DataLocker Enterprise
|
|
|
- Grace Goodman
- 5 years ago
- Views:
Transcription
1 DataLocker Enterprise The DataLocker Enterprise is a secure portable hard drive that offers hardware-based, militarygrade encryption. The DataLocker crypto engine and enclosure are FIPS validated, issued by the National Institute of Technology (NIST). No software is ever needed to manage, encrypt or deploy the DataLocker Enterprise. Simply connect, authenticate with your personal passcode and go. DataLocker Enterprise Capabilities: Protects sensitive data from loss or theft through hardware-based 256-bit AES / CBC encryption Requires no software or drivers because all encryption and management functions are performed at the device level, 100 percent independent of the host computer Patented touchscreen display allows users to enter their password directly on the device Mitigates shoulder surfing PIN observation attacks through a randomized keypad Handles large volumes of data with up to 1 TB of storage Certifications include FIPS (Cert #1504), FIPS 197, TAA and NMCI USB 2.0 Interface No External Power Required Screens Simulated Randomized Keypad (To Prevent Fingerprint Lifting) Rapid Secure Wipe Self-Destruct Mode (Optional) No Software or Drivers Mac, Linux and Windows Compatible The touch screen is definitely slick, and this drive is worth considering if you need to move sensitive data between machines. If you work for a secret government agency, you d better get one now.
2 DataLocker Enterprise Dedicated MX Crypto Engine Validated at FIPS Level 1 Roles, Services and Authentication Validated at FIPS Level 2 EMI/EMC Validated at FIPS Level 3 Firmware-Based Anti-Malware Protection Self-Destruct Mode for Protection Against Brute Force Attacks Randomized Keypad for Mitigation of Fingerprint Lifting Attacks and Shoulder Surfing User Experience Patented Touchscreen Display and User-Friendly Interface 100% Platform Independent Compatible with Mac, Linux and Windows High-Capacity Storage up to 1 TB Hardware Specs Dimensions (L x W x D): 5 inch x 3 inch x 0.9 inch Weight: Approximately 9 oz. USB 2.0 Compatible Available in 500GB, 1TB, 128GB SSD & 256GB SSD Capacities Data Locker, Inc. All rights reserved. DataLocker is a registered trademark of Data Locker Inc. Protected by United States Patent No. 8,185,709 and Korean Patent No Other patents pending. DataLocker is a manufacturer of data encryption solutions for governments, military and businesses around the world. Its award-winning products are designed to be Simply Secure and platform independent, requiring no software or drivers. Founded in 2007 and based in Overland Park, Kansas, DataLocker is a proven leader in providing innovative technologies and data encryption solutions. For more information, visit DataLocker.com. Headquarters Data Locker 7500 College Blvd. Suite 1200 Overland Park, KS Fax: Europe Data Locker Europe Ltd Castle House St. Peter s Hill Stamford, Lincolnshire PE9 2PE Tel: +44 (0) Web Sales: emea@datalocker.com Asia Data Locker International Samsung Midas Bldg. # Janghang-Dong, Ilsandong-Gu, Goyang-si, , Korea Fax: +82.(0)
3 DataLocker DL3 The DataLocker DL3 sets a new standard in portable data security. This sleek, portable hard drive is ideal for users who require mobility, simplicity and advanced security. No software is ever needed to manage, encrypt or deploy the DL3. Simply connect, authenticate with your personal passcode and go. DataLocker DL3 Capabilities: Protects sensitive data from loss or theft through hardware-based 256-bit AES encryption Requires no software or drivers because all encryption and management functions are performed at the device level, 100 percent independent of the host computer Patented touchscreen display allows users to enter their password directly on the device Mitigates shoulder surfing PIN observation attacks through a randomized keypad Supports two-factor authentication via an optional RFID module Handles large volumes of data with up to 1 terabyte of storage USB 3.0 Interface (USB 2.0 Compatible) No External Power Required Randomized Keypad (To Prevent Fingerprint Lifting) Rapid Secure Wipe Self-Destruct Mode (Optional) No Software or Drivers Mac, Linux and Windows Compatible Screens Simulated Two-Factor Authentication via RFID Card (available in some models) The touch screen is definitely slick, and this drive is worth considering if you need to move sensitive data between machines. If you work for a secret government agency, you d better get one now.
4 DataLocker DL3 Hardware-Based Encryption Dedicated 256-Bit AES XTS Mode Crypto Engine Two-Factor Authentication via RFID Card (Optional) All Encryption, Administration and Authentication Performed on the DataLocker Unit Rapid Key Zeroization for Secure Redeployment Self-Destruct Mode for Protection Against Brute Force Attacks Rotating Keypad for Mitigation of Fingerprint Lifting Attacks and Shoulder Surfing DL Link: Pair DL3 to Allow Access only on Specified Computers Virtual CD Partition (VCD) Strong Password Rule (Non Sequential, Repeating, Alpha + Num, Min 7 characters) User Experience Patented Touch-Screen Display and User-Friendly Interface 100% Platform Independent Compatible with Mac, Linux and Windows High-Capacity Storage Up to 1 TB Multi-Lingual User Interface (English, French, German and Spanish) Hardware Specs Dimensions (L x W x D): 120mm x 80mm x 23mm Weight: Approximately 9 oz. USB 3.0 and 2.0 Compatible Shock and Drop Resistant Available in 500GB, 1TB, 128GB SSD & 256GB SSD Capacities Data Locker, Inc. All rights reserved. DataLocker is a registered trademark of Data Locker Inc. Protected by United States Patent No. 8,185,709 and Korean Patent No Other patents pending. DataLocker is a manufacturer of data encryption solutions for governments, military and businesses around the world. Its award-winning products are designed to be Simply Secure and platform independent, requiring no software or drivers. Founded in 2007 and based in Overland Park, Kansas, DataLocker is a proven leader in providing innovative technologies and data encryption solutions. For more information, visit DataLocker.com. Headquarters Data Locker 7500 College Blvd. Suite 1200 Overland Park, KS Fax: Europe Data Locker Europe Ltd Castle House St. Peter s Hill Stamford, Lincolnshire PE9 2PE Tel: +44 (0) Web Sales: emea@datalocker.com Asia Data Locker International Samsung Midas Bldg. # Janghang-Dong, Ilsandong-Gu, Goyang-si, , Korea Fax: +82.(0)
