Submitting Evidence to the Vault. FRCC CIP Spring Compliance Workshop May 13-16, 2013
|
|
|
- Olivia Stevens
- 5 years ago
- Views:
Transcription
1 Submitting Evidence to the Vault FRCC CIP Spring Compliance Workshop May 13-16, 2013
2 Objectives Explain the step-by-step process for submitting evidence to FRCC Vault Share what happens to the evidence after it is uploaded 2
3 Software Needed You will need the following software to properly secure your evidence: Anti-virus scan: Software used by your company Cryptographic hash utility: MultiHasher along with SHA-1 hashing algorithm File Compression & Encryption Utility: 3
4 Instructions and Password Obtain a copy of the Instructions for Evidence Submittal and your password FRCC website: Compliance tab > Entity Secure File Transfer Click on: Detailed View > Entity Acronym (HVEC) > 2013 CIP Audit* > Instructions for Evidence Submittal folder Items in the folder: o DOC-09 - Instructions for Evidence Submittal o HVEC Password (txt document) Don t wait until the day the evidence is due to start uploading, it takes some time to run the utilities! * Will change depending on the year of the event and the type of Compliance action 4
5 Preparing the Evidence Package Locate the folder on your computer system containing your evidence: Perform a virus check then put the anti-virus scan report or a screen shot into a Text file, Word document or such called: antivirus-check.txt Create a hash listing of ALL your evidence then put the hash file into a Text file, Word document or such called: hash.txt Include the antivirus-check.txt, the hash.txt, and evidence files in the evidence folder to be zipped 5
6 Secure the Evidence Package Create a secure encrypted evidence package Open 7zip software While in your evidence folder, highlight all the evidence files and the 2 documents Click the Add to Archive button o Name the file (see next slide for naming convention) o Enter or paste in the password provided by FRCC o Select Encryption method: AES-256 o Check: Encrypt file names o Click: OK o Your evidence package has been zipped! 6
7 Name the Evidence Package Name the folder as follows: YYYY-MM-DD.NCR00###.XXX.001.7z YYYY-MM-DD is the start date of the audit or the start date of an enforcement or TFE request NCR00### is your Entity s NCR number, which can be found on the NERC website under registry XXX is in reference to whether this evidence if for an O&P (693) or CIP (706) audit, an enforcement request (ENF) or a Technical Feasibility Exception (TFE) 001 is the number for the first package of evidence sent for an audit. Add one (1) every time a new package is sent (002, 003 etc). Note: For Mitigation Plan (MP) requests or Determination Requests (DR) use MP001 or DR001, respectively. 7
8 Upload the Evidence Package Upload your zipped evidence folder Sign-on to the FRCC website Click on Compliance > FRCC Evidence Vault Click on your FRCC Evidence Data Folder XX (XX is number 01 to 10) Copy or move your zipped folder to the Evidence Data Folder; after folder is uploaded, no taking it back A message will appear to notify you that the upload was successful or rejected. Possible reasons for rejection: file size is too big, file name is too long, unpermitted characters in the file name Approx. 15 minutes after being placed in the Evidence Data Folder, your zipped folder should disappear. You re done! 8
9 Where s Your Zipped File? Your zipped file is in transit Your fully encrypted zipped file has been swept to the FRCC Vault staging area Automatic messages go to the ComplianceManager box and the Compliance Administrators personal box 9
10 Where s Your Evidence Stored? Compliance Administrator unzips your zipped evidence file Sends a confirmation receipt to the Entity s primary compliance contact, and Sends an to the Lead Auditor or Enforcement Specialist to let them know the evidence is ready for review. 10
11 Questions? 11
FRCC Secure Transfer & Storage Infrastructure. Training for new data transfer process
 FRCC Secure Transfer & Storage Infrastructure Training for new data transfer process Training Objects Understand the changes in regards to the data transfer process using PKI Installation Key management
FRCC Secure Transfer & Storage Infrastructure Training for new data transfer process Training Objects Understand the changes in regards to the data transfer process using PKI Installation Key management
FRCC Secure Data Transfer. Users Guide V1.5
 FRCC Secure Data Transfer Users Guide V1.5 Table of Contents I. Introduction... 2 II. Part 1 - Software Installation... 3 III. Part 2 - Creating Your PKI Certificate... 7 IV. Part 3 - Importing FRCC Public
FRCC Secure Data Transfer Users Guide V1.5 Table of Contents I. Introduction... 2 II. Part 1 - Software Installation... 3 III. Part 2 - Creating Your PKI Certificate... 7 IV. Part 3 - Importing FRCC Public
CIP 007 Compliance. Kevin B. Perry Dir, Critical Infrastructure Protection
 CIP 007 Compliance Kevin B. Perry Dir, Critical Infrastructure Protection kperry@spp.org 501.614.3251 Agenda CIP 007 Purpose CIP 007 Requirement Overview Past Non Compliance Potential Non Compliance Concerns
CIP 007 Compliance Kevin B. Perry Dir, Critical Infrastructure Protection kperry@spp.org 501.614.3251 Agenda CIP 007 Purpose CIP 007 Requirement Overview Past Non Compliance Potential Non Compliance Concerns
Reliability Standard Audit Worksheet 1
 Reliability Standard Audit Wksheet 1 CIP 007 6 Cyber Security System Security Management This section to be completed by the Compliance Enfcement Authity. Audit ID: Registered Entity: NCR Number: Compliance
Reliability Standard Audit Wksheet 1 CIP 007 6 Cyber Security System Security Management This section to be completed by the Compliance Enfcement Authity. Audit ID: Registered Entity: NCR Number: Compliance
Comprehensive Mitigation
 Comprehensive Mitigation Jenny Anderson Compliance Engineer - CIP janderson.re@spp.org 501.614.3299 July 25, 2013 Goals and Benefits of Mitigation Mitigation should lessen the risk of unintended consequences
Comprehensive Mitigation Jenny Anderson Compliance Engineer - CIP janderson.re@spp.org 501.614.3299 July 25, 2013 Goals and Benefits of Mitigation Mitigation should lessen the risk of unintended consequences
General Use. Searching for Assets (All users) Browsing for Assets (All users) Viewing and Downloading an Asset (All Users)
 User Guide Rev1.1 Table of Contents General Use... 2 Searching for Assets (All users)... 2 Browsing for Assets (All users)... 2 Viewing and Downloading an Asset (All Users)... 2 Downloading Large Files
User Guide Rev1.1 Table of Contents General Use... 2 Searching for Assets (All users)... 2 Browsing for Assets (All users)... 2 Viewing and Downloading an Asset (All Users)... 2 Downloading Large Files
I. Downloading Grades from the Grade Center
 I. Downloading Grades from the Grade Center If you use the Blackboard Grade Center for grading, it is recommended that you download the data from the Grade Center into Excel to keep a backup copy for yourself.
