Reducing the Circuit Window Size in Tor
|
|
|
- Barnard Cooper
- 6 years ago
- Views:
Transcription
1 Reducing the Circuit Window Size in Tor Karsten Loesing Tor Tech Report September 20, Introduction As one approach to make Tor faster, the circuit window size can be reduced from currently 1000 cells to only 101 cells. In theory, the effect is reduced latency for client connections, because the number of cells that are buffered in the Tor network is smaller. This report analyzes the effect in practice. 2 Measurement Setup The measurement setup consists of 1 webserver serving a 40 KiB, a 50 KiB, and a 1 MiB file, 2 Tor exit relays, 2 Tor clients, and 2 SOCKS clients measuring download times. One of the exit relays is compiled with a reduced circuit window size, the other one is built without any code changes. In detail, the measurement setup is as follows: The webserver that serves the 40 KiB, 50 KiB, and 1 MiB test files is The test files containing random data are available under ~karsten/perf/.40kbfile,.50kbfile, and.1mbfile. The first exit relay that is compiled with a reduced circuit window size is echelon1 with fingerprint B1 8F3A 5CA C9A 8FDD 22B3 D0A8 1EBB. Its Tor version is alpha-dev. It is configured to permit exiting using the default exit policy. It has been running as non-exit relay for a few days before starting these measurements. The second exit relay is using Tor version alpha-dev, too, but compiled without code changes. Its nickname is echelon2, and its fingerprint is 3EED FC C06D EF4D DD8 47D It is configured to use the default exit policy and was running as non-exit relay for a few days, too. Both exit relays are running on the same host located in Canada. 1
2 md = 7.68 md = 8.1 Time to connect to website (40 KiB) md = 7.5 md = 7.78 Time to connect to website (50 KiB) md = 6.73md = 6.8 Time to connect to website (1 MiB) Figure 1: Kernel density estimates of times to connect to website The two Tor clients are configured to use no entry guards and to use circuits only with a maximum dirtiness of 1 minute. Both Tor clients are running version alpha-dev. They are located on the same host as the two exit relays. The two SOCKS clients are the trivial SOCKS clients used for other torperf measurements, too. In contrast to previous measurements, the clients specify an exit relay using the.exit notation. 3 Results Results include three data points: The first measured time is the time to connect to the website. This step requires the Tor client to create a circuit using the specified exit and send a CONNECT command to the exit relay. As soon as the exit relay replies with a CONNECTED cell, the connection to the website is established. Figure 1 shows kernel density estimates of the connection times. The second measured time is the time between starting a request and receiving the first byte of the response. Figure 2 shows these times for the three requested file sizes. The third measured time is the overall time to complete a request. This time include all steps from connecting to the website until having received all bytes of the response. Figure 3 shows the distributions of these times. 2
3 Time until receiving first response byte (40 KiB) md = 10.6 md = 11.4 Time until receiving first response byte (50 KiB) md = 10.6md = 10.7 md = 9.54md = 9.7 Time until receiving first response byte (1 MiB) Figure 2: Kernel density estimates of times until receiving first response byte 3
4 Time to complete request (40 KiB) md = 16.7 md = 18.8 md = 18.2 Time to complete request (50 KiB) md = 20.1 md = 92.2 Time to complete request (1 MiB) md = Figure 3: Kernel density estimates of times to complete request 4
5 4 Discussion The results, especially the time to complete requests, indicate an improvement of the circuit window reduction to 101 cells for downloads of 40 KiB files at the cost of significant decreasing performance for 1 MiB files. A possible explanation is that 40 KiB downloads fit into one circuit window of 101 cells in contrast to 50 KiB and 1 MiB downloads. The latter two require additional round-trips for the 101 cells circuit window. However, these are only early measurements of downloads for each setting (or even 820 for 1 MiB downloads) that need to be confirmed in the future. Results might also differ as soon as a certain number of other relays in the network have upgraded to smaller circuit windows. As an alternative to changing the circuit window from 1000 to 101 cells in the code, the circuit window size could be included in the network status consensus. That way, the optimal circuit window size could be switched easily as soon as a certain fraction of relays has upgraded to use the included circuit window size. 5
Measuring the Tor Network Evaluation of Relays from Public Directory Data
 Measuring the Tor Network Evaluation of Relays from Public Directory Data Karsten Loesing karsten@torproject.org Tor Tech Report 2009-06-001 June 22, 2009 Abstract This document contains the results of
Measuring the Tor Network Evaluation of Relays from Public Directory Data Karsten Loesing karsten@torproject.org Tor Tech Report 2009-06-001 June 22, 2009 Abstract This document contains the results of
Counting daily bridge users
 Counting daily bridge users Karsten Loesing karsten@torproject.org Tor Tech Report 212-1-1 October 24, 212 Abstract As part of the Tor Metrics Project, we want to learn how many people use the Tor network
Counting daily bridge users Karsten Loesing karsten@torproject.org Tor Tech Report 212-1-1 October 24, 212 Abstract As part of the Tor Metrics Project, we want to learn how many people use the Tor network
Performance Evaluation of Tor Hidden Services
 University of Bamberg Distributed and Mobile Systems Group Paper on the Seminar Tor Research Topic: Performance Evaluation of Tor Hidden Services Presented by: Christian Wilms Supervisor: Karsten Loesing
University of Bamberg Distributed and Mobile Systems Group Paper on the Seminar Tor Research Topic: Performance Evaluation of Tor Hidden Services Presented by: Christian Wilms Supervisor: Karsten Loesing
CIS-331 Final Exam Spring 2018 Total of 120 Points. Version 1
 Version 1 Instructions 1. Write your name and version number on the top of the yellow paper and the routing tables sheet. 2. Answer Question 2 on the routing tables sheet. 3. Answer Questions 1, 3, 4,
Version 1 Instructions 1. Write your name and version number on the top of the yellow paper and the routing tables sheet. 2. Answer Question 2 on the routing tables sheet. 3. Answer Questions 1, 3, 4,
