Scalable Queue-Based Spin Locks with Timeout
|
|
|
- Pauline Gilmore
- 6 years ago
- Views:
Transcription
1 Scalable Queue-Based Spin Locks with imeout Michael L. Scott and illiam N. Scherer III Department of Computer Science University of Rochester Rochester, NY ABSRAC Queue-based spin locks allow programs with busy-wait synchronization to scale to very large multiprocessors, without fear of starvation or performance-destroying contention. Socalled try locks, traditionally based on non-scalable test-andset locks, allow a process to abandon its attempt to acquire a lock after a given amount of time. he process can then pursue an alternative code path, or yield the processor to some other process. e demonstrate that it is possible to obtain both scalability and bounded waiting, using variants of the queuebased locks of Craig, Landin, and Hagersten, and of Mellor- Crummey and Scott. A process that decides to stop waiting for one of these new locks can link itself out of line atomically. Single-processor experiments reveal performance penalties of 5 1% for the CLH and MCS try locks in comparison to their standard versions; this marginal cost decreases with larger numbers of processors. e have also compared our queue-based locks to a traditional test-and-test and set lock with exponential backoff and timeout. At modest (non-zero) levels of contention, the queued locks sacrifice cache locality for fairness, resulting in a worst-case 3X performance penalty. At high levels of contention, however, they display a 1.5 X performance advantage, with significantly more regular timings and significantly higher rates of acquisition prior to timeout. 1. INRODUCION Spin locks are widely used for mutual exclusion on sharedmemory multiprocessors. raditional test and set-based spin locks are vulnerable to memory and interconnect contention, and do not scale well to large machines. Queuebased spin locks avoid contention by arranging for every waiting process to spin on a separate, local flag in memory. his work was supported in part by NSF grants numbers EIA , EIA-814, CCR , and CCR , and by DARPA/AFRL contract number F961- -K-18. Permission to make digital or hard copies of all or part of this work for personal or classroom use is granted without fee provided that copies are not made or distributed for profit or commercial advantage and that copies bear this notice and the full citation on the first page. o copy otherwise, to republish, to post on servers or to redistribute to lists, requires prior specific permission and/or a fee. PPOPP 1, June 18-, 1, Snowbird, Utah, USA. Copyright 1 ACM /1/6...$5.. Several researchers (ourselves among them) have conjectured that any program that routinely encounters high levels of lock contention is unlikely to scale well to large machines. Conversely, in any program that scales well, the overhead of spin locks may not be a serious concern. he problem with this argument is that infrequent pathological events can be a serious problem to users. An improvement in worst case performance from, say, to 1% efficiency may be enormously valuable, even if typical efficiency is more like 8%. ith the increasing popularity of medium-scale ( 1 processor) server-class machines, we believe that scalable spin locks will prove increasingly important. In a traditional test and set spin lock, processes are mutually anonymous. In a queue-based lock, they are not: each waiting process is linked to its predecessor and successor in the queue. In previous work [6], members of our group considered the possibility that a spinning process might be preempted, thereby unnecessarily delaying processes farther down the queue. In the current paper we consider the possibility that a spinning process may become impatient and wish to leave the queue before acquiring the lock. imeout-capable spin locks, sometimes referred to as trylocks, are important for several reasons: 1. A process in a soft real-time application may need to bound the time it spends waiting for a lock. If the timeout expires, the process can choose to announce an error or to pursue an alternative code path that does not require the lock.. Absent special OS support, a user-level process in a multiprogrammed environment may be preempted while holding a lock. imeout allows other processes waiting for the lock to give up, yield the processor, and try again when rescheduled. 3. In a parallel database system, timeout provides a viable strategy for deadlock recovery. A process that waits too long for a lock can assume that deadlock has occurred, abort the current transaction, and retry. e are aware of commercially significant signal processing applications that use timeout for reason (1), and parallel database servers that use timeout for reasons () and (3). In the latter case, timeout may be the deciding factor in making spin locks usable in user-level code. In contrast to the problem of preemption among spinning processes, timeout does not require interaction between the scheduler and the synchronization algorithm. It is complicated, however, by the fact that a timed-out process may
2 attempt to acquire the lock again, possibly many times, before the point at which it would have acquired the lock if it had stayed in line. he possibility of multiple aborted acquisition attempts suggests that a timed-out process must remove itself from the queue entirely, leaving nothing behind; otherwise we would be unable to bound the space or time requirements of the algorithm. e have developed so-called try lock (timeout capable) versions of our MCS queue-based lock [8] and of the CLH queue-based lock of Craig [] and Landin and Hagersten [7]. After presenting additional background information in section, we describe our new locks in section 3. Both new locks employ swap and compare and swap instructions, and can be implemented on any shared-memory machine, with or without cache coherence, that provides these operations or their equivalent. In section 4 we present performance results obtained on a 56-processor Sun ildfire machine. e conclude with a summary of recommendations in section 5.. BACKGROUND Programmers face several choices when synchronizing processes on a shared-memory multiprocessor. he most basic choice is between spinning (busy-waiting), in which processes actively poll for a desired condition, and blocking, in which processes yield the processor in expectation that they will be made runnable again when the desired condition holds. Spinning is the method of choice when the expected wait time is small, or when there is no other productive use for the processor. he most basic busy-wait mechanism is a test-and-set lock, in which a process desiring entry to a critical section repeatedly attempts to change a locked flag from false to true, using an atomic hardware primitive. Unfortunately, test-and-set locks lead to increasing amounts of contention for memory and bus or interconnect bandwidth as the number of competing processors grows. his contention can be reduced somewhat by polling with ordinary read operations, rather than atomic test and set operations; polls are then satisfied from local caches during critical sections, with a burst of refill traffic whenever the lock is released. he cost of the burst can be further reduced using Ethernet-style exponential backoff [8]. Figure 1 shows code for a test-andtest and set () lock with exponential backoff..1 Queue-based locks Even with exponential backoff, test-and-test and set locks still induce significant contention, leading to irregular timings and compromised memory performance on large machines. Queue-based spin locks eliminate these problems by arranging for every competing process to spin on a different memory location. o ensure scalability, each location must be local to the spinning process, either by virtue of hardware cache coherence or as a result of explicit local allocation on a non-cache-coherent machine. Several researchers, working independently and roughly concurrently, developed queue-based spin locks in the late 198s. Anderson [1] and Graunke and hakkar [3] embed their queues in per-lock arrays, requiring space per lock proportional to the maximum number of processes that may compete for access concurrently. Anderson s lock uses atomic fetch and increment instructions to assign slots in the array to waiting processes; Graunke and hakkar s lock uses swap instead. Our MCS lock, co-designed with John Mellortypedef unsigned long bool; typedef volatile bool tatas_lock; void tatas_acquire(tatas_lock *L) { if (tas(l)) { int b = BACKOFF_BASE; do { for (i = b; i; i--); // delay b = min(b * BACKOFF_FACOR, BACKOFF_CAP); if (*L) continue; // spin with reads while (tas(l)); void tatas_release(tatas_lock *L) { *L = ; Figure 1: est-and-test and set () lock with exponential backoff. Parameters BACKOFF BASE, BACKOFF FACOR, and BACKOFF CAP must be tuned by trial and error for each individual machine architecture. Crummey [8], employs a linked list with pointers from each process to its successor; it relies on swap and compare and swap, and has the advantage of requiring total space linear in the number of locks and the number of competing processes. (he lock can be re-written to use only swap, but at the expense of FIFO ordering: in the swap-only version of mcs release there is a timing window that may allow newly arriving processes to jump ahead of processes already in the queue.) he MCS lock is naturally suited to local-only spinning on both cache-coherent and non-cachecoherent machines. he Anderson and Graunke/hakkar locks must be modified to employ an extra level of indirection on non-cache-coherent machines. typedef struct mcs_qnode { volatile bool waiting; volatile struct mcs_qnode *volatile next; mcs_qnode; typedef volatile mcs_qnode *mcs_qnode_ptr; typedef mcs_qnode_ptr mcs_lock; // initialized to nil void mcs_acquire(mcs_lock *L, mcs_qnode_ptr I) { I->next = nil; mcs_qnode_ptr pred = swap(l, I); if (pred == nil) return; // lock was free I->waiting = true; // word on which to spin pred->next = I; // make pred point to me while (I->waiting); // spin void mcs_release(mcs_lock *L, mcs_qnode_ptr I) { mcs_qnode_ptr succ; if (!(succ = I->next)) { // I seem to have no succ. // try to fix global pointer if (compare_and_store(l, I, nil)) return; do { succ = I->next; while (!succ); // wait for successor succ->waiting = false; Figure : he MCS queue-based spin lock. Parameter I points to a qnode record allocated (in an enclosing scope) in shared memory locally-accessible to the invoking processor.
