USE OF TECHNOLOGY TO DISTRIBUTE CHILD PORNOGRAPHY
|
|
|
- Colin Dickerson
- 6 years ago
- Views:
Transcription
1 Peer to Peer Networking BitTorrent, a popular peer to peer networking software, can be downloaded for free from the BitTorrent website. Once the user has installed the program on their computer, they can search for a variety of files. A user can find books in PDF format, movies that are still in theaters, copies of Microsoft Office, or pictures from a recent magazine. The distribution of all of these files is illegal for copyright purposes and others. However, another common use of the software is for distribution of child pornography. Suppose the user wants to find pictures containing the keywords child pornography. The user can simply go to Google and perform a search for child pornography torrent. When they find the description of a file they want, they download the torrent to their computer and open it in BitTorrent. The torrent file has information describing the actual file the user will download (such as a picture or video). What separates peer to peer networking from the rest of the Internet is that when a user downloads a file on BitTorrent, the file itself is not coming from the BitTorrent server, but rather from other users computers. In the early days of music downloading, downloads came directly from a server. This made it much easier to place legal blame on the software provider. However, shifting hosting responsibilities to the user allows the software provider to say that they cannot control what their users are sharing online. Therefore, when a user opens a torrent file in BitTorrent, the software searches the entire network to see how many others have the same file. A file might be downloaded by hundreds of users at a time. When the user s computer begins downloading it, the computer takes pieces of the file from each computer until the download is 1 TYPES OF TECHNOLOGY finished. Thus, each of the users was a distributor of parts of the file, but not the entire file. Some computers have a faster connection to the Internet than others. Those with a faster connection will often share more parts of the file. The download of a picture may take less than a minute. An hour long video may take between a half hour and several days depending on how many other users have the file and how fast their connection is. How can it be used? Suppose John recently downloaded BitTorrent to his computer in order to download music. During one search, he noticed a result that seemed to suggest it was child pornography. Curious, John decided to download it. He later decided to download more and now has a collection of approximately 200 photos on his computer. His computer is connected to the Internet through a cable service, and John never turns his computer off. He also never closes BitTorrent because he is constantly downloading large video files which take several days to complete. One night, Officer Smith is searching for child pornography on BitTorrent in order to catch distributors. One file name that comes up appears to be child pornography, and he downloads it. The file is being downloaded from four different
2 computers, one of which is connected to the Internet with an IP Address of Smith obtains a subpoena and finds that the account belongs to John. Several questions arise. Where are the files? Can Smith contact BitTorrent to help provide evidence? If John is only distributing part of a file, is he a distributor of child pornography? Program Settings BitTorrent can be personalized with a variety of settings. Below is a quick run through of some of them. Incomplete Downloads Once a user begins to download a file, the incomplete snippets are now available for download from other users. Thus, if a user attempts to download a picture containing child pornography but never completes the download, the parts of the file may still remain on their computer for download by other users. Also, just because the download has not been completed does not mean that a part of the picture cannot be viewed. Security Settings A user may turn off file sharing so that they are still able to download files from other computers on the network, but those users cannot download from them. Using a program like BitTorrent allows the user to restrict search results so that copyrighted files and/or adult content do not appear. Chat Software While a user is connected to programs like BitTorrent, they are able to chat with other users. For example, if they had been using BitTorrent, Officer Smith could have started a chat conversation with John. File Storage When the file is being downloaded, but is incomplete, the default location on the user s computer is on the user s computer in a folder titled Incomplete. Once it finishes, the file automatically moves to a folder marked Shared. Proxy Servers Users can connect to the network through a proxy server. A proxy server allows the user to connect anonymously through a third party computer. It also might allow a user to connect to the network if the computer s security settings do not allow a connection to the LimeWire network. File Sharing Many file sharing problems can allow a user to share every file on their computer rather than just those stored in the Shared folder. Thus, there is the potential for a user to unknowingly share their private information without restriction on the Internet. IP Address Blocking Individual IP addresses or a range of addresses can be blocked using P2P software. If a user knew a range of IP addresses for their state law enforcement, they could block their computer from appearing in search results from law enforcement. Peer to Peer networking can easily be used to distribute child pornography. The environment seems anonymous (users are only identified by IP address), so many people feel comfortable sharing child pornography and other illegal files on P2P networks. Suppose two people meet in a chatroom and want to share child pornography. As e mail is a little too personal, they can exchange IP addresses and connect to each other s computers to download files. There is no way to charge money for files downloaded from other users on a P2P network. 2
3 Cellular Phones Regular text messages, known as SMS (short message service) are small amounts of text that are sent between cell phones. Most messages are 160 characters or less. After the user types the message using his cell phone and presses send, the message is transferred to his cell phone provider through the closest cell towers. From there, the message is transferred to the server of the recipient s provider. Then, the message travels to the recipient through the nearest cell towers. In addition to the text of the message, additional information is attached to it which helps the servers direct the messages. This information is in the form of 70 or so numbers which tell the servers the time and date, phone numbers of the sender and receiver, and other information. Upon receiving the message, the user can choose to reply to the message. That message then travels through the opposite route. SMS is known as a store and forward service. This means that if the server realizes that the recipient s cell phone is turned off, the message will be stored on the server until it can be delivered. Most servers delete these messages if not delivered within a few days. Similar to SMS is MMS (Multimedia Messaging Service). MMS works just like SMS except it allows the sender to share pictures, audio, and video. For example, a user can create a new MMS and insert a video that can then be transferred to another s cell phone (or e mail). MMS is not a default service for cell phones. Both the sender and recipient must be subscribed to the service in order to send or receive multimedia messages. Miscellaneous Facts Often, text messages can be sent through websites or to a cell phone. When sent through a website, these messages are often anonymous. Text messages can also be sent from a cell phone to an address. Messages are usually stored on the recipient s cell phone until they delete them. Outgoing messages are usually saved on the phone s memory as well. Since most modern day cell phones have a large amount of memory, text messages often remain on the phone for months or even for the life of the phone. Like , text messages can be sent to multiple recipients. However, unlike , there is no way for the recipients to know everyone it was sent to or to reply to all. Some cell phones allow the user to request message delivery confirmation which will allow them to know when the message has been delivered. 3
4 Cameras and File Storage Most cell phones now come equipped with a digital camera built into the phone. Newer phones have cameras that are capable of taking very high quality shots. When the picture is taken, it is saved automatically on the phone s internal memory or memory card. The photos remain there and can be viewed on the phone or transferred elsewhere. They could be ed or copied to a computer with a cable or wirelessly through Bluetooth. Many cell phones can connect to a computer. Doing so allows files to be copied from the cell phone to the computer but also for files to be transferred from the computer to the cell phone. Thus, a cell phone can be a good hiding place for files. Internet Access Many phones now including BlackBerrys and the iphone have full access to the Internet. In some cases, it works just like the Internet on a regular computer. Users can check their , send instant messages, access their social networking accounts, and make postings to chat rooms and other interactive sites. Most cell phone users today have access to a 3G network on their phone. A 3G network connects at up to 3 Mbps, roughly six times the speed of dial up. The new 4G network technology may be up to 500 times faster than 3G. Computers can often use a cell phone s connection to access the Internet as well. This signal can be used with a USB cable or wirelessly through Bluetooth. The 3G connection is provided through the cell phone network and data is transmitted from servers to the phone through cell phone towers. Many cell phones have a data synchronization option that allows their phone to upload all of the contents of the phone to a server as a backup. Smartphone Apps Smartphone owners have the ability to download their choice of millions of applications for their phone. These apps provide many new ways to store and exchange data and make the jobs of forensics investigators much more difficult. Bulletin Boards and Message Boards Traditional bulletin boards have mostly been replaced by message boards, also known as forums. Today, social networking seems to be replacing the traditional uses of these services as well, but they still are frequently used in the distribution of child pornography. The use of peer to peer networking would seem to be the safest way to download child pornography because the user is downloading directly from another computer. However, Internet message boards are very anonymous, and the user s IP address is not as easy to find. Further, the main difference between the two is that with many message boards, a user has to be invited. Typically, a message board is a place where those interested in a specific topic can go to share their thoughts. They exist for professional purposes to share information on specific topics and for educational reasons. People create them to discuss sports teams or their favorite video games or hobbies. However, they are also created 4
