Manipulation of data structures in a numerical analysis problem solving system-napss
|
|
|
- Esmond Mitchell
- 5 years ago
- Views:
Transcription
1 Manipulation of data structures in a numerical analysis problem solving system-napss by LAWRENCE R. SYMES Purdue University Lafayette, Indiana AIMS OF SYSTEM During the past several years considerable effort has been expended designing and implementing systems which are intended to provide extended capabilities for persons with mathematical problems to solve. Some of them in addition to NAPSS are CULLER FRIED, KLERER MAY, MAP, RECKONER, AMTRAN, and POSE. These systems can be classified as problem solving systems for applied mathematics. Before the advent of these systems the research scientist or engineer used a procedural language such as FORTRAN or ALGOL when he employed the computer to aid him in s.olving a problem. Both of these languages, although they resemble mathematical notation more closely than machine language, are somewhat artificial and contain many unnecessary, from the user's point of view, rules. The artificial appearance and the rules must be mastered before the language can be used. Therefore the scientist or engineer is diverted from his main purpose into becoming a programmer. Even after he has learned the language, its complexity increases the probability of error, and thus red~ces his efficiency. In addition to these difficulties, the user with a mathematical problem had to use program libraries in order to obtain routines for solving commonly occurring problems. These libraries frequently were inadequate and almost always confusing. The routines often were poorly documented and performed little or no monitoring of the accuracy of the results. Thus the user of such a library had to know enough numerical analysis to select the best method for solving problems and to determine the accuracy of the results. NAPSS has been designed to remove some or all of these problems and to offer several other desirable features. It, in some sense, endeavors to have man do what he is best equipped to do and to have the computer do what it is best equipped to do. Six general techniques have been utilized to assist the user in stating and solving his problem. First, the source language used to pre~ent a problem to the computer is similar to normal "text book" mathematical notation. This permits one to use the system without: first having to intensively study the input language. It also reduced the probability of user programming errors, because the user is familiar with the notation. Second, clerical statements used for dimensipning arrays and declaring variables are removed from the source language. These are tasks which the computer can easily perform but which are a constant source of errors if the user does them. Third, N APSS permits the direct manipulation of quantities other than scalars. These include numeric arrays, symbolic expressions, functions, and arrays of functions. This further allows the source language to resemble more closely "text book" form, and thereby leads to fewer statements; hence fewer opportunities for programming errors. Fourth, solve statements are included in the source language. These statements permit the user to state a problem he wishes to solve in a concise, natural form. The user may include parameters such as initial values, the accuracy desired, the method he would like used, or he may omit any or all of the additional parameters. The solve statements invoke routines, polyalgorithms, 4,5 from a built-in library. They attempt to solve the user's problem automatically. They request additional informatio~ as needed and monitor the accuracy of the results in order to insure that it remains within the specified limits. The inclusion of these solve statements greatly. reduces the burden normally imposed on the user. To solve commonly occurring problems with the aid of the solve statements, the user is only required to know how to define the equations for the problem; he is not required to know the numerical analysis involved or 157
2 158 Spring Joint Computer Conference, 1970 even the method used. The method is selected by the system and the accuracy of the results is assured. Fifth, on-line communication between the system and the user is provided by either a teletype or graphic display device. The use of these terminals bring the computer and the user closer together and consequently improve the user's efficiency. Sixth, incremental execution of a program is allowed. This, combined with the use of on-line terminals, creates a closed loop between the user and the system. The user is able to monitor his program during execution and the system is able to request information from the user and point out errors when they arise. This eliminates much of the time that is wasted in preparing and submitting runs of a program which are unproductive because the user tried several fruitless cases, has an incorrect program, or has forgotten to initialize a variable. NAPSS LANGUAGE Rather than present a detailed description of the NAPSS language,1o,12 we describe a sampling of the allowable assignment statements. The arithmetic expression in N APSS permits the \ direct manipulation of numeric scalars, vectors, arrays, symbolic functions and variables which denote symbolic expressions. The user need not worry about the type or mode of the operands; rather, all that need concern him is whether or not the arithmetic expression is mathematically correct. Several examples of arithmetic expressions and assignment statements appear below: i) D ~ (B + C) I D * E I ii) ARRAY ~ ([3, 0:2] 1,2,..., 9)/10 iii) E = VI + V2 j 2 iv) F(X) ~ A X j 2 + B X + C, (X < 0) ~ A X j 2 -BX+C v) G(X) = A X j 2 + B X + C, (X < 0) AXj2-BX+C vi) K (X) [1, 1] ~ X j 2 - B, (X = C) ~ - (X j 2) - B, (X > C) vii) H(X, Y)[5, -2] = G'(X) + J X j A (X ~ 0 TO Y) viii) S ~ "I AM A NAPPS STRING" ix) R[l, 1] ~ S I I "ARRAY ELEMENT" The left arrow operator (~) indicates that the arithmetic expression on the right is to be evaluated and its value is to be assigned to the variable on the left. The value assigned to D is either a scalar or an array depending upon the operands in the expression on the right; while the value assigned to ARRAY is a 3 by 3 array. The equals sign (=) has the more mathematical meaning. Statement three establishes that a future occurrence of E is equivalent to the expression VI + V2 j 2. Values are only substituted for the variables in the expression on the right of the = when a value of the variable on the left is needed. Thus if the value of VI or V2 should change between the definition of E and the use of E this is reflected in the value of E. Variables defined to the left of an = are referred to as equals variables, and variables defined to the left of an ~ are called left arrow variables, or simply variables. Statements four and five illustrate that a symbolic function may be assigned different definitions on different domains. The difference between statements four and five is similar to the difference between statements two and thre~. In the definition of F the variables A, B, and C have their current values substituted for them, while in the definition of G they do not. Values are only substituted for A, B, and C when a value of the function G is needed. Functions defined to the left of an = sign are called equals functions and functions defined to the left of an ~ are called left arrow functions. Statements six and seven illustrate how arrays of functions are defined. All the elements in array of functions must have the same number of arguments and they all must be either left arrow or equals functions. Statement eight assigns to S a string, and statement nine assigns a string to an element of an array. Although N APSS is intended primarily as a problem statement language, the features of a procedural language have been included to increase its power for the user who wishes to create a personal library of NAPSS routines. External and internal procedures may be written in NAPSS. The use of these facilities is optional. The casual user need not be concerned with the rules that procedures introduce, for he can employ the system on what is called console level. On console level the user does not set up any procedures. Statements are entered without having to go through any initial set up, and are normally executed as they are received. OVER-ALL STRUCTURE OF THE SYSTEM The N APSS system currently running on the Control Data 6500 at Purdue University consists of four main modules: the supervisor, the compiler, the interpreter and the editor. These modules are composed of 115
3 lvlanipulation of Data Structures 159 different routines, which are combined into 28 overlays. Almost all of the system is written in FORTRAN, with the exception of a few machine dependent operations which are restricted to "black-box" modules coded in assembly language. This is doi)-e to aid the goal of machine independence for the system. The supervisor controls the flow into each of the three other modules. It distinguishes between NAPSS sources statements, which are processed by the compiler and edit statements, which are processed by the editor. The supervisor is also responsible for invoking the interpreter when a NAPSS statement is to be executed. N APSS source statements are transformed by the compiler into an internal text which the interpreter processes. This scheme was adopted for several reasons. First, the complexity of the elements to be manipulated and the absence of declarations require execution time decoding of operands. Second, it easily allows for extensions to the system. Third, it gives the user incremental execution. Fourth, it permits extensive error diagnostics and permits error corrections without having to recompile the whole program. Fifth, statements which are repeatedly executed are only translated once into internal text. The internal and source text for each statement is stored in secondary storage. When a statement is to be executed, a copy of the internal text is passed to the interpreter. This reduces considerably the core storage required for a user's programme. Since the system is intended for use in an incrementally executing mode, no reference to secondary storage is normally required to obtain the internal text of a statement. The system operates in one of two modes: suppress mode or execute mode. In the suppress mode, each statement is compiled into internal text and the internal and source text is saved on secondary storage for later execution. Suppress mode is entered by typing the statement.suppress. A block of statements which have been compiled in suppress mode may be executed at any time by typing the statement.go. The normal mode of execution is execute mode. Here, each statement is executed immediately after it has been compiled and a copy of its internal and source text saved in secondary storage. The system automatically enters suppress mode when the user starts a compound statement (a FOR statement) or a procedure. This is necessary because a compound statement cannot be executed until the whole statement is received and a procedure is only executed when invoked. The system re-enters execute mode automatically as soon as the compound statement or procedure is completed. The memory of a N APSS program is made up of a few pages of real memory which reside in core and a larger number of virtual pages of virtual memory which reside in secondary storage and are brought in and out of real memory. Two vectors (one dealing with virtual and the other with real memory) and several pointers are used to keep track of real and virtual memory. Each element in the virtual memory vector is sub~ivided into three twenty-bit bytes. The first byte contains a flag indicating what type of information is stored in the page. The second byte is a switch, used when a page is in real memory to indicate whether or not a copy of the page also resides in secondary storage. The third byte contains the real page number the virtual page is in, when it is in real memory. The elements of the virtual memory vector which denote available pages are linked together. Initially, the element for virtual page one points to the element for virtual page two and the last element contains a zero. When a page of virtual memory is returned to the system its element is again linked to the top of the list of available virtual pages. The real memory vector elements contain one entry per real page. This entry is the number of the virtual page occupying it (zero of it is free). This pointer from real memory to virtual memory is used when a new virtual page is placed in real memory. The virtual page currently in the real page must be copied out into secondary storage if a copy of it is not already there. The amount of core assigned to real memory is dynamic. Pages are removed from the top and bottom of real memory in order to obtain contiguous blocks of storage. Pages are removed from the top of real memory for two purposes: first, to expand the name table, and second, to obtain space for the work pool. Pages are removed from the bottom of real memory to obtain space for local name control blocks during the evaluation of left arrow functions. See Figure 1. The work pool is used to hold arrays when performing array arithmetic. Requests for work pool space are always made in terms of words. However, the amount of real memory assigned to the work pool is always an integral number of pages. When a request is made for work pool space and the work pool is empty, the space supplied is zeroed. When space is requested for the work pool and the work pool is not empty, one of two situations arises. First, the space requested is less than the current size of the work pool. If the difference between the space requested and the current size of th~ work pool amounts to one or more pages, a corresponding number of pages is returned to real memory from the bottom of the work pool. Second, the space requested exceeds the current size of the work pool. If additional pages are obtained from real memory to satisfy the request, they are zeroed. Virtual pages are assigned to real pages sequentially. Thus a virtual page is not removed until all real pages