5 DataLocker SecureDisk The Most Secure Writeable DVD and Compact Disk Technical Specs INFORMATION Format Recording Speed Capacity CD-R 52x 700MB DVD-R 52x 4.7GB SYSTEM COMPATIBILITY Windows 2000/XP/Vista/Windows 7/ Server 2000/Server 2003/Server 2008 The DataLocker SecureDisk combines AES 256-bit encryption and disc burning functionality, all self-contained on a recordable CD or DVD. SecureDisk offers built-in software for disc burning and government strength FIPS AES 256-bit encryption. There s no software to install and no need for third-party software applications. SecureDisk addresses the needs of users who require a simple, highly secure method to transport, share and archive sensitive data and records. Secure disk is the proven choice for low-cost, high-capacity optical media that adheres to industry standards. Easy to Use Simply insert SecureDisk and create a password when prompted. There s even password recovery if you forget. Automatic, Powerful Encryption With SecureDisk you are guaranteed that your data is protected with government certified FIPS Level 1 AES 256-bit encryption. SecureDisk cannot be written in the clear. It is always encrypted. Securely Share Users can easily share SecureDisk from PC to PC either as closed (CD ROM) or open discs for additional updates. STANDARDS AND CERTIFICATIONS FIPS Level 1 Validated RoHS TAA Compliant MSRP Format 10-Pack 100-Pack CD-R $29.99 $ DVD-R $34.99 $ DataLocker is a manufacturer of data encryption solutions for governments, military and businesses around the world. Its award-winning products are designed to be Simply Secure and platform independent, requiring no software or drivers. Founded in 2007 and based in Overland Park, Kansas, DataLocker is a proven leader in providing innovative technologies and data encryption solutions. For more information, visit DataLocker.com Data Locker, Inc. All rights reserved. DataLocker is a registered trademark of Data Locker Inc. Protected by United States Patent No. 8,185,709 and Korean Patent No Other patents pending. DataLocker US DataLocker Europe Phone: +44 (0) emea@datalocker.com DataLocker Asia
Integral Memory PLC. Crypto Dual (Underlying Steel Chassis) and Crypto Dual Plus (Underlying Steel Chassis) FIPS Security Policy
 Integral Memory PLC. Chassis) and Crypto Dual Plus (Underlying FIPS 140-2 Security Policy Table of Contents 1. INTRODUCTION... 1 1.1 Purpose....1 1.2 References... 1 1.3 Document History... 1 2. PRODUCT
Integral Memory PLC. Chassis) and Crypto Dual Plus (Underlying FIPS 140-2 Security Policy Table of Contents 1. INTRODUCTION... 1 1.1 Purpose....1 1.2 References... 1 1.3 Document History... 1 2. PRODUCT
Encrypted Solutions. Your essential guide to encrypted data storage
 Encrypted Solutions Your essential guide to encrypted data storage 2017 Are you GDPR Ready? The General Data Protection Regulation is a new EU legislation which aims to strengthen and future-proof data
Encrypted Solutions Your essential guide to encrypted data storage 2017 Are you GDPR Ready? The General Data Protection Regulation is a new EU legislation which aims to strengthen and future-proof data
Creating Trust in a Highly Mobile World
 Creating Trust in a Highly Mobile World Technical White Paper Oct, 2014 MobileCrypt with Hardware Strength Security MobileCrypt s solution leverages an Android based mobile application and a Hardware Security
Creating Trust in a Highly Mobile World Technical White Paper Oct, 2014 MobileCrypt with Hardware Strength Security MobileCrypt s solution leverages an Android based mobile application and a Hardware Security
Security for Wireless Handhelds
 wireless security solutions security applications developer toolkits professional services Security for Wireless Handhelds integrating strong, transparent security without increasing costs or time-to-market
wireless security solutions security applications developer toolkits professional services Security for Wireless Handhelds integrating strong, transparent security without increasing costs or time-to-market
ThinkPad USB Portable Secure Hard Drives GB and 320GB options -- Compact, secure, easy-to-use data storage and image recovery solutions
 , dated vember 18, 2008 ThinkPad USB Portable Secure Hard Drives -- 160GB and 320GB options -- Compact, secure, easy-to-use data storage and image recovery solutions Table of contents 1 At a glance 2 Additional
, dated vember 18, 2008 ThinkPad USB Portable Secure Hard Drives -- 160GB and 320GB options -- Compact, secure, easy-to-use data storage and image recovery solutions Table of contents 1 At a glance 2 Additional
If you print the file, make sure that the left and right margins are set to a width of 25 millimetres (approximately 1 inch) for A4 portrait.
 Notes on Installation and Use The information and notes contained here are more up-to-date and therefore valid compared with information in other documents. Please read the notes carefully as they contain
Notes on Installation and Use The information and notes contained here are more up-to-date and therefore valid compared with information in other documents. Please read the notes carefully as they contain
BlackVault Hardware Security Platform SECURE TRUSTED INTUITIVE. Cryptographic Appliances with Integrated Level 3+ Hardware Security Module
 BlackVault Hardware Security Platform SECURE TRUSTED INTUITIVE Cryptographic Appliances with Integrated Level 3+ Hardware Security Module The BlackVault hardware security platform keeps cryptographic material
BlackVault Hardware Security Platform SECURE TRUSTED INTUITIVE Cryptographic Appliances with Integrated Level 3+ Hardware Security Module The BlackVault hardware security platform keeps cryptographic material
Company Profile MAY
 Company Profile MAY.2015 www.clonix.com General About US Company Name Clonix Co., Ltd. Establishment November. 2004 Address(HQ) #101-1211, Digital Empire Ⅱ, 88, Sinwon-ro, Yeongtong-Gu, Suwon-si, Gyeonggi-Do,
Company Profile MAY.2015 www.clonix.com General About US Company Name Clonix Co., Ltd. Establishment November. 2004 Address(HQ) #101-1211, Digital Empire Ⅱ, 88, Sinwon-ro, Yeongtong-Gu, Suwon-si, Gyeonggi-Do,
Steganos Safe Professional th June 2007
 Steganos Safe Professional 2007 26 th June 2007 Contents Page Introduction 4 Installation and Deployment 5 Managing and Policies 6 Recovery Using EDK 8 Setting Up Network Shares 8 Creating A Key Pair 8
Steganos Safe Professional 2007 26 th June 2007 Contents Page Introduction 4 Installation and Deployment 5 Managing and Policies 6 Recovery Using EDK 8 Setting Up Network Shares 8 Creating A Key Pair 8
256-bit AES HARDWARE ENCRYPTED SOLID STATE DRIVES
 256-bit AES HARDWARE ENCRYPTED SOLID STATE DRIVES integralmemoryusa.com About Us Introducing Integral Memory plc are one of the largest digital memory producers in Europe with more than 20 years of sales
256-bit AES HARDWARE ENCRYPTED SOLID STATE DRIVES integralmemoryusa.com About Us Introducing Integral Memory plc are one of the largest digital memory producers in Europe with more than 20 years of sales
In today s business environment, data creates value so it s more important than ever to protect it as a vital business asset
 In today s business environment, data creates value so it s more important than ever to protect it as a vital business asset Seagate Secure Reliable Data Protection Solutions Always-on Data Protection
In today s business environment, data creates value so it s more important than ever to protect it as a vital business asset Seagate Secure Reliable Data Protection Solutions Always-on Data Protection
TODAY AND TOMORROW. Storage CHAPTER
 1 TODAY AND TOMORROW 3 Storage CHAPTER Storage Systems Characteristics All storage systems have specific characteristics Storage medium (what data is stored on) Can be removable or nonremovable from the
1 TODAY AND TOMORROW 3 Storage CHAPTER Storage Systems Characteristics All storage systems have specific characteristics Storage medium (what data is stored on) Can be removable or nonremovable from the
Encrypted containers for secure file transport
 Encrypted containers for secure file transport Use Zed! encrypted containers to protect your file transports regardless of the method used (email attachment, USB stick, removable device, file transfer,
Encrypted containers for secure file transport Use Zed! encrypted containers to protect your file transports regardless of the method used (email attachment, USB stick, removable device, file transfer,
User Manual FIPS SSD. Remember to save your PIN in a safe place. If lost or forgotten, there is no way to access the drive.