I. Downloading Grades from the Grade Center If you use the Blackboard Grade Center for grading, it is recommended that you download the data from the Grade Center into Excel to keep a backup copy for yourself.
Better Practice Elements for Audit Preparation
 Better Practice Elements for Audit Preparation David Cerasoli, CISSP Manager, CIP Audits John Muir Director, Compliance Monitoring 3/23/2018 1 This presentation will cover the major milestones of an audit,
Better Practice Elements for Audit Preparation David Cerasoli, CISSP Manager, CIP Audits John Muir Director, Compliance Monitoring 3/23/2018 1 This presentation will cover the major milestones of an audit,
Sensitive Data transmission using Outlook
 Sending sensitive data by email using Outlook Purpose Sensitive Data transmission using Outlook This document provides operating instructions for using cryptographic controls to protect sensitive data.
Sending sensitive data by email using Outlook Purpose Sensitive Data transmission using Outlook This document provides operating instructions for using cryptographic controls to protect sensitive data.
Bryan Carr PMP, CISA Compliance Auditor Cyber Security. Audit Evidence & Attachment G CIP 101 Salt Lake City, UT September 25, 2013
 Bryan Carr PMP, CISA Compliance Auditor Cyber Security Audit Evidence & Attachment G CIP 101 Salt Lake City, UT September 25, 2013 About Me Joined WECC in August 2012 Before WECC CIP Compliance Program
Bryan Carr PMP, CISA Compliance Auditor Cyber Security Audit Evidence & Attachment G CIP 101 Salt Lake City, UT September 25, 2013 About Me Joined WECC in August 2012 Before WECC CIP Compliance Program
msis Security Policy and Protocol
 msis Security Policy and Protocol Introduction This Policy details the secure use of msis as a tool for the capture and reporting of internet intelligence and investigations (i3). msis is a powerful i3
msis Security Policy and Protocol Introduction This Policy details the secure use of msis as a tool for the capture and reporting of internet intelligence and investigations (i3). msis is a powerful i3
PCI Compliance Assessment Module
 User Guide PCI Compliance Assessment Module Instructions to Perform a PCI Compliance Assessment V20180316 Network Detective PCI Compliance Module without Inspector User Guide Contents About the Network
User Guide PCI Compliance Assessment Module Instructions to Perform a PCI Compliance Assessment V20180316 Network Detective PCI Compliance Module without Inspector User Guide Contents About the Network
Compliance: Evidence Requests for Low Impact Requirements
 MIDWEST RELIABILITY ORGANIZATION Compliance: Evidence Requests for Low Impact Requirements Jess Syring, CIP Compliance Engineer MRO CIP Low Impact Workshop March 1, 2017 Improving RELIABILITY and mitigating
MIDWEST RELIABILITY ORGANIZATION Compliance: Evidence Requests for Low Impact Requirements Jess Syring, CIP Compliance Engineer MRO CIP Low Impact Workshop March 1, 2017 Improving RELIABILITY and mitigating
BC Timber Sales Supplier s Guide to Browsing TSL Opportunities and e-bidding
 Procurement Services - Ministry of Technology, Innovation and Citizens Services BC Bid System BC Timber Sales Supplier s Guide to Browsing TSL Opportunities and e-bidding NOTE: You must register for an
Procurement Services - Ministry of Technology, Innovation and Citizens Services BC Bid System BC Timber Sales Supplier s Guide to Browsing TSL Opportunities and e-bidding NOTE: You must register for an
Nicolás Vidal, CLABB System Data Manager SDM600. See the unseen from a new perspective
 Nicolás Vidal, CLABB System Data Manager SDM600 See the unseen from a new perspective See the unseen from a new perspective A comprehensive software solution for automatic management of service and cyber
Nicolás Vidal, CLABB System Data Manager SDM600 See the unseen from a new perspective See the unseen from a new perspective A comprehensive software solution for automatic management of service and cyber
CMEP Data Acquisition & Administration (CDAA) Portal User Guide
 CMEP Data Acquisition & Administration (CDAA) Portal User Guide November 5, 2018 Revision 4 1 Table of Contents Introduction... 4 What is the NPCC Compliance Portal ( CDAA )?... 4 How do I access the CDAA?...
CMEP Data Acquisition & Administration (CDAA) Portal User Guide November 5, 2018 Revision 4 1 Table of Contents Introduction... 4 What is the NPCC Compliance Portal ( CDAA )?... 4 How do I access the CDAA?...
Internal Controls Procedure
 Internal Controls Procedure September 30, 2017 MON-114 3000 Bayport Drive, Suite 600 Tampa, Florida 33607-8411 (813) 289-5644 - Phone (813) 289-5646 Fax www.frcc.com Table of Contents Page 3 of 7 Page
Internal Controls Procedure September 30, 2017 MON-114 3000 Bayport Drive, Suite 600 Tampa, Florida 33607-8411 (813) 289-5644 - Phone (813) 289-5646 Fax www.frcc.com Table of Contents Page 3 of 7 Page
Cyber Security Reliability Standards CIP V5 Transition Guidance:
 Cyber Security Reliability Standards CIP V5 Transition Guidance: ERO Compliance and Enforcement Activities during the Transition to the CIP Version 5 Reliability Standards To: Regional Entities and Responsible
Cyber Security Reliability Standards CIP V5 Transition Guidance: ERO Compliance and Enforcement Activities during the Transition to the CIP Version 5 Reliability Standards To: Regional Entities and Responsible
Moving Materials from Blackboard to Moodle
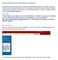 Moving Materials from Blackboard to Moodle Blackboard and Moodle organize course material somewhat differently and the conversion process can be a little messy (but worth it). Because of this, we ve gathered
Moving Materials from Blackboard to Moodle Blackboard and Moodle organize course material somewhat differently and the conversion process can be a little messy (but worth it). Because of this, we ve gathered
Risk-Based Compliance Monitoring & Enforcement Oversight Framework. FRCC Spring Compliance Workshop April 14 16, 2015
 Risk-Based Compliance Monitoring & Enforcement Oversight Framework FRCC Spring Compliance Workshop April 14 16, 2015 Upcoming Events FRCC is Conducting Individual Outreach NERC CIP Version 5 Workshop &
Risk-Based Compliance Monitoring & Enforcement Oversight Framework FRCC Spring Compliance Workshop April 14 16, 2015 Upcoming Events FRCC is Conducting Individual Outreach NERC CIP Version 5 Workshop &
Online Permitting Directions
 1 Online Permitting Directions Please be sure to read the Electronic Plan Submittal Instructions before beginning your online submittal. A paper permit application is NOT required for upload, a permit
1 Online Permitting Directions Please be sure to read the Electronic Plan Submittal Instructions before beginning your online submittal. A paper permit application is NOT required for upload, a permit
Welcome to InSite: A GUIDE TO PROOFING ONLINE. Getting Started Viewing Job Information Uploading Files Viewing Pages Requesting Corrections
 Welcome to InSite: A GUIDE TO PROOFING ONLINE Getting Started Viewing Job Information Uploading Files Viewing Pages Requesting Corrections PROOF.REGISTERGRAPHICS.COM *NOTE: There is no www in this address.