PuppeTor. Performing automatic tests and measurements in Tor networks. Karsten Loesing. Distributed and Mobile Systems Group, University of Bamberg
 PuppeTor Performing automatic tests and measurements in Tor networks Karsten Loesing Distributed and Mobile Systems Group, University of Bamberg PET-Con 2007, Frankfurt, 2007-08-16 Karsten Loesing (University
PuppeTor Performing automatic tests and measurements in Tor networks Karsten Loesing Distributed and Mobile Systems Group, University of Bamberg PET-Con 2007, Frankfurt, 2007-08-16 Karsten Loesing (University
CIS-331 Final Exam Spring 2015 Total of 115 Points. Version 1
 Version 1 1. (25 Points) Given that a frame is formatted as follows: And given that a datagram is formatted as follows: And given that a TCP segment is formatted as follows: Assuming no options are present
Version 1 1. (25 Points) Given that a frame is formatted as follows: And given that a datagram is formatted as follows: And given that a TCP segment is formatted as follows: Assuming no options are present
Introduction to Tor. January 20, Secure Web Browsing and Anonymity. Tor Mumbai Meetup, Sukhbir Singh
 Introduction to Tor Secure Web Browsing and Anonymity Tor Mumbai Meetup, 2018 Sukhbir Singh sukhbir@torproject.org January 20, 2018 Before We Begin... 2 / 18 Before We Begin... Understand your threat model
Introduction to Tor Secure Web Browsing and Anonymity Tor Mumbai Meetup, 2018 Sukhbir Singh sukhbir@torproject.org January 20, 2018 Before We Begin... 2 / 18 Before We Begin... Understand your threat model
IMUX: Managing Tor Connections from Two to Infinity, and Beyond
 IMUX: Managing Tor Connections from Two to Infinity, and Beyond John Geddes Rob Jansen Nicholas Hopper ABSTRACT University of Minnesota Minneapolis, MN {geddes, hopper}@cs.umn.edu We consider proposals
IMUX: Managing Tor Connections from Two to Infinity, and Beyond John Geddes Rob Jansen Nicholas Hopper ABSTRACT University of Minnesota Minneapolis, MN {geddes, hopper}@cs.umn.edu We consider proposals
CIS-331 Fall 2014 Exam 1 Name: Total of 109 Points Version 1
 Version 1 1. (24 Points) Show the routing tables for routers A, B, C, and D. Make sure you account for traffic to the Internet. Router A Router B Router C Router D Network Next Hop Next Hop Next Hop Next
Version 1 1. (24 Points) Show the routing tables for routers A, B, C, and D. Make sure you account for traffic to the Internet. Router A Router B Router C Router D Network Next Hop Next Hop Next Hop Next
Computer Architecture. R. Poss
 Computer Architecture R. Poss 1 lecture-7-24 september 2015 Virtual Memory cf. Henessy & Patterson, App. C4 2 lecture-7-24 september 2015 Virtual Memory It is easier for the programmer to have a large
Computer Architecture R. Poss 1 lecture-7-24 september 2015 Virtual Memory cf. Henessy & Patterson, App. C4 2 lecture-7-24 september 2015 Virtual Memory It is easier for the programmer to have a large
Anonymous communications: Crowds and Tor
 Anonymous communications: Crowds and Tor Basic concepts What do we want to hide? sender anonymity attacker cannot determine who the sender of a particular message is receiver anonymity attacker cannot
Anonymous communications: Crowds and Tor Basic concepts What do we want to hide? sender anonymity attacker cannot determine who the sender of a particular message is receiver anonymity attacker cannot
Shadow: Real Applications, Simulated Networks. Dr. Rob Jansen U.S. Naval Research Laboratory Center for High Assurance Computer Systems
 Shadow: Real Applications, Simulated Networks Dr. Rob Jansen Center for High Assurance Computer Systems Cyber Modeling and Simulation Technical Working Group Mark Center, Alexandria, VA October 25 th,
Shadow: Real Applications, Simulated Networks Dr. Rob Jansen Center for High Assurance Computer Systems Cyber Modeling and Simulation Technical Working Group Mark Center, Alexandria, VA October 25 th,
Adaptive throttling of Tor clients by entry guards
 Adaptive throttling of Tor clients by entry guards Roger Dingledine arma@torproject.org Tor Tech Report 2010-09-001 September 19, 2010 Abstract Looking for a paper topic (or a thesis topic)? Here s a Tor
Adaptive throttling of Tor clients by entry guards Roger Dingledine arma@torproject.org Tor Tech Report 2010-09-001 September 19, 2010 Abstract Looking for a paper topic (or a thesis topic)? Here s a Tor
Perle Dial-Out User s Guide
 Perle Dial-Out User s Guide 95-2345-05 Copyrights Copyright 1996-2000, Perle Systems Limited and its suppliers. IBM is the registered trademark of International Business Machines Corporation. Microsoft,
Perle Dial-Out User s Guide 95-2345-05 Copyrights Copyright 1996-2000, Perle Systems Limited and its suppliers. IBM is the registered trademark of International Business Machines Corporation. Microsoft,
Onion Routing. Varun Pandey Dept. of Computer Science, Virginia Tech. CS 6204, Spring
 Onion Routing Varun Pandey Dept. of Computer Science, Virginia Tech 1 What is Onion Routing? a distributed overlay network to anonymize TCP based routing Circuit based (clients choose the circuit) Each
Onion Routing Varun Pandey Dept. of Computer Science, Virginia Tech 1 What is Onion Routing? a distributed overlay network to anonymize TCP based routing Circuit based (clients choose the circuit) Each
4. Specifications and Additional Information
 4. Specifications and Additional Information AGX52004-1.0 8B/10B Code This section provides information about the data and control codes for Arria GX devices. Code Notation The 8B/10B data and control
4. Specifications and Additional Information AGX52004-1.0 8B/10B Code This section provides information about the data and control codes for Arria GX devices. Code Notation The 8B/10B data and control
CIS-331 Exam 2 Fall 2015 Total of 105 Points Version 1
 Version 1 1. (20 Points) Given the class A network address 117.0.0.0 will be divided into multiple subnets. a. (5 Points) How many bits will be necessary to address 4,000 subnets? b. (5 Points) What is
Version 1 1. (20 Points) Given the class A network address 117.0.0.0 will be divided into multiple subnets. a. (5 Points) How many bits will be necessary to address 4,000 subnets? b. (5 Points) What is
CIS-331 Spring 2016 Exam 1 Name: Total of 109 Points Version 1
 Version 1 Instructions Write your name on the exam paper. Write your name and version number on the top of the yellow paper. Answer Question 1 on the exam paper. Answer Questions 2-4 on the yellow paper.
Version 1 Instructions Write your name on the exam paper. Write your name and version number on the top of the yellow paper. Answer Question 1 on the exam paper. Answer Questions 2-4 on the yellow paper.
