Twi$er s Trending Topics exploita4on pa$erns
|
|
|
- Lucas Rice
- 5 years ago
- Views:
Transcription
1 Twi$er s Trending Topics exploita4on pa$erns Despoina Antonakaki Paraskevi Fragopoulou, So6ris Ioannidis isocial Mee6ng, February 4-5th, 2014
2 Online Users World popula6ons percentage of online users: 39% of 7.1 billion 58% are in any SN, 56% in Facebook, 14% in LinkedIn, 11% in Twi$er Alexa's web: TwiSer one of the ten- most- visited websites worldwide by traffic analysis
3 Twi$er in numbers Fast growing OSN with 650 million registered users 232 million monthly ac4ve users - daily tweets: March million, now 500 million tweets per day in the world TwiSer queries per day: 2.1 billion In our experiments we apply to US data (1/3 of worldwide traffic) Spam: 8% of 25 million URLs [Chris Grier, CCS2010] 2011: 3.5 billion malicious tweets
4 The problem of Spam in Twi$er TwiSer is ideal place for spammers: Public content Easy crea6on of network (without approval of users) Missing filtering mechanism Twi$er Features used by spammers: Trend hijacking: Ride on success of trends Trend seing: Create trending topic Men6ons used to personalize Tweet hijacking: RT prepending the tweet with spam URLs Retweets: RT of blacklisted URLs [Chris Grier, CCS2010]
5 Feature frequency in spam by blacklists 8% of 25 million URLs posted point to phishing, malware, and scams listed on popular blacklists. Blacklists lag behind Twi$er: most spam messages appear 4 20 days before the URLs embedded in messages become flagged [Chris Grier, CCS2010] hence, we are not coun4ng (en4rely) on blacklists! Twi$er - A marketplace for spammers Twi$er account sellers: accounts composing & sending tweets, Paid Owner Sponsored Tweets: pay users to host ads in their tweets Spam affiliate programs: bots that create accounts and post spam links (exploi6ng trends). [Thomas SIGCOMM 11 ] 5% Google hashtags # 93% retweets 2% This work deals with Spam in Twi$er
6 Background work General about Spam: Malicious URL detec4on in Design and Evalua.on of a Real- Time URL Spam Filtering Service [Security and Privacy 11] Measuring the conversion rate of spam in Spamaly.cs [CACMSpam09] Distribu6on infiltra4on for measuring spam campaigns from the inside in On the Spam Campaign Trail [Usenix 2008] Privacy in SNs: Building working prototype of a variant of TwiSer protec6ng tweet contents, hash tags, interests in Hummingbird: Privacy at the.me of TwiGer [Security and Privacy 12] Inferring private from public asributes in SNs in You are what you like informa.on leakage through users' interest [NDSS 12] Decoupling the retrieval of user- specific content from the loading of a social plugin in Privacy- Preserving Social Plugins [Usenix 12]
7 Background work Spam in Twi$er: Reconstruct spam into campaigns for clustering: six features used by spammers & provide online spam filtering in OSN server in Towards Online Spam Filtering in Social Networks [NDSS 12] Detec6ng if account is automated from tweet 6mestamp in Detec.ng and Analyzing Automated Ac4vity on TwiGer [PAM 11] A complete analysis of spam in twiser: analyzing compromised accounts, analyzing features spammer use, group spam to campaigns, iden4fy trends that dis4nguish phishing malware and test blacklists Detec.ng and Analyzing Automated Ac.vity on TwiGer [CCS 2010] Iden4fy spam accounts, campaigns, iden6fy marketplace/spam affiliate programs in Suspended Accounts in Retrospect: An Analysis of TwiGer Spam [IMC 11]
8 A new approach Given that: spammers exploit trends We need to: inves6gate the features of: Spam tweets (#trends, #followers, ) Spam campaigns (graph structure) In order to: Understand spam Iden6fy spammers vs. legit
9 Our Dataset Top ten trending topics every ten minutes for 10 days Ten twiser accounts downloading in parallel In average: tweets / day Data from US USA trending topics In average: different users / day Use blacklists and heuris6cs to iden6fy spammers
10 Preprocessing of data For every user we download & save : o #tweets o #trends o #different trends o #number of tweets for each trend o #spam_urls (according to blacklists) o #legit_urls o #percentage of tweets with trends o #percentage of tweets with urls o #RTs (not yet included) o #User Mentions (not yet included) o #followings (not yet included) o #followers (not yet included)
11 Google heuris4c Spam URLs are hidden in a Google search results link sa=t&rct=j&q=&esrc=s&frm=1&source=web&cd=4&cad=rja &sqi=2&ved=0ceaqfjad&url=http%3a%2f %2Fwww.followmania.us %2F&ei=FveHUoDBHITdswa2q4HYCw&usg=AFQjCNG1f WSqWsWxdI2QCMSeu3WGXHEtaw&sig2=fEuJc66pEvdq 9vLp2XyGdg&bvm=bv ,d.Yms Fast identification Reliable Use as a golden standard spammers ( ~1%) Growing industry: Twitter follower markets 1-10 millions of victims 40$-200$ per victim
12 How does a get more followers campaign looks like? morefollowers.me Central nodes are the campaign links
13 Why not blacklists? SpamHaus o Many False Positives (i.e. instagram.com) Surbl not so strict filters o High specificity (Few False Positives) o Low sensitivity (Many False Negatives) Google Safe Browsing API o Only for phishing and malware o links lookup / 24hrs
14 According to these data what are the paserns that dis6nguish spammers?
15 CDF of unique & total trends If we sort spam users according to #UT, then 14% of them ( =500 out of users) have more than 5 trends. In total trends the distinction is not so clear as with unique trends The equivalent percentage for legit users is 0.06% (250 out of )
16 Plot of unique & total trends per user Users are sorted by the number of unique trends. Spammers have clearly more trends than legit users on blue line.
17 Classifica4on Legit users, Spam users 10-fold Cross Validation Method Logistic Regression True Positive Ratio (Spam identified as Spam) 55.1% 99.9% SVM 55.0% 99.8% Decision Trees Random Forest 59.2% 99.9% 59.3% 99.9% True Negative Ratio (Legit identified as Legit)
18 Decision Tree Visualization Complex and overfitted but.. the first rule is always interesting..! X[2] is #trends / #tweets
19 Plot: #Trends / #Tweets If we sort spam users according to trends/tweets, then 8% of them ( =300 out of users) have more than 4 trends. The equivalent percentage for legit users is < 0.06% (250 out of ) False negatives.. L
20 Discover spam campaigns Plot TLDs linked by top trend users: o For top trend users plot the TLDs of links contained in tweets o Manually check the TLDs o Blue nodes: usernames o Green nodes: TLDs o Labels on users: username/#unique trends of user o Labels on edges: number of times the user has sent a tweet with that TLD o Threshold = Minimum #unique_trends o Plot for different threshold values
21 For #trends>=6 Zoom in..
22 Για #trends>=6 Online Share trading site, when you click on links it forwards you to a follow app in twi$er.
23
24
25 High payout rates, good monthly income, fast & customized url shortener, and non- intrusive ads to my blogs. Also I've got a lot of visitors with AdF.ly as a publisher. Keep your awesome service going on! Earn fast easy money schemes: URL shrinking service that pays the users depending on the #clicks & Ponzi scheme!
