The Future of Campus Video Surveillance
|
|
|
- Emory Barrett
- 5 years ago
- Views:
Transcription
1
2 The Future of Campus Video Surveillance Thursday, Dec. 6, :30 a.m. 09:30 a.m. Mark Bonde Parallel Technologies
3 Mark Bonde Publisher IPVS Magazine Publication Focused on the transition from Analog to IP (12 issues) Security Consultants International Clients included: Acti, Agent Vi, Allina Health, Axis Communication, BriefCam, Cernium, Firetide, Microsoft VP of Sales and Operation EMEA/APAC - Connex International Training and Professional Services Division of Milestone Systems Sr. Manage Business and Partner Development EMEA/APAC - Milestone Systems Sr. Account Manager Parallel Technologies Physical Security
4 Parallel Technologies WHAT WE DO HOW WE DO IT BETTER WHY WE MATTER We provide complete solutions for Reliable Data Centers and Intelligent Buildings. We help clients define their needs, and deliver better solutions through superior engineering and technology. We are the only single source provider that delivers complete solutions for reliable data centers and intelligent buildings.
5 Presentation Objectives 6S References Architecture History of the video security market The rise of IP video The future of video surveillance Preparing for the future
6 Video Surveillance: The Basics
7 SURVEILLANCE REFERENCE ARCHITECTURE 6 S Reference Architecture is an easy way to think about video surveillance solutions Each of the 6 S represent a critical component of the solution o Surveillance o Structured Cabling o Switches o Servers o Software o Storage You cannot have a video surveillance without having each of these elements
8 6S REFERENCE ARCHITECTURE OVERVIEW Each S Category has a plethora of particulars Each S can have a wide array of variables based on the particulars within a given environment and the overall objectives of the solution The order of the S matter in thinking about the relationship of each of the components Follow the Light. Surveillance Resolution Framerate Compression Image Sensor Structured Cabling CAT 6 UTP Cable Management Switches Power Over Ethernet (PoE) Bandwidth VLAN Server CPU Video processing Throughput Software GUI Operating System Integration Active Directory Storage Terabytes Retention Time
9 6S REFERENCE ARCHITECTURE OVERVIEW All of the S categories are interdependent. Decisions that you make on one will have an impact on another Gaining an understanding how each of the technologies interrelates is important to delivering the most optimal solution Understanding that there are implications of a decision in 1 dimension to another dimension is important in managing a video surveillance solution
10 Video Surveillance: A History
11 THE HISTORY OF PHYSICAL SECURITY TECHNOLOGY Stand alone systems (i.e. no communication between applications) Non-network based technology (aka Analog) Proprietary systems Plug in and forget Limited use and planning Non-strategic application in most settings Highly fragmented market Non-sophistication use cases and applications
12 A NEW ERA BEGINS The Rise of the Network!!! Internet Revolutions Invention of the IP Camera Power over Ethernet Processor Development Software Development Martin Gren
13 CROSSING THE CHASM Geoffrey Moore saw how innovation worked (1991) Many physical security technologies have recently crossed the chasm bringing additional capital investment into the market from major corporations
14 THE IMPACT OF CHASM CROSSINGS Technology offers more for less Increased interoperability enabling the streamlining of process and procedure All physical security application on a single network Open Systems Application Program Interface Software Development Kits Increasingly more strategic
15 GREATER SPECIALIZATION
16 Video Surveillance into the Future
17 In technology, whatever can be done will be done -Andy Grove
18 MORE MORE MORE The market will continue to demand more from its video surveillance solution. More includes: More cameras More resolution More retention time More connections to other systems More strategic More use cases
19 GREATER SPECIALIZATION Greater specialization for the administration and management of camera technology will continue to expand Subject matter experts on both camera hardware and system software will grow more valuable within organizations as video surveillance continues to be more strategically important
20 INCREASE VALUE IN TRAINING Ongoing training for end users will continue to be a major push as knowledge required to operate and manage video surveillance solutions increases. Systems will continue to evolve and change, staying on top of the technology will increase in importance. Video management software provides user and administrators with more options on their system understanding these elements will allow users to extract more value from their video.
21 USE CASE EXPLOSION The use cases for video surveillance technology will continue to expand as organizations learn they can improve operational efficiency through video. Process management will become a greater driver of more robust video technology being deployed in small organizations. Organizations will increase efficiencies by leveraging video technology that is accessible to a wider audience and is no longer seen as simply a security function.
22 360 DEGREE More 360 degree cameras will be deployed as more manufacturers will produce this technology Coverage areas and post investigative benefits will drive these into various production areas De-warping improvements will continue and higher density pixilation will make these cameras appealing
23 MULTI-SENSOR OPTIONS More multi-sensor cameras will be deployed as more manufacturers will produce this technology Coverage areas and post investigative benefits will drive these into various locations especially on the exterior of buildings
24 THE UPPER LIMITS OF RESOLUTION! The upper limits of video resolution will be reached as manufacturers race to meet user requirements. Higher resolution cameras will become more common place. The resolution war will ultimately fizzle out as the upper limits will be reached and new applications will be hard to find. These cameras will place additional strain on storage and workstation computing as users look to view these cameras. Video management software organizations will continue to improve their edge decoding capabilities in light of this.
25 COMPRESSION IMPROVEMENTS An increase in camera counts and resolution will continue to push the market to great compression capability. Compression will improve through two methods: 1.Proprietary compression algorithms on the edge will get better and reduce image file size 2.Camera manufacturers and VMS providers will more widely adopt h.265
26 DECOMPRESSING ON THE EDGE Given the larger image sizes and greater compression technology the ability to decompress images on the edge will be more important. Recent releases of major VMS software have focused on solving this problem as client workstations are looking to view 5 MP and 4K cameras. End users will need to be more mindful then ever on the workstation impact of their camera technology.
27 VIDEO ANALYTICS Simple video analytics will continue to be adopted more frequently as users learn the full capability of the camera technologies that can be deployed. Directional motion Crossing a line More complex behavior analytic scenarios will continue to grow but wide adoption will be limited as most organization will not commit to long-term management and support of these analytics. Crowd gathering Objective left behind
28 VIDEO ANALYTICS Learning analytics will improve and will be adopted at high installation. Sound analytics that use camera technology will become more prevalent.
29 Sound Analytics Sound analytics that detect aggression and gunshots will become more common and will alert on video surveillance applications. These analytics will be deployed on the camera and as separate microphones.
30 Video Redaction The redaction of faces in live video is going to become a requirement as protecting innocent people in video becomes more and more important.
