COMP 2000 W 2012 Lab no. 3 Page 1 of 11
|
|
|
- Jared Manning
- 5 years ago
- Views:
Transcription
1 COMP 2000 W 2012 Lab no. 3 Page 1 of 11 Lab Introduction Background The Internet is based on packet-switched protocols. Information is carried in packets (it is divided into packets), which can be imagined as small parcels being passed from computer to computer. Large chunks of data are usually broken up into several smaller packets before being sent through the network. The delivery mechanism employs protocols to encode the packet, ensures safe transit, and provides a way of reconstructing the data when it reaches its destination. The main protocols used on the Internet are referred to as TCP/IP, standing for Transmission Control Protocol / Internet Protocol. Before beginning this lab, you should have already tried using Wireshark for examining traffic and be familiar with the ping and traceroute programs on wired workstations (with physical internet connections). You should have used wireshark to examine HTTP packets created when browsing the Web. In this lab, you will be examining the use of wireless devices for the same kind of activity. Programs used in the Lab traceroute is a computer network diagnostic tool for displaying the route (path) and measuring transit delays of packets across an Internet Protocol (IP) network. It attempts to show a possible route over the network between two systems, listing all the nodes (intermediate routers) it can find at one hop distance, two hops distance, three hops, and so on. These are potentially the nodes a packet must pass through to get to its destination. It can help you determine why your connections to a given server might be poor, and can often help you figure out where exactly the problem is. It can also show how systems are connected to each other, letting you see how your Internet Service Provider ISP connects to the Internet as well as how the target system is connected. Unfortunately, many hosts or firewalls prevent the packets traceroute sends (it uses the ICMP protocol to get responses) from getting to their destination, so traceroute does not always provide the desired information. ping is a simpler program that attempts to get a specific host to respond and show the delay time in getting a message back from that host. Like traceroute, many hosts or firewalls prevent the packets from getting to their destination, or they simply ignore the requests, so ping may not always work. Wireshark is a sophisticated packet analysis tool, too complicated to discuss in detail here. There is some information at the end of this section. It captures packet information for traffic passing through a specific network node.
2 COMP 2000 W 2012 Lab no. 3 Page 2 of 11 Connecting an ipod to the campus network (lab activity 1 and 2) Connect IPod to the internet: 1. Choose setting>wi-fi and turn the Wi-Fi on. 2. Wait a moment as the IPod touch detects available Wi-Fi network in range then choose a network, enter the password if necessary and tap join. Networks which require a password appear with a lock icon. 3. If there is not STU option in the name of networks, you have to set it up manually. Tap other and enter the network name stu. You need to select the security seetings for the network. Choose WPA Enterprise.
3 COMP 2000 W 2012 Lab no. 3 Page 3 of Fill in the user name and password with the user name and password which you use for connecting to the campus wireless at MUN. If you don t have a wireless account, you will have to borrow a connected device in the lab. 5. Check your connection by using the safari web browser on the ipod. Description of application traceroute on Ipod Traceroute shows a possible route to the target host. At the same time you can know the open/close status of the TCP port on the host. If the port is open, the target host label is shown by green color. If the port is closed, it is colored with red. The default port number is 80 (http) and the maximum TTL (Time- To- Live) is 30. You may set the port number and the TTL. There are various traceroute programs on different devices that work similarly. For traceroute on the ipod: 1. Connect to campus internet service 2. Tap traceroute icon on ipod touch 3. Enter the internet host you want to find 4. Press start This picture shows the trace route of
4 COMP 2000 W 2012 Lab no. 3 Page 4 of 11 How to make an ipod touch forget a Wi-Fi network: Do not return the ipod with your password on it. Once you connect to a WiFi network once the iphone automatically remembers the network and connects you to it later. To forget a network so you don't get automatically connected: Choose the "WiFi" option on the menu. Tap the right arrow button next to one of the networks that the iphone already remembers. Then tap "Forget This Network" to erase the phone's memory of the network. Connecting an ipod to the isolated network (lab activity 3 and 4) How to connect to the router: (without security) 1. Choose setting>wi-fi, turn wifi on. 2. In available network list, choose unsecure (the name of network). Now you are connected to the WLAN network unsecure. (If you press the arrow next to the unsecure you can see the IP address which your Ipod is working with. 3. If you want to check your Ipod is in connect with web server/ router you can tap the Ping icon (one of the application installed on your IPods), then fill the web server/ Ipod IP address in the related space and tap start. Browsing the web page for activity 3: Tap safari Icon on your ipod, enter IP address goes here/comp2000 as the web page address; enter a message and submit it. Let the lab instructor know to finish your data capture. Check with the lab assistant to get access to the captured data.
5 COMP 2000 W 2012 Lab no. 3 Page 5 of 11 How to connect to the router: (with security) 1. Choose setting>wi-fi, turn wifi on. 2. In available network list, choose secured As for password type iamsecured. Now you are connected to the WLAN network secured. (If you press the arrow next to the secured you can see the IP address which your Ipod is working with. Browsing the web page for activity 4: Tap safari Icon on your ipod, enter IP address goes here/comp2000 as the web page address; enter a message and submit it. Let the lab instructor know to finish your data capture. More about Wireshark Installing Wireshark Wireshark software is easy to install. Simply go to download the software for your applicable operating system, and perform the installation. Capturing packets In our lab, the lab assistant will do the wireless data capture part. The following information is included here so you will have an idea what the lab assistant is doing. A problem you ll likely run into is that Wireshark may not display any packets after starting a capture using your existing client card, especially if running in Windows. The issue is that many of the cards don t support promiscuous mode. In this case, you can try turning promiscuous mode off (from inside Wireshark), but you ll only see (at best) packets being sent to and from the computer running Wireshark. If you have trouble getting Wireshark working with existing client cards, then consider purchasing a USB-based receiver designed to work effectively with Wireshark. Before capturing packets, configure Wireshark to interface with an client device; otherwise, you ll get an alert No capture interface selected! when starting a packet capture. To select an interface, click the Capture menu, choose Options, and select the appropriate interface. Be certain to monitor the correct RF channel. For example, if the wireless network is set to channel 1 for the traffic you re interested in, then configure Wireshark to monitor channel 1. To do this, click the Capture menu, choose Options, and click
6 COMP 2000 W 2012 Lab no. 3 Page 6 of 11 Wireless Settings. The menu Advanced Wireless Settings will appear where you can change the channel. Consider filtering the packet capture to reduce clutter when analyzing packet traces. For example, you may be troubleshooting a particular client device connecting to the network. In this case, you can set a filter that excludes all packets except those associated with the IP address of the client you re troubleshooting. To set a filter, click the Capture menu, choose Options, and click Capture Filter. The Wireshark Capture Filter window will appear where you can set various filters. To start the packet capturing process, click the Capture menu and choose Start. Wireshark will continue capturing and displaying packets until the capture buffer fills up. The buffer is 1 Mbytes by default. This size is generally good enough, but to change it click the Capture menu, choose Options, and adjust the Buffer size value accordingly. When you re done capturing packets, click the Capture menu and choose Stop. Alternatively, you can set the capture run length (in packets or minutes), and the capture will automatically stop when that length has been met. You ll be prompted to save the capture for later viewing. The packet capture will display the details of each packet as they were transmitted over the wireless LAN. The figure is a screenshot of a sample packet capture window. The top panel of the window identifies each packet s source and destination nodes, the protocol used, and further information about each packet. You can select a specific packet to display more details. For example, packet 334 in the figure contains an HTTP message. The middle panel displays information about this packet, and you can choose a specific field of the packet, and the contents of that field are displayed in binary and ASCII format in the bottom panel. As a result, you re able to analyze the flow and view each field (including data field payloads) of all packets.
