CONTENTS. Page 3 CEOP: Keeping your child safe online A checklist for parents and carers
|
|
|
- Elfrieda Morrison
- 5 years ago
- Views:
Transcription
1 Page 1 of 24
2 CONTENTS Page 3 CEOP: Keeping your child safe online A checklist for parents and carers 4 60 Texting Slangs of Teens Parents Should Know 5 CEOP: Risks children face online: Accessing inappropriate websites 6 K9 Web Protection 7 CEOP: Risks children face online: Cyberbullying 8 Cyberbullying Key safety advice 9 11 CEOP: Risks children face online: Online grooming Suggested Facebook Privacy Settings 23 How today s technology can be used 24 When and how to contact the Service Provider Page 2 of 24
3 Page 3 of 24
4 60 Texting Slangs of Teens Parents Should Know Are you trying to decode your teen's slang or decipher the text messaging abbreviations you often see? Teens are clever at keeping their private life hidden from their parents and it can be difficult to get information. They are the best at using slang and abbreviations while texting friends in secret code. It's easy for them to get ahead of the game, but they may not realise you can get your hands on some good reference material that can give you a look into what's inside their "technical" lingo. There are hundreds of them, for more details please visit or ASL = Age, Sex, Location 2. ASLP = Age, Sex, Location, Picture 3. BF = Boyfriend 4. BOM = Bitch of Mine 5. BRB = Be Right Back 6. CD9 = Parents Are Around 7. GF = Girlfriend 8. GNOC = Get Naked on Cam 9. G2G = Got to Go 10. HSWM = Have Sex with Me 11. IDK = I Don't Know 12. KMA = Kiss my A** 13. (L)MIL = (Let's) Meet in Real Life 14. MOS = Mom Over Shoulder 15. N/S = No Sh** 16. NIFOC = Naked In Front of Computer 17. NMJC = Nothin' Much, Just Chillin' 18. NMU = Not Much, You? 19. NOOB = code for saying someone doesn't know much about something 20. P911 = Parent Emergency 21. PIR = Parent in Room 22. POS = Parent Over Shoulder or piece of sh** 23. PRON = Porn 24. PRW = Parents Are Watching 25. SR2 = Send to Receive (photos) 26. STFU = Shut the F*** Up 27. TDTM = Talk Dirty to Me 28. Warez - Pirated Software 29. W/E = Whatever 30. ZZZ = Sleeping, Bored, Tired = Oral Sex = One to one = Elite = I love you = I hate you 36. 2c4u = Too cool for you 37. 2h2h = Too hot to handle = Marijuana = I love you = Parent has left 41. A3 = Anyplace, anywhere, anytime 42. Addy or ADR = Address 43. AH = At home 44. Banana = Penis 45. GYPO = Get your pants off 46. IMEZRU = I am easy, are you? 47. KFY or K4Y = Kiss for you? 48. Kitty = Vagina 49. KPC = Keeping parents clueless 50. MorF = Male of Female 51. LMIRL = Let s meet in real life 52. MOOS = Member of the opposite sex 53. MOS = Mum over shoulder 54. NALOPKT = Not a lot of people know that 55. NIFOC = Nude in front of the computer 56. NMU = Not much, you? 57. RU/18 = Are you over 18? 58. WYCM = Will you call me? 59. YOLO = You only live once 60. MPFB = My personal f*** buddy Page 4 of 24
5 Page 5 of 24
6 K9 Web Protection A wide open Internet is unsafe for children. Pornography and other adult content are available with ease to curious young minds, and often appear without any explicit action on the part of the child. Social media web sites can impose uncomfortable or offensive interactions with others pretending to be friends. K9 Web Protection is a FREE Internet filtering and parental control software for the home. K9 puts YOU in control of the Internet so you can protect your kids. It will work on any recent version of Microsoft Windows or Apple MAC. There is also a browser app available for Android, iphone, ipod Touch or ipad. K9 Features to protect your children: Web site blocking by category, including pornography, illegal drugs, personals/dating, violence/hate/racism Easy pre-set levels to choose from depending on the age of your children Safe Search enabled on all search engines to show cleaner search results Time restrictions, including Night Guard(tm), to disallow internet access during designated times Custom always allow and always block lists for your personal preferences Ability to override a block with the parent password Tamper resistant for more savvy kids Reports showing activity to categories of web sites Real-time categorization of new web sites Compatible with Windows or Mac machines In addition to filtering the categories or sites you choose, K9 also offers: Real-time malware protection Blue Coat Web Filter helps identify and block illegal or undesirable content in real time, including malware-infected sites. You also benefit from the Web Pulse cloud service, a growing community of more than 62 million users who provide more than six billion real-time Web content ratings per day. Automatic content ratings New Web sites and pages are created every minute, and no one person can possibly rate or categorize all of them. To ensure protection against new or previously unrated Web sites, Blue Coat s patent-pending Dynamic Real-Time Rating (DRTR) technology automatically determines the category of an unrated Web page, and allows or blocks it according to your specifications. Continuous protection that won t slow down your computer Caching is the method your Web browser uses to save frequently used data, which increases efficiency by reducing the amount of information requested over the Internet. K9 uses Blue Coat s unique caching technology, so your Internet experience is always as fast as possible. Page 6 of 24
7 Page 7 of 24
8 Cyber-Bullying Key Safety Advice For Children & Young People 1. Always respect others be careful what you say online and what images you send. 2. Think before you send whatever you send can be made public very quickly and could stay online forever. 3. Treat your password like your toothbrush - keep it to yourself. Only give your mobile number or personal website address to trusted friends. 4. Block the bully learn how to block or report someone who is behaving badly. 5. Don t retaliate or reply! 6. Save the evidence learn how to keep records of offending messages, pictures or online conversations. 7. Make sure you tell: an adult you trust, or call a helpline like Child Line on in confidence; the provider of the service; check the service provider s website to see where to report incidents; your school your form tutor or your Head of Year can help you. Finally, don t just stand there if you see cyber-bullying going on, support the victim and report the bullying. How would you feel if no one stood up for you? Key Safety Advice For Parents & Carers 1. Be aware, your child may as likely cyber-bully as be a target of cyber-bullying. Be alert to your child seeming upset after using the internet or their mobile phone. This might involve subtle comments or changes in relationships with friends. They might be unwilling to talk or be secretive about their online activities and mobile phone use. 2. Talk with your children and understand the ways in which they are using the internet and their mobile phone. See the seven key messages for children (above) to get you started. 3. Use the tools on the service and turn on in-built internet safety features. North Walsham High School can offer parents free computer monitoring software. 4. Remind your child not to retaliate. 5. Keep the evidence of offending s, text messages or online conversations. 6. Report cyber-bullying: Contact your child s school if it involves another student, so that they can take appropriate action. Contact the service provider. If the cyber-bullying is a potential criminal offence, you should consider contacting the police Page 8 of 24
9 Page 9 of 24
10 Page 10 of 24
11 Page 11 of 24
12 Suggested Facebook Privacy Settings Copyright Linda Garratt and Hilden Oaks School Published under a Creative Commons Attribution/Share-alike license, see This document is updated at regular intervals as facebook changes their settings. For the most recent version, please visit Disclaimer: Facebook changes and updates its privacy system on an on-going basis. Neither the author, the school nor any of its employees accepts any liability or warranty, express or implied, for the advice given in this document. It is your sole responsibility to ensure that your privacy settings are appropriate and up-to-date. Original document: Update for facebook Places: Update for changes to tagging privacy Update for general changes to privacy settings Update for timeline Further updates for timeline Updates for changes to privacy settings Updates for changes Page 12 of 24
13 Suggested Facebook Privacy Settings It can be very hard to work out which Privacy Settings are best for you. What is recommended to keep you safe? Employers and colleges are routinely checking social networking sites, so it is vital that every user of these sites actively reviews their Privacy Settings on a regular basis to ensure that their information is only shared with the intended people and that personal and professional reputations are protected. Facebook s Terms and Conditions contain some very important clauses: 1. For content that is covered by intellectual property rights, like photos and videos (IP content), you specifically give us the following permission, subject to your privacy and application settings: you grant us a non-exclusive, transferable, sub-licensable, royalty-free, worldwide license to use any IP content that you post on or in connection with Facebook (IP License). This IP License ends when you delete your IP content or your account unless your content has been shared with others, and they have not deleted it. 2. When you delete IP content, it is deleted in a manner similar to emptying the recycle bin on a computer. However, you understand that removed content may persist in backup copies for a reasonable period of time (but will not be available to others). 3. When you use an application, the application may ask for your permission to access your content and information as well as content and information that others have shared with you. We require applications to respect your privacy, and your agreement with that application will control how the application can use, store, and transfer that content and information. (To learn more about Platform, read our Privacy Policy and Platform Page.) 4. When you publish content or information using the Public setting, it means that you are allowing everyone, including people off of Facebook, to access and use that information, and to associate it with you (i.e., your name and profile picture). 5. We always appreciate your feedback or other suggestions about Facebook, but you understand that we may use them without any obligation to compensate you for them (just as you have no obligation to offer them). This means that unless you sort your settings out, facebook could use your pictures and information however they choose. If you don t want someone to see your pictures, personal information or innermost thoughts, don t put it on facebook in the first place. Mobile Apps The mobile apps for facebook supplied on mobile phones and tablets is very handy, but trying to find all the privacy setting details can be tricky. It is recommended that you log into facebook using a web browser to ensure you get everything covered in this guide. Location Services The great thing about facebook is being able to tell everyone about where you ve been and Location Services enable you to tell everyone exactly where you are. Please think carefully before you use it. You could well be telling the entire world that your home is empty and available from burglary or telling everyone that you are not at school or work when you should be! Even without using facebook s own location services, every photograph that you take on a mobile phone, tablet, or camera with GPS, will automatically be tagged with your location unless you explicitly turn this off. This feature does help to run down the battery quicker, so you may wish to disable it on your device for that reason alone. If these location-tagged photos are then posted on the internet, anyone then has access to your location via the photo. You may be giving away your home address, the place where your children play on their own, or showing the exact location of a valuable item without even realising. Page 13 of 24