31 SECURITY OF SECURITY INCREASINGLY MORE IMPORTANT Breaches of network security cameras will continue to happen as hackers seek to disrupt organizations Various video will be found on YouTube and systems will be held hijacked Manufacturers will increase education and technology to limit the exposure that camera systems have to hackers Integrators, IT, and security will improve their security protocols with systems to manage passwords, users rights and encryption
32 Firmware One Impacts Many Writing the code for cameras Problems extend to products across the manufacturer line
33 AND OEM RELATIONSHIPS Become Many More. Manufacturers sell to other organizations around the world Security Problems are dismissed or take time to filter through the supply chain. Cameras remain vulnerable
34 LICENSE PLATE RECOGNITION Deployment of license plate recognition will decrease because of the following: The price to deploy this technology comes down Infrastructure to support the addition of LPR cameras is in place and it is just an incremental addition Cloud based applications providing reduced licensing method are established Accuracy increase for reading plates
35 UNIFICATION More organizations will deploy unified security solutions that enable multiple security functions to operate on a single platform Single platform for video, card access, intercom, and License Plate Recognition Streamline event management and investigation processes Increase visibility and capacity to visualize alarm activities
36 CLOUD, CLOUD, CLOUD Cloud services will continue to expand for smaller installations and remote offices Additional services like LPR will get processed in the Cloud for installation of all sizes Large scale video surveillance deployments will continue to be housed onsite until bandwidth limitations are reduced
37 WATCHING THE WATCHERS Oversight on those that are using and managing video surveillance systems will become more important. Developing of policies and procedures around video surveillance usage and review will become more common.
38 Preparing for the Future Today
39 GIVE YOURSELF OPTIONS Build on open platform systems Use best of breed hardware to provide flexibility Expand the system you have over time Continue to learn the systems that you have to take advantage of the features and functionality that exist Select a strategic partner to assist you on the path
40 Thank you! Mark Bonde Parallel Technologies
41 WE VALUE YOUR INPUT Please complete the session evaluation in the conference app: 1. Open your app and open the Schedule tab 2. Find and open this session 3. Click the Session Evaluation link and complete! Thank you!
Security of Security. Cyber-Secure? Is Your Security. Mark Bonde Parallel Technologies. Wednesday, Dec. 5, :00 a.m. 11:00 a.m.
 Security of Security Is Your Security Cyber-Secure? Wednesday, Dec. 5, 2018 10:00 a.m. 11:00 a.m. Mark Bonde Parallel Technologies Mark Bonde Publisher IPVS Magazine Publication Focused on the transition
Security of Security Is Your Security Cyber-Secure? Wednesday, Dec. 5, 2018 10:00 a.m. 11:00 a.m. Mark Bonde Parallel Technologies Mark Bonde Publisher IPVS Magazine Publication Focused on the transition
Securing Your Campus
 Securing Your Campus Copyright CheckVideo LLC. All Rights Reserved. Introduction Security and Safety Officers are committed to providing a safe and welcoming learning environment that prepares students
Securing Your Campus Copyright CheckVideo LLC. All Rights Reserved. Introduction Security and Safety Officers are committed to providing a safe and welcoming learning environment that prepares students
Axis IP-Surveillance. Endless possibilities for video surveillance.
 Axis IP-Surveillance. Endless possibilities for video surveillance. Meeting today s video surveillance challenges The video surveillance market is booming, driven by increased public and private security
Axis IP-Surveillance. Endless possibilities for video surveillance. Meeting today s video surveillance challenges The video surveillance market is booming, driven by increased public and private security
Video Surveillance Solutions Product Brochure
 Video Surveillance Solutions Product Brochure Avigilon surveillance solutions provide enhanced image detail and system control Avigilon designs and manufactures innovative, high-definition surveillance
Video Surveillance Solutions Product Brochure Avigilon surveillance solutions provide enhanced image detail and system control Avigilon designs and manufactures innovative, high-definition surveillance
The smart choice for industrial switches
 The smart choice for industrial switches Help your customers transform their smart cities, automated factories and wireless outdoor environments. A healthy margin and full support Specify D-Link industrial
The smart choice for industrial switches Help your customers transform their smart cities, automated factories and wireless outdoor environments. A healthy margin and full support Specify D-Link industrial
Grow Your Services Business
 Grow Your Services Business Cisco Services Channel Program One Experience. Expanding Opportunities. Expand Your Services Practice More Profitably Together with Cisco Our customers face tough business
Grow Your Services Business Cisco Services Channel Program One Experience. Expanding Opportunities. Expand Your Services Practice More Profitably Together with Cisco Our customers face tough business
Enhancing the Cybersecurity of Federal Information and Assets through CSIP
 TECH BRIEF How BeyondTrust Helps Government Agencies Address Privileged Access Management to Improve Security Contents Introduction... 2 Achieving CSIP Objectives... 2 Steps to improve protection... 3
TECH BRIEF How BeyondTrust Helps Government Agencies Address Privileged Access Management to Improve Security Contents Introduction... 2 Achieving CSIP Objectives... 2 Steps to improve protection... 3
Hybrid Cloud for Business Communications
 Hybrid Cloud for Business Communications THE ESSENTIAL GUIDE So you re considering hybrid cloud for your business communications. You re not alone! In fact, more and more businesses are turning to cloud
Hybrid Cloud for Business Communications THE ESSENTIAL GUIDE So you re considering hybrid cloud for your business communications. You re not alone! In fact, more and more businesses are turning to cloud
ProDeploy Suite. Accelerate enterprise technology adoption with expert deployment designed for you
 Accelerate enterprise technology adoption with expert deployment designed for you 1 Shift resources to innovate and drive better business outcomes The landscape faced by IT managers and business leaders
Accelerate enterprise technology adoption with expert deployment designed for you 1 Shift resources to innovate and drive better business outcomes The landscape faced by IT managers and business leaders
