FC-SP and DHCHAP. Fibre Channel Security Protocol. Send documentation comments to CHAPTER
|
|
|
- Sheila Cain
- 6 years ago
- Views:
Transcription
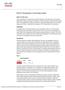
1 30 CHAPTER Fibre Channel Security Protocol () capabilities provide switch-switch and host-switch authentication to overcome security challenges for enterprise-wide fabrics. Diffie-Hellman Challenge Handshake Authentication Protocol (DHCHAP) is an protocol that provides authentication between Cisco MDS 9000 Family switches and other devices. It consists of the CHAP protocol combined with the Diffie-Hellman exchange. This chapter includes the following sections: Fibre Channel Security Protocol, page 30-1 Configuring DHCHAP Authentication, page 30-3 Fibre Channel Security Protocol All switches in the Cisco MDS 9000 Family enable fabric-wide authentication from one switch to another switch, or from a switch to a host. These switch and host authentications are performed locally or remotely in each fabric. As storage islands are consolidated and migrated to enterprise-wide fabrics new security challenges arise. The approach of securing storage islands cannot always be guaranteed in enterprise-wide fabrics. For example, in a campus environment with geographically distributed switches someone could maliciously interconnect incompatible switches or you could accidentally do so, resulting in Inter-Switch Link (ISL) isolation and link disruption. This need for physical security is addressed by switches in the Cisco MDS 9000 Family (see Figure 30-1). 30-1
2 Fibre Channel Security Protocol Chapter 30 Figure 30-1 Switch and Host Authentication Trusted hosts RADIUS server (DH-CHAP) Unauthorized hosts and switches (DH-CHAP) Storage Subsytems Fibre Channel host bus adapters (HBAs) with appropriate firmware and drivers are required for host-switch authentication. About DHCHAP DHCHAP is an authentication protocol that authenticates the devices connecting to a switch. Fibre Channel authentication allows only trusted devices to be added to a fabric, thus preventing unauthorized devices from accessing the switch. The terms are used interchangeably in this chapter. DHCHAP is a mandatory password-based, key-exchange authentication protocol that supports both switch-to-switch and host-to-switch authentication. DHCHAP negotiates hash algorithms and Diffie-Hellman groups before performing authentication. It supports MD5 and SHA-1 algorithm-based authentication. Configuring the DHCHAP feature requires the ENTERPRISE_PKG license (see Chapter 9, Obtaining and Installing Licenses ). 30-2
3 Chapter 30 Configuring DHCHAP Authentication DHCHAP Compatibility with Existing Cisco MDS Features This sections identifies the impact of configuring the DHCHAP feature along with existing Cisco MDS features: PortChannel interfaces If DHCHAP is enabled for ports belonging to a PortChannel, DHCHAP authentication is performed at the physical interface level, not at the PortChannel level. FCIP interfaces The DHCHAP protocol works with the FCIP interface just as it would with a physical interface. Port security or fabric binding Fabric binding policies are enforced based on identities authenticated by DHCHAP. VSANs DHCHAP authentication is not done on a per-vsan basis. High availability DHCHAP authentication works transparently with existing HA features. Configuring DHCHAP Authentication To configure DHCHAP authentication using the local password database, follow these steps: Step 5 Step 6 Enable DHCHAP. Identify and configure the DHCHAP authentication modes. Configure the hash algorithm and DH group. Configure the DHCHAP password for the local switch and other switches in the fabric. Configure the DHCHAP timeout value for reauthentication. Verify the DHCHAP configuration. Enabling DHCHAP By default, the DHCHAP feature is disabled in all switches in the Cisco MDS 9000 Family. You must explicitly enable the DHCHAP feature to access the configuration and verification commands for fabric authentication. When you disable this feature, all related configurations are automatically discarded. To enable DHCHAP and, follow these steps: From Fabric Manager, choose Switches > Security >. You see the configuration in the Information pane. From Device Manager, choose Security >. You see the Enable dialog box. Click Yes to enable for this switch. Choose the Control tab in Fabric Manager. You see the enable state for all switches in the fabric. Set the Command drop-down menu to enable for all switches that you want to enable on. 30-3
4 Configuring DHCHAP Authentication Chapter 30 Click the Apply Changes icon to enable on the selected switches. Configuring DHCHAP Authentication Modes The DHCHAP authentication status for each interface depends on the configured DHCHAP port mode. When the DHCHAP feature is enabled in a switch, each Fibre Channel interface or FCIP interface may be configured to be in one of four DHCHAP port modes: On During switch initialization, if the connecting device supports DHCHAP authentication, the software performs the authentication sequence. If the connecting device does not support DHCHAP authentication, the software moves the link to an isolated state. AutoActive During switch initialization, if the connecting device supports DHCHAP authentication, the software performs the authentication sequence. If the connecting device does not support DHCHAP authentication, the software continues with the rest of the initialization sequence. AutoPassive (default) The switch does not initiate DHCHAP authentication, but participates in DHCHAP authentication if the connecting device initiates DHCHAP authentication. Off The switch does not support DHCHAP authentication. Authentication messages sent to such ports return error messages to the initiating switch. Whenever DHCHAP port mode is changed to a mode other than the Off mode, reauthentication is performed. Table 30-1 identifies the switch-to-switch authentication behavior between two Cisco MDS switches in various modes. Table 30-1 Switch N DHCHAP Modes on auto-active auto-passive off DHCHAP Authentication Status Between Two MDS Switches Switch 1 DHCHAP Modes on auto-active auto-passive off authentication is performed. Link is brought down. authentication is performed. authentication is performed. authentication is not performed. authentication is not performed. Link is brought down. authentication is not performed. 30-4
5 Chapter 30 Configuring DHCHAP Authentication To configure the DHCHAP port authentication mode, follow these steps: From Fabric Manager, choose Switches > Interfaces > FC Physical. You see the configuration in the Information pane. From Device Manager, choose Security >. You see the Configuration dialog box. Choose the tab. You see the DHCHAP authentication mode for each interface. Set the Mode drop-down menu to the DHCHAP authentication mode you want to configure for that interface. Click the Apply Changes icon in Fabric Manager or click Apply in Device Manager to save these DHCHAP port mode settings. Changing the DHCHAP Hash Algorithm Cisco MDS switches support a default hash algorithm priority list of MD5 followed by SHA-1 for DHCHAP authentication. Tip If you change the hash algorithm priority list, then change it globally for all switches in the fabric. Caution RADIUS and TACACS+ protocols always use MD5 for CHAP authentication. Using SHA-1 as the hash algorithm may prevent RADIUS and TACACS+ usage even if these AAA protocols are enabled for DHCHAP authentication. To change the DHCHAP hash algorithm priority list using Fabric Manager, follow these steps: Choose Switches > Security >. You see the configuration in the Information pane. Choose the General/Password tab. You see the DHCHAP general settings mode for each switch. Change the HashList for each switch in the fabric. Click the Apply Changes icon to save the updated hash algorithm priority list or click the Undo Changes icon to discard any unsaved changes. Changing DHCHAP Group Settings All switches in the Cisco MDS Family support all DHCHAP groups specified in the standard: 0 (null DH group, which does not perform the Diffie-Hellman exchange), 1, 2, 3, or 4. Tip If you change the DH group configuration, change it globally for all switches in the fabric. 30-5
