University of Illinois at Chicago & Technische Universiteit Eindhoven
|
|
|
- Garey Bartholomew Harris
- 5 years ago
- Views:
Transcription
1 Engineering cryptographic software 1 Daniel J. Bernstein University of Illinois at Chicago & Technische Universiteit Eindhoven This is easy, right? 1. Take general principles of software engineering. 2. Apply principles to crypto. Let s try some examples : : :
2 1972 Parnas On the criteria to be used in decomposing systems into modules : 2 We propose instead that one begins with a list of difficult design decisions or design decisions which are likely to change. Each module is then designed to hide such a decision from the others. e.g. If number of cipher rounds is properly modularized as #define ROUNDS 20 then it is easy to change.
3 Another general principle of software engineering: Make the right thing simple and the wrong thing complex. 3
4 Another general principle of software engineering: Make the right thing simple and the wrong thing complex. 3 e.g. Make it difficult to ignore invalid authenticators.
5 Another general principle of software engineering: Make the right thing simple and the wrong thing complex. 3 e.g. Make it difficult to ignore invalid authenticators. Do not design APIs like this: The sample code used in this manual omits the checking of status values for clarity, but when using cryptlib you should check return values, particularly for critical functions : : :
6 Not so easy: Timing attacks s: TENEX operating system compares user-supplied string against secret password one character at a time, stopping at first difference: AAAAAA vs. SECRET: stop at 1. SAAAAA vs. SECRET: stop at 2. SEAAAA vs. SECRET: stop at 3. Attacker sees comparison time, deduces position of difference. A few hundred tries reveal secret password.
7 How typical software checks 16-byte authenticator: for (i = 0;i < 16;++i) if (x[i]!= y[i]) return 0; return 1; 5 Fix, eliminating information flow from secrets to timings: diff = 0; for (i = 0;i < 16;++i) diff = x[i] ^ y[i]; return 1 & ((diff-1) >> 8); Notice that the language makes the wrong thing simple and the right thing complex.
8 Language designer s notion of right is too weak for security. 6 So mistakes continue to happen.
9 Language designer s notion of right is too weak for security. 6 So mistakes continue to happen. One of many examples, part of the reference software for CAESAR candidate CLOC: /* compare the tag */ int i; for(i = 0;i < CRYPTO_ABYTES;i++) if(tag[i]!= c[(*mlen) + i]){ return RETURN_TAG_NO_MATCH; } return RETURN_SUCCESS;
10 Do timing attacks really work? 7 Objection: Timings are noisy!
11 Do timing attacks really work? 7 Objection: Timings are noisy! Answer #1: Does noise stop all attacks? To guarantee security, defender must block all information flow.
12 Do timing attacks really work? 7 Objection: Timings are noisy! Answer #1: Does noise stop all attacks? To guarantee security, defender must block all information flow. Answer #2: Attacker uses statistics to eliminate noise.
13 Do timing attacks really work? 7 Objection: Timings are noisy! Answer #1: Does noise stop all attacks? To guarantee security, defender must block all information flow. Answer #2: Attacker uses statistics to eliminate noise. Answer #3, what the 1970s attackers actually did: Cross page boundary, inducing page faults, to amplify timing signal.
14 Defenders don t learn 8 Some of the literature: 1996 Kocher pointed out timing attacks on cryptographic key bits. Briefly mentioned by Kocher and by 1998 Kelsey Schneier Wagner Hall: secret array indices can affect timing via cache misses Page, 2003 Tsunoo Saito Suzaki Shigeri Miyauchi: timing attacks on DES.
15 Guaranteed countermeasure: load entire table into cache. 9
16 Guaranteed countermeasure: load entire table into cache / Bernstein: Timing attacks on AES. Countermeasure isn t safe; e.g., secret array indices can affect timing via cache-bank collisions. What is safe: kill all data flow from secrets to array indices.
17 Guaranteed countermeasure: load entire table into cache / Bernstein: Timing attacks on AES. Countermeasure isn t safe; e.g., secret array indices can affect timing via cache-bank collisions. What is safe: kill all data flow from secrets to array indices Tromer Osvik Shamir: 65ms to steal Linux AES key used for hard-disk encryption.
18 Intel recommends, and OpenSSL integrates, cheaper countermeasure: always loading from known lines of cache. 10
19 Intel recommends, and OpenSSL integrates, cheaper countermeasure: always loading from known lines of cache Bernstein Schwabe A word of warning : This countermeasure isn t safe. Same issues described in 2004.
20 Intel recommends, and OpenSSL integrates, cheaper countermeasure: always loading from known lines of cache Bernstein Schwabe A word of warning : This countermeasure isn t safe. Same issues described in Yarom Genkin Heninger CacheBleed steals RSA secret key via timings of OpenSSL.
21 2008 RFC 5246 The Transport Layer Security (TLS) Protocol, Version 1.2 : This leaves a small timing channel, since MAC performance depends to some extent on the size of the data fragment, but it is not believed to be large enough to be exploitable, due to the large block size of existing MACs and the small size of the timing signal. 11
22 2008 RFC 5246 The Transport Layer Security (TLS) Protocol, Version 1.2 : This leaves a small timing channel, since MAC performance depends to some extent on the size of the data fragment, but it is not believed to be large enough to be exploitable, due to the large block size of existing MACs and the small size of the timing signal AlFardan Paterson Lucky Thirteen: breaking the TLS and DTLS record protocols : exploit these timings; steal plaintext.
23 How to write constant-time code 12 If possible, write code in asm to control instruction selection. Look for documentation identifying variability: e.g., Division operations terminate when the divide operation completes, with the number of cycles required dependent on the values of the input operands. Measure cycles rather than trusting CPU documentation.
24 Cut off all data flow from secrets to branch conditions. 13 Cut off all data flow from secrets to array indices. Cut off all data flow from secrets to shift/rotate distances. Prefer logic instructions. Prefer vector instructions. Watch out for CPUs with variable-time multipliers: e.g., Cortex-M3 and most PowerPCs.
25 Software optimization 14 Almost all software is much slower than it could be.
26 Software optimization 14 Almost all software is much slower than it could be. Is software applied to much data? Usually not. Usually the wasted CPU time is negligible.
27 Software optimization 14 Almost all software is much slower than it could be. Is software applied to much data? Usually not. Usually the wasted CPU time is negligible. But crypto software should be applied to all communication. Crypto that s too slow fewer users fewer cryptanalysts less attractive for everybody.
28 Typical situation: You want (constant-time) software that computes cipher X as efficiently as possible. 15 Starting point: You have written a reference implementation of X. You have chosen a target CPU. (Can repeat for other CPUs.) You measure performance of the implementation. Now what?
29 A simplified example 16 Target CPU: TI LM4F120H5QR microcontroller containing one ARM Cortex-M4F core. Reference implementation: int sum(int *x) { int result = 0; int i; for (i = 0;i < 1000;++i) result += x[i]; return result; }
30 Counting cycles: 17 static volatile unsigned int *const DWT_CYCCNT = (void *) 0xE ;... int beforesum = *DWT_CYCCNT; int result = sum(x); int aftersum = *DWT_CYCCNT; UARTprintf("sum %d %d\n", result,aftersum-beforesum); Output shows 8012 cycles. Change 1000 to 500: 4012.
31 Okay, 8 cycles per addition. Um, are microcontrollers really this slow at addition? 18
32 Okay, 8 cycles per addition. Um, are microcontrollers really this slow at addition? 18 Bad practice: Apply random optimizations (and tweak compiler options) until you get bored. Keep the fastest results.
33 Okay, 8 cycles per addition. Um, are microcontrollers really this slow at addition? 18 Bad practice: Apply random optimizations (and tweak compiler options) until you get bored. Keep the fastest results. Good practice: Figure out lower bound for cycles spent on arithmetic etc. Understand gap between lower bound and observed time.
34 Find ARM Cortex-M4 Processor Technical Reference Manual. Rely on Wikipedia comment that M4F = M4 + floating-point unit. 19 Manual says that Cortex-M4 implements the ARMv7E-M architecture profile. Points to the ARMv7-M Architecture Reference Manual, which defines instructions: e.g., ADD for 32-bit addition. First manual says that ADD takes just 1 cycle.
35 Inputs and output of ADD are integer registers. ARMv7-M has 16 integer registers, including special-purpose stack pointer and program counter. 20 Each element of x array needs to be loaded into a register. Basic load instruction: LDR. Manual says 2 cycles but adds a note about pipelining. Then more explanation: if next instruction is also LDR (with address not based on first LDR) then it saves 1 cycle.