 User Manual FIPS Level 2 Certified 140-2 Certificate number 1970 SSD Remember to save your PIN in a safe place. If lost or forgotten, there is no way to access the drive. If you are having difficulty please
User Manual FIPS Level 2 Certified 140-2 Certificate number 1970 SSD Remember to save your PIN in a safe place. If lost or forgotten, there is no way to access the drive. If you are having difficulty please
IDCore. Flexible, Trusted Open Platform. financial services & retail. Government. telecommunications. transport. Alexandra Miller
 IDCore Flexible, Trusted Open Platform financial services & retail enterprise > SOLUTION Government telecommunications transport Trusted Open Platform Java Card Alexandra Miller >network identity >smart
IDCore Flexible, Trusted Open Platform financial services & retail enterprise > SOLUTION Government telecommunications transport Trusted Open Platform Java Card Alexandra Miller >network identity >smart
Architecture 1 3. SecureToken. 32-bit microprocessor smart chip. Support onboard RSA key pair generation. Built-in advanced cryptographic functions
 SecureToken Architecture 1 3 2 32-bit microprocessor smart chip Support onboard RSA key pair generation Built-in advanced cryptographic functions 4 5 6 7 8 9 10 Support onboard digital signing Supports
SecureToken Architecture 1 3 2 32-bit microprocessor smart chip Support onboard RSA key pair generation Built-in advanced cryptographic functions 4 5 6 7 8 9 10 Support onboard digital signing Supports
Certicom Security for Government Suppliers developing products to meet the US Government FIPS security requirement
 certicom application notes Certicom Security for Government Suppliers developing products to meet the US Government FIPS 140-2 security requirement THE PROBLEM How can vendors take advantage of the lucrative
certicom application notes Certicom Security for Government Suppliers developing products to meet the US Government FIPS 140-2 security requirement THE PROBLEM How can vendors take advantage of the lucrative
Intel and Symantec: Improving performance, security, manageability and data protection
 Intel and Symantec: Improving performance, security, manageability and data protection Terry Cutler Enterprise Solution Architect Omid Meshkin Strategic Business Development 1 Session Objectives By the
Intel and Symantec: Improving performance, security, manageability and data protection Terry Cutler Enterprise Solution Architect Omid Meshkin Strategic Business Development 1 Session Objectives By the
midentity midentity Basic KOBIL midentity Basic Mobile, Secure and Flexible
 KOBIL Mobile, Secure and Flexible KOBIL is the ideal product for the mobile, yet safe transportation of your data and the protection of your digital identity. The perfectly integrated smartcard technology
KOBIL Mobile, Secure and Flexible KOBIL is the ideal product for the mobile, yet safe transportation of your data and the protection of your digital identity. The perfectly integrated smartcard technology
Moser Baer Group 25 years of excellence
 Moser Baer Group 25 years of excellence Introduction to the Moser Baer Group Established in 1983 25 years legacy as India s leading technology manufacturing company 8,000 Employees Rs11,000 Crores in Assets
Moser Baer Group 25 years of excellence Introduction to the Moser Baer Group Established in 1983 25 years legacy as India s leading technology manufacturing company 8,000 Employees Rs11,000 Crores in Assets
Importing your or Personal Authentication certificate to Android Devices
 Personal Authentication Certificates Importing your Email or Personal Authentication certificate to Android Devices This document explains how you can import your CPAC/Email onto Android devices. Background
Personal Authentication Certificates Importing your Email or Personal Authentication certificate to Android Devices This document explains how you can import your CPAC/Email onto Android devices. Background
Endpoint Security. E80.30 Localized Version. Release Notes
 Endpoint Security E80.30 Localized Version Release Notes 30 September 2013 2013 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by copyright
Endpoint Security E80.30 Localized Version Release Notes 30 September 2013 2013 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by copyright
NetIQ Secure Configuration Manager Installation Guide. October 2016
 NetIQ Secure Configuration Manager Installation Guide October 2016 Legal Notice For information about NetIQ legal notices, disclaimers, warranties, export and other use restrictions, U.S. Government restricted
NetIQ Secure Configuration Manager Installation Guide October 2016 Legal Notice For information about NetIQ legal notices, disclaimers, warranties, export and other use restrictions, U.S. Government restricted
Rugged All-in-one Handheld Computer. BIP-1500 Series
 Rugged All-in-one Handheld Computer BIP-1500 Series BIP-1500 Series INDUSTRIES Retail Public Transport Hospitality Finance The rugged all-in-one handheld computer, BIP-1500 Series, is designed to meet
Rugged All-in-one Handheld Computer BIP-1500 Series BIP-1500 Series INDUSTRIES Retail Public Transport Hospitality Finance The rugged all-in-one handheld computer, BIP-1500 Series, is designed to meet
DataTraveler 5000 (DT5000) and DataTraveler 6000 (DT6000) Ultimate Security in a USB Flash Drive. Submitted by SPYRUS, Inc.
 Submitted by SPYRUS, Inc. Contents DT5000 and DT6000 Technology Overview...2 Why DT5000 and DT6000 Encryption Is Different...3 Why DT5000 and DT6000 Encryption Is Different - Summary...4 XTS-AES Sector-Based
Submitted by SPYRUS, Inc. Contents DT5000 and DT6000 Technology Overview...2 Why DT5000 and DT6000 Encryption Is Different...3 Why DT5000 and DT6000 Encryption Is Different - Summary...4 XTS-AES Sector-Based
SecureDoc Disk Encryption Cryptographic Engine
 SecureDoc Disk Encryption Cryptographic Engine Security Policy Abstract: This document specifies Security Policy enforced by the SecureDoc Cryptographic Engine compliant with the requirements of FIPS 140-2
SecureDoc Disk Encryption Cryptographic Engine Security Policy Abstract: This document specifies Security Policy enforced by the SecureDoc Cryptographic Engine compliant with the requirements of FIPS 140-2
Smart and Flexible! BIP-7000 Series. Industrial Handheld Computer. BIP-7000Plus BIP-7000
 Smart and Flexible! Series Industrial Handheld Computer Plus Handheld Barcode Series Industrial Handheld Computer INDUSTRIES Retail Public Transport Healthcare Warehousing industrial handheld computer
Smart and Flexible! Series Industrial Handheld Computer Plus Handheld Barcode Series Industrial Handheld Computer INDUSTRIES Retail Public Transport Healthcare Warehousing industrial handheld computer
Steganos Security Suite 2006 released to increase privacy protection for UK PC users
 1 Steganos Security Suite 2006 released to increase privacy protection for UK PC users The latest version of the leading encryption software offers stronger encryption and more user-friendly decryption,
1 Steganos Security Suite 2006 released to increase privacy protection for UK PC users The latest version of the leading encryption software offers stronger encryption and more user-friendly decryption,
TECHNOLOGY LEADER IN GLOBAL REAL-TIME TWO-FACTOR AUTHENTICATION
 TECHNOLOGY LEADER IN GLOBAL REAL-TIME TWO-FACTOR AUTHENTICATION SMS PASSCODE is the leading technology in a new generation of two-factor authentication systems protecting against the modern Internet threats.
TECHNOLOGY LEADER IN GLOBAL REAL-TIME TWO-FACTOR AUTHENTICATION SMS PASSCODE is the leading technology in a new generation of two-factor authentication systems protecting against the modern Internet threats.
