Routing & Congestion Control
|
|
|
- Irma Whitney Harvey
- 5 years ago
- Views:
Transcription
1 WIDE AREA NETWORK Routing & Congestion Control
2 Introduction Congestion control and routing are major issues to be handled in Wide Area Networks. Congestion is handled at transport layer and routing is handled at network layer.
3 Congestion Control When one part of the subnet (e.g. one or more routers in an area) becomes overloaded, congestion results. Because routers are receiving packets faster than they can forward them, one of two things must happen: The subnet must prevent additional packets from entering the congested region until those already present can be processed. The congested routers can discard queued packets to make room for those that are arriving. 3
4 Factors that Cause Congestion Packet arrival rate exceeds the outgoing link capacity. Insufficient memory to store arriving packets Bursty traffic Slow processor 4
5 Congestion Control vs Flow Control Congestion control is a global issue involves every router and host within the subnet Flow control scope is point-to-point; involves just sender and receiver.
6 Congestion Control (cont.) Congestion Control is concerned with efficiently using a network at high load. Several techniques can be employed. These include: Warning bit Choke packets Load shedding Random early discard Traffic shaping The first 3 deal with congestion detection and recovery. The last deal with congestion avoidance.
7 Warning Bit A special bit in the packet header is set by the router to warn the source when congestion is detected. The bit is copied and piggy-backed on the ACK and sent to the sender. The sender monitors the number of ACK packets it receives with the warning bit set and adjusts its transmission rate accordingly. 7
8 Choke Packets A more direct way of telling the source to slow down. A choke packet is a control packet generated at a congested node and transmitted to restrict traffic flow. The source, on receiving the choke packet must reduce its transmission rate by a certain percentage. An example of a choke packet is the ICMP Source Quench Packet 8
9 Hop-by-Hop Choke Packets Over long distances or at high speeds choke packets are not very effective. A more efficient method is to send to choke packets hop-by-hop. This requires each hop to reduce its transmission even before the choke packet arrive at the source.
10 Load Shedding When buffers become full, routers simply discard packets. Which packet is chosen to be the victim depends on the application and on the error strategy used in the data link layer. For a file transfer, for, e.g. cannot discard older packets since this will cause a gap in the received data. For real-time voice or video it is probably better to throw away old data and keep new packets. Get the application to mark packets with discard priority. 10
11 Random Early Discard (RED) This is a proactive approach in which the router discards one or more packets before the buffer becomes completely full. Each time a packet arrives, the RED algorithm computes the average queue length, avg. If avg is lower than some lower threshold, congestion is assumed to be minimal or non-existent and the packet is queued. 11
12 RED, (Cont.) If avg is greater than some upper threshold, congestion is assumed to be serious and the packet is discarded. If avg is between the two thresholds, this might indicate the onset of congestion. The probability of congestion is then calculated. 1
13 Traffic Shaping Another method of congestion control is to shape the traffic before it enters the network. Traffic shaping controls the rate at which packets are sent (not just how many). Used in ATM and Integrated Services networks. At connection set-up time, the sender and carrier negotiate a traffic pattern (shape). 13
14 What is Routing? Moving information across the network from a source to a destination, typically through intermediate node(s). It consists of: Determining optimal routing paths Transporting information (e.g. grouped in packets, cells in packet switching)
15 Path Determination Routing protocols use routing algorithms to populate routing tables, which contain the route information such as destination/next hop association desirability of a path, and other Routers build a picture of network topology based on routing information received from other routers 1
16 Shortest Path 8 A 0 4 B C D E F 1
17 Weighted Graphs In a weighted graph, each edge has an associated numerical value, called the weight of the edge Edge weights may represent, distances, costs, etc. Example: In a flight route graph, the weight of an edge represents the distance in miles between the endpoint airports SFO ORD LGA PVD HNL LAX DFW MIA 17
18 Shortest Path Problem Given a weighted graph and two vertices u and v, we want to find a path of minimum total weight between u and v. Length of a path is the sum of the weights of its edges. Example: Shortest path between Providence and Honolulu Applications Internet packet routing Flight reservations Driving directions HNL SFO LAX ORD DFW LGA PVD MIA 18
19 Shortest Path Properties Property 1: A subpath of a shortest path is itself a shortest path Property : There is a tree of shortest paths from a start vertex to all the other vertices Example: Tree of shortest paths from Providence SFO ORD LGA PVD HNL LAX DFW MIA 1
20 Weighted Graphs In a weighted graph, each edge has an associated numerical value, called the weight of the edge Edge weights may represent, distances, costs, etc. Example: In a flight route graph, the weight of an edge represents the distance in miles between the endpoint airports SFO ORD LGA PVD HNL LAX DFW MIA 0
21 Shortest Path Problem Given a weighted graph and two vertices u and v, we want to find a path of minimum total weight between u and v. Length of a path is the sum of the weights of its edges. Example: Shortest path between Providence and Honolulu Applications Internet packet routing Flight reservations Driving directions SFO ORD LGA PVD HNL LAX DFW MIA 1
22 Shortest Path Properties Property 1: A subpath of a shortest path is itself a shortest path Property : There is a tree of shortest paths from a start vertex to all the other vertices Example: Tree of shortest paths from Providence SFO ORD LGA PVD HNL LAX DFW MIA
23 Dijkstra s Algorithm The distance of a vertex v from a vertex s is the length of a shortest path between s and v Dijkstra s algorithm computes the distances of all the vertices from a given start vertex s Assumptions: the graph is connected the edges are undirected the edge weights are nonnegative We grow a cloud of vertices, beginning with s and eventually covering all the vertices We store with each vertex v a label d(v) representing the distance of v from s in the subgraph consisting of the cloud and its adjacent vertices At each step We add to the cloud the vertex u outside the cloud with the smallest distance label, d(u) We update the labels of the vertices adjacent to u 3
24 Dijkstra's Shortest Path Algorithm Find shortest path from s to t. 3 3 s t 4
25 Dijkstra's Shortest Path Algorithm S = { } Q = { s,, 3, 4,,, 7, t } 0 s distance label 7 44 t
26 Dijkstra's Shortest Path Algorithm ExtractMin() S = { } Q = { s,, 3, 4,,, 7, t } 0 s distance label 7 44 t
27 Dijkstra's Shortest Path Algorithm decrease key S = { s } Q = {, 3, 4,,, 7, t } 0 s distance label 7 X 1 44 t 7
28 Dijkstra's Shortest Path Algorithm S = { s } Q = {, 3, 4,,, 7, t } ExtractMin() 0 s distance label 7 X 1 44 t 8
29 Dijkstra's Shortest Path Algorithm S = { s, } Q = { 3, 4,,, 7, t } 0 s X 1 44 t
30 Dijkstra's Shortest Path Algorithm S = { s, } Q = { 3, 4,,, 7, t } decrease key X 3 0 s X 1 44 t 30
