Configure Initial Router Settings on Cisco 4000 Series ISRs
|
|
|
- Heather Blankenship
- 5 years ago
- Views:
Transcription
1 Configure Initial Router Settings on Cisco 4000 Series ISRs This chapter describes how to perform the initial configuration on Cisco 4000 Series Integrated Services Routers (ISRs). It contains the following sections: Perform Initial Configuration on Cisco 4000 Series ISRs, on page 1 Verify Network Connectivity, on page 19 Verify Initial Configuration on Cisco 4000 Series ISRs, on page 23 Perform Initial Configuration on Cisco 4000 Series ISRs You can perform initial configuration on Cisco 4000 Series ISRs by using either the setup command facility or the Cisco IOS command-line interface (CLI): Use Cisco Setup Command Facility The setup command facility prompts you to enter the information about your router and network. The facility steps guides you through the initial configuration, which includes LAN and WAN interfaces. For more general information about the setup command facility, see the following document: Cisco IOS Configuration Fundamentals Configuration Guide, Release 12.4, Part 2: Cisco IOS User Interfaces: Using AutoInstall and Setup: This section explains how to configure a hostname for the router, set passwords, and configure an interface to communicate with the management network. Note The messages that are displayed will vary based on your router model, the installed interface modules, and the software image. The following example and the user entries (in bold) are shown only as examples. Note If you make a mistake while using the setup command facility, you can exit and run the setup command facility again. Press Ctrl-C, and enter the setup command in privileged EXEC mode (Router#) 1
2 Use Cisco Setup Command Facility To configure the initial router settings by using the setup command facility, follow these steps: 1. From the Cisco IOS-XE CLI, enter the setup command in privileged EXEC mode: 2. To proceed using the setup command facility, enter yes. 3. To enter the basic management setup, enter yes. 4. Enter a hostname for the router (this example uses myrouter ): 5. Enter an enable secret password. This password is encrypted (for more security) and cannot be seen when viewing the configuration. 6. Enter an enable password that is different from the enable secret password. This password is not encrypted (and is less secure) and can be seen when viewing the configuration. 7. Enter the virtual terminal password, which prevents unauthenticated access to the router through ports other than the console port: 8. Respond to the following prompts as appropriate for your network: 9. Respond to the following prompts as appropriate for your network: 10. Respond to the following prompts. Select [2] to save the initial configuration: From the Cisco IOS-XE CLI, enter the setup command in privileged EXEC mode: Password: <password> Router# setup --- System Configuration Dialog --- Continue with configuration dialog? [yes/no]: You are now in the Setup Configuration Utility. Depending on your router model, the installed interface modules, and the software image, the prompts in the setup command facility vary. The following steps and the user entries (in bold) are shown only as examples. Note Note This setup command facility is also entered automatically if there is no configuration on the router when it is booted into Cisco IOS-XE. If you make a mistake while using the setup command facility, you can exit and run the setup command facility again. Press Ctrl-C, and enter the setup command at the privileged EXEC mode prompt (Router#). For more information on using the setup command facility, see The Setup Command chapter in Cisco IOS Configuration Fundamentals Command Reference, Release 12.2T, at the following URL: To proceed using the setup command facility, enter yes. Continue with configuration dialog? [yes/no]: At any point you may enter a question mark '?' for help. 2
3 Use Cisco Setup Command Facility Use ctrl-c to abort configuration dialog at any prompt. Default settings are in square brackets '[]'. Step 3 To enter the basic management setup, enter yes. Would you like to enter basic management setup? [yes/no]: yes Step 4 Enter a hostname for the router (this example uses myrouter ): Configuring global parameters: Enter host name [Router]: myrouter Step 5 Enter an enable secret password. This password is encrypted (for more security) and cannot be seen when viewing the configuration. The enable secret is a password used to protect access to privileged EXEC and configuration modes. This password, after entered, becomes encrypted in the configuration. Enter enable secret: cisco Step 6 Enter an enable password that is different from the enable secret password. This password is not encrypted (and is less secure) and can be seen when viewing the configuration. The enable password is used when you do not specify an enable secret password, with some older software versions, and some boot images. Enter enable password: cisco123 Step 7 Enter the virtual terminal password, which prevents unauthenticated access to the router through ports other than the console port: The virtual terminal password is used to protect access to the router over a network interface. Enter virtual terminal password: cisco Step 8 Respond to the following prompts as appropriate for your network: Configure SNMP Network Management? [no]: yes Community string [public]: A summary of the available interfaces is displayed. Note The interface summary includes interface numbering, which is dependent on the router model and the installed modules and interface cards. Current interface summary 3
4 Use Cisco Setup Command Facility Interface IP-Address OK? Method Status Protocol GigabitEthernet0/0/0 unassigned YES NVRAM administratively down down GigabitEthernet0/1/ YES DHCP up up GigabitEthernet0/2/0 unassigned YES NVRAM administratively down down SSLVPN-VIF0 unassigned NO unset up Any interface listed with OK? value "NO" does not have a valid configuration Step 9 Respond to the following prompts as appropriate for your network: Configuring interface GigabitEthernet0/1/0 : Configure IP on this interface? [yes]: yes IP address for this interface [ ]: Subnet mask for this interface [ ] : Class A network is , 24 subnet bits; mask is /24 The following configuration command script was created: hostname myrouter enable secret 5 $1$t/Dj$yAeGKviLLZNOBX0b9eifO0 enable password cisco123 line vty 0 4 password cisco snmp-server community public! no ip routing! interface GigabitEthernet0/0/0 shutdown no ip address! interface GigabitEthernet0/1/0 no shutdown ip address ! interface GigabitEthernet0/2/0 shutdown no ip address! end 0 Respond to the following prompts. Select [2] to save the initial configuration: [0] Go to the IOS command prompt without saving this config. [1] Return back to the setup without saving this config. [2] Save this configuration to nvram and exit. Enter your selection [2]: 2 Building configuration... Use the enabled mode 'configure' command to modify this configuration. Press RETURN to get started! RETURN The user prompt is displayed: myrouter> 4
5 Complete the Configuration Complete the Configuration When using the Cisco Setup, and after you have provided all the information requested by the facility, the final configuration appears. To complete your router configuration, follow these steps: 1. Choose to save the configuration when the facility prompts you to save the configuration. 2. When the messages stop appearing on your screen, press Return to get the Router> prompt. 3. Choose to modify the existing configuration or create another configuration. The Router> prompt indicates that you are now at the command-line interface (CLI) and you have just completed a initial router configuration. Nevertheless, this is not a complete configuration. At this point, you have two choices: Choose to save the configuration when the facility prompts you to save the configuration. If you answer no, the configuration information you entered is not saved, and you return to the router enable prompt (Router#). Enter setup to return to the System Configuration Dialog. If you answer yes, the configuration is saved, and you are returned to the user EXEC prompt (Router>). Use this configuration? {yes/no} : yes Building configuration... Use the enabled mode 'configure' command to modify this configuration. Press RETURN to get started! %LINK-3-UPDOWN: Interface Ethernet0/0, changed state to up %LINK-3-UPDOWN: Interface Ethernet0/1, changed state to up %LINK-3-UPDOWN: Interface Serial0/0/0, changed state to up %LINK-3-UPDOWN: Interface Serial0/0/1, changed state to down %LINK-3-UPDOWN: Interface Serial0/2, changed state to down %LINK-3-UPDOWN: Interface Serial1/0, changed state to up %LINK-3-UPDOWN: Interface Serial1/1, changed state to down %LINK-3-UPDOWN: Interface Serial1/2, changed state to down <Additional messages omitted.> Step 3 When the messages stop appearing on your screen, press Return to get the Router> prompt. Choose to modify the existing configuration or create another configuration. The Router> prompt indicates that you are now at the command-line interface (CLI) and you have just completed a initial router configuration. Nevertheless, this is not a complete configuration. At this point, you have two choices: Run the setup command facility again, and create another configuration. Password: password Router# setup Modify the existing configuration or configure additional features by using the CLI: Password: password 5
6 Use Cisco IOS XE CLI Manual Configuration Router# configure terminal Router(config)# Use Cisco IOS XE CLI Manual Configuration This section describes you how to access the command-line interface (CLI) to perform the initial configuration on the router. Note To configure the initial router settings by using the Cisco IOS CLI, you must set up a console connection. If the default configuration file is installed on the router prior to shipping, the system configuration dialog message does not appear, To configure the device, follow these steps: 1. Enter the appropriate answer when the following system message appears on the router. 2. Press Return to terminate autoinstall and continue with manual configuration: 3. Press Return to bring up the Router> prompt. 4. Type enable to enter privileged EXEC mode: Enter the appropriate answer when the following system message appears on the router. --- System Configuration Dialog --- At any point you may enter a question mark '?' for help. Use ctrl-c to abort configuration dialog at any prompt. Default settings are in square brackets '[]'. Would you like to enter the initial configuration dialog? [yes/no]: no Press Return to terminate autoinstall and continue with manual configuration: Would you like to terminate autoinstall? [yes] Return Several messages are displayed, ending with a line similar to the following:... Copyright (c) by cisco Systems, Inc. Compiled <date > <time > by <person > 6