7 COMP 2000 W 2012 Lab no. 3 Page 7 of 11 Website You will find lots of useful information on the Wireshark homepage at The Wireshark Wiki at provides a wide range of information related to Wireshark and packet capturing in general. You will find a lot of information not part of this user s guide. You can find another wireshark user guide at There are samples of captured file at
8 COMP 2000 W 2012 Lab no. 3 Page 8 of 11 Lab 3. Network Packets and Wireless Devices In this lab, you are encouraged to explore network traffic from and to a wireless device using the Wireshark packet analysis program.. The lab has four activities, labelled as explorations. The first 2 activities are worth 15 points each; the last two activities are worth 35 points each. Create a lab report to be submitted, which includes your observations for each activity. Observations should include any program out you consider relevant, answers to the questions put forward on in these lab instructions, and any conclusions appropriate to the activity. You can create your lab report using a word processor to type your observations, including screen images. You may need to learn how to make screen captures and paste the screen images into your lab report. The lab makes use of ipod Touch mobile devices and their internet connection. In activities 1 and 2, you need to connect to the campus network. If you have a wireless account and password, you can use them to connect. Otherwise, you may need to borrow one of the devices from an instructor or a classmate for these activities. Activities 3 and 4 involve using wireshark to look at packets sent to and from the ipod device. Since the university network uses secure encryption, you won t be able to see many details in the data traffic. Everything inside the link layer protocol (that is, the wireless protocol) may be encrypted. For this reason, and also because we should only be sniffing traffic with the users permission, we will set up a wireless router and server that is not connected to the internet, and you can examine packets sent to and from that isolated server. In activity 3, you will look at unsecure unencrypted traffic, and in activity 4, you will look at the traffic with router-level encryption turned on. Before beginning activities 1 and 2, you will need to connect the ipod device to the campus network. Instructions for connecting the device are included at the beginning of the lab. Lab Exploration 1. Latency with PING Instructions: Using the PING utility from an ipod Touch device, determine the latency to two common sites. Try something close, like and something more remote, like Explain the different results. Keep in mind with this exercise that many sites may not respond to the requests sent by
9 COMP 2000 W 2012 Lab no. 3 Page 9 of 11 ping or the responses may be blocked by intervening sites. Lab Exploration 2. Multiple hops using Labnet Instructions: Using the TRACEROUTE utility from an ipod Touch device, to show the intervening hops between you and those sites. Try something close, like and something more remote, like If any intervening sites have domain names, see if you can tell anything about them. Explain why the results are different for the two different sites. Keep in mind with this exercise that many sites may not respond to the requests sent by traceroute or the responses may be blocked by intervening sites. Lab Exploration 3. Examine Wireless packets For this exercise, you should disconnect the wireless device (ipod) from the internet and connect to our isolated router and server. Remember to remove all of your account and/or password information from the device after completing lab exercise 2. This exercise has two parts: (1) using the wireless service with the mobile device, while the lab assistant collects traffic information, and (2) using wireshark to analyze the data. You won t be able to perform the data capture yourself on the wireless device. Part 1. Use the wireless service A. Connect to the wireless service. See the introduction on connecting to the router (without security) B. Start the ipod web browser Safari program C. Make sure the lab assistant is started capturing wireless packets using wireshark. D. Browse to the website on the isolated server. The URL Web Address will be provided for you by the lab assistant. E. You should see the web site shown in the figure below. Type in some unique message to distinguish your message from other people in the class. F. Submit your answer on the web page. You should get a response back from the server. G. Let the lab assitant know you have completed the task, so packet capture can stop.
10 COMP 2000 W 2012 Lab no. 3 Page 10 of 11 Part 2. Packet analysis The lab assistant will now put the saved packet capture on a common file for you to access. You ll need to log onto a workstation, start up wireshark and load the file in order to see the data. A. Start Wireshark, installing it if necessary. B. Get the location of the captured data file from the lab assistant C. Load the captured data file into Wireshark D. Complete the lab activity as instructed below Instructions: Recall the web page access you performed in part 1. Find the packets corresponding to sending your unique message to the web server, and the packet that carries the web server s response. HINT: these should correspond to POST and GET actions under the HTTP protocol. Include the packets you found in your observations (you may want to use screen capture for this). In the packet, identify your IP address for your device. Also identify the unique message you entered in the web page, indicating where it occurs in the packet data. Practice: This is not required, but you can practice wireshark by looking at some data already captured in the lab. Data files are available on the course web page for this practice. In order to look for the information in the packets, you need to know that in this practice scenario, the server URL web page address was the server IP address was: , the Ipod IP address was: , and the message typed into the webpage was why are dog noses always wet?
11 COMP 2000 W 2012 Lab no. 3 Page 11 of 11 Lab Exploration 4. Examine Secure Wireless packets This activity repeats the activity of exploration 4, but this time the router will be set to encrypt all of the traffic. This means that everything above the Link Layer of the Protocol Stack should be encrypted by the router for its hop to your ipod device, and you should not be able to see any information that is secured in this fashion, even using wireshark. In this activity, the instructions have changed so you can examine what information is now hidden from the user, and you are asked to reflect on the security effects. Wait for the lab instructor to start the secure router service, then repeat the steps of Activity 3, part 1, A-E, connecting to the secure server in step A. Wait for the lab instructor to make the new capture of secure data available as a data file, and then Repeat the steps of Activity 3, part 2, A-D, but use the instructions below. Instructions: Try to find the packets corresponding to sending your unique message to the web server, and the packet that carries the web server s response. What difficulties do you encounter that were not apparent in the unsecure version of this activity? Explain what information is no longer available to Wireshark that you used in activity 3, and explain how the devices are still able to communicate without this information being available in the captured data. Show packet traffic to illustrate your discussion of what information is unavailable. Practice: This is not required, but you can practice wireshark by looking at some data already captured in the lab. Data files are available on the course web page for this practice. For the secured data capture, you need to know that in this practice scenario, the server URL web page address was the server IP address was: , the Ipod IP address was: , and the message typed into the webpage was because they lick their noses
9. Wireshark I: Protocol Stack and Ethernet
 Distributed Systems 205/2016 Lab Simon Razniewski/Florian Klement 9. Wireshark I: Protocol Stack and Ethernet Objective To learn how protocols and layering are represented in packets, and to explore the
Distributed Systems 205/2016 Lab Simon Razniewski/Florian Klement 9. Wireshark I: Protocol Stack and Ethernet Objective To learn how protocols and layering are represented in packets, and to explore the
Lab Exercise Protocol Layers
 Lab Exercise Protocol Layers Objective To learn how protocols and layering are represented in packets. They are key concepts for structuring networks that are covered in 1.3 and 1.4 of your text. Review
Lab Exercise Protocol Layers Objective To learn how protocols and layering are represented in packets. They are key concepts for structuring networks that are covered in 1.3 and 1.4 of your text. Review
Networking Background
 Networking Background CMSC 414 October 30, 2017 General Overview We are going to take a quick look at What a network protocol is The abstract design of the network The 7-Layer network stack Protocols We
Networking Background CMSC 414 October 30, 2017 General Overview We are going to take a quick look at What a network protocol is The abstract design of the network The 7-Layer network stack Protocols We
ICS 351: Networking Protocols
 ICS 351: Networking Protocols IP packet forwarding application layer: DNS, HTTP transport layer: TCP and UDP network layer: IP, ICMP, ARP data-link layer: Ethernet, WiFi 1 Networking concepts each protocol
ICS 351: Networking Protocols IP packet forwarding application layer: DNS, HTTP transport layer: TCP and UDP network layer: IP, ICMP, ARP data-link layer: Ethernet, WiFi 1 Networking concepts each protocol
Wireshark Lab: Getting Started v7.0
 Wireshark Lab: Getting Started v7.0 Supplement to Computer Networking: A Top-Down Approach, 7th ed., J.F. Kurose and K.W. Ross Tell me and I forget. Show me and I remember. Involve me and I understand.