Evolution For Enterprises In A Cloud World
 Evolution For Enterprises In A Cloud World Foreword Cloud is no longer an unseen, futuristic technology that proves unattainable for enterprises. Rather, it s become the norm; a necessity for realizing
Evolution For Enterprises In A Cloud World Foreword Cloud is no longer an unseen, futuristic technology that proves unattainable for enterprises. Rather, it s become the norm; a necessity for realizing
Using the Network to Optimize a Virtualized Data Center
 Using the Network to Optimize a Virtualized Data Center Contents Section I: Introduction The Rise of Virtual Computing. 1 Section II: The Role of the Network. 3 Section III: Network Requirements of the
Using the Network to Optimize a Virtualized Data Center Contents Section I: Introduction The Rise of Virtual Computing. 1 Section II: The Role of the Network. 3 Section III: Network Requirements of the
Internet of Things Toolkit for Small and Medium Businesses
 Your Guide #IoTatWork to IoT Security #IoTatWork Internet of Things Toolkit for Small and Medium Businesses Table of Contents Introduction 1 The Internet of Things (IoT) 2 Presence of IoT in Business Sectors
Your Guide #IoTatWork to IoT Security #IoTatWork Internet of Things Toolkit for Small and Medium Businesses Table of Contents Introduction 1 The Internet of Things (IoT) 2 Presence of IoT in Business Sectors
White paper. Axis and Intelligent Video (IV)
 White paper Axis and Intelligent Video (IV) Table of contents 1. What is intelligent video? 3 2. Why is it an important development? 3 3. System design strategies for intelligent video 4 4. Axis and intelligent
White paper Axis and Intelligent Video (IV) Table of contents 1. What is intelligent video? 3 2. Why is it an important development? 3 3. System design strategies for intelligent video 4 4. Axis and intelligent
Transforming Security from Defense in Depth to Comprehensive Security Assurance
 Transforming Security from Defense in Depth to Comprehensive Security Assurance February 28, 2016 Revision #3 Table of Contents Introduction... 3 The problem: defense in depth is not working... 3 The new
Transforming Security from Defense in Depth to Comprehensive Security Assurance February 28, 2016 Revision #3 Table of Contents Introduction... 3 The problem: defense in depth is not working... 3 The new
Intelligent IP Video Surveillance
 Intelligent IP Video Surveillance Omnicast is the ideal solution for organizations requiring seamless management of digital video, audio and data across any IP network. With innovative features such as
Intelligent IP Video Surveillance Omnicast is the ideal solution for organizations requiring seamless management of digital video, audio and data across any IP network. With innovative features such as
Bringing OpenStack to the Enterprise. An enterprise-class solution ensures you get the required performance, reliability, and security
 Bringing OpenStack to the Enterprise An enterprise-class solution ensures you get the required performance, reliability, and security INTRODUCTION Organizations today frequently need to quickly get systems
Bringing OpenStack to the Enterprise An enterprise-class solution ensures you get the required performance, reliability, and security INTRODUCTION Organizations today frequently need to quickly get systems
IBM POWER SYSTEMS: YOUR UNFAIR ADVANTAGE
 IBM POWER SYSTEMS: YOUR UNFAIR ADVANTAGE Choosing IT infrastructure is a crucial decision, and the right choice will position your organization for success. IBM Power Systems provides an innovative platform
IBM POWER SYSTEMS: YOUR UNFAIR ADVANTAGE Choosing IT infrastructure is a crucial decision, and the right choice will position your organization for success. IBM Power Systems provides an innovative platform
Cisco Wireless Video Surveillance: Improving Operations and Security
 Cisco Wireless Video Surveillance: Improving Operations and Security What You Will Learn Today s organizations need flexible, intelligent systems to help protect people and assets as well as streamline
Cisco Wireless Video Surveillance: Improving Operations and Security What You Will Learn Today s organizations need flexible, intelligent systems to help protect people and assets as well as streamline
Qshare - ISO compliance made easy. Get ahead of the competition. Get 1SO 9001 Certified. We make it happen. ENVIRONMENTAL & QUALITY SOLUTIONS
 Get ahead of the competition. Get 1SO 9001 Certified. We make it happen. Forge ahead in new markets. Be environmentally responsible. Stay ISO 14001 compliant. We make it possible. Stay health and safety
Get ahead of the competition. Get 1SO 9001 Certified. We make it happen. Forge ahead in new markets. Be environmentally responsible. Stay ISO 14001 compliant. We make it possible. Stay health and safety
Security Challenges: Integrating Apple Computers into Windows Environments
 Integrating Apple Computers into Windows Environments White Paper Parallels Mac Management for Microsoft SCCM 2018 Presented By: Table of Contents Environments... 3 Requirements for Managing Mac Natively
Integrating Apple Computers into Windows Environments White Paper Parallels Mac Management for Microsoft SCCM 2018 Presented By: Table of Contents Environments... 3 Requirements for Managing Mac Natively
The New Video Discussion: Selling New Innovative Products or Time Tested Technologies.
 The New Video Discussion: Selling New Innovative Products or Time Tested Technologies. Steven Fair, EVP Sales - NVT Phybridge Rob Hile, General Manager - Florida, GC&E Systems Group Tim Purpura, VP / Publisher
The New Video Discussion: Selling New Innovative Products or Time Tested Technologies. Steven Fair, EVP Sales - NVT Phybridge Rob Hile, General Manager - Florida, GC&E Systems Group Tim Purpura, VP / Publisher
MASERGY S MANAGED SD-WAN
 MASERGY S MANAGED New Performance Options for Hybrid Networks Business Challenges WAN Ecosystem Features and Benefits Use Cases INTRODUCTION Organizations are leveraging technology to transform the way
MASERGY S MANAGED New Performance Options for Hybrid Networks Business Challenges WAN Ecosystem Features and Benefits Use Cases INTRODUCTION Organizations are leveraging technology to transform the way
Digital Renewable Ecosystem on Predix Platform from GE Renewable Energy
 Digital Renewable Ecosystem on Predix Platform from GE Renewable Energy Business Challenges Investment in the Industrial Internet of Things (IIoT) is expected to top $60 trillion during the next 15 years.
Digital Renewable Ecosystem on Predix Platform from GE Renewable Energy Business Challenges Investment in the Industrial Internet of Things (IIoT) is expected to top $60 trillion during the next 15 years.