14 Part 1: You cannot choose your family, but you can choose your facebook friends. Casual acquaintances are less likely to be careful with your information than close friends. Think carefully about who you accept as a friend on facebook. It is not a competition to see who can have the most friends! You see your colleagues every day at work; do they need to be friends on facebook too? That moment of frustration may be seen by more people than you intended. Teachers and other public figures run the risk of fake accounts being set up in their name. By friending these accounts you allow the fraudster to see things you thought were private. It s a ploy used by bullies too. If you are invited to be the friend of someone whose account could be fraudulent, send an to their work address (which is less likely to be hacked than one like gmail or yahoo) or telephone them (not text) to double check that the invitation is genuine. It could save you being embarrassed by a fraudster or mischief-maker getting access to your profile information. of are people known to your friends. Many of them will be complete strangers to you. If you use this privacy setting, you may as well use Public. Where you can choose who can see or do something to your wall or profile, you have more flexibility now. In addition to Public, of, and Only Me, you will now see Lists (family or friends who share an interest, school or university for example). Click on See all lists to get other lists created by yourself or automatically by facebook. Sometimes the setting you want isn t there (Only Me often disappears), or you wish to hide things from certain people. Click on Custom to get this window In the Custom privacy window, you could allow all your friends to see something, but hide (Don t share) things from one or more specific users or Lists if you wanted to. Using the drop down box allows you to choose different options for visibility or hiding. To be honest, if you use Only Me, the information really shouldn t be there in the first place, BUT it does stop accidents; so do it anyway! Page 14 of 24
15 Part 2: Privacy Settings Login to facebook - in the top right hand corner click on the Cog symbol to the right of the word Home and choose Privacy Settings from the drop-down menu to get the following screen. 1. Who can see my stuff? Who can see your future posts? This one s very simple; click on Edit and choose to limit what you post to your facebook friends by default. Be aware that this is easily changed by accident. When posting a status on your wall, you can change the privacy setting for that post and this changes this default setting for all future posts. Review all your posts and things your tagged in Click on Use Activity Log to go back through all your previous activity and decide, one by one, whether you wish these things to appear on your timeline or not. If the post was originally made by someone else, you cannot change the Privacy Setting, but you can choose whether or not it appears on your Timeline. Limit the audience for posts you ve shared with of or Public? This one will save a lot of time going back through past public posts. If you have tagged someone in a post or picture, the privacy of that post through their timeline is controlled by their privacy setting, not yours. This means any post or picture containing tags will be available to of your ; in other words, it is effectively Public. Use tagging with caution. Page 15 of 24
16 2. Who can look me up? These are the basic settings allowing people to find you in facebook. Who can look you up using the address or phone number you provided? Use Edi to set this to. Do you want other search engines to link to your timeline? This controls how users who are not logged into facebook can see your information, e.g. Google. Controlling your privacy is hard enough already, without letting Google broadcast your world too. Uncheck the Let other search engines box to disable it, ignoring any dire warnings of doom and gloom from doing so. If you are under the age of 18, this will be switched off by default, but it does give you the option to let facebook switch it on for you on your 18 th birthday make sure it s disabled anyway! 3. Timeline and tagging Click on Timeline and Tagging in the Column on the left to get this screen: This group of settings controls tagging and facebook places. Both of these can be great fun, but if you don t know that you ve been tagged or you are checked in to somewhere that you haven t been to, you could end up in a lot of trouble! The minimum recommended settings should be as above. It is very important that you have Review posts turned On so that you are only tagged in things you consider to be appropriate. Tag suggestions are not currently available due to law suits concerning privacy. If they become available again, I recommend that you do not allow them. Page 16 of 24
17 4. Followers Click on Followers in the Column on the left to get this screen: Followers are people who are not your friends. When they subscribe to your Timeline, they will see all Public posts and photos. To avoid accidents, it is better NOT to allow followers. 5. Apps The apps and websites you access through facebook have permission to use all sorts of information on your profile and then broadcast it. The list of Apps you have ever used can be much longer than expected, click on Apps in the column on the left to get this screen: 5a. Apps you use: Apps are a matter of preference. If you really don t use them or want to use them you can click on Edi to Turn Off platform apps on this screen. You can be in control of the Apps you use, but you do need to check each one individually as they are all different. Click on Edit for each to find out what is happening. Don t forget to make sure that the Posts on your behalf is appropriate. Do you really want all your friends to know every time you use the app? Farmville may only be irritating to them, other apps could raise questions. Notifications are purely a matter of choice how much do you want to know about what s happening in this app? There is also an option to Remove the App and all its permissions and also to Report an app that you think is inappropriate or is doing something it shouldn t. Page 17 of 24
18 5b. Apps others use: Other people use apps too. Use Edi to see the screen below. Uncheck everything and Save Changes. 5c. Instant personalisation: This controls how other selected websites can access your information. Going into this option brings up a video clip telling you how wonderful it is. Close the video! You then get this screen. Uncheck the Enable box and you ll get an Are you really sure you want to do this? box. The only thing that will lose out is facebook s advertising revenue, so Confirm and it is then switched off! 5d. Old versions of facebook for mobile: As long as you keep mobile versions of facebook updated, you should be able to keep up with latest privacy settings changes. However, it is sensible to do this just in case. Page 18 of 24
19 6. Adverts Click on Adverts in the Column on the left to get this screen: Do you find those adverts spookily pertinent to you? Did you realise that facebook accesses your account information to tailor these? Third Party Sites: Facebook says it doesn t give your information away to third parties at the moment, but they very kindly give you the option to opt out now should they change this in the future. The fact that they have this option suggests that they are thinking of doing so in the foreseeable future. Click on Edit and change this setting to No one and then Save Changes, ignoring any messages of doom and gloom from facebook for doing so. Ads & : Your information is being used to promote products to you and other people (even if they are your friends). Again this may reveal information about you that you may not wish others to know. Click on Edit and change this setting to No one and then Save Changes, ignoring any messages of doom and gloom from facebook for doing so. Page 19 of 24
20 6. Security Settings Click on Security Settings in the Column on the left to get this screen: Friend s Name Friend s Name Friend s Name Friend s Name This is where you can have some degree of control over how your account is accessed. These settings enable you to control which devices (computers, phones) are authorised to access your facebook account and how you are notified if your account is accessed from a new device. Login Approvals requires your mobile phone to be switched on this may not be convenient! Part 3: Your Timeline Profile Your profile is where facebook encourages you to enter everything about your entire life and tell the world treat it with care. With timeline it is all neatly indexed by year making things easier to find. Do your friends really want to know? Could your information be open to misinterpretation by someone else? Could the information come back to haunt you in years to come? To get to your Timeline, click on your profile picture to the left of your name in the blue bar at the top. You will then see your timeline. Under the cover picture, click on the Update Info button. Make changes by clicking on the Edit button for the block. Click on the About tab to get to the drop down menu giving you access to the other parts of your profile. Page 20 of 24
21 LESS IS MORE! As you work your way through each of the profile content options, think carefully about what information should be seen by whom. Do you actually need to put that information up there in the first place? For example: Your friends and family probably know your mobile number and address already. If they need to get in touch and they ve lost your number, they can always use facebook messaging to contact you so don t put them in your profile or set the privacy to Only Me. Political and religious views cause an awful lot of arguments and mistrust. Keep them to yourself. Don t put them on facebook, that way they cannot be misinterpreted. If you are looking for a partner, don t broadcast it on facebook where all your colleagues / students / clients can see it if your privacy settings aren t correct, you could be embarrassed. THINK BEFORE YOU POST! IF YOU MUST PUT IT ON FACEBOOK, MAKE SURE THE PRIVACY IS TIGHT ENOUGH! The following tables are the minimum suggested settings for each option. Remember to save after changing them and use more restrictive settings if preferred. Work and Education Employment history College/University Secondary School Living (Edit button) Current city Hometown Family (Edit button) Relationship status Family About You (Edit button) Basic Info (Edit button) Show my sex on my timeline Birthday Interested in Relationship status Languages Religion Political Views Contact Info (Edit button) s Mobile phones Other phones IM screen names Address Website Favourite Quotations (Edit button) Click on the Edit button Who can see your full friend list? About Public Public Only me Only me Check box if you wish to Only me Only me Only me Only me Only me Only me Only me Only me Only me Page 21 of 24