4 160 Spring Joint Computer Conference, 1970 AEPDA < REAL MEMORY <, r'" 1< ~ INTERPRETER'S... RECURSIVE VARIABLES INTERNAL TEXT TEMPORARY NAME CONTROL BLOCKS RESULT NAME CONTROL BLOCK GLOBAL NAME TABLE NAME TABLE REAL MEMORY PAGE 2 REAL MEMORY PAGE J REAL MEMORY PAGE N-4 REAL MEMORY PAGE N-3 LEFT ARROW FUNCTION LOCAL NAME TABLE REAL MEMORY VECTOR VIRTUAL MEMORY VECTOR <> Figure I-NAPSS memory organization... > AENCBS are assigned a virtual page. This sequential process may be broken whenever space is assigned to the work pool or to hold the local name control blocks for a left arrow function, since, after the space request is satisfied, the next real page to receive a virtual page may no longer belong to real memory. When this occurs the pointer to the next real page to receive a virtual page is reset to the first page now in real memory. - The algorithm for bringing virtual pages into real memory is further modified when the work pool returns a page to real memory. Since the page returned is empty, a virtual page may be placed in it directly, avoiding the possibility of having to save the virtual page currently there in secondary storage. Thus the normal sequential process is interrupted until all pages returned to real memory by the work pool are reused. The system does not assign all of real memory to either the work pool or to space for left arrow function's local name control blocks. A request for real memory space is honored as long as two pages remain in real memory after the request is satisfied. If more space is requested than can be supplied, the request is modified to correspond to the maximum amount of space available. This permits the systen:t to continue if this is adequate. Two pages are required in real memory to facilitate the linking of virtual pages. With two pages in real memory the above algorithm guarantees that the previous and current virtual pages referenced remain in real memory. Thus they may be linked together if necessary, without having to save pointers and reread a virtual page to fill in link information. Associated with each procedure is a name table containing entries for each variable, label and constant in that procedure. The entries, called mime control blocks, are created during compilation when the name or constant is introduced. At this time it contaii).s the name of the variable, and some basic attributes describing how the variable appears in the program. During execution the name control block is used to hold values, pointers to values and a complete set of attributes for the variable. This double usage of the name control block entries poses no problem if compilation and execution are performed separately. But in N APSS the normal mode of operation is to execute each statement as soon as it is compiled. Thus, three situations are possible when a variable is entered in the name table. First, the variable may never have been used before in the program. Second, the variable may have appeared before in the program but have no value assigned to it. Therefore, it is just as it was when the compiler last saw it. Here a limited compatability check is made between the two uses of the variable in the program. For example, the use of a name as a label and as a variable in an arithmetic expression is illegal. Third, the variable has appeared before in the program and has been assigned a value and a complete set of attributes. This enables more checking to be performed. However, the name table routine must not disrupt any of the attribute flags, for 'if any of them are changed the attribute may no longer correspond to the value associated with the name control block. The name table is constructed sequentially. This method requires a minimum amount of space, and permits the name. table to grow dynamically. The name table is expanded by removing pages permanently from real memory. This method of name table construction does require that the name table be searched sequentially. The search goes through the name table from bottom to top. This is done because frequently the greatest percentage of references to a variable occur in the immediate vicinity of its definition.
5 Manipulation of Data Structures 161 A variable which is declared to be global in N different procedures has N + 1 name control blocks associated with it. There is a name control block for the variable in the name table of each of the procedures in which it appears. Only compile time information and a pointer to the N + 1st copy is contained' in these name control blocks. The N + 1st copy is in the global variable name table and contains a complete set of attributes for the variable and its value or a pointer to its value. The N + 1st copy of a global variable's name control block is placed in the global name table when the first procedure is invoked in which the global variable appears, or when the variable is declared global on the console level (the portion of the program not contained in a procedure). When a global variable is added to the global name table and it already appears there, a check is made on the compatability of the attributes. An error results when they conflict. Otherwise a pointer to the N + 1st copy is placed in the procedure's copy of the variable's name control block. A count is kept in the global name control block of the number of procedures referencing the global variable. When a global variable is no longer referenced, then its name control block is removed from the global name table and the storage associated with it is returned to the system. A procedure is compiled when it is defined. To permit it to be linked into the program, the text generated uses only relative. pointers to name table entries, and all linking between entries in a procedure's name table is done with relative pointers. This allows procedure A, for example, to be compiled as an external procedure and to be invoked either directly from the console level or from another procedure which itself is invoked from the console level. The name table for procedure A is placed in the name table after the last entry presently there when it is invoked and a base address is set up. Variables which are not declared to be either local or global in an internal procedure are assumed to be known in the containing block. * After the procedure is compiled an~ a copy of its name table saved, a pass is made through the procedure's name table. This pass goes through the name table from top to bottom and places a copy of the name control block for each variable not declared to be either local or global, in the name table of the containing block. If the variable has appeared in the containing block, a compatability check is made between the attributes. During execution only one name control block is used for the value and attributes of a variable which is not declared to be local or global. This is the name control block entry in the outermost block. The name control * A block is either a procedure or the console level routine. block in the internal procedure is linked to this when the interval procedure is invoked. The linkage is constructed so that only one step is required to obtain the value of the variable regardless of the depth of the procedure. There are three types of name control blocks in different memory areas: ordinary, local for left arrow functions, and temporary. See Figure 1. Temporary name control blocks are used to hold temporary results during the evaluation of an arithmetic expression. A central routine is used to decode variable name control blocks during execution. This routine determines the type of the name control block and handles the linkage betw~en global, and non-local, non-global name control blocks. Three things are returned when a name control block is decoded: the attribute number, the data pointer field and the index of the array AENCBS of first word of the data pointer portion of the name control block. See Figures 1 and 2. DATA STRUCTURES A name control block is the basic unit of all data structures in the system. In some cases it holds the actual values of the variable, and in others it contains a pointer to the actual values and descriptive information. A name control block is made up of seven sixty-bit words of twenty-one twenty bit bytes. See Figure 2. A name control block which denotes a numeric scalar contains the value of the scalar in its data portion. One or two words of the data portion are used depending upon whether the value is single precision real, double precision real or single precision complex. When a name control block denotes a numeric array, the data portion of the name control block contains the actual bounds for the array, the declared bounds for the ITERATION DATA ATTRIBUTE POINTER POINTER FLAGS Figure 2-The layout of a name control block } NAME DATA PORTION
6 162 Spring Joint Computer Conference, 1970 array (these mayor may not have been specified by the programmer), and the number of dimensions in the array. The data pointer byte of the name control block points to where the actual array is stored, by rows, as a contiguous block. The array is stored as a contiguous block tq speed up array operations. If the data pointer byte of the name control block is non zero, a copy of the array exists in secondary storage in the array file. The data pointer is then the number of the record used to store the array and an index in the vector AEP AR. The vector AEP AR contains additional information about the array. Each word in AEP AR is subdivided into three bytes. The first byte contains the reference count for the array. This is incremented by one each time the array appears in a left arrow function definition. The values of all non-parameter variables are fixed when a left arrow function is -defined. The use of a reference count for arrays permits only one copy of the actual array to be kept, and. if the non-parameter array variable is assigned a new value the value of the function will not change. The second byte contains the number of dimensions in the array. And the third byte contains the number of words in the array. The number of words is equal to the number of elements in the array times the number of words in each element. This factor is one for a single precision real array and two for a double precision real array or single precision,complex array. If the data pointer byte of the array's name control block is zero, the only copy of the array exists in the work pool, and the array is the result of the last array operation performed. The work pool can contain anywhere from zero to three arrays. A counter is kept of the number of arrays in the work pool. In addition, for each array in the work pool the index of the first word of the array, the index of the first word of the data portion of the array's name control block, and the information contained in the array's AEP AR entry is kept. When an array operation is to be performed a check is made to see if any of the arrays involved already exist in the work pool. If they do, no reference to secondary storage needs to be made to obtain the operands. A check is also made to determine if the result of the previous array operation is an operand of the current array operation. If it is not the previous result array must be stored temporarily in secondary storage. A name control block which denotes an equals variable contains the virtual page number of the first page used to store the internal text for the expression in its data pointer byte. The first word of each virtual page is used for linkage. The link contains the virtual page number of the next page used to hold the text of the expression or zero if the page is the last. When an equals variable is an operand of an arithmetic expression this internal text is evaluated to obtain a value for the equals variable. If a name control block denotes a scalar symbolic left arrow function, the data pointer contains the page number of the first virtual page used to store the internal text of the arithmetic expression for the first domain of definition. The first byte of the fourth word