Wireshark Lab: Getting Started v7.0 Supplement to Computer Networking: A Top-Down Approach, 7th ed., J.F. Kurose and K.W. Ross Tell me and I forget. Show me and I remember. Involve me and I understand.
COMPUTER NETWORKING LAB EXERCISES (TP) 4
 Name 1: Name 2: Group number: COMPUTER NETWORKING LAB EXERCISES (TP) 4 IPV6 December 14, 2009 Abstract In this TP you will revisit some of the basic networking tools that were introduced in TP1, only this
Name 1: Name 2: Group number: COMPUTER NETWORKING LAB EXERCISES (TP) 4 IPV6 December 14, 2009 Abstract In this TP you will revisit some of the basic networking tools that were introduced in TP1, only this
Lab 6.7.1: Ping and Traceroute
 Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway R1-ISP R2-Central Eagle Server S0/0/0 10.10.10.6 255.255.255.252 N/A Fa0/0 192.168.254.253 255.255.255.0 N/A S0/0/0
Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway R1-ISP R2-Central Eagle Server S0/0/0 10.10.10.6 255.255.255.252 N/A Fa0/0 192.168.254.253 255.255.255.0 N/A S0/0/0
Wireshark Lab: Getting Started v7.0
 Wireshark Lab: Getting Started v7.0 Adapted by HMC from the supplement to Computer Networking: A Top-Down Approach, 7 th ed., J.F. Kurose and K.W. Ross Tell me and I forget. Show me and I remember. Involve
Wireshark Lab: Getting Started v7.0 Adapted by HMC from the supplement to Computer Networking: A Top-Down Approach, 7 th ed., J.F. Kurose and K.W. Ross Tell me and I forget. Show me and I remember. Involve
Wireshark Lab: Getting Started v6.0
 Wireshark Lab: Getting Started v6.0 Supplement to Computer Networking: A Top-Down Approach, 6 th ed., J.F. Kurose and K.W. Ross Tell me and I forget. Show me and I remember. Involve me and I understand.
Wireshark Lab: Getting Started v6.0 Supplement to Computer Networking: A Top-Down Approach, 6 th ed., J.F. Kurose and K.W. Ross Tell me and I forget. Show me and I remember. Involve me and I understand.
June Using Apple AirPrint with Xerox ConnectKey Devices User Guide
 June 2013 Using Apple AirPrint with Xerox ConnectKey Devices User Guide 2013 Xerox Corporation. All rights reserved. Xerox, Xerox and Design and ConnectKey are trademarks of the Xerox Corporation in the
June 2013 Using Apple AirPrint with Xerox ConnectKey Devices User Guide 2013 Xerox Corporation. All rights reserved. Xerox, Xerox and Design and ConnectKey are trademarks of the Xerox Corporation in the
Connecting Your iphone, ipad, or ipod touch to the NEIU Secured Network
 Connecting Your iphone, ipad, or ipod touch to the NEIU Secured Network This document has been written to assist Northeastern Illinois University faculty, staff, and students connect their iphones, ipads,
Connecting Your iphone, ipad, or ipod touch to the NEIU Secured Network This document has been written to assist Northeastern Illinois University faculty, staff, and students connect their iphones, ipads,
Genie Snoop lab. Laboration in data communication GenieLab Department of Information Technology, Uppsala University
 Genie Snoop lab Laboration in data communication GenieLab Department of Information Technology, Uppsala University Overview This lab deals with network layers, services and HTTP transactions as well as
Genie Snoop lab Laboration in data communication GenieLab Department of Information Technology, Uppsala University Overview This lab deals with network layers, services and HTTP transactions as well as
Computer Networks Security: intro. CS Computer Systems Security
 Computer Networks Security: intro CS 166 - Computer Systems Security A very easy network 3/14/16 Computer Networks: Intro 2 Two philosophers example Translator Language Translator Engineer Communication
Computer Networks Security: intro CS 166 - Computer Systems Security A very easy network 3/14/16 Computer Networks: Intro 2 Two philosophers example Translator Language Translator Engineer Communication
Lab Assignment 4 ECE374 Spring Posted: 03/22/18 Due: 03/29/18. In this lab, we ll take a quick look at the ICMP and IP protocols.
 Lab Assignment 4 ECE374 Spring 2018 Posted: 03/22/18 Due: 03/29/18 In this lab, we ll take a quick look at the ICMP and IP protocols. Whenever possible you should hand in Wireshark screenshots that you
Lab Assignment 4 ECE374 Spring 2018 Posted: 03/22/18 Due: 03/29/18 In this lab, we ll take a quick look at the ICMP and IP protocols. Whenever possible you should hand in Wireshark screenshots that you
Lab Two Using Wireshark to Discover IP NAME:
 Lab Two Using Wireshark to Discover IP NAME: In this lab, we ll investigate the IP protocol, focusing on the IP datagram. We ll do so by analyzing a trace of IP datagrams sent and received by an execution
Lab Two Using Wireshark to Discover IP NAME: In this lab, we ll investigate the IP protocol, focusing on the IP datagram. We ll do so by analyzing a trace of IP datagrams sent and received by an execution
RFT CARES ios App Administrator Guide
 RFT CARES ios App Administrator Guide 2017 RF Technologies, Inc. All specifications subject to change without notice. All Rights Reserved. No Part of this work may be reproduced or copied in any form or
RFT CARES ios App Administrator Guide 2017 RF Technologies, Inc. All specifications subject to change without notice. All Rights Reserved. No Part of this work may be reproduced or copied in any form or
Packet: Data can be broken into distinct pieces or packets and then reassembled after delivery. Computers on the Internet communicate via packets.
 Broadband Setup from A to Z Print out all the info below and get to work...have fun!! A word of caution! It is very important that you SECURE your wireless network using WEP or WPA encryption (password).
Broadband Setup from A to Z Print out all the info below and get to work...have fun!! A word of caution! It is very important that you SECURE your wireless network using WEP or WPA encryption (password).
Introduction to Computer Networks. CS 166: Introduction to Computer Systems Security
 Introduction to Computer Networks CS 166: Introduction to Computer Systems Security Network Communication Communication in modern networks is characterized by the following fundamental principles Packet
Introduction to Computer Networks CS 166: Introduction to Computer Systems Security Network Communication Communication in modern networks is characterized by the following fundamental principles Packet
Lab 2: Network Troubleshooting NET311 - Computer Networks Management
 Lab 2: Network Troubleshooting NET311 - Computer Networks Management Instructor: Dr. Mostafa Dahshan Objectives 1. Use protocol analyzers, such as Wireshark, to inspect the packet contents. 2. Use basic
Lab 2: Network Troubleshooting NET311 - Computer Networks Management Instructor: Dr. Mostafa Dahshan Objectives 1. Use protocol analyzers, such as Wireshark, to inspect the packet contents. 2. Use basic
XFINITY Welcome Packet
 XFINITY Welcome Packet Welcome! Your building comes with a fast, reliable property-wide WiFi network as well as access to our popular XFINITY TV video streaming service for university students. In the
XFINITY Welcome Packet Welcome! Your building comes with a fast, reliable property-wide WiFi network as well as access to our popular XFINITY TV video streaming service for university students. In the
HW/Lab 4: IPSec and Wireless Security. CS 336/536: Computer Network Security DUE 11 am on 12/01/2014 (Monday)
 HW/Lab 4: IPSec and Wireless Security CS 336/536: Computer Network Security DUE 11 am on 12/01/2014 (Monday) This HW/Lab assignment covers Lectures 8 (IPSec) and 10 (Wireless Security). Please review these
HW/Lab 4: IPSec and Wireless Security CS 336/536: Computer Network Security DUE 11 am on 12/01/2014 (Monday) This HW/Lab assignment covers Lectures 8 (IPSec) and 10 (Wireless Security). Please review these
Project points. CSE422 Computer Networking Spring 2018
 Project 1 100 points Introduction One s understanding of network protocols can often be greatly deepened by seeing protocols in action and by playing around with protocols observing the sequence of messages
Project 1 100 points Introduction One s understanding of network protocols can often be greatly deepened by seeing protocols in action and by playing around with protocols observing the sequence of messages
CSE4344 Project 2 (Spring 2017) Wireshark Lab: HTTP
 Objectives CSE4344 Project 2 (Spring 2017) Wireshark Lab: HTTP To get familiar with capturing network packets using Wireshark. To explore the HTTP message formats and basic operations of HTTP protocol.