5 to share pornography. Each message board has a list of categories. Under those categories are various discussion topics (called threads) which have been posted by users. Under those topics are the actual posts from users of the site. Many message boards allow users to post pictures and attachments in addition to text. For example, on a message board, a user could create a discussion topic called European port pictures. Each user that has gone to a European port may post pictures from their travels to share with the others. Message boards are normally moderated by a member with special privileges to ensure that the rules are being followed. However, a message board can be created almost anonymously and that board is controlled entirely by the creator. Further, it is possible for a message board to be private, meaning that it is only accessible by approved users. Most message boards require registration of a user. They often must give their age, name, address, and create a username and password. Their posts on the site will be attributed to their username rather than their name. Of course, users can often register under a fake name and address. Some message boards allow anonymous postings (although that may violate COPPA). Forums in China and Japan rarely require registration as anonymity is greatly valued. What makes it different? A message board differs from a mailing list because unlike the mailing list, a user must go to the message board to see updates. When a user posts on a mailing list, it is automatically distributed to the group s addresses. However, many message boards have an notification option so a user can be aware of new posts. Unlike chat rooms, posts on a message board remain there. The users do not have to be online simultaneously to reply to each other s messages. Chat rooms require the users to be online at the same time to communicate. Message boards are often used in child pornography rings. Users meet in various ways across the Internet in order to get access to the boards. Once inside, users can distribute child pornography by posting it in a thread. Other users will then be able to download it and distribute it through other mediums. Chat Rooms and Instant Messaging Chat Rooms Like message boards, chat rooms have mostly been replaced by social networking. However, they are still used occasionally, and can be used to distribute child pornography. Also like message boards, users often must register to use a chat room, although some simply allow a user to choose an anonymous username. Users can sometimes change their names throughout the chat. Also, chat rooms are often established by topic, so that users with a specific interest will be involved in the chat. 5
6 Once the user logs in, they see a list of all users who are reading the chat. They are able to see what each user posts, but they cannot see what was said before they logged in. A user can often begin a private chat with another user if they choose. Some chat rooms allow users to see video of each other and some allow attachments of files. Depending on the number of users in a chat room, there may be multiple conversations happening at once. Many chat rooms are for a specific age group (children, teens, etc.). Many teens are drawn to chat rooms because of the anonymity. They are free to use a new identity or personality inside of a chat room. Dateline s To Catch a Predator tracks chat room conversations. Instant Messaging Instant messaging (IM) is used very much in the same way that chat rooms are except that users only communicate with those they have approved. When a user opens their IM program, they see which of their friends are currently online. They can then open a private conversation with that friend and begin to send messages back and forth. Popular IM programs include Skype, America Online Instant Messenger (AIM), MSN Messenger (or Windows Messenger), Yahoo Messenger, and Google Chat. Facebook has even joined the group with its own service. Many of these programs have file, picture, audio, and video sharing capabilities. It is also possible to message multiple people privately at the same time or to have a group conversation. An account is required to use these free services, but account information can always be fake. Even information for services requiring a valid address can be falsified. Conversations can be saved, printed or ed easily. Some services also allow the user to save the conversations on the server for the user s benefit. Chat rooms can be private like message boards and allow users to share files like pornographic images. Instant messaging is much more private and users only communicate with friends. If a distributor meets someone they can trust, this would be an excellent tool for them. Social Networking How It Works Popular social networking sites include Facebook, Twitter, MySpace, and LinkedIn. However, Facebook beats out the second most popular site by over four times the number of users. Facebook allows over a half billion users to 6
7 share large amounts of information with the world. People spend over 700 billion minutes per month on Facebook. Each user shares as much as they want, but often displays a picture, name, interests, educational and professional background, and contact information. Other users update their status by telling other users what they are doing or how they feel. They can also upload pictures and video from their computer or cell phone. When someone joins Facebook, they search for friends in order to connect with other people. A user can easily search for people they went to school with or work with. Searches can be done by name, company, school, city, or address. Users can also meet others by joining groups or pages with people who have similar interests. Privacy settings give a user the ability to restrict access to their information. They can choose to share it with no one, just friends, friends of friends, or everyone. Users can communicate by public message (called wall posts), private messaging (very similar to ), or by Facebook Chat (an instant messaging interface). A new Facebook service, Places, allows a user to check in at their current location (such as a restaurant) using their GPS. In addition to reuniting with long lost friends, Facebook has become an excellent way to meet people. Its search capabilities allow users to find each other easily. Facebook is not a great tool for the distribution of pornography or for meeting other distributors (unless there is a secret language of sorts that allows them to inconspicuously communicate). However, Facebook does allow predators to seek out children within a geographic area. Users can share photos or video from their webcam with other users either privately or publicly. Facebook recently announced an expansion of their messaging program which would allow file attachments. Virtual Worlds How It Works When all the other methods of anonymity on the Internet fail, there is always a virtual world. Most virtual worlds are interactive between multiple users, although some are single person. In a virtual world, you choose your name, lifestyle, body, personality, job, and everything else. You can be an animal or a plant. The only thing that stops you is money. One popular virtual world is called Second Life. It is available free to its 18 million users, although a paid version is available with more features and a weekly stipend to spend in the virtual world. Like the real world, nothing is free. You must use money to buy clothes, buildings, cars, and to pay for services. Second Life s 7 currency, the Linden, can be purchased using US Dollars. Selling virtual items has allowed many people to make real money, including some who have made millions. People in a virtual world, known as Avatars, live however they are controlled. They move around and communicate with others by chatting or instant messaging. Second Life is available for users 18 years or older, but Teen Second Life is available for children ages Several countries have embassies in Second Life. The embassy for The Maldives allows visitors to talk to a computer ambassador about visas, trade, and other information. Groups are often established based on
8 subculture and language. Due to geographical divides, these groups rarely interact. Oh, you can fly, too! Users of Second Life must follow the laws of their own countries, and Second Life has also adopted its own laws, such as a ban on gambling. One company, Slustler, has published a pornographic magazine that is only available on Second Life for approximately 60 cents. Thus, the distribution of real child pornography in a virtual world is certainly an issue. However, the most troubling problem is what to do about virtual sex. Second Life has become a Gomorrah of sorts. Users are certainly capable of having sex with each other within the virtual world. It is possible to rape someone on Second Life, but many complex legal issues arise from prosecution of such. Several countries have tried dealing with the issue of an adult having an avatar that looks like a child and then having sex with other users. The United Kingdom has given this act the same status as child pornography. Linden Lab, the company owning Second Life, finally made this act a bannable offense for users. The United States once banned such activities, but the law was struck down by the Supreme Court under the First Amendment. Animation pornography (called hentai), which involves the likeness of children, is also sold on Second Life. Second Life also has a slave market where auctions take place. Some scholars suggest that any illegal act in the real world is also illegal in the virtual world, but many evidentiary issues arise. How do you track someone down? What do you do with witnesses to a crime? A user s appearance can change at any time, so how do you use descriptions? For an excellent discussion on these issues, see: Caroline Meek, Recent Development, Just Age Playing Around? How Second Life Aids and Abets Child Pornography, 9 N.C. J.L. & TECH. ON. 88 (2008) Websites & Blogs How It Works Many services on the Internet allow users to create their own websites for free or for only a few dollars per month. While most website hosting companies forbid their users to store pornography of any type on their servers, this is often hard to prevent. The average website is hosted by a company that is paid to host their files. Most pornographic websites are hosted by a provider that specializes in pornographic material since many hosts forbid pornography. Some hosting companies allow users to store files on their servers for no cost in exchange for allowing the host to place advertisements on the website. 8 On a typical website, every file (pages, images, videos, etc.) has to be uploaded through an FTP server from the creator s computer. One of the common methods of sharing pornography today is to create a blog on a service like Google Blogger. A blog can be created in seconds, and photos uploaded only seconds later. The blog and photos are immediately available to anyone on the Internet. Since free websites or blogs can be established so quickly and anonymously, child pornography may be shared for hours or days before it is found and shutdown. With the right exposure, that could enable thousands of users to download the images or video.