User Guide. IronKey Workspace Models: W700 Updated: September 2013 IRONKEY WORKSPACE W700 USER GUIDE
 User Guide IronKey Workspace Models: W700 Updated: September 2013 PAGE 1 Thank you for your interest in IronKey Workspace W700 by Imation. Imation s Mobile Security Group is committed to creating and developing
User Guide IronKey Workspace Models: W700 Updated: September 2013 PAGE 1 Thank you for your interest in IronKey Workspace W700 by Imation. Imation s Mobile Security Group is committed to creating and developing
Prepared by the Fortress Technologies, Inc., Government Technology Group 4023 Tampa Rd. Suite Oldsmar, FL 34677
 Non-Proprietary Security Policy for the FIPS 140-2 Level 2 Validated AirFortress Wireless Security Gateway Hardware Model AF7500 (Document Version 2.3) March 2007 Prepared by the Fortress Technologies,
Non-Proprietary Security Policy for the FIPS 140-2 Level 2 Validated AirFortress Wireless Security Gateway Hardware Model AF7500 (Document Version 2.3) March 2007 Prepared by the Fortress Technologies,
3 System Requirements for SecureLogin
 NetIQ SecureLogin Quick Start Guide July 2018 1 About This Document It is highly recommended that you read this guide carefully before proceeding with installing, configuring, and deploying NetIQ SecureLogin.
NetIQ SecureLogin Quick Start Guide July 2018 1 About This Document It is highly recommended that you read this guide carefully before proceeding with installing, configuring, and deploying NetIQ SecureLogin.
Implementing Disk Encryption on System x Servers with IBM Security Key Lifecycle Manager Solution Guide
 Implementing Disk Encryption on System x Servers with IBM Security Key Lifecycle Manager Solution Guide Securing sensitive client and company data is becoming an IT task of paramount importance. Often
Implementing Disk Encryption on System x Servers with IBM Security Key Lifecycle Manager Solution Guide Securing sensitive client and company data is becoming an IT task of paramount importance. Often
FIPS Non-Proprietary Security Policy. Level 1 Validation Version 1.2
 Oracle Solaris Kernel Cryptographic Framework with SPARC T4 and T5 Software Version: 1.0 and 1.1; Hardware Version: SPARC T4 (527-1437-01) and T5 (7043165) FIPS 140-2 Non-Proprietary Security Policy Level
Oracle Solaris Kernel Cryptographic Framework with SPARC T4 and T5 Software Version: 1.0 and 1.1; Hardware Version: SPARC T4 (527-1437-01) and T5 (7043165) FIPS 140-2 Non-Proprietary Security Policy Level
Install and setup TrueCrypt
 Install and setup TrueCrypt Install and setup TrueCrypt This guide is for organisations and individuals who wish to use TrueCrypt to secure their computer(s) and/or portable USB drives. It explains how
Install and setup TrueCrypt Install and setup TrueCrypt This guide is for organisations and individuals who wish to use TrueCrypt to secure their computer(s) and/or portable USB drives. It explains how
Cipherchain-e kit with Single CipherChain-e
 INTRODUCTION Have you been looking for a simple and affordable solution to secure the sensitvie data storage in your external hard drive? The Addonics products is the answer. Designed using the same field
INTRODUCTION Have you been looking for a simple and affordable solution to secure the sensitvie data storage in your external hard drive? The Addonics products is the answer. Designed using the same field
CompTIA A+ Accelerated course for & exams
 CompTIA A+ Accelerated course for 220-901 & 220-902 exams Course overview Target Audience This course is for Participants wishing to take and pass both CompTIA A+ exams (220-901 and 220-902) exam. It is
CompTIA A+ Accelerated course for 220-901 & 220-902 exams Course overview Target Audience This course is for Participants wishing to take and pass both CompTIA A+ exams (220-901 and 220-902) exam. It is
Security Requirements of FIPS PUB 140 & Reconfigurable Hardware. G. Bertoni Politecnico di Milano
 Security Requirements of FIPS PUB 140 & Reconfigurable Hardware G. Bertoni Politecnico di Milano What is FIPS PUB 140? It is a standard, issued by NIST and CSE, to define different levels of security requirements
Security Requirements of FIPS PUB 140 & Reconfigurable Hardware G. Bertoni Politecnico di Milano What is FIPS PUB 140? It is a standard, issued by NIST and CSE, to define different levels of security requirements
Keep Your Vehicle Safe. g.net system Car Dash Cam Solution
 Keep Your Vehicle Safe g.net system Car Dash Cam Solution As Korean based Manufacturer, G-Net System has been developing and producing for 20 years and has high awareness background for Car Dashcam in
Keep Your Vehicle Safe g.net system Car Dash Cam Solution As Korean based Manufacturer, G-Net System has been developing and producing for 20 years and has high awareness background for Car Dashcam in
Setup Guide. Setting Up the Machine. Installing the Software. FAX settings. Scan settings. Control Panel Sheet
 Setup Guide Setting Up the Machine 1 Installing the Software 2 FAX settings 3 Scan settings Control Panel Sheet 1 2 1. Setting Up the Machine 24 cm (9.5 inches) 20 cm (7.9 inches) 32 89.6 10 50 15 80
Setup Guide Setting Up the Machine 1 Installing the Software 2 FAX settings 3 Scan settings Control Panel Sheet 1 2 1. Setting Up the Machine 24 cm (9.5 inches) 20 cm (7.9 inches) 32 89.6 10 50 15 80
USB-C to esata Cable - For External Storage Devices - USB 3.0 (5Gbps) - 3 ft. (1 m)
 USB-C to esata Cable - For External Storage Devices - USB 3.0 (5Gbps) - 3 ft. (1 m) Product ID: USB3C2ESAT3 This USB-C to esata cable is an external drive adapter that gives you quick and easy access to
USB-C to esata Cable - For External Storage Devices - USB 3.0 (5Gbps) - 3 ft. (1 m) Product ID: USB3C2ESAT3 This USB-C to esata cable is an external drive adapter that gives you quick and easy access to
Setup Guide. Setting Up the Machine. Installing the Software. Scan/FAX and other settings
 Setup Guide Setting Up the Machine 1 Installing the Software 2 Scan/FAX and other settings 1 2 For safe and correct use, please be sure to read the Safety Information before using the machine. 1. Setting
Setup Guide Setting Up the Machine 1 Installing the Software 2 Scan/FAX and other settings 1 2 For safe and correct use, please be sure to read the Safety Information before using the machine. 1. Setting
VIRDI-4000 Fingerprint Access Control Terminal. High Security & Convenient Use
 VIRDI-4000 Fingerprint Access Control Terminal 1 1. COMPANY OVERVIEW A. Our businesses Union Community is a leading biometrics company for access control, time & attendance, door lock, PC peripherals,