26 Social media followers market Social media followers contests Social media followers market An Interna4onal Crowd funding PlaAorm to Raise Money
27 Monster MMORPG game online
28 Discussion Metrics like trends/tweets, unique_trends can dis6nguish more than half of spammers We shouldn t rely on blacklists to iden6fy spam Campaign plots show that there are more complex spammish techniques. The complete picture is not yet revealed..
29 Future work: Run for more days / weeks / months Assess more heuris6cs / blacklists Build simple classifica6on mechanisms What are the graph proper6es of spam campaigns?
30 Collaboration: Distributed Spam Filtering Adjust the procedure in a gossip algorithm: Trend and Tweet collec6on is already distributed among mul6ple accounts Store in MongoDB Run ensemble methods for classifica6on: o Adaboost o Random Forest Classifier Merge campaign graphs in order to iden6fy larger spam campaigns, get the complete picture
Think before RT: An Experimental Study of Abusing Twitter Trends
 Think before RT: An Experimental Study of Abusing Twitter Trends Despoina Antonakaki 1, Iasonas Polakis 2, Elias Athanasopoulos 1, Sotiris Ioannidis 1, and Paraskevi Fragopoulou 1 1 FORTH-ICS, Greece {despoina,elathan,sotiris,fragopou}@ics.forth.gr
Think before RT: An Experimental Study of Abusing Twitter Trends Despoina Antonakaki 1, Iasonas Polakis 2, Elias Athanasopoulos 1, Sotiris Ioannidis 1, and Paraskevi Fragopoulou 1 1 FORTH-ICS, Greece {despoina,elathan,sotiris,fragopou}@ics.forth.gr
Consequences of Compromise: Characterizing Account Hijacking on Twitter
 Consequences of Compromise: Characterizing Account Hijacking on Twitter Frank Li UC Berkeley With: Kurt Thomas (UCB Google), Chris Grier (UCB/ICSI Databricks), Vern Paxson (UCB/ICSI) Accounts on Social
Consequences of Compromise: Characterizing Account Hijacking on Twitter Frank Li UC Berkeley With: Kurt Thomas (UCB Google), Chris Grier (UCB/ICSI Databricks), Vern Paxson (UCB/ICSI) Accounts on Social
deseo: Combating Search-Result Poisoning Yu USF
 deseo: Combating Search-Result Poisoning Yu Jin @MSCS USF Your Google is not SAFE! SEO Poisoning - A new way to spread malware! Why choose SE? 22.4% of Google searches in the top 100 results > 50% for
deseo: Combating Search-Result Poisoning Yu Jin @MSCS USF Your Google is not SAFE! SEO Poisoning - A new way to spread malware! Why choose SE? 22.4% of Google searches in the top 100 results > 50% for
Discover (n.): This feature surfaces personalized content tailored to your interests.
 Glossary: General Terms @: The @ sign is used to call out usernames in Tweets: "Hello @twitter!" People will use your @username to mention you in Tweets, send you a message or link to your profile. @username:
Glossary: General Terms @: The @ sign is used to call out usernames in Tweets: "Hello @twitter!" People will use your @username to mention you in Tweets, send you a message or link to your profile. @username:
Introduction to Twitter
 Introduction to Twitter Objectives After completing this class you will be able to: Identify what Twitter is Create a Twitter Account Customize your Twitter profile and settings Follow other users on Twitter
Introduction to Twitter Objectives After completing this class you will be able to: Identify what Twitter is Create a Twitter Account Customize your Twitter profile and settings Follow other users on Twitter
Digital Marketing. Introduction of Marketing. Introductions
 Digital Marketing Introduction of Marketing Origin of Marketing Why Marketing is important? What is Marketing? Understanding Marketing Processes Pillars of marketing Marketing is Communication Mass Communication
Digital Marketing Introduction of Marketing Origin of Marketing Why Marketing is important? What is Marketing? Understanding Marketing Processes Pillars of marketing Marketing is Communication Mass Communication
AURA ACADEMY Training With Expertised Faculty Call us on for Free Demo
 AURA ACADEMY Training With Expertised Faculty Call us on 8121216332 for Free Demo DIGITAL MARKETING TRAINING Digital Marketing Basics Basics of Advertising What is Digital Media? Digital Media Vs. Traditional
AURA ACADEMY Training With Expertised Faculty Call us on 8121216332 for Free Demo DIGITAL MARKETING TRAINING Digital Marketing Basics Basics of Advertising What is Digital Media? Digital Media Vs. Traditional
Create an Account... 2 Setting up your account... 2 Send a Tweet... 4 Add Link... 4 Add Photo... 5 Delete a Tweet...
 Twitter is a social networking site allowing users to post thoughts and ideas in 140 characters or less. http://www.twitter.com Create an Account... 2 Setting up your account... 2 Send a Tweet... 4 Add
Twitter is a social networking site allowing users to post thoughts and ideas in 140 characters or less. http://www.twitter.com Create an Account... 2 Setting up your account... 2 Send a Tweet... 4 Add
Hey Guys, My name is Piyush Mathur. By Profession I am a Digital marketing consultant.
 BY PIYUSH MATHUR Hey Guys, My name is Piyush Mathur. By Profession I am a Digital marketing consultant. I work with many startups and large companies to develop intelligent and effective online strategies.
BY PIYUSH MATHUR Hey Guys, My name is Piyush Mathur. By Profession I am a Digital marketing consultant. I work with many startups and large companies to develop intelligent and effective online strategies.