3 typedef struct clh_qnode { volatile bool waiting; volatile struct clh_qnode *volatile prev; clh_qnode; typedef volatile clh_qnode *clh_qnode_ptr; typedef clh_qnode_ptr clh_lock; // initialized to point to an unowned qnode void clh_acquire(clh_lock *L, clh_qnode_ptr I) { I->waiting = true; clh_qnode_ptr pred = I->prev = swap(l, I); while (pred->waiting); // spin void clh_release(clh_qnode_ptr *I) { clh_qnode_ptr pred = (*I)->prev; (*I)->waiting = false; *I = pred; // take pred s qnode Figure 3: he CLH queue-based spin lock. Parameter I points to qnode record or, in clh release, to a pointer to a qnode record. he qnode belongs to the calling process, but may be in main memory anywhere in the system, and will generally change identity as a result of releasing the lock. he CLH lock, developed about three years later by Craig [] and, independently, Landin and Hagersten [7], also employs a linked list, but with pointers from each process to its predecessor. he CLH lock relies on atomic swap, and may outperform the MCS lock on cache-coherent machines. Like the Anderson and Graunke/hakkar locks, it requires an extra level of indirection to avoid spinning on remote locations on a non-cache-coherent machine []. Code for the MCS and CLH locks appears in Figures, 3, and 4. typedef struct clh_numa_qnode { volatile bool *w_ptr; volatile struct clh_qnode *volatile prev; clh_numa_qnode; typedef volatile clh_numa_qnode *clh_numa_qnode_ptr; typedef clh_numa_qnode_ptr clh_numa_lock; // initialized to point to an unowned qnode const bool *granted = x1; void clh_numa_acquire(clh_numa_lock *L, clh_numa_qnode_ptr I) { volatile bool waiting = true; I->w_ptr = nil; clh_numa_qnode_ptr pred = I->prev = swap(l, I); volatile bool *p = swap(&pred->w_ptr, &waiting); if (p == granted) return; while (waiting); // spin void clh_numa_release(clh_numa_qnode_ptr *I) { clh_numa_qnode_ptr pred = (*I)->prev; volatile bool *p = swap(&((*i)->w_ptr), granted); if (p) *p = false; *I = pred; // take pred s qnode Figure 4: Alternative version of the CLH lock, with an extra level of indirection to avoid remote spinning on a non-cache-coherent machine. // return value indicates whether lock was acquired bool tatas_try_acquire(tatas_lock *L, hrtime_r ) { if (tas(l)) { hrtime_t start = gethrtime(); int b = BACKOFF_BASE; do { if (gethrtime() - start > ) return false; for (i = b; i; i--); // delay b = min(b * BACKOFF_FACOR, BACKOFF_CAP); if (*L) continue; // spin with reads while (tas(l)); Figure 5: he standard -try lock. ype definitions and release code are the same as in Figure 1.. Atomic primitives In this paper we make reference to several atomic operations. Swap(address, value) atomically writes a memory location and returns its original contents. Compare and swap(address, expected value, new value) atomically checks the contents of a memory location to see if it matches an expected value and, if so, replaces it with a new value. In either event it returns the original contents. e also use an alternative form, compare and store, that instead returns a Boolean value indicating whether the comparison succeeded. Fetch and increment(address)atomically increments the contents of a memory location and returns the original contents. Compare and swap first appeared in the IBM 37 instruction set. Swap and compare and swap are provided by Sparc V9. Several recent processors, including the Alpha, MIPS, and PowerPC, provide a pair of instructions, load linked and store conditional, that can be implemented naturally and efficiently as part of an invalidation-based cachecoherence protocol, and which together provide the rough equivalent of compare and swap. Both compare and swap and load linked/store conditional are universal atomic operations, in the sense that they can be used without locking (but at the cost of some global spinning) to implement any other atomic operation [5]. Fetch and increment, together with a host of other atomic operations, is supported directly but comparatively inefficiently on the x RY CKS As noted in section 1, a process may wish to bound the time it may wait for a lock, in order to accommodate soft real-time constraints, to avoid waiting for a preempted peer, or to recover from transaction deadlock. Such a bound is easy to achieve with a test and set lock (see Figure 5): processes are anonymous and compete with one another chaotically. hings are not so simple, however, in a queue-based lock: a waiting process is linked into a data structure on which other processes depend; it cannot simply leave. A similar problem occurs in multiprogrammed systems when a process stops spinning because it has been preempted. Our previous work in scheduler-conscious synchronization [6] arranged to mark the queue node of a preempted process so that the process releasing the lock would simply pass it over. Upon being rescheduled, a skipped-over process would have to reenter the queue. A process that had yet to reach the head of the queue when rescheduled would retain its original position.
4 Craig [] proposes (in narrative form) a similar mark the node strategy for queue-based try locks. Specifically, he suggests that a timed-out process leave its queue node behind, where it will be reclaimed by another process when it reaches the head of the queue. Unfortunately, this strategy does not work nearly as well for timeout as it does for preemption. he problem is that a timed-out process is not idle: it may want to acquire other locks. Because we have no bound on how long it may take for a marked queue node to reach the head of the queue, we cannot guarantee that the same queue node will be available the next time the process tries to acquire a lock. As Craig notes, the total space required for P processes and L locks rises from O(P + L) with the original CLH lock to O(P L) in a mark-the-node try lock. e also note that the need to skip over abandoned queue nodes increases the worst case lock release time from O(1) to O(P ). e have addressed these space and time problems in new try-lock versions of both the CLH and MCS locks. In fairness to Craig, the code presented here requires a compare and swap operation; his work was predicated on the assumption that only swap was available. A different version of the MCS-try lock, also using only swap, has been developed by Vitaly Oratovsky and Michael O Donnell of Mercury Computer Corp. [9]. heir lock has the disadvantage that newly arriving processes that have not specified a timeout interval (i.e. that are willing to wait indefinitely) will bypass any already-waiting processes whose patience is more limited. A process that specifies a timeout may thus fail to acquire a lock may in fact never acquire a lock, even if it repeatedly becomes available before the expiration of the timeout interval so long as processes that have not specified a timeout continue to arrive. 3.1 he CLH-try lock In the standard CLH lock, a process leaves its queue node behind when releasing the lock. In its place it takes the node abandoned by its predecessor. For a try lock, we must arrange for a process that times out to leave with its own queue node. Otherwise, as noted above, we might need O(P L) queue nodes in the system as a whole. It is relatively easy for a process B to leave the middle of the queue. Since B s intended successor C (the process behind it in the queue) is already spinning on B s queue node, B can simply mark the node as leaving. C can then dereference the node to find B s predecessor A, and mark B s node as recycled, whereupon B can safely leave. here is no race between A and B because A never inspects B s queue node. Complications arise when the departing process B is the last process in the queue. In this case B must attempt to modify the queue s tail pointer to refer to A s queue node instead of its own. e can naturally express the attempt with a compare and swap operation. If the compare and swap fails we know that another process C has arrived. At this point we might hope to revert to the previous (middleof-the-queue) case. Unfortunately, it is possible that C may successfully leave the queue after B s compare and swap, at which point B may wait indefinitely for a handshake that never occurs. e could protect against the indefinite wait by repeatedly re-checking the queue s tail pointer, but that would constitute spinning on a non-local location, something we want to avoid. Our solution is to require C to handshake with B in a way that prevents B from trying to leave the queue while C is in the middle of leaving. Code for this solution can be found on-line at pseudocode/timeout.html#clh-try. It comprises about 95 lines of C. he two principal cases (B in the middle of the queue and at the end) are illustrated in Figure 6. Like the standard CLH lock, the CLH-try lock depends on cache coherence to avoid remote spinning. In the CLHtry lock it is actually possible for two processes to end up spinning on the same location. In the fourth line of the righthand side of Figure 6, if process A calls clh release, it will spin until the transient flag reverts to waiting. If a new process C arrives at about this time, it, too, will begin to spin on the flag in A s queue node. hen B finally updates the flag, its write will terminate both spins. 3. he MCS-try lock A feature of the standard MCS lock is that each process spins on its own queue node, which may be allocated in local memory even on a non-cache-coherent machine. o leave the queue, therefore, a process B must update the successor pointer in the queue node of its predecessor A so that it points to B s successor C, ifany,ratherthantob. If C later chooses to leave the queue as well, it will again need to update A s queue node, implying that B must tell it where A s queue node resides. Pointers to both predecessors and successors must therefore reside in the queue nodes in memory, where they can be read and written by neighboring processes. hese observations imply that an MCS-try lock must employ a doubly linked queue, making it substantially more complex than the CLH-try lock. he benefit of the complexity is better memory locality on a non-cachecoherent machine. (e believe we could construct a version of the CLH-try lock, starting from the code in Figure 4, that would avoid remote spins on a non-cache-coherent machine, but it would require more atomic operations on its critical path, and would be unlikely to be competitive with the MCS-try lock.) As in the CLH-try lock there are two principal cases to consider for the MCS-try lock, depending on whether the departing process B is currently in the middle or at the end of the queue. hese cases are illustrated in Figure 7. hile waiting to be granted the lock, a process ordinarily spins on its predecessor pointer. In the middle-of-the-queue case, departing process B first replaces the four pointers into and out of its queue node, respectively, with leaving other and leaving self flags (shown as and LS in the figure). It then updates C s predecessor pointer, and relies on C to update A s successor pointer. In the end-of-the-queue case, B tags A s nil successor pointer to indicate that additional changes are pending. Absent any race conditions, B eventually clears the tag using compare and swap. Unfortunately, there are many potential races that have to be resolved. he process at the head of the queue may choose to grant the lock to its successor while the successor is attempting to leave the queue. wo neighboring processes may decide to leave the queue at approximately the same time. A process that is at the end of the queue in step may discover in step 5 that it now has a successor. A complete discussion of these races and how we resolve them is too lengthy to include here. In general, the order of updates to pointers is chosen to ensure that (1) no process ever returns
5 A B C A B Q B marks A's node transient B marks A's node transient L B marks its own node leaving L B marks its own node leaving L C dereferences B's node L B updates lock tail pointer R C marks B's node recycled L B marks A's node waiting R B marks A's node waiting B leaves queue B leaves queue Figure 6: he two principal cases in the CLH-try lock. In the figure at left process B can leave the middle of the queue as soon as it receives confirmation from its successor, C, that no pointer to its queue node remains. In the figure at right, B can leave the end of the queue once it has updated the tail pointer, Q, using compare and swap. he transitions from waiting to leaving and from waiting to available (not shown) must also be made with compare and swap, to avoid overwriting a transient flag. A B C A B Q LS Step 1 LS LS Step Step 3 action by B Step 4 Step 5 Step 6 B leaves queue; action by C (left), B (right) Figure 7: he two principal cases in the MCS-try lock. In the figure at left process B uses atomic swap operations to replace the pointers into and out of its queue node, in a carefully chosen order, with leaving other and leaving self flags. It then updates the pointer from C to A, and relies on C to update the pointer from A to C. In the figure at right, B has no successor at step, so it must perform the final update itself. In the meantime it leaves a tag on A s (otherwise nil) successor pointer to ensure that a newly arriving process will wait for B s departure to be finalized.