36 n consecutive LDRs takes only n + 1 cycles ( more multiple LDRs can be pipelined together ). 21 Can achieve this speed in other ways (LDRD, LDM) but nothing seems faster. Lower bound for n LDR + n ADD: 2n + 1 cycles, including n cycles of arithmetic. Why observed time is higher: non-consecutive LDRs; costs of manipulating i.
37 int sum(int *x) { int result = 0; int *y = x ; int x0,x1,x2,x3,x4, x5,x6,x7,x8,x9; 22 while (x!= y) { x0 = 0[(volatile int *)x]; x1 = 1[(volatile int *)x]; x2 = 2[(volatile int *)x]; x3 = 3[(volatile int *)x]; x4 = 4[(volatile int *)x]; x5 = 5[(volatile int *)x]; x6 = 6[(volatile int *)x];
38 x7 = 7[(volatile int *)x]; x8 = 8[(volatile int *)x]; x9 = 9[(volatile int *)x]; result += x0; result += x1; result += x2; result += x3; result += x4; result += x5; result += x6; result += x7; result += x8; result += x9; x0 = 10[(volatile int *)x]; x1 = 11[(volatile int *)x]; 23
39 x2 = 12[(volatile int *)x]; x3 = 13[(volatile int *)x]; x4 = 14[(volatile int *)x]; x5 = 15[(volatile int *)x]; x6 = 16[(volatile int *)x]; x7 = 17[(volatile int *)x]; x8 = 18[(volatile int *)x]; x9 = 19[(volatile int *)x]; x += 20; result += x0; result += x1; result += x2; result += x3; result += x4; result += x5; 24
40 } result += x6; result += x7; result += x8; result += x9; 25 } return result;
41 } result += x6; result += x7; result += x8; result += x9; 25 } return result; 2526 cycles. Even better in asm.
42 } result += x6; result += x7; result += x8; result += x9; 25 } return result; 2526 cycles. Even better in asm. Wikipedia: By the late 1990s for even performance sensitive code, optimizing compilers exceeded the performance of human experts.
43 } result += x6; result += x7; result += x8; result += x9; 25 } return result; 2526 cycles. Even better in asm. Wikipedia: By the late 1990s for even performance sensitive code, optimizing compilers exceeded the performance of human experts. [citation needed]
44 A real example 26 Salsa20 reference software: cycles/byte on this CPU. Lower bound for arithmetic: 64 bytes require cycle ADDs, cycle XORs, so at least 10:25 cycles/byte. ARMv7-M instruction set includes free rotation as part of XOR instruction. (Compiler knows this.)
45 Detailed benchmarks show several cycles/byte spent on load_littleendian and store_littleendian. 27 Can replace with LDR and STR. (Compiler doesn t see this.) Then observe 23 cycles/byte: 18 cycles/byte for rounds, plus 5 cycles/byte overhead. Still far above cycles/byte.
46 Detailed benchmarks show several cycles/byte spent on load_littleendian and store_littleendian. 27 Can replace with LDR and STR. (Compiler doesn t see this.) Then observe 23 cycles/byte: 18 cycles/byte for rounds, plus 5 cycles/byte overhead. Still far above cycles/byte. Gap is mostly loads, stores. Minimize load/store cost by choosing spills carefully.
47 Which of the 16 Salsa20 words should be in registers? Don t trust compiler to optimize register allocation. 28 Make loads consecutive? Don t trust compiler to optimize instruction scheduling. Spill to FPU instead of stack? Don t trust compiler to optimize instruction selection. On bigger CPUs, selecting vector instructions is critical for performance.
48 The big picture 29 CPUs are evolving farther and farther away from naive models of CPUs.
49 The big picture 29 CPUs are evolving farther and farther away from naive models of CPUs. Minor optimization challenges: Pipelining. Superscalar processing. Major optimization challenges: Vectorization. Many threads; many cores. The memory hierarchy; the ring; the mesh. Larger-scale parallelism. Larger-scale networking.
50 CPU design in a nutshell 30 f 0 g 0 g f h 0 h 1 h 3 h 2 Gates : a; b 1 ab computing product h 0 + 2h 1 + 4h 2 + 8h 3 of integers f 0 + 2f 1 ; g 0 + 2g 1.
51 Electricity takes time to percolate through wires and gates. If f 0 ; f 1 ; g 0 ; g 1 are stable then h 0 ; h 1 ; h 2 ; h 3 are stable a few moments later. 31
52 Electricity takes time to percolate through wires and gates. If f 0 ; f 1 ; g 0 ; g 1 are stable then h 0 ; h 1 ; h 2 ; h 3 are stable a few moments later. 31 Build circuit with more gates to multiply (e.g.) 32-bit integers: (Details omitted.)
53 Build circuit to compute bit integer r i given 4-bit integer i and 32-bit integers r 0 ; r 1 ; : : : ; r 15 : register read
54 Build circuit to compute bit integer r i given 4-bit integer i and 32-bit integers r 0 ; r 1 ; : : : ; r 15 : register read Build circuit for register write : r 0 ; : : : ; r 15 ; s; i r 0 ; : : : ; r 15 where r j = r j except r i = s.
55 Build circuit to compute bit integer r i given 4-bit integer i and 32-bit integers r 0 ; r 1 ; : : : ; r 15 : register read Build circuit for register write : r 0 ; : : : ; r 15 ; s; i r 0 ; : : : ; r 15 where r j = r j except r i = s. Build circuit for addition. Etc.
56 r 0 ; : : : ; r 15 ; i; j; k r 0 ; : : : ; r 15 where r = r except r i = r j r k : 33 register read register read register write
57 Add more flexibility. 34 More arithmetic: replace (i; j; k) with ( ; i; j; k) and ( + ; i; j; k) and more options.
58 Add more flexibility. 34 More arithmetic: replace (i; j; k) with ( ; i; j; k) and ( + ; i; j; k) and more options. Instruction fetch : p o p ; i p ; j p ; k p ; p.
59 Add more flexibility. 34 More arithmetic: replace (i; j; k) with ( ; i; j; k) and ( + ; i; j; k) and more options. Instruction fetch : p o p ; i p ; j p ; k p ; p. Instruction decode : decompression of compressed format for o p ; i p ; j p ; k p ; p.
60 Add more flexibility. 34 More arithmetic: replace (i; j; k) with ( ; i; j; k) and ( + ; i; j; k) and more options. Instruction fetch : p o p ; i p ; j p ; k p ; p. Instruction decode : decompression of compressed format for o p ; i p ; j p ; k p ; p. More (but slower) storage: load from and store to larger RAM arrays.
61 Build flip-flops storing (p; r 0 ; : : : ; r 15 ). 35 Hook (p; r 0 ; : : : ; r 15 ) flip-flops into circuit inputs. Hook outputs (p ; r 0 ; : : : ; r 15 ) into the same flip-flops. At each clock tick, flip-flops are overwritten with the outputs. Clock needs to be slow enough for electricity to percolate all the way through the circuit, from flip-flops to flip-flops.
62 Now have semi-flexible CPU: flip-flops insn fetch 36 insn decode register read register read register write Further flexibility is useful: e.g., rotation instructions.
63 Pipelining allows faster clock: flip-flops insn fetch flip-flops insn decode flip-flops register read register read flip-flops flip-flops register write stage 1 stage 2 stage 3 stage 4 stage 5 37
64 Goal: Stage n handles instruction one tick after stage n Instruction fetch reads next instruction, feeds p back, sends instruction. After next clock tick, instruction decode uncompresses this instruction, while instruction fetch reads another instruction. Some extra flip-flop area. Also extra area to preserve instruction semantics: e.g., stall on read-after-write.
65 Superscalar processing: register read flip-flops insn insn fetch fetch flip-flops insn insn decode decode flip-flops register read register read flip-flops register read flip-flops register write register write
66 Vector processing: 40 Expand each 32-bit integer into n-vector of 32-bit integers. ARM NEON has n = 4; Intel AVX2 has n = 8; Intel AVX-512 has n = 16; GPUs have larger n.
67 Vector processing: 40 Expand each 32-bit integer into n-vector of 32-bit integers. ARM NEON has n = 4; Intel AVX2 has n = 8; Intel AVX-512 has n = 16; GPUs have larger n. n speedup if n arithmetic circuits, n read/write circuits. Benefit: Amortizes insn circuits.
68 Vector processing: 40 Expand each 32-bit integer into n-vector of 32-bit integers. ARM NEON has n = 4; Intel AVX2 has n = 8; Intel AVX-512 has n = 16; GPUs have larger n. n speedup if n arithmetic circuits, n read/write circuits. Benefit: Amortizes insn circuits. Huge effect on higher-level algorithms and data structures.
