDOWS 10 ENTERPRISE New Security Features
 WINDOWS 10 ENTERPRISE New Security Features J. Abernethy mindshift Technologies Josh Quinn mindshift Technologies #ILTALSS #LSS26 TODAY S AGENDA Windows 10 Security Fundamentals Managing Windows 10 Security
WINDOWS 10 ENTERPRISE New Security Features J. Abernethy mindshift Technologies Josh Quinn mindshift Technologies #ILTALSS #LSS26 TODAY S AGENDA Windows 10 Security Fundamentals Managing Windows 10 Security
PEOPLE CENTRIC SECURITY THE NEW
 PEOPLE CENTRIC SECURITY THE NEW PARADIGM IN CYBERSECURITY David Karlsson SE Nordics March 2018 1 2018 Proofpoint, Inc. Proofpoint at a Glance LEADING CUSTOMERS DEEP SECURITY DNA UNIQUE VISIBILITY PARTNERS
PEOPLE CENTRIC SECURITY THE NEW PARADIGM IN CYBERSECURITY David Karlsson SE Nordics March 2018 1 2018 Proofpoint, Inc. Proofpoint at a Glance LEADING CUSTOMERS DEEP SECURITY DNA UNIQUE VISIBILITY PARTNERS
Managing EUC Threats. 3 Simple Ways To Improve Endpoint SECURITY
 Managing EUC Threats 3 Simple Ways To Improve Endpoint SECURITY Contents SECTION 01: THE CHALLENGE... 2 Emerging Threats: The Endpoint Explosion SECTION 02: LESSONS LEARNED... 5 Learning from a Cybersecurity
Managing EUC Threats 3 Simple Ways To Improve Endpoint SECURITY Contents SECTION 01: THE CHALLENGE... 2 Emerging Threats: The Endpoint Explosion SECTION 02: LESSONS LEARNED... 5 Learning from a Cybersecurity
Microsoft Windows 10 Upgrade Guide for Education
 Microsoft Windows 10 Upgrade Guide for Education A comprehensive guide for Educators, School Administrators and IT Professionals The best Windows 10 devices and apps Education licensing options Deployment
Microsoft Windows 10 Upgrade Guide for Education A comprehensive guide for Educators, School Administrators and IT Professionals The best Windows 10 devices and apps Education licensing options Deployment
with Advanced Protection
 with Advanced Email Protection OVERVIEW Today s sophisticated threats are changing. They re multiplying. They re morphing into new variants. And they re targeting people, not just technology. As organizations
with Advanced Email Protection OVERVIEW Today s sophisticated threats are changing. They re multiplying. They re morphing into new variants. And they re targeting people, not just technology. As organizations
Microsoft 365 Security & Compliance For Small- and Mid-Sized Businesses
 Microsoft 365 Security & Compliance For Small- and Mid-Sized Businesses The reality for your business today, and the importance of proactive security Cyberthreats are becoming more of a reality each day.
Microsoft 365 Security & Compliance For Small- and Mid-Sized Businesses The reality for your business today, and the importance of proactive security Cyberthreats are becoming more of a reality each day.
Guide Series. How to upgrade to Microsoft Windows 10? Guide Series
 How to upgrade to Microsoft Windows 10? Acuutech All rights reserved 2016 1 Contents Introduction... 2 Why use Windows 10?... 3 What are the advantages of Windows 10?... 4 Windows 10 editions comparison...
How to upgrade to Microsoft Windows 10? Acuutech All rights reserved 2016 1 Contents Introduction... 2 Why use Windows 10?... 3 What are the advantages of Windows 10?... 4 Windows 10 editions comparison...
Printing and Personal Systems
 Printing and Personal Systems Dion Weisler Executive Vice President Printing and Personal Systems Three waves Printing and Personal Systems 3 Three waves Printing and Personal Systems Wave one Capitalize
Printing and Personal Systems Dion Weisler Executive Vice President Printing and Personal Systems Three waves Printing and Personal Systems 3 Three waves Printing and Personal Systems Wave one Capitalize
Unified Communications Market Opportunity - EMEA. Andrew Wyatt Vice President Strategy - Broadsoft
 Unified Communications Market Opportunity - EMEA Andrew Wyatt Vice President Strategy - Broadsoft Evolution of Business Communications 2000 PBX Key Systems Centrex 2009 Mobile PBX Early UC Systems 2014
Unified Communications Market Opportunity - EMEA Andrew Wyatt Vice President Strategy - Broadsoft Evolution of Business Communications 2000 PBX Key Systems Centrex 2009 Mobile PBX Early UC Systems 2014
for Education Jason Trump Senior Education Specialist - Devices
 for Education Jason Trump Senior Education Specialist - Devices a 2 + b 2 = c 2 WATCHING, LISTENING INDIVIDUAL STUDY READING COLLABORATING ASSESSING WRITING PRESENTING Ipad Chromebook Surface Design Principles
for Education Jason Trump Senior Education Specialist - Devices a 2 + b 2 = c 2 WATCHING, LISTENING INDIVIDUAL STUDY READING COLLABORATING ASSESSING WRITING PRESENTING Ipad Chromebook Surface Design Principles
Data Protection Everywhere
 Data Protection Everywhere For the modern data center Syed Saleem Advisory Systems Engineer Pillars of the modern data center Protection and trust Security/Governance Encryption Data Protection Services/Support
Data Protection Everywhere For the modern data center Syed Saleem Advisory Systems Engineer Pillars of the modern data center Protection and trust Security/Governance Encryption Data Protection Services/Support
Table of Contents Table of Contents...2 Introduction...3 Mission of IT...3 Primary Service Delivery Objectives...3 Availability of Systems...