CLOAK OF VISIBILITY : DETECTING WHEN MACHINES BROWSE A DIFFERENT WEB
 CLOAK OF VISIBILITY : DETECTING WHEN MACHINES BROWSE A DIFFERENT WEB CIS 601: Graduate Seminar Prof. S. S. Chung Presented By:- Amol Chaudhari CSU ID 2682329 AGENDA About Introduction Contributions Background
CLOAK OF VISIBILITY : DETECTING WHEN MACHINES BROWSE A DIFFERENT WEB CIS 601: Graduate Seminar Prof. S. S. Chung Presented By:- Amol Chaudhari CSU ID 2682329 AGENDA About Introduction Contributions Background
PhishEye: Live Monitoring of Sandboxed Phishing Kits. Xiao Han Nizar Kheir Davide Balzarotti
 PhishEye: Live Monitoring of Sandboxed Phishing Kits Xiao Han Nizar Kheir Davide Balzarotti Summary Motivation Sandboxed phishing kits Implementation Results [APWG Phishing Activity Trends Report 2 nd
PhishEye: Live Monitoring of Sandboxed Phishing Kits Xiao Han Nizar Kheir Davide Balzarotti Summary Motivation Sandboxed phishing kits Implementation Results [APWG Phishing Activity Trends Report 2 nd
Fighting Spam, Phishing and Malware With Recurrent Pattern Detection
 Fighting Spam, Phishing and Malware With Recurrent Pattern Detection White Paper September 2017 www.cyren.com 1 White Paper September 2017 Fighting Spam, Phishing and Malware With Recurrent Pattern Detection
Fighting Spam, Phishing and Malware With Recurrent Pattern Detection White Paper September 2017 www.cyren.com 1 White Paper September 2017 Fighting Spam, Phishing and Malware With Recurrent Pattern Detection
DIGITAL MARKETING AND SOCIAL MEDIA COMMUNICATION FOR THE NSS EPALE CY TEAM AND STAKEHOLDERS
 DIGITAL MARKETING AND SOCIAL MEDIA COMMUNICATION FOR THE NSS EPALE CY TEAM AND STAKEHOLDERS 6 και 7 Ιουνίου, 8:00 π.μ.-15:00 μ.μ. Παιδαγωγικό Ινστιτούτο Κύπρου, Αίθουσα Π206 THE SEMINAR WAS HELD DURING
DIGITAL MARKETING AND SOCIAL MEDIA COMMUNICATION FOR THE NSS EPALE CY TEAM AND STAKEHOLDERS 6 και 7 Ιουνίου, 8:00 π.μ.-15:00 μ.μ. Παιδαγωγικό Ινστιτούτο Κύπρου, Αίθουσα Π206 THE SEMINAR WAS HELD DURING
Social Media Tip and Tricks
 Social Media Tip and Tricks Hey 2016 CCP attendees! The Technology Council has put together social media tips and tricks to support your CCP process. Social media and other online tools can be great resources
Social Media Tip and Tricks Hey 2016 CCP attendees! The Technology Council has put together social media tips and tricks to support your CCP process. Social media and other online tools can be great resources
Advertising Network Affiliate Marketing Algorithm Analytics Auto responder autoresponder Backlinks Blog
 Advertising Network A group of websites where one advertiser controls all or a portion of the ads for all sites. A common example is the Google Search Network, which includes AOL, Amazon,Ask.com (formerly
Advertising Network A group of websites where one advertiser controls all or a portion of the ads for all sites. A common example is the Google Search Network, which includes AOL, Amazon,Ask.com (formerly
A Generic Statistical Approach for Spam Detection in Online Social Networks
 Final version of the accepted paper. Cite as: F. Ahmad and M. Abulaish, A Generic Statistical Approach for Spam Detection in Online Social Networks, Computer Communications, 36(10-11), Elsevier, pp. 1120-1129,
Final version of the accepted paper. Cite as: F. Ahmad and M. Abulaish, A Generic Statistical Approach for Spam Detection in Online Social Networks, Computer Communications, 36(10-11), Elsevier, pp. 1120-1129,
A Performance Evaluation of Lfun Algorithm on the Detection of Drifted Spam Tweets
 A Performance Evaluation of Lfun Algorithm on the Detection of Drifted Spam Tweets Varsha Palandulkar 1, Siddhesh Bhujbal 2, Aayesha Momin 3, Vandana Kirane 4, Raj Naybal 5 Professor, AISSMS Polytechnic
A Performance Evaluation of Lfun Algorithm on the Detection of Drifted Spam Tweets Varsha Palandulkar 1, Siddhesh Bhujbal 2, Aayesha Momin 3, Vandana Kirane 4, Raj Naybal 5 Professor, AISSMS Polytechnic
MEASURING AND FINGERPRINTING CLICK-SPAM IN AD NETWORKS
 MEASURING AND FINGERPRINTING CLICK-SPAM IN AD NETWORKS Vacha Dave *, Saikat Guha and Yin Zhang * * The University of Texas at Austin Microsoft Research India Internet Advertising Today 2 Online advertising
MEASURING AND FINGERPRINTING CLICK-SPAM IN AD NETWORKS Vacha Dave *, Saikat Guha and Yin Zhang * * The University of Texas at Austin Microsoft Research India Internet Advertising Today 2 Online advertising
SOCIAL MEDIA. Charles Murphy
 SOCIAL MEDIA Charles Murphy Social Media Overview 1. Introduction 2. Social Media Areas Blogging Bookmarking Deals Location-based Music Photo sharing Video 3. The Fab Four FaceBook Google+ Linked In Twitter
SOCIAL MEDIA Charles Murphy Social Media Overview 1. Introduction 2. Social Media Areas Blogging Bookmarking Deals Location-based Music Photo sharing Video 3. The Fab Four FaceBook Google+ Linked In Twitter
Setup... 3 Connect your accounts in GatorSocial... 4 Competitors...10 Topics Tab...12
 GATORSOCIAL Table of Contents Setup... 3 Connect your accounts in... 4 Competitors...10 Topics Tab...12 How to compose a message...16 Composing a new message in...17 Dispatched and Scheduled Posts...20
GATORSOCIAL Table of Contents Setup... 3 Connect your accounts in... 4 Competitors...10 Topics Tab...12 How to compose a message...16 Composing a new message in...17 Dispatched and Scheduled Posts...20
Social Networking for Business. Kathryn McCauley MidYork Library System
 Social Networking for Business Kathryn McCauley MidYork Library System WHERE SHOULD I START? 1. What kinds of content do you want to post? Lengthy stories Links Multimedia (video, pictures) Short updates
Social Networking for Business Kathryn McCauley MidYork Library System WHERE SHOULD I START? 1. What kinds of content do you want to post? Lengthy stories Links Multimedia (video, pictures) Short updates
How To Guide. ADENION GmbH Merkatorstraße Grevenbroich Germany Fon: Fax:
 How To Guide ADENION GmbH Merkatorstraße 2 41515 Grevenbroich Germany Fon: +49 2181 7569-140 Fax: +49 2181 7569-199 The! Complete Guide to Social Media Sharing The following social media sharing guide
How To Guide ADENION GmbH Merkatorstraße 2 41515 Grevenbroich Germany Fon: +49 2181 7569-140 Fax: +49 2181 7569-199 The! Complete Guide to Social Media Sharing The following social media sharing guide
Functionality, Challenges and Architecture of Social Networks
 Functionality, Challenges and Architecture of Social Networks INF 5370 Outline Social Network Services Functionality Business Model Current Architecture and Scalability Challenges Conclusion 1 Social Network
Functionality, Challenges and Architecture of Social Networks INF 5370 Outline Social Network Services Functionality Business Model Current Architecture and Scalability Challenges Conclusion 1 Social Network
The Ultimate Digital Marketing Glossary (A-Z) what does it all mean? A-Z of Digital Marketing Translation
 The Ultimate Digital Marketing Glossary (A-Z) what does it all mean? In our experience, we find we can get over-excited when talking to clients or family or friends and sometimes we forget that not everyone
The Ultimate Digital Marketing Glossary (A-Z) what does it all mean? In our experience, we find we can get over-excited when talking to clients or family or friends and sometimes we forget that not everyone
Characteriza*on of Blacklists and Tainted Network Traffic
 Characteriza*on of Blacklists and Tainted Network Traffic Jing Zhang 1, Ari Chivukula 1, Michael Bailey 1, Manish Karir 2, and Mingyan Liu 1 1 University of Michigan 2 Cyber Security Division, Department
Characteriza*on of Blacklists and Tainted Network Traffic Jing Zhang 1, Ari Chivukula 1, Michael Bailey 1, Manish Karir 2, and Mingyan Liu 1 1 University of Michigan 2 Cyber Security Division, Department
Digital Marketing Proposal
 Digital Marketing Proposal ---------------------------------------------------------------------------------------------------------------------------------------------- 1 P a g e We at Tronic Solutions
Digital Marketing Proposal ---------------------------------------------------------------------------------------------------------------------------------------------- 1 P a g e We at Tronic Solutions
#DGPConf18. Digital Growth Conference 18: What s New in Social? Liam Lally
 Digital Growth Conference 18: What s New in Social? Liam Lally General Updates General Updates Forget All Them.. What s New In Social March 2018 Edition Facebook Updates (There s a lot!) OCTOBER 2017 GIF
Digital Growth Conference 18: What s New in Social? Liam Lally General Updates General Updates Forget All Them.. What s New In Social March 2018 Edition Facebook Updates (There s a lot!) OCTOBER 2017 GIF
Campaign Goals, Objectives and Timeline SEO & Pay Per Click Process SEO Case Studies SEO, SEM, Social Media Strategy On Page SEO Off Page SEO
 Campaign Goals, Objectives and Timeline SEO & Pay Per Click Process SEO Case Studies SEO, SEM, Social Media Strategy On Page SEO Off Page SEO Reporting Pricing Plans Why Us & Contact Generate organic search
Campaign Goals, Objectives and Timeline SEO & Pay Per Click Process SEO Case Studies SEO, SEM, Social Media Strategy On Page SEO Off Page SEO Reporting Pricing Plans Why Us & Contact Generate organic search
Advanced Digital Markeitng Training Syllabus
 Advanced Digital Markeitng Training Syllabus Digital Marketing Overview What is marketing? What is Digital Marketing? Understanding Marketing Process Why Digital Marketing Wins Over Traditional Marketing?