6 Configuring DHCHAP Authentication Chapter 30 To change the DH group list using Fabric Manager, follow these steps: Choose Switches > Security >. You see the configuration in the Information pane. Choose the General/Password tab. You see the DHCHAP general settings mode for each switch. Change the GroupList for each switch in the fabric. Click the Apply Changes icon to save the updated DH group lists or click the Undo Changes icon to discard any unsaved changes. Configuring the DHCHAP Password DHCHAP authentication in each direction requires a shared secret password between the connected devices. To do this, you can use one of three approaches to manage passwords for all switches in the fabric that participate in DHCHAP. Approach 1 Use the same password for all switches in the fabric. This is the simplest approach. When you add a new switch, you use the same password to authenticate that switch in this fabric. It is also the most vulnerable approach if someone from the outside maliciously attempts to access any one switch in the fabric. Approach 2 Use a different password for each switch and maintain that password list in each switch in the fabric. When you add a new switch, you create a new password list and update all switches with the new list. Accessing one switch yields the password list for all switches in that fabric. Approach 3 Use different passwords for different switches in the fabric. When you add a new switch, multiple new passwords corresponding to each switch in the fabric must be generated and configured in each switch. Even if one switch is compromised, the password of other switches are still protected. This approach requires considerable password maintenance by the user. All passwords are restricted to 64 alphanumeric characters and can be changed, but not deleted. Tip We recommend using RADIUS or TACACS+ for fabrics with more than five switches. If you need to use a local password database, you can continue to do so using Approach 3 and using the Cisco MDS 9000 Family Fabric Manager to manage the password database. 30-6
7 Chapter 30 Configuring DHCHAP Authentication Configuring the DHCHAP Password for the Local Switch To configure the DHCHAP password for the local switch, follow these steps: Step 5 Step 6 From Fabric Manager, choose Switches > Security >. You see the configuration in the Information pane. From Device Manager, choose Security >. You see the Enable dialog box. Choose the Local Passwords tab. You see the DHCHAP local password for each switch. Click the Create Row icon in Fabric Manager or Create in Device Manager to create a new local password. You see the Create Local Passwords dialog box. Optionally, check the switches that you want to configure the same local password on in Fabric Manager. Select the switch WNN and set the Password. Click the Create to save the updated password or click Close to discard any unsaved changes. Configuring Remote Passwords for Other Devices You can configure passwords in the local authentication database for other devices in a fabric. The other devices are identified by their device name, which is also know as the switch WWN or device WWN. The password is restricted to 64 characters and can be specified in clear text (0) or in encrypted text (7). The switch WWN identifies the physical switch. This WWN is used to authenticate the switch and is different from the VSAN node WWN To configure the DHCHAP password for remote switches, follow these steps: Step 5 Step 6 From Fabric Manager, choose Switches > Security >. You see the configuration in the Information pane. From Device Manager, choose Security >. You see the Enable dialog box. Choose the Remote Passwords tab. You see the DHCHAP local password for each switch. Click the Create Row icon in Fabric Manager or Create in Device Manager to create a remote password. You see the Create Remote Passwords dialog box. Optionally, check the switches that you want to configure the same remote password on in Fabric Manager. Select the switch WNN and set the Password. Click the Create to save the updated password or click Close to discard any unsaved changes. 30-7
8 Configuring DHCHAP Authentication Chapter 30 Setting the DHCHAP Timeout Value During the DHCHAP protocol exchange, if the MDS switch does not receive the expected DHCHAP message within a specified time interval, authentication failure is assumed. The time ranges from 20 (no authentication is performed) to 1000 seconds. The default is 30 seconds. When changing the timeout value, consider the following factors: The existing RADIUS and TACACS+ timeout values. The same value must also be configured all switches in the fabric. To change the DHCHAP timeout value using Fabric Manager, follow these steps: Choose Switches > Security > in Fabric Manager. You see the configuration in the Information pane. Choose the General/Password tab. You see the DHCHAP general settings mode for each switch. Change the DHCHAP timeout value for each switch in the fabric. Click the Apply Changes icon to save the updated timeout value or click the Undo Changes icon to discard any unsaved changes. Configuring DHCHAP AAA Authentication You can individually set authentication options. If authentication is not configured, local authentication is used by default. Enabling on ISLs There is a new ISL pop-up menu called Enable that enables on switches at either end of the ISL. You are prompted for an generic password, then asked to set interface mode to ON for affected ports. Right-click an ISL and click Enable to access this feature. 30-8
Inter-VSAN Routing Configuration
 CHAPTER 16 This chapter explains the inter-vsan routing (IVR) feature and provides details on sharing resources across VSANs using IVR management interfaces provided in the switch. This chapter includes
CHAPTER 16 This chapter explains the inter-vsan routing (IVR) feature and provides details on sharing resources across VSANs using IVR management interfaces provided in the switch. This chapter includes
Configuring and Managing Zones
 Send documentation comments to mdsfeedback-doc@cisco.com CHAPTER 30 Zoning enables you to set up access control between storage devices or user groups. If you have administrator privileges in your fabric,
Send documentation comments to mdsfeedback-doc@cisco.com CHAPTER 30 Zoning enables you to set up access control between storage devices or user groups. If you have administrator privileges in your fabric,
Configuring and Managing Zones
 CHAPTER 5 Zoning enables you to set up access control between storage devices or user groups. If you have administrator privileges in your fabric, you can create zones to increase network security and
CHAPTER 5 Zoning enables you to set up access control between storage devices or user groups. If you have administrator privileges in your fabric, you can create zones to increase network security and