of the data portion contains the number of arguments of the function. The first four words of the first virtual page used to store the internal arithmetic expression text for each domain contains a set of pointers. The first word is used to link together the pages required to store the internal text for the arithmetic expression for the domain. It contains the virtual page number of the next virtual page used. A zero link denotes the last page. The next three words are subdivided into nine bytes. The first byte contains the number of words of internal text in the boolean expression for the domain. This is used when the boolean expression, is being moved prior to its evaluation. The second byte contains the reference count for the function. If the function appears in the definition of another left arrow function this is increased by one so that only one copy of this function needs to be kept. The third byte is the virtual page number of the first page used to hold the text for the boolean expression for the domain. This byte is zero if the domain has no boolean expression. The fourth byte contains the number of virtual pages that are required to hold the local name table for the domain. The local name table contains a name control block for each non-parameter variable appearing in the boolean and arithmetic expression for the domain. This is necessary so that the value of these variables can be fixed when the function is defined. Byte five is unused. Byte six contains the virtual page number of the first page used to hold the local name table for the domain. Byte seven contains the number of words of internal text in the arithmetic expression for the domain" Byte eight is unused and byte nine contains the virtual page number of the first page of internal, arithmetic expression, text for the next domain. If this byte is zero, there is not another domain defined for the function. The virtual pages used to store the text for a boolean expression or a local name table are linked together by the first word of each' page. A zero link specifies the last page. The name control block for a scalar symbolic equals function contains the same information as a scalar symbolic left arrow function. The text for the function is also stored in a similar fashion except that in the first virtual page used to store the internal text for a domain's arithmetic expression bytes two, four and six are not
7 Manipulation of Data Structures 163 used. There is no local name table required for an equals function since all non-parameter variables appearing in the function definition assume their current values when the function is evaluated. There is no reference count because if an equals function appears in the definition of a left arrow function, a copy of the equals function must be created. While the copy is being made the equals function is transformed into a left arrow function to insure that the values of all non-parameter variables are fixed. If a name control block denotes an array of symbolic functions, it contains the same information as a numeric array name control block. In addition the first byte of the fourth word of the data portion contains the number of arguments in each of the functions. The array is treated as if it is an array of real single precision numbers. Each element contains the virtual page number of the first page used to store the arithmetic expression text for the first domain of the element's definition. If an element is not defined, its value is zero. The text for the definition of each element is linked together in the same manner as a scalar symbolic function. N APSS is not designed for string processing but it does allow the user to create strings, concatenate them and assign them to variables. This is done to permit the programmer to label his output. The data pointer byte of a string valued variable's name control block contains the number of the string. The string number is the index of an entry in the string relocation vector. Each entry is subdivided into three bytes. Byte one contains the index of the start of the actual string description in the string picture table. The second byte contains the reference count for the string. The reference count designates the number of times the string variable has been concatenated to form another string, plus one. The third byte contains the index of the first word of the data portion of the name control block for the string variable. The string picture table contains a description of each string. Several entries compose the description of a string. Each entry denotes either a literal string, a reference to a previously defined string variable, or the end of a string picture. An entry in the string picture table is subdivided into three bytes. If byte one is not zero the entry describes a literal. Byte one is the number of characters in the literal, byte three is the number of the virtual page in which the literal is stored, and byte two is the displacement on that page to where the literal begins. Each word in a virtual page used to hold string literals is subdivided into three bytes. A literal is divided into segments of three characters. Each segment is stored in a byte. If a string literal will not fit in the current string page, the literal is broken. As many segments of the literal as possible are placed in the current page and the remainder are placed in a new string page. When this occurs two entries are placed in the string picture table. This avoids the problem of linking pages used to hold string literals. The maximum length of one string literal is 576 characters. If byte one of a string picture table entry is 1313, then the entry denotes the null string. It has no length and does not require any storage, so byte two and three are unused. If byte one is zero and byte three is not 501, the entry denotes a reference to a previously defined string variable. So that a new copy of the previously defined variable's string is not created, byte three contains the index of its entry in the string relocation table. When this occurs the reference count in the relocation table for the variable is increased by one. If byte one is zero and byte three is 501, the entry denotes the end of a string picture. When a name control block denotes an array of strings, it contains the same information as a numeric array. The array is treated as a single precision real array. The elements of the array contain the indices of the entries in the string relocation table for the string descriptions. If an element is undefined, its value is zero. As can be seen from the descriptions of the various data structures, the primary concerns in their design has been to facilitate their use as operands while at the sam~ time reducing the amount of physical storage required. ACKNOWLEDGMENT The work was supported in part by NSF Contract GP REFERENCES 1 G J CULLER Mathematical laboratories: A new power for the phy.'jical sciences Interactive Systems for Experimental Applied Mathematics Klerer and Reinfelds eds pp M KLERER J MAY An experiment in a user-oriented computer system Communications of the ACM Vol 7 No,1') pp M KLERER J MAY A user oriented programming language Computer Journal Vol 8 No 2 pp ;) 4 J R RICE On the construction of polyalgorithms for automatic numerical analysis Interactive Systems for Experimental Applied Mathematics Klerer and Reinfelds eds pp J R RICE A polyalgorithm for the automatic solution of non-linear
8 164 Spring Joint Computer Conference, 1970 equations Proc of ACM 24th National Conference pp ACM Publication P A RULYE J W BRACKETT R KAPLOW The status of systems for on-h"ne mathematical assistance Proceedings ACM National Meeting pp S SCHLESINGER L SASHKIN POSE-A language for. posing problems to the computer Communications of the ACM Vol 10 No R N SEITZ L H WOOD C ELY AMTRAN -A utomatic mathematical translation Interactive Systems for Experimental Applied Mathematics Klerer and Reinfelds eds pp A N STOWE R A WEISEN D B YNTEMA J W FORGIE The Lincoln reckoner: An operation-orientedon-line facility with distributed control Proceedings FJCC p L R SYMES R V ROMAN Structure of a language for a numerical analysis problem solving system Interactive Systems for Experimental Applied Mathematics Klerer and Reinfelds eds pp L R SYMES Evaluation of NAPSS expressions involving polyalgorithms, functions, recursion and untyped variables Purdue University Technical Report CDS TR L R SYMES R V ROMAN Syntatic and semantic description of the numerical analysis programming language (N APSS) Purdue University Technical Report CSD TR 11 Revised 1969
Chapter 16. Burroughs' B6500/B7500 Stack Mechanism 1. E. A. Hauck / B. A. Dent. Introduction
 Chapter 16 Burroughs' B6500/B7500 Stack Mechanism 1 E. A. Hauck / B. A. Dent Introduction Burroughs' B6500/B7500 system structure and philosophy are an extention of the concepts employed in the development
Chapter 16 Burroughs' B6500/B7500 Stack Mechanism 1 E. A. Hauck / B. A. Dent Introduction Burroughs' B6500/B7500 system structure and philosophy are an extention of the concepts employed in the development
Evaluation of NAPSS Expression Involving Polyalgorithms, Functions, Recursion, and Untyped Variables
 Purdue University Purdue e-pubs Department of Computer Science Technical Reports Department of Computer Science 1969 Evaluation of NAPSS Expression Involving Polyalgorithms, Functions, Recursion, and Untyped
Purdue University Purdue e-pubs Department of Computer Science Technical Reports Department of Computer Science 1969 Evaluation of NAPSS Expression Involving Polyalgorithms, Functions, Recursion, and Untyped
UNIT V SYSTEM SOFTWARE TOOLS
 5.1 Text editors UNIT V SYSTEM SOFTWARE TOOLS A text editor is a type of program used for editing plain text files. Text editors are often provided with operating systems or software development packages,
5.1 Text editors UNIT V SYSTEM SOFTWARE TOOLS A text editor is a type of program used for editing plain text files. Text editors are often provided with operating systems or software development packages,
UNIT-II. Part-2: CENTRAL PROCESSING UNIT
 Page1 UNIT-II Part-2: CENTRAL PROCESSING UNIT Stack Organization Instruction Formats Addressing Modes Data Transfer And Manipulation Program Control Reduced Instruction Set Computer (RISC) Introduction:
Page1 UNIT-II Part-2: CENTRAL PROCESSING UNIT Stack Organization Instruction Formats Addressing Modes Data Transfer And Manipulation Program Control Reduced Instruction Set Computer (RISC) Introduction:
indexing and subroutines; a full complement of logical, relational and control operators should be provided to enable efficient
 Chapter 9 Design of the B 5000 System^ William Lonergan /Paul King Computing systems have conventionally been designed via the "hardware" route. Subsequent to design, these systems have been handed over
Chapter 9 Design of the B 5000 System^ William Lonergan /Paul King Computing systems have conventionally been designed via the "hardware" route. Subsequent to design, these systems have been handed over
Declaring Pointers. Declaration of pointers <type> *variable <type> *variable = initial-value Examples:
 1 Programming in C Pointer Variable A variable that stores a memory address Allows C programs to simulate call-by-reference Allows a programmer to create and manipulate dynamic data structures Must be
1 Programming in C Pointer Variable A variable that stores a memory address Allows C programs to simulate call-by-reference Allows a programmer to create and manipulate dynamic data structures Must be
CSc 10200! Introduction to Computing. Lecture 1 Edgardo Molina Fall 2013 City College of New York
 CSc 10200! Introduction to Computing Lecture 1 Edgardo Molina Fall 2013 City College of New York 1 Introduction to Computing Lectures: Tuesday and Thursday s (2-2:50 pm) Location: NAC 1/202 Recitation:
CSc 10200! Introduction to Computing Lecture 1 Edgardo Molina Fall 2013 City College of New York 1 Introduction to Computing Lectures: Tuesday and Thursday s (2-2:50 pm) Location: NAC 1/202 Recitation:
General Objective:To understand the basic memory management of operating system. Specific Objectives: At the end of the unit you should be able to:
 F2007/Unit6/1 UNIT 6 OBJECTIVES General Objective:To understand the basic memory management of operating system Specific Objectives: At the end of the unit you should be able to: define the memory management
F2007/Unit6/1 UNIT 6 OBJECTIVES General Objective:To understand the basic memory management of operating system Specific Objectives: At the end of the unit you should be able to: define the memory management
MICROPROGRAMMED CONTROL
 MICROPROGRAMMED CONTROL Hardwired Control Unit: When the control signals are generated by hardware using conventional logic design techniques, the control unit is said to be hardwired. Micro programmed
MICROPROGRAMMED CONTROL Hardwired Control Unit: When the control signals are generated by hardware using conventional logic design techniques, the control unit is said to be hardwired. Micro programmed
Addresses in the source program are generally symbolic. A compiler will typically bind these symbolic addresses to re-locatable addresses.