Advanced Digital Markeitng Training Syllabus Digital Marketing Overview What is marketing? What is Digital Marketing? Understanding Marketing Process Why Digital Marketing Wins Over Traditional Marketing?
Digital Marketing Overview of Digital Marketing Website Creation Search Engine Optimization What is Google Page Rank?
 Digital Marketing Overview of Digital Marketing What is marketing and digital marketing? Understanding Marketing and Digital Marketing Process? Website Creation Understanding about Internet, websites,
Digital Marketing Overview of Digital Marketing What is marketing and digital marketing? Understanding Marketing and Digital Marketing Process? Website Creation Understanding about Internet, websites,
Getting Started With Google Analytics Detailed Beginner s Guide
 Getting Started With Google Analytics Detailed Beginner s Guide Copyright 2009-2016 FATbit - All rights reserved. The number of active websites on the internet could exceed the billionth mark by the end
Getting Started With Google Analytics Detailed Beginner s Guide Copyright 2009-2016 FATbit - All rights reserved. The number of active websites on the internet could exceed the billionth mark by the end
Detecting Abuse in TLDs
 Detecting Abuse in TLDs A NameSentry TM presentation by Greg Aaron and Michael Young ICANN Toronto: 15 October 2012 2012 Illumintel Inc. All rights reserved. 1 Defining Abuse Every service provider has
Detecting Abuse in TLDs A NameSentry TM presentation by Greg Aaron and Michael Young ICANN Toronto: 15 October 2012 2012 Illumintel Inc. All rights reserved. 1 Defining Abuse Every service provider has
Spamming Botnets: Signatures and Characteristics
 Spamming Botnets: Signatures and Characteristics Himanshu Jethawa Department of Computer Science Missouri University of Science and Technology hj5y3@mst.edu http://www.sigcomm.org/sites/default/files/ccr/papers/2008/
Spamming Botnets: Signatures and Characteristics Himanshu Jethawa Department of Computer Science Missouri University of Science and Technology hj5y3@mst.edu http://www.sigcomm.org/sites/default/files/ccr/papers/2008/
An MCL-Based Approach for Spam Profile Detection in Online Social Networks
 12 IEEE 11th International Conference on Trust, Security and Privacy in Computing and Communications An MCL-Based Approach for Profile Detection in Online Social Networks Faraz Ahmed Center of Excellence
12 IEEE 11th International Conference on Trust, Security and Privacy in Computing and Communications An MCL-Based Approach for Profile Detection in Online Social Networks Faraz Ahmed Center of Excellence
Base Estimate Price List
 Base Estimate Price List Last Updated: February 2, 2018* Website & Application Development *PLEASE NOTE: Many of the prices indicated below should be considered fuel for further conversation only. Almost
Base Estimate Price List Last Updated: February 2, 2018* Website & Application Development *PLEASE NOTE: Many of the prices indicated below should be considered fuel for further conversation only. Almost
Google Analytics Basics. John Sammon CEO, Sixth City Marketing
 Google Analytics Basics John Sammon CEO, Sixth City Marketing john@sixthcitymarketing.com About Sixth City Marketing Advertising agency specializing in internet marketing Mission is to help client s achieve
Google Analytics Basics John Sammon CEO, Sixth City Marketing john@sixthcitymarketing.com About Sixth City Marketing Advertising agency specializing in internet marketing Mission is to help client s achieve
Better Funding Better Roads Video Series. 8. Display d. Interactive Presentation
 8. Display d. Interactive Presentation MDOT Created with VideoScribe software. view series How is MDOT Held Accountable? MDOT Funding What is a Pothole? MDOT First Responders MDOT Equipment and Vehicles
8. Display d. Interactive Presentation MDOT Created with VideoScribe software. view series How is MDOT Held Accountable? MDOT Funding What is a Pothole? MDOT First Responders MDOT Equipment and Vehicles
Exploring the ecosystem of malicious domain registrations in the.eu TLD
 Exploring the ecosystem of malicious domain registrations in the.eu TLD Lieven Desmet OWASP BeNeLux Day 2017 Tilburg, NL Lieven.Desmet@cs.kuleuven.be @lieven_desmet Joint research between KU Leuven and
Exploring the ecosystem of malicious domain registrations in the.eu TLD Lieven Desmet OWASP BeNeLux Day 2017 Tilburg, NL Lieven.Desmet@cs.kuleuven.be @lieven_desmet Joint research between KU Leuven and
Sharp Social. Natural Language Understanding
 Sharp Social Natural Language Understanding Step 1 Go to the URL https://console.ng.bluemix.net/ and press enter. A new window appears of IBM Bluemix which asks you to sign up and create a Bluemix account.
Sharp Social Natural Language Understanding Step 1 Go to the URL https://console.ng.bluemix.net/ and press enter. A new window appears of IBM Bluemix which asks you to sign up and create a Bluemix account.