Run a Smart Workplace Introducing the Digital Building. Digital Building Solutions
 Digital Building Solutions Run a Smart Workplace Introducing the Digital Building Maximize efficiency and productivity Enhance infrastructure flexibility & network security Reduce installation and operating
Digital Building Solutions Run a Smart Workplace Introducing the Digital Building Maximize efficiency and productivity Enhance infrastructure flexibility & network security Reduce installation and operating
Halifax Regional Municipality
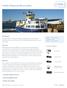 Halifax Regional Municipality Challenge Leverage existing IT infrastructure to design a high-definition surveillance system that helps protect corporate assets across the Halifax Regional Municipality
Halifax Regional Municipality Challenge Leverage existing IT infrastructure to design a high-definition surveillance system that helps protect corporate assets across the Halifax Regional Municipality
CASE STUDY: USING THE HYBRID CLOUD TO INCREASE CORPORATE VALUE AND ADAPT TO COMPETITIVE WORLD TRENDS
 CASE STUDY: USING THE HYBRID CLOUD TO INCREASE CORPORATE VALUE AND ADAPT TO COMPETITIVE WORLD TRENDS Geoff Duncan, Senior Solutions Architect, Digital Fortress Brandon Tanner, Senior Manager, Rentsys Recovery
CASE STUDY: USING THE HYBRID CLOUD TO INCREASE CORPORATE VALUE AND ADAPT TO COMPETITIVE WORLD TRENDS Geoff Duncan, Senior Solutions Architect, Digital Fortress Brandon Tanner, Senior Manager, Rentsys Recovery
The Latest in Open Space Video Surveillance: Multi-Sensor Camera Technology
 The Latest in Open Space Video Surveillance: Multi-Sensor Camera Technology 1 TEAM Chris Sessa Arecont Vision Director of Sales Northeast & Great Lakes Jim Henry KratosPSS Executive VP Kevin Saldanha Schneider
The Latest in Open Space Video Surveillance: Multi-Sensor Camera Technology 1 TEAM Chris Sessa Arecont Vision Director of Sales Northeast & Great Lakes Jim Henry KratosPSS Executive VP Kevin Saldanha Schneider
Achieving Digital Transformation: FOUR MUST-HAVES FOR A MODERN VIRTUALIZATION PLATFORM WHITE PAPER
 Achieving Digital Transformation: FOUR MUST-HAVES FOR A MODERN VIRTUALIZATION PLATFORM WHITE PAPER Table of Contents The Digital Transformation 3 Four Must-Haves for a Modern Virtualization Platform 3
Achieving Digital Transformation: FOUR MUST-HAVES FOR A MODERN VIRTUALIZATION PLATFORM WHITE PAPER Table of Contents The Digital Transformation 3 Four Must-Haves for a Modern Virtualization Platform 3
Secure Data Acquisition, Communication, and Processing for Your IoT Solutions
 Secure Data Acquisition, Communication, and Processing for Your IoT Solutions Guidelines for Ensuring a Successful Implementation by Dr. Mihai Voicu, Chief Information Security Officer, Telit Contents
Secure Data Acquisition, Communication, and Processing for Your IoT Solutions Guidelines for Ensuring a Successful Implementation by Dr. Mihai Voicu, Chief Information Security Officer, Telit Contents
Axis Megapixel Network Cameras. See what you ve been missing
 Axis Megapixel Network Cameras See what you ve been missing Megapixel network cameras Megapixel network cameras have an important role to play in video surveillance applications. They are obviously more
Axis Megapixel Network Cameras See what you ve been missing Megapixel network cameras Megapixel network cameras have an important role to play in video surveillance applications. They are obviously more
Milestone Systems. XProtect VMS 2017 R2. System Architecture Document. XProtect Corporate XProtect Expert XProtect Professional+ XProtect Express+
 Milestone Systems XProtect VMS 2017 R2 System Architecture Document XProtect Corporate XProtect Expert XProtect Professional+ XProtect Express+ Contents Introduction... 6 Target audience and purpose...
Milestone Systems XProtect VMS 2017 R2 System Architecture Document XProtect Corporate XProtect Expert XProtect Professional+ XProtect Express+ Contents Introduction... 6 Target audience and purpose...
Technology for a Changing World
 Technology for a Changing World Cisco Expo 2009 Axel Clauberg Director, Solutions & Architectures, Emerging Markets, Cisco Systems November 10, 2009 1 VISION Changing the way the World Lives, Works, Plays
Technology for a Changing World Cisco Expo 2009 Axel Clauberg Director, Solutions & Architectures, Emerging Markets, Cisco Systems November 10, 2009 1 VISION Changing the way the World Lives, Works, Plays
Avigilon Control Center 6 Software
 Avigilon Control Center 6 Software ACC software is easy-to-use video management software that optimizes the way security professionals manage and interact with high-definition video. It efficiently captures
Avigilon Control Center 6 Software ACC software is easy-to-use video management software that optimizes the way security professionals manage and interact with high-definition video. It efficiently captures
Desktop Virtualization for Higher Education. The Virtual Lab
 Desktop Virtualization for Higher Education The Virtual Lab What is the Virtual Lab? WHAT IS THE VIRTUAL LAB? Transformational technology for Higher Ed labs collaboration between Dell & VMware Virtualize
Desktop Virtualization for Higher Education The Virtual Lab What is the Virtual Lab? WHAT IS THE VIRTUAL LAB? Transformational technology for Higher Ed labs collaboration between Dell & VMware Virtualize
Virtual Security Server
 Data Sheet VSS Virtual Security Server Security clients anytime, anywhere, any device CENTRALIZED CLIENT MANAGEMENT UP TO 50% LESS BANDWIDTH UP TO 80 VIDEO STREAMS MOBILE ACCESS INTEGRATED SECURITY SYSTEMS
Data Sheet VSS Virtual Security Server Security clients anytime, anywhere, any device CENTRALIZED CLIENT MANAGEMENT UP TO 50% LESS BANDWIDTH UP TO 80 VIDEO STREAMS MOBILE ACCESS INTEGRATED SECURITY SYSTEMS
Core Services for ediscovery Perfection
 BEST-IN-CLASS DATA ENVIRONMENTS. Core Services for ediscovery Perfection MANAGE MANAGE IMPLEMENT IMPLEMENT ASSESS Core Services for ediscovery Perfection George Jon is an ediscovery infrastructure specialist
BEST-IN-CLASS DATA ENVIRONMENTS. Core Services for ediscovery Perfection MANAGE MANAGE IMPLEMENT IMPLEMENT ASSESS Core Services for ediscovery Perfection George Jon is an ediscovery infrastructure specialist
HPE Partner Ready Digital Marketing Program
 HPE Partner Ready Digital Marketing Program Accelerating your digital marketing proficiency and execution to drive business growth Collaborate Get started Table of Contents Changing B2B Buyer Behavior
HPE Partner Ready Digital Marketing Program Accelerating your digital marketing proficiency and execution to drive business growth Collaborate Get started Table of Contents Changing B2B Buyer Behavior
Modernizing Healthcare IT for the Data-driven Cognitive Era Storage and Software-Defined Infrastructure
 Modernizing Healthcare IT for the Data-driven Cognitive Era Storage and Software-Defined Infrastructure An IDC InfoBrief, Sponsored by IBM April 2018 Executive Summary Today s healthcare organizations
Modernizing Healthcare IT for the Data-driven Cognitive Era Storage and Software-Defined Infrastructure An IDC InfoBrief, Sponsored by IBM April 2018 Executive Summary Today s healthcare organizations
ALPR to Milestone Integration. User Ma
 C2P ALPR ALPR to Milestone Integration User Ma Page 1 Contents Overview... 3 Introduction... 3 Critical features include:... 4 Installation... 5 Figure 1... 5 Pre-install requirements... 6 Installation
C2P ALPR ALPR to Milestone Integration User Ma Page 1 Contents Overview... 3 Introduction... 3 Critical features include:... 4 Installation... 5 Figure 1... 5 Pre-install requirements... 6 Installation