 1 Memory Management Address Binding The normal procedures is to select one of the processes in the input queue and to load that process into memory. As the process executed, it accesses instructions and
1 Memory Management Address Binding The normal procedures is to select one of the processes in the input queue and to load that process into memory. As the process executed, it accesses instructions and
ARM ARCHITECTURE. Contents at a glance:
 UNIT-III ARM ARCHITECTURE Contents at a glance: RISC Design Philosophy ARM Design Philosophy Registers Current Program Status Register(CPSR) Instruction Pipeline Interrupts and Vector Table Architecture
UNIT-III ARM ARCHITECTURE Contents at a glance: RISC Design Philosophy ARM Design Philosophy Registers Current Program Status Register(CPSR) Instruction Pipeline Interrupts and Vector Table Architecture
Operating system Dr. Shroouq J.
 2.2.2 DMA Structure In a simple terminal-input driver, when a line is to be read from the terminal, the first character typed is sent to the computer. When that character is received, the asynchronous-communication
2.2.2 DMA Structure In a simple terminal-input driver, when a line is to be read from the terminal, the first character typed is sent to the computer. When that character is received, the asynchronous-communication
AS-2883 B.Sc.(Hon s)(fifth Semester) Examination,2013 Computer Science (PCSC-503) (System Software) [Time Allowed: Three Hours] [Maximum Marks : 30]
![AS-2883 B.Sc.(Hon s)(fifth Semester) Examination,2013 Computer Science (PCSC-503) (System Software) [Time Allowed: Three Hours] [Maximum Marks : 30] AS-2883 B.Sc.(Hon s)(fifth Semester) Examination,2013 Computer Science (PCSC-503) (System Software) [Time Allowed: Three Hours] [Maximum Marks : 30]](/thumbs/80/81792243.jpg) AS-2883 B.Sc.(Hon s)(fifth Semester) Examination,2013 Computer Science (PCSC-503) (System Software) [Time Allowed: Three Hours] [Maximum Marks : 30] Note: Question Number 1 is compulsory. Marks : 10X1
AS-2883 B.Sc.(Hon s)(fifth Semester) Examination,2013 Computer Science (PCSC-503) (System Software) [Time Allowed: Three Hours] [Maximum Marks : 30] Note: Question Number 1 is compulsory. Marks : 10X1
THE CONSTRUCTION OF AN ALGOL TRANSLATOR FOR A SMALL COMPUTER
 i.i THE CONSTRUCTION OF AN ALGOL TRANSLATOR FOR A SMALL COMPUTER w. L. van der Poet Dr. Neher Laboratory PTT, Leidschendam, Netherlands For the computer Zebra we have undertaken a project of constructing
i.i THE CONSTRUCTION OF AN ALGOL TRANSLATOR FOR A SMALL COMPUTER w. L. van der Poet Dr. Neher Laboratory PTT, Leidschendam, Netherlands For the computer Zebra we have undertaken a project of constructing
6.001 Notes: Section 6.1
 6.001 Notes: Section 6.1 Slide 6.1.1 When we first starting talking about Scheme expressions, you may recall we said that (almost) every Scheme expression had three components, a syntax (legal ways of
6.001 Notes: Section 6.1 Slide 6.1.1 When we first starting talking about Scheme expressions, you may recall we said that (almost) every Scheme expression had three components, a syntax (legal ways of
Chapter 6: Deferred Report Writer
 Chapter 6: Deferred Report Writer CHAPTER 6: DEFERRED REPORT WRITER... 1 DEFERRED REPORT WRITER OVERVIEW... 2 REPORT TITLE (TYPE 01 PARAMETER)... 3 Type 01 Parameter Fields... 3 EXPANDER OPTION (TYPE 02
Chapter 6: Deferred Report Writer CHAPTER 6: DEFERRED REPORT WRITER... 1 DEFERRED REPORT WRITER OVERVIEW... 2 REPORT TITLE (TYPE 01 PARAMETER)... 3 Type 01 Parameter Fields... 3 EXPANDER OPTION (TYPE 02
Hardware-Supported Pointer Detection for common Garbage Collections
 2013 First International Symposium on Computing and Networking Hardware-Supported Pointer Detection for common Garbage Collections Kei IDEUE, Yuki SATOMI, Tomoaki TSUMURA and Hiroshi MATSUO Nagoya Institute
2013 First International Symposium on Computing and Networking Hardware-Supported Pointer Detection for common Garbage Collections Kei IDEUE, Yuki SATOMI, Tomoaki TSUMURA and Hiroshi MATSUO Nagoya Institute
UNIT - 5 EDITORS AND DEBUGGING SYSTEMS
 UNIT - 5 EDITORS AND DEBUGGING SYSTEMS 5.1 Introduction An Interactive text editor has become an important part of almost any computing environment. Text editor acts as a primary interface to the computer
UNIT - 5 EDITORS AND DEBUGGING SYSTEMS 5.1 Introduction An Interactive text editor has become an important part of almost any computing environment. Text editor acts as a primary interface to the computer
Memory Addressing, Binary, and Hexadecimal Review
 C++ By A EXAMPLE Memory Addressing, Binary, and Hexadecimal Review You do not have to understand the concepts in this appendix to become well-versed in C++. You can master C++, however, only if you spend
C++ By A EXAMPLE Memory Addressing, Binary, and Hexadecimal Review You do not have to understand the concepts in this appendix to become well-versed in C++. You can master C++, however, only if you spend
Model answer of AS-4159 Operating System B.tech fifth Semester Information technology
 Q.no I Ii Iii Iv V Vi Vii viii ix x Model answer of AS-4159 Operating System B.tech fifth Semester Information technology Q.1 Objective type Answer d(321) C(Execute more jobs in the same time) Three/three
Q.no I Ii Iii Iv V Vi Vii viii ix x Model answer of AS-4159 Operating System B.tech fifth Semester Information technology Q.1 Objective type Answer d(321) C(Execute more jobs in the same time) Three/three
CS201 - Introduction to Programming Glossary By
 CS201 - Introduction to Programming Glossary By #include : The #include directive instructs the preprocessor to read and include a file into a source code file. The file name is typically enclosed with
CS201 - Introduction to Programming Glossary By #include : The #include directive instructs the preprocessor to read and include a file into a source code file. The file name is typically enclosed with
Module 5 - CPU Design
 Module 5 - CPU Design Lecture 1 - Introduction to CPU The operation or task that must perform by CPU is: Fetch Instruction: The CPU reads an instruction from memory. Interpret Instruction: The instruction
Module 5 - CPU Design Lecture 1 - Introduction to CPU The operation or task that must perform by CPU is: Fetch Instruction: The CPU reads an instruction from memory. Interpret Instruction: The instruction
Chapter 9 Memory Management Main Memory Operating system concepts. Sixth Edition. Silberschatz, Galvin, and Gagne 8.1
 Chapter 9 Memory Management Main Memory Operating system concepts. Sixth Edition. Silberschatz, Galvin, and Gagne 8.1 Chapter 9: Memory Management Background Swapping Contiguous Memory Allocation Segmentation
Chapter 9 Memory Management Main Memory Operating system concepts. Sixth Edition. Silberschatz, Galvin, and Gagne 8.1 Chapter 9: Memory Management Background Swapping Contiguous Memory Allocation Segmentation
ASSIST Assembler Replacement User s Guide
