6% Writes. 4% Writes. 2% Writes. D e g r e e o f R e p l i c a t i o n
|
|
|
- Andra Ryan
- 5 years ago
- Views:
Transcription
1 Power-Aware Replication of Data Structures in Distributed Embedded Real-Time Systems? Osman S. Unsal, Israel Koren, C. Mani Krishna Department of Electrical and Computer Engineering University of Massachusetts, Amherst, MA Abstract. In this paper, we study the problem of positioning copies of shared data structures to reduce power consumption in real-time systems. Power-constrained real-time systems are of increasing importance in defense, space, and consumer applications. We describe our energy consumption model and present numerical results linking the placement of data structures to energy consumption. 1 System Model This paper explores the power ramifications of various task assignment heuristics as well as network topology/routing issues. We study distributed real-time systems, with each node having a private memory and each task having a worstcase execution time and deadline. If two tasks reside on different processors then the communication power cost depends on the routing algorithm and topology. The objective is to study the impact of a particular assignment-topology-routing combination on power consumption. To save energy, part of a remote task's data structure may be replicated closer to the consuming node(s). The aim is to find the ideal degree of replication. Increasing the replication increases local memory size and its energy consumption, while decreasing the volume of network transfers and the associated power consumption. Therefore a sweet spot" may exist, beyond which increasing the degree of replication increases the energy consumption. More formally, the total energy consumed, denoted by E, is: E = X n tasks i=1 E i where (1) E i = N writei e write + N readi e read + X n tasks ( j=1 N netij ) e net + Size memi e static (2)? This work is supported in part by DARPA through contract No. F The views and conclusions contained in this document are those of the authors and should not be interpreted as necessarily representing the official policies or endorsements, either expressed or implied, of the Defense Advanced Research Projects Agency, the Air Force or the U.S. Government.
2 Here, E i is the energy consumed in executing the i-th task, e write and e read are the memory energy consumption per write and read access, e static is the memory static energy consumption, e net is the energy cost of a per-hop data transfer per-bit, N writei and N readi are the number of local memory write and read accesses of task i respectively and N netij is the number of remote accesses from task i to task j. If the two tasks i and j are assigned to the same node then, N netij =0. Memory consistency is preserved by updating all the replicated copies of a data item when a task writes a shared data item to its private memory. For typical programs the writes are at most 15 percent of reads. This characteristic facilitates the usefulness of replication. All links are assumed to be of the same type, i.e., the link power consumption to transfer one byte is the same for all links. Various routing strategies such as broadcasting or flooding are also implemented in the model. As for the case of multicasting, efficient multicasting algorithms rely on building and trimming a minimum spanning tree [3]. However, this is not optimal from a power point of view since it builds a minimum spanning tree for all the nodes instead of the subset of nodes in the multicast group. To obtain a better solution, we have developed an energy-saving Steiner tree heuristic for systems with multiple multicasting requirements. Given a weighted graph G, the Steiner tree problem is to find a tree that spans a specified subset of nodes of G with minimal total distance on its edges. Various distinct trees that span the same subset of nodes of G can be constructed and one can select the tree that has less total edge cost than that of the other trees in the set. Since the problem is NP-complete, heuristics are needed. We have adapted such a heuristic [5] for our purposes. The heuristic finds a solution with total distance no more than 2(1 1=k) times that of the optimal tree in time O(pn 2 ). Here, n is the number of nodes in G, p the number of Steiner points and k the number of leaves in the optimal Steiner tree. A short description of the Steiner heuristic algorithm is given in Figure 1. For intertask-communication-bound real-time systems, the allocation of tasks to nodes can also have a significant impact on power. We use a steepest-descent heuristic[2] for power-aware task allocation. The heuristic starts from an initial allocation and then reallocates that pair of tasks to the same node which results in the largest decrease in the energy consumption from among the set of candidate task pairs. This reallocation is done iteratively until the energy saving is below a given threshold. Thus, the heuristic tends to assign tasks which communicate heavily to the same node. 2 Numerical Results For the results in this section, unless otherwise noted, the number of tasks is 10 and the task execution times, periods as well as intertask communication sizes are random. The number of nodes is 4, the write-to-read power ratio is 1.22, 8% of the memory operations are writes and 92% are reads, and per-hop remote
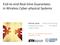
3 Step 1. For every multicast group repeat steps 2 through 6. Step 2. Construct the complete graph H from G and S in such away that the set of nodes in H is equal to S; for every edge (u; v) inh, the distance of (u; v) is set equal to the shortest path between u and v in G. Step 3. Find a minimum spanning tree T H of H. Step 4. Replace each edge (u; v) int H by the shortest path between u and v in G; the resulting graph R is a subgraph of G. Step 5. Find a minimum spanning tree T R of R. Step 6. Delete edges in T R, if necessary, so that all the leaves in T R are elements of S. The resulting tree is returned as the solution. Fig. 1. The Steiner heuristic algorithm access energy cost is three times that of a local access energy cost. 2.1 Effect of Application Write Ratios We begin by considering a situation in which each nodekeeps a fraction of the global data structures in its private memory. Figure 2 illustrates the effect of changing write ratios on power. As can be seen from the figure the optimum energy point shifts towards lower replication as the write percentage gets higher. Another observation is that as the degree of replication gets higher the energy consumption increases sharply for higher write ratios. This stems from the memory consistency constraint and is caused by the need to update all the replicated copies of a data item that has been modified by the local task. 2.2 Impact of Per-hop Transfer Cost The per-link power cost per bit transferred depends on the interconnection hardware used. For example, a wireless link may consume less power than a twistedpair link. If the real-time system designer has multiple options for choosing interconnection hardware, he/she can find the optimum degree of memory replication for each option. Figure 3 illustrates this. Here the per-hop energy consumption varies from being equal to memory energy consumption per operation to four times that of the memory energy consumption per operation. We observe that the optimum energy point shifts toward higher degrees of replication as the perlink power consumption is increased. Also, the system energy consumption starts converging at higher degrees of replication. This phenomenon is due to the fact
4 that most of the data is locally replicated, thus decreasing the sensitivity of total energy consumption to the per-link power cost Total System Energy % Writes 8% Writes 6% Writes 4% Writes 2% Writes Net Power=4* Loc Power Net Power=3* Loc Power Net Power=2* Loc Power Net Power=Loc Power Fig. 2. Effect of write ratios on energy Fig. 3. Effect of per-link power on energy 2.3 Task Allocation and Network Topology Figure 4 shows the energy consumption impact of the task allocation scheme by comparing the previously mentioned power-aware optimization heuristic with a simple, power-blind round-robin scheme. The resulting saving in energy consumption emphasizes the importance of the task allocation step. Network topology and routing are also important design considerations in realtime design. Figure 5 shows the energy comparisons of two different choices, a 16-node mesh topology and a 16-node torus topology. The extra wraparound edges of the torus result in lower energy consumption, but the energy difference between the two topologies is not very large. 2.4 Routing Issues Multicasting has received little attention in real-time systems but is an important problem: sensors providing data to multiple processes and process outputs driving redundant actuators can all benefit from efficient multicasting algorithms. For the baseline case, we implemented the minimal spanning tree truncation scheme [3]. As mentioned in the previous section, we have developed a better multicasting scheme which makes use of a Steiner tree heuristic to find a path with the minimum cost among the multicasting nodes. Figure 6 shows the energy comparison of the two approaches. Here the number of nodes is 16 and the number of tasks is 40.
5 Total System Energy Round-Robin Optimized Fig. 4. Impact of task allocation strategy Total System Energy Node Mesh 16-Node Torus Fig. 5. Topology choice and energy The routing capabilities of a Real-Time Operating System (RTOS) determines the power impact of multicasting tasks. A minimalist micro-kernel RTOS might just supply a simple flooding model. In this model the multicast message is sent to all the nodes in the system. A slightly more sophisticated RTOS would do a broadcast by sending a unique message to each of the multicast nodes. Broadcasting is considered to be more efficient than flooding [4]. However, as seen in Figure 7, flooding surprisingly does better than broadcasting from an energy point of view. This is because only a single copy of the multicast message is sent in flooding.