USE OF TECHNOLOGY TO DISTRIBUTE CHILD PORNOGRAPHY
 TYPES OF TECHNOLOGY Peer to Peer Networking Networks in which computers are equal partners using common file sharing programs that allow users to connect directly to each other s computer hard drive to
TYPES OF TECHNOLOGY Peer to Peer Networking Networks in which computers are equal partners using common file sharing programs that allow users to connect directly to each other s computer hard drive to
Outside the Box: Networks and The Internet
 Outside the Box: Networks and The Internet Don Mason Associate Director Copyright 2011 National Center for Justice and the Rule of Law All Rights Reserved Inside vs. Outside Inside the Box What the computer
Outside the Box: Networks and The Internet Don Mason Associate Director Copyright 2011 National Center for Justice and the Rule of Law All Rights Reserved Inside vs. Outside Inside the Box What the computer
Inside vs. Outside. Inside the Box What the computer owner actually has possession of 1/18/2011
 Outside the Box: Networks and The Internet Don Mason Associate Director Copyright 2011 National Center for Justice and the Rule of Law All Rights Reserved Inside vs. Outside Inside the Box What the computer
Outside the Box: Networks and The Internet Don Mason Associate Director Copyright 2011 National Center for Justice and the Rule of Law All Rights Reserved Inside vs. Outside Inside the Box What the computer
THE NATIONAL CENTER FOR JUSTICE AND
 THE NATIONAL CENTER FOR JUSTICE AND THE RULE OF LAW AND THE NATIONAL JUDICIAL COLLEGE USE OF TECHNOLOGY TO DISTRIBUTE CHILD PORNOGRAPHY DIVIDER 2 Professor Donald R. Mason OBJECTIVES: After this session,
THE NATIONAL CENTER FOR JUSTICE AND THE RULE OF LAW AND THE NATIONAL JUDICIAL COLLEGE USE OF TECHNOLOGY TO DISTRIBUTE CHILD PORNOGRAPHY DIVIDER 2 Professor Donald R. Mason OBJECTIVES: After this session,
Social Networking Applied
 Social Networking Applied 1 I. Facebook Social Networking Applied Uses: An address book: Facebook users can share their current city, e-mail address, phone number, screen name, street address, and birthday
Social Networking Applied 1 I. Facebook Social Networking Applied Uses: An address book: Facebook users can share their current city, e-mail address, phone number, screen name, street address, and birthday
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
 Glossary A B C D E F G H I J K L M N O P Q R S T U V W X Y Z A App See Application Application An application (sometimes known as an app ) is a computer program which allows the user to perform a specific
Glossary A B C D E F G H I J K L M N O P Q R S T U V W X Y Z A App See Application Application An application (sometimes known as an app ) is a computer program which allows the user to perform a specific
Social Media and Cyber Safety
 Social Media and Cyber Safety Social Media Apps/Sites Middle School Students May Be Using Facebook Twitter Instagram Ask.fm Kik Messenger SnapChat Tumblr Web-based games Group Chats Facebook and Twitter
Social Media and Cyber Safety Social Media Apps/Sites Middle School Students May Be Using Facebook Twitter Instagram Ask.fm Kik Messenger SnapChat Tumblr Web-based games Group Chats Facebook and Twitter
The ICT4me Curriculum
 The ICT4me Curriculum About ICT4me ICT4me is an after school and summer curriculum for middle school youth to develop ICT fluency, interest in mathematics, and knowledge of information, communication,
The ICT4me Curriculum About ICT4me ICT4me is an after school and summer curriculum for middle school youth to develop ICT fluency, interest in mathematics, and knowledge of information, communication,
The ICT4me Curriculum
 The ICT4me Curriculum About ICT4me ICT4me is an after school and summer curriculum for middle school youth to develop ICT fluency, interest in mathematics, and knowledge of information, communication,
The ICT4me Curriculum About ICT4me ICT4me is an after school and summer curriculum for middle school youth to develop ICT fluency, interest in mathematics, and knowledge of information, communication,
Definitions Know What I Mean?
 Definitions Know What I Mean? The list below contains words you will read about in this resource and that your children probably use regularly as they are a normal part of their school world (if not their
Definitions Know What I Mean? The list below contains words you will read about in this resource and that your children probably use regularly as they are a normal part of their school world (if not their
The Internet and World Wide Web. Chapter4
 The Internet and World Wide Web Chapter4 ITBIS105 IS-IT-UOB 2016 The Internet What is the Internet? Worldwide collection of millions of computers networks that connects ITBIS105 IS-IT-UOB 2016 2 History
The Internet and World Wide Web Chapter4 ITBIS105 IS-IT-UOB 2016 The Internet What is the Internet? Worldwide collection of millions of computers networks that connects ITBIS105 IS-IT-UOB 2016 2 History
Mobile Devices. Questions. NCJRL ICAC Webinar Mobile Devices October 25, Don Mason Associate Director, NCJRL. Presenter
 Mobile Devices Presenter Don Mason Associate Director, NCJRL 662-915-6898 drmason@olemiss.edu Questions Feel free to email any time to: drmason@olemiss.edu Please include your phone number In case it might
Mobile Devices Presenter Don Mason Associate Director, NCJRL 662-915-6898 drmason@olemiss.edu Questions Feel free to email any time to: drmason@olemiss.edu Please include your phone number In case it might
Online Communication. Chat Rooms Instant Messaging Blogging Social Media
 Online Communication E-mail Chat Rooms Instant Messaging Blogging Social Media Advantages: Reduces cost of postage Fast and convenient Eliminates phone charges Disadvantages: May be difficult to understand
Online Communication E-mail Chat Rooms Instant Messaging Blogging Social Media Advantages: Reduces cost of postage Fast and convenient Eliminates phone charges Disadvantages: May be difficult to understand
Prayerful Living Singles User s Manual
 Prayerful Living Singles User s Manual Rev. 7/30/15 1 Contents Welcome... 2 Join for free! (Register)... 2 Setting up your profile... 3 Click on Home... 5 Adding Pics... 5 Editing your profile... 6 Understanding
Prayerful Living Singles User s Manual Rev. 7/30/15 1 Contents Welcome... 2 Join for free! (Register)... 2 Setting up your profile... 3 Click on Home... 5 Adding Pics... 5 Editing your profile... 6 Understanding
KIK s GUIDE FOR LAW ENFORCEMENT
 Thanks for checking out our law enforcement guide. We take the safety of our users very seriously, and we hope this guide will be a useful tool for you. It includes information about our app; the features
Thanks for checking out our law enforcement guide. We take the safety of our users very seriously, and we hope this guide will be a useful tool for you. It includes information about our app; the features
Mobile Devices. Objectives. Types of Devices 4/25/2012
 Mobile Devices Objectives Identify mobile devices Learn how mobile devices obtain and transmit information Identify potential evidence that may be obtained from mobile devices Learn where data is stored
Mobile Devices Objectives Identify mobile devices Learn how mobile devices obtain and transmit information Identify potential evidence that may be obtained from mobile devices Learn where data is stored
The Table Privacy Policy Last revised on August 22, 2012
 The Table Privacy Policy Last revised on August 22, 2012 The Table, an online venue through which your organization and its members/employees can connect to better fulfill its mission respects and is committed
The Table Privacy Policy Last revised on August 22, 2012 The Table, an online venue through which your organization and its members/employees can connect to better fulfill its mission respects and is committed