31 Dijkstra's Shortest Path Algorithm S = { s, } Q = { 3, 4,,, 7, t } X 3 0 s 1 0 ExtractMin() X 1 44 t 31
32 Dijkstra's Shortest Path Algorithm S = { s,, } Q = { 3, 4,, 7, t } X 3 0 s X 1 44 t 3
33 Dijkstra's Shortest Path Algorithm S = { s,, } Q = { 3, 4,, 7, t } X 3 0 s X 1 ExtractMin() 44 t 33
34 Dijkstra's Shortest Path Algorithm S = { s,,, 7 } Q = { 3, 4,, t } X 3 0 s X X 1 44 t 34
35 Dijkstra's Shortest Path Algorithm S = { s,,, 7 } Q = { 3, 4,, t } ExtractMin X 3 0 s X X 1 44 t 3
36 Dijkstra's Shortest Path Algorithm S = { s,, 3,, 7 } Q = { 4,, t } X 3 0 s X X X t X 3
37 Dijkstra's Shortest Path Algorithm S = { s,, 3,, 7 } Q = { 4,, t } X 3 0 s X 3 X 34 ExtractMin X t X 37
38 Dijkstra's Shortest Path Algorithm S = { s,, 3,,, 7 } Q = { 4, t } X 3 0 s X X X X t X 38
39 Dijkstra's Shortest Path Algorithm S = { s,, 3,,, 7 } Q = { 4, t } X 3 0 s X X ExtractMin X X t X 3
40 Dijkstra's Shortest Path Algorithm S = { s,, 3, 4,,, 7 } Q = { t } X 3 0 s X X X X t X 40
41 Dijkstra's Shortest Path Algorithm S = { s,, 3, 4,,, 7 } Q = { t } X 3 0 s X X X 1 44 ExtractMin 0 1 X t X 41
42 Dijkstra s Algorithm A priority queue stores the vertices outside the cloud Key: distance Element: vertex Locator-based methods insert(k,e) returns a locator replacekey(l,k) changes the key of an item We store two labels with each vertex: Distance (d(v) label) locator in priority queue Algorithm DijkstraDistances(G, s) Q new heap-based priority queue for all v G.vertices() if v = s setdistance(v, 0) else setdistance(v, ) l Q.insert(getDistance(v), v) setlocator(v,l) while Q.isEmpty() u Q.removeMin() for all e G.incidentEdges(u) { relax edge e } z G.opposite(u,e) r getdistance(u) + weight(e) if r < getdistance(z) setdistance(z,r) Q.replaceKey(getLocator(z),r) 4
43 Why Dijkstra s Algorithm Works Dijkstra s algorithm is based on the greedy method. It adds vertices by increasing distance. Suppose it didn t find all shortest distances. Let F be the first wrong vertex the algorithm processed. When the previous node, D, on the true shortest path was considered, its distance was correct. But the edge (D,F) was relaxed at that time! Thus, so long as d(f)>d(d), F s distance cannot be wrong. That is, there is no wrong vertex. 0 8 A B C D 3 8 E F 3 43
44 Application Congestion and routing are two main areas of WAN which can help us to improve network performance. With congestion control, delay in packet delivery can be reduced to much extent. With optimal algorithms for routing, best possible routes can give much better network performnace and faster delivery of packets. 44
45 Scope of Research Traffic management in wireless networks Route optimization in IPv 4
46 Assignment Explain different congestion control techniques in WAN. What is routing? How an optimal routing algorithm can improve network performance? 4
Shortest Paths D E. Shortest Paths 1
 Shortest Paths A 2 7 2 B C D 2 E F Shortest Paths Outline and Reading Weighted graphs ( 7.) Shortest path problem Shortest path properties Dijkstra s algorithm ( 7..) Algorithm Edge relaxation The Bellman-Ford
Shortest Paths A 2 7 2 B C D 2 E F Shortest Paths Outline and Reading Weighted graphs ( 7.) Shortest path problem Shortest path properties Dijkstra s algorithm ( 7..) Algorithm Edge relaxation The Bellman-Ford
Graphs Weighted Graphs. Reading: 12.5, 12.6, 12.7
 Graphs Weighted Graphs Reading: 1.5, 1.6, 1. Weighted Graphs, a.k.a. Networks In a weighted graph, each edge has an associated numerical value, called the weight or cost of the edge Edge weights may represent,
Graphs Weighted Graphs Reading: 1.5, 1.6, 1. Weighted Graphs, a.k.a. Networks In a weighted graph, each edge has an associated numerical value, called the weight or cost of the edge Edge weights may represent,
Graph Algorithms shortest paths, minimum spanning trees, etc.
 Graph Algorithms shortest paths, minimum spanning trees, etc. SFO ORD LAX DFW Graphs 1 Outline and Reading Graphs ( 1.1) Definition Applications Terminology Properties ADT Data structures for graphs (
Graph Algorithms shortest paths, minimum spanning trees, etc. SFO ORD LAX DFW Graphs 1 Outline and Reading Graphs ( 1.1) Definition Applications Terminology Properties ADT Data structures for graphs (
Graph Algorithms shortest paths, minimum spanning trees, etc.
 SFO ORD LAX Graph Algorithms shortest paths, minimum spanning trees, etc. DFW Nancy Amato Parasol Lab, Dept. CSE, Texas A&M University Acknowledgement: These slides are adapted from slides provided with
SFO ORD LAX Graph Algorithms shortest paths, minimum spanning trees, etc. DFW Nancy Amato Parasol Lab, Dept. CSE, Texas A&M University Acknowledgement: These slides are adapted from slides provided with
Lecture 17: Weighted Graphs, Dijkstra s Algorithm. Courtesy of Goodrich, Tamassia and Olga Veksler
 Lecture 17: Weighted Graphs, Shortest Paths: Dijkstra s Algorithm A 4 B 7 C 1 D 3 5 3 9 5 E Courtesy of Goodrich, Tamassia and Olga Veksler Instructor: Yuzhen Xie Weighted Graphs In a weighted graph, each
Lecture 17: Weighted Graphs, Shortest Paths: Dijkstra s Algorithm A 4 B 7 C 1 D 3 5 3 9 5 E Courtesy of Goodrich, Tamassia and Olga Veksler Instructor: Yuzhen Xie Weighted Graphs In a weighted graph, each
Dijkstra s Algorithm
 Dijkstra s Algorithm 7 1 3 1 Weighted Graphs In a weighted graph, each edge has an associated numerical value, called the weight of the edge Edge weights may represent, distances, costs, etc. Example:
Dijkstra s Algorithm 7 1 3 1 Weighted Graphs In a weighted graph, each edge has an associated numerical value, called the weight of the edge Edge weights may represent, distances, costs, etc. Example:
ADVANCED COMPUTER NETWORKS
 ADVANCED COMPUTER NETWORKS Congestion Control and Avoidance 1 Lecture-6 Instructor : Mazhar Hussain CONGESTION CONTROL When one part of the subnet (e.g. one or more routers in an area) becomes overloaded,
ADVANCED COMPUTER NETWORKS Congestion Control and Avoidance 1 Lecture-6 Instructor : Mazhar Hussain CONGESTION CONTROL When one part of the subnet (e.g. one or more routers in an area) becomes overloaded,
Graphs ORD SFO LAX DFW. Data structures and Algorithms
 SFO 143 ORD 337 1743 02 Graphs LAX 1233 DFW Data structures and Algorithms Acknowledgement: These slides are adapted from slides provided with Data Structures and Algorithms in C++ Goodrich, Tamassia and
SFO 143 ORD 337 1743 02 Graphs LAX 1233 DFW Data structures and Algorithms Acknowledgement: These slides are adapted from slides provided with Data Structures and Algorithms in C++ Goodrich, Tamassia and
Weighted Graphs ( 12.5) Shortest Paths. Shortest Paths ( 12.6) Shortest Path Properties PVD ORD SFO LGA HNL LAX DFW MIA PVD PVD ORD ORD SFO SFO LGA
 Shortest Paths A Weighted Graphs (.) In a weighted graph, each edge has an associated numerical value, called the weight of the edge dge weights may represent, distances, costs, etc. xample: In a flight
Shortest Paths A Weighted Graphs (.) In a weighted graph, each edge has an associated numerical value, called the weight of the edge dge weights may represent, distances, costs, etc. xample: In a flight
CHAPTER 13 GRAPH ALGORITHMS
 CHAPTER 13 GRAPH ALGORITHMS SFO LAX ACKNOWLEDGEMENT: THESE SLIDES ARE ADAPTED FROM SLIDES PROVIDED WITH DATA STRUCTURES AND ALGORITHMS IN C++, GOODRICH, TAMASSIA AND MOUNT (WILEY 00) AND SLIDES FROM NANCY
CHAPTER 13 GRAPH ALGORITHMS SFO LAX ACKNOWLEDGEMENT: THESE SLIDES ARE ADAPTED FROM SLIDES PROVIDED WITH DATA STRUCTURES AND ALGORITHMS IN C++, GOODRICH, TAMASSIA AND MOUNT (WILEY 00) AND SLIDES FROM NANCY
Graphs ORD SFO LAX DFW. Graphs 1
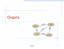 Graphs ORD 1843 SFO 802 1743 337 1233 LAX DFW Graphs 1 Outline and Reading Graphs ( 12.1) Definition Applications Terminology Properties ADT Data structures for graphs ( 12.2) Edge list structure Adjacency