6 Energy Ratio Fig. 6. Energy Ratio of Steiner / Minimal Spanning Tree Truncation Total System Power Broadcasting Flooding Fig. 7. Flooding versus Broadcasting 2.5 Selective Replication Up to this point, we have considered the task-to-task communication data structures to be fully replicated. This means that for a multicast group, the data
7 structure of the multicast source task is replicated at all multicast destination tasks. We now relax this requirement and selectively replicate the data structure of the source task only at some of the destination tasks, thus saving energy. Consider the example of Figure 8. This is a 16-node mesh and part of the task assignment is shown in the figure. Our focus is multicasting group A with task A:1 being the source and the other tasks in group A being the destinations. We selectively replicate task A:1's data structure only at task A:4's node. The result is compared against full replication and no replication in Figure 9. Here, the energy is plotted against the per-hop energy cost and it is normalized with respect to the energy consumption of no replication. As can be seen, selective replication results in significant energy savings. Task Task Task Task A.1 B.1 A.2 B.2 Task Task Task Task C.1 C.2 B.3 C.3 Task Task Task Task B.4 C.4 D.1 D.2 Task D.3 Task Task Task A.3 A.4 A.5 Fig. 8. Example for selective replication 3 Conclusion We have constructed a model to gauge the power impact of task assignment, network topology and routing strategies within the context of data structure replication to decrease energy. Our results show that substantial energy savings are possible by careful design. Our model also gives us the ability to calculate the energy impact of new power aware heuristics. We have adapted a Steiner tree heuristic for multicasting and compared its energy consumption with the baseline case of minimal spanning tree truncation. Currently,we are studying the more general case of heterogeneous data consumption rates at the destination tasks. We are also developing a heuristic which will
8 Normalized Energy of Replication Total Replication Selective Replication Per-Hop Power Cost (As a multiple of memory cost) Fig. 9. Advantage of selective replication optimize the memory replication needs of each task. References 1. Coumeri, S. L., and Thomas, D. E., Memory Modeling for System Synthesis, thomas/research/list.html 2. Press, W. H., Flannery, B. P., Teukolsky, S. A., Vetterling, W. T., Numerical Recipes, Cambridge University Press, Deering, S. E., and Cheriton, D.R., Multicast Routing in Datagram Internetworks and Extended LANs, ACM Trans. on Computer Systems May Tanenbaum, A. S., Computer Networks, Third Edition, Prentice Hall, Lau, H. T., Combinatorial Heuristic Algorithms with FORTRAN, Springer-Verlag, 1986 This article was processed using the LATEX macro package with LLNCS style
Cooperative Data Dissemination to Mission Sites
 Cooperative Data Dissemination to Mission Sites Fangfei Chen a, Matthew P. Johnson b, Amotz Bar-Noy b and Thomas F. La Porta a a Department of Computer Science and Engineering, the Pennsylvania State University
Cooperative Data Dissemination to Mission Sites Fangfei Chen a, Matthew P. Johnson b, Amotz Bar-Noy b and Thomas F. La Porta a a Department of Computer Science and Engineering, the Pennsylvania State University
Measuring the Vulnerability of Interconnection. Networks in Embedded Systems. University of Massachusetts, Amherst, MA 01003
 Measuring the Vulnerability o Interconnection Networks in Embedded Systems V. Lakamraju, Z. Koren, I. Koren, and C. M. Krishna Department o Electrical and Computer Engineering University o Massachusetts,
Measuring the Vulnerability o Interconnection Networks in Embedded Systems V. Lakamraju, Z. Koren, I. Koren, and C. M. Krishna Department o Electrical and Computer Engineering University o Massachusetts,
Computer Networks 1 (Mạng Máy Tính 1) Lectured by: Dr. Phạm Trần Vũ
 Computer Networks 1 (Mạng Máy Tính 1) Lectured by: Dr. Phạm Trần Vũ Lecture 5: Network Layer Reference: Chapter 5 - Computer Networks, Andrew S. Tanenbaum, 4th Edition, Prentice Hall, 2003. Contents The
Computer Networks 1 (Mạng Máy Tính 1) Lectured by: Dr. Phạm Trần Vũ Lecture 5: Network Layer Reference: Chapter 5 - Computer Networks, Andrew S. Tanenbaum, 4th Edition, Prentice Hall, 2003. Contents The
Multicast Communications. Tarik Čičić, 4. March. 2016
 Multicast Communications Tarik Čičić, 4. March. 06 Overview One-to-many communication, why and how Algorithmic approach: Steiner trees Practical algorithms Multicast tree types Basic concepts in multicast
Multicast Communications Tarik Čičić, 4. March. 06 Overview One-to-many communication, why and how Algorithmic approach: Steiner trees Practical algorithms Multicast tree types Basic concepts in multicast
Backup segments. Path after failure recovery. Fault. Primary channel. Initial path D1 D2. Primary channel 1. Backup channel 1.
 A Segmented Backup Scheme for Dependable Real Time Communication in Multihop Networks Gummadi P. Krishna M. Jnana Pradeep and C. Siva Ram Murthy Department of Computer Science and Engineering Indian Institute
A Segmented Backup Scheme for Dependable Real Time Communication in Multihop Networks Gummadi P. Krishna M. Jnana Pradeep and C. Siva Ram Murthy Department of Computer Science and Engineering Indian Institute
Lecture 7. Reminder: Homework 2, Programming Project 1 due today. Homework 3, Programming Project 2 out, due Thursday next week. Questions?