Gaggle 101 User Guide
 Gaggle 101 User Guide Home Tab The Home tab is the first page displayed upon login. Here you will see customized windows or widgets. Once set, the widgets can be accessed directly by clicking on them from
Gaggle 101 User Guide Home Tab The Home tab is the first page displayed upon login. Here you will see customized windows or widgets. Once set, the widgets can be accessed directly by clicking on them from
Adobe Spark. Schools and Educators. A Guide for. spark.adobe.com
 Adobe Spark A Guide for Schools and Educators spark.adobe.com CONTENTS 1: What Is Adobe Spark?... 3 2: How Much Does Adobe Spark Cost?... 4 3: Is Adobe Spark A Web Application Or An App?... 4 4: Three
Adobe Spark A Guide for Schools and Educators spark.adobe.com CONTENTS 1: What Is Adobe Spark?... 3 2: How Much Does Adobe Spark Cost?... 4 3: Is Adobe Spark A Web Application Or An App?... 4 4: Three
Knowledge Hub Walkthrough
 Knowledge Hub Walkthrough Welcome page Sign in Use your Knowledge Hub account to sign in. Register Are you new to the Knowledge Hub, then please register a new account Forgotten Password? You will be asked
Knowledge Hub Walkthrough Welcome page Sign in Use your Knowledge Hub account to sign in. Register Are you new to the Knowledge Hub, then please register a new account Forgotten Password? You will be asked
Network Applications and Protocols
 Network Applications and Protocols VoIP (Voice over Internet Protocol) Voice over IP (VoIP) is a methodology and group of technologies for the delivery of voice communications and multimedia sessions over
Network Applications and Protocols VoIP (Voice over Internet Protocol) Voice over IP (VoIP) is a methodology and group of technologies for the delivery of voice communications and multimedia sessions over
Ning Frequently Asked Questions
 Ning Frequently Asked Questions Ning is a Web tool that allows anyone to create a customizable social network, allowing users to share pictures and videos, maintain blogs, communicate in chat and discussion
Ning Frequently Asked Questions Ning is a Web tool that allows anyone to create a customizable social network, allowing users to share pictures and videos, maintain blogs, communicate in chat and discussion
FACEBOOK SAFETY FOR JOURNALISTS. Thanks to these partners for reviewing these safety guidelines:
 FACEBOOK SAFETY FOR JOURNALISTS Thanks to these partners for reviewing these safety guidelines: 10 STEPS TO KEEP YOURSELF SAFE Journalists are using Facebook in innovative ways to do their jobs, tell stories,
FACEBOOK SAFETY FOR JOURNALISTS Thanks to these partners for reviewing these safety guidelines: 10 STEPS TO KEEP YOURSELF SAFE Journalists are using Facebook in innovative ways to do their jobs, tell stories,
EADS up. stop think connect
 EADS up stop think connect You text, you play games, you share photos and video. You update your status, you post comments, you probably spend some time in a virtual world. Being online connected through
EADS up stop think connect You text, you play games, you share photos and video. You update your status, you post comments, you probably spend some time in a virtual world. Being online connected through
WHAT IS GOOGLE+ AND WHY SHOULD I USE IT?
 CHAPTER ONE WHAT IS GOOGLE+ AND WHY SHOULD I USE IT? In this chapter: + Discovering Why Google+ Is So Great + What Is the Difference between Google+ and Other Social Networks? + Does It Cost Money to Use
CHAPTER ONE WHAT IS GOOGLE+ AND WHY SHOULD I USE IT? In this chapter: + Discovering Why Google+ Is So Great + What Is the Difference between Google+ and Other Social Networks? + Does It Cost Money to Use
Website Privacy Policy
 Website Privacy Policy Last updated: May 12, 2016 This privacy policy (the Privacy Policy ) applies to this website and all services provided through this website, including any games or sweepstakes (collectively,
Website Privacy Policy Last updated: May 12, 2016 This privacy policy (the Privacy Policy ) applies to this website and all services provided through this website, including any games or sweepstakes (collectively,
TC2-Computer Literacy Mr. Sencer February 4, 2010
 TC2-Computer Literacy Mr. Sencer February 4, 2010 What is a network? A network is a collection of computers and devices connected together, sometimes wirelessly, via communications devices. When a computer
TC2-Computer Literacy Mr. Sencer February 4, 2010 What is a network? A network is a collection of computers and devices connected together, sometimes wirelessly, via communications devices. When a computer
Chapter 2 The Internet and World Wide Web
 Chapter 2 The Internet and World Wide Web Chapter 2 Objectives Discuss the history of the Internet Describe the types of Web sites Explain how to access and connect to the Internet Recognize how Web pages
Chapter 2 The Internet and World Wide Web Chapter 2 Objectives Discuss the history of the Internet Describe the types of Web sites Explain how to access and connect to the Internet Recognize how Web pages
Cyber Smarts Using Social Media Wisely
 Cyber Smarts Using Social Media Wisely Posted on March 24, 2016 by Shridevi Stock Photo You have access to the world s largest museum, art gallery, library and social group ever created. You also have
Cyber Smarts Using Social Media Wisely Posted on March 24, 2016 by Shridevi Stock Photo You have access to the world s largest museum, art gallery, library and social group ever created. You also have
Sunday January Atlantic Shores Baptist Church
 Sunday January 31 2016 Atlantic Shores Baptist Church NOTES RAISING KIDS IN THE DIGITAL AGE Every generation of parents face new challenges that were never set before the previous generation. Our generation
Sunday January 31 2016 Atlantic Shores Baptist Church NOTES RAISING KIDS IN THE DIGITAL AGE Every generation of parents face new challenges that were never set before the previous generation. Our generation
The internet and the web
 1 The internet and the web Internet lunched in 1969 National computer network called: Advanced Research Project Agency Network (ARPANET). The internet is : -Large network that connects together smaller
1 The internet and the web Internet lunched in 1969 National computer network called: Advanced Research Project Agency Network (ARPANET). The internet is : -Large network that connects together smaller
Collaborating via Social Networks and Groupware
 Collaborating via Social Networks and Groupware When all team members have access to the Internet, why not use the Internet to connect the members of the group to enable communication, file sharing, and
Collaborating via Social Networks and Groupware When all team members have access to the Internet, why not use the Internet to connect the members of the group to enable communication, file sharing, and
Frequently Asked Questions. OTA (Firmware Upgrades) & Parental Registration
 Frequently Asked Questions OTA (Firmware Upgrades) & Parental Registration Q: What is OTA? Why is this important for me to know? A: OTA is a firmware upgrade to your Meep! that brings the Meep! to the
Frequently Asked Questions OTA (Firmware Upgrades) & Parental Registration Q: What is OTA? Why is this important for me to know? A: OTA is a firmware upgrade to your Meep! that brings the Meep! to the
Content Curation Mistakes
 Table of Contents Table of Contents... 2 Introduction... 3 Mistake #1 Linking to Poor Quality Content... 4 Mistake #2 Using the Same Few Sources... 5 Mistake #3 Curating Only Blog Posts... 6 Mistake #4
Table of Contents Table of Contents... 2 Introduction... 3 Mistake #1 Linking to Poor Quality Content... 4 Mistake #2 Using the Same Few Sources... 5 Mistake #3 Curating Only Blog Posts... 6 Mistake #4
Table of Contents 1 CREATING AN ACCOUNT Sign up Download Skype Sign in Test Audio and Video...
