... Chair of Mobile Business & Multilateral Security. Mentorium Business Informatics 2 (PWIN)
|
|
|
- Nigel Price
- 6 years ago
- Views:
Transcription
1 Mentorium Business Informatics (PWIN) Communication Systems I, II & Management of IT Projects WS 05/06 Shuzhe Yang Chair of Mobile Business & Multilateral Security Jenser (Flickr.com) Business Informatics (PWIN) WS 05/06, Chair of Mobile Business & Multilateral Security
2 Using Dijkstra Algorithm nd Example Wired Networks Wireless Networks IT-Project Management Agenda Business Informatics (PWIN) WS 05/06, Chair of Mobile Business & Multilateral Security
3 A (0,-) 3 D B C 4 Dijkstra Algorithm () Business Informatics (PWIN) WS 05/06, Chair of Mobile Business & Multilateral Security 3 E F G H
4 A (0,-) 3 D B C 4 Dijkstra Algorithm () Business Informatics (PWIN) WS 05/06, Chair of Mobile Business & Multilateral Security 4 E F G H
5 A (0,-) 3 D B C (,A) (,A) 4 Dijkstra Algorithm () Business Informatics (PWIN) WS 05/06, Chair of Mobile Business & Multilateral Security 5 E (,A) (3,A) F G H
6 A (0,-) 3 D B C (,A) (,A) 4 Dijkstra Algorithm () Business Informatics (PWIN) WS 05/06, Chair of Mobile Business & Multilateral Security 6 E (8,B) (3,A) F G H
7 A (0,-) 3 D B C (,A) (,A) 4 Dijkstra Algorithm () Business Informatics (PWIN) WS 05/06, Chair of Mobile Business & Multilateral Security E (,D) (3,A) (5,D) F G H
8 A (0,-) 3 D (6,F) (,A) B C 4 Dijkstra Algorithm () Business Informatics (PWIN) WS 05/06, Chair of Mobile Business & Multilateral Security 8 E (,D) (3,A) (5,D) F G H (,F)
9 A (0,-) 3 D (6,F) (,A) B C 4 Dijkstra Algorithm () Business Informatics (PWIN) WS 05/06, Chair of Mobile Business & Multilateral Security E (,D) (3,A) (5,D) F G H (,F)
10 A (0,-) 3 D (6,F) (,A) B C 4 Dijkstra Algorithm () Business Informatics (PWIN) WS 05/06, Chair of Mobile Business & Multilateral Security 0 E (,D) (,E) (3,A) (5,D) F G H (,F)
11 A (0,-) 3 D (6,F) (,A) B C 4 Dijkstra Algorithm () Business Informatics (PWIN) WS 05/06, Chair of Mobile Business & Multilateral Security E (,D) (,E) (3,A) (5,D) F G H (,G)
12 A (0,-) 3 D (3,A) C (6,F) (,A) B 4 Dijkstra Algorithm () Business Informatics (PWIN) WS 05/06, Chair of Mobile Business & Multilateral Security E (,D) F (5,D) G (,E) Shortest path: A à D à E à G à H or: A à D à F à C à E à G à H H (,G)
13 Using Dijkstra Algorithm nd Example Wired Networks Wireless Networks IT-Project Management Agenda Business Informatics (PWIN) WS 05/06, Chair of Mobile Business & Multilateral Security 3
14 Wired Networks Name and explain the application areas of Ethernet, xdsl and FTTx. The myplace Service constitutes a mobile application/service. Nevertheless, it also makes use of wired networks for its data communications. Explain where and why. Source: Business Laudon, Informatics K.C., Laudon, (PWIN) J.P., WS 05/06, Schoder, D. Chair (006) of Mobile Business & Multilateral Security 4
15 Ethernet Wired Networks: Solution In Building with a range up to about 00m, (bandwidth up to 0Gbit) xdsl use existing copper wires of a telephone network DSL communication is enabled by a connection between DSL modem (User) and a Digital Subscriber Line Access Multiplexer (DSLAM) (Provider) FTTx a generic term for any broadband network architecture that uses optical fiber for the so-called last mile Expensive and only short distance with high date rate Source: Business Laudon, Informatics K.C., Laudon, (PWIN) J.P., WS 05/06, Schoder, D. Chair (006) of Mobile Business & Multilateral Security 5
16 Access to mobile portal setting user profile mobile customer contact Creation of dyn. () user profile () Profile DB myplace service Localisation DB Process overview of the myplace service Services Campaigns Promotions Customer Care POI POI n Business Informatics (PWIN) WS 05/06, Chair of Mobile Business & Multilateral Security 6 (3) Personalized Service offer Targetgroup DB POI... Define target group & Usage context
17 Wired Networks (myplace): Solution Data centre: Server use wired network Infrastructure of mobile phone network are usually wired Wlan access points use wire network Internet access at home is most certainly partially wired, e.g. DSL or cable internet Source: Business Laudon, Informatics K.C., Laudon, (PWIN) J.P., WS 05/06, Schoder, D. Chair (006) of Mobile Business & Multilateral Security
18 Using Dijkstra Algorithm nd Example Wired Networks Wireless Networks IT-Project Management Agenda Business Informatics (PWIN) WS 05/06, Chair of Mobile Business & Multilateral Security 8
19 Wireless Local Area Networks (Wi-Fi) Name a secure method for the encryption of Wireless Local Area Networks (Wi-Fi). Why is Wi-Fi encryption important? What could be the potential consequences for users failing to enable encryption for their Wi-Fi network? What could be the potential harm if the data communication of the myplace service is not encrypted? Name at least one consequence from the myplace Provider as well as the mobile user perspective. Business Informatics (PWIN) WS 05/06, Chair of Mobile Business & Multilateral Security
20 Wi-Fi Proteced Access: WPA or WPA Unsecure Wi-Fi: Wi-Fi: Solution Data can be extracted from the local network Internet access can be used by other for free and illegal activities like file sharing Router manipulation Phone can be misused Business Informatics (PWIN) WS 05/06, Chair of Mobile Business & Multilateral Security 0
21 Man-In-The-Middle Attack Wi-Fi: Solution Attacker between the communication parties and he has the full control of the data traffic Eavesdrop and manipulation of data traffic Passwords, data, personal information DNS manipulation, malware E.g. Redirect online banking to a fishing site Snarfing (fake wlan access point) Business Informatics (PWIN) WS 05/06, Chair of Mobile Business & Multilateral Security
22 Eavesdropping on communication Wi-Fi (myplace): Solution Redirect to a manipulated service is possible Mobile user s perspective: Passwords can be stolen and an attacker can slip into this identity myplace s perspective Unsecure services results in image loss Suit for violating the legal framework Business Informatics (PWIN) WS 05/06, Chair of Mobile Business & Multilateral Security
23 Using Dijkstra Algorithm nd Example Wired Networks Wireless Networks IT-Project Management Agenda Business Informatics (PWIN) WS 05/06, Chair of Mobile Business & Multilateral Security 3
24 IT-Project Management What could be the consequences of carrying out a software development project without proper project management? Business Informatics (PWIN) WS 05/06, Chair of Mobile Business & Multilateral Security 4
25 IT-Project Management: Solution What are the hints for bad project management within a software development company Failed to meet project deadlines Budget overrun Results do not match with the expectations of the customer Overload of the employees, they have to work overtime to meet the deadlines Unsatisfied employees Employees consider, that they do not get positive results from the project Employees work frantically Frequent personnel turnover Project manager leaves and no replacement in sight Former Project with Similar or comparable objectives has already failed Business Informatics (PWIN) WS 05/06, Chair of Mobile Business & Multilateral Security 5