 Table of Contents Table of Contents...2 Introduction...3 Mission of IT...3 Primary Service Delivery Objectives...3 Availability of Systems...3 Improve Processes...4 Innovation...4 IT Planning & Alignment
Table of Contents Table of Contents...2 Introduction...3 Mission of IT...3 Primary Service Delivery Objectives...3 Availability of Systems...3 Improve Processes...4 Innovation...4 IT Planning & Alignment
SOLUTION BRIEF HELPING BREACH RESPONSE FOR GDPR WITH RSA SECURITY ADDRESSING THE TICKING CLOCK OF GDPR COMPLIANCE
 HELPING BREACH RESPONSE FOR GDPR WITH RSA SECURITY ADDRESSING THE TICKING CLOCK OF GDPR COMPLIANCE PREPARATION FOR GDPR IS ESSENTIAL The EU GDPR imposes interrelated obligations for organizations handling
HELPING BREACH RESPONSE FOR GDPR WITH RSA SECURITY ADDRESSING THE TICKING CLOCK OF GDPR COMPLIANCE PREPARATION FOR GDPR IS ESSENTIAL The EU GDPR imposes interrelated obligations for organizations handling
Microsoft 365 powered device webinar series Microsoft 365 powered device Assessment Kit. Alan Maddison, Architect Amit Bhatia, Architect
 Microsoft 365 powered device webinar series Microsoft 365 powered device Assessment Kit Alan Maddison, Architect Amit Bhatia, Architect Why did we create the Assessment kit? Assessment objectives Assess
Microsoft 365 powered device webinar series Microsoft 365 powered device Assessment Kit Alan Maddison, Architect Amit Bhatia, Architect Why did we create the Assessment kit? Assessment objectives Assess
Windows 10 for enterprise. Pramiti Bhatnagar
 Windows 10 for enterprise Pramiti Bhatnagar The intelligent platform designed for today Windows 10 Intelligent security Simplified updates Flexible management Enhanced productivity Intelligent security
Windows 10 for enterprise Pramiti Bhatnagar The intelligent platform designed for today Windows 10 Intelligent security Simplified updates Flexible management Enhanced productivity Intelligent security
Reinvent learning HP Education Solutions
 Reinvent learning HP Education Solutions 2018 1 HP EDUCATION HP Education solutions are designed to deliver meaningful outcomes for students, schools, and communities. They inspire students to learn everywhere,
Reinvent learning HP Education Solutions 2018 1 HP EDUCATION HP Education solutions are designed to deliver meaningful outcomes for students, schools, and communities. They inspire students to learn everywhere,
Optimizing IT: Toward Modern Workplace Management With Windows 10
 POINT OF VIEW DYNAMIC WORKPLACE SERVICES Optimizing IT: Toward Modern Workplace Management With Windows 10 JULY 2018 JON CONRAD, SENIOR DIRECTOR, INFRASTRUCTURE, CLOUD AND SECURITY SERVICES, NTT DATA SERVICES
POINT OF VIEW DYNAMIC WORKPLACE SERVICES Optimizing IT: Toward Modern Workplace Management With Windows 10 JULY 2018 JON CONRAD, SENIOR DIRECTOR, INFRASTRUCTURE, CLOUD AND SECURITY SERVICES, NTT DATA SERVICES
Go mobile. Stay in control.