6 from mcs try acquire until we are certain that no pointers to its queue node remain, and () if two adjacent processes decide to leave concurrently, the one closer to the front of the queue leaves first. Code for the MCS-try lock is available online at pseudocode/timeout.html#mcs-try. 3.3 Correctness Synchronization algorithms are notoriously subtle. Correctness proofs for such algorithms tend to be less subtle, but more tedious and significantly longer than the original code. e have not attempted to construct such a proof for either of our algorithms; for the MCS-try lock in particular, which runs to more than 36 lines of Ccode, it appears a daunting exercise. esting, of course, cannot demonstrate the absence of bugs, but it can significantly decrease their likelihood. e have tested both our algorithms extensively, under a variety of loads and schedules, and did indeed find and fix several bugs. e are reasonably confident of our code, but acknowledge the possibility that bugs remain. here is a third possible approach to verification. e are in the process of constructing a simulation testbed that will allow us, for a given set of processes, to exhaustively explore all possible interleavings of execution paths. e plan to verify that these interleavings preserve all necessary correctness invariants for the operation of a queue-based lock, and to argue that they cover all the interesting states that could arise with any larger set of processes. 4. PERFORMANCE RESULS e have implemented the, CLH, and MCS locks, with and without timeout, using the swap and compare and swap operations available in the Sparc V9 instruction set. Initial testing and single-processor results employed a 336 MHz Sun Ultra 45. Scalability tests were conducted on a 56-processor Sun ildfire machine [4] (not to be confused with the Compaq product of the same name) with 5 MHz processors. Architecturally, the ildfire machine consists of four banks of up to 16 processors each, connected by a central crossbar. Backoff constants for the lock were tuned separately for each machine. Our tests employ a microbenchmark consisting of a tight loop containing a single acquire/release pair. Aside from counting the number of iterations and the number of successful acquires (these may be different in the case of a try lock), the loop does no useful work. Machines used for tests were otherwise unloaded. 4.1 Single-processor results ecanobtainanestimateoflockoverheadintheabsence of contention by running the microbenchmark on a single processor, and then subtracting the loop overhead. Results on on our Ultra 45 are as follows: 137ns MCS 17ns CLH 137ns CLH-NUMA 6ns MCS-try 56ns CLH-try 74ns In an attempt to avoid perturbation due to other activity on the machine, we have reported the minima over a series of NUMA CLH MCS Figure 8: Microbenchmark iteration time for nontry locks. he very low overhead of the lock is an artifact of repeated acquisition by a single processor Figure 9: Microbenchmark iteration time for try locks, with patience (timeout interval) of 15µs. several runs. As one might expect, none of the more complex locksisabletoimproveuponthetimeofthelock, though the CLH locks does tie it. he extra 35ns overhead in the MCS lock is primarily due to the compare and swap in mcs release. he CLH-try and MCS-try locks pay an additional penalty for the extra argument to their acquire operations and, in the case of CLH-try, the compare and swap in clh-release. Neither of the try locks calls the Sun high-resolution timer if it is able to acquire the lock immediately. Each call to the timer consumes an additional 5ns, which we would like to hide in wait time. 4. Lock passing time e can obtain an estimate of the time required to pass a lock from one processor to another by running our microbenchmark on a large collection of processors. his passing time is not the same as total lock overhead: as discussed by Magnussen, Landin, and Hagersten [7], queue-based locks tend toward heavily pipelined execution, in which the initial cost of entering the queue and the final cost of leaving it are overlapped with the critical sections of other processors.
7 Figures 8 and 9 show the behaviors of all five queue-based locks on one bank of the ildfire machine, with timeout values ( patience ) set high enough that timeout never occurs in the queue-based try locks. All tests were run with a single process (pthread) on every processor. ith only one active processor, the plotted value represents the sum of lock andloopoverheadwithperfectcachelocality.hevaluefor the queue-based locks jumps dramatically with two active processors, as a result of coherence misses. ith three or more active processors, lock passing is fully pipelined, and the plotted value represents the time to pass the lock from one processor to the next. Among the non-try locks (Figure 8), CLH-NUMA has a noticeably greater passing time (3.1µs) than either MCS or CLH. he passing times for MCS and CLH are just about the same, at.4µs and.5µs respectively. Both MCS and CLH are faster than either of their try lock counterparts, though at.7µs, CLH-try beats out the CLH-NUMA lock. At 3.µs, MCS-try has the slowest passing time. hile the lock appears to be passing much faster than any of the other locks, this result is somewhat misleading. he queued locks are all fair: requests are granted in the order they were made. he lock, by contrast, is not fair: since the most recent owner of a lock has the advantage of cache locality, it tends to outrace its peers and acquire the lock repeatedly. (his effect would be reduced in a more realistic benchmark, with work outside the critical section.) In our experiments successive acquisitions of a queued lock with high patience occurred on different processors more than 99% of the time; successive acquisitions of a lock occurred on the same processor about 99% of the time. his unfairness has ramifications for timeout: even with 15µs patience (long enough for every processor, on average, to acquire and release the lock 1 times), still fails to acquire the lock some 4% of the time. 4.3 Bimodal behavior of try locks Figure 1 plots the percentage of time that a processor in the microbenchmark succeed in acquiring a try lock. For this test the timeout interval (patience) has been set at only 5µs. Figure 11 plots iteration time for the same experiment. ith this lower patence level the the MCS-try and CLH-try locks exhibit distinctly bimodal behavior. ith nine or fewer active processors, timeout almost never occurs, and behavior mimics that of the non-try locks. ith ten or more active processors, timeouts begin to occur. For higher processor counts, or for lower patience levels, the chance of a processor getting a lock is primarily a function of the number of processors that are in the queue ahead of it minus the number of those that time out and leave the queue before obtaining the lock. As is evident in these graphs, this chance drops off sharply with insufficient patience. he average time per iteration also drops, because giving up an attempt to acquire a lock is cheaper than waitingtoacquireit. 4.4 Comparison of regular and try locks with he tradeoff between MCS-try and plain MCS is as expected: at the cost of a higher average iteration time (per attempt), the plain MCS lock always manages to successfully acquire the lock. At the cost of greater complexity, the MCS-try lock provides the option of timing out. he same 1% 1% 8% 6% 4% % % Figure 1: %Acquisition at 5µs patience Figure 11: Iteration time at 5µs patience. NUMA CLH MCS tradeoff holds between the CLH and CLH-try locks. he tradeoffs between MCS-try or CLH-try and are more interesting. hile the iteration time is consistently higher for the queue-based locks (Figure 11), the acquisition (success) rate depends critically on the ratio between patience and the level of competition for the lock. hen patience is high, relative to competition, the queue-based locks are successful all the time. Once the expected wait time exceeds the timeout interval in the queue-based locks, however, the lock displays a higher acquisition rate. As we will see in Figures 14 and 15, is not able to maintain this advantage once we exceed the number of processors in a single bank of the ildfire machine. 4.5 Results for high processor counts Generally speaking, the results for larger numbers of processors are comparable to those seen within a single bank of the machine. Although crossing the interconnect between banks introduces a fair amount of noise into the timing results (see Figures 1 and 13), the MCS-try and CLH-try locks continue to have very similar iteration times, with MCS-try coming out somewhat slower than CLH-try. he influence of the interconnect is particularly evident in the MCS-try iteration time in Figure 13: an additional bank of processors, requiring additional traversals of the in-
8 1 1% 1 1% NUMA MCS CLH 8% 6% 4% % % Figure 1: Iteration time at µs patience. Figure 14: %Acquisition at µs patience. 14 1% 1 1% NUMA MCS CLH 8% 6% 4% % % Figure 13: Iteration time at 5µs patience. Figure 15: %Acquisition at 5µs patience. terconnect, comes into play between 16 and processors, and again between 8 and 3 processors. (A third transition point, between 4 and 44 processors, is not visible in the graph.) Figures 14 and 15 show the establishment of a very long pipeline for lock acquisition. hile the CLH-try lock sees a lower acquisition rate than the MCS-try lock at very high levels of competition relative to patience (Figure 14), there is a significant intermediate range where its acquisition rate is higher (Figure 15 and the center of Figure 14). 5. CONCLUSIONS e have shown that it is possible, given standard atomic operations, to construct queue-based locks in which a process can time out and abandon its attempt to acquire the lock. Our algorithms provide reasonable performance on both small and large cache-coherent multiprocessors. Our future plans include tests on the non-cache-coherent Cray 3E; here we expect the MCS-try lock to perform particularly well. In the decade since our original comparison of spin lock algorithms, ratios of single-processor latencies have remained remarkably stable. On a 16MHz Sequent Symmetry multiprocessor, a lock without contention consumed 7µs in he MCS lock consumed 9µs, a difference of 8%. On a 336 MHz Sun Enterprise machine, a lock without contention takes 137ns today. he MCS lock takes 17ns, a difference of 5%. he CLH lock, which we did not test in 1991, is tied with on a single processor. ith two or more processes competing for access to a lock, the numbers have changed more significantly over the years. In 1991 the lock (with backoff) ran slightly slower than the MCS lock at modest levels of contention. oday it appears to run in less than a third of the time of all the queue-based locks. hy then would one consider a queue-based lock? he answer is three-fold. First, the performance advantage of the lock is exaggerated in our experiments by the use of back-to-back critical sections, allowing a single processor to leverage cache locality and acquire the lock repeatedly. Second, does not scale well. Once processes on the ildfire machine are scattered across multiple banks, and must communicate through the central crossbar, iteration time for rises to 5 1% above that of the queue-based locks. hird, even with patience as high as ms times the average lock-passing time the algorithm with timeout fails to acquire the lock about % of the time. his failure rate suggests that a regular lock (no timeout) will see significant variance in acquisition
9 times in other words, significant unfairness. he queue based locks, by contrast, guarantee that processes acquire the lock in order of their requests. For small-scale multiprocessors the lock remains the most attractive overall performer, provided that its backoff parameters have been tuned to the underlying hardware. Queue-based locks are attractive for larger machines, or for cases in which fairness and regularity of timing are particularly important. he CLH lock, both with and without timeout, has better overall performance on cache-coherent machines. he version with timeout is also substantially simpler than the MCS-try lock. One disadvantage of the CLH lock is its need for an initial queue node in each currently unheld lock. In a system with a very large number of locks this overhead might be an important consideration. Because the queue nodes of the MCS lock can be allocated statically in the local memory of the processors that spin on them, the MCS-try lock is likely to outperform the CLH-try lock on a non-cache-coherent machine. It is also likely, we believe, to be faster than a hypothetical try lock based on the CLH-NUMA lock. 6. ACKNOLEDGMENS e are indebted to Vitaly Oratovsky and Michael O Donnell of Mercury Computer Corp. for drawing our attention to the subject of queue-based try locks, and to Mark Hill, Alaa Alameldeen, and the Computer Sciences Department at the University of isconsin Madison for the use of their Sun ildfire machine. 7. REFERENCES [1]. E. Anderson. he performance of spin lock alternatives for shared-memory multiprocessors. IEEE PDS, 1(1):6 16, Jan []. S. Craig. Building FIFO and priority-queueing spin locks from atomic swap. echnical Report R 93--, Dept. of Computer Science, Univ. of ashington, Feb [3] G. Graunke and S. hakkar. Synchronization algorithms for shared-memory multiprocessors. Computer, 3(6):6 69, June 199. [4] E. Hagersten and M. Koster. ildfire: A scalable path for SMPs. In 5th HPCA, pages , Orlando, FL, Jan [5] M. Herlihy. ait-free synchronization. ACM OPLAS, 13(1):14 149, Jan [6] L. I. Kontothanassis, R.. isniewski, and M. L. Scott. Scheduler-conscious synchronization. ACM OCS, 15(1):3 4, Feb [7] P. Magnussen, A. Landin, and E. Hagersten. Queue locks on cache coherent multiprocessors. In 8th IPPS, pages , Cancun, Mexico, Apr Expanded version available as Efficient Software Synchronization on Large Cache Coherent Multiprocessors, SICS Research Report 94:7, Swedish Institute of Computer Science, Feb [8] J. M. Mellor-Crummey and M. L. Scott. Algorithms for scalable synchronization on shared-memory multiprocessors. ACM OCS, 9(1):1 65, Feb [9] V. Oratovsky and M. O Donnell. Personal communication, Feb.. Mercury Computer Corp.