 SIGBI GUIDE - SKYPE For the purpose of this document, references to Soroptimist International Great Britain and Ireland (SIGBI) Limited and Soroptimist International may be written as SIGBI and SI only.
SIGBI GUIDE - SKYPE For the purpose of this document, references to Soroptimist International Great Britain and Ireland (SIGBI) Limited and Soroptimist International may be written as SIGBI and SI only.
TITLE SOCIAL MEDIA AND COLLABORATION POLICY
 DATE 9/20/2010 TITLE 408.01 SOCIAL MEDIA AND COLLABORATION POLICY ORG. AGENCY Department of Communications Approved AFT As more and more citizens in our community make the shift towards, or include the
DATE 9/20/2010 TITLE 408.01 SOCIAL MEDIA AND COLLABORATION POLICY ORG. AGENCY Department of Communications Approved AFT As more and more citizens in our community make the shift towards, or include the
Social Media. The infinite abilities of a smart phone
 Social Media The infinite abilities of a smart phone It s all about the Likes, Shares and Stats Social Media is driven by users desire for Likes - Shares - Retweets - Followers to the point that users
Social Media The infinite abilities of a smart phone It s all about the Likes, Shares and Stats Social Media is driven by users desire for Likes - Shares - Retweets - Followers to the point that users
Focused on locking down and monitoring a child s computer/cell phone use. Created for use by Canal Computer Services
 Focused on locking down and monitoring a child s computer/cell phone use. Education Background -Bachelors in Information Technology Security -Certified: A+ Network+ Security+ Microsoft Professional Microsoft
Focused on locking down and monitoring a child s computer/cell phone use. Education Background -Bachelors in Information Technology Security -Certified: A+ Network+ Security+ Microsoft Professional Microsoft
VoIP/SIP: Economy and Mobility
 Nowadays VoIP-services become more and more popular all over the world. VoIP stands for Voice Over Internet Protocol, a communications protocol that allows for telephonic communication via the Internet.
Nowadays VoIP-services become more and more popular all over the world. VoIP stands for Voice Over Internet Protocol, a communications protocol that allows for telephonic communication via the Internet.
A guide to GOOGLE+LOCAL. for business. Published by. hypercube.co.nz
 A guide to GOOGLE+LOCAL for business Published by hypercube.co.nz An introduction You have probably noticed that since June 2012, changes have been taking place with the local search results appearing
A guide to GOOGLE+LOCAL for business Published by hypercube.co.nz An introduction You have probably noticed that since June 2012, changes have been taking place with the local search results appearing
Internet Applications. Q. What is Internet Explorer? Explain features of Internet Explorer.
 Internet Applications Q. What is Internet Explorer? Explain features of Internet Explorer. Internet explorer: Microsoft Internet Explorer is a computer program called a browser that helps you interact
Internet Applications Q. What is Internet Explorer? Explain features of Internet Explorer. Internet explorer: Microsoft Internet Explorer is a computer program called a browser that helps you interact
Internet Basics. Basic Terms and Concepts. Connecting to the Internet
 Internet Basics In this Learning Unit, we are going to explore the fascinating and ever-changing world of the Internet. The Internet is the largest computer network in the world, connecting more than a
Internet Basics In this Learning Unit, we are going to explore the fascinating and ever-changing world of the Internet. The Internet is the largest computer network in the world, connecting more than a
I Shopping on mobile / RU
 I Shopping on mobile / RU Exploring how people use their smartphones for shopping activities Q3 2016 I About this study Background: Objective: Mobile apps and sites are a vital channel for advertisers
I Shopping on mobile / RU Exploring how people use their smartphones for shopping activities Q3 2016 I About this study Background: Objective: Mobile apps and sites are a vital channel for advertisers
Social Media E-Safety Guide. For more help and advice visit:
 Social Media E-Safety Guide For more help and advice visit: https://www.net-aware.org.uk/ https://www.thinkuknow.co.uk/ https://www.ceop.police.uk/ Twitter https://www.net-aware.org.uk/networks/twitter/
Social Media E-Safety Guide For more help and advice visit: https://www.net-aware.org.uk/ https://www.thinkuknow.co.uk/ https://www.ceop.police.uk/ Twitter https://www.net-aware.org.uk/networks/twitter/
Iphone Setting Privacy Microphone Viber Set To On >>>CLICK HERE<<<
 Iphone Setting Privacy Microphone Viber Set To On In privacy setting i don't find facetime accessing microphone. iphone 4S Again while using viber, if I set it to loud speaker, rare end doesn't hear my
Iphone Setting Privacy Microphone Viber Set To On In privacy setting i don't find facetime accessing microphone. iphone 4S Again while using viber, if I set it to loud speaker, rare end doesn't hear my
CANVAS OBSERVER GUIDE
 CANVAS OBSERVER GUIDE This work is licensed under a Creative Commons Attribution-NonCommercial-ShareAlike License Table of Contents Introduction...3 What is the Observer role?...4 How can I use Canvas
CANVAS OBSERVER GUIDE This work is licensed under a Creative Commons Attribution-NonCommercial-ShareAlike License Table of Contents Introduction...3 What is the Observer role?...4 How can I use Canvas
ETSY.COM - PRIVACY POLICY
 At Etsy, we value our community. You trust us with your information, and we re serious about that responsibility. We believe in transparency, and we re committed to being upfront about our privacy practices,
At Etsy, we value our community. You trust us with your information, and we re serious about that responsibility. We believe in transparency, and we re committed to being upfront about our privacy practices,
ASTE 2016 Ning Network access our Ning on a mobile device, browsers FREE should NOT To join the ASTE 2016 Ning
 ASTE 2016 Ning Network Ning is a social networking site where groups of people can interact in a number of ways, including forums, photos, videos, and other options as the site expands. Ning also uses
ASTE 2016 Ning Network Ning is a social networking site where groups of people can interact in a number of ways, including forums, photos, videos, and other options as the site expands. Ning also uses
McAfee Family Protection The Easiest, Most Complete Way to Keep Your Children Safe Online
 The Easiest, Most Complete Way to Keep Your Children Safe Online 1 Quick Start Easy Installation STEP 1: First, ensure that your computer meets or exceeds the minimum systems requirements listed below.
The Easiest, Most Complete Way to Keep Your Children Safe Online 1 Quick Start Easy Installation STEP 1: First, ensure that your computer meets or exceeds the minimum systems requirements listed below.