 ASSIST Assembler Replacement User s Guide Program&Documentation: John R. Mashey Pro ject Supervision : Graham Campbell PSU Computer Science Department Preface This manual is the key reference source for
ASSIST Assembler Replacement User s Guide Program&Documentation: John R. Mashey Pro ject Supervision : Graham Campbell PSU Computer Science Department Preface This manual is the key reference source for
Chapter 8 & Chapter 9 Main Memory & Virtual Memory
 Chapter 8 & Chapter 9 Main Memory & Virtual Memory 1. Various ways of organizing memory hardware. 2. Memory-management techniques: 1. Paging 2. Segmentation. Introduction Memory consists of a large array
Chapter 8 & Chapter 9 Main Memory & Virtual Memory 1. Various ways of organizing memory hardware. 2. Memory-management techniques: 1. Paging 2. Segmentation. Introduction Memory consists of a large array
AVL 4 4 PDV DECLARE 7 _NEW_
 Glossary Program Control... 2 SAS Variable... 2 Program Data Vector (PDV)... 2 SAS Expression... 2 Data Type... 3 Scalar... 3 Non-Scalar... 3 Big O Notation... 3 Hash Table... 3 Hash Algorithm... 4 Hash
Glossary Program Control... 2 SAS Variable... 2 Program Data Vector (PDV)... 2 SAS Expression... 2 Data Type... 3 Scalar... 3 Non-Scalar... 3 Big O Notation... 3 Hash Table... 3 Hash Algorithm... 4 Hash
MACHINE INDEPENDENCE IN COMPILING*
 MACHINE INDEPENDENCE IN COMPILING* Harry D. Huskey University of California Berkeley, California, USA Since 1958, there has been a substantial interest in the development of problem-oriented languages
MACHINE INDEPENDENCE IN COMPILING* Harry D. Huskey University of California Berkeley, California, USA Since 1958, there has been a substantial interest in the development of problem-oriented languages
Principle of Complier Design Prof. Y. N. Srikant Department of Computer Science and Automation Indian Institute of Science, Bangalore
 Principle of Complier Design Prof. Y. N. Srikant Department of Computer Science and Automation Indian Institute of Science, Bangalore Lecture - 20 Intermediate code generation Part-4 Run-time environments
Principle of Complier Design Prof. Y. N. Srikant Department of Computer Science and Automation Indian Institute of Science, Bangalore Lecture - 20 Intermediate code generation Part-4 Run-time environments
Short Notes of CS201
 #includes: Short Notes of CS201 The #include directive instructs the preprocessor to read and include a file into a source code file. The file name is typically enclosed with < and > if the file is a system
#includes: Short Notes of CS201 The #include directive instructs the preprocessor to read and include a file into a source code file. The file name is typically enclosed with < and > if the file is a system
Operating Systems 2230
 Operating Systems 2230 Computer Science & Software Engineering Lecture 6: Memory Management Allocating Primary Memory to Processes The important task of allocating memory to processes, and efficiently
Operating Systems 2230 Computer Science & Software Engineering Lecture 6: Memory Management Allocating Primary Memory to Processes The important task of allocating memory to processes, and efficiently
Unit 9 : Fundamentals of Parallel Processing
 Unit 9 : Fundamentals of Parallel Processing Lesson 1 : Types of Parallel Processing 1.1. Learning Objectives On completion of this lesson you will be able to : classify different types of parallel processing
Unit 9 : Fundamentals of Parallel Processing Lesson 1 : Types of Parallel Processing 1.1. Learning Objectives On completion of this lesson you will be able to : classify different types of parallel processing
COMPILER DESIGN LECTURE NOTES
 COMPILER DESIGN LECTURE NOTES UNIT -1 1.1 OVERVIEW OF LANGUAGE PROCESSING SYSTEM 1.2 Preprocessor A preprocessor produce input to compilers. They may perform the following functions. 1. Macro processing:
COMPILER DESIGN LECTURE NOTES UNIT -1 1.1 OVERVIEW OF LANGUAGE PROCESSING SYSTEM 1.2 Preprocessor A preprocessor produce input to compilers. They may perform the following functions. 1. Macro processing:
Request for Comments: 851 Obsoletes RFC: 802. The ARPANET 1822L Host Access Protocol RFC 851. Andrew G. Malis ARPANET Mail:
 Request for Comments: 851 Obsoletes RFC: 802 The ARPANET 1822L Host Access Protocol Andrew G. Malis ARPANET Mail: malis@bbn-unix Bolt Beranek and Newman Inc. 50 Moulton St. Cambridge, MA 02238 April 1983
Request for Comments: 851 Obsoletes RFC: 802 The ARPANET 1822L Host Access Protocol Andrew G. Malis ARPANET Mail: malis@bbn-unix Bolt Beranek and Newman Inc. 50 Moulton St. Cambridge, MA 02238 April 1983
CHAPTER SEVEN PROGRAMMING THE BASIC COMPUTER
 CHAPTER SEVEN 71 Introduction PROGRAMMING THE BASIC COMPUTER A computer system as it was mentioned before in chapter 1, it is subdivided into two functional parts: 1 Hardware, which consists of all physical
CHAPTER SEVEN 71 Introduction PROGRAMMING THE BASIC COMPUTER A computer system as it was mentioned before in chapter 1, it is subdivided into two functional parts: 1 Hardware, which consists of all physical
A First Book of ANSI C
 A First Book of ANSI C Fourth Edition Chapter 13 Dynamic Data Structures Objectives Introduction to Linked Lists Dynamic Memory Allocation Dynamically Linked Lists Common Programming and Compiler Errors
A First Book of ANSI C Fourth Edition Chapter 13 Dynamic Data Structures Objectives Introduction to Linked Lists Dynamic Memory Allocation Dynamically Linked Lists Common Programming and Compiler Errors
Machine Language Instructions Introduction. Instructions Words of a language understood by machine. Instruction set Vocabulary of the machine
 Machine Language Instructions Introduction Instructions Words of a language understood by machine Instruction set Vocabulary of the machine Current goal: to relate a high level language to instruction
Machine Language Instructions Introduction Instructions Words of a language understood by machine Instruction set Vocabulary of the machine Current goal: to relate a high level language to instruction
Memory Management. 3. What two registers can be used to provide a simple form of memory protection? Base register Limit Register
 Memory Management 1. Describe the sequence of instruction-execution life cycle? A typical instruction-execution life cycle: Fetches (load) an instruction from specific memory address. Decode the instruction
Memory Management 1. Describe the sequence of instruction-execution life cycle? A typical instruction-execution life cycle: Fetches (load) an instruction from specific memory address. Decode the instruction
icroprocessor istory of Microprocessor ntel 8086:
 Microprocessor A microprocessor is an electronic device which computes on the given input similar to CPU of a computer. It is made by fabricating millions (or billions) of transistors on a single chip.
Microprocessor A microprocessor is an electronic device which computes on the given input similar to CPU of a computer. It is made by fabricating millions (or billions) of transistors on a single chip.