22 Photos For every separate album choose a privacy level. is the maximum recommended The exception is your Profile picture/cover photo which is automatically public so choose those pictures wisely! Be aware that your camera, phone, ipad or other device maybe recording the location of a photo without you being aware. Posting these photos on facebook means that anyone who has access to a photo can see where it was taken and thus find out where you live, where your valuables are, where your holiday home is, etc. To prevent this, you must turn off location services on the device taking the photo. Map A record of everywhere you have ever been and you can include photos and tag your companions. If you must use it, make sure that you set privacy to maximum of, but be aware how easy it would be to compromise yourself by adding to it. Check locations already recorded by clicking on the map pin. If you are away from home and your house is empty, don t tell others where you are by using this feature; it s very good way of inviting burglars round! Favourites Likes (Edit button) Music, books, movies, television, games, athletes, sports team, favourite sports, activities, interests, inspirational people Other Pages you like By liking pages for companies and products you are giving these pages permission to access your personal information. You are recommended to think carefully before you do this! Do you really want them to have access to your life story? Or don t use these Click on Edit button If you ever use this Subscriptions Notes Only me Everything that you do in facebook can be controlled by privacy settings. Get in the habit of double checking the privacy every time you post to your wall. Part 4: Your Status Updates may be the most appropriate setting most of the time, but sometime you may not want somebody in your facebook friend list to know something. Use the icon to change it, but remember that customisation will be remembered for your next Status Update and might need changing again. Lovely as it is to tell everyone exactly where you are and what you re doing, try not to advertise that your house is empty. Tell your friends when you get home! Almost It can be guaranteed that the look and functionality of facebook will change again. This is what the facebook screens look like on 14 th October 2013! Page 22 of 24
23 The table below explores the range of ways today s technology can be used. Technology Great for: Examples of misuse: Mobile phone Instant messenger (IM) Chatrooms & message boards s Webcams Social network Sites Video hosting sites Virtual Learning Environment Gaming sites, consoles and virtual worlds Keeping in touch by voice or text, taking and sending pictures and film, listening to music, playing games, going online and sending s. Useful in emergency situations and for allowing children a greater sense of independence. Text or voice chatting live with friends online. A quick and effective way of keeping in touch even while working on other things. Groups of people around the world can text or voice chat live about common interests. For young people, this can be an easy way to meet new people and explore issues which they are too shy to talk about in person. Sending electronic letters, pictures and other files quickly and cheaply anywhere in the world. Taking pictures or recording messages. Being able to see and talk to someone live on your computer screen. Bringing far- off places to life or video conferencing. Socialising with your friends and making new ones within online communities. Allowing young people to be creative online, even publishing online music. Personalising homepages and profiles, creating and uploading content. Accessing useful educational, entertaining and original creative video content and uploading your own. School site, usually available from home and school, set up for tracking and recording student assignments, tests and activities, with message boards, chat and IM Live text or voice chat during online gaming between players across the world, or on handheld consoles with people in the same local area. Virtual worlds where users design their own avatars or figure that represents them in the virtual world. Sending nasty calls or text messages, including threats, intimidation, and harassment. Taking and sharing humiliating and/or inappropriate images. Videoing other people being harassed and sending these to other phones or internet sites. Taking photos or video of people without their permission or against their will. Sending nasty messages or content. Using someone else s account to forward rude or mean messages via their contacts list. Sending nasty or threatening anonymous messages. Groups of people deciding to pick on or ignore individuals. Making friends under false pretences people pretending to be someone they re not in order to get personal information that they can misuse in a range of ways e.g. by spreading secrets or blackmailing. Sending nasty or threatening messages. Forwarding unsuitable content including images and video clips, or sending computer viruses. Accessing someone else s account, e.g. to forward personal s or delete s. Making and sending inappropriate content. Persuading or threatening young people to act in inappropriate ways. Using inappropriate recordings to manipulate young people. Posting nasty comments, humiliating images / video. Accessing another person s account details and sending unpleasant messages, deleting information or making private information public. Groups of people picking on individuals by excluding them. Creating fake profiles to pretend to be someone else, e.g. to bully, harass or get the person into trouble. Posting embarrassing, humiliating film of someone. Posting copyrighted material. Posting inappropriate messages or images. Hacking into someone else s account to post inappropriate comments or delete schoolwork. Name-calling, making abusive/derogatory remarks. Players may pick on weaker or less experienced users, repeatedly bulling their characters. Forwarding unwanted messages to other devices in the immediate vicinity. Playing adult rated games. Page 23 of 24
24 When and how to contact the Service Provider Mobile Phones: All UK mobile phone operators have nuisance call centres set up and / or procedures in place to deal with such instances. They may be able to change the number of the person being bullied. Mobile operators cannot bar a particular number from contacting a phone, but some phone handsets do have this capacity. Action can be taken against the bully s phone account (e.g. blocking their account) only with police involvement. Social networking sites (e.g., Facebook, Twitter, Tumblr): It is good practice for social network providers to make reporting incidents of cyber bullying easy, and thus have clear, accessible and prominent reporting features. Many of these reporting features will be within the profiles themselves, so they are handy for the user. If social network sites do receive reports about cyber bullying, they will investigate and can remove content that is illegal or break their terms and conditions in other ways. They can delete the account of those who have broken the rules. 02: ncb@02.com or Vodafone: 191 from a Vodafone phone or for Pay Monthly customers and for Pay as you Go. 3: Call 333 from a 3 phone or Orange: Call 450 on an Orange phone or for Pay as you Go, or 150 or for Pay Monthly. T-Mobile: Call 150 on a T-Mobile phone or Video hosting sites: Contacts of some social network sites Facebook: The best way to report abusive content on Facebook is by using the Report link that appears near the content itself. North Walsham High School can provide a Facebook Privacy Settings guide. This is an up to date document that gives you recommended settings on how to make your account secure and safe. Twitter: Twitter has a comprehensive Help Centre offering information, advice and guidance. If your issue cannot be resolved you can file an online report. Tumblr: Tumblr has an where you can report both users and blogs for abuse, harassment, illicit content or spam messages. There is also a link right next to the person/blog where you can block them. To report someone on Tumblr, first of all, try to always keep the message that this person/blog has sent you. This is a proof that you can send to Tumblr just in case they ask for it. Sent an to abuse@tumblr.com including the user s name and screenshots of the harassment message. You can also go to enter the username, and right next to it (or below) click on spam, harassment. Video hosting Sites: It is possible to get content taken down from video hosting sites, though the content will need to be illegal or have broken the terms of service of the site in other ways. On YouTube, perhaps the most well known of such sites, it is possible to report content to the site provider as inappropriate. In order to do this, you will need to create an account (this is free) and log in, and then you will have the option to flag content as inappropriate. The option to flag the content is under the video content itself. YouTube provides information on what is considered inappropriate in its terms of service. See Instant Messenger (e.g., Windows Live Messenger or MSN Messenger): It is good practice for Instant Messenger (IM) providers to have visible and easy to access reporting features on their service. Instant Messenger providers can investigate and shut down any accounts that have been misused and clearly break their terms of service. The best evidence for the service provider is archived or recorded conversations and most IM providers allow the user to record all messages. Contacts of some IM providers: MSN: When in Windows Live Messenger, clicking the Help tab will bring up a range of options, including Report Abuse and there is also an online feedback form at: support.msn.com/default.aspx?mkt=en-gb to report on a range of products including MSN Messenger. Yahoo!: When in Yahoo! Messenger, clicking the Help tab will bring up a range of options, including Report Abuse. Chatrooms, individual website owners / forums, message board hosts: It is good practice for chat providers to have a clear and prominent reporting mechanism to enable the user to contact the service provider. Users that abuse the service can have their account deleted. Some services may be moderated, and the moderators will warn users posting abusive comments or take down content that breaks their term of use. Page 24 of 24
Suggested Facebook Privacy Settings
 Suggested Facebook Privacy Settings Copyright Linda Garratt and Hilden Oaks School 2013. Published under a Creative Commons Attribution/Share-alike license, see http://creativecommons.org/licenses/by-sa/3.0/
Suggested Facebook Privacy Settings Copyright Linda Garratt and Hilden Oaks School 2013. Published under a Creative Commons Attribution/Share-alike license, see http://creativecommons.org/licenses/by-sa/3.0/
EADS up. stop think connect
 EADS up stop think connect You text, you play games, you share photos and video. You update your status, you post comments, you probably spend some time in a virtual world. Being online connected through
EADS up stop think connect You text, you play games, you share photos and video. You update your status, you post comments, you probably spend some time in a virtual world. Being online connected through
Anti-Cyber Bullying Policy.