NeighborWatcher: A Content-Agnostic Comment Spam Inference System
 NeighborWatcher: A Content-Agnostic Comment Spam Inference System Jialong Zhang and Guofei Gu Secure Communication and Computer Systems Lab Department of Computer Science & Engineering Texas A&M University
NeighborWatcher: A Content-Agnostic Comment Spam Inference System Jialong Zhang and Guofei Gu Secure Communication and Computer Systems Lab Department of Computer Science & Engineering Texas A&M University
Identifying Fraudulently Promoted Online Videos
 Identifying Fraudulently Promoted Online Videos Vlad Bulakh, Christopher W. Dunn, Minaxi Gupta April 7, 2014 April 7, 2014 Vlad Bulakh 2 Motivation Online video sharing websites are visited by millions
Identifying Fraudulently Promoted Online Videos Vlad Bulakh, Christopher W. Dunn, Minaxi Gupta April 7, 2014 April 7, 2014 Vlad Bulakh 2 Motivation Online video sharing websites are visited by millions
Social Marketing User Guide
 Social Marketing User Guide 1 Table of Contents 3 4 8 10 11 12 13 Settings Creating a New Post My Posts Customer Posts Leads Content Analytics 2 Settings The first time you log in, navigate to the left
Social Marketing User Guide 1 Table of Contents 3 4 8 10 11 12 13 Settings Creating a New Post My Posts Customer Posts Leads Content Analytics 2 Settings The first time you log in, navigate to the left
The Bots Are Coming The Bots Are Coming Scott Taylor Director, Solutions Engineering
 The Bots Are Coming The Bots Are Coming Scott Taylor Director, Solutions Engineering Safe Harbor Statement The following is intended to outline our general product direction. It is intended for information
The Bots Are Coming The Bots Are Coming Scott Taylor Director, Solutions Engineering Safe Harbor Statement The following is intended to outline our general product direction. It is intended for information
Efficient and Scalable Socware Detec2on in Online Social Networks
 Efficient and Scalable Socware Detec2on in Online Social Networks Md Sazzadur Rahman, Ting- Kai Huang, Harsha Madhyastha, Michalis Faloutsos University of California, Riverside Problem Statement Social
Efficient and Scalable Socware Detec2on in Online Social Networks Md Sazzadur Rahman, Ting- Kai Huang, Harsha Madhyastha, Michalis Faloutsos University of California, Riverside Problem Statement Social
Real- &me Archiving of Spontaneous Events (Use- Case : Hurricane Sandy)
 Archive- it Partner Mee&ng, Annapolis, Maryland December 3, 2012 Real- &me Archiving of Spontaneous Events (Use- Case : Hurricane Sandy) Kiran ChiBuri, Digital Library Research Laboratory, Virginia Tech.
Archive- it Partner Mee&ng, Annapolis, Maryland December 3, 2012 Real- &me Archiving of Spontaneous Events (Use- Case : Hurricane Sandy) Kiran ChiBuri, Digital Library Research Laboratory, Virginia Tech.
Social Networking in Action
 Social Networking In Action 1 Social Networking in Action I. Facebook Friends Friends are people on Facebook whom you know, which can run the range from your immediate family to that person from high school
Social Networking In Action 1 Social Networking in Action I. Facebook Friends Friends are people on Facebook whom you know, which can run the range from your immediate family to that person from high school
Technical Brief: Domain Risk Score Proactively uncover threats using DNS and data science
 Technical Brief: Domain Risk Score Proactively uncover threats using DNS and data science 310 Million + Current Domain Names 11 Billion+ Historical Domain Profiles 5 Million+ New Domain Profiles Daily
Technical Brief: Domain Risk Score Proactively uncover threats using DNS and data science 310 Million + Current Domain Names 11 Billion+ Historical Domain Profiles 5 Million+ New Domain Profiles Daily
Get Twitter Followers in an Easy Way Step by Step Guide
 Get Twitter Followers in an Easy Way Step by Step Guide See how I made $2300 in 3 Days using Twitter Traffic All in one guide for getting traffic via Twitter 1 Get Twitter Followers in an easy way Step
Get Twitter Followers in an Easy Way Step by Step Guide See how I made $2300 in 3 Days using Twitter Traffic All in one guide for getting traffic via Twitter 1 Get Twitter Followers in an easy way Step
ADVANCED DIGITAL MARKETING COURSE
 ADVANCED DIGITAL MARKETING COURSE Master the Art of Digital Introduction to Digital marketing PPC MARKETING (Google Adwords) Website designing Introduction Display Advertising Search Engine Optimization
ADVANCED DIGITAL MARKETING COURSE Master the Art of Digital Introduction to Digital marketing PPC MARKETING (Google Adwords) Website designing Introduction Display Advertising Search Engine Optimization
Part 1. Learn how to collect streaming data from Twitter web API.
 Tonight Part 1. Learn how to collect streaming data from Twitter web API. Part 2. Learn how to store the streaming data to files or a database so that you can use it later for analyze or representation
Tonight Part 1. Learn how to collect streaming data from Twitter web API. Part 2. Learn how to store the streaming data to files or a database so that you can use it later for analyze or representation
How to Use Social Media Analytics
 Echo & Co. Lecture Series How to Use Social Media Analytics Juan Gonzalez Partner & Managing Director Director of Client Services Echo & Co. March 2, 2015 Review: Digital Behavior The Digital Action Funnel
Echo & Co. Lecture Series How to Use Social Media Analytics Juan Gonzalez Partner & Managing Director Director of Client Services Echo & Co. March 2, 2015 Review: Digital Behavior The Digital Action Funnel
Manually Create Phishing Page For Facebook 2014
 Manually Create Phishing Page For Facebook 2014 While you are creating phishing page manually you have to do a lot of work Web Templates -- For importing premade template for Gmail, Facebook from SET.
Manually Create Phishing Page For Facebook 2014 While you are creating phishing page manually you have to do a lot of work Web Templates -- For importing premade template for Gmail, Facebook from SET.
YOU CAN'T AFFORD FAKE ACCOUNTS. NOW, NEITHER CAN THE FRAUDSTERS. Fraud Report
 YOU CAN'T AFFORD FAKE ACCOUNTS. NOW, NEITHER CAN THE FRAUDSTERS. Fraud Report Fake Accounts and the Black Market There s a thriving black market for fake accounts on the internet. Fake accounts are accounts
YOU CAN'T AFFORD FAKE ACCOUNTS. NOW, NEITHER CAN THE FRAUDSTERS. Fraud Report Fake Accounts and the Black Market There s a thriving black market for fake accounts on the internet. Fake accounts are accounts
Module: Internet Security Seminar Lecturer: Tom Chothia Presented By: Donald Mkpanam
 Module: Internet Security Seminar Lecturer: Tom Chothia Presented By: Donald Mkpanam ! Introduc=on! History detec=on mechanisms! Data Collec=on! Web Behavioral Fingerprints! Web History Profile Uniqueness!
Module: Internet Security Seminar Lecturer: Tom Chothia Presented By: Donald Mkpanam ! Introduc=on! History detec=on mechanisms! Data Collec=on! Web Behavioral Fingerprints! Web History Profile Uniqueness!
Classification Methods for Spam Detection In Online Social Network
 International Research Journal of Engineering and Technology (IRJET) e-issn: 2395-56 Volume: 4 Issue: 7 July-217 www.irjet.net p-issn: 2395-72 Classification Methods for Spam Detection In Online Social
International Research Journal of Engineering and Technology (IRJET) e-issn: 2395-56 Volume: 4 Issue: 7 July-217 www.irjet.net p-issn: 2395-72 Classification Methods for Spam Detection In Online Social
Google Analytics. Gain insight into your users. How To Digital Guide 1
 Google Analytics Gain insight into your users How To Digital Guide 1 Table of Content What is Google Analytics... 3 Before you get started.. 4 The ABC of Analytics... 5 Audience... 6 Behaviour... 7 Acquisition...
Google Analytics Gain insight into your users How To Digital Guide 1 Table of Content What is Google Analytics... 3 Before you get started.. 4 The ABC of Analytics... 5 Audience... 6 Behaviour... 7 Acquisition...