Hitachi Unified Compute Platform Pro for VMware vsphere
 SOLUTION PROFILE Hitachi Unified Compute Platform Pro for VMware vsphere Accelerate Your Business-Critical Workloads to the Next-Generation Converged Infrastructure Relentless trends of increasing data
SOLUTION PROFILE Hitachi Unified Compute Platform Pro for VMware vsphere Accelerate Your Business-Critical Workloads to the Next-Generation Converged Infrastructure Relentless trends of increasing data
ALIENVAULT USM FOR AWS SOLUTION GUIDE
 ALIENVAULT USM FOR AWS SOLUTION GUIDE Summary AlienVault Unified Security Management (USM) for AWS is a unified security platform providing threat detection, incident response, and compliance management
ALIENVAULT USM FOR AWS SOLUTION GUIDE Summary AlienVault Unified Security Management (USM) for AWS is a unified security platform providing threat detection, incident response, and compliance management
21ST CENTURY CYBER SECURITY FOR MEDIA AND BROADCASTING
 WWW.HCLTECH.COM 21ST CENTURY CYBER SECURITY FOR MEDIA AND BROADCASTING THE AGE OF DISRUPTION: THE AGE OF CYBER THREATS While the digital era has brought with it significant advances in technology, capabilities
WWW.HCLTECH.COM 21ST CENTURY CYBER SECURITY FOR MEDIA AND BROADCASTING THE AGE OF DISRUPTION: THE AGE OF CYBER THREATS While the digital era has brought with it significant advances in technology, capabilities
Moving From Reactive to Proactive Storage Management with an On-demand Cloud Solution
 Moving From Reactive to Proactive Storage Management with an On-demand Cloud Solution The Ever-Present Storage Management Conundrum In the modern IT landscape, the storage management conundrum is as familiar
Moving From Reactive to Proactive Storage Management with an On-demand Cloud Solution The Ever-Present Storage Management Conundrum In the modern IT landscape, the storage management conundrum is as familiar
Complete Data Protection & Disaster Recovery Solution
 Complete Data Protection & Disaster Recovery Solution Quadric Software 2015 We were looking at other solutions. Alike was the best with XenServer, and none of them had Alike s compression abilities. After
Complete Data Protection & Disaster Recovery Solution Quadric Software 2015 We were looking at other solutions. Alike was the best with XenServer, and none of them had Alike s compression abilities. After
Virtualized Network Services SDN solution for enterprises
 Virtualized Network Services SDN solution for enterprises Nuage Networks Virtualized Network Services (VNS) is a fresh approach to business networking that seamlessly links your enterprise s locations
Virtualized Network Services SDN solution for enterprises Nuage Networks Virtualized Network Services (VNS) is a fresh approach to business networking that seamlessly links your enterprise s locations
Transform your video services with a cloud platform: Succeed in a fragmented marketplace
 with a cloud platform: Succeed in a fragmented marketplace Contents 3 4 7 cloud-based platform 8 10 12 14 16 points: Great in action 18 : Your business faces a significant challenge. Subscriber demands
with a cloud platform: Succeed in a fragmented marketplace Contents 3 4 7 cloud-based platform 8 10 12 14 16 points: Great in action 18 : Your business faces a significant challenge. Subscriber demands
Understanding Office 365: Is A Cloud Based Solution Right For Your Business?
 Understanding Office 365: Is A Cloud Based Solution Right For Your Business? (855) 479-4343 www.it-va.com 4530 Plank Rd., Ste. 111, Fredericksburg, VA 22407 Table of Contents Introduction 3 What is Cloud
Understanding Office 365: Is A Cloud Based Solution Right For Your Business? (855) 479-4343 www.it-va.com 4530 Plank Rd., Ste. 111, Fredericksburg, VA 22407 Table of Contents Introduction 3 What is Cloud
Part of the complete suite of itracs award-winning DCIM capabilities. DCIM Software. itracs CPIM : Mastering the Connectivity Challenge
 Part of the complete suite of itracs award-winning DCIM capabilities DCIM Software itracs CPIM : Mastering the Connectivity Challenge itracs CPIM Intelligence. Automation. Insight. Impact! Business Value
Part of the complete suite of itracs award-winning DCIM capabilities DCIM Software itracs CPIM : Mastering the Connectivity Challenge itracs CPIM Intelligence. Automation. Insight. Impact! Business Value
WHITE PAPER AUTHENTICATION YOUR WAY SECURING ACCESS IN A CHANGING WORLD
 WHITE PAPER AUTHENTICATION YOUR WAY SECURING ACCESS IN A CHANGING WORLD Imagine that you re a CISO in charge of identity and access management for a major global technology and manufacturing company. You
WHITE PAPER AUTHENTICATION YOUR WAY SECURING ACCESS IN A CHANGING WORLD Imagine that you re a CISO in charge of identity and access management for a major global technology and manufacturing company. You
Milestone Interconnect TM
 White paper Milestone Interconnect TM Prepared by: John Rasmussen, Senior Technical Product Manager, Corporate Business Unit, Milestone Systems Date: July 05, 2013 Table of Contents Introduction... 3 Target
White paper Milestone Interconnect TM Prepared by: John Rasmussen, Senior Technical Product Manager, Corporate Business Unit, Milestone Systems Date: July 05, 2013 Table of Contents Introduction... 3 Target
REMOTE MONITORING. Why Your Security Force Needs Support
 REMOTE MONITORING Why Your Security Force Needs Support In today s security industry, emerging technologies and an increased level of connectedness are creating opportunities for facility managers, IT
REMOTE MONITORING Why Your Security Force Needs Support In today s security industry, emerging technologies and an increased level of connectedness are creating opportunities for facility managers, IT
VMware Technology Overview. Leverage Nextiva Video Management Solution with VMware Virtualization Technology
 VMware Technology Overview Leverage Nextiva Video Management Solution with VMware Virtualization Technology Table of Contents Overview... 2 Seamless Integration within the IT Infrastructure... 2 Support
VMware Technology Overview Leverage Nextiva Video Management Solution with VMware Virtualization Technology Table of Contents Overview... 2 Seamless Integration within the IT Infrastructure... 2 Support
HOW TO ENABLE AFFORDABLE ENTERPRISE VIDEO FOR EVERYONE
 HOW TO ENABLE AFFORDABLE ENTERPRISE VIDEO FOR EVERYONE John Antanaitis VP Product & Solutions Marketing Jonathan Nikols VP Professional and Managed Services Polycom, Inc. All rights reserved. Agenda The
HOW TO ENABLE AFFORDABLE ENTERPRISE VIDEO FOR EVERYONE John Antanaitis VP Product & Solutions Marketing Jonathan Nikols VP Professional and Managed Services Polycom, Inc. All rights reserved. Agenda The
VMware Cloud Operations Management Technology Consulting Services
 VMware Cloud Operations Management Technology Consulting Services VMware Technology Consulting Services for Cloud Operations Management The biggest hurdle [that CIOs face as they move infrastructure and
VMware Cloud Operations Management Technology Consulting Services VMware Technology Consulting Services for Cloud Operations Management The biggest hurdle [that CIOs face as they move infrastructure and
ExtremeWireless WiNG NX 9500
 DATA SHEET ExtremeWireless WiNG NX 9500 Integrated Services Platform Series for the Private Cloud FEATURES COMPLETE VISIBILITY OF THE ENTIRE DISTRIBUTED DEPLOYMENT One point of configuration; ExtremeWireless
DATA SHEET ExtremeWireless WiNG NX 9500 Integrated Services Platform Series for the Private Cloud FEATURES COMPLETE VISIBILITY OF THE ENTIRE DISTRIBUTED DEPLOYMENT One point of configuration; ExtremeWireless
Create a sustainable, high-performance university campus.