Objectives CSE4344 Project 2 (Spring 2017) Wireshark Lab: HTTP To get familiar with capturing network packets using Wireshark. To explore the HTTP message formats and basic operations of HTTP protocol.
Department Of Computer Science
 Department Of Computer Science Laboratory Manual Prepared By: Muhammad Nouman Farooq Lecturer and Course Coordinator Course: Network Security (CS-242) Page 1 of 47 Table of Contents Lab 1- Introduction
Department Of Computer Science Laboratory Manual Prepared By: Muhammad Nouman Farooq Lecturer and Course Coordinator Course: Network Security (CS-242) Page 1 of 47 Table of Contents Lab 1- Introduction
Wireshark HTTP. Introduction. The Basic HTTP GET/response interaction
 Wireshark HTTP Introduction Having gotten our feet wet with the Wireshark packet sniffer in the introductory lab, we re now ready to use Wireshark to investigate protocols in operation. In this lab, we
Wireshark HTTP Introduction Having gotten our feet wet with the Wireshark packet sniffer in the introductory lab, we re now ready to use Wireshark to investigate protocols in operation. In this lab, we
Smart Device Simple World
 Smart Device Simple World Thank you for choosing HUAWEI Mobile WiFi Supported functions and actual appearance depend on the specific models you purchased. The illustrations are provided for your reference
Smart Device Simple World Thank you for choosing HUAWEI Mobile WiFi Supported functions and actual appearance depend on the specific models you purchased. The illustrations are provided for your reference
Problem Set 10 Due: Start of class December 11
 CS242 Computer Networks Handout # 20 Randy Shull December 4, 2017 Wellesley College Problem Set 10 Due: Start of class December 11 Reading: Kurose & Ross, Sections 7.1 7.3, 8.1 8.4 Wireshark Lab [16] Recall
CS242 Computer Networks Handout # 20 Randy Shull December 4, 2017 Wellesley College Problem Set 10 Due: Start of class December 11 Reading: Kurose & Ross, Sections 7.1 7.3, 8.1 8.4 Wireshark Lab [16] Recall
How to connect to a Wi-Fi or Wireless Network
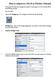 How to connect to a Wi-Fi or Wireless Network This guide will walk you through the steps of connecting to a Wi-Fi network that is broadcasting its name. Start the ipad. 1. Tap on the Settings app. The
How to connect to a Wi-Fi or Wireless Network This guide will walk you through the steps of connecting to a Wi-Fi network that is broadcasting its name. Start the ipad. 1. Tap on the Settings app. The
VERSION Lab 3: Link Layer
 Lab 3: Link Layer Objective In this lab, you will investigate Ethernet and the ARP protocol. You will also prove you are a Wireshark Ninja by dissecting an unknown protocol. Knowledge from Lecture 20 and
Lab 3: Link Layer Objective In this lab, you will investigate Ethernet and the ARP protocol. You will also prove you are a Wireshark Ninja by dissecting an unknown protocol. Knowledge from Lecture 20 and
Monitoring the Mobility Express Network
 About the Cisco Mobility Express Monitoring Service, on page 1 Customizing the Network Summary View, on page 2 Viewing the Details of Configured WLANs, on page 5 Customizing Access Points Table View, on
About the Cisco Mobility Express Monitoring Service, on page 1 Customizing the Network Summary View, on page 2 Viewing the Details of Configured WLANs, on page 5 Customizing Access Points Table View, on
Methodist University. Wireless Connectivity Guide. Version 1.5.0
 Methodist University Wireless Connectivity Guide Version 1.5.0 Guide Updates... 3 Getting Started... 4 Available SSID s... 5 Unsecured Connectivity... 5 Methodist University... 5 MU_Guest... 5 MU_Devices...
Methodist University Wireless Connectivity Guide Version 1.5.0 Guide Updates... 3 Getting Started... 4 Available SSID s... 5 Unsecured Connectivity... 5 Methodist University... 5 MU_Guest... 5 MU_Devices...
CS 3640: Introduction to Networks and Their Applications
 CS 3640: Introduction to Networks and Their Applications Fall 2018, Lecture 2: More layering and the end-to-end principle. Instructor: Rishab Nithyanand Teaching Assistant: Md. Kowsar Hossain 1 Today in
CS 3640: Introduction to Networks and Their Applications Fall 2018, Lecture 2: More layering and the end-to-end principle. Instructor: Rishab Nithyanand Teaching Assistant: Md. Kowsar Hossain 1 Today in
RouterCheck Installation and Usage
 RouterCheck Installation and Usage February 16, 2015 No part of this document may be reproduced, copied, or distributed in any fashion without the express written permission of Sericon Technology Inc.
RouterCheck Installation and Usage February 16, 2015 No part of this document may be reproduced, copied, or distributed in any fashion without the express written permission of Sericon Technology Inc.
How to configure a wireless router
 How to configure a wireless router Your wireless router has documentation explaining how to configure it. There are differences between manufacturers. This document explains how to configure a NetGear
How to configure a wireless router Your wireless router has documentation explaining how to configure it. There are differences between manufacturers. This document explains how to configure a NetGear
Event Password: NationalCenter2017 DON T FORGET STEP 2 ON THE NEXT PAGE!
 Hi, We ve built a mobile app for 2017 Parents as Teachers International Conference! It has all the important information you ll need for the event, and features to enhance your event experience. Step 1:
Hi, We ve built a mobile app for 2017 Parents as Teachers International Conference! It has all the important information you ll need for the event, and features to enhance your event experience. Step 1:
VMware AirWatch tvos Platform Guide Deploying and managing tvos devices
 VMware AirWatch tvos Platform Guide Deploying and managing tvos devices AirWatch v9.3 Have documentation feedback? Submit a Documentation Feedback support ticket using the Support Wizard on support.air-watch.com.
VMware AirWatch tvos Platform Guide Deploying and managing tvos devices AirWatch v9.3 Have documentation feedback? Submit a Documentation Feedback support ticket using the Support Wizard on support.air-watch.com.
AirServer Connect User Guide
 1 Contents Welcome... 3 Unique features... 3 Set up your AirServer Connect... 4 The Home Screen... 5 Navigating Menus... 5 Configuring Basic Settings... 6 Screen Mirroring Methods... 7 Airplay... 7 Mac...
1 Contents Welcome... 3 Unique features... 3 Set up your AirServer Connect... 4 The Home Screen... 5 Navigating Menus... 5 Configuring Basic Settings... 6 Screen Mirroring Methods... 7 Airplay... 7 Mac...