1. Memory technology & Hierarchy
 1 Memory technology & Hierarchy Caching and Virtual Memory Parallel System Architectures Andy D Pimentel Caches and their design cf Henessy & Patterson, Chap 5 Caching - summary Caches are small fast memories
1 Memory technology & Hierarchy Caching and Virtual Memory Parallel System Architectures Andy D Pimentel Caches and their design cf Henessy & Patterson, Chap 5 Caching - summary Caches are small fast memories
Views of Memory. Real machines have limited amounts of memory. Programmer doesn t want to be bothered. 640KB? A few GB? (This laptop = 2GB)
 CS6290 Memory Views of Memory Real machines have limited amounts of memory 640KB? A few GB? (This laptop = 2GB) Programmer doesn t want to be bothered Do you think, oh, this computer only has 128MB so
CS6290 Memory Views of Memory Real machines have limited amounts of memory 640KB? A few GB? (This laptop = 2GB) Programmer doesn t want to be bothered Do you think, oh, this computer only has 128MB so
UNH-IOL MIPI Alliance Test Program
 DSI Receiver Protocol Conformance Test Report UNH-IOL 121 Technology Drive, Suite 2 Durham, NH 03824 +1-603-862-0090 mipilab@iol.unh.edu +1-603-862-0701 Engineer Name engineer@company.com Panel Company
DSI Receiver Protocol Conformance Test Report UNH-IOL 121 Technology Drive, Suite 2 Durham, NH 03824 +1-603-862-0090 mipilab@iol.unh.edu +1-603-862-0701 Engineer Name engineer@company.com Panel Company
Avoiding The Man on the Wire: Improving Tor s Security with Trust-Aware Path Selection
 Avoiding The Man on the Wire: Improving Tor s Security with Trust-Aware Path Selection Aaron Johnson Rob Jansen Aaron D. Jaggard Joan Feigenbaum Paul Syverson (U.S. Naval Research Laboratory) (U.S. Naval
Avoiding The Man on the Wire: Improving Tor s Security with Trust-Aware Path Selection Aaron Johnson Rob Jansen Aaron D. Jaggard Joan Feigenbaum Paul Syverson (U.S. Naval Research Laboratory) (U.S. Naval
DKT 122/3 DIGITAL SYSTEM 1
 Company LOGO DKT 122/3 DIGITAL SYSTEM 1 BOOLEAN ALGEBRA (PART 2) Boolean Algebra Contents Boolean Operations & Expression Laws & Rules of Boolean algebra DeMorgan s Theorems Boolean analysis of logic circuits
Company LOGO DKT 122/3 DIGITAL SYSTEM 1 BOOLEAN ALGEBRA (PART 2) Boolean Algebra Contents Boolean Operations & Expression Laws & Rules of Boolean algebra DeMorgan s Theorems Boolean analysis of logic circuits
Parallel Computing Trends: from MPPs to NoWs
 Parallel Computing Trends: from MPPs to NoWs (from Massively Parallel Processors to Networks of Workstations) Fall Research Forum Oct 18th, 1994 Thorsten von Eicken Department of Computer Science Cornell
Parallel Computing Trends: from MPPs to NoWs (from Massively Parallel Processors to Networks of Workstations) Fall Research Forum Oct 18th, 1994 Thorsten von Eicken Department of Computer Science Cornell
Lecture 7: Ethernet Hardware Addressing and Frame Format. Dr. Mohammed Hawa. Electrical Engineering Department, University of Jordan.
 Lecture 7: Ethernet Hardware Addressing and Frame Format Dr. Mohammed Hawa Electrical Engineering Department University of Jordan EE426: Communication Networks MAC Addresses The shared medium in a LAN
Lecture 7: Ethernet Hardware Addressing and Frame Format Dr. Mohammed Hawa Electrical Engineering Department University of Jordan EE426: Communication Networks MAC Addresses The shared medium in a LAN
CMPE223/CMSE222 Digital Logic
 CMPE223/CMSE222 Digital Logic Optimized Implementation of Logic Functions: Strategy for Minimization, Minimum Product-of-Sums Forms, Incompletely Specified Functions Terminology For a given term, each
CMPE223/CMSE222 Digital Logic Optimized Implementation of Logic Functions: Strategy for Minimization, Minimum Product-of-Sums Forms, Incompletely Specified Functions Terminology For a given term, each
Identifying and characterizing Sybils in the Tor network
 Identifying and characterizing Sybils in the Tor network August 12, 2016 USENIX Security Symposium Philipp Winter Princeton University and Karlstad University Roya Ensafi Princeton University Karsten Loesing
Identifying and characterizing Sybils in the Tor network August 12, 2016 USENIX Security Symposium Philipp Winter Princeton University and Karlstad University Roya Ensafi Princeton University Karsten Loesing
TorScan: Tracing Long-lived Connections and Differential Scanning Attacks
 TorScan: Tracing Long-lived Connections and Differential Scanning Attacks A. Biryukov, I. Pustogarov, R.P. Weinmann University of Luxembourg ivan.pustogarov@uni.lu September 5, 2012 A. Biryukov, I. Pustogarov,
TorScan: Tracing Long-lived Connections and Differential Scanning Attacks A. Biryukov, I. Pustogarov, R.P. Weinmann University of Luxembourg ivan.pustogarov@uni.lu September 5, 2012 A. Biryukov, I. Pustogarov,
Analysis on End-to-End Node Selection Probability in Tor Network
 Analysis on End-to-End Node Selection Probability in Tor Network Saurav Dahal 1, Junghee Lee 2, Jungmin Kang 2 and Seokjoo Shin 1 1 Department of Computer Engineering, Chosun University, Gwangju, South
Analysis on End-to-End Node Selection Probability in Tor Network Saurav Dahal 1, Junghee Lee 2, Jungmin Kang 2 and Seokjoo Shin 1 1 Department of Computer Engineering, Chosun University, Gwangju, South
UNIT-V MEMORY ORGANIZATION
 UNIT-V MEMORY ORGANIZATION 1 The main memory of a computer is semiconductor memory.the main memory unit is basically consists of two kinds of memory: RAM (RWM):Random access memory; which is volatile in
UNIT-V MEMORY ORGANIZATION 1 The main memory of a computer is semiconductor memory.the main memory unit is basically consists of two kinds of memory: RAM (RWM):Random access memory; which is volatile in
Virtual Memory Overview
 Virtual Memory Overview Virtual address (VA): What your program uses Virtual Page Number Page Offset Physical address (PA): What actually determines where in memory to go Physical Page Number Page Offset
Virtual Memory Overview Virtual address (VA): What your program uses Virtual Page Number Page Offset Physical address (PA): What actually determines where in memory to go Physical Page Number Page Offset
Problem 3. (12 points):
 Problem 3. (12 points): This problem tests your understanding of basic cache operations. Harry Q. Bovik has written the mother of all game-of-life programs. The Game-of-life is a computer game that was
Problem 3. (12 points): This problem tests your understanding of basic cache operations. Harry Q. Bovik has written the mother of all game-of-life programs. The Game-of-life is a computer game that was
ECE380 Digital Logic
 ECE38 Digital Logic Optimized Implementation of Logic Functions: Strategy for Minimization, Minimum Product-of-Sums Forms, Incompletely Specified Functions Dr. D. J. Jackson Lecture 8- Terminology For
ECE38 Digital Logic Optimized Implementation of Logic Functions: Strategy for Minimization, Minimum Product-of-Sums Forms, Incompletely Specified Functions Dr. D. J. Jackson Lecture 8- Terminology For
The ZCPR3 INSTALLATION WORKBOOK. by Richard Conn. First Revision, 8 March 1985 Original Draft, 20 February 1985
 The ZCPR3 INSTALLATION WORKBOOK by Richard Conn First Revision, 8 March 1985 Original Draft, 20 February 1985 About this Workbook This workbook takes you through the eight steps of ZCPR3 installation.