 Create a sustainable, high-performance university campus. Discover how to maximize efficiency, safety, and productivity with an integrated university infrastructure. Make the most of your energy SM Today
Create a sustainable, high-performance university campus. Discover how to maximize efficiency, safety, and productivity with an integrated university infrastructure. Make the most of your energy SM Today
SD-WAN. Enabling the Enterprise to Overcome Barriers to Digital Transformation. An IDC InfoBrief Sponsored by Comcast
 SD-WAN Enabling the Enterprise to Overcome Barriers to Digital Transformation An IDC InfoBrief Sponsored by Comcast SD-WAN Is Emerging as an Important Driver of Business Results The increasing need for
SD-WAN Enabling the Enterprise to Overcome Barriers to Digital Transformation An IDC InfoBrief Sponsored by Comcast SD-WAN Is Emerging as an Important Driver of Business Results The increasing need for
Addressing the Challenges and Complexities Facing Physical Security Networks
 Addressing the Challenges and Complexities Facing Physical Security Networks CHAPTERS I. II. III. IV. V. VI. Introduction What is Physical Security Network Monitoring? About Vunetrix Areas of Expertise
Addressing the Challenges and Complexities Facing Physical Security Networks CHAPTERS I. II. III. IV. V. VI. Introduction What is Physical Security Network Monitoring? About Vunetrix Areas of Expertise
STRATEGIC PLAN
 STRATEGIC PLAN 2013-2018 In an era of growing demand for IT services, it is imperative that strong guiding principles are followed that will allow for the fulfillment of the Division of Information Technology
STRATEGIC PLAN 2013-2018 In an era of growing demand for IT services, it is imperative that strong guiding principles are followed that will allow for the fulfillment of the Division of Information Technology
NVIDIA DGX SYSTEMS PURPOSE-BUILT FOR AI
 NVIDIA DGX SYSTEMS PURPOSE-BUILT FOR AI Overview Unparalleled Value Product Portfolio Software Platform From Desk to Data Center to Cloud Summary AI researchers depend on computing performance to gain
NVIDIA DGX SYSTEMS PURPOSE-BUILT FOR AI Overview Unparalleled Value Product Portfolio Software Platform From Desk to Data Center to Cloud Summary AI researchers depend on computing performance to gain
Changing the Economics of Lossless Full Packet Capture Enabling Real-time Visibility
 Executive Summary: Changing the Economics of Lossless Full Packet Capture Enabling Real-time Visibility March 2017 All questions and enquiries regarding this white paper should be directed to: Dan Cybulski
Executive Summary: Changing the Economics of Lossless Full Packet Capture Enabling Real-time Visibility March 2017 All questions and enquiries regarding this white paper should be directed to: Dan Cybulski
The Top Five Reasons to Deploy Software-Defined Networks and Network Functions Virtualization
 The Top Five Reasons to Deploy Software-Defined Networks and Network Functions Virtualization May 2014 Prepared by: Zeus Kerravala The Top Five Reasons to Deploy Software-Defined Networks and Network Functions
The Top Five Reasons to Deploy Software-Defined Networks and Network Functions Virtualization May 2014 Prepared by: Zeus Kerravala The Top Five Reasons to Deploy Software-Defined Networks and Network Functions
Gen 1 Early 70s: 1 camera, 1 monitor. Gen 2 Late 70s: Add more Cameras
 What is Video Security? Gen 1 Early 70s: 1 camera, 1 monitor Gen 2 Late 70s: Add more Cameras Switcher Alarm Inputs What is Video Security? Gen 3 Early 80s: Add camera movement Video Switcher What is Video
What is Video Security? Gen 1 Early 70s: 1 camera, 1 monitor Gen 2 Late 70s: Add more Cameras Switcher Alarm Inputs What is Video Security? Gen 3 Early 80s: Add camera movement Video Switcher What is Video
The SD-WAN implementation handbook
 The SD-WAN implementation handbook Your practical guide to a pain-free deployment This is the future of your business Moving to SD-WAN makes plenty of sense, solving a lot of technical headaches and enabling
The SD-WAN implementation handbook Your practical guide to a pain-free deployment This is the future of your business Moving to SD-WAN makes plenty of sense, solving a lot of technical headaches and enabling
ALCATEL-LUCENT OPENTOUCH PERSONAL CLOUD A Revolution in Communications Applications for Enterprise End Users
 ALCATEL-LUCENT OPENTOUCH PERSONAL CLOUD A Revolution in Communications Applications for Enterprise End Users For the past 30 years, enterprise communications have been built around the personal computer,
ALCATEL-LUCENT OPENTOUCH PERSONAL CLOUD A Revolution in Communications Applications for Enterprise End Users For the past 30 years, enterprise communications have been built around the personal computer,
WiFi Evolution Drives the Need for Multigigabit Networks
 WiFi Evolution Drives the Need for Multigigabit Networks January 2015 Prepared by: Zeus Kerravala WiFi Evolution Drives the Need for Multigigabit Networks by Zeus Kerravala January 2015 º º º º º º º º
WiFi Evolution Drives the Need for Multigigabit Networks January 2015 Prepared by: Zeus Kerravala WiFi Evolution Drives the Need for Multigigabit Networks by Zeus Kerravala January 2015 º º º º º º º º
24th MONDAY. Overview 2018
 24th MONDAY Overview 2018 Imagination: your route to success At Imagination, we create and license market-leading processor solutions for graphics, vision & AI processing, and multi-standard communications.
24th MONDAY Overview 2018 Imagination: your route to success At Imagination, we create and license market-leading processor solutions for graphics, vision & AI processing, and multi-standard communications.