26 IT-Project Management Project Team What is the general problem of increasing the number of project staff members? Assume you are the IT-Project manager for the development of the myplace service and it becomes foreseeable that you will not meet the final deadline. Does it help to increase the number of project staff members? Where are the benefits, problems and limits for this approach? Business Informatics (PWIN) WS 05/06, Chair of Mobile Business & Multilateral Security 6
27 Project Team: Solution An one person project do not need internal communication and distribution of work Increasing the member of the project results in higher needs of communications and with that, the project duration increases On the other side the productivity of every member can be increased due to higher specialization (distribution of work) Business Informatics (PWIN) WS 05/06, Chair of Mobile Business & Multilateral Security
28 Project Team: Solution Example: An IT project is getting out of the hand and it is not able to meet the deadlines (-) Every new member must be incorporated and integrated (-) Overhead, higher need of communication with current employees (+) specialization in problematic areas are possible Business Informatics (PWIN) WS 05/06, Chair of Mobile Business & Multilateral Security 8
29 Open Questions? Questions Business Informatics (PWIN) WS 05/06, Chair of Mobile Business & Multilateral Security
... Chair of Mobile Business & Multilateral Security. Lecture 11 Business Informatics 2 (PWIN)
 Lecture 11 Business Informatics 2 (PWIN) Database Management I Databases & Dataoriented Modelling WS 2015/16 Prof. Dr. Kai Rannenberg www.m-chair.de Chair of Mobile Business & Multilateral Security Jenser
Lecture 11 Business Informatics 2 (PWIN) Database Management I Databases & Dataoriented Modelling WS 2015/16 Prof. Dr. Kai Rannenberg www.m-chair.de Chair of Mobile Business & Multilateral Security Jenser
Broadband access technologies and their introduction in fixed networks of Uzbekistan
 Bridging the ICT standardization gap in developing countries Broadband access technologies and their introduction in fixed networks of Uzbekistan Zokhid ZIYAEV, Engineer of Scientific Engineering and Marketing
Bridging the ICT standardization gap in developing countries Broadband access technologies and their introduction in fixed networks of Uzbekistan Zokhid ZIYAEV, Engineer of Scientific Engineering and Marketing
... Chair of Mobile Business & Multilateral Security. Mentorium Business Informatics 2 (PWIN)
 Mentorium Business Informatics (PWIN) Information Systems II, III & Communication Systems I WS 0/08 Akos Grosz www.m-chair.de Chair of Mobile Business & Multilateral Security Jenser (Flickr.com) Business
Mentorium Business Informatics (PWIN) Information Systems II, III & Communication Systems I WS 0/08 Akos Grosz www.m-chair.de Chair of Mobile Business & Multilateral Security Jenser (Flickr.com) Business
A+ Guide to Hardware: Managing, Maintaining, and Troubleshooting, 5e. Chapter 10 Networking Essentials
 A+ Guide to Hardware: Managing, Maintaining, and Troubleshooting, 5e Chapter 10 Networking Essentials Objectives Learn about hardware devices used for networking Learn about the different types of networks
A+ Guide to Hardware: Managing, Maintaining, and Troubleshooting, 5e Chapter 10 Networking Essentials Objectives Learn about hardware devices used for networking Learn about the different types of networks
Wireless Network Security
 Wireless Network Security Why wireless? Wifi, which is short for wireless fi something, allows your computer to connect to the Internet using magic. -Motel 6 commercial 2 but it comes at a price Wireless
Wireless Network Security Why wireless? Wifi, which is short for wireless fi something, allows your computer to connect to the Internet using magic. -Motel 6 commercial 2 but it comes at a price Wireless
It is the process of sharing data, programs, and information between two or more computers.
 1 Communications It is the process of sharing data, programs, and information between two or more computers. Numerous applications depend on communication systems: E-mail Instant messaging (IM) Internet
1 Communications It is the process of sharing data, programs, and information between two or more computers. Numerous applications depend on communication systems: E-mail Instant messaging (IM) Internet
Setting up the Linksys Smart Wi-Fi Router using the Smart Setup Wizard
 Setting up the Linksys Smart Wi-Fi Router using the Smart Setup Wizard This article will guide you on how to set up your Linksys Smart Wi-Fi Router using the Smart Setup Wizard. QUICK TIP: The Smart Setup
Setting up the Linksys Smart Wi-Fi Router using the Smart Setup Wizard This article will guide you on how to set up your Linksys Smart Wi-Fi Router using the Smart Setup Wizard. QUICK TIP: The Smart Setup
Internet Concepts. Learning objectives. An understanding of the services available through the Internet
 lesson plan Learning objectives An understanding of the services available through the Internet An understanding of the technology underlying Internet security 0 An understanding of the risks associated
lesson plan Learning objectives An understanding of the services available through the Internet An understanding of the technology underlying Internet security 0 An understanding of the risks associated
A+ Guide to Hardware: Managing, Maintaining, and Troubleshooting, 5e. Chapter 10 Networking Essentials
 A+ Guide to Hardware: Managing, Maintaining, and Troubleshooting, 5e Chapter 10 Networking Essentials Objectives Learn about hardware devices used for networking Learn about the different types of networks
A+ Guide to Hardware: Managing, Maintaining, and Troubleshooting, 5e Chapter 10 Networking Essentials Objectives Learn about hardware devices used for networking Learn about the different types of networks
(Network Programming) Basic Networking Hardware
 EEE 448 Computer Networks with (Network Programming) Basic Networking Hardware Lecture #2 Dept of Electrical and Electronics Engineering Çukurova University Agenda What is a network device? Network Media
EEE 448 Computer Networks with (Network Programming) Basic Networking Hardware Lecture #2 Dept of Electrical and Electronics Engineering Çukurova University Agenda What is a network device? Network Media
16/06/56. Communications and Networks. Communications and Networks. Communications and Networks
 Discuss connectivity, the wireless revolution, and communication systems. Describe physical and wireless communications channels. Discuss connection devices and services, including dial-up, DSL, cable,
Discuss connectivity, the wireless revolution, and communication systems. Describe physical and wireless communications channels. Discuss connection devices and services, including dial-up, DSL, cable,
Reset the Router's factory defaults by hold the button pressed down for about 10 seconds.