69 Network on chip: the mesh 41 How expensive is sorting? Input: array of n 1; numbers. Each number in 2; : : : ; n 2, represented in binary. Output: array of n numbers, in increasing order, represented in binary; same multiset as input.
70 Network on chip: the mesh 41 How expensive is sorting? Input: array of n 1; numbers. Each number in 2; : : : ; n 2, represented in binary. Output: array of n numbers, in increasing order, represented in binary; same multiset as input. Metric: seconds used by circuit of area n 1+o(1). For simplicity assume n = 4 k.
71 Spread array across square mesh of n small cells, each of area n o(1), with near-neighbor wiring: 42
72 Sort row of n 0:5 cells in n 0:5+o(1) seconds: 43 Sort each pair in parallel Sort alternate pairs in parallel Repeat until number of steps equals row length.
73 Sort row of n 0:5 cells in n 0:5+o(1) seconds: 43 Sort each pair in parallel Sort alternate pairs in parallel Repeat until number of steps equals row length. Sort each row, in parallel, in a total of n 0:5+o(1) seconds.
74 Sort all n cells in n 0:5+o(1) seconds: 44 Recursively sort quadrants in parallel, if n > 1. Sort each column in parallel. Sort each row in parallel. Sort each column in parallel. Sort each row in parallel. With proper choice of left-to-right/right-to-left for each row, can prove that this sorts whole array.
75 For example, assume that this 8 8 array is in cells:
76 Recursively sort quadrants, top, bottom :
77 Sort each column in parallel:
78 Sort each row in parallel, alternately, :
79 Sort each column in parallel:
80 Sort each row in parallel, or as desired:
81 Chips are in fact evolving towards having this much parallelism and communication. 51 GPUs: parallel + global RAM. Old Xeon Phi: parallel + ring. New Xeon Phi: parallel + mesh.
82 Chips are in fact evolving towards having this much parallelism and communication. 51 GPUs: parallel + global RAM. Old Xeon Phi: parallel + ring. New Xeon Phi: parallel + mesh. Algorithm designers don t even get the right exponent without taking this into account.
83 Chips are in fact evolving towards having this much parallelism and communication. 51 GPUs: parallel + global RAM. Old Xeon Phi: parallel + ring. New Xeon Phi: parallel + mesh. Algorithm designers don t even get the right exponent without taking this into account. Shock waves from subroutines into high-level algorithm design.
Example: Adding 1000 integers on Cortex-M4F. Lower bound: 2n + 1 cycles for n LDR + n ADD. Imagine not knowing this : : :
 Cryptographic software engineering, part 2 1 Daniel J. Bernstein Last time: General software engineering. Using const-time instructions. Comparing time to lower bound. Example: Adding 1000 integers on
Cryptographic software engineering, part 2 1 Daniel J. Bernstein Last time: General software engineering. Using const-time instructions. Comparing time to lower bound. Example: Adding 1000 integers on
Daniel J. Bernstein University of Illinois at Chicago & Technische Universiteit Eindhoven
 Goals of authenticated encryption Daniel J. Bernstein University of Illinois at Chicago & Technische Universiteit Eindhoven More details, credits: competitions.cr.yp.to /features.html Encryption sender
Goals of authenticated encryption Daniel J. Bernstein University of Illinois at Chicago & Technische Universiteit Eindhoven More details, credits: competitions.cr.yp.to /features.html Encryption sender
High-Performance Cryptography in Software
 High-Performance Cryptography in Software Peter Schwabe Research Center for Information Technology Innovation Academia Sinica September 3, 2012 ECRYPT Summer School: Challenges in Security Engineering
High-Performance Cryptography in Software Peter Schwabe Research Center for Information Technology Innovation Academia Sinica September 3, 2012 ECRYPT Summer School: Challenges in Security Engineering
Cryptographic Engineering
 Cryptographic Engineering Cryptography in software the basics Radboud University, Nijmegen, The Netherlands Spring 2019 The software arena(s) Embedded microcontrollers This is what you re looking at in
Cryptographic Engineering Cryptography in software the basics Radboud University, Nijmegen, The Netherlands Spring 2019 The software arena(s) Embedded microcontrollers This is what you re looking at in
Sorting integer arrays: security, speed, and verification. D. J. Bernstein
 Sorting integer arrays: security, speed, and verification 1 D. J. Bernstein Bob s laptop screen: 2 From: Alice Thank you for your submission. We received many interesting papers, and unfortunately your
Sorting integer arrays: security, speed, and verification 1 D. J. Bernstein Bob s laptop screen: 2 From: Alice Thank you for your submission. We received many interesting papers, and unfortunately your
Salsa20 speed. Daniel J. Bernstein
 Salsa20 speed Daniel J. Bernstein Department of Mathematics, Statistics, and Computer Science (M/C 249) The University of Illinois at Chicago Chicago, IL 60607 7045 snuffle@box.cr.yp.to 1 Introduction
Salsa20 speed Daniel J. Bernstein Department of Mathematics, Statistics, and Computer Science (M/C 249) The University of Illinois at Chicago Chicago, IL 60607 7045 snuffle@box.cr.yp.to 1 Introduction
Fixed-Point Math and Other Optimizations
 Fixed-Point Math and Other Optimizations Embedded Systems 8-1 Fixed Point Math Why and How Floating point is too slow and integers truncate the data Floating point subroutines: slower than native, overhead
Fixed-Point Math and Other Optimizations Embedded Systems 8-1 Fixed Point Math Why and How Floating point is too slow and integers truncate the data Floating point subroutines: slower than native, overhead
Computer Organization and Assembly Language (CS-506)
 Computer Organization and Assembly Language (CS-506) Muhammad Zeeshan Haider Ali Lecturer ISP. Multan ali.zeeshan04@gmail.com https://zeeshanaliatisp.wordpress.com/ Lecture 2 Memory Organization and Structure
Computer Organization and Assembly Language (CS-506) Muhammad Zeeshan Haider Ali Lecturer ISP. Multan ali.zeeshan04@gmail.com https://zeeshanaliatisp.wordpress.com/ Lecture 2 Memory Organization and Structure
Computer Systems. Binary Representation. Binary Representation. Logical Computation: Boolean Algebra
 Binary Representation Computer Systems Information is represented as a sequence of binary digits: Bits What the actual bits represent depends on the context: Seminar 3 Numerical value (integer, floating
Binary Representation Computer Systems Information is represented as a sequence of binary digits: Bits What the actual bits represent depends on the context: Seminar 3 Numerical value (integer, floating
McBits: fast constant-time code-based cryptography. (to appear at CHES 2013)
 McBits: fast constant-time code-based cryptography (to appear at CHES 2013) D. J. Bernstein University of Illinois at Chicago & Technische Universiteit Eindhoven Joint work with: Tung Chou Technische Universiteit
McBits: fast constant-time code-based cryptography (to appear at CHES 2013) D. J. Bernstein University of Illinois at Chicago & Technische Universiteit Eindhoven Joint work with: Tung Chou Technische Universiteit
Benchmarking benchmarking, and optimizing optimization. Daniel J. Bernstein. University of Illinois at Chicago & Technische Universiteit Eindhoven
 Benchmarking benchmarking, and optimizing optimization 1 Daniel J. Bernstein University of Illinois at Chicago & Technische Universiteit Eindhoven Bit operations per bit of plaintext 2 (assuming precomputed
Benchmarking benchmarking, and optimizing optimization 1 Daniel J. Bernstein University of Illinois at Chicago & Technische Universiteit Eindhoven Bit operations per bit of plaintext 2 (assuming precomputed
Implementing AES : performance and security challenges
 Implementing AES 2000-2010: performance and security challenges Emilia Käsper Katholieke Universiteit Leuven SPEED-CC Berlin, October 2009 Emilia Käsper Implementing AES 2000-2010 1/ 31 1 The AES Performance
Implementing AES 2000-2010: performance and security challenges Emilia Käsper Katholieke Universiteit Leuven SPEED-CC Berlin, October 2009 Emilia Käsper Implementing AES 2000-2010 1/ 31 1 The AES Performance
Mo Money, No Problems: Caches #2...