The ZCPR3 INSTALLATION WORKBOOK by Richard Conn First Revision, 8 March 1985 Original Draft, 20 February 1985 About this Workbook This workbook takes you through the eight steps of ZCPR3 installation.
UNH-IOL MIPI Alliance Test Program
 CSI-2 Receiver Protocol Conformance Test Report UNH-IOL 121 Technology Drive, Suite 2 Durham, NH 03824 +1-603-862-0090 mipilab@iol.unh.edu +1-603-862-0701 Engineer Name engineer@company.com Host Company
CSI-2 Receiver Protocol Conformance Test Report UNH-IOL 121 Technology Drive, Suite 2 Durham, NH 03824 +1-603-862-0090 mipilab@iol.unh.edu +1-603-862-0701 Engineer Name engineer@company.com Host Company
GSN8 Ethernet Data Logger (optional GPS)
 GSN8 Ethernet Data Logger (optional GPS) TCP Modbus GSX8 TCP Switch Software Version 1.1.4 Revision 170804 [V3NE2P] In TCP Client mode, GSN8 Ethernet Data Logger will initiate the data upload to central
GSN8 Ethernet Data Logger (optional GPS) TCP Modbus GSX8 TCP Switch Software Version 1.1.4 Revision 170804 [V3NE2P] In TCP Client mode, GSN8 Ethernet Data Logger will initiate the data upload to central
Throttling Tor Bandwidth Parasites. Technical Report
 Throttling Tor Bandwidth Parasites Technical Report Department of Computer Science and Engineering University of Minnesota 4-192 Keller Hall 200 Union Street SE Minneapolis, MN 55455-0159 USA TR 11-019
Throttling Tor Bandwidth Parasites Technical Report Department of Computer Science and Engineering University of Minnesota 4-192 Keller Hall 200 Union Street SE Minneapolis, MN 55455-0159 USA TR 11-019
Improving Cache Performance
 Improving Cache Performance Tuesday 27 October 15 Many slides adapted from: and Design, Patterson & Hennessy 5th Edition, 2014, MK and from Prof. Mary Jane Irwin, PSU Summary Previous Class Memory hierarchy
Improving Cache Performance Tuesday 27 October 15 Many slides adapted from: and Design, Patterson & Hennessy 5th Edition, 2014, MK and from Prof. Mary Jane Irwin, PSU Summary Previous Class Memory hierarchy
Research Collection. Systematic Testing of Tor. Master Thesis. ETH Library. Author(s): Lazzari, Marco. Publication Date: 2014
 Research Collection Master Thesis Systematic Testing of Tor Author(s): Lazzari, Marco Publication Date: 2014 Permanent Link: https://doi.org/10.3929/ethz-a-010144381 Rights / License: In Copyright - Non-Commercial
Research Collection Master Thesis Systematic Testing of Tor Author(s): Lazzari, Marco Publication Date: 2014 Permanent Link: https://doi.org/10.3929/ethz-a-010144381 Rights / License: In Copyright - Non-Commercial
Analyzing the Effectiveness of Passive Correlation Attacks on the Tor Anonymity Network
 Wesleyan University The Honors College Analyzing the Effectiveness of Passive Correlation Attacks on the Tor Anonymity Network by Sam DeFabbia-Kane Class of 211 A thesis submitted to the faculty of Wesleyan
Wesleyan University The Honors College Analyzing the Effectiveness of Passive Correlation Attacks on the Tor Anonymity Network by Sam DeFabbia-Kane Class of 211 A thesis submitted to the faculty of Wesleyan
JANUARY 28, 2014, SAN JOSE, CA. Microsoft Lead Partner Architect OS Vendors: What NVM Means to Them
 JANUARY 28, 2014, SAN JOSE, CA PRESENTATION James TITLE Pinkerton GOES HERE Microsoft Lead Partner Architect OS Vendors: What NVM Means to Them Why should NVM be Interesting to OS Vendors? New levels of
JANUARY 28, 2014, SAN JOSE, CA PRESENTATION James TITLE Pinkerton GOES HERE Microsoft Lead Partner Architect OS Vendors: What NVM Means to Them Why should NVM be Interesting to OS Vendors? New levels of
1 Beta extension of the 1394a PHY Link Interface Specification
 1 Beta extension of the 1394a PHY Link Interface Specification 1.1 Introduction The beta PHY- Link interface provides the ability to extend the existing 1394a interface (as currently proposed) to support
1 Beta extension of the 1394a PHY Link Interface Specification 1.1 Introduction The beta PHY- Link interface provides the ability to extend the existing 1394a interface (as currently proposed) to support
a) Memory management unit b) CPU c) PCI d) None of the mentioned
 1. CPU fetches the instruction from memory according to the value of a) program counter b) status register c) instruction register d) program status word 2. Which one of the following is the address generated
1. CPU fetches the instruction from memory according to the value of a) program counter b) status register c) instruction register d) program status word 2. Which one of the following is the address generated
Digital Lighting Systems, Inc. CD400-DMX DMX512 Four Channel Dimmer and Switch module
 , Inc. DMX512 Four Channel Dimmer and Switch module Input: 5 Amps @ 6-24 VDC Outputs: 5 Amps Maximum each, total 4 outputs 8 Amps Maximum. FRONT BACK USER'S MANUAL -UM User's Manual - Page 1 GENERAL DESCRIPTION
, Inc. DMX512 Four Channel Dimmer and Switch module Input: 5 Amps @ 6-24 VDC Outputs: 5 Amps Maximum each, total 4 outputs 8 Amps Maximum. FRONT BACK USER'S MANUAL -UM User's Manual - Page 1 GENERAL DESCRIPTION
Tor s Been KIST: A Case Study of Transitioning Tor Research to Practice
 Tor s Been KIST: A Case Study of Transitioning Tor Research to Practice Rob Jansen and Matthew Traudt U.S. Naval Research Laboratory {rob.g.jansen, matthew.traudt}@nrl.navy.mil Abstract Most computer science
Tor s Been KIST: A Case Study of Transitioning Tor Research to Practice Rob Jansen and Matthew Traudt U.S. Naval Research Laboratory {rob.g.jansen, matthew.traudt}@nrl.navy.mil Abstract Most computer science
The cache is 4-way set associative, with 4-byte blocks, and 16 total lines
 Sample Problem 1 Assume the following memory setup: Virtual addresses are 20 bits wide Physical addresses are 15 bits wide The page size if 1KB (2 10 bytes) The TLB is 2-way set associative, with 8 total
Sample Problem 1 Assume the following memory setup: Virtual addresses are 20 bits wide Physical addresses are 15 bits wide The page size if 1KB (2 10 bytes) The TLB is 2-way set associative, with 8 total
CE Advanced Network Security Anonymity II
 CE 817 - Advanced Network Security Anonymity II Lecture 19 Mehdi Kharrazi Department of Computer Engineering Sharif University of Technology Acknowledgments: Some of the slides are fully or partially obtained
CE 817 - Advanced Network Security Anonymity II Lecture 19 Mehdi Kharrazi Department of Computer Engineering Sharif University of Technology Acknowledgments: Some of the slides are fully or partially obtained
Memory Hierarchies 2009 DAT105
 Memory Hierarchies Cache performance issues (5.1) Virtual memory (C.4) Cache performance improvement techniques (5.2) Hit-time improvement techniques Miss-rate improvement techniques Miss-penalty improvement