Graphs ORD 1843 SFO 802 1743 337 1233 LAX DFW Graphs 1 Outline and Reading Graphs ( 12.1) Definition Applications Terminology Properties ADT Data structures for graphs ( 12.2) Edge list structure Adjacency
Prim & Kruskal Algorithm
 Prim & Kruskal Algorithm Minimum Spanning Tree Spanning subgraph Subgraph of a graph G containing all the vertices of G Spanning tree 1 10 PIT Spanning subgraph that is itself a (free) tree Minimum spanning
Prim & Kruskal Algorithm Minimum Spanning Tree Spanning subgraph Subgraph of a graph G containing all the vertices of G Spanning tree 1 10 PIT Spanning subgraph that is itself a (free) tree Minimum spanning
Minimum Spanning Trees
 Minimum Spanning Trees 04 6 33 49 PVD 1 40 146 61 14 15 0 Minimum Spanning Trees 1 Minimum Spanning Trees ( 1.) Spanning subgraph Subgraph of a graph G containing all the vertices of G Spanning tree 1
Minimum Spanning Trees 04 6 33 49 PVD 1 40 146 61 14 15 0 Minimum Spanning Trees 1 Minimum Spanning Trees ( 1.) Spanning subgraph Subgraph of a graph G containing all the vertices of G Spanning tree 1
The big picture: from Perception to Planning to Control
 The big picture: from Perception to Planning to Control Perception Location, Map Signals: video, inertial, range Sensors Real World 1 Planning vs Control 0. In control we go from to A to B in free space
The big picture: from Perception to Planning to Control Perception Location, Map Signals: video, inertial, range Sensors Real World 1 Planning vs Control 0. In control we go from to A to B in free space
CS2210 Data Structures and Algorithms
 S1 ata Structures and Algorithms Lecture 1 : Shortest Paths A 4 1 5 5 3 4 Goodrich, Tamassia Outline Weighted Graphs Shortest Paths Algorithm (ijkstra s) Weighted Graphs ach edge has an associated numerical
S1 ata Structures and Algorithms Lecture 1 : Shortest Paths A 4 1 5 5 3 4 Goodrich, Tamassia Outline Weighted Graphs Shortest Paths Algorithm (ijkstra s) Weighted Graphs ach edge has an associated numerical
Minimum Spanning Trees
 Minimum Spanning Trees 04 6 33 135 49 1 40 146 61 14 15 0 111 34 Minimum Spanning Trees 1 Minimum Spanning Trees ( 1.) Spanning subgraph Subgraph of a graph G containing all the vertices of G Spanning
Minimum Spanning Trees 04 6 33 135 49 1 40 146 61 14 15 0 111 34 Minimum Spanning Trees 1 Minimum Spanning Trees ( 1.) Spanning subgraph Subgraph of a graph G containing all the vertices of G Spanning
Minimum Spanning Trees
 Minimum Spanning Trees 04 6 33 135 49 PVD 1 40 146 61 JFK 14 15 0 111 34 Minimum Spanning Trees 1 Outline and Reading Minimum Spanning Trees Definitions A crucial fact The Prim-Jarnik Algorithm Kruskal's
Minimum Spanning Trees 04 6 33 135 49 PVD 1 40 146 61 JFK 14 15 0 111 34 Minimum Spanning Trees 1 Outline and Reading Minimum Spanning Trees Definitions A crucial fact The Prim-Jarnik Algorithm Kruskal's
Graph Algorithms Introduction to Data Structures. Ananda Gunawardena 7/31/2011 1
 Graph Algorithms 15-121 Introduction to Data Structures Ananda Gunawardena 7/31/2011 1 In this lecture.. Main idea is finding the Shortest Path between two points in a Graph We will look at Graphs with
Graph Algorithms 15-121 Introduction to Data Structures Ananda Gunawardena 7/31/2011 1 In this lecture.. Main idea is finding the Shortest Path between two points in a Graph We will look at Graphs with
Graphs ORD SFO LAX DFW Goodrich, Tamassia Graphs 1
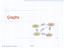 Graphs SFO 33 143 ORD 02 LAX 1233 DFW 2004 Goodrich, Tamassia Graphs 1 What is a Graph? (in computer science, it s not a data plot) General structure for representing positions with an arbitrary connectivity
Graphs SFO 33 143 ORD 02 LAX 1233 DFW 2004 Goodrich, Tamassia Graphs 1 What is a Graph? (in computer science, it s not a data plot) General structure for representing positions with an arbitrary connectivity
CHAPTER 3 EFFECTIVE ADMISSION CONTROL MECHANISM IN WIRELESS MESH NETWORKS
 28 CHAPTER 3 EFFECTIVE ADMISSION CONTROL MECHANISM IN WIRELESS MESH NETWORKS Introduction Measurement-based scheme, that constantly monitors the network, will incorporate the current network state in the
28 CHAPTER 3 EFFECTIVE ADMISSION CONTROL MECHANISM IN WIRELESS MESH NETWORKS Introduction Measurement-based scheme, that constantly monitors the network, will incorporate the current network state in the
II. Principles of Computer Communications Network and Transport Layer
 II. Principles of Computer Communications Network and Transport Layer A. Internet Protocol (IP) IPv4 Header An IP datagram consists of a header part and a text part. The header has a 20-byte fixed part
II. Principles of Computer Communications Network and Transport Layer A. Internet Protocol (IP) IPv4 Header An IP datagram consists of a header part and a text part. The header has a 20-byte fixed part
Routing in packet-switching networks
 Routing in packet-switching networks Circuit switching vs. Packet switching Most of WANs based on circuit or packet switching Circuit switching designed for voice Resources dedicated to a particular call
Routing in packet-switching networks Circuit switching vs. Packet switching Most of WANs based on circuit or packet switching Circuit switching designed for voice Resources dedicated to a particular call
CHAPTER 14 GRAPH ALGORITHMS ORD SFO LAX DFW
 SFO ORD CHAPTER 14 GRAPH ALGORITHMS LAX DFW ACKNOWLEDGEMENT: THESE SLIDES ARE ADAPTED FROM SLIDES PROVIDED WITH DATA STRUCTURES AND ALGORITHMS IN JAVA, GOODRICH, TAMASSIA AND GOLDWASSER (WILEY 2016) GRAPH
SFO ORD CHAPTER 14 GRAPH ALGORITHMS LAX DFW ACKNOWLEDGEMENT: THESE SLIDES ARE ADAPTED FROM SLIDES PROVIDED WITH DATA STRUCTURES AND ALGORITHMS IN JAVA, GOODRICH, TAMASSIA AND GOLDWASSER (WILEY 2016) GRAPH
Congestion Control in Communication Networks
 Congestion Control in Communication Networks Introduction Congestion occurs when number of packets transmitted approaches network capacity Objective of congestion control: keep number of packets below
Congestion Control in Communication Networks Introduction Congestion occurs when number of packets transmitted approaches network capacity Objective of congestion control: keep number of packets below
Chapter 24 Congestion Control and Quality of Service 24.1
 Chapter 24 Congestion Control and Quality of Service 24.1 Copyright The McGraw-Hill Companies, Inc. Permission required for reproduction or display. 24-1 DATA TRAFFIC The main focus of congestion control
Chapter 24 Congestion Control and Quality of Service 24.1 Copyright The McGraw-Hill Companies, Inc. Permission required for reproduction or display. 24-1 DATA TRAFFIC The main focus of congestion control
Course 6. Internetworking Routing 1/33
 Course 6 Internetworking Routing 1/33 Routing The main function of the network layer is routing packets from the source machine to the destination machine. Along the way, at least one intermediate node
Course 6 Internetworking Routing 1/33 Routing The main function of the network layer is routing packets from the source machine to the destination machine. Along the way, at least one intermediate node
Unit 2 Packet Switching Networks - II
 Unit 2 Packet Switching Networks - II Dijkstra Algorithm: Finding shortest path Algorithm for finding shortest paths N: set of nodes for which shortest path already found Initialization: (Start with source
Unit 2 Packet Switching Networks - II Dijkstra Algorithm: Finding shortest path Algorithm for finding shortest paths N: set of nodes for which shortest path already found Initialization: (Start with source
Chapter 5 (Week 9) The Network Layer ANDREW S. TANENBAUM COMPUTER NETWORKS FOURTH EDITION PP BLM431 Computer Networks Dr.