Configuring Fabric Congestion Control and QoS
 Send documentation comments to mdsfeedback-doc@cisco.com CHAPTER 64 Configuring Fabric Congestion Control and QoS Fibre Channel Congestion Control (FCC) is a Cisco proprietary flow control mechanism that
Send documentation comments to mdsfeedback-doc@cisco.com CHAPTER 64 Configuring Fabric Congestion Control and QoS Fibre Channel Congestion Control (FCC) is a Cisco proprietary flow control mechanism that
Configuring RADIUS and TACACS+
 28 CHAPTER The authentication, authorization, and accounting (AAA) mechanism verifies the identity of, grants access to, and tracks the actions of users managing a switch. All Cisco MDS 9000 Family switches
28 CHAPTER The authentication, authorization, and accounting (AAA) mechanism verifies the identity of, grants access to, and tracks the actions of users managing a switch. All Cisco MDS 9000 Family switches
Configuring SAN Port Channel
 Configuring SAN Port Channel This chapter contains the following sections: Configuring SAN Port Channels, page 1 Configuring SAN Port Channels SAN port channels refer to the aggregation of multiple physical
Configuring SAN Port Channel This chapter contains the following sections: Configuring SAN Port Channels, page 1 Configuring SAN Port Channels SAN port channels refer to the aggregation of multiple physical
Storage Access Network Design Using the Cisco MDS 9124 Multilayer Fabric Switch
 Storage Access Network Design Using the Cisco MDS 9124 Multilayer Fabric Switch Executive Summary Commercial customers are experiencing rapid storage growth which is primarily being fuelled by E- Mail,
Storage Access Network Design Using the Cisco MDS 9124 Multilayer Fabric Switch Executive Summary Commercial customers are experiencing rapid storage growth which is primarily being fuelled by E- Mail,
Managing FLOGI, Name Server, FDMI, and RSCN Databases
 CHAPTER 17 Managing FLOGI, Name Server, FDMI, and RSCN Databases This chapter describes the fabric login database, the name server features, and Registered State Change Notification (RSCN) information
CHAPTER 17 Managing FLOGI, Name Server, FDMI, and RSCN Databases This chapter describes the fabric login database, the name server features, and Registered State Change Notification (RSCN) information
Configuring PortChannels
 This chapter provides information about PortChannels and how to configure the PortChannels. Finding Feature Information, page 1 Information About PortChannels, page 1 Prerequisites for PortChannels, page
This chapter provides information about PortChannels and how to configure the PortChannels. Finding Feature Information, page 1 Information About PortChannels, page 1 Prerequisites for PortChannels, page
Configuring Fabric Congestion Control and QoS
 CHAPTER 1 Fibre Channel Congestion Control (FCC) is a Cisco proprietary flow control mechanism that alleviates congestion on Fibre Channel networks. Quality of service () offers the following advantages:
CHAPTER 1 Fibre Channel Congestion Control (FCC) is a Cisco proprietary flow control mechanism that alleviates congestion on Fibre Channel networks. Quality of service () offers the following advantages:
Configuring Security Features on an External AAA Server
 CHAPTER 3 Configuring Security Features on an External AAA Server The authentication, authorization, and accounting (AAA) feature verifies the identity of, grants access to, and tracks the actions of users
CHAPTER 3 Configuring Security Features on an External AAA Server The authentication, authorization, and accounting (AAA) feature verifies the identity of, grants access to, and tracks the actions of users
Fibre Channel Zoning
 Information About, page 1 Support for in Cisco UCS Manager, page 2 Guidelines and recommendations for Cisco UCS Manager-Based, page 4 Configuring, page 4 Creating a VSAN for, page 6 Creating a New Fibre
Information About, page 1 Support for in Cisco UCS Manager, page 2 Guidelines and recommendations for Cisco UCS Manager-Based, page 4 Configuring, page 4 Creating a VSAN for, page 6 Creating a New Fibre
Cisco MDS 9000 Family Blade Switch Solutions Guide
 . Solutions Guide Cisco MDS 9000 Family Blade Switch Solutions Guide Introduction This document provides design and configuration guidance for administrators implementing large-scale blade server deployments
. Solutions Guide Cisco MDS 9000 Family Blade Switch Solutions Guide Introduction This document provides design and configuration guidance for administrators implementing large-scale blade server deployments
Configure Cisco DNA Center System Settings
 About DNA Center and Cisco ISE Integration, page 1 Configure Authentication and Policy Servers, page 2 Device Controllability, page 3 Configure Device Controllability, page 4 Configure an IP Address Manager,
About DNA Center and Cisco ISE Integration, page 1 Configure Authentication and Policy Servers, page 2 Device Controllability, page 3 Configure Device Controllability, page 4 Configure an IP Address Manager,
The Virtual Machine Aware SAN
 The Virtual Machine Aware SAN What You Will Learn Virtualization of the data center, which includes servers, storage, and networks, has addressed some of the challenges related to consolidation, space
The Virtual Machine Aware SAN What You Will Learn Virtualization of the data center, which includes servers, storage, and networks, has addressed some of the challenges related to consolidation, space
AAA and the Local Database
 This chapter describes authentication, authorization, and accounting (AAA, pronounced triple A ). AAA is a a set of services for controlling access to computer resources, enforcing policies, assessing
This chapter describes authentication, authorization, and accounting (AAA, pronounced triple A ). AAA is a a set of services for controlling access to computer resources, enforcing policies, assessing
Cisco Nexus 5000 Series NX-OS SAN Switching Configuration Guide
 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387) Fax: 408 527-0883 Text Part Number: OL-xxxxx-xx THE
Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387) Fax: 408 527-0883 Text Part Number: OL-xxxxx-xx THE
National Information Assurance Partnership
 National Information Assurance Partnership Common Criteria Evaluation and Validation Scheme Validation Report Family with SAN-OS Release 3.2(2c) Report Number: CCEVS-VR-VID10015-2008 Dated: 25 September
National Information Assurance Partnership Common Criteria Evaluation and Validation Scheme Validation Report Family with SAN-OS Release 3.2(2c) Report Number: CCEVS-VR-VID10015-2008 Dated: 25 September
PPP configuration commands
 Contents PPP configuration commands 1 ip address ppp-negotiate 1 ip pool 1 link-protocol ppp 2 ppp authentication-mode 2 ppp chap password 4 ppp chap user 5 ppp ipcp remote-address forced 5 ppp pap local-user
Contents PPP configuration commands 1 ip address ppp-negotiate 1 ip pool 1 link-protocol ppp 2 ppp authentication-mode 2 ppp chap password 4 ppp chap user 5 ppp ipcp remote-address forced 5 ppp pap local-user
Fabric Manager Client
 CHAPTER 5 Cisco is a java-based GUI application that provides access to the Fabric Manager applications from a remote workstation. This chapter contains the following sections: About, page 5-1 Launching
CHAPTER 5 Cisco is a java-based GUI application that provides access to the Fabric Manager applications from a remote workstation. This chapter contains the following sections: About, page 5-1 Launching
VPN Ports and LAN-to-LAN Tunnels