Web Mechanisms. Draft: 2/23/13 6:54 PM 2013 Christopher Vickery
 Web Mechanisms Draft: 2/23/13 6:54 PM 2013 Christopher Vickery Introduction While it is perfectly possible to create web sites that work without knowing any of their underlying mechanisms, web developers
Web Mechanisms Draft: 2/23/13 6:54 PM 2013 Christopher Vickery Introduction While it is perfectly possible to create web sites that work without knowing any of their underlying mechanisms, web developers
CS519: Computer Networks. Lecture 2: Feb 2, 2004 IP (Internet Protocol)
 : Computer Networks Lecture 2: Feb 2, 2004 IP (Internet Protocol) A hypothetical service You want a mail delivery service You have two choices: Acme Guaranteed Mail Delivery Service We never fail Rocko
: Computer Networks Lecture 2: Feb 2, 2004 IP (Internet Protocol) A hypothetical service You want a mail delivery service You have two choices: Acme Guaranteed Mail Delivery Service We never fail Rocko
UIP1869V User Interface Guide
 UIP1869V User Interface Guide (Firmware version 0.1.8 and later) Table of Contents Opening the UIP1869V's Configuration Utility... 3 Connecting to Your Broadband Modem... 5 Setting up with DHCP... 5 Updating
UIP1869V User Interface Guide (Firmware version 0.1.8 and later) Table of Contents Opening the UIP1869V's Configuration Utility... 3 Connecting to Your Broadband Modem... 5 Setting up with DHCP... 5 Updating
Module 11 Technical Troubleshooting for Restaurant Managers
 Module 11 Technical Troubleshooting for Restaurant Managers Overview This module is about troubleshooting at an introductory level and to help you gain confidence and knowledge to problem-solve Pilot POS
Module 11 Technical Troubleshooting for Restaurant Managers Overview This module is about troubleshooting at an introductory level and to help you gain confidence and knowledge to problem-solve Pilot POS
Quick Installation Guide
 V38.01 IP Wireless / Wired Camera Quick Installation Guide (For Windows OS) ShenZhen Foscam Intelligent Technology Co., Ltd Packing List Quick Installation Guide 1) IP CAMERA X 1 2) Wi-Fi Antenna (only
V38.01 IP Wireless / Wired Camera Quick Installation Guide (For Windows OS) ShenZhen Foscam Intelligent Technology Co., Ltd Packing List Quick Installation Guide 1) IP CAMERA X 1 2) Wi-Fi Antenna (only
Sierra Radio Systems. WiFly Configuration. Quick Reference. Version 1.0
 Sierra Radio Systems WiFly Configuration Quick Reference Version 1.0 Hardware Connections SERIAL PORT CONNECTIONS FOR WIFLY DEVICE PROGRAMMING The serial port on the WiFly device provides a 3.3v logic
Sierra Radio Systems WiFly Configuration Quick Reference Version 1.0 Hardware Connections SERIAL PORT CONNECTIONS FOR WIFLY DEVICE PROGRAMMING The serial port on the WiFly device provides a 3.3v logic
PreLab for CS356 Lab NIL (Lam) (To be submitted when you come for the lab)
 PreLab for CS356 Lab NIL (Lam) (To be submitted when you come for the lab) Name: UT EID: 1. Differentiate between Routers, Switches, and Hubs. 2. Explain subnet masks. 3. For this lab, where is subnet
PreLab for CS356 Lab NIL (Lam) (To be submitted when you come for the lab) Name: UT EID: 1. Differentiate between Routers, Switches, and Hubs. 2. Explain subnet masks. 3. For this lab, where is subnet
A+ Guide to Managing & Maintaining Your PC, 8th Edition. Chapter 17 Windows Resources on a Network
 Chapter 17 Windows Resources on a Network Objectives Learn how to support some client/server applications Learn how to share and secure files and folders on the network Learn how to troubleshoot network
Chapter 17 Windows Resources on a Network Objectives Learn how to support some client/server applications Learn how to share and secure files and folders on the network Learn how to troubleshoot network
Quick Install Guide. Model: PLC-223W, PLC-233W
 Quick Install Guide Model: PLC-223W, PLC-233W This installation guide provides basic instructions for installing the PLC-213W/ PLC-223W/PLC-233W indoor wireless IP camera on your network. By following
Quick Install Guide Model: PLC-223W, PLC-233W This installation guide provides basic instructions for installing the PLC-213W/ PLC-223W/PLC-233W indoor wireless IP camera on your network. By following
Access Switch VLAN Y Y.1 /24
 Topology: Fa 0/1 VNC Server Fa 0/0 Port B Access Router Trunk VLAN X Access Switch VLAN Y Backbone Router 141.85.Y.1 /24 28.0.0.42 OSPF X.0.0.0/8 Port A 27.45.67.89 Work Station DHCP Server The Goal: Connect
Topology: Fa 0/1 VNC Server Fa 0/0 Port B Access Router Trunk VLAN X Access Switch VLAN Y Backbone Router 141.85.Y.1 /24 28.0.0.42 OSPF X.0.0.0/8 Port A 27.45.67.89 Work Station DHCP Server The Goal: Connect
Ayrstone AyrMesh Router Setup
 Ayrstone AyrMesh Router Setup This guide should help you set up AyrMesh Router SP. The setup is relatively simple but should you need more detailed directions, such as slide shows, video, or troubleshooting
Ayrstone AyrMesh Router Setup This guide should help you set up AyrMesh Router SP. The setup is relatively simple but should you need more detailed directions, such as slide shows, video, or troubleshooting
Experiment 2: Wireshark as a Network Protocol Analyzer
 Experiment 2: Wireshark as a Network Protocol Analyzer Learning Objectives: To become familiarized with the Wireshark application environment To perform basic PDU capture using Wireshark To perform basic
Experiment 2: Wireshark as a Network Protocol Analyzer Learning Objectives: To become familiarized with the Wireshark application environment To perform basic PDU capture using Wireshark To perform basic
Lab 4: Network Packet Capture and Analysis using Wireshark
 Lab 4: Network Packet Capture and Analysis using Wireshark 4.1 Details Aim: To provide a foundation in network packet capture and analysis. You may be faced with network traffic analysis, from traffic
Lab 4: Network Packet Capture and Analysis using Wireshark 4.1 Details Aim: To provide a foundation in network packet capture and analysis. You may be faced with network traffic analysis, from traffic
Objectives: (1) To learn to capture and analyze packets using wireshark. (2) To learn how protocols and layering are represented in packets.
 Team Project 1 Due: Beijing 00:01, Friday Nov 7 Language: English Turn-in (via email) a.pdf file. Objectives: (1) To learn to capture and analyze packets using wireshark. (2) To learn how protocols and
Team Project 1 Due: Beijing 00:01, Friday Nov 7 Language: English Turn-in (via email) a.pdf file. Objectives: (1) To learn to capture and analyze packets using wireshark. (2) To learn how protocols and
DKT 224/3 LAB 2 NETWORK PROTOCOL ANALYZER DATA COMMUNICATION & NETWORK SNIFFING AND IDENTIFY PROTOCOL USED IN LIVE NETWORK
 DKT 224/3 DATA COMMUNICATION & NETWORK LAB 2 NETWORK PROTOCOL ANALYZER SNIFFING AND IDENTIFY PROTOCOL USED IN LIVE NETWORK Lab #2 2 Lab #2 : Network Protocol Analyzer (Sniffing and Identify Protocol used
DKT 224/3 DATA COMMUNICATION & NETWORK LAB 2 NETWORK PROTOCOL ANALYZER SNIFFING AND IDENTIFY PROTOCOL USED IN LIVE NETWORK Lab #2 2 Lab #2 : Network Protocol Analyzer (Sniffing and Identify Protocol used
Protocol Layers & Wireshark TDTS11:COMPUTER NETWORKS AND INTERNET PROTOCOLS
 Protocol Layers & Wireshark TDTS11:COMPUTER NETWORKS AND INTERNET PROTOCOLS Mail seban649@student.liu.se Protocol Hi Hi Got the time? 2:00 time TCP connection request TCP connection response Whats
Protocol Layers & Wireshark TDTS11:COMPUTER NETWORKS AND INTERNET PROTOCOLS Mail seban649@student.liu.se Protocol Hi Hi Got the time? 2:00 time TCP connection request TCP connection response Whats
Thank you for purchasing the Mobile WiFi. This Mobile WiFi brings you a high speed wireless network connection.