Welcome to InSite: A GUIDE TO PROOFING ONLINE Getting Started Viewing Job Information Uploading Files Viewing Pages Requesting Corrections PROOF.REGISTERGRAPHICS.COM *NOTE: There is no www in this address.
Bell County. E-Discovery Portal. Training Guide. 1/8/2014 Version 1.0
 Bell County E-Discovery Portal Training Guide 1/8/2014 Version 1.0 The E-Discovery portal has been developed to provide the District Attorney s Office with the ability to electronically upload discoverable
Bell County E-Discovery Portal Training Guide 1/8/2014 Version 1.0 The E-Discovery portal has been developed to provide the District Attorney s Office with the ability to electronically upload discoverable
How to Submit Settlement Inquiry Remedy Tickets
 How to Submit Settlement Inquiry Remedy Tickets Defense Finance and Accounting Service Integrity - Service - Innovation BMC REMEDY AR SYSTEM First log into Web Remedy: https://dcii-cat- web.dfas.mil/arsys/forms/fin-ss72z2/home-
How to Submit Settlement Inquiry Remedy Tickets Defense Finance and Accounting Service Integrity - Service - Innovation BMC REMEDY AR SYSTEM First log into Web Remedy: https://dcii-cat- web.dfas.mil/arsys/forms/fin-ss72z2/home-
Reliability Standard Audit Worksheet 1
 Reliability Standard Audit Wksheet 1 CIP-005-6 Cyber Security Electronic Security Perimeter(s) This section to be completed by the Compliance Enfcement Authity. Audit ID: Registered Entity: NCR Number:
Reliability Standard Audit Wksheet 1 CIP-005-6 Cyber Security Electronic Security Perimeter(s) This section to be completed by the Compliance Enfcement Authity. Audit ID: Registered Entity: NCR Number:
CORRECTIVE ACTIONS USER GUIDE FOR SUPPLIERS
 1 CORRECTIVE ACTIONS USER GUIDE FOR SUPPLIERS Contents Table of Contents Step One: Logging Into Repositrak... 2 Step Two: Finding the Audit... 3 Step Three: Entering Corrective Actions... 6 Completing
1 CORRECTIVE ACTIONS USER GUIDE FOR SUPPLIERS Contents Table of Contents Step One: Logging Into Repositrak... 2 Step Two: Finding the Audit... 3 Step Three: Entering Corrective Actions... 6 Completing
OASIS Next Gen Project NCR Management
 OASIS Next Gen Project NCR Management March 31, 2017 V3 Instructions This guidance material was created to provide user instructions for the creation and management of the on-line Non Conformance Report
OASIS Next Gen Project NCR Management March 31, 2017 V3 Instructions This guidance material was created to provide user instructions for the creation and management of the on-line Non Conformance Report
DSG Maintenance Code Description
 DSG Maintenance Code Description 11-14-2015 Index maintenance_director_portal.php maintenance_secretary_portal.php maintenance_submittal_status.php maintenance_emails_folder.php maintenance_dir_submittal_log.php
DSG Maintenance Code Description 11-14-2015 Index maintenance_director_portal.php maintenance_secretary_portal.php maintenance_submittal_status.php maintenance_emails_folder.php maintenance_dir_submittal_log.php
RELID & CDASWEB INSTALLATION GUIDE
 RELID & CDASWEB INSTALLATION GUIDE PART-1: Browser Settings (Recommended) Step-1 on Tools on Internet Options Step-2 on General on Delete Step-3 Uncheck this option Check all options except for the 1 st
RELID & CDASWEB INSTALLATION GUIDE PART-1: Browser Settings (Recommended) Step-1 on Tools on Internet Options Step-2 on General on Delete Step-3 Uncheck this option Check all options except for the 1 st
Table of contents. Zip Processor 3.0 DMXzone.com
 Table of contents About Zip Processor 3.0... 2 Features In Detail... 3 Before you begin... 6 Installing the extension... 6 The Basics: Automatically Zip an Uploaded File and Download it... 7 Introduction...
Table of contents About Zip Processor 3.0... 2 Features In Detail... 3 Before you begin... 6 Installing the extension... 6 The Basics: Automatically Zip an Uploaded File and Download it... 7 Introduction...
PCI Compliance Assessment Module with Inspector
 Quick Start Guide PCI Compliance Assessment Module with Inspector Instructions to Perform a PCI Compliance Assessment Performing a PCI Compliance Assessment (with Inspector) 2 PCI Compliance Assessment
Quick Start Guide PCI Compliance Assessment Module with Inspector Instructions to Perform a PCI Compliance Assessment Performing a PCI Compliance Assessment (with Inspector) 2 PCI Compliance Assessment
Standard CIP 007 4a Cyber Security Systems Security Management
 A. Introduction 1. Title: Cyber Security Systems Security Management 2. Number: CIP-007-4a 3. Purpose: Standard CIP-007-4 requires Responsible Entities to define methods, processes, and procedures for
A. Introduction 1. Title: Cyber Security Systems Security Management 2. Number: CIP-007-4a 3. Purpose: Standard CIP-007-4 requires Responsible Entities to define methods, processes, and procedures for
Standard CIP Cyber Security Systems Security Management
 A. Introduction 1. Title: Cyber Security Systems Security Management 2. Number: CIP-007-4 3. Purpose: Standard CIP-007-4 requires Responsible Entities to define methods, processes, and procedures for securing
A. Introduction 1. Title: Cyber Security Systems Security Management 2. Number: CIP-007-4 3. Purpose: Standard CIP-007-4 requires Responsible Entities to define methods, processes, and procedures for securing
Interactive Remote Access FERC Remote Access Study Compliance Workshop October 27, Eric Weston Compliance Auditor Cyber Security.