VIRDI-4000 Fingerprint Access Control Terminal 1 1. COMPANY OVERVIEW A. Our businesses Union Community is a leading biometrics company for access control, time & attendance, door lock, PC peripherals,
Getting Started With Parallels Desktop 14
 Getting Started With Parallels Desktop 14 Parallels International GmbH Vordergasse 59 8200 Schaffhausen Switzerland Tel: + 41 52 672 20 30 www.parallels.com Copyright 1999-2018 Parallels International
Getting Started With Parallels Desktop 14 Parallels International GmbH Vordergasse 59 8200 Schaffhausen Switzerland Tel: + 41 52 672 20 30 www.parallels.com Copyright 1999-2018 Parallels International
ProtectV StartGuard. FIPS Level 1 Non-Proprietary Security Policy
 ProtectV StartGuard FIPS 140-2 Level 1 Non-Proprietary Security Policy DOCUMENT NUMBER: 002-010841-001 AUTHOR: DEPARTMENT: LOCATION OF ISSUE: SafeNet Certification Team R & D Program Managaement Redwood
ProtectV StartGuard FIPS 140-2 Level 1 Non-Proprietary Security Policy DOCUMENT NUMBER: 002-010841-001 AUTHOR: DEPARTMENT: LOCATION OF ISSUE: SafeNet Certification Team R & D Program Managaement Redwood
Lenovo Europe, Middle East, and Africa Hardware Announcement ZG , dated January 27, 2009
 Hardware Announcement ZG09-0077, dated January 27, 2009 Utimaco SafeGuard Enterprise suite of offerings for ThinkVantage Technologies offers hard drive encryption and additional modules for complete PC
Hardware Announcement ZG09-0077, dated January 27, 2009 Utimaco SafeGuard Enterprise suite of offerings for ThinkVantage Technologies offers hard drive encryption and additional modules for complete PC
USER-FRIENDLY CONTROL PANEL
 The Brother QL-570 Professional Label Printer is the perfect synergy of functionality and design. Introducing the sleek, compact and stylish Brother QL-570 Professional Label Printer. Perfect for creating
The Brother QL-570 Professional Label Printer is the perfect synergy of functionality and design. Introducing the sleek, compact and stylish Brother QL-570 Professional Label Printer. Perfect for creating
EXECUTIVE VIEW. KuppingerCole Report
 KuppingerCole Report EXECUTIVE VIEW by Martin Kuppinger August 2017 is a mature enterprise-class offering for Privilege Management, supporting the key areas of the market such as Shared Account and Privileged
KuppingerCole Report EXECUTIVE VIEW by Martin Kuppinger August 2017 is a mature enterprise-class offering for Privilege Management, supporting the key areas of the market such as Shared Account and Privileged
CoSign Hardware version 7.0 Firmware version 5.2
 CoSign Hardware version 7.0 Firmware version 5.2 FIPS 140-2 Non-Proprietary Security Policy Level 3 Validation July 2010 Copyright 2009 AR This document may be freely reproduced and distributed whole and
CoSign Hardware version 7.0 Firmware version 5.2 FIPS 140-2 Non-Proprietary Security Policy Level 3 Validation July 2010 Copyright 2009 AR This document may be freely reproduced and distributed whole and
Aegis Padlock SSD. User Guide. Remember to save your PIN in a safe place. If lost or forgotten, there is no way to access the drive.
 Aegis Padlock SSD User Guide Remember to save your PIN in a safe place. If lost or forgotten, there is no way to access the drive. If you are having difficulty please refer to the complete user s manual
Aegis Padlock SSD User Guide Remember to save your PIN in a safe place. If lost or forgotten, there is no way to access the drive. If you are having difficulty please refer to the complete user s manual
USB Flash Drive. RoHS Compliant. AH321 Product Specifications. March 23, Version 2.5. Apacer Technology Inc.
 RoHS Compliant USB Flash Drive AH321 Product Specifications March 23, 2017 Version 2.5 Apacer Technology Inc. 1F, No.32, Zhongcheng Rd., Tucheng Dist., New Taipei City, Taiwan, R.O.C Tel: +886-2-2267-8000
RoHS Compliant USB Flash Drive AH321 Product Specifications March 23, 2017 Version 2.5 Apacer Technology Inc. 1F, No.32, Zhongcheng Rd., Tucheng Dist., New Taipei City, Taiwan, R.O.C Tel: +886-2-2267-8000
Security Solutions. End-to-end security. Protecting your physical access control system.
 Security Solutions End-to-end security Protecting your physical access control system. www.nedapsecurity.com security common practice Bringing IT best practices to physical security Often, companies don
Security Solutions End-to-end security Protecting your physical access control system. www.nedapsecurity.com security common practice Bringing IT best practices to physical security Often, companies don
USB Flash Drive. RoHS Compliant. AH322 Specifications. November 26, Version 1.9. Apacer Technology Inc.
 RoHS Compliant USB Flash Drive AH322 Specifications November 26, 2015 Version 1.9 Apacer Technology Inc. 1F, No.32, Zhongcheng Rd., Tucheng Dist., New Taipei City, Taiwan, R.O.C Tel: +886-2-2267-8000 Fax:
RoHS Compliant USB Flash Drive AH322 Specifications November 26, 2015 Version 1.9 Apacer Technology Inc. 1F, No.32, Zhongcheng Rd., Tucheng Dist., New Taipei City, Taiwan, R.O.C Tel: +886-2-2267-8000 Fax:
Setup Guide. Setting Up the Machine. Installing the Software. Control Panel Sheet
 Setup Guide Setting Up the Machine 1 Installing the Software 2 Control Panel Sheet 1 2 1. Setting Up the Machine 10 cm (4.0 inches) 10 cm (4.0 inches) 20 cm (7.9 inches) 10 cm (4.0 inches) 32 89.6 10
Setup Guide Setting Up the Machine 1 Installing the Software 2 Control Panel Sheet 1 2 1. Setting Up the Machine 10 cm (4.0 inches) 10 cm (4.0 inches) 20 cm (7.9 inches) 10 cm (4.0 inches) 32 89.6 10
FIPS SECURITY POLICY FOR
 FIPS 140-2 SECURITY POLICY FOR SPECTRAGUARD ENTERPRISE SENSOR August 26, 2011 FIPS 140-2 LEVEL-2 SECURITY POLICY FOR AIRTIGHT NETWORKS SPECTRAGUARD ENTERPRISE SENSOR 1. Introduction This document describes
FIPS 140-2 SECURITY POLICY FOR SPECTRAGUARD ENTERPRISE SENSOR August 26, 2011 FIPS 140-2 LEVEL-2 SECURITY POLICY FOR AIRTIGHT NETWORKS SPECTRAGUARD ENTERPRISE SENSOR 1. Introduction This document describes
Fast. Easy to use. Built for business. Two powerful new desktop document scanners join our award winning line-up ADS-2200 I ADS-2700W
 OPY OPY Fast. Easy to use. Built for business Two powerful new desktop document SCAN FAX WIRELESS scanners join our award winning line-up SCAN ADS-2200 I ADS-2700W FAX WIRELESS Brother document scanners:
OPY OPY Fast. Easy to use. Built for business Two powerful new desktop document SCAN FAX WIRELESS scanners join our award winning line-up SCAN ADS-2200 I ADS-2700W FAX WIRELESS Brother document scanners:
16/06/56. Secondary Storage. Secondary Storage. Secondary Storage The McGraw-Hill Companies, Inc. All rights reserved.