Spin Locks and Contention Management
 Chapter 7 Spin Locks and Contention Management 7.1 Introduction We now turn our attention to the performance of mutual exclusion protocols on realistic architectures. Any mutual exclusion protocol poses
Chapter 7 Spin Locks and Contention Management 7.1 Introduction We now turn our attention to the performance of mutual exclusion protocols on realistic architectures. Any mutual exclusion protocol poses
Advance Operating Systems (CS202) Locks Discussion
 Advance Operating Systems (CS202) Locks Discussion Threads Locks Spin Locks Array-based Locks MCS Locks Sequential Locks Road Map Threads Global variables and static objects are shared Stored in the static
Advance Operating Systems (CS202) Locks Discussion Threads Locks Spin Locks Array-based Locks MCS Locks Sequential Locks Road Map Threads Global variables and static objects are shared Stored in the static
Multiprocessor Systems. Chapter 8, 8.1
 Multiprocessor Systems Chapter 8, 8.1 1 Learning Outcomes An understanding of the structure and limits of multiprocessor hardware. An appreciation of approaches to operating system support for multiprocessor
Multiprocessor Systems Chapter 8, 8.1 1 Learning Outcomes An understanding of the structure and limits of multiprocessor hardware. An appreciation of approaches to operating system support for multiprocessor
A simple correctness proof of the MCS contention-free lock. Theodore Johnson. Krishna Harathi. University of Florida. Abstract
 A simple correctness proof of the MCS contention-free lock Theodore Johnson Krishna Harathi Computer and Information Sciences Department University of Florida Abstract Mellor-Crummey and Scott present
A simple correctness proof of the MCS contention-free lock Theodore Johnson Krishna Harathi Computer and Information Sciences Department University of Florida Abstract Mellor-Crummey and Scott present
Algorithms for Scalable Lock Synchronization on Shared-memory Multiprocessors
 Algorithms for Scalable Lock Synchronization on Shared-memory Multiprocessors John Mellor-Crummey Department of Computer Science Rice University johnmc@cs.rice.edu COMP 422 Lecture 18 17 March 2009 Summary
Algorithms for Scalable Lock Synchronization on Shared-memory Multiprocessors John Mellor-Crummey Department of Computer Science Rice University johnmc@cs.rice.edu COMP 422 Lecture 18 17 March 2009 Summary
Adaptive Lock. Madhav Iyengar < >, Nathaniel Jeffries < >
 Adaptive Lock Madhav Iyengar < miyengar@andrew.cmu.edu >, Nathaniel Jeffries < njeffrie@andrew.cmu.edu > ABSTRACT Busy wait synchronization, the spinlock, is the primitive at the core of all other synchronization
Adaptive Lock Madhav Iyengar < miyengar@andrew.cmu.edu >, Nathaniel Jeffries < njeffrie@andrew.cmu.edu > ABSTRACT Busy wait synchronization, the spinlock, is the primitive at the core of all other synchronization
Algorithms for Scalable Lock Synchronization on Shared-memory Multiprocessors
 Algorithms for Scalable Lock Synchronization on Shared-memory Multiprocessors John Mellor-Crummey Department of Computer Science Rice University johnmc@rice.edu COMP 422/534 Lecture 21 30 March 2017 Summary
Algorithms for Scalable Lock Synchronization on Shared-memory Multiprocessors John Mellor-Crummey Department of Computer Science Rice University johnmc@rice.edu COMP 422/534 Lecture 21 30 March 2017 Summary
6.852: Distributed Algorithms Fall, Class 15
 6.852: Distributed Algorithms Fall, 2009 Class 15 Today s plan z z z z z Pragmatic issues for shared-memory multiprocessors Practical mutual exclusion algorithms Test-and-set locks Ticket locks Queue locks
6.852: Distributed Algorithms Fall, 2009 Class 15 Today s plan z z z z z Pragmatic issues for shared-memory multiprocessors Practical mutual exclusion algorithms Test-and-set locks Ticket locks Queue locks
Distributed Computing Group
 Distributed Computing Group HS 2009 Prof. Dr. Roger Wattenhofer, Thomas Locher, Remo Meier, Benjamin Sigg Assigned: December 11, 2009 Discussion: none Distributed Systems Theory exercise 6 1 ALock2 Have
Distributed Computing Group HS 2009 Prof. Dr. Roger Wattenhofer, Thomas Locher, Remo Meier, Benjamin Sigg Assigned: December 11, 2009 Discussion: none Distributed Systems Theory exercise 6 1 ALock2 Have
Preemption Adaptivity in Time-Published Queue-Based Spin Locks
 Preemption Adaptivity in Time-Published Queue-Based Spin Locks Bijun He, William N. Scherer III, and Michael L. Scott Department of Computer Science, University of Rochester, Rochester, NY 14627-0226,
Preemption Adaptivity in Time-Published Queue-Based Spin Locks Bijun He, William N. Scherer III, and Michael L. Scott Department of Computer Science, University of Rochester, Rochester, NY 14627-0226,
Multiprocessors II: CC-NUMA DSM. CC-NUMA for Large Systems
 Multiprocessors II: CC-NUMA DSM DSM cache coherence the hardware stuff Today s topics: what happens when we lose snooping new issues: global vs. local cache line state enter the directory issues of increasing
Multiprocessors II: CC-NUMA DSM DSM cache coherence the hardware stuff Today s topics: what happens when we lose snooping new issues: global vs. local cache line state enter the directory issues of increasing
The complete license text can be found at
 SMP & Locking These slides are made distributed under the Creative Commons Attribution 3.0 License, unless otherwise noted on individual slides. You are free: to Share to copy, distribute and transmit
SMP & Locking These slides are made distributed under the Creative Commons Attribution 3.0 License, unless otherwise noted on individual slides. You are free: to Share to copy, distribute and transmit
Algorithms for Scalable Synchronization on Shared Memory Multiprocessors by John M. Mellor Crummey Michael L. Scott
 Algorithms for Scalable Synchronization on Shared Memory Multiprocessors by John M. Mellor Crummey Michael L. Scott Presentation by Joe Izraelevitz Tim Kopp Synchronization Primitives Spin Locks Used for
Algorithms for Scalable Synchronization on Shared Memory Multiprocessors by John M. Mellor Crummey Michael L. Scott Presentation by Joe Izraelevitz Tim Kopp Synchronization Primitives Spin Locks Used for
Interprocess Communication By: Kaushik Vaghani
 Interprocess Communication By: Kaushik Vaghani Background Race Condition: A situation where several processes access and manipulate the same data concurrently and the outcome of execution depends on the
Interprocess Communication By: Kaushik Vaghani Background Race Condition: A situation where several processes access and manipulate the same data concurrently and the outcome of execution depends on the
Priority Inheritance Spin Locks for Multiprocessor Real-Time Systems
 Priority Inheritance Spin Locks for Multiprocessor Real-Time Systems Cai-Dong Wang, Hiroaki Takada, and Ken Sakamura Department of Information Science, Faculty of Science, University of Tokyo 7-3-1 Hongo,
Priority Inheritance Spin Locks for Multiprocessor Real-Time Systems Cai-Dong Wang, Hiroaki Takada, and Ken Sakamura Department of Information Science, Faculty of Science, University of Tokyo 7-3-1 Hongo,
Process- Concept &Process Scheduling OPERATING SYSTEMS
 OPERATING SYSTEMS Prescribed Text Book Operating System Principles, Seventh Edition By Abraham Silberschatz, Peter Baer Galvin and Greg Gagne PROCESS MANAGEMENT Current day computer systems allow multiple
OPERATING SYSTEMS Prescribed Text Book Operating System Principles, Seventh Edition By Abraham Silberschatz, Peter Baer Galvin and Greg Gagne PROCESS MANAGEMENT Current day computer systems allow multiple
MULTIPROCESSORS AND THREAD LEVEL PARALLELISM
 UNIT III MULTIPROCESSORS AND THREAD LEVEL PARALLELISM 1. Symmetric Shared Memory Architectures: The Symmetric Shared Memory Architecture consists of several processors with a single physical memory shared
UNIT III MULTIPROCESSORS AND THREAD LEVEL PARALLELISM 1. Symmetric Shared Memory Architectures: The Symmetric Shared Memory Architecture consists of several processors with a single physical memory shared
Multiprocessor System. Multiprocessor Systems. Bus Based UMA. Types of Multiprocessors (MPs) Cache Consistency. Bus Based UMA. Chapter 8, 8.