 Quick Start Thank you for purchasing the Mobile WiFi. This Mobile WiFi brings you a high speed wireless network connection. This document will help you understand your Mobile WiFi so you can start using
Quick Start Thank you for purchasing the Mobile WiFi. This Mobile WiFi brings you a high speed wireless network connection. This document will help you understand your Mobile WiFi so you can start using
BSc Year 2 Data Communications Lab - Using Wireshark to View Network Traffic. Topology. Objectives. Background / Scenario
 BSc Year 2 Data Communications Lab - Using Wireshark to View Network Traffic Topology Objectives Part 1: (Optional) Download and Install Wireshark Part 2: Capture and Analyze Local ICMP Data in Wireshark
BSc Year 2 Data Communications Lab - Using Wireshark to View Network Traffic Topology Objectives Part 1: (Optional) Download and Install Wireshark Part 2: Capture and Analyze Local ICMP Data in Wireshark
COMPUTER NETWORKING LAB EXERCISES (TP) 1 BASIC CONFIGURATION AND TOOLS FOR EVERYBODY:
 Name 1: Name 2: Group number: COMPUTER NETWORKING LAB EXERCISES (TP) 1 BASIC CONFIGURATION AND TOOLS FOR EVERYBODY: PING(6), DIG, TRACEROUTE(6), NETSTAT September 24, 2012 Abstract In this TP you will
Name 1: Name 2: Group number: COMPUTER NETWORKING LAB EXERCISES (TP) 1 BASIC CONFIGURATION AND TOOLS FOR EVERYBODY: PING(6), DIG, TRACEROUTE(6), NETSTAT September 24, 2012 Abstract In this TP you will
Problem Set 7 Due: Start of Class, November 2
 CS242 Computer Networks Handout # 14 Randy Shull October 26, 2017 Wellesley College Problem Set 7 Due: Start of Class, November 2 Reading: Kurose & Ross, Sections 3.6, 3.7, 3.8 Wireshark Lab [26] In these
CS242 Computer Networks Handout # 14 Randy Shull October 26, 2017 Wellesley College Problem Set 7 Due: Start of Class, November 2 Reading: Kurose & Ross, Sections 3.6, 3.7, 3.8 Wireshark Lab [26] In these
CSCD 433/533 Advanced Networks
 CSCD 433/533 Advanced Networks Lecture 2 Network Review Winter 2017 Reading: Chapter 1 1 Topics Network Topics Some Review from CSCD330 Applications Common Services Architecture OSI Model AS and Routing
CSCD 433/533 Advanced Networks Lecture 2 Network Review Winter 2017 Reading: Chapter 1 1 Topics Network Topics Some Review from CSCD330 Applications Common Services Architecture OSI Model AS and Routing
Using Apple AirPrint with Xerox Devices Built on Xerox ConnectKey Technology User Guide. February 2016
 Using Apple AirPrint with Xerox Devices Built on Xerox ConnectKey Technology User Guide February 2016 2016 Xerox Corporation. All rights reserved. Xerox, Xerox and Design and ConnectKey are trademarks
Using Apple AirPrint with Xerox Devices Built on Xerox ConnectKey Technology User Guide February 2016 2016 Xerox Corporation. All rights reserved. Xerox, Xerox and Design and ConnectKey are trademarks
UNI CS 3470 Networking Project 5: Using Wireshark to Analyze Packet Traces 12
 UNI CS 3470 Networking Project 5: Using Wireshark to Analyze Packet Traces 12 Due Wednesday, 12/7, at 11:59:59 PM. One s understanding of network protocols can often be greatly deepened by seeing protocols
UNI CS 3470 Networking Project 5: Using Wireshark to Analyze Packet Traces 12 Due Wednesday, 12/7, at 11:59:59 PM. One s understanding of network protocols can often be greatly deepened by seeing protocols
ECE 697J Advanced Topics in Computer Networks
 ECE 697J Advanced Topics in Computer Networks Network Measurement 12/02/03 Tilman Wolf 1 Overview Lab 3 requires performance measurement Throughput Collecting of packet headers Network Measurement Active
ECE 697J Advanced Topics in Computer Networks Network Measurement 12/02/03 Tilman Wolf 1 Overview Lab 3 requires performance measurement Throughput Collecting of packet headers Network Measurement Active
Wireshark Lab: Getting Started v6.0
 Wireshark Lab: Getting Started v6.0 Supplement to Computer Networking: A Top-Down Approach, 6 th ed., J.F. Kurose and K.W. Ross Tell me and I forget. Show me and I remember. Involve me and I understand.
Wireshark Lab: Getting Started v6.0 Supplement to Computer Networking: A Top-Down Approach, 6 th ed., J.F. Kurose and K.W. Ross Tell me and I forget. Show me and I remember. Involve me and I understand.
R (2) Implementation of following spoofing assignments using C++ multi-core Programming a) IP Spoofing b) Web spoofing.
 R (2) N (5) Oral (3) Total (10) Dated Sign Experiment No: 1 Problem Definition: Implementation of following spoofing assignments using C++ multi-core Programming a) IP Spoofing b) Web spoofing. 1.1 Prerequisite:
R (2) N (5) Oral (3) Total (10) Dated Sign Experiment No: 1 Problem Definition: Implementation of following spoofing assignments using C++ multi-core Programming a) IP Spoofing b) Web spoofing. 1.1 Prerequisite:
ipad + itunes Tips & Tricks 2012
 Contents How to Set Up a Brand New ipad Without Wi-Fi Access... 1 Prevent Syncing... 4 Setting up an itunes Account Without a Credit Card... 5 Purchasing & Transferring Apps to an ipad Using a Laptop...
Contents How to Set Up a Brand New ipad Without Wi-Fi Access... 1 Prevent Syncing... 4 Setting up an itunes Account Without a Credit Card... 5 Purchasing & Transferring Apps to an ipad Using a Laptop...
Wireshark Lab: Getting Started v6.0 Supplement to Computer Networking: A Top-Down Approach, 6th ed., J.F. Kurose and K.W. Ross
 Wireshark Lab: Getting Started v6.0 Supplement to Computer Networking: A Top-Down Approach, 6th ed., J.F. Kurose and K.W. Ross 2005-21012, J.F Kurose and K.W. Ross, All Rights Reserved In the Wireshark
Wireshark Lab: Getting Started v6.0 Supplement to Computer Networking: A Top-Down Approach, 6th ed., J.F. Kurose and K.W. Ross 2005-21012, J.F Kurose and K.W. Ross, All Rights Reserved In the Wireshark
Vendor: Microsoft. Exam Code: Exam Name: MTA Security Fundamentals Practice Test. Version: Demo
 Vendor: Microsoft Exam Code: 98-367 Exam Name: MTA Security Fundamentals Practice Test Version: Demo DEMO QUESTION 1 To prevent users from copying data to removable media, you should: A. Lock the computer
Vendor: Microsoft Exam Code: 98-367 Exam Name: MTA Security Fundamentals Practice Test Version: Demo DEMO QUESTION 1 To prevent users from copying data to removable media, you should: A. Lock the computer
ERS-1.0 Web Server Ethernet/RS232 Adapter
 OWNER S MANUAL ERS-1.0 Web Server Ethernet/RS232 Adapter Revision 1 KIT INCLUDES: (1) RSA-1.0 (1) ERS-1.0 (1) 6 ft. DB9F to DB9F Null Modem Cable (1) ERS-1.0 Quick Start Guide EQUIPMENT NEEDED: (2) 6 ft.
OWNER S MANUAL ERS-1.0 Web Server Ethernet/RS232 Adapter Revision 1 KIT INCLUDES: (1) RSA-1.0 (1) ERS-1.0 (1) 6 ft. DB9F to DB9F Null Modem Cable (1) ERS-1.0 Quick Start Guide EQUIPMENT NEEDED: (2) 6 ft.