 Mo Money, No Problems: Caches #2... 1 Reminder: Cache Terms... Cache: A small and fast memory used to increase the performance of accessing a big and slow memory Uses temporal locality: The tendency to
Mo Money, No Problems: Caches #2... 1 Reminder: Cache Terms... Cache: A small and fast memory used to increase the performance of accessing a big and slow memory Uses temporal locality: The tendency to
Show Me the $... Performance And Caches
 Show Me the $... Performance And Caches 1 CPU-Cache Interaction (5-stage pipeline) PCen 0x4 Add bubble PC addr inst hit? Primary Instruction Cache IR D To Memory Control Decode, Register Fetch E A B MD1
Show Me the $... Performance And Caches 1 CPU-Cache Interaction (5-stage pipeline) PCen 0x4 Add bubble PC addr inst hit? Primary Instruction Cache IR D To Memory Control Decode, Register Fetch E A B MD1
1 Motivation for Improving Matrix Multiplication
 CS170 Spring 2007 Lecture 7 Feb 6 1 Motivation for Improving Matrix Multiplication Now we will just consider the best way to implement the usual algorithm for matrix multiplication, the one that take 2n
CS170 Spring 2007 Lecture 7 Feb 6 1 Motivation for Improving Matrix Multiplication Now we will just consider the best way to implement the usual algorithm for matrix multiplication, the one that take 2n
Memory management units
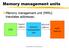 Memory management units Memory management unit (MMU) translates addresses: CPU logical address memory management unit physical address main memory Computers as Components 1 Access time comparison Media
Memory management units Memory management unit (MMU) translates addresses: CPU logical address memory management unit physical address main memory Computers as Components 1 Access time comparison Media
LECTURE 4: LARGE AND FAST: EXPLOITING MEMORY HIERARCHY
 LECTURE 4: LARGE AND FAST: EXPLOITING MEMORY HIERARCHY Abridged version of Patterson & Hennessy (2013):Ch.5 Principle of Locality Programs access a small proportion of their address space at any time Temporal
LECTURE 4: LARGE AND FAST: EXPLOITING MEMORY HIERARCHY Abridged version of Patterson & Hennessy (2013):Ch.5 Principle of Locality Programs access a small proportion of their address space at any time Temporal
Performance analysis basics
 Performance analysis basics Christian Iwainsky Iwainsky@rz.rwth-aachen.de 25.3.2010 1 Overview 1. Motivation 2. Performance analysis basics 3. Measurement Techniques 2 Why bother with performance analysis
Performance analysis basics Christian Iwainsky Iwainsky@rz.rwth-aachen.de 25.3.2010 1 Overview 1. Motivation 2. Performance analysis basics 3. Measurement Techniques 2 Why bother with performance analysis
CPSC 313, 04w Term 2 Midterm Exam 2 Solutions
 1. (10 marks) Short answers. CPSC 313, 04w Term 2 Midterm Exam 2 Solutions Date: March 11, 2005; Instructor: Mike Feeley 1a. Give an example of one important CISC feature that is normally not part of a
1. (10 marks) Short answers. CPSC 313, 04w Term 2 Midterm Exam 2 Solutions Date: March 11, 2005; Instructor: Mike Feeley 1a. Give an example of one important CISC feature that is normally not part of a
Countermeasures against Bernstein s Remote Cache Timing Attack
 Countermeasures against Bernstein s Remote Cache Timing Attack Janaka Alawatugoda, Darshana Jayasinghe, and Roshan Ragel, Member, IEEE Abstract- Cache timing attack is a type of side channel attack where
Countermeasures against Bernstein s Remote Cache Timing Attack Janaka Alawatugoda, Darshana Jayasinghe, and Roshan Ragel, Member, IEEE Abstract- Cache timing attack is a type of side channel attack where
All the AES You Need on Cortex-M3 and M4 Peter Schwabe and Ko Stoffelen
 All the AES You Need on Cortex-M3 and M4 Peter Schwabe and Ko Stoffelen More AES software implementations? AES on AVR [OBSC10] AES on SPARC [BS08] AES on PowerPC [BS08] AES on NVIDIA GPU [OBSC10] AES on
All the AES You Need on Cortex-M3 and M4 Peter Schwabe and Ko Stoffelen More AES software implementations? AES on AVR [OBSC10] AES on SPARC [BS08] AES on PowerPC [BS08] AES on NVIDIA GPU [OBSC10] AES on
Vectorized implementations of post-quantum crypto
 Vectorized implementations of post-quantum crypto Peter Schwabe January 12, 2015 DIMACS Workshop on the Mathematics of Post-Quantum Cryptography The multicore revolution Until early years 2000 each new
Vectorized implementations of post-quantum crypto Peter Schwabe January 12, 2015 DIMACS Workshop on the Mathematics of Post-Quantum Cryptography The multicore revolution Until early years 2000 each new
ChaCha, a variant of Salsa20
 ChaCha, a variant of Salsa20 Daniel J. Bernstein Department of Mathematics, Statistics, and Computer Science (M/C 249) The University of Illinois at Chicago Chicago, IL 60607 7045 snuffle6@box.cr.yp.to
ChaCha, a variant of Salsa20 Daniel J. Bernstein Department of Mathematics, Statistics, and Computer Science (M/C 249) The University of Illinois at Chicago Chicago, IL 60607 7045 snuffle6@box.cr.yp.to
Universität Dortmund. ARM Architecture
 ARM Architecture The RISC Philosophy Original RISC design (e.g. MIPS) aims for high performance through o reduced number of instruction classes o large general-purpose register set o load-store architecture
ARM Architecture The RISC Philosophy Original RISC design (e.g. MIPS) aims for high performance through o reduced number of instruction classes o large general-purpose register set o load-store architecture
CS6303 Computer Architecture Regulation 2013 BE-Computer Science and Engineering III semester 2 MARKS
 CS6303 Computer Architecture Regulation 2013 BE-Computer Science and Engineering III semester 2 MARKS UNIT-I OVERVIEW & INSTRUCTIONS 1. What are the eight great ideas in computer architecture? The eight
CS6303 Computer Architecture Regulation 2013 BE-Computer Science and Engineering III semester 2 MARKS UNIT-I OVERVIEW & INSTRUCTIONS 1. What are the eight great ideas in computer architecture? The eight
Dynamic Control Hazard Avoidance
 Dynamic Control Hazard Avoidance Consider Effects of Increasing the ILP Control dependencies rapidly become the limiting factor they tend to not get optimized by the compiler more instructions/sec ==>
Dynamic Control Hazard Avoidance Consider Effects of Increasing the ILP Control dependencies rapidly become the limiting factor they tend to not get optimized by the compiler more instructions/sec ==>
Latches. IT 3123 Hardware and Software Concepts. Registers. The Little Man has Registers. Data Registers. Program Counter
 IT 3123 Hardware and Software Concepts Notice: This session is being recorded. CPU and Memory June 11 Copyright 2005 by Bob Brown Latches Can store one bit of data Can be ganged together to store more
IT 3123 Hardware and Software Concepts Notice: This session is being recorded. CPU and Memory June 11 Copyright 2005 by Bob Brown Latches Can store one bit of data Can be ganged together to store more
TDT Coarse-Grained Multithreading. Review on ILP. Multi-threaded execution. Contents. Fine-Grained Multithreading
 Review on ILP TDT 4260 Chap 5 TLP & Hierarchy What is ILP? Let the compiler find the ILP Advantages? Disadvantages? Let the HW find the ILP Advantages? Disadvantages? Contents Multi-threading Chap 3.5
Review on ILP TDT 4260 Chap 5 TLP & Hierarchy What is ILP? Let the compiler find the ILP Advantages? Disadvantages? Let the HW find the ILP Advantages? Disadvantages? Contents Multi-threading Chap 3.5
CPU Pipelining Issues
 CPU Pipelining Issues What have you been beating your head against? This pipe stuff makes my head hurt! L17 Pipeline Issues & Memory 1 Pipelining Improve performance by increasing instruction throughput
CPU Pipelining Issues What have you been beating your head against? This pipe stuff makes my head hurt! L17 Pipeline Issues & Memory 1 Pipelining Improve performance by increasing instruction throughput
Cache-timing attack against aes crypto system - countermeasures review
 Edith Cowan University Research Online Australian Information Security Management Conference Conferences, Symposia and Campus Events 2014 Cache-timing attack against aes crypto system - countermeasures
Edith Cowan University Research Online Australian Information Security Management Conference Conferences, Symposia and Campus Events 2014 Cache-timing attack against aes crypto system - countermeasures
Lecture-14 (Memory Hierarchy) CS422-Spring
 Lecture-14 (Memory Hierarchy) CS422-Spring 2018 Biswa@CSE-IITK The Ideal World Instruction Supply Pipeline (Instruction execution) Data Supply - Zero-cycle latency - Infinite capacity - Zero cost - Perfect
Lecture-14 (Memory Hierarchy) CS422-Spring 2018 Biswa@CSE-IITK The Ideal World Instruction Supply Pipeline (Instruction execution) Data Supply - Zero-cycle latency - Infinite capacity - Zero cost - Perfect
Chapter 5 - Input / Output
 Chapter 5 - Input / Output Luis Tarrataca luis.tarrataca@gmail.com CEFET-RJ L. Tarrataca Chapter 5 - Input / Output 1 / 90 1 Motivation 2 Principle of I/O Hardware I/O Devices Device Controllers Memory-Mapped
Chapter 5 - Input / Output Luis Tarrataca luis.tarrataca@gmail.com CEFET-RJ L. Tarrataca Chapter 5 - Input / Output 1 / 90 1 Motivation 2 Principle of I/O Hardware I/O Devices Device Controllers Memory-Mapped
Optimized Scientific Computing:
 Optimized Scientific Computing: Coding Efficiently for Real Computing Architectures Noah Kurinsky SASS Talk, November 11 2015 Introduction Components of a CPU Architecture Design Choices Why Is This Relevant
Optimized Scientific Computing: Coding Efficiently for Real Computing Architectures Noah Kurinsky SASS Talk, November 11 2015 Introduction Components of a CPU Architecture Design Choices Why Is This Relevant