 Anti-Cyber Bullying Policy. Bullying, in any form, is an issue that we all take very seriously at Bredon School. We accept that victims can become depressed and suicidal, and even take their own lives.
Anti-Cyber Bullying Policy. Bullying, in any form, is an issue that we all take very seriously at Bredon School. We accept that victims can become depressed and suicidal, and even take their own lives.
Social Media Reputation Management
 Social Media Reputation Management If you are using social media sites such as Facebook or Twitter, there are some simple steps you can take to manage your reputation and protect your identity. Even if
Social Media Reputation Management If you are using social media sites such as Facebook or Twitter, there are some simple steps you can take to manage your reputation and protect your identity. Even if
Digital Safety and Digital Citizenship
 Digital Safety and Digital Citizenship A Guide for Students The laptop has been given to you as a tool for learning. Use it for that. While doing so, here are some important rules for keeping yourself
Digital Safety and Digital Citizenship A Guide for Students The laptop has been given to you as a tool for learning. Use it for that. While doing so, here are some important rules for keeping yourself
Facebook Basics (for individuals)
 P a g e 1 Facebook Basics (for individuals) ABOUT THIS CLASS This class is designed to give a basic introduction into Facebook Basics. Throughout the class, we will progress from learning how to create
P a g e 1 Facebook Basics (for individuals) ABOUT THIS CLASS This class is designed to give a basic introduction into Facebook Basics. Throughout the class, we will progress from learning how to create
HOW TO CONFIGURE SOCIAL MEDIA PRIVACY SETTINGS
 HOW TO CONFIGURE SOCIAL MEDIA PRIVACY SETTINGS The right settings are critical when it comes to keeping your kids safe on social media. Here s a quick guide to safe settings for some of the most popular
HOW TO CONFIGURE SOCIAL MEDIA PRIVACY SETTINGS The right settings are critical when it comes to keeping your kids safe on social media. Here s a quick guide to safe settings for some of the most popular
Cyber Smarts Using Social Media Wisely
 Cyber Smarts Using Social Media Wisely Posted on March 24, 2016 by Shridevi Stock Photo You have access to the world s largest museum, art gallery, library and social group ever created. You also have
Cyber Smarts Using Social Media Wisely Posted on March 24, 2016 by Shridevi Stock Photo You have access to the world s largest museum, art gallery, library and social group ever created. You also have
Lambton Primary School
 Lambton Primary School Advice to pupils on Cyber Bullying For pupils If you re being bullied by phone or the internet Remember, bullying is never your fault. It can be stopped, and it can usually be traced.
Lambton Primary School Advice to pupils on Cyber Bullying For pupils If you re being bullied by phone or the internet Remember, bullying is never your fault. It can be stopped, and it can usually be traced.
Social Networking Applied
 Social Networking Applied 1 I. Facebook Social Networking Applied Uses: An address book: Facebook users can share their current city, e-mail address, phone number, screen name, street address, and birthday
Social Networking Applied 1 I. Facebook Social Networking Applied Uses: An address book: Facebook users can share their current city, e-mail address, phone number, screen name, street address, and birthday
Social Media and Cyber Safety
 Social Media and Cyber Safety Social Media Apps/Sites Middle School Students May Be Using Facebook Twitter Instagram Ask.fm Kik Messenger SnapChat Tumblr Web-based games Group Chats Facebook and Twitter
Social Media and Cyber Safety Social Media Apps/Sites Middle School Students May Be Using Facebook Twitter Instagram Ask.fm Kik Messenger SnapChat Tumblr Web-based games Group Chats Facebook and Twitter
Sky Social Media Guidelines for Contributors
 Sky Social Media Guidelines for Contributors Social chatter around TV shows is inevitable and, for the most part, positive. However, contributors are advised that people have a tendency to publish things
Sky Social Media Guidelines for Contributors Social chatter around TV shows is inevitable and, for the most part, positive. However, contributors are advised that people have a tendency to publish things
FACEBOOK SAFETY FOR JOURNALISTS. Thanks to these partners for reviewing these safety guidelines:
 FACEBOOK SAFETY FOR JOURNALISTS Thanks to these partners for reviewing these safety guidelines: 10 STEPS TO KEEP YOURSELF SAFE Journalists are using Facebook in innovative ways to do their jobs, tell stories,
FACEBOOK SAFETY FOR JOURNALISTS Thanks to these partners for reviewing these safety guidelines: 10 STEPS TO KEEP YOURSELF SAFE Journalists are using Facebook in innovative ways to do their jobs, tell stories,
ONLINE SAFETY. Messaging, , Vlogging and Sexting
 ONLINE SAFETY Messaging, email, Vlogging and Sexting www.eitts.co.uk Contents WhatsApp & Messaging Email Vlogging Sexting THE RISKS People online are not necessarily who they say they are or seem to be.
ONLINE SAFETY Messaging, email, Vlogging and Sexting www.eitts.co.uk Contents WhatsApp & Messaging Email Vlogging Sexting THE RISKS People online are not necessarily who they say they are or seem to be.
Getting started with social media and comping
 Getting started with social media and comping Promotors are taking a leap further into the digital age, and we are finding that more and more competitions are migrating to Facebook and Twitter. If you
Getting started with social media and comping Promotors are taking a leap further into the digital age, and we are finding that more and more competitions are migrating to Facebook and Twitter. If you
Adobe Spark. Schools and Educators. A Guide for. spark.adobe.com
 Adobe Spark A Guide for Schools and Educators spark.adobe.com CONTENTS 1: What Is Adobe Spark?... 3 2: How Much Does Adobe Spark Cost?... 4 3: Is Adobe Spark A Web Application Or An App?... 4 4: Three
Adobe Spark A Guide for Schools and Educators spark.adobe.com CONTENTS 1: What Is Adobe Spark?... 3 2: How Much Does Adobe Spark Cost?... 4 3: Is Adobe Spark A Web Application Or An App?... 4 4: Three
TELSTRA TECH SAVVY SENIORS - BEGINNERS GUIDE INTRODUCTION TO SOCIAL MEDIA - PART 1
 TOPIC: INTRODUCTION TO SOCIAL MEDIA PART 1 WHAT TO USE AND WHEN The internet helps you stay in touch with friends and loved ones. Social media sites like Facebook and Twitter let you see what s happening
TOPIC: INTRODUCTION TO SOCIAL MEDIA PART 1 WHAT TO USE AND WHEN The internet helps you stay in touch with friends and loved ones. Social media sites like Facebook and Twitter let you see what s happening
Social Media E-Safety Guide. For more help and advice visit:
 Social Media E-Safety Guide For more help and advice visit: https://www.net-aware.org.uk/ https://www.thinkuknow.co.uk/ https://www.ceop.police.uk/ Twitter https://www.net-aware.org.uk/networks/twitter/
Social Media E-Safety Guide For more help and advice visit: https://www.net-aware.org.uk/ https://www.thinkuknow.co.uk/ https://www.ceop.police.uk/ Twitter https://www.net-aware.org.uk/networks/twitter/
Learning and Development. UWE Staff Profiles (USP) User Guide
 Learning and Development UWE Staff Profiles (USP) User Guide About this training manual This manual is yours to keep and is intended as a guide to be used during the training course and as a reference
Learning and Development UWE Staff Profiles (USP) User Guide About this training manual This manual is yours to keep and is intended as a guide to be used during the training course and as a reference
facebook a guide to social networking for massage therapists
 facebook a guide to social networking for massage therapists table of contents 2 3 5 6 7 9 10 13 15 get the facts first the importance of social media, facebook and the difference between different facebook
facebook a guide to social networking for massage therapists table of contents 2 3 5 6 7 9 10 13 15 get the facts first the importance of social media, facebook and the difference between different facebook
Facebook Guide. How many Facebook friends should I have?