STRUCTURE OF DESKTOP COMPUTERS
 Page no: 1 UNIT 1 STRUCTURE OF DESKTOP COMPUTERS The desktop computers are the computers which are usually found on a home or office desk. They consist of processing unit, storage unit, visual display
Page no: 1 UNIT 1 STRUCTURE OF DESKTOP COMPUTERS The desktop computers are the computers which are usually found on a home or office desk. They consist of processing unit, storage unit, visual display
Operating Systems. Designed and Presented by Dr. Ayman Elshenawy Elsefy
 Operating Systems Designed and Presented by Dr. Ayman Elshenawy Elsefy Dept. of Systems & Computer Eng.. AL-AZHAR University Website : eaymanelshenawy.wordpress.com Email : eaymanelshenawy@yahoo.com Reference
Operating Systems Designed and Presented by Dr. Ayman Elshenawy Elsefy Dept. of Systems & Computer Eng.. AL-AZHAR University Website : eaymanelshenawy.wordpress.com Email : eaymanelshenawy@yahoo.com Reference
Module 27 Switch-case statements and Run-time storage management
 Module 27 Switch-case statements and Run-time storage management In this module we will discuss the pending constructs in generating three-address code namely switch-case statements. We will also discuss
Module 27 Switch-case statements and Run-time storage management In this module we will discuss the pending constructs in generating three-address code namely switch-case statements. We will also discuss
MEMORY MANAGEMENT/1 CS 409, FALL 2013
 MEMORY MANAGEMENT Requirements: Relocation (to different memory areas) Protection (run time, usually implemented together with relocation) Sharing (and also protection) Logical organization Physical organization
MEMORY MANAGEMENT Requirements: Relocation (to different memory areas) Protection (run time, usually implemented together with relocation) Sharing (and also protection) Logical organization Physical organization
Programming Languages Third Edition. Chapter 9 Control I Expressions and Statements
 Programming Languages Third Edition Chapter 9 Control I Expressions and Statements Objectives Understand expressions Understand conditional statements and guards Understand loops and variation on WHILE
Programming Languages Third Edition Chapter 9 Control I Expressions and Statements Objectives Understand expressions Understand conditional statements and guards Understand loops and variation on WHILE
A Feasibility Study for Methods of Effective Memoization Optimization
 A Feasibility Study for Methods of Effective Memoization Optimization Daniel Mock October 2018 Abstract Traditionally, memoization is a compiler optimization that is applied to regions of code with few
A Feasibility Study for Methods of Effective Memoization Optimization Daniel Mock October 2018 Abstract Traditionally, memoization is a compiler optimization that is applied to regions of code with few
RI AND RF CRITERIA AND FORMATS
 RI-42 RI AND RF CRITERIA AND FORMATS PURPOSE This procedure establishes design criteria and standard formats for detailed procedures and records required for effective operations, communications and management
RI-42 RI AND RF CRITERIA AND FORMATS PURPOSE This procedure establishes design criteria and standard formats for detailed procedures and records required for effective operations, communications and management
Digital System Design Using Verilog. - Processing Unit Design
 Digital System Design Using Verilog - Processing Unit Design 1.1 CPU BASICS A typical CPU has three major components: (1) Register set, (2) Arithmetic logic unit (ALU), and (3) Control unit (CU) The register
Digital System Design Using Verilog - Processing Unit Design 1.1 CPU BASICS A typical CPU has three major components: (1) Register set, (2) Arithmetic logic unit (ALU), and (3) Control unit (CU) The register
INTRODUCTION. José Luis Calva 1. José Luis Calva Martínez
 USING DATA SETS José Luis Calva Martínez Email: jose.luis.calva@rav.com.mx rav.jlcm@prodigy.net.mx INTRODUCTION In working with the z/os operating system, you must understand data sets, the files that
USING DATA SETS José Luis Calva Martínez Email: jose.luis.calva@rav.com.mx rav.jlcm@prodigy.net.mx INTRODUCTION In working with the z/os operating system, you must understand data sets, the files that
Theory of 3-4 Heap. Examining Committee Prof. Tadao Takaoka Supervisor
 Theory of 3-4 Heap A thesis submitted in partial fulfilment of the requirements for the Degree of Master of Science in the University of Canterbury by Tobias Bethlehem Examining Committee Prof. Tadao Takaoka
Theory of 3-4 Heap A thesis submitted in partial fulfilment of the requirements for the Degree of Master of Science in the University of Canterbury by Tobias Bethlehem Examining Committee Prof. Tadao Takaoka
The PCAT Programming Language Reference Manual
 The PCAT Programming Language Reference Manual Andrew Tolmach and Jingke Li Dept. of Computer Science Portland State University September 27, 1995 (revised October 15, 2002) 1 Introduction The PCAT language
The PCAT Programming Language Reference Manual Andrew Tolmach and Jingke Li Dept. of Computer Science Portland State University September 27, 1995 (revised October 15, 2002) 1 Introduction The PCAT language
Computer Programming C++ (wg) CCOs
 Computer Programming C++ (wg) CCOs I. The student will analyze the different systems, and languages of the computer. (SM 1.4, 3.1, 3.4, 3.6) II. The student will write, compile, link and run a simple C++
Computer Programming C++ (wg) CCOs I. The student will analyze the different systems, and languages of the computer. (SM 1.4, 3.1, 3.4, 3.6) II. The student will write, compile, link and run a simple C++
Chapter 2 Using Data. Instructor s Manual Table of Contents. At a Glance. Overview. Objectives. Teaching Tips. Quick Quizzes. Class Discussion Topics
 Java Programming, Sixth Edition 2-1 Chapter 2 Using Data At a Glance Instructor s Manual Table of Contents Overview Objectives Teaching Tips Quick Quizzes Class Discussion Topics Additional Projects Additional
Java Programming, Sixth Edition 2-1 Chapter 2 Using Data At a Glance Instructor s Manual Table of Contents Overview Objectives Teaching Tips Quick Quizzes Class Discussion Topics Additional Projects Additional
Q.1 Explain Computer s Basic Elements
 Q.1 Explain Computer s Basic Elements Ans. At a top level, a computer consists of processor, memory, and I/O components, with one or more modules of each type. These components are interconnected in some
Q.1 Explain Computer s Basic Elements Ans. At a top level, a computer consists of processor, memory, and I/O components, with one or more modules of each type. These components are interconnected in some
Computer Architecture Prof. Mainak Chaudhuri Department of Computer Science & Engineering Indian Institute of Technology, Kanpur
 Computer Architecture Prof. Mainak Chaudhuri Department of Computer Science & Engineering Indian Institute of Technology, Kanpur Lecture - 7 Case study with MIPS-I So, we were discussing (Refer Time: 00:20),
Computer Architecture Prof. Mainak Chaudhuri Department of Computer Science & Engineering Indian Institute of Technology, Kanpur Lecture - 7 Case study with MIPS-I So, we were discussing (Refer Time: 00:20),
Programming Languages Third Edition
 Programming Languages Third Edition Chapter 12 Formal Semantics Objectives Become familiar with a sample small language for the purpose of semantic specification Understand operational semantics Understand
Programming Languages Third Edition Chapter 12 Formal Semantics Objectives Become familiar with a sample small language for the purpose of semantic specification Understand operational semantics Understand
MODULE 5 LINKERS AND LOADERS
 MODULE 5 LINKERS AND LOADERS Execution phases The execution of a program involves 4 steps:- 1) Translation Converting source program to object modules. The assemblers and compilers fall under the category
MODULE 5 LINKERS AND LOADERS Execution phases The execution of a program involves 4 steps:- 1) Translation Converting source program to object modules. The assemblers and compilers fall under the category
ITERATIVE MULTI-LEVEL MODELLING - A METHODOLOGY FOR COMPUTER SYSTEM DESIGN. F. W. Zurcher B. Randell
 ITERATIVE MULTI-LEVEL MODELLING - A METHODOLOGY FOR COMPUTER SYSTEM DESIGN F. W. Zurcher B. Randell Thomas J. Watson Research Center Yorktown Heights, New York Abstract: The paper presents a method of
ITERATIVE MULTI-LEVEL MODELLING - A METHODOLOGY FOR COMPUTER SYSTEM DESIGN F. W. Zurcher B. Randell Thomas J. Watson Research Center Yorktown Heights, New York Abstract: The paper presents a method of
1. NUMBER SYSTEMS USED IN COMPUTING: THE BINARY NUMBER SYSTEM
 1. NUMBER SYSTEMS USED IN COMPUTING: THE BINARY NUMBER SYSTEM 1.1 Introduction Given that digital logic and memory devices are based on two electrical states (on and off), it is natural to use a number
1. NUMBER SYSTEMS USED IN COMPUTING: THE BINARY NUMBER SYSTEM 1.1 Introduction Given that digital logic and memory devices are based on two electrical states (on and off), it is natural to use a number
IBM. Enterprise Systems Architecture/ Extended Configuration Principles of Operation. z/vm. Version 6 Release 4 SC
 z/vm IBM Enterprise Systems Architecture/ Extended Configuration Principles of Operation Version 6 Release 4 SC24-6192-01 Note: Before you use this information and the product it supports, read the information
z/vm IBM Enterprise Systems Architecture/ Extended Configuration Principles of Operation Version 6 Release 4 SC24-6192-01 Note: Before you use this information and the product it supports, read the information
Chapter 12. File Management