 Indicator Color Status Description Power Green On Power is on. - Off Power is off or the device is down. WLAN Green Blink Data is being transmitted. - Off Radio switch is shut off. Green On Connection
Indicator Color Status Description Power Green On Power is on. - Off Power is off or the device is down. WLAN Green Blink Data is being transmitted. - Off Radio switch is shut off. Green On Connection
A network is two or more computers, or other electronic devices, connected together so that they can exchange data.
 Computer Networks What is a Network? A network is two or more computers, or other electronic devices, connected together so that they can exchange data. For example; a network allows computers to share
Computer Networks What is a Network? A network is two or more computers, or other electronic devices, connected together so that they can exchange data. For example; a network allows computers to share
Union Springs Telephone Company, Inc. Network TRANSPARENCY statement
 Union Springs Telephone Company, Inc. Network TRANSPARENCY statement Union Springs Telephone Company, Inc. ( Company ) provides this Network Transparency Statement in accordance with the FCC s Restore
Union Springs Telephone Company, Inc. Network TRANSPARENCY statement Union Springs Telephone Company, Inc. ( Company ) provides this Network Transparency Statement in accordance with the FCC s Restore
Wireless Printing Updated 10/30/2008 POLICY. The use of Wireless Networking is not permitted at any site for full client/server networking of Taxwise.
 Updated 10/30/2008 POLICY Tax-Aide Wireless Printing Policy The use of Wireless Networking is not permitted at any site for full client/server networking of Taxwise. Wireless networking, for the purpose
Updated 10/30/2008 POLICY Tax-Aide Wireless Printing Policy The use of Wireless Networking is not permitted at any site for full client/server networking of Taxwise. Wireless networking, for the purpose
The poor state of SIP endpoint security
 The poor state of SIP endpoint security Kamailio World, 03.04.2014 Henning Westerholt Head of IT Operations Access 1 Agenda Introduction Reasons for security issues, motivation for attackers Past security
The poor state of SIP endpoint security Kamailio World, 03.04.2014 Henning Westerholt Head of IT Operations Access 1 Agenda Introduction Reasons for security issues, motivation for attackers Past security
Router Router Microprocessor controlled traffic direction home router DSL modem Computer Enterprise routers Core routers
 Router Router is a Microprocessor controlled device that forwards data packets across the computer network. It is used to connect two or more data lines from different net works. The function of the router
Router Router is a Microprocessor controlled device that forwards data packets across the computer network. It is used to connect two or more data lines from different net works. The function of the router
Children s Health System. Remote User Policy
 Children s Health System Remote User Policy July 28, 2008 Reason for this Policy This policy defines standards for connecting to the Children s Health System (CHS) network from any remote host. These standards
Children s Health System Remote User Policy July 28, 2008 Reason for this Policy This policy defines standards for connecting to the Children s Health System (CHS) network from any remote host. These standards
LSI Industries AirLink Network Security. Best Practices. System Information 01/31/18. Physical Access. Software Updates. Network Encryption
 LSI Industries AirLink Network Security 01/31/18 Best Practices AirLink can provide all of its basic lighting control services without an internet connection. However, many customers will find that internet
LSI Industries AirLink Network Security 01/31/18 Best Practices AirLink can provide all of its basic lighting control services without an internet connection. However, many customers will find that internet
Palmetto rural telephone cooperative, INC. Network TRANSPARENCY statement
 Palmetto rural telephone cooperative, INC. Network TRANSPARENCY statement Palmetto Rural Telephone Cooperative, Inc. ( PRTC or Company ) provides this Network Transparency Statement in accordance with
Palmetto rural telephone cooperative, INC. Network TRANSPARENCY statement Palmetto Rural Telephone Cooperative, Inc. ( PRTC or Company ) provides this Network Transparency Statement in accordance with
Southwest Arkansas telephone cooperative. Network TRANSPARENCY statement
 Southwest Arkansas telephone cooperative Network TRANSPARENCY statement Southwest Arkansas Telephone Cooperative ( SWATCO or Company ) provides this Network Transparency Statement in accordance with the
Southwest Arkansas telephone cooperative Network TRANSPARENCY statement Southwest Arkansas Telephone Cooperative ( SWATCO or Company ) provides this Network Transparency Statement in accordance with the
RiverStreet Networks Network TRANSPARENCY Statement
 RiverStreet Networks Network TRANSPARENCY Statement RiverStreet Networks ( RiverStreet or Company ) provides this Network Transparency Statement in accordance with the FCC s Restore Internet Freedom Rules
RiverStreet Networks Network TRANSPARENCY Statement RiverStreet Networks ( RiverStreet or Company ) provides this Network Transparency Statement in accordance with the FCC s Restore Internet Freedom Rules
Network TRANSPARENCY statement
 Network TRANSPARENCY statement ND Tel ( NDTC or Company ) provides this Network Transparency Statement in accordance with the FCC s Restore Internet Freedom Rules to ensure that you have sufficient information
Network TRANSPARENCY statement ND Tel ( NDTC or Company ) provides this Network Transparency Statement in accordance with the FCC s Restore Internet Freedom Rules to ensure that you have sufficient information
The WiMAX Technology
 Page 2 Oeconomics of Knowledge, Volume 2, Issue 2, 2Q 2010 The WiMAX Technology Felician ALECU, PhD, University Lecturer Department of Economic Informatics Academy of Economic Studies, Bucharest, Romania
Page 2 Oeconomics of Knowledge, Volume 2, Issue 2, 2Q 2010 The WiMAX Technology Felician ALECU, PhD, University Lecturer Department of Economic Informatics Academy of Economic Studies, Bucharest, Romania
Wilkes Communications, Inc. Network TRANSPARENCY Statement
 Wilkes Communications, Inc. Network TRANSPARENCY Statement Wilkes Communications, Inc. ( Wilkes or Company ) provides this Network Transparency Statement in accordance with the FCC s Restore Internet Freedom
Wilkes Communications, Inc. Network TRANSPARENCY Statement Wilkes Communications, Inc. ( Wilkes or Company ) provides this Network Transparency Statement in accordance with the FCC s Restore Internet Freedom
GO Internet Modem. User Guide
 GO Internet Modem User Guide Follow us go.com.mt 2 Index 1. Filter Installation 04 2. Installing Your Modem 06 Speedtouch 546 Only 08 3. Wired Network Set-up 10 4. Wireless Network Set-up 13 5. Setting
GO Internet Modem User Guide Follow us go.com.mt 2 Index 1. Filter Installation 04 2. Installing Your Modem 06 Speedtouch 546 Only 08 3. Wired Network Set-up 10 4. Wireless Network Set-up 13 5. Setting
VISUAL SUMMARY COMMUNICATION CHANNELS COMMUNICATIONS. Communications and Networks
 Rev.Confirming Pages VISUAL SUMMARY Communications and Networks COMMUNICATIONS COMMUNICATION CHANNELS Communications is the process of sharing data, programs, and information between two or more computers.