 To Friend or Not to Friend How many Facebook friends should I have? Facebook is a great way to stay in connected with your friends when you are not in direct contact with them. As soon as you add a friend
To Friend or Not to Friend How many Facebook friends should I have? Facebook is a great way to stay in connected with your friends when you are not in direct contact with them. As soon as you add a friend
A GUIDE TO CYBERBULLYING THINK BEFORE YOU POST
 A GUIDE TO CYBERBULLYING THINK BEFORE YOU POST WHAT IS BULLYING? Bullying is repeated aggression, verbal, psychological or physical conduct by an individual or a group against others. Bullying is always
A GUIDE TO CYBERBULLYING THINK BEFORE YOU POST WHAT IS BULLYING? Bullying is repeated aggression, verbal, psychological or physical conduct by an individual or a group against others. Bullying is always
ANDROID PRIVACY & SECURITY GUIDE ANDROID DEVICE SETTINGS
 ANDROID PRIVACY & SECURITY GUIDE WESNET The Women s Services Network Smartphones store a lot of personal information, including email or social media accounts, reminders and notes, the number of steps
ANDROID PRIVACY & SECURITY GUIDE WESNET The Women s Services Network Smartphones store a lot of personal information, including email or social media accounts, reminders and notes, the number of steps
CLIENT ONBOARDING PLAN & SCRIPT
 CLIENT ONBOARDING PLAN & SCRIPT FIRST STEPS Receive Order form from Sales Representative. This may come in the form of a BPQ from client Ensure the client has an account in Reputation Management and in
CLIENT ONBOARDING PLAN & SCRIPT FIRST STEPS Receive Order form from Sales Representative. This may come in the form of a BPQ from client Ensure the client has an account in Reputation Management and in
CLIENT ONBOARDING PLAN & SCRIPT
 CLIENT ONBOARDING PLAN & SCRIPT FIRST STEPS Receive Order form from Sales Representative. This may come in the form of a BPQ from client Ensure the client has an account in Reputation Management and in
CLIENT ONBOARDING PLAN & SCRIPT FIRST STEPS Receive Order form from Sales Representative. This may come in the form of a BPQ from client Ensure the client has an account in Reputation Management and in
AOL keyword: UPGRADE HELP = This keyword will give you much information about how to install or upgrade to a higher version of AOL.
 Helpful Keywords AOL keyword: SHOW ME = This keyword gives you online tutorial or demonstrations about how a particular feature of AOL works e.g. inserting pictures through email, using Mail Art, Buddy
Helpful Keywords AOL keyword: SHOW ME = This keyword gives you online tutorial or demonstrations about how a particular feature of AOL works e.g. inserting pictures through email, using Mail Art, Buddy
The Table Privacy Policy Last revised on August 22, 2012
 The Table Privacy Policy Last revised on August 22, 2012 The Table, an online venue through which your organization and its members/employees can connect to better fulfill its mission respects and is committed
The Table Privacy Policy Last revised on August 22, 2012 The Table, an online venue through which your organization and its members/employees can connect to better fulfill its mission respects and is committed
A SIMPLE STEP-BY-STEP GUIDE FOR COMPUTER BEGINNERS
 A SIMPLE STEP-BY-STEP GUIDE FOR COMPUTER BEGINNERS EXPLORING THE INTERNET through HOBBIES AND INTERESTS. LEARN HOW TO KEEP IN TOUCH WITH FRIENDS AND FAMILY USING THE INTERNET In these busy times it s easy
A SIMPLE STEP-BY-STEP GUIDE FOR COMPUTER BEGINNERS EXPLORING THE INTERNET through HOBBIES AND INTERESTS. LEARN HOW TO KEEP IN TOUCH WITH FRIENDS AND FAMILY USING THE INTERNET In these busy times it s easy
Session Booklet Social Media & Facebook
 Session Booklet Social Media & Facebook Social networking refers to the use of online social networks such as Facebook to communicate with other people. A social network can include blogs and other ways
Session Booklet Social Media & Facebook Social networking refers to the use of online social networks such as Facebook to communicate with other people. A social network can include blogs and other ways
Thank you for purchasing your new Moochies Watch. We hope you, and more importantly your kids will love it as much as we did creating it.
 www.moochies.com Thank you for purchasing your new Moochies Watch. We hope you, and more importantly your kids will love it as much as we did creating it. This manual will take you through all the steps
www.moochies.com Thank you for purchasing your new Moochies Watch. We hope you, and more importantly your kids will love it as much as we did creating it. This manual will take you through all the steps
WHAT IS GOOGLE+ AND WHY SHOULD I USE IT?
 CHAPTER ONE WHAT IS GOOGLE+ AND WHY SHOULD I USE IT? In this chapter: + Discovering Why Google+ Is So Great + What Is the Difference between Google+ and Other Social Networks? + Does It Cost Money to Use
CHAPTER ONE WHAT IS GOOGLE+ AND WHY SHOULD I USE IT? In this chapter: + Discovering Why Google+ Is So Great + What Is the Difference between Google+ and Other Social Networks? + Does It Cost Money to Use
Prayerful Living Singles User s Manual
 Prayerful Living Singles User s Manual Rev. 7/30/15 1 Contents Welcome... 2 Join for free! (Register)... 2 Setting up your profile... 3 Click on Home... 5 Adding Pics... 5 Editing your profile... 6 Understanding
Prayerful Living Singles User s Manual Rev. 7/30/15 1 Contents Welcome... 2 Join for free! (Register)... 2 Setting up your profile... 3 Click on Home... 5 Adding Pics... 5 Editing your profile... 6 Understanding
Facebook Basics. Agenda:
 Basics Agenda: 1. Introduction 2. The evolution of Facebook 3. Your profile 4. Finding friends 5. Saving and sharing 6. Chat and messages 7. Facebook privacy 8. Practice, Questions, Evaluation In order
Basics Agenda: 1. Introduction 2. The evolution of Facebook 3. Your profile 4. Finding friends 5. Saving and sharing 6. Chat and messages 7. Facebook privacy 8. Practice, Questions, Evaluation In order
Social Media. Best practice template and general guidance leaflet
 Social Media Best practice template and general guidance leaflet This leaflet is produced by members of and on behalf of the Marketing, PR and Communications Committee Rotary District 1220, United Kingdom.
Social Media Best practice template and general guidance leaflet This leaflet is produced by members of and on behalf of the Marketing, PR and Communications Committee Rotary District 1220, United Kingdom.
Online Dangers. According to the National Center for Missing and Exploited Children.
 Online Dangers One in five youths say they have received a sexual approach or solicitation. One in 33 had received an aggressive sexual solicitation. One in four had unwanted exposure to sexually explicit
Online Dangers One in five youths say they have received a sexual approach or solicitation. One in 33 had received an aggressive sexual solicitation. One in four had unwanted exposure to sexually explicit
It is my great pleasure to inform that you have won the latest model of Ferrari Car and 4 Bed Room Villa in Palm Jumeirah for attending this Seminar
 You Won!!! It is my great pleasure to inform that you have won the latest model of Ferrari Car and 4 Bed Room Villa in Palm Jumeirah for attending this Seminar To Process and deliver your Car and Villa
You Won!!! It is my great pleasure to inform that you have won the latest model of Ferrari Car and 4 Bed Room Villa in Palm Jumeirah for attending this Seminar To Process and deliver your Car and Villa
NOTE: Facebook frequently changes how privacy and access settings work. What is described in this document is valid as of Aug
 Facebook (Facebook) FeaturesOverview This table shows you Facebook features and how they work. It s not formatted in the most user-friendly manner. I will update this file eventually with one that is.
Facebook (Facebook) FeaturesOverview This table shows you Facebook features and how they work. It s not formatted in the most user-friendly manner. I will update this file eventually with one that is.
What is Facebook? By
 What is Facebook? By www.digitalunite.com Facebook is probably the best known of the social networking sites. Created in 2004 by Mark Zuckerberg and his friends, originally as a way for students at Harvard
What is Facebook? By www.digitalunite.com Facebook is probably the best known of the social networking sites. Created in 2004 by Mark Zuckerberg and his friends, originally as a way for students at Harvard
Family Technology Boundaries:
 General questions to answer Family Technology Boundaries: How much time per day/week will various technologies be allowed? Can social media be accessed from all devices? What should children do if they
General questions to answer Family Technology Boundaries: How much time per day/week will various technologies be allowed? Can social media be accessed from all devices? What should children do if they
Cyber Safety Awareness in Schools. A Delhi Police Initiative
 Cyber Safety Awareness in Schools A Delhi Police Initiative 1 INTRODUCTION Concerns: You all are very inquisitive; The Internet offers a world of opportunities to you; But it is also full of risks: Inappropriate
Cyber Safety Awareness in Schools A Delhi Police Initiative 1 INTRODUCTION Concerns: You all are very inquisitive; The Internet offers a world of opportunities to you; But it is also full of risks: Inappropriate
Why isn t your chapter on Facebook?
