Picture to . How-To: ROBIN Tech Note. Version: ENG Datum:
|
|
|
- Suzan Snow
- 6 years ago
- Views:
Transcription
1 ROBIN Tech Note Version: ENG Datum: How-To: Picture to
2 gf2 About this Tech Note This Tech Note is meant for the following Robin products: C C03058 : Proline SV C C03074 : Proline Classic SV C C02058 : Compact SV Software release and higher
3 Picture to gf3 Picture to feature enables the Robin SV to a picture of the visitor to an address defined for that particular button or preset. The Robin SV utilizes its build-in High-Defenition camera to take the picture the moment a person pressed the call button. This document explains how to configure Picture to in the WebGui of the Robin SV.! Note 1: To make use of the Picture To feature, the Robin SV must have a connection to the Internet or to a network with access to an server.!! Note 2: The use of Picture to may be subject to national privacy regulations that vary from country to country. Please consult your relevant Local Administration for instructions on how to deploy the Picture to feature.!
4 gf4 Configuration steps To enable the Picture to feature, the following configuration steps need to be followed: 1. Configuring of the settings 2. Adding the addresses 3. Testing the settings 4. Configuring of the Event mechanism 5. Selecting addresses per button or Preset 6. Testing of the Picture to feature
5 gf5 1. Configuring of the settings The Robin SV needs to be able to connect to an existing server. This can be a local server or an server from an ISP (Internet Service Provider). The following information is required: A From- name (the address that the Robin SV uses to send the s from) The Domain name or the IP address of the server Does the server need encryption or not? -> Type of encryption, username & password Advanced settings: Does the server use Submission / TCP port 587? Go to the menu -Network-Mail- The green + creates a new line. The >> behind a line opens the details for this line. The red X behind a line deletes the line from the list. From address Mail server Encryption Auth Submission Set the from address of the Robin Enter the server address or hostname Select a encryption method (none, SSL, TLS) Select this option if mail server authentication is required Select this option if the mail server uses the Submission protocol / TCP port 587
6 gf6 2. Adding the addresses The Picture to feature can send s to different destinations, depending on the model Robin SV used. A Robin SV 1, 2, 4 or 6 can be configured with one address per button. The Robin SV with Keypad works with Presets that can be dialed using the Keypad. Every Preset can be configured with an address. The addresses need to be defined before they can be attached to a button or preset. To do this, go to the menu -Network-Mail-, section Address book and click Add Recipient. The green + creates a new line. The >> behind a line opens the details for this line. The red X behind a line deletes the line from the list. Name Address The name that is associated with this address The address
7 gf7 3. Testing the settings After configuration of the mail server settings and adding of the addresses, we recommend testing them before proceeding with the Picture to configuration. Tests the connection with the configured server. Select the address to send the test to and click on the button Test SMTP server. If the configuration of the server settings was successful, a test should arrive at the selected address. To Test SMTP server SMTP test result Select a recipient for the test message Initiates the test message Shows the test result
8 gf8 4. Configuring of the Event mechanism The Picture to feature depends on an event: the push of a button on the Robin SV with buttons or the dialing of a preset on the Robin SV with Keypad. When such an event occurs, an Action needs to start: take a picture and send it to its designated address. To configure this event, go to the menu -System-Events- The green + creates a new line. The >> behind a line opens the details for this line. The red X behind a line deletes the line from the list. Add a source Select as Source type Button
9 gf9 Select the button that will trigger the Picture to . 1 to 6-> Button one to six. Select Keypad when using a Robin SV Keypad. Provide a descriptive name for this Source, in this example Button Apply settings Add an Action Select as Action type Picture2
10 gf10 Select as Source type the just added source Button Set the Edge to Rising Provide a descriptive name for this Action, in this example Pic2 By default, the will be send to the address configured at the buttons or presets (see next step). It is possible to select a different address for an action by unchecking the Send to default address for this button checkbox. A drop-down menu with all configured addresses appears. Select the designation to send the s to. Apply settings! Note: When using a Robin SV with 1, 2, 4 or 6 buttons, you ll need to create a Source and an Action for every button where Picture to is required.!
11 gf11 5. Selecting addresses per button or Preset You can configure one address for each button on a Robin SV with 1, 2, 4 or 6 buttons. A Robin SV with Keypad doesn t have fixed call buttons, but instead works with Presets. Every Preset can contain one address. To define addresses for one or more buttons, go to the menu -Telephony-Call settings- At Call priority - , select the address to use. Do this for each button when using a Robin SV 2, 4 or 6. To define addresses for one or more Presets (when using a Robin SV Keypad), go to the menu -Telephony-Phonebook- When creating a new Preset or modifying an existing Preset, select the address to use for that Preset at .
12 gf12 6. Testing of the Picture to feature When the configuration is finished, the only thing left to do is to test the Picture to feature. Go to the Robin SV and press on the button to test (on the Robin SV with 1, 2, 4 or 6 buttons) or enter the Preset (on the Robin SV with Keypad). A picture should now be sent to the defined address. You can check the logfile in the menu -System-Log- to see if the was sent successfully.