 Chapter 5 (Week 9) The Network Layer ANDREW S. TANENBAUM COMPUTER NETWORKS FOURTH EDITION PP. 343-396 1 5.1. NETWORK LAYER DESIGN ISSUES 5.2. ROUTING ALGORITHMS 5.3. CONGESTION CONTROL ALGORITHMS 5.4.
Chapter 5 (Week 9) The Network Layer ANDREW S. TANENBAUM COMPUTER NETWORKS FOURTH EDITION PP. 343-396 1 5.1. NETWORK LAYER DESIGN ISSUES 5.2. ROUTING ALGORITHMS 5.3. CONGESTION CONTROL ALGORITHMS 5.4.
UNIT IV -- TRANSPORT LAYER
 UNIT IV -- TRANSPORT LAYER TABLE OF CONTENTS 4.1. Transport layer. 02 4.2. Reliable delivery service. 03 4.3. Congestion control. 05 4.4. Connection establishment.. 07 4.5. Flow control 09 4.6. Transmission
UNIT IV -- TRANSPORT LAYER TABLE OF CONTENTS 4.1. Transport layer. 02 4.2. Reliable delivery service. 03 4.3. Congestion control. 05 4.4. Connection establishment.. 07 4.5. Flow control 09 4.6. Transmission
The Network Layer and Routers
 The Network Layer and Routers Daniel Zappala CS 460 Computer Networking Brigham Young University 2/18 Network Layer deliver packets from sending host to receiving host must be on every host, router in
The Network Layer and Routers Daniel Zappala CS 460 Computer Networking Brigham Young University 2/18 Network Layer deliver packets from sending host to receiving host must be on every host, router in
Jaringan Komputer. Network Layer. Network Layer. Network Layer. Network Layer Design Issues. Store-and-Forward Packet Switching
 Network Layer Jaringan Komputer Network Layer Concerned with getting packets from the source all the way to the destination May require making many hops at intermediate routers along the way Contrasts
Network Layer Jaringan Komputer Network Layer Concerned with getting packets from the source all the way to the destination May require making many hops at intermediate routers along the way Contrasts
What Is Congestion? Effects of Congestion. Interaction of Queues. Chapter 12 Congestion in Data Networks. Effect of Congestion Control
 Chapter 12 Congestion in Data Networks Effect of Congestion Control Ideal Performance Practical Performance Congestion Control Mechanisms Backpressure Choke Packet Implicit Congestion Signaling Explicit
Chapter 12 Congestion in Data Networks Effect of Congestion Control Ideal Performance Practical Performance Congestion Control Mechanisms Backpressure Choke Packet Implicit Congestion Signaling Explicit
Lecture Outline. Bag of Tricks
 Lecture Outline TELE302 Network Design Lecture 3 - Quality of Service Design 1 Jeremiah Deng Information Science / Telecommunications Programme University of Otago July 15, 2013 2 Jeremiah Deng (Information
Lecture Outline TELE302 Network Design Lecture 3 - Quality of Service Design 1 Jeremiah Deng Information Science / Telecommunications Programme University of Otago July 15, 2013 2 Jeremiah Deng (Information
MST & Shortest Path -Prim s -Djikstra s
 MST & Shortest Path -Prim s -Djikstra s PRIM s - Minimum Spanning Tree - A spanning tree of a graph is a tree that has all the vertices of the graph connected by some edges. - A graph can have one or more
MST & Shortest Path -Prim s -Djikstra s PRIM s - Minimum Spanning Tree - A spanning tree of a graph is a tree that has all the vertices of the graph connected by some edges. - A graph can have one or more
Graphs 3/25/14 15:37 SFO LAX Goodrich, Tamassia, Goldwasser Graphs 2
 Presentation for use with the textbook Data Structures and Algorithms in Java, 6 th edition, by M. T. Goodrich, R. Tamassia, and M. H. Goldwasser, Wiley, 2014 Graphs SFO 337 LAX 1843 1743 1233 802 DFW
Presentation for use with the textbook Data Structures and Algorithms in Java, 6 th edition, by M. T. Goodrich, R. Tamassia, and M. H. Goldwasser, Wiley, 2014 Graphs SFO 337 LAX 1843 1743 1233 802 DFW
The Network Layer. Network Layer Design Objectives
 1 next CITS3002 help3002 CITS3002 schedule The Network Layer The Data Link Layer had the responsibility of reliably transmitting frames across along a single wire (or wireless,...) link. The Network Layer's
1 next CITS3002 help3002 CITS3002 schedule The Network Layer The Data Link Layer had the responsibility of reliably transmitting frames across along a single wire (or wireless,...) link. The Network Layer's
Quality of Service. Traffic Descriptor Traffic Profiles. Figure 24.1 Traffic descriptors. Figure Three traffic profiles
 24-1 DATA TRAFFIC Chapter 24 Congestion Control and Quality of Service The main focus of control and quality of service is data traffic. In control we try to avoid traffic. In quality of service, we try
24-1 DATA TRAFFIC Chapter 24 Congestion Control and Quality of Service The main focus of control and quality of service is data traffic. In control we try to avoid traffic. In quality of service, we try
Autonomous robot motion path planning using shortest path planning algorithms
 IOSR Journal of Engineering (IOSRJEN) e-issn: 2250-3021, p-issn: 2278-8719 Vol. 3, Issue 1 (Jan. 2013), V1 PP 65-69 Autonomous robot motion path planning using shortest path planning algorithms T. Ravi
IOSR Journal of Engineering (IOSRJEN) e-issn: 2250-3021, p-issn: 2278-8719 Vol. 3, Issue 1 (Jan. 2013), V1 PP 65-69 Autonomous robot motion path planning using shortest path planning algorithms T. Ravi
ECE 333: Introduction to Communication Networks Fall 2001
 ECE : Introduction to Communication Networks Fall 00 Lecture : Routing and Addressing I Introduction to Routing/Addressing Lectures 9- described the main components of point-to-point networks, i.e. multiplexed
ECE : Introduction to Communication Networks Fall 00 Lecture : Routing and Addressing I Introduction to Routing/Addressing Lectures 9- described the main components of point-to-point networks, i.e. multiplexed
Computer Networks 1 (Mạng Máy Tính 1) Lectured by: Dr. Phạm Trần Vũ
 Computer Networks 1 (Mạng Máy Tính 1) Lectured by: Dr. Phạm Trần Vũ 1 Lecture 5: Network Layer (cont ) Reference: Chapter 5 - Computer Networks, Andrew S. Tanenbaum, 4th Edition, Prentice Hall, 2003. 2
Computer Networks 1 (Mạng Máy Tính 1) Lectured by: Dr. Phạm Trần Vũ 1 Lecture 5: Network Layer (cont ) Reference: Chapter 5 - Computer Networks, Andrew S. Tanenbaum, 4th Edition, Prentice Hall, 2003. 2
What Is Congestion? Computer Networks. Ideal Network Utilization. Interaction of Queues
 168 430 Computer Networks Chapter 13 Congestion in Data Networks What Is Congestion? Congestion occurs when the number of packets being transmitted through the network approaches the packet handling capacity
168 430 Computer Networks Chapter 13 Congestion in Data Networks What Is Congestion? Congestion occurs when the number of packets being transmitted through the network approaches the packet handling capacity
EEC-484/584 Computer Networks
 EEC-484/584 Computer Networks Lecture 13 wenbing@ieee.org (Lecture nodes are based on materials supplied by Dr. Louise Moser at UCSB and Prentice-Hall) Outline 2 Review of lecture 12 Routing Congestion
EEC-484/584 Computer Networks Lecture 13 wenbing@ieee.org (Lecture nodes are based on materials supplied by Dr. Louise Moser at UCSB and Prentice-Hall) Outline 2 Review of lecture 12 Routing Congestion