Rev.Confirming Pages VISUAL SUMMARY Communications and Networks COMMUNICATIONS COMMUNICATION CHANNELS Communications is the process of sharing data, programs, and information between two or more computers.
Area Covered is small Area covered is large. Data transfer rate is high Data transfer rate is low
 Chapter 15 Networking Concepts 1. Define networking. It is the interconnection of independent computing devices for sharing of information over shared medium. 2. What is the need for networking? / What
Chapter 15 Networking Concepts 1. Define networking. It is the interconnection of independent computing devices for sharing of information over shared medium. 2. What is the need for networking? / What
NINESTAR CONNECT. Network TRANSPARENCY statement
 NINESTAR CONNECT Network TRANSPARENCY statement NineStar Connect ( NineStar Connect or Company ) provides this Network Transparency Statement in accordance with the FCC s Restore Internet Freedom Rules
NINESTAR CONNECT Network TRANSPARENCY statement NineStar Connect ( NineStar Connect or Company ) provides this Network Transparency Statement in accordance with the FCC s Restore Internet Freedom Rules
Livingston Communications. Network TRANSPARENCY statement
 Livingston Communications Network TRANSPARENCY statement Livingston Communications provides this Network Transparency Statement in accordance with the FCC s Restore Internet Freedom Rules to ensure that
Livingston Communications Network TRANSPARENCY statement Livingston Communications provides this Network Transparency Statement in accordance with the FCC s Restore Internet Freedom Rules to ensure that
Dialup Internet Access. Broadband Networks. Broadband Connectivity. Broadband Challenges. Connectivity Options. State of the Art
 Dialup Internet Access Broadband Networks A Practical Guide for Educators Problem - Speed World Wide Wait Telephone lines Using Technology designed for voice not computers Analog Modems are at the limit
Dialup Internet Access Broadband Networks A Practical Guide for Educators Problem - Speed World Wide Wait Telephone lines Using Technology designed for voice not computers Analog Modems are at the limit
54Mbps Pocket Wireless Access Point (WL-330g)
 54Mbps Pocket Wireless Access Point (WL-330g) Copyright 2004 ASUSTeK COMPUTER INC. All Rights Reserved. Contents Conventions... 2 Welcome!... 3 Package contents... 3 System requirements... 3 Device installation...
54Mbps Pocket Wireless Access Point (WL-330g) Copyright 2004 ASUSTeK COMPUTER INC. All Rights Reserved. Contents Conventions... 2 Welcome!... 3 Package contents... 3 System requirements... 3 Device installation...
Network TRANSPARENCY statement
 Network TRANSPARENCY statement Gridley Communications, Inc. ( Gridcom or Company ) an affiliate of Gridley Telephone Co. provides this Network Transparency Statement in accordance with the FCC s Restore
Network TRANSPARENCY statement Gridley Communications, Inc. ( Gridcom or Company ) an affiliate of Gridley Telephone Co. provides this Network Transparency Statement in accordance with the FCC s Restore
CANADIAN VALLEY TELEPHONE. Network TRANSPARENCY statement
 CANADIAN VALLEY TELEPHONE Network TRANSPARENCY statement Canadian Valley Telephone ( Canadian Valley or Company ) provides this Network Transparency Statement in accordance with the FCC s Restore Internet
CANADIAN VALLEY TELEPHONE Network TRANSPARENCY statement Canadian Valley Telephone ( Canadian Valley or Company ) provides this Network Transparency Statement in accordance with the FCC s Restore Internet
Wireless technology Principles of Security
 Wireless technology Principles of Security 1 Wireless technologies 2 Overview This module provides an introduction to the rapidly evolving technology of wireless LANs (WLANs). WLANs redefine the way the
Wireless technology Principles of Security 1 Wireless technologies 2 Overview This module provides an introduction to the rapidly evolving technology of wireless LANs (WLANs). WLANs redefine the way the
MULTIPLE CHOICE. Choose the one alternative that best completes the statement or answers the question.
 CS Chapter 7 Study Guide _ MULTIPLE CHOICE. Choose the one alternative that best completes the statement or answers the question. 1) Throughput, the actual speed of data transfer that is achieved in a
CS Chapter 7 Study Guide _ MULTIPLE CHOICE. Choose the one alternative that best completes the statement or answers the question. 1) Throughput, the actual speed of data transfer that is achieved in a
Internet Access Technologies
 Lecture 4: Local Loop Technologies, Internet Access and Leased Lines Dr. Mohammed Hawa Electrical Engineering Department University of Jordan EE426: Communication Networks Internet Access Technologies
Lecture 4: Local Loop Technologies, Internet Access and Leased Lines Dr. Mohammed Hawa Electrical Engineering Department University of Jordan EE426: Communication Networks Internet Access Technologies
FOOTHILLS COMMUNICATIONS. Network TRANSPARENCY statement
 FOOTHILLS COMMUNICATIONS Network TRANSPARENCY statement Foothills Communications ( Foothills or Company ) provides this Network Transparency Statement in accordance with the FCC s Restore Internet Freedom
FOOTHILLS COMMUNICATIONS Network TRANSPARENCY statement Foothills Communications ( Foothills or Company ) provides this Network Transparency Statement in accordance with the FCC s Restore Internet Freedom
VDSL Router 4 Port Wi-Fi Dual Band (NT3BB-4PVWN-147) Quick Installation Guide
 VDSL Router 4 Port Wi-Fi Dual Band (NT3BB-4PVWN-147) Quick Installation Guide 1. Packing List The following table lists the items in the product package. Item Quantity VDSL Router 1 Power Adapter 1 RJ
VDSL Router 4 Port Wi-Fi Dual Band (NT3BB-4PVWN-147) Quick Installation Guide 1. Packing List The following table lists the items in the product package. Item Quantity VDSL Router 1 Power Adapter 1 RJ
Unit title: Mobile Technology: Device Connectivity (SCQF level 5) Outcome 1
 1 Outcome 1 A description of mobile device internet connectivity using two current Wi-Fi methods. A description of mobile device internet connectivity using two current GSM mobile telephony methods. A
1 Outcome 1 A description of mobile device internet connectivity using two current Wi-Fi methods. A description of mobile device internet connectivity using two current GSM mobile telephony methods. A
How to Configure a Hybrid WAN in Parallel to An Existing Traditional Wan Infrastructure
 Table of Contents Introducing Hybrid WAN The WAN Evolution What is a Traditional Private WAN? Example IP Addressing What is a Hybrid WAN? SD-WAN - Centrally Managed Hybrid WAN Hybrid WAN Example Hybrid
Table of Contents Introducing Hybrid WAN The WAN Evolution What is a Traditional Private WAN? Example IP Addressing What is a Hybrid WAN? SD-WAN - Centrally Managed Hybrid WAN Hybrid WAN Example Hybrid
Network Transparency Statement
 Network Transparency Statement September 4 th, 2018 Total Highspeed Internet Solutions Network Transparency Statement Total Highspeed Internet Solutions ( Company ) provides this Network Transparency Statement