 Interactive Remote Access Compliance Workshop October 27, 2016 Eric Weston Compliance Auditor Cyber Security 2 Agenda Interactive Remote Access Overview Review of Use Cases and Strategy 1 Interactive Remote
Interactive Remote Access Compliance Workshop October 27, 2016 Eric Weston Compliance Auditor Cyber Security 2 Agenda Interactive Remote Access Overview Review of Use Cases and Strategy 1 Interactive Remote
Manage Files. Accessing Manage Files
 1 Manage Files The Manage Files tool is a file management system for your course. You can use this tool to organize and upload files associated with your course offering. We recommend that you organize
1 Manage Files The Manage Files tool is a file management system for your course. You can use this tool to organize and upload files associated with your course offering. We recommend that you organize
Reliability Standard Audit Worksheet 1
 Reliability Standard Audit Worksheet 1 PRC-004-3 Protection System Misoperation Identification and Correction This section to be completed by the Compliance Enforcement Authority. Audit ID: Registered
Reliability Standard Audit Worksheet 1 PRC-004-3 Protection System Misoperation Identification and Correction This section to be completed by the Compliance Enforcement Authority. Audit ID: Registered
DRAFT Reliability Standard Audit Worksheet 1
 DRAFT Reliability Standard Audit Worksheet 1 PRC-025-2 Generator Relay Loadability This section to be completed by the Compliance Enforcement Authority. Audit ID: Registered Entity: NCR Number: Compliance
DRAFT Reliability Standard Audit Worksheet 1 PRC-025-2 Generator Relay Loadability This section to be completed by the Compliance Enforcement Authority. Audit ID: Registered Entity: NCR Number: Compliance
RMS Client Guide. AS Audit Process. August 2018
 RMS Client Guide AS Audit Process August 2018 Table of Contents Scheduling/Accepting an Audit Slides 4-6 Audit Planning Documentation Slides 8-10 OASIS Slides 12-14 Scheduling the Next Audit Slide 16 After
RMS Client Guide AS Audit Process August 2018 Table of Contents Scheduling/Accepting an Audit Slides 4-6 Audit Planning Documentation Slides 8-10 OASIS Slides 12-14 Scheduling the Next Audit Slide 16 After
CIP Baseline Configuration Management Overview. FRCC Spring Compliance Workshop April 14-16, 2015
 CIP-010-1 Baseline Configuration Management Overview FRCC Spring Compliance Workshop April 14-16, 2015 Overview Review the configuration change management requirements found in CIP- 10-1 R1 and R2 2 R1.1
CIP-010-1 Baseline Configuration Management Overview FRCC Spring Compliance Workshop April 14-16, 2015 Overview Review the configuration change management requirements found in CIP- 10-1 R1 and R2 2 R1.1
Once you see the screen below click on the MESA Dropbox
 The following provides instructions for uploading competition files to the online dropbox. The dropbox can be used to submit the following MESA competition components: Elementary School SCRATCH Interactive
The following provides instructions for uploading competition files to the online dropbox. The dropbox can be used to submit the following MESA competition components: Elementary School SCRATCH Interactive
NPCC Compliance Monitoring Team Classroom Session
 NPCC Compliance Monitoring Team Classroom Session John Muir - Director, Compliance Monitoring Jacqueline Jimenez - Senior Compliance Engineer David Cerasoli, CISSP - Manager, CIP Audits 5/14/2018 1 Compliance
NPCC Compliance Monitoring Team Classroom Session John Muir - Director, Compliance Monitoring Jacqueline Jimenez - Senior Compliance Engineer David Cerasoli, CISSP - Manager, CIP Audits 5/14/2018 1 Compliance
Exporting a Course. This tutorial will explain how to export a course in Blackboard and the difference between exporting and archiving.
 Blackboard Tutorial Exporting a Course This tutorial will explain how to export a course in Blackboard and the difference between exporting and archiving. Exporting vs. Archiving The Export/Archive course
Blackboard Tutorial Exporting a Course This tutorial will explain how to export a course in Blackboard and the difference between exporting and archiving. Exporting vs. Archiving The Export/Archive course
Version: 4.0. Quatrix Data Sheet. January 2018 Author: Maytech
 Version: 4.0 Quatrix Data Sheet January 2018 Author: Maytech Problem Consumer file sharing services such as Hightail, WeTransfer and Dropbox are causing a massive headache for enterprise IT as BYOFT (bring
Version: 4.0 Quatrix Data Sheet January 2018 Author: Maytech Problem Consumer file sharing services such as Hightail, WeTransfer and Dropbox are causing a massive headache for enterprise IT as BYOFT (bring
PG&E strongly encourages Participants to register with Power Advocate well before Offers are due.