 Distinguish between primary and secondary storage. Discuss the important characteristics of secondary storage, including media, capacity, storage devices, and access speed. Describe hard disk platters,
Distinguish between primary and secondary storage. Discuss the important characteristics of secondary storage, including media, capacity, storage devices, and access speed. Describe hard disk platters,
Sleek yet Semi-rugged! BM-170. Enterprise Handheld PDA. Handheld
 Sleek yet Semi-rugged! BM-170 Enterprise Handheld PDA Handheld BM-170 Enterprise Handheld PDA INDUSTRIES Education Retail Public Transport Hospitality Healthcare BM-170 enterprise handheld PDA presents
Sleek yet Semi-rugged! BM-170 Enterprise Handheld PDA Handheld BM-170 Enterprise Handheld PDA INDUSTRIES Education Retail Public Transport Hospitality Healthcare BM-170 enterprise handheld PDA presents
FEATURES. One local and remote user Enables a remote user to contect via a CATx cable and share access to the 16 computers with the local user.
 16 Port KVM Rack Tray High density rack tray with fully featured USB, PS2, SUN and Video control ADDERVIEW RDX 1000 High density fully featured control for local and remote users PRODUCT IN BRIEF The ADDERView
16 Port KVM Rack Tray High density rack tray with fully featured USB, PS2, SUN and Video control ADDERVIEW RDX 1000 High density fully featured control for local and remote users PRODUCT IN BRIEF The ADDERView
8/25/2018. Kingston Complete Dealer Pricelist. Product Image & Description SKU Capacity DP SRP USB DT101 G2 DT SE9. USB Gen 1 (USB 3.
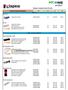 8/25/2018 Kingston Complete Dealer Pricelist DT101 G2 - standard USB 2.0 Speed DT101G2/32GB 32GB RM 29.00 RM 41 DT SE9 - standard USB 2.0 Speed - stylish metal casing DTSE9H/16GB 16GB RM 17.50 RM 25 -
8/25/2018 Kingston Complete Dealer Pricelist DT101 G2 - standard USB 2.0 Speed DT101G2/32GB 32GB RM 29.00 RM 41 DT SE9 - standard USB 2.0 Speed - stylish metal casing DTSE9H/16GB 16GB RM 17.50 RM 25 -
How To Install Windows Update Vista From Usb Drive Detailed 100 Working Guide
 How To Install Windows Update Vista From Usb Drive Detailed 100 Working Guide By using this guide you will be able to Install Windows 7/Vista, if you don't have a Windows 7 Or Windows 8 From USB Drive
How To Install Windows Update Vista From Usb Drive Detailed 100 Working Guide By using this guide you will be able to Install Windows 7/Vista, if you don't have a Windows 7 Or Windows 8 From USB Drive
Thunderbolt Range Audio Photo Video Backup Archive
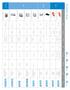 Thunderbolt Range Audio Photo Video Backup Archive Storage InterfacesC apacities RPM Max. RAID Modes Strengths Uses Mobile LaCie Rugged Thunderbolt LaCie Rugged RAID SSD or HDD 1 x Thunderbolt (integrated)
Thunderbolt Range Audio Photo Video Backup Archive Storage InterfacesC apacities RPM Max. RAID Modes Strengths Uses Mobile LaCie Rugged Thunderbolt LaCie Rugged RAID SSD or HDD 1 x Thunderbolt (integrated)
VIRDI-430 Fingerprint Identification Door Lock. High Security & Convenient Use
 VIRDI-430 Fingerprint Identification Door Lock 1 1. COMPANY OVERVIEW A. Our businesses Union Community is a leading biometrics company for access control, time & attendance, door lock, PC peripherals,
VIRDI-430 Fingerprint Identification Door Lock 1 1. COMPANY OVERVIEW A. Our businesses Union Community is a leading biometrics company for access control, time & attendance, door lock, PC peripherals,
Windows Xp User Manual 32 Bit Iso Image File
 Windows Xp User Manual 32 Bit Iso Image File I've spent about two hours looking for legitimate Vista or XP downloads to You'll often see ISO files of programs and operating systems on bit torrent directories
Windows Xp User Manual 32 Bit Iso Image File I've spent about two hours looking for legitimate Vista or XP downloads to You'll often see ISO files of programs and operating systems on bit torrent directories
I AM THE NCR REALPOS XR7
 I AM THE NCR REALPOS XR7 POS perfected The NCR RealPOS XR7 features a stylish all-in-one design, bestin-class performance, exceptional versatility, plus the ruggedness and data security you need for mission-critical
I AM THE NCR REALPOS XR7 POS perfected The NCR RealPOS XR7 features a stylish all-in-one design, bestin-class performance, exceptional versatility, plus the ruggedness and data security you need for mission-critical
Encrypted Solutions. Your essential guide to encrypted data storage
 Encrypted Solutions Your essential guide to encrypted data storage 2016 Are you GDPR Ready? The General Data Protection Regulation is a new EU legislation which aims to strengthen and future-proof data
Encrypted Solutions Your essential guide to encrypted data storage 2016 Are you GDPR Ready? The General Data Protection Regulation is a new EU legislation which aims to strengthen and future-proof data
Disk Encryption Buyers Guide
 Briefing Paper Disk Encryption Buyers Guide Why not all solutions are the same and how to choose the one that s right for you.com CommercialSector Introduction We have written this guide to help you understand
Briefing Paper Disk Encryption Buyers Guide Why not all solutions are the same and how to choose the one that s right for you.com CommercialSector Introduction We have written this guide to help you understand
FIPS Security Policy
 Motorola Mobility Linux Kernel Software Cryptographic Module FIPS 140-2 Security Policy Module Version 1.0 Document version 1.13 March 11, 2015 This document may be freely copied and distributed provided
Motorola Mobility Linux Kernel Software Cryptographic Module FIPS 140-2 Security Policy Module Version 1.0 Document version 1.13 March 11, 2015 This document may be freely copied and distributed provided
Enova X-Wall MX Frequently Asked Questions FAQs Ver. 4
 Enova X-Wall MX Frequently Asked Questions FAQs Ver. 4 Q: What is X-Wall MX? A: X-Wall MX is the seventh generation of the X-Wall real-time full disk encryption technology. X- Wall MX equips with both
Enova X-Wall MX Frequently Asked Questions FAQs Ver. 4 Q: What is X-Wall MX? A: X-Wall MX is the seventh generation of the X-Wall real-time full disk encryption technology. X- Wall MX equips with both
3 System Requirements for SecureLogin
 NetIQ SecureLogin Quick Start Guide February 2019 1 About This Document It is highly recommended that you read this guide carefully before proceeding with installing, configuring, and deploying NetIQ SecureLogin.
NetIQ SecureLogin Quick Start Guide February 2019 1 About This Document It is highly recommended that you read this guide carefully before proceeding with installing, configuring, and deploying NetIQ SecureLogin.
Need high speed movement and rapid responsiveness? Utilize the Altivar 71 drive. Make the most of your energy SM. Altivar 71 drive
 Need high speed movement and rapid responsiveness? Utilize the Altivar 71 drive. Make the most of your energy SM Altivar 71 drive When your business is moving products, you need a drive that can move your
Need high speed movement and rapid responsiveness? Utilize the Altivar 71 drive. Make the most of your energy SM Altivar 71 drive When your business is moving products, you need a drive that can move your
Sentry ONE User Guide
 version 6.1 DataLocker Inc. April, 2018 Sentry ONE Standard and Managed 1 Contents About This Guide 2 Quick Start 3 About My Device 3 How Is This Different Than A Regular USB Drive?...........................
version 6.1 DataLocker Inc. April, 2018 Sentry ONE Standard and Managed 1 Contents About This Guide 2 Quick Start 3 About My Device 3 How Is This Different Than A Regular USB Drive?...........................