Network Transparency Statement September 4 th, 2018 Total Highspeed Internet Solutions Network Transparency Statement Total Highspeed Internet Solutions ( Company ) provides this Network Transparency Statement
Technology in Action. Chapter Topics. Participation Question. Participation Question 8/17/11. Chapter 7 Networking: Connecting Computing Devices
 Technology in Action Chapter 7 Networking: Connecting Computing Devices 1 2 Chapter Topics Networking fundamentals Network architecture Network components Peer-to-peer networks Ethernet networks Power-line
Technology in Action Chapter 7 Networking: Connecting Computing Devices 1 2 Chapter Topics Networking fundamentals Network architecture Network components Peer-to-peer networks Ethernet networks Power-line
Mapping Maryland s Broadband Inventory: The Maryland Broadband Mapping Initiative. David Sides Center for GIS at Towson University
 Mapping Maryland s Broadband Inventory: The Maryland Broadband Mapping Initiative David Sides Center for GIS at Towson University Maryland Broadband Mapping Initiative Funded Under and By: American Reinvestment
Mapping Maryland s Broadband Inventory: The Maryland Broadband Mapping Initiative David Sides Center for GIS at Towson University Maryland Broadband Mapping Initiative Funded Under and By: American Reinvestment
Chapter 1: introduction
 Chapter 1: introduction our goal: v get feel and terminology v more depth, detail later in course v approach: use Internet as example overview: v what s the Internet? v what s a protocol? v edge; hosts,
Chapter 1: introduction our goal: v get feel and terminology v more depth, detail later in course v approach: use Internet as example overview: v what s the Internet? v what s a protocol? v edge; hosts,
Remote Access Techniques and Issues
 Remote Access Techniques and Issues Bill Klein Networking and Telecommunications Services 10/25/2006 klein@ku.edu Introduction Presenter bio The Information Services "triad" Information repositories Libraries
Remote Access Techniques and Issues Bill Klein Networking and Telecommunications Services 10/25/2006 klein@ku.edu Introduction Presenter bio The Information Services "triad" Information repositories Libraries
Hart telephone company. Network TRANSPARENCY statement
 Hart telephone company Network TRANSPARENCY statement Hart Telephone Company ( HTC or Company ) provides this Network Transparency Statement in accordance with the FCC s Restore Internet Freedom Rules
Hart telephone company Network TRANSPARENCY statement Hart Telephone Company ( HTC or Company ) provides this Network Transparency Statement in accordance with the FCC s Restore Internet Freedom Rules
Modern IP Communication bears risks
 Modern IP Communication bears risks How to protect your business telephony from cyber attacks Voice-over-IP (VoIP) provides many new features over PSTN. However, the interconnection with your IT infrastructure
Modern IP Communication bears risks How to protect your business telephony from cyber attacks Voice-over-IP (VoIP) provides many new features over PSTN. However, the interconnection with your IT infrastructure
Wireless LAN Security (RM12/2002)
 Information Technology in Education Project Reference Materials Wireless LAN Security (RM12/2002) Infrastructure Division Education Department The Government of HKSAR www.ited.ed.gov.hk December 2002 For
Information Technology in Education Project Reference Materials Wireless LAN Security (RM12/2002) Infrastructure Division Education Department The Government of HKSAR www.ited.ed.gov.hk December 2002 For
Networking Jamie Tees
 Ethernet is the main networking technology, UTP (Unshielded Twisted Pair) cabling is the main networking cable types, this cabling uses RJ-45 connectors either end. While UTP is the main type we have STP
Ethernet is the main networking technology, UTP (Unshielded Twisted Pair) cabling is the main networking cable types, this cabling uses RJ-45 connectors either end. While UTP is the main type we have STP
Broadband Internet Access Disclosure
 Broadband Internet Access Disclosure This document provides information about the network practices, performance characteristics, and commercial terms applicable broadband Internet access services provided
Broadband Internet Access Disclosure This document provides information about the network practices, performance characteristics, and commercial terms applicable broadband Internet access services provided
Study Guide. Module Three
 Exam Three will draw questions four content areas: our textbook, our assignments, the Rackspace Web Hosting Tutorial, and our class lectures. The purpose of this guide is to help you focus your exam preparations.
Exam Three will draw questions four content areas: our textbook, our assignments, the Rackspace Web Hosting Tutorial, and our class lectures. The purpose of this guide is to help you focus your exam preparations.
Pioneer Communications Internet Services Disclosure
 Pioneer Communications Internet Services Disclosure Pioneer Communications ( Pioneer ) is the leading Internet service provider for Southwest Kansas communities with a reputation for excellence that goes
Pioneer Communications Internet Services Disclosure Pioneer Communications ( Pioneer ) is the leading Internet service provider for Southwest Kansas communities with a reputation for excellence that goes
Olli-Pekka Hiironen, Antti Pietiläinen, Arne Nylund, Nokia. 1 Privacy in EPON.PPT/ / OPH, AP, AN IEEE802.3ah Ethernet in the First Mile
 Olli-Pekka Hiironen, Antti Pietiläinen, Arne Nylund, Nokia 1 Privacy in EPON.PPT/ 20.-22.5.2002 / OPH, AP, AN IEEE802.3ah Ethernet in the First Mile Carlos Ribeiro, CTBC Telecom Kent G. McCammon, SBC Yukihiro
Olli-Pekka Hiironen, Antti Pietiläinen, Arne Nylund, Nokia 1 Privacy in EPON.PPT/ 20.-22.5.2002 / OPH, AP, AN IEEE802.3ah Ethernet in the First Mile Carlos Ribeiro, CTBC Telecom Kent G. McCammon, SBC Yukihiro
2) INSERT THE SETUP CD
 1 2 3 1) POWER UP After you have correctly connected your Range Extender to an available Ethernet port on your Network, please power on the Extender and a PC that is also on the netw ork.. 2) INSERT THE
1 2 3 1) POWER UP After you have correctly connected your Range Extender to an available Ethernet port on your Network, please power on the Extender and a PC that is also on the netw ork.. 2) INSERT THE
Class X Subject : IT (Vocational) Chapter -1 Ouestion / Answer
 Class X Subject : IT (Vocational) Chapter -1 Ouestion / Answer Q1 What is a computer network? A computer network, often simply referred to as a network, is a collection of computers and other hardware
Class X Subject : IT (Vocational) Chapter -1 Ouestion / Answer Q1 What is a computer network? A computer network, often simply referred to as a network, is a collection of computers and other hardware
An Overview. 12/22/2011 Hardev Singh Manager (BB-NOC) MTNL Delhi
 Broadband Technology An Overview 12/22/2011 Hardev Singh Manager (BB-NOC) MTNL Delhi 1 1 2 3 4 5 6 7 8 9 * 8 # 1 2 3 4 5 6 7 8 9 * 8 # Typical Narrowband (voice) setup Local Exchange PSTNSwitch telephone