Memory Hierarchies Cache performance issues (5.1) Virtual memory (C.4) Cache performance improvement techniques (5.2) Hit-time improvement techniques Miss-rate improvement techniques Miss-penalty improvement
CIS-331 Fall 2013 Exam 1 Name: Total of 120 Points Version 1
 Version 1 1. (24 Points) Show the routing tables for routers A, B, C, and D. Make sure you account for traffic to the Internet. NOTE: Router E should only be used for Internet traffic. Router A Router
Version 1 1. (24 Points) Show the routing tables for routers A, B, C, and D. Make sure you account for traffic to the Internet. NOTE: Router E should only be used for Internet traffic. Router A Router
2 ND GENERATION ONION ROUTER
 2 ND GENERATION ONION ROUTER Roger Dingledine, Nick Mathewson and Paul Syverson Presenter: Alejandro Villanueva Agenda Threat model Cells and circuits Other features Related work How does it work? Rendezvous
2 ND GENERATION ONION ROUTER Roger Dingledine, Nick Mathewson and Paul Syverson Presenter: Alejandro Villanueva Agenda Threat model Cells and circuits Other features Related work How does it work? Rendezvous
ABRA CADABRA: Magically Increasing Network Utilization in Tor by Avoiding Bottlenecks
 ABRA CADABRA: Magically Increasing Network Utilization in Tor by Avoiding Bottlenecks John Geddes University of Minnesota geddes@cs.umn.edu Mike Schliep University of Minnesota schliep@cs.umn.edu Nicholas
ABRA CADABRA: Magically Increasing Network Utilization in Tor by Avoiding Bottlenecks John Geddes University of Minnesota geddes@cs.umn.edu Mike Schliep University of Minnesota schliep@cs.umn.edu Nicholas
Challenges in protecting Tor hidden services from botnet abuse
 Challenges in protecting Tor hidden services from botnet abuse Nicholas Hopper University of Minnesota, Minneapolis, MN USA hopper@cs.umn.edu Abstract. In August 2013, the Tor network experienced a sudden,
Challenges in protecting Tor hidden services from botnet abuse Nicholas Hopper University of Minnesota, Minneapolis, MN USA hopper@cs.umn.edu Abstract. In August 2013, the Tor network experienced a sudden,
Privacy defense on the Internet. Csaba Kiraly
 Advanced Networking Privacy defense on the Internet Csaba Kiraly 1 Topics Anonymity on the Internet Chaum Mix Mix network & Onion Routing Low-latency anonymous routing 2 Anonymity: Chaum mix David L. Chaum
Advanced Networking Privacy defense on the Internet Csaba Kiraly 1 Topics Anonymity on the Internet Chaum Mix Mix network & Onion Routing Low-latency anonymous routing 2 Anonymity: Chaum mix David L. Chaum
CS106X Handout 03 Autumn 2012 September 24 th, 2012 Getting Started
 CS106X Handout 03 Autumn 2012 September 24 th, 2012 Getting Started Handout written by Julie Zelenski, Mehran Sahami, Robert Plummer, and Jerry Cain. After today s lecture, you should run home and read
CS106X Handout 03 Autumn 2012 September 24 th, 2012 Getting Started Handout written by Julie Zelenski, Mehran Sahami, Robert Plummer, and Jerry Cain. After today s lecture, you should run home and read
Mid Term from Feb-2005 to Nov 2012 CS604- Operating System
 Mid Term from Feb-2005 to Nov 2012 CS604- Operating System Latest Solved from Mid term Papers Resource Person Hina 1-The problem with priority scheduling algorithm is. Deadlock Starvation (Page# 84) Aging
Mid Term from Feb-2005 to Nov 2012 CS604- Operating System Latest Solved from Mid term Papers Resource Person Hina 1-The problem with priority scheduling algorithm is. Deadlock Starvation (Page# 84) Aging
Using Multilink PPP over Frame Relay
 Using Multilink PPP over Frame Relay Multilink PPP is a method used to reduce latency and jitter for real-time traffic. This module contains conceptual information and configuration tasks for using Multilink
Using Multilink PPP over Frame Relay Multilink PPP is a method used to reduce latency and jitter for real-time traffic. This module contains conceptual information and configuration tasks for using Multilink
Switching and Forwarding - continued
 Fall 9/7 CptS/EE 555 Fall 9/7 CptS/EE 555 4 Housekeeping Look at select system call See homework solutions on the Lecture Notes web page for answer to the probability difficulties we (I) had last time
Fall 9/7 CptS/EE 555 Fall 9/7 CptS/EE 555 4 Housekeeping Look at select system call See homework solutions on the Lecture Notes web page for answer to the probability difficulties we (I) had last time
Switching and Forwarding - continued
 Fall 9/ CptS/EE 555 Fall 9/ CptS/EE 555 4 Housekeeping Look at select system call See homework solutions on the Lecture Notes web page for answer to the probability difficulties we (I) had last time No
Fall 9/ CptS/EE 555 Fall 9/ CptS/EE 555 4 Housekeeping Look at select system call See homework solutions on the Lecture Notes web page for answer to the probability difficulties we (I) had last time No
CS/COE 1550
 CS/COE 1550 www.cs.pitt.edu/~nlf4/cs1550/ Virtual Memory What if a program is too big for memory? Ye olde solution: Overlays! Programmers split their programs up into overlays containing a subset of the
CS/COE 1550 www.cs.pitt.edu/~nlf4/cs1550/ Virtual Memory What if a program is too big for memory? Ye olde solution: Overlays! Programmers split their programs up into overlays containing a subset of the
Attacking Tor with covert channel based on cell counting
 Technion, Winter 2011/12 Semester 236349 - Project in Computer Security Attacking Tor with covert channel based on cell counting Final report Matan Peled 200729218 Dan Goldstein 052861747 Alexander Yavorovsky
Technion, Winter 2011/12 Semester 236349 - Project in Computer Security Attacking Tor with covert channel based on cell counting Final report Matan Peled 200729218 Dan Goldstein 052861747 Alexander Yavorovsky
Beyond Latency and Throughput
 Beyond Latency and Throughput Performance for Heterogeneous Multi-Core Architectures JoAnn M. Paul Virginia Tech, ECE National Capital Region Common basis for two themes Flynn s Taxonomy Computers viewed
Beyond Latency and Throughput Performance for Heterogeneous Multi-Core Architectures JoAnn M. Paul Virginia Tech, ECE National Capital Region Common basis for two themes Flynn s Taxonomy Computers viewed
DefenestraTor: Throwing out Windows in Tor
 DefenestraTor: Throwing out Windows in Tor Mashael AlSabah 1, Kevin Bauer 2, an Goldberg 1, Dirk Grunwald 2, Damon McCoy 3, Stefan Savage 3, and Geoffrey Voelker 3 1 University of Waterloo {malsabah,iang}@cs.uwaterloo.ca
DefenestraTor: Throwing out Windows in Tor Mashael AlSabah 1, Kevin Bauer 2, an Goldberg 1, Dirk Grunwald 2, Damon McCoy 3, Stefan Savage 3, and Geoffrey Voelker 3 1 University of Waterloo {malsabah,iang}@cs.uwaterloo.ca
Software Pipelining for Coarse-Grained Reconfigurable Instruction Set Processors