 Multiprocessor System Multiprocessor Systems Chapter 8, 8.1 We will look at shared-memory multiprocessors More than one processor sharing the same memory A single CPU can only go so fast Use more than
Multiprocessor System Multiprocessor Systems Chapter 8, 8.1 We will look at shared-memory multiprocessors More than one processor sharing the same memory A single CPU can only go so fast Use more than
Reactive Synchronization Algorithms for Multiprocessors
 Synchronization Algorithms for Multiprocessors Beng-Hong Lim and Anant Agarwal Laboratory for Computer Science Massachusetts Institute of Technology Cambridge, MA 039 Abstract Synchronization algorithms
Synchronization Algorithms for Multiprocessors Beng-Hong Lim and Anant Agarwal Laboratory for Computer Science Massachusetts Institute of Technology Cambridge, MA 039 Abstract Synchronization algorithms
Scalable Locking. Adam Belay
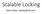 Scalable Locking Adam Belay Problem: Locks can ruin performance 12 finds/sec 9 6 Locking overhead dominates 3 0 0 6 12 18 24 30 36 42 48 Cores Problem: Locks can ruin performance the locks
Scalable Locking Adam Belay Problem: Locks can ruin performance 12 finds/sec 9 6 Locking overhead dominates 3 0 0 6 12 18 24 30 36 42 48 Cores Problem: Locks can ruin performance the locks
Multiprocessor Systems. COMP s1
 Multiprocessor Systems 1 Multiprocessor System We will look at shared-memory multiprocessors More than one processor sharing the same memory A single CPU can only go so fast Use more than one CPU to improve
Multiprocessor Systems 1 Multiprocessor System We will look at shared-memory multiprocessors More than one processor sharing the same memory A single CPU can only go so fast Use more than one CPU to improve
Multiprocessors and Locking
 Types of Multiprocessors (MPs) Uniform memory-access (UMA) MP Access to all memory occurs at the same speed for all processors. Multiprocessors and Locking COMP9242 2008/S2 Week 12 Part 1 Non-uniform memory-access
Types of Multiprocessors (MPs) Uniform memory-access (UMA) MP Access to all memory occurs at the same speed for all processors. Multiprocessors and Locking COMP9242 2008/S2 Week 12 Part 1 Non-uniform memory-access
250P: Computer Systems Architecture. Lecture 14: Synchronization. Anton Burtsev March, 2019
 250P: Computer Systems Architecture Lecture 14: Synchronization Anton Burtsev March, 2019 Coherence and Synchronization Topics: synchronization primitives (Sections 5.4-5.5) 2 Constructing Locks Applications
250P: Computer Systems Architecture Lecture 14: Synchronization Anton Burtsev March, 2019 Coherence and Synchronization Topics: synchronization primitives (Sections 5.4-5.5) 2 Constructing Locks Applications
Hardware: BBN Butterfly
 Algorithms for Scalable Synchronization on Shared-Memory Multiprocessors John M. Mellor-Crummey and Michael L. Scott Presented by Charles Lehner and Matt Graichen Hardware: BBN Butterfly shared-memory
Algorithms for Scalable Synchronization on Shared-Memory Multiprocessors John M. Mellor-Crummey and Michael L. Scott Presented by Charles Lehner and Matt Graichen Hardware: BBN Butterfly shared-memory
Operating Systems. Designed and Presented by Dr. Ayman Elshenawy Elsefy
 Operating Systems Designed and Presented by Dr. Ayman Elshenawy Elsefy Dept. of Systems & Computer Eng.. AL-AZHAR University Website : eaymanelshenawy.wordpress.com Email : eaymanelshenawy@yahoo.com Reference
Operating Systems Designed and Presented by Dr. Ayman Elshenawy Elsefy Dept. of Systems & Computer Eng.. AL-AZHAR University Website : eaymanelshenawy.wordpress.com Email : eaymanelshenawy@yahoo.com Reference
Lock cohorting: A general technique for designing NUMA locks
 Lock cohorting: A general technique for designing NUMA locks The MIT Faculty has made this article openly available. Please share how this access benefits you. Your story matters. Citation As Published
Lock cohorting: A general technique for designing NUMA locks The MIT Faculty has made this article openly available. Please share how this access benefits you. Your story matters. Citation As Published
Relative Performance of Preemption-Safe Locking and Non-Blocking Synchronization on Multiprogrammed Shared Memory Multiprocessors
 Relative Performance of Preemption-Safe Locking and Non-Blocking Synchronization on Multiprogrammed Shared Memory Multiprocessors Maged M. Michael Michael L. Scott University of Rochester Department of
Relative Performance of Preemption-Safe Locking and Non-Blocking Synchronization on Multiprogrammed Shared Memory Multiprocessors Maged M. Michael Michael L. Scott University of Rochester Department of
AST: scalable synchronization Supervisors guide 2002
 AST: scalable synchronization Supervisors guide 00 tim.harris@cl.cam.ac.uk These are some notes about the topics that I intended the questions to draw on. Do let me know if you find the questions unclear
AST: scalable synchronization Supervisors guide 00 tim.harris@cl.cam.ac.uk These are some notes about the topics that I intended the questions to draw on. Do let me know if you find the questions unclear
Distributed Operating Systems
 Distributed Operating Systems Synchronization in Parallel Systems Marcus Völp 2009 1 Topics Synchronization Locking Analysis / Comparison Distributed Operating Systems 2009 Marcus Völp 2 Overview Introduction
Distributed Operating Systems Synchronization in Parallel Systems Marcus Völp 2009 1 Topics Synchronization Locking Analysis / Comparison Distributed Operating Systems 2009 Marcus Völp 2 Overview Introduction
Mutual Exclusion Algorithms with Constant RMR Complexity and Wait-Free Exit Code
 Mutual Exclusion Algorithms with Constant RMR Complexity and Wait-Free Exit Code Rotem Dvir 1 and Gadi Taubenfeld 2 1 The Interdisciplinary Center, P.O.Box 167, Herzliya 46150, Israel rotem.dvir@gmail.com
Mutual Exclusion Algorithms with Constant RMR Complexity and Wait-Free Exit Code Rotem Dvir 1 and Gadi Taubenfeld 2 1 The Interdisciplinary Center, P.O.Box 167, Herzliya 46150, Israel rotem.dvir@gmail.com
Lecture 9: Multiprocessor OSs & Synchronization. CSC 469H1F Fall 2006 Angela Demke Brown
 Lecture 9: Multiprocessor OSs & Synchronization CSC 469H1F Fall 2006 Angela Demke Brown The Problem Coordinated management of shared resources Resources may be accessed by multiple threads Need to control
Lecture 9: Multiprocessor OSs & Synchronization CSC 469H1F Fall 2006 Angela Demke Brown The Problem Coordinated management of shared resources Resources may be accessed by multiple threads Need to control
Synchronization. Jinkyu Jeong Computer Systems Laboratory Sungkyunkwan University
 Synchronization Jinkyu Jeong (jinkyu@skku.edu) Computer Systems Laboratory Sungkyunkwan University http://csl.skku.edu Types of Synchronization Mutual Exclusion Locks Event Synchronization Global or group-based
Synchronization Jinkyu Jeong (jinkyu@skku.edu) Computer Systems Laboratory Sungkyunkwan University http://csl.skku.edu Types of Synchronization Mutual Exclusion Locks Event Synchronization Global or group-based
Memory Consistency Models
 Memory Consistency Models Contents of Lecture 3 The need for memory consistency models The uniprocessor model Sequential consistency Relaxed memory models Weak ordering Release consistency Jonas Skeppstedt
Memory Consistency Models Contents of Lecture 3 The need for memory consistency models The uniprocessor model Sequential consistency Relaxed memory models Weak ordering Release consistency Jonas Skeppstedt
OPERATING SYSTEMS. Prescribed Text Book. Operating System Principles, Seventh Edition. Abraham Silberschatz, Peter Baer Galvin and Greg Gagne
 OPERATING SYSTEMS Prescribed Text Book Operating System Principles, Seventh Edition By Abraham Silberschatz, Peter Baer Galvin and Greg Gagne 1 DEADLOCKS In a multi programming environment, several processes
OPERATING SYSTEMS Prescribed Text Book Operating System Principles, Seventh Edition By Abraham Silberschatz, Peter Baer Galvin and Greg Gagne 1 DEADLOCKS In a multi programming environment, several processes
Synchronization. Jinkyu Jeong Computer Systems Laboratory Sungkyunkwan University
 Synchronization Jinkyu Jeong (jinkyu@skku.edu) Computer Systems Laboratory Sungkyunkwan University http://csl.skku.edu SSE3054: Multicore Systems, Spring 2017, Jinkyu Jeong (jinkyu@skku.edu) Types of Synchronization
Synchronization Jinkyu Jeong (jinkyu@skku.edu) Computer Systems Laboratory Sungkyunkwan University http://csl.skku.edu SSE3054: Multicore Systems, Spring 2017, Jinkyu Jeong (jinkyu@skku.edu) Types of Synchronization
Computer Engineering II Solution to Exercise Sheet Chapter 10
 Distributed Computing FS 2017 Prof. R. Wattenhofer Computer Engineering II Solution to Exercise Sheet Chapter 10 Quiz 1 Quiz a) The AtomicBoolean utilizes an atomic version of getandset() implemented in
Distributed Computing FS 2017 Prof. R. Wattenhofer Computer Engineering II Solution to Exercise Sheet Chapter 10 Quiz 1 Quiz a) The AtomicBoolean utilizes an atomic version of getandset() implemented in
Concurrent Preliminaries
 Concurrent Preliminaries Sagi Katorza Tel Aviv University 09/12/2014 1 Outline Hardware infrastructure Hardware primitives Mutual exclusion Work sharing and termination detection Concurrent data structures
Concurrent Preliminaries Sagi Katorza Tel Aviv University 09/12/2014 1 Outline Hardware infrastructure Hardware primitives Mutual exclusion Work sharing and termination detection Concurrent data structures
Remaining Contemplation Questions
 Process Synchronisation Remaining Contemplation Questions 1. The first known correct software solution to the critical-section problem for two processes was developed by Dekker. The two processes, P0 and
Process Synchronisation Remaining Contemplation Questions 1. The first known correct software solution to the critical-section problem for two processes was developed by Dekker. The two processes, P0 and