Chapter 2. Parallel Hardware and Parallel Software. An Introduction to Parallel Programming. The Von Neuman Architecture
 An Introduction to Parallel Programming Peter Pacheco Chapter 2 Parallel Hardware and Parallel Software 1 The Von Neuman Architecture Control unit: responsible for deciding which instruction in a program
An Introduction to Parallel Programming Peter Pacheco Chapter 2 Parallel Hardware and Parallel Software 1 The Von Neuman Architecture Control unit: responsible for deciding which instruction in a program
Memory Hierarchy, Fully Associative Caches. Instructor: Nick Riasanovsky
 Memory Hierarchy, Fully Associative Caches Instructor: Nick Riasanovsky Review Hazards reduce effectiveness of pipelining Cause stalls/bubbles Structural Hazards Conflict in use of datapath component Data
Memory Hierarchy, Fully Associative Caches Instructor: Nick Riasanovsky Review Hazards reduce effectiveness of pipelining Cause stalls/bubbles Structural Hazards Conflict in use of datapath component Data
Chapter 13 Reduced Instruction Set Computers
 Chapter 13 Reduced Instruction Set Computers Contents Instruction execution characteristics Use of a large register file Compiler-based register optimization Reduced instruction set architecture RISC pipelining
Chapter 13 Reduced Instruction Set Computers Contents Instruction execution characteristics Use of a large register file Compiler-based register optimization Reduced instruction set architecture RISC pipelining
Multi-level Translation. CS 537 Lecture 9 Paging. Example two-level page table. Multi-level Translation Analysis
 Multi-level Translation CS 57 Lecture 9 Paging Michael Swift Problem: what if you have a sparse address space e.g. out of GB, you use MB spread out need one PTE per page in virtual address space bit AS
Multi-level Translation CS 57 Lecture 9 Paging Michael Swift Problem: what if you have a sparse address space e.g. out of GB, you use MB spread out need one PTE per page in virtual address space bit AS
CS 61C: Great Ideas in Computer Architecture. The Memory Hierarchy, Fully Associative Caches
 CS 61C: Great Ideas in Computer Architecture The Memory Hierarchy, Fully Associative Caches Instructor: Alan Christopher 7/09/2014 Summer 2014 -- Lecture #10 1 Review of Last Lecture Floating point (single
CS 61C: Great Ideas in Computer Architecture The Memory Hierarchy, Fully Associative Caches Instructor: Alan Christopher 7/09/2014 Summer 2014 -- Lecture #10 1 Review of Last Lecture Floating point (single
The CPU and Memory. How does a computer work? How does a computer interact with data? How are instructions performed? Recall schematic diagram:
 The CPU and Memory How does a computer work? How does a computer interact with data? How are instructions performed? Recall schematic diagram: 1 Registers A register is a permanent storage location within
The CPU and Memory How does a computer work? How does a computer interact with data? How are instructions performed? Recall schematic diagram: 1 Registers A register is a permanent storage location within
Key Point. What are Cache lines
 Caching 1 Key Point What are Cache lines Tags Index offset How do we find data in the cache? How do we tell if it s the right data? What decisions do we need to make in designing a cache? What are possible
Caching 1 Key Point What are Cache lines Tags Index offset How do we find data in the cache? How do we tell if it s the right data? What decisions do we need to make in designing a cache? What are possible
Computer Fundamentals and Operating System Theory. By Neil Bloomberg Spring 2017
 Computer Fundamentals and Operating System Theory By Neil Bloomberg Spring 2017 INTRODUCTION This presentation will cover the fundamentals of Computer Operating Systems as a layered architecture using
Computer Fundamentals and Operating System Theory By Neil Bloomberg Spring 2017 INTRODUCTION This presentation will cover the fundamentals of Computer Operating Systems as a layered architecture using
Computer Architecture V Fall Practice Exam Questions
 Computer Architecture V22.0436 Fall 2002 Practice Exam Questions These are practice exam questions for the material covered since the mid-term exam. Please note that the final exam is cumulative. See the
Computer Architecture V22.0436 Fall 2002 Practice Exam Questions These are practice exam questions for the material covered since the mid-term exam. Please note that the final exam is cumulative. See the
Data Speculation. Architecture. Carnegie Mellon School of Computer Science
 Data Speculation Adam Wierman Daniel Neill Lipasti and Shen. Exceeding the dataflow limit, 1996. Sodani and Sohi. Understanding the differences between value prediction and instruction reuse, 1998. 1 A
Data Speculation Adam Wierman Daniel Neill Lipasti and Shen. Exceeding the dataflow limit, 1996. Sodani and Sohi. Understanding the differences between value prediction and instruction reuse, 1998. 1 A
ECE 571 Advanced Microprocessor-Based Design Lecture 4
 ECE 571 Advanced Microprocessor-Based Design Lecture 4 Vince Weaver http://www.eece.maine.edu/~vweaver vincent.weaver@maine.edu 28 January 2016 Homework #1 was due Announcements Homework #2 will be posted
ECE 571 Advanced Microprocessor-Based Design Lecture 4 Vince Weaver http://www.eece.maine.edu/~vweaver vincent.weaver@maine.edu 28 January 2016 Homework #1 was due Announcements Homework #2 will be posted
! Addition! Multiplication! Bigger Example - RSA cryptography
 ! Addition! Multiplication! Bigger Example - RSA cryptography Modular Arithmetic Modular Exponentiation Primality Testing (Fermat s little theorem) Probabilistic algorithm Euclid s Algorithm for gcd (greatest
! Addition! Multiplication! Bigger Example - RSA cryptography Modular Arithmetic Modular Exponentiation Primality Testing (Fermat s little theorem) Probabilistic algorithm Euclid s Algorithm for gcd (greatest
These slides do not give detailed coverage of the material. See class notes and solved problems (last page) for more information.
 11 1 This Set 11 1 These slides do not give detailed coverage of the material. See class notes and solved problems (last page) for more information. Text covers multiple-issue machines in Chapter 4, but
11 1 This Set 11 1 These slides do not give detailed coverage of the material. See class notes and solved problems (last page) for more information. Text covers multiple-issue machines in Chapter 4, but
ASSEMBLY LANGUAGE MACHINE ORGANIZATION
 ASSEMBLY LANGUAGE MACHINE ORGANIZATION CHAPTER 3 1 Sub-topics The topic will cover: Microprocessor architecture CPU processing methods Pipelining Superscalar RISC Multiprocessing Instruction Cycle Instruction
ASSEMBLY LANGUAGE MACHINE ORGANIZATION CHAPTER 3 1 Sub-topics The topic will cover: Microprocessor architecture CPU processing methods Pipelining Superscalar RISC Multiprocessing Instruction Cycle Instruction
The Last Mile An Empirical Study of Timing Channels on sel4
 The Last Mile An Empirical Study of Timing on David Cock Qian Ge Toby Murray Gernot Heiser 4 November 2014 NICTA Funding and Supporting Members and Partners Outline The Last Mile Copyright NICTA 2014 David
The Last Mile An Empirical Study of Timing on David Cock Qian Ge Toby Murray Gernot Heiser 4 November 2014 NICTA Funding and Supporting Members and Partners Outline The Last Mile Copyright NICTA 2014 David
CS Computer Architecture
 CS 35101 Computer Architecture Section 600 Dr. Angela Guercio Fall 2010 An Example Implementation In principle, we could describe the control store in binary, 36 bits per word. We will use a simple symbolic
CS 35101 Computer Architecture Section 600 Dr. Angela Guercio Fall 2010 An Example Implementation In principle, we could describe the control store in binary, 36 bits per word. We will use a simple symbolic
F28HS Hardware-Software Interface: Systems Programming
 F28HS Hardware-Software Interface: Systems Programming Hans-Wolfgang Loidl School of Mathematical and Computer Sciences, Heriot-Watt University, Edinburgh Semester 2 2017/18 0 No proprietary software has
F28HS Hardware-Software Interface: Systems Programming Hans-Wolfgang Loidl School of Mathematical and Computer Sciences, Heriot-Watt University, Edinburgh Semester 2 2017/18 0 No proprietary software has
MARIE: An Introduction to a Simple Computer
 MARIE: An Introduction to a Simple Computer Outline Learn the components common to every modern computer system. Be able to explain how each component contributes to program execution. Understand a simple
MARIE: An Introduction to a Simple Computer Outline Learn the components common to every modern computer system. Be able to explain how each component contributes to program execution. Understand a simple
Memory Technology. Chapter 5. Principle of Locality. Chapter 5 Large and Fast: Exploiting Memory Hierarchy 1
 COMPUTER ORGANIZATION AND DESIGN The Hardware/Software Interface Chapter 5 Large and Fast: Exploiting Memory Hierarchy 5 th Edition Memory Technology Static RAM (SRAM) 0.5ns 2.5ns, $2000 $5000 per GB Dynamic
COMPUTER ORGANIZATION AND DESIGN The Hardware/Software Interface Chapter 5 Large and Fast: Exploiting Memory Hierarchy 5 th Edition Memory Technology Static RAM (SRAM) 0.5ns 2.5ns, $2000 $5000 per GB Dynamic
Chapter 4. MARIE: An Introduction to a Simple Computer
 Chapter 4 MARIE: An Introduction to a Simple Computer Chapter 4 Objectives Learn the components common to every modern computer system. Be able to explain how each component contributes to program execution.