 Go mobile. Stay in control. Enterprise Mobility + Security Jeff Alexander Sr. Technical Evangelist http://about.me/jeffa36 Mobile-first, cloud-first reality 63% 80% 0.6% Data breaches Shadow IT IT Budget
Go mobile. Stay in control. Enterprise Mobility + Security Jeff Alexander Sr. Technical Evangelist http://about.me/jeffa36 Mobile-first, cloud-first reality 63% 80% 0.6% Data breaches Shadow IT IT Budget
WHITE PAPER Migrating to Windows 10: a practical guide
 WHITE PAPER Migrating to Windows 10: a practical guide Look before you leap Things to consider before migrating to Windows 10 2 There s a bunch of good reasons to migrate all the Windowsdevices in your
WHITE PAPER Migrating to Windows 10: a practical guide Look before you leap Things to consider before migrating to Windows 10 2 There s a bunch of good reasons to migrate all the Windowsdevices in your
Behavioral Analytics A Closer Look
 SESSION ID: GPS2-F03 Behavioral Analytics A Closer Look Mike Huckaby VP, Global Systems Engineering RSA The world is full of obvious things which nobody by any chance ever observes. Sherlock Holmes 2 Patterns
SESSION ID: GPS2-F03 Behavioral Analytics A Closer Look Mike Huckaby VP, Global Systems Engineering RSA The world is full of obvious things which nobody by any chance ever observes. Sherlock Holmes 2 Patterns
Enterprise & Cloud Security
 Enterprise & Cloud Security Greg Brown VP and CTO: Cloud and Internet of Things McAfee An Intel Company August 20, 2013 You Do NOT Want to Own the Data Intel: 15B 2015 Cisco: 50B 2020 2 August 21, 2013
Enterprise & Cloud Security Greg Brown VP and CTO: Cloud and Internet of Things McAfee An Intel Company August 20, 2013 You Do NOT Want to Own the Data Intel: 15B 2015 Cisco: 50B 2020 2 August 21, 2013
IT & DATA SECURITY BREACH PREVENTION
 IT & DATA SECURITY BREACH PREVENTION A PRACTICAL GUIDE Part 1: Reducing Employee and Application Risks CONTENTS EMPLOYEES: IT security hygiene best practice APPLICATIONS: Make patching a priority AS CORPORATE
IT & DATA SECURITY BREACH PREVENTION A PRACTICAL GUIDE Part 1: Reducing Employee and Application Risks CONTENTS EMPLOYEES: IT security hygiene best practice APPLICATIONS: Make patching a priority AS CORPORATE
Remote employee. / future ready / Remote employee
 Remote employee Business success is, literally, in your employees hands in the form of the IT they use every day. It s your choice: Equip employees with the solutions that will help your organization win,
Remote employee Business success is, literally, in your employees hands in the form of the IT they use every day. It s your choice: Equip employees with the solutions that will help your organization win,
Bring your Own Device
 \ Advi Wha CONTENTS INCLUDE Why BYOD? BYOD HANDBOOK 2017 Suggested Devices Advice Support Documents Bring your Own Device This booklet advice and information regarding student owned devices for 2017. Version
\ Advi Wha CONTENTS INCLUDE Why BYOD? BYOD HANDBOOK 2017 Suggested Devices Advice Support Documents Bring your Own Device This booklet advice and information regarding student owned devices for 2017. Version
THE EFFECTIVE APPROACH TO CYBER SECURITY VALIDATION BREACH & ATTACK SIMULATION
 BREACH & ATTACK SIMULATION THE EFFECTIVE APPROACH TO CYBER SECURITY VALIDATION Cymulate s cyber simulation platform allows you to test your security assumptions, identify possible security gaps and receive
BREACH & ATTACK SIMULATION THE EFFECTIVE APPROACH TO CYBER SECURITY VALIDATION Cymulate s cyber simulation platform allows you to test your security assumptions, identify possible security gaps and receive
Protecting Against Modern Attacks. Protection Against Modern Attack Vectors
 Protecting Against Modern Attacks Protection Against Modern Attack Vectors CYBER SECURITY IS A CEO ISSUE. - M C K I N S E Y $4.0M 81% >300K 87% is the average cost of a data breach per incident. of breaches
Protecting Against Modern Attacks Protection Against Modern Attack Vectors CYBER SECURITY IS A CEO ISSUE. - M C K I N S E Y $4.0M 81% >300K 87% is the average cost of a data breach per incident. of breaches
Lenovo nomination Dutch IT Channel
 Lenovo nomination Dutch IT Channel WE BELIEVE DIFFERENT IS BETTER 1981 KICKSTARTED THE AGE OF DIGITAL PRODUCTIVITY the IBM PC.. the world s 1 st PC 1983 ENABLED PHONE CALLS WITHOUT WIRES Motorola DynaTAC..