 Software Pipelining for Coarse-Grained Reconfigurable Instruction Set Processors Francisco Barat, Murali Jayapala, Pieter Op de Beeck and Geert Deconinck K.U.Leuven, Belgium. {f-barat, j4murali}@ieee.org,
Software Pipelining for Coarse-Grained Reconfigurable Instruction Set Processors Francisco Barat, Murali Jayapala, Pieter Op de Beeck and Geert Deconinck K.U.Leuven, Belgium. {f-barat, j4murali}@ieee.org,
Address Space Randomization
 Address Space Randomization A n E f f e c t i v e I m p l e m e n t a t i o n Michael Cloppert May, 2006 Address Space Randomization Theory Randomize location of memory objects Libraries Heap User, kernel-space
Address Space Randomization A n E f f e c t i v e I m p l e m e n t a t i o n Michael Cloppert May, 2006 Address Space Randomization Theory Randomize location of memory objects Libraries Heap User, kernel-space
COMP9242 Advanced OS. S2/2017 W03: Caches: What Every OS Designer Must
 COMP9242 Advanced OS S2/2017 W03: Caches: What Every OS Designer Must Know @GernotHeiser Copyright Notice These slides are distributed under the Creative Commons Attribution 3.0 License You are free: to
COMP9242 Advanced OS S2/2017 W03: Caches: What Every OS Designer Must Know @GernotHeiser Copyright Notice These slides are distributed under the Creative Commons Attribution 3.0 License You are free: to
QoS: Time-Based Thresholds for WRED and Queue Limit
 QoS: Time-Based Thresholds for WRED and Queue Limit The QoS: Time-Based Thresholds for WRED and Queue Limit feature allows you to specify the Weighted Random Early Detection (WRED) minimum and maximum
QoS: Time-Based Thresholds for WRED and Queue Limit The QoS: Time-Based Thresholds for WRED and Queue Limit feature allows you to specify the Weighted Random Early Detection (WRED) minimum and maximum
Converting Fractions to Decimals
 Converting Fractions to Decimals There is a close relationship between fractions and decimals. In fact, fractions and decimals are just two different ways of writing numbers. For example, consider and
Converting Fractions to Decimals There is a close relationship between fractions and decimals. In fact, fractions and decimals are just two different ways of writing numbers. For example, consider and
CSE 431 Computer Architecture Fall Chapter 5A: Exploiting the Memory Hierarchy, Part 1
 CSE 431 Computer Architecture Fall 2008 Chapter 5A: Exploiting the Memory Hierarchy, Part 1 Mary Jane Irwin ( www.cse.psu.edu/~mji ) [Adapted from Computer Organization and Design, 4 th Edition, Patterson
CSE 431 Computer Architecture Fall 2008 Chapter 5A: Exploiting the Memory Hierarchy, Part 1 Mary Jane Irwin ( www.cse.psu.edu/~mji ) [Adapted from Computer Organization and Design, 4 th Edition, Patterson
Low-Cost Traffic Analysis of Tor
 Low-Cost Traffic Analysis of Tor Steven J. Murdoch, George Danezis University of Cambridge, Computer Laboratory Review of Tor Support anonymous transport of TCP streams over the Internet Support anonymous
Low-Cost Traffic Analysis of Tor Steven J. Murdoch, George Danezis University of Cambridge, Computer Laboratory Review of Tor Support anonymous transport of TCP streams over the Internet Support anonymous
Challenges in building overlay networks: a case study of Tor. Steven Murdoch Principal Research Fellow University College London
 Challenges in building overlay networks: a case study of Steven Murdoch Principal Research Fellow University College London Who uses? Ordinary people e.g. to avoid unscrupulous marketers, protect children,
Challenges in building overlay networks: a case study of Steven Murdoch Principal Research Fellow University College London Who uses? Ordinary people e.g. to avoid unscrupulous marketers, protect children,
Bits, bytes and digital information. Lecture 2 COMPSCI111/111G
 Bits, bytes and digital information Lecture 2 COMPSCI111/111G Today s lecture Understand the difference between analogue and digital information Convert between decimal numbers and binary numbers Analogue
Bits, bytes and digital information Lecture 2 COMPSCI111/111G Today s lecture Understand the difference between analogue and digital information Convert between decimal numbers and binary numbers Analogue
DRAM Tutorial Lecture. Vivek Seshadri
 DRAM Tutorial 18-447 Lecture Vivek Seshadri DRAM Module and Chip 2 Goals Cost Latency Bandwidth Parallelism Power Energy 3 DRAM Chip Bank I/O 4 Sense Amplifier top enable Inverter bottom 5 Sense Amplifier
DRAM Tutorial 18-447 Lecture Vivek Seshadri DRAM Module and Chip 2 Goals Cost Latency Bandwidth Parallelism Power Energy 3 DRAM Chip Bank I/O 4 Sense Amplifier top enable Inverter bottom 5 Sense Amplifier
5G Overview. Aminata A. Garba Carnegie Mellon University, Africa
 5G Overview Aminata A. Garba Carnegie Mellon University, Africa 5G Views View 1 The hyper-connected generation: A blend of technologies (pre-existing) covering 2G, 3G, 4G, Wi-fi, Wimax, etc. higher coverage
5G Overview Aminata A. Garba Carnegie Mellon University, Africa 5G Views View 1 The hyper-connected generation: A blend of technologies (pre-existing) covering 2G, 3G, 4G, Wi-fi, Wimax, etc. higher coverage
CS 61C: Great Ideas in Computer Architecture. Direct Mapped Caches
 CS 61C: Great Ideas in Computer Architecture Direct Mapped Caches Instructor: Justin Hsia 7/05/2012 Summer 2012 Lecture #11 1 Review of Last Lecture Floating point (single and double precision) approximates
CS 61C: Great Ideas in Computer Architecture Direct Mapped Caches Instructor: Justin Hsia 7/05/2012 Summer 2012 Lecture #11 1 Review of Last Lecture Floating point (single and double precision) approximates
Declaring Pointers. Declaration of pointers <type> *variable <type> *variable = initial-value Examples:
 1 Programming in C Pointer Variable A variable that stores a memory address Allows C programs to simulate call-by-reference Allows a programmer to create and manipulate dynamic data structures Must be
1 Programming in C Pointer Variable A variable that stores a memory address Allows C programs to simulate call-by-reference Allows a programmer to create and manipulate dynamic data structures Must be
Terawave Communications, Inc. P13- An EPON System Ryan Hirth September 2001 IEEE 802.3ah(EFM) Copenhagen,Denmark
 Terawave Communications, Inc. P13- An EPON System Ryan Hirth September 2001 IEEE 802.3ah(EFM) Copenhagen,Denmark EPON Goals Advanced features in the OLT The OLT determines the performance of the system
Terawave Communications, Inc. P13- An EPON System Ryan Hirth September 2001 IEEE 802.3ah(EFM) Copenhagen,Denmark EPON Goals Advanced features in the OLT The OLT determines the performance of the system
Cell Bell What's Ringing in Calc?