Use the Robin Peer-to-Peer - Grandstream. How-To: ROBIN Tech Note. Version: ENG Datum:
 ROBIN Tech Note Version: 1.0.2 ENG Datum: 7-06-2018 How-To: Use the Robin Peer-to-Peer - Grandstream gf2 About this Tech Note This Tech Note is meant for the following Robin products:: C03060 - C03067
ROBIN Tech Note Version: 1.0.2 ENG Datum: 7-06-2018 How-To: Use the Robin Peer-to-Peer - Grandstream gf2 About this Tech Note This Tech Note is meant for the following Robin products:: C03060 - C03067
Connect the Robin to MS Lync. How-To: ROBIN Tech Note. Version: ENG Datum:
 ROBIN Tech Note Version: 1.0.3 ENG Datum: 7-06-2018 How-To: Connect the Robin to MS Lync gf2 About this Tech Note This Tech Note is meant for the following Robin products:: C03060 - C03067 : Proline SIP
ROBIN Tech Note Version: 1.0.3 ENG Datum: 7-06-2018 How-To: Connect the Robin to MS Lync gf2 About this Tech Note This Tech Note is meant for the following Robin products:: C03060 - C03067 : Proline SIP
Use the Robin Peer-to-Peer - Bria3-mobile. How-To: ROBIN Tech Note. Version: ENG Datum:
 ROBIN Tech Note Version: 1.0.3 ENG Datum: 7-06-2018 How-To: Use the Robin Peer-to-Peer - Bria3-mobile About this Tech Note gf2 This Tech Note is meant for the following Robin products: C03060 - C03067
ROBIN Tech Note Version: 1.0.3 ENG Datum: 7-06-2018 How-To: Use the Robin Peer-to-Peer - Bria3-mobile About this Tech Note gf2 This Tech Note is meant for the following Robin products: C03060 - C03067
Configure Settings and Customize Notifications on FindIT Network Probe
 Configure Email Settings and Customize Email Notifications on FindIT Network Probe Objective Cisco FindIT Network Probe equips a network administrator with indispensable tools that help securely monitor
Configure Email Settings and Customize Email Notifications on FindIT Network Probe Objective Cisco FindIT Network Probe equips a network administrator with indispensable tools that help securely monitor
Grandstream Networks, Inc. Robin SmartView IP Door System & Grandstream IP Multimedia Phones Configuration Guide
 Grandstream Networks, Inc. Robin SmartView IP Door System & Grandstream IP Multimedia Phones Configuration Guide TABLE OF CONTENTS ROBIN SMARTVIEW IP DOOR SYSTEM & GRANDSTREAM IP MULTIMEDIA PHONES CONFIGURATION
Grandstream Networks, Inc. Robin SmartView IP Door System & Grandstream IP Multimedia Phones Configuration Guide TABLE OF CONTENTS ROBIN SMARTVIEW IP DOOR SYSTEM & GRANDSTREAM IP MULTIMEDIA PHONES CONFIGURATION
Adding your IMAP Mail Account in Outlook 2013 on Windows
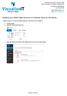 Adding your IMAP Mail Account in Outlook 2013 on Windows Replace example.co.za with your domain name as it was sent to you by Visualize IT 1. Launch Outlook 2. Select File on the top left menu bar 3. Select
Adding your IMAP Mail Account in Outlook 2013 on Windows Replace example.co.za with your domain name as it was sent to you by Visualize IT 1. Launch Outlook 2. Select File on the top left menu bar 3. Select
Scan-to- . Copytech s guide to setting up Scan-to- on Konica Minolta M FDs
 Scan-to-Email Copytech s guide to setting up Scan-to- Email on Konica Minolta MFDs Time required for set up: Approximately 20 minutes Engineer required: No Copytech s guide to setting up Scan-to-Email
Scan-to-Email Copytech s guide to setting up Scan-to- Email on Konica Minolta MFDs Time required for set up: Approximately 20 minutes Engineer required: No Copytech s guide to setting up Scan-to-Email
Configuring SSL. SSL Overview CHAPTER
 7 CHAPTER This topic describes the steps required to configure your ACE appliance as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination. The topics included in this section are:
7 CHAPTER This topic describes the steps required to configure your ACE appliance as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination. The topics included in this section are:
To Setup your Business id in MacOS X El Capitan Mail (POP) To find MacOS version please visit: Apple Support macos version
 To Setup your Business email id in MacOS X El Capitan Mail (POP) To find MacOS version please visit: Apple Support macos version Depending on your MAC OS version, your screens may appear a bit different,
To Setup your Business email id in MacOS X El Capitan Mail (POP) To find MacOS version please visit: Apple Support macos version Depending on your MAC OS version, your screens may appear a bit different,
To Setup your Business id in MacOS X El Capitan Mail (POP) To find MacOS version please visit: Apple Support macos version
 To Setup your Business email id in MacOS X El Capitan Mail (POP) To find MacOS version please visit: Apple Support macos version Depending on your MAC OS version, your screens may appear a bit different,
To Setup your Business email id in MacOS X El Capitan Mail (POP) To find MacOS version please visit: Apple Support macos version Depending on your MAC OS version, your screens may appear a bit different,
Set Up with Microsoft Outlook 2013 using POP3
 Page 1 of 14 Help Center Set Up E-mail with Microsoft Outlook 2013 using POP3 Learn how to configure Microsoft Outlook 2013 for use with your 1&1 e-mail account using the POP3 Protocol. Before you begin,
Page 1 of 14 Help Center Set Up E-mail with Microsoft Outlook 2013 using POP3 Learn how to configure Microsoft Outlook 2013 for use with your 1&1 e-mail account using the POP3 Protocol. Before you begin,
Scan to Quick Setup Guide
 Xerox WorkCentre M118i Scan to E-mail Quick Setup Guide 701P42574 This guide provides a quick reference for setting up the Scan to E-mail feature on the Xerox WorkCentre M118i. It includes procedures for:
Xerox WorkCentre M118i Scan to E-mail Quick Setup Guide 701P42574 This guide provides a quick reference for setting up the Scan to E-mail feature on the Xerox WorkCentre M118i. It includes procedures for:
Send Setting Guide ATTENTION
 Send Setting Guide This guide explains how to set up the Send to E-mail and Store to Shared Folder functions using the Send Function Setting Tool, and how to check if the functions are set properly by
Send Setting Guide This guide explains how to set up the Send to E-mail and Store to Shared Folder functions using the Send Function Setting Tool, and how to check if the functions are set properly by
Orbital provide a secure (SSL) Mailserver to protect your privacy and accounts.
 Email Configuration This document is designed to help our clients in setting up email accounts on popular devices and email client software. Orbital provide a secure (SSL) Mailserver to protect your privacy
Email Configuration This document is designed to help our clients in setting up email accounts on popular devices and email client software. Orbital provide a secure (SSL) Mailserver to protect your privacy
Configuring an IMAP4 or POP3 Journal Account for Microsoft Exchange Server 2003
 Configuring an IMAP4 or POP3 Journal Account for Microsoft Exchange Server 2003 This article refers to Microsoft Exchange Server 2003. As of April 8, 2014, Microsoft no longer issues security updates for
Configuring an IMAP4 or POP3 Journal Account for Microsoft Exchange Server 2003 This article refers to Microsoft Exchange Server 2003. As of April 8, 2014, Microsoft no longer issues security updates for
Oracle Connector for Outlook Clinic Version
 Oracle Connector for Outlook Clinic Version 9.0426 2 Required Information: 1. Your name:. 2. Your Kerberos Principle (username/e-mail):. 3. Your e-mail address:. 4. Your post office server po.mit.edu (i.e.
Oracle Connector for Outlook Clinic Version 9.0426 2 Required Information: 1. Your name:. 2. Your Kerberos Principle (username/e-mail):. 3. Your e-mail address:. 4. Your post office server po.mit.edu (i.e.