Lenovo nomination Dutch IT Channel WE BELIEVE DIFFERENT IS BETTER 1981 KICKSTARTED THE AGE OF DIGITAL PRODUCTIVITY the IBM PC.. the world s 1 st PC 1983 ENABLED PHONE CALLS WITHOUT WIRES Motorola DynaTAC..
RSA Advanced Security Operations Richard Nichols, Director EMEA. Copyright 2015 EMC Corporation. All rights reserved. 1
 RSA Advanced Security Operations Richard Nichols, Director EMEA 1 What is the problem we need to solve? 2 Attackers Are Outpacing Defenders..and the Gap is Widening Attacker Capabilities The defender-detection
RSA Advanced Security Operations Richard Nichols, Director EMEA 1 What is the problem we need to solve? 2 Attackers Are Outpacing Defenders..and the Gap is Widening Attacker Capabilities The defender-detection
CloudSOC and Security.cloud for Microsoft Office 365
 Solution Brief CloudSOC and Email Security.cloud for Microsoft Office 365 DID YOU KNOW? Email is the #1 delivery mechanism for malware. 1 Over 40% of compliance related data in Office 365 is overexposed
Solution Brief CloudSOC and Email Security.cloud for Microsoft Office 365 DID YOU KNOW? Email is the #1 delivery mechanism for malware. 1 Over 40% of compliance related data in Office 365 is overexposed
Introduction to Device Trust Architecture
 Introduction to Device Trust Architecture July 2018 www.globalplatform.org 2018 GlobalPlatform, Inc. THE TECHNOLOGY The Device Trust Architecture is a security framework which shows how GlobalPlatform
Introduction to Device Trust Architecture July 2018 www.globalplatform.org 2018 GlobalPlatform, Inc. THE TECHNOLOGY The Device Trust Architecture is a security framework which shows how GlobalPlatform
EU GENERAL DATA PROTECTION: TIME TO ACT. Laurent Vanderschrick Channel Manager Belgium & Luxembourg Stefaan Van Hoornick Technical Manager BeNeLux
 EU GENERAL DATA PROTECTION: TIME TO ACT Laurent Vanderschrick Channel Manager Belgium & Luxembourg Stefaan Van Hoornick Technical Manager BeNeLux Is this the WAY you handle GDPR today 2 3 area s to consider
EU GENERAL DATA PROTECTION: TIME TO ACT Laurent Vanderschrick Channel Manager Belgium & Luxembourg Stefaan Van Hoornick Technical Manager BeNeLux Is this the WAY you handle GDPR today 2 3 area s to consider
Reinvention and Transformation in Personal Systems March 22,
 Reinvention and Transformation in Personal Systems March 22, 2017 http://www.hp.com/investor/home 1 Copyright 2017 HP Development Company, L.P. The information contained herein is subject to change without
Reinvention and Transformation in Personal Systems March 22, 2017 http://www.hp.com/investor/home 1 Copyright 2017 HP Development Company, L.P. The information contained herein is subject to change without
TOMORROW S SECURITY, DELIVERED TODAY. Protection Service for Business
 TOMORROW S SECURITY, DELIVERED TODAY Protection Service for Business TOMORROW S SECURITY, DELIVERED TODAY. Cyber security never stops. New attackers, tactics, and threats emerge every day. Hackers will
TOMORROW S SECURITY, DELIVERED TODAY Protection Service for Business TOMORROW S SECURITY, DELIVERED TODAY. Cyber security never stops. New attackers, tactics, and threats emerge every day. Hackers will
Make security part of your client systems refresh
 Make security part of your client systems refresh Safeguard your information with Dell Data Security Solutions while boosting productivity and reducing costs Your organization might have many reasons for
Make security part of your client systems refresh Safeguard your information with Dell Data Security Solutions while boosting productivity and reducing costs Your organization might have many reasons for
Converged Cloud and Digital Transformation: A Strategy for Business Success
 Converged and Digital Transformation: A Strategy for Business Success An IDC InfoBrief, Sponsored by Lenovo December 2017 Sponsored by Lenovo Page 1 Digital Transformation (DX) is Changing Everything About
Converged and Digital Transformation: A Strategy for Business Success An IDC InfoBrief, Sponsored by Lenovo December 2017 Sponsored by Lenovo Page 1 Digital Transformation (DX) is Changing Everything About
Securing Today s Mobile Workforce
 WHITE PAPER Securing Today s Mobile Workforce Secure and Manage Mobile Devices and Users with Total Defense Mobile Security Table of Contents Executive Summary..................................................................................
WHITE PAPER Securing Today s Mobile Workforce Secure and Manage Mobile Devices and Users with Total Defense Mobile Security Table of Contents Executive Summary..................................................................................