ELECTRIC APP - PRIVACY POLICY
 By accessing the website at http://electricchats.com ( Electric Site ) or any Electric mobile application (e.g., Electric ios, or Electric Android,) ( Electric App ) (collectively, the Electric Service
By accessing the website at http://electricchats.com ( Electric Site ) or any Electric mobile application (e.g., Electric ios, or Electric Android,) ( Electric App ) (collectively, the Electric Service
Advertising Network Affiliate Marketing Algorithm Analytics Auto responder autoresponder Backlinks Blog
 Advertising Network A group of websites where one advertiser controls all or a portion of the ads for all sites. A common example is the Google Search Network, which includes AOL, Amazon,Ask.com (formerly
Advertising Network A group of websites where one advertiser controls all or a portion of the ads for all sites. A common example is the Google Search Network, which includes AOL, Amazon,Ask.com (formerly
DoConference Web Conferencing: DoMore DoConference
 DoConference Web Conferencing: DoMore DoConference Use DoConference Conferencing for: Training and E-Learning Deliver interactive online classes, E-Learning sessions and educate easily and affordably.
DoConference Web Conferencing: DoMore DoConference Use DoConference Conferencing for: Training and E-Learning Deliver interactive online classes, E-Learning sessions and educate easily and affordably.
Social Media Tools. March 13, 2010 Presented by: Noble Studios, Inc.
 March 13, 2010 Presented by: Noble Studios, Inc. 1 Communication Timeline 2 Familiar Social Media Sites According to Facebook, more than 1.5 million local businesses have active pages on Facebook According
March 13, 2010 Presented by: Noble Studios, Inc. 1 Communication Timeline 2 Familiar Social Media Sites According to Facebook, more than 1.5 million local businesses have active pages on Facebook According
WHITE PAPER THE SOCIAL MEDIA FRAUD REVOLUTION A STUDY OF THE EXPANSION OF CYBERCRIME TO NEW PLATFORMS
 WHITE PAPER THE SOCIAL MEDIA FRAUD REVOLUTION A STUDY OF THE EXPANSION OF CYBERCRIME TO NEW PLATFORMS Social media platforms have become one of the most visible and fastestgrowing technologies in the last
WHITE PAPER THE SOCIAL MEDIA FRAUD REVOLUTION A STUDY OF THE EXPANSION OF CYBERCRIME TO NEW PLATFORMS Social media platforms have become one of the most visible and fastestgrowing technologies in the last
Facebook Basics. Agenda:
 Basics Agenda: 1. Introduction 2. The evolution of Facebook 3. Your profile 4. Finding friends 5. Saving and sharing 6. Chat and messages 7. Facebook privacy 8. Practice, Questions, Evaluation In order
Basics Agenda: 1. Introduction 2. The evolution of Facebook 3. Your profile 4. Finding friends 5. Saving and sharing 6. Chat and messages 7. Facebook privacy 8. Practice, Questions, Evaluation In order
Social Media Reputation Management
 Social Media Reputation Management If you are using social media sites such as Facebook or Twitter, there are some simple steps you can take to manage your reputation and protect your identity. Even if
Social Media Reputation Management If you are using social media sites such as Facebook or Twitter, there are some simple steps you can take to manage your reputation and protect your identity. Even if
Safety and Security in a Digital Age. South Carolina Bar Convention Family Law Section January 22, 2010
 Safety and Security in a Digital Age South Carolina Bar Convention Family Law Section January 22, 2010 Melissa F. Brown Melissa F. Brown, LLC 145 King Street, Suite 405 Charleston, SC 29401 843.722.8900
Safety and Security in a Digital Age South Carolina Bar Convention Family Law Section January 22, 2010 Melissa F. Brown Melissa F. Brown, LLC 145 King Street, Suite 405 Charleston, SC 29401 843.722.8900
Computers Are Your Future
 Computers Are Your Future Computers Are Your Future The Internet and World Wide Web 2006 Prentice-Hall, Inc. Slide 2 What You Will Learn... What You Will Learn... How the Internet works Methods for accessing
Computers Are Your Future Computers Are Your Future The Internet and World Wide Web 2006 Prentice-Hall, Inc. Slide 2 What You Will Learn... What You Will Learn... How the Internet works Methods for accessing
Verizon Family Protection Powered by McAfee. User Guide
 Verizon Family Protection Powered by McAfee User Guide ii Contents Welcome to Verizon Family Protection Powered by McAfee User Guide 3 Setting up Family Protection 5 Activating your software...6 Activate
Verizon Family Protection Powered by McAfee User Guide ii Contents Welcome to Verizon Family Protection Powered by McAfee User Guide 3 Setting up Family Protection 5 Activating your software...6 Activate
I Shopping on mobile / KSA
 I Shopping on mobile / KSA Exploring how people use their smartphones for shopping activities Q3 2016 I About this study Background: Objective: Mobile apps and sites are a vital channel for advertisers
I Shopping on mobile / KSA Exploring how people use their smartphones for shopping activities Q3 2016 I About this study Background: Objective: Mobile apps and sites are a vital channel for advertisers
Computer networks 2013
 Chapter 4 EXERCISE 1 1 Describe what is meant by each of the following: a Router b Bridge c Proxy server Answers: see the Glossary. 2 Many small businesses have computer networks. a List three advantages
Chapter 4 EXERCISE 1 1 Describe what is meant by each of the following: a Router b Bridge c Proxy server Answers: see the Glossary. 2 Many small businesses have computer networks. a List three advantages
Social Media Tip and Tricks
 Social Media Tip and Tricks Hey 2016 CCP attendees! The Technology Council has put together social media tips and tricks to support your CCP process. Social media and other online tools can be great resources
Social Media Tip and Tricks Hey 2016 CCP attendees! The Technology Council has put together social media tips and tricks to support your CCP process. Social media and other online tools can be great resources
Ambiguity Handling in Mobile-capable Social Networks
 Ambiguity Handling in Mobile-capable Social Networks Péter Ekler Department of Automation and Applied Informatics Budapest University of Technology and Economics peter.ekler@aut.bme.hu Abstract. Today
Ambiguity Handling in Mobile-capable Social Networks Péter Ekler Department of Automation and Applied Informatics Budapest University of Technology and Economics peter.ekler@aut.bme.hu Abstract. Today
STUDENT ICT ACCEPTABLE USE POLICY
 The Olive School, Blackburn This policy is in line with the Mission Statement of the School To promote a culture of educational excellence, from within a caring and secure Islamic environment enriched
The Olive School, Blackburn This policy is in line with the Mission Statement of the School To promote a culture of educational excellence, from within a caring and secure Islamic environment enriched
Chapter 002 The Internet, the Web, and Electronic Commerce
 Chapter 002 The Internet, the Web, and Electronic Commerce Multiple Choice Questions 1. Launched in 1969 as a U.S. funded project that developed a national computer network, the Internet was initially
Chapter 002 The Internet, the Web, and Electronic Commerce Multiple Choice Questions 1. Launched in 1969 as a U.S. funded project that developed a national computer network, the Internet was initially
Discovering Computers Chapter 2 The Internet and World Wide Web
 Discovering Computers 2009 Chapter 2 The Internet and World Wide Web Chapter 2 Objectives Discuss the history of the Internet Describe the types of Web sites Explain how to access and connect to the Internet
Discovering Computers 2009 Chapter 2 The Internet and World Wide Web Chapter 2 Objectives Discuss the history of the Internet Describe the types of Web sites Explain how to access and connect to the Internet
TELSTRA TECH SAVVY SENIORS - BEGINNERS GUIDE INTRODUCTION TO SOCIAL MEDIA - PART 1
 TOPIC: INTRODUCTION TO SOCIAL MEDIA PART 1 WHAT TO USE AND WHEN The internet helps you stay in touch with friends and loved ones. Social media sites like Facebook and Twitter let you see what s happening