The Domain Abuse Activity Reporting System (DAAR)
 The Domain Abuse Activity Reporting System (DAAR) Dave Piscitello APWG EU October 2017 The Domain Abuse Activity Reporting system What is the Domain Abuse Activity Reporting system? A system for reporting
The Domain Abuse Activity Reporting System (DAAR) Dave Piscitello APWG EU October 2017 The Domain Abuse Activity Reporting system What is the Domain Abuse Activity Reporting system? A system for reporting
Author: Andrea Bartolini 30/10/2016
 Author: Andrea Bartolini 30/10/2016 Social media Organic posts calendar (1 week of promotion) 3 Facebook posts 1 boosted Facebook post 10 Tweets 1 promoted tweet If performance is good, consider paid social
Author: Andrea Bartolini 30/10/2016 Social media Organic posts calendar (1 week of promotion) 3 Facebook posts 1 boosted Facebook post 10 Tweets 1 promoted tweet If performance is good, consider paid social
Techno Expert Solutions An institute for specialized studies! 0.20 hrs hrs. 2 hrs
 1 2 3 Course Content of Digital Marketing What is Marketing: Understanding Marketing AIDA Model 4 Ps of Marketing Onilne and Offline Marketing KISS Formula Different Types of Marketing Integrated Marketing
1 2 3 Course Content of Digital Marketing What is Marketing: Understanding Marketing AIDA Model 4 Ps of Marketing Onilne and Offline Marketing KISS Formula Different Types of Marketing Integrated Marketing
Netvibes A field guide for missions, posts and IRCs
 Netvibes A field guide for missions, posts and IRCs 7/2/2012 U.S. Department of State International Information Programs Office of Innovative Engagement Table of Contents Introduction... 3 Setting up your
Netvibes A field guide for missions, posts and IRCs 7/2/2012 U.S. Department of State International Information Programs Office of Innovative Engagement Table of Contents Introduction... 3 Setting up your
EVILCOHORT: Detecting Communities of Malicious Accounts on Online Services
 EVILCOHORT: Detecting Communities of Malicious Accounts on Online Services Gianluca Stringhini,, Pierre Mourlanne, Gregoire Jacob, Manuel Egele, Christopher Kruegel, and Giovanni Vigna University College
EVILCOHORT: Detecting Communities of Malicious Accounts on Online Services Gianluca Stringhini,, Pierre Mourlanne, Gregoire Jacob, Manuel Egele, Christopher Kruegel, and Giovanni Vigna University College
Marketing & Back Office Management
 Marketing & Back Office Management Menu Management Add, Edit, Delete Menu Gallery Management Add, Edit, Delete Images Banner Management Update the banner image/background image in web ordering Online Data
Marketing & Back Office Management Menu Management Add, Edit, Delete Menu Gallery Management Add, Edit, Delete Images Banner Management Update the banner image/background image in web ordering Online Data
Easy Website Creation Using WordPress. Welcome and thank you to our Sponsors
 Easy Website Creation Using WordPress Welcome and thank you to our Sponsors Easy Website Creation Using WordPress Every Business Needs a Website! Presented by: Todd Schafer Designer & WordPress Developer
Easy Website Creation Using WordPress Welcome and thank you to our Sponsors Easy Website Creation Using WordPress Every Business Needs a Website! Presented by: Todd Schafer Designer & WordPress Developer
Advanced Digital Marketing Course
 Page 1 Advanced Digital Marketing Course Launch your successful career in Digital Marketing Page 2 Table of Contents 1. About Varistor. 4 2. About this Course. 5 3. Course Fee 19 4. Batches 19 5. Syllabus
Page 1 Advanced Digital Marketing Course Launch your successful career in Digital Marketing Page 2 Table of Contents 1. About Varistor. 4 2. About this Course. 5 3. Course Fee 19 4. Batches 19 5. Syllabus
Mobile Friendly Website. Checks whether your website is responsive. Out of 10. Out of Social
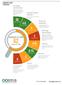 Website Score Overview On-Page Optimization Checks your website for different issues impacting performance and Search Engine Optimization problems. 3 3 WEBSITE SCORE 62 1 1 Competitor Analysis 4.6 5 Analysis
Website Score Overview On-Page Optimization Checks your website for different issues impacting performance and Search Engine Optimization problems. 3 3 WEBSITE SCORE 62 1 1 Competitor Analysis 4.6 5 Analysis
How Facebook knows exactly what turns you on
 How Facebook knows exactly what turns you on We have developed our anti tracking system to combat a culture of user data collection which, we believe, has gone too far. These systems operate hidden from
How Facebook knows exactly what turns you on We have developed our anti tracking system to combat a culture of user data collection which, we believe, has gone too far. These systems operate hidden from
Digital Marketing Glossary of Basic Terms & Concepts
 Digital Marketing Glossary of Basic Terms & Concepts A/B Testing Testing done to compare two variations of something against a variable. Often done to test the effectiveness of marketing tactics such as
Digital Marketing Glossary of Basic Terms & Concepts A/B Testing Testing done to compare two variations of something against a variable. Often done to test the effectiveness of marketing tactics such as
Trusted Profile Identification and Validation Model
 International Journal of Engineering Research and Development e-issn: 2278-067X, p-issn: 2278-800X, www.ijerd.com Volume 7, Issue 1 (May 2013), PP. 01-05 Himanshu Gupta 1, A Arokiaraj Jovith 2 1, 2 Dept.
International Journal of Engineering Research and Development e-issn: 2278-067X, p-issn: 2278-800X, www.ijerd.com Volume 7, Issue 1 (May 2013), PP. 01-05 Himanshu Gupta 1, A Arokiaraj Jovith 2 1, 2 Dept.