Speaker Introduction Who Mate Barany, VMware Manuel Mazzolin, VMware Peter Schmitt, Deutsche Bahn Systel Why VMworld 2017 Understanding the modern sec
 SIE3197BE Secure Your Windows 10 and Office 365 Deployment with VMware Security Solutions Mate Barany, VMware Manuel Mazzolin, VMware Peter Schmitt, Deutsche Bahn Systel #VMworld #SIE3197BE Speaker Introduction
SIE3197BE Secure Your Windows 10 and Office 365 Deployment with VMware Security Solutions Mate Barany, VMware Manuel Mazzolin, VMware Peter Schmitt, Deutsche Bahn Systel #VMworld #SIE3197BE Speaker Introduction
The result is a new Windows experience that s fresh yet familiar and is great for helping you stay organized, have fun, and get things done.
 Quick Guide Page 1 Contents Welcome to Windows 10... 3 Key innovations... 3 Cortana... 3 Microsoft Edge... 4 Built-in apps... 6 Enterprise-grade secure and fast... 7 Windows Defender... 8 Smart Screen...
Quick Guide Page 1 Contents Welcome to Windows 10... 3 Key innovations... 3 Cortana... 3 Microsoft Edge... 4 Built-in apps... 6 Enterprise-grade secure and fast... 7 Windows Defender... 8 Smart Screen...
Toshiba Product Update
 Toshiba Product Update Lee Sanvitale Higher Education Business Development Lead 17 November 2016 Agenda Toshiba Update 2016 Product Roadmap 2017 Kabylake Product Update Toshiba Recommends For Higher Education
Toshiba Product Update Lee Sanvitale Higher Education Business Development Lead 17 November 2016 Agenda Toshiba Update 2016 Product Roadmap 2017 Kabylake Product Update Toshiba Recommends For Higher Education
Mobile Devices prioritize User Experience
 Mobile Security 1 Uniqueness of Mobile Mobile Devices are Shared More Often Mobile Devices are Used in More Locations Mobile Devices prioritize User Experience Mobile Devices have multiple personas Mobile
Mobile Security 1 Uniqueness of Mobile Mobile Devices are Shared More Often Mobile Devices are Used in More Locations Mobile Devices prioritize User Experience Mobile Devices have multiple personas Mobile
10 KEY WAYS THE FINANCIAL SERVICES INDUSTRY CAN COMBAT CYBER THREATS
 10 KEY WAYS THE FINANCIAL SERVICES INDUSTRY CAN COMBAT CYBER THREATS WHITE PAPER INTRODUCTION BANKS ARE A COMMON TARGET FOR CYBER CRIMINALS AND OVER THE LAST YEAR, FIREEYE HAS BEEN HELPING CUSTOMERS RESPOND
10 KEY WAYS THE FINANCIAL SERVICES INDUSTRY CAN COMBAT CYBER THREATS WHITE PAPER INTRODUCTION BANKS ARE A COMMON TARGET FOR CYBER CRIMINALS AND OVER THE LAST YEAR, FIREEYE HAS BEEN HELPING CUSTOMERS RESPOND
Inside Windows 10. Howard Burpee
 Inside Windows 10 1 Why Windows 10? 7 ate 9 Too much code refers to Windows 9 Or 2 3 Due date In April, AMD s CEO, Lisa Su let slip that Windows 10 will be provided (to OEMs only?) by the end of July Microsoft
Inside Windows 10 1 Why Windows 10? 7 ate 9 Too much code refers to Windows 9 Or 2 3 Due date In April, AMD s CEO, Lisa Su let slip that Windows 10 will be provided (to OEMs only?) by the end of July Microsoft
Surface Go for Education
 Surface Go for Education Unlock limitless learning with Surface Go Spark creativity in students with Surface Go, a powerful, versatile device that s great for education and exploration. As versatile as
Surface Go for Education Unlock limitless learning with Surface Go Spark creativity in students with Surface Go, a powerful, versatile device that s great for education and exploration. As versatile as
Windows Server The operating system
 Windows Server 2019 The operating system that bridges onpremises and cloud By maximizing technology and infrastructure investments with Windows Server 2019, forward-facing businesses can capture direct
Windows Server 2019 The operating system that bridges onpremises and cloud By maximizing technology and infrastructure investments with Windows Server 2019, forward-facing businesses can capture direct
M365 Powered Device Proof of Concept
 M365 Powered Device Proof of Concept 365 A complete, intelligent, secure solution to empower employees Office 365 Windows 10 Enterprise Mobility + Security Modern IT Multiple Device Platforms User and