 CHAPTER 6 A VPN port is a virtual port which handles tunneled traffic. Tunnels are virtual point-to-point connections through a public network such as the Internet. All packets sent through a VPN tunnel
CHAPTER 6 A VPN port is a virtual port which handles tunneled traffic. Tunnels are virtual point-to-point connections through a public network such as the Internet. All packets sent through a VPN tunnel
Configuring Zones and Zone Sets
 CHAPTER 6 Before setting up zones and zone sets make sure you have configured VSANs and interfaces. See Chapter 5, Configuring VSANs and Interfaces. Zoning enables you to set up access control between
CHAPTER 6 Before setting up zones and zone sets make sure you have configured VSANs and interfaces. See Chapter 5, Configuring VSANs and Interfaces. Zoning enables you to set up access control between
CCIE Data Center Storage Networking. Fibre Channel Switching Configuration. Nexus 5500UP FC Initialization Allocate interfaces as type FC
 CCIE Data Center Storage Networking Fibre Channel Switching Configuration Nexus 5500UP FC Initialization Allocate interfaces as type FC slot 1 port 25 32 type fc FC must start at top of module and count
CCIE Data Center Storage Networking Fibre Channel Switching Configuration Nexus 5500UP FC Initialization Allocate interfaces as type FC slot 1 port 25 32 type fc FC must start at top of module and count
Configuring Authentication, Authorization, and Accounting
 Configuring Authentication, Authorization, and Accounting This chapter contains the following sections: Information About AAA, page 1 Prerequisites for Remote AAA, page 5 Guidelines and Limitations for
Configuring Authentication, Authorization, and Accounting This chapter contains the following sections: Information About AAA, page 1 Prerequisites for Remote AAA, page 5 Guidelines and Limitations for
Large SAN Design Best Practices Using Cisco MDS 9700 and MDS 9500 Multilayer Directors
 White Paper Large SAN Design Best Practices Using Cisco MDS 9700 and MDS 9500 Multilayer Directors What You Will Learn As SANs continue to grow in size, many factors need to be considered to help scale
White Paper Large SAN Design Best Practices Using Cisco MDS 9700 and MDS 9500 Multilayer Directors What You Will Learn As SANs continue to grow in size, many factors need to be considered to help scale
Internet. SonicWALL IP Cisco IOS IP IP Network Mask
 Prepared by SonicWALL, Inc. 9/20/2001 Introduction: VPN standards are still evolving and interoperability between products is a continued effort. SonicWALL has made progress in this area and is interoperable
Prepared by SonicWALL, Inc. 9/20/2001 Introduction: VPN standards are still evolving and interoperability between products is a continued effort. SonicWALL has made progress in this area and is interoperable
Obtaining and Installing Licenses
 CHAPTER 10 Licenses are available in all switches in the Cisco MDS 9000 Family. Licensing allows you to access specified premium features on the switch after you install the appropriate license for that
CHAPTER 10 Licenses are available in all switches in the Cisco MDS 9000 Family. Licensing allows you to access specified premium features on the switch after you install the appropriate license for that
Configuring Service Profiles
 Configuring Service Profiles This chapter includes the following sections: Service Profiles that Override Server Identity, page 1 Service Profiles that Inherit Server Identity, page 2 Service Profile Templates,
Configuring Service Profiles This chapter includes the following sections: Service Profiles that Override Server Identity, page 1 Service Profiles that Inherit Server Identity, page 2 Service Profile Templates,
Best Current Practices and Implementing the FC Security Protocol (FC-SP)
 Best Current Practices and Implementing the FC Security Protocol (FC-SP) Larry Hofer, CISSP Emulex SNIA Legal Notice The material contained in this tutorial is copyrighted by the SNIA. Member companies
Best Current Practices and Implementing the FC Security Protocol (FC-SP) Larry Hofer, CISSP Emulex SNIA Legal Notice The material contained in this tutorial is copyrighted by the SNIA. Member companies
Cisco Nexus 5600 Series NX-OS SAN Switching Configuration Guide, Release 7.x
 Cisco Nexus 5600 Series NX-OS SAN Switching Configuration Guide, Release 7.x Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000
Cisco Nexus 5600 Series NX-OS SAN Switching Configuration Guide, Release 7.x Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000
Interoperability Limitations
 CHAPTER 2 This chapter describes the restrictions and limitations imposed on specific vendor switches when working in interoperability mode. It includes the following sections: Cisco MDS 9000 Family, page
CHAPTER 2 This chapter describes the restrictions and limitations imposed on specific vendor switches when working in interoperability mode. It includes the following sections: Cisco MDS 9000 Family, page
IBM Europe Announcement ZG , dated February 13, 2007
 IBM Europe Announcement ZG07-0221, dated February 13, 2007 Cisco MDS 9200 for IBM System Storage switches, models 9216i and 9216A, offer enhanced performance, scalability, multiprotocol capabilities, and
IBM Europe Announcement ZG07-0221, dated February 13, 2007 Cisco MDS 9200 for IBM System Storage switches, models 9216i and 9216A, offer enhanced performance, scalability, multiprotocol capabilities, and
Scheduling Maintenance Jobs
 CHAPTER 5 The Cisco MDS command scheduler feature helps you schedule configuration and maintenance jobs in any switch in the Cisco MDS 9000 Family.You can use this feature to schedule jobs on a one-time
CHAPTER 5 The Cisco MDS command scheduler feature helps you schedule configuration and maintenance jobs in any switch in the Cisco MDS 9000 Family.You can use this feature to schedule jobs on a one-time
Cisco ASA 5500 LAB Guide
 INGRAM MICRO Cisco ASA 5500 LAB Guide Ingram Micro 4/1/2009 The following LAB Guide will provide you with the basic steps involved in performing some fundamental configurations on a Cisco ASA 5500 series
INGRAM MICRO Cisco ASA 5500 LAB Guide Ingram Micro 4/1/2009 The following LAB Guide will provide you with the basic steps involved in performing some fundamental configurations on a Cisco ASA 5500 series
Send documentation comments to
 Send documentation comments to mdsfeedback-doc@cisco.com. INDEX Numerics 16-port modules BB_credits 18-8 32-port modules BB_credits 18-8 configuration guidelines 18-5 A AAA description 27-1 distributing
Send documentation comments to mdsfeedback-doc@cisco.com. INDEX Numerics 16-port modules BB_credits 18-8 32-port modules BB_credits 18-8 configuration guidelines 18-5 A AAA description 27-1 distributing
Configuring VSANs and Interfaces
 CHAPTER 3 You can achieve higher security and greater stability in Fibre Channel fabrics by using virtual storage area networks (VSANs). VSANs provide isolation among devices that are physically connected
CHAPTER 3 You can achieve higher security and greater stability in Fibre Channel fabrics by using virtual storage area networks (VSANs). VSANs provide isolation among devices that are physically connected
Cisco MDS 9710 Multilayer Director for IBM System Networking IBM Redbooks Product Guide
 Cisco MDS 9710 Multilayer Director for IBM System Networking IBM Redbooks Product Guide This IBM Redbooks Product Guide introduces Cisco MDS 9710 Multilayer Director for IBM System Networking (9710-E08).
Cisco MDS 9710 Multilayer Director for IBM System Networking IBM Redbooks Product Guide This IBM Redbooks Product Guide introduces Cisco MDS 9710 Multilayer Director for IBM System Networking (9710-E08).