Spinlocks. Spinlocks. Message Systems, Inc. April 8, 2011
 Spinlocks Samy Al Bahra Devon H. O Dell Message Systems, Inc. April 8, 2011 Introduction Mutexes A mutex is an object which implements acquire and relinquish operations such that the execution following
Spinlocks Samy Al Bahra Devon H. O Dell Message Systems, Inc. April 8, 2011 Introduction Mutexes A mutex is an object which implements acquire and relinquish operations such that the execution following
Role of Synchronization. CS 258 Parallel Computer Architecture Lecture 23. Hardware-Software Trade-offs in Synchronization and Data Layout
 CS 28 Parallel Computer Architecture Lecture 23 Hardware-Software Trade-offs in Synchronization and Data Layout April 21, 2008 Prof John D. Kubiatowicz http://www.cs.berkeley.edu/~kubitron/cs28 Role of
CS 28 Parallel Computer Architecture Lecture 23 Hardware-Software Trade-offs in Synchronization and Data Layout April 21, 2008 Prof John D. Kubiatowicz http://www.cs.berkeley.edu/~kubitron/cs28 Role of
Midterm Exam Amy Murphy 6 March 2002
 University of Rochester Midterm Exam Amy Murphy 6 March 2002 Computer Systems (CSC2/456) Read before beginning: Please write clearly. Illegible answers cannot be graded. Be sure to identify all of your
University of Rochester Midterm Exam Amy Murphy 6 March 2002 Computer Systems (CSC2/456) Read before beginning: Please write clearly. Illegible answers cannot be graded. Be sure to identify all of your
Chapter 8. Multiprocessors. In-Cheol Park Dept. of EE, KAIST
 Chapter 8. Multiprocessors In-Cheol Park Dept. of EE, KAIST Can the rapid rate of uniprocessor performance growth be sustained indefinitely? If the pace does slow down, multiprocessor architectures will
Chapter 8. Multiprocessors In-Cheol Park Dept. of EE, KAIST Can the rapid rate of uniprocessor performance growth be sustained indefinitely? If the pace does slow down, multiprocessor architectures will
Spin Locks and Contention. Companion slides for The Art of Multiprocessor Programming by Maurice Herlihy & Nir Shavit
 Spin Locks and Contention Companion slides for The Art of Multiprocessor Programming by Maurice Herlihy & Nir Shavit Focus so far: Correctness and Progress Models Accurate (we never lied to you) But idealized
Spin Locks and Contention Companion slides for The Art of Multiprocessor Programming by Maurice Herlihy & Nir Shavit Focus so far: Correctness and Progress Models Accurate (we never lied to you) But idealized
Advanced Multiprocessor Programming: Locks
 Advanced Multiprocessor Programming: Locks Martin Wimmer, Jesper Larsson Träff TU Wien 20th April, 2015 Wimmer, Träff AMP SS15 1 / 31 Locks we have seen so far Peterson Lock ilter Lock Bakery Lock These
Advanced Multiprocessor Programming: Locks Martin Wimmer, Jesper Larsson Träff TU Wien 20th April, 2015 Wimmer, Träff AMP SS15 1 / 31 Locks we have seen so far Peterson Lock ilter Lock Bakery Lock These
Concurrency, Mutual Exclusion and Synchronization C H A P T E R 5
 Concurrency, Mutual Exclusion and Synchronization C H A P T E R 5 Multiple Processes OS design is concerned with the management of processes and threads: Multiprogramming Multiprocessing Distributed processing
Concurrency, Mutual Exclusion and Synchronization C H A P T E R 5 Multiple Processes OS design is concerned with the management of processes and threads: Multiprogramming Multiprocessing Distributed processing
Locks Chapter 4. Overview. Introduction Spin Locks. Queue locks. Roger Wattenhofer. Test-and-Set & Test-and-Test-and-Set Backoff lock
 Locks Chapter 4 Roger Wattenhofer ETH Zurich Distributed Computing www.disco.ethz.ch Overview Introduction Spin Locks Test-and-Set & Test-and-Test-and-Set Backoff lock Queue locks 4/2 1 Introduction: From
Locks Chapter 4 Roger Wattenhofer ETH Zurich Distributed Computing www.disco.ethz.ch Overview Introduction Spin Locks Test-and-Set & Test-and-Test-and-Set Backoff lock Queue locks 4/2 1 Introduction: From
Lecture 19: Synchronization. CMU : Parallel Computer Architecture and Programming (Spring 2012)
 Lecture 19: Synchronization CMU 15-418: Parallel Computer Architecture and Programming (Spring 2012) Announcements Assignment 4 due tonight at 11:59 PM Synchronization primitives (that we have or will
Lecture 19: Synchronization CMU 15-418: Parallel Computer Architecture and Programming (Spring 2012) Announcements Assignment 4 due tonight at 11:59 PM Synchronization primitives (that we have or will
Midterm Exam Amy Murphy 19 March 2003
 University of Rochester Midterm Exam Amy Murphy 19 March 2003 Computer Systems (CSC2/456) Read before beginning: Please write clearly. Illegible answers cannot be graded. Be sure to identify all of your
University of Rochester Midterm Exam Amy Murphy 19 March 2003 Computer Systems (CSC2/456) Read before beginning: Please write clearly. Illegible answers cannot be graded. Be sure to identify all of your
Process Synchronisation (contd.) Deadlock. Operating Systems. Spring CS5212
 Operating Systems Spring 2009-2010 Outline Process Synchronisation (contd.) 1 Process Synchronisation (contd.) 2 Announcements Presentations: will be held on last teaching week during lectures make a 20-minute
Operating Systems Spring 2009-2010 Outline Process Synchronisation (contd.) 1 Process Synchronisation (contd.) 2 Announcements Presentations: will be held on last teaching week during lectures make a 20-minute
Atomic Transactions in Cilk
 Atomic Transactions in Jim Sukha 12-13-03 Contents 1 Introduction 2 1.1 Determinacy Races in Multi-Threaded Programs......................... 2 1.2 Atomicity through Transactions...................................
Atomic Transactions in Jim Sukha 12-13-03 Contents 1 Introduction 2 1.1 Determinacy Races in Multi-Threaded Programs......................... 2 1.2 Atomicity through Transactions...................................
Virtual Memory - Overview. Programmers View. Virtual Physical. Virtual Physical. Program has its own virtual memory space.
 Virtual Memory - Overview Programmers View Process runs in virtual (logical) space may be larger than physical. Paging can implement virtual. Which pages to have in? How much to allow each process? Program
Virtual Memory - Overview Programmers View Process runs in virtual (logical) space may be larger than physical. Paging can implement virtual. Which pages to have in? How much to allow each process? Program
CMSC Computer Architecture Lecture 15: Memory Consistency and Synchronization. Prof. Yanjing Li University of Chicago
 CMSC 22200 Computer Architecture Lecture 15: Memory Consistency and Synchronization Prof. Yanjing Li University of Chicago Administrative Stuff! Lab 5 (multi-core) " Basic requirements: out later today
CMSC 22200 Computer Architecture Lecture 15: Memory Consistency and Synchronization Prof. Yanjing Li University of Chicago Administrative Stuff! Lab 5 (multi-core) " Basic requirements: out later today
Real-Time Scalability of Nested Spin Locks. Hiroaki Takada and Ken Sakamura. Faculty of Science, University of Tokyo
 Real-Time Scalability of Nested Spin Locks Hiroaki Takada and Ken Sakamura Department of Information Science, Faculty of Science, University of Tokyo 7-3-1, Hongo, Bunkyo-ku, Tokyo 113, Japan Abstract
Real-Time Scalability of Nested Spin Locks Hiroaki Takada and Ken Sakamura Department of Information Science, Faculty of Science, University of Tokyo 7-3-1, Hongo, Bunkyo-ku, Tokyo 113, Japan Abstract
What is the Race Condition? And what is its solution? What is a critical section? And what is the critical section problem?
 What is the Race Condition? And what is its solution? Race Condition: Where several processes access and manipulate the same data concurrently and the outcome of the execution depends on the particular
What is the Race Condition? And what is its solution? Race Condition: Where several processes access and manipulate the same data concurrently and the outcome of the execution depends on the particular
A Concurrent Skip List Implementation with RTM and HLE
 A Concurrent Skip List Implementation with RTM and HLE Fan Gao May 14, 2014 1 Background Semester Performed: Spring, 2014 Instructor: Maurice Herlihy The main idea of my project is to implement a skip
A Concurrent Skip List Implementation with RTM and HLE Fan Gao May 14, 2014 1 Background Semester Performed: Spring, 2014 Instructor: Maurice Herlihy The main idea of my project is to implement a skip
GLocks: Efficient Support for Highly- Contended Locks in Many-Core CMPs
 GLocks: Efficient Support for Highly- Contended Locks in Many-Core CMPs Authors: Jos e L. Abell an, Juan Fern andez and Manuel E. Acacio Presenter: Guoliang Liu Outline Introduction Motivation Background
GLocks: Efficient Support for Highly- Contended Locks in Many-Core CMPs Authors: Jos e L. Abell an, Juan Fern andez and Manuel E. Acacio Presenter: Guoliang Liu Outline Introduction Motivation Background
Spin Locks and Contention. Companion slides for The Art of Multiprocessor Programming by Maurice Herlihy & Nir Shavit
 Spin Locks and Contention Companion slides for The Art of Multiprocessor Programming by Maurice Herlihy & Nir Shavit Real world concurrency Understanding hardware architecture What is contention How to
Spin Locks and Contention Companion slides for The Art of Multiprocessor Programming by Maurice Herlihy & Nir Shavit Real world concurrency Understanding hardware architecture What is contention How to
Part 1: Concepts and Hardware- Based Approaches
 Part 1: Concepts and Hardware- Based Approaches CS5204-Operating Systems Introduction Provide support for concurrent activity using transactionstyle semantics without explicit locking Avoids problems with
Part 1: Concepts and Hardware- Based Approaches CS5204-Operating Systems Introduction Provide support for concurrent activity using transactionstyle semantics without explicit locking Avoids problems with
CPSC/ECE 3220 Summer 2018 Exam 2 No Electronics.