Move to IP with Confidence
 Move to IP with Confidence Extend PoE & IP Wherever You Need CHARIoT Series IP-Enabling Solutions FLEX Extender Kits Understanding the Core & Supporting Business Networks Single Pair UTP Point-topoint
Move to IP with Confidence Extend PoE & IP Wherever You Need CHARIoT Series IP-Enabling Solutions FLEX Extender Kits Understanding the Core & Supporting Business Networks Single Pair UTP Point-topoint
Top 4 considerations for choosing a converged infrastructure for private clouds
 Top 4 considerations for choosing a converged infrastructure for private clouds Organizations are increasingly turning to private clouds to improve efficiencies, lower costs, enhance agility and address
Top 4 considerations for choosing a converged infrastructure for private clouds Organizations are increasingly turning to private clouds to improve efficiencies, lower costs, enhance agility and address
UNLEASHING THE VALUE OF THE TERADATA UNIFIED DATA ARCHITECTURE WITH ALTERYX
 UNLEASHING THE VALUE OF THE TERADATA UNIFIED DATA ARCHITECTURE WITH ALTERYX 1 Successful companies know that analytics are key to winning customer loyalty, optimizing business processes and beating their
UNLEASHING THE VALUE OF THE TERADATA UNIFIED DATA ARCHITECTURE WITH ALTERYX 1 Successful companies know that analytics are key to winning customer loyalty, optimizing business processes and beating their
EVOLVING FROM BREACH PREVENTION TO BREACH ACCEPTANCE TO SECURING THE BREACH
 EVOLVING FROM BREACH PREVENTION TO BREACH ACCEPTANCE TO SECURING THE BREACH Jason Hart CISSP CISM VP Cloud Solutions Safenet Inc Session ID: Session Classification: SP0-W10 General Interest Today s issues
EVOLVING FROM BREACH PREVENTION TO BREACH ACCEPTANCE TO SECURING THE BREACH Jason Hart CISSP CISM VP Cloud Solutions Safenet Inc Session ID: Session Classification: SP0-W10 General Interest Today s issues
5G networks use-cases in 4G networks
 5G networks use-cases in 4G networks 5G Networks offering superior performance are just around the corner! Wait! Are applications that maximize the benefits of these networks ready? Contents 5G networks
5G networks use-cases in 4G networks 5G Networks offering superior performance are just around the corner! Wait! Are applications that maximize the benefits of these networks ready? Contents 5G networks
Cognizant Cloud Security Solution
 CLOUD SECURITY OVERVIEW Cognizant Cloud Security Solution Transform your security operation to protect your business across public and hybrid cloud environments. December 2017 The advantages of moving
CLOUD SECURITY OVERVIEW Cognizant Cloud Security Solution Transform your security operation to protect your business across public and hybrid cloud environments. December 2017 The advantages of moving
Experience Security, Risk, and Governance
 Experience Security, Risk, and Governance Agenda and recommended event path 26 28 March Vienna, Austria Contents 3 Welcome 4 Overview 5 Evening Programs 6 Sessions at-a-glance 11 Digital Transformation
Experience Security, Risk, and Governance Agenda and recommended event path 26 28 March Vienna, Austria Contents 3 Welcome 4 Overview 5 Evening Programs 6 Sessions at-a-glance 11 Digital Transformation
Effective and Essential Design Considerations in IP Surveillance. by: David Heath
 Effective and Essential Design Considerations in IP Surveillance by: David Heath Axis Communications Effective Design Why? When designing an IP Video Solution there are many factors that must be considered
Effective and Essential Design Considerations in IP Surveillance by: David Heath Axis Communications Effective Design Why? When designing an IP Video Solution there are many factors that must be considered
Accelerate Your Enterprise Private Cloud Initiative
 Cisco Cloud Comprehensive, enterprise cloud enablement services help you realize a secure, agile, and highly automated infrastructure-as-a-service (IaaS) environment for cost-effective, rapid IT service
Cisco Cloud Comprehensive, enterprise cloud enablement services help you realize a secure, agile, and highly automated infrastructure-as-a-service (IaaS) environment for cost-effective, rapid IT service
Virtualized Network Services SDN solution for service providers
 Virtualized Network Services SDN solution for service providers Nuage Networks Virtualized Network Services (VNS) is a fresh approach to business networking that seamlessly links your enterprise customers
Virtualized Network Services SDN solution for service providers Nuage Networks Virtualized Network Services (VNS) is a fresh approach to business networking that seamlessly links your enterprise customers
SUNY - BUFFALO. 10 Years Going and SUNYBuffalo Still Expanding. Campus-wide Security with Milestone Software. The Challenge.
 Customer Story 10 Years Going and SUNYBuffalo Still Expanding Campus-wide Security with Milestone Software The Challenge After successfully implementing Milestone IP video as a security solution in the
Customer Story 10 Years Going and SUNYBuffalo Still Expanding Campus-wide Security with Milestone Software The Challenge After successfully implementing Milestone IP video as a security solution in the
Application Security at Scale
 Jake Marcinko Standards Manager, PCI Security Standards Council Jeff Williams CTO, Contrast Security Application Security at Scale AppSec at Scale Delivering Timely Security Solutions / Services to Meet
Jake Marcinko Standards Manager, PCI Security Standards Council Jeff Williams CTO, Contrast Security Application Security at Scale AppSec at Scale Delivering Timely Security Solutions / Services to Meet
Preparing your network for the next wave of innovation
 Preparing your network for the next wave of innovation The future is exciting. Ready? 2 Executive brief For modern businesses, every day brings fresh challenges and opportunities. You must be able to adapt
Preparing your network for the next wave of innovation The future is exciting. Ready? 2 Executive brief For modern businesses, every day brings fresh challenges and opportunities. You must be able to adapt
Cloud Based Video Surveillance
 Cloud Based Video Surveillance Sharing video footage is a breeze with offsite cloud backup View multiple locations on a single screen Your video is always in your pocket with our awesome ios and Android
Cloud Based Video Surveillance Sharing video footage is a breeze with offsite cloud backup View multiple locations on a single screen Your video is always in your pocket with our awesome ios and Android
THE JOURNEY OVERVIEW THREE PHASES TO A SUCCESSFUL MIGRATION ADOPTION ACCENTURE IS 80% IN THE CLOUD
 OVERVIEW Accenture is in the process of transforming itself into a digital-first enterprise. Today, Accenture is 80 percent in a public cloud. As the journey continues, Accenture shares its key learnings
OVERVIEW Accenture is in the process of transforming itself into a digital-first enterprise. Today, Accenture is 80 percent in a public cloud. As the journey continues, Accenture shares its key learnings
Cisco Smart+Connected Communities
 Brochure Cisco Smart+Connected Communities Helping Cities on Their Digital Journey Cities worldwide are becoming digital or are evaluating strategies for doing so in order to make use of the unprecedented
Brochure Cisco Smart+Connected Communities Helping Cities on Their Digital Journey Cities worldwide are becoming digital or are evaluating strategies for doing so in order to make use of the unprecedented
product overview CRASH
 product overview CRASH e back up everyone, everywhere PROe Software Continuous backup for business Use CrashPlan PROe for continuous, cross-platform backup that works everywhere, enabling users to easily