Managing Events and Alarms
 CHAPTER 8 By configuring how events are reported, you can monitor those events more effectively and take corrective action, if necessary. Cisco Fabric Manager provides the following features for reporting
CHAPTER 8 By configuring how events are reported, you can monitor those events more effectively and take corrective action, if necessary. Cisco Fabric Manager provides the following features for reporting
Configuring Fibre Channel Interfaces
 This chapter contains the following sections:, page 1 Information About Fibre Channel Interfaces Licensing Requirements for Fibre Channel On Cisco Nexus 3000 Series switches, Fibre Channel capability is
This chapter contains the following sections:, page 1 Information About Fibre Channel Interfaces Licensing Requirements for Fibre Channel On Cisco Nexus 3000 Series switches, Fibre Channel capability is
Designing and Deploying a Cisco Unified Computing System SAN Using Cisco MDS 9000 Family Switches
 Designing and Deploying a Cisco Unified Computing System SAN Using Cisco MDS 9000 Family Switches What You Will Learn The Cisco Unified Computing System helps address today s business challenges by streamlining
Designing and Deploying a Cisco Unified Computing System SAN Using Cisco MDS 9000 Family Switches What You Will Learn The Cisco Unified Computing System helps address today s business challenges by streamlining
Configuring Request Authentication and Authorization
 CHAPTER 15 Configuring Request Authentication and Authorization Request authentication and authorization is a means to manage employee use of the Internet and restrict access to online content. This chapter
CHAPTER 15 Configuring Request Authentication and Authorization Request authentication and authorization is a means to manage employee use of the Internet and restrict access to online content. This chapter
P Commands. Send documentation comments to CHAPTER
 CHAPTER 17 The commands in this chapter apply to the Cisco MDS 9000 Family of multilayer directors and fabric switches. All commands are shown here in alphabetical order regardless of command mode. See
CHAPTER 17 The commands in this chapter apply to the Cisco MDS 9000 Family of multilayer directors and fabric switches. All commands are shown here in alphabetical order regardless of command mode. See
Configuring RADIUS. Information About RADIUS. RADIUS Network Environments. Send document comments to
 3 CHAPTER This chapter describes how to configure Remote Access Dial-In User Service (RADIUS) protocol on NX-OS devices. This chapter includes the following sections: Information About RADIUS, page 3-1
3 CHAPTER This chapter describes how to configure Remote Access Dial-In User Service (RADIUS) protocol on NX-OS devices. This chapter includes the following sections: Information About RADIUS, page 3-1
Configuring Microsoft Outlook to Connect to Hosted Exchange Service
 Configuring Microsoft Outlook to Connect to Hosted Exchange Service Configuring Microsoft Outlook for Hosted Exchange Service Version: 1.0 Updated on: April 27, 2011 Page 1 of 7 TABLE OF CONTENTS Configuring
Configuring Microsoft Outlook to Connect to Hosted Exchange Service Configuring Microsoft Outlook for Hosted Exchange Service Version: 1.0 Updated on: April 27, 2011 Page 1 of 7 TABLE OF CONTENTS Configuring
Security Setup CHAPTER
 CHAPTER 8 This chapter describes how to set up your bridge s security features. This chapter contains the following sections: Security Overview, page 8-2 Setting Up WEP, page 8-7 Enabling Additional WEP
CHAPTER 8 This chapter describes how to set up your bridge s security features. This chapter contains the following sections: Security Overview, page 8-2 Setting Up WEP, page 8-7 Enabling Additional WEP
Internet Key Exchange
 CHAPTER16 The help topics in this section describe the (IKE) configuration screens. (IKE) What Do You Want to Do? (IKE) is a standard method for arranging for secure, authenticated communications. IKE
CHAPTER16 The help topics in this section describe the (IKE) configuration screens. (IKE) What Do You Want to Do? (IKE) is a standard method for arranging for secure, authenticated communications. IKE
N-Port Virtualization in the Data Center
 N-Port Virtualization in the Data Center What You Will Learn N-Port virtualization is a feature that has growing importance in the data center. This document addresses the design requirements for designing
N-Port Virtualization in the Data Center What You Will Learn N-Port virtualization is a feature that has growing importance in the data center. This document addresses the design requirements for designing
Managing Zones and Zone Sets
 mdsfeedback-doc@cisco.com.send CHAPTER 3 The Fabric Manager allows you to configure and monitor zones and zone sets (groups of zones) on the Cisco 9000 switch. Zoning allows you to set up access control
mdsfeedback-doc@cisco.com.send CHAPTER 3 The Fabric Manager allows you to configure and monitor zones and zone sets (groups of zones) on the Cisco 9000 switch. Zoning allows you to set up access control
Service Profiles. Service Profiles in UCS Manager
 in UCS Manager, on page 1 that Override Server Identity, on page 2 that Inherit Server Identity, on page 2 Guidelines and Recommendations for, on page 3 Methods of Creating, on page 3 Inband, on page 7
in UCS Manager, on page 1 that Override Server Identity, on page 2 that Inherit Server Identity, on page 2 Guidelines and Recommendations for, on page 3 Methods of Creating, on page 3 Inband, on page 7
IBM Storage Networking SAN384C-6 Product Guide IBM Redbooks Product Guide
 IBM Storage Networking SAN384C-6 Product Guide IBM Redbooks Product Guide This IBM Redbooks Product Guide introduces IBM Storage Networking SAN384C-6. It is a director-class storage area network (SAN)
IBM Storage Networking SAN384C-6 Product Guide IBM Redbooks Product Guide This IBM Redbooks Product Guide introduces IBM Storage Networking SAN384C-6. It is a director-class storage area network (SAN)
Symbols. Numerics MASTER INDEX. Send documentation comments to
 MASTER INDEX The following MDS NX-OS configuration guide abbreviations are used in the Master Index. IOA- I/O Accelerator Configuration Guide Fund - Fabric Manager Fundamentals Guide Fabric - Fabric Configuration
MASTER INDEX The following MDS NX-OS configuration guide abbreviations are used in the Master Index. IOA- I/O Accelerator Configuration Guide Fund - Fabric Manager Fundamentals Guide Fabric - Fabric Configuration
Direct Attached Storage
 , page 1 Fibre Channel Switching Mode, page 1 Configuring Fibre Channel Switching Mode, page 2 Creating a Storage VSAN, page 3 Creating a VSAN for Fibre Channel Zoning, page 4 Configuring a Fibre Channel
, page 1 Fibre Channel Switching Mode, page 1 Configuring Fibre Channel Switching Mode, page 2 Creating a Storage VSAN, page 3 Creating a VSAN for Fibre Channel Zoning, page 4 Configuring a Fibre Channel
Cisco MDS 9000 Family SAN-OS Release 3.2(2c)
 August 2008 Version: 3.0 Table of Contents Table of Contents 1 List of Tables 3 List of Figures 4 Conventions 4 References 5 Introduction 5 Acronyms 6 ST and TOE Identification 7 Security Target Overview