 Lecture 7 Reminder: Homework 2, Programming Project 1 due today. Homework 3, Programming Project 2 out, due Thursday next week. Questions? Thursday, September 15 CS 475 Networks - Lecture 7 1 Outline Chapter
Lecture 7 Reminder: Homework 2, Programming Project 1 due today. Homework 3, Programming Project 2 out, due Thursday next week. Questions? Thursday, September 15 CS 475 Networks - Lecture 7 1 Outline Chapter
Communication Networks I December 4, 2001 Agenda Graph theory notation Trees Shortest path algorithms Distributed, asynchronous algorithms Page 1
 Communication Networks I December, Agenda Graph theory notation Trees Shortest path algorithms Distributed, asynchronous algorithms Page Communication Networks I December, Notation G = (V,E) denotes a
Communication Networks I December, Agenda Graph theory notation Trees Shortest path algorithms Distributed, asynchronous algorithms Page Communication Networks I December, Notation G = (V,E) denotes a
Data Caching under Number Constraint
 1 Data Caching under Number Constraint Himanshu Gupta and Bin Tang Abstract Caching can significantly improve the efficiency of information access in networks by reducing the access latency and bandwidth
1 Data Caching under Number Constraint Himanshu Gupta and Bin Tang Abstract Caching can significantly improve the efficiency of information access in networks by reducing the access latency and bandwidth
Multicast routing Draft
 Multicast routing Draft Lucia Tudose Nokia Research Center E-mail: tudose@research.nokia.com Abstract Multicast routing is establishing a tree which is routed from the source node and contains all the
Multicast routing Draft Lucia Tudose Nokia Research Center E-mail: tudose@research.nokia.com Abstract Multicast routing is establishing a tree which is routed from the source node and contains all the
CONSTRUCTION AND EVALUATION OF MESHES BASED ON SHORTEST PATH TREE VS. STEINER TREE FOR MULTICAST ROUTING IN MOBILE AD HOC NETWORKS
 CONSTRUCTION AND EVALUATION OF MESHES BASED ON SHORTEST PATH TREE VS. STEINER TREE FOR MULTICAST ROUTING IN MOBILE AD HOC NETWORKS 1 JAMES SIMS, 2 NATARAJAN MEGHANATHAN 1 Undergrad Student, Department
CONSTRUCTION AND EVALUATION OF MESHES BASED ON SHORTEST PATH TREE VS. STEINER TREE FOR MULTICAST ROUTING IN MOBILE AD HOC NETWORKS 1 JAMES SIMS, 2 NATARAJAN MEGHANATHAN 1 Undergrad Student, Department
Optimal Energy-Efficient Routing for Wireless Sensor Networks
 Optimal Energy-Efficient Routing for Wireless Sensor Networks Chih-Wei Shiou, Frank Yeong-Sung Lin, Hsu-Chen Cheng, and Department of Information Management, National Taiwan University yslin; edu. Wen
Optimal Energy-Efficient Routing for Wireless Sensor Networks Chih-Wei Shiou, Frank Yeong-Sung Lin, Hsu-Chen Cheng, and Department of Information Management, National Taiwan University yslin; edu. Wen
ROUTING ALGORITHMS Part 1: Data centric and hierarchical protocols
 ROUTING ALGORITHMS Part 1: Data centric and hierarchical protocols 1 Why can t we use conventional routing algorithms here?? A sensor node does not have an identity (address) Content based and data centric
ROUTING ALGORITHMS Part 1: Data centric and hierarchical protocols 1 Why can t we use conventional routing algorithms here?? A sensor node does not have an identity (address) Content based and data centric
A Localized Algorithm for Reducing the Size of Dominating Set in Mobile Ad Hoc Networks
 A Localized Algorithm for Reducing the Size of Dominating Set in Mobile Ad Hoc Networks Yamin Li and Shietung Peng Department of Computer Science Hosei University Tokyo 18-858 Japan {yamin, speng}@k.hosei.ac.jp
A Localized Algorithm for Reducing the Size of Dominating Set in Mobile Ad Hoc Networks Yamin Li and Shietung Peng Department of Computer Science Hosei University Tokyo 18-858 Japan {yamin, speng}@k.hosei.ac.jp
The Memetic Algorithm for The Minimum Spanning Tree Problem with Degree and Delay Constraints
 The Memetic Algorithm for The Minimum Spanning Tree Problem with Degree and Delay Constraints Minying Sun*,Hua Wang* *Department of Computer Science and Technology, Shandong University, China Abstract
The Memetic Algorithm for The Minimum Spanning Tree Problem with Degree and Delay Constraints Minying Sun*,Hua Wang* *Department of Computer Science and Technology, Shandong University, China Abstract
3. Evaluation of Selected Tree and Mesh based Routing Protocols
 33 3. Evaluation of Selected Tree and Mesh based Routing Protocols 3.1 Introduction Construction of best possible multicast trees and maintaining the group connections in sequence is challenging even in
33 3. Evaluation of Selected Tree and Mesh based Routing Protocols 3.1 Introduction Construction of best possible multicast trees and maintaining the group connections in sequence is challenging even in
EEC-484/584 Computer Networks
 EEC-484/584 Computer Networks Lecture 2 Wenbing Zhao wenbing@ieee.org (Lecture nodes are based on materials supplied by Dr. Louise Moser at UCSB and Prentice-Hall) Misc. Interested in research? Secure
EEC-484/584 Computer Networks Lecture 2 Wenbing Zhao wenbing@ieee.org (Lecture nodes are based on materials supplied by Dr. Louise Moser at UCSB and Prentice-Hall) Misc. Interested in research? Secure
Ad hoc and Sensor Networks Topology control
 Ad hoc and Sensor Networks Topology control Goals of this chapter Networks can be too dense too many nodes in close (radio) vicinity This chapter looks at methods to deal with such networks by Reducing/controlling
Ad hoc and Sensor Networks Topology control Goals of this chapter Networks can be too dense too many nodes in close (radio) vicinity This chapter looks at methods to deal with such networks by Reducing/controlling
CHAPTER 2 WIRELESS SENSOR NETWORKS AND NEED OF TOPOLOGY CONTROL
 WIRELESS SENSOR NETWORKS AND NEED OF TOPOLOGY CONTROL 2.1 Topology Control in Wireless Sensor Networks Network topology control is about management of network topology to support network-wide requirement.
WIRELESS SENSOR NETWORKS AND NEED OF TOPOLOGY CONTROL 2.1 Topology Control in Wireless Sensor Networks Network topology control is about management of network topology to support network-wide requirement.
CompSci 356: Computer Network Architectures. Lecture 7: Switching technologies Chapter 3.1. Xiaowei Yang
 CompSci 356: Computer Network Architectures Lecture 7: Switching technologies Chapter 3.1 Xiaowei Yang xwy@cs.duke.edu Types of switching Datagram Virtual circuit Source routing Today Bridges and LAN switches
CompSci 356: Computer Network Architectures Lecture 7: Switching technologies Chapter 3.1 Xiaowei Yang xwy@cs.duke.edu Types of switching Datagram Virtual circuit Source routing Today Bridges and LAN switches
Efficient Broadcast Algorithms To Reduce number of transmission Based on Probability Scheme
 Efficient Broadcast s To Reduce number of transmission Based on Probability Scheme S.Tharani, R.Santhosh Abstract Two main approaches to broadcast packets in wireless ad hoc networks are static and dynamic.
Efficient Broadcast s To Reduce number of transmission Based on Probability Scheme S.Tharani, R.Santhosh Abstract Two main approaches to broadcast packets in wireless ad hoc networks are static and dynamic.
Approximating Fault-Tolerant Steiner Subgraphs in Heterogeneous Wireless Networks
 Approximating Fault-Tolerant Steiner Subgraphs in Heterogeneous Wireless Networks Ambreen Shahnaz and Thomas Erlebach Department of Computer Science University of Leicester University Road, Leicester LE1
Approximating Fault-Tolerant Steiner Subgraphs in Heterogeneous Wireless Networks Ambreen Shahnaz and Thomas Erlebach Department of Computer Science University of Leicester University Road, Leicester LE1
Analysis and Algorithms for Partial Protection in Mesh Networks
 Analysis and Algorithms for Partial Protection in Mesh Networks Greg uperman MIT LIDS Cambridge, MA 02139 gregk@mit.edu Eytan Modiano MIT LIDS Cambridge, MA 02139 modiano@mit.edu Aradhana Narula-Tam MIT
Analysis and Algorithms for Partial Protection in Mesh Networks Greg uperman MIT LIDS Cambridge, MA 02139 gregk@mit.edu Eytan Modiano MIT LIDS Cambridge, MA 02139 modiano@mit.edu Aradhana Narula-Tam MIT