M365 Powered Device Proof of Concept 365 A complete, intelligent, secure solution to empower employees Office 365 Windows 10 Enterprise Mobility + Security Modern IT Multiple Device Platforms User and
DATA SHEET RISK & CYBERSECURITY PRACTICE EMPOWERING CUSTOMERS TO TAKE COMMAND OF THEIR EVOLVING RISK & CYBERSECURITY POSTURE
 DATA SHEET RISK & CYBERSECURITY PRACTICE EMPOWERING CUSTOMERS TO TAKE COMMAND OF THEIR EVOLVING RISK & CYBERSECURITY POSTURE EXECUTIVE SUMMARY ALIGNING CYBERSECURITY WITH RISK The agility and cost efficiencies
DATA SHEET RISK & CYBERSECURITY PRACTICE EMPOWERING CUSTOMERS TO TAKE COMMAND OF THEIR EVOLVING RISK & CYBERSECURITY POSTURE EXECUTIVE SUMMARY ALIGNING CYBERSECURITY WITH RISK The agility and cost efficiencies
RSA NetWitness Suite Respond in Minutes, Not Months
 RSA NetWitness Suite Respond in Minutes, Not Months Overview One can hardly pick up a newspaper or turn on the news without hearing about the latest security breaches. The Verizon 2015 Data Breach Investigations
RSA NetWitness Suite Respond in Minutes, Not Months Overview One can hardly pick up a newspaper or turn on the news without hearing about the latest security breaches. The Verizon 2015 Data Breach Investigations
THE EVOLUTION OF SIEM
 THE EVOLUTION OF SIEM Why it is critical to move beyond logs BUSINESS-DRIVEN SECURITY SOLUTIONS THE EVOLUTION OF SIEM Why it is critical to move beyond logs Despite increasing investments in security,
THE EVOLUTION OF SIEM Why it is critical to move beyond logs BUSINESS-DRIVEN SECURITY SOLUTIONS THE EVOLUTION OF SIEM Why it is critical to move beyond logs Despite increasing investments in security,
Windows 10 Identity and Security
 Windows 10 Identity and Security CYBER SECURITY IS A CEO ISSUE. - M C K I N S E Y $3.0 TRILLION $3.5 MILLION $500 MILLION Impact of lost productivity and growth Average cost of a data breach (15% YoY
Windows 10 Identity and Security CYBER SECURITY IS A CEO ISSUE. - M C K I N S E Y $3.0 TRILLION $3.5 MILLION $500 MILLION Impact of lost productivity and growth Average cost of a data breach (15% YoY
SOLUTION BRIEF RSA NETWITNESS NETWORK VISIBILITY-DRIVEN THREAT DEFENSE
 RSA NETWITNESS NETWORK VISIBILITY-DRIVEN THREAT DEFENSE KEY CUSTOMER BENEFITS: Gain complete visibility across enterprise networks Continuously monitor all traffic Faster analysis reduces risk exposure
RSA NETWITNESS NETWORK VISIBILITY-DRIVEN THREAT DEFENSE KEY CUSTOMER BENEFITS: Gain complete visibility across enterprise networks Continuously monitor all traffic Faster analysis reduces risk exposure
Introducing MVISION. Cohesive Cloud-based Management of Threat Countermeasures and Devices Leveraging Built-in Device Controls. Jon Parkes.
 Introducing MVISION Cohesive Cloud-based Management of Threat Countermeasures and Devices Leveraging Built-in Device Controls Jon Parkes McAfee 1 All information provided here is subject to non-disclosure
Introducing MVISION Cohesive Cloud-based Management of Threat Countermeasures and Devices Leveraging Built-in Device Controls Jon Parkes McAfee 1 All information provided here is subject to non-disclosure
benefits for customers with subscriptions in CSP
 Windows 10 upgrade benefits for customers with subscriptions in CSP Windows 10 upgrade benefits for customers Resources and guidance for organizations upgrading from Windows 7 and Windows 8/8.1 with subscriptions
Windows 10 upgrade benefits for customers with subscriptions in CSP Windows 10 upgrade benefits for customers Resources and guidance for organizations upgrading from Windows 7 and Windows 8/8.1 with subscriptions
BDPA Conference Windows 10
 BDPA Conference Windows 10 Tommy Patterson- Sr Technical Evangelist @tommy_patterson Do The you digital have economy what it takes to succeed? Are cybersecurity threats keeping you up at night? Your people
BDPA Conference Windows 10 Tommy Patterson- Sr Technical Evangelist @tommy_patterson Do The you digital have economy what it takes to succeed? Are cybersecurity threats keeping you up at night? Your people
How do you decide what s best for you?