Dualog Connection Suite LDAP Server. User Manual and Configuration Guide
 Dualog Connection Suite LDAP Server User Manual and Configuration Guide Author Vidar Berg Date 10.Nov 2010 Description Revision Number User manual for setting up and maintaining the Dualog Connection Suite
Dualog Connection Suite LDAP Server User Manual and Configuration Guide Author Vidar Berg Date 10.Nov 2010 Description Revision Number User manual for setting up and maintaining the Dualog Connection Suite
Adding a POP/IMAP
 Adding a POP/IMAP Email POP and IMAP are used for webmail (i.e. your company does not have an exchange server). POP and IMAP are two different protocols but are added the same way. The settings are split
Adding a POP/IMAP Email POP and IMAP are used for webmail (i.e. your company does not have an exchange server). POP and IMAP are two different protocols but are added the same way. The settings are split
Instruction Manual Archiving with Office 365. Revision 2.0
 Instruction Manual Archiving with Office 365 Revision 2.0 Copyright 2013 by REDDOXX GmbH REDDOXX GmbH Neue Weilheimer Str. 14 D-73230 Kirchheim Fon: +49 (0)7021 92846-0 Fax: +49 (0)7021 92846-99 E-Mail:
Instruction Manual Archiving with Office 365 Revision 2.0 Copyright 2013 by REDDOXX GmbH REDDOXX GmbH Neue Weilheimer Str. 14 D-73230 Kirchheim Fon: +49 (0)7021 92846-0 Fax: +49 (0)7021 92846-99 E-Mail:
Configuring and Managing the IP Camera
 CHAPTER 3 The Cisco Video Surveillance IP Camera provides configuration windows that you use to configure and manage the IP camera. This chapter explains how to access the configuration windows, describes
CHAPTER 3 The Cisco Video Surveillance IP Camera provides configuration windows that you use to configure and manage the IP camera. This chapter explains how to access the configuration windows, describes
Configuring SSL CHAPTER
 7 CHAPTER This chapter describes the steps required to configure your ACE appliance as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination. The topics included in this section
7 CHAPTER This chapter describes the steps required to configure your ACE appliance as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination. The topics included in this section
How to set up an account in Outlook
 How to set up an e-mail account in Outlook Note: To complete these steps, you will need to know your email address, password, incoming mail server name, and outgoing mail server name that is provided by
How to set up an e-mail account in Outlook Note: To complete these steps, you will need to know your email address, password, incoming mail server name, and outgoing mail server name that is provided by
APPLICATION NOTE. Subject: C-more setup and functionality Date Issued: C-more functionality
 APPLICATION NOTE THIS INFORMATION PROVIDED BY AUTOMATIONDIRECT.COM TECHNICAL SUPPORT IS PROVIDED "AS IS" WITHOUT A GUARANTEE OF ANY KIND. These documents are provided by our technical support department
APPLICATION NOTE THIS INFORMATION PROVIDED BY AUTOMATIONDIRECT.COM TECHNICAL SUPPORT IS PROVIDED "AS IS" WITHOUT A GUARANTEE OF ANY KIND. These documents are provided by our technical support department
Introduction. Setting Up POP3/IMAP Accounts
 Introduction In order to send and receive email outside of the webmail portal, you ll need to setup up an email client application on your device(s). We ve included some examples of how to configure a
Introduction In order to send and receive email outside of the webmail portal, you ll need to setup up an email client application on your device(s). We ve included some examples of how to configure a
Configuring an IMAP or POP3 Journal Account for Microsoft Exchange Server 2007 and 2010
 Configuring an IMAP or POP3 Journal Account for Microsoft Exchange Server 2007 and 2010 This article refers to Barracuda Message Archiver Legacy Release firmware or higher, and Microsoft Exchange Server
Configuring an IMAP or POP3 Journal Account for Microsoft Exchange Server 2007 and 2010 This article refers to Barracuda Message Archiver Legacy Release firmware or higher, and Microsoft Exchange Server
System Menu Send Setup
 System Menu Send Email Setup In the SETUP menu, select the SYSTEM tab. Then, the SYSTEM menu is displayed as pictured below. Select ON (in red circle) on Send Email column, and then select the enter button
System Menu Send Email Setup In the SETUP menu, select the SYSTEM tab. Then, the SYSTEM menu is displayed as pictured below. Select ON (in red circle) on Send Email column, and then select the enter button
inode Fax Relay Agent Integrated with Windows Fax Services
 inode Fax Relay Agent Integrated with Windows Fax Services Users Guide 2008 Dataways Communications inode Fax Relay Agent v1.2.2 October 2008 inode Fax Relay Agent 1.2.2, Published October 2008. Copyright
inode Fax Relay Agent Integrated with Windows Fax Services Users Guide 2008 Dataways Communications inode Fax Relay Agent v1.2.2 October 2008 inode Fax Relay Agent 1.2.2, Published October 2008. Copyright
COREN. User Manual.
 COREN User Manual www.tecnosicurezza.it Rev. A 10/2015 Page 2 of 40 v. 1.2.4 IU_Coren_00_eng Table of contents 1 - COREN overview... 4 2 - Software installation... 5 3 - First launch of Coren... 10 4 Software
COREN User Manual www.tecnosicurezza.it Rev. A 10/2015 Page 2 of 40 v. 1.2.4 IU_Coren_00_eng Table of contents 1 - COREN overview... 4 2 - Software installation... 5 3 - First launch of Coren... 10 4 Software
Aimetis Symphony Mobile Bridge. 2.7 Installation Guide
 Aimetis Symphony Mobile Bridge 2.7 Installation Guide Contents Contents Introduction...3 Installation... 4 Install the Mobile Bridge... 4 Upgrade the Mobile Bridge...4 Network configuration... 4 Configuration...
Aimetis Symphony Mobile Bridge 2.7 Installation Guide Contents Contents Introduction...3 Installation... 4 Install the Mobile Bridge... 4 Upgrade the Mobile Bridge...4 Network configuration... 4 Configuration...