 PG&E strongly encourages Participants to register with Power Advocate well before Offers are due. Registration: All Offer submittal information pertaining to this RFO will be hosted on the Power Advocate
PG&E strongly encourages Participants to register with Power Advocate well before Offers are due. Registration: All Offer submittal information pertaining to this RFO will be hosted on the Power Advocate
Introduction With the move to the digital enterprise, all organizations regulated or not, are required to provide customers and anonymous users alike
 Anonymous Application Access Product Brief Contents Introduction 1 The Safe-T Solution 1 How It Works 2-3 Capabilities 4 Benefits 4 List 5-11 Introduction With the move to the digital enterprise, all organizations
Anonymous Application Access Product Brief Contents Introduction 1 The Safe-T Solution 1 How It Works 2-3 Capabilities 4 Benefits 4 List 5-11 Introduction With the move to the digital enterprise, all organizations
CIP Cyber Security Systems Security Management
 A. Introduction 1. Title: Cyber Security System Security Management 2. Number: CIP-007-5 3. Purpose: To manage system security by specifying select technical, operational, and procedural requirements in
A. Introduction 1. Title: Cyber Security System Security Management 2. Number: CIP-007-5 3. Purpose: To manage system security by specifying select technical, operational, and procedural requirements in
PDA Workspace User Guide
 PDA Workspace User Guide An Introduction to PDA s Online Task Force/Technical Report Team Management and Collaboration Platform Table of Topic Page # Account sign up 3 Finding your group 4-5 Accessing
PDA Workspace User Guide An Introduction to PDA s Online Task Force/Technical Report Team Management and Collaboration Platform Table of Topic Page # Account sign up 3 Finding your group 4-5 Accessing
Critical Infrastructure Protection Version 5
 Critical Infrastructure Protection Version 5 Tobias Whitney, Senior CIP Manager, Grid Assurance, NERC Compliance Committee Open Meeting August 9, 2017 Agenda Critical Infrastructure Protection (CIP) Standards
Critical Infrastructure Protection Version 5 Tobias Whitney, Senior CIP Manager, Grid Assurance, NERC Compliance Committee Open Meeting August 9, 2017 Agenda Critical Infrastructure Protection (CIP) Standards
Standard CIP 007 3a Cyber Security Systems Security Management
 A. Introduction 1. Title: Cyber Security Systems Security Management 2. Number: CIP-007-3a 3. Purpose: Standard CIP-007-3 requires Responsible Entities to define methods, processes, and procedures for
A. Introduction 1. Title: Cyber Security Systems Security Management 2. Number: CIP-007-3a 3. Purpose: Standard CIP-007-3 requires Responsible Entities to define methods, processes, and procedures for
Tier II Portal Tutorial. Latest Revision January
 Tier II Portal Tutorial Latest Revision January 2018 2018 Topics to be covered 1. Creating the Tier2Submit file 2. Accessing the portal 3. Populating the input fields on the portal 4. Uploading your Tier2Submit
Tier II Portal Tutorial Latest Revision January 2018 2018 Topics to be covered 1. Creating the Tier2Submit file 2. Accessing the portal 3. Populating the input fields on the portal 4. Uploading your Tier2Submit
Reliability Standard Audit Worksheet 1
 Reliability Standard Audit Worksheet 1 CIP-006-6 Cyber Security Physical Security of BES Cyber Systems This section to be completed by the Compliance Enforcement Authority. Audit ID: Registered Entity:
Reliability Standard Audit Worksheet 1 CIP-006-6 Cyber Security Physical Security of BES Cyber Systems This section to be completed by the Compliance Enforcement Authority. Audit ID: Registered Entity:
QUICK REFERENCE TO LTCH CARE FILE SUBMISSIONS, SUBMISSION STATUS, AND VALIDATION REPORTS
 A QUICK REFERENCE TO LTCH CARE FILE SUBMISSIONS, SUBMISSION STATUS, AND VALIDATION REPORTS FILE SUBMISSION...2 FILE SUBMISSION STATUS...4 SYSTEM-GENERATED LTCH PROVIDER FINAL VALIDATION REPORT...6 LTCH
A QUICK REFERENCE TO LTCH CARE FILE SUBMISSIONS, SUBMISSION STATUS, AND VALIDATION REPORTS FILE SUBMISSION...2 FILE SUBMISSION STATUS...4 SYSTEM-GENERATED LTCH PROVIDER FINAL VALIDATION REPORT...6 LTCH
Standard CIP Cyber Security Electronic Security Perimeter(s)
 A. Introduction 1. Title: Cyber Security Electronic Security Perimeter(s) 2. Number: CIP-005-2 3. Purpose: Standard CIP-005-2 requires the identification and protection of the Electronic Security Perimeter(s)
A. Introduction 1. Title: Cyber Security Electronic Security Perimeter(s) 2. Number: CIP-005-2 3. Purpose: Standard CIP-005-2 requires the identification and protection of the Electronic Security Perimeter(s)
Reliability Standard Audit Worksheet 1
 Reliability Standard Audit Worksheet 1 CIP-012-1 Cyber Security Communications between Control Centers This section to be completed by the Compliance Enforcement Authority. Audit ID: Registered Entity:
Reliability Standard Audit Worksheet 1 CIP-012-1 Cyber Security Communications between Control Centers This section to be completed by the Compliance Enforcement Authority. Audit ID: Registered Entity:
Internal Controls Evaluation (ICE) Processing
 Internal Controls Evaluation (ICE) September 28, 2017 RAM-102 3000 Bayport Drive, Suite 600 Tampa, Florida 33607-8411 (813) 289-5644 - Phone (813) 289-5646 Fax www.frcc.com Table of Contents Page 3 of
Internal Controls Evaluation (ICE) September 28, 2017 RAM-102 3000 Bayport Drive, Suite 600 Tampa, Florida 33607-8411 (813) 289-5644 - Phone (813) 289-5646 Fax www.frcc.com Table of Contents Page 3 of
BVA LLP Web Portal User Guide
 BVA LLP Web Portal User Guide Opening the Web Portal Website The Web Portal is accessed from the link found on the BVA website homepage: http://www.bvateam.com Web Portal Users Each portal user requires
BVA LLP Web Portal User Guide Opening the Web Portal Website The Web Portal is accessed from the link found on the BVA website homepage: http://www.bvateam.com Web Portal Users Each portal user requires
Self-Certification Tutorial. Version 1.0 April 2013
 Version 1.0 April 2013 The PLAN At the end of this tutorial, you will be able to: 1. Describe the purposes of Self-Certification 2. Identify deadlines 3. Describe the use of the Self-Certification template
Version 1.0 April 2013 The PLAN At the end of this tutorial, you will be able to: 1. Describe the purposes of Self-Certification 2. Identify deadlines 3. Describe the use of the Self-Certification template
HMIS APR v5.1 CSV Export for Sage
 HMIS APR v5.1 CSV Export for Sage The HMIS APR v5.1 CSV Export is designed to meet HUD reporting requirements with the SAGE Repository. It is an export consisting of 65 separate CSV files. Similar to other
HMIS APR v5.1 CSV Export for Sage The HMIS APR v5.1 CSV Export is designed to meet HUD reporting requirements with the SAGE Repository. It is an export consisting of 65 separate CSV files. Similar to other
ELECTRONIC DATA PROCESSOR (EDP) QUICKSTART GUIDE FOR DATA PROVIDERS
 ELECTRONIC DATA PROCESSOR (EDP) QUICKSTART GUIDE FOR DATA PROVIDERS This document provides a quick overview on how to download, install, and use the EQuIS Data Processor (EDP) software to check and submit