Broadband Technology An Overview 12/22/2011 Hardev Singh Manager (BB-NOC) MTNL Delhi 1 1 2 3 4 5 6 7 8 9 * 8 # 1 2 3 4 5 6 7 8 9 * 8 # Typical Narrowband (voice) setup Local Exchange PSTNSwitch telephone
NETWORKS AND THE EFFECTS OF USING THEM (Work Sheet)
 NETWORKS AND THE EFFECTS OF USING THEM (Work Sheet) 1. An organization is planning to train all staff online rather than video-conference. Describe what is meant by a web conference. 2. Explain the differences
NETWORKS AND THE EFFECTS OF USING THEM (Work Sheet) 1. An organization is planning to train all staff online rather than video-conference. Describe what is meant by a web conference. 2. Explain the differences
Chapter 11: Networks
 Chapter 11: Networks Devices in a Small Network Small Network A small network can comprise a few users, one router, one switch. A Typical Small Network Topology looks like this: Device Selection Factors
Chapter 11: Networks Devices in a Small Network Small Network A small network can comprise a few users, one router, one switch. A Typical Small Network Topology looks like this: Device Selection Factors
WAN Technology & Design. Dr. Nawaporn Wisitpongphan
 WAN Technology & Design Dr. Nawaporn Wisitpongphan 1 WAN Connection Modules 2 WAN Comparison 3 Integrated Services Digital Network (ISDN) All-digital phone line connection Technology since 1980s Allow
WAN Technology & Design Dr. Nawaporn Wisitpongphan 1 WAN Connection Modules 2 WAN Comparison 3 Integrated Services Digital Network (ISDN) All-digital phone line connection Technology since 1980s Allow
White Paper / S4 Access Switch
 White Paper / S4 Access Switch Teleste S4 Access Switch Secure Subscriber Connections in an Open-Access FttH Networking Topology Teleste S4 Access Switch Secure Subscriber Connections in an Open-Access
White Paper / S4 Access Switch Teleste S4 Access Switch Secure Subscriber Connections in an Open-Access FttH Networking Topology Teleste S4 Access Switch Secure Subscriber Connections in an Open-Access
Chapter 9 Introduction to Networks
 Chapter 9 Introduction to Networks 9.1 Uses of a network Networks are used in many situations. We can see networks in places like offices, airports and factories. In fact we use networks in many situations
Chapter 9 Introduction to Networks 9.1 Uses of a network Networks are used in many situations. We can see networks in places like offices, airports and factories. In fact we use networks in many situations
BEC 8920AC Ultimum The Ultimate Residential Gateway with ac VDSL2/ADSL2+/Bonded/FTTH Quick Start Guide
 BEC 8920AC Ultimum The Ultimate Residential Gateway with 802.11ac VDSL2/ADSL2+/Bonded/FTTH Quick Start Guide BEC 8920AC The Ultimate Residential Gateway w/ 802.11ac PLEASE READ THE QUICK START GUIDE AND
BEC 8920AC Ultimum The Ultimate Residential Gateway with 802.11ac VDSL2/ADSL2+/Bonded/FTTH Quick Start Guide BEC 8920AC The Ultimate Residential Gateway w/ 802.11ac PLEASE READ THE QUICK START GUIDE AND
Billion BiPAC 7700NR2. Setup Guide
 Billion BiPAC 7700NR2 Setup Guide Modem reference & light status sheet On the front of your modem you will notice a number of lights. The below table explains what each of these lights mean: LABEL ACTION
Billion BiPAC 7700NR2 Setup Guide Modem reference & light status sheet On the front of your modem you will notice a number of lights. The below table explains what each of these lights mean: LABEL ACTION
CSC Introduction to Computers and Their Applications. Background
 CSC 170 - Introduction to Computers and Their Applications Lecture 7 The Internet Background The history of the Internet begins in 1957. In a response to the Soviet Union launching Sputnik, the first man-made
CSC 170 - Introduction to Computers and Their Applications Lecture 7 The Internet Background The history of the Internet begins in 1957. In a response to the Soviet Union launching Sputnik, the first man-made
How to successfully set up your service.
 CenturyLink Business VoIP How to successfully set up your service. Onboarding process for Business VoIP This guide will review the steps needed to get you up and running. Welcome to CenturyLink Business
CenturyLink Business VoIP How to successfully set up your service. Onboarding process for Business VoIP This guide will review the steps needed to get you up and running. Welcome to CenturyLink Business
HG531 V1 300Mbps Wireless ADSL2+ Router Product Description. Issue _01 HUAWEI TECHNOLOGIES CO., LTD.
 HG531 V1 300Mbps Wireless ADSL2+ Router Issue 203275_01 HUAWEI TECHNOLOGIES CO., LTD. Copyright Huawei Technologies Co., Ltd. 2013. All rights reserved. No part of this document may be reproduced or transmitted
HG531 V1 300Mbps Wireless ADSL2+ Router Issue 203275_01 HUAWEI TECHNOLOGIES CO., LTD. Copyright Huawei Technologies Co., Ltd. 2013. All rights reserved. No part of this document may be reproduced or transmitted
IT114 NETWORK+ Learning Unit 1 Objectives: 1, 2 Time In-Class Time Out-Of-Class Hours 2-3. Lectures: Course Introduction and Overview
 IT114 NETWORK+ Course Objectives Upon successful completion of this course, the student will be able to: 1. Identify the devices and elements of computer networks; 2. Diagram network models using the appropriate
IT114 NETWORK+ Course Objectives Upon successful completion of this course, the student will be able to: 1. Identify the devices and elements of computer networks; 2. Diagram network models using the appropriate
Application Example (Standalone EAP)
 Application Example (Standalone EAP) CHAPTERS 1. Determine the Network Requirements 2. Build the Network Topology 3. Log In to the EAP 4. Configure the EAP 5. Test the Network This guide applies to: EAP225-Outdoor
Application Example (Standalone EAP) CHAPTERS 1. Determine the Network Requirements 2. Build the Network Topology 3. Log In to the EAP 4. Configure the EAP 5. Test the Network This guide applies to: EAP225-Outdoor
AiM User Manual. Wi-Fi Configuration. Release 1.01
 AiM User Manual Wi-Fi Configuration Release 1.01 1 Wi-Fi configuration Your AiM device Wi-Fi connectivity is disabled by default and must be enabled via a USB connection or on the device menu. Your AiM
AiM User Manual Wi-Fi Configuration Release 1.01 1 Wi-Fi configuration Your AiM device Wi-Fi connectivity is disabled by default and must be enabled via a USB connection or on the device menu. Your AiM
31270 Networking Essentials Focus, Pre-Quiz, and Sample Exam Answers
 31270 Networking Essentials Focus, Pre-Quiz, and Sample Exam Answers CONTENTS Focus Questions... 2 Chapter 1: Explore the Network... 2 Chapter 2: Configure a Network Operating System... 5 Chapter 3: Network
31270 Networking Essentials Focus, Pre-Quiz, and Sample Exam Answers CONTENTS Focus Questions... 2 Chapter 1: Explore the Network... 2 Chapter 2: Configure a Network Operating System... 5 Chapter 3: Network
Chapter 3. Wired and Wireless Communication. What You Will Learn... Computers Are Your Future. What You Will Learn...