T-Server for Cisco UCM Deployment Guide. T-Servers 8.1.2
 T-Server for Cisco UCM Deployment Guide T-Servers 8.1.2 3/8/2018 Table of Contents Supplement to T-Server for Cisco UCM Deployment Guide 3 Cross-cluster supervisor monitoring 4 Extend and connect 5 TLS
T-Server for Cisco UCM Deployment Guide T-Servers 8.1.2 3/8/2018 Table of Contents Supplement to T-Server for Cisco UCM Deployment Guide 3 Cross-cluster supervisor monitoring 4 Extend and connect 5 TLS
Authorized Send Installation and Configuration Guide Version 3.5
 Canon Authorized Send Installation and Configuration Guide Version 3.5 08011-35-UD2-004 This page is intentionally left blank. 2 Authorized Send Installation and Configuration Guide Contents Preface...5
Canon Authorized Send Installation and Configuration Guide Version 3.5 08011-35-UD2-004 This page is intentionally left blank. 2 Authorized Send Installation and Configuration Guide Contents Preface...5
The Applications and Gaming Tab - Port Range Forward
 The Applications and Gaming Tab - Port Range Forward The Applications and Gaming Tab allows you to set up public services on your network, such as web servers, ftp servers, e-mail servers, or other specialized
The Applications and Gaming Tab - Port Range Forward The Applications and Gaming Tab allows you to set up public services on your network, such as web servers, ftp servers, e-mail servers, or other specialized
Manual for Migrating Data from Gmail to
 Manual for Migrating Email Data from Gmail to Office 365 Ver. 1.0 August 1, 2018 Information Systems Administrative Office 1 目次 1. Introduction... 3 Migrating Email Data... 4 2-1. Installing Thunderbird
Manual for Migrating Email Data from Gmail to Office 365 Ver. 1.0 August 1, 2018 Information Systems Administrative Office 1 目次 1. Introduction... 3 Migrating Email Data... 4 2-1. Installing Thunderbird
Mobile Client. User Manual. Version: 2.0.0
 Mobile Client User Manual Version: 2.0.0 Index Sr. No. Topic Page 1 Requirement 3 2 How to use Mobile Client 4 3 Compose Message 5 4 Select Contacts 6 5 Manage Contacts 17 6 Manage Distribution List 23
Mobile Client User Manual Version: 2.0.0 Index Sr. No. Topic Page 1 Requirement 3 2 How to use Mobile Client 4 3 Compose Message 5 4 Select Contacts 6 5 Manage Contacts 17 6 Manage Distribution List 23
LRS File Transfer Service
 LRS File Transfer Service Version 2 User Guide October 27, 2017 Introduction The LRS File Transfer Service offers customers a secure way to send and receive files using HTTPS or FTPS protocols. This can
LRS File Transfer Service Version 2 User Guide October 27, 2017 Introduction The LRS File Transfer Service offers customers a secure way to send and receive files using HTTPS or FTPS protocols. This can
Remote Support Security Provider Integration: RADIUS Server
 Remote Support Security Provider Integration: RADIUS Server 2003-2019 BeyondTrust Corporation. All Rights Reserved. BEYONDTRUST, its logo, and JUMP are trademarks of BeyondTrust Corporation. Other trademarks
Remote Support Security Provider Integration: RADIUS Server 2003-2019 BeyondTrust Corporation. All Rights Reserved. BEYONDTRUST, its logo, and JUMP are trademarks of BeyondTrust Corporation. Other trademarks
Symantec Encryption Management Server and Symantec Data Loss Prevention. Integration Guide
 Symantec Encryption Management Server and Symantec Data Loss Prevention Integration Guide The software described in this book is furnished under a license agreement and may be used only in accordance
Symantec Encryption Management Server and Symantec Data Loss Prevention Integration Guide The software described in this book is furnished under a license agreement and may be used only in accordance
1. A broadband connection. 2. Windows Vista (for these instructions; other operating systems have other instructions).
 A VPN (Virtual Private Network) provides a secure, encrypted tunnel from your computer to UHCL's network when off campus. UHCL offers VPN software to allow authenticated, secure access to many UHCL resources
A VPN (Virtual Private Network) provides a secure, encrypted tunnel from your computer to UHCL's network when off campus. UHCL offers VPN software to allow authenticated, secure access to many UHCL resources
Configuring SSL. SSL Overview CHAPTER
 CHAPTER 8 Date: 4/23/09 This topic describes the steps required to configure your ACE (both the ACE module and the ACE appliance) as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination.
CHAPTER 8 Date: 4/23/09 This topic describes the steps required to configure your ACE (both the ACE module and the ACE appliance) as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination.
PREFACE. This is the reference guide for the Month-End Module for IQ Business & IQ Enterprise software systems.
 MONTH-END MODULE PREFACE This is the reference guide for the Month-End Module for IQ Business & IQ Enterprise software systems. The document will aid in understanding and configuration of the Month-End
MONTH-END MODULE PREFACE This is the reference guide for the Month-End Module for IQ Business & IQ Enterprise software systems. The document will aid in understanding and configuration of the Month-End
Setting Up Windows 2K VPN Connection Through The Symantec Raptor Firewall Firewall
 Setting Up Windows 2K VPN Connection Through The Symantec Raptor Firewall Firewall By: Loc Huynh Date: 24 March 2003 Table of Contents 1.0 Foreword...2 2.0 Setting VPN on VPN Server...2 3.0 Setting Symantec
Setting Up Windows 2K VPN Connection Through The Symantec Raptor Firewall Firewall By: Loc Huynh Date: 24 March 2003 Table of Contents 1.0 Foreword...2 2.0 Setting VPN on VPN Server...2 3.0 Setting Symantec
Configuring Communication Services
 This chapter includes the following sections: Configuring HTTP, on page 1 Configuring SSH, on page 2 Configuring XML API, on page 3 Enabling Redfish, on page 3 Configuring IPMI, on page 4 Configuring SNMP,
This chapter includes the following sections: Configuring HTTP, on page 1 Configuring SSH, on page 2 Configuring XML API, on page 3 Enabling Redfish, on page 3 Configuring IPMI, on page 4 Configuring SNMP,
Traveling Setup Apple Mail
 Traveling Email Setup Apple Mail Table Of Contents 1 : Traveling Email Questions (and answers) 2 : Email server settings 2 : Configuring your email client (Apple Mail) 3 : Reporting Problems Version 1.0
Traveling Email Setup Apple Mail Table Of Contents 1 : Traveling Email Questions (and answers) 2 : Email server settings 2 : Configuring your email client (Apple Mail) 3 : Reporting Problems Version 1.0
Webthority can provide single sign-on to web applications using one of the following authentication methods:
 Webthority HOW TO Configure Web Single Sign-On Webthority can provide single sign-on to web applications using one of the following authentication methods: HTTP authentication (for example Kerberos, NTLM,
Webthority HOW TO Configure Web Single Sign-On Webthority can provide single sign-on to web applications using one of the following authentication methods: HTTP authentication (for example Kerberos, NTLM,
Using on Your Sprint PCS Vision Smart Device PPC-6700
 Using Email on Your Sprint PCS Vision Smart Device PPC-6700 2006 Sprint Nextel. All rights reserved. SPRINT, the "Going Forward" logo, and other trademarks are trademarks of Sprint Nextel. June 7, 2006
Using Email on Your Sprint PCS Vision Smart Device PPC-6700 2006 Sprint Nextel. All rights reserved. SPRINT, the "Going Forward" logo, and other trademarks are trademarks of Sprint Nextel. June 7, 2006
Internet access system through the Wireless Network of the University of Bologna
 Internet access system through the Wireless Network of the University of Bologna (last update 6/3/2017) Printable service summary document: the updated version is available online at the address http://www.unibo.it/almawifi
Internet access system through the Wireless Network of the University of Bologna (last update 6/3/2017) Printable service summary document: the updated version is available online at the address http://www.unibo.it/almawifi
Using FF240-IP with T38fax.com. Application Notes Rev
 Using FF240-IP with T38fax.com Application Notes Rev. 0.02 www.multitech.com Using FF240-IP with T38fax.com Application Notes Rev.0.02 S000641 Copyright This publication may not be reproduced, in whole
Using FF240-IP with T38fax.com Application Notes Rev. 0.02 www.multitech.com Using FF240-IP with T38fax.com Application Notes Rev.0.02 S000641 Copyright This publication may not be reproduced, in whole
Brekeke PBX Version 3 Administrator's Guide (Basic) Brekeke Software, Inc.