 Why isn t your chapter on Facebook? Last Updated February 2011 Why Facebook? Interact with other Women of Today members Recruit members for your chapter Connect with younger generation Facebook is the
Why isn t your chapter on Facebook? Last Updated February 2011 Why Facebook? Interact with other Women of Today members Recruit members for your chapter Connect with younger generation Facebook is the
Student E-Safety Induction
 Central College Nottingham Student E-Safety Induction Academic Year 2015-16 Training & Learning Technologies September 2015 E-Safety It is important to the College that all students know how to stay safe
Central College Nottingham Student E-Safety Induction Academic Year 2015-16 Training & Learning Technologies September 2015 E-Safety It is important to the College that all students know how to stay safe
INTRODUCTION TO SOCIAL MEDIA Part 1
 TECH SAVVY SENIORS The NSW Tech Savvy Seniors program is a key initiative of the NSW Ageing Strategy and the Telstra Digital Literacy Strategy. Victorian Tech Savvy Seniors is a Seniors Card Age Friendly
TECH SAVVY SENIORS The NSW Tech Savvy Seniors program is a key initiative of the NSW Ageing Strategy and the Telstra Digital Literacy Strategy. Victorian Tech Savvy Seniors is a Seniors Card Age Friendly
Unit 9 Tech savvy? Tech support. 1 I have no idea why... Lesson A. A Unscramble the questions. Do you know which battery I should buy?
 Unit 9 Tech savvy? Lesson A Tech support 1 I have no idea why... A Unscramble the questions. 1. which battery / Do you know / should / buy / I? Do you know which battery I should buy? 2. they / where /
Unit 9 Tech savvy? Lesson A Tech support 1 I have no idea why... A Unscramble the questions. 1. which battery / Do you know / should / buy / I? Do you know which battery I should buy? 2. they / where /
GOOGLE APPS. GETTING STARTED Page 02 Prerequisites What You Will Learn. INTRODUCTION Page 03 What is Google? SETTING UP AN ACCOUNT Page 03 Gmail
 GOOGLE APPS GETTING STARTED Page 02 Prerequisites What You Will Learn INTRODUCTION Page 03 What is Google? SETTING UP AN ACCOUNT Page 03 Gmail DRIVE Page 07 Uploading Files to Google Drive Sharing/Unsharing
GOOGLE APPS GETTING STARTED Page 02 Prerequisites What You Will Learn INTRODUCTION Page 03 What is Google? SETTING UP AN ACCOUNT Page 03 Gmail DRIVE Page 07 Uploading Files to Google Drive Sharing/Unsharing
New user introduction to Attend
 1 New user introduction to Attend 1. Sign up to Attend... 2 2. First Steps Create a Course... 2 3. Sharing your course... 4 4. Viewing the course participants... 5 5. Create a new member of Staff... 6
1 New user introduction to Attend 1. Sign up to Attend... 2 2. First Steps Create a Course... 2 3. Sharing your course... 4 4. Viewing the course participants... 5 5. Create a new member of Staff... 6
HOW-TO GUIDE. Join or Login. About this Guide!
 HOW-TO GUIDE About this Guide In this guide, you will learn about each section of the online community to help you make the best use of all it has to offer. Here you will find information on: Join or Login
HOW-TO GUIDE About this Guide In this guide, you will learn about each section of the online community to help you make the best use of all it has to offer. Here you will find information on: Join or Login
Facebook Tutorial. An Introduction to Today s Most Popular Online Community
 Facebook Tutorial An Introduction to Today s Most Popular Online Community Introduction to Facebook Facebook is the most popular social network, in the U.S. and internationally. In October 2011, more than
Facebook Tutorial An Introduction to Today s Most Popular Online Community Introduction to Facebook Facebook is the most popular social network, in the U.S. and internationally. In October 2011, more than
Welcome to the world of .
 Welcome to the world of e-mail. E-mail, short for electronic mail, allows computer users to easily send messages back and forth between acquaintances around the world. There are a variety of ways to do
Welcome to the world of e-mail. E-mail, short for electronic mail, allows computer users to easily send messages back and forth between acquaintances around the world. There are a variety of ways to do
Circle Link 1 "Know Before You Go" Web Literacy Tips:
 5 th Grade Scavenger Hunt Content Circle Link 1 http://pbskids.org/privacy/literacytips.html "Know Before You Go" Web Literacy Tips: You know not to talk to strangers on the street but what about on the
5 th Grade Scavenger Hunt Content Circle Link 1 http://pbskids.org/privacy/literacytips.html "Know Before You Go" Web Literacy Tips: You know not to talk to strangers on the street but what about on the
Edmodo for Teachers Guide (Taken directly from Edmodo s site.)
 Edmodo for Teachers Guide (Taken directly from Edmodo s site.) Table of Contents: 1. Teacher Sign Up 2. Create a Group 3. Manage Your Groups 4. Small Group 5. Co-Teaching 6. Student Sign up 7. Post a Message
Edmodo for Teachers Guide (Taken directly from Edmodo s site.) Table of Contents: 1. Teacher Sign Up 2. Create a Group 3. Manage Your Groups 4. Small Group 5. Co-Teaching 6. Student Sign up 7. Post a Message
(10/17) PATIENT GUIDE
 (10/17) PATIENT GUIDE Welcome to Parkview MyChart! mychart.parkview.com Welcome to your one story of care. As a patient of Parkview, you now have access to your health information from the convenience
(10/17) PATIENT GUIDE Welcome to Parkview MyChart! mychart.parkview.com Welcome to your one story of care. As a patient of Parkview, you now have access to your health information from the convenience
KIK s GUIDE FOR LAW ENFORCEMENT
 Thanks for checking out our law enforcement guide. We take the safety of our users very seriously, and we hope this guide will be a useful tool for you. It includes information about our app; the features
Thanks for checking out our law enforcement guide. We take the safety of our users very seriously, and we hope this guide will be a useful tool for you. It includes information about our app; the features
Welcome to Facebook. Presented by Suzi Huisman
 Welcome to Facebook Presented by Suzi Huisman PRESENTATION GUIDELINES No cell phones, please turn the sound off. Questions at the end, but at the presenter s discretion. See hhiccbb.org for link to slides
Welcome to Facebook Presented by Suzi Huisman PRESENTATION GUIDELINES No cell phones, please turn the sound off. Questions at the end, but at the presenter s discretion. See hhiccbb.org for link to slides
The purchaser of the ebook is licensed to copy ebook for use with immediate family members only.
 Copyright 2017 Leah Nieman www.leahnieman.com All rights reserved. No part of this publication may be reproduced, stored in a retrieval system or transmitted in any form by any means, electronic, mechanical,
Copyright 2017 Leah Nieman www.leahnieman.com All rights reserved. No part of this publication may be reproduced, stored in a retrieval system or transmitted in any form by any means, electronic, mechanical,
Common iphone problems, tips and tricks
 Common iphone problems, tips and tricks F. M. Spowart Upd April 2018 Page 2 of 9 Randomly losing contacts; iphone does this for some strange reason. The reason why numbers disappear unlike other phones,
Common iphone problems, tips and tricks F. M. Spowart Upd April 2018 Page 2 of 9 Randomly losing contacts; iphone does this for some strange reason. The reason why numbers disappear unlike other phones,
Configuring Twitter for a More Secure Social Networking Experience
 CPF 00006-18-CID361-9H 8 November 2018 Configuring Twitter for a More Secure Social Networking Experience Basic Notes About Social Media The internet s social media ecosystem is vast. To some people, social
CPF 00006-18-CID361-9H 8 November 2018 Configuring Twitter for a More Secure Social Networking Experience Basic Notes About Social Media The internet s social media ecosystem is vast. To some people, social
Windows users range in experience from people
 Part I Getting Started, Windows users range in experience from people who are just getting started with their first PC to folks with years of Windows experience under their belts. Part I attempts to address
Part I Getting Started, Windows users range in experience from people who are just getting started with their first PC to folks with years of Windows experience under their belts. Part I attempts to address
FAQs. A guide for school app administrators
 FAQs A guide for school app administrators Introduction myschoolapp is a simple and cost-effective way to engage with today s mobile parents and carers who run their lives from their phones. It helps you
FAQs A guide for school app administrators Introduction myschoolapp is a simple and cost-effective way to engage with today s mobile parents and carers who run their lives from their phones. It helps you
Getting to know your ipad exploring the settings, App store, Mail
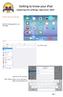 Getting to know your ipad exploring the settings, App store, Mail Exploring the settings Open the settings app from your homepage Wi-Fi Turn Wi-Fi on/off Add new Wi-Fi Connection Enter Network Name, any
Getting to know your ipad exploring the settings, App store, Mail Exploring the settings Open the settings app from your homepage Wi-Fi Turn Wi-Fi on/off Add new Wi-Fi Connection Enter Network Name, any
2013 edition (version 1.1)
 2013 edition (version 1.1) Contents 1 Introduction... 3 2 Signing in to your Office 365 account... 3 2.1 Acceptable Use Policy and Terms of Use... 4 3 Setting your profile and options... 4 3.1 Settings:
2013 edition (version 1.1) Contents 1 Introduction... 3 2 Signing in to your Office 365 account... 3 2.1 Acceptable Use Policy and Terms of Use... 4 3 Setting your profile and options... 4 3.1 Settings:
McAfee Family Protection The Easiest, Most Complete Way to Keep Your Children Safe Online
 The Easiest, Most Complete Way to Keep Your Children Safe Online 1 Quick Start Easy Installation STEP 1: First, ensure that your computer meets or exceeds the minimum systems requirements listed below.