 What You Will Learn... Computers Are Your Future Chapter 3 The definition of bandwidth The bandwidth needs of a typical user How modems change digital signals into analog Transmission media and methods
What You Will Learn... Computers Are Your Future Chapter 3 The definition of bandwidth The bandwidth needs of a typical user How modems change digital signals into analog Transmission media and methods
Several types of DSL technology have implemented nowadays and adopted by PLANET broadband solutions to fulfill customer s needs:
 Broadband Communication What is xdsl? xdsl is a family of technologies that provides digital data transmission over the wires of a local telephone network. DSL originally stood for digital subscriber loop,
Broadband Communication What is xdsl? xdsl is a family of technologies that provides digital data transmission over the wires of a local telephone network. DSL originally stood for digital subscriber loop,
COMPUTER SKILLS COMP101
 COMPUTER SKILLS COMP101 Chapter 4 Introduction to Computer Networks Definitions and Terminologies Computer Network A network consists of two or more computers that are linked in order to share resources
COMPUTER SKILLS COMP101 Chapter 4 Introduction to Computer Networks Definitions and Terminologies Computer Network A network consists of two or more computers that are linked in order to share resources
Web Cash Fraud Prevention Best Practices
 Web Cash Fraud Prevention Best Practices Tips on what you can do to prevent Online fraud. This document provides best practices to avoid or reduce exposure to fraud. You can use it to educate your Web
Web Cash Fraud Prevention Best Practices Tips on what you can do to prevent Online fraud. This document provides best practices to avoid or reduce exposure to fraud. You can use it to educate your Web
Introduction to Information Technology Turban, Rainer and Potter John Wiley & Sons, Inc. Copyright 2005
 Introduction to Information Technology Turban, Rainer and Potter John Wiley & Sons, Inc. Copyright 2005 Network and Telecommunications Basics Chapter Outline The telecommunications system Network services
Introduction to Information Technology Turban, Rainer and Potter John Wiley & Sons, Inc. Copyright 2005 Network and Telecommunications Basics Chapter Outline The telecommunications system Network services
Chapter 8 Networking and Digital Communication
 Tomorrow s Technology and You 8/e George Beekman Michael J. Quinn Networking and Digital Communication 2008 Prentice-Hall, Inc. Slide 1 A computer network is any system of two or more computers that are
Tomorrow s Technology and You 8/e George Beekman Michael J. Quinn Networking and Digital Communication 2008 Prentice-Hall, Inc. Slide 1 A computer network is any system of two or more computers that are
Figure 4-6: The Router with the Internet Connection is connected through the Internet Port
 8. Connect a standard Ethernet network cable to the Broadband Router s Internet port. Then, connect the other end of the Ethernet cable to one of the numbered Ethernet ports on your other router. Figure
8. Connect a standard Ethernet network cable to the Broadband Router s Internet port. Then, connect the other end of the Ethernet cable to one of the numbered Ethernet ports on your other router. Figure
Objectives. Learn how computers are connected. Become familiar with different types of transmission media
 Objectives Learn how computers are connected Become familiar with different types of transmission media Learn the differences between guided and unguided media Learn how protocols enable networking 2 Objectives
Objectives Learn how computers are connected Become familiar with different types of transmission media Learn the differences between guided and unguided media Learn how protocols enable networking 2 Objectives
Choose an internet connection to suit your business
 Choose an internet connection to suit your business With an ever increasing demand for bandwidth, your internet connection has never been so important to your business. Whether you re a small business
Choose an internet connection to suit your business With an ever increasing demand for bandwidth, your internet connection has never been so important to your business. Whether you re a small business
E-companion. Quiz for IT-knowledge
 E-companion Quiz for IT-knowledge 1. The is used in combination with other keys to perform shortcuts and special tasks. A) Control (Ctrl) key B) Function key C) Toggle key D) Windows key 2. is the place
E-companion Quiz for IT-knowledge 1. The is used in combination with other keys to perform shortcuts and special tasks. A) Control (Ctrl) key B) Function key C) Toggle key D) Windows key 2. is the place
Wireless Attacks and Countermeasures
 Wireless Attacks and Countermeasures Wireless Network Technology Wireless network refers to any type of computer network which is wireless, and is commonly associated with a network whose interconnections
Wireless Attacks and Countermeasures Wireless Network Technology Wireless network refers to any type of computer network which is wireless, and is commonly associated with a network whose interconnections
Week 1 Computer Networking 1 ( Internet, DSL, Fiber to Home )
 Week 1 Computer Networking 1 ( Internet, DSL, Fiber to Home ) Instructor : Nasmee Salaeh Email : nasmees@gmail.com Keyword Dial up Refers to connecting a device to a network via a modem and a public telephone
Week 1 Computer Networking 1 ( Internet, DSL, Fiber to Home ) Instructor : Nasmee Salaeh Email : nasmees@gmail.com Keyword Dial up Refers to connecting a device to a network via a modem and a public telephone
Home-Mobile. The Cast Devices. The Cast Network Related (2) The Cast Network Related. Voice over IP (VoIP) Dr. Hayden Kwok-Hay So
 The Cast Devices Home-Mobile Desktop Computer Mostly data Wired network Standard Telephone Mostly voice Wired phone line CCST9015 6th Oct, 2010 Dr. Hayden Kwok-Hay So Notebook Computer Mostly data Wireless
The Cast Devices Home-Mobile Desktop Computer Mostly data Wired network Standard Telephone Mostly voice Wired phone line CCST9015 6th Oct, 2010 Dr. Hayden Kwok-Hay So Notebook Computer Mostly data Wireless
Setting up the Linksys WRT32X
 Setting up the Linksys WRT32X Share the Article: The Linksys WRT32X AC3200 Dual-Band Wi-Fi Gaming Router with Killer Prioritization Engine uses the Killer Prioritization Engine to provide the best home
Setting up the Linksys WRT32X Share the Article: The Linksys WRT32X AC3200 Dual-Band Wi-Fi Gaming Router with Killer Prioritization Engine uses the Killer Prioritization Engine to provide the best home
Billion BiPAC 7800VDOX. Setup Guide
 Billion BiPAC 7800VDOX Setup Guide MODEM REFERENCE & LIGHT STATUS SHEET On the front of your modem you will notice a number of lights. The below table explains what each of these lights mean: LABEL ACTION
Billion BiPAC 7800VDOX Setup Guide MODEM REFERENCE & LIGHT STATUS SHEET On the front of your modem you will notice a number of lights. The below table explains what each of these lights mean: LABEL ACTION
Chapter 15 Networks. Chapter Goals. Networking. Chapter Goals. Networking. Networking. Computer network. Node (host) Any device on a network
 Chapter Goals Chapter 15 Networks Describe the core issues related to computer networks List various types of networks and their characteristics Explain various topologies of local-area networks Explain
Chapter Goals Chapter 15 Networks Describe the core issues related to computer networks List various types of networks and their characteristics Explain various topologies of local-area networks Explain
Special Provision No. 683S27 June 2017
 GATEWAY ROUTERS - Item No. Special Provision No. 683S27 June 2017 1. SCOPE This Special Provision covers the requirements for the installation of Gateway Routers with integrated digital subscriber line
GATEWAY ROUTERS - Item No. Special Provision No. 683S27 June 2017 1. SCOPE This Special Provision covers the requirements for the installation of Gateway Routers with integrated digital subscriber line
1-Port 10/100/1000T 802.3at PoE+ Ethernet to VDSL2 Converter
 1-Port 10/100/1000T 802.3at + Ethernet to Converter Physical Ports 1-port 10/100/1000BASE-T RJ45 with IEEE 802.3af/802.3at Injector 1 RJ11, connector for xdsl port with or ADSL2+ connection Plus High Performance
1-Port 10/100/1000T 802.3at + Ethernet to Converter Physical Ports 1-port 10/100/1000BASE-T RJ45 with IEEE 802.3af/802.3at Injector 1 RJ11, connector for xdsl port with or ADSL2+ connection Plus High Performance
Computer Communications and Network Basics p. 1 Overview of Computer Communications and Networking p. 2 What Does Computer Communications and
 Computer Communications and Network Basics p. 1 Overview of Computer Communications and Networking p. 2 What Does Computer Communications and Networking Technologies Mean? p. 3 What Is a Computer Network?