Big Data Analytics CSCI 4030
 High dim. data Graph data Infinite data Machine learning Apps Locality sensitive hashing PageRank, SimRank Filtering data streams SVM Recommen der systems Clustering Community Detection Queries on streams
High dim. data Graph data Infinite data Machine learning Apps Locality sensitive hashing PageRank, SimRank Filtering data streams SVM Recommen der systems Clustering Community Detection Queries on streams
The Ultimate YouTube SEO Guide: Tips & Tricks on How to Increase Views and Rankings for your Online Videos
 The Ultimate YouTube SEO Guide: Tips & Tricks on How to Increase Views and Rankings for your Online Videos The Ultimate App Store Optimization Guide Summary 1. Introduction 2. Choose the right video topic
The Ultimate YouTube SEO Guide: Tips & Tricks on How to Increase Views and Rankings for your Online Videos The Ultimate App Store Optimization Guide Summary 1. Introduction 2. Choose the right video topic
Social Network Mining An Introduction
 Social Network Mining An Introduction Jiawei Zhang Assistant Professor Florida State University Big Data A Questionnaire Please raise your hands, if you (1) use Facebook (2) use Instagram (3) use Snapchat
Social Network Mining An Introduction Jiawei Zhang Assistant Professor Florida State University Big Data A Questionnaire Please raise your hands, if you (1) use Facebook (2) use Instagram (3) use Snapchat
Cheryl Bledsoe, EM Division Manager Clark Regional Emergency Services Agency (CRESA)
 Cheryl Bledsoe, EM Division Manager Clark Regional Emergency Services Agency (CRESA) WHO? Cheryl Bledsoe, Sociologist & Trend Watcher 10 years background in Criminal Justice WHAT? Emergency Manager w/no
Cheryl Bledsoe, EM Division Manager Clark Regional Emergency Services Agency (CRESA) WHO? Cheryl Bledsoe, Sociologist & Trend Watcher 10 years background in Criminal Justice WHAT? Emergency Manager w/no
ITP 140 Mobile Technologies. Mobile Topics
 ITP 140 Mobile Technologies Mobile Topics Topics Analytics APIs RESTful Facebook Twitter Google Cloud Web Hosting 2 Reach We need users! The number of users who try our apps Retention The number of users
ITP 140 Mobile Technologies Mobile Topics Topics Analytics APIs RESTful Facebook Twitter Google Cloud Web Hosting 2 Reach We need users! The number of users who try our apps Retention The number of users
URL ATTACKS: Classification of URLs via Analysis and Learning
 International Journal of Electrical and Computer Engineering (IJECE) Vol. 6, No. 3, June 2016, pp. 980 ~ 985 ISSN: 2088-8708, DOI: 10.11591/ijece.v6i3.7208 980 URL ATTACKS: Classification of URLs via Analysis
International Journal of Electrical and Computer Engineering (IJECE) Vol. 6, No. 3, June 2016, pp. 980 ~ 985 ISSN: 2088-8708, DOI: 10.11591/ijece.v6i3.7208 980 URL ATTACKS: Classification of URLs via Analysis
Machine-Powered Learning for People-Centered Security
 White paper Machine-Powered Learning for People-Centered Security Protecting Email with the Proofpoint Stateful Composite Scoring Service www.proofpoint.com INTRODUCTION: OUTGUNNED AND OVERWHELMED Today
White paper Machine-Powered Learning for People-Centered Security Protecting Email with the Proofpoint Stateful Composite Scoring Service www.proofpoint.com INTRODUCTION: OUTGUNNED AND OVERWHELMED Today
Digital Marketing Courses. Digital Marketing. Who Can Join? Our Achievements. Our Features. Contact: Website:
 Email: admissions@ @hemworld.in Digital Marketing Courses Digital Marketing Opportunity Digital marketing is becoming mainstream in India. Until 2010, many businesses did not take digital marketing seriously.
Email: admissions@ @hemworld.in Digital Marketing Courses Digital Marketing Opportunity Digital marketing is becoming mainstream in India. Until 2010, many businesses did not take digital marketing seriously.
DIGITAL MARKETING TRAINING. What is marketing and digital marketing? Understanding Marketing and Digital Marketing Process?
 DIGITAL MARKETING TRAINING CURRICULUM Overview of Digital Marketing What is marketing and digital marketing? Understanding Marketing and Digital Marketing Process? Website Creation Understanding about
DIGITAL MARKETING TRAINING CURRICULUM Overview of Digital Marketing What is marketing and digital marketing? Understanding Marketing and Digital Marketing Process? Website Creation Understanding about
Jason Polakis, Marco Lancini, Georgios Kontaxis, Federico Maggi, So5ris Ioannidis, Angelos Keromy5s, Stefano Zanero.
 Jason Polakis, Marco Lancini, Georgios Kontaxis, Federico Maggi, So5ris Ioannidis, Angelos Keromy5s, Stefano Zanero polakis@ics.forth.gr Annual Computer Security Applica5ons Conference (ACSAC) 2012 Introduc5on
Jason Polakis, Marco Lancini, Georgios Kontaxis, Federico Maggi, So5ris Ioannidis, Angelos Keromy5s, Stefano Zanero polakis@ics.forth.gr Annual Computer Security Applica5ons Conference (ACSAC) 2012 Introduc5on
Social Media Workshop
 Social Media Workshop RHS Wisley, 21 March 2017 Social: interacting with other people, sharing information with them & receiving information from them. + Media: instrument of communication, like the internet,
Social Media Workshop RHS Wisley, 21 March 2017 Social: interacting with other people, sharing information with them & receiving information from them. + Media: instrument of communication, like the internet,
Anti-Phishing Method for Detecting Suspicious URLs in Twitter
 Anti-Phishing Method for Detecting Suspicious URLs in Twitter Salu Sudhakar 1, Narasimhan T 2 P.G. Scholar, Dept of Computer Science, Mohandas College of engineering and technology Anad, TVM 1 Assistant
Anti-Phishing Method for Detecting Suspicious URLs in Twitter Salu Sudhakar 1, Narasimhan T 2 P.G. Scholar, Dept of Computer Science, Mohandas College of engineering and technology Anad, TVM 1 Assistant
Sitecore Experience Platform 8.0 Rev: September 13, Sitecore Experience Platform 8.0
 Sitecore Experience Platform 8.0 Rev: September 13, 2018 Sitecore Experience Platform 8.0 All the official Sitecore documentation. Page 1 of 455 Experience Analytics glossary This topic contains a glossary
Sitecore Experience Platform 8.0 Rev: September 13, 2018 Sitecore Experience Platform 8.0 All the official Sitecore documentation. Page 1 of 455 Experience Analytics glossary This topic contains a glossary
Detecting Botnets Using Cisco NetFlow Protocol
 Detecting Botnets Using Cisco NetFlow Protocol Royce Clarenz C. Ocampo 1, *, and Gregory G. Cu 2 1 Computer Technology Department, College of Computer Studies, De La Salle University, Manila 2 Software
Detecting Botnets Using Cisco NetFlow Protocol Royce Clarenz C. Ocampo 1, *, and Gregory G. Cu 2 1 Computer Technology Department, College of Computer Studies, De La Salle University, Manila 2 Software
You have to have a reason for using Twitter otherwise it is just another IT tool.
 Twitter Workshop Twitter is a service for users that communicate and stay connected through the exchange of quick messages. This digital communication often leads to the creation of a social network formed
Twitter Workshop Twitter is a service for users that communicate and stay connected through the exchange of quick messages. This digital communication often leads to the creation of a social network formed
Countering Spam Using Classification Techniques. Steve Webb Data Mining Guest Lecture February 21, 2008
 Countering Spam Using Classification Techniques Steve Webb webb@cc.gatech.edu Data Mining Guest Lecture February 21, 2008 Overview Introduction Countering Email Spam Problem Description Classification
Countering Spam Using Classification Techniques Steve Webb webb@cc.gatech.edu Data Mining Guest Lecture February 21, 2008 Overview Introduction Countering Email Spam Problem Description Classification
Scaling Local Markets Together. Christian A. Hendricks President
 Scaling Local Markets Together Christian A. Hendricks President Christian A. Hendricks Vice President, Strategic Initiatives Vice President, Products, Marketing & Innovation Vice President, Interactive
Scaling Local Markets Together Christian A. Hendricks President Christian A. Hendricks Vice President, Strategic Initiatives Vice President, Products, Marketing & Innovation Vice President, Interactive
The Ultimate Blogging Cheat Sheet Over 90 Blogging Terms and Tools Defined
 This document is brought to you by MomBlogMentor.com and may include affiliate links. Wordpress.org A blogging platform software that you use on a self-hosted site. Wordpress.com A free blogging platform.
This document is brought to you by MomBlogMentor.com and may include affiliate links. Wordpress.org A blogging platform software that you use on a self-hosted site. Wordpress.com A free blogging platform.