The Easiest, Most Complete Way to Keep Your Children Safe Online 1 Quick Start Easy Installation STEP 1: First, ensure that your computer meets or exceeds the minimum systems requirements listed below.
PUPIL ICT ACCEPTABLE USE POLICY
 PUPIL ICT ACCEPTABLE USE POLICY Document control This document has been approved for operation within: All Trust Schools Date of last review August 2018 Date of next review August 2020 Review period Status
PUPIL ICT ACCEPTABLE USE POLICY Document control This document has been approved for operation within: All Trust Schools Date of last review August 2018 Date of next review August 2020 Review period Status
Norton Online Reputation Report: Why Millennials should manage their online footprint
 Norton Online Reputation Report: Why Millennials should manage their online footprint UK May 2016 Methodology A quantitative survey was conducted online among 1,000 mobile users aged 18-34 years who own
Norton Online Reputation Report: Why Millennials should manage their online footprint UK May 2016 Methodology A quantitative survey was conducted online among 1,000 mobile users aged 18-34 years who own
The ICT4me Curriculum
 The ICT4me Curriculum About ICT4me ICT4me is an after school and summer curriculum for middle school youth to develop ICT fluency, interest in mathematics, and knowledge of information, communication,
The ICT4me Curriculum About ICT4me ICT4me is an after school and summer curriculum for middle school youth to develop ICT fluency, interest in mathematics, and knowledge of information, communication,
The ICT4me Curriculum
 The ICT4me Curriculum About ICT4me ICT4me is an after school and summer curriculum for middle school youth to develop ICT fluency, interest in mathematics, and knowledge of information, communication,
The ICT4me Curriculum About ICT4me ICT4me is an after school and summer curriculum for middle school youth to develop ICT fluency, interest in mathematics, and knowledge of information, communication,
When representing Girl Scouts on social media channels make safety a priority.
 Communicating through Social Media Communications Liaisons are encouraged to share information with their volunteers via a local area website or other social media platform. The purpose is to enhance the
Communicating through Social Media Communications Liaisons are encouraged to share information with their volunteers via a local area website or other social media platform. The purpose is to enhance the
Gaggle 101 User Guide
 Gaggle 101 User Guide Home Tab The Home tab is the first page displayed upon login. Here you will see customized windows or widgets. Once set, the widgets can be accessed directly by clicking on them from
Gaggle 101 User Guide Home Tab The Home tab is the first page displayed upon login. Here you will see customized windows or widgets. Once set, the widgets can be accessed directly by clicking on them from
Key questions to ask before commissioning any web designer to build your website.
 Key questions to ask before commissioning any web designer to build your website. KEY QUESTIONS TO ASK Before commissioning a web designer to build your website. As both an entrepreneur and business owner,
Key questions to ask before commissioning any web designer to build your website. KEY QUESTIONS TO ASK Before commissioning a web designer to build your website. As both an entrepreneur and business owner,
INTRODUCTION TO CLOUD STORAGE
 INTRODUCTION TO CLOUD STORAGE GETTING STARTED PAGE 02 Class Overview What You Will Learn WHAT IS THE CLOUD? PAGE 03 Basic Vocabulary Advantages of the Cloud Disadvantages of the Cloud CLOUD STORAGE SERVICES
INTRODUCTION TO CLOUD STORAGE GETTING STARTED PAGE 02 Class Overview What You Will Learn WHAT IS THE CLOUD? PAGE 03 Basic Vocabulary Advantages of the Cloud Disadvantages of the Cloud CLOUD STORAGE SERVICES
My Digital Footprint. A guide to digital footprint awareness and management
 My Digital Footprint A guide to digital footprint awareness and management 2017 Crown copyright 2017 You may re-use this information (excluding logos) free of charge in any format or medium, under the
My Digital Footprint A guide to digital footprint awareness and management 2017 Crown copyright 2017 You may re-use this information (excluding logos) free of charge in any format or medium, under the
DCSZ Student AUP Policy
 Dulwich College Suzhou DCSZ Student AUP Policy This Policy is underpinned by our School Guiding Statement (No.2) The College provides a safe, secure and stimulating environment Policy Code G1.1.2 Effective
Dulwich College Suzhou DCSZ Student AUP Policy This Policy is underpinned by our School Guiding Statement (No.2) The College provides a safe, secure and stimulating environment Policy Code G1.1.2 Effective
So, you re child wants to sign up for Myspace...
 So, you re child wants to sign up for Myspace... Social networking is a brilliant concept that has sadly been tainted by several nefarious individuals. The term simply means a website that allows its users
So, you re child wants to sign up for Myspace... Social networking is a brilliant concept that has sadly been tainted by several nefarious individuals. The term simply means a website that allows its users
Chromebooks boot in seconds, and resume instantly. When you turn on a Chromebook and sign in, you can get online fast.
 chromebook meet chromebook What is a chromebook? Chromebooks are... A new type of computer that is fast, simple and secure. Built for the web best of Google and access to thousands of online web apps.
chromebook meet chromebook What is a chromebook? Chromebooks are... A new type of computer that is fast, simple and secure. Built for the web best of Google and access to thousands of online web apps.
Introduction to
 Introduction to Email gcflearnfree.org/print/email101/introduction-to-email Introduction Do you ever feel like the only person who doesn't use email? You don't have to feel left out. If you're just getting
Introduction to Email gcflearnfree.org/print/email101/introduction-to-email Introduction Do you ever feel like the only person who doesn't use email? You don't have to feel left out. If you're just getting
Synthesis Paper CEP 416 Erica Lewis. variations of innovations within technology. Each technology has both strengths and
 Synthesis Paper CEP 416 Erica Lewis Today technology is very important to our everyday lives. Yet, there are many variations of innovations within technology. Each technology has both strengths and weaknesses.
Synthesis Paper CEP 416 Erica Lewis Today technology is very important to our everyday lives. Yet, there are many variations of innovations within technology. Each technology has both strengths and weaknesses.
Twitter Basics at the Deerfield Public Library
 Twitter Basics at the Deerfield Public Library Class Outline: 1) What is Twitter? 2) Setting up an account and profile 3) Terms you should know & examples 4) How do I decide what to write? 5) Q & A Expected
Twitter Basics at the Deerfield Public Library Class Outline: 1) What is Twitter? 2) Setting up an account and profile 3) Terms you should know & examples 4) How do I decide what to write? 5) Q & A Expected
Easy Video Blogging and Marketing on Youtube! by Leslie Truex
 Easy Video Blogging and Marketing on Youtube! by Leslie Truex NOTICE: You Do NOT Have the Right to Reprint or Resell this Report! You Also MAY NOT Give Away, Sell or Share the Content Herein If you obtained
Easy Video Blogging and Marketing on Youtube! by Leslie Truex NOTICE: You Do NOT Have the Right to Reprint or Resell this Report! You Also MAY NOT Give Away, Sell or Share the Content Herein If you obtained
Website/Blog Admin Using WordPress
 Website/Blog Admin Using WordPress Table of Contents How to login... 2 How to get support... 2 About the WordPress dashboard... 3 WordPress pages vs posts... 3 How to add a new blog post... 5 How to edit
Website/Blog Admin Using WordPress Table of Contents How to login... 2 How to get support... 2 About the WordPress dashboard... 3 WordPress pages vs posts... 3 How to add a new blog post... 5 How to edit
It starts like this...
 Need help with your phone? No problem. Just get in touch with the store or website you bought it from. If you need a hand with your mobile service, one of our team will be happy to help. 789 on your mobile
Need help with your phone? No problem. Just get in touch with the store or website you bought it from. If you need a hand with your mobile service, one of our team will be happy to help. 789 on your mobile
 Slide 1 Hello, I m Jason Borgen, Program Coordinator for the TICAL project and a Google Certified Teacher. This Quick Take will show you a variety of ways to search Google to maximize your research and
Slide 1 Hello, I m Jason Borgen, Program Coordinator for the TICAL project and a Google Certified Teacher. This Quick Take will show you a variety of ways to search Google to maximize your research and
Password & Tutorials Packet
 & Tutorials Packet Print, staple, and use this & Tutorials Packet Sign up for Secure Backup Service: visit rowleyservices.com for a free trial & setup info Follow attached: Check iphone Camera Settings
& Tutorials Packet Print, staple, and use this & Tutorials Packet Sign up for Secure Backup Service: visit rowleyservices.com for a free trial & setup info Follow attached: Check iphone Camera Settings
LEARNER I.T. ACCEPTABLE USE POLICY. Learner I.T. Acceptable Use Policy [Type text] Updated November Authorised by ILT Board/Executive.