A Cluster-Based Energy Balancing Scheme in Heterogeneous Wireless Sensor Networks
 A Cluster-Based Energy Balancing Scheme in Heterogeneous Wireless Sensor Networks Jing Ai, Damla Turgut, and Ladislau Bölöni Networking and Mobile Computing Research Laboratory (NetMoC) Department of Electrical
A Cluster-Based Energy Balancing Scheme in Heterogeneous Wireless Sensor Networks Jing Ai, Damla Turgut, and Ladislau Bölöni Networking and Mobile Computing Research Laboratory (NetMoC) Department of Electrical
Topological Synthesis of Mobile Backbone Networks for Managing Ad Hoc Wireless Networks 1
 Topological Synthesis of Mobile Backbone Networks for Managing Ad Hoc Wireless Networks 1 Izhak Rubin and Patrick Vincent Electrical Engineering Department, University of California (UCLA) Los Angeles,
Topological Synthesis of Mobile Backbone Networks for Managing Ad Hoc Wireless Networks 1 Izhak Rubin and Patrick Vincent Electrical Engineering Department, University of California (UCLA) Los Angeles,
ECE 4450:427/527 - Computer Networks Spring 2017
 ECE 4450:427/527 - Computer Networks Spring 2017 Dr. Nghi Tran Department of Electrical & Computer Engineering Lecture 6.1: Internetworking Dr. Nghi Tran (ECE-University of Akron) ECE 4450:427/527 Computer
ECE 4450:427/527 - Computer Networks Spring 2017 Dr. Nghi Tran Department of Electrical & Computer Engineering Lecture 6.1: Internetworking Dr. Nghi Tran (ECE-University of Akron) ECE 4450:427/527 Computer
Course Routing Classification Properties Routing Protocols 1/39
 Course 8 3. Routing Classification Properties Routing Protocols 1/39 Routing Algorithms Types Static versus dynamic Single-path versus multipath Flat versus hierarchical Host-intelligent versus router-intelligent
Course 8 3. Routing Classification Properties Routing Protocols 1/39 Routing Algorithms Types Static versus dynamic Single-path versus multipath Flat versus hierarchical Host-intelligent versus router-intelligent
Internetworking Part 1
 CMPE 344 Computer Networks Spring 2012 Internetworking Part 1 Reading: Peterson and Davie, 3.1 22/03/2012 1 Not all networks are directly connected Limit to how many hosts can be attached Point-to-point:
CMPE 344 Computer Networks Spring 2012 Internetworking Part 1 Reading: Peterson and Davie, 3.1 22/03/2012 1 Not all networks are directly connected Limit to how many hosts can be attached Point-to-point:
Chapter 5. The Network Layer FATİH ŞAHİN Network Layer Design Isues. Store-and-Forward Packet Switching
 Chapter 5 The Network Layer FATİH ŞAHİN 2007513806 Network Layer Design Isues Store-and-Forward Packet Switching Services Provided to the Transport Layer Implementation of Connectionless Service Implementation
Chapter 5 The Network Layer FATİH ŞAHİN 2007513806 Network Layer Design Isues Store-and-Forward Packet Switching Services Provided to the Transport Layer Implementation of Connectionless Service Implementation
Computer Networks 1 (Mạng Máy Tính 1) Lectured by: Dr. Phạm Trần Vũ
 Computer Networks 1 (Mạng Máy Tính 1) Lectured by: Dr. Phạm Trần Vũ 1 Lecture 5: Network Layer (cont ) Reference: Chapter 5 - Computer Networks, Andrew S. Tanenbaum, 4th Edition, Prentice Hall, 2003. 2
Computer Networks 1 (Mạng Máy Tính 1) Lectured by: Dr. Phạm Trần Vũ 1 Lecture 5: Network Layer (cont ) Reference: Chapter 5 - Computer Networks, Andrew S. Tanenbaum, 4th Edition, Prentice Hall, 2003. 2
A Distributed Optimization Algorithm for Multi-hop Cognitive Radio Networks
 A Distributed Optimization Algorithm for Multi-hop Cognitive Radio Networks Yi Shi Y. Thomas Hou The Bradley Department of Electrical and Computer Engineering, Virginia Tech, Blacksburg, VA Abstract Cognitive
A Distributed Optimization Algorithm for Multi-hop Cognitive Radio Networks Yi Shi Y. Thomas Hou The Bradley Department of Electrical and Computer Engineering, Virginia Tech, Blacksburg, VA Abstract Cognitive
European Network on New Sensing Technologies for Air Pollution Control and Environmental Sustainability - EuNetAir COST Action TD1105
 European Network on New Sensing Technologies for Air Pollution Control and Environmental Sustainability - EuNetAir COST Action TD1105 A Holistic Approach in the Development and Deployment of WSN-based
European Network on New Sensing Technologies for Air Pollution Control and Environmental Sustainability - EuNetAir COST Action TD1105 A Holistic Approach in the Development and Deployment of WSN-based
A local area network that employs either a full mesh topology or partial mesh topology
 and Ad Hoc Networks Definition A local area network that employs either a full mesh topology or partial mesh topology Full mesh topology each node is connected directly to each of the others Partial mesh
and Ad Hoc Networks Definition A local area network that employs either a full mesh topology or partial mesh topology Full mesh topology each node is connected directly to each of the others Partial mesh
Data Caching in Networks with Reading, Writing and Storage Costs
 Data Caching in Networks with Reading, Writing and Storage Costs Bin Tang a, Himanshu Gupta b a Department of Electrical Engineering and Computer Science, Wichita State University, Wichita, KS 67260 b
Data Caching in Networks with Reading, Writing and Storage Costs Bin Tang a, Himanshu Gupta b a Department of Electrical Engineering and Computer Science, Wichita State University, Wichita, KS 67260 b
Bandwidth Aware Routing Algorithms for Networks-on-Chip
 1 Bandwidth Aware Routing Algorithms for Networks-on-Chip G. Longo a, S. Signorino a, M. Palesi a,, R. Holsmark b, S. Kumar b, and V. Catania a a Department of Computer Science and Telecommunications Engineering
1 Bandwidth Aware Routing Algorithms for Networks-on-Chip G. Longo a, S. Signorino a, M. Palesi a,, R. Holsmark b, S. Kumar b, and V. Catania a a Department of Computer Science and Telecommunications Engineering
Chapter 7: Routing Dynamically. Routing & Switching
 Chapter 7: Routing Dynamically Routing & Switching The Evolution of Dynamic Routing Protocols Dynamic routing protocols used in networks since the late 1980s Newer versions support the communication based
Chapter 7: Routing Dynamically Routing & Switching The Evolution of Dynamic Routing Protocols Dynamic routing protocols used in networks since the late 1980s Newer versions support the communication based
Routing. Information Networks p.1/35
 Routing Routing is done by the network layer protocol to guide packets through the communication subnet to their destinations The time when routing decisions are made depends on whether we are using virtual
Routing Routing is done by the network layer protocol to guide packets through the communication subnet to their destinations The time when routing decisions are made depends on whether we are using virtual
Constructive floorplanning with a yield objective
 Constructive floorplanning with a yield objective Rajnish Prasad and Israel Koren Department of Electrical and Computer Engineering University of Massachusetts, Amherst, MA 13 E-mail: rprasad,koren@ecs.umass.edu
Constructive floorplanning with a yield objective Rajnish Prasad and Israel Koren Department of Electrical and Computer Engineering University of Massachusetts, Amherst, MA 13 E-mail: rprasad,koren@ecs.umass.edu
Routing Algorithms McGraw-Hill The McGraw-Hill Companies, Inc., 2001
 Routing Algorithms Main issue is how the routers that constitute the network layer of a network cooperate to find the best routes between all pairs of stations. Routing algorithm at a router decides which
Routing Algorithms Main issue is how the routers that constitute the network layer of a network cooperate to find the best routes between all pairs of stations. Routing algorithm at a router decides which
CSEP 561 Routing. David Wetherall
 CSEP 561 Routing David Wetherall djw@cs.washington.edu Routing Focus: How to find and set up paths through a network Distance-vector and link-state Application Shortest path routing Transport Key properties
CSEP 561 Routing David Wetherall djw@cs.washington.edu Routing Focus: How to find and set up paths through a network Distance-vector and link-state Application Shortest path routing Transport Key properties
Chapter 3 Part 2 Switching and Bridging. Networking CS 3470, Section 1