 Brekeke PBX Version 3 Administrator's Guide (Basic) Brekeke Software, Inc. Version Brekeke PBX version 3, Administrator s Guide (Basic) Copyright This document is copyrighted by Brekeke Software, Inc.
Brekeke PBX Version 3 Administrator's Guide (Basic) Brekeke Software, Inc. Version Brekeke PBX version 3, Administrator s Guide (Basic) Copyright This document is copyrighted by Brekeke Software, Inc.
Setting up your Student on Windows Mail or Microsoft Outlook
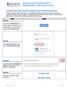 Setting up your Student Email on Windows Mail or Microsoft Outlook Complete First: Allow Less Secure Apps on your Student Email Account Changes in Google s Policy means that you must enable this feature
Setting up your Student Email on Windows Mail or Microsoft Outlook Complete First: Allow Less Secure Apps on your Student Email Account Changes in Google s Policy means that you must enable this feature
Zivif Security Camera
 Zivif Security Camera Quick Installation Guide (RH and RS Series) Support and downloads: www.zivif.com CONNECTION OVERVIEW Wifi / SD onboard storage (supported models only) Wired Camera Router Modem Global
Zivif Security Camera Quick Installation Guide (RH and RS Series) Support and downloads: www.zivif.com CONNECTION OVERVIEW Wifi / SD onboard storage (supported models only) Wired Camera Router Modem Global
Grandstream Networks, Inc. GWN7000 Multi-WAN Gigabit VPN Router VPN Configuration Guide
 Grandstream Networks, Inc. GWN7000 Multi-WAN Gigabit VPN Router VPN Configuration Guide Table of Contents SUPPORTED DEVICES... 5 INTRODUCTION... 6 GWN7000 VPN FEATURE... 7 OPENVPN CONFIGURATION... 8 OpenVPN
Grandstream Networks, Inc. GWN7000 Multi-WAN Gigabit VPN Router VPN Configuration Guide Table of Contents SUPPORTED DEVICES... 5 INTRODUCTION... 6 GWN7000 VPN FEATURE... 7 OPENVPN CONFIGURATION... 8 OpenVPN
How to Configure Mobile VPN for Forcepoint NGFW TECHNICAL DOCUMENT
 How to Configure Mobile VPN for Forcepoint NGFW TECHNICAL DOCUMENT Table of Contents TABLE OF CONTENTS 1 BACKGROUND 2 WINDOWS SERVER CONFIGURATION STEPS 2 CONFIGURING USER AUTHENTICATION 3 ACTIVE DIRECTORY
How to Configure Mobile VPN for Forcepoint NGFW TECHNICAL DOCUMENT Table of Contents TABLE OF CONTENTS 1 BACKGROUND 2 WINDOWS SERVER CONFIGURATION STEPS 2 CONFIGURING USER AUTHENTICATION 3 ACTIVE DIRECTORY
User Identity Sources
 The following topics describe Firepower System user identity sources, which are sources for user awareness. These users can be controlled with identity and access control policies: About, on page 1 The
The following topics describe Firepower System user identity sources, which are sources for user awareness. These users can be controlled with identity and access control policies: About, on page 1 The
Security Provider Integration RADIUS Server
 Security Provider Integration RADIUS Server 2017 Bomgar Corporation. All rights reserved worldwide. BOMGAR and the BOMGAR logo are trademarks of Bomgar Corporation; other trademarks shown are the property
Security Provider Integration RADIUS Server 2017 Bomgar Corporation. All rights reserved worldwide. BOMGAR and the BOMGAR logo are trademarks of Bomgar Corporation; other trademarks shown are the property
Outlook 2010 Setup Guide (POP3 Transmailaccess)
 Versions Addressed: Microsoft Office Outlook 2010 Document Updated: 7 /22/2013 Copyright 2012 Smarsh, Inc. All rights reserved. Purpose: This document will assist the end user in configuring Outlook 2010
Versions Addressed: Microsoft Office Outlook 2010 Document Updated: 7 /22/2013 Copyright 2012 Smarsh, Inc. All rights reserved. Purpose: This document will assist the end user in configuring Outlook 2010
Configuring and Managing the IP Camera
 CHAPTER 3 The Cisco Video Surveillance IP Camera provides configuration windows that you use to configure and manage the IP camera. This chapter explains how to access the configuration windows, describes
CHAPTER 3 The Cisco Video Surveillance IP Camera provides configuration windows that you use to configure and manage the IP camera. This chapter explains how to access the configuration windows, describes
Signup for Multi-Factor Authentication
 What is Multi-Factor Authentication? Multi-Factor Authentication (MFA) helps safeguard access to data and applications while maintaining simplicity for users. It provides additional security by requiring
What is Multi-Factor Authentication? Multi-Factor Authentication (MFA) helps safeguard access to data and applications while maintaining simplicity for users. It provides additional security by requiring
RM Series IP Cameras. Configuration manual. WiFi IP Cameras CONFIGURATION MANUAL RM SERIES - IP CAMERAS WIFI. How to configure camera options
 Page: 1 RM Series IP Cameras WiFi IP Cameras Configuration manual How to configure camera options Page: 2 Contents of this handbook The range of RM series cameras is a range of IP cameras for network connection
Page: 1 RM Series IP Cameras WiFi IP Cameras Configuration manual How to configure camera options Page: 2 Contents of this handbook The range of RM series cameras is a range of IP cameras for network connection
My Account Login System Instructions
 My Account Login System Instructions Introduction With ExcalTech s Client Login system, you will have access to your appointments, files, invoices, knowledge base, quotes, tasks, and tickets from wherever
My Account Login System Instructions Introduction With ExcalTech s Client Login system, you will have access to your appointments, files, invoices, knowledge base, quotes, tasks, and tickets from wherever
PASSWORD (Creating a program in the PLC and touchscreen)
 PASSWORD (Creating a program in the PLC and touchscreen) This sample program provides a step by step process on how to create a password to protect a screen. It involves creating a program in the touchscreen
PASSWORD (Creating a program in the PLC and touchscreen) This sample program provides a step by step process on how to create a password to protect a screen. It involves creating a program in the touchscreen
Password Change and Mail Client Configuration Guide for sltnet.lk/slt.lk Mail Server
 User Guide Password Change and Mail Client Configuration Guide for sltnet.lk/slt.lk Mail Server 2018/05/10 LEGAL INFORMATION Copyright 2018 Sri Lanka Telecom Plc All rights reserved. We reserve the right
User Guide Password Change and Mail Client Configuration Guide for sltnet.lk/slt.lk Mail Server 2018/05/10 LEGAL INFORMATION Copyright 2018 Sri Lanka Telecom Plc All rights reserved. We reserve the right
User Identity Sources