7 Configure Cisco 4000 Series ISR Hostname Step 3 Press Return to bring up the Router> prompt.... flashfs[4]: Initialization complete. Router> Step 4 Type enable to enter privileged EXEC mode: Router# Configure Cisco 4000 Series ISR Hostname The hostname is used in CLI prompts and default configuration filenames. If you do not configure the router hostname, the router uses the factory-assigned default hostname Router. 1. enable 2. configure terminal 3. hostname name 4. Verify that the router prompt displays your new hostname. 5. end enable Enables privileged EXEC mode. Enter your password if prompted. configure terminal Enters global configuration mode. Step 3 Router# configure terminal hostname name Specifies or modifies the hostname for the network server. Step 4 Router(config)# hostname myrouter Verify that the router prompt displays your new hostname. 7
8 Configure the Enable and Enable Secret Passwords Step 5 myrouter(config)# end (Optional) Returns to privileged EXEC mode. myrouter# end Configure the Enable and Enable Secret Passwords To provide an additional layer of security, particularly for passwords that cross the network or are stored on a TFTP server, you can use either the enable password command or enable secret command. Both commands accomplish the same thing they allow you to establish an encrypted password that users must enter to access privileged EXEC (enable) mode. We recommend that you use the enable secret command because it uses an improved encryption algorithm. Use the enable password command only if you boot an older image of the Cisco IOS XE software. For more information, see the Configuring Passwords and Privileges chapter in the Cisco IOS Security Configuration Guide. Also see the Cisco IOS Password Encryption Facts tech note and the Improving Security on Cisco Routers tech note. Note If you configure the enable secret command, it takes precedence over the enable password command; the two commands cannot be in effect simultaneously. 1. enable 2. configure terminal 3. enable password password 4. enable secret password 5. end 6. enable 7. end enable Enables privileged EXEC mode. Enter your password if prompted. configure terminal Enters global configuration mode. 8
9 Configure the Console Idle Privileged EXEC Timeout Step 3 Step 4 Step 5 Router# configure terminal enable password password Router(config)# enable password pswd2 enable secret password Router(config)# enable secret greentree end (Optional) Sets a local password to control access to various privilege levels. We recommend that you perform this step only if you boot an older image of the Cisco IOS-XE software or if you boot older boot ROMs that do not recognize the enable secret command. Specifies an additional layer of security over the enable password command. Do not use the same password that you entered in Step 3. Returns to privileged EXEC mode. Step 6 Step 7 Router(config)# end enable end Enables privileged EXEC mode. Verify that your new enable or enable secret password works. (Optional) Returns to privileged EXEC mode. Router(config)# end Configure the Console Idle Privileged EXEC Timeout This section describes how to configure the console line s idle privileged EXEC timeout. By default, the privileged EXEC command interpreter waits 10 minutes to detect user input before timing out. When you configure the console line, you can also set communication parameters, specify autobaud connections, and configure terminal operating parameters for the terminal that you are using. For more information on configuring the console line, see the Cisco IOS Configuration Fundamentals and Network Management Configuration Guide. In particular, see the Configuring Operating Characteristics for Terminals and Troubleshooting and Fault Management chapters. 1. enable 2. configure terminal 3. line console 0 4. exec-timeout minutes [seconds] 5. end 9
10 Examples 6. show running-config enable Enables privileged EXEC mode. Enter your password if prompted. configure terminal Enters global configuration mode. Step 3 Router# configure terminal line console 0 Configures the console line and starts the line configuration command collection mode. Step 4 Step 5 Router(config)# line console 0 exec-timeout minutes [seconds] Router(config-line)# exec-timeout 0 0 end Sets the idle privileged EXEC timeout, which is the interval that the privileged EXEC command interpreter waits until user input is detected. The example shows how to specify no timeout. Setting the exec-timeout value to 0 will cause the router to never log out after it is logged in. This could have security implications if you leave the console without manually logging out using the disable command. Returns to privileged EXEC mode. Step 6 Router(config)# end show running-config Router(config)# show running-config Displays the running configuration file. Verify that you properly configured the idle privileged EXEC timeout. Examples The following example shows how to set the console idle privileged EXEC timeout to 2 minutes 30 seconds: line console exec-timeout 2 30 The following example shows how to set the console idle privileged EXEC timeout to 30 seconds: line console exec-timeout
11 Gigabit Ethernet Management Interface Overview Gigabit Ethernet Management Interface Overview The router provides an Ethernet management port named GigabitEthernet0. The purpose of this interface is to allow users to perform management tasks on the router. It is an interface that should not and often cannot forward network traffic. It ca, however, be used to access the router through Telnet and SSH to perform management tasks on the router. The interface is most useful before a router begins routing, or in troubleshooting scenarios when other forwarding interfaces are inactive. Note he following aspects of the management ethernet interface: Default Gigabit Ethernet Configuration The router has one management ethernet interface named GigabitEthernet0. IPv4, IPv6, and ARP are the only routed protocols supported for the interface. The interface provides a way to access to the router even if forwarding interfaces are not functional, or the IOS process is down. The management ethernet interface is part of its own VRF. See the Management Ethernet Interface VRF section in the Software Configuration Guide for Cisco 4000 Series ISRs for more details. By default, a forwarding VRF is configured for the interface with a special group named Mgmt-intf. This cannot be changed. This isolates the traffic on the management interface away from the forwarding plane. The basic configuration is like other interfaces; however, there are many forwarding features that are not supported on these interfaces. No forwarding features can be configured on the GigabitEthernet0 interface as it is only used for management. Gigabit Ethernet Port Numbering For example, the default configuration is as follows: interface GigabitEthernet0 vrf forwarding Mgmt-intf ip address negotiation auto The Gigabit Ethernet Management port is always GigabitEthernet0. The port can be accessed in configuration mode. Router# config t Enter configuration commands, one per line. Router(config)#interface gigabitethernet0 Router(config-if)# End with CNTL/Z. Configure Gigabit Ethernet Interfaces This sections shows how to assign an IP address and interface description to an Ethernet interface on your router. For comprehensive configuration information on Gigabit Ethernet interfaces, see the Configuring LAN Interfaces chapter of Cisco IOS Interface and Hardware Component Configuration Guide, For information on interface numbering, see the software configuration guide for your router. 11
12 Configure Gigabit Ethernet Interfaces 1. enable 2. show ip interface brief 3. configure terminal 4. interface {fastethernet gigabitethernet} 0/port 5. description string 6. ip address ip-address mask 7. no shutdown 8. end 9. show ip interface brief enable Enables privileged EXEC mode. Enter your password if prompted. Step 3 show ip interface brief Router# show ip interface brief configure terminal Displays a brief status of the interfaces that are configured for IP. Learn which type of Ethernet interface is on your router. Enters global configuration mode. Step 4 Router# configure terminal interface {fastethernet gigabitethernet} 0/port Router(config)# interface gigabitethernet 0/0/0 Specifies the Ethernet interface and enters interface configuration mode. Note For information on interface numbering, see Slots, Subslots (Bay), Ports, and Interfaces in Cisco 4000 Series ISRs, page Step 5 description string (Optional) Adds a description to an interface configuration. The description helps you remember what is attached to this interface. The description can be useful for troubleshooting. Router(config-if)# description GE int to 2nd floor south wing Step 6 ip address ip-address mask Sets a primary IP address for an interface. Router(config-if)# ip address
13 Configuration Examples Step 7 no shutdown Enables an interface. Step 8 Router(config-if)# no shutdown end Returns to privileged EXEC mode. Step 9 Router(config)# end show ip interface brief Router# show ip interface brief Displays a brief status of the interfaces that are configured for IP. Verify that the Ethernet interfaces are up and configured correctly. Configuration Examples Configuring the GigabitEthernet Interface: Example! interface GigabitEthernet0/0/0 description GE int to HR group ip address duplex auto speed auto no shutdown! Sample Output for the show ip interface brief Command Router#show ip interface brief Interface IP-Address OK? Method Status Protocol GigabitEthernet0/0/0 unassigned YES NVRAM administratively down down GigabitEthernet0/0/1 unassigned YES NVRAM administratively down down GigabitEthernet0/0/2 unassigned YES NVRAM administratively down down GigabitEthernet0/0/3 unassigned YES NVRAM administratively down down GigabitEthernet YES manual up up Specify a Default Route or Gateway of Last Resort This section describes how to specify a default route with IP routing enabled. For alternative methods of specifying a default route, see the Configuring a Gateway of Last Resort Using IP Commands Technical Specifications Note. The Cisco IOS-XE software uses the gateway (router) as a last resort if it does not have a better route for a packet and if the destination is not a connected network. This section describes how to select a network as a default route (a candidate route for computing the gateway of last resort). The way in which routing protocols propagate the default route information varies for each protocol. 13
14 Configure IP Routing and IP Protocols Configure IP Routing and IP Protocols For comprehensive configuration information about IP routing and IP routing protocols, see the Configuring IP Routing Protocol-Independent Feature at cisco.com. IP Routing IP routing is automatically enabled in the Cisco ISO- XE software. When IP routing is configured, the system will use a configured or learned route to forward packets, including a configured default route. Note This task section does not apply when IP routing is disabled. To specify a default route when IP routing is disabled, refer to the Configuring a Gateway of Last Resort Using IP Commands Technical Specifications Note at cisco.com. Default Routes A router might not be able to determine the routes to all other networks. To provide complete routing capability, the common practice is to use some routers as smart routers and give the remaining routers default routes to the smart router. (Smart routers have routing table information for the entire internetwork.) These default routes can be passed along dynamically, or can be configured into the individual routers. Most dynamic interior routing protocols include a mechanism for causing a smart router to generate dynamic default information that is then passed along to other routers. Default Network Gateway of Last Resort If a router has an interface that is directly connected to the specified default network, the dynamic routing protocols running on the router generates or sources a default route. In the case of RIP, the router will advertise the pseudonetwork In the case of IGRP, the network itself is advertised and flagged as an exterior route. A router that is generating the default for a network may also need a default of its own. One way a router can generate its own default is to specify a static route to the network through the appropriate device. When default information is being passed along through a dynamic routing protocol, no further configuration is required. The system periodically scans its routing table to choose the optimal default network as its default route. In the case of RIP, there is only one choice, network In the case of IGRP, there might be several networks that can be candidates for the system default. The Cisco IOS-XE software uses both administrative distance and metric information to determine the default route (gateway of last resort). The selected default route appears in the gateway of last resort display of the show ip route EXEC command. If dynamic default information is not being passed to the software, candidates for the default route are specified with the ip default-network global configuration command. In this usage, the ip default-network command takes an unconnected network as an argument. If this network appears in the routing table from any source (dynamic or static), it is flagged as a candidate default route and is a possible choice for the default route. If the router has no interface on the default network, but does have a route to it, it considers this network as a candidate default path. The route candidates are examined and based on administrative distance and metric, the best one is chosen. The gateway to the best default path becomes the gateway of last resort. 14
15 Gateway of Last Resort 1. enable 2. configure terminal 3. ip routing 4. ip route dest-prefix mask next-hop-ip-address [admin-distance] [permanent] 5. Do one of the following: ip default-network network-number ip route dest-prefix mask next-hop-ip-address 6. end 7. show ip route enable Enables privileged EXEC mode. Enter your password if prompted. configure terminal Enters global configuration mode. Step 3 Router# configure terminal ip routing Enables IP routing. Step 4 Router(config)# ip routing ip route dest-prefix mask next-hop-ip-address [admin-distance] [permanent] Establishes a static route. Step 5 Router(config)# ip route Do one of the following: ip default-network network-number ip route dest-prefix mask next-hop-ip-address Selects a network as a candidate route for computing the gateway of last resort. Creates a static route to network for computing the gateway of last resort. Router(config)# ip default-network
16 Configuration Examples Step 6 Router(config)# ip route end Returns to privileged EXEC mode. Step 7 Router(config)# end show ip route Displays the current routing table information. Verify that the gateway of last resort is set. Router# show ip route Configuration Examples Specifying a Default Route: Example! ip route ! ip default-network ! Sample Output for the show ip route Command Router# show ip route Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 E1 - OSPF external type 1, E2 - OSPF external type 2 i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2 ia - IS-IS inter area, * - candidate default, U - per-user static route o - ODR, P - periodic downloaded static route, H - NHRP, l - LISP a - application route + - replicated route, % - next hop override Gateway of last resort is not set /8 is variably subnetted, 2 subnets, 2 masks C /24 is directly connected, Loopback1 L /32 is directly connected, Loopback1 Router# Configure Virtual Terminal Lines for Remote Console Access Virtual terminal (vty) lines are used to allow remote access to the router. This section shows you how to configure the virtual terminal lines with a password, so that only authorized users can remotely access the router. By default, the router has five virtual terminal lines. However, you can create additional virtual terminal lines. See the Cisco IOS XE Dial Technologies Configuration Guide at Line passwords and password encryption is described in the C isco IOS XE Security Configuration Guide: Secure Connectivity document available at the following URL: 16
17 Configure Virtual Terminal Lines for Remote Console Access. See the Security with Passwords, Privilege Levels, and Login Usernames for CLI Sessions on Networking Devices section. If you want to secure the virtual terminal lines (vty) with an access list, see the Access Control Lists: Overview and Guidelines. 1. enable 2. configure terminal 3. line vty line-number [ending-line-number] 4. password password 5. login 6. end 7. show running-config 8. From another network device, attempt to open a Telnet session to the router. enable Enables privileged EXEC mode. Enter your password if prompted. configure terminal Enters global configuration mode. Step 3 Step 4 Router# configure terminal line vty line-number [ending-line-number] Router(config)# line vty 0 4 password password Starts the line configuration command collection mode for the virtual terminal lines (vty) for remote console access. Note Make sure that you configure all vty lines on your router. To verify the number of vty lines on your router, use the line vty? command. Specifies a password on a line. Step 5 Router(config-line)# password guessagain login Enables password checking at login. Step 6 Router(config-line)# login end Returns to privileged EXEC mode. 17
18 Configuration Examples Step 7 Step 8 Router(config-line)# end show running-config Router# show running-config From another network device, attempt to open a Telnet session to the router. Displays the running configuration file. Verify that you bave properly configured the virtual terminal lines for remote access. Verifies that you can remotely access the router and that the virtual terminal line password is correctly configured. Router# Password: Configuration Examples The following example shows how to configure virtual terminal lines with a password:! line vty 0 4 password guessagain login! What to Do Next After you configure the vty lines, follow these steps: (Optional) To encrypt the virtual terminal line password, see the Configuring Passwords and Privileges chapter in the Cisco IOS Security Configuration Guide. Also see the Cisco IOS Password Encryption Facts tech note. (Optional) To secure the VTY lines with an access list, see the Part 3: Traffic Filtering and Firewalls in the Cisco IOS Security Configuration Guide. Configure the Auxiliary Line This section describes how to enter line configuration mode for the auxiliary line. How you configure the auxiliary line depends on your particular implementation of the auxiliary (AUX) port. See the following documents for information on configuring the auxiliary line: Configuring a Modem on the AUX Port for EXEC Dialin Connectivity, Technical Specifications Note Configuring Dialout Using a Modem on the AUX Port, sample configuration Configuring AUX-to-AUX Port Async Backup with Dialer Watch, sample configuration Modem-Router Connection Guide, Technical Specifications Note 18
19 Verify Network Connectivity 1. enable 2. configure terminal 3. line aux 0 4. See the Technical Specifications Note and sample configurations to configure the line for your particular implementation of the AUX port. enable Enables privileged EXEC mode. Enter your password if prompted. configure terminal Enters global configuration mode. Step 3 Router# configure terminal line aux 0 Starts the line configuration command collection mode for the auxiliary line. Step 4 Router(config)# line aux 0 See the Technical Specifications Note and sample configurations to configure the line for your particular implementation of the AUX port. Verify Network Connectivity This section describes how to verify network connectivity for your router. Before you begin All configuration tasks describe in this chapter must be completed. The router must be connected to a properly configured network host. 1. enable 2. ping [ip-address hostname] 3. telnet {ip-address hostname} 19
20 Examples enable Enables privileged EXEC mode. Enter your password if prompted. Step 3 ping [ip-address hostname] Router# ping telnet {ip-address hostname} Router# telnet Diagnoses initial network connectivity. To verify connectivity, ping the next hop router or connected host for each configured interface to. Logs in to a host that supports Telnet. If you want to test the vty line password, perform this step from a different network device, and use your router s IP address. Examples The following display shows sample output for the ping command when you ping the IP address : Router# ping Protocol [ip]: Target IP address: Repeat count [5]: Datagram size [100]: Timeout in seconds [2]: Extended commands [n]: Sweep range of sizes [n]: Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to , timeout is 2 seconds:!!!!! Success rate is 100 percent, round-trip min/avg/max = 1/2/4 ms The following display shows sample output for the ping command when you ping the IP hostname donald: Router# ping donald Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to , timeout is 2 seconds:!!!!! Success rate is 100 percent, round-trip min/avg/max = 1/3/4 ms Save Your Device Configuration This section describes how to avoid losing your configuration at the next system reload or power cycle by saving the running configuration to the startup configuration in NVRAM. The NVRAM provides 256KB of storage on the router. 20
21 Save Backup Copies of Configuration and System Image 1. enable 2. copy running-config startup-config enable Enables privileged EXEC mode. Enter your password if prompted. copy running-config startup-config Saves the running configuration to the startup configuration. Router# copy running-config startup-config Save Backup Copies of Configuration and System Image To aid file recovery and minimize downtime in case of file corruption, we recommend that you save backup copies of the startup configuration file and the Cisco IOS-XE software system image file on a server. 1. enable 2. copy nvram:startup-config {ftp: rcp: tftp:} 3. show {bootflash0 bootflash1}: 4. copy {bootflash0 bootflash1}: {ftp: rcp: tftp:} enable Enables privileged EXEC mode. Enter your password if prompted. Step 3 copy nvram:startup-config {ftp: rcp: tftp:} Router# copy nvram:startup-config ftp: show {bootflash0 bootflash1}: Copies the startup configuration file to a server. The configuration file copy can serve as a backup copy.enter the destination URL when prompted. Displays the layout and contents of a flash memory file system. Learn the name of the system image file. Router# show {bootflash0 bootflash1}: 21
22 Configuration Examples Step 4 copy {bootflash0 bootflash1}: {ftp: rcp: tftp:} Router# copy {bootflash0 bootflash1}: ftp: Copies a file from flash memory to a server. Copy the system image file to a server to serve as a backup copy. Enter the filename and destination URL when prompted. Configuration Examples Copying the Startup Configuration to a TFTP Server: Example The following example shows the startup configuration being copied to a TFTP server: Router# copy nvram:startup-config tftp: Remote host[]? Name of configuration file to write [rtr2-confg]? <cr> Write file rtr2-confg on host ?[confirm] <cr>![ok] Copying from Flash Memory to a TFTP Server: Example The following example shows the use of the show {flash0 flash1}: command in privileged EXEC to learn the name of the system image file and the use of the copy {flash0 flash1}: tftp: privileged EXEC command to copy the system image to a TFTP server. The router uses the default username and password. Router#Directory of bootflash: 11 drwx Jun :31:45 +00:00 lost+found drwx Sep :33:26 +00:00 core drwx 4096 Oct :28:27 +00:00.prst_sync drwx 4096 Jun :32:39 +00:00.rollback_timer 12 -rw- 0 Jun :32:50 +00:00 tracelogs drwx Oct :24:26 +00:00 tracelogs drwx 4096 Jun :32:51 +00:00.installer drwx 4096 Jul :14:51 +00:00 vman_fdb 13 -rw Aug :01:31 +00:00 crankshaft-universalk9.bld_mcp_dev_latest_ _ ssa.bin 14 -rw Aug :03:25 +00:00 uut2_2000_ikev1.cfg 15 -rw Aug :40:28 +00:00 crankshaft-universalk9.bld_mcp_dev_latest_ _ ssa.bin 16 -rw Aug :24:38 +00:00 base.cfg 17 -rw Aug :10:02 +00:00 uut2_1000_ikev1.cfg 18 -rw Aug :34:19 +00:00 crankshaft-universalk9.bld_mcp_dev_latest_ _ ssa.bin 19 -rw Aug :31:57 +00:00 crankshaft-universalk9.bld_mcp_dev_latest_ _ ssa.bin 20 -rw Sep :48:15 +00:00 uut2_1000_ikev1_v2.cfg 21 -rw Sep :36:20 +00:00 upgrade_stage_1_of_1.bin delta 22 -rw Sep :28:23 +00:00 crankshaft-universalk _00.45_cveerapa.ssa.bin 23 -rw Oct :43:36 +00:00 old-config.conf 24 -rw Oct :34:08 +00:00 _1010t.bin bytes total ( bytes free) Router#show bootflash: -#- --length date/time path Oct :22:19 +00:00 /bootflash/ Jun :31:45 +00:00 /bootflash/lost+found Sep :33:26 +00:00 /bootflash/core Sep :31:17 +00:00 /bootflash/core/uut2_rp_0_iomd_17360.core.gz Sep :31:24 +00:00 /bootflash/core/uut2_rp_0_iomd_23385.core.gz Sep :31:30 +00:00 /bootflash/core/uut2_rp_0_iomd_24973.core.gz Sep :31:37 +00:00 /bootflash/core/uut2_rp_0_iomd_26241.core.gz Sep :31:43 +00:00 /bootflash/core/uut2_rp_0_iomd_27507.core.gz Sep :31:50 +00:00 22
23 Verify Initial Configuration on Cisco 4000 Series ISRs /bootflash/core/uut2_rp_0_iomd_28774.core.gz Sep :31:56 +00:00 /bootflash/core/uut2_rp_0_iomd_30045.core.gz Sep :32:02 +00:00 /bootflash/core/uut2_rp_0_iomd_31332.core.gz Sep :32:09 +00:00 /bootflash/core/uut2_rp_0_iomd_5528.core.gz Sep :32:15 +00:00 /bootflash/core/uut2_rp_0_iomd_7950.core.gz Sep :32:22 +00:00 /bootflash/core/uut2_rp_0_iomd_9217.core.gz Sep :32:28 +00:00 /bootflash/core/uut2_rp_0_iomd_10484.core.gz Sep :32:35 +00:00 /bootflash/core/uut2_rp_0_iomd_11766.core.gz Sep :32:41 +00:00 /bootflash/core/uut2_rp_0_iomd_13052.core.gz Sep :32:48 +00:00 /bootflash/core/uut2_rp_0_iomd_14351.core.gz Sep :32:54 +00:00 /bootflash/core/uut2_rp_0_iomd_15644.core.gz Sep :33:00 +00:00 /bootflash/core/uut2_rp_0_iomd_17171.core.gz Sep :33:07 +00:00 /bootflash/core/uut2_rp_0_iomd_18454.core.gz Sep :33:13 +00:00 /bootflash/core/uut2_rp_0_iomd_19741.core.gz Sep :33:20 +00:00 /bootflash/core/uut2_rp_0_iomd_21039.core.gz Sep :33:26 +00:00 /bootflash/core/uut2_rp_0_iomd_22323.core.gz Oct :28:27 +00:00 /bootflash/.prst_sync Jun :32:39 +00:00 /bootflash/.rollback_timer 27 0 Jun :32:50 +00:00 /bootflash/tracelogs Oct :24:26 +00:00 /bootflash/tracelogs Oct :22:19 +00:00 /bootflash/tracelogs/inst_cleanup_r0-0.log.gz Oct :39:43 +00:00 /bootflash/tracelogs/inst_cleanup_r0-0.log gz Oct :49:44 +00:00 /bootflash/tracelogs/inst_cleanup_r0-0.log gz Oct :35:39 +00:00 /bootflash/tracelogs/hman_r0-0.log gz Oct :59:45 +00:00 /bootflash/tracelogs/inst_cleanup_r0-0.log gz Oct :19:47 +00:00 /bootflash/tracelogs/inst_cleanup_r0-0.log gz Oct :37:14 +00:00 /bootflash/tracelogs/inst_cleanup_r0-0.log gz Oct :47:15 +00:00 /bootflash/tracelogs/inst_cleanup_r0-0.log gz Oct :57:16 +00:00 /bootflash/tracelogs/inst_cleanup_r0-0.log gz Oct :07:17 +00:00 /bootflash/tracelogs/inst_cleanup_r0-0.log gz Oct :12:18 +00:00 /bootflash/tracelogs/inst_cleanup_r0-0.log gz Oct :17:18 +00:00 /bootflash/tracelogs/inst_cleanup_r0-0.log gz Oct :47:42 +00:00 /bootflash/tracelogs/hman_r0-0.log gz Oct :47:59 +00:00 /bootflash/tracelogs/fman-fp_f0-0.log gz Oct :27:03 +00:00 /bootflash/tracelogs/inst_compmatrix_r0-0.log.gz Oct :24:41 +00:00 /bootflash/tracelogs/inst_cleanup_r0-0.log gz Oct :29:42 +00:00 /bootflash/tracelogs/inst_cleanup_r0-0.log gz Oct :49:19 +00:00 /bootflash/tracelogs/hman_r0-0.log gz Oct :44:43 +00:00 /bootflash/tracelogs/inst_cleanup_r0-0.log gz Oct :04:46 +00:00 /bootflash/tracelogs/inst_cleanup_r0-0.log gz Oct :21:49 +00:00 /bootflash/tracelogs/iosrp_r0-0.log Oct :06:44 +00:00 /bootflash/tracelogs/binos_log_r0-0.log Note To avoid losing work you have completed, be sure to save your configuration occasionally as you proceed. Use the copy running-config startup-config command to save the configuration to NVRAM. Verify Initial Configuration on Cisco 4000 Series ISRs Enter the following commands at Cisco IOS-XE to verify the initial configuration on the router: show version Displays the system hardware version; the installed software version; the names and sources of configuration files; the boot images; and the amount of installed DRAM, NVRAM, and flash memory. 23
24 Verify Initial Configuration on Cisco 4000 Series ISRs show diag Lists and displays diagnostic information about the installed controllers, interface processors, and port adapters. show interfaces Shows interfaces are operating correctly and that the interfaces and line protocol are in the correct state; either up or down. show ip interface brief Displays a summary status of the interfaces configured for IP protocol. show configuration Verifies that you have configured the correct hostname and password. show platform Displays the software/rommon version, and so on. When you have completed and verified the initial configuration, specific features and functions are ready to be configured. See the Software Configuration Guide for the Cisco 4400 and Cisco 4300 Series ISRs. 24
Chapter 6: Network Layer
 Chapter 6: Network Layer Introduction to Networks Intro to Networks v5 Network Layer Intro to Networks v5 2 The Network Layer End to End Transport processes Addressing end devices Encapsulation of Packets
Chapter 6: Network Layer Introduction to Networks Intro to Networks v5 Network Layer Intro to Networks v5 2 The Network Layer End to End Transport processes Addressing end devices Encapsulation of Packets
Basic Router Configuration
 This section includes information about some basic router configuration, and contains the following sections: Default Configuration, on page 1 Configuring Global Parameters, on page 2 Configuring Gigabit
This section includes information about some basic router configuration, and contains the following sections: Default Configuration, on page 1 Configuring Global Parameters, on page 2 Configuring Gigabit
Lab Configuring IPv4 Static and Default Routes (Solution)
 (Solution) Topology Addressing Table Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.0.1 255.255.255.0 N/A S0/0/1 10.1.1.1 255.255.255.252 N/A R3 G0/1 192.168.1.1 255.255.255.0
(Solution) Topology Addressing Table Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.0.1 255.255.255.0 N/A S0/0/1 10.1.1.1 255.255.255.252 N/A R3 G0/1 192.168.1.1 255.255.255.0
Lab - Troubleshooting Connectivity Issues
 Lab - Troubleshooting Connectivity Issues Topology Addressing Table R1 ISP Objectives Device Interface IP Address Subnet Mask Default Gateway G0/1 192.168.1.1 255.255.255.0 N/A S0/0/0 10.1.1.1 255.255.255.252
Lab - Troubleshooting Connectivity Issues Topology Addressing Table R1 ISP Objectives Device Interface IP Address Subnet Mask Default Gateway G0/1 192.168.1.1 255.255.255.0 N/A S0/0/0 10.1.1.1 255.255.255.252
Initial Configuration for the Switch
 Options for Initial Configuration, page 1 Configuring the Switch Using the Web User Interface, page 1 Configuring the Switch Using the CLI, page 4 Configuring the Switch in the ROMMON Mode, page 12 Options
Options for Initial Configuration, page 1 Configuring the Switch Using the Web User Interface, page 1 Configuring the Switch Using the CLI, page 4 Configuring the Switch in the ROMMON Mode, page 12 Options
Lab 2.8.1: Basic Static Route Configuration
 Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway R1 Fa0/0 172.16.3.1 255.255.255.0 N/A S0/0/0 172.16.2.1 255.255.255.0 N/A Fa0/0 172.16.1.1 255.255.255.0 N/A R2
Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway R1 Fa0/0 172.16.3.1 255.255.255.0 N/A S0/0/0 172.16.2.1 255.255.255.0 N/A Fa0/0 172.16.1.1 255.255.255.0 N/A R2
Chapter 10 - Configure ASA Basic Settings and Firewall using ASDM
 Chapter 10 - Configure ASA Basic Settings and Firewall using ASDM This lab has been updated for use on NETLAB+ Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces.
Chapter 10 - Configure ASA Basic Settings and Firewall using ASDM This lab has been updated for use on NETLAB+ Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces.
Building the Routing Table. Introducing the Routing Table Directly Connected Networks Static Routing Dynamic Routing Routing Table Principles
 Building the Routing Table Introducing the Routing Table Directly Connected Networks Static Routing Dynamic Routing Routing Table Principles Introducing the Routing Table R1# show ip route Codes: C - connected,
Building the Routing Table Introducing the Routing Table Directly Connected Networks Static Routing Dynamic Routing Routing Table Principles Introducing the Routing Table R1# show ip route Codes: C - connected,
Lab Configuring IGRP Instructor Version 2500
 Lab 7.3.5 Configuring IGRP Instructor Version 2500 Objective Setup IP an addressing scheme using class C networks. Configure IGRP on routers. Background/Preparation Cable a network similar to the one in
Lab 7.3.5 Configuring IGRP Instructor Version 2500 Objective Setup IP an addressing scheme using class C networks. Configure IGRP on routers. Background/Preparation Cable a network similar to the one in
RR> RR> RR>en RR# RR# RR# RR# *Oct 2 04:57:03.684: %AMDP2_FE-6-EXCESSCOLL: Ethernet0/2 TDR=0, TRC=0 RR#
 RR> RR> RR>en *Oct 2 04:57:03.684: %AMDP2_FE-6-EXCESSCOLL: Ethernet0/2 TDR=0, TRC=0 term len 0 show run Building configuration... Current configuration : 2568 bytes version 15.4 service timestamps debug
RR> RR> RR>en *Oct 2 04:57:03.684: %AMDP2_FE-6-EXCESSCOLL: Ethernet0/2 TDR=0, TRC=0 term len 0 show run Building configuration... Current configuration : 2568 bytes version 15.4 service timestamps debug
First-Time Configuration
 This chapter describes the actions to take before turning on your router for the first time Setup Mode, on page 1 Verifying the Cisco IOS Software Version, on page 4 Configuring the Hostname and Password,
This chapter describes the actions to take before turning on your router for the first time Setup Mode, on page 1 Verifying the Cisco IOS Software Version, on page 4 Configuring the Hostname and Password,
Lab 7 Configuring Basic Router Settings with IOS CLI
 Lab 7 Configuring Basic Router Settings with IOS CLI Objectives Part 1: Set Up the Topology and Initialize Devices Cable equipment to match the network topology. Initialize and restart the router and switch.
Lab 7 Configuring Basic Router Settings with IOS CLI Objectives Part 1: Set Up the Topology and Initialize Devices Cable equipment to match the network topology. Initialize and restart the router and switch.
Powering On the Cisco VG224 Voice Gateway
 CHAPTER 4 To power on your Cisco VG224 voice gateway, perform the following tasks in the order listed, as required: Checklist for Power-On, page 4-1 Power-On Procedure, page 4-1 Initial Configuration Procedures,
CHAPTER 4 To power on your Cisco VG224 voice gateway, perform the following tasks in the order listed, as required: Checklist for Power-On, page 4-1 Power-On Procedure, page 4-1 Initial Configuration Procedures,
Chapter 7 Lab 7-1, Configuring BGP with Default Routing
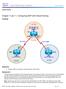 Chapter 7 Topology Objectives Configure BGP to exchange routing information with two ISPs. Background The International Travel Agency (ITA) relies extensively on the Internet for sales. For this reason,
Chapter 7 Topology Objectives Configure BGP to exchange routing information with two ISPs. Background The International Travel Agency (ITA) relies extensively on the Internet for sales. For this reason,
Lab Configuring Per-Interface Inter-VLAN Routing (Solution)
 (Solution) Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/0 192.168.20.1 255.255.255.0 N/A G0/1 192.168.10.1 255.255.255.0 N/A S1 VLAN 10 192.168.10.11
(Solution) Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/0 192.168.20.1 255.255.255.0 N/A G0/1 192.168.10.1 255.255.255.0 N/A S1 VLAN 10 192.168.10.11
Using the Management Ethernet Interface
 This chapter covers the following topics: Gigabit Ethernet Management Interface Overview, page 1 Gigabit Ethernet Port Numbering, page 1 IP Address Handling in ROMmon and the Management Ethernet Port,
This chapter covers the following topics: Gigabit Ethernet Management Interface Overview, page 1 Gigabit Ethernet Port Numbering, page 1 IP Address Handling in ROMmon and the Management Ethernet Port,
Using the Management Ethernet Interface
 The Cisco ASR 920 Series Router has one Gigabit Ethernet Management Ethernet interface on each Route Switch Processor. The purpose of this interface is to allow users to perform management tasks on the
The Cisco ASR 920 Series Router has one Gigabit Ethernet Management Ethernet interface on each Route Switch Processor. The purpose of this interface is to allow users to perform management tasks on the
TELECOMMUNICATION MANAGEMENT AND NETWORKS
 QUAID-E-AWAM UNIVERSITY OF ENGINEERING SCIENCE AND TECHNOLOGY, NAWABSHAH TELECOMMUNICATION MANAGEMENT AND NETWORKS LAB # 3 CONFIGURING INTERFACES OF ROUTER AND SWITCH Topology Diagram Addressing Table
QUAID-E-AWAM UNIVERSITY OF ENGINEERING SCIENCE AND TECHNOLOGY, NAWABSHAH TELECOMMUNICATION MANAGEMENT AND NETWORKS LAB # 3 CONFIGURING INTERFACES OF ROUTER AND SWITCH Topology Diagram Addressing Table
Lab Configuring Per-Interface Inter-VLAN Routing (Instructor Version)
 (Instructor Version) Instructor Note: Red font color or Gray highlights indicate text that appears in the instructor copy only. Topology Addressing Table Objectives Device Interface IP Address Subnet Mask
(Instructor Version) Instructor Note: Red font color or Gray highlights indicate text that appears in the instructor copy only. Topology Addressing Table Objectives Device Interface IP Address Subnet Mask
Lab Configuring Basic Router Settings with IOS CLI (Instructor Version Optional Lab)
 (Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
(Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
How to Configure a Cisco Router Behind a Non-Cisco Cable Modem
 How to Configure a Cisco Router Behind a Non-Cisco Cable Modem Document ID: 19268 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations Verify
How to Configure a Cisco Router Behind a Non-Cisco Cable Modem Document ID: 19268 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations Verify
This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document for non-commercial distribution and
 This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document for non-commercial distribution and exclusive use by instructors in the CCNA Exploration:
This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document for non-commercial distribution and exclusive use by instructors in the CCNA Exploration:
Module 9, Assignment 7
 Module 9, Assignment 7 7.2.3 Control Router via Console (in Packet Tracer) 1. Prepare a Cisco 1841 Router (see figure 6-9). 2. Prepare a PC for administration. 3. Prepare a console cable and plug the serial
Module 9, Assignment 7 7.2.3 Control Router via Console (in Packet Tracer) 1. Prepare a Cisco 1841 Router (see figure 6-9). 2. Prepare a PC for administration. 3. Prepare a console cable and plug the serial
Lab 4.2.5a Connectivity Tests Ping
 Lab 4.2.5a Connectivity Tests Ping Objective Use the ping command to send ICMP datagrams to target host. Verify that the network layer between source and destination is working properly. Retrieve information
Lab 4.2.5a Connectivity Tests Ping Objective Use the ping command to send ICMP datagrams to target host. Verify that the network layer between source and destination is working properly. Retrieve information
Using Cisco IOS XE Software
 This chapter describes the basics of using the Cisco IOS XE software and includes the following section: Accessing the CLI Using a Router Console, on page 1 Accessing the CLI Using a Router Console Before
This chapter describes the basics of using the Cisco IOS XE software and includes the following section: Accessing the CLI Using a Router Console, on page 1 Accessing the CLI Using a Router Console Before
KIM DONNERBORG / RTS. Cisco Lab Øvelse Af Kim Donnerborg / RTS. Side 0 af 8
 KIM DONNERBORG / RTS Side 0 af 8 INDHOLDSFORTEGNELSE Lab: Basic Router Configuration... 2 Topology Diagram... 2 Addressing Table... 2 Learning Objectives... 2 Scenario... 2 Task 1: Cable the Network....
KIM DONNERBORG / RTS Side 0 af 8 INDHOLDSFORTEGNELSE Lab: Basic Router Configuration... 2 Topology Diagram... 2 Addressing Table... 2 Learning Objectives... 2 Scenario... 2 Task 1: Cable the Network....
Lab- Troubleshooting Basic EIGRP for 1Pv4
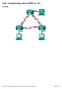 Lab- Troubleshooting Basic EIGRP for 1Pv4 Topology G0/0 G0/0 PC-A PC-C 2013 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 27 Addressing Table efault Gateway
Lab- Troubleshooting Basic EIGRP for 1Pv4 Topology G0/0 G0/0 PC-A PC-C 2013 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 27 Addressing Table efault Gateway
Chapter 11. Configuring and Testing Your Network
 Chapter 11 Configuring and Testing Your Network CCNA1-1 Chapter 11 Note for Instructors These presentations are the result of a collaboration among the instructors at St. Clair College in Windsor, Ontario.
Chapter 11 Configuring and Testing Your Network CCNA1-1 Chapter 11 Note for Instructors These presentations are the result of a collaboration among the instructors at St. Clair College in Windsor, Ontario.
Lab Configuring and Verifying Standard IPv4 ACLs (Instructor Version Optional Lab)
 (Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
(Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
Chapter 7 Lab 7-2, Using the AS_PATH Attribute
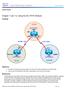 Chapter 7 Topology Objectives Use BGP commands to prevent private AS numbers from being advertised to the outside world. Use the AS_PATH attribute to filter BGP routes based on their source AS numbers.
Chapter 7 Topology Objectives Use BGP commands to prevent private AS numbers from being advertised to the outside world. Use the AS_PATH attribute to filter BGP routes based on their source AS numbers.
Checklists for Configuring the Gateway
 CHAPTER 7 The Cisco Unified Communications Manager Business Edition 3000 uses either Cisco 2901 Integrated Services Router (ISR2901) or Cisco Media Convergence Server 7890C1 (MCS7890-C1) to serve as your
CHAPTER 7 The Cisco Unified Communications Manager Business Edition 3000 uses either Cisco 2901 Integrated Services Router (ISR2901) or Cisco Media Convergence Server 7890C1 (MCS7890-C1) to serve as your
Upgrading the Cisco IOS XE Software
 Prerequisites for the Software Upgrade Process, page 1 Saving Backup Copies of Your Old System Image and Configuration, page 2 Using TFTP or Remote Copy Protocol to Copy the System Image into Boot Flash
Prerequisites for the Software Upgrade Process, page 1 Saving Backup Copies of Your Old System Image and Configuration, page 2 Using TFTP or Remote Copy Protocol to Copy the System Image into Boot Flash
Lab VTY Restriction Instructor Version 2500
 Lab 11.2.6 VTY Restriction Instructor Version 2500 NOTE: The loopback entry in this graphic is not required in the lab. Objective Scenario Use the access-class and line commands to control Telnet access
Lab 11.2.6 VTY Restriction Instructor Version 2500 NOTE: The loopback entry in this graphic is not required in the lab. Objective Scenario Use the access-class and line commands to control Telnet access
Lab Troubleshooting Routing Issues with show ip route and show ip protocols Instructor Version 2500
 Lab 9.3.5 Troubleshooting Routing Issues with show ip route and show ip protocols Instructor Version 2500 Objective Use the show ip route and show ip protocol commands to diagnose a routing configuration
Lab 9.3.5 Troubleshooting Routing Issues with show ip route and show ip protocols Instructor Version 2500 Objective Use the show ip route and show ip protocol commands to diagnose a routing configuration
Lab Troubleshooting Using traceroute Instructor Version 2500
 Lab 9.3.4 Troubleshooting Using traceroute Instructor Version 2500 294-833 CCNA 2: Routers and Routing Basics v 3.1 - Lab 9.3.4 Copyright 2003, Cisco Systems, Inc. Objective Use the traceroute Cisco IOS
Lab 9.3.4 Troubleshooting Using traceroute Instructor Version 2500 294-833 CCNA 2: Routers and Routing Basics v 3.1 - Lab 9.3.4 Copyright 2003, Cisco Systems, Inc. Objective Use the traceroute Cisco IOS
Configurations for the Layer 3 Switch Router
 CHAPTER 3 This chapter describes the initial configuration of the Layer 3 switch router and contains the following major sections: Starting Up the Layer 3 Switch Router, page 3-1 Using the Console and
CHAPTER 3 This chapter describes the initial configuration of the Layer 3 switch router and contains the following major sections: Starting Up the Layer 3 Switch Router, page 3-1 Using the Console and
Using the Management Interfaces
 The following management interfaces are provided for external users and applications: Gigabit Ethernet Management Interface, page 1 SNMP, page 7 Gigabit Ethernet Management Interface Gigabit Ethernet Management
The following management interfaces are provided for external users and applications: Gigabit Ethernet Management Interface, page 1 SNMP, page 7 Gigabit Ethernet Management Interface Gigabit Ethernet Management
SEMESTER 2 Chapter 1 Planning and Cabling a Network V 4.0
 SEMESTER 2 Chapter 1 Planning and Cabling a Network V 4.0 135 points 1.1.1 What are the common components between a router and other computers? CPU RAM ROM Operating System 1.1.1.2 What does a router connect?
SEMESTER 2 Chapter 1 Planning and Cabling a Network V 4.0 135 points 1.1.1 What are the common components between a router and other computers? CPU RAM ROM Operating System 1.1.1.2 What does a router connect?
Lab Troubleshooting Routing Issues with debug Instructor Version 2500
 Lab 9.3.7 Troubleshooting Routing Issues with debug Instructor Version 2500 Objective Utilize a systematic OSI troubleshooting process to diagnose routing problems. Use various show commands to gather
Lab 9.3.7 Troubleshooting Routing Issues with debug Instructor Version 2500 Objective Utilize a systematic OSI troubleshooting process to diagnose routing problems. Use various show commands to gather
Chapter 1 Lab 1-1, Basic RIPng and Default Gateway Configuration
 Chapter 1 Lab 1-1, Basic RIPng and Default Gateway Configuration Topology Objectives Configure IPv6 addressing. Configure and verify RIPng on R1 and R2. Configure IPv6 static routes between R2 and R3.
Chapter 1 Lab 1-1, Basic RIPng and Default Gateway Configuration Topology Objectives Configure IPv6 addressing. Configure and verify RIPng on R1 and R2. Configure IPv6 static routes between R2 and R3.
Lab Configuring OSPF Timers 2500 Series
 Lab 2.3.5 Configuring OSPF Timers 2500 Series Objective Setup an IP addressing scheme for OSPF area. Configure and verify OSPF routing. Modify OSPF interface timers to adjust efficiency of network. Background/Preparation
Lab 2.3.5 Configuring OSPF Timers 2500 Series Objective Setup an IP addressing scheme for OSPF area. Configure and verify OSPF routing. Modify OSPF interface timers to adjust efficiency of network. Background/Preparation
Packet Tracer - Connect a Router to a LAN (Instructor Version)
 (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Topology Addressing Table Device Interface IP Address Subnet Mask Default
(Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Topology Addressing Table Device Interface IP Address Subnet Mask Default
Lab 1. CLI Navigation. Scenario. Initial Configuration for R1
 Lab 1 CLI Navigation This lab covers the most basic skills for accessing and using the command-line interface (CLI) on a Cisco router or switch. Many of the small, picky details of how the CLI works cannot
Lab 1 CLI Navigation This lab covers the most basic skills for accessing and using the command-line interface (CLI) on a Cisco router or switch. Many of the small, picky details of how the CLI works cannot
LAB5: OSPF IPv4. OSPF: Stub. Disclaimer
 Page1 LAB5: SPF IPv4 Disclaimer This onfiguration Guide is designed to assist members to enhance their skills in respective technology area. While every effort has been made to ensure that all material
Page1 LAB5: SPF IPv4 Disclaimer This onfiguration Guide is designed to assist members to enhance their skills in respective technology area. While every effort has been made to ensure that all material
Lab Configuring and Verifying Standard IPv4 ACLs Topology
 Topology 2016 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 10 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.10.1
Topology 2016 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 10 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.10.1
Configuration File Management Commands
 This chapter provides detailed descriptions of commands used to manage configuration files in Cisco IOS Release 12.2. Configuration files contain the set of commands used to customize the function of the
This chapter provides detailed descriptions of commands used to manage configuration files in Cisco IOS Release 12.2. Configuration files contain the set of commands used to customize the function of the
Configuring Easy Virtual Network Shared Services
 Configuring Easy Virtual Network Shared Services This chapter describes how to use route replication and redistribution to share services in an Easy Virtual Network (EVN). Finding Feature Information,
Configuring Easy Virtual Network Shared Services This chapter describes how to use route replication and redistribution to share services in an Easy Virtual Network (EVN). Finding Feature Information,
Lab Configuring Basic RIPv2 (Solution)
 (Solution) Topology 2017 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 15 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway
(Solution) Topology 2017 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 15 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway
Lab Using the CLI to Gather Network Device Information Topology
 Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.1.1 255.255.255.0 N/A Lo0 209.165.200.225 255.255.255.224 N/A S1 VLAN 1 192.168.1.11 255.255.255.0
Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.1.1 255.255.255.0 N/A Lo0 209.165.200.225 255.255.255.224 N/A S1 VLAN 1 192.168.1.11 255.255.255.0
CCNA Explorer 1 Chapter 11 Configuring & Testing Your Network
 CCNA Explorer 1 Chapter 11 Configuring & Testing Your Network 11.1.1 What is the system software in Cisco devices? The Cisco IOS provides devices with what network services? How is the IOS generally accessed?
CCNA Explorer 1 Chapter 11 Configuring & Testing Your Network 11.1.1 What is the system software in Cisco devices? The Cisco IOS provides devices with what network services? How is the IOS generally accessed?
Lab: Basic Static Route Configuration
 Lab: Basic Static Route onfiguration Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway R1 Fa0/0 172.16.3.1 255.255.255.0 N/A S0/0/0 172.16.2.1 255.255.255.0 N/A
Lab: Basic Static Route onfiguration Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway R1 Fa0/0 172.16.3.1 255.255.255.0 N/A S0/0/0 172.16.2.1 255.255.255.0 N/A
CCNA 1 Chapter 2 v5.0 Exam Answers %
 CCNA 1 Chapter 2 v5.0 Exam Answers 2015 100% 1. Which two features are characteristics of flash memory? (Choose two.) Flash provides nonvolatile storage. Flash receives a copy of the IOS from RAM when
CCNA 1 Chapter 2 v5.0 Exam Answers 2015 100% 1. Which two features are characteristics of flash memory? (Choose two.) Flash provides nonvolatile storage. Flash receives a copy of the IOS from RAM when
Lab Securing Network Devices
 Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.1.1 255.255.255.0 N/A S1 VLAN 1 192.168.1.11 255.255.255.0 192.168.1.1 PC-A NIC 192.168.1.3
Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.1.1 255.255.255.0 N/A S1 VLAN 1 192.168.1.11 255.255.255.0 192.168.1.1 PC-A NIC 192.168.1.3
Lab Catalyst 2950T and 3550 Series Basic Setup
 Lab 1.2.9.1 Catalyst 2950T and 3550 Series Basic Setup Objective Configure a Cisco Catalyst 2950T or 3550 series Ethernet switch for the first time using the command-line interface (CLI) mode. Basic first
Lab 1.2.9.1 Catalyst 2950T and 3550 Series Basic Setup Objective Configure a Cisco Catalyst 2950T or 3550 series Ethernet switch for the first time using the command-line interface (CLI) mode. Basic first
Chapter 6 Lab 6-3, Configuring IBGP and EBGP Sessions, Local Preference, and MED
 Chapter 6 Lab 6-3, Configuring IBGP and EBGP Sessions, Local Preference, and MED Topology Objectives Background For IBGP peers to correctly exchange routing information, use the next-hop-self command with
Chapter 6 Lab 6-3, Configuring IBGP and EBGP Sessions, Local Preference, and MED Topology Objectives Background For IBGP peers to correctly exchange routing information, use the next-hop-self command with
No Service Password-Recovery
 No Service Password-Recovery Last Updated: January 18, 2012 The No Service Password-Recovery feature is a security enhancement that prevents anyone with console access from accessing the router configuration
No Service Password-Recovery Last Updated: January 18, 2012 The No Service Password-Recovery feature is a security enhancement that prevents anyone with console access from accessing the router configuration
Lab : Challenge OSPF Configuration Lab. Topology Diagram. Addressing Table. Default Gateway. Device Interface IP Address Subnet Mask
 Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway Fa0/0 HQ S0/0/0 S0/0/1 Lo1 10.10.10.1 255.255.255.252 Fa0/0 Branch1 S0/0/0 S0/0/1 Fa0/0 Branch2 S0/0/0 S0/0/1 PC1
Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway Fa0/0 HQ S0/0/0 S0/0/1 Lo1 10.10.10.1 255.255.255.252 Fa0/0 Branch1 S0/0/0 S0/0/1 Fa0/0 Branch2 S0/0/0 S0/0/1 PC1
Chapter 5 Lab 5-1 Inter-VLAN Routing INSTRUCTOR VERSION
 CCNPv7.1 SWITCH Chapter 5 Lab 5-1 Inter-VLAN Routing INSTRUCTOR VERSION Topology Objectives Implement a Layer 3 EtherChannel Implement Static Routing Implement Inter-VLAN Routing Background Cisco's switching
CCNPv7.1 SWITCH Chapter 5 Lab 5-1 Inter-VLAN Routing INSTRUCTOR VERSION Topology Objectives Implement a Layer 3 EtherChannel Implement Static Routing Implement Inter-VLAN Routing Background Cisco's switching
CCNA Semester 2 labs. Labs for chapters 2 10
 CCNA Semester 2 labs Labs for chapters 2 10 2.2.2.5 Lab - Configuring IPv4 Static and Default Routes 2.3.2.4 Lab - Troubleshooting Static Routes 3.2.1.9 Lab - Configuring Basic RIPv2 5.2.2.9 Lab - Configuring
CCNA Semester 2 labs Labs for chapters 2 10 2.2.2.5 Lab - Configuring IPv4 Static and Default Routes 2.3.2.4 Lab - Troubleshooting Static Routes 3.2.1.9 Lab - Configuring Basic RIPv2 5.2.2.9 Lab - Configuring
Lab Configuring Static Routes Instructor Version 2500
 Lab 6.1.6 Configuring Static Routes Instructor Version 2500 Objective Configure static routes between routers to allow data transfer between routers without the use of dynamic routing protocols. Background/Preparation
Lab 6.1.6 Configuring Static Routes Instructor Version 2500 Objective Configure static routes between routers to allow data transfer between routers without the use of dynamic routing protocols. Background/Preparation
Using Setup Mode to Configure a Cisco Networking Device
 Using Setup Mode to Configure a Cisco Networking Device First Published: August 9, 2005 Last Updated: December 3, 2010 Setup mode provides an interactive menu to help you to create an initial configuration
Using Setup Mode to Configure a Cisco Networking Device First Published: August 9, 2005 Last Updated: December 3, 2010 Setup mode provides an interactive menu to help you to create an initial configuration
RealCiscoLAB.com. Chapter 6 Lab 6-2, Using the AS_PATH Attribute. Topology. Objectives. Background. CCNPv6 ROUTE
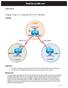 RealCiscoLAB.com CCNPv6 ROUTE Chapter 6 Lab 6-2, Using the AS_PATH Attribute Topology Objectives Background Use BGP commands to prevent private AS numbers from being advertised to the outside world. Use
RealCiscoLAB.com CCNPv6 ROUTE Chapter 6 Lab 6-2, Using the AS_PATH Attribute Topology Objectives Background Use BGP commands to prevent private AS numbers from being advertised to the outside world. Use
MiPDF.COM. 3. Which procedure is used to access a Cisco 2960 switch when performing an initial configuration in a secure environment?
 CCNA1 v6.0 Chapter 2 Exam Answers 2017 (100%) MiPDF.COM 1. What is the function of the kernel of an operating software? It provides a user interface that allows users to request a specific task. The kernel
CCNA1 v6.0 Chapter 2 Exam Answers 2017 (100%) MiPDF.COM 1. What is the function of the kernel of an operating software? It provides a user interface that allows users to request a specific task. The kernel
Chapter 4: Routing Concepts. Routing & Switching
 Chapter 4: Routing Concepts Routing & Switching Routers are Computers Routers are specialized computers containing the following required components to operate: Central processing unit (CPU) Operating
Chapter 4: Routing Concepts Routing & Switching Routers are Computers Routers are specialized computers containing the following required components to operate: Central processing unit (CPU) Operating
1. Which OSI layers offers reliable, connection-oriented data communication services?
 CCNA 1 Practice Final Exam Answers v4.0 100% 1. Which OSI layers offers reliable, connection-oriented data communication services? application presentation session transport network 2. Refer to the exhibit.
CCNA 1 Practice Final Exam Answers v4.0 100% 1. Which OSI layers offers reliable, connection-oriented data communication services? application presentation session transport network 2. Refer to the exhibit.
Lab Troubleshooting IPv4 and IPv6 Static Routes (Instructor Version Optional Lab)
 (Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
(Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
Lab Configuring 802.1Q Trunk-Based Inter-VLAN Routing (Instructor Version Optional Lab)
 (Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
(Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
Using the Cisco NX-OS Setup Utility
 This chapter contains the following sections: Configuring the Switch, page 1 Configuring the Switch Image Files on the Switch The Cisco Nexus devices have the following images: BIOS and loader images combined
This chapter contains the following sections: Configuring the Switch, page 1 Configuring the Switch Image Files on the Switch The Cisco Nexus devices have the following images: BIOS and loader images combined
Cisco IOS Commands. abort CHAPTER
 CHAPTER 2 abort Use the abort VLAN database command to abandon the proposed new VLAN database, exit VLAN database mode, and return to privileged EXEC mode. abort This command has no arguments or keywords.
CHAPTER 2 abort Use the abort VLAN database command to abandon the proposed new VLAN database, exit VLAN database mode, and return to privileged EXEC mode. abort This command has no arguments or keywords.
CCNA 1 Chapter 2 v5.0 Exam Answers 2013
 CCNA 1 Chapter 2 v5.0 Exam Answers 2013 1. Refer to the exhibit. A switch was configured as shown. A ping to the default gateway was issued, but the ping was not successful. Other switches in the same
CCNA 1 Chapter 2 v5.0 Exam Answers 2013 1. Refer to the exhibit. A switch was configured as shown. A ping to the default gateway was issued, but the ping was not successful. Other switches in the same
Lab 3: Basic Device Configuration
 Lab 3: Basic Device Configuration University of Jordan Faculty of Engineering & Technology Computer Engineering Department Computer Networks Laboratory 907528 2 Lab 3: Basic Device Configuration **Given
Lab 3: Basic Device Configuration University of Jordan Faculty of Engineering & Technology Computer Engineering Department Computer Networks Laboratory 907528 2 Lab 3: Basic Device Configuration **Given
Using Setup Mode to Configure a Cisco Networking Device
 Using Setup Mode to Configure a Cisco Networking Device Setup mode provides an interactive menu to help you to create an initial configuration file for a new networking device, or a device that you have
Using Setup Mode to Configure a Cisco Networking Device Setup mode provides an interactive menu to help you to create an initial configuration file for a new networking device, or a device that you have
Chapter 4 Lab 4-1, Redistribution Between RIP and OSPF
 hapter 4 Lab 4-1, Redistribution Between RIP and OSPF Topology Objectives Review configuration and verification of RIP and OSPF. onfigure passive interfaces in both RIP and OSPF. Filter routing updates
hapter 4 Lab 4-1, Redistribution Between RIP and OSPF Topology Objectives Review configuration and verification of RIP and OSPF. onfigure passive interfaces in both RIP and OSPF. Filter routing updates
Lab Configuring and Verifying Standard ACLs Topology
 Topology 2013 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 9 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.10.1
Topology 2013 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 9 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.10.1
Lab 19a. Router On A Stick
 Rev. 00.0 Lab a. Router On A Stick c cnac o okbook.com G O A L Configure routing on R, enabling host H to communicate with host H, then make VLAN 0 native on the trunk. Topology You'll need A router (R)
Rev. 00.0 Lab a. Router On A Stick c cnac o okbook.com G O A L Configure routing on R, enabling host H to communicate with host H, then make VLAN 0 native on the trunk. Topology You'll need A router (R)
Lab Configuring OSPF Authentication 2500 Series
 Lab 2.3.4 Configuring OSPF Authentication 2500 Series Objective Setup an IP addressing scheme for Open Shortest Path First (OSPF) area. Configure and verify OSPF routing. Introduce OSPF authentication
Lab 2.3.4 Configuring OSPF Authentication 2500 Series Objective Setup an IP addressing scheme for Open Shortest Path First (OSPF) area. Configure and verify OSPF routing. Introduce OSPF authentication
First-Time Configuration
 CHAPTER 3 This chapter contains information with which you should be familiar before you begin to configure your router for the first time, including information about understanding boot images, interface
CHAPTER 3 This chapter contains information with which you should be familiar before you begin to configure your router for the first time, including information about understanding boot images, interface
Layer3 VPN with OSPF Protocol between CE-PE
 MPLS Layer3 VPN with OSPF Protocol between CE-PE Disclaimer This Configuration Guide is designed to assist members to enhance their skills in particular technology area. While every effort has been made
MPLS Layer3 VPN with OSPF Protocol between CE-PE Disclaimer This Configuration Guide is designed to assist members to enhance their skills in particular technology area. While every effort has been made
Configuring Redundant Routing on the VPN 3000 Concentrator
 Configuring Redundant Routing on the VPN 3000 Concentrator Document ID: 13354 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Router Configurations
Configuring Redundant Routing on the VPN 3000 Concentrator Document ID: 13354 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Router Configurations
LAB MANUAL for Computer Network
 LAB MANUAL for Computer Network CSE-310 F Computer Network Lab L T P - - 3 Class Work : 25 Marks Exam : 25 MARKS Total : 50 Marks This course provides students with hands on training regarding the design,
LAB MANUAL for Computer Network CSE-310 F Computer Network Lab L T P - - 3 Class Work : 25 Marks Exam : 25 MARKS Total : 50 Marks This course provides students with hands on training regarding the design,
Using the Cisco NX-OS Setup Utility
 This chapter contains the following sections: Configuring the Switch, page 1 Configuring the Switch Image Files on the Switch The Cisco Nexus devices have the following images: BIOS and loader images combined
This chapter contains the following sections: Configuring the Switch, page 1 Configuring the Switch Image Files on the Switch The Cisco Nexus devices have the following images: BIOS and loader images combined
Lab Managing Router Configuration Files with Terminal Emulation Software
 Lab Managing Router Configuration Files with Terminal Emulation Software Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.1.1 255.255.255.0 N/A
Lab Managing Router Configuration Files with Terminal Emulation Software Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.1.1 255.255.255.0 N/A
Lab 5.6.2: Challenge RIP Configuration
 Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway BRANCH HQ ISP PC1 PC2 PC3 Fa0/0 S0/0/0 Fa0/0 S0/0/0 S0/0/1 Fa0/0 S0/0/1 NIC NIC NIC Learning Objectives Upon completion
Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway BRANCH HQ ISP PC1 PC2 PC3 Fa0/0 S0/0/0 Fa0/0 S0/0/0 S0/0/1 Fa0/0 S0/0/1 NIC NIC NIC Learning Objectives Upon completion
This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document for non-commercial distribution and
 This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document for non-commercial distribution and exclusive use by instructors in the CCNA Exploration:
This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document for non-commercial distribution and exclusive use by instructors in the CCNA Exploration:
Lab Configuring Basic Switch Settings (Solution)
 (Solution) Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway S1 VLAN 99 192.168.1.2 255.255.255.0 192.168.1.1 PC-A NIC 192.168.1.10 255.255.255.0 192.168.1.1
(Solution) Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway S1 VLAN 99 192.168.1.2 255.255.255.0 192.168.1.1 PC-A NIC 192.168.1.10 255.255.255.0 192.168.1.1
Chapter 8 Lab 8-3, Configuring 6to4 Tunnels
 Chapter 8 Lab 8-3, Configuring 6to4 Tunnels Topology Objectives Configure EIGRP for IPv4. Create a 6to4 tunnel. Configure static IPv6 routes. Background In this lab, you configure EIGRP for full connectivity
Chapter 8 Lab 8-3, Configuring 6to4 Tunnels Topology Objectives Configure EIGRP for IPv4. Create a 6to4 tunnel. Configure static IPv6 routes. Background In this lab, you configure EIGRP for full connectivity
Lab b Simple DMZ Extended Access Lists Instructor Version 2500
 Lab 11.2.3b Simple DMZ Extended Access Lists Instructor Version 2500 Objective In this lab, the use of extended access lists to create a simple DeMilitarized Zone (DMZ) will be learned. 372-833 CCNA 2:
Lab 11.2.3b Simple DMZ Extended Access Lists Instructor Version 2500 Objective In this lab, the use of extended access lists to create a simple DeMilitarized Zone (DMZ) will be learned. 372-833 CCNA 2:
Cisco Branch Routers Series Network Analysis Module (NME-NAM-120S) Installation and Configuration Note, 4.2
 Cisco Branch Routers Series Network Analysis Module (NME-NAM-120S) Installation and Configuration Note, 4.2 The Cisco Network Analysis Module (NAM) is an integrated module that enables network managers
Cisco Branch Routers Series Network Analysis Module (NME-NAM-120S) Installation and Configuration Note, 4.2 The Cisco Network Analysis Module (NAM) is an integrated module that enables network managers
Configuring Network Access to the GGSN
 CHAPTER 7 This chapter describes how to configure access from the gateway GPRS support node (GGSN) to a serving GPRS support node (SGSN), public data network (PDN), and optionally to a Virtual Private
CHAPTER 7 This chapter describes how to configure access from the gateway GPRS support node (GGSN) to a serving GPRS support node (SGSN), public data network (PDN), and optionally to a Virtual Private
Configuring the Switch with the CLI-Based Setup Program
 Configuring the Switch with the CLI-Based Setup Program Accessing the CLI Through Express Setup, page 1 Accessing the CLI Through the Console Port, page 1 Entering the Initial Configuration Information,
Configuring the Switch with the CLI-Based Setup Program Accessing the CLI Through Express Setup, page 1 Accessing the CLI Through the Console Port, page 1 Entering the Initial Configuration Information,
Lab 9.6.2: Challenge EIGRP Configuration Lab
 Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway HQ BRANCH1 BRANCH2 PC1 PC2 PC3 Fa0/0 S0/0/0 S0/0/1 Lo1 Fa0/0 S0/0/0 S0/0/1 Fa0/0 S0/0/0 S0/0/1 NIC NIC NIC All
Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway HQ BRANCH1 BRANCH2 PC1 PC2 PC3 Fa0/0 S0/0/0 S0/0/1 Lo1 Fa0/0 S0/0/0 S0/0/1 Fa0/0 S0/0/0 S0/0/1 NIC NIC NIC All
Using the setup Command Facility
 CHAPTER 2 This chapter describes how to use the setup command facility to configure your Cisco integrated access device (IAD). The setup command facility prompts you to enter information needed to start
CHAPTER 2 This chapter describes how to use the setup command facility to configure your Cisco integrated access device (IAD). The setup command facility prompts you to enter information needed to start
CCNA 1 Chapter 11 V4.0 Answers
 CCNA 1 Chapter 11 V4.0 Answers 1. Refer to the exhibit. What command will place the router into the correct mode to configure an appropriate interface to connect to a LAN? UBAMA# configure terminal UBAMA(config)#
CCNA 1 Chapter 11 V4.0 Answers 1. Refer to the exhibit. What command will place the router into the correct mode to configure an appropriate interface to connect to a LAN? UBAMA# configure terminal UBAMA(config)#
Lab Configuring IPv6 Static and Default Routes (Solution)
 (Solution) Topology Addressing Table Device Interface IPv6 Address / Prefix Length Default Gateway R1 G0/1 2001:DB8:ACAD:A::/64 eui-64 N/A S0/0/1 FC00::1/64 N/A R3 G0/1 2001:DB8:ACAD:B::/64 eui-64 N/A
(Solution) Topology Addressing Table Device Interface IPv6 Address / Prefix Length Default Gateway R1 G0/1 2001:DB8:ACAD:A::/64 eui-64 N/A S0/0/1 FC00::1/64 N/A R3 G0/1 2001:DB8:ACAD:B::/64 eui-64 N/A
Using the Setup Script
 APPENDIX A Using the Setup Script The information herein applies to the Cisco AS5350, Cisco AS5400, and Cisco AS5400HPX universal gateways that the latter requires use of Cisco IOS release 122(2)XB or
APPENDIX A Using the Setup Script The information herein applies to the Cisco AS5350, Cisco AS5400, and Cisco AS5400HPX universal gateways that the latter requires use of Cisco IOS release 122(2)XB or
Before you start the lab exercises see the lab administrator or EEE3080F tutor to get assigned to your routers.
 EEE00F Lab Basics of the Network Lab Student Lab Manual Before you start the lab exercises see the lab administrator or EEE00F tutor to get assigned to your routers. Contents. Resources used in the labs...
EEE00F Lab Basics of the Network Lab Student Lab Manual Before you start the lab exercises see the lab administrator or EEE00F tutor to get assigned to your routers. Contents. Resources used in the labs...
Chapter 4. Network Security. Part II
 Chapter 4 Network Security Part II CCNA4-1 Chapter 4-2 Introducing Network Security Securing Cisco Routers CCNA4-2 Chapter 4-2 Router Security Issues The Role of Routers in Network Security: Router security
Chapter 4 Network Security Part II CCNA4-1 Chapter 4-2 Introducing Network Security Securing Cisco Routers CCNA4-2 Chapter 4-2 Router Security Issues The Role of Routers in Network Security: Router security
Configuring the Switch with the CLI-Based Setup Program
 Configuring the Switch with the CLI-Based Setup Program This appendix contains these topics: Accessing the CLI Through Express Setup, page 1 Accessing the CLI Through the Console Port, page 1 Entering
Configuring the Switch with the CLI-Based Setup Program This appendix contains these topics: Accessing the CLI Through Express Setup, page 1 Accessing the CLI Through the Console Port, page 1 Entering
Chapter 6: Network Layer
 Chapter 6: Network Layer CCNA Routing and Switching Introduction to Networks v6.0 Chapter 6 - Sections & Objectives 6.1 Network Layer Protocols Explain how network layer protocols and services support
Chapter 6: Network Layer CCNA Routing and Switching Introduction to Networks v6.0 Chapter 6 - Sections & Objectives 6.1 Network Layer Protocols Explain how network layer protocols and services support
Shortcut Switching Enhancements for NHRP in DMVPN Networks
 Shortcut Switching Enhancements for NHRP in DMVPN Networks Routers in a Dynamic Multipoint VPN (DMVPN) Phase 3 network use Next Hop Resolution Protocol (NHRP) Shortcut Switching to discover shorter paths
Shortcut Switching Enhancements for NHRP in DMVPN Networks Routers in a Dynamic Multipoint VPN (DMVPN) Phase 3 network use Next Hop Resolution Protocol (NHRP) Shortcut Switching to discover shorter paths