Company Intro. for 2017 FOSTEC INC.
 Company Intro. for 2017 FOSTEC INC. INTRODUCTION FOSTEC Inc. is a fiber optic components, cables and equipment manufacturer in South Korea. Being founded in 1998, with 15 years history FOSTEC could expand
Company Intro. for 2017 FOSTEC INC. INTRODUCTION FOSTEC Inc. is a fiber optic components, cables and equipment manufacturer in South Korea. Being founded in 1998, with 15 years history FOSTEC could expand
Total Biometric Solution Provider
 Total Biometric Solution Provider Physical Access Control 04 Access Control Security Solution 06 NAC-5000 08 enbioaccess-t5 10 enbioaccess-t3 12 Fingkey Access Plus 14 NAC-2500 Plus 16 Fingkey Access 138-050
Total Biometric Solution Provider Physical Access Control 04 Access Control Security Solution 06 NAC-5000 08 enbioaccess-t5 10 enbioaccess-t3 12 Fingkey Access Plus 14 NAC-2500 Plus 16 Fingkey Access 138-050
Federal Information Processing Standard (FIPS) What is it? Why should you care?
 Federal Information Processing Standard (FIPS) 140-2 What is it? Why should you care? SECURITY IS BECOMING A GROWING CONCERN The migration from TDM to IP communication networks has drastically increased
Federal Information Processing Standard (FIPS) 140-2 What is it? Why should you care? SECURITY IS BECOMING A GROWING CONCERN The migration from TDM to IP communication networks has drastically increased
Trusted Optical Disc March 2008
 Trusted Optical Disc March 2008 1 Agenda TCG - Trusted Optical Disc mission Overview - 2 minute drill Target Features/Platforms/Markets Optical SSC Details 2 Trusted Optical Disc Mission Encrypt data on
Trusted Optical Disc March 2008 1 Agenda TCG - Trusted Optical Disc mission Overview - 2 minute drill Target Features/Platforms/Markets Optical SSC Details 2 Trusted Optical Disc Mission Encrypt data on
CompTIA A+ Certification ( ) Study Guide Table of Contents
 CompTIA A+ Certification (220-902) Study Guide Table of Contents Course Introduction About This Course About CompTIA Certifications Module 1 / Supporting Windows 1 Module 1 / Unit 1 Windows Operating System
CompTIA A+ Certification (220-902) Study Guide Table of Contents Course Introduction About This Course About CompTIA Certifications Module 1 / Supporting Windows 1 Module 1 / Unit 1 Windows Operating System
Backing Up Your Data
 Backing Up Your Data Class Description A look at various ways to back up your precious data, whether pictures, videos, music, e-mail, or other documents. The 'Cloud' and online services, as well as do-it-yourself-and-maintain-control
Backing Up Your Data Class Description A look at various ways to back up your precious data, whether pictures, videos, music, e-mail, or other documents. The 'Cloud' and online services, as well as do-it-yourself-and-maintain-control
SECURE CLOUD BACKUP AND RECOVERY
 SECURE CLOUD BACKUP AND RECOVERY Learn more about how KeepItSafe can help to reduce costs, save time, and provide compliance for online backup, disaster recovery-as-a-service, mobile data protection, and
SECURE CLOUD BACKUP AND RECOVERY Learn more about how KeepItSafe can help to reduce costs, save time, and provide compliance for online backup, disaster recovery-as-a-service, mobile data protection, and
ABOUT THE GSS BUYING EVENT (SEPTEMBER - DECEMBER 2016)
 Government-Wide SPECIAL BUYING EVENT NOTIFICATION Strategic Sourcing (GSS) for Desktops & Laptops ABM Federal GSS Contract GS-26F-DA012 ABOUT THE GSS BUYING EVENT (SEPTEMBER - DECEMBER 2016) OMB GSS Desktop
Government-Wide SPECIAL BUYING EVENT NOTIFICATION Strategic Sourcing (GSS) for Desktops & Laptops ABM Federal GSS Contract GS-26F-DA012 ABOUT THE GSS BUYING EVENT (SEPTEMBER - DECEMBER 2016) OMB GSS Desktop
Security Requirements for Crypto Devices
 Security Requirements for Crypto Devices Version 1.0 02 May 2018 Controller of Certifying Authorities Ministry of Electronics and Information Technology 1 Document Control Document Name Security Requirements
Security Requirements for Crypto Devices Version 1.0 02 May 2018 Controller of Certifying Authorities Ministry of Electronics and Information Technology 1 Document Control Document Name Security Requirements
Enforcing Patch Management
 VMWARE TECHNICAL NOTE VMware ACE Enforcing Patch Management This technical note explains how to use VMware ACE to enforce the patch management policies that have been adopted by your company. This document
VMWARE TECHNICAL NOTE VMware ACE Enforcing Patch Management This technical note explains how to use VMware ACE to enforce the patch management policies that have been adopted by your company. This document
SuperCopier TM 7 Mini IT Hard Drive Duplicators Unit 3 x SATA and 4 x USB3.0-7 Touchscreen Color LCD Display Linux Base
 SuperCopier TM 7 Mini IT Hard Drive Duplicators Unit 3 x SATA and 4 x USB3.0-7 Touchscreen Color LCD Display Linux Base (SCR-0001) The SuperCopier 7 Mini field - IT unit is one of the top quality and performing
SuperCopier TM 7 Mini IT Hard Drive Duplicators Unit 3 x SATA and 4 x USB3.0-7 Touchscreen Color LCD Display Linux Base (SCR-0001) The SuperCopier 7 Mini field - IT unit is one of the top quality and performing
PKI Credentialing Handbook
 PKI Credentialing Handbook Contents Introduction...3 Dissecting PKI...4 Components of PKI...6 Digital certificates... 6 Public and private keys... 7 Smart cards... 8 Certificate Authority (CA)... 10 Key
PKI Credentialing Handbook Contents Introduction...3 Dissecting PKI...4 Components of PKI...6 Digital certificates... 6 Public and private keys... 7 Smart cards... 8 Certificate Authority (CA)... 10 Key
Chameleon series CM-5200
 w w w. a d v a n p o s. c o m Chameleon series CM-5200 15 Chameleon POS Terminal Features 15 TFT LCD with Resistive Touch Fanless Operation with Intel Atom TM processor N270 1.6 GHz Easy Detachable Monitor
w w w. a d v a n p o s. c o m Chameleon series CM-5200 15 Chameleon POS Terminal Features 15 TFT LCD with Resistive Touch Fanless Operation with Intel Atom TM processor N270 1.6 GHz Easy Detachable Monitor
Rugged All-in-one Handheld Computer. BIP-1500 Series
 Rugged All-in-one Handheld Computer BIP-1500 Series BIP-1500 Series INDUSTRIES Retail Public Transport Hospitality Finance The rugged all-in-one handheld computer, BIP-1500 Series, is designed to meet
Rugged All-in-one Handheld Computer BIP-1500 Series BIP-1500 Series INDUSTRIES Retail Public Transport Hospitality Finance The rugged all-in-one handheld computer, BIP-1500 Series, is designed to meet
Symantec Corporation