SOCIAL NETWORKING'S EFFECT ON BUSINESS SECURITY CONTROLS
 SOCIAL NETWORKING'S EFFECT ON BUSINESS SECURITY CONTROLS Jon Hanny Director of Information Security and Assurance, Buckley Sandler LLP Gaurav Chikara Senior Security Engineer, Cooley LLP AGENDA Social
SOCIAL NETWORKING'S EFFECT ON BUSINESS SECURITY CONTROLS Jon Hanny Director of Information Security and Assurance, Buckley Sandler LLP Gaurav Chikara Senior Security Engineer, Cooley LLP AGENDA Social
Detect Cyber Threats with Securonix Proxy Traffic Analyzer
 Detect Cyber Threats with Securonix Proxy Traffic Analyzer Introduction Many organizations encounter an extremely high volume of proxy data on a daily basis. The volume of proxy data can range from 100
Detect Cyber Threats with Securonix Proxy Traffic Analyzer Introduction Many organizations encounter an extremely high volume of proxy data on a daily basis. The volume of proxy data can range from 100
SEO TECHNIQUE 9 B E S T O F F P A G E O P T I M I Z A T I O N M E T H O D
 SEO TECHNIQUE 9 B E S T O F F P A G E O P T I M I Z A T I O N M E T H O D By Ajay Kumar Rai The two important element of SEO is on page Optimization and off page optimization but in both the Seo techniques
SEO TECHNIQUE 9 B E S T O F F P A G E O P T I M I Z A T I O N M E T H O D By Ajay Kumar Rai The two important element of SEO is on page Optimization and off page optimization but in both the Seo techniques
ESTABLISHING YOUR COUNTY S ONLINE PRESENCE
 ESTABLISHING YOUR COUNTY S ONLINE PRESENCE OCTOBER 26, 2016 LAUREN-COLBY LINDLEY EXTENSION INSTRUCTOR CENTER FOR TECHNOLOGY OUTREACH MISSISSIPPI STATE UNIVERSITY EXTENSION WHAT S OUT THERE Types of Digital
ESTABLISHING YOUR COUNTY S ONLINE PRESENCE OCTOBER 26, 2016 LAUREN-COLBY LINDLEY EXTENSION INSTRUCTOR CENTER FOR TECHNOLOGY OUTREACH MISSISSIPPI STATE UNIVERSITY EXTENSION WHAT S OUT THERE Types of Digital
Looking Forward: Challenges in Mobile Security. John Mitchell Stanford University
 Looking Forward: Challenges in Mobile Security John Mitchell Stanford University Outline Mobile platform security SessionJuggler Using phone as authentication token SelectiveAuth Protecting resources on
Looking Forward: Challenges in Mobile Security John Mitchell Stanford University Outline Mobile platform security SessionJuggler Using phone as authentication token SelectiveAuth Protecting resources on
Navigating Your CrowdRise Dashboard Team Member Guide
 Navigating Your CrowdRise Dashboard Team Member Guide Once you have set up a fundraising page and added some pictures, it s time to explore more options available on your Dashboard. Step 1 - Log in to
Navigating Your CrowdRise Dashboard Team Member Guide Once you have set up a fundraising page and added some pictures, it s time to explore more options available on your Dashboard. Step 1 - Log in to
Webinar Series. Sign up at February 15 th. Website Optimization - What Does Google Think of Your Website?
 Webinar Series February 15 th Website Optimization - What Does Google Think of Your Website? March 21 st Getting Found on Google using SEO April 18 th Crush Your Competitors with Inbound Marketing May
Webinar Series February 15 th Website Optimization - What Does Google Think of Your Website? March 21 st Getting Found on Google using SEO April 18 th Crush Your Competitors with Inbound Marketing May
Getting Started: Log on or Create Account
 Getting Started: Log on or Create Account Sign into CD To begin, on the right side of the top menu below the Search box, click Log In. The Log in to CD page appears. This page allows you to create an account,
Getting Started: Log on or Create Account Sign into CD To begin, on the right side of the top menu below the Search box, click Log In. The Log in to CD page appears. This page allows you to create an account,
Website Planning & Creation (14 hrs)
 Website Planning & Creation (14 hrs) Understanding Internet Difference between Internet & web Understanding websites Understanding domain names & domain extensions What is web server & web hosting Different
Website Planning & Creation (14 hrs) Understanding Internet Difference between Internet & web Understanding websites Understanding domain names & domain extensions What is web server & web hosting Different
WEB ANALYTICS. An Overview
 WEB ANALYTICS An Overview What We ll Cover Introduction Metrics Standard Reports Tracking Codes Real life Use Cases 3 Why Use Analytics? To optimize the site To optimize marketing To increase conversions
WEB ANALYTICS An Overview What We ll Cover Introduction Metrics Standard Reports Tracking Codes Real life Use Cases 3 Why Use Analytics? To optimize the site To optimize marketing To increase conversions
Size Matters Measuring a Botnet Operator s Pinkie
 VB2010, Vancouver Size Matters Measuring a Botnet Operator s Pinkie Gunter Ollmann, VP Research gollmann@damballa.com About Gunter Ollmann VP of Research, Damballa Inc. Board of Advisors, IOActive Inc.
VB2010, Vancouver Size Matters Measuring a Botnet Operator s Pinkie Gunter Ollmann, VP Research gollmann@damballa.com About Gunter Ollmann VP of Research, Damballa Inc. Board of Advisors, IOActive Inc.
Vulnerability Disclosure in the Age of Social Media: Exploiting Twitter for Predicting Real-World Exploits
 Vulnerability Disclosure in the Age of Social Media: Exploiting Twitter for Predicting Real-World Exploits Carl Sabottke Octavian Suciu Tudor Dumitraș University of Maryland 2 Problem Increasing number
Vulnerability Disclosure in the Age of Social Media: Exploiting Twitter for Predicting Real-World Exploits Carl Sabottke Octavian Suciu Tudor Dumitraș University of Maryland 2 Problem Increasing number
Comping Guide. Rafflecopter & Blogs
 Comping Guide Blogs 2 Following blogs 2 Commenting on blogs 2 Prize promotions on blogs 4 Notifying winners 4 How to find Blog comps 4 Rafflecopter 5 Types of Rafflecopter giveaway 6 An example Rafflecopter
Comping Guide Blogs 2 Following blogs 2 Commenting on blogs 2 Prize promotions on blogs 4 Notifying winners 4 How to find Blog comps 4 Rafflecopter 5 Types of Rafflecopter giveaway 6 An example Rafflecopter
TRACKING YOUR WEBSITE WITH GOOGLE ANALYTICS CHRIS EDWARDS
 TRACKING YOUR WEBSITE WITH GOOGLE ANALYTICS CHRIS EDWARDS Hi, I am Chris Edwards Data Nerd & Agency Owner Website Developer 18 years WordPress Developer 6 years Google Analytics 13 years Digital Marketer/SEO
TRACKING YOUR WEBSITE WITH GOOGLE ANALYTICS CHRIS EDWARDS Hi, I am Chris Edwards Data Nerd & Agency Owner Website Developer 18 years WordPress Developer 6 years Google Analytics 13 years Digital Marketer/SEO