 Cell Bell What's Ringing in Calc? Eike Rathke (erack) erack@redhat.com ROME 13 October 2017 About the Speaker Eike Rathke, known on the net as erack Based in Hamburg, Germany Worked on StarOffice from
Cell Bell What's Ringing in Calc? Eike Rathke (erack) erack@redhat.com ROME 13 October 2017 About the Speaker Eike Rathke, known on the net as erack Based in Hamburg, Germany Worked on StarOffice from
CS650 Computer Architecture. Lecture 9 Memory Hierarchy - Main Memory
 CS65 Computer Architecture Lecture 9 Memory Hierarchy - Main Memory Andrew Sohn Computer Science Department New Jersey Institute of Technology Lecture 9: Main Memory 9-/ /6/ A. Sohn Memory Cycle Time 5
CS65 Computer Architecture Lecture 9 Memory Hierarchy - Main Memory Andrew Sohn Computer Science Department New Jersey Institute of Technology Lecture 9: Main Memory 9-/ /6/ A. Sohn Memory Cycle Time 5
LINKING TOR CIRCUITS
 LINKING TOR CIRCUITS MSc Information Security, 2014 University College London Otto Huhta Supervisor: Dr George Danezis This report is submitted as part requirement for the MSc in Information Security at
LINKING TOR CIRCUITS MSc Information Security, 2014 University College London Otto Huhta Supervisor: Dr George Danezis This report is submitted as part requirement for the MSc in Information Security at
Registers. Instruction Memory A L U. Data Memory C O N T R O L M U X A D D A D D. Sh L 2 M U X. Sign Ext M U X ALU CTL INSTRUCTION FETCH
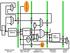 PC Instruction Memory 4 M U X Registers Sign Ext M U X Sh L 2 Data Memory M U X C O T R O L ALU CTL ISTRUCTIO FETCH ISTR DECODE REG FETCH EXECUTE/ ADDRESS CALC MEMOR ACCESS WRITE BACK A D D A D D A L U
PC Instruction Memory 4 M U X Registers Sign Ext M U X Sh L 2 Data Memory M U X C O T R O L ALU CTL ISTRUCTIO FETCH ISTR DECODE REG FETCH EXECUTE/ ADDRESS CALC MEMOR ACCESS WRITE BACK A D D A D D A L U
Using Multilink PPP over Frame Relay
 Multilink PPP is a method used to reduce latency and jitter for real-time traffic. This module contains conceptual information and configuration tasks for using Multilink PPP over Frame Relay. Finding
Multilink PPP is a method used to reduce latency and jitter for real-time traffic. This module contains conceptual information and configuration tasks for using Multilink PPP over Frame Relay. Finding
Digital Lighting Systems, Inc.
 Digital Lighting Systems, Inc. Four Channel Dry Contacts Relays Switch Pack DMX512 compatible USER'S MANUAL -UM User's Manual - Page 1 GENERAL DESCRIPTION The is a 4-channel DMX-512 compatible electro-mechanical
Digital Lighting Systems, Inc. Four Channel Dry Contacts Relays Switch Pack DMX512 compatible USER'S MANUAL -UM User's Manual - Page 1 GENERAL DESCRIPTION The is a 4-channel DMX-512 compatible electro-mechanical
COSC 3406: COMPUTER ORGANIZATION
 COSC 3406: COMPUTER ORGANIZATION Home-Work 5 Due Date: Friday, December 8 by 2.00 pm Instructions for submitting: Type your answers and send it by email or take a printout or handwritten (legible) on paper,
COSC 3406: COMPUTER ORGANIZATION Home-Work 5 Due Date: Friday, December 8 by 2.00 pm Instructions for submitting: Type your answers and send it by email or take a printout or handwritten (legible) on paper,
CE161-4-AU UNIVERSITY OF ESSEX. Undergraduate Examinations 2014 DIGITAL SYSTEMS ARCHITECTURE. Time allowed: TWO hours
 CE161-4-AU UNIVERSITY OF ESSEX Undergraduate Examinations 2014 DIGITAL SYSTEMS ARCHITECTURE Time allowed: TWO hours The following items are provided: Graph paper (available on invigilator s desk) Candidates
CE161-4-AU UNIVERSITY OF ESSEX Undergraduate Examinations 2014 DIGITAL SYSTEMS ARCHITECTURE Time allowed: TWO hours The following items are provided: Graph paper (available on invigilator s desk) Candidates
E-rate Program Applicant Training. Eligible Services. September November Universal Service Administrative Company. All rights reserved.
 E-rate Program Applicant Training Eligible Services September November 2016 Overview FY2017 Eligible Services List (ESL) Category One Broadband Voice Services Category Two Internal Connections Managed
E-rate Program Applicant Training Eligible Services September November 2016 Overview FY2017 Eligible Services List (ESL) Category One Broadband Voice Services Category Two Internal Connections Managed
A SIMPLE INTRODUCTION TO TOR
 A SIMPLE INTRODUCTION TO TOR The Onion Router Fabrizio d'amore May 2015 Tor 2 Privacy on Public Networks Internet is designed as a public network Wi-Fi access points, network routers see all traffic that
A SIMPLE INTRODUCTION TO TOR The Onion Router Fabrizio d'amore May 2015 Tor 2 Privacy on Public Networks Internet is designed as a public network Wi-Fi access points, network routers see all traffic that
CSE Qualifying Exam, Spring February 2, 2008
 CSE Qualifying Exam, Spring 2008 February 2, 2008 Architecture 1. You are building a system around a processor with in-order execution that runs at 1.1 GHz and has a CPI of 0.7 excluding memory accesses.
CSE Qualifying Exam, Spring 2008 February 2, 2008 Architecture 1. You are building a system around a processor with in-order execution that runs at 1.1 GHz and has a CPI of 0.7 excluding memory accesses.