 CPSC/ECE 3220 Summer 2018 Exam 2 No Electronics. Name: Write one of the words or terms from the following list into the blank appearing to the left of the appropriate definition. Note that there are more
CPSC/ECE 3220 Summer 2018 Exam 2 No Electronics. Name: Write one of the words or terms from the following list into the blank appearing to the left of the appropriate definition. Note that there are more
CHAPTER 6: PROCESS SYNCHRONIZATION
 CHAPTER 6: PROCESS SYNCHRONIZATION The slides do not contain all the information and cannot be treated as a study material for Operating System. Please refer the text book for exams. TOPICS Background
CHAPTER 6: PROCESS SYNCHRONIZATION The slides do not contain all the information and cannot be treated as a study material for Operating System. Please refer the text book for exams. TOPICS Background
CS5460: Operating Systems
 CS5460: Operating Systems Lecture 9: Implementing Synchronization (Chapter 6) Multiprocessor Memory Models Uniprocessor memory is simple Every load from a location retrieves the last value stored to that
CS5460: Operating Systems Lecture 9: Implementing Synchronization (Chapter 6) Multiprocessor Memory Models Uniprocessor memory is simple Every load from a location retrieves the last value stored to that
1 Multiprocessors. 1.1 Kinds of Processes. COMP 242 Class Notes Section 9: Multiprocessor Operating Systems
 COMP 242 Class Notes Section 9: Multiprocessor Operating Systems 1 Multiprocessors As we saw earlier, a multiprocessor consists of several processors sharing a common memory. The memory is typically divided
COMP 242 Class Notes Section 9: Multiprocessor Operating Systems 1 Multiprocessors As we saw earlier, a multiprocessor consists of several processors sharing a common memory. The memory is typically divided
CPSC/ECE 3220 Summer 2017 Exam 2
 CPSC/ECE 3220 Summer 2017 Exam 2 Name: Part 1: Word Bank Write one of the words or terms from the following list into the blank appearing to the left of the appropriate definition. Note that there are
CPSC/ECE 3220 Summer 2017 Exam 2 Name: Part 1: Word Bank Write one of the words or terms from the following list into the blank appearing to the left of the appropriate definition. Note that there are
Chapter 5. Multiprocessors and Thread-Level Parallelism
 Computer Architecture A Quantitative Approach, Fifth Edition Chapter 5 Multiprocessors and Thread-Level Parallelism 1 Introduction Thread-Level parallelism Have multiple program counters Uses MIMD model
Computer Architecture A Quantitative Approach, Fifth Edition Chapter 5 Multiprocessors and Thread-Level Parallelism 1 Introduction Thread-Level parallelism Have multiple program counters Uses MIMD model
Memory Consistency. Challenges. Program order Memory access order
 Memory Consistency Memory Consistency Memory Consistency Reads and writes of the shared memory face consistency problem Need to achieve controlled consistency in memory events Shared memory behavior determined
Memory Consistency Memory Consistency Memory Consistency Reads and writes of the shared memory face consistency problem Need to achieve controlled consistency in memory events Shared memory behavior determined
Lecture 26: Multiprocessing continued Computer Architecture and Systems Programming ( )
 Systems Group Department of Computer Science ETH Zürich Lecture 26: Multiprocessing continued Computer Architecture and Systems Programming (252-0061-00) Timothy Roscoe Herbstsemester 2012 Today Non-Uniform
Systems Group Department of Computer Science ETH Zürich Lecture 26: Multiprocessing continued Computer Architecture and Systems Programming (252-0061-00) Timothy Roscoe Herbstsemester 2012 Today Non-Uniform
Distributed Operating Systems
 Distributed Operating Systems Synchronization in Parallel Systems Marcus Völp 203 Topics Synchronization Locks Performance Distributed Operating Systems 203 Marcus Völp 2 Overview Introduction Hardware
Distributed Operating Systems Synchronization in Parallel Systems Marcus Völp 203 Topics Synchronization Locks Performance Distributed Operating Systems 203 Marcus Völp 2 Overview Introduction Hardware
A Basic Snooping-Based Multi-Processor Implementation
 Lecture 15: A Basic Snooping-Based Multi-Processor Implementation Parallel Computer Architecture and Programming CMU 15-418/15-618, Spring 2015 Tunes Pushing On (Oliver $ & Jimi Jules) Time for the second
Lecture 15: A Basic Snooping-Based Multi-Processor Implementation Parallel Computer Architecture and Programming CMU 15-418/15-618, Spring 2015 Tunes Pushing On (Oliver $ & Jimi Jules) Time for the second
Scalable Reader-Writer Synchronization for Shared-Memory Multiprocessors
 Scalable Reader-Writer Synchronization for Shared-Memory Multiprocessors John M. Mellor-Crummey' (johnmcgrice.edu) Center for Research on Parallel Computation Rice University, P.O. Box 1892 Houston, TX
Scalable Reader-Writer Synchronization for Shared-Memory Multiprocessors John M. Mellor-Crummey' (johnmcgrice.edu) Center for Research on Parallel Computation Rice University, P.O. Box 1892 Houston, TX
Operating Systems: Quiz2 December 15, Class: No. Name:
 Operating Systems: Quiz2 December 15, 2006 Class: No. Name: Part I (30%) Multiple Choice Each of the following questions has only one correct answer. Fill the correct one in the blank in front of each
Operating Systems: Quiz2 December 15, 2006 Class: No. Name: Part I (30%) Multiple Choice Each of the following questions has only one correct answer. Fill the correct one in the blank in front of each
Lecture Notes on Queues
 Lecture Notes on Queues 15-122: Principles of Imperative Computation Frank Pfenning and Jamie Morgenstern Lecture 9 February 14, 2012 1 Introduction In this lecture we introduce queues as a data structure
Lecture Notes on Queues 15-122: Principles of Imperative Computation Frank Pfenning and Jamie Morgenstern Lecture 9 February 14, 2012 1 Introduction In this lecture we introduce queues as a data structure
CSC2/458 Parallel and Distributed Systems Scalable Synchronization
 CSC2/458 Parallel and Distributed Systems Scalable Synchronization Sreepathi Pai February 20, 2018 URCS Outline Scalable Locking Barriers Outline Scalable Locking Barriers An alternative lock ticket lock
CSC2/458 Parallel and Distributed Systems Scalable Synchronization Sreepathi Pai February 20, 2018 URCS Outline Scalable Locking Barriers Outline Scalable Locking Barriers An alternative lock ticket lock
Chapter seven: Deadlock and Postponement
 Chapter seven: Deadlock and Postponement -One problem that arises in multiprogrammed systems is deadlock. A process or thread is in a state of deadlock if it is waiting for a particular event that will
Chapter seven: Deadlock and Postponement -One problem that arises in multiprogrammed systems is deadlock. A process or thread is in a state of deadlock if it is waiting for a particular event that will
Distributed Shared Memory and Memory Consistency Models
 Lectures on distributed systems Distributed Shared Memory and Memory Consistency Models Paul Krzyzanowski Introduction With conventional SMP systems, multiple processors execute instructions in a single
Lectures on distributed systems Distributed Shared Memory and Memory Consistency Models Paul Krzyzanowski Introduction With conventional SMP systems, multiple processors execute instructions in a single
MULTIPROCESSORS AND THREAD-LEVEL. B649 Parallel Architectures and Programming
 MULTIPROCESSORS AND THREAD-LEVEL PARALLELISM B649 Parallel Architectures and Programming Motivation behind Multiprocessors Limitations of ILP (as already discussed) Growing interest in servers and server-performance
MULTIPROCESSORS AND THREAD-LEVEL PARALLELISM B649 Parallel Architectures and Programming Motivation behind Multiprocessors Limitations of ILP (as already discussed) Growing interest in servers and server-performance
Non-Blocking Timeout in Scalable Queue-Based Spin Locks
 Non-Blocking Timeout in Scalable Queue-Based Spin Locks Michael L. Scott Technical Report #773 Department of Computer Science University of Rochester Rochester, NY 14627-0226 scott@cs.rochester.edu Λ February
Non-Blocking Timeout in Scalable Queue-Based Spin Locks Michael L. Scott Technical Report #773 Department of Computer Science University of Rochester Rochester, NY 14627-0226 scott@cs.rochester.edu Λ February
MULTIPROCESSORS AND THREAD-LEVEL PARALLELISM. B649 Parallel Architectures and Programming
 MULTIPROCESSORS AND THREAD-LEVEL PARALLELISM B649 Parallel Architectures and Programming Motivation behind Multiprocessors Limitations of ILP (as already discussed) Growing interest in servers and server-performance
MULTIPROCESSORS AND THREAD-LEVEL PARALLELISM B649 Parallel Architectures and Programming Motivation behind Multiprocessors Limitations of ILP (as already discussed) Growing interest in servers and server-performance
Concurrency, Thread. Dongkun Shin, SKKU
 Concurrency, Thread 1 Thread Classic view a single point of execution within a program a single PC where instructions are being fetched from and executed), Multi-threaded program Has more than one point
Concurrency, Thread 1 Thread Classic view a single point of execution within a program a single PC where instructions are being fetched from and executed), Multi-threaded program Has more than one point
Enhancing Linux Scheduler Scalability
 Enhancing Linux Scheduler Scalability Mike Kravetz IBM Linux Technology Center Hubertus Franke, Shailabh Nagar, Rajan Ravindran IBM Thomas J. Watson Research Center {mkravetz,frankeh,nagar,rajancr}@us.ibm.com
Enhancing Linux Scheduler Scalability Mike Kravetz IBM Linux Technology Center Hubertus Franke, Shailabh Nagar, Rajan Ravindran IBM Thomas J. Watson Research Center {mkravetz,frankeh,nagar,rajancr}@us.ibm.com
15 418/618 Project Final Report Concurrent Lock free BST
 15 418/618 Project Final Report Concurrent Lock free BST Names: Swapnil Pimpale, Romit Kudtarkar AndrewID: spimpale, rkudtark 1.0 SUMMARY We implemented two concurrent binary search trees (BSTs): a fine
15 418/618 Project Final Report Concurrent Lock free BST Names: Swapnil Pimpale, Romit Kudtarkar AndrewID: spimpale, rkudtark 1.0 SUMMARY We implemented two concurrent binary search trees (BSTs): a fine
Chapter 7 The Potential of Special-Purpose Hardware
 Chapter 7 The Potential of Special-Purpose Hardware The preceding chapters have described various implementation methods and performance data for TIGRE. This chapter uses those data points to propose architecture
Chapter 7 The Potential of Special-Purpose Hardware The preceding chapters have described various implementation methods and performance data for TIGRE. This chapter uses those data points to propose architecture
NUMA-aware Reader-Writer Locks. Tom Herold, Marco Lamina NUMA Seminar
 04.02.2015 NUMA Seminar Agenda 1. Recap: Locking 2. in NUMA Systems 3. RW 4. Implementations 5. Hands On Why Locking? Parallel tasks access shared resources : Synchronization mechanism in concurrent environments
04.02.2015 NUMA Seminar Agenda 1. Recap: Locking 2. in NUMA Systems 3. RW 4. Implementations 5. Hands On Why Locking? Parallel tasks access shared resources : Synchronization mechanism in concurrent environments
Ch 4 : CPU scheduling
 Ch 4 : CPU scheduling It's the basis of multiprogramming operating systems. By switching the CPU among processes, the operating system can make the computer more productive In a single-processor system,
Ch 4 : CPU scheduling It's the basis of multiprogramming operating systems. By switching the CPU among processes, the operating system can make the computer more productive In a single-processor system,
Network Working Group Request for Comments: 1046 ISI February A Queuing Algorithm to Provide Type-of-Service for IP Links
 Network Working Group Request for Comments: 1046 W. Prue J. Postel ISI February 1988 A Queuing Algorithm to Provide Type-of-Service for IP Links Status of this Memo This memo is intended to explore how
Network Working Group Request for Comments: 1046 W. Prue J. Postel ISI February 1988 A Queuing Algorithm to Provide Type-of-Service for IP Links Status of this Memo This memo is intended to explore how
Module 7: Synchronization Lecture 13: Introduction to Atomic Primitives. The Lecture Contains: Synchronization. Waiting Algorithms.