 The following topics describe Firepower System user identity sources, which are sources for user awareness. These users can be controlled with identity and access control policies: About, page 1 The User
The following topics describe Firepower System user identity sources, which are sources for user awareness. These users can be controlled with identity and access control policies: About, page 1 The User
Soft Phone Quick Start Guide
 i Soft Phone Quick Start Guide Soft Phone Quick Start Guide Version: 1.1 Firmware Version: V1.1.0 Date: 05/10/2010 Copyright Declarations Trademarks Copyright 2010 All rights reserved. This publication
i Soft Phone Quick Start Guide Soft Phone Quick Start Guide Version: 1.1 Firmware Version: V1.1.0 Date: 05/10/2010 Copyright Declarations Trademarks Copyright 2010 All rights reserved. This publication
X500 Series Scan Destination and Alert Message Setup Guide
 X500 Series Scan Destination and Alert Message Setup Guide www.lexmark.com July 2007 Lexmark and Lexmark with diamond design are trademarks of Lexmark International, Inc., registered in the United States
X500 Series Scan Destination and Alert Message Setup Guide www.lexmark.com July 2007 Lexmark and Lexmark with diamond design are trademarks of Lexmark International, Inc., registered in the United States
SMTP Sending s While on PureVPN
 SMTP Sending E-Mails While on PureVPN If you are facing difficulties sending e-mails while being connected to PureVPN, this may be because we are blocking outgoing e-mail services (SMTP). We block outgoing
SMTP Sending E-Mails While on PureVPN If you are facing difficulties sending e-mails while being connected to PureVPN, this may be because we are blocking outgoing e-mail services (SMTP). We block outgoing
Optimal Performance and Installation Guide
 Outlook Connector for MDaemon How To Quick Start Guide Optimal Performance and Installation Guide This guide provides information on how to get the optimal performance from Outlook Connector, how to install
Outlook Connector for MDaemon How To Quick Start Guide Optimal Performance and Installation Guide This guide provides information on how to get the optimal performance from Outlook Connector, how to install
Client Configuration Guide
 Email Client Configuration Guide Contents Prerequisites... 1 Microsoft Outlook 2007... 2 Microsoft Outlook 2002/XP and 2003... 7 Microsoft Windows Mail (available with Vista only)... 11 Microsoft Outlook
Email Client Configuration Guide Contents Prerequisites... 1 Microsoft Outlook 2007... 2 Microsoft Outlook 2002/XP and 2003... 7 Microsoft Windows Mail (available with Vista only)... 11 Microsoft Outlook
Configuring IDS TCP Reset Using VMS IDS MC
 Configuring IDS TCP Reset Using VMS IDS MC Document ID: 47560 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations Initial Sensor Configuration
Configuring IDS TCP Reset Using VMS IDS MC Document ID: 47560 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations Initial Sensor Configuration
Network Security and Cryptography. 2 September Marking Scheme
 Network Security and Cryptography 2 September 2015 Marking Scheme This marking scheme has been prepared as a guide only to markers. This is not a set of model answers, or the exclusive answers to the questions,
Network Security and Cryptography 2 September 2015 Marking Scheme This marking scheme has been prepared as a guide only to markers. This is not a set of model answers, or the exclusive answers to the questions,
NotifySync 4.7. Notify Technology Corporation
 1 NotifySync 4.7 Notify Technology Corporation Device Requirements 2 BlackBerry OS 4.1 4.7 (5.0 coming soon) 4.5.0 and later Attachments can be downloaded and saved to the file system or SD Card. Any attachment
1 NotifySync 4.7 Notify Technology Corporation Device Requirements 2 BlackBerry OS 4.1 4.7 (5.0 coming soon) 4.5.0 and later Attachments can be downloaded and saved to the file system or SD Card. Any attachment
1 Requirements. 2 Configuring Camera Analytics. exacqvision UDP Integration Guide.
 exacqvision UDP Integration Guide 1 Requirements The UDP camera with analytics can be used with any exacqvision server running exacqvision version 4.11 or later. 2 Configuring Camera Analytics 1. On the
exacqvision UDP Integration Guide 1 Requirements The UDP camera with analytics can be used with any exacqvision server running exacqvision version 4.11 or later. 2 Configuring Camera Analytics 1. On the
APPLICATION LAYER APPLICATION LAYER : DNS, HTTP, , SMTP, Telnet, FTP, Security-PGP-SSH.
 APPLICATION LAYER : DNS, HTTP, E-mail, SMTP, Telnet, FTP, Security-PGP-SSH. To identify an entity, the Internet used the IP address, which uniquely identifies the connection of a host to the Internet.
APPLICATION LAYER : DNS, HTTP, E-mail, SMTP, Telnet, FTP, Security-PGP-SSH. To identify an entity, the Internet used the IP address, which uniquely identifies the connection of a host to the Internet.
s and Anti-spam
 E-mails and Anti-spam Standard authentication AUTH method As the spammers become increasing aggressive more and more legit emails get banned as spam. When you send e-mails from your webcrm system, we use
E-mails and Anti-spam Standard authentication AUTH method As the spammers become increasing aggressive more and more legit emails get banned as spam. When you send e-mails from your webcrm system, we use
FAQ 106 How do I access and set up client applications? There are two ways to access a mailbox for sending and receiving messages:
 FAQ 106 How do I access email and set up email client applications? Page 1 Access your webmail Outlook 2016 Setup Access from Mozilla Thunderbird Access from Apple Mail Access from iphone Access from Android
FAQ 106 How do I access email and set up email client applications? Page 1 Access your webmail Outlook 2016 Setup Access from Mozilla Thunderbird Access from Apple Mail Access from iphone Access from Android
How to use Gmail to access your JBN
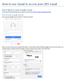 How to use Gmail to access your JBN email Step 1: Sign in or create a Google account. If you have an existing Gmail account, sign into it and skip to Step 2: Import your jbntelco email. Part A: Create
How to use Gmail to access your JBN email Step 1: Sign in or create a Google account. If you have an existing Gmail account, sign into it and skip to Step 2: Import your jbntelco email. Part A: Create
Configuring /Text Alerts in ThorPCX SUPPORT DOCUMENT
 1 CONFIGURING EMAIL/TEXT ALERTS IN THORPCX Section I Page 2 Email Tab, Mail Server & Server Authentication. Section II Page 3 Configuring Email Addresses, Groups & Messages. Also Edit Email Addresses.