August 2008 Version: 3.0 Table of Contents Table of Contents 1 List of Tables 3 List of Figures 4 Conventions 4 References 5 Introduction 5 Acronyms 6 ST and TOE Identification 7 Security Target Overview
Virtual Private Cloud. User Guide. Issue 03 Date
 Issue 03 Date 2016-10-19 Change History Change History Release Date What's New 2016-10-19 This issue is the third official release. Modified the following content: Help Center URL 2016-07-15 This issue
Issue 03 Date 2016-10-19 Change History Change History Release Date What's New 2016-10-19 This issue is the third official release. Modified the following content: Help Center URL 2016-07-15 This issue
IBM To Resell Cisco Systems MDS 9000 Multilayer Switch and Director Family of Intelligent Storage Networking Products
 Hardware Announcement February 17, 2003 IBM To Resell Cisco Systems MDS 9000 Multilayer Switch and Director Family of Intelligent Storage Networking Products Overview IBM announces the availability of
Hardware Announcement February 17, 2003 IBM To Resell Cisco Systems MDS 9000 Multilayer Switch and Director Family of Intelligent Storage Networking Products Overview IBM announces the availability of
Cisco I/O Accelerator Deployment Guide
 Cisco I/O Accelerator Deployment Guide Introduction This document provides design and configuration guidance for deploying the Cisco MDS 9000 Family I/O Accelerator (IOA) feature, which significantly improves
Cisco I/O Accelerator Deployment Guide Introduction This document provides design and configuration guidance for deploying the Cisco MDS 9000 Family I/O Accelerator (IOA) feature, which significantly improves
Digest Authentication Setup for SIP Trunks
 This chapter provides information about digest authentication setup for SIP trunks. When you configure digest authentication for SIP trunks, Cisco Unified Communications Manager challenges the identity
This chapter provides information about digest authentication setup for SIP trunks. When you configure digest authentication for SIP trunks, Cisco Unified Communications Manager challenges the identity
Configuring Role-Based Access Control
 Configuring Role-Based Access Control This chapter includes the following sections: Role-Based Access Control, page 1 User Accounts for Cisco UCS Manager, page 1 User Roles, page 3 Privileges, page 4 User
Configuring Role-Based Access Control This chapter includes the following sections: Role-Based Access Control, page 1 User Accounts for Cisco UCS Manager, page 1 User Roles, page 3 Privileges, page 4 User
Configuring TACACS+ Information About TACACS+ Send document comments to CHAPTER
 4 CHAPTER This chapter describes how to configure the Terminal Access Controller Access Control System Plus (TACACS+) protocol on NX-OS devices. This chapter includes the following sections: Information
4 CHAPTER This chapter describes how to configure the Terminal Access Controller Access Control System Plus (TACACS+) protocol on NX-OS devices. This chapter includes the following sections: Information
Cisco MDS 9000 Family 4-Gbps Fibre Channel Switching Modules
 Cisco MDS 9000 Family 4-Gbps Fibre Channel Switching Modules Cisco MDS 9000 Family 4-Gbps Fibre Channel switching modules deliver the intelligence and advanced features required to build truly scalable
Cisco MDS 9000 Family 4-Gbps Fibre Channel Switching Modules Cisco MDS 9000 Family 4-Gbps Fibre Channel switching modules deliver the intelligence and advanced features required to build truly scalable
Network Security 1. Module 7 Configure Trust and Identity at Layer 2
 Network Security 1 Module 7 Configure Trust and Identity at Layer 2 1 Learning Objectives 7.1 Identity-Based Networking Services (IBNS) 7.2 Configuring 802.1x Port-Based Authentication 2 Module 7 Configure
Network Security 1 Module 7 Configure Trust and Identity at Layer 2 1 Learning Objectives 7.1 Identity-Based Networking Services (IBNS) 7.2 Configuring 802.1x Port-Based Authentication 2 Module 7 Configure
Emulex OneCommand Manager Application for VMware vcenter
 Release Notes Emulex OneCommand Manager Application for VMware vcenter Release 12.0.261.9 Purpose and Contact Information These release notes describe the supported operating systems, new features, resolved
Release Notes Emulex OneCommand Manager Application for VMware vcenter Release 12.0.261.9 Purpose and Contact Information These release notes describe the supported operating systems, new features, resolved
Configuring Users and Common Roles
 Send documentation comments to mdsfeedback-doc@cisco.com. 26 CHAPTER Configuring Users and Common Roles The CLI and SNMP use common roles in all switches in the Cisco MDS 9000 Family. You can use CLI to
Send documentation comments to mdsfeedback-doc@cisco.com. 26 CHAPTER Configuring Users and Common Roles The CLI and SNMP use common roles in all switches in the Cisco MDS 9000 Family. You can use CLI to
Defining IPsec Networks and Customers
 CHAPTER 4 Defining the IPsec Network Elements In this product, a VPN network is a unique group of targets; a target can be a member of only one network. Thus, a VPN network allows a provider to partition
CHAPTER 4 Defining the IPsec Network Elements In this product, a VPN network is a unique group of targets; a target can be a member of only one network. Thus, a VPN network allows a provider to partition
Configuring TACACS+ About TACACS+
 This chapter describes how to configure the Terminal Access Controller Access Control System Plus (TACACS+) protocol on Cisco NX-OS devices. This chapter includes the following sections: About TACACS+,
This chapter describes how to configure the Terminal Access Controller Access Control System Plus (TACACS+) protocol on Cisco NX-OS devices. This chapter includes the following sections: About TACACS+,
AAA Administration. Setting up RADIUS. Information About RADIUS
 Setting up RADIUS, page 1 Setting up TACACS+, page 26 Maximum Local Database Entries, page 37 Information About Configuring Maximum Local Database Entries, page 37 Configuring Maximum Local Database Entries
Setting up RADIUS, page 1 Setting up TACACS+, page 26 Maximum Local Database Entries, page 37 Information About Configuring Maximum Local Database Entries, page 37 Configuring Maximum Local Database Entries
Configuration Guide. How to connect to an IPSec VPN using an iphone in ios. Overview
 Configuration Guide How to connect to an IPSec VPN using an iphone in ios Overview Currently, users can conveniently use the built-in IPSec client on an iphone to connect to a VPN server. IPSec VPN can
Configuration Guide How to connect to an IPSec VPN using an iphone in ios Overview Currently, users can conveniently use the built-in IPSec client on an iphone to connect to a VPN server. IPSec VPN can
Configuring and Managing Zones
 CHAPTER 19 Zoning enables you to set up access control between storage devices or user groups. If you have administrator privileges in your fabric, you can create zones to increase network security and
CHAPTER 19 Zoning enables you to set up access control between storage devices or user groups. If you have administrator privileges in your fabric, you can create zones to increase network security and
Manage Your Device Inventory
 About Device Inventory, page 1 Device Inventory and Cisco ISE Authentication, page 7 Device Inventory Tasks, page 7 Add a Device Manually, page 8 Filter Devices, page 12 Change Devices Layout View, page