 Operating System Chapter 12. File Management Lynn Choi School of Electrical Engineering Files In most applications, files are key elements For most systems except some real-time systems, files are used
Operating System Chapter 12. File Management Lynn Choi School of Electrical Engineering Files In most applications, files are key elements For most systems except some real-time systems, files are used
ASSEMBLY LANGUAGE MACHINE ORGANIZATION
 ASSEMBLY LANGUAGE MACHINE ORGANIZATION CHAPTER 3 1 Sub-topics The topic will cover: Microprocessor architecture CPU processing methods Pipelining Superscalar RISC Multiprocessing Instruction Cycle Instruction
ASSEMBLY LANGUAGE MACHINE ORGANIZATION CHAPTER 3 1 Sub-topics The topic will cover: Microprocessor architecture CPU processing methods Pipelining Superscalar RISC Multiprocessing Instruction Cycle Instruction
INTERNATIONAL TELECOMMUNICATION UNION
 INTERNATIONAL TELECOMMUNICATION UNION CCITT G.709 THE INTERNATIONAL TELEGRAPH AND TELEPHONE CONSULTATIVE COMMITTEE (11/1988) SERIES G: TRANSMISSION SYSTEMS AND MEDIA, DIGITAL SYSTEMS AND NETWORKS General
INTERNATIONAL TELECOMMUNICATION UNION CCITT G.709 THE INTERNATIONAL TELEGRAPH AND TELEPHONE CONSULTATIVE COMMITTEE (11/1988) SERIES G: TRANSMISSION SYSTEMS AND MEDIA, DIGITAL SYSTEMS AND NETWORKS General
Multi-version Data recovery for Cluster Identifier Forensics Filesystem with Identifier Integrity
 Multi-version Data recovery for Cluster Identifier Forensics Filesystem with Identifier Integrity Mohammed Alhussein, Duminda Wijesekera Department of Computer Science George Mason University Fairfax,
Multi-version Data recovery for Cluster Identifier Forensics Filesystem with Identifier Integrity Mohammed Alhussein, Duminda Wijesekera Department of Computer Science George Mason University Fairfax,
A First Book of ANSI C Fourth Edition. Chapter 8 Arrays
 A First Book of ANSI C Fourth Edition Chapter 8 Arrays One-Dimensional Arrays Array Initialization Objectives Arrays as Function Arguments Case Study: Computing Averages and Standard Deviations Two-Dimensional
A First Book of ANSI C Fourth Edition Chapter 8 Arrays One-Dimensional Arrays Array Initialization Objectives Arrays as Function Arguments Case Study: Computing Averages and Standard Deviations Two-Dimensional
A DESIGN FOR A MULTIPLE USER MULTIPROCESSING SYSTEM
 A DESIGN FOR A MULTIPLE USER MULTIPROCESSING SYSTEM James D. McCullough Kermith H. Speierman and Frank W. Zurcher Burroughs Corporation Paoli, Pennsylvania INTRODUCTION The B8500 system is designed to
A DESIGN FOR A MULTIPLE USER MULTIPROCESSING SYSTEM James D. McCullough Kermith H. Speierman and Frank W. Zurcher Burroughs Corporation Paoli, Pennsylvania INTRODUCTION The B8500 system is designed to
Full file at
 Java Programming, Fifth Edition 2-1 Chapter 2 Using Data within a Program At a Glance Instructor s Manual Table of Contents Overview Objectives Teaching Tips Quick Quizzes Class Discussion Topics Additional
Java Programming, Fifth Edition 2-1 Chapter 2 Using Data within a Program At a Glance Instructor s Manual Table of Contents Overview Objectives Teaching Tips Quick Quizzes Class Discussion Topics Additional
Chapter 11: Implementing File-Systems
 Chapter 11: Implementing File-Systems Chapter 11 File-System Implementation 11.1 File-System Structure 11.2 File-System Implementation 11.3 Directory Implementation 11.4 Allocation Methods 11.5 Free-Space
Chapter 11: Implementing File-Systems Chapter 11 File-System Implementation 11.1 File-System Structure 11.2 File-System Implementation 11.3 Directory Implementation 11.4 Allocation Methods 11.5 Free-Space
Chapter 9: Virtual Memory
 Chapter 9: Virtual Memory Chapter 9: Virtual Memory 9.1 Background 9.2 Demand Paging 9.3 Copy-on-Write 9.4 Page Replacement 9.5 Allocation of Frames 9.6 Thrashing 9.7 Memory-Mapped Files 9.8 Allocating
Chapter 9: Virtual Memory Chapter 9: Virtual Memory 9.1 Background 9.2 Demand Paging 9.3 Copy-on-Write 9.4 Page Replacement 9.5 Allocation of Frames 9.6 Thrashing 9.7 Memory-Mapped Files 9.8 Allocating
Top-Level View of Computer Organization
 Top-Level View of Computer Organization Bởi: Hoang Lan Nguyen Computer Component Contemporary computer designs are based on concepts developed by John von Neumann at the Institute for Advanced Studies
Top-Level View of Computer Organization Bởi: Hoang Lan Nguyen Computer Component Contemporary computer designs are based on concepts developed by John von Neumann at the Institute for Advanced Studies
Interprocess Communication By: Kaushik Vaghani
 Interprocess Communication By: Kaushik Vaghani Background Race Condition: A situation where several processes access and manipulate the same data concurrently and the outcome of execution depends on the
Interprocess Communication By: Kaushik Vaghani Background Race Condition: A situation where several processes access and manipulate the same data concurrently and the outcome of execution depends on the
File System Interface and Implementation
 Unit 8 Structure 8.1 Introduction Objectives 8.2 Concept of a File Attributes of a File Operations on Files Types of Files Structure of File 8.3 File Access Methods Sequential Access Direct Access Indexed
Unit 8 Structure 8.1 Introduction Objectives 8.2 Concept of a File Attributes of a File Operations on Files Types of Files Structure of File 8.3 File Access Methods Sequential Access Direct Access Indexed
MIB BROADCAST STREAM SPECIFICATION
 MIB BROADCAST STREAM SPECIFICATION November 5, 2002, Version 1.0 This document contains a specification for the MIB broadcast stream. It will be specified in a language independent manner. It is intended
MIB BROADCAST STREAM SPECIFICATION November 5, 2002, Version 1.0 This document contains a specification for the MIB broadcast stream. It will be specified in a language independent manner. It is intended
A macro- generator for ALGOL
 A macro- generator for ALGOL byh.leroy Compagnie Bull-General Electric Paris, France INTRODUCfION The concept of macro-facility is ambiguous, when applied to higher level languages. For some authorsl,2,
A macro- generator for ALGOL byh.leroy Compagnie Bull-General Electric Paris, France INTRODUCfION The concept of macro-facility is ambiguous, when applied to higher level languages. For some authorsl,2,
1 Lexical Considerations
 Massachusetts Institute of Technology Department of Electrical Engineering and Computer Science 6.035, Spring 2013 Handout Decaf Language Thursday, Feb 7 The project for the course is to write a compiler
Massachusetts Institute of Technology Department of Electrical Engineering and Computer Science 6.035, Spring 2013 Handout Decaf Language Thursday, Feb 7 The project for the course is to write a compiler
CIS 1.5 Course Objectives. a. Understand the concept of a program (i.e., a computer following a series of instructions)
 By the end of this course, students should CIS 1.5 Course Objectives a. Understand the concept of a program (i.e., a computer following a series of instructions) b. Understand the concept of a variable
By the end of this course, students should CIS 1.5 Course Objectives a. Understand the concept of a program (i.e., a computer following a series of instructions) b. Understand the concept of a variable
PROCESS STATES AND TRANSITIONS:
 The kernel contains a process table with an entry that describes the state of every active process in the system. The u area contains additional information that controls the operation of a process. The
The kernel contains a process table with an entry that describes the state of every active process in the system. The u area contains additional information that controls the operation of a process. The
Basic Processing Unit: Some Fundamental Concepts, Execution of a. Complete Instruction, Multiple Bus Organization, Hard-wired Control,
 UNIT - 7 Basic Processing Unit: Some Fundamental Concepts, Execution of a Complete Instruction, Multiple Bus Organization, Hard-wired Control, Microprogrammed Control Page 178 UNIT - 7 BASIC PROCESSING
UNIT - 7 Basic Processing Unit: Some Fundamental Concepts, Execution of a Complete Instruction, Multiple Bus Organization, Hard-wired Control, Microprogrammed Control Page 178 UNIT - 7 BASIC PROCESSING
Computer Architecture
 Computer Architecture Lecture 1: Digital logic circuits The digital computer is a digital system that performs various computational tasks. Digital computers use the binary number system, which has two
Computer Architecture Lecture 1: Digital logic circuits The digital computer is a digital system that performs various computational tasks. Digital computers use the binary number system, which has two
The SPL Programming Language Reference Manual
 The SPL Programming Language Reference Manual Leonidas Fegaras University of Texas at Arlington Arlington, TX 76019 fegaras@cse.uta.edu February 27, 2018 1 Introduction The SPL language is a Small Programming
The SPL Programming Language Reference Manual Leonidas Fegaras University of Texas at Arlington Arlington, TX 76019 fegaras@cse.uta.edu February 27, 2018 1 Introduction The SPL language is a Small Programming
Run-time Environments
 Run-time Environments Status We have so far covered the front-end phases Lexical analysis Parsing Semantic analysis Next come the back-end phases Code generation Optimization Register allocation Instruction
Run-time Environments Status We have so far covered the front-end phases Lexical analysis Parsing Semantic analysis Next come the back-end phases Code generation Optimization Register allocation Instruction
File Management By : Kaushik Vaghani