ELECTRONIC DATA PROCESSOR (EDP) QUICKSTART GUIDE FOR DATA PROVIDERS This document provides a quick overview on how to download, install, and use the EQuIS Data Processor (EDP) software to check and submit
DIGITAL FORENSIC PROCEDURE. Procedure Name: Mounting an EnCase E01 Logical Image file with FTK Imager. Category: Image Mounting
 DIGITAL FORENSIC PROCEDURE Procedure Name: Mounting an EnCase E01 Logical Image file with FTK Imager Category: Image Mounting Procedure Development Development Owner Mr. O Organization DFIR Team Document
DIGITAL FORENSIC PROCEDURE Procedure Name: Mounting an EnCase E01 Logical Image file with FTK Imager Category: Image Mounting Procedure Development Development Owner Mr. O Organization DFIR Team Document
Instructions for Migrating (importing) Data to CTAS 2018 (or later) from CTAS 7
 Instructions for Migrating (importing) Data to CTAS 2018 (or later) from CTAS 7 Office of the State Auditor Website: http://www.osa.state.mn.us/ IMPORTANT: Install the most current version of CTAS on your
Instructions for Migrating (importing) Data to CTAS 2018 (or later) from CTAS 7 Office of the State Auditor Website: http://www.osa.state.mn.us/ IMPORTANT: Install the most current version of CTAS on your
Analysis of CIP-006 and CIP-007 Violations
 Electric Reliability Organization (ERO) Compliance Analysis Report Reliability Standard CIP-006 Physical Security of Critical Cyber Assets Reliability Standard CIP-007 Systems Security Management December
Electric Reliability Organization (ERO) Compliance Analysis Report Reliability Standard CIP-006 Physical Security of Critical Cyber Assets Reliability Standard CIP-007 Systems Security Management December
Security Architecture
 Security Architecture RDX s top priority is to safeguard our customers sensitive information. Introduction RDX understands that our customers have turned over the keys to their sensitive data stores to
Security Architecture RDX s top priority is to safeguard our customers sensitive information. Introduction RDX understands that our customers have turned over the keys to their sensitive data stores to
TREENO ELECTRONIC DOCUMENT MANAGEMENT. Administration Guide
 TREENO ELECTRONIC DOCUMENT MANAGEMENT Administration Guide February 2012 Contents Introduction... 8 About This Guide... 9 About Treeno... 9 Managing Security... 10 Treeno Security Overview... 10 Administrator
TREENO ELECTRONIC DOCUMENT MANAGEMENT Administration Guide February 2012 Contents Introduction... 8 About This Guide... 9 About Treeno... 9 Managing Security... 10 Treeno Security Overview... 10 Administrator
A Lakeside Software White Paper February SysTrack Community: How-to and FAQ
 A Lakeside Software White Paper February 2016 SysTrack Community: How-to and FAQ 2 SysTrack Community: How-to and FAQ Table of Contents Introduction... 3 Operating Principles... 3 Data Sharing... 3 Data
A Lakeside Software White Paper February 2016 SysTrack Community: How-to and FAQ 2 SysTrack Community: How-to and FAQ Table of Contents Introduction... 3 Operating Principles... 3 Data Sharing... 3 Data
Arkansas All-Payer Claims Database (APCD) Onboarding Packet
 Arkansas All-Payer Claims Database (APCD) Onboarding Packet October 2018 Introduction The onboarding packet contains information for submitting entities (SEs) to establish connectivity for secure data
Arkansas All-Payer Claims Database (APCD) Onboarding Packet October 2018 Introduction The onboarding packet contains information for submitting entities (SEs) to establish connectivity for secure data
Standard CIP 005 2a Cyber Security Electronic Security Perimeter(s)
 A. Introduction 1. Title: Cyber Security Electronic Security Perimeter(s) 2. Number: CIP-005-2a 3. Purpose: Standard CIP-005-2 requires the identification and protection of the Electronic Security Perimeter(s)
A. Introduction 1. Title: Cyber Security Electronic Security Perimeter(s) 2. Number: CIP-005-2a 3. Purpose: Standard CIP-005-2 requires the identification and protection of the Electronic Security Perimeter(s)
Reliability Standard Audit Worksheet 1
 Reliability Standard Audit Worksheet 1 PRC-004-3 Protection System Misoperation Identification and Correction This section to be completed by the Compliance Enforcement Authority. Audit ID: Registered
Reliability Standard Audit Worksheet 1 PRC-004-3 Protection System Misoperation Identification and Correction This section to be completed by the Compliance Enforcement Authority. Audit ID: Registered
THCIC 837 Electronic File Processing Tests and Production
 Purpose: The purpose of testing the electronic data files is to ensure the file format is compatible with the THCIC System and includes all required data fields. Before beginning the testing of data files,
Purpose: The purpose of testing the electronic data files is to ensure the file format is compatible with the THCIC System and includes all required data fields. Before beginning the testing of data files,
Arizona Talking Book Library. BARD Submittal Process
 Arizona Talking Book Library BARD Submittal Process Maria Pina, Brian Blackwell & Mary Alyce Grube 1-30-2018 Contents Introduction... 1 Compress the Files... 1 Upload into BARD... 2 Verify Upload is Correct...
Arizona Talking Book Library BARD Submittal Process Maria Pina, Brian Blackwell & Mary Alyce Grube 1-30-2018 Contents Introduction... 1 Compress the Files... 1 Upload into BARD... 2 Verify Upload is Correct...
Standard CIP Cyber Security Systems Security Management
 A. Introduction 1. Title: Cyber Security Systems Security Management 2. Number: CIP-007-1 3. Purpose: Standard CIP-007 requires Responsible Entities to define methods, processes, and procedures for securing
A. Introduction 1. Title: Cyber Security Systems Security Management 2. Number: CIP-007-1 3. Purpose: Standard CIP-007 requires Responsible Entities to define methods, processes, and procedures for securing
The e-doc Manger. The e-doc Manager. Date and Time Stamps
 The e-doc Manger The e-doc Manager The e-doc Manager is the digital document folder for a loan file. All of a loan s files and documents are digitally stored in the e-doc Manager. To access a loan s e-doc
The e-doc Manger The e-doc Manager The e-doc Manager is the digital document folder for a loan file. All of a loan s files and documents are digitally stored in the e-doc Manager. To access a loan s e-doc
OPIA-ECCU INSTRUCTION STEPS FOR SUBMITTING AND RETRIEVING CARI REPORTS. Once the screen below has loaded, enter your Username, Password and the
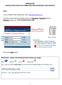 OPIA-ECCU INSTRUCTION STEPS FOR SUBMITTING AND RETRIEVING CARI REPORTS Step 1 In your browser s web address bar, enter: https://ftpw.dhs.state.nj.us/ Once the screen below has loaded, enter your Username,
OPIA-ECCU INSTRUCTION STEPS FOR SUBMITTING AND RETRIEVING CARI REPORTS Step 1 In your browser s web address bar, enter: https://ftpw.dhs.state.nj.us/ Once the screen below has loaded, enter your Username,
Introduction to Dropbox Management Add a Category Add a Folder Set Availability for Dropbox Folders Add Special Access...