Chapter 4 MARIE: An Introduction to a Simple Computer Chapter 4 Objectives Learn the components common to every modern computer system. Be able to explain how each component contributes to program execution.
SAE5C Computer Organization and Architecture. Unit : I - V
 SAE5C Computer Organization and Architecture Unit : I - V UNIT-I Evolution of Pentium and Power PC Evolution of Computer Components functions Interconnection Bus Basics of PCI Memory:Characteristics,Hierarchy
SAE5C Computer Organization and Architecture Unit : I - V UNIT-I Evolution of Pentium and Power PC Evolution of Computer Components functions Interconnection Bus Basics of PCI Memory:Characteristics,Hierarchy
Blind Differential Cryptanalysis for Enhanced Power Attacks
 Blind Differential Cryptanalysis for Enhanced Power Attacks Bart Preneel COSIC K.U.Leuven - Belgium bart.preneel(at)esat.kuleuven.be Joint work with Helena Handschuh Concept Differential cryptanalysis
Blind Differential Cryptanalysis for Enhanced Power Attacks Bart Preneel COSIC K.U.Leuven - Belgium bart.preneel(at)esat.kuleuven.be Joint work with Helena Handschuh Concept Differential cryptanalysis
BASIC COMPUTER ORGANIZATION. Operating System Concepts 8 th Edition
 BASIC COMPUTER ORGANIZATION Silberschatz, Galvin and Gagne 2009 Topics CPU Structure Registers Memory Hierarchy (L1/L2/L3/RAM) Machine Language Assembly Language Running Process 3.2 Silberschatz, Galvin
BASIC COMPUTER ORGANIZATION Silberschatz, Galvin and Gagne 2009 Topics CPU Structure Registers Memory Hierarchy (L1/L2/L3/RAM) Machine Language Assembly Language Running Process 3.2 Silberschatz, Galvin
CS24: INTRODUCTION TO COMPUTING SYSTEMS. Spring 2017 Lecture 13
 CS24: INTRODUCTION TO COMPUTING SYSTEMS Spring 2017 Lecture 13 COMPUTER MEMORY So far, have viewed computer memory in a very simple way Two memory areas in our computer: The register file Small number
CS24: INTRODUCTION TO COMPUTING SYSTEMS Spring 2017 Lecture 13 COMPUTER MEMORY So far, have viewed computer memory in a very simple way Two memory areas in our computer: The register file Small number
Firmware Updates for Internet of Things Devices
 Firmware Updates for Internet of Things Devices Brendan Moran, Milosch Meriac, Hannes Tschofenig Drafts: draft-moran-suit-architecture draft-moran-suit-manifest 1 WHY DO WE CARE? 2 IoT needs a firmware
Firmware Updates for Internet of Things Devices Brendan Moran, Milosch Meriac, Hannes Tschofenig Drafts: draft-moran-suit-architecture draft-moran-suit-manifest 1 WHY DO WE CARE? 2 IoT needs a firmware
A Review on Cache Memory with Multiprocessor System
 A Review on Cache Memory with Multiprocessor System Chirag R. Patel 1, Rajesh H. Davda 2 1,2 Computer Engineering Department, C. U. Shah College of Engineering & Technology, Wadhwan (Gujarat) Abstract
A Review on Cache Memory with Multiprocessor System Chirag R. Patel 1, Rajesh H. Davda 2 1,2 Computer Engineering Department, C. U. Shah College of Engineering & Technology, Wadhwan (Gujarat) Abstract
Chapter 5B. Large and Fast: Exploiting Memory Hierarchy
 Chapter 5B Large and Fast: Exploiting Memory Hierarchy One Transistor Dynamic RAM 1-T DRAM Cell word access transistor V REF TiN top electrode (V REF ) Ta 2 O 5 dielectric bit Storage capacitor (FET gate,
Chapter 5B Large and Fast: Exploiting Memory Hierarchy One Transistor Dynamic RAM 1-T DRAM Cell word access transistor V REF TiN top electrode (V REF ) Ta 2 O 5 dielectric bit Storage capacitor (FET gate,
Job Posting (Aug. 19) ECE 425. ARM7 Block Diagram. ARM Programming. Assembly Language Programming. ARM Architecture 9/7/2017. Microprocessor Systems
 Job Posting (Aug. 19) ECE 425 Microprocessor Systems TECHNICAL SKILLS: Use software development tools for microcontrollers. Must have experience with verification test languages such as Vera, Specman,
Job Posting (Aug. 19) ECE 425 Microprocessor Systems TECHNICAL SKILLS: Use software development tools for microcontrollers. Must have experience with verification test languages such as Vera, Specman,
Computer Security CS 526
 Computer Security CS 526 Topic 4 Cryptography: Semantic Security, Block Ciphers and Encryption Modes CS555 Topic 4 1 Readings for This Lecture Required reading from wikipedia Block Cipher Ciphertext Indistinguishability
Computer Security CS 526 Topic 4 Cryptography: Semantic Security, Block Ciphers and Encryption Modes CS555 Topic 4 1 Readings for This Lecture Required reading from wikipedia Block Cipher Ciphertext Indistinguishability
CHAPTER 4 MARIE: An Introduction to a Simple Computer
 CHAPTER 4 MARIE: An Introduction to a Simple Computer 4.1 Introduction 177 4.2 CPU Basics and Organization 177 4.2.1 The Registers 178 4.2.2 The ALU 179 4.2.3 The Control Unit 179 4.3 The Bus 179 4.4 Clocks
CHAPTER 4 MARIE: An Introduction to a Simple Computer 4.1 Introduction 177 4.2 CPU Basics and Organization 177 4.2.1 The Registers 178 4.2.2 The ALU 179 4.2.3 The Control Unit 179 4.3 The Bus 179 4.4 Clocks
MARIE: An Introduction to a Simple Computer
 MARIE: An Introduction to a Simple Computer 4.2 CPU Basics The computer s CPU fetches, decodes, and executes program instructions. The two principal parts of the CPU are the datapath and the control unit.
MARIE: An Introduction to a Simple Computer 4.2 CPU Basics The computer s CPU fetches, decodes, and executes program instructions. The two principal parts of the CPU are the datapath and the control unit.