product overview CRASH e back up everyone, everywhere PROe Software Continuous backup for business Use CrashPlan PROe for continuous, cross-platform backup that works everywhere, enabling users to easily
Securing Digital Transformation
 September 4, 2017 Securing Digital Transformation DXC Security Andreas Wuchner, CTO Security Innovation Risk surface is evolving and increasingly complex The adversary is highly innovative and sophisticated
September 4, 2017 Securing Digital Transformation DXC Security Andreas Wuchner, CTO Security Innovation Risk surface is evolving and increasingly complex The adversary is highly innovative and sophisticated
Please give me your feedback
 #HPEDiscover Please give me your feedback Session ID: B4385 Speaker: Aaron Spurlock Use the mobile app to complete a session survey 1. Access My schedule 2. Click on the session detail page 3. Scroll down
#HPEDiscover Please give me your feedback Session ID: B4385 Speaker: Aaron Spurlock Use the mobile app to complete a session survey 1. Access My schedule 2. Click on the session detail page 3. Scroll down
Best Practices in Securing a Multicloud World
 Best Practices in Securing a Multicloud World Actions to take now to protect data, applications, and workloads We live in a multicloud world. A world where a multitude of offerings from Cloud Service Providers
Best Practices in Securing a Multicloud World Actions to take now to protect data, applications, and workloads We live in a multicloud world. A world where a multitude of offerings from Cloud Service Providers
Video Surveillance. Best practices: Management of video surveillance streaming. Abstract. Introduction
 Video Surveillance Best practices: Management of video surveillance streaming Billy Short 3/30/2017 Abstract Video surveillance is becoming more and more prevalent in today's enterprise environments. Business
Video Surveillance Best practices: Management of video surveillance streaming Billy Short 3/30/2017 Abstract Video surveillance is becoming more and more prevalent in today's enterprise environments. Business
Windows 10 IoT Overview. Microsoft Corporation
 Windows 10 IoT Overview Microsoft Corporation 25 $7.2 BILLION TRILLION Connected things will by 2020 be in use by 2020 worldwide market for IoT solutions IDC: Worldwide and Regional Internet of Things
Windows 10 IoT Overview Microsoft Corporation 25 $7.2 BILLION TRILLION Connected things will by 2020 be in use by 2020 worldwide market for IoT solutions IDC: Worldwide and Regional Internet of Things
+ milestone. Milestone Systems. XProtect VMS 2017 R3. System Architecture Document
 + milestone Milestone Systems XProtect VMS 2017 R3 System Architecture Document XProtect Corporate XProtect Expert XProtect Professional+ XProtect Express+ Contents Introduction... 6 Target audience and
+ milestone Milestone Systems XProtect VMS 2017 R3 System Architecture Document XProtect Corporate XProtect Expert XProtect Professional+ XProtect Express+ Contents Introduction... 6 Target audience and
M2M Zone Conference Thursday, September 8, :30-2pm
 M2M Zone Conference Thursday, September 8, 2016 10:30-2pm 10:30 am - Opening Remarks Jared Bazzy, Director of Research, IoT M2M Council Session I: 10:40 am - 11:50 am End to End Security Is it the Holy
M2M Zone Conference Thursday, September 8, 2016 10:30-2pm 10:30 am - Opening Remarks Jared Bazzy, Director of Research, IoT M2M Council Session I: 10:40 am - 11:50 am End to End Security Is it the Holy
Code42 Defines its Critical Capabilities Methodology
 Tech Overview Product Defines its Critical Capabilities Methodology A technical analysis of top enterprise requirements from the leader in enterprise endpoint backup No enterprise technology purchase is
Tech Overview Product Defines its Critical Capabilities Methodology A technical analysis of top enterprise requirements from the leader in enterprise endpoint backup No enterprise technology purchase is
STATE OF STORAGE IN VIRTUALIZED ENVIRONMENTS INSIGHTS FROM THE MIDMARKET
 STATE OF STORAGE IN VIRTUALIZED ENVIRONMENTS INSIGHTS FROM THE MIDMARKET PAGE 1 ORGANIZATIONS THAT MAKE A GREATER COMMITMENT TO VIRTUALIZING THEIR OPERATIONS GAIN GREATER EFFICIENCIES. PAGE 2 SURVEY TOPLINE
STATE OF STORAGE IN VIRTUALIZED ENVIRONMENTS INSIGHTS FROM THE MIDMARKET PAGE 1 ORGANIZATIONS THAT MAKE A GREATER COMMITMENT TO VIRTUALIZING THEIR OPERATIONS GAIN GREATER EFFICIENCIES. PAGE 2 SURVEY TOPLINE
Service. Sentry Cyber Security Gain protection against sophisticated and persistent security threats through our layered cyber defense solution
 Service SM Sentry Cyber Security Gain protection against sophisticated and persistent security threats through our layered cyber defense solution Product Protecting sensitive data is critical to being
Service SM Sentry Cyber Security Gain protection against sophisticated and persistent security threats through our layered cyber defense solution Product Protecting sensitive data is critical to being
Discover Kaseya FAQ for KSDU
 Q: Are additional licenses needed for the Policy Manager? A: Licensing questions should be brought to your sales representative Q: Are Windows service packs supported? A: Yes. Any Manual Install Only SP's
Q: Are additional licenses needed for the Policy Manager? A: Licensing questions should be brought to your sales representative Q: Are Windows service packs supported? A: Yes. Any Manual Install Only SP's
Preserving the World s Most Important Data. Yours. SYSTEMS AT-A-GLANCE: KEY FEATURES AND BENEFITS
 Preserving the World s Most Important Data. Yours. SYSTEMS AT-A-GLANCE: KEY FEATURES AND BENEFITS We are the only company to integrate disk, tape, and replication in a single solution set for better near-term
Preserving the World s Most Important Data. Yours. SYSTEMS AT-A-GLANCE: KEY FEATURES AND BENEFITS We are the only company to integrate disk, tape, and replication in a single solution set for better near-term
The fast-track to NFV
 The fast-track to NFV Five years from now, there will only be two kinds of telco: those that have put NFV at the heart of their network architecture and business model, and those that fail. The challenge
The fast-track to NFV Five years from now, there will only be two kinds of telco: those that have put NFV at the heart of their network architecture and business model, and those that fail. The challenge
Get more out of technology starting day one. ProDeploy Enterprise Suite
 Enterprise Suite Get more out of technology starting day one 1 Secure the path to a future-ready data center The landscape faced by IT managers and business leaders today can be daunting to navigate. Continually
Enterprise Suite Get more out of technology starting day one 1 Secure the path to a future-ready data center The landscape faced by IT managers and business leaders today can be daunting to navigate. Continually
Solution Guide. 10 Non-Negotiables of IT Infrastructure Performance Management
 Solution Guide 10 Non-Negotiables of IT Infrastructure Performance Management Many IT optimization efforts fail because of management s inability to recognize the importance of an integrated infrastructure
Solution Guide 10 Non-Negotiables of IT Infrastructure Performance Management Many IT optimization efforts fail because of management s inability to recognize the importance of an integrated infrastructure
Integrated IP Video Surveillance Solution. G inex
 Integrated IP Video Surveillance Solution G150802 inex inex, highly scalable & fully integrated network video surveillance solution G4S Policy is to maintains the Highest quality standard in service &
Integrated IP Video Surveillance Solution G150802 inex inex, highly scalable & fully integrated network video surveillance solution G4S Policy is to maintains the Highest quality standard in service &