 Dropbox Introduction to Dropbox Management... 2 Add a Category... 3 Add a Folder... 4 Set Availability for Dropbox Folders... 8 Add Special Access... 10 Reorder Folders and Categories... 12 Delete a Folder...
Dropbox Introduction to Dropbox Management... 2 Add a Category... 3 Add a Folder... 4 Set Availability for Dropbox Folders... 8 Add Special Access... 10 Reorder Folders and Categories... 12 Delete a Folder...
TAX REPORTING SUITE MODULE IDES VERSION 1712
 TAX REPORTING SUITE MODULE IDES VERSION 1712 USERS S MANUAL Published: Jan 2018 For the latest information and to leave feedback, please visit Vogele IT-Services at http://www.section11.ch. 2 The information
TAX REPORTING SUITE MODULE IDES VERSION 1712 USERS S MANUAL Published: Jan 2018 For the latest information and to leave feedback, please visit Vogele IT-Services at http://www.section11.ch. 2 The information
Turnitin assignments are added from the course s home page. To open the course home page, click on the course from the Moodle start page.
 Guides.turnitin.com Creating a Turnitin Assignment Creating a PeerMark Assignment Submitting Papers The Turnitin Assignment Inbox GradeMark Viewing the PeerMark Assignment Inbox Assignment Inbox Navigation
Guides.turnitin.com Creating a Turnitin Assignment Creating a PeerMark Assignment Submitting Papers The Turnitin Assignment Inbox GradeMark Viewing the PeerMark Assignment Inbox Assignment Inbox Navigation
1. After turning Edit Mode On at the top right of the Contents page, select Turnitin Assignment using the Create Assessment pull down menu
 Guides.turnitin.com Creating a Turnitin Assignment Revision Assignments Creating a PeerMark Assignment Submitting Papers The Turnitin Assignment Inbox Viewing the PeerMark Assignment Inbox Glossary 1 Creating
Guides.turnitin.com Creating a Turnitin Assignment Revision Assignments Creating a PeerMark Assignment Submitting Papers The Turnitin Assignment Inbox Viewing the PeerMark Assignment Inbox Glossary 1 Creating
PDA Workspace. (powered by Kavi ) An Introduction to PDA s Online Task Force/Technical Report Team Management and Collaboration Platform
 PDA Workspace (powered by Kavi ) An Introduction to PDA s Online Task Force/Technical Report Team Management and Collaboration Platform Table Topic Slide # Overview 3-4 Accessing the site 5-11 Landing
PDA Workspace (powered by Kavi ) An Introduction to PDA s Online Task Force/Technical Report Team Management and Collaboration Platform Table Topic Slide # Overview 3-4 Accessing the site 5-11 Landing
Taxpayer Secure Portal Instructions
 Taxpayer Secure Portal Instructions Secure Portal Walk-Through (External User) Secure Portal is an email solution that allows you to exchange email containing Personally Identifiable Information with your
Taxpayer Secure Portal Instructions Secure Portal Walk-Through (External User) Secure Portal is an email solution that allows you to exchange email containing Personally Identifiable Information with your
Creating Interactive Video with Camtasia
 Creating Interactive Video with Camtasia Audio SCORM Quizzes PowerPoint and Screen Shots v1.2: 2009 Page 1 Camtasia Studio 6.0.2 http://www.techsmith.com/camtasia.asp (free trial download) Table of Contents
Creating Interactive Video with Camtasia Audio SCORM Quizzes PowerPoint and Screen Shots v1.2: 2009 Page 1 Camtasia Studio 6.0.2 http://www.techsmith.com/camtasia.asp (free trial download) Table of Contents
I-MINDS USER MANUAL. Download and Install I-MINDS
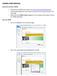 I-MINDS USER MANUAL Download and Install I-MINDS Running I-MINDS Download the I-MINDS Student Agent from http://cse.unl.edu/~knobel/i-minds Unzip the downloaded file in your local drive (Your Z: drive
I-MINDS USER MANUAL Download and Install I-MINDS Running I-MINDS Download the I-MINDS Student Agent from http://cse.unl.edu/~knobel/i-minds Unzip the downloaded file in your local drive (Your Z: drive
IceWarp Unified Communications. AntiVirus Reference. Version 10.4
 IceWarp Unified Communications AntiVirus Reference Version 10.4 Printed on 30 November, 2012 Contents AntiVirus 1 Anti-Virus... 2 Latest Avast! Engine... 2 Kaspersky Anti-Virus Support... 2 Support for
IceWarp Unified Communications AntiVirus Reference Version 10.4 Printed on 30 November, 2012 Contents AntiVirus 1 Anti-Virus... 2 Latest Avast! Engine... 2 Kaspersky Anti-Virus Support... 2 Support for
WinZip for Android User Guide
 WinZip for Android User Guide WinZip for Android is available from Google Play and Amazon as a free version with a limited feature set. It can be converted to the full version by an in-app purchase. WinZip
WinZip for Android User Guide WinZip for Android is available from Google Play and Amazon as a free version with a limited feature set. It can be converted to the full version by an in-app purchase. WinZip
Supplier User Guide - Postbox
 Supplier User Guide - Postbox Page 1 Table of Contents What is the Postbox?... 3 Postbox Response Workspace... 3 Notice Response List... 4 Dispatched List... 5 Postbox Response Creation... 7 Create Postbox
Supplier User Guide - Postbox Page 1 Table of Contents What is the Postbox?... 3 Postbox Response Workspace... 3 Notice Response List... 4 Dispatched List... 5 Postbox Response Creation... 7 Create Postbox
Unofficial Comment Form for Interpretation of CIP-007-3, Requirement R5, for ITC (Project 2012-INT-04)
 Unofficial Comment Form for Interpretation of, Requirement R5, for ITC (Project 2012-INT-04) Project 2012-INT-04 Interpretation for ITC Unofficial Comment Form Project 2012-INT-04 Interpretation of Applicability
Unofficial Comment Form for Interpretation of, Requirement R5, for ITC (Project 2012-INT-04) Project 2012-INT-04 Interpretation for ITC Unofficial Comment Form Project 2012-INT-04 Interpretation of Applicability
GUIDE. MetaDefender Kiosk Deployment Guide
 GUIDE MetaDefender Kiosk Deployment Guide 1 SECTION 1.0 Recommended Deployment of MetaDefender Kiosk(s) OPSWAT s MetaDefender Kiosk product is deployed by organizations to scan portable media and detect
GUIDE MetaDefender Kiosk Deployment Guide 1 SECTION 1.0 Recommended Deployment of MetaDefender Kiosk(s) OPSWAT s MetaDefender Kiosk product is deployed by organizations to scan portable media and detect
Install Kaspersky Endpoint Security for Mac Version b (This user guide is applicable to Mac OS X 10.9 macos )
 Install Kaspersky Endpoint Security for Mac Version 10.2.1.319b (This user guide is applicable to Mac OS X 10.9 macos 10.14.) Contents A. Download Kaspersky Endpoint Security 10 for Mac... 1 B. Install