About Device Inventory, page 1 Device Inventory and Cisco ISE Authentication, page 7 Device Inventory Tasks, page 7 Add a Device Manually, page 8 Filter Devices, page 12 Change Devices Layout View, page
Fibre Channel Specialist Lab
 Fibre Channel Specialist Lab 203.11 Enterprise Fabric Suite Operation Objective: This lab will familiarize the learner with the Enterprise Fabric Suite Graphical User Interface for SANbox switches. Lab
Fibre Channel Specialist Lab 203.11 Enterprise Fabric Suite Operation Objective: This lab will familiarize the learner with the Enterprise Fabric Suite Graphical User Interface for SANbox switches. Lab
Network Access Flows APPENDIXB
 APPENDIXB This appendix describes the authentication flows in Cisco Identity Services Engine (ISE) by using RADIUS-based Extensible Authentication Protocol (EAP) and non-eap protocols. Authentication verifies
APPENDIXB This appendix describes the authentication flows in Cisco Identity Services Engine (ISE) by using RADIUS-based Extensible Authentication Protocol (EAP) and non-eap protocols. Authentication verifies
Summary. Deployment Guide: Configuring the Cisco Wireless Security Suite 1 OL
 Summary Numerous papers have been written on the topic of IEEE 802.11 security for wireless LANs (WLANs). The major vulnerabilities of 802.11 security can be summarized as follows: Weak device-only authentication:
Summary Numerous papers have been written on the topic of IEEE 802.11 security for wireless LANs (WLANs). The major vulnerabilities of 802.11 security can be summarized as follows: Weak device-only authentication:
Cisco SME Tape Configuration
 CHAPTER 5 This chapter contains information about managing tapes that are encrypted using Cisco SME. It includes the following sections: About Cisco Storage Media Encryption Tape Management, page 5-1 Adding
CHAPTER 5 This chapter contains information about managing tapes that are encrypted using Cisco SME. It includes the following sections: About Cisco Storage Media Encryption Tape Management, page 5-1 Adding
IBM Storage Networking SAN192C-6 Product Guide IBM Redbooks Product Guide
 IBM Storage Networking SAN192C-6 Product Guide IBM Redbooks Product Guide This IBM Redbooks Product Guide describes the IBM Storage Networking SAN192C-6. The IBM Storage Networking SAN192C-6 is a director-class
IBM Storage Networking SAN192C-6 Product Guide IBM Redbooks Product Guide This IBM Redbooks Product Guide describes the IBM Storage Networking SAN192C-6. The IBM Storage Networking SAN192C-6 is a director-class
PT Activity: Configure AAA Authentication on Cisco Routers
 PT Activity: Configure AAA Authentication on Cisco Routers Instructor Version Topology Diagram Addressing Table Device Interface IP Address Subnet Mask R1 Fa0/0 192.168.1.1 255.255.255.0 S0/0/0 10.1.1.2
PT Activity: Configure AAA Authentication on Cisco Routers Instructor Version Topology Diagram Addressing Table Device Interface IP Address Subnet Mask R1 Fa0/0 192.168.1.1 255.255.255.0 S0/0/0 10.1.1.2
Configuring Cisco VPN Concentrator to Support Avaya 96xx Phones Issue 1.0. Issue th October 2009 ABSTRACT
 Avaya CAD-SV Configuring Cisco VPN Concentrator to Support Avaya 96xx Phones Issue 1.0 Issue 1.0 30th October 2009 ABSTRACT These Application Notes describe the steps to configure the Cisco VPN 3000 Concentrator
Avaya CAD-SV Configuring Cisco VPN Concentrator to Support Avaya 96xx Phones Issue 1.0 Issue 1.0 30th October 2009 ABSTRACT These Application Notes describe the steps to configure the Cisco VPN 3000 Concentrator
Cisco SME Tape Configuration
 CHAPTER 5 This chapter contains information about managing tapes that are encrypted using Cisco SME. It includes the following sections: About Cisco Storage Media Encryption Tape Management Adding Tape
CHAPTER 5 This chapter contains information about managing tapes that are encrypted using Cisco SME. It includes the following sections: About Cisco Storage Media Encryption Tape Management Adding Tape
Monitoring Inventory. Inventory Management. This chapter includes the following sections:
 This chapter includes the following sections: Inventory Management, page 1 Overview to Global Logical Resources, page 2 Configuring Inventory Data Collection Schedule, page 3 Viewing Inventory Details,
This chapter includes the following sections: Inventory Management, page 1 Overview to Global Logical Resources, page 2 Configuring Inventory Data Collection Schedule, page 3 Viewing Inventory Details,
QuickSpecs. Key Features and Benefits. Cisco MDS 9216i W/0 1Gb Ethernet SFP Fabric Switch Overview
 Overview The Cisco MDS 9216i brings the most flexible storage networking capability available in the fabric switch market today. Sharing a consistent architecture with the Cisco MDS 9500 Directors, the
Overview The Cisco MDS 9216i brings the most flexible storage networking capability available in the fabric switch market today. Sharing a consistent architecture with the Cisco MDS 9500 Directors, the
Virtual Private Network. Network User Guide. Issue 05 Date
 Issue 05 Date 2018-03-30 Contents Contents 1 Overview... 1 1.1 Concepts... 1 1.1.1 VPN... 1 1.1.2 IPsec VPN...1 1.2 Application Scenarios...2 1.3 Billing Standards... 3 1.4 VPN Reference Standards and
Issue 05 Date 2018-03-30 Contents Contents 1 Overview... 1 1.1 Concepts... 1 1.1.1 VPN... 1 1.1.2 IPsec VPN...1 1.2 Application Scenarios...2 1.3 Billing Standards... 3 1.4 VPN Reference Standards and
RSA SecurID Ready Implementation Guide
 RSA SecurID Ready Implementation Guide Partner Information Last Modified: April 20, 2005 Product Information Partner Name Cisco Web Site www.cisco.com Product Name Cisco PIX Security Appliance Version
RSA SecurID Ready Implementation Guide Partner Information Last Modified: April 20, 2005 Product Information Partner Name Cisco Web Site www.cisco.com Product Name Cisco PIX Security Appliance Version
OmniVista 3.5 Discovery Help
 Using Discovery Open the Discovery application by clicking Discovery in the Task Bar, selecting Discovery from the Applications menu, or by clicking the Discovery icon in the Topology Toolbar. The Discovery
Using Discovery Open the Discovery application by clicking Discovery in the Task Bar, selecting Discovery from the Applications menu, or by clicking the Discovery icon in the Topology Toolbar. The Discovery
How to Configure a Site-to-Site IPsec IKEv1 VPN Tunnel
 How to Configure a Site-to-Site IPsec IKEv1 VPN Tunnel The Barracuda NextGen Firewall F-Series can establish IPsec VPN tunnels to any standard-compliant third party IKEv1 IPsec VPN gateway. The Site-to-Site
How to Configure a Site-to-Site IPsec IKEv1 VPN Tunnel The Barracuda NextGen Firewall F-Series can establish IPsec VPN tunnels to any standard-compliant third party IKEv1 IPsec VPN gateway. The Site-to-Site
Configuring Certificate Authorities and Digital Certificates
 CHAPTER 43 Configuring Certificate Authorities and Digital Certificates Public Key Infrastructure (PKI) support provides the means for the Cisco MDS 9000 Family switches to obtain and use digital certificates
CHAPTER 43 Configuring Certificate Authorities and Digital Certificates Public Key Infrastructure (PKI) support provides the means for the Cisco MDS 9000 Family switches to obtain and use digital certificates