Adapted from instructor s supplementary material from Computer. Patterson & Hennessy, 2008, MK]
![Adapted from instructor s supplementary material from Computer. Patterson & Hennessy, 2008, MK] Adapted from instructor s supplementary material from Computer. Patterson & Hennessy, 2008, MK]](/thumbs/80/82108809.jpg) Lecture 17 Adapted from instructor s supplementary material from Computer Organization and Design, 4th Edition, Patterson & Hennessy, 2008, MK] SRAM / / Flash / RRAM / HDD SRAM / / Flash / RRAM/ HDD SRAM
Lecture 17 Adapted from instructor s supplementary material from Computer Organization and Design, 4th Edition, Patterson & Hennessy, 2008, MK] SRAM / / Flash / RRAM / HDD SRAM / / Flash / RRAM/ HDD SRAM
CS 31: Intro to Systems Caching. Martin Gagne Swarthmore College March 23, 2017
 CS 1: Intro to Systems Caching Martin Gagne Swarthmore College March 2, 2017 Recall A cache is a smaller, faster memory, that holds a subset of a larger (slower) memory We take advantage of locality to
CS 1: Intro to Systems Caching Martin Gagne Swarthmore College March 2, 2017 Recall A cache is a smaller, faster memory, that holds a subset of a larger (slower) memory We take advantage of locality to
Optimising for the p690 memory system
 Optimising for the p690 memory Introduction As with all performance optimisation it is important to understand what is limiting the performance of a code. The Power4 is a very powerful micro-processor
Optimising for the p690 memory Introduction As with all performance optimisation it is important to understand what is limiting the performance of a code. The Power4 is a very powerful micro-processor
 Cache Architectures Design of Digital Circuits 217 Srdjan Capkun Onur Mutlu http://www.syssec.ethz.ch/education/digitaltechnik_17 Adapted from Digital Design and Computer Architecture, David Money Harris
Cache Architectures Design of Digital Circuits 217 Srdjan Capkun Onur Mutlu http://www.syssec.ethz.ch/education/digitaltechnik_17 Adapted from Digital Design and Computer Architecture, David Money Harris
10/16/2017. Miss Rate: ABC. Classifying Misses: 3C Model (Hill) Reducing Conflict Misses: Victim Buffer. Overlapping Misses: Lockup Free Cache
 Classifying Misses: 3C Model (Hill) Divide cache misses into three categories Compulsory (cold): never seen this address before Would miss even in infinite cache Capacity: miss caused because cache is
Classifying Misses: 3C Model (Hill) Divide cache misses into three categories Compulsory (cold): never seen this address before Would miss even in infinite cache Capacity: miss caused because cache is
COMPUTER ORGANIZATION AND DESIGN The Hardware/Software Interface. 5 th. Edition. Chapter 5. Large and Fast: Exploiting Memory Hierarchy
 COMPUTER ORGANIZATION AND DESIGN The Hardware/Software Interface 5 th Edition Chapter 5 Large and Fast: Exploiting Memory Hierarchy Principle of Locality Programs access a small proportion of their address
COMPUTER ORGANIZATION AND DESIGN The Hardware/Software Interface 5 th Edition Chapter 5 Large and Fast: Exploiting Memory Hierarchy Principle of Locality Programs access a small proportion of their address
CISC / RISC. Complex / Reduced Instruction Set Computers
 Systems Architecture CISC / RISC Complex / Reduced Instruction Set Computers CISC / RISC p. 1/12 Instruction Usage Instruction Group Average Usage 1 Data Movement 45.28% 2 Flow Control 28.73% 3 Arithmetic
Systems Architecture CISC / RISC Complex / Reduced Instruction Set Computers CISC / RISC p. 1/12 Instruction Usage Instruction Group Average Usage 1 Data Movement 45.28% 2 Flow Control 28.73% 3 Arithmetic
ECE 471 Embedded Systems Lecture 2
 ECE 471 Embedded Systems Lecture 2 Vince Weaver http://web.eece.maine.edu/~vweaver vincent.weaver@maine.edu 7 September 2018 Announcements Reminder: The class notes are posted to the website. HW#1 will
ECE 471 Embedded Systems Lecture 2 Vince Weaver http://web.eece.maine.edu/~vweaver vincent.weaver@maine.edu 7 September 2018 Announcements Reminder: The class notes are posted to the website. HW#1 will
Performance. CS 3410 Computer System Organization & Programming. [K. Bala, A. Bracy, E. Sirer, and H. Weatherspoon]
![Performance. CS 3410 Computer System Organization & Programming. [K. Bala, A. Bracy, E. Sirer, and H. Weatherspoon] Performance. CS 3410 Computer System Organization & Programming. [K. Bala, A. Bracy, E. Sirer, and H. Weatherspoon]](/thumbs/93/113797768.jpg) Performance CS 3410 Computer System Organization & Programming [K. Bala, A. Bracy, E. Sirer, and H. Weatherspoon] Performance Complex question How fast is the processor? How fast your application runs?
Performance CS 3410 Computer System Organization & Programming [K. Bala, A. Bracy, E. Sirer, and H. Weatherspoon] Performance Complex question How fast is the processor? How fast your application runs?
Computer Systems A Programmer s Perspective 1 (Beta Draft)
 Computer Systems A Programmer s Perspective 1 (Beta Draft) Randal E. Bryant David R. O Hallaron August 1, 2001 1 Copyright c 2001, R. E. Bryant, D. R. O Hallaron. All rights reserved. 2 Contents Preface
Computer Systems A Programmer s Perspective 1 (Beta Draft) Randal E. Bryant David R. O Hallaron August 1, 2001 1 Copyright c 2001, R. E. Bryant, D. R. O Hallaron. All rights reserved. 2 Contents Preface
SOLUTION. Midterm #1 February 26th, 2018 Professor Krste Asanovic Name:
 SOLUTION Notes: CS 152 Computer Architecture and Engineering CS 252 Graduate Computer Architecture Midterm #1 February 26th, 2018 Professor Krste Asanovic Name: I am taking CS152 / CS252 This is a closed
SOLUTION Notes: CS 152 Computer Architecture and Engineering CS 252 Graduate Computer Architecture Midterm #1 February 26th, 2018 Professor Krste Asanovic Name: I am taking CS152 / CS252 This is a closed
EE282 Computer Architecture. Lecture 1: What is Computer Architecture?
 EE282 Computer Architecture Lecture : What is Computer Architecture? September 27, 200 Marc Tremblay Computer Systems Laboratory Stanford University marctrem@csl.stanford.edu Goals Understand how computer
EE282 Computer Architecture Lecture : What is Computer Architecture? September 27, 200 Marc Tremblay Computer Systems Laboratory Stanford University marctrem@csl.stanford.edu Goals Understand how computer
Embedded processors. Timo Töyry Department of Computer Science and Engineering Aalto University, School of Science timo.toyry(at)aalto.
 Embedded processors Timo Töyry Department of Computer Science and Engineering Aalto University, School of Science timo.toyry(at)aalto.fi Comparing processors Evaluating processors Taxonomy of processors
Embedded processors Timo Töyry Department of Computer Science and Engineering Aalto University, School of Science timo.toyry(at)aalto.fi Comparing processors Evaluating processors Taxonomy of processors
Pipelining, Branch Prediction, Trends
 Pipelining, Branch Prediction, Trends 10.1-10.4 Topics 10.1 Quantitative Analyses of Program Execution 10.2 From CISC to RISC 10.3 Pipelining the Datapath Branch Prediction, Delay Slots 10.4 Overlapping
Pipelining, Branch Prediction, Trends 10.1-10.4 Topics 10.1 Quantitative Analyses of Program Execution 10.2 From CISC to RISC 10.3 Pipelining the Datapath Branch Prediction, Delay Slots 10.4 Overlapping
Cache Optimisation. sometime he thought that there must be a better way
 Cache sometime he thought that there must be a better way 2 Cache 1. Reduce miss rate a) Increase block size b) Increase cache size c) Higher associativity d) compiler optimisation e) Parallelism f) prefetching
Cache sometime he thought that there must be a better way 2 Cache 1. Reduce miss rate a) Increase block size b) Increase cache size c) Higher associativity d) compiler optimisation e) Parallelism f) prefetching
Side-Channel Attacks on RSA with CRT. Weakness of RSA Alexander Kozak Jared Vanderbeck
 Side-Channel Attacks on RSA with CRT Weakness of RSA Alexander Kozak Jared Vanderbeck What is RSA? As we all know, RSA (Rivest Shamir Adleman) is a really secure algorithm for public-key cryptography.
Side-Channel Attacks on RSA with CRT Weakness of RSA Alexander Kozak Jared Vanderbeck What is RSA? As we all know, RSA (Rivest Shamir Adleman) is a really secure algorithm for public-key cryptography.