Chapter -6 IMPROVED CONGESTION CONTROL MECHANISM FOR REAL TIME DATA TRANSMISSION
 Chapter -6 IMPROVED CONGESTION CONTROL MECHANISM FOR REAL TIME DATA TRANSMISSION Chapter 6 IMPROVED CONGESTION CONTROL MECHANISM FOR REAL TIME DATA TRANSMISSION 6.1 Introduction Supporting Quality of Service
Chapter -6 IMPROVED CONGESTION CONTROL MECHANISM FOR REAL TIME DATA TRANSMISSION Chapter 6 IMPROVED CONGESTION CONTROL MECHANISM FOR REAL TIME DATA TRANSMISSION 6.1 Introduction Supporting Quality of Service
Congestion in Data Networks. Congestion in Data Networks
 Congestion in Data Networks CS420/520 Axel Krings 1 Congestion in Data Networks What is Congestion? Congestion occurs when the number of packets being transmitted through the network approaches the packet
Congestion in Data Networks CS420/520 Axel Krings 1 Congestion in Data Networks What is Congestion? Congestion occurs when the number of packets being transmitted through the network approaches the packet
Artificial Intelligence
 Artificial Intelligence Shortest Path Problem G. Guérard Department of Nouvelles Energies Ecole Supérieur d Ingénieurs Léonard de Vinci Lecture 3 GG A.I. 1/42 Outline 1 The Shortest Path Problem Introduction
Artificial Intelligence Shortest Path Problem G. Guérard Department of Nouvelles Energies Ecole Supérieur d Ingénieurs Léonard de Vinci Lecture 3 GG A.I. 1/42 Outline 1 The Shortest Path Problem Introduction
SHORTEST PATHS. Weighted Digraphs. Shortest paths. Shortest Paths BOS ORD JFK SFO LAX DFW MIA
 SHORTEST PATHS Weighted Digraphs Shortest paths 6 867 1 Weighted Graphs weights on the edges of a graph represent distances, costs, etc. An example of an undirected weighted graph: 6 867 2 Shortest Path
SHORTEST PATHS Weighted Digraphs Shortest paths 6 867 1 Weighted Graphs weights on the edges of a graph represent distances, costs, etc. An example of an undirected weighted graph: 6 867 2 Shortest Path
CHAPTER 9: PACKET SWITCHING N/W & CONGESTION CONTROL
 CHAPTER 9: PACKET SWITCHING N/W & CONGESTION CONTROL Dr. Bhargavi Goswami, Associate Professor head, Department of Computer Science, Garden City College Bangalore. PACKET SWITCHED NETWORKS Transfer blocks
CHAPTER 9: PACKET SWITCHING N/W & CONGESTION CONTROL Dr. Bhargavi Goswami, Associate Professor head, Department of Computer Science, Garden City College Bangalore. PACKET SWITCHED NETWORKS Transfer blocks
Fairness Example: high priority for nearby stations Optimality Efficiency overhead
 Routing Requirements: Correctness Simplicity Robustness Under localized failures and overloads Stability React too slow or too fast Fairness Example: high priority for nearby stations Optimality Efficiency
Routing Requirements: Correctness Simplicity Robustness Under localized failures and overloads Stability React too slow or too fast Fairness Example: high priority for nearby stations Optimality Efficiency
From Routing to Traffic Engineering
 1 From Routing to Traffic Engineering Robert Soulé Advanced Networking Fall 2016 2 In the beginning B Goal: pair-wise connectivity (get packets from A to B) Approach: configure static rules in routers
1 From Routing to Traffic Engineering Robert Soulé Advanced Networking Fall 2016 2 In the beginning B Goal: pair-wise connectivity (get packets from A to B) Approach: configure static rules in routers
CHAPTER 14 GRAPH ALGORITHMS ORD SFO LAX DFW
 SO OR HPTR 1 GRPH LGORITHMS LX W KNOWLGMNT: THS SLIS R PT ROM SLIS PROVI WITH T STRUTURS N LGORITHMS IN JV, GOORIH, TMSSI N GOLWSSR (WILY 16) 6 OS MINIMUM SPNNING TRS SO 16 PV OR 1 1 16 61 JK 1 1 11 WI
SO OR HPTR 1 GRPH LGORITHMS LX W KNOWLGMNT: THS SLIS R PT ROM SLIS PROVI WITH T STRUTURS N LGORITHMS IN JV, GOORIH, TMSSI N GOLWSSR (WILY 16) 6 OS MINIMUM SPNNING TRS SO 16 PV OR 1 1 16 61 JK 1 1 11 WI
CS 457 Networking and the Internet. Network Overview (cont d) 8/29/16. Circuit Switching (e.g., Phone Network) Fall 2016 Indrajit Ray
 8/9/6 CS 457 Networking and the Internet Fall 06 Indrajit Ray Network Overview (cont d) Circuit vs. Packet Switching Best Effort Internet Model Circuit Switching (e.g., Phone Network) Step : Source establishes
8/9/6 CS 457 Networking and the Internet Fall 06 Indrajit Ray Network Overview (cont d) Circuit vs. Packet Switching Best Effort Internet Model Circuit Switching (e.g., Phone Network) Step : Source establishes
Graphs ADTs and Implementations
 Graphs ADTs and Implementations SFO 337 1843 802 ORD LAX 1233 DFW - 1 - Applications of Graphs Ø Electronic circuits cslab1a cslab1b q Printed circuit board math.brown.edu q Integrated circuit Ø Transportation
Graphs ADTs and Implementations SFO 337 1843 802 ORD LAX 1233 DFW - 1 - Applications of Graphs Ø Electronic circuits cslab1a cslab1b q Printed circuit board math.brown.edu q Integrated circuit Ø Transportation
Computer Science 461 Midterm Exam March 14, :00-10:50am
 NAME: Login name: Computer Science 461 Midterm Exam March 14, 2012 10:00-10:50am This test has seven (7) questions, each worth ten points. Put your name on every page, and write out and sign the Honor
NAME: Login name: Computer Science 461 Midterm Exam March 14, 2012 10:00-10:50am This test has seven (7) questions, each worth ten points. Put your name on every page, and write out and sign the Honor
CS200: Graphs. Rosen Ch , 9.6, Walls and Mirrors Ch. 14
 CS200: Graphs Rosen Ch. 9.1-9.4, 9.6, 10.4-10.5 Walls and Mirrors Ch. 14 Trees as Graphs Tree: an undirected connected graph that has no cycles. A B C D E F G H I J K L M N O P Rooted Trees A rooted tree
CS200: Graphs Rosen Ch. 9.1-9.4, 9.6, 10.4-10.5 Walls and Mirrors Ch. 14 Trees as Graphs Tree: an undirected connected graph that has no cycles. A B C D E F G H I J K L M N O P Rooted Trees A rooted tree
ICMP, ARP, RARP, IGMP
 Internet Layer Lehrstuhl für Informatik 4 Raw division into three tasks: Data transfer over a global network Route decision at the sub-nodes Control of the network or transmission status Routing Protocols
Internet Layer Lehrstuhl für Informatik 4 Raw division into three tasks: Data transfer over a global network Route decision at the sub-nodes Control of the network or transmission status Routing Protocols
Basics (cont.) Characteristics of data communication technologies OSI-Model
 48 Basics (cont.) Characteristics of data communication technologies OSI-Model Topologies Packet switching / Circuit switching Medium Access Control (MAC) mechanisms Coding Quality of Service (QoS) 49
48 Basics (cont.) Characteristics of data communication technologies OSI-Model Topologies Packet switching / Circuit switching Medium Access Control (MAC) mechanisms Coding Quality of Service (QoS) 49
Graphs. CS16: Introduction to Data Structures & Algorithms Spring 2018
 Graphs CS16: Introduction to Data Structures & Algorithms Spring 2018 Outline What is a Graph Terminology Properties Graph Types Representations Performance BFS/DFS Applications 2 What is a Graph A graph
Graphs CS16: Introduction to Data Structures & Algorithms Spring 2018 Outline What is a Graph Terminology Properties Graph Types Representations Performance BFS/DFS Applications 2 What is a Graph A graph
Congestion. Can t sustain input rate > output rate Issues: - Avoid congestion - Control congestion - Prioritize who gets limited resources
 Congestion Source 1 Source 2 10-Mbps Ethernet 100-Mbps FDDI Router 1.5-Mbps T1 link Destination Can t sustain input rate > output rate Issues: - Avoid congestion - Control congestion - Prioritize who gets
Congestion Source 1 Source 2 10-Mbps Ethernet 100-Mbps FDDI Router 1.5-Mbps T1 link Destination Can t sustain input rate > output rate Issues: - Avoid congestion - Control congestion - Prioritize who gets
ICMP (Internet Control Message Protocol)
 ABSTRACT : ICMP stands for internet control message protocol it is a vital protocol of network layer among the seven layers of OSI(open system interconnection). Here we deal with the several situations
ABSTRACT : ICMP stands for internet control message protocol it is a vital protocol of network layer among the seven layers of OSI(open system interconnection). Here we deal with the several situations
Department of Computer Science and Engineering. COSC 4213: Computer Networks II (Fall 2005) Instructor: N. Vlajic Date: November 3, 2005
 Department of Computer Science and Engineering COSC 4213: Computer Networks II (Fall 2005) Instructor: N. Vlajic Date: November 3, 2005 Midterm Examination Instructions: Examination time: 75 min. Print
Department of Computer Science and Engineering COSC 4213: Computer Networks II (Fall 2005) Instructor: N. Vlajic Date: November 3, 2005 Midterm Examination Instructions: Examination time: 75 min. Print
VI. ROUTING. - "routing protocol" nodes exchange information to ensure consistent understanding of paths
 (a) General Concepts VI. ROUTING - "routing" determination of suitable (i.e., least cost) path from a source to every destination (i.e., which nodes/switches/routers are in path) - "routing protocol" nodes
(a) General Concepts VI. ROUTING - "routing" determination of suitable (i.e., least cost) path from a source to every destination (i.e., which nodes/switches/routers are in path) - "routing protocol" nodes
CIS 632 / EEC 687 Mobile Computing
 CIS 63 / EEC 687 Mobile Computing IP Software: Routing Prof. Chansu Yu Network Protocols for Wired Network: Ethernet Ethernet address 48-bit, also called hardware/physical/mac/layer address Globally unique:
CIS 63 / EEC 687 Mobile Computing IP Software: Routing Prof. Chansu Yu Network Protocols for Wired Network: Ethernet Ethernet address 48-bit, also called hardware/physical/mac/layer address Globally unique:
Lecture 8. Network Layer (cont d) Network Layer 1-1
 Lecture 8 Network Layer (cont d) Network Layer 1-1 Agenda The Network Layer (cont d) What is inside a router Internet Protocol (IP) IPv4 fragmentation and addressing IP Address Classes and Subnets Network
Lecture 8 Network Layer (cont d) Network Layer 1-1 Agenda The Network Layer (cont d) What is inside a router Internet Protocol (IP) IPv4 fragmentation and addressing IP Address Classes and Subnets Network
Resource allocation in networks. Resource Allocation in Networks. Resource allocation
 Resource allocation in networks Resource Allocation in Networks Very much like a resource allocation problem in operating systems How is it different? Resources and jobs are different Resources are buffers
Resource allocation in networks Resource Allocation in Networks Very much like a resource allocation problem in operating systems How is it different? Resources and jobs are different Resources are buffers
Review for Chapter 4 R1,R2,R3,R7,R10,R11,R16,R17,R19,R22,R24, R26,R30 P1,P2,P4,P7,P10,P11,P12,P14,P15,P16,P17,P22,P24,P29,P30
 Review for Chapter 4 R1,R2,R3,R7,R10,R11,R16,R17,R19,R22,R24, R26,R30 P1,P2,P4,P7,P10,P11,P12,P14,P15,P16,P17,P22,P24,P29,P30 R1. Let s review some of the terminology used in this textbook. Recall that
Review for Chapter 4 R1,R2,R3,R7,R10,R11,R16,R17,R19,R22,R24, R26,R30 P1,P2,P4,P7,P10,P11,P12,P14,P15,P16,P17,P22,P24,P29,P30 R1. Let s review some of the terminology used in this textbook. Recall that
Lecture 14: Performance Architecture
 Lecture 14: Performance Architecture Prof. Shervin Shirmohammadi SITE, University of Ottawa Prof. Shervin Shirmohammadi CEG 4185 14-1 Background Performance: levels for capacity, delay, and RMA. Performance
Lecture 14: Performance Architecture Prof. Shervin Shirmohammadi SITE, University of Ottawa Prof. Shervin Shirmohammadi CEG 4185 14-1 Background Performance: levels for capacity, delay, and RMA. Performance
Network Management & Monitoring Network Delay
 Network Management & Monitoring Network Delay These materials are licensed under the Creative Commons Attribution-Noncommercial 3.0 Unported license (http://creativecommons.org/licenses/by-nc/3.0/) End-to-end
Network Management & Monitoring Network Delay These materials are licensed under the Creative Commons Attribution-Noncommercial 3.0 Unported license (http://creativecommons.org/licenses/by-nc/3.0/) End-to-end
CSCD 433/533 Advanced Networks Spring Lecture 22 Quality of Service
 CSCD 433/533 Advanced Networks Spring 2016 Lecture 22 Quality of Service 1 Topics Quality of Service (QOS) Defined Properties Integrated Service Differentiated Service 2 Introduction Problem Overview Have
CSCD 433/533 Advanced Networks Spring 2016 Lecture 22 Quality of Service 1 Topics Quality of Service (QOS) Defined Properties Integrated Service Differentiated Service 2 Introduction Problem Overview Have
Priority Traffic CSCD 433/533. Advanced Networks Spring Lecture 21 Congestion Control and Queuing Strategies
 CSCD 433/533 Priority Traffic Advanced Networks Spring 2016 Lecture 21 Congestion Control and Queuing Strategies 1 Topics Congestion Control and Resource Allocation Flows Types of Mechanisms Evaluation
CSCD 433/533 Priority Traffic Advanced Networks Spring 2016 Lecture 21 Congestion Control and Queuing Strategies 1 Topics Congestion Control and Resource Allocation Flows Types of Mechanisms Evaluation
Homework 3 Discussion
 Homework 3 Discussion Address Resolution Protocol (ARP) Data Link Layer Network Layer Data Link Layer Network Layer Protocol Data Unit(PDU) Frames Packets Typical Device Switch/Bridge Router Range Local
Homework 3 Discussion Address Resolution Protocol (ARP) Data Link Layer Network Layer Data Link Layer Network Layer Protocol Data Unit(PDU) Frames Packets Typical Device Switch/Bridge Router Range Local
Episode 4. Flow and Congestion Control. Baochun Li Department of Electrical and Computer Engineering University of Toronto
 Episode 4. Flow and Congestion Control Baochun Li Department of Electrical and Computer Engineering University of Toronto Recall the previous episode Detailed design principles in: The link layer The network
Episode 4. Flow and Congestion Control Baochun Li Department of Electrical and Computer Engineering University of Toronto Recall the previous episode Detailed design principles in: The link layer The network
Each ICMP message contains three fields that define its purpose and provide a checksum. They are TYPE, CODE, and CHECKSUM fields.