 File Management By : Kaushik Vaghani File Concept Access Methods File Types File Operations Directory Structure File-System Structure File Management Directory Implementation (Linear List, Hash Table)
File Management By : Kaushik Vaghani File Concept Access Methods File Types File Operations Directory Structure File-System Structure File Management Directory Implementation (Linear List, Hash Table)
Bits, Words, and Integers
 Computer Science 52 Bits, Words, and Integers Spring Semester, 2017 In this document, we look at how bits are organized into meaningful data. In particular, we will see the details of how integers are
Computer Science 52 Bits, Words, and Integers Spring Semester, 2017 In this document, we look at how bits are organized into meaningful data. In particular, we will see the details of how integers are
Run-time Environments
 Run-time Environments Status We have so far covered the front-end phases Lexical analysis Parsing Semantic analysis Next come the back-end phases Code generation Optimization Register allocation Instruction
Run-time Environments Status We have so far covered the front-end phases Lexical analysis Parsing Semantic analysis Next come the back-end phases Code generation Optimization Register allocation Instruction
Programming Level A.R. Hurson Department of Computer Science Missouri University of Science & Technology Rolla, Missouri
 Programming Level A.R. Hurson Department of Computer Science Missouri University of Science & Technology Rolla, Missouri 65409 hurson@mst.edu A.R. Hurson 1 Programming Level Computer: A computer with a
Programming Level A.R. Hurson Department of Computer Science Missouri University of Science & Technology Rolla, Missouri 65409 hurson@mst.edu A.R. Hurson 1 Programming Level Computer: A computer with a
Have examined process Creating program Have developed program Written in C Source code
 Preprocessing, Compiling, Assembling, and Linking Introduction In this lesson will examine Architecture of C program Introduce C preprocessor and preprocessor directives How to use preprocessor s directives
Preprocessing, Compiling, Assembling, and Linking Introduction In this lesson will examine Architecture of C program Introduce C preprocessor and preprocessor directives How to use preprocessor s directives
Indexing and Hashing
 C H A P T E R 1 Indexing and Hashing This chapter covers indexing techniques ranging from the most basic one to highly specialized ones. Due to the extensive use of indices in database systems, this chapter
C H A P T E R 1 Indexing and Hashing This chapter covers indexing techniques ranging from the most basic one to highly specialized ones. Due to the extensive use of indices in database systems, this chapter
Qualifying Exam in Programming Languages and Compilers
 Qualifying Exam in Programming Languages and Compilers University of Wisconsin Fall 1991 Instructions This exam contains nine questions, divided into two parts. All students taking the exam should answer
Qualifying Exam in Programming Languages and Compilers University of Wisconsin Fall 1991 Instructions This exam contains nine questions, divided into two parts. All students taking the exam should answer
Directory Structure and File Allocation Methods
 ISSN:0975-9646 Mandeep Kaur et al, / (IJCSIT) International Journal of Computer Science and Information Technologies, Vol. 7 (2), 2016, 577-582 Directory Structure and ile Allocation Methods Mandeep Kaur,
ISSN:0975-9646 Mandeep Kaur et al, / (IJCSIT) International Journal of Computer Science and Information Technologies, Vol. 7 (2), 2016, 577-582 Directory Structure and ile Allocation Methods Mandeep Kaur,
Chapter 7 Memory Management
 Operating Systems: Internals and Design Principles Chapter 7 Memory Management Ninth Edition William Stallings Frame Page Segment A fixed-length block of main memory. A fixed-length block of data that
Operating Systems: Internals and Design Principles Chapter 7 Memory Management Ninth Edition William Stallings Frame Page Segment A fixed-length block of main memory. A fixed-length block of data that
Computer support for an experimental PICTUREPHONE /computer system at Bell Telephone Laboratories, Incorporated
 Computer support for an experimental PICTUREPHONE /computer system at Bell Telephone Laboratories, Incorporated by ERNESTO J. RODRIGUEZ Bell Telephone Laboratories, Incorporated Holmdel, New Jersey INTRODUCTION
Computer support for an experimental PICTUREPHONE /computer system at Bell Telephone Laboratories, Incorporated by ERNESTO J. RODRIGUEZ Bell Telephone Laboratories, Incorporated Holmdel, New Jersey INTRODUCTION
RPR CRITERIA AND FORMATS
 RPR CRITERIA AND FORMATS PURPOSE This procedure establishes design criteria and standard formats for detailed procedures and records required for effective operations, communications and management of
RPR CRITERIA AND FORMATS PURPOSE This procedure establishes design criteria and standard formats for detailed procedures and records required for effective operations, communications and management of
Chapter 7: Statement Generator
 Chapter 7: Statement Generator CHAPTER 7: STATEMENT GENERATOR... 1 STATEMENT GENERATOR OVERVIEW... 1 PARAMETER FORMATS... 2 CONTROL (TYPE 3 PARAMETER)... 2 Type 3 Parameter Fields... 2 ADDITIONAL GROUPS
Chapter 7: Statement Generator CHAPTER 7: STATEMENT GENERATOR... 1 STATEMENT GENERATOR OVERVIEW... 1 PARAMETER FORMATS... 2 CONTROL (TYPE 3 PARAMETER)... 2 Type 3 Parameter Fields... 2 ADDITIONAL GROUPS
Lexical Considerations
 Massachusetts Institute of Technology Department of Electrical Engineering and Computer Science 6.035, Spring 2010 Handout Decaf Language Tuesday, Feb 2 The project for the course is to write a compiler
Massachusetts Institute of Technology Department of Electrical Engineering and Computer Science 6.035, Spring 2010 Handout Decaf Language Tuesday, Feb 2 The project for the course is to write a compiler
Problem Solving and 'C' Programming
 Problem Solving and 'C' Programming Targeted at: Entry Level Trainees Session 15: Files and Preprocessor Directives/Pointers 2007, Cognizant Technology Solutions. All Rights Reserved. The information contained
Problem Solving and 'C' Programming Targeted at: Entry Level Trainees Session 15: Files and Preprocessor Directives/Pointers 2007, Cognizant Technology Solutions. All Rights Reserved. The information contained
Basic Memory Management
 Basic Memory Management CS 256/456 Dept. of Computer Science, University of Rochester 10/15/14 CSC 2/456 1 Basic Memory Management Program must be brought into memory and placed within a process for it
Basic Memory Management CS 256/456 Dept. of Computer Science, University of Rochester 10/15/14 CSC 2/456 1 Basic Memory Management Program must be brought into memory and placed within a process for it
UNIT - I: COMPUTER ARITHMETIC, REGISTER TRANSFER LANGUAGE & MICROOPERATIONS
 UNIT - I: COMPUTER ARITHMETIC, REGISTER TRANSFER LANGUAGE & MICROOPERATIONS (09 periods) Computer Arithmetic: Data Representation, Fixed Point Representation, Floating Point Representation, Addition and
UNIT - I: COMPUTER ARITHMETIC, REGISTER TRANSFER LANGUAGE & MICROOPERATIONS (09 periods) Computer Arithmetic: Data Representation, Fixed Point Representation, Floating Point Representation, Addition and
GUJARAT TECHNOLOGICAL UNIVERSITY MASTER OF COMPUTER APPLICATION SEMESTER: III
 GUJARAT TECHNOLOGICAL UNIVERSITY MASTER OF COMPUTER APPLICATION SEMESTER: III Subject Name: Operating System (OS) Subject Code: 630004 Unit-1: Computer System Overview, Operating System Overview, Processes
GUJARAT TECHNOLOGICAL UNIVERSITY MASTER OF COMPUTER APPLICATION SEMESTER: III Subject Name: Operating System (OS) Subject Code: 630004 Unit-1: Computer System Overview, Operating System Overview, Processes
Chapter 1 INTRODUCTION. SYS-ED/ Computer Education Techniques, Inc.
 Chapter 1 INTRODUCTION SYS-ED/ Computer Education Techniques, Inc. Objectives You will learn: Facilities and features of PL/1. Structure of programs written in PL/1. Data types. Storage classes, control,
Chapter 1 INTRODUCTION SYS-ED/ Computer Education Techniques, Inc. Objectives You will learn: Facilities and features of PL/1. Structure of programs written in PL/1. Data types. Storage classes, control,
ISPF Users Boot Camp - Part 2 of 2
 Interactive System Productivity Facility (ISPF) ISPF Users Boot Camp - Part 2 of 2 SHARE 116 Session 8677 Peter Van Dyke IBM Australia SHARE 116, Winter 2011 pvandyke@au1.ibm.com Introduction Our jobs
Interactive System Productivity Facility (ISPF) ISPF Users Boot Camp - Part 2 of 2 SHARE 116 Session 8677 Peter Van Dyke IBM Australia SHARE 116, Winter 2011 pvandyke@au1.ibm.com Introduction Our jobs
A Proposal for Endian-Portable Record Representation Clauses
 A Proposal for Endian-Portable Record Representation Clauses Norman H. Cohen What problem are we solving? There are at least two endian problems. One is the run-time problem of transferring data between
A Proposal for Endian-Portable Record Representation Clauses Norman H. Cohen What problem are we solving? There are at least two endian problems. One is the run-time problem of transferring data between
Goals of this Lecture
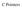 C Pointers Goals of this Lecture Help you learn about: Pointers and application Pointer variables Operators & relation to arrays 2 Pointer Variables The first step in understanding pointers is visualizing
C Pointers Goals of this Lecture Help you learn about: Pointers and application Pointer variables Operators & relation to arrays 2 Pointer Variables The first step in understanding pointers is visualizing