TOPIC: INTRODUCTION TO SOCIAL MEDIA PART 1 WHAT TO USE AND WHEN The internet helps you stay in touch with friends and loved ones. Social media sites like Facebook and Twitter let you see what s happening
Getting Started: Log on or Create Account
 Getting Started: Log on or Create Account Sign into CD To begin, on the right side of the top menu below the Search box, click Log In. The Log in to CD page appears. This page allows you to create an account,
Getting Started: Log on or Create Account Sign into CD To begin, on the right side of the top menu below the Search box, click Log In. The Log in to CD page appears. This page allows you to create an account,
INTERNET SAFETY* GALEN GARRETSON RASCAL MARCH 2-3, * Sources include learnfree.org, PC World, wikpedia.com, techterms.com
 INTERNET SAFETY* GALEN GARRETSON RASCAL MARCH 2-3, 2016 * Sources include learnfree.org, PC World, wikpedia.com, techterms.com SOME QUESTIONS TO ASK YOURSELF. HAVE YOU.. 1. Googled yourself to see what
INTERNET SAFETY* GALEN GARRETSON RASCAL MARCH 2-3, 2016 * Sources include learnfree.org, PC World, wikpedia.com, techterms.com SOME QUESTIONS TO ASK YOURSELF. HAVE YOU.. 1. Googled yourself to see what
Technology Safety Quick Tips
 Technology Safety Quick Tips Spyware: Computer & Phone Monitoring Software It enables a person to secretly monitor someone else s entire computer activity. It can be installed remotely by sending an email,
Technology Safety Quick Tips Spyware: Computer & Phone Monitoring Software It enables a person to secretly monitor someone else s entire computer activity. It can be installed remotely by sending an email,
Online Communication. Chat Rooms Instant Messaging Blogging Social Media
 Online Communication E-mail Chat Rooms Instant Messaging Blogging Social Media { Advantages: { Reduces cost of postage Fast and convenient Need an email address to sign up for other online accounts. Eliminates
Online Communication E-mail Chat Rooms Instant Messaging Blogging Social Media { Advantages: { Reduces cost of postage Fast and convenient Need an email address to sign up for other online accounts. Eliminates
Chapter 2 The Internet and World Wide Web
 Chapter 2 The Internet and World Wide Web Chapter 2 Objectives Explain how to access and connect to the Internet Explain how to view pages and search for information on the Web Describe the types of Web
Chapter 2 The Internet and World Wide Web Chapter 2 Objectives Explain how to access and connect to the Internet Explain how to view pages and search for information on the Web Describe the types of Web
Facebook Tutorial. An Introduction to Today s Most Popular Online Community
 Facebook Tutorial An Introduction to Today s Most Popular Online Community Introduction to Facebook Facebook is the most popular social network, in the U.S. and internationally. In October 2011, more than
Facebook Tutorial An Introduction to Today s Most Popular Online Community Introduction to Facebook Facebook is the most popular social network, in the U.S. and internationally. In October 2011, more than
Everyday Digital Skills Projects Plus skills learned through the project
 Everyday Digital Skills Projects Plus skills learned through the project Embedded ICT skills printed on the back of each project. Compiled by Digital Learning Futures for NG Media Hints and tips Apps or
Everyday Digital Skills Projects Plus skills learned through the project Embedded ICT skills printed on the back of each project. Compiled by Digital Learning Futures for NG Media Hints and tips Apps or
PUPIL ICT ACCEPTABLE USE POLICY
 PUPIL ICT ACCEPTABLE USE POLICY Document control This document has been approved for operation within: All Trust Schools Date of last review August 2018 Date of next review August 2020 Review period Status
PUPIL ICT ACCEPTABLE USE POLICY Document control This document has been approved for operation within: All Trust Schools Date of last review August 2018 Date of next review August 2020 Review period Status
Verizon Family Protection Powered by McAfee. User Guide
 Verizon Family Protection Powered by McAfee User Guide ii Contents Welcome to Verizon Family Protection Powered by McAfee User Guide 3 Setting up Family Protection 5 Activating your software... 6 Activate
Verizon Family Protection Powered by McAfee User Guide ii Contents Welcome to Verizon Family Protection Powered by McAfee User Guide 3 Setting up Family Protection 5 Activating your software... 6 Activate
INTRODUCTION TO SOCIAL MEDIA Part 1
 TECH SAVVY SENIORS The NSW Tech Savvy Seniors program is a key initiative of the NSW Ageing Strategy and the Telstra Digital Literacy Strategy. Victorian Tech Savvy Seniors is a Seniors Card Age Friendly
TECH SAVVY SENIORS The NSW Tech Savvy Seniors program is a key initiative of the NSW Ageing Strategy and the Telstra Digital Literacy Strategy. Victorian Tech Savvy Seniors is a Seniors Card Age Friendly
Introduction to
 Introduction to Email gcflearnfree.org/print/email101/introduction-to-email Introduction Do you ever feel like the only person who doesn't use email? You don't have to feel left out. If you're just getting
Introduction to Email gcflearnfree.org/print/email101/introduction-to-email Introduction Do you ever feel like the only person who doesn't use email? You don't have to feel left out. If you're just getting
Lesson 17: Your Life Online
 Living Online Lesson 17: Your Life Online Lesson Objectives In this lesson, you will learn about your online identity and how to protect it. You will also learn about the adverse effects prolonged computing
Living Online Lesson 17: Your Life Online Lesson Objectives In this lesson, you will learn about your online identity and how to protect it. You will also learn about the adverse effects prolonged computing
The Internet and World Wide Web
 1 Chapter 2 The Internet and World Wide Web 2 Chapter 2 Objectives 3 The Internet What are some services found on the Internet? 4 History of the Internet How did the Internet originate? 5 History of the
1 Chapter 2 The Internet and World Wide Web 2 Chapter 2 Objectives 3 The Internet What are some services found on the Internet? 4 History of the Internet How did the Internet originate? 5 History of the
Getting to know your ipad exploring the settings, App store, Mail
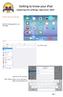 Getting to know your ipad exploring the settings, App store, Mail Exploring the settings Open the settings app from your homepage Wi-Fi Turn Wi-Fi on/off Add new Wi-Fi Connection Enter Network Name, any
Getting to know your ipad exploring the settings, App store, Mail Exploring the settings Open the settings app from your homepage Wi-Fi Turn Wi-Fi on/off Add new Wi-Fi Connection Enter Network Name, any
The Essential Guide to VIRTUAL TEAM. Building Tools
 The Essential Guide to VIRTUAL TEAM Building Tools The Essential Guide to Virtual Team Building Tools By Chris Ducker Thank you for checking out this guide on all my personal favourite tools and resources
The Essential Guide to VIRTUAL TEAM Building Tools The Essential Guide to Virtual Team Building Tools By Chris Ducker Thank you for checking out this guide on all my personal favourite tools and resources
ONLINE SAFETY. Messaging, , Vlogging and Sexting
 ONLINE SAFETY Messaging, email, Vlogging and Sexting www.eitts.co.uk Contents WhatsApp & Messaging Email Vlogging Sexting THE RISKS People online are not necessarily who they say they are or seem to be.
ONLINE SAFETY Messaging, email, Vlogging and Sexting www.eitts.co.uk Contents WhatsApp & Messaging Email Vlogging Sexting THE RISKS People online are not necessarily who they say they are or seem to be.
VIEWING AND/OR USE AND/OR COMMUNICATION IS CONSTRUED AS ACCEPTANCE OF THE TERMS OF THIS POLICY
 PRIVACY POLICY Last Modified: September 11, 2017 PERSONS OR PARTIES COVERED This Privacy Policy is intended to cover all visitors to this website, all subscribers to lists or newsletters associated with
PRIVACY POLICY Last Modified: September 11, 2017 PERSONS OR PARTIES COVERED This Privacy Policy is intended to cover all visitors to this website, all subscribers to lists or newsletters associated with
Edmodo for Teachers Guide (Taken directly from Edmodo s site.)