 IP address ICMP Each ICMP message contains three fields that define its purpose and provide a checksum. They are TYPE, CODE, and CHECKSUM fields. The TYPE field identifies the ICMP message, the CODE field
IP address ICMP Each ICMP message contains three fields that define its purpose and provide a checksum. They are TYPE, CODE, and CHECKSUM fields. The TYPE field identifies the ICMP message, the CODE field
Routing Strategies. Fixed Routing. Fixed Flooding Random Adaptive
 Routing Strategies Fixed Flooding Random Adaptive Fixed Routing Single permanent route for each source to destination pair Determine routes using a least cost algorithm Route fixed, at least until a change
Routing Strategies Fixed Flooding Random Adaptive Fixed Routing Single permanent route for each source to destination pair Determine routes using a least cost algorithm Route fixed, at least until a change
CS 421: COMPUTER NETWORKS SPRING FINAL May 16, minutes
 CS 4: COMPUTER NETWORKS SPRING 03 FINAL May 6, 03 50 minutes Name: Student No: Show all your work very clearly. Partial credits will only be given if you carefully state your answer with a reasonable justification.
CS 4: COMPUTER NETWORKS SPRING 03 FINAL May 6, 03 50 minutes Name: Student No: Show all your work very clearly. Partial credits will only be given if you carefully state your answer with a reasonable justification.
EE-311 Data Communication & Networks
 National University of Computer & Emerging Sciences, Islamabad, Pakistan Name: Roll No: EE-311 Data Communication & Networks Summer 2007 Final Thursday, 2 nd August 2007 Total Time: 3 Hours Total Marks:
National University of Computer & Emerging Sciences, Islamabad, Pakistan Name: Roll No: EE-311 Data Communication & Networks Summer 2007 Final Thursday, 2 nd August 2007 Total Time: 3 Hours Total Marks:
Single Source Shortest Path
 Single Source Shortest Path A directed graph G = (V, E) and a pair of nodes s, d is given. The edges have a real-valued weight W i. This time we are looking for the weight and the shortest path from s
Single Source Shortest Path A directed graph G = (V, E) and a pair of nodes s, d is given. The edges have a real-valued weight W i. This time we are looking for the weight and the shortest path from s
CHAPTER 3 ENHANCEMENTS IN DATA LINK LAYER
 32 CHAPTER 3 ENHANCEMENTS IN DATA LINK LAYER This proposed work describes the techniques used in the data link layer to improve the performance of the TCP in wireless networks and MANETs. In the data link
32 CHAPTER 3 ENHANCEMENTS IN DATA LINK LAYER This proposed work describes the techniques used in the data link layer to improve the performance of the TCP in wireless networks and MANETs. In the data link
Supporting Service Differentiation for Real-Time and Best-Effort Traffic in Stateless Wireless Ad-Hoc Networks (SWAN)
 Supporting Service Differentiation for Real-Time and Best-Effort Traffic in Stateless Wireless Ad-Hoc Networks (SWAN) G. S. Ahn, A. T. Campbell, A. Veres, and L. H. Sun IEEE Trans. On Mobile Computing
Supporting Service Differentiation for Real-Time and Best-Effort Traffic in Stateless Wireless Ad-Hoc Networks (SWAN) G. S. Ahn, A. T. Campbell, A. Veres, and L. H. Sun IEEE Trans. On Mobile Computing
TCP/IP THE TCP/IP ARCHITECTURE
 TCP/IP-1 The Internet Protocol (IP) enables communications across a vast and heterogeneous collection of networks that are based on different technologies. Any host computer that is connected to the Internet
TCP/IP-1 The Internet Protocol (IP) enables communications across a vast and heterogeneous collection of networks that are based on different technologies. Any host computer that is connected to the Internet
Computer Networks. Routing
 Computer Networks Routing Topics Link State Routing (Continued) Hierarchical Routing Broadcast Routing Sending distinct packets Flooding Multi-destination routing Using spanning tree Reverse path forwarding
Computer Networks Routing Topics Link State Routing (Continued) Hierarchical Routing Broadcast Routing Sending distinct packets Flooding Multi-destination routing Using spanning tree Reverse path forwarding
ETSF10 Internet Protocols Transport Layer Protocols
 ETSF10 Internet Protocols Transport Layer Protocols 2012, Part 2, Lecture 2.2 Kaan Bür, Jens Andersson Transport Layer Protocols Special Topic: Quality of Service (QoS) [ed.4 ch.24.1+5-6] [ed.5 ch.30.1-2]
ETSF10 Internet Protocols Transport Layer Protocols 2012, Part 2, Lecture 2.2 Kaan Bür, Jens Andersson Transport Layer Protocols Special Topic: Quality of Service (QoS) [ed.4 ch.24.1+5-6] [ed.5 ch.30.1-2]
Tutorial 2 : Networking
 Lund University ETSN01 Advanced Telecommunication Tutorial 2 : Networking Author: Emma Fitzgerald Tutor: Farnaz Moradi November 26, 2015 Contents I Before you start 3 II Whole Class Exercise: Networking
Lund University ETSN01 Advanced Telecommunication Tutorial 2 : Networking Author: Emma Fitzgerald Tutor: Farnaz Moradi November 26, 2015 Contents I Before you start 3 II Whole Class Exercise: Networking
User Datagram Protocol
 Topics Transport Layer TCP s three-way handshake TCP s connection termination sequence TCP s TIME_WAIT state TCP and UDP buffering by the socket layer 2 Introduction UDP is a simple, unreliable datagram
Topics Transport Layer TCP s three-way handshake TCP s connection termination sequence TCP s TIME_WAIT state TCP and UDP buffering by the socket layer 2 Introduction UDP is a simple, unreliable datagram
Outline EEC-682/782 Computer Networks I. Midterm 1 Statistics. Midterm 1 Statistics. High 99, Low 34, Average 66
 Outline EEC-682/782 Computer Networks I Lecture 12 Wenbing Zhao w.zhao1@csuohio.edu http://academic.csuohio.edu/zhao_w/teaching/eec682.htm (Lecture nodes are based on materials supplied by Dr. Louise Moser
Outline EEC-682/782 Computer Networks I Lecture 12 Wenbing Zhao w.zhao1@csuohio.edu http://academic.csuohio.edu/zhao_w/teaching/eec682.htm (Lecture nodes are based on materials supplied by Dr. Louise Moser
A common issue that affects the QoS of packetized audio is jitter. Voice data requires a constant packet interarrival rate at receivers to convert
 A common issue that affects the QoS of packetized audio is jitter. Voice data requires a constant packet interarrival rate at receivers to convert data into a proper analog signal for playback. The variations
A common issue that affects the QoS of packetized audio is jitter. Voice data requires a constant packet interarrival rate at receivers to convert data into a proper analog signal for playback. The variations
ETSF05/ETSF10 Internet Protocols. Performance & QoS Congestion Control
 ETSF05/ETSF10 Internet Protocols Performance & QoS Congestion Control Quality of Service (QoS) Maintaining a functioning network Meeting applications demands User s demands = QoE (Quality of Experience)