 How do you decide what s best for you? Experience Transparency Leadership Commitment Cost reduction Security Trustworthiness Credibility Confidence Reliability Compliance Privacy Expertise Flexibility
How do you decide what s best for you? Experience Transparency Leadership Commitment Cost reduction Security Trustworthiness Credibility Confidence Reliability Compliance Privacy Expertise Flexibility
CDW.ca/lenovo
 Choose Lenovo Lenovo is built for work Lenovo has a wide selection of powerful and adaptable mobile devices, from laptop solutions to touch-enabled Windows 8 devices. CDW.ca/lenovo 800.732.8197 Why choose
Choose Lenovo Lenovo is built for work Lenovo has a wide selection of powerful and adaptable mobile devices, from laptop solutions to touch-enabled Windows 8 devices. CDW.ca/lenovo 800.732.8197 Why choose
We need a browser that just works with modern web sites and services. I m worried about Internet security threats and the risk to my business
 WHAT WE HEARD FROM YOU We need a browser that just works with modern web sites and services I m worried about Internet security threats and the risk to my business My employees need to be productive when
WHAT WE HEARD FROM YOU We need a browser that just works with modern web sites and services I m worried about Internet security threats and the risk to my business My employees need to be productive when
Enhancing the Cybersecurity of Federal Information and Assets through CSIP
 TECH BRIEF How BeyondTrust Helps Government Agencies Address Privileged Access Management to Improve Security Contents Introduction... 2 Achieving CSIP Objectives... 2 Steps to improve protection... 3
TECH BRIEF How BeyondTrust Helps Government Agencies Address Privileged Access Management to Improve Security Contents Introduction... 2 Achieving CSIP Objectives... 2 Steps to improve protection... 3
Windows 10 Basics For Windows 7 and 8 users
 Windows 10 Basics For Windows 7 and 8 users Introduction Windows 7/Vista/XP users first need to read Windows 10 Primer, particularly to understand Apps, User Accounts & One Drive. See also the Hints &
Windows 10 Basics For Windows 7 and 8 users Introduction Windows 7/Vista/XP users first need to read Windows 10 Primer, particularly to understand Apps, User Accounts & One Drive. See also the Hints &
Deliver a seamless user experience for Windows apps on Chromebooks
 Deliver a seamless user experience for Windows apps on Chromebooks Citrix XenApp powers Chromebooks with business-critical apps to simplify your adoption of the Chrome OS computing platform. citrix.com
Deliver a seamless user experience for Windows apps on Chromebooks Citrix XenApp powers Chromebooks with business-critical apps to simplify your adoption of the Chrome OS computing platform. citrix.com
Using Biometric Authentication to Elevate Enterprise Security
 Using Biometric Authentication to Elevate Enterprise Security Biometric authentication in the enterprise? It s just a matter of time Mobile biometric authentication is officially here to stay. Most of
Using Biometric Authentication to Elevate Enterprise Security Biometric authentication in the enterprise? It s just a matter of time Mobile biometric authentication is officially here to stay. Most of
Secure Data Acquisition, Communication, and Processing for Your IoT Solutions
 Secure Data Acquisition, Communication, and Processing for Your IoT Solutions Guidelines for Ensuring a Successful Implementation by Dr. Mihai Voicu, Chief Information Security Officer, Telit Contents
Secure Data Acquisition, Communication, and Processing for Your IoT Solutions Guidelines for Ensuring a Successful Implementation by Dr. Mihai Voicu, Chief Information Security Officer, Telit Contents
The Maximum Security Marriage: Mobile File Management is Necessary and Complementary to Mobile Device Management
 The Maximum Security Marriage: Mobile File Management is Necessary and Complementary to Mobile Device Management The bring your own device (BYOD) trend in the workplace is at an all-time high, and according
The Maximum Security Marriage: Mobile File Management is Necessary and Complementary to Mobile Device Management The bring your own device (BYOD) trend in the workplace is at an all-time high, and according
Designing an Adaptive Defense Security Architecture. George Chiorescu FireEye
 Designing an Adaptive Defense Security Architecture George Chiorescu FireEye Designing an Adaptive Security Architecture Key Challanges Existing blocking and prevention capabilities are insufficient to
Designing an Adaptive Defense Security Architecture George Chiorescu FireEye Designing an Adaptive Security Architecture Key Challanges Existing blocking and prevention capabilities are insufficient to
HP Printing and Personal Systems
 HP Printing and Personal Systems Presented by: Hope Gannon Partner Business Manager Agenda What is Managed Print Services (MPS) Why MPS Customer Benefits HP s Mobility Strategy Copyright 2013Hewlett-Packard