Memory Hierarchy Motivation, Definitions, Four Questions about Memory Hierarchy
 Memory Hierarchy Motivation, Definitions, Four Questions about Memory Hierarchy Soner Onder Michigan Technological University Randy Katz & David A. Patterson University of California, Berkeley Levels in
Memory Hierarchy Motivation, Definitions, Four Questions about Memory Hierarchy Soner Onder Michigan Technological University Randy Katz & David A. Patterson University of California, Berkeley Levels in
Lab 6.7.1: Ping and Traceroute
 Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway R1-ISP R2-Central Eagle Server S0/0/0 10.10.10.6 255.255.255.252 N/A Fa0/0 192.168.254.253 255.255.255.0 N/A S0/0/0
Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway R1-ISP R2-Central Eagle Server S0/0/0 10.10.10.6 255.255.255.252 N/A Fa0/0 192.168.254.253 255.255.255.0 N/A S0/0/0
Anonymity C S A D VA N C E D S E C U R I T Y TO P I C S P R E S E N TAT I O N BY: PA N AY I OTO U M A R KO S 4 T H O F A P R I L
 Anonymity C S 6 8 2 A D VA N C E D S E C U R I T Y TO P I C S P R E S E N TAT I O N BY: PA N AY I OTO U M A R KO S 4 T H O F A P R I L 2 0 1 9 Tor: The Second- Generation Onion Router R. DINGLEDINE N.
Anonymity C S 6 8 2 A D VA N C E D S E C U R I T Y TO P I C S P R E S E N TAT I O N BY: PA N AY I OTO U M A R KO S 4 T H O F A P R I L 2 0 1 9 Tor: The Second- Generation Onion Router R. DINGLEDINE N.
Industrial Network UPS Firmware Release Notes
 Industrial Network UPS Firmware Release Notes 200.300 World Headquarters U.S.A. 18900 Panduit Drive Tinley Park, IL 60487 P: 800-777-3300 www.panduit.com 1 Contents General... 2 Supported Hardware... 2
Industrial Network UPS Firmware Release Notes 200.300 World Headquarters U.S.A. 18900 Panduit Drive Tinley Park, IL 60487 P: 800-777-3300 www.panduit.com 1 Contents General... 2 Supported Hardware... 2
CSF Cache Introduction. [Adapted from Computer Organization and Design, Patterson & Hennessy, 2005]
![CSF Cache Introduction. [Adapted from Computer Organization and Design, Patterson & Hennessy, 2005] CSF Cache Introduction. [Adapted from Computer Organization and Design, Patterson & Hennessy, 2005]](/thumbs/73/69213006.jpg) CSF Cache Introduction [Adapted from Computer Organization and Design, Patterson & Hennessy, 2005] Review: The Memory Hierarchy Take advantage of the principle of locality to present the user with as much
CSF Cache Introduction [Adapted from Computer Organization and Design, Patterson & Hennessy, 2005] Review: The Memory Hierarchy Take advantage of the principle of locality to present the user with as much
Tor: Online anonymity, privacy, and security.
 Tor: Online anonymity, privacy, and security. Runa A. Sandvik runa@torproject.org 12 September 2011 Runa A. Sandvik runa@torproject.org () Tor: Online anonymity, privacy, and security. 12 September 2011
Tor: Online anonymity, privacy, and security. Runa A. Sandvik runa@torproject.org 12 September 2011 Runa A. Sandvik runa@torproject.org () Tor: Online anonymity, privacy, and security. 12 September 2011
Random Access Memory (RAM)
 Random Access Memory (RAM) EED2003 Digital Design Dr. Ahmet ÖZKURT Dr. Hakkı YALAZAN 1 Overview Memory is a collection of storage cells with associated input and output circuitry Possible to read and write
Random Access Memory (RAM) EED2003 Digital Design Dr. Ahmet ÖZKURT Dr. Hakkı YALAZAN 1 Overview Memory is a collection of storage cells with associated input and output circuitry Possible to read and write
(MCQZ-CS604 Operating Systems)
 command to resume the execution of a suspended job in the foreground fg (Page 68) bg jobs kill commands in Linux is used to copy file is cp (Page 30) mv mkdir The process id returned to the child process
command to resume the execution of a suspended job in the foreground fg (Page 68) bg jobs kill commands in Linux is used to copy file is cp (Page 30) mv mkdir The process id returned to the child process
Lecture 5: Directory Protocols. Topics: directory-based cache coherence implementations
 Lecture 5: Directory Protocols Topics: directory-based cache coherence implementations 1 Flat Memory-Based Directories Block size = 128 B Memory in each node = 1 GB Cache in each node = 1 MB For 64 nodes
Lecture 5: Directory Protocols Topics: directory-based cache coherence implementations 1 Flat Memory-Based Directories Block size = 128 B Memory in each node = 1 GB Cache in each node = 1 MB For 64 nodes
CC888 EZcarsharing Control System & T-Box Communication Protocol-V3.5
 CC888 EZcarsharing Control System & T-Box Communication Protocol-V3.5 This Protocol is used for communication between car sharing control system and the platform server, command & message from server to
CC888 EZcarsharing Control System & T-Box Communication Protocol-V3.5 This Protocol is used for communication between car sharing control system and the platform server, command & message from server to
Safely Measuring Tor. Rob Jansen U.S. Naval Research Laboratory Center for High Assurance Computer Systems
 Safely Measuring Tor Safely Measuring Tor, Rob Jansen and Aaron Johnson, In the Proceedings of the 23rd ACM Conference on Computer and Communication Security (CCS 2016). Rob Jansen Center for High Assurance
Safely Measuring Tor Safely Measuring Tor, Rob Jansen and Aaron Johnson, In the Proceedings of the 23rd ACM Conference on Computer and Communication Security (CCS 2016). Rob Jansen Center for High Assurance
Safely Measuring Tor. Rob Jansen U.S. Naval Research Laboratory Center for High Assurance Computer Systems
 Safely Measuring Tor Safely Measuring Tor, Rob Jansen and Aaron Johnson, In the Proceedings of the 23rd ACM Conference on Computer and Communication Security (CCS 2016). Rob Jansen Center for High Assurance
Safely Measuring Tor Safely Measuring Tor, Rob Jansen and Aaron Johnson, In the Proceedings of the 23rd ACM Conference on Computer and Communication Security (CCS 2016). Rob Jansen Center for High Assurance
CMSC411 Fall 2013 Midterm 2 Solutions
 CMSC411 Fall 2013 Midterm 2 Solutions 1. (12 pts) Memory hierarchy a. (6 pts) Suppose we have a virtual memory of size 64 GB, or 2 36 bytes, where pages are 16 KB (2 14 bytes) each, and the machine has
CMSC411 Fall 2013 Midterm 2 Solutions 1. (12 pts) Memory hierarchy a. (6 pts) Suppose we have a virtual memory of size 64 GB, or 2 36 bytes, where pages are 16 KB (2 14 bytes) each, and the machine has