 Chapter 3 Part 2 Switching and Bridging Networking CS 3470, Section 1 Refresher We can use switching technologies to interconnect links to form a large network What is a hub? What is a switch? What is
Chapter 3 Part 2 Switching and Bridging Networking CS 3470, Section 1 Refresher We can use switching technologies to interconnect links to form a large network What is a hub? What is a switch? What is
3. INTERCONNECTING NETWORKS WITH SWITCHES. THE SPANNING TREE PROTOCOL (STP)
 3. INTERCONNECTING NETWORKS WITH SWITCHES. THE SPANNING TREE PROTOCOL (STP) 3.1. STP Operation In an extended Ethernet network (a large network, including many switches) multipath propagation may exist
3. INTERCONNECTING NETWORKS WITH SWITCHES. THE SPANNING TREE PROTOCOL (STP) 3.1. STP Operation In an extended Ethernet network (a large network, including many switches) multipath propagation may exist
Keywords: Medium access control, network coding, routing, throughput, transmission rate. I. INTRODUCTION
 Performance Analysis of Network Parameters, Throughput Optimization Using Joint Routing, XOR Routing and Medium Access Control in Wireless Multihop Network 1 Dr. Anuradha M. S., 2 Ms. Anjali kulkarni 1
Performance Analysis of Network Parameters, Throughput Optimization Using Joint Routing, XOR Routing and Medium Access Control in Wireless Multihop Network 1 Dr. Anuradha M. S., 2 Ms. Anjali kulkarni 1
Energy-Efficient Communication Protocol for Wireless Micro-sensor Networks
 Energy-Efficient Communication Protocol for Wireless Micro-sensor Networks Paper by: Wendi Rabiner Heinzelman, Anantha Chandrakasan, and Hari Balakrishnan Outline Brief Introduction on Wireless Sensor
Energy-Efficient Communication Protocol for Wireless Micro-sensor Networks Paper by: Wendi Rabiner Heinzelman, Anantha Chandrakasan, and Hari Balakrishnan Outline Brief Introduction on Wireless Sensor
An Evolutionary Algorithm for Minimizing Multimodal Functions
 An Evolutionary Algorithm for Minimizing Multimodal Functions D.G. Sotiropoulos, V.P. Plagianakos and M.N. Vrahatis University of Patras, Department of Mamatics, Division of Computational Mamatics & Informatics,
An Evolutionary Algorithm for Minimizing Multimodal Functions D.G. Sotiropoulos, V.P. Plagianakos and M.N. Vrahatis University of Patras, Department of Mamatics, Division of Computational Mamatics & Informatics,
Image Transmission in Sensor Networks
 Image Transmission in Sensor Networks King-Shan Lui and Edmund Y. Lam Department of Electrical and Electronic Engineering The University of Hong Kong Pokfulam Road, Hong Kong, China Email {kslui,elam}@eee.hku.hk
Image Transmission in Sensor Networks King-Shan Lui and Edmund Y. Lam Department of Electrical and Electronic Engineering The University of Hong Kong Pokfulam Road, Hong Kong, China Email {kslui,elam}@eee.hku.hk
Performance Behavior of Unmanned Vehicle Aided Mobile Backbone Based Wireless Ad Hoc Networks
 Performance Behavior of Unmanned Vehicle Aided Mobile Backbone Based Wireless Ad Hoc Networks Izhak Rubin and Runhe Zhang Abstract We introduce Unmanned Vehicles (UVs) to aid the operation of the mobile
Performance Behavior of Unmanned Vehicle Aided Mobile Backbone Based Wireless Ad Hoc Networks Izhak Rubin and Runhe Zhang Abstract We introduce Unmanned Vehicles (UVs) to aid the operation of the mobile
Dual Power Management for Network Connectivity in Wireless Sensor Networks
 Dual Power Management for Network Connectivity in Wireless Sensor Networks Yanxia Rong, Hongsik Choi and Hyeong-Ah Choi Department of Computer Science George Washington University Washington DC Department
Dual Power Management for Network Connectivity in Wireless Sensor Networks Yanxia Rong, Hongsik Choi and Hyeong-Ah Choi Department of Computer Science George Washington University Washington DC Department
Growth. Individual departments in a university buy LANs for their own machines and eventually want to interconnect with other campus LANs.
 Internetworking Multiple networks are a fact of life: Growth. Individual departments in a university buy LANs for their own machines and eventually want to interconnect with other campus LANs. Fault isolation,
Internetworking Multiple networks are a fact of life: Growth. Individual departments in a university buy LANs for their own machines and eventually want to interconnect with other campus LANs. Fault isolation,
Traffic Grooming and Regenerator Placement in Impairment-Aware Optical WDM Networks
 Traffic Grooming and Regenerator Placement in Impairment-Aware Optical WDM Networks Ankitkumar N. Patel, Chengyi Gao, and Jason P. Jue Erik Jonsson School of Engineering and Computer Science The University
Traffic Grooming and Regenerator Placement in Impairment-Aware Optical WDM Networks Ankitkumar N. Patel, Chengyi Gao, and Jason P. Jue Erik Jonsson School of Engineering and Computer Science The University
Data Storage in Sensor Networks for Multi-dimensional Range Queries
 Data Storage in Sensor Networks for Multi-dimensional Range Queries Ji Yeon Lee 1, Yong Hun Lim 2, Yon Dohn Chung 3,*, and Myoung Ho Kim 4 1 E-Government Team, National Computerization Agency, Seoul, Korea
Data Storage in Sensor Networks for Multi-dimensional Range Queries Ji Yeon Lee 1, Yong Hun Lim 2, Yon Dohn Chung 3,*, and Myoung Ho Kim 4 1 E-Government Team, National Computerization Agency, Seoul, Korea
End-to-end Real-time Guarantees in Wireless Cyber-physical Systems
 End-to-end Real-time Guarantees in Wireless Cyber-physical Systems Romain Jacob Marco Zimmerling Pengcheng Huang Jan Beutel Lothar Thiele RTSS 16 - IoT and Networking Session December 1, 2016 Predictability
End-to-end Real-time Guarantees in Wireless Cyber-physical Systems Romain Jacob Marco Zimmerling Pengcheng Huang Jan Beutel Lothar Thiele RTSS 16 - IoT and Networking Session December 1, 2016 Predictability
Energy aware geographic routing in wireless sensor networks with anchor nodes. Mircea Cretu Stancu Utrecht University Computing Science May 2013
 Energy aware geographic routing in wireless sensor networks with anchor nodes Mircea Cretu Stancu Utrecht University Computing Science May 2013 Overview Introduction Current paradigm EAGR preliminaries
Energy aware geographic routing in wireless sensor networks with anchor nodes Mircea Cretu Stancu Utrecht University Computing Science May 2013 Overview Introduction Current paradigm EAGR preliminaries
Figure 1. Clustering in MANET.
 Volume 6, Issue 12, December 2016 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com Performance
Volume 6, Issue 12, December 2016 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com Performance
Graph Theoretic Models for Ad hoc Wireless Networks
 Graph Theoretic Models for Ad hoc Wireless Networks Prof. Srikrishnan Divakaran DA-IICT 10/4/2009 DA-IICT 1 Talk Outline Overview of Ad hoc Networks Design Issues in Modeling Ad hoc Networks Graph Theoretic
Graph Theoretic Models for Ad hoc Wireless Networks Prof. Srikrishnan Divakaran DA-IICT 10/4/2009 DA-IICT 1 Talk Outline Overview of Ad hoc Networks Design Issues in Modeling Ad hoc Networks Graph Theoretic
An AIAD-Based Adaptive Routing Protocol in Ad-Hoc Wireless Networks
 An AIAD-Based Adaptive Routing Protocol in Ad-Hoc Wireless Networks Youn-Sik Hong 1 and Ki-Young Lee 2 1 Department of Computer Science and Eng. 2 Department of Information and Telecommunication Eng.,
An AIAD-Based Adaptive Routing Protocol in Ad-Hoc Wireless Networks Youn-Sik Hong 1 and Ki-Young Lee 2 1 Department of Computer Science and Eng. 2 Department of Information and Telecommunication Eng.,
Chapter 16 Networking
 Chapter 16 Networking Outline 16.1 Introduction 16.2 Network Topology 16.3 Network Types 16.4 TCP/IP Protocol Stack 16.5 Application Layer 16.5.1 Hypertext Transfer Protocol (HTTP) 16.5.2 File Transfer
Chapter 16 Networking Outline 16.1 Introduction 16.2 Network Topology 16.3 Network Types 16.4 TCP/IP Protocol Stack 16.5 Application Layer 16.5.1 Hypertext Transfer Protocol (HTTP) 16.5.2 File Transfer
Source-Route Bridging
 25 CHAPTER Chapter Goals Describe when to use source-route bridging. Understand the difference between SRB and transparent bridging. Know the mechanism that end stations use to specify a source-route.
25 CHAPTER Chapter Goals Describe when to use source-route bridging. Understand the difference between SRB and transparent bridging. Know the mechanism that end stations use to specify a source-route.
Deadline Guaranteed Service for Multi- Tenant Cloud Storage Guoxin Liu and Haiying Shen
 Deadline Guaranteed Service for Multi- Tenant Cloud Storage Guoxin Liu and Haiying Shen Presenter: Haiying Shen Associate professor *Department of Electrical and Computer Engineering, Clemson University,
Deadline Guaranteed Service for Multi- Tenant Cloud Storage Guoxin Liu and Haiying Shen Presenter: Haiying Shen Associate professor *Department of Electrical and Computer Engineering, Clemson University,
Admission Control in Time-Slotted Multihop Mobile Networks
 dmission ontrol in Time-Slotted Multihop Mobile Networks Shagun Dusad and nshul Khandelwal Information Networks Laboratory Department of Electrical Engineering Indian Institute of Technology - ombay Mumbai
dmission ontrol in Time-Slotted Multihop Mobile Networks Shagun Dusad and nshul Khandelwal Information Networks Laboratory Department of Electrical Engineering Indian Institute of Technology - ombay Mumbai
Performance Evaluation of Mesh - Based Multicast Routing Protocols in MANET s
 Performance Evaluation of Mesh - Based Multicast Routing Protocols in MANET s M. Nagaratna Assistant Professor Dept. of CSE JNTUH, Hyderabad, India V. Kamakshi Prasad Prof & Additional Cont. of. Examinations
Performance Evaluation of Mesh - Based Multicast Routing Protocols in MANET s M. Nagaratna Assistant Professor Dept. of CSE JNTUH, Hyderabad, India V. Kamakshi Prasad Prof & Additional Cont. of. Examinations
CHAPTER 4: ROUTING DYNAMIC. Routing & Switching
 CHAPTER 4: ROUTING DYNAMIC Routing & Switching CHAPTER4 4.1 Dynamic Routing Protocols 4.2 Distance Vector Dynamic Routing 4.3 RIP and RIPng Routing 4.4 Link-State Dynamic Routing 4.5 The Routing Table
CHAPTER 4: ROUTING DYNAMIC Routing & Switching CHAPTER4 4.1 Dynamic Routing Protocols 4.2 Distance Vector Dynamic Routing 4.3 RIP and RIPng Routing 4.4 Link-State Dynamic Routing 4.5 The Routing Table
On characterizing BGP routing table growth
 University of Massachusetts Amherst From the SelectedWorks of Lixin Gao 00 On characterizing BGP routing table growth T Bu LX Gao D Towsley Available at: https://works.bepress.com/lixin_gao/66/ On Characterizing
University of Massachusetts Amherst From the SelectedWorks of Lixin Gao 00 On characterizing BGP routing table growth T Bu LX Gao D Towsley Available at: https://works.bepress.com/lixin_gao/66/ On Characterizing
Efficient Directional Network Backbone Construction in Mobile Ad Hoc Networks
 Efficient Directional Network Backbone Construction in Mobile Ad Hoc Networks Shuhui Yang, Jie Wu, and Fei Dai Department of Computer Science Rensselaer Polytechnic Institute Troy, NY 12180 Department
Efficient Directional Network Backbone Construction in Mobile Ad Hoc Networks Shuhui Yang, Jie Wu, and Fei Dai Department of Computer Science Rensselaer Polytechnic Institute Troy, NY 12180 Department
EEC-684/584 Computer Networks
 EEC-684/584 Computer Networks Lecture 14 wenbing@ieee.org (Lecture nodes are based on materials supplied by Dr. Louise Moser at UCSB and Prentice-Hall) Outline 2 Review of last lecture Internetworking
EEC-684/584 Computer Networks Lecture 14 wenbing@ieee.org (Lecture nodes are based on materials supplied by Dr. Louise Moser at UCSB and Prentice-Hall) Outline 2 Review of last lecture Internetworking
A Path Decomposition Approach for Computing Blocking Probabilities in Wavelength-Routing Networks
 IEEE/ACM TRANSACTIONS ON NETWORKING, VOL. 8, NO. 6, DECEMBER 2000 747 A Path Decomposition Approach for Computing Blocking Probabilities in Wavelength-Routing Networks Yuhong Zhu, George N. Rouskas, Member,
IEEE/ACM TRANSACTIONS ON NETWORKING, VOL. 8, NO. 6, DECEMBER 2000 747 A Path Decomposition Approach for Computing Blocking Probabilities in Wavelength-Routing Networks Yuhong Zhu, George N. Rouskas, Member,
EEC-484/584 Computer Networks
 EEC-484/584 Computer Networks Lecture 13 wenbing@ieee.org (Lecture nodes are based on materials supplied by Dr. Louise Moser at UCSB and Prentice-Hall) Outline 2 Review of lecture 12 Routing Congestion
EEC-484/584 Computer Networks Lecture 13 wenbing@ieee.org (Lecture nodes are based on materials supplied by Dr. Louise Moser at UCSB and Prentice-Hall) Outline 2 Review of lecture 12 Routing Congestion
GMNF-DVMRP: AN ENHANCED VERSION OF DISTANCE VECTOR MULTICAST ROUTING PROTOCOL
 GMNF-DVMRP: AN ENHANCED VERSION OF DISTANCE VECTOR MULTICAST ROUTING PROTOCOL YUAN-CHENG LAI YING-DAR LIN AND WEI-CHE YU Department of Computer and Information Science, National Chiao Tung University,
GMNF-DVMRP: AN ENHANCED VERSION OF DISTANCE VECTOR MULTICAST ROUTING PROTOCOL YUAN-CHENG LAI YING-DAR LIN AND WEI-CHE YU Department of Computer and Information Science, National Chiao Tung University,
IP Multicast Technology Overview
 IP multicast is a bandwidth-conserving technology that reduces traffic by delivering a single stream of information simultaneously to potentially thousands of businesses and homes. Applications that take
IP multicast is a bandwidth-conserving technology that reduces traffic by delivering a single stream of information simultaneously to potentially thousands of businesses and homes. Applications that take
Efficient Cluster Based Data Collection Using Mobile Data Collector for Wireless Sensor Network
 ISSN (e): 2250 3005 Volume, 06 Issue, 06 June 2016 International Journal of Computational Engineering Research (IJCER) Efficient Cluster Based Data Collection Using Mobile Data Collector for Wireless Sensor
ISSN (e): 2250 3005 Volume, 06 Issue, 06 June 2016 International Journal of Computational Engineering Research (IJCER) Efficient Cluster Based Data Collection Using Mobile Data Collector for Wireless Sensor
Sensor Deployment, Self- Organization, And Localization. Model of Sensor Nodes. Model of Sensor Nodes. WiSe
 Sensor Deployment, Self- Organization, And Localization Material taken from Sensor Network Operations by Shashi Phoa, Thomas La Porta and Christopher Griffin, John Wiley, 2007 5/20/2008 WiSeLab@WMU; www.cs.wmich.edu/wise
Sensor Deployment, Self- Organization, And Localization Material taken from Sensor Network Operations by Shashi Phoa, Thomas La Porta and Christopher Griffin, John Wiley, 2007 5/20/2008 WiSeLab@WMU; www.cs.wmich.edu/wise
Internetworking. Problem: There is more than one network (heterogeneity & scale)
 Internetworking Problem: There is more than one network (heterogeneity & scale) Hongwei Zhang http://www.cs.wayne.edu/~hzhang Internetworking: Internet Protocol (IP) Routing and scalability Group Communication
Internetworking Problem: There is more than one network (heterogeneity & scale) Hongwei Zhang http://www.cs.wayne.edu/~hzhang Internetworking: Internet Protocol (IP) Routing and scalability Group Communication
Rumor Routing Algorithm
 Aleksi.Ahtiainen@hut.fi T-79.194 Seminar on Theoretical Computer Science Feb 9 2005 Contents Introduction The Algorithm Research Results Future Work Criticism Conclusions Introduction is described in paper:
Aleksi.Ahtiainen@hut.fi T-79.194 Seminar on Theoretical Computer Science Feb 9 2005 Contents Introduction The Algorithm Research Results Future Work Criticism Conclusions Introduction is described in paper:
An Iterative Greedy Approach Using Geographical Destination Routing In WSN
 ISSN (Online) : 2319-8753 ISSN (Print) : 2347-6710 International Journal of Innovative Research in Science, Engineering and Technology Volume 3, Special Issue 3, March 2014 2014 International Conference
ISSN (Online) : 2319-8753 ISSN (Print) : 2347-6710 International Journal of Innovative Research in Science, Engineering and Technology Volume 3, Special Issue 3, March 2014 2014 International Conference
A Hybrid Load Balance Mechanism for Distributed Home Agents in Mobile IPv6
 A Hybrid Load Balance Mechanism for Distributed Home Agents in Mobile IPv6 1 Hui Deng 2Xiaolong Huang 3Kai Zhang 3 Zhisheng Niu 1Masahiro Ojima 1R&D Center Hitachi (China) Ltd. Beijing 100004, China 2Dept.