1 CONFIGURING EMAIL/TEXT ALERTS IN THORPCX Section I Page 2 Email Tab, Mail Server & Server Authentication. Section II Page 3 Configuring Email Addresses, Groups & Messages. Also Edit Email Addresses.
Lightspeed Online Self Care Guide
 Lightspeed Online Self Care Guide 1. Open up your browser and go to https://myportal.lightspeedtelecom.com 2. Enter your user name and password. 3. For your username, use your email address. 4. For your
Lightspeed Online Self Care Guide 1. Open up your browser and go to https://myportal.lightspeedtelecom.com 2. Enter your user name and password. 3. For your username, use your email address. 4. For your
Incident Commander Pro V7 Beacon Tracking and Messaging
 http://sartechnology.ca sartechnology@telus.net Incident Commander Pro V7 Beacon Tracking and Messaging Section 1: Creating a GeoPro Tracking/Messaging Account - for DeLorme InReach, Messenger and Nano
http://sartechnology.ca sartechnology@telus.net Incident Commander Pro V7 Beacon Tracking and Messaging Section 1: Creating a GeoPro Tracking/Messaging Account - for DeLorme InReach, Messenger and Nano
Hotel Phone - H3 & H5 Quick Installation Guide
 Hotel Phone - H3 & H5 Quick Installation Guide Connection methods Please connect power adapter, network, PC, and handset to the corresponding ports as described in below picture. 2 / 6 1 Introduction to
Hotel Phone - H3 & H5 Quick Installation Guide Connection methods Please connect power adapter, network, PC, and handset to the corresponding ports as described in below picture. 2 / 6 1 Introduction to
USER S MANUAL INDEX 1.1 SET-UP SET IP 2
 USER S MANUAL INDEX Ver.02 Updated 2013/4/17 1 INTRODUCTION 1 1.1 SET-UP 1.1 2 SET IP 2 2.1 Automatic Network Configuration using DHCP 2.1 2.2 Network Configuration using a Static IP Address 2.2 2.3 Set
USER S MANUAL INDEX Ver.02 Updated 2013/4/17 1 INTRODUCTION 1 1.1 SET-UP 1.1 2 SET IP 2 2.1 Automatic Network Configuration using DHCP 2.1 2.2 Network Configuration using a Static IP Address 2.2 2.3 Set
External Alerting for Intrusion Events
 The following topics describe how to configure external alerting for intrusion events: About, page 1 Configuring SNMP Alerting for Intrusion Events, page 2 Configuring Syslog Alerting for Intrusion Events,
The following topics describe how to configure external alerting for intrusion events: About, page 1 Configuring SNMP Alerting for Intrusion Events, page 2 Configuring Syslog Alerting for Intrusion Events,
Configuring 802.1X Settings on the WAP351
 Article ID: 5078 Configuring 802.1X Settings on the WAP351 Objective IEEE 802.1X authentication allows the WAP device to gain access to a secured wired network. You can configure the WAP device as an 802.1X
Article ID: 5078 Configuring 802.1X Settings on the WAP351 Objective IEEE 802.1X authentication allows the WAP device to gain access to a secured wired network. You can configure the WAP device as an 802.1X
Setting Up Apple Mail
 EMAIL ACCOUNT SETUP 1. Open Apple Mail. If you are not prompted to create an account, go to Mail -> Preferences. 2. Click on the + button in the lower left hand corner. Work, Personal Your Name 1 3. Enter
EMAIL ACCOUNT SETUP 1. Open Apple Mail. If you are not prompted to create an account, go to Mail -> Preferences. 2. Click on the + button in the lower left hand corner. Work, Personal Your Name 1 3. Enter
SET UP VPN FOR WINDOWS 10
 SET UP VPN FOR WINDOWS 10 A VPN (Virtual Private Network) provides a secure, encrypted tunnel from your computer to UHCL's network when off campus. UHCL offers VPN software to allow authenticated, secure
SET UP VPN FOR WINDOWS 10 A VPN (Virtual Private Network) provides a secure, encrypted tunnel from your computer to UHCL's network when off campus. UHCL offers VPN software to allow authenticated, secure
700 Fox Glen Barrington, Illinois ph/fx: [847] Setup Guide
![700 Fox Glen Barrington, Illinois ph/fx: [847] Setup Guide 700 Fox Glen Barrington, Illinois ph/fx: [847] Setup Guide](/thumbs/92/107779966.jpg) Email Setup Guide 1. Mac Mail Page 2 2. ios/iphone Page 7 3. Outlook 2016 Page 12 4. Outlook 2013 Page 20 5. Windows Mail Page 26 Mac Mail 1. Open Mac Mail. 2. In the top left, click Mail, then click Add
Email Setup Guide 1. Mac Mail Page 2 2. ios/iphone Page 7 3. Outlook 2016 Page 12 4. Outlook 2013 Page 20 5. Windows Mail Page 26 Mac Mail 1. Open Mac Mail. 2. In the top left, click Mail, then click Add
Alert Configuration on the Cisco WAP121 and WAP321 Access Point
 Email Alert Configuration on the Cisco WAP121 and WAP321 Access Point Objective System events are activities in the system that may require attention and necessary actions to be taken in order to run the
Email Alert Configuration on the Cisco WAP121 and WAP321 Access Point Objective System events are activities in the system that may require attention and necessary actions to be taken in order to run the
Instructions Eudora OSE Page 1
 Instructions Eudora OSE Page 1 Instructions Eudora OSE This manual is written for users who already have an e-mail account configured in Eudora OSE and will therefore only focus on how to change the SMTP
Instructions Eudora OSE Page 1 Instructions Eudora OSE This manual is written for users who already have an e-mail account configured in Eudora OSE and will therefore only focus on how to change the SMTP
How to setup accounts for the following: 1) Elastic 2) Maligun 3) Mailjet 4) Sendgrid 4) Amazon SES 5) G suite 6) Sparkpost
 How to setup accounts for the following: 1) Elastic email 2) Maligun 3) Mailjet 4) Sendgrid 4) Amazon SES 5) G suite 6) Sparkpost Elastic Email SMTP Port : 587, 465, 2525 Host: smtp.elasticmail.com Sparkpost
How to setup accounts for the following: 1) Elastic email 2) Maligun 3) Mailjet 4) Sendgrid 4) Amazon SES 5) G suite 6) Sparkpost Elastic Email SMTP Port : 587, 465, 2525 Host: smtp.elasticmail.com Sparkpost
Cisco Expressway with Jabber Guest
 Cisco Expressway with Jabber Guest Deployment Guide First Published: Decemeber 2016 Cisco Expressway X8.9 Cisco Jabber Guest Server 10.6.9 (or later) Cisco Systems, Inc. www.cisco.com Contents Preface
Cisco Expressway with Jabber Guest Deployment Guide First Published: Decemeber 2016 Cisco Expressway X8.9 Cisco Jabber Guest Server 10.6.9 (or later) Cisco Systems, Inc. www.cisco.com Contents Preface
Generic IP Camera Driver
 Generic IP Camera Driver Information Sheet for Crimson v3.0+ Compatible Devices IP cameras and web cameras where the static image is accessible through a web interface in either JPEG or bitmap formats.