 The Lecture Contains: Synchronization Waiting Algorithms Implementation Hardwired Locks Software Locks Hardware Support Atomic Exchange Test & Set Fetch & op Compare & Swap Traffic of Test & Set Backoff
The Lecture Contains: Synchronization Waiting Algorithms Implementation Hardwired Locks Software Locks Hardware Support Atomic Exchange Test & Set Fetch & op Compare & Swap Traffic of Test & Set Backoff
Today. SMP architecture. SMP architecture. Lecture 26: Multiprocessing continued Computer Architecture and Systems Programming ( )
 Lecture 26: Multiprocessing continued Computer Architecture and Systems Programming (252-0061-00) Timothy Roscoe Herbstsemester 2012 Systems Group Department of Computer Science ETH Zürich SMP architecture
Lecture 26: Multiprocessing continued Computer Architecture and Systems Programming (252-0061-00) Timothy Roscoe Herbstsemester 2012 Systems Group Department of Computer Science ETH Zürich SMP architecture
CSL373: Lecture 5 Deadlocks (no process runnable) + Scheduling (> 1 process runnable)
 CSL373: Lecture 5 Deadlocks (no process runnable) + Scheduling (> 1 process runnable) Past & Present Have looked at two constraints: Mutual exclusion constraint between two events is a requirement that
CSL373: Lecture 5 Deadlocks (no process runnable) + Scheduling (> 1 process runnable) Past & Present Have looked at two constraints: Mutual exclusion constraint between two events is a requirement that
Simple, Fast, and Practical Non-Blocking and Blocking Concurrent Queue Algorithms
 Simple, Fast, and Practical Non-Blocking and Blocking Concurrent Queue Algorithms Maged M. Michael Michael L. Scott Department of Computer Science University of Rochester Rochester, NY 14627-0226 fmichael,scottg@cs.rochester.edu
Simple, Fast, and Practical Non-Blocking and Blocking Concurrent Queue Algorithms Maged M. Michael Michael L. Scott Department of Computer Science University of Rochester Rochester, NY 14627-0226 fmichael,scottg@cs.rochester.edu
Hoard: A Fast, Scalable, and Memory-Efficient Allocator for Shared-Memory Multiprocessors
 Hoard: A Fast, Scalable, and Memory-Efficient Allocator for Shared-Memory Multiprocessors Emery D. Berger Robert D. Blumofe femery,rdbg@cs.utexas.edu Department of Computer Sciences The University of Texas
Hoard: A Fast, Scalable, and Memory-Efficient Allocator for Shared-Memory Multiprocessors Emery D. Berger Robert D. Blumofe femery,rdbg@cs.utexas.edu Department of Computer Sciences The University of Texas
CSE 410 Final Exam 6/09/09. Suppose we have a memory and a direct-mapped cache with the following characteristics.
 Question 1. (10 points) (Caches) Suppose we have a memory and a direct-mapped cache with the following characteristics. Memory is byte addressable Memory addresses are 16 bits (i.e., the total memory size
Question 1. (10 points) (Caches) Suppose we have a memory and a direct-mapped cache with the following characteristics. Memory is byte addressable Memory addresses are 16 bits (i.e., the total memory size
Design Patterns for Real-Time Computer Music Systems
 Design Patterns for Real-Time Computer Music Systems Roger B. Dannenberg and Ross Bencina 4 September 2005 This document contains a set of design patterns for real time systems, particularly for computer
Design Patterns for Real-Time Computer Music Systems Roger B. Dannenberg and Ross Bencina 4 September 2005 This document contains a set of design patterns for real time systems, particularly for computer
Barrelfish Project ETH Zurich. Message Notifications
 Barrelfish Project ETH Zurich Message Notifications Barrelfish Technical Note 9 Barrelfish project 16.06.2010 Systems Group Department of Computer Science ETH Zurich CAB F.79, Universitätstrasse 6, Zurich
Barrelfish Project ETH Zurich Message Notifications Barrelfish Technical Note 9 Barrelfish project 16.06.2010 Systems Group Department of Computer Science ETH Zurich CAB F.79, Universitätstrasse 6, Zurich
Tasks. Task Implementation and management
 Tasks Task Implementation and management Tasks Vocab Absolute time - real world time Relative time - time referenced to some event Interval - any slice of time characterized by start & end times Duration
Tasks Task Implementation and management Tasks Vocab Absolute time - real world time Relative time - time referenced to some event Interval - any slice of time characterized by start & end times Duration
Computer Architecture. A Quantitative Approach, Fifth Edition. Chapter 5. Multiprocessors and Thread-Level Parallelism
 Computer Architecture A Quantitative Approach, Fifth Edition Chapter 5 Multiprocessors and Thread-Level Parallelism 1 Introduction Thread-Level parallelism Have multiple program counters Uses MIMD model
Computer Architecture A Quantitative Approach, Fifth Edition Chapter 5 Multiprocessors and Thread-Level Parallelism 1 Introduction Thread-Level parallelism Have multiple program counters Uses MIMD model
SSC - Concurrency and Multi-threading Advanced topics about liveness
 SSC - Concurrency and Multi-threading Advanced topics about liveness Shan He School for Computational Science University of Birmingham Module 06-19321: SSC Outline Outline of Topics Review what we learned
SSC - Concurrency and Multi-threading Advanced topics about liveness Shan He School for Computational Science University of Birmingham Module 06-19321: SSC Outline Outline of Topics Review what we learned
Processes, PCB, Context Switch
 THE HONG KONG POLYTECHNIC UNIVERSITY Department of Electronic and Information Engineering EIE 272 CAOS Operating Systems Part II Processes, PCB, Context Switch Instructor Dr. M. Sakalli enmsaka@eie.polyu.edu.hk
THE HONG KONG POLYTECHNIC UNIVERSITY Department of Electronic and Information Engineering EIE 272 CAOS Operating Systems Part II Processes, PCB, Context Switch Instructor Dr. M. Sakalli enmsaka@eie.polyu.edu.hk
Distributed Systems Synchronization. Marcus Völp 2007
 Distributed Systems Synchronization Marcus Völp 2007 1 Purpose of this Lecture Synchronization Locking Analysis / Comparison Distributed Operating Systems 2007 Marcus Völp 2 Overview Introduction Hardware
Distributed Systems Synchronization Marcus Völp 2007 1 Purpose of this Lecture Synchronization Locking Analysis / Comparison Distributed Operating Systems 2007 Marcus Völp 2 Overview Introduction Hardware
Readers-Writers Problem. Implementing shared locks. shared locks (continued) Review: Test-and-set spinlock. Review: Test-and-set on alpha
 Readers-Writers Problem Implementing shared locks Multiple threads may access data - Readers will only observe, not modify data - Writers will change the data Goal: allow multiple readers or one single
Readers-Writers Problem Implementing shared locks Multiple threads may access data - Readers will only observe, not modify data - Writers will change the data Goal: allow multiple readers or one single
Chapter 5 Concurrency: Mutual Exclusion and Synchronization
 Operating Systems: Internals and Design Principles Chapter 5 Concurrency: Mutual Exclusion and Synchronization Seventh Edition By William Stallings Designing correct routines for controlling concurrent
Operating Systems: Internals and Design Principles Chapter 5 Concurrency: Mutual Exclusion and Synchronization Seventh Edition By William Stallings Designing correct routines for controlling concurrent
High Performance Synchronization Algorithms for. Multiprogrammed Multiprocessors. (Extended Abstract)
 High Performance Synchronization Algorithms for Multiprogrammed Multiprocessors (Extended Abstract) Robert W. Wisniewski, Leonidas Kontothanassis, and Michael L. Scott Department of Computer Science University
High Performance Synchronization Algorithms for Multiprogrammed Multiprocessors (Extended Abstract) Robert W. Wisniewski, Leonidas Kontothanassis, and Michael L. Scott Department of Computer Science University