Implementing Practical leakage-resilient symmetric cryptography. University of Illinois at Chicago, Technische Universiteit Eindhoven
 Implementing Practical leakage-resilient symmetric cryptography Daniel J. Bernstein University of Illinois at Chicago, Technische Universiteit Eindhoven CHES 2012 paper Practical leakage-resilient symmetric
Implementing Practical leakage-resilient symmetric cryptography Daniel J. Bernstein University of Illinois at Chicago, Technische Universiteit Eindhoven CHES 2012 paper Practical leakage-resilient symmetric
Hardware Design I Chap. 10 Design of microprocessor
 Hardware Design I Chap. 0 Design of microprocessor E-mail: shimada@is.naist.jp Outline What is microprocessor? Microprocessor from sequential machine viewpoint Microprocessor and Neumann computer Memory
Hardware Design I Chap. 0 Design of microprocessor E-mail: shimada@is.naist.jp Outline What is microprocessor? Microprocessor from sequential machine viewpoint Microprocessor and Neumann computer Memory
Pipelining Exercises, Continued
 Pipelining Exercises, Continued. Spot all data dependencies (including ones that do not lead to stalls). Draw arrows from the stages where data is made available, directed to where it is needed. Circle
Pipelining Exercises, Continued. Spot all data dependencies (including ones that do not lead to stalls). Draw arrows from the stages where data is made available, directed to where it is needed. Circle
CSE 141 Summer 2016 Homework 2
 CSE 141 Summer 2016 Homework 2 PID: Name: 1. A matrix multiplication program can spend 10% of its execution time in reading inputs from a disk, 10% of its execution time in parsing and creating arrays
CSE 141 Summer 2016 Homework 2 PID: Name: 1. A matrix multiplication program can spend 10% of its execution time in reading inputs from a disk, 10% of its execution time in parsing and creating arrays
UNIVERSITY OF MORATUWA CS2052 COMPUTER ARCHITECTURE. Time allowed: 2 Hours 10 min December 2018
 Index No: UNIVERSITY OF MORATUWA Faculty of Engineering Department of Computer Science & Engineering B.Sc. Engineering 2017 Intake Semester 2 Examination CS2052 COMPUTER ARCHITECTURE Time allowed: 2 Hours
Index No: UNIVERSITY OF MORATUWA Faculty of Engineering Department of Computer Science & Engineering B.Sc. Engineering 2017 Intake Semester 2 Examination CS2052 COMPUTER ARCHITECTURE Time allowed: 2 Hours
Course Administration
 Spring 207 EE 363: Computer Organization Chapter 5: Large and Fast: Exploiting Memory Hierarchy - Avinash Kodi Department of Electrical Engineering & Computer Science Ohio University, Athens, Ohio 4570
Spring 207 EE 363: Computer Organization Chapter 5: Large and Fast: Exploiting Memory Hierarchy - Avinash Kodi Department of Electrical Engineering & Computer Science Ohio University, Athens, Ohio 4570
Chapter 5. Large and Fast: Exploiting Memory Hierarchy
 Chapter 5 Large and Fast: Exploiting Memory Hierarchy Principle of Locality Programs access a small proportion of their address space at any time Temporal locality Items accessed recently are likely to
Chapter 5 Large and Fast: Exploiting Memory Hierarchy Principle of Locality Programs access a small proportion of their address space at any time Temporal locality Items accessed recently are likely to
Where Does The Cpu Store The Address Of The
 Where Does The Cpu Store The Address Of The Next Instruction To Be Fetched The three most important buses are the address, the data, and the control buses. The CPU always knows where to find the next instruction
Where Does The Cpu Store The Address Of The Next Instruction To Be Fetched The three most important buses are the address, the data, and the control buses. The CPU always knows where to find the next instruction
Picture of memory. Word FFFFFFFD FFFFFFFE FFFFFFFF
 Memory Sequential circuits all depend upon the presence of memory A flip-flop can store one bit of information A register can store a single word, typically 32-64 bits Memory allows us to store even larger
Memory Sequential circuits all depend upon the presence of memory A flip-flop can store one bit of information A register can store a single word, typically 32-64 bits Memory allows us to store even larger
Memory. From Chapter 3 of High Performance Computing. c R. Leduc
 Memory From Chapter 3 of High Performance Computing c 2002-2004 R. Leduc Memory Even if CPU is infinitely fast, still need to read/write data to memory. Speed of memory increasing much slower than processor
Memory From Chapter 3 of High Performance Computing c 2002-2004 R. Leduc Memory Even if CPU is infinitely fast, still need to read/write data to memory. Speed of memory increasing much slower than processor
CS 31: Introduction to Computer Systems : Threads & Synchronization April 16-18, 2019
 CS 31: Introduction to Computer Systems 22-23: Threads & Synchronization April 16-18, 2019 Making Programs Run Faster We all like how fast computers are In the old days (1980 s - 2005): Algorithm too slow?
CS 31: Introduction to Computer Systems 22-23: Threads & Synchronization April 16-18, 2019 Making Programs Run Faster We all like how fast computers are In the old days (1980 s - 2005): Algorithm too slow?
Reducing Hit Times. Critical Influence on cycle-time or CPI. small is always faster and can be put on chip
 Reducing Hit Times Critical Influence on cycle-time or CPI Keep L1 small and simple small is always faster and can be put on chip interesting compromise is to keep the tags on chip and the block data off
Reducing Hit Times Critical Influence on cycle-time or CPI Keep L1 small and simple small is always faster and can be put on chip interesting compromise is to keep the tags on chip and the block data off
Processors, Performance, and Profiling
 Processors, Performance, and Profiling Architecture 101: 5-Stage Pipeline Fetch Decode Execute Memory Write-Back Registers PC FP ALU Memory Architecture 101 1. Fetch instruction from memory. 2. Decode
Processors, Performance, and Profiling Architecture 101: 5-Stage Pipeline Fetch Decode Execute Memory Write-Back Registers PC FP ALU Memory Architecture 101 1. Fetch instruction from memory. 2. Decode
The Central Processing Unit
 The Central Processing Unit All computers derive from the same basic design, usually referred to as the von Neumann architecture. This concept involves solving a problem by defining a sequence of commands
The Central Processing Unit All computers derive from the same basic design, usually referred to as the von Neumann architecture. This concept involves solving a problem by defining a sequence of commands
15 Sharing Main Memory Segmentation and Paging
 Operating Systems 58 15 Sharing Main Memory Segmentation and Paging Readings for this topic: Anderson/Dahlin Chapter 8 9; Siberschatz/Galvin Chapter 8 9 Simple uniprogramming with a single segment per
Operating Systems 58 15 Sharing Main Memory Segmentation and Paging Readings for this topic: Anderson/Dahlin Chapter 8 9; Siberschatz/Galvin Chapter 8 9 Simple uniprogramming with a single segment per
Marching Memory マーチングメモリ. UCAS-6 6 > Stanford > Imperial > Verify 中村維男 Based on Patent Application by Tadao Nakamura and Michael J.
 UCAS-6 6 > Stanford > Imperial > Verify 2011 Marching Memory マーチングメモリ Tadao Nakamura 中村維男 Based on Patent Application by Tadao Nakamura and Michael J. Flynn 1 Copyright 2010 Tadao Nakamura C-M-C Computer
UCAS-6 6 > Stanford > Imperial > Verify 2011 Marching Memory マーチングメモリ Tadao Nakamura 中村維男 Based on Patent Application by Tadao Nakamura and Michael J. Flynn 1 Copyright 2010 Tadao Nakamura C-M-C Computer
Advanced processor designs
 Advanced processor designs We ve only scratched the surface of CPU design. Today we ll briefly introduce some of the big ideas and big words behind modern processors by looking at two example CPUs. The
Advanced processor designs We ve only scratched the surface of CPU design. Today we ll briefly introduce some of the big ideas and big words behind modern processors by looking at two example CPUs. The
HPC VT Machine-dependent Optimization
 HPC VT 2013 Machine-dependent Optimization Last time Choose good data structures Reduce number of operations Use cheap operations strength reduction Avoid too many small function calls inlining Use compiler
HPC VT 2013 Machine-dependent Optimization Last time Choose good data structures Reduce number of operations Use cheap operations strength reduction Avoid too many small function calls inlining Use compiler
CPE300: Digital System Architecture and Design
 CPE300: Digital System Architecture and Design Fall 2011 MW 17:30-18:45 CBC C316 Number Representation 09212011 http://www.egr.unlv.edu/~b1morris/cpe300/ 2 Outline Recap Logic Circuits for Register Transfer
CPE300: Digital System Architecture and Design Fall 2011 MW 17:30-18:45 CBC C316 Number Representation 09212011 http://www.egr.unlv.edu/~b1morris/cpe300/ 2 Outline Recap Logic Circuits for Register Transfer
UNIT- 5. Chapter 12 Processor Structure and Function
 UNIT- 5 Chapter 12 Processor Structure and Function CPU Structure CPU must: Fetch instructions Interpret instructions Fetch data Process data Write data CPU With Systems Bus CPU Internal Structure Registers
UNIT- 5 Chapter 12 Processor Structure and Function CPU Structure CPU must: Fetch instructions Interpret instructions Fetch data Process data Write data CPU With Systems Bus CPU Internal Structure Registers