Spreedbox Getting Started Guide
 Spreedbox Getting Started Guide Last Updated: September 2017 CONTENTS 1. Introduction... 3 2. Prerequisites... 4 3. Opening the box... 5 4. USB Manual, Quick Start Guide & MAC Sticker... 6 5. International
Spreedbox Getting Started Guide Last Updated: September 2017 CONTENTS 1. Introduction... 3 2. Prerequisites... 4 3. Opening the box... 5 4. USB Manual, Quick Start Guide & MAC Sticker... 6 5. International
Wireless Printing Updated 10/30/2008 POLICY. The use of Wireless Networking is not permitted at any site for full client/server networking of Taxwise.
 Updated 10/30/2008 POLICY Tax-Aide Wireless Printing Policy The use of Wireless Networking is not permitted at any site for full client/server networking of Taxwise. Wireless networking, for the purpose
Updated 10/30/2008 POLICY Tax-Aide Wireless Printing Policy The use of Wireless Networking is not permitted at any site for full client/server networking of Taxwise. Wireless networking, for the purpose
Lab #4 TECH 4281 Spring 2015
 Lab #4 TECH 4281 Spring 2015 If you have not done so yet, install GNS3 from http://www.gns3.com/. When starting GNS3, please name the project Lab3_Yourname. For this lab, we will be using the Cisco.bin
Lab #4 TECH 4281 Spring 2015 If you have not done so yet, install GNS3 from http://www.gns3.com/. When starting GNS3, please name the project Lab3_Yourname. For this lab, we will be using the Cisco.bin
TROUBLESHOOTING GUIDE
 TROUBLESHOOTING GUIDE Difficulty installing apps on LeapFrog Epic tablet Q: While purchased apps appear in the App Manager on the "Not installed" tab, the Install button is grayed out. How can I install
TROUBLESHOOTING GUIDE Difficulty installing apps on LeapFrog Epic tablet Q: While purchased apps appear in the App Manager on the "Not installed" tab, the Install button is grayed out. How can I install
Thank you for purchasing the CPE. This CPE brings you a high speed wireless network connection.
 Quick Start Thank you for purchasing the CPE. This CPE brings you a high speed wireless network connection. This document will help you understand your CPE (customer premises equipment) so you can start
Quick Start Thank you for purchasing the CPE. This CPE brings you a high speed wireless network connection. This document will help you understand your CPE (customer premises equipment) so you can start
The Applications and Gaming Tab - Port Range Forward
 The Applications and Gaming Tab - Port Range Forward The Applications and Gaming Tab allows you to set up public services on your network, such as web servers, ftp servers, e-mail servers, or other specialized
The Applications and Gaming Tab - Port Range Forward The Applications and Gaming Tab allows you to set up public services on your network, such as web servers, ftp servers, e-mail servers, or other specialized
Networking. Robotics is networking. Liam Paull, co-inventor of Duckietown and professor at University of Montreal
 Networking Robotics is networking. Liam Paull, co-inventor of Duckietown and professor at University of Montreal 1 Programs nc (netcat) nmap traceroute ping whois wireshark iftop 2 3 Connecting to Your
Networking Robotics is networking. Liam Paull, co-inventor of Duckietown and professor at University of Montreal 1 Programs nc (netcat) nmap traceroute ping whois wireshark iftop 2 3 Connecting to Your
Thank you for purchasing the CharJi EVO CLOUD. This CharJi EVO CLOUD brings you a high speed wireless network connection.
 Thank you for purchasing the CharJi EVO CLOUD. This CharJi EVO CLOUD brings you a high speed wireless network connection. This document will help you understand your CharJi EVO CLOUD so you can start using
Thank you for purchasing the CharJi EVO CLOUD. This CharJi EVO CLOUD brings you a high speed wireless network connection. This document will help you understand your CharJi EVO CLOUD so you can start using
VMware Workspace ONE UEM Apple tvos Device Management. VMware Workspace ONE UEM 1811 VMware AirWatch
 VMware Workspace ONE UEM Apple tvos Device Management VMware Workspace ONE UEM 1811 VMware AirWatch You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/
VMware Workspace ONE UEM Apple tvos Device Management VMware Workspace ONE UEM 1811 VMware AirWatch You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/
NETWORK PACKET ANALYSIS PROGRAM
 NETWORK PACKET ANALYSIS PROGRAM Duration: 3 days (21 hours) Mode: 1. Instructor Led Class room Training and Labs 2. Online In this hands-on course, you will receive in-depth training on Protocol analysis
NETWORK PACKET ANALYSIS PROGRAM Duration: 3 days (21 hours) Mode: 1. Instructor Led Class room Training and Labs 2. Online In this hands-on course, you will receive in-depth training on Protocol analysis
Click on Close button to close Network Connection Details. You are back to the Local Area Connection Status window.
 How to configure EW-7228APn/EW-7416APn as a Repeater to extend wireless range This article can apply on EW-7228APn and EW-7416APn. We used screen shots of EW-7416APn in this instruction. We recommend you
How to configure EW-7228APn/EW-7416APn as a Repeater to extend wireless range This article can apply on EW-7228APn and EW-7416APn. We used screen shots of EW-7416APn in this instruction. We recommend you
CONFIGURATION MANUAL. English version
 CONFIGURATION MANUAL English version Frama F-Link Configuration Manual (EN) All rights reserved. Frama Group. The right to make changes in this Installation Guide is reserved. Frama Ltd also reserves the
CONFIGURATION MANUAL English version Frama F-Link Configuration Manual (EN) All rights reserved. Frama Group. The right to make changes in this Installation Guide is reserved. Frama Ltd also reserves the
Thank you for choosing the LTE Mobile WiFi Smart. The LTE Mobile WiFi Smart allows you to access a wireless network at high speeds.
 Thank you for choosing the LTE Mobile WiFi Smart. The LTE Mobile WiFi Smart allows you to access a wireless network at high speeds. Note: This guide briefly describes the appearance of the LTE Mobile WiFi
Thank you for choosing the LTE Mobile WiFi Smart. The LTE Mobile WiFi Smart allows you to access a wireless network at high speeds. Note: This guide briefly describes the appearance of the LTE Mobile WiFi
Setup Guide for Wi-Fi Hotspot Boosting Kit
 Setup Guide for WI-KIT-02 Wi-Fi Hotspot Boosting Kit Congratulations on purchasing the WI-KIT-02, this contains everything you need to be able to connect to Wi-Fi at a camp site / marina / other location.
Setup Guide for WI-KIT-02 Wi-Fi Hotspot Boosting Kit Congratulations on purchasing the WI-KIT-02, this contains everything you need to be able to connect to Wi-Fi at a camp site / marina / other location.
How do I configure my Roqos Core to work with a Verizon FIOS router?
 Getting Started How do I configure my Roqos Core to work with a Verizon FIOS router? A modem and wireless router come together in a Verizon FIOS router. Please refer to the instructions within the article
Getting Started How do I configure my Roqos Core to work with a Verizon FIOS router? A modem and wireless router come together in a Verizon FIOS router. Please refer to the instructions within the article
ICS 451: Today's plan
 ICS 451: Today's plan ICMP ping traceroute ARP DHCP summary of IP processing ICMP Internet Control Message Protocol, 2 functions: error reporting (never sent in response to ICMP error packets) network
ICS 451: Today's plan ICMP ping traceroute ARP DHCP summary of IP processing ICMP Internet Control Message Protocol, 2 functions: error reporting (never sent in response to ICMP error packets) network
OTC Student Wireless Network
 OTC Student Wireless Network (Connection Instructions for Windows 8, Windows 7, MAC OSX, ios and Kindle) Note: The OTC student wireless network conforms to the IEEE 802.11 a/b/g protocol and standards.
OTC Student Wireless Network (Connection Instructions for Windows 8, Windows 7, MAC OSX, ios and Kindle) Note: The OTC student wireless network conforms to the IEEE 802.11 a/b/g protocol and standards.