ETSF05/ETSF10 Internet Protocols Performance & QoS Congestion Control Quality of Service (QoS) Maintaining a functioning network Meeting applications demands User s demands = QoE (Quality of Experience)
Kent State University
 CS 4/54201 Computer Communication Network Kent State University Dept. of Computer Science www.mcs.kent.edu/~javed/class-net06f/ 1 A Course on Networking and Computer Communication LECT-11, S-2 Congestion
CS 4/54201 Computer Communication Network Kent State University Dept. of Computer Science www.mcs.kent.edu/~javed/class-net06f/ 1 A Course on Networking and Computer Communication LECT-11, S-2 Congestion
Routing. Information Networks p.1/35
 Routing Routing is done by the network layer protocol to guide packets through the communication subnet to their destinations The time when routing decisions are made depends on whether we are using virtual
Routing Routing is done by the network layer protocol to guide packets through the communication subnet to their destinations The time when routing decisions are made depends on whether we are using virtual
Information Network Systems The network layer. Stephan Sigg
 Information Network Systems The network layer Stephan Sigg Tokyo, November 1, 2012 Error-detection and correction Decoding of Reed-Muller codes Assume a second order (16, 11) code for m = 4. The r-th order
Information Network Systems The network layer Stephan Sigg Tokyo, November 1, 2012 Error-detection and correction Decoding of Reed-Muller codes Assume a second order (16, 11) code for m = 4. The r-th order
PRACTICE QUESTIONS ON RESOURCE ALLOCATION
 PRACTICE QUESTIONS ON RESOURCE ALLOCATION QUESTION : Internet Versus Station Wagon A famous maxim, sometimes attributed to Dennis Ritchie, says Never underestimate the bandwidth of a station wagon full
PRACTICE QUESTIONS ON RESOURCE ALLOCATION QUESTION : Internet Versus Station Wagon A famous maxim, sometimes attributed to Dennis Ritchie, says Never underestimate the bandwidth of a station wagon full
CEN445 Network Protocols & Algorithms. Network Layer. Prepared by Dr. Mohammed Amer Arafah Summer 2008
 CEN445 Network Protocols & Algorithms Network Layer Prepared by Dr. Mohammed Amer Arafah Summer 2008 1 Congestion Control Algorithms General Principles of Congestion Control Congestion Prevention Policies
CEN445 Network Protocols & Algorithms Network Layer Prepared by Dr. Mohammed Amer Arafah Summer 2008 1 Congestion Control Algorithms General Principles of Congestion Control Congestion Prevention Policies
Quality of Service II
 Quality of Service II Patrick J. Stockreisser p.j.stockreisser@cs.cardiff.ac.uk Lecture Outline Common QoS Approaches Best Effort Integrated Services Differentiated Services Integrated Services Integrated
Quality of Service II Patrick J. Stockreisser p.j.stockreisser@cs.cardiff.ac.uk Lecture Outline Common QoS Approaches Best Effort Integrated Services Differentiated Services Integrated Services Integrated
Toward a Reliable Data Transport Architecture for Optical Burst-Switched Networks
 Toward a Reliable Data Transport Architecture for Optical Burst-Switched Networks Dr. Vinod Vokkarane Assistant Professor, Computer and Information Science Co-Director, Advanced Computer Networks Lab University
Toward a Reliable Data Transport Architecture for Optical Burst-Switched Networks Dr. Vinod Vokkarane Assistant Professor, Computer and Information Science Co-Director, Advanced Computer Networks Lab University
CS519: Computer Networks. Lecture 5, Part 4: Mar 29, 2004 Transport: TCP congestion control
 : Computer Networks Lecture 5, Part 4: Mar 29, 2004 Transport: TCP congestion control TCP performance We ve seen how TCP the protocol works Sequencing, receive window, connection setup and teardown And
: Computer Networks Lecture 5, Part 4: Mar 29, 2004 Transport: TCP congestion control TCP performance We ve seen how TCP the protocol works Sequencing, receive window, connection setup and teardown And
Mobile Transport Layer
 Mobile Transport Layer 1 Transport Layer HTTP (used by web services) typically uses TCP Reliable transport between TCP client and server required - Stream oriented, not transaction oriented - Network friendly:
Mobile Transport Layer 1 Transport Layer HTTP (used by web services) typically uses TCP Reliable transport between TCP client and server required - Stream oriented, not transaction oriented - Network friendly:
Vorlesung Kommunikationsnetze
 Picture 15 13 Vorlesung Kommunikationsnetze Prof. Dr. H. P. Großmann mit B. Wiegel sowie A. Schmeiser und M. Rabel Sommersemester 2009 Institut für Organisation und Management von Informationssystemen
Picture 15 13 Vorlesung Kommunikationsnetze Prof. Dr. H. P. Großmann mit B. Wiegel sowie A. Schmeiser und M. Rabel Sommersemester 2009 Institut für Organisation und Management von Informationssystemen
Department of Computer Science and Engineering. Final Examination. Instructor: N. Vlajic Date: April 15, 2011
 Department of Computer Science and Engineering CSE 3214: Computer Network Protocols and Applications Final Examination Instructor: N. Vlajic Date: April 15, 2011 Instructions: Examination time: 180 min.
Department of Computer Science and Engineering CSE 3214: Computer Network Protocols and Applications Final Examination Instructor: N. Vlajic Date: April 15, 2011 Instructions: Examination time: 180 min.
Contents. Configuring GRE 1
 Contents Configuring GRE 1 Overview 1 GRE encapsulation format 1 GRE tunnel operating principle 1 GRE security mechanisms 2 GRE application scenarios 2 Protocols and standards 4 Configuring a GRE/IPv4
Contents Configuring GRE 1 Overview 1 GRE encapsulation format 1 GRE tunnel operating principle 1 GRE security mechanisms 2 GRE application scenarios 2 Protocols and standards 4 Configuring a GRE/IPv4
Chapter 13 TRANSPORT. Mobile Computing Winter 2005 / Overview. TCP Overview. TCP slow-start. Motivation Simple analysis Various TCP mechanisms
 Overview Chapter 13 TRANSPORT Motivation Simple analysis Various TCP mechanisms Distributed Computing Group Mobile Computing Winter 2005 / 2006 Distributed Computing Group MOBILE COMPUTING R. Wattenhofer
Overview Chapter 13 TRANSPORT Motivation Simple analysis Various TCP mechanisms Distributed Computing Group Mobile Computing Winter 2005 / 2006 Distributed Computing Group MOBILE COMPUTING R. Wattenhofer
ETSF05/ETSF10 Internet Protocols. Routing on the Internet
 ETSF05/ETSF10 Internet Protocols Routing on the Internet Circuit switched routing ETSF05/ETSF10 - Internet Protocols 2 Routing in Packet Switching Networks Key design issue for (packet) switched networks
ETSF05/ETSF10 Internet Protocols Routing on the Internet Circuit switched routing ETSF05/ETSF10 - Internet Protocols 2 Routing in Packet Switching Networks Key design issue for (packet) switched networks