Manage Your Inventory
 About Inventory About Inventory, on page 1 Inventory and Cisco ISE Authentication, on page 6 Add a Device Manually, on page 7 Integrate Meraki Dashboard, on page 10 Filter Devices, on page 11 Change Devices
About Inventory About Inventory, on page 1 Inventory and Cisco ISE Authentication, on page 6 Add a Device Manually, on page 7 Integrate Meraki Dashboard, on page 10 Filter Devices, on page 11 Change Devices
Configuring LAN-to-LAN IPsec VPNs
 CHAPTER 28 A LAN-to-LAN VPN connects networks in different geographic locations. The ASA 1000V supports LAN-to-LAN VPN connections to Cisco or third-party peers when the two peers have IPv4 inside and
CHAPTER 28 A LAN-to-LAN VPN connects networks in different geographic locations. The ASA 1000V supports LAN-to-LAN VPN connections to Cisco or third-party peers when the two peers have IPv4 inside and
PPP Configuration Options
 PPP Configuration Options 1 PPP Configuration Options PPP can be configured to support various functions including: Authentication using either PAP or CHAP Compression using either Stacker or Predictor
PPP Configuration Options 1 PPP Configuration Options PPP can be configured to support various functions including: Authentication using either PAP or CHAP Compression using either Stacker or Predictor
HPE IMC UAM Binding Access Users with PCs Configuration Examples
 HPE IMC UAM Binding Access Users with PCs Configuration Examples Part Number: 5200-1372 Software version: IMC UAM 7.2 (E0403) Document version: 2 The information in this document is subject to change without
HPE IMC UAM Binding Access Users with PCs Configuration Examples Part Number: 5200-1372 Software version: IMC UAM 7.2 (E0403) Document version: 2 The information in this document is subject to change without
CONNECTRIX MDS-9250I SWITCH
 Specification Sheet MDS-9250i CONNECTRIX MDS-9250I SWITCH Multipurpose Switch The Connectrix MDS-9250i Multilayer Switch offers up to forty 16 Gigabit per second (Gb/s) Fibre Channel ports, two 1/10 Gigabit
Specification Sheet MDS-9250i CONNECTRIX MDS-9250I SWITCH Multipurpose Switch The Connectrix MDS-9250i Multilayer Switch offers up to forty 16 Gigabit per second (Gb/s) Fibre Channel ports, two 1/10 Gigabit
Cisco MDS 9000 Series Switches
 Cisco MDS 9000 Series Switches Overview of Cisco Storage Networking Solutions Cisco MDS 9000 Series Directors Cisco MDS 9718 Cisco MDS 9710 Cisco MDS 9706 Configuration Chassis, dual Supervisor-1E Module,
Cisco MDS 9000 Series Switches Overview of Cisco Storage Networking Solutions Cisco MDS 9000 Series Directors Cisco MDS 9718 Cisco MDS 9710 Cisco MDS 9706 Configuration Chassis, dual Supervisor-1E Module,
Fibre Channel Gateway Overview
 CHAPTER 5 This chapter describes the Fibre Channel gateways and includes the following sections: About the Fibre Channel Gateway, page 5-1 Terms and Concepts, page 5-2 Cisco SFS 3500 Fibre Channel Gateway
CHAPTER 5 This chapter describes the Fibre Channel gateways and includes the following sections: About the Fibre Channel Gateway, page 5-1 Terms and Concepts, page 5-2 Cisco SFS 3500 Fibre Channel Gateway
Fibre Channel Specialist Lab
 Fibre Channel Specialist Lab 203.21 Enterprise Fabric Suite Zoning Operation Objective: This lab will demonstrate the configuration and management of zoning in a QLogic fabric. Unless noted, all operations
Fibre Channel Specialist Lab 203.21 Enterprise Fabric Suite Zoning Operation Objective: This lab will demonstrate the configuration and management of zoning in a QLogic fabric. Unless noted, all operations
UpgradingFirmwarethroughFirmwarePackages in Service Profiles
 UpgradingFirmwarethroughFirmwarePackages in Service Profiles This chapter includes the following sections: Firmware Upgrades through Firmware Packages in Service Profiles, page 1 Creating a Host Firmware
UpgradingFirmwarethroughFirmwarePackages in Service Profiles This chapter includes the following sections: Firmware Upgrades through Firmware Packages in Service Profiles, page 1 Creating a Host Firmware
Cisco MDS 9000 Series Fabric Configuration Guide, Release 8.x
 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387) Fax: 408 527-0883 2018 Cisco Systems, Inc. All rights
Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387) Fax: 408 527-0883 2018 Cisco Systems, Inc. All rights
Remote Authentication
 Authentication Services, page 1 Guidelines and Recommendations for Providers, page 2 User Attributes in Providers, page 2 Two-Factor Authentication, page 4 LDAP Providers and Groups, page 5 RADIUS Providers,
Authentication Services, page 1 Guidelines and Recommendations for Providers, page 2 User Attributes in Providers, page 2 Two-Factor Authentication, page 4 LDAP Providers and Groups, page 5 RADIUS Providers,
Configuring RADIUS Clients
 CHAPTER 8 This chapter describes the following: Overview Adding RADIUS Clients Editing RADIUS Clients Deleting RADIUS Clients Overview Remote Authentication Dial In User Service (RADIUS) is an AAA (authentication,
CHAPTER 8 This chapter describes the following: Overview Adding RADIUS Clients Editing RADIUS Clients Deleting RADIUS Clients Overview Remote Authentication Dial In User Service (RADIUS) is an AAA (authentication,
Emulex OneCommand Manager Application for LightPulse Adapters for Windows Release Notes
 Emulex OneCommand Manager Application for LightPulse Adapters for Windows Release Notes Version: 11.4.204.11 System: Windows Server 2016 Windows Server 2012 and Windows Server 2012 R2 (x64 versions, Enterprise,
Emulex OneCommand Manager Application for LightPulse Adapters for Windows Release Notes Version: 11.4.204.11 System: Windows Server 2016 Windows Server 2012 and Windows Server 2012 R2 (x64 versions, Enterprise,
Encryption Algorithms Authentication Protocols Message Integrity Protocols Key Distribution Firewalls
 Security Outline Encryption Algorithms Authentication Protocols Message Integrity Protocols Key Distribution Firewalls Overview Cryptography functions Secret key (e.g., DES) Public key (e.g., RSA) Message
Security Outline Encryption Algorithms Authentication Protocols Message Integrity Protocols Key Distribution Firewalls Overview Cryptography functions Secret key (e.g., DES) Public key (e.g., RSA) Message
Cisco MDS 9000 Series Switches
 Cisco MDS 9000 Series Switches Overview of Cisco Storage Networking Solutions Cisco MDS 9000 Series 32-Gbps Directors Cisco MDS 9718 Cisco MDS 9710 Cisco MDS 9706 Configuration Chassis, dual Supervisor-1E
Cisco MDS 9000 Series Switches Overview of Cisco Storage Networking Solutions Cisco MDS 9000 Series 32-Gbps Directors Cisco MDS 9718 Cisco MDS 9710 Cisco MDS 9706 Configuration Chassis, dual Supervisor-1E
OpenVPN protocol. Restrictions in Conel routers. Modified on: Thu, 14 Aug, 2014 at 2:29 AM
 1/2/2016 OpenVPN protocol : Support Portal OpenVPN protocol Modified on: Thu, 14 Aug, 2014 at 2:29 AM OpenVPN (Open Virtual Private Network) is a means of interconnection of several computers through an
1/2/2016 OpenVPN protocol : Support Portal OpenVPN protocol Modified on: Thu, 14 Aug, 2014 at 2:29 AM OpenVPN (Open Virtual Private Network) is a means of interconnection of several computers through an