![LEARNER I.T. ACCEPTABLE USE POLICY. Learner I.T. Acceptable Use Policy [Type text] Updated November Authorised by ILT Board/Executive. LEARNER I.T. ACCEPTABLE USE POLICY. Learner I.T. Acceptable Use Policy [Type text] Updated November Authorised by ILT Board/Executive.](/thumbs/87/95594334.jpg) LEARNER I.T. ACCEPTABLE USE POLICY Learner I.T. Acceptable Use Policy 2012-13 [Type text] Updated November 2011. Authorised by ILT Board/Executive. Learner I.T. Acceptable Use Policy Table of Contents
LEARNER I.T. ACCEPTABLE USE POLICY Learner I.T. Acceptable Use Policy 2012-13 [Type text] Updated November 2011. Authorised by ILT Board/Executive. Learner I.T. Acceptable Use Policy Table of Contents
Glossary
 Glossary www.cybersmart.gov.au/cyberquoll CyberQuoll Internet Safety Education for Primary School Students, Parents Guide Website: www.cybersmart.gov.au/cyberquoll Source: Commonwealth of Australia 2009
Glossary www.cybersmart.gov.au/cyberquoll CyberQuoll Internet Safety Education for Primary School Students, Parents Guide Website: www.cybersmart.gov.au/cyberquoll Source: Commonwealth of Australia 2009
Troubleshooting and Tips
 LESSON 10 Troubleshooting and Tips Flickr is a large site, and like any large site, tons of questions come up. This chapter handles many such questions by digging into the Flickr back story for the answer
LESSON 10 Troubleshooting and Tips Flickr is a large site, and like any large site, tons of questions come up. This chapter handles many such questions by digging into the Flickr back story for the answer
Definitions Know What I Mean?
 Definitions Know What I Mean? The list below contains words you will read about in this resource and that your children probably use regularly as they are a normal part of their school world (if not their
Definitions Know What I Mean? The list below contains words you will read about in this resource and that your children probably use regularly as they are a normal part of their school world (if not their
Social Media. The infinite abilities of a smart phone
 Social Media The infinite abilities of a smart phone It s all about the Likes, Shares and Stats Social Media is driven by users desire for Likes - Shares - Retweets - Followers to the point that users
Social Media The infinite abilities of a smart phone It s all about the Likes, Shares and Stats Social Media is driven by users desire for Likes - Shares - Retweets - Followers to the point that users
Beginners Guide to Google+ and Google+ Pages
 Beginners Guide to Google+ and Google+ Pages 1 P a g e C o p y r i g h t 2 0 1 1 S E O I n c. (760) 929-0039 Table of Contents INTRODUCTION... 3 WHAT IS THE GOOGLE+ PROJECT?... 3 WHAT IS A GOOGLE+ PAGE...
Beginners Guide to Google+ and Google+ Pages 1 P a g e C o p y r i g h t 2 0 1 1 S E O I n c. (760) 929-0039 Table of Contents INTRODUCTION... 3 WHAT IS THE GOOGLE+ PROJECT?... 3 WHAT IS A GOOGLE+ PAGE...
Session Booklet Facebook part 2
 Session Booklet Facebook part 2 Facebook, like any online or offline meeting place, carries with it some risks. Remember that you should apply the same common sense and safety rules as you do when you
Session Booklet Facebook part 2 Facebook, like any online or offline meeting place, carries with it some risks. Remember that you should apply the same common sense and safety rules as you do when you
Comping Guide. Rafflecopter & Blogs
 Comping Guide Blogs 2 Following blogs 2 Commenting on blogs 2 Prize promotions on blogs 4 Notifying winners 4 How to find Blog comps 4 Rafflecopter 5 Types of Rafflecopter giveaway 6 An example Rafflecopter
Comping Guide Blogs 2 Following blogs 2 Commenting on blogs 2 Prize promotions on blogs 4 Notifying winners 4 How to find Blog comps 4 Rafflecopter 5 Types of Rafflecopter giveaway 6 An example Rafflecopter
Online Communication. Chat Rooms Instant Messaging Blogging Social Media
 Online Communication E-mail Chat Rooms Instant Messaging Blogging Social Media Advantages: Reduces cost of postage Fast and convenient Eliminates phone charges Disadvantages: May be difficult to understand
Online Communication E-mail Chat Rooms Instant Messaging Blogging Social Media Advantages: Reduces cost of postage Fast and convenient Eliminates phone charges Disadvantages: May be difficult to understand
Having said this, there are some workarounds you can use to integrate video into your course.
 HOW TO SESSION : Options for creating & sharing video Overview Video is everywhere. We watch it on YouTube and Netflix. It s how we get our news, communicate with friends and family in other cities, and
HOW TO SESSION : Options for creating & sharing video Overview Video is everywhere. We watch it on YouTube and Netflix. It s how we get our news, communicate with friends and family in other cities, and
Taskbar: Working with Several Windows at Once
 Taskbar: Working with Several Windows at Once Your Best Friend at the Bottom of the Screen How to Make the Most of Your Taskbar The taskbar is the wide bar that stretches across the bottom of your screen,
Taskbar: Working with Several Windows at Once Your Best Friend at the Bottom of the Screen How to Make the Most of Your Taskbar The taskbar is the wide bar that stretches across the bottom of your screen,
Online Communication. Chat Rooms Instant Messaging Blogging Social Media
 Online Communication E-mail Chat Rooms Instant Messaging Blogging Social Media { Advantages: { Reduces cost of postage Fast and convenient Need an email address to sign up for other online accounts. Eliminates
Online Communication E-mail Chat Rooms Instant Messaging Blogging Social Media { Advantages: { Reduces cost of postage Fast and convenient Need an email address to sign up for other online accounts. Eliminates
LEARN HOW TO USE FACEBOOK
 LEARN HOW TO USE FACEBOOK BOONE COUNTY PUBLIC LIBRARY www.bcpl.org Contents What is Facebook?...1 Sign up...1-2 Add a status update...2-3 Edit a post...3 Like (Reactions), Comment or Share...3 Share your
LEARN HOW TO USE FACEBOOK BOONE COUNTY PUBLIC LIBRARY www.bcpl.org Contents What is Facebook?...1 Sign up...1-2 Add a status update...2-3 Edit a post...3 Like (Reactions), Comment or Share...3 Share your
TITLE SOCIAL MEDIA AND COLLABORATION POLICY
 DATE 9/20/2010 TITLE 408.01 SOCIAL MEDIA AND COLLABORATION POLICY ORG. AGENCY Department of Communications Approved AFT As more and more citizens in our community make the shift towards, or include the
DATE 9/20/2010 TITLE 408.01 SOCIAL MEDIA AND COLLABORATION POLICY ORG. AGENCY Department of Communications Approved AFT As more and more citizens in our community make the shift towards, or include the
GUIDE TO KEEPING YOUR SOCIAL MEDIA ACCOUNTS SECURE
 GUIDE TO KEEPING YOUR SOCIAL MEDIA ACCOUNTS SECURE TABLE OF CONTENTS PROTECTIVE MEASURES... 2 PREPARATION CHECKLIST... 2 IF YOU SUSPECT YOUR ACCOUNT IS COMPROMISED, THE FOLLOWING ACTIONS ARE ADVISED:...
GUIDE TO KEEPING YOUR SOCIAL MEDIA ACCOUNTS SECURE TABLE OF CONTENTS PROTECTIVE MEASURES... 2 PREPARATION CHECKLIST... 2 IF YOU SUSPECT YOUR ACCOUNT IS COMPROMISED, THE FOLLOWING ACTIONS ARE ADVISED:...
Thinkuknow Parents and Carers Guide to Periscope. Periscope
 Thinkuknow Parents and Carers Guide to Periscope Periscope Periscope is a live streaming app, developed by the creators of Twitter as a way to share live, realtime events and news stories from around the
Thinkuknow Parents and Carers Guide to Periscope Periscope Periscope is a live streaming app, developed by the creators of Twitter as a way to share live, realtime events and news stories from around the
Strong signs your website needs a professional redesign
 Strong signs your website needs a professional redesign Think - when was the last time that your business website was updated? Better yet, when was the last time you looked at your website? When the Internet
Strong signs your website needs a professional redesign Think - when was the last time that your business website was updated? Better yet, when was the last time you looked at your website? When the Internet
BT CLOUD PHONE. USER GUIDE FOR MY EXTENSION.
 BT CLOUD PHONE. USER GUIDE FOR MY EXTENSION. WHAT S IN THIS GUIDE. 1. Welcome to BT Cloud Phone. 3 2. Express setup. 4 3. Accessing the BT Cloud Phone Portal. 5 4. My Extension Dashboard. 6 4.1 Overview:
BT CLOUD PHONE. USER GUIDE FOR MY EXTENSION. WHAT S IN THIS GUIDE. 1. Welcome to BT Cloud Phone. 3 2. Express setup. 4 3. Accessing the BT Cloud Phone Portal. 5 4. My Extension Dashboard. 6 4.1 Overview:
