Valkyrie Detectors Tutorial
|
|
|
- Earl Bridges
- 5 years ago
- Views:
Transcription
1 Valkyrie Detectors Tutorial
2 Contents 1. Valkyrie Academia Precise Detectors Precise Detector Types Supported File Types Custom Precise Detector Implementation Detector Language Templates Method Definitions Static Python Detector Static C/C++ Detector Dynamic Python Detector Dynamic C/C++ Detector Hybrid Python Detector Hybrid C/C++ Detector Submission to Valkyrie Academia Constraints Template Detector Files Python Detector Template C++ Detector Template Example Precise Detectors Example Python Detector Example C++ Detector Appendix A: Dynamic Analysis Behaviors Data Appendix B: Dynamic Analysis Dropped Files Data Appendix C: Dynamic Analysis Network Data... 8 ALL RIGHTS RESERVED. 2 / 8
3 1. Valkyrie Academia Valkyrie Academia [1] is an extended version of original Valkyrie [2] service for academicians and community researching malware analysis and different detection techniques. Valkyrie is a cloud based file analysis and classification service, designed with modular analysis services architecture (See Figure- 1), conducting several static and dynamic file analysis. Valkyrie Academia offers researches to integrate their own implemented detection techniques in to the analysis flow and run for each file analysis as Precise Detectors. This document explains, what is a Precise Detector, types of precise detectors, how to implement and submit a new detector, best practices for implementation and constraints. Figure 1 - Analysis Flow 2. Precise Detectors Precise Detector is an implementation of a particular malware detection technique that runs on each file analysis in Valkyrie. Valkyrie provides different data to each detector according to its type, and provides a template class in Python and C++ languages. Following section describes different types of precise detectors, data provided to each one and supported file types in latest Valkyrie Academia version Precise Detector Types There are 3 different detector types that researches can implement and add in to Valkyrie Academia analysis flow, namely: Static Type: This type of detector operates on file's data. Valkyrie provides file's full path that to this detector. Method to be implemented for these type of detectors. Dynamic Type: This type of detector operates on data generated by Dynamic Analysis Hybrid Type: This type of detector uses both data generated by Dynamic Analysis and file's data ALL RIGHTS RESERVED. 3 / 8
4 Each detector type fits in to proper place in analysis flow and is executed when required input data is generated by the system. Implementation details of each type are explained in next sections Supported File Types In current version, only detectors for PE 32/64 file types are supported in Valkyrie Academia. 3. Custom Precise Detector Implementation 3.1. Detector Language There are two different programming language supported by the system, Python / C++: Using python template and implementing related method Using C++ template and implementing related method 3.2. Templates In order to implement own detection technique as precise detector, a researcher must implement one of the related methods in provided detector.py template script or detector.cpp template, as explained in Section 3.3. Also template folders are provided to researchers for both of the language types in compressed format. Once archive file extracted, you will find a main folder called GPD_python/GPD_c_cpp that has template files/folders to be filled by detector owners. Content of this GPD_python/GPD_c_cpp folders are as follows: Python Detector (Provided Archive File: GPD_python.zip) data (Folder): Detector owner may put any data file that detector needs in this folder. detector_codes (Folder): This folder holds all of the custom python scripts and/or sub-folders used by researchers. python_requirements.txt: This is the Python's Virtual Environment dependencies. We will install these via pip and run detector.py using this Virtual Environment. os_requirements.txt: This is the additional Operating System (Ubuntu 16.04) dependencies. We will install these via sudo rights. readme.txt: This is information file that Detector owner provides detector related data. C/C++.so Detector (Provided Archive File: GPD_c_cpp.zip) data (Folder): Detector owner may put any data file that detector needs in this folder. os_requirements.txt: This is the additional Operating System (Ubuntu 16.04) dependencies. We will install these via sudo rights. readme.txt: This is information file that Detector owner provides detector related data Method Definitions Static Python Detector def on_static(self, sha1, filename, sample_filepath): :param sha1: SHA1 of the file, String :param filename: filename seen on client, String :param sample_filepath: full file path that you can read binary data using open, String :return: you must call self.form_json() and provide related parameters ALL RIGHTS RESERVED. 4 / 8
5 ############## IMPLEMENT THIS METHOD DETECTOR TYPE IS STATIC ################ # If your detector type is Static, we will call this method in each analysis ##################################################################### Static C/C++ Detector char * on_static (char *sha1, char *filename, char *filepath) { /* :param sha1: SHA1 of the file, char * :param filename: filename seen on client, char * :param filepath: full file path that you can read binary data using open, char * :return: you must return a string with following format: "{\"verdict\":1, \"sha1\":\"<sha1>\",\"reason\":\"detected the XXX Virus!\"}" */ /* IMPLEMENT THIS METHOD DETECTOR TYPE IS STATIC*/ /* If your detector type is Static, we will call this method in each analysis*/ } Dynamic Python Detector def on_dynamic(self, sha1, filename, all_behaviors_filepath, dropped_files_filepath, network_activity_filepath): :param sha1: SHA1 of the file, String :param filename: filename seen on client, String :param all_behaviors_ filepath: full file path of the behaviors collected in dynamic analysis of the file that you can read using open, String (See: Appendix A) :param dropped_files_filepath: full file path of dropped files information during the analysis that you can read using open, String (See: Appendix B) :param network_activity_filepath: full file path of the network activity of the file that you can read using open, String (See: Appendix C) :return: you must call self.form_json() and provide related parameters ############## IMPLEMENT THIS METHOD DETECTOR TYPE IS DYNAMIC ################ # If your detector type is Dynamic, we will call this method in each analysis when we perform our Dynamic analysis # and generate required data for your detector ##################################################################### Dynamic C/C++ Detector char * on_dynamic char * sha1, char * filename, char * all_behaviors_ filepath, char * dropped_files_filepath, char * network_activity_filepath) { ALL RIGHTS RESERVED. 5 / 8
6 /* :param sha1: SHA1 of the file, char * :param filename: filename seen on client, char * :param all_behaviors_ filepath: full file path of the behavior summary of the file that you can read using open, char * (See: Appendix A) :param dropped_files_filepath: full file path of dropped files information during the analysis that you can read using open, char * (See: Appendix B) :param network_activity_filepath: full file path of the network activity of the file that you can read using open, char * (See: Appendix C) :return: you must return a string with following format: "{\"verdict\":1, \"sha1\":\"<sha1>\",\"reason\":\"detected the XXX Virus!\"}" */ /* IMPLEMENT THIS METHOD DETECTOR TYPE IS DYNAMIC */ /* If your detector type is Dynamic, we will call this method in each analysis when we perform our Dynamic analysis and generate required data for your detector*/ } Hybrid Python Detector def on_hybrid(self, sha1, filename, sample_filepath, all_behaviors_ filepath, dropped_files_filepath, network_activity_filepath): :param sha1: SHA1 of the file, String :param filename: filename seen on client, String :param sample_filepath: full file path that you can read binary data using open, String :param all_behaviors_ filepath: full file path of the behaviors collected in dynamic analysis of the file that you can read using open, String (See: Appendix A) :param dropped_files_filepath: full file path of dropped files information during the analysis that you can read using open, String (See: Appendix B) :param network_activity_filepath: full file path of the network activity of the file that you can read using open, String (See: Appendix C) :return: you must call self.form_json() and provide related parameters ############## IMPLEMENT THIS METHOD DETECTOR TYPE IS DYNAMIC ################ # If your detector type is Dynamic, we will call this method in each analysis when we perform our Dynamic analysis # and generate required data for your detector ##################################################################### Hybrid C/C++ Detector char * on_hybrid char * sha1, char * filename, char *filepath, char * all_behaviors_ filepath, char * dropped_files_filepath, char * network_activity_filepath) { /* :param sha1: SHA1 of the file, char * :param filename: filename seen on client, char * :param filepath: full file path that you can read binary data using open, char * ALL RIGHTS RESERVED. 6 / 8
7 :param all_behaviors_ filepath: full file path of the behavior summary of the file that you can read using open, char * (See: Appendix A) :param dropped_files_filepath: full file path of dropped files information during the analysis that you can read using open, char * (See: Appendix B) :param network_activity_filepath: full file path of the network activity of the file that you can read using open, char * (See: Appendix C) :return: you must return a string with following format: "{\"verdict\":1, \"sha1\":\"<sha1>\",\"reason\":\"detected the XXX Virus!\"}" */ /* IMPLEMENT THIS METHOD DETECTOR TYPE IS DYNAMIC */ /* If your detector type is Dynamic, we will call this method in each analysis when we perform our Dynamic analysis and generate required data for your detector*/ } 3.4. Submission to Valkyrie Academia If detector owner decides to write a detector with python, the following steps should be followed: 1. Related detector type method should be implemented in template detector.py file in detector_codes directory. If there are any extra python script they should also be in detector_codes directory and imports should be in either in same directory or satisfied by requirements. 2. python_requirements.txt and os_requirements.txt files should be filled if necessary. 3. Fields in readme.txt should be filled. 4. Any extra data files, models, etc. should be put in data folder. 5. These files and folders should be zipped with the name GPD_python and be sent to the Valkyrie Academia team. If detector owner decides to write a detector with C/C++, the following steps should be followed: 1. Related detector type method should be implemented in detector.cpp file in detector_codes directory. If there are any extra C++ codes as dependencies, they should also be in detector_codes directory and imports should be in either in same directory or satisfied by requirements. 2. os_requirements.txt files should be filled if necessary. 3. Fields in readme.txt should be filled. 4. Any extra data files, models, etc. should be put in data folder. 5. These files and folders should be zipped with the name GPD_c_cpp and be sent to the Valkyrie Academia team. 4. Constraints Following constraints apply for each detector: No write / execute permission for detector will be given. data folder max. size: 250 MB. max. size of other files and folders except data: 50 MB ALL RIGHTS RESERVED. 7 / 8
8 Each detector has 30 seconds time limit to process given data and provide an output. 5. Template Detector Files 5.1. Python Detector Template See detector.py for python detector template. This is the file mostly researches will use to implement their techniques C++ Detector Template See detector.cpp for C++ detector template. This is the file mostly researches will use to implement their techniques. 6. Example Precise Detectors 6.1. Example Python Detector See static_python_detector_example.py for a dummy python detector written by Valkyrie Academia team to given an insight about python detectors Example C++ Detector See static_cpp_detector_example.cpp for a dummy C++ detector written by Valkyrie Academia team to given an insight about C++ detectors. 7. Appendix A: Dynamic Analysis Behaviors Data See behavior.json file and its content for this dynamic analysis data given to dynamic and hybrid type detectors. 8. Appendix B: Dynamic Analysis Dropped Files Data See dropped.json file and its content for this dynamic analysis data given to dynamic and hybrid type detectors. 9. Appendix C: Dynamic Analysis Network Data See network.json file and its content for this dynamic analysis data given to dynamic and hybrid type detectors. [1] [2] ALL RIGHTS RESERVED. 8 / 8
Homework 01 : Deep learning Tutorial
 Homework 01 : Deep learning Tutorial Introduction to TensorFlow and MLP 1. Introduction You are going to install TensorFlow as a tutorial of deep learning implementation. This instruction will provide
Homework 01 : Deep learning Tutorial Introduction to TensorFlow and MLP 1. Introduction You are going to install TensorFlow as a tutorial of deep learning implementation. This instruction will provide
Moving Materials from Blackboard to Moodle
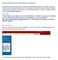 Moving Materials from Blackboard to Moodle Blackboard and Moodle organize course material somewhat differently and the conversion process can be a little messy (but worth it). Because of this, we ve gathered
Moving Materials from Blackboard to Moodle Blackboard and Moodle organize course material somewhat differently and the conversion process can be a little messy (but worth it). Because of this, we ve gathered
HESP PIPELINE v. 1.0
 HESP PIPELINE v. 1.0 Installation and Usage Arun Surya 20/06/2017 1. INSTALLATION The HESP pipeline installation zip file can be downloaded from, https://www.iiap.res.in/hesp/hesp_pipeline.zip. The zip
HESP PIPELINE v. 1.0 Installation and Usage Arun Surya 20/06/2017 1. INSTALLATION The HESP pipeline installation zip file can be downloaded from, https://www.iiap.res.in/hesp/hesp_pipeline.zip. The zip
Metasploit. Installation Guide Release 4.4
 Metasploit Installation Guide Release 4.4 TABLE OF CONTENTS About this Guide Target Audience...1 Organization...1 Document Conventions...1 Support...2 Support for Metasploit Pro and Metasploit Express...2
Metasploit Installation Guide Release 4.4 TABLE OF CONTENTS About this Guide Target Audience...1 Organization...1 Document Conventions...1 Support...2 Support for Metasploit Pro and Metasploit Express...2
Table of contents. Zip Processor 3.0 DMXzone.com
 Table of contents About Zip Processor 3.0... 2 Features In Detail... 3 Before you begin... 6 Installing the extension... 6 The Basics: Automatically Zip an Uploaded File and Download it... 7 Introduction...
Table of contents About Zip Processor 3.0... 2 Features In Detail... 3 Before you begin... 6 Installing the extension... 6 The Basics: Automatically Zip an Uploaded File and Download it... 7 Introduction...
Exporting a Course. This tutorial will explain how to export a course in Blackboard and the difference between exporting and archiving.
 Blackboard Tutorial Exporting a Course This tutorial will explain how to export a course in Blackboard and the difference between exporting and archiving. Exporting vs. Archiving The Export/Archive course
Blackboard Tutorial Exporting a Course This tutorial will explain how to export a course in Blackboard and the difference between exporting and archiving. Exporting vs. Archiving The Export/Archive course
OPIA-ECCU INSTRUCTION STEPS FOR SUBMITTING AND RETRIEVING CARI REPORTS. Once the screen below has loaded, enter your Username, Password and the
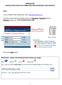 OPIA-ECCU INSTRUCTION STEPS FOR SUBMITTING AND RETRIEVING CARI REPORTS Step 1 In your browser s web address bar, enter: https://ftpw.dhs.state.nj.us/ Once the screen below has loaded, enter your Username,
OPIA-ECCU INSTRUCTION STEPS FOR SUBMITTING AND RETRIEVING CARI REPORTS Step 1 In your browser s web address bar, enter: https://ftpw.dhs.state.nj.us/ Once the screen below has loaded, enter your Username,
The Log packing plugin PRINTED MANUAL
 The Log packing plugin PRINTED MANUAL Log packing plugin All rights reserved. No parts of this work may be reproduced in any form or by any means - graphic, electronic, or mechanical, including photocopying,
The Log packing plugin PRINTED MANUAL Log packing plugin All rights reserved. No parts of this work may be reproduced in any form or by any means - graphic, electronic, or mechanical, including photocopying,
Not For Sale. Offline Scratch Development. Appendix B. Scratch 1.4
 Appendix B Offline Scratch Development If you only have occasional access to the Internet or your Internet access is extremely slow (aka 56k dial-up access), you are going to have a difficult time trying
Appendix B Offline Scratch Development If you only have occasional access to the Internet or your Internet access is extremely slow (aka 56k dial-up access), you are going to have a difficult time trying
IEMS 5722 Mobile Network Programming and Distributed Server Architecture Semester 2
 IEMS 5722 Mobile Network Programming and Distributed Server Architecture 2016-2017 Semester 2 Assignment 3: Developing a Server Application Due Date: 10 th March, 2017 Notes: i.) Read carefully the instructions
IEMS 5722 Mobile Network Programming and Distributed Server Architecture 2016-2017 Semester 2 Assignment 3: Developing a Server Application Due Date: 10 th March, 2017 Notes: i.) Read carefully the instructions
Electronic Records Inventories
 Electronic Records Inventories Published January 2018 CONTACT US Division of Library, Archives and Museum Collections govarc@wisconsinhistory.org 1 Electronic Records Inventories Contents Introduction...
Electronic Records Inventories Published January 2018 CONTACT US Division of Library, Archives and Museum Collections govarc@wisconsinhistory.org 1 Electronic Records Inventories Contents Introduction...
Hi rat. Comodo Valkyrie. Software Version User Guide Guide Version Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013
 Hi rat Comodo Valkyrie Software Version 1.19 User Guide Guide Version 1.19.091217 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1 Introduction to Comodo Valkyrie... 3
Hi rat Comodo Valkyrie Software Version 1.19 User Guide Guide Version 1.19.091217 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1 Introduction to Comodo Valkyrie... 3
Programming Assignment
 Overview Programming Assignment In this assignment, you will program the OpenFlow controller POX and use it to implement two applications. Task 1: Firewall In this part, your task is to implement a layer-2
Overview Programming Assignment In this assignment, you will program the OpenFlow controller POX and use it to implement two applications. Task 1: Firewall In this part, your task is to implement a layer-2
Exercise 6a: Using free and/or open source tools to build workflows to manipulate. LAStools
 Exercise 6a: Using free and/or open source tools to build workflows to manipulate and process LiDAR data: LAStools Christopher Crosby Last Revised: December 1st, 2009 Exercises in this series: 1. LAStools
Exercise 6a: Using free and/or open source tools to build workflows to manipulate and process LiDAR data: LAStools Christopher Crosby Last Revised: December 1st, 2009 Exercises in this series: 1. LAStools
Unzip zip files command line
 Unzip zip files command line The Borg System is 100 % Unzip zip files command line Can I unzip files through the command line? Preferably using open source/free tools. There is a zip/unzip option in the
Unzip zip files command line The Borg System is 100 % Unzip zip files command line Can I unzip files through the command line? Preferably using open source/free tools. There is a zip/unzip option in the
Python Tutorial Ubuntu Pdf Beginners Filetype
 Python Tutorial Ubuntu Pdf Beginners Filetype Note that this is a Python 3 tutorial, which means that most of the examples will not so if you learn one, you should be able to read programs written for
Python Tutorial Ubuntu Pdf Beginners Filetype Note that this is a Python 3 tutorial, which means that most of the examples will not so if you learn one, you should be able to read programs written for
Institutional Records & Archives March 2017 ACCESSIONING FILES FROM EXTERNAL DRIVE
 ACCESSIONING FILES FROM EXTERNAL DRIVE CONTENTS I. Basic Workflow... 1 II. Unique Identifier... 2 III. Write-Blocking... 2 IV. Virus Scans... 4 V. File Transfer... 5 A. Bagger... 5 B. FTK Imager... 5 VI.
ACCESSIONING FILES FROM EXTERNAL DRIVE CONTENTS I. Basic Workflow... 1 II. Unique Identifier... 2 III. Write-Blocking... 2 IV. Virus Scans... 4 V. File Transfer... 5 A. Bagger... 5 B. FTK Imager... 5 VI.
Unzip command in unix
 Unzip command in unix Search 24-4-2015 Howto Extract Zip Files in a Linux and. You need to use the unzip command on a Linux or Unix like system. The nixcraft takes a lot of my time and. 16-4-2010 Howto:
Unzip command in unix Search 24-4-2015 Howto Extract Zip Files in a Linux and. You need to use the unzip command on a Linux or Unix like system. The nixcraft takes a lot of my time and. 16-4-2010 Howto:
Comodo APT Assessment Tool
 rat Comodo APT Assessment Tool Software Version 1.1 Administrator Guide Guide Version 1.1.102815 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1 Introduction to Comodo
rat Comodo APT Assessment Tool Software Version 1.1 Administrator Guide Guide Version 1.1.102815 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1 Introduction to Comodo
CSCI544, Fall 2016: Assignment 1
 CSCI544, Fall 2016: Assignment 1 Due Date: September 23 rd, 4pm. Introduction The goal of this assignment is to get some experience implementing the simple but effective machine learning technique, Naïve
CSCI544, Fall 2016: Assignment 1 Due Date: September 23 rd, 4pm. Introduction The goal of this assignment is to get some experience implementing the simple but effective machine learning technique, Naïve
ClientTrack Administrator Guide Texas Database for Refugee Cash Assistance and Refugee Social Services
 ClientTrack Administrator Guide Texas Database for Refugee Cash Assistance and Refugee Social Services Working Draft Revised December 4, 2017 CONTENTS Disclaimer... 2 About This User Guide... 2 User Management...
ClientTrack Administrator Guide Texas Database for Refugee Cash Assistance and Refugee Social Services Working Draft Revised December 4, 2017 CONTENTS Disclaimer... 2 About This User Guide... 2 User Management...
CSCI 4210 Operating Systems CSCI 6140 Computer Operating Systems Project 2 (document version 1.4) CPU Scheduling Algorithms
 CSCI 4210 Operating Systems CSCI 6140 Computer Operating Systems Project 2 (document version 14) CPU Scheduling Algorithms Overview This project is due by 11:59:59 PM on Monday, October 5, 2015 Projects
CSCI 4210 Operating Systems CSCI 6140 Computer Operating Systems Project 2 (document version 14) CPU Scheduling Algorithms Overview This project is due by 11:59:59 PM on Monday, October 5, 2015 Projects
Project 1 for CMPS 181: Implementing a Paged File Manager
 Project 1 for CMPS 181: Implementing a Paged File Manager Deadline: Sunday, April 23, 2017, 11:59 pm, on Canvas. Introduction In project 1, you will implement a very simple paged file (PF) manager. It
Project 1 for CMPS 181: Implementing a Paged File Manager Deadline: Sunday, April 23, 2017, 11:59 pm, on Canvas. Introduction In project 1, you will implement a very simple paged file (PF) manager. It
Com S 227 Assignment Submission HOWTO
 Com S 227 Assignment Submission HOWTO This document provides detailed instructions on: 1. How to submit an assignment via Canvas and check it 3. How to examine the contents of a zip file 3. How to create
Com S 227 Assignment Submission HOWTO This document provides detailed instructions on: 1. How to submit an assignment via Canvas and check it 3. How to examine the contents of a zip file 3. How to create
143a, Spring 2018 Discussion Week 4 Programming Assignment. Jia Chen 27 Apr 2018
 143a, Spring 2018 Discussion Week 4 Programming Assignment Jia Chen 27 Apr 2018 Setting up Linux environment Setting up Linux environment For Ubuntu or other Linux distribution users sudo apt-get update
143a, Spring 2018 Discussion Week 4 Programming Assignment Jia Chen 27 Apr 2018 Setting up Linux environment Setting up Linux environment For Ubuntu or other Linux distribution users sudo apt-get update
Comodo Unknown File Hunter Software Version 2.1
 rat Comodo Unknown File Hunter Software Version 2.1 Administrator Guide Guide Version 2.1.061118 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1 Introduction to Comodo
rat Comodo Unknown File Hunter Software Version 2.1 Administrator Guide Guide Version 2.1.061118 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1 Introduction to Comodo
CSCI544, Fall 2016: Assignment 2
 CSCI544, Fall 2016: Assignment 2 Due Date: October 28 st, before 4pm. Introduction The goal of this assignment is to get some experience implementing the simple but effective machine learning model, the
CSCI544, Fall 2016: Assignment 2 Due Date: October 28 st, before 4pm. Introduction The goal of this assignment is to get some experience implementing the simple but effective machine learning model, the
OneGate Linux Client. Release Notes. Version Thinspace Technology Ltd Published: 03 JULY Updated:
 OneGate Linux Client Version 4.1.2 Release Notes Thinspace Technology Ltd Published: 03 JULY 2015 Updated: Copyright (c) 2015 Thinspace Technology Ltd. Overview This document outlines the installation
OneGate Linux Client Version 4.1.2 Release Notes Thinspace Technology Ltd Published: 03 JULY 2015 Updated: Copyright (c) 2015 Thinspace Technology Ltd. Overview This document outlines the installation
Files to Contents. User Guide March 11, 2008
 Files 8.3.0 to 8.4.1 User Guide March 11, 2008 Contents Managing files File properties Opening a file or folder Creating a new folder Copying a file or folder Deleting a file or folder Renaming of a file
Files 8.3.0 to 8.4.1 User Guide March 11, 2008 Contents Managing files File properties Opening a file or folder Creating a new folder Copying a file or folder Deleting a file or folder Renaming of a file
STEAM Clown Productions. Python lab. Binary Register. STEAM Clown & Productions Copyright 2017 STEAM Clown. Page 1
 Python lab Binary Register Page 1 Copyright 2017 Overview Introduction Task: Get an input string from the user in the form of 1 s and 0 s and convert it to a list of Integers, and then an actual binary
Python lab Binary Register Page 1 Copyright 2017 Overview Introduction Task: Get an input string from the user in the form of 1 s and 0 s and convert it to a list of Integers, and then an actual binary
Data Science and Machine Learning Essentials
 Data Science and Machine Learning Essentials Lab 2B Transforming Data with Scripts By Graeme Malcolm and Stephen Elston Overview In this lab, you will learn how to use Python or R to manipulate and analyze
Data Science and Machine Learning Essentials Lab 2B Transforming Data with Scripts By Graeme Malcolm and Stephen Elston Overview In this lab, you will learn how to use Python or R to manipulate and analyze
WinZip for Sending Files. Zipping a file
 WinZip for Sending Files You can use WinZip to decrease the space your files take up. This will allow you to send the files in an email, faster. WinZip compresses files by removing any extra space; squishing
WinZip for Sending Files You can use WinZip to decrease the space your files take up. This will allow you to send the files in an email, faster. WinZip compresses files by removing any extra space; squishing
Basic Python 3 Programming (Theory & Practical)
 Basic Python 3 Programming (Theory & Practical) Length Delivery Method : 5 Days : Instructor-led (Classroom) Course Overview This Python 3 Programming training leads the student from the basics of writing
Basic Python 3 Programming (Theory & Practical) Length Delivery Method : 5 Days : Instructor-led (Classroom) Course Overview This Python 3 Programming training leads the student from the basics of writing
INSTALLATION INSTRUCTIONS FOR IPYTHON ENVIRONMENT
 ENGL-S3024 Computational Methods for Literary and Cultural Criticism INSTALLATION INSTRUCTIONS FOR IPYTHON ENVIRONMENT Instructor: Graham Sack CCNMTL: Jonah Bossewitch Anders Pearson OVERVIEW Why am I
ENGL-S3024 Computational Methods for Literary and Cultural Criticism INSTALLATION INSTRUCTIONS FOR IPYTHON ENVIRONMENT Instructor: Graham Sack CCNMTL: Jonah Bossewitch Anders Pearson OVERVIEW Why am I
Core Staff Review Approve with Contingencies
 Core Staff Review Approve with Contingencies Important Information In the event a submission is Approved with Contingencies, extra steps are required to complete the approval process. The basic steps to
Core Staff Review Approve with Contingencies Important Information In the event a submission is Approved with Contingencies, extra steps are required to complete the approval process. The basic steps to
CSC 380/530 Advanced Database Take-Home Midterm Exam (document version 1.0) SQL and PL/SQL
 CSC 380/530 Advanced Database Take-Home Midterm Exam (document version 1.0) SQL and PL/SQL The take-home midterm exam is due by 11:59:59 PM on Thursday, November 5, 2015 and must be submitted electronically.
CSC 380/530 Advanced Database Take-Home Midterm Exam (document version 1.0) SQL and PL/SQL The take-home midterm exam is due by 11:59:59 PM on Thursday, November 5, 2015 and must be submitted electronically.
GigaCentral ios User Guide V2.0. For User and Storage Admin
 V2.0 For User and Storage Admin Copyright 2018 by Inspire-Tech Pte Ltd. All rights reserved. All trademarks or registered trademarks mentioned in this document are properties of their respective owners.
V2.0 For User and Storage Admin Copyright 2018 by Inspire-Tech Pte Ltd. All rights reserved. All trademarks or registered trademarks mentioned in this document are properties of their respective owners.
GUIDE Development tools for Windows(10) installation... 2
 GUIDE Development tools for Windows(10) installation... 2 C\C++ compiler and CMake installation... 2 Mingw download... 2 Mingw installation... 3 Adding Mingw compilers folder to PATH variable... 7 CMake
GUIDE Development tools for Windows(10) installation... 2 C\C++ compiler and CMake installation... 2 Mingw download... 2 Mingw installation... 3 Adding Mingw compilers folder to PATH variable... 7 CMake
The Python Mini-Degree Development Environment Guide
 The Python Mini-Degree Development Environment Guide By Zenva Welcome! We are happy to welcome you to the premiere Python development program available on the web The Python Mini-Degree by Zenva. This
The Python Mini-Degree Development Environment Guide By Zenva Welcome! We are happy to welcome you to the premiere Python development program available on the web The Python Mini-Degree by Zenva. This
Viewing Capture ATP Status
 Capture ATP Viewing Capture ATP Status Configuring Capture ATP Viewing Capture ATP Status Capture ATP > Status About the Chart About the Log Table Uploading a File for Analysis Viewing Threat Reports Capture
Capture ATP Viewing Capture ATP Status Configuring Capture ATP Viewing Capture ATP Status Capture ATP > Status About the Chart About the Log Table Uploading a File for Analysis Viewing Threat Reports Capture
inmailx scales easily to meet the needs of virtually any organization.
 Introduction inmailx is an integrated email management, compliance and productivity solution for Microsoft Outlook, which brings together features and functionality that enable users to effectively manage
Introduction inmailx is an integrated email management, compliance and productivity solution for Microsoft Outlook, which brings together features and functionality that enable users to effectively manage
About the Tutorial. Audience. Prerequisites. Copyright & Disclaimer. Gerrit
 Gerrit About the Tutorial Gerrit is a web-based code review tool, which is integrated with Git and built on top of Git version control system (helps developers to work together and maintain the history
Gerrit About the Tutorial Gerrit is a web-based code review tool, which is integrated with Git and built on top of Git version control system (helps developers to work together and maintain the history
SUREedge MIGRATOR INSTALLATION GUIDE FOR HYPERV
 SUREedge MIGRATOR INSTALLATION GUIDE 5.0.1 FOR HYPERV 2025 Gateway Place, Suite #480, San Jose, CA, 95110 Important Notice This document is provided "as is" without any representations or warranties, express
SUREedge MIGRATOR INSTALLATION GUIDE 5.0.1 FOR HYPERV 2025 Gateway Place, Suite #480, San Jose, CA, 95110 Important Notice This document is provided "as is" without any representations or warranties, express
Deploying Cisco Nexus Data Broker Embedded for OpenFlow
 Deploying Cisco Nexus Data Broker Embedded for OpenFlow This chapter contains the following sections: Obtaining the Cisco Nexus Data Broker Embedded Software for OpenFlow, page 1 Upgrading to Release 3.2.2,
Deploying Cisco Nexus Data Broker Embedded for OpenFlow This chapter contains the following sections: Obtaining the Cisco Nexus Data Broker Embedded Software for OpenFlow, page 1 Upgrading to Release 3.2.2,
SUREedge MIGRATOR INSTALLATION GUIDE FOR NUTANIX ACROPOLIS
 SUREedge MIGRATOR INSTALLATION GUIDE 5.0.1 FOR NUTANIX ACROPOLIS 2025 Gateway Place, Suite #480, San Jose, CA, 95110 Important Notice This document is provided "as is" without any representations or warranties,
SUREedge MIGRATOR INSTALLATION GUIDE 5.0.1 FOR NUTANIX ACROPOLIS 2025 Gateway Place, Suite #480, San Jose, CA, 95110 Important Notice This document is provided "as is" without any representations or warranties,
The following tutorial provides step-by-step instructions and best practices for using My Content and the Course Content file directories.
 OVERVIEW: The content system in Blackboard is the file storage and management system for the support documentation, individual courses, and CityU faculty (course instructors, course managers, builders,
OVERVIEW: The content system in Blackboard is the file storage and management system for the support documentation, individual courses, and CityU faculty (course instructors, course managers, builders,
INTERNATIONALIZATION IN GVIM
 INTERNATIONALIZATION IN GVIM A PROJECT REPORT Submitted by Ms. Nisha Keshav Chaudhari Ms. Monali Eknath Chim In partial fulfillment for the award of the degree Of B. Tech Computer Engineering UNDER THE
INTERNATIONALIZATION IN GVIM A PROJECT REPORT Submitted by Ms. Nisha Keshav Chaudhari Ms. Monali Eknath Chim In partial fulfillment for the award of the degree Of B. Tech Computer Engineering UNDER THE
Quick Start Guide. by Burak Himmetoglu. Supercomputing Consultant. Enterprise Technology Services & Center for Scientific Computing
 Quick Start Guide by Burak Himmetoglu Supercomputing Consultant Enterprise Technology Services & Center for Scientific Computing E-mail: bhimmetoglu@ucsb.edu Linux/Unix basic commands Basic command structure:
Quick Start Guide by Burak Himmetoglu Supercomputing Consultant Enterprise Technology Services & Center for Scientific Computing E-mail: bhimmetoglu@ucsb.edu Linux/Unix basic commands Basic command structure:
Submitting Evidence to the Vault. FRCC CIP Spring Compliance Workshop May 13-16, 2013
 Submitting Evidence to the Vault FRCC CIP Spring Compliance Workshop May 13-16, 2013 Objectives Explain the step-by-step process for submitting evidence to FRCC Vault Share what happens to the evidence
Submitting Evidence to the Vault FRCC CIP Spring Compliance Workshop May 13-16, 2013 Objectives Explain the step-by-step process for submitting evidence to FRCC Vault Share what happens to the evidence
MARKING CANVAS ASSIGNMENTS OFFLINE (INCLUDING MARKING ANONYMOUSLY)
 LEARNING TECHNOLOGY AT LJMU MARKING CANVAS ASSIGNMENTS OFFLINE (INCLUDING MARKING ANONYMOUSLY) Information about Downloading Student Submissions If you want to download all student submissions for an assignment,
LEARNING TECHNOLOGY AT LJMU MARKING CANVAS ASSIGNMENTS OFFLINE (INCLUDING MARKING ANONYMOUSLY) Information about Downloading Student Submissions If you want to download all student submissions for an assignment,
Citrix Analytics Data Governance Collection, storage, and retention of logs generated in connection with Citrix Analytics service.
 Citrix Analytics Data Governance Collection, storage, and retention of logs generated in connection with Citrix Analytics service. Citrix.com Data Governance For up-to-date information visit: This section
Citrix Analytics Data Governance Collection, storage, and retention of logs generated in connection with Citrix Analytics service. Citrix.com Data Governance For up-to-date information visit: This section
Intro to Computer Science Project - Address Book 2
 Intro to Computer Science Project - Address Book 2 ASSIGNMENT OVERVIEW In this assignment, you ll be creating a program called addressbook2.py which allows the user to manage a list of contact information.
Intro to Computer Science Project - Address Book 2 ASSIGNMENT OVERVIEW In this assignment, you ll be creating a program called addressbook2.py which allows the user to manage a list of contact information.
Homework: MIME Diversity in the Text Retrieval Conference (TREC) Polar Dynamic Domain Dataset Due: Friday, March 4, pm PT
 Homework: MIME Diversity in the Text Retrieval Conference (TREC) Polar Dynamic Domain Dataset Due: Friday, March 4, 2016 12pm PT 1. Overview Figure 1: The TREC Dynamic Domain Polar Dataset http://github.com/chrismattmann/trec-dd-polar/
Homework: MIME Diversity in the Text Retrieval Conference (TREC) Polar Dynamic Domain Dataset Due: Friday, March 4, 2016 12pm PT 1. Overview Figure 1: The TREC Dynamic Domain Polar Dataset http://github.com/chrismattmann/trec-dd-polar/
Once you see the screen below click on the MESA Dropbox
 The following provides instructions for uploading competition files to the online dropbox. The dropbox can be used to submit the following MESA competition components: Elementary School SCRATCH Interactive
The following provides instructions for uploading competition files to the online dropbox. The dropbox can be used to submit the following MESA competition components: Elementary School SCRATCH Interactive
CMX: IEEE Clean File Metadata Exchange. Dr. Igor Muttik, McAfee Mark Kennedy, Symantec
 CMX: IEEE Clean File Metadata Exchange Dr. Igor Muttik, McAfee Mark Kennedy, Symantec Who We Represent IEEE ICSG MWG CMX project q IEEE Industry Connections Security Group (ICSG) ¾ Many security companies
CMX: IEEE Clean File Metadata Exchange Dr. Igor Muttik, McAfee Mark Kennedy, Symantec Who We Represent IEEE ICSG MWG CMX project q IEEE Industry Connections Security Group (ICSG) ¾ Many security companies
ID: Sample Name: dronefly.apk Cookbook: default.jbs Time: 10:24:54 Date: 07/06/2018 Version:
 ID: 001 Sample Name: dronefly.apk Cookbook: default.jbs Time: 10:24:4 Date: 0/0/201 Version: 22.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection Confidence
ID: 001 Sample Name: dronefly.apk Cookbook: default.jbs Time: 10:24:4 Date: 0/0/201 Version: 22.0.0 Table of Contents Table of Contents Analysis Report Overview General Information Detection Confidence
SPC Documentation. Release Wesley Brewer
 SPC Documentation Release 0.33 Wesley Brewer Nov 14, 2018 Contents 1 Getting started 3 2 Installing Apps 5 3 Pre-/Post-processing 9 4 User Authentication 11 5 Web Server 13 6 Job Scheduler 15 7 config.py
SPC Documentation Release 0.33 Wesley Brewer Nov 14, 2018 Contents 1 Getting started 3 2 Installing Apps 5 3 Pre-/Post-processing 9 4 User Authentication 11 5 Web Server 13 6 Job Scheduler 15 7 config.py
Project Tracking and Cost Estimation Tool PR
 Project Tracking and Cost Estimation Tool PR20120007 Member Test Plan MAINTAINED BY Cary Frizzell PUBLISHED: May 22, 2012 Copyright 2012 by Southwest Power Pool, Inc. All rights reserved. 1. OVERVIEW...
Project Tracking and Cost Estimation Tool PR20120007 Member Test Plan MAINTAINED BY Cary Frizzell PUBLISHED: May 22, 2012 Copyright 2012 by Southwest Power Pool, Inc. All rights reserved. 1. OVERVIEW...
============================================================
 Release Notes for McAfee(R) VirusScan Enterprise for Linux Version 2.0.0 Hotfix 967083 Copyright (C) 2014 McAfee, Inc. All Rights Reserved. ============================================================
Release Notes for McAfee(R) VirusScan Enterprise for Linux Version 2.0.0 Hotfix 967083 Copyright (C) 2014 McAfee, Inc. All Rights Reserved. ============================================================
SystemTools Software Inc. White Paper Series Reporting NTFS and Share Permissions
 SystemTools Software Inc. White Paper Series Reporting NTFS and Share Permissions SystemTools Software s Tech Support department receives numerous requests asking about permissions reporting, so we ve
SystemTools Software Inc. White Paper Series Reporting NTFS and Share Permissions SystemTools Software s Tech Support department receives numerous requests asking about permissions reporting, so we ve
Quintic Software Tutorial 5A. Video Codec Set-Up
 Quintic Software Tutorial 5A Video Codec Set-Up Contents Page TUTORIALS TUTORIAL 1 TUTORIAL 2 TUTORIAL 3 TUTORIAL 4 TUTORIAL 5A TUTORIAL 5B TUTORIAL 5C TUTORIAL 6A TUTORIAL 6B TUTORIAL 7 TUTORIAL 8 GETTING
Quintic Software Tutorial 5A Video Codec Set-Up Contents Page TUTORIALS TUTORIAL 1 TUTORIAL 2 TUTORIAL 3 TUTORIAL 4 TUTORIAL 5A TUTORIAL 5B TUTORIAL 5C TUTORIAL 6A TUTORIAL 6B TUTORIAL 7 TUTORIAL 8 GETTING
ENVI Py for ArcGIS Documentation
 ENVI Py for ArcGIS Documentation Release 1.0 Exelis Visual Information Solutions, Inc. Nov 14, 2017 Contents 1 System Requirements 3 2 Installation and Configuration 5 2.1 ArcMap..................................................
ENVI Py for ArcGIS Documentation Release 1.0 Exelis Visual Information Solutions, Inc. Nov 14, 2017 Contents 1 System Requirements 3 2 Installation and Configuration 5 2.1 ArcMap..................................................
Binary Analysis Tool
 Binary Analysis Tool Quick Start Guide This tool was developed by: Sponsored by Version 4 Table of Contents Getting and installing the tool...3 Technical requirements...3 Get the tool...3 Confirm it is
Binary Analysis Tool Quick Start Guide This tool was developed by: Sponsored by Version 4 Table of Contents Getting and installing the tool...3 Technical requirements...3 Get the tool...3 Confirm it is
Week 10 Part A MIS 5214
 Week 10 Part A MIS 5214 Agenda Project Authentication Biometrics Access Control Models (DAC Part A) Access Control Techniques Centralized Remote Access Control Technologies Project assignment You and your
Week 10 Part A MIS 5214 Agenda Project Authentication Biometrics Access Control Models (DAC Part A) Access Control Techniques Centralized Remote Access Control Technologies Project assignment You and your
Product Guide. McAfee GetClean. version 2.0
 Product Guide McAfee GetClean version 2.0 About this guide COPYRIGHT LICENSE INFORMATION Copyright 2013-2017 McAfee, LLC. YOUR RIGHTS TO COPY AND RUN THIS TOOL ARE DEFINED BY THE MCAFEE SOFTWARE ROYALTY-FREE
Product Guide McAfee GetClean version 2.0 About this guide COPYRIGHT LICENSE INFORMATION Copyright 2013-2017 McAfee, LLC. YOUR RIGHTS TO COPY AND RUN THIS TOOL ARE DEFINED BY THE MCAFEE SOFTWARE ROYALTY-FREE
rat Comodo Valkyrie Software Version 1.1 Administrator Guide Guide Version Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013
 rat Comodo Valkyrie Software Version 1.1 Administrator Guide Guide Version 1.1.122415 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1 Introduction to Comodo Valkyrie...
rat Comodo Valkyrie Software Version 1.1 Administrator Guide Guide Version 1.1.122415 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1 Introduction to Comodo Valkyrie...
How to Submit Settlement Inquiry Remedy Tickets
 How to Submit Settlement Inquiry Remedy Tickets Defense Finance and Accounting Service Integrity - Service - Innovation BMC REMEDY AR SYSTEM First log into Web Remedy: https://dcii-cat- web.dfas.mil/arsys/forms/fin-ss72z2/home-
How to Submit Settlement Inquiry Remedy Tickets Defense Finance and Accounting Service Integrity - Service - Innovation BMC REMEDY AR SYSTEM First log into Web Remedy: https://dcii-cat- web.dfas.mil/arsys/forms/fin-ss72z2/home-
CIS581: Computer Vision and Computational Photography Project 4, Part B: Convolutional Neural Networks (CNNs) Due: Dec.11, 2017 at 11:59 pm
 CIS581: Computer Vision and Computational Photography Project 4, Part B: Convolutional Neural Networks (CNNs) Due: Dec.11, 2017 at 11:59 pm Instructions CNNs is a team project. The maximum size of a team
CIS581: Computer Vision and Computational Photography Project 4, Part B: Convolutional Neural Networks (CNNs) Due: Dec.11, 2017 at 11:59 pm Instructions CNNs is a team project. The maximum size of a team
Module 3: Changes and Correspondence
 Table of Contents Module 3: Changes and Correspondence Module 3 Objective: Covers how to request application changes and communicate with study team, core staff and reviewers. Important Points: eresearch
Table of Contents Module 3: Changes and Correspondence Module 3 Objective: Covers how to request application changes and communicate with study team, core staff and reviewers. Important Points: eresearch
Kollaborate Server. Installation Guide
 1 Kollaborate Server Installation Guide Kollaborate Server is a local implementation of the Kollaborate cloud workflow system that allows you to run the service in-house on your own server and storage.
1 Kollaborate Server Installation Guide Kollaborate Server is a local implementation of the Kollaborate cloud workflow system that allows you to run the service in-house on your own server and storage.
EE382M 15: Assignment 2
 EE382M 15: Assignment 2 Professor: Lizy K. John TA: Jee Ho Ryoo Department of Electrical and Computer Engineering University of Texas, Austin Due: 11:59PM September 28, 2014 1. Introduction The goal of
EE382M 15: Assignment 2 Professor: Lizy K. John TA: Jee Ho Ryoo Department of Electrical and Computer Engineering University of Texas, Austin Due: 11:59PM September 28, 2014 1. Introduction The goal of
DOMjudge team manual. Summary. Reading and writing. Submitting solutions. Viewing scores, submissions, etc.
 judge DOMjudge team manual Summary /\ DOM DOM judge This page gives a short summary of the system interface. The summary is meant as a quick introduction, to be able to start using the system. It is, however,
judge DOMjudge team manual Summary /\ DOM DOM judge This page gives a short summary of the system interface. The summary is meant as a quick introduction, to be able to start using the system. It is, however,
Movidius Neural Compute Stick
 Movidius Neural Compute Stick You may not use or facilitate the use of this document in connection with any infringement or other legal analysis concerning Intel products described herein. You agree to
Movidius Neural Compute Stick You may not use or facilitate the use of this document in connection with any infringement or other legal analysis concerning Intel products described herein. You agree to
Tizen TCT User Guide
 Tizen 2.3.1 TCT User Guide Table of Contents 1. Environment setup... 3 1.1. Symbols and abbreviations... 3 1.2. Hardware Requirements... 3 1.3. Software Requirements... 3 2. Getting TCT-source and TCT-manager...
Tizen 2.3.1 TCT User Guide Table of Contents 1. Environment setup... 3 1.1. Symbols and abbreviations... 3 1.2. Hardware Requirements... 3 1.3. Software Requirements... 3 2. Getting TCT-source and TCT-manager...
CSCI 311 Spring 2019: Lab 6
 Learning Objectives: Use bootstrap to create a user-responsive page Explore possibilities not covered in class What to hand in: Submit the following files to VIU Learn no later than Feb. 23, 23:59: self-assessment
Learning Objectives: Use bootstrap to create a user-responsive page Explore possibilities not covered in class What to hand in: Submit the following files to VIU Learn no later than Feb. 23, 23:59: self-assessment
Comodo Unknown File Hunter Software Version 5.0
 rat Comodo Unknown File Hunter Software Version 5.0 Administrator Guide Guide Version 5.0.073118 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1 Introduction to Comodo
rat Comodo Unknown File Hunter Software Version 5.0 Administrator Guide Guide Version 5.0.073118 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1 Introduction to Comodo
Assignment 6: Motif Finding Bio5488 2/24/17. Slide Credits: Nicole Rockweiler
 Assignment 6: Motif Finding Bio5488 2/24/17 Slide Credits: Nicole Rockweiler Assignment 6: Motif finding Input Promoter sequences PWMs of DNA-binding proteins Goal Find putative binding sites in the sequences
Assignment 6: Motif Finding Bio5488 2/24/17 Slide Credits: Nicole Rockweiler Assignment 6: Motif finding Input Promoter sequences PWMs of DNA-binding proteins Goal Find putative binding sites in the sequences
Lab Assignment 4 for ECE671 Posted: 11/15/16 Due: 11/29/16. Network Address Translation (NAT) on GENI
 ECE671: Lab Assignment 4 1 Lab Assignment 4 for ECE671 Posted: 11/15/16 Due: 11/29/16 Network Address Translation (NAT) on GENI This assignment builds on assignment 3 and has the goal to introduce you
ECE671: Lab Assignment 4 1 Lab Assignment 4 for ECE671 Posted: 11/15/16 Due: 11/29/16 Network Address Translation (NAT) on GENI This assignment builds on assignment 3 and has the goal to introduce you
7zip command line powershell
 7zip command line powershell This will also work (it's just condensing the previous one into one line): 7za e $ file_path $("-o" + answer. Mar 22, 2016. Powershell Module 7-Zip - 7-Zip commands for PowerShell..
7zip command line powershell This will also work (it's just condensing the previous one into one line): 7za e $ file_path $("-o" + answer. Mar 22, 2016. Powershell Module 7-Zip - 7-Zip commands for PowerShell..
Lab Exercise 3 (part A) Introduction to Mininet
 Lab Exercise 3 (part A) Introduction to Mininet Objectives: Learn the basic commands in Mininet Learn how to create basic network topologies in Mininet Learn Mininet API Marks: This exercise forms the
Lab Exercise 3 (part A) Introduction to Mininet Objectives: Learn the basic commands in Mininet Learn how to create basic network topologies in Mininet Learn Mininet API Marks: This exercise forms the
Homework: Content extraction and search using Apache Tika Employment Postings Dataset contributed via DARPA XDATA Due: October 6, pm PT
 Homework: Content extraction and search using Apache Tika Employment Postings Dataset contributed via DARPA XDATA Due: October 6, 2014 12pm PT 1. Overview Figure 1: Map of Jobs (Colored by Country) In
Homework: Content extraction and search using Apache Tika Employment Postings Dataset contributed via DARPA XDATA Due: October 6, 2014 12pm PT 1. Overview Figure 1: Map of Jobs (Colored by Country) In
Note, you must have Java installed on your computer in order to use Exactly. Download Java here: Installing Exactly
 Exactly: User Guide Exactly is used to safely transfer your files in strict accordance with digital preservation best practices. Before you get started with Exactly, have you discussed with the archive
Exactly: User Guide Exactly is used to safely transfer your files in strict accordance with digital preservation best practices. Before you get started with Exactly, have you discussed with the archive
Newforma Contact Directory Quick Reference Guide
 Newforma Contact Directory Quick Reference Guide This topic provides a reference for the Newforma Contact Directory. Purpose The Newforma Contact Directory gives users access to the central list of companies
Newforma Contact Directory Quick Reference Guide This topic provides a reference for the Newforma Contact Directory. Purpose The Newforma Contact Directory gives users access to the central list of companies
Comodo Client - Security for Linux Software Version 2.2
 Comodo Client - Security for Linux Software Version 2.2 User Guide Guide Version 2.2.091818 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1. Introduction to Comodo Client
Comodo Client - Security for Linux Software Version 2.2 User Guide Guide Version 2.2.091818 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1. Introduction to Comodo Client
ELEC6910Q Analytics and Systems for Social Media and Big Data Applications
 ELEC6910Q Analytics and Systems for Social Media and Big Data Applications Tutorial 1 [Visualization and Data Analytic] Prof. James She james.she@ust.hk 1 Outcomes of this tutorial 1. Basic Task: Visualization
ELEC6910Q Analytics and Systems for Social Media and Big Data Applications Tutorial 1 [Visualization and Data Analytic] Prof. James She james.she@ust.hk 1 Outcomes of this tutorial 1. Basic Task: Visualization
EL2310 Scientific Programming
 Lecture 6: Introduction to C (pronobis@kth.se) Overview Overview Lecture 6: Introduction to C Roots of C Getting started with C Closer look at Hello World Programming Environment Schedule Last time (and
Lecture 6: Introduction to C (pronobis@kth.se) Overview Overview Lecture 6: Introduction to C Roots of C Getting started with C Closer look at Hello World Programming Environment Schedule Last time (and
Computer Systems and -architecture
 Computer Systems and -architecture Project 3: ALU 1 Ba INF 2018-2019 Brent van Bladel brent.vanbladel@uantwerpen.be Don t hesitate to contact the teaching assistant of this course. M.G.305 or by e-mail.
Computer Systems and -architecture Project 3: ALU 1 Ba INF 2018-2019 Brent van Bladel brent.vanbladel@uantwerpen.be Don t hesitate to contact the teaching assistant of this course. M.G.305 or by e-mail.
Drupal Command Line Instructions Windows 7 List All Printers
 Drupal Command Line Instructions Windows 7 List All Printers We won't show you that ad again. Can I configure the Ubuntu print server section of the tutorial via Terminal instead of via GUI. All what you
Drupal Command Line Instructions Windows 7 List All Printers We won't show you that ad again. Can I configure the Ubuntu print server section of the tutorial via Terminal instead of via GUI. All what you
CS155: Computer Security Spring Project #1
 CS155: Computer Security Spring 2018 Project #1 Due: Part 1: Thursday, April 12-11:59pm, Parts 2 and 3: Thursday, April 19-11:59pm. The goal of this assignment is to gain hands-on experience finding vulnerabilities
CS155: Computer Security Spring 2018 Project #1 Due: Part 1: Thursday, April 12-11:59pm, Parts 2 and 3: Thursday, April 19-11:59pm. The goal of this assignment is to gain hands-on experience finding vulnerabilities
Neural Network Compiler BNN Scripts User Guide
 FPGA-UG-02055 Version 1.0 May 2018 Contents 1. Introduction... 3 2. Software Requirements... 3 3. Directory Structure... 3 4. Installation Guide... 4 4.1. Installing Dependencies... 4 4.2. Installing Packages...
FPGA-UG-02055 Version 1.0 May 2018 Contents 1. Introduction... 3 2. Software Requirements... 3 3. Directory Structure... 3 4. Installation Guide... 4 4.1. Installing Dependencies... 4 4.2. Installing Packages...
Upload. OU Campus v10. OmniUpdate, Inc Flynn Road, Suite 100 Camarillo, CA 93012
 Upload v10 OmniUpdate, Inc. 1320 Flynn Road, Suite 100 Camarillo, CA 93012 OmniUpdate, Inc. 1320 Flynn Road, Suite 100 Camarillo, CA 93012 800.362.2605 805.484.9428 (fax) www.omniupdate.com Copyright 2014
Upload v10 OmniUpdate, Inc. 1320 Flynn Road, Suite 100 Camarillo, CA 93012 OmniUpdate, Inc. 1320 Flynn Road, Suite 100 Camarillo, CA 93012 800.362.2605 805.484.9428 (fax) www.omniupdate.com Copyright 2014
Immersion Day. Getting Started with AWS Lambda. August Rev
 Getting Started with AWS Lambda August 2016 Rev 2016-08-19 Table of Contents Overview... 3 AWS Lambda... 3 Amazon S3... 3 Amazon CloudWatch... 3 Handling S3 Events using the AWS Lambda Console... 4 Create
Getting Started with AWS Lambda August 2016 Rev 2016-08-19 Table of Contents Overview... 3 AWS Lambda... 3 Amazon S3... 3 Amazon CloudWatch... 3 Handling S3 Events using the AWS Lambda Console... 4 Create
SpanDisc. U s e r s G u i d e
 SpanDisc U s e r s G u i d e Introduction SpanDisc User s Guide SpanDisc is a complete disc archival and backup solution. SpanDisc uses the automation features or Rimage Corporation s Digital Publishing
SpanDisc U s e r s G u i d e Introduction SpanDisc User s Guide SpanDisc is a complete disc archival and backup solution. SpanDisc uses the automation features or Rimage Corporation s Digital Publishing
Streaming Profile Recipe
 Streaming Profile Recipe Package_Manufacturer_Version Streaming Profile Recipe for Package_Manufacturer_Version Submitted by: Date Submitted: 3/3/2011 11:25:00 AM
Streaming Profile Recipe Package_Manufacturer_Version Streaming Profile Recipe for Package_Manufacturer_Version Submitted by: Date Submitted: 3/3/2011 11:25:00 AM
MOVE AntiVirus page-level reference
 McAfee MOVE AntiVirus 4.7.0 Interface Reference Guide (McAfee epolicy Orchestrator) MOVE AntiVirus page-level reference General page (Configuration tab) Allows you to configure your McAfee epo details,
McAfee MOVE AntiVirus 4.7.0 Interface Reference Guide (McAfee epolicy Orchestrator) MOVE AntiVirus page-level reference General page (Configuration tab) Allows you to configure your McAfee epo details,
1. ECI Hosted Clients Installing Release 6.3 for the First Time (ECI Hosted) Upgrading to Release 6.3SP2 (ECI Hosted)
 1. ECI Hosted Clients........................................................................................... 2 1.1 Installing Release 6.3 for the First Time (ECI Hosted)...........................................................
1. ECI Hosted Clients........................................................................................... 2 1.1 Installing Release 6.3 for the First Time (ECI Hosted)...........................................................
Technical Notes Eclipse Integration version 1.2.1
 .1 Electric Cloud ElectricCommander Technical Notes Eclipse Integration version 1.2.1 September 2010 This document contains information about the ElectricCommander integration with Eclipse for Eclipse
.1 Electric Cloud ElectricCommander Technical Notes Eclipse Integration version 1.2.1 September 2010 This document contains information about the ElectricCommander integration with Eclipse for Eclipse
SmartSolutions Portal User Guide
 SmartSolutions Portal User Guide Managing group permissions Updated 28/04/17 v1 In this guide we will show you how to manage and edit the permissions of other users within your organisation. 1. First,
SmartSolutions Portal User Guide Managing group permissions Updated 28/04/17 v1 In this guide we will show you how to manage and edit the permissions of other users within your organisation. 1. First,
Hydra Installation Manual
 Hydra Installation Manual Table of Contents 1. Introduction...1 2. Download...1 3. Configuration...1 4. Creating the Database...2 5. Importing WordNets...2 6. Known Issues...3 7. Detailed installation
Hydra Installation Manual Table of Contents 1. Introduction...1 2. Download...1 3. Configuration...1 4. Creating the Database...2 5. Importing WordNets...2 6. Known Issues...3 7. Detailed installation
SAS Model Manager 15.1: Quick Start Tutorial
 SAS Model Manager 15.1: Quick Start Tutorial Overview This Quick Start Tutorial is an introduction to some of the primary features of SAS Model Manager. The tutorial covers basic tasks that are related
SAS Model Manager 15.1: Quick Start Tutorial Overview This Quick Start Tutorial is an introduction to some of the primary features of SAS Model Manager. The tutorial covers basic tasks that are related