Install Kaspersky Endpoint Security for Mac Version 10.2.1.319b (This user guide is applicable to Mac OS X 10.9 macos 10.14.) Contents A. Download Kaspersky Endpoint Security 10 for Mac... 1 B. Install
Filelocker-Yale s Secure File Transfer Service
 If you need to transfer large files, or large quantities of files, which would normally exceed the email attachment limit of 20MB, Yale s Filelocker transfer service can help. It is safe and secure for
If you need to transfer large files, or large quantities of files, which would normally exceed the email attachment limit of 20MB, Yale s Filelocker transfer service can help. It is safe and secure for
MOVE AntiVirus page-level reference
 McAfee MOVE AntiVirus 4.7.0 Interface Reference Guide (McAfee epolicy Orchestrator) MOVE AntiVirus page-level reference General page (Configuration tab) Allows you to configure your McAfee epo details,
McAfee MOVE AntiVirus 4.7.0 Interface Reference Guide (McAfee epolicy Orchestrator) MOVE AntiVirus page-level reference General page (Configuration tab) Allows you to configure your McAfee epo details,
Step [2]: Hit on Create icon and Choose the "Create macos Profile" from the drop-down menu
![Step [2]: Hit on Create icon and Choose the Create macos Profile from the drop-down menu Step [2]: Hit on Create icon and Choose the Create macos Profile from the drop-down menu](/thumbs/82/84933536.jpg) This guide allows a user to configure Antivirus Settings through a profile. The settings include all low-level details to be parameterized from ITSM hence the Realtime Scan (at the time of threats encountered),
This guide allows a user to configure Antivirus Settings through a profile. The settings include all low-level details to be parameterized from ITSM hence the Realtime Scan (at the time of threats encountered),
Client Portal FAQ's. Client Portal FAQ's. Why is the Portal more secure?
 Client Portal FAQ's Client Portal FAQ's Why is the Portal more secure? The Bishop Fleming Portal is powered by Virtual Cabinet who have a team of experts to ensure that the latest technologies and best
Client Portal FAQ's Client Portal FAQ's Why is the Portal more secure? The Bishop Fleming Portal is powered by Virtual Cabinet who have a team of experts to ensure that the latest technologies and best
A weekly Spa Day for your Computer
 A weekly Spa Day for your Computer To keep your PC running smoothly and clean, I recommend this procedure on a weekly basis: 1. ATF Cleaner Double Click on ATF Cleaner on your desktop, Check Select All
A weekly Spa Day for your Computer To keep your PC running smoothly and clean, I recommend this procedure on a weekly basis: 1. ATF Cleaner Double Click on ATF Cleaner on your desktop, Check Select All
Student Password Management and Office 365 Directions
 PART I: You will sign in to the Password Self-Service to retrieve your Office 365 account information and set up a new password. This can only be done on a school computer. 1. Double Click on the Password
PART I: You will sign in to the Password Self-Service to retrieve your Office 365 account information and set up a new password. This can only be done on a school computer. 1. Double Click on the Password
CIP Cyber Security Configuration Change Management and Vulnerability AssessmentsManagement
 The Background, VRF/VSLs, and Guidelines and Technical Basis Sections have been removed for this informal posting. The Project 2016-02 is seeking comments around the concept of the Requirement/Measure
The Background, VRF/VSLs, and Guidelines and Technical Basis Sections have been removed for this informal posting. The Project 2016-02 is seeking comments around the concept of the Requirement/Measure
National Insurance Crime Training Academy NICTA
 The National Insurance Crime Training Academy, or NICTA, is an industry partnership with a common goal of providing anti-fraud training to the insurance industry and to law enforcement. NICTA provides
The National Insurance Crime Training Academy, or NICTA, is an industry partnership with a common goal of providing anti-fraud training to the insurance industry and to law enforcement. NICTA provides
Compliance Enforcement Initiative
 Compliance Enforcement Initiative Filing and Status Update November 2, 2011 Rebecca Michael Status of the Filings NERC filed several components of the Compliance Enforcement Initiative on September 30,
Compliance Enforcement Initiative Filing and Status Update November 2, 2011 Rebecca Michael Status of the Filings NERC filed several components of the Compliance Enforcement Initiative on September 30,
Patient Reported Outcome Measures (PROMs)
 Patient Reported Outcome Measures (PROMs) Published September 2017 Copyright 2017 Health and Social Care Information Centre. The Health and Social Care Information Centre is a non-departmental body created
Patient Reported Outcome Measures (PROMs) Published September 2017 Copyright 2017 Health and Social Care Information Centre. The Health and Social Care Information Centre is a non-departmental body created
GUIDELINES. Effective date: April 2018 Contact: United Nations Archives and Records Management Section: Review date: April 2020
 GUIDELINES Transfer of Records and Archives to the United Nations Archives and Records Management Section (ARMS) Effective date: April 2018 Contact: United Nations Archives and Records Management Section:
GUIDELINES Transfer of Records and Archives to the United Nations Archives and Records Management Section (ARMS) Effective date: April 2018 Contact: United Nations Archives and Records Management Section:
Broker Documents USER GUIDE
 Broker Documents USER GUIDE Aviva Canada Inc. Page 1 of 23 Table of Contents 1 Abbreviations, Acronyms and Definitions...3 2 Introduction...3 Document Objective...3 3 Broker Documents...3 Background...3
Broker Documents USER GUIDE Aviva Canada Inc. Page 1 of 23 Table of Contents 1 Abbreviations, Acronyms and Definitions...3 2 Introduction...3 Document Objective...3 3 Broker Documents...3 Background...3
You also have the option of being able to automatically delete the document from SharePoint if the Note is deleted within CRM.
 Overview The SharePoint Integration provides functionality for you to be able to automatically upload documents to a SharePoint site when they are entered as a Note within CRM. Once uploaded to SharePoint,
Overview The SharePoint Integration provides functionality for you to be able to automatically upload documents to a SharePoint site when they are entered as a Note within CRM. Once uploaded to SharePoint,