Generic IP Camera Driver Information Sheet for Crimson v3.0+ Compatible Devices IP cameras and web cameras where the static image is accessible through a web interface in either JPEG or bitmap formats.
Scannex Collector Manual
 Scannex Collector Manual Thursday, 28 th August 2008 Issue 3 Document History Issue Date Comments 01 08-Oct-2004 Initial Release. 02 19-Nov-2004 General update. 03 28-Aug-2008 Update for ip.buffer Copyright
Scannex Collector Manual Thursday, 28 th August 2008 Issue 3 Document History Issue Date Comments 01 08-Oct-2004 Initial Release. 02 19-Nov-2004 General update. 03 28-Aug-2008 Update for ip.buffer Copyright
Settings tab. User guide
 Settings tab User guide Contents 1. Introduction... 2 Documentation... 2 Licensing... 2 Settings overview... 2 2. Settings tab selections... 3 Backup user identity... 3 Email server settings... 4 Email
Settings tab User guide Contents 1. Introduction... 2 Documentation... 2 Licensing... 2 Settings overview... 2 2. Settings tab selections... 3 Backup user identity... 3 Email server settings... 4 Email
My Instant Communicator for iphone
 My Instant Communicator for iphone Alcatel-Lucent OmniTouch 8600 OmniPCX Office Rich Communication Edition User guide 8AL90849USAAed05 02 / 2014 CONTENTS 1. Overview... 3 2. Benefits... 3 3. Connectivity...
My Instant Communicator for iphone Alcatel-Lucent OmniTouch 8600 OmniPCX Office Rich Communication Edition User guide 8AL90849USAAed05 02 / 2014 CONTENTS 1. Overview... 3 2. Benefits... 3 3. Connectivity...
User Inputs for Installation, Reinstallation, and Upgrade
 APPENDIXA User Inputs for Installation, Reinstallation, and Upgrade This appendix provides information on the user inputs during Service Monitor installation, reinstallation, and upgrade. This appendix
APPENDIXA User Inputs for Installation, Reinstallation, and Upgrade This appendix provides information on the user inputs during Service Monitor installation, reinstallation, and upgrade. This appendix
Grandstream Networks, Inc. UCM6xxx SIP Trunks Guide
 Grandstream Networks, Inc. Table of Content INTRODUCTION... 4 REGISTER SIP TRUNKS... 5 Configuration... 5 DID / DOD Configuration... 9 Direct Inward Dialing (DID)... 9 Direct Outward Dialing (DOD)... 10
Grandstream Networks, Inc. Table of Content INTRODUCTION... 4 REGISTER SIP TRUNKS... 5 Configuration... 5 DID / DOD Configuration... 9 Direct Inward Dialing (DID)... 9 Direct Outward Dialing (DOD)... 10
User Guide. for the VersaMail. application
 User Guide for the VersaMail application Copyright and Trademark 2004-2007 Palm, Inc. All rights reserved. Palm, HotSync, the HotSync logo, Palm OS, the Palm logo, and VersaMail are among the trademarks
User Guide for the VersaMail application Copyright and Trademark 2004-2007 Palm, Inc. All rights reserved. Palm, HotSync, the HotSync logo, Palm OS, the Palm logo, and VersaMail are among the trademarks
APP NOTES Onsight Rugged Smart Camera Wireless Network Configuration
 APP NOTES Onsight Rugged Smart Camera Wireless Network Configuration July 2016 Table of Contents 1. Overview... 4 1.1 Onsight Setup Wizard... 4 1.2 Onsight Wireless Manual Setup... 4 1.3 Hotspot Login...
APP NOTES Onsight Rugged Smart Camera Wireless Network Configuration July 2016 Table of Contents 1. Overview... 4 1.1 Onsight Setup Wizard... 4 1.2 Onsight Wireless Manual Setup... 4 1.3 Hotspot Login...
Exam Questions SY0-401
 Exam Questions SY0-401 CompTIA Security+ Certification https://www.2passeasy.com/dumps/sy0-401/ 1. A company has implemented PPTP as a VPN solution. Which of the following ports would need to be opened
Exam Questions SY0-401 CompTIA Security+ Certification https://www.2passeasy.com/dumps/sy0-401/ 1. A company has implemented PPTP as a VPN solution. Which of the following ports would need to be opened
LifeSize Passport Configuration Preferences Version 4.7
 LifeSize Passport Configuration Preferences Version 4.7 This document presents a visual depiction of the preferences users and administrators can set to configure LifeSize Passport using software release
LifeSize Passport Configuration Preferences Version 4.7 This document presents a visual depiction of the preferences users and administrators can set to configure LifeSize Passport using software release
User Manual of Webmail Version 5
 User Manual of Webmail Version 5 English Version: 1.0 Page 1 of 13 TABLE OF CONTENTS 1. ACCESS...3 1.1 Accessing to Webmail 5...3 2. COMPOSE AND SEND E-MAIL MESSAGE...4 2.1 Composing a new E-mail message...4
User Manual of Webmail Version 5 English Version: 1.0 Page 1 of 13 TABLE OF CONTENTS 1. ACCESS...3 1.1 Accessing to Webmail 5...3 2. COMPOSE AND SEND E-MAIL MESSAGE...4 2.1 Composing a new E-mail message...4