A Hybrid Load Balance Mechanism for Distributed Home Agents in Mobile IPv6 1 Hui Deng 2Xiaolong Huang 3Kai Zhang 3 Zhisheng Niu 1Masahiro Ojima 1R&D Center Hitachi (China) Ltd. Beijing 100004, China 2Dept.
The Energy-Robustness Tradeoff for Routing in Wireless Sensor Networks
 The Energy-Robustness Tradeoff for Routing in Wireless Sensor Networks Bhaskar Krishnamachari y, Yasser Mourtada *, and Stephen Wicker * y Department of Electrical Engineering, University of Southern California,
The Energy-Robustness Tradeoff for Routing in Wireless Sensor Networks Bhaskar Krishnamachari y, Yasser Mourtada *, and Stephen Wicker * y Department of Electrical Engineering, University of Southern California,
Flexible-Hybrid Sequential Floating Search in Statistical Feature Selection
 Flexible-Hybrid Sequential Floating Search in Statistical Feature Selection Petr Somol 1,2, Jana Novovičová 1,2, and Pavel Pudil 2,1 1 Dept. of Pattern Recognition, Institute of Information Theory and
Flexible-Hybrid Sequential Floating Search in Statistical Feature Selection Petr Somol 1,2, Jana Novovičová 1,2, and Pavel Pudil 2,1 1 Dept. of Pattern Recognition, Institute of Information Theory and
Approximation Algorithms
 Approximation Algorithms Prof. Tapio Elomaa tapio.elomaa@tut.fi Course Basics A new 4 credit unit course Part of Theoretical Computer Science courses at the Department of Mathematics There will be 4 hours
Approximation Algorithms Prof. Tapio Elomaa tapio.elomaa@tut.fi Course Basics A new 4 credit unit course Part of Theoretical Computer Science courses at the Department of Mathematics There will be 4 hours
Distributed Detection in Sensor Networks: Connectivity Graph and Small World Networks
 Distributed Detection in Sensor Networks: Connectivity Graph and Small World Networks SaeedA.AldosariandJoséM.F.Moura Electrical and Computer Engineering Department Carnegie Mellon University 5000 Forbes
Distributed Detection in Sensor Networks: Connectivity Graph and Small World Networks SaeedA.AldosariandJoséM.F.Moura Electrical and Computer Engineering Department Carnegie Mellon University 5000 Forbes
Applying Real-Time Scheduling Techniques to Software Processes: A Position Paper
 To Appear in Proc. of the 8th European Workshop on Software Process Technology.19-21 June 2001. Witten, Germany. Applying Real-Time Scheduling Techniques to Software Processes: A Position Paper Aaron G.
To Appear in Proc. of the 8th European Workshop on Software Process Technology.19-21 June 2001. Witten, Germany. Applying Real-Time Scheduling Techniques to Software Processes: A Position Paper Aaron G.
Top-Down Network Design, Ch. 7: Selecting Switching and Routing Protocols. Top-Down Network Design. Selecting Switching and Routing Protocols
 Top-Down Network Design Chapter Seven Selecting Switching and Routing Protocols Copyright 2010 Cisco Press & Priscilla Oppenheimer 1 Switching 2 Page 1 Objectives MAC address table Describe the features
Top-Down Network Design Chapter Seven Selecting Switching and Routing Protocols Copyright 2010 Cisco Press & Priscilla Oppenheimer 1 Switching 2 Page 1 Objectives MAC address table Describe the features
LOW-DENSITY PARITY-CHECK (LDPC) codes [1] can
![LOW-DENSITY PARITY-CHECK (LDPC) codes [1] can LOW-DENSITY PARITY-CHECK (LDPC) codes [1] can](/thumbs/96/128999908.jpg) 208 IEEE TRANSACTIONS ON MAGNETICS, VOL 42, NO 2, FEBRUARY 2006 Structured LDPC Codes for High-Density Recording: Large Girth and Low Error Floor J Lu and J M F Moura Department of Electrical and Computer
208 IEEE TRANSACTIONS ON MAGNETICS, VOL 42, NO 2, FEBRUARY 2006 Structured LDPC Codes for High-Density Recording: Large Girth and Low Error Floor J Lu and J M F Moura Department of Electrical and Computer
Randomized rounding of semidefinite programs and primal-dual method for integer linear programming. Reza Moosavi Dr. Saeedeh Parsaeefard Dec.
 Randomized rounding of semidefinite programs and primal-dual method for integer linear programming Dr. Saeedeh Parsaeefard 1 2 3 4 Semidefinite Programming () 1 Integer Programming integer programming
Randomized rounding of semidefinite programs and primal-dual method for integer linear programming Dr. Saeedeh Parsaeefard 1 2 3 4 Semidefinite Programming () 1 Integer Programming integer programming
Chapter 5 (Week 9) The Network Layer ANDREW S. TANENBAUM COMPUTER NETWORKS FOURTH EDITION PP BLM431 Computer Networks Dr.
 Chapter 5 (Week 9) The Network Layer ANDREW S. TANENBAUM COMPUTER NETWORKS FOURTH EDITION PP. 343-396 1 5.1. NETWORK LAYER DESIGN ISSUES 5.2. ROUTING ALGORITHMS 5.3. CONGESTION CONTROL ALGORITHMS 5.4.
Chapter 5 (Week 9) The Network Layer ANDREW S. TANENBAUM COMPUTER NETWORKS FOURTH EDITION PP. 343-396 1 5.1. NETWORK LAYER DESIGN ISSUES 5.2. ROUTING ALGORITHMS 5.3. CONGESTION CONTROL ALGORITHMS 5.4.