 Edmodo for Teachers Guide (Taken directly from Edmodo s site.) Table of Contents: 1. Teacher Sign Up 2. Create a Group 3. Manage Your Groups 4. Small Group 5. Co-Teaching 6. Student Sign up 7. Post a Message
Edmodo for Teachers Guide (Taken directly from Edmodo s site.) Table of Contents: 1. Teacher Sign Up 2. Create a Group 3. Manage Your Groups 4. Small Group 5. Co-Teaching 6. Student Sign up 7. Post a Message
AAG Mobile App User Manual
 AAG Mobile App User Manual Tired of carrying a large printed program around the AAG Annual Meeting? Want to easily organize your AAG session schedule in a digital calendar format? Looking to save some
AAG Mobile App User Manual Tired of carrying a large printed program around the AAG Annual Meeting? Want to easily organize your AAG session schedule in a digital calendar format? Looking to save some
Typical Investigative Steps and Traveler cases
 Typical Investigative Steps and Traveler cases Thomas K. Clancy copyright, Thomas K. Clancy, all rights reserved, 2012. "inside the box, outside the box" Outside the box The Box Sender (AOL) obtaining
Typical Investigative Steps and Traveler cases Thomas K. Clancy copyright, Thomas K. Clancy, all rights reserved, 2012. "inside the box, outside the box" Outside the box The Box Sender (AOL) obtaining
Internet. Class-In charge: S.Sasirekha
 Internet Class-In charge: S.Sasirekha COMPUTER NETWORK A computer network is a collection of two or more computers, which are connected together to share information and resources. Network Operating Systems
Internet Class-In charge: S.Sasirekha COMPUTER NETWORK A computer network is a collection of two or more computers, which are connected together to share information and resources. Network Operating Systems
Introduction to Skype
 http://www.gerrykruyer.com Social Media, Internet & E-mail: Topic 7 Skype This lesson is an introduction to Skype. Introduction to Skype Of all of the Internet tools available today, Skype is probably
http://www.gerrykruyer.com Social Media, Internet & E-mail: Topic 7 Skype This lesson is an introduction to Skype. Introduction to Skype Of all of the Internet tools available today, Skype is probably
Profile and Settings
 Profile and Settings 1 Account Dashboard: An Overview p6 p19 p10 p4 p5 p18 2 Past and Upcoming Conferences Click on Past on your dashboard to view your call history for the last 30 days. Click on Upcoming
Profile and Settings 1 Account Dashboard: An Overview p6 p19 p10 p4 p5 p18 2 Past and Upcoming Conferences Click on Past on your dashboard to view your call history for the last 30 days. Click on Upcoming
How to Create and Use a Skype Account
 How to Create and Use a Skype Account Step 1: Go to www.skype.com You will need an email address to create your Skype account Step 2: At the top, right corner, there will be a place to click Get Skype
How to Create and Use a Skype Account Step 1: Go to www.skype.com You will need an email address to create your Skype account Step 2: At the top, right corner, there will be a place to click Get Skype
GETTING STARTED WITH THE SDLAP NING
 GETTING STARTED WITH THE SDLAP NING A resource for the participants in Richmond s Self-Directed Language Acquisition Program is The SDLAP Ning (http://sdlapur.ning.com). Participants use the blogging function
GETTING STARTED WITH THE SDLAP NING A resource for the participants in Richmond s Self-Directed Language Acquisition Program is The SDLAP Ning (http://sdlapur.ning.com). Participants use the blogging function
Facebook Page Insights
 Facebook Product Guide for Facebook Page owners Businesses will be better in a connected world. That s why we connect 845M people and their friends to the things they care about, using social technologies
Facebook Product Guide for Facebook Page owners Businesses will be better in a connected world. That s why we connect 845M people and their friends to the things they care about, using social technologies
Facebook Guide. How many Facebook friends should I have?
 To Friend or Not to Friend How many Facebook friends should I have? Facebook is a great way to stay in connected with your friends when you are not in direct contact with them. As soon as you add a friend
To Friend or Not to Friend How many Facebook friends should I have? Facebook is a great way to stay in connected with your friends when you are not in direct contact with them. As soon as you add a friend
Dugan's Travels. Agent Website. User Guide
 Dugan's Travels Agent Website User Guide Lundy Innovations Ken Lundy, Sr. v1.2 1 v1.6 Table of Content Website Overview.................................................................... 3 Home Page -
Dugan's Travels Agent Website User Guide Lundy Innovations Ken Lundy, Sr. v1.2 1 v1.6 Table of Content Website Overview.................................................................... 3 Home Page -
Collaborate App for Android Smartphones
 Collaborate App for Android Smartphones The AT&T Collaborate service provides the Collaborate app to help you manage calls and conferences on the go. The app comes in 3 versions: Collaborate - Mobile Collaborate
Collaborate App for Android Smartphones The AT&T Collaborate service provides the Collaborate app to help you manage calls and conferences on the go. The app comes in 3 versions: Collaborate - Mobile Collaborate
Parks Industries LLC Privacy Policy
 Parks Industries LLC Privacy Policy We collect the following types of information about you: Information you provide us directly: We ask for certain information such as your username, real name, birthdate,
Parks Industries LLC Privacy Policy We collect the following types of information about you: Information you provide us directly: We ask for certain information such as your username, real name, birthdate,
WYNN SOCIAL CASINO PRIVACY POLICY
 WYNN SOCIAL CASINO PRIVACY POLICY This privacy policy for the Wynn Slots App ( App ), made available by Wynn Social Gaming, LLC ( Wynn Social, Us, We, or Our ), describes our privacy practices (the "Privacy
WYNN SOCIAL CASINO PRIVACY POLICY This privacy policy for the Wynn Slots App ( App ), made available by Wynn Social Gaming, LLC ( Wynn Social, Us, We, or Our ), describes our privacy practices (the "Privacy
How App Ratings and Reviews Impact Rank on Google Play and the App Store
 APP STORE OPTIMIZATION MASTERCLASS How App Ratings and Reviews Impact Rank on Google Play and the App Store BIG APPS GET BIG RATINGS 13,927 AVERAGE NUMBER OF RATINGS FOR TOP-RATED IOS APPS 196,833 AVERAGE
APP STORE OPTIMIZATION MASTERCLASS How App Ratings and Reviews Impact Rank on Google Play and the App Store BIG APPS GET BIG RATINGS 13,927 AVERAGE NUMBER OF RATINGS FOR TOP-RATED IOS APPS 196,833 AVERAGE
37 FAQs ABOUT CELLCONTROL ASKED BY PARENTS OF NEW DRIVERS
 37 FAQs ABOUT CELLCONTROL ASKED BY PARENTS OF NEW DRIVERS TABLE OF CONTENTS INTRODUCTION 3 QUESTIONS BEFORE YOU BUY 4 USING CELLCONTROL 9 iphone-specific QUESTIONS 14 ANDROID AND WINDOWS PHONE-SPECIFIC
37 FAQs ABOUT CELLCONTROL ASKED BY PARENTS OF NEW DRIVERS TABLE OF CONTENTS INTRODUCTION 3 QUESTIONS BEFORE YOU BUY 4 USING CELLCONTROL 9 iphone-specific QUESTIONS 14 ANDROID AND WINDOWS PHONE-SPECIFIC