Computer Communications and Network Basics p. 1 Overview of Computer Communications and Networking p. 2 What Does Computer Communications and Networking Technologies Mean? p. 3 What Is a Computer Network?
Access Networks. Based on: Optical Networks, a Practical Perspective (2 nd Edition) Chapter 11, by R.Ramaswami, K.N.Sivarajan
 Access Networks Based on: Optical Networks, a Practical Perspective (2 nd Edition) Chapter 11, by R.Ramaswami, K.N.Sivarajan Access Network! The network feeding the metro (and core) networks by gathering
Access Networks Based on: Optical Networks, a Practical Perspective (2 nd Edition) Chapter 11, by R.Ramaswami, K.N.Sivarajan Access Network! The network feeding the metro (and core) networks by gathering
Configuring your Home Wireless Network
 Configuring your Home Wireless Network Questions How many of you have more than one computer at home? How many of you connect to the Internet using broadband (Cable or DSL) How many already have a home
Configuring your Home Wireless Network Questions How many of you have more than one computer at home? How many of you connect to the Internet using broadband (Cable or DSL) How many already have a home
Digital Entertainment. Networking Made Easy
 Digital Entertainment 2003 by TiVo Inc. Reproduction in whole or in part without written permission is prohibited. All rights reserved. Printed in the USA. TiVo, TiVo Central, and TiVolution are registered
Digital Entertainment 2003 by TiVo Inc. Reproduction in whole or in part without written permission is prohibited. All rights reserved. Printed in the USA. TiVo, TiVo Central, and TiVolution are registered
INTRODUCTION TO ICT.
 INTRODUCTION TO ICT. (Introducing Basic Network Concepts) Lecture # 24-25 By: M.Nadeem Akhtar. Department of CS & IT. URL: https://sites.google.com/site/nadeemcsuoliict/home/lectures 1 INTRODUCTION TO
INTRODUCTION TO ICT. (Introducing Basic Network Concepts) Lecture # 24-25 By: M.Nadeem Akhtar. Department of CS & IT. URL: https://sites.google.com/site/nadeemcsuoliict/home/lectures 1 INTRODUCTION TO
SOLUTION GUIDE. Connecting the Gigabit Broadband Infrastructure Broadband Access Solutions. broadcom.com
 SOLUTION GUIDE Connecting the Gigabit Broadband Infrastructure Broadband Access Solutions broadcom.com 1 The Need for Gigabit Broadband Global Internet traffic continues to grow by leaps and bounds. By
SOLUTION GUIDE Connecting the Gigabit Broadband Infrastructure Broadband Access Solutions broadcom.com 1 The Need for Gigabit Broadband Global Internet traffic continues to grow by leaps and bounds. By
Access Connections 5.1 for Windows Vista: User Guide
 Access Connections 5.1 for Windows Vista: User Guide Access Connections 5.1 for Windows Vista: User Guide Note Before using this information and the product it supports, read the general information in
Access Connections 5.1 for Windows Vista: User Guide Access Connections 5.1 for Windows Vista: User Guide Note Before using this information and the product it supports, read the general information in
Redundancy for Corporate Broadband WHITE PAPER
 Redundancy for Corporate Broadband WHITE PAPER Introduction Over the past twenty years, broadband service providers have been using different mediums to deliver their services. From wireless to wired (fiber,
Redundancy for Corporate Broadband WHITE PAPER Introduction Over the past twenty years, broadband service providers have been using different mediums to deliver their services. From wireless to wired (fiber,
Home Networking. Kaikham Onedamdy Rachel Krajc Kareem Sumner
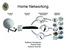 Home Networking Kaikham Onedamdy Rachel Krajc Kareem Sumner Agenda Introduction Home Networking Trends Methodology Design Goals Assumptions Needs Analysis Geographic Scope Network Users Proposed Solution
Home Networking Kaikham Onedamdy Rachel Krajc Kareem Sumner Agenda Introduction Home Networking Trends Methodology Design Goals Assumptions Needs Analysis Geographic Scope Network Users Proposed Solution
VR1600v (NBN FTTN & NBN FTTB) Windows 10
 (NBN FTTN & NBN FTTB) Windows 10 IMPORTANT MESSAGE Your modem has already been pre-configured, you do not need to follow each step of the set-up guide but should retain this document in case you need to
(NBN FTTN & NBN FTTB) Windows 10 IMPORTANT MESSAGE Your modem has already been pre-configured, you do not need to follow each step of the set-up guide but should retain this document in case you need to
ON-LINE EXPERT SUPPORT THROUGH VPN ACCESS
 ON-LINE EXPERT SUPPORT THROUGH VPN ACCESS P. Fidry, V. Rakotomanana, C. Ausanneau Pierre.fidry@alcatel-lucent.fr Alcatel-Lucent, Centre de Villarceaux, 91620, Nozay, France Abstract: As a consequence of
ON-LINE EXPERT SUPPORT THROUGH VPN ACCESS P. Fidry, V. Rakotomanana, C. Ausanneau Pierre.fidry@alcatel-lucent.fr Alcatel-Lucent, Centre de Villarceaux, 91620, Nozay, France Abstract: As a consequence of