HP Printing and Personal Systems Presented by: Hope Gannon Partner Business Manager Agenda What is Managed Print Services (MPS) Why MPS Customer Benefits HP s Mobility Strategy Copyright 2013Hewlett-Packard
The New Enterprise Network In The Era Of The Cloud. Rohit Mehra Director, Enterprise Communications Infrastructure IDC
 The New Enterprise Network In The Era Of The Cloud Rohit Mehra Director, Enterprise Communications Infrastructure IDC Agenda 1. Dynamics of the Cloud Era 2. Market Landscape 3. Implications for the new
The New Enterprise Network In The Era Of The Cloud Rohit Mehra Director, Enterprise Communications Infrastructure IDC Agenda 1. Dynamics of the Cloud Era 2. Market Landscape 3. Implications for the new
Cisco Start. IT solutions designed to propel your business
 Cisco Start IT solutions designed to propel your business Small and medium-sized businesses (SMBs) typically have very limited resources to invest in new technologies. With every IT investment made, they
Cisco Start IT solutions designed to propel your business Small and medium-sized businesses (SMBs) typically have very limited resources to invest in new technologies. With every IT investment made, they
Windows 10 Tips and Tricks
 Windows 10 Tips and Tricks You've made the move to Windows 10. The Start Menu has returned and its cloud integration is obvious, but most everything else is unfamiliar. This session will help you setup
Windows 10 Tips and Tricks You've made the move to Windows 10. The Start Menu has returned and its cloud integration is obvious, but most everything else is unfamiliar. This session will help you setup
HP 2018 commercial desktop portfolio
 HP 2018 commercial desktop portfolio Chromebox HP ProDesk - ProOne EliteDesk - EliteOne Elite Z Chromebox USFF Boost productivity in the office with an affordable and easy-to- manage HP Chromebox 200 Series
HP 2018 commercial desktop portfolio Chromebox HP ProDesk - ProOne EliteDesk - EliteOne Elite Z Chromebox USFF Boost productivity in the office with an affordable and easy-to- manage HP Chromebox 200 Series
2018 Edition. Security and Compliance for Office 365
 2018 Edition Security and Compliance for Office 365 [Proofpoint has] given us our time back to focus on the really evil stuff. CISO, Global 500 Manufacturer Like millions of businesses around the world,
2018 Edition Security and Compliance for Office 365 [Proofpoint has] given us our time back to focus on the really evil stuff. CISO, Global 500 Manufacturer Like millions of businesses around the world,
MATURE YOUR CYBER DEFENSE OPERATIONS with Accenture s SIEM Transformation Services
 MATURE YOUR CYBER DEFENSE OPERATIONS with Accenture s SIEM Transformation Services THE NEED FOR MATURE CYBER DEFENSE CAPABILITIES The average annual cost of cyber crime reached $11.7 million per organization
MATURE YOUR CYBER DEFENSE OPERATIONS with Accenture s SIEM Transformation Services THE NEED FOR MATURE CYBER DEFENSE CAPABILITIES The average annual cost of cyber crime reached $11.7 million per organization
Benefit from the breadth of innovative PC solutions available from Dell
 Benefit from the breadth of innovative PC solutions available from Dell Our differentiated approach Address Top IT Concerns Services, Security & Support that enableit Innovation underpins everything Devices
Benefit from the breadth of innovative PC solutions available from Dell Our differentiated approach Address Top IT Concerns Services, Security & Support that enableit Innovation underpins everything Devices
Apple Device Management
 A COMPREHENSIVE GUIDE Apple Device Management FOR SMALL AND MEDIUM BUSINESSES With a renewed focus on mobile devices in the work environment, Apple has become the device of choice in small and medium businesses.
A COMPREHENSIVE GUIDE Apple Device Management FOR SMALL AND MEDIUM BUSINESSES With a renewed focus on mobile devices in the work environment, Apple has become the device of choice in small and medium businesses.
DaaS in Education Chromebook Solutions
 in Education Solutions Agenda: Introduction Program overview Pricing & Product offerings Q&A ITaaS powered by IT as a service (ITaaS) is an operational model where the IT service provider delivers an information
in Education Solutions Agenda: Introduction Program overview Pricing & Product offerings Q&A ITaaS powered by IT as a service (ITaaS) is an operational model where the IT service provider delivers an information
A Comedy of Errors: Assessing and Managing the Human Element of Cyber Risk
 SESSION ID: GRC-T10 A Comedy of Errors: Assessing and Managing the Human Element of Cyber Risk R Jason Straight Sr. VP, Chief Privacy Officer UnitedLex Corp. Has anyone seen this man? 2 3 4 We re getting
SESSION ID: GRC-T10 A Comedy of Errors: Assessing and Managing the Human Element of Cyber Risk R Jason Straight Sr. VP, Chief Privacy Officer UnitedLex Corp. Has anyone seen this man? 2 3 4 We re getting