Thank You for Choosing the CRICKET CROSSWAVE
 CRICKET CROSSWAVE Thank You for Choosing the CRICKET CROSSWAVE The supported functions and actual appearance depend on the product you purchased. The following pictures are provided for illustration only.
CRICKET CROSSWAVE Thank You for Choosing the CRICKET CROSSWAVE The supported functions and actual appearance depend on the product you purchased. The following pictures are provided for illustration only.
CS356 Lab NIL (Lam) In this lab you will learn: Cisco 2600 Router Configuration Static Routing PartB 20 min Access Control Lists PartC 30 min Explore!
 CS356 Lab NIL (Lam) In this lab you will learn: PartA Time: 2 hrs 40 min Cisco 2600 Router Configuration Static Routing PartB 20 min Access Control Lists PartC 30 min Explore! Components used: 2 computers
CS356 Lab NIL (Lam) In this lab you will learn: PartA Time: 2 hrs 40 min Cisco 2600 Router Configuration Static Routing PartB 20 min Access Control Lists PartC 30 min Explore! Components used: 2 computers
CS 326e Lab 2, Edmondson-Yurkanan, Spring 2004 Router Configuration, Routing and Access Lists
 CS 326e Lab 2, Edmondson-Yurkanan, Spring 2004 Router Configuration, Routing and Access Lists Name: In this lab you will learn: PartA Cisco 2600 Router Configuration Static Routing PartB 20 min Dynamic
CS 326e Lab 2, Edmondson-Yurkanan, Spring 2004 Router Configuration, Routing and Access Lists Name: In this lab you will learn: PartA Cisco 2600 Router Configuration Static Routing PartB 20 min Dynamic
Wireshark Lab: IP v6.0
 Wireshark Lab: IP v6.0 Supplement to Computer Networking: A Top-Down Approach, 6 th ed., J.F. Kurose and K.W. Ross Tell me and I forget. Show me and I remember. Involve me and I understand. Chinese proverb
Wireshark Lab: IP v6.0 Supplement to Computer Networking: A Top-Down Approach, 6 th ed., J.F. Kurose and K.W. Ross Tell me and I forget. Show me and I remember. Involve me and I understand. Chinese proverb
Wireshark Lab: Getting Started
 Wireshark Lab: Getting Started This following content is edited from the wireshark lab exercise provided by J.F. Kurose, and K.W. Ross, "Computer Networking: A Top down approach" 5th ed. Pearson, 2010.
Wireshark Lab: Getting Started This following content is edited from the wireshark lab exercise provided by J.F. Kurose, and K.W. Ross, "Computer Networking: A Top down approach" 5th ed. Pearson, 2010.
Downloaded from manuals search engine. Quick Start
 Quick Start Thank you for purchasing the Mobile WiFi. This Mobile WiFi brings you a high speed wireless network connection. This document will help you understand your Mobile WiFi so you can start using
Quick Start Thank you for purchasing the Mobile WiFi. This Mobile WiFi brings you a high speed wireless network connection. This document will help you understand your Mobile WiFi so you can start using
Lab Assignment 3 for ECE374
 Lab Assignment 3 for ECE374 Posted: 02/25/18 Due: 03/08/18 In this lab, we ll take a quick look at the UDP and TCP transport protocol. Whenever possible you should hand in a Wireshark screenshot that you
Lab Assignment 3 for ECE374 Posted: 02/25/18 Due: 03/08/18 In this lab, we ll take a quick look at the UDP and TCP transport protocol. Whenever possible you should hand in a Wireshark screenshot that you
Manually Enable Wireless Windows 7 Network Connection 2
 Manually Enable Wireless Windows 7 Network Connection 2 I open Network Connection and I double click on Wireless Network Connection, then a little Windows couldn't automatically bind the IP protocol stack
Manually Enable Wireless Windows 7 Network Connection 2 I open Network Connection and I double click on Wireless Network Connection, then a little Windows couldn't automatically bind the IP protocol stack
Oct Wi-Fi Concierge Web Portal User Guide - English
 Oct 2017 Wi-Fi Concierge Web Portal User Guide - English Table of Contents 1 Overview of Wi-Fi Concierge Web Portal... 3 2 Access Wi-Fi Concierge Web Portal... 3 3 Language Settings... 4 4 Register a New
Oct 2017 Wi-Fi Concierge Web Portal User Guide - English Table of Contents 1 Overview of Wi-Fi Concierge Web Portal... 3 2 Access Wi-Fi Concierge Web Portal... 3 3 Language Settings... 4 4 Register a New
Assignment #1. Csci4211 Spring Due on Feb. 13th, Notes: There are five questions in this assignment. Each question has 10 points.
 Assignment #1 Csci4211 Spring 2017 Due on Feb. 13th, 2017 Notes: There are five questions in this assignment. Each question has 10 points. 1. (10 pt.) Describe the special properties of the following transmission
Assignment #1 Csci4211 Spring 2017 Due on Feb. 13th, 2017 Notes: There are five questions in this assignment. Each question has 10 points. 1. (10 pt.) Describe the special properties of the following transmission
INSITES CONNECT ADMINISTRATION GUIDE. Version 1.4.3
 INSITES CONNECT ADMINISTRATION GUIDE Version 1.4.3 CONTENTS GETTING STARTED... 2 Version Compatibility... 2 Installing the InSites Connect app... 2 APP CONFIGURATION... 4 CONFIGURING PUSH NOTIFICATIONS...
INSITES CONNECT ADMINISTRATION GUIDE Version 1.4.3 CONTENTS GETTING STARTED... 2 Version Compatibility... 2 Installing the InSites Connect app... 2 APP CONFIGURATION... 4 CONFIGURING PUSH NOTIFICATIONS...
Learn How to Configure EnGenius Wi-Fi Products for Popular Applications
 Learn How to Configure EnGenius Wi-Fi Products for Popular Applications Operation Modes Access Point (AP) / WDS AP Client Bridge (CB) Repeater WDS Bridge Client Router AP Router Access Point An access
Learn How to Configure EnGenius Wi-Fi Products for Popular Applications Operation Modes Access Point (AP) / WDS AP Client Bridge (CB) Repeater WDS Bridge Client Router AP Router Access Point An access
Ayrstone AyrMesh Router SP Setup
 Ayrstone AyrMesh Router SP Setup This guide should help you set up AyrMesh Router SP. The setup is relatively simple but should you need more detailed directions, such as slide shows, video, or troubleshooting
Ayrstone AyrMesh Router SP Setup This guide should help you set up AyrMesh Router SP. The setup is relatively simple but should you need more detailed directions, such as slide shows, video, or troubleshooting
Protocol Analysis: Capturing Packets
 Protocol Analysis: Capturing Packets This project is intended to be done on the EiLab Network, but if you want to try to VPN into the EiLab Network on your own PC from your home or workplace, follow these
Protocol Analysis: Capturing Packets This project is intended to be done on the EiLab Network, but if you want to try to VPN into the EiLab Network on your own PC from your home or workplace, follow these
Wireless LAN Controller Web Authentication Configuration Example
 Wireless LAN Controller Web Authentication Configuration Example Document ID: 69340 Contents Introduction Prerequisites Requirements Components Used Conventions Web Authentication Web Authentication Process
Wireless LAN Controller Web Authentication Configuration Example Document ID: 69340 Contents Introduction Prerequisites Requirements Components Used Conventions Web Authentication Web Authentication Process
Networking Basics. Crystal Printer Network Installation Guidelines
 Networking Basics & Crystal Printer Network Installation Guidelines 1. Overview This guide is intended to provide the necessary basic knowledge of wireless networking needed to enable the Crystal printer
Networking Basics & Crystal Printer Network Installation Guidelines 1. Overview This guide is intended to provide the necessary basic knowledge of wireless networking needed to enable the Crystal printer