Performance Evaluation of DSDV, DSR AND ZRP Protocol in MANET
 Performance Evaluation of, AND Protocol in MANET Zaiba Ishrat IIMT Engg college,meerut Meerut, India Pankaj singh Sidhi vinayak Group of College,Alwar Alwar,Rajasthan Rehan Ahmad IIMT Engg college,meerut
Performance Evaluation of, AND Protocol in MANET Zaiba Ishrat IIMT Engg college,meerut Meerut, India Pankaj singh Sidhi vinayak Group of College,Alwar Alwar,Rajasthan Rehan Ahmad IIMT Engg college,meerut
Networking Sensors, II
 Networking Sensors, II Sensing Networking Leonidas Guibas Stanford University Computation CS321 ZG Book, Ch. 3 1 Class Administration Paper presentation preferences due today, by class time Project info
Networking Sensors, II Sensing Networking Leonidas Guibas Stanford University Computation CS321 ZG Book, Ch. 3 1 Class Administration Paper presentation preferences due today, by class time Project info
TDMH-MAC: Real-time and multi-hop in the same wireless MAC
 TDMH-MAC: Real-time and multi-hop in the same wireless MAC Federico Terraneo, Paolo Polidori, Alberto Leva, William Fornaciari Politecnico di Milano, Italy RTSS 8 Nashville, December 8 Quick context This
TDMH-MAC: Real-time and multi-hop in the same wireless MAC Federico Terraneo, Paolo Polidori, Alberto Leva, William Fornaciari Politecnico di Milano, Italy RTSS 8 Nashville, December 8 Quick context This
Achieving Lightweight Multicast in Asynchronous Networks-on-Chip Using Local Speculation
 Achieving Lightweight Multicast in Asynchronous Networks-on-Chip Using Local Speculation Kshitij Bhardwaj Dept. of Computer Science Columbia University Steven M. Nowick 2016 ACM/IEEE Design Automation
Achieving Lightweight Multicast in Asynchronous Networks-on-Chip Using Local Speculation Kshitij Bhardwaj Dept. of Computer Science Columbia University Steven M. Nowick 2016 ACM/IEEE Design Automation
Wireless Sensor Networks: Clustering, Routing, Localization, Time Synchronization
 Wireless Sensor Networks: Clustering, Routing, Localization, Time Synchronization Maurizio Bocca, M.Sc. Control Engineering Research Group Automation and Systems Technology Department maurizio.bocca@tkk.fi
Wireless Sensor Networks: Clustering, Routing, Localization, Time Synchronization Maurizio Bocca, M.Sc. Control Engineering Research Group Automation and Systems Technology Department maurizio.bocca@tkk.fi
CompSci 356: Computer Network Architectures. Lecture 8: Spanning Tree Algorithm and Basic Internetworking Ch & 3.2. Xiaowei Yang
 CompSci 356: Computer Network Architectures Lecture 8: Spanning Tree Algorithm and Basic Internetworking Ch 3.1.5 & 3.2 Xiaowei Yang xwy@cs.duke.edu Review Past lectures Single link networks Point-to-point,
CompSci 356: Computer Network Architectures Lecture 8: Spanning Tree Algorithm and Basic Internetworking Ch 3.1.5 & 3.2 Xiaowei Yang xwy@cs.duke.edu Review Past lectures Single link networks Point-to-point,
Routing protocols in WSN
 Routing protocols in WSN 1.1 WSN Routing Scheme Data collected by sensor nodes in a WSN is typically propagated toward a base station (gateway) that links the WSN with other networks where the data can
Routing protocols in WSN 1.1 WSN Routing Scheme Data collected by sensor nodes in a WSN is typically propagated toward a base station (gateway) that links the WSN with other networks where the data can
USING BRIDGES, ROUTERS AND GATEWAYS IN DATA ACQUISITION NETWORKS
 USING BRIDGES, ROUTERS AND GATEWAYS IN DATA ACQUISITION NETWORKS Tom De Selms JDANS Lead Engineer Veridian Engineering thomas.deselms@veridian.com ABSTRACT Using acquisition networks requires an understanding
USING BRIDGES, ROUTERS AND GATEWAYS IN DATA ACQUISITION NETWORKS Tom De Selms JDANS Lead Engineer Veridian Engineering thomas.deselms@veridian.com ABSTRACT Using acquisition networks requires an understanding
The Spanning Tree Protocol
 Università Ca Foscari di Venezia Dipartimento di Informatica Corso di Sistemi Distribuiti 2009 Presentation outline Introduction 1 Introduction Local internetworking Motivations 2 High level description
Università Ca Foscari di Venezia Dipartimento di Informatica Corso di Sistemi Distribuiti 2009 Presentation outline Introduction 1 Introduction Local internetworking Motivations 2 High level description
This Lecture. BUS Computer Facilities Network Management. Switching Network. Simple Switching Network
 This Lecture BUS0 - Computer Facilities Network Management Switching networks Circuit switching Packet switching gram approach Virtual circuit approach Routing in switching networks Faculty of Information
This Lecture BUS0 - Computer Facilities Network Management Switching networks Circuit switching Packet switching gram approach Virtual circuit approach Routing in switching networks Faculty of Information
MINIMUM HOP MULTICASTING IN BROADCAST WIRELESS NETWORKS WITH OMNI-DIRECTIONAL ANTENNAS
 MINIMUM HOP MULTICASTING IN BROADCAST WIRELESS NETWORKS WITH OMNI-DIRECTIONAL ANTENNAS Arindam K. Das, Mohamed El-Sharkawi Department of Electrical Engineering University of Washington, Box 352500, Seattle,
MINIMUM HOP MULTICASTING IN BROADCAST WIRELESS NETWORKS WITH OMNI-DIRECTIONAL ANTENNAS Arindam K. Das, Mohamed El-Sharkawi Department of Electrical Engineering University of Washington, Box 352500, Seattle,
Constructing Connected Dominating Sets with Bounded Diameters in Wireless Networks
 Constructing Connected Dominating Sets with Bounded Diameters in Wireless Networks Yingshu Li Department of Computer Science Georgia State University Atlanta, GA 30303 yli@cs.gsu.edu Donghyun Kim Feng
Constructing Connected Dominating Sets with Bounded Diameters in Wireless Networks Yingshu Li Department of Computer Science Georgia State University Atlanta, GA 30303 yli@cs.gsu.edu Donghyun Kim Feng
Efficient Broadcasting in Ad Hoc Wireless Networks Using Directional Antennas
 Efficient Broadcasting in Ad Hoc Wireless Networks Using Directional Antennas Fei Dai Department of Electrical and Computer Engineering North Dakota State University Fargo, ND 5805 Email: fdai@ece.ndsu.edu
Efficient Broadcasting in Ad Hoc Wireless Networks Using Directional Antennas Fei Dai Department of Electrical and Computer Engineering North Dakota State University Fargo, ND 5805 Email: fdai@ece.ndsu.edu
The Interconnection Structure of. The Internet. EECC694 - Shaaban
 The Internet Evolved from the ARPANET (the Advanced Research Projects Agency Network), a project funded by The U.S. Department of Defense (DOD) in 1969. ARPANET's purpose was to provide the U.S. Defense
The Internet Evolved from the ARPANET (the Advanced Research Projects Agency Network), a project funded by The U.S. Department of Defense (DOD) in 1969. ARPANET's purpose was to provide the U.S. Defense
Top-Down Network Design
 Top-Down Network Design Chapter Seven Selecting Switching and Routing Protocols Original slides by Cisco Press & Priscilla Oppenheimer Selection Criteria for Switching and Routing Protocols Network traffic
Top-Down Network Design Chapter Seven Selecting Switching and Routing Protocols Original slides by Cisco Press & Priscilla Oppenheimer Selection Criteria for Switching and Routing Protocols Network traffic
CSE 417 Branch & Bound (pt 4) Branch & Bound
 CSE 417 Branch & Bound (pt 4) Branch & Bound Reminders > HW8 due today > HW9 will be posted tomorrow start early program will be slow, so debugging will be slow... Review of previous lectures > Complexity
CSE 417 Branch & Bound (pt 4) Branch & Bound Reminders > HW8 due today > HW9 will be posted tomorrow start early program will be slow, so debugging will be slow... Review of previous lectures > Complexity
Low Power Hitch-hiking Broadcast in Ad Hoc Wireless Networks
 Low Power Hitch-hiking Broadcast in Ad Hoc Wireless Networks Mihaela Cardei, Jie Wu, and Shuhui Yang Department of Computer Science and Engineering Florida Atlantic University Boca Raton, FL 33431 {mihaela,jie}@cse.fau.edu,
Low Power Hitch-hiking Broadcast in Ad Hoc Wireless Networks Mihaela Cardei, Jie Wu, and Shuhui Yang Department of Computer Science and Engineering Florida Atlantic University Boca Raton, FL 33431 {mihaela,jie}@cse.fau.edu,