 Symantec Corporation Symantec PGP Cryptographic Engine FIPS 140-2 Non-proprietary Security Policy Document Version 1.0.4 Revision Date 05/01/2015 Symantec Corporation, 2015 May be reproduced only in its
Symantec Corporation Symantec PGP Cryptographic Engine FIPS 140-2 Non-proprietary Security Policy Document Version 1.0.4 Revision Date 05/01/2015 Symantec Corporation, 2015 May be reproduced only in its
Pegasus Equipments Export Limited. Local Contact:
 Pegasus Equipments Export Limited Add: #31G, Haiyige, Scienway Palace Science & Technology Industrial Park Shenzhen, China. Tel: +86 755 2658 3464 +86 755 2658 3596 Fax: +86 755 8611 0167 web: www.pegasusexport.com
Pegasus Equipments Export Limited Add: #31G, Haiyige, Scienway Palace Science & Technology Industrial Park Shenzhen, China. Tel: +86 755 2658 3464 +86 755 2658 3596 Fax: +86 755 8611 0167 web: www.pegasusexport.com
Plug into more places
 USB EVERYWHERE Plug into more places with our new family of USB flash drives USB ports are popping up everywhere... With more ports in more places, I can plug in just about anywhere SanDisk Cruzer USB
USB EVERYWHERE Plug into more places with our new family of USB flash drives USB ports are popping up everywhere... With more ports in more places, I can plug in just about anywhere SanDisk Cruzer USB
Unit 3 Part B. Computer Storage. Computer Technology
 Unit 3 Part B Computer Storage Computer Technology Storage The place in the computer where data is held while it is not needed for processing A storage device is device used to record (store) data The
Unit 3 Part B Computer Storage Computer Technology Storage The place in the computer where data is held while it is not needed for processing A storage device is device used to record (store) data The
3Com Wireless Bluetooth PC Card, USB Adapter, and Printer Adapter
 DATA SHEET 3Com Wireless Bluetooth PC Card, USB Adapter, and Printer Adapter Key Benefits Simplicity Bluetooth Connection Manager provides automatic discovery and point-and-click management of devices,
DATA SHEET 3Com Wireless Bluetooth PC Card, USB Adapter, and Printer Adapter Key Benefits Simplicity Bluetooth Connection Manager provides automatic discovery and point-and-click management of devices,
FIPS Non-Proprietary Security Policy
 Quantum Corporation Scalar Key Manager Software Version 2.0.1 FIPS 140-2 Non-Proprietary Security Policy Document Version 1.4 Last Update: 2010-11-03 8:43:00 AM 2010 Quantum Corporation. May be freely
Quantum Corporation Scalar Key Manager Software Version 2.0.1 FIPS 140-2 Non-Proprietary Security Policy Document Version 1.4 Last Update: 2010-11-03 8:43:00 AM 2010 Quantum Corporation. May be freely
Hewlett-Packard Development Company, L.P. NonStop Volume Level Encryption (NSVLE) Product No: T0867 SW Version: 2.0
 Hewlett-Packard Development Company, L.P. NonStop Volume Level Encryption (NSVLE) Product No: T0867 SW Version: 2.0 FIPS 140 2 Non Proprietary Security Policy FIPS Security Level: 1 Document Version: 1.3
Hewlett-Packard Development Company, L.P. NonStop Volume Level Encryption (NSVLE) Product No: T0867 SW Version: 2.0 FIPS 140 2 Non Proprietary Security Policy FIPS Security Level: 1 Document Version: 1.3
VMware, SQL Server and Encrypting Private Data Townsend Security
 VMware, SQL Server and Encrypting Private Data Townsend Security 724 Columbia Street NW, Suite 400 Olympia, WA 98501 360.359.4400 Today s Agenda! What s new from Microsoft?! Compliance, standards, and
VMware, SQL Server and Encrypting Private Data Townsend Security 724 Columbia Street NW, Suite 400 Olympia, WA 98501 360.359.4400 Today s Agenda! What s new from Microsoft?! Compliance, standards, and
PARALLELS SERVER 4.0 FOR MAC BARE METAL EDITION README
 PARALLELS SERVER 4.0 FOR MAC BARE METAL EDITION README February 18, 2010 1999-2010 Parallels Holdings, Ltd. and its affiliates. All rights reserved. This document provides the first-priority information
PARALLELS SERVER 4.0 FOR MAC BARE METAL EDITION README February 18, 2010 1999-2010 Parallels Holdings, Ltd. and its affiliates. All rights reserved. This document provides the first-priority information
CLASS 5. Encrypted High Security
 CLASS 5 Encrypted High Security 2 What is INDEPENDENTLY CERTIFIED Inner Range is proud to state that we are the FIRST electronic security manufacturer to gain independent CLASS 5 CERTIFICATION by the Australian
CLASS 5 Encrypted High Security 2 What is INDEPENDENTLY CERTIFIED Inner Range is proud to state that we are the FIRST electronic security manufacturer to gain independent CLASS 5 CERTIFICATION by the Australian
Samsung SSD PM863 and SM863 for Data Centers. Groundbreaking SSDs that raise the bar on satisfying big data demands
 Samsung SSD PM863 and SM863 for Data Centers Groundbreaking SSDs that raise the bar on satisfying big data demands 2 Samsung SSD PM863 and SM863 Innovations in solid state As the importance of data in
Samsung SSD PM863 and SM863 for Data Centers Groundbreaking SSDs that raise the bar on satisfying big data demands 2 Samsung SSD PM863 and SM863 Innovations in solid state As the importance of data in
Visual Evolution H.264 SVR-1670/490. Premium Digital Video Recorder
 H.264 Visual Evolution Premium Digital Video Recorder /490 H.264 high performance image compression Real-time High resolution recording H.264/JPEG multi-stream for high network performance Centralized
H.264 Visual Evolution Premium Digital Video Recorder /490 H.264 high performance image compression Real-time High resolution recording H.264/JPEG multi-stream for high network performance Centralized
Mobile Internet Devices and the Cloud
 Mobile Internet Devices and the Cloud What Is a Smartphone? Mobile Operating Systems for Smartphones 1. iphone 2. Google (Android) 3. Blackberry 4. Windows Mobile 5. Ubuntu Mobile Internet Device (MID)
Mobile Internet Devices and the Cloud What Is a Smartphone? Mobile Operating Systems for Smartphones 1. iphone 2. Google (Android) 3. Blackberry 4. Windows Mobile 5. Ubuntu Mobile Internet Device (MID)
FIPS Level 1 Validation March 31, 2011 Version 1.12
 KoolSpan TrustChip Developer Kit (TDK) Cryptographic Library Version 3.0 Security Policy FIPS 140-2 Level 1 Validation March 31, 2011 Version 1.12 Table of Contents 1 Introduction... 1 1.1 Acronyms and
KoolSpan TrustChip Developer Kit (TDK) Cryptographic Library Version 3.0 Security Policy FIPS 140-2 Level 1 Validation March 31, 2011 Version 1.12 Table of Contents 1 Introduction... 1 1.1 Acronyms and